Digital image watermarking method based on adversarial attack
A digital image and watermark technology, applied in the fields of image processing and information hiding, can solve the problems of weak watermark robustness, poor watermark invisibility, and low watermark embedding capacity, and achieve strong watermark invisibility and high watermark embedding capacity. , the effect of increasing the watermark embedding capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
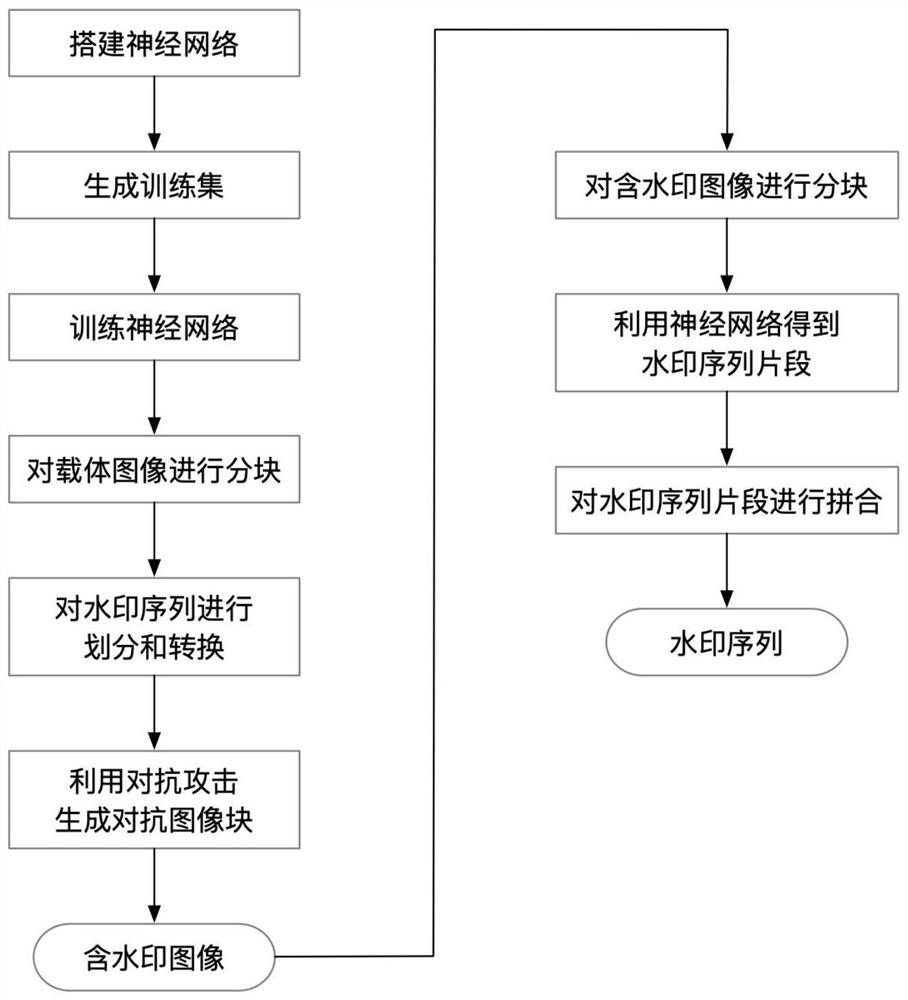
[0040] The present invention will be described in detail below in conjunction with the accompanying drawings.
[0041] refer to figure 1 , to further describe in detail the specific steps realized by the method of the present invention.
[0042] Step 1. Construct a neural network with an input dimension of 1024 and an output dimension of 10 and set parameters.
[0043] Build a 12-layer neural network, its structure is as follows: the first convolutional layer, the second convolutional layer, the first pooling layer, the first dropout layer, the third convolutional layer, the fourth convolutional layer, the second The pooling layer, the second dropout layer, the flattening layer, the first fully connected layer, the third dropout layer, and the second fully connected layer.
[0044] Set the output channels of the first to fourth convolutional layers to 32, 32, 64, and 64 respectively, and the convolution kernel sizes to 32×32, 30×30, 15×15, 13×13, and the step sizes are all set
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap