Method and apparatus for limiting session number
A technology for restricting groups and establishing sessions, which is applied in the field of communication and can solve problems such as occupying session resources, occupying the number of sessions, and being difficult to control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
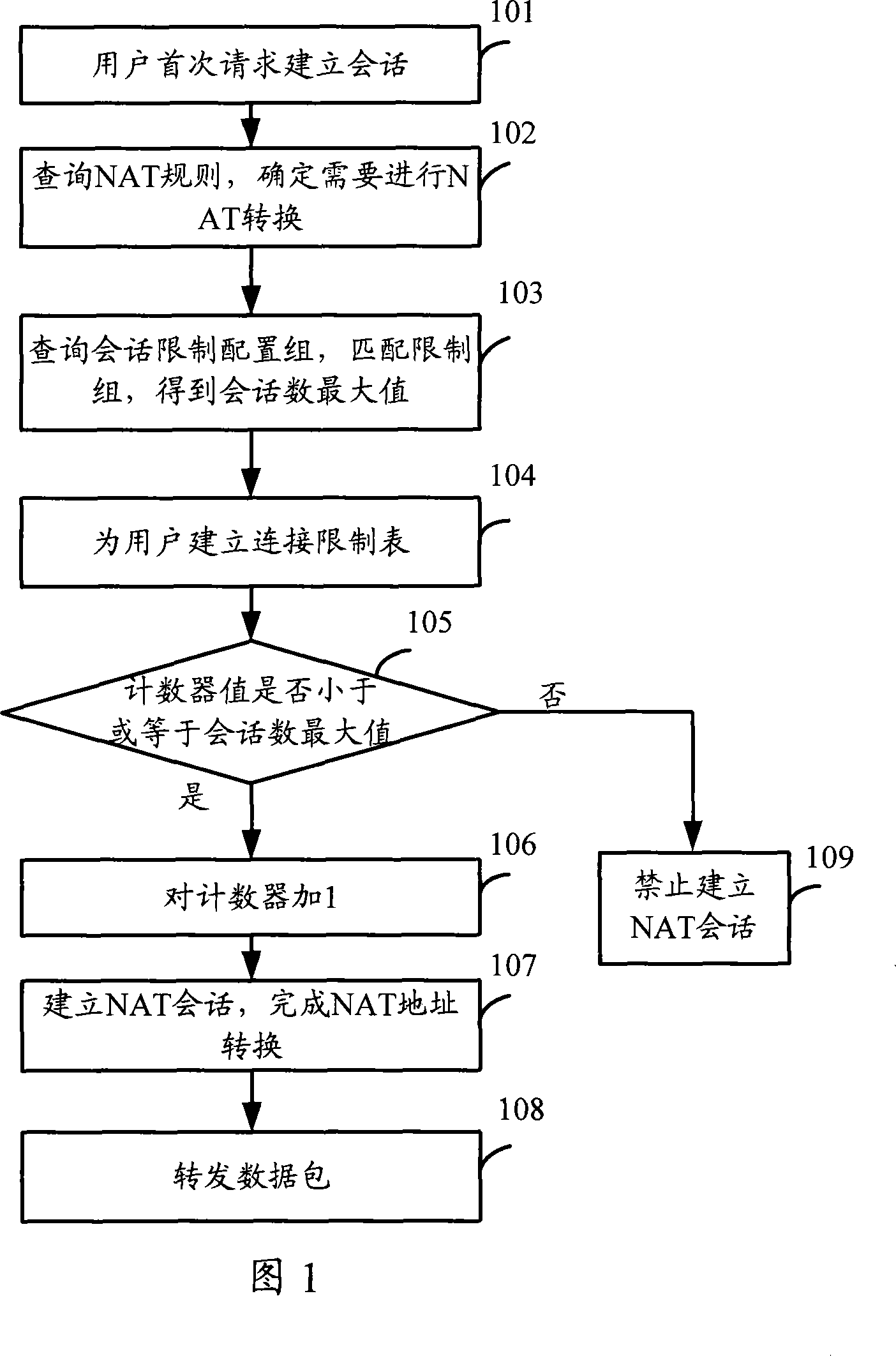
[0035] (1) To configure the maximum number of sessions and counters for various applications, each type of application corresponds to a restriction group, then multiple restriction groups can form a session restriction configuration table.
[0036] See Table 1, which is a typical example of the session restriction configuration table formed by setting the ACL by using "protocol type, destination IP and destination port".
[0037] Table 1
[0038] Restricted group number
[0039] Wherein, each restriction group number represents a restriction group, that is, an application. Each restriction group can contain one ACL, such as restriction group 1; it can also contain multiple ACLs, for example, restriction group 2, which consists of "protocol type: TCP, destination port: 80" and "protocol type: TCP, destination port : 443" consists of two ACLs. Assume that the ACL contained in the restriction group 2 represents the HTTP protocol, that is, only the data flows that meet th
Embodiment 2
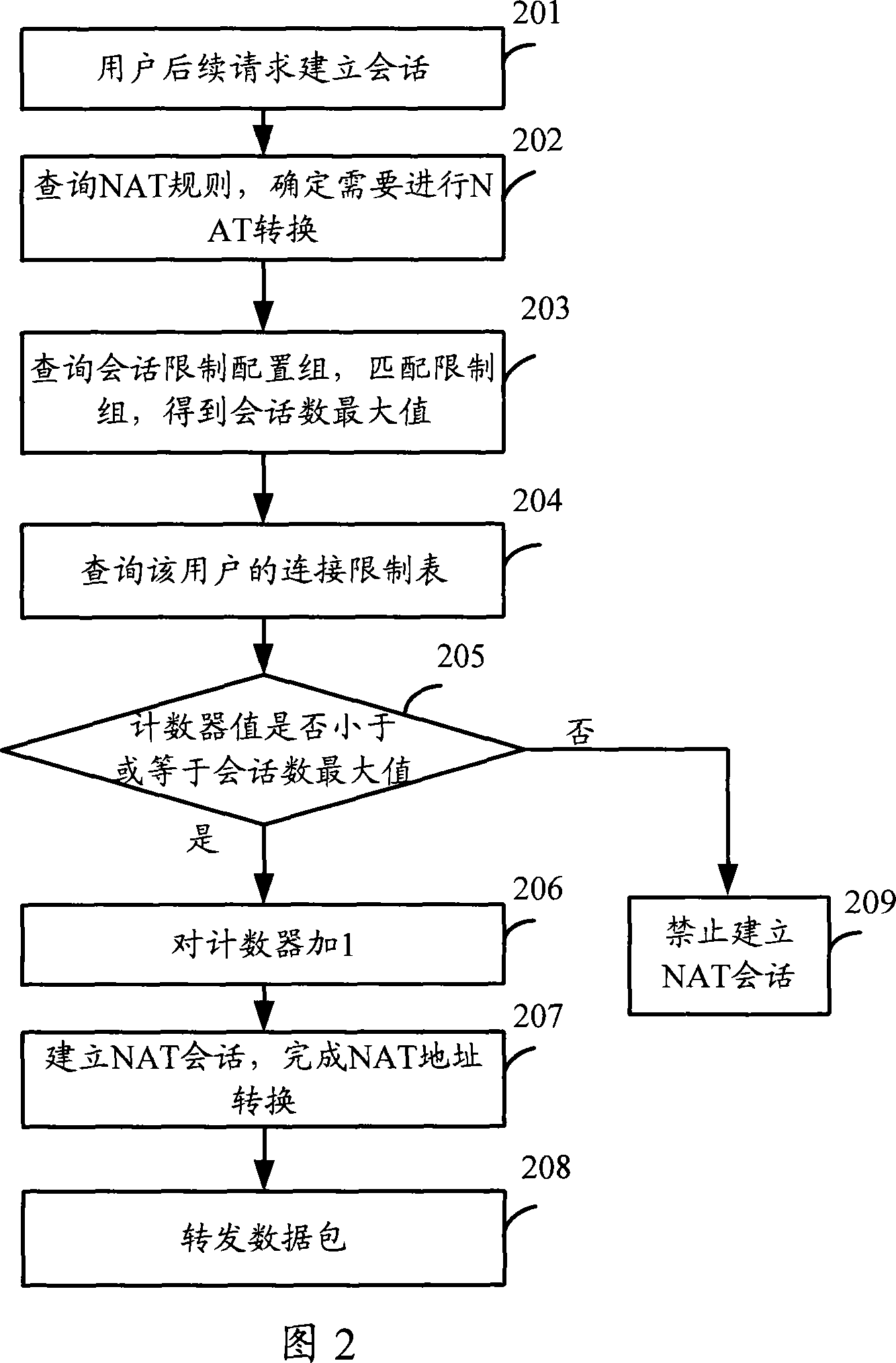
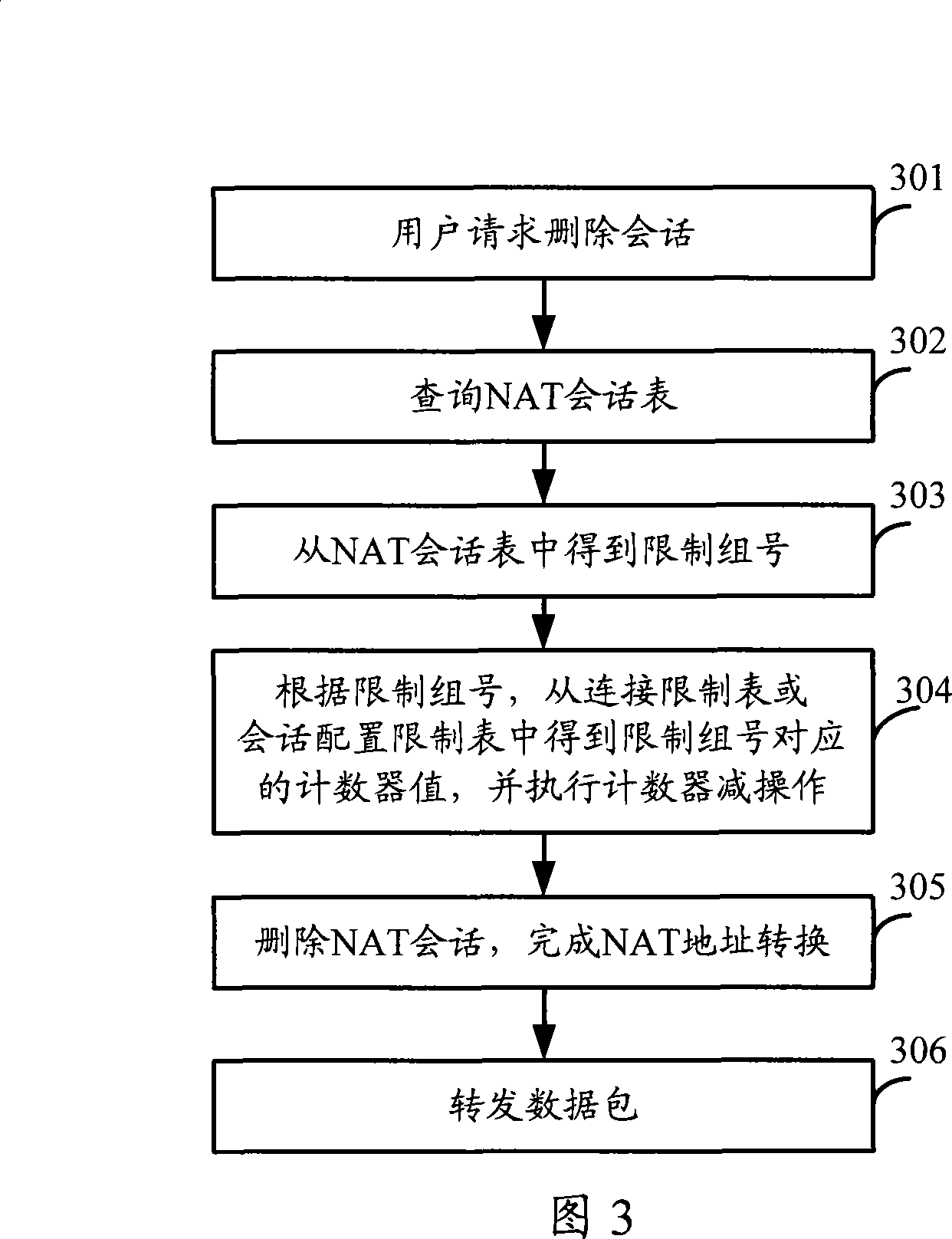
[0081] In this embodiment, on the basis of the first embodiment, the implementation of deleting a session is added.
[0082] There are two situations where a session needs to be deleted. One is that the user actively requests deletion, for example, the session is deleted after receiving a TCP delete control packet; the other is that the NAT session table is aging, and then the session needs to be deleted.
[0083] Wherein, the NAT session table mentioned above is a session table generally referred to in the art, and it is for recording the NAT transformation relationship of a data flow, and establishes a positive and negative session record in both directions, as long as it meets the positive and negative of the session Address translation is performed in a unified manner to the data stream. Usually, the NAT session table uses the IP quintuple before conversion as an index (key), and uses the IP quintuple after conversion as a result.
[0084] On the basis of understanding the N
Embodiment 3
[0118] The first and second embodiments mentioned above limit the number of sessions for a single user, but this embodiment limits the number of sessions for a virtual private network (Virtual Private Network, VPN) that supports multiple instances.
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap