Method for detecting random linear network coding tampering data in spatial information network
A random linear, network coding technology, applied in the field of secure communication, can solve problems such as increasing node computing overhead and reducing network performance, and achieves the effect of reducing the number of tampering detections, shortening the transmission distance, and reducing the search time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] An embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings.
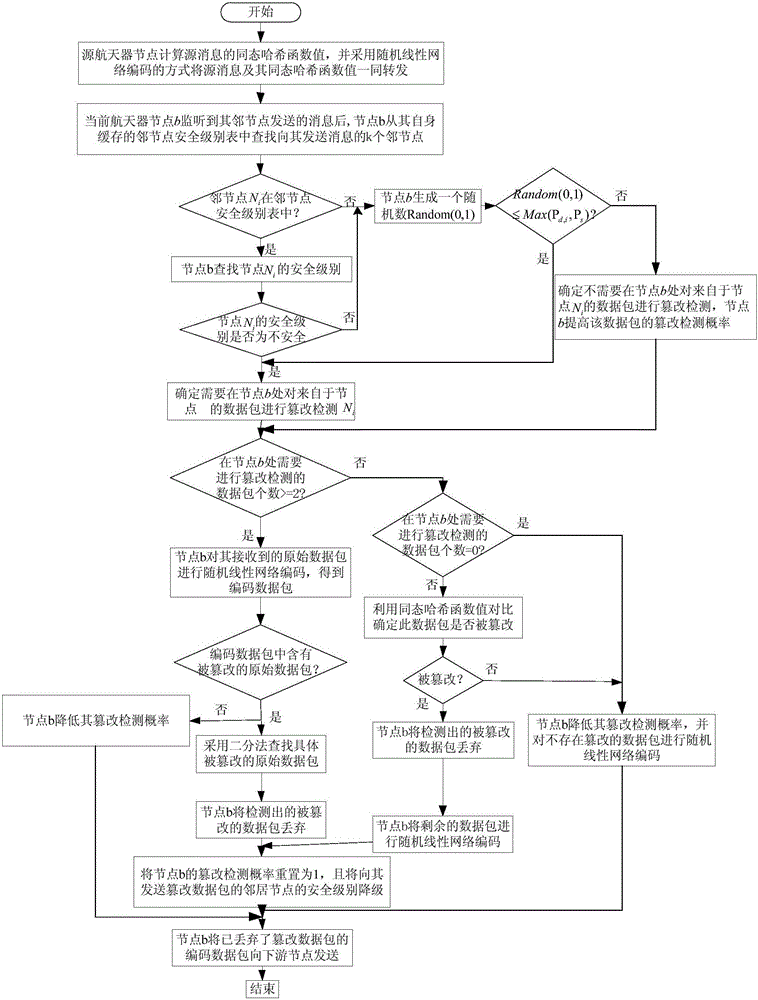
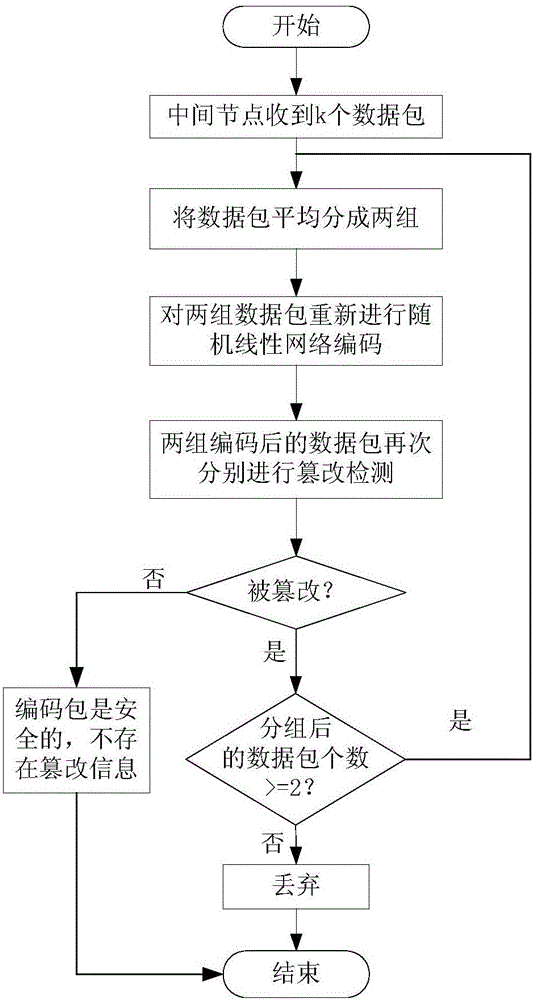
[0040] The method for detecting tampered data with random linear network coding in the spatial information network of this embodiment, such as figure 1 shown, including the following steps:
[0041] Step 1: In the spatial information network, the source node, that is, the source spacecraft node, calculates the homomorphic hash function value of the source message, and forwards the source message and its homomorphic hash function value together by means of random linear network coding;
[0042] In this embodiment, random linear network coding is used to code the data transmitted by the spatial information network, so that the network reaches the maximum transmission flow limit. In this embodiment, a directed graph G=(V, E) is used to represent the space information network, where V is the set of all spacecraft nodes in the space information network, and
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap