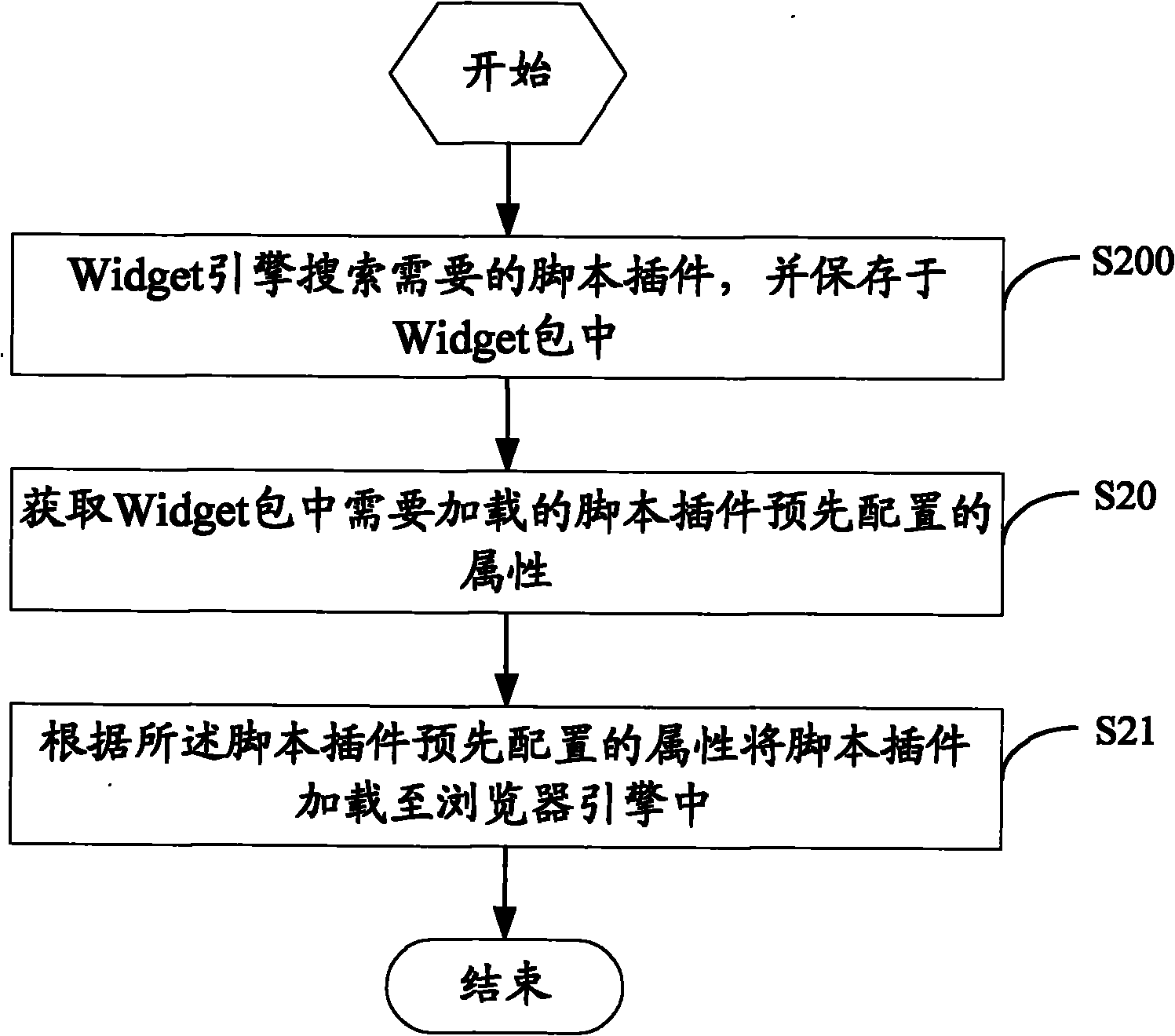
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
95results about "Program loading/initiating" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
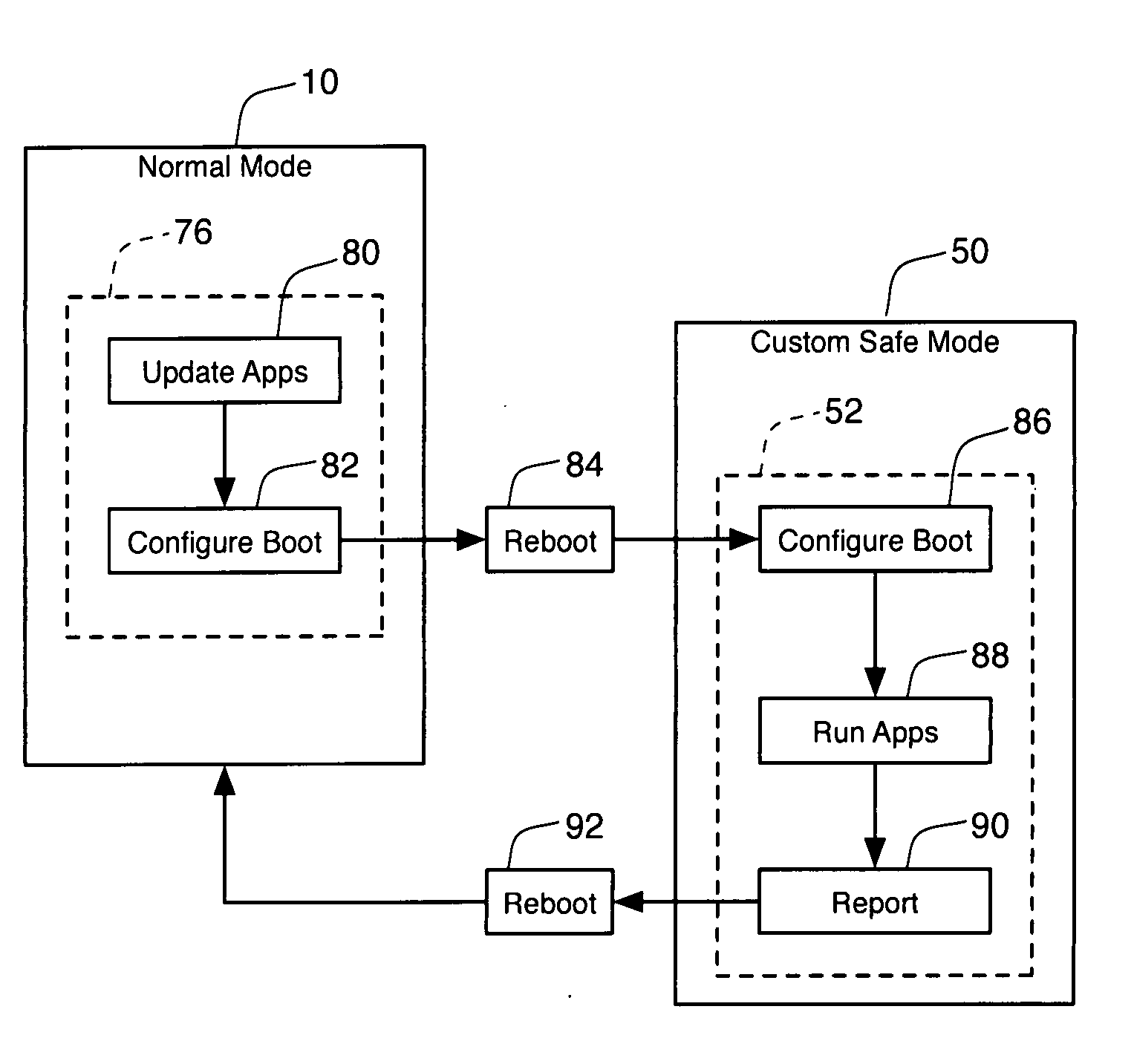
Dynamic identification and administration of networked clients
ActiveUS7568018B1Data resettingMultiple digital computer combinationsSubject matterDistributed computing
The present inventive subject matter relates to networked computing environments and more specifically to dynamic identification and administration of networked clients. Various embodiments of the present inventive subject matter include systems and methods for defining, on a server, a configuration of interest comprising one or more potential properties of a client, communicating the configurations of interest over a network to one or more clients, dynamically evaluating a client state relative to the configurations of interest, and communicating a representation of the client state in relation to the configuration of interest to the server. Further embodiments include automatically creating and displaying associations of clients based on configurations of interest. Yet further embodiments include clients requesting and receiving updates to the configurations of interest. Still further embodiments include actions associated with configurations of interest. Such actions, in various embodiments, include performing administrative actions on various networked clients.
Owner:NEW BOUNDARY TECH
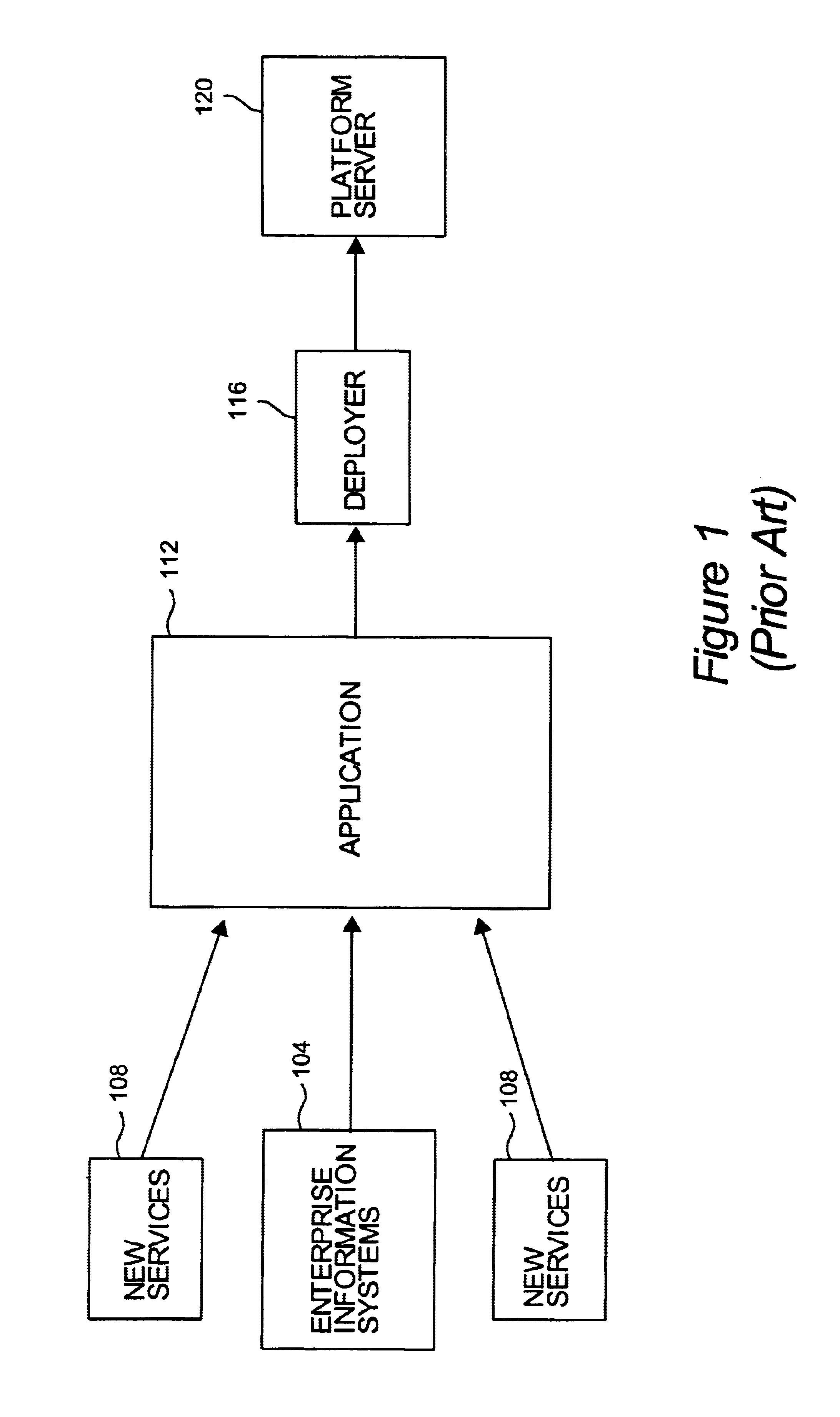
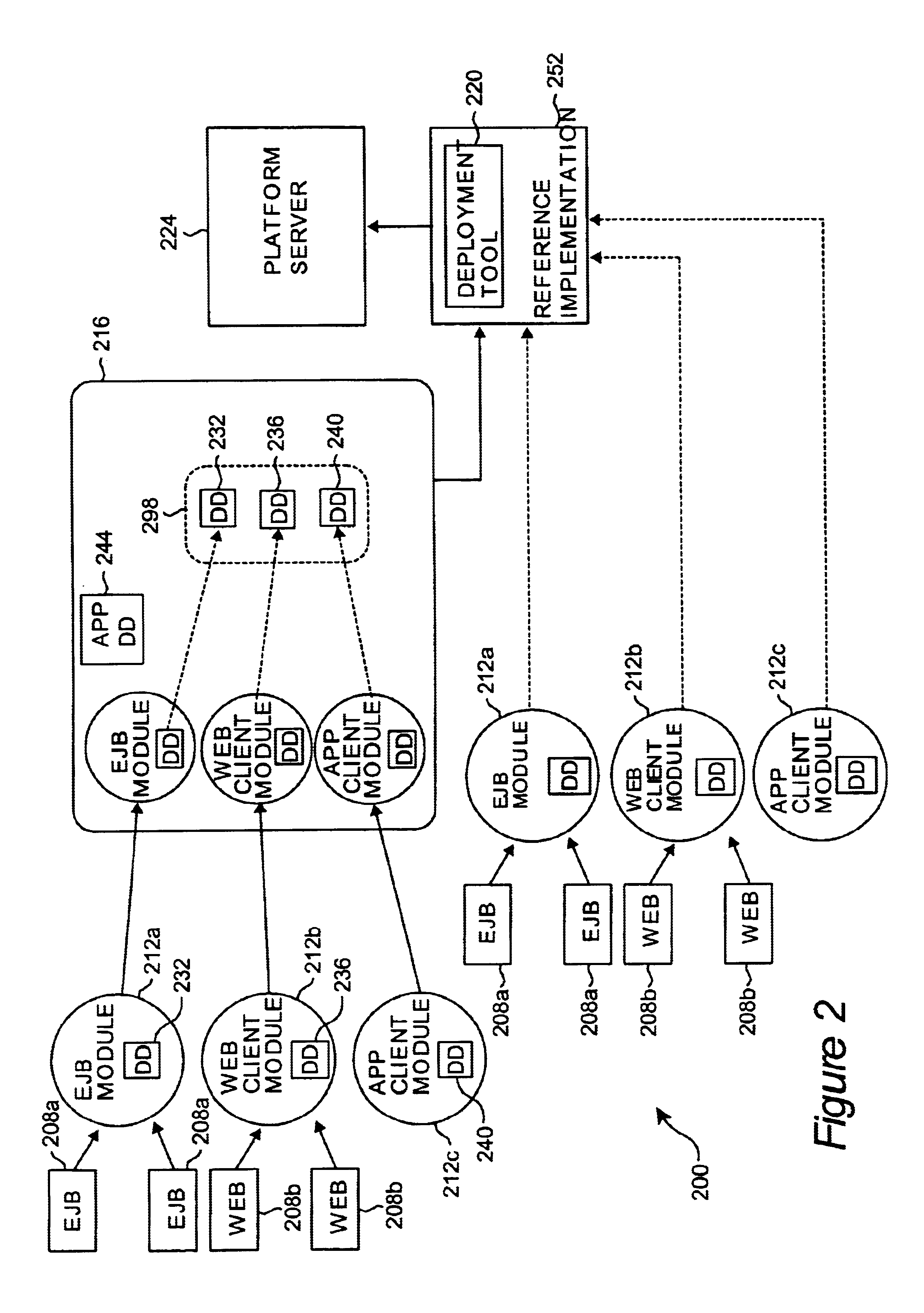
Method and apparatus for implementing deployment descriptors in an enterprise environment
Methods and apparatus for implementing deployment descriptors which are used to deploy modules in an enterprise environment are disclosed. According to one aspect of the present invention, a method for deploying an application using a deployment tool for use on a platform server includes creating the application, creating an application deployment descriptor for the application, packaging the application in an archive, and deploying the application packaged in the archive. Creating the application includes obtaining an application component which has an associated application component deployment descriptor that has information relating to the deployment of the application component. The application deployment descriptor for the application includes information arranged to identify the application component, and packaging the application in an archive includes packaging the application component, the application component deployment descriptor, and the application deployment descriptor. The application packaged in the archive is deployed using the application component deployment descriptor.
Owner:ORACLE INT CORP
Automated entitlement verification for delivery of licensed software
ActiveUS20030005427A1Computer security arrangementsProgram loading/initiatingClient-sideCentralized management
Owner:ACTIVISION PUBLISHING
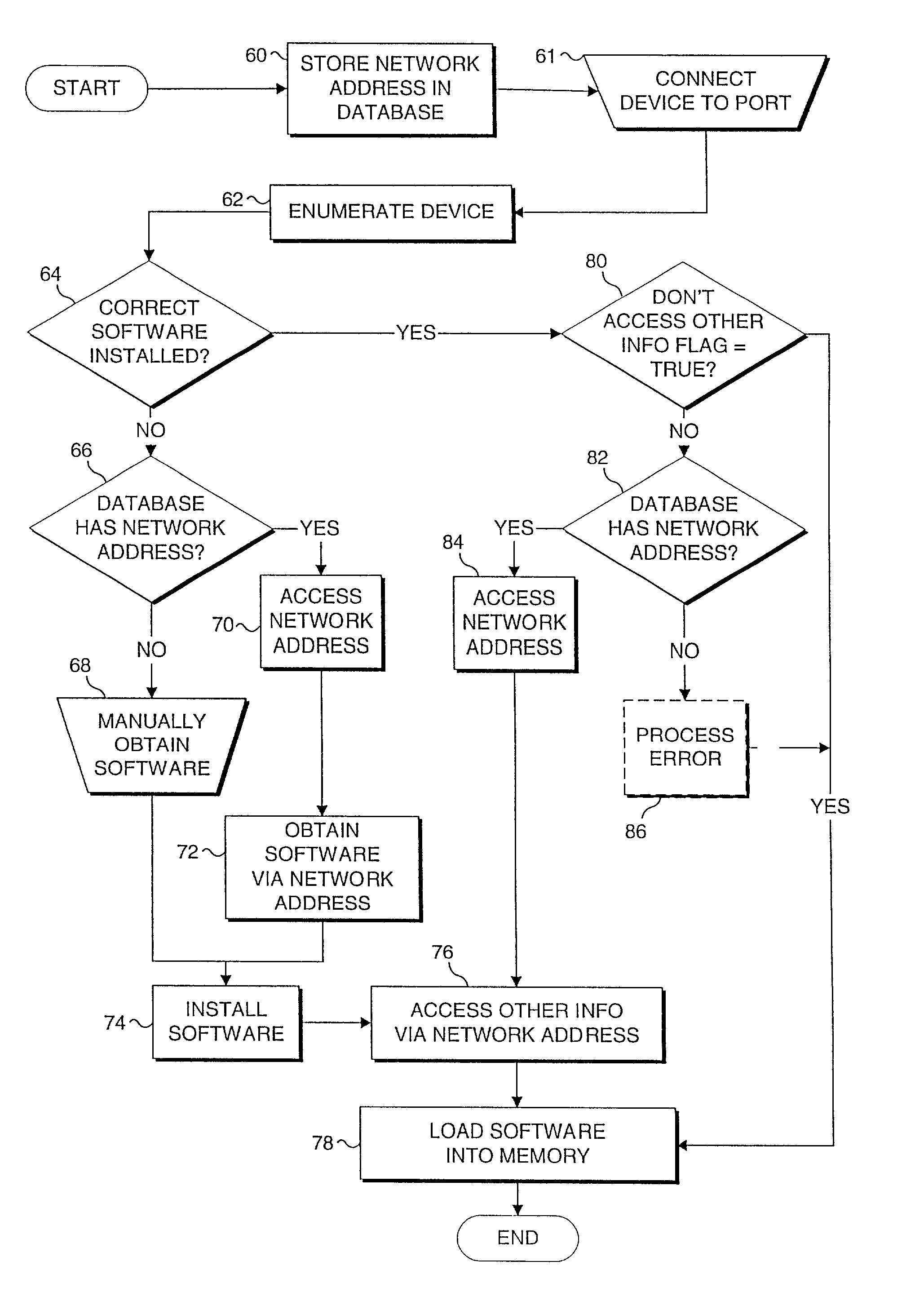
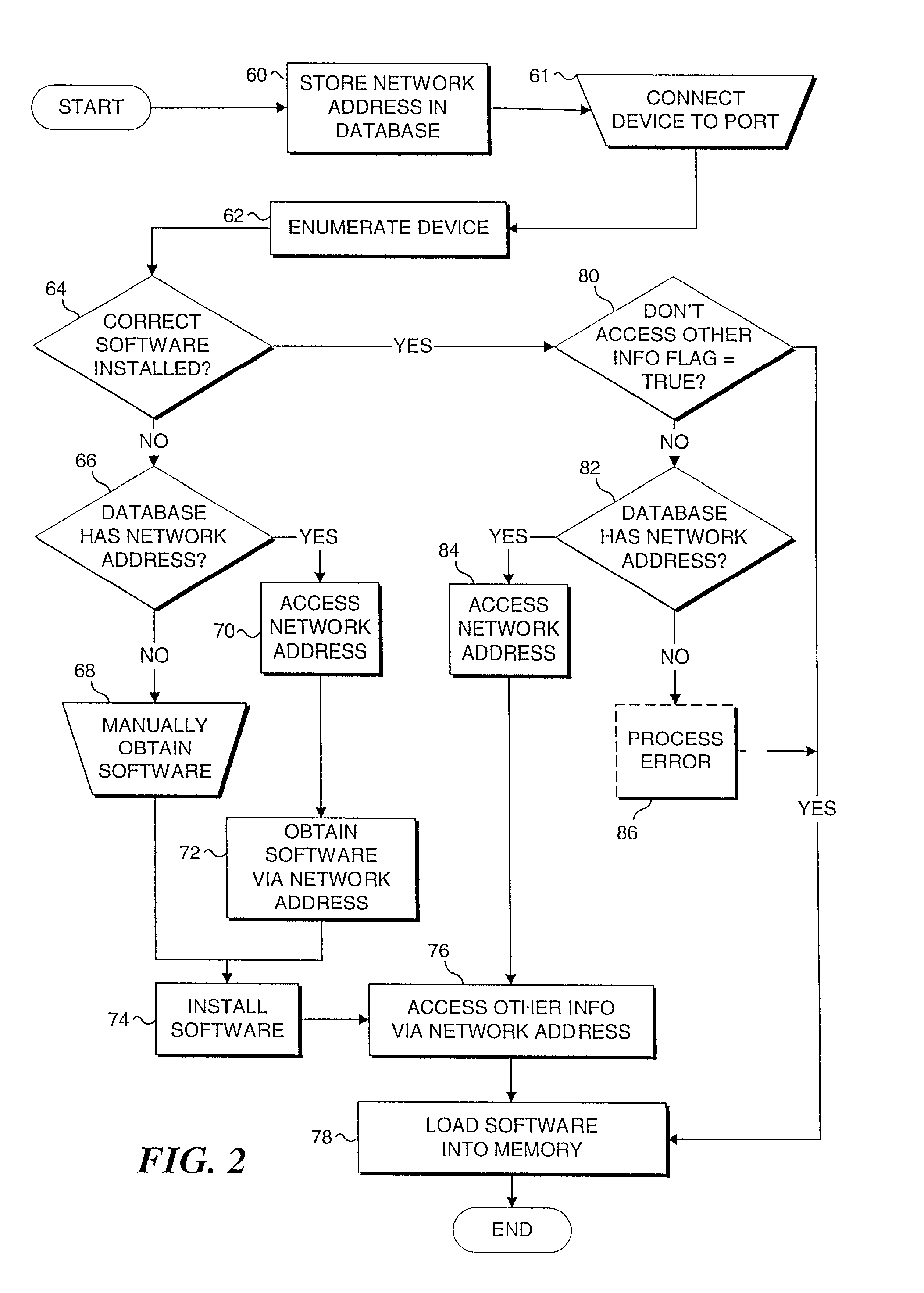
Method and system to access software pertinent to an electronic peripheral device at an address based on a peripheral device identifier
InactiveUS7076536B2Digital computer detailsProgram loading/initiatingNetwork addressingNetwork address
Owner:MICROSOFT TECH LICENSING LLC
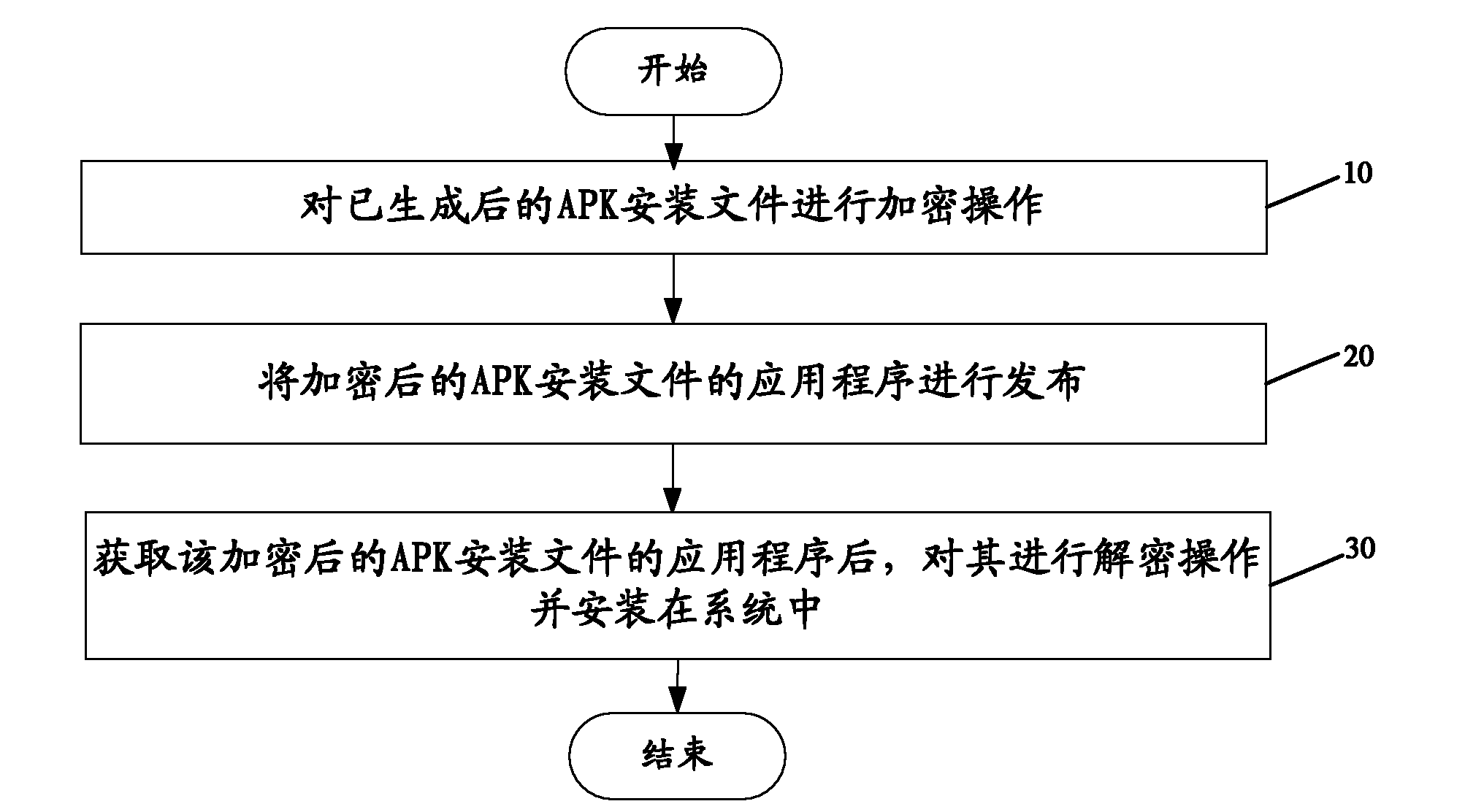
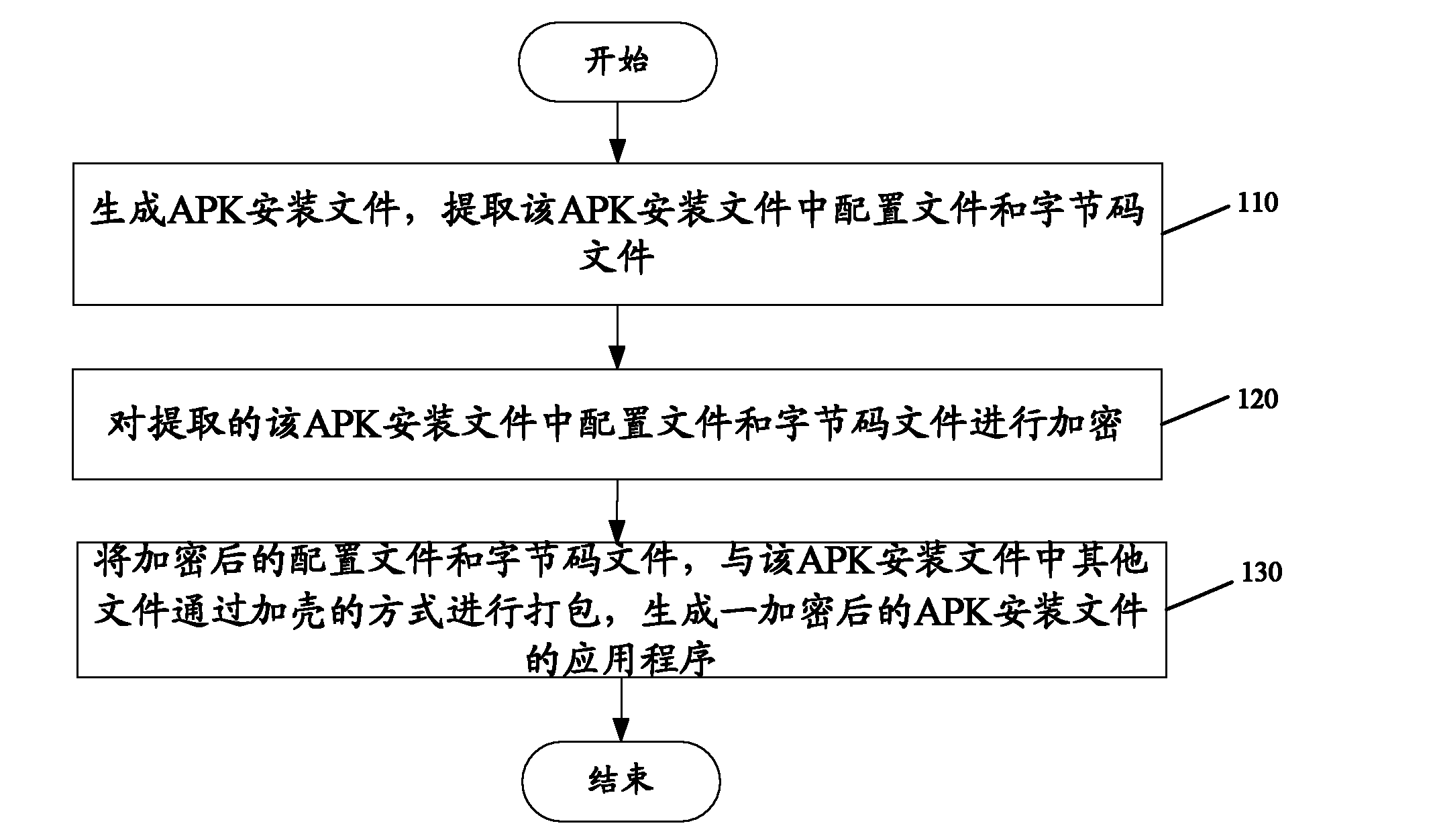
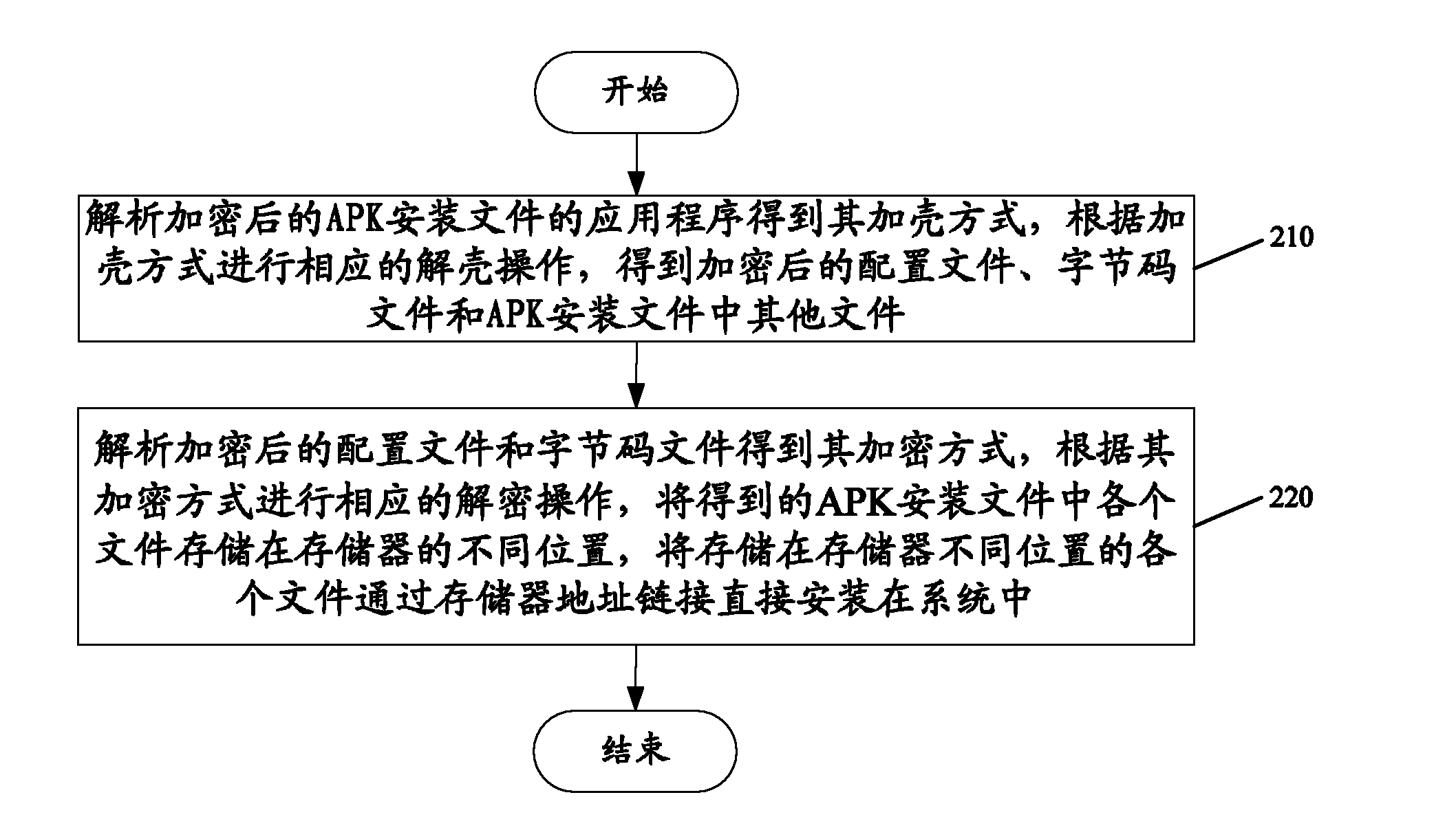
Android-based platform application installation control method and system
InactiveCN102087605AComputer security arrangementsProgram loading/initiatingApplication softwareEncryption
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Application program control method based on two-time signature verification technology
ActiveCN103886260AEnsure safetyProgram loading/initiatingPlatform integrity maintainanceThird partyApplication software
An application program control method based on a two-time signature verification technology is achieved by performing two times of signing and two times of signature verification on application programs on an android terminal. Security detection is performed on the application programs through a reliable third-party security detection mechanism, the application programs passing the detection will be signed by the third-party security detection mechanism, and then the signed applications are returned to developers. When the application programs are installed on the intelligent android terminal, security detection is performed on the application programs first to see whether the application programs are signed by the third-party security detection mechanism or not, and signatures are verified; if signatures of the third-party detection mechanism do not exist or the signatures cannot pass verification, installation of the application programs is refused. Through the technical scheme, the application program control method based on the two-time signature verification technology has the advantages that signature information is fixed through introduction of the third-party detection signatures and a security control module of the android terminal so that secure application programs can be downloaded and installed in an android system through multiple channels, and while security of the android terminal is guaranteed, a flexible and efficient application program verification scheme is provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
Deployment method of utility software and the system thereof
InactiveCN101788917AImplement automatic installationImprove reliabilityProgram loading/initiatingTransmissionOperational systemSoftware deployment
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Malware automated removal system and method
ActiveUS20090013409A1Automate operationImprove software performanceMemory loss protectionError detection/correctionComputerized systemMalware
Owner:BBY SOLUTIONS
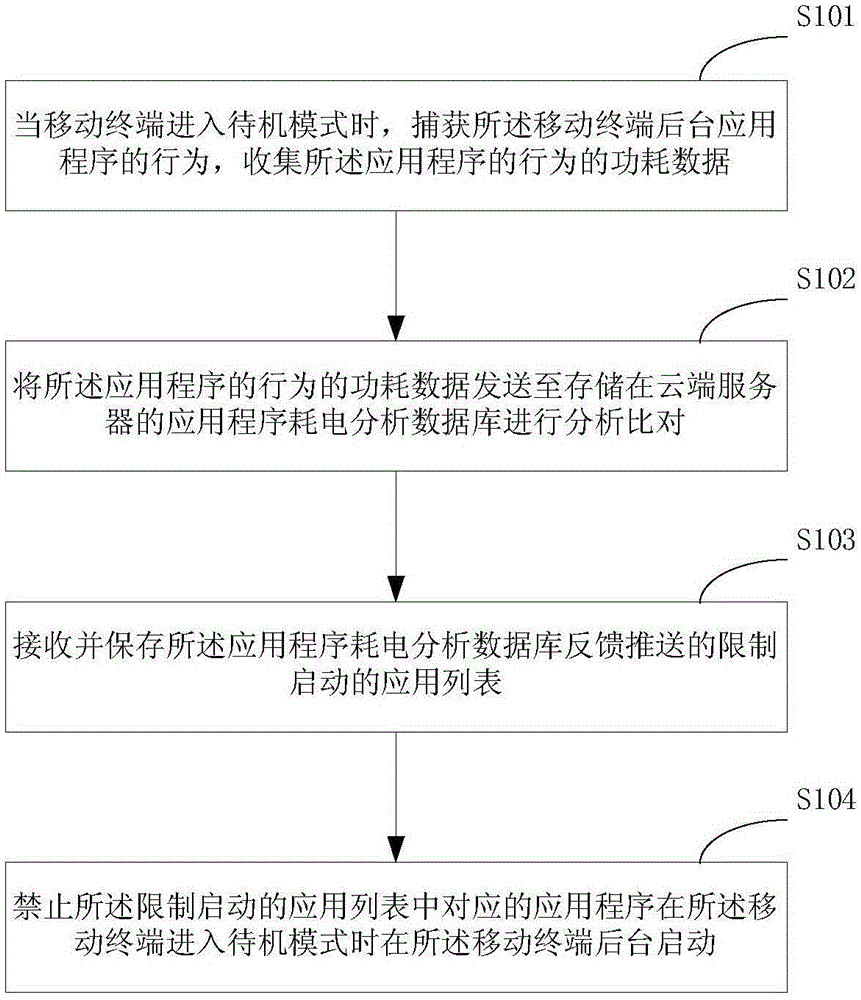
Method for reducing power consumption of device, mobile terminal and system
ActiveCN105159816AReduce power consumptionImprove battery lifeHardware monitoringCurrent supply arrangementsTerminal equipmentComputer terminal
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method for realizing rapid Web Service publishment in service oriented architecture application systems
ActiveCN101957758AProgram loading/initiatingTransmissionWeb Services Description LanguageBusiness function
Owner:PRIMETON INFORMATION TECH
Delivery parameter burning method, equipment to be burnt, burning tool equipment
Owner:SHENZHEN SKYWORTH SOFTWARE +1
Automated provisioning of computing networks using a network database data model
ActiveUS8019835B2Minimize security riskMultiple digital computer combinationsProgram loading/initiatingFile systemCentral database
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Identifying The Origin Of Application Resources
A tool is provided for translation verification testing of various forms of translatable objects in an installed application. The tool attaches tags to a select set of translatable objects. In general, the tags attached to the translatable objects identify the source of the tag. This enables the component of the tag to be verified in a non-complex manner. In one embodiment, a set of rules are selected and followed to predetermine attaching of tags to translatable objects in the application.
Owner:INT BUSINESS MASCH CORP
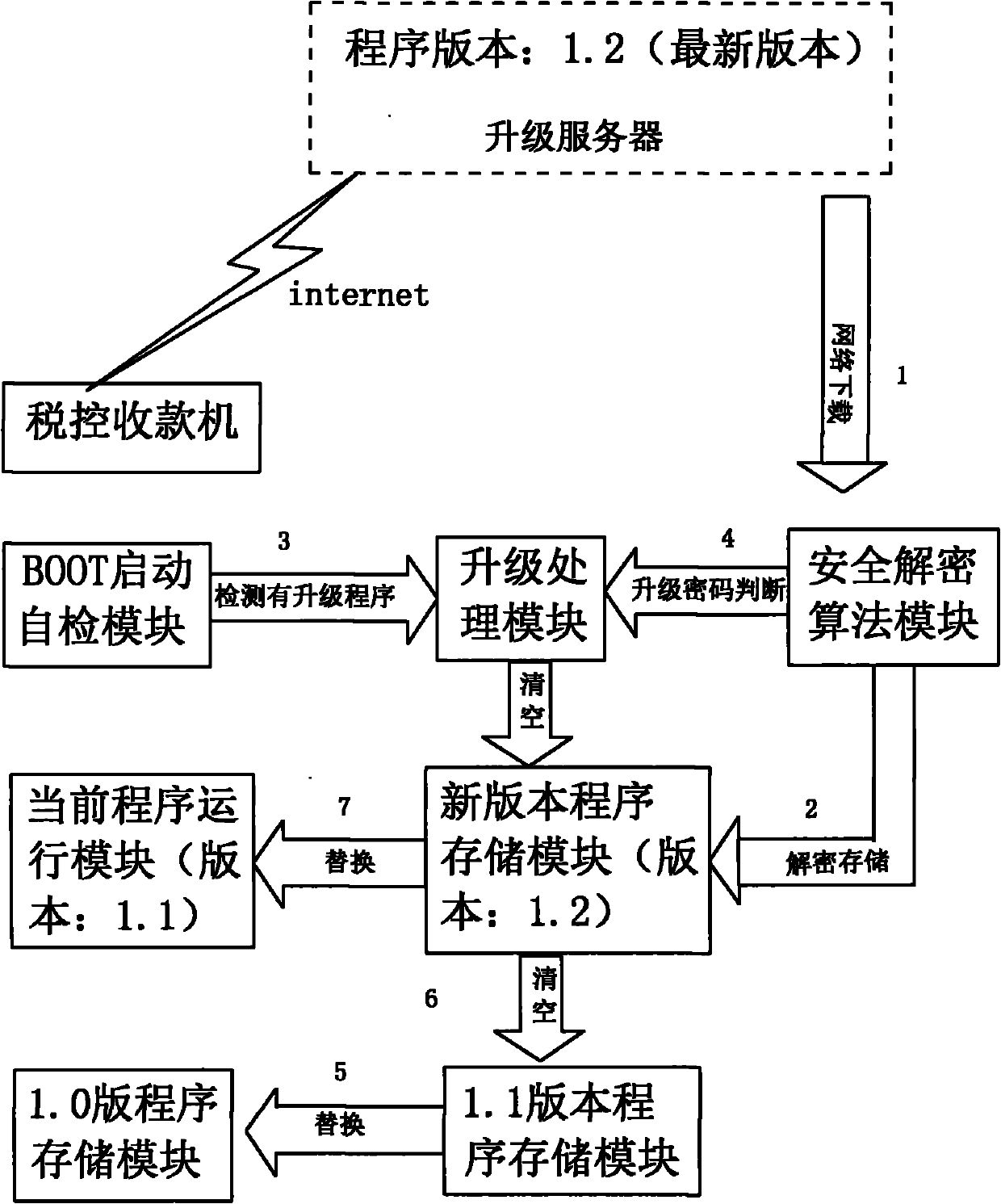
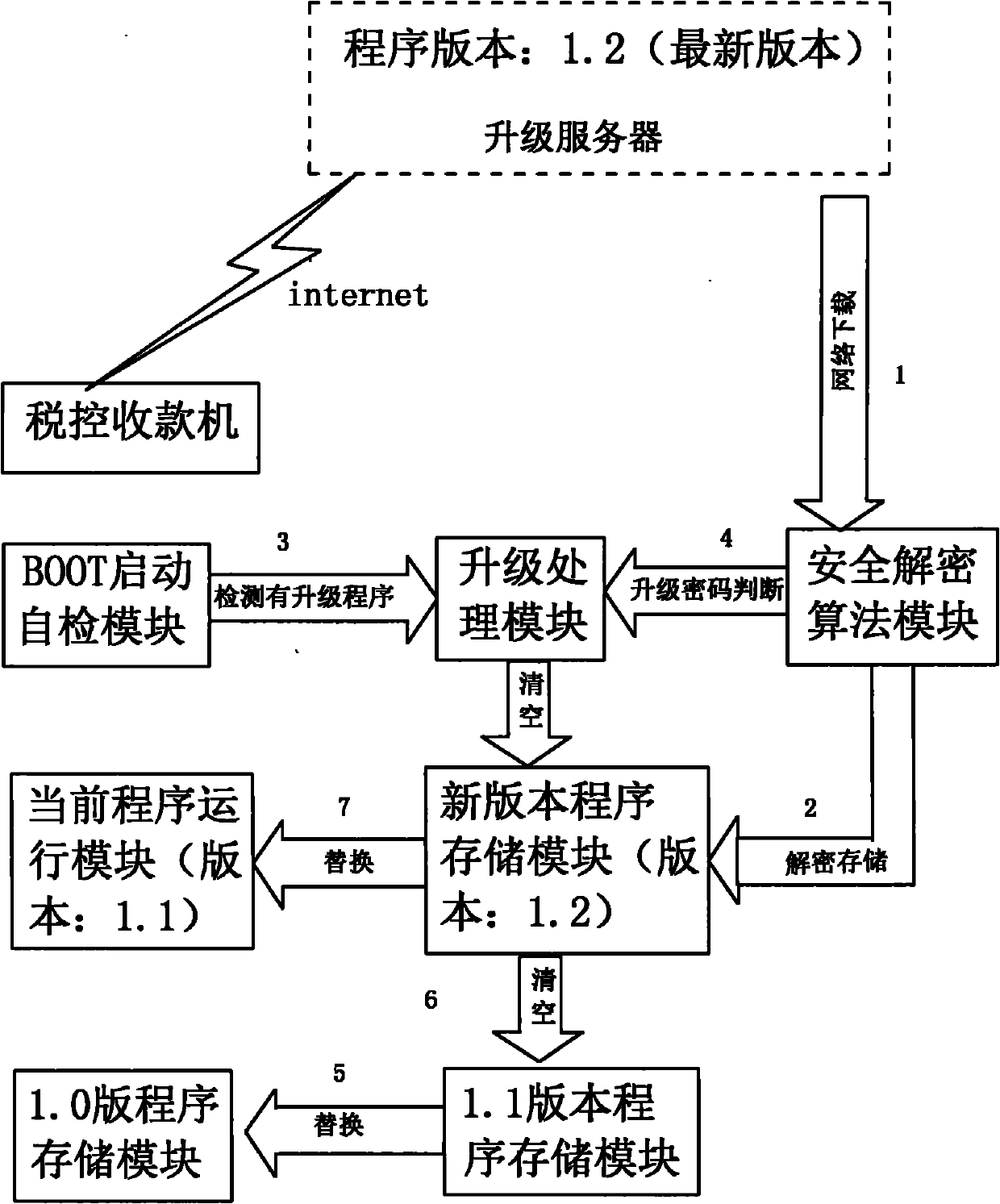
Remote update method of fiscal cash register
InactiveCN101907996AImprove data consistencyProgram loading/initiatingTransmissionLower gradeTerminal equipment
Owner:INSPUR QILU SOFTWARE IND
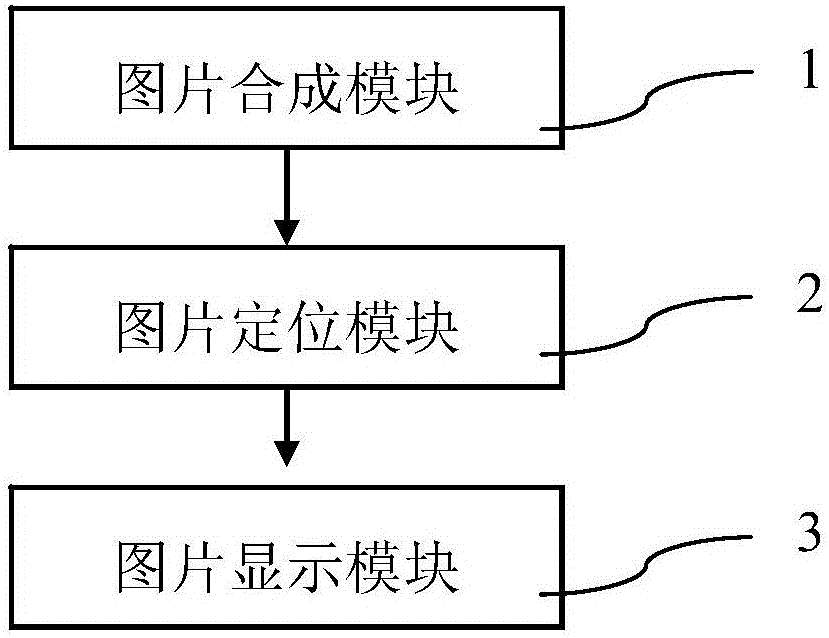
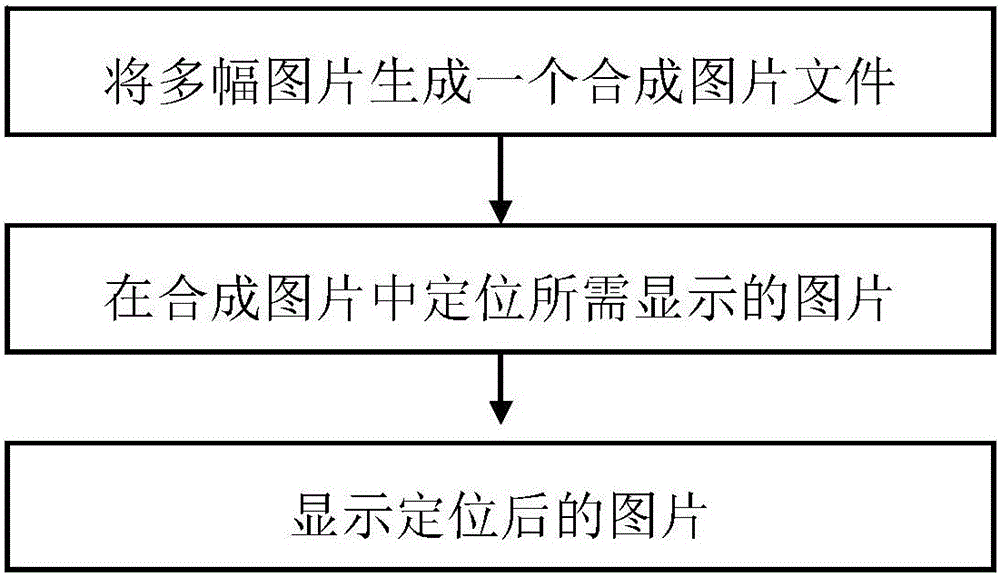
Image positioning system and method
InactiveCN105094930AReduce under-displayProgram loading/initiatingSpecial data processing applicationsComputer graphics (images)Background image
Owner:PHICOMM (SHANGHAI) CO LTD
Embedded remote universal upgrading system based on general packet radio service (GPRS) and upgrading method based on embedded remote universal upgrading system
InactiveCN103078917AMeet the needs of upgradingRealize remote upgradeProgram loading/initiatingTransmissionGeneral Packet Radio ServiceIp address
The invention relates to an embedded remote universal upgrading system based on general packet radio service (GPRS) and a upgrading method based on the embedded remote universal upgrading system, which aims at solving the problems of the existing manual upgrading way that the labor and the material resource are greatly wasted and the universality of the upgrading system is poor. When a remote device needs to be upgraded, relevant upgrading configuration of the remote device is conducted by the remote working personnel through a liquid crystal screen of a remote upgrading controller, then an upgrading request and own internet protocol (IP) address are transmitted to a server, the server transmits a corresponding upgrading program file through a special upgrading software on the server to begin the upgrading. After the upgrading is completed, the remote device returns and transmits an upgrading completion log to through the remote upgrading controller so as to notify the server that the remote upgrading is completed. The embedded remote universal upgrading system and the upgrading method are suitable for upgrading the remote device to be upgraded.
Owner:HARBIN INST OF TECH
Method and system for dynamically loading data structures into memory with global constant pool
A method of operating a computer involving data structures in a set of data structures. As unloaded data structures are needed during runtime, a data structure is received from a first memory. The data structure includes one or more sets of instructions and one or more constants. Instructions from the data structure are stored in a first portion of a second memory, which comprises RAM. Constants from the data structure are stored in a second portion of the second memory if only if the respective constant has not been stored in the second portion of the second memory. Indexes in instructions that reference the constants are modified to correspond to the respective locations of the constants in the second portion of the second memory, and at least some instructions from the data structure are read and executed from the RAM. Also described is a computer system including a memory and logic that, for classes in a set of classes, receives a class from a class file and stores constants from the class in a second portion of the memory if only if the respective constant has not been stored in the second portion of the memory.
Owner:ALTO DYNAMICS LLC +1
Starting method of satellite borne software
InactiveCN106648809AImprove securitySave space costProgram loading/initiatingStatic random-access memoryProgrammable read-only memory
The invention relates to a starting method of satellite borne software. The method comprises the following steps: ground compression software stores an object code of the satellite borne software in a programmable read only memory (PROM) after multiple lossless compression; and after a satellite computer is electrified or reset, a starting program decompresses and reduces compression data of the satellite borne software stored in the PROM to a static random access memory (SRAM) and operates. The memory efficiency of the PROm is effectively improved, the flight program and the starting program which are normally cured in the PROM are realized, so that the space cost and the maintenance cost brought by redundant backup are lowered, the safety of the satellite is extremely improved, the PROM is not overturned by single particles, EEPROM is not dependent, on-orbit maintenance times in the later stage can be greatly reduced, and the fault-tolerant ability of operation of the satellite borne computer is enhanced.
Owner:SHANGHAI AEROSPACE CONTROL TECH INST
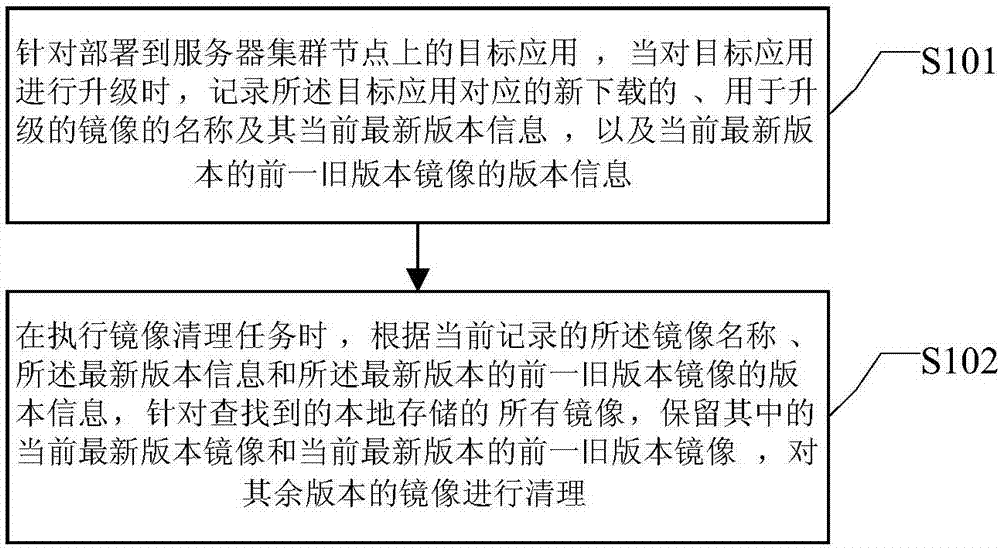
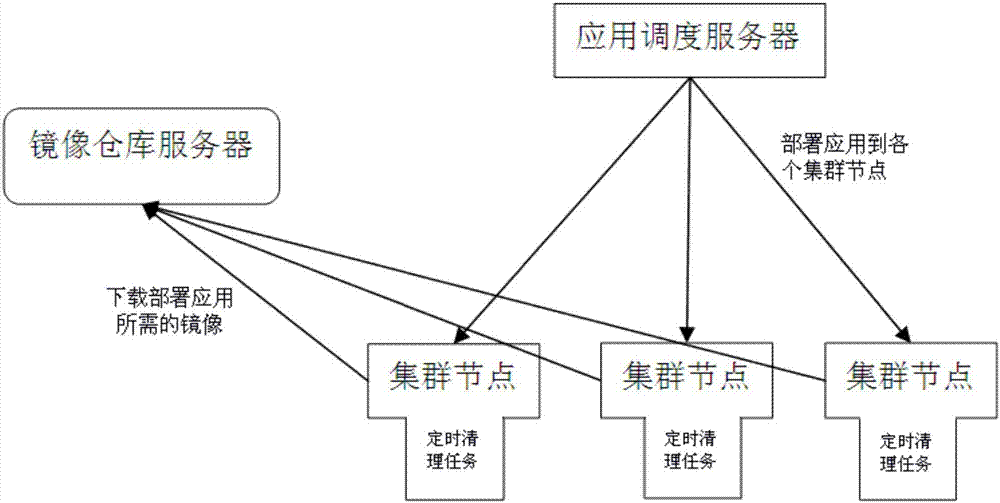
Method and device for clearing mirror image in cluster node
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
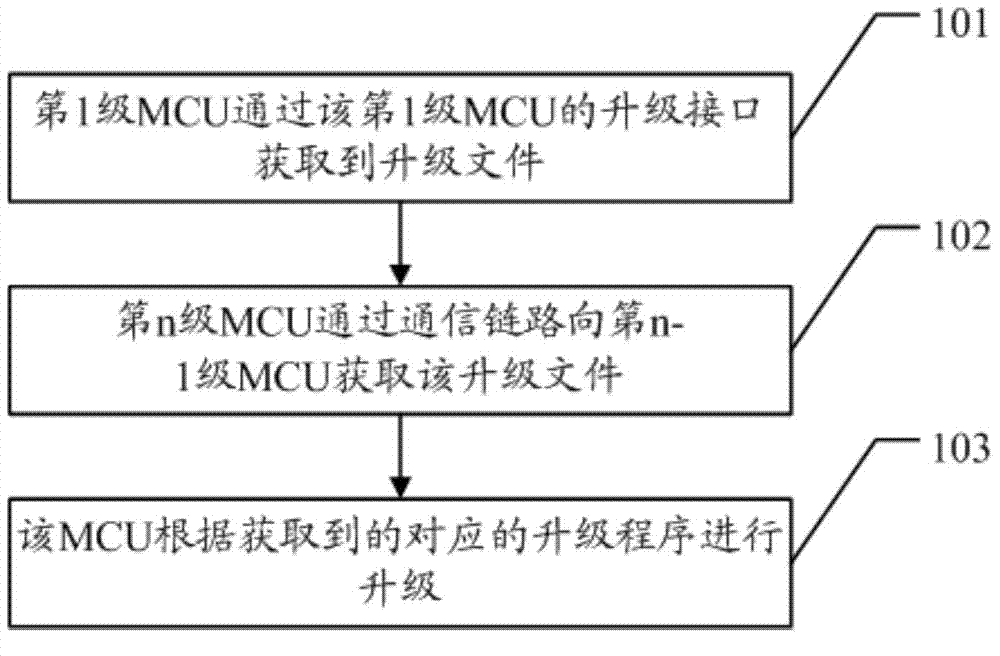
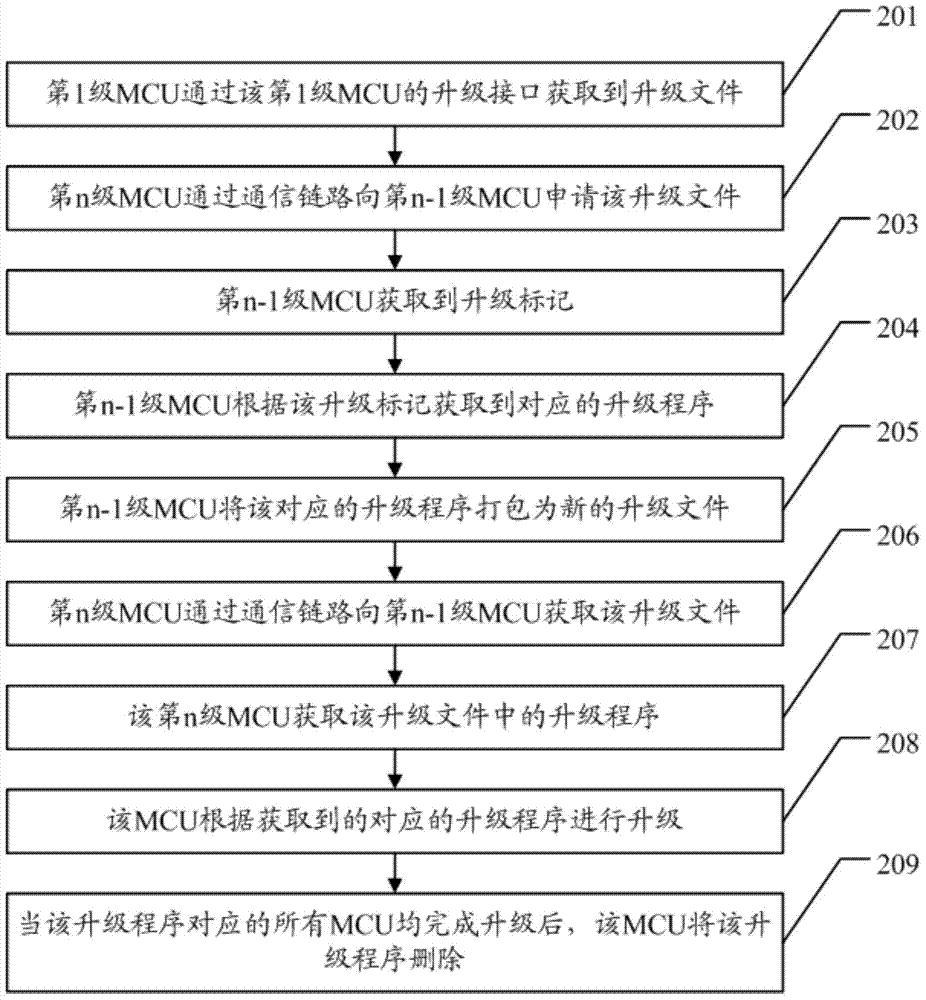
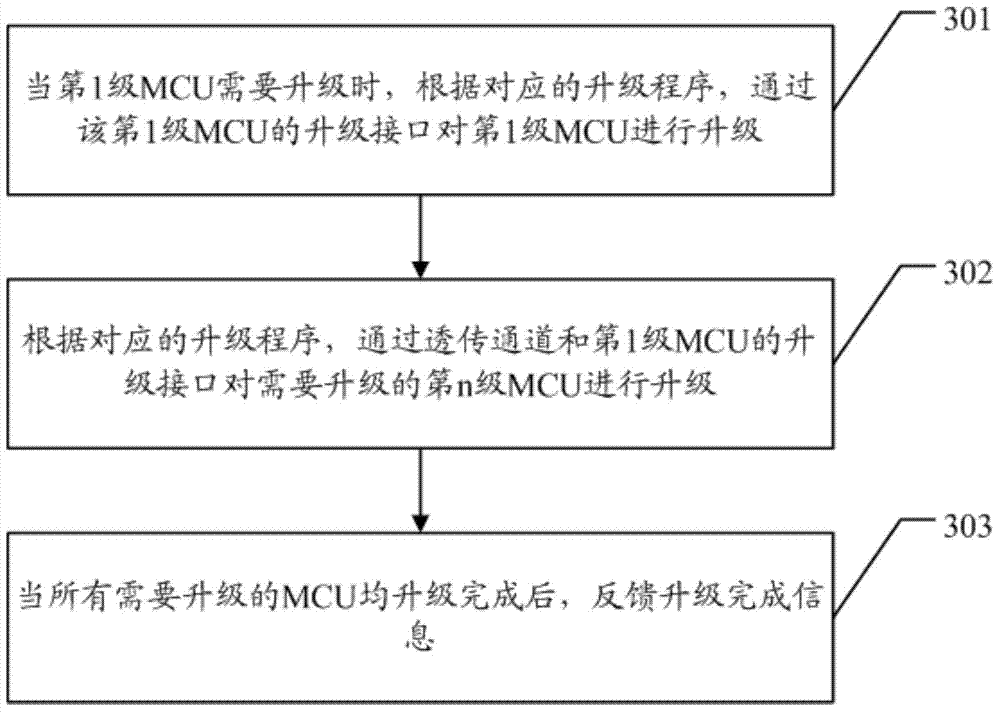
Method for upgrading master and slave MCUs (micro control units)
Owner:GUANGZHOU HUAXIN ELECTRONICS TECH
Android application host process awakening method, storage medium, equipment and system
Owner:WUHAN DOUYU NETWORK TECH CO LTD
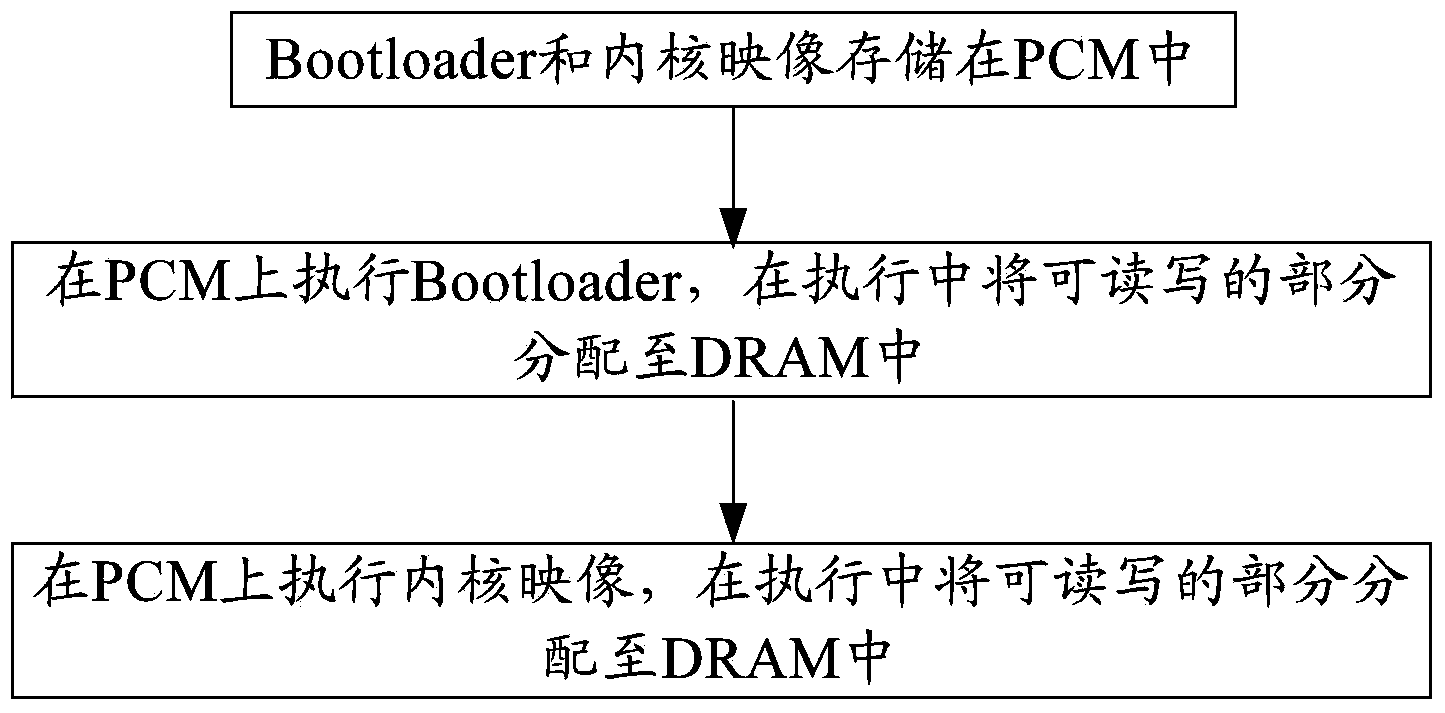
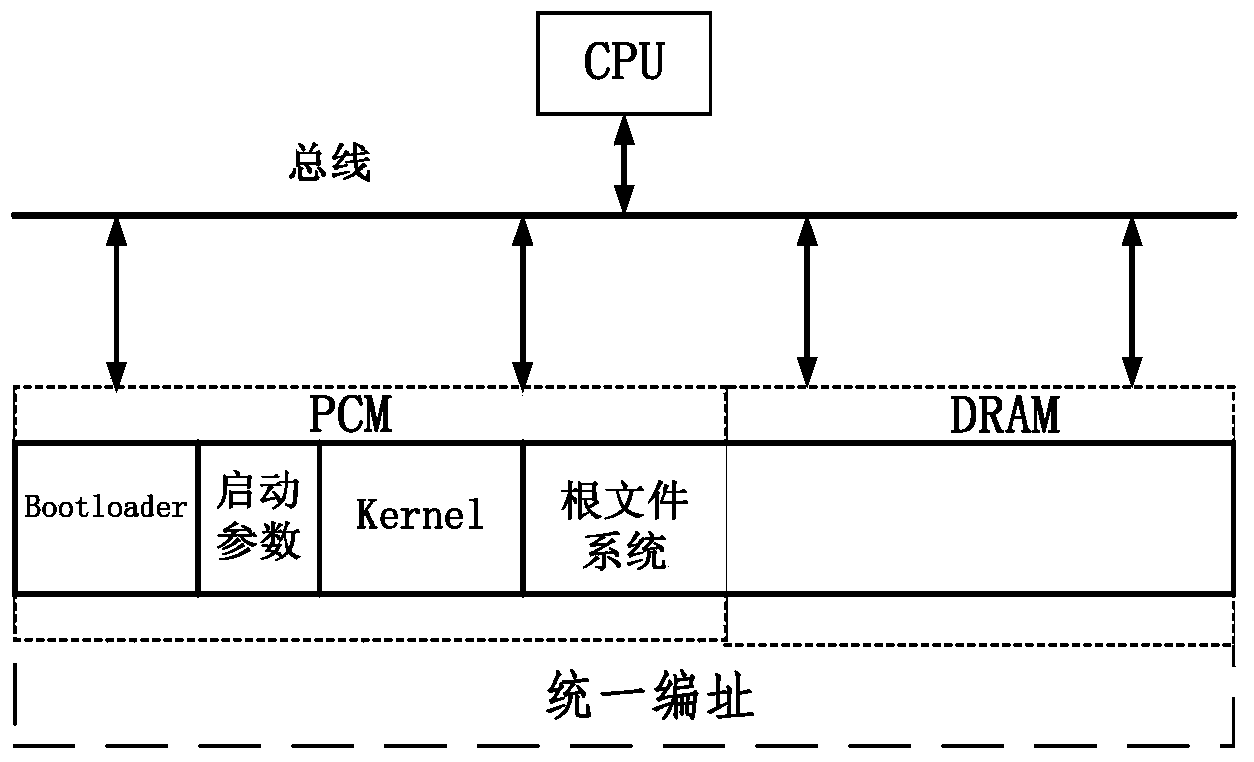
System startup method based on PCM (Phase Change Random Access Memory)
ActiveCN103955389AShorten the timeImprove system efficiencyProgram loading/initiatingData segmentRandom access memory
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
Mesh communications network having mesh ports
A method for communicating over a mesh network established between a plurality of devices is disclosed. Each device has a wireless radio and the method involves launching a mesh service on each device, the mesh service being operable to cause a processor circuit of the device to provide functionality for controlling the wireless radio for communication between devices over the mesh network. Each device has at least one application running on the device, the at least one application being associated with a mesh port, the mesh port being used to designate data transmissions as being associated with instances of a specific application running on at least some of the devices in the plurality of devices, the at least one application and the mesh service on each device being in data communication. The method also involves, in response to a specific application running on a device requesting the mesh service to provide access to the mesh network for communication via a specific mesh port, causing the mesh service to determine whether the specific application is authorized for communications on the specific mesh port, and if the specific application is authorized, processing requests from the application to communicate on the specific mesh port over the mesh network and forwarding data transmissions associated with the specific mesh port to the specific application, and if the specific application is not authorized, declining requests from the application to communicate on the specific mesh port over the mesh network and preventing access by the specific application to data transmissions associated with the specific mesh port.
Owner:LEFT OF THE DOT MEDIA
System and method for executing hybridized code on a dynamically configurable hardware environment
InactiveUS7032103B2Software engineeringGeneral purpose stored program computerMultiple contextTheoretical computer science
A system and method for executing previously created run time executables in a configurable processing element array is disclosed. In one embodiment, this system and method begins by identifying at least one subset of program code. The method may then generate at least one set of configuration memory contexts that replaces each of the at least one subsets of program code, the at least one set of configuration memory contexts emulating the at least one subset of program code. The method may then manipulate the at least one set of multiple context processing elements using the at least one set of configuration memory contexts. The method may then execute the plurality of threads of program code using the at least one set of multiple context processing elements.
Owner:QUALCOMM INC
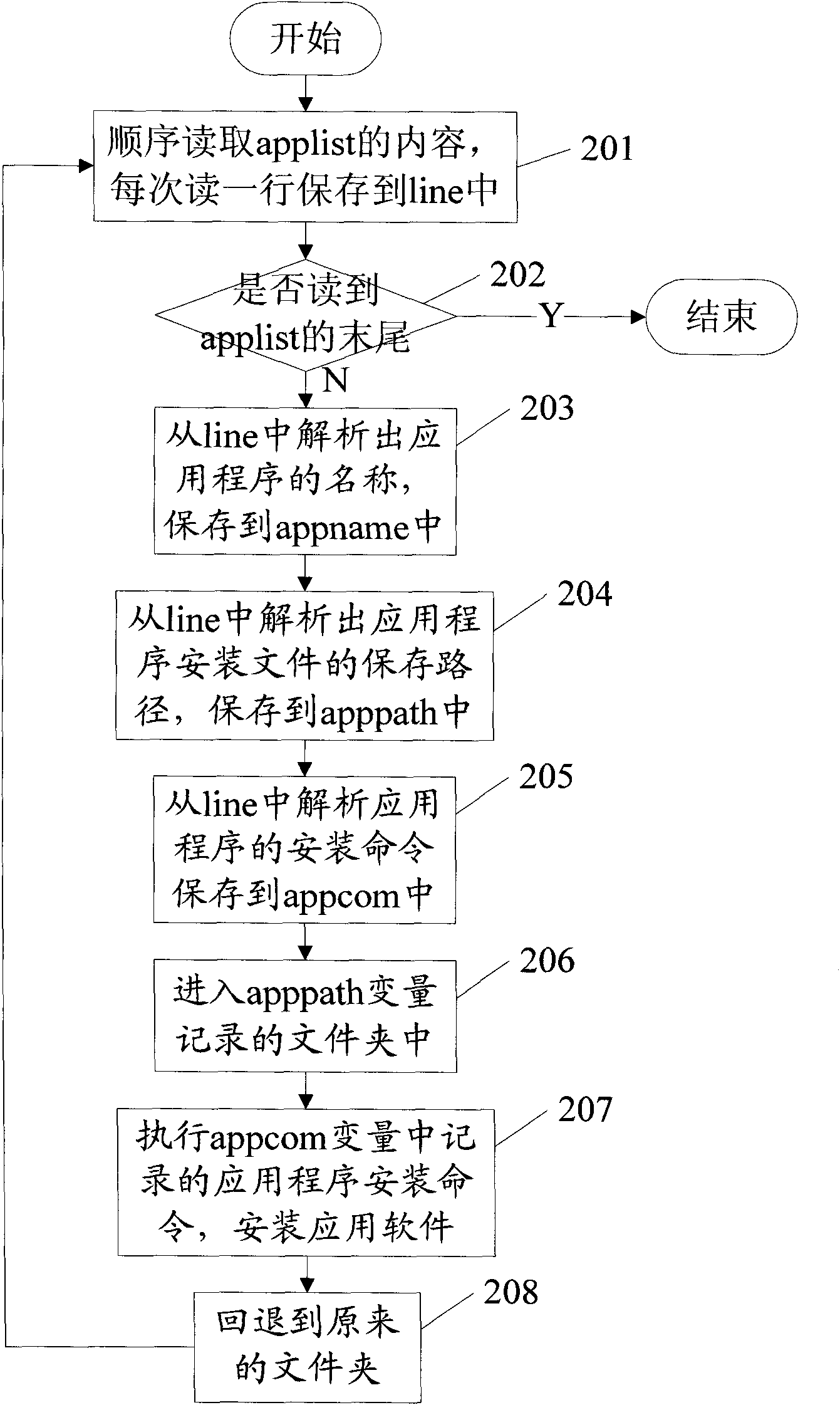
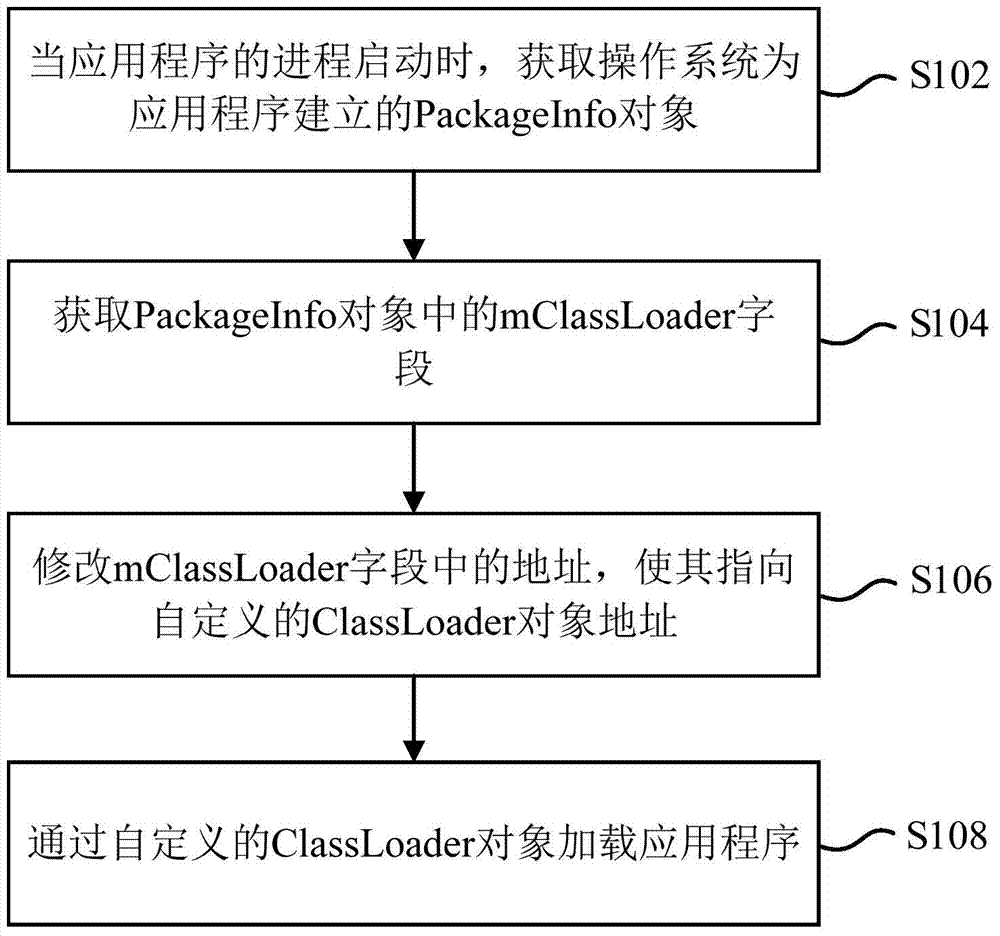
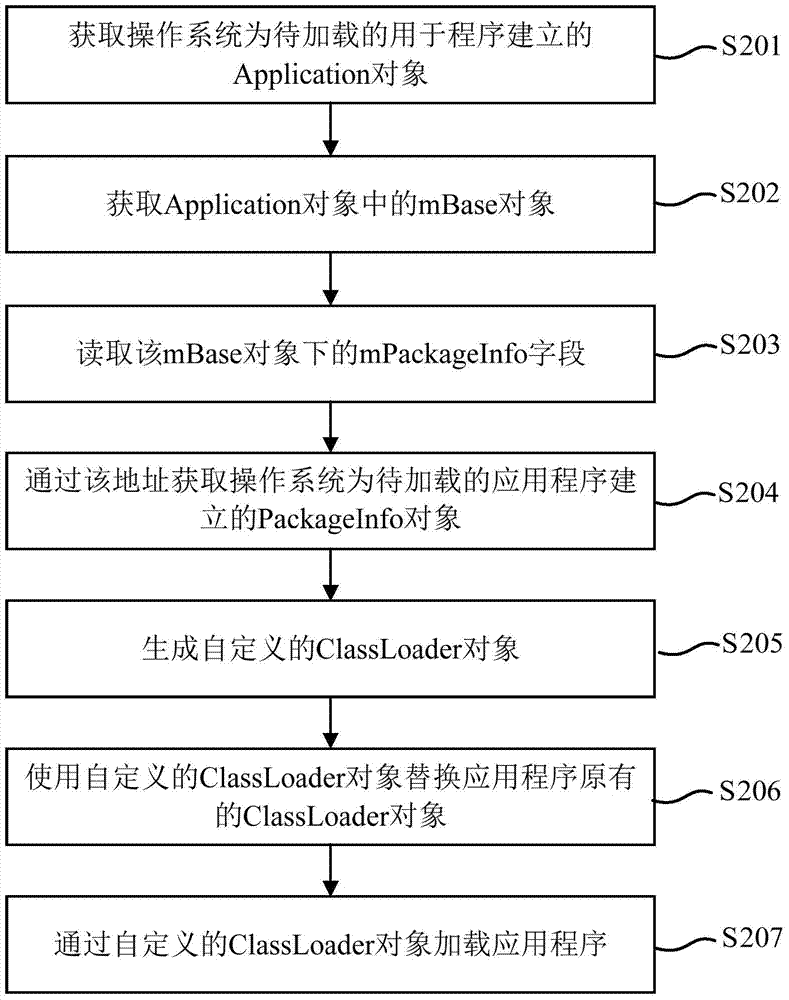
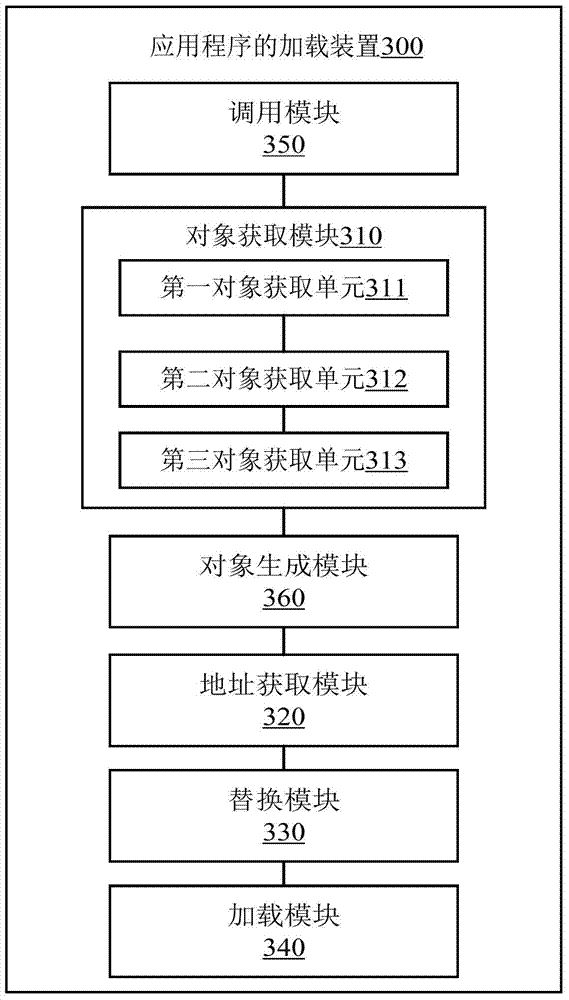
Application program loading method and device and mobile terminal
ActiveCN104731622AFlexible loadingNatural way of callingProgram loading/initiatingComputer terminalApplication software
Owner:BEIJING QIHOO TECH CO LTD
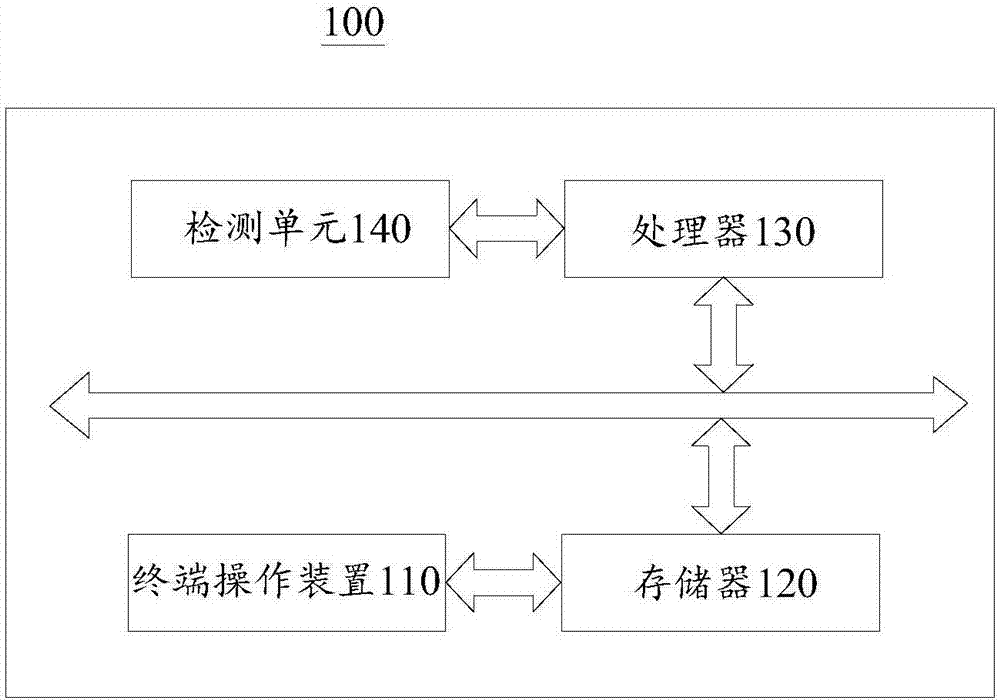
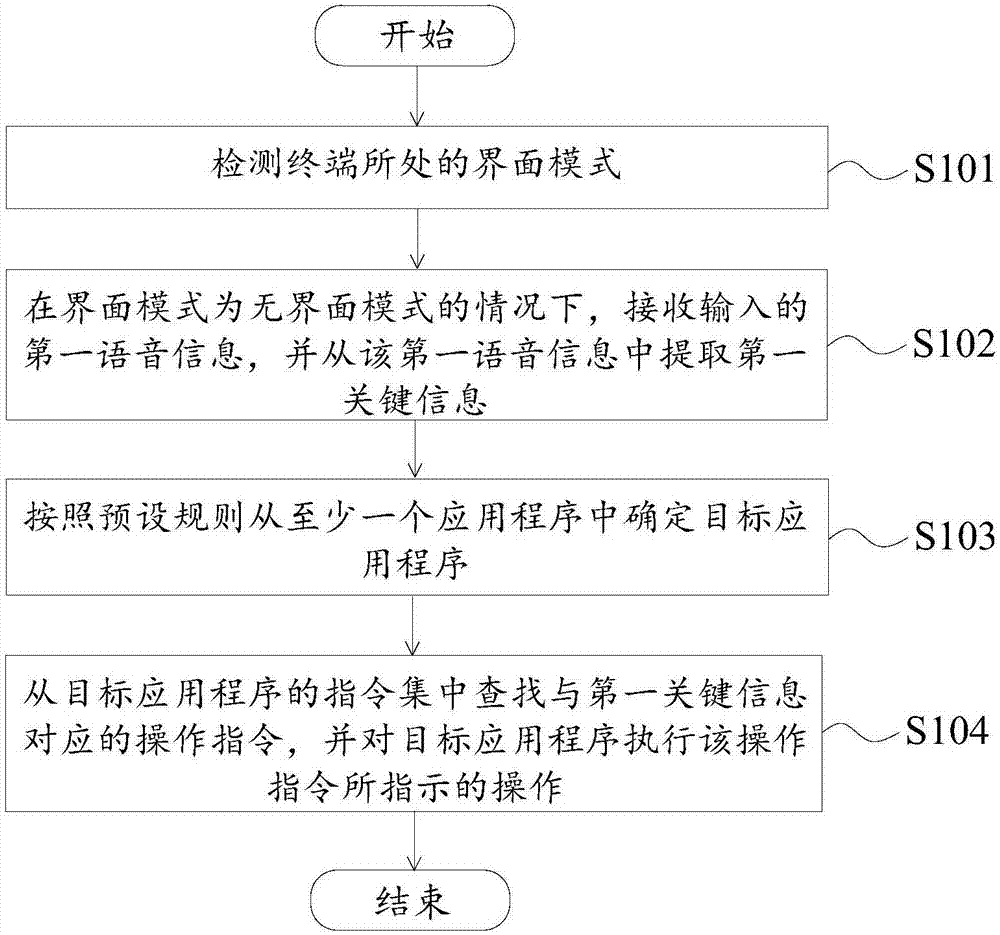
Terminal operation method and device
ActiveCN107240400ASubstation equipmentProgram loading/initiatingInstruction setOperating instruction
Owner:SIMPLECREDIT MICRO LENDING CO LTD
Incremental program modification based on usage data
InactiveUS20080034349A1Well formedError detection/correctionProgram loading/initiatingParallel computingComputerized system
Owner:MICROSOFT TECH LICENSING LLC
Control method and device for mobile terminal and mobile terminal
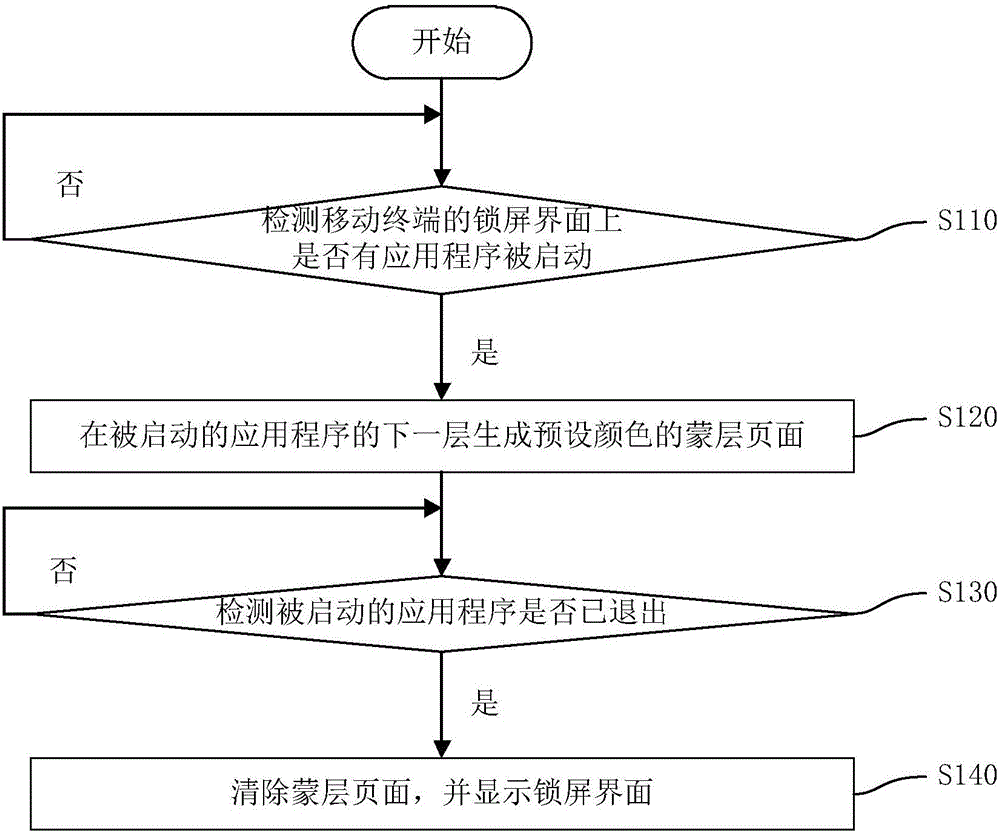
ActiveCN106250152AAvoid mistaking that the mobile terminal itself has a splash screen, etc.Improve visual effectsProgram loading/initiatingComputer terminalLock screen
Owner:KINGSOFT
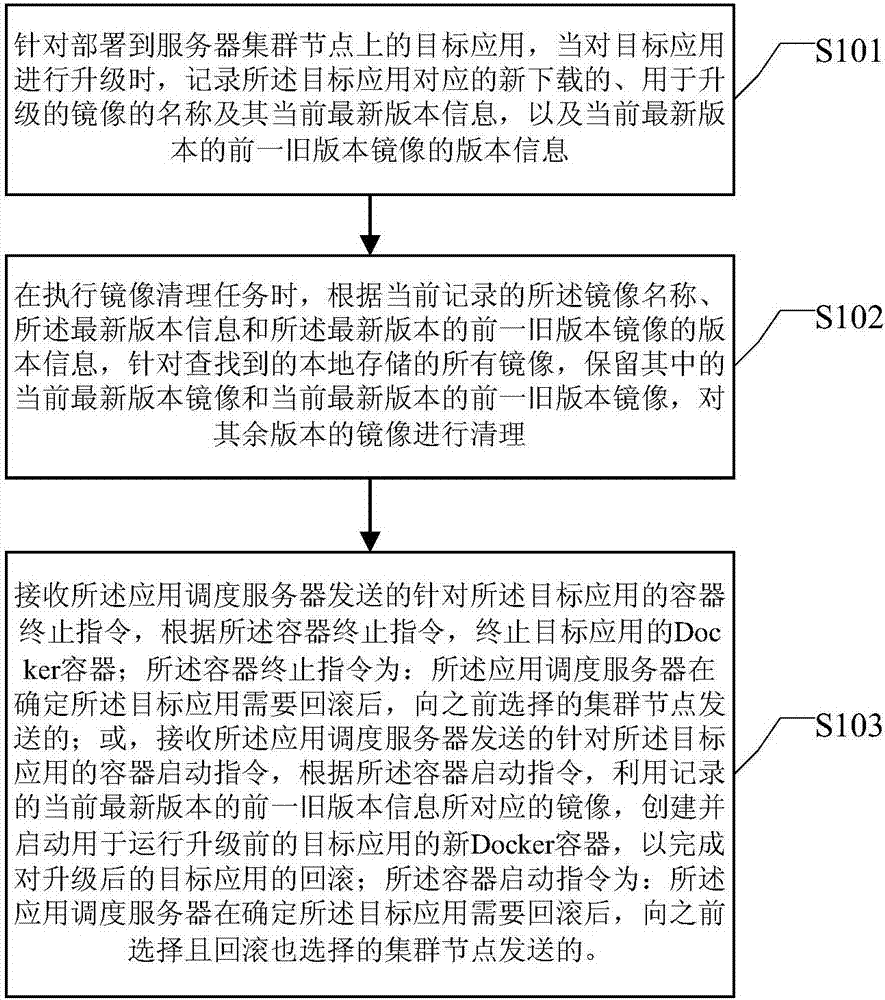
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap