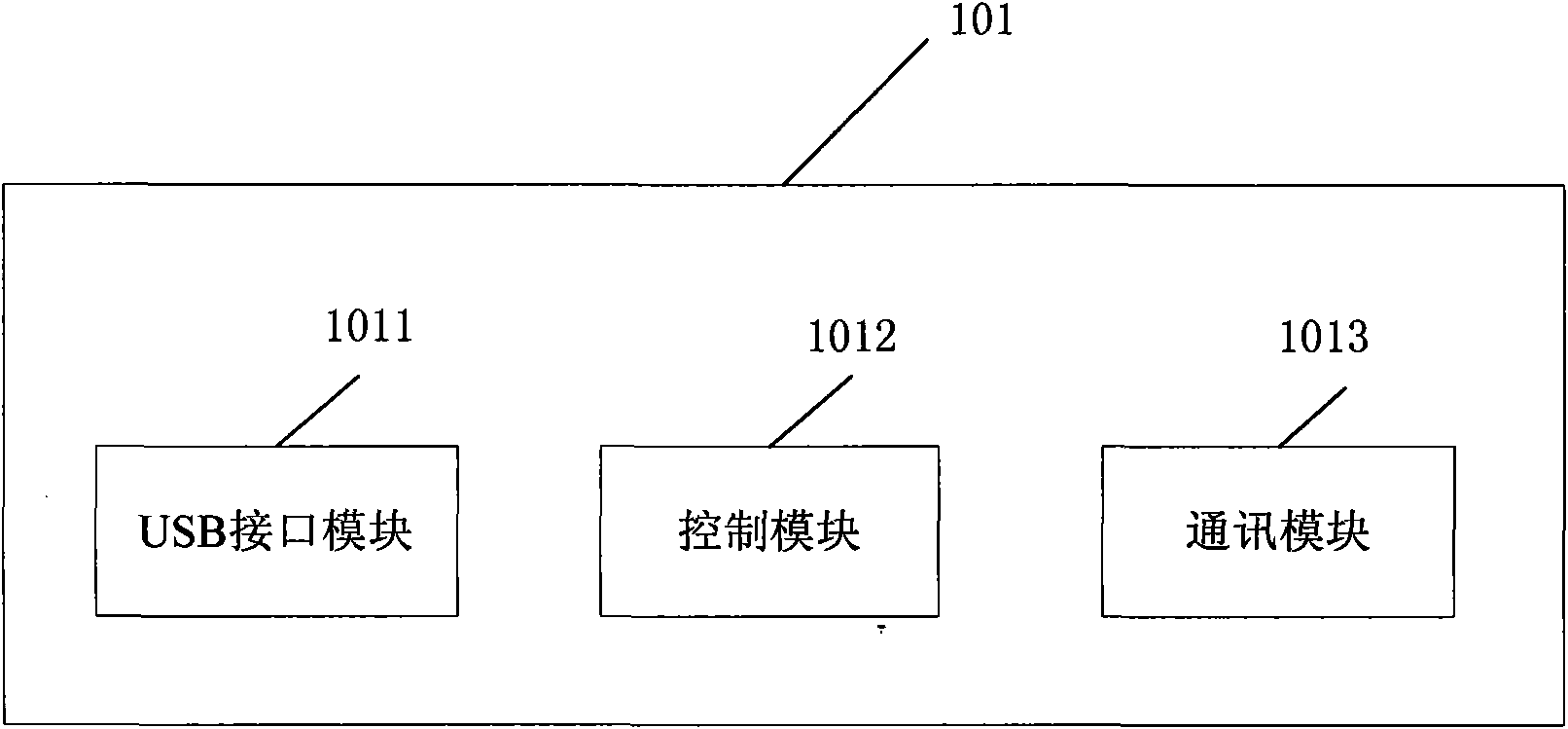
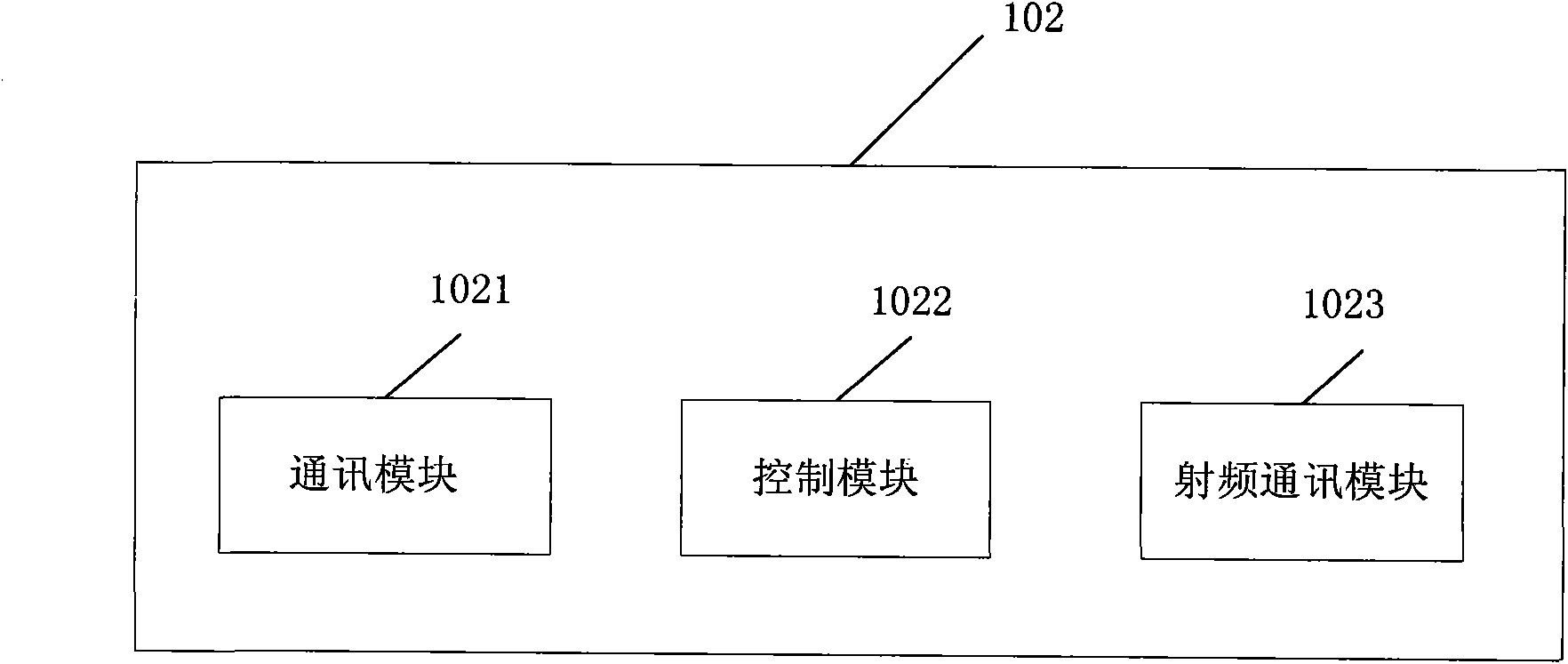
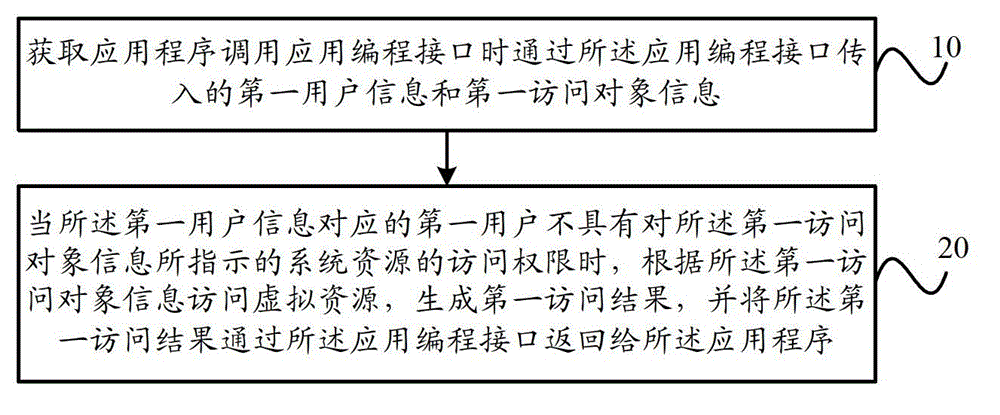
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37results about "Computer security arrangements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Methods for combating malicious software
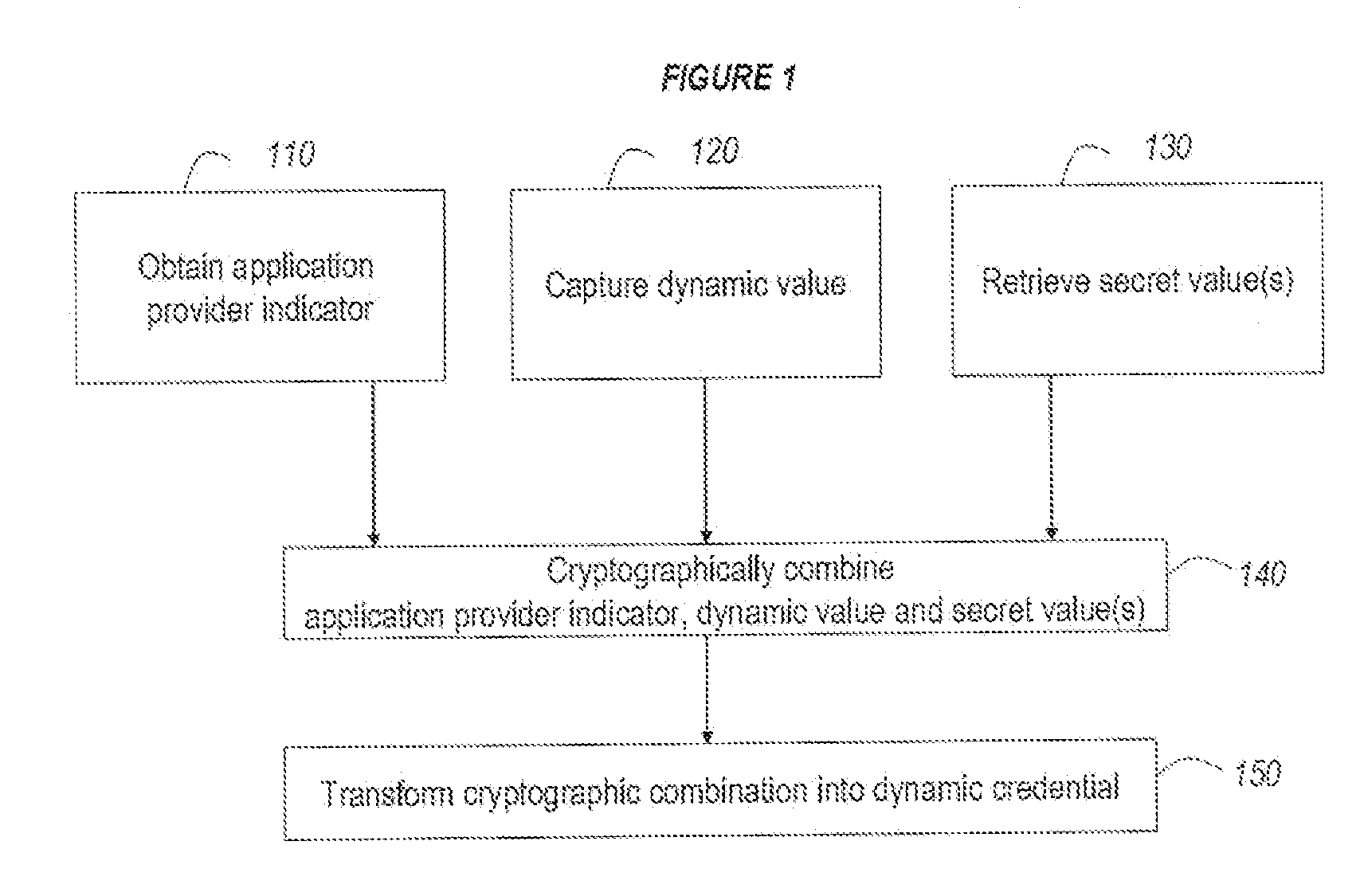
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
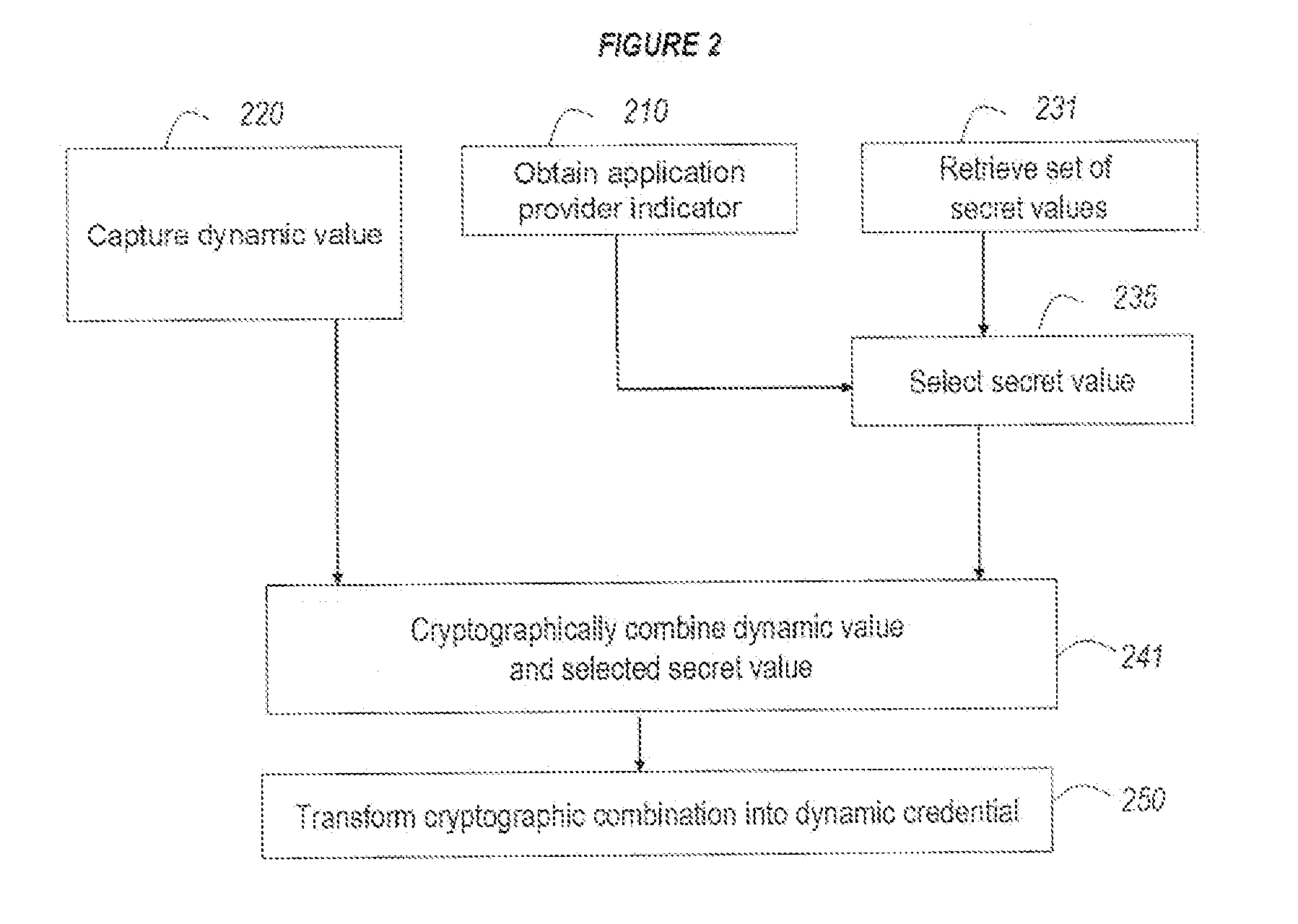
Methods for Single Signon (SSO) Using Decentralized Password and Credential Management
ActiveUS20130166918A1Decentralized credential managementShorten the timeUser identity/authority verificationComputer security arrangementsDistributed serversEnd to end security
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
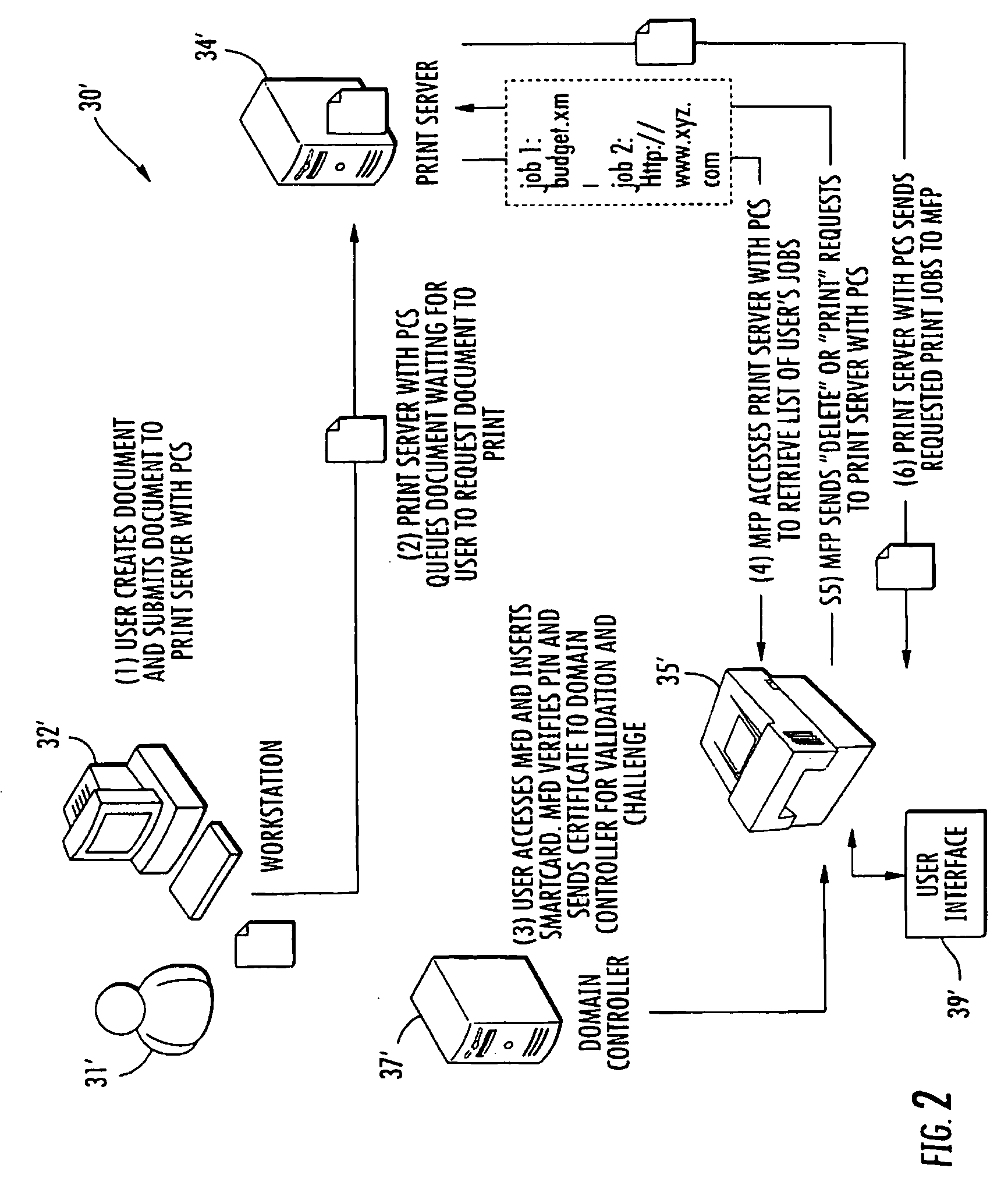
Print management system and related methods
ActiveUS20090009802A1Easy to manageComputer security arrangementsMultiple digital computer combinationsClient-sideComputer science
Owner:PHAROS SYST INT
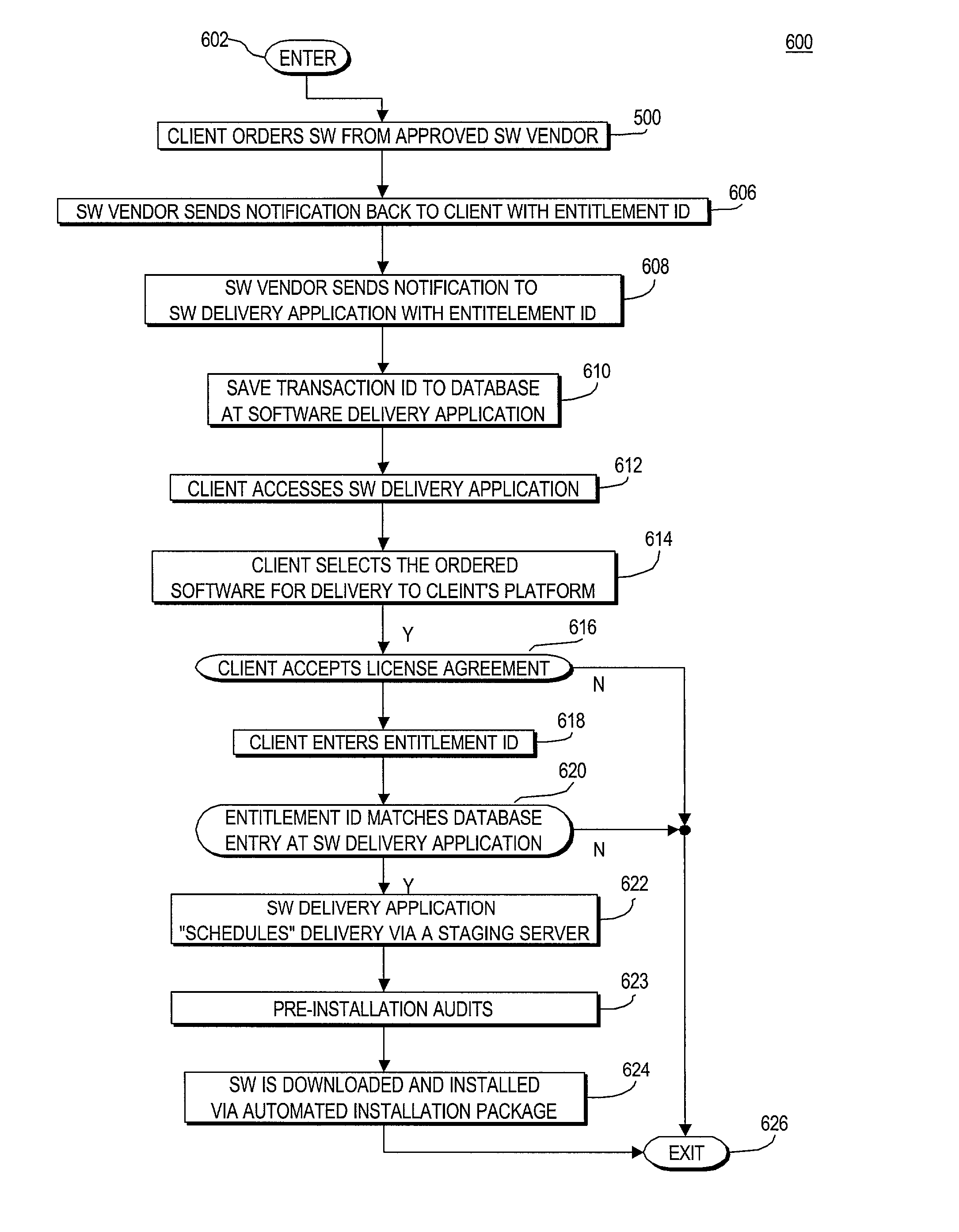
Automated entitlement verification for delivery of licensed software
ActiveUS20030005427A1Computer security arrangementsProgram loading/initiatingClient-sideCentralized management
Owner:ACTIVISION PUBLISHING
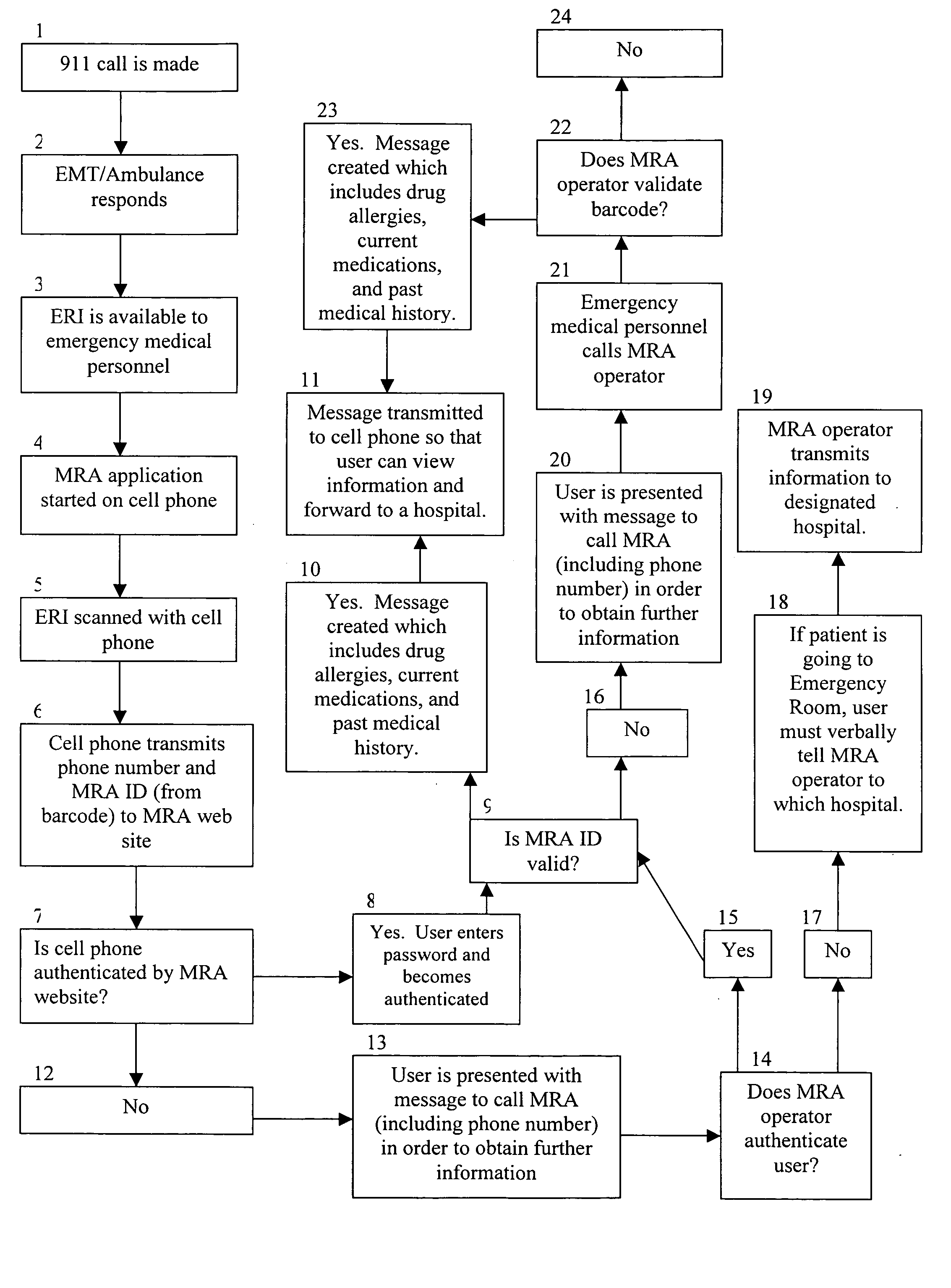
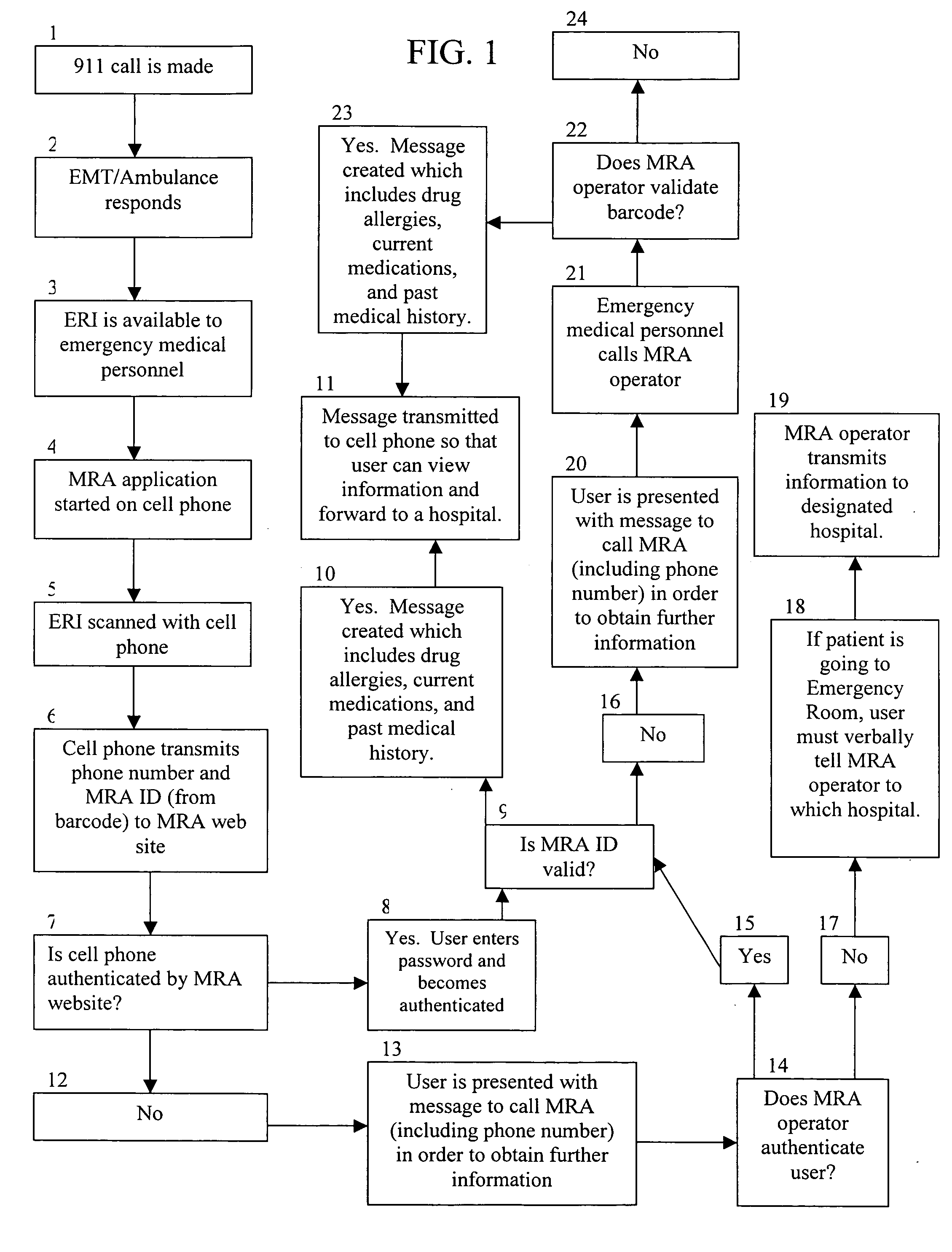
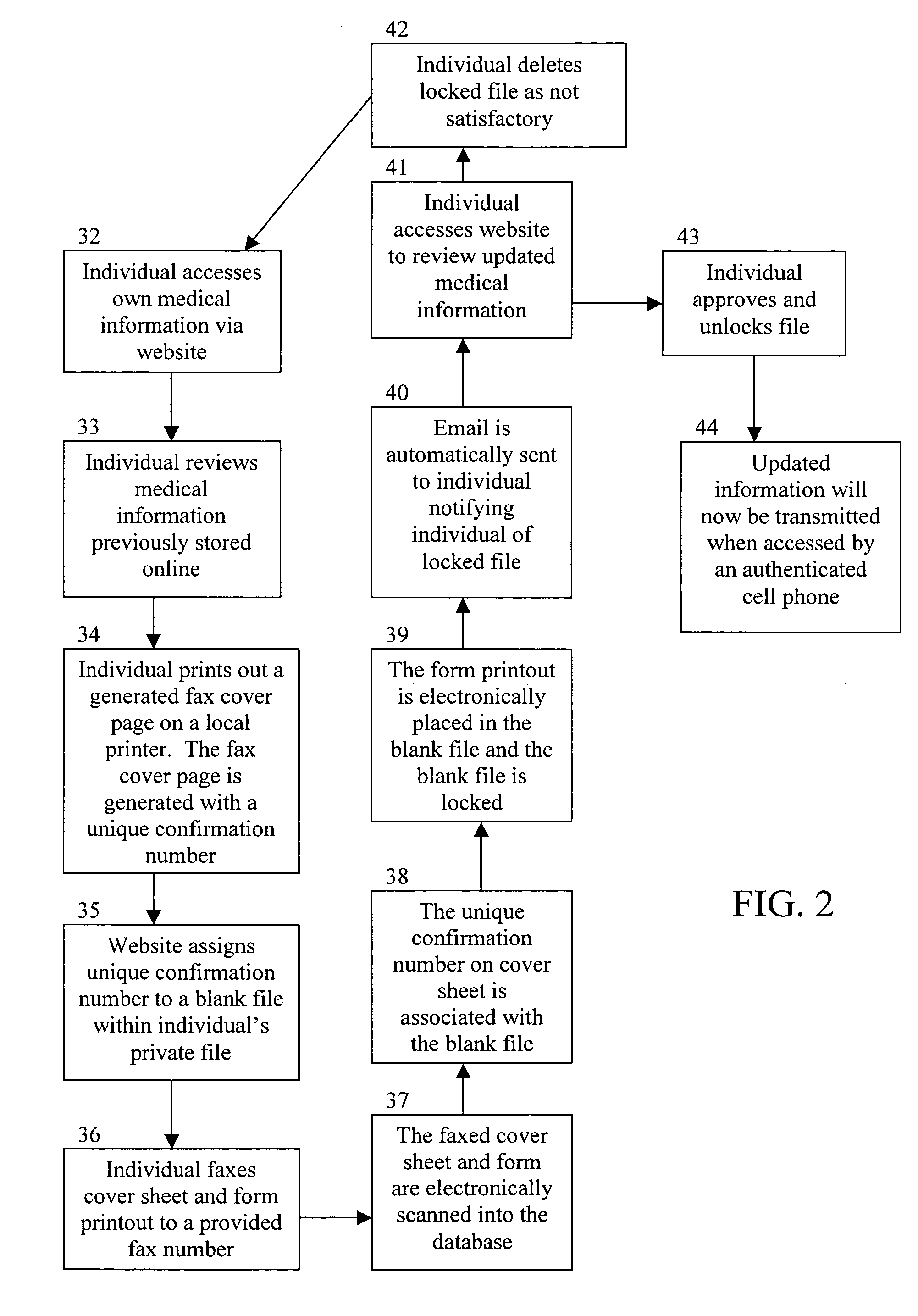
Method for transmitting medical information idetified by a unique identifier
ActiveUS20070138253A1Accessing medical informationGuaranteed normal transmissionData processing applicationsComputer security arrangementsEmergency medical careMedical emergency
Owner:BML MEDRECORDSALERT
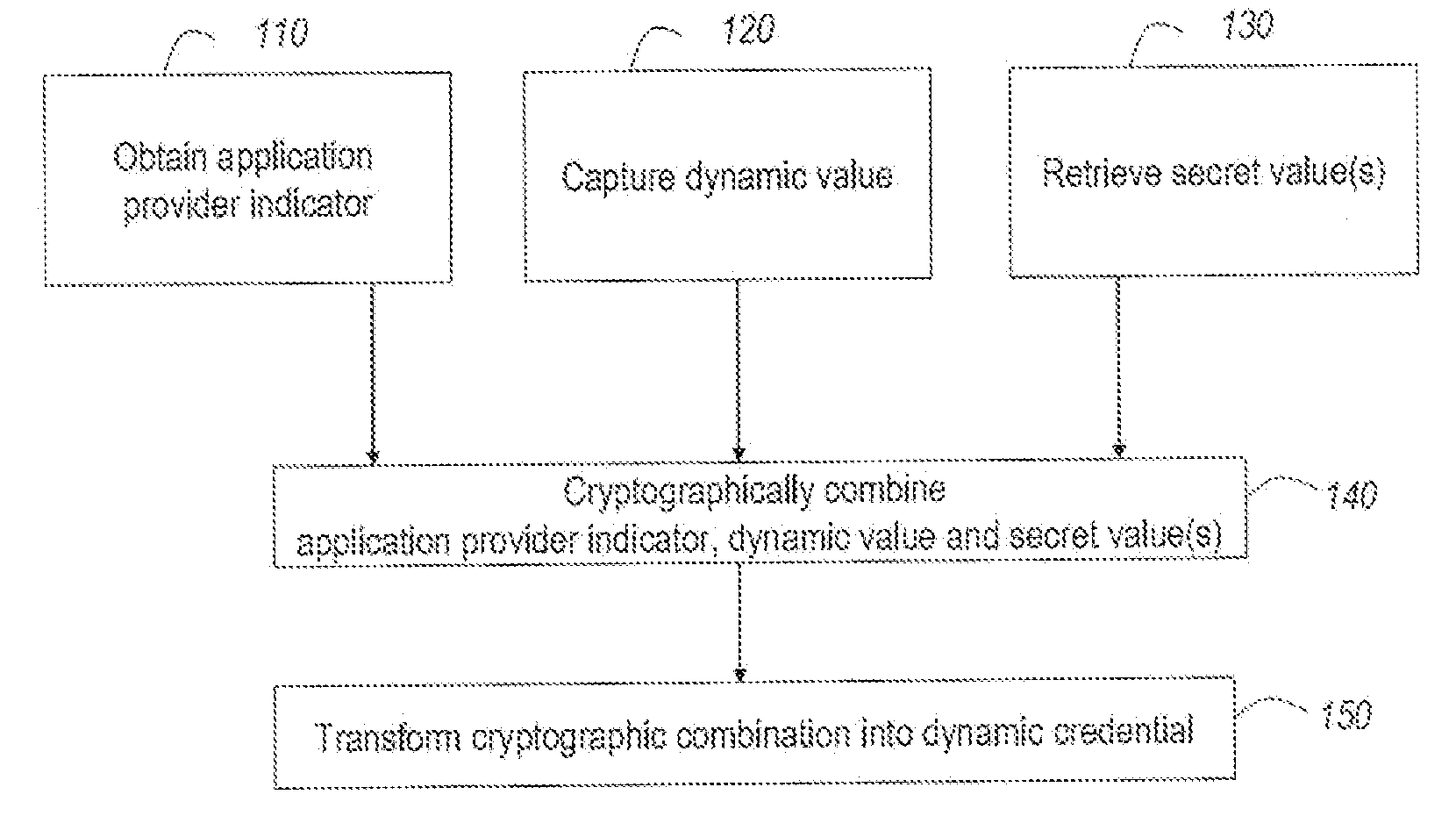
Strong authentication token usable with a plurality of independent application providers
ActiveUS20110099384A1Low costCost can be dividedMultiple keys/algorithms usageDigital data processing detailsPersonalizationUnique identifier
Owner:ONESPAN NORTH AMERICA INC
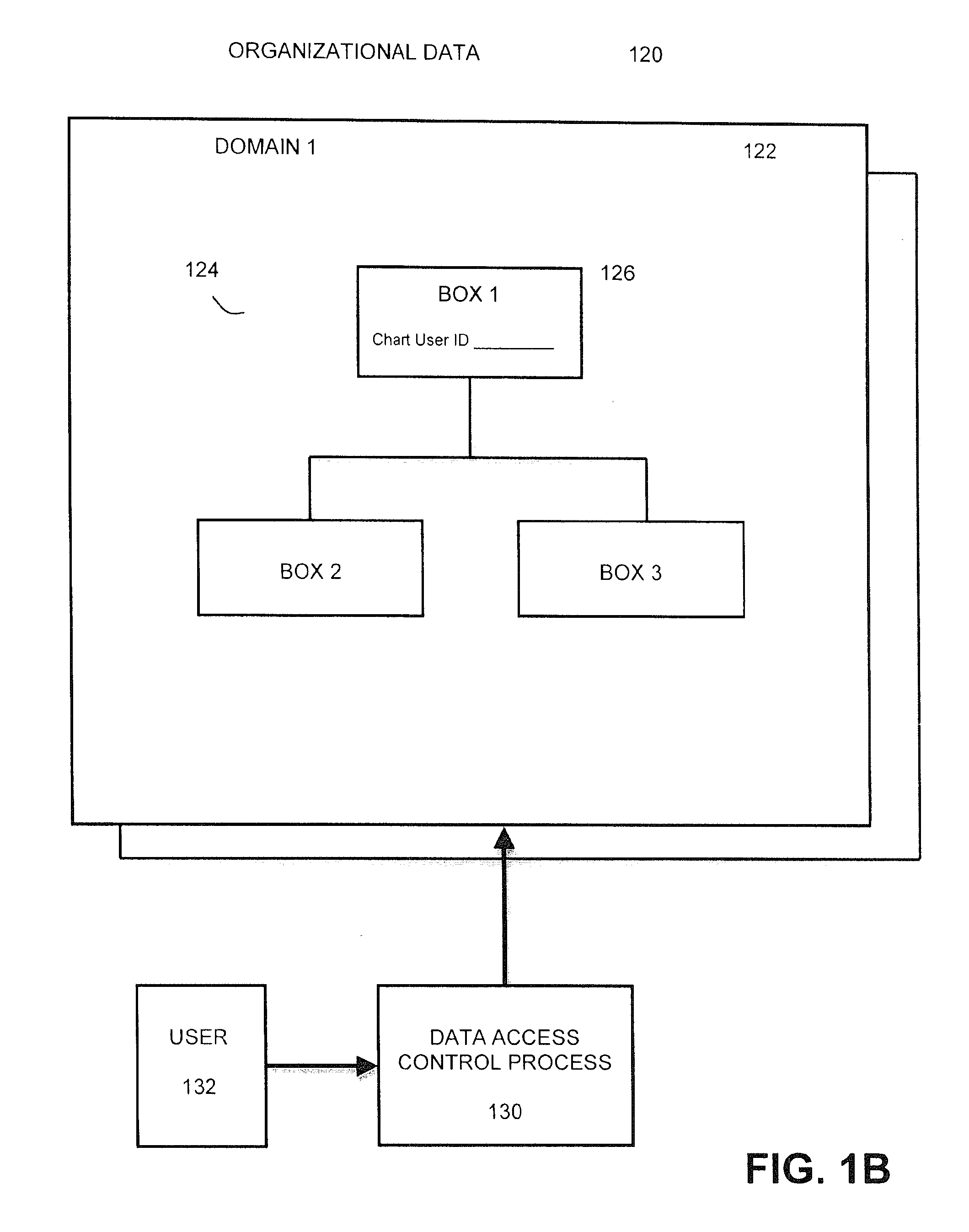
Method and system for controlling data access to organizational data maintained in hierarchical
Owner:SABA SOFTWARE
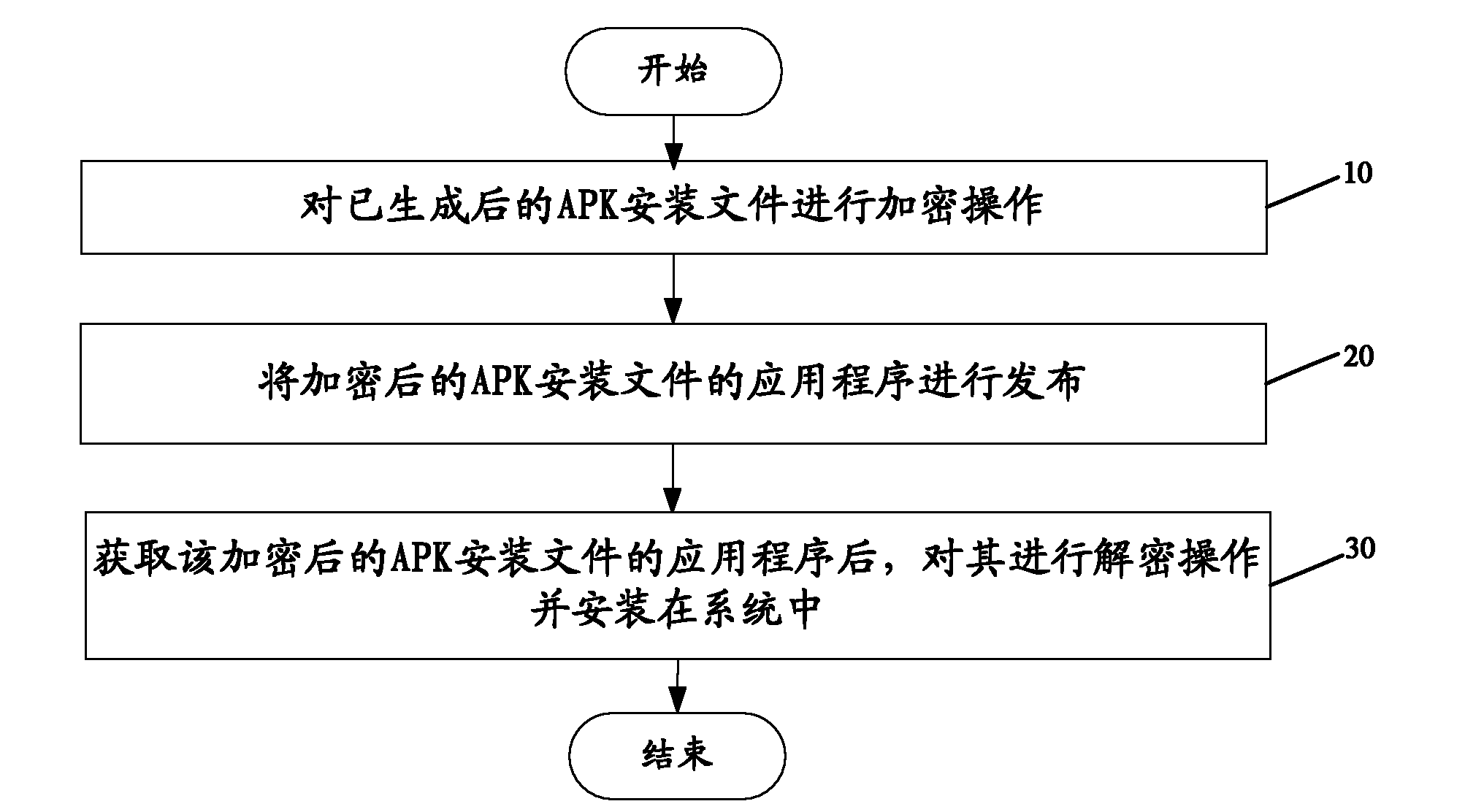
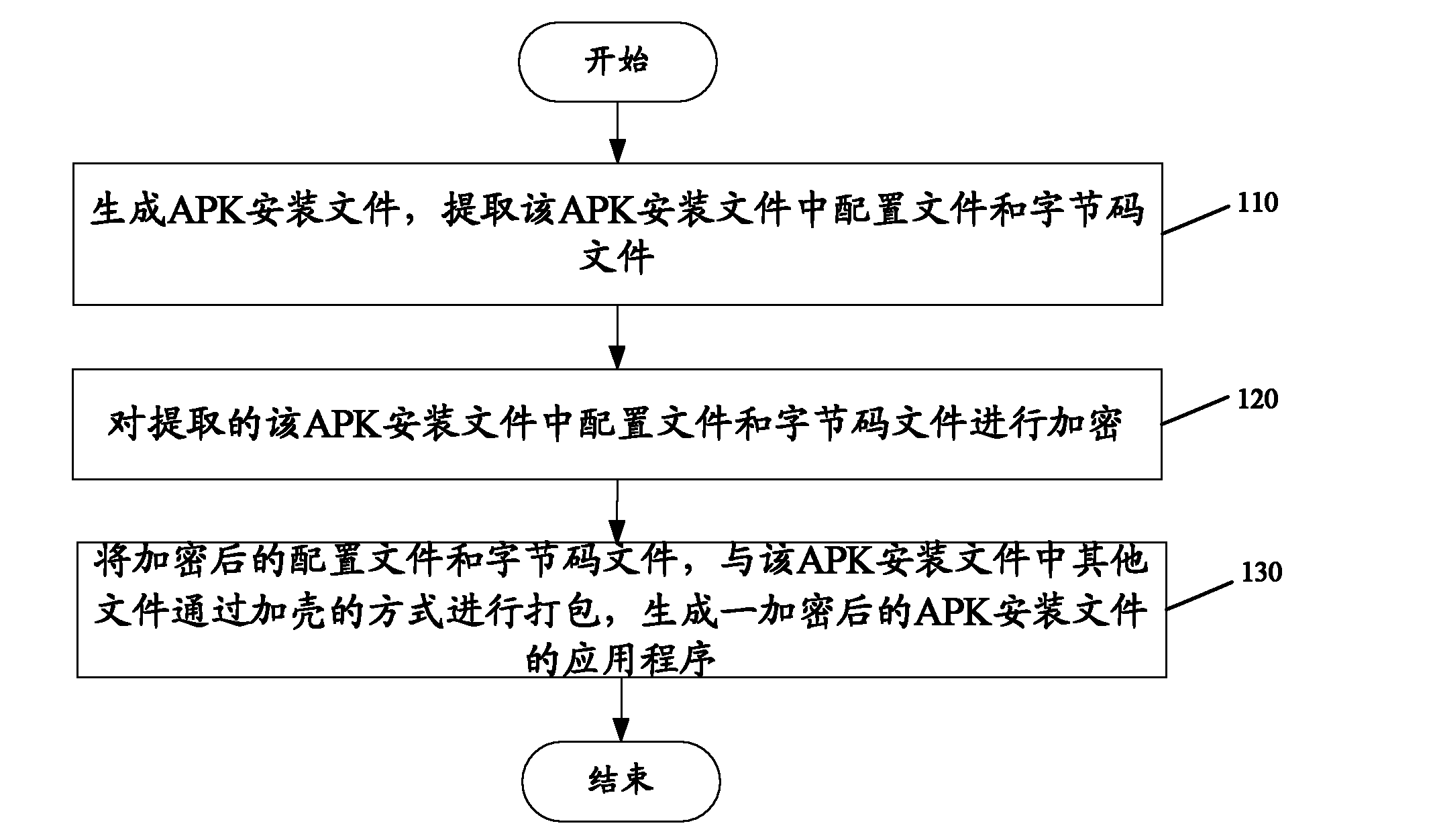
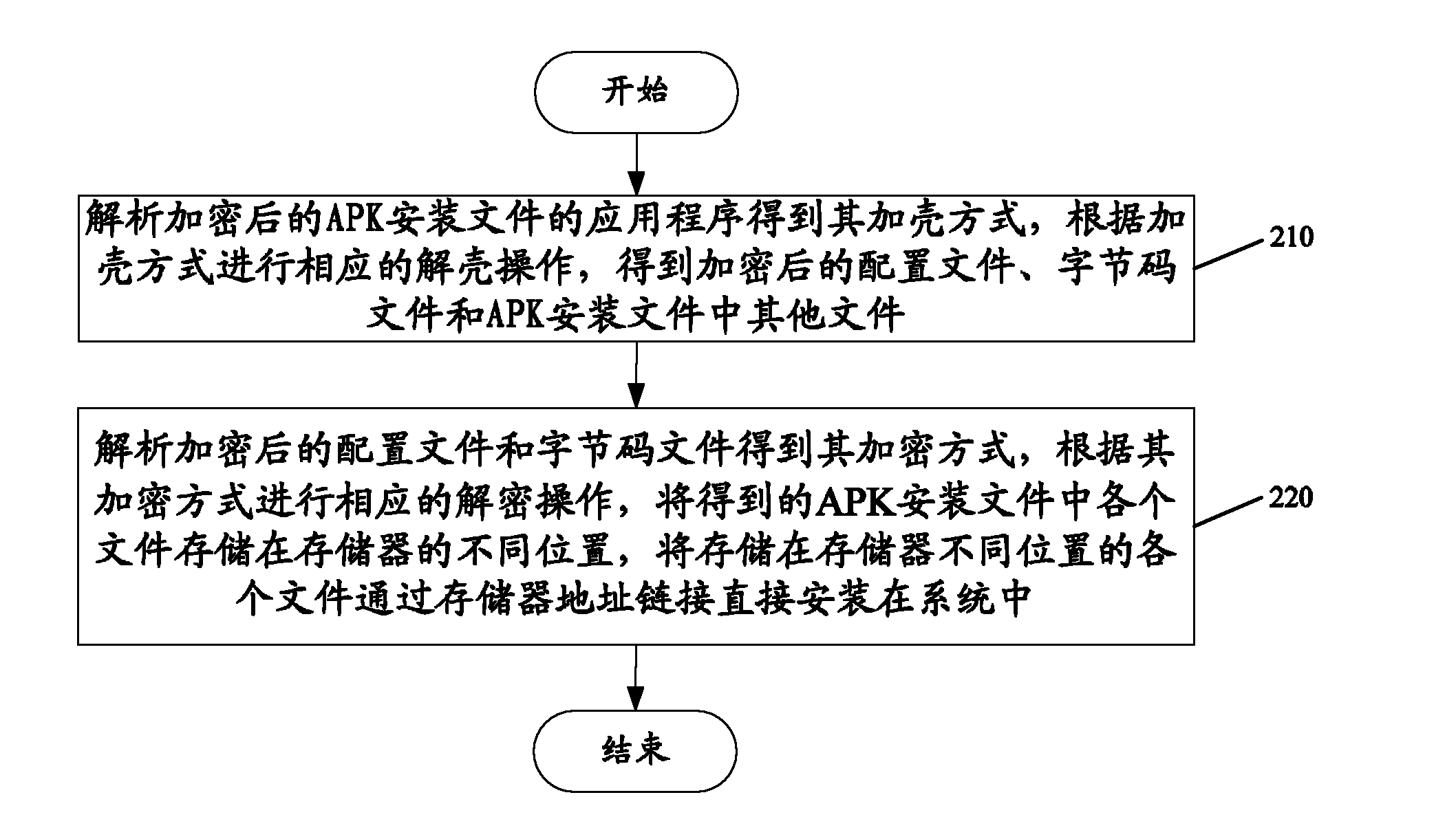
Android-based platform application installation control method and system
InactiveCN102087605AComputer security arrangementsProgram loading/initiatingApplication softwareEncryption
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
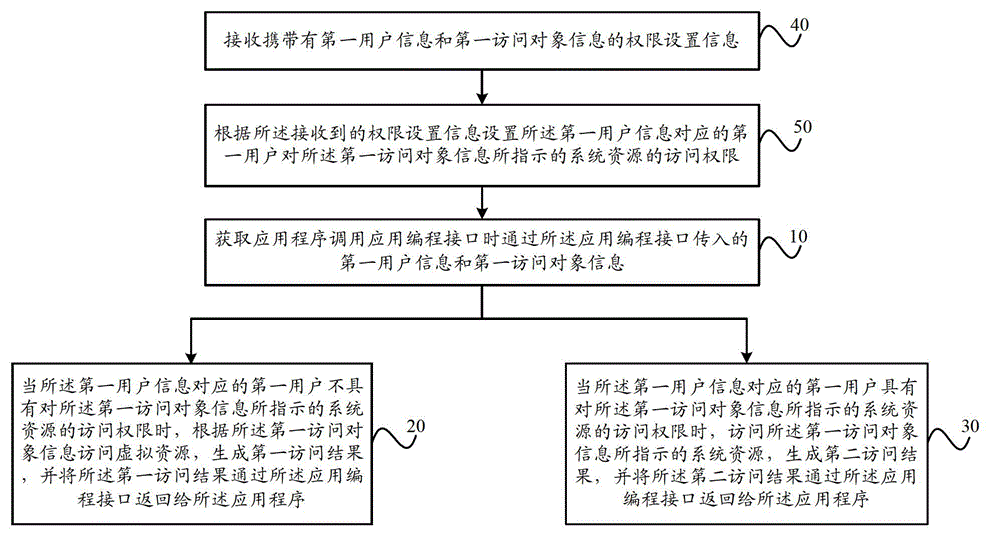
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS20090182873A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyNetwork behavior
Owner:CONNEXITY AUDIENCE INC
Centralized Device Virtualization Layer For Heterogeneous Processing Units
ActiveUS20100146620A1Operational speed enhancementResource allocationVirtualizationOperational system
A method for providing an operating system access to devices, including enumerating hardware devices and virtualized devices, where resources associated with a first hardware device are divided into guest physical resources creating a software virtualized device, and multiple instances of resources associated with a second hardware device are advertised thereby creating a hardware virtualized device. First and second permission lists are generated that specify which operating systems are permitted to access the software virtualized device and the hardware virtualized device, respectively. First and second sets of virtual address maps are generated, where each set maps an address space associated with either the software virtualized device or the hardware virtualized device into an address space associated with each operating system included in the corresponding permission list. The method further includes arbitrating access requests from each of the plurality of operating systems based on the permission lists and the virtual address maps.
Owner:NVIDIA CORP
Systems, methods and computer program products for administration of computer security threat countermeasures to a computer system
InactiveUS20050039046A1Memory loss protectionDigital data processing detailsCountermeasureOperational system
Owner:TREND MICRO INC
Malware detection system with contextual analysis
ActiveUS10581874B1Improve accuracyDecrease positive outcomeComputer security arrangementsSecuring communicationEngineeringMalware
A computerized method for detecting malware associated with an object. The method includes operations of analyzing an object to obtain a first set of attributes, where the first set of attributes include one or more characteristics associated with the object. Furthermore, the object is processed with a virtual machine to obtain a second set of attributes. The second set of attributes corresponds to one or more monitored behaviors of the virtual machine during processing of the object. Thereafter, a threat index is determined based, at least in part, on a combination of at least one attribute of the first set of attributes and at least one attribute of the second set of attributes. The threat index represents a probability of maliciousness associated with the object.
Owner:FIREEYE SECURITY HLDG US LLC
Kernel acceleration technology for virtual machine optimization
Owner:PARALLELS INT GMBH
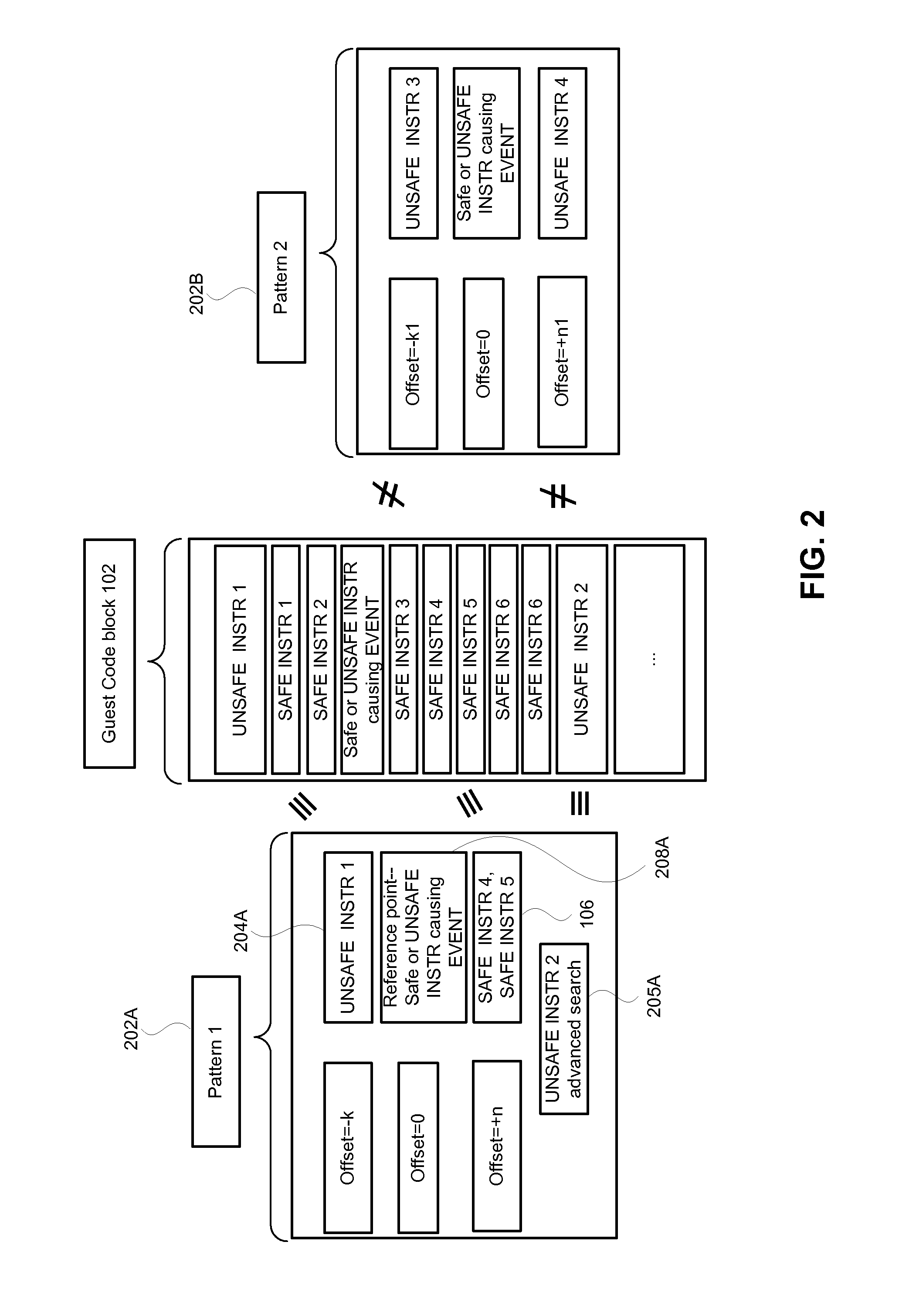
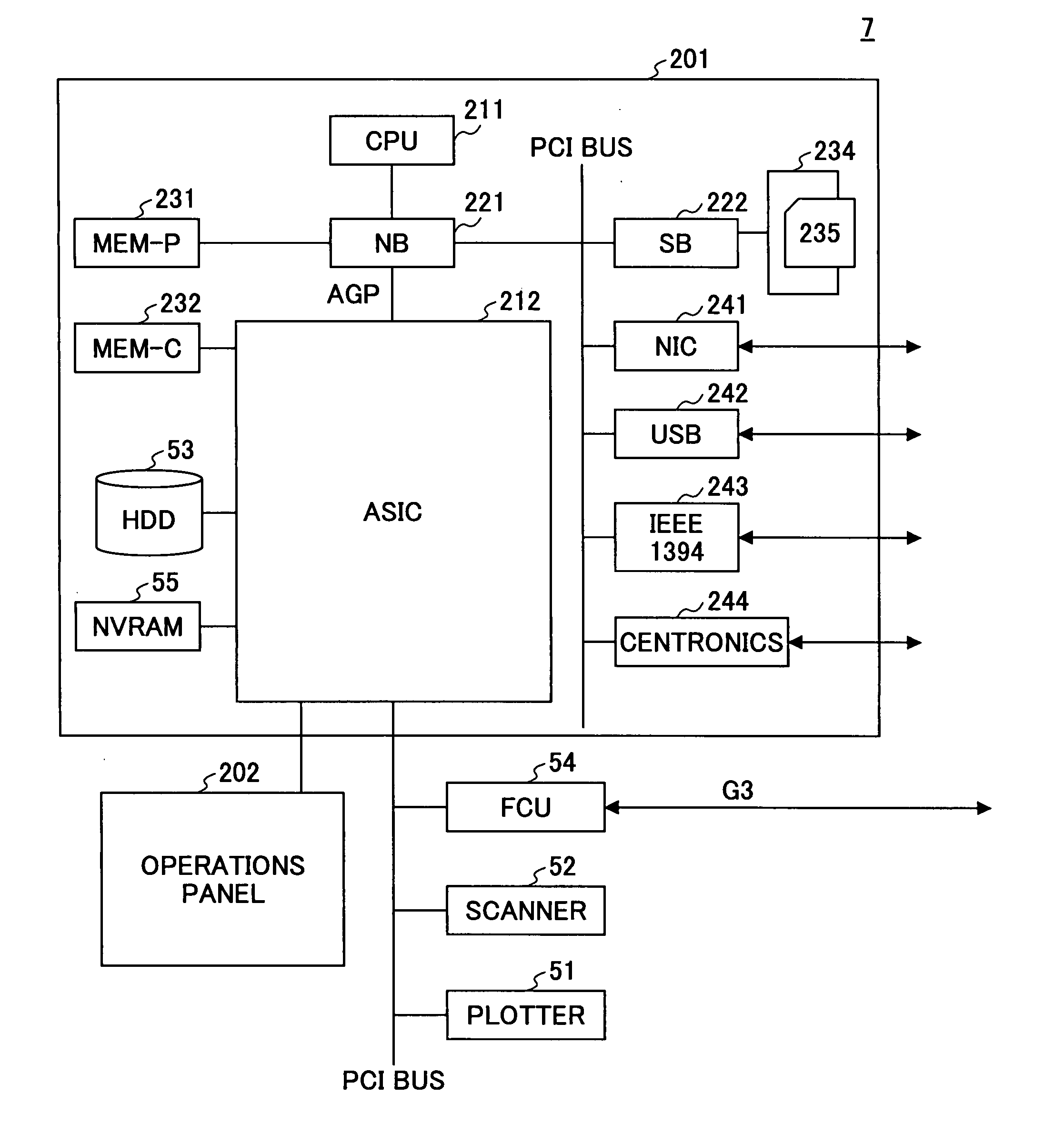
Image forming apparatus capable of managing configuration information of multiple modules
ActiveUS20070283253A1Prevent serious security vulnerabilityImprove securityDigital computer detailsComputer security arrangementsMultiple applicationsInformation storage
Owner:RICOH KK
Secure wireless communication
ActiveUS20090103728A1Unauthorised/fraudulent call preventionDigital data processing detailsHash-based message authentication codeCryptographic protocol
Owner:ALCATEL LUCENT SAS
System and Method for Detecting and Evicting Malicious Vehicles in a Vehicle Communications Network
ActiveUS20110214178A1Improve performanceReduce impactMemory loss protectionError detection/correctionMathematical modelSimulation
In a vehicle communication network, some vehicles may be used by attackers to send false information to other vehicles which may jeopardize the safety of other vehicles. Vehicles should be able to detect malicious communications activities and to mitigate the impact of malicious vehicles by evicting (eliminating) suspected malicious vehicles from the system. Evicting a vehicle is to ignore the messages sent from the vehicle for a specified time period. Voting and sacrifice principles are combined using a mathematical model based on the “Mafia Game”. The Mafia Game model focuses on the relative size of the group of attackers within a neighborhood necessary to dominate the entire network in the neighborhood (i.e., to eventually evict all the innocent vehicles).
Owner:PERSPECTA LABS INC
Shop apparatus, purchaser apparatus, purchaser identity proving apparatus, and purchaser identity verifying apparatus
ActiveUS20080177636A1Eliminate unlinkabilityEliminate inconvenienceComputer security arrangementsBuying/selling/leasing transactionsZero-knowledge proofAuthentication
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
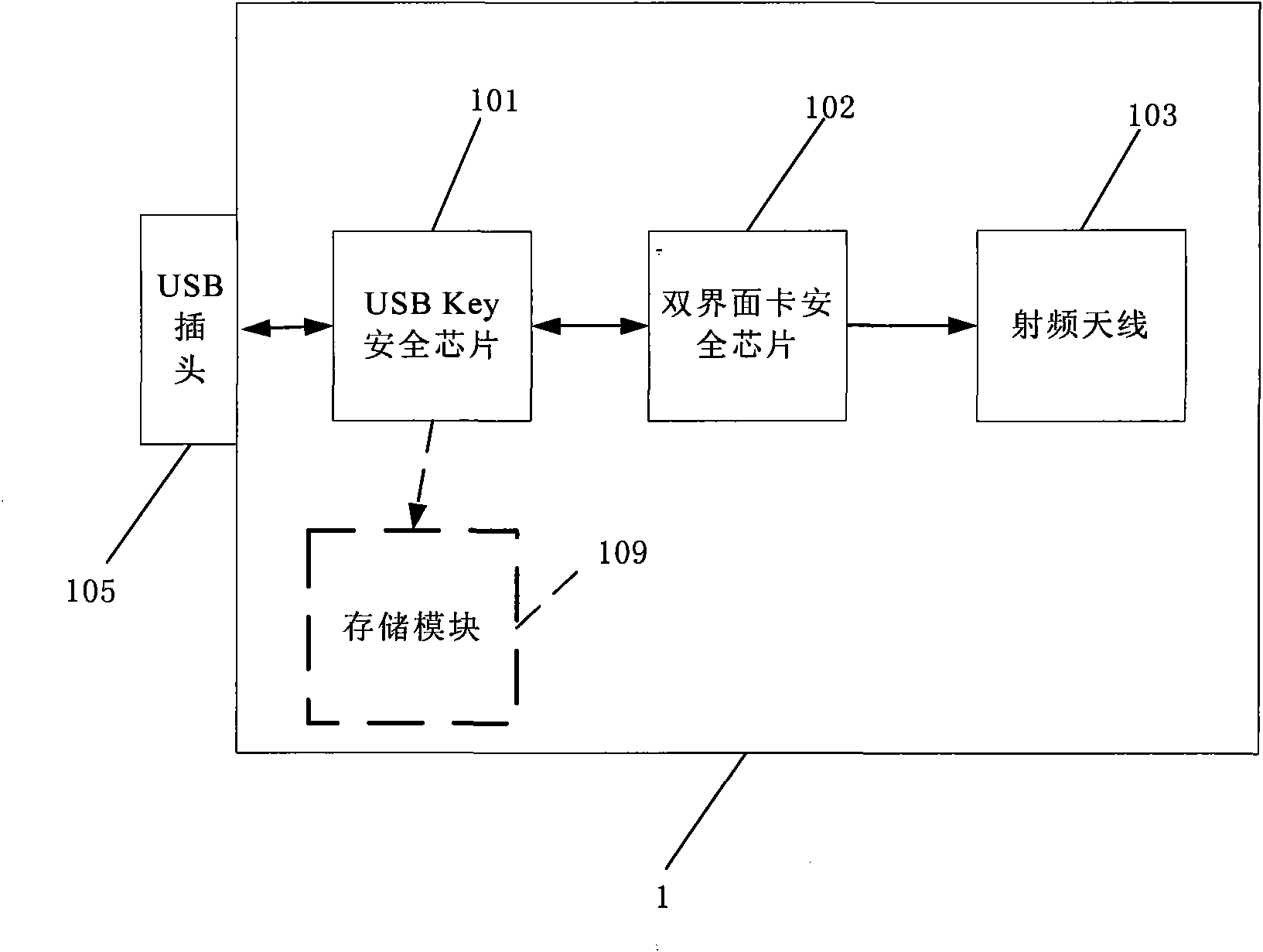
Encrypting and authenticating equipment with dual safety chips
InactiveCN101667163AUnauthorized memory use protectionComputer security arrangementsRadio frequencyEngineering
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
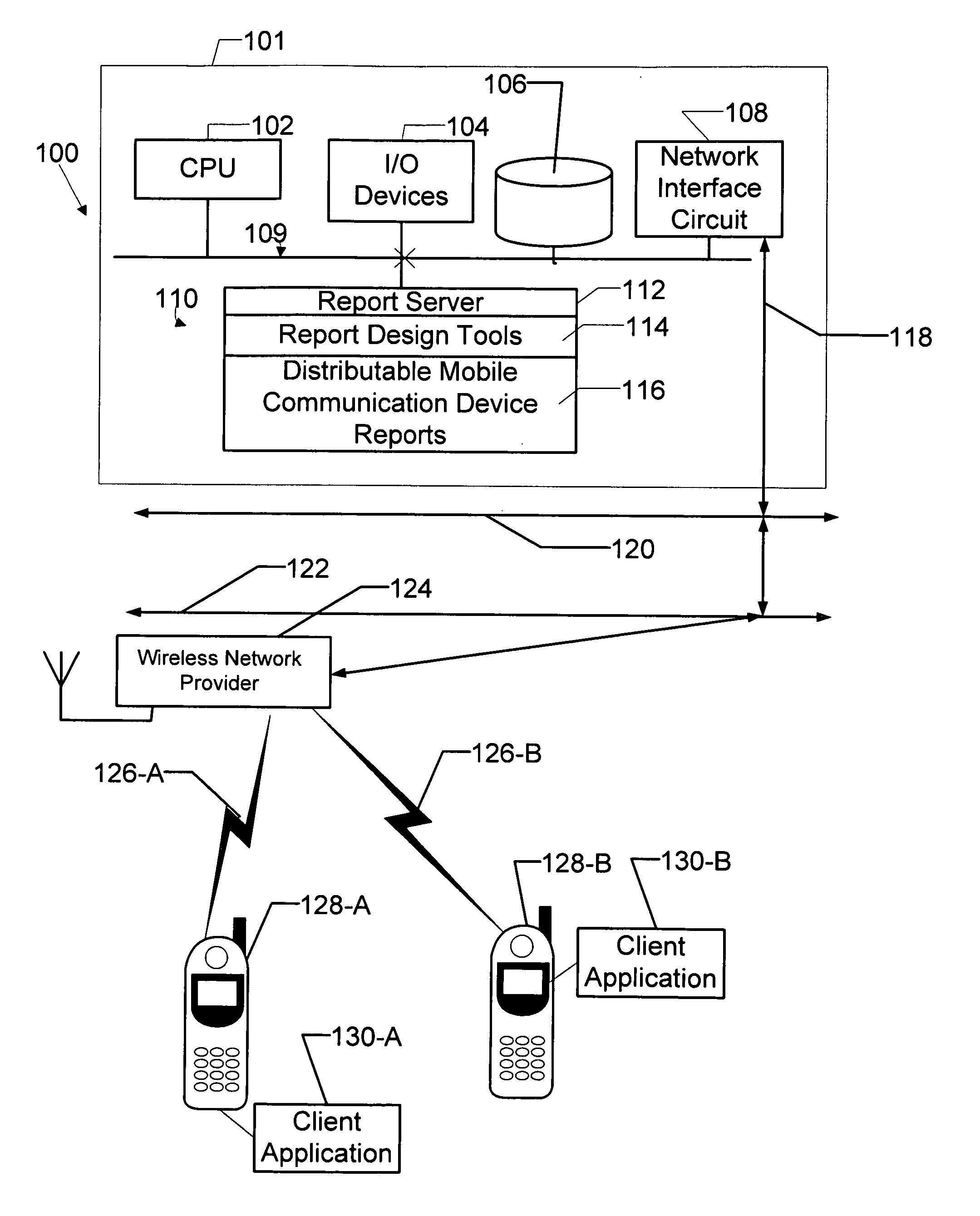
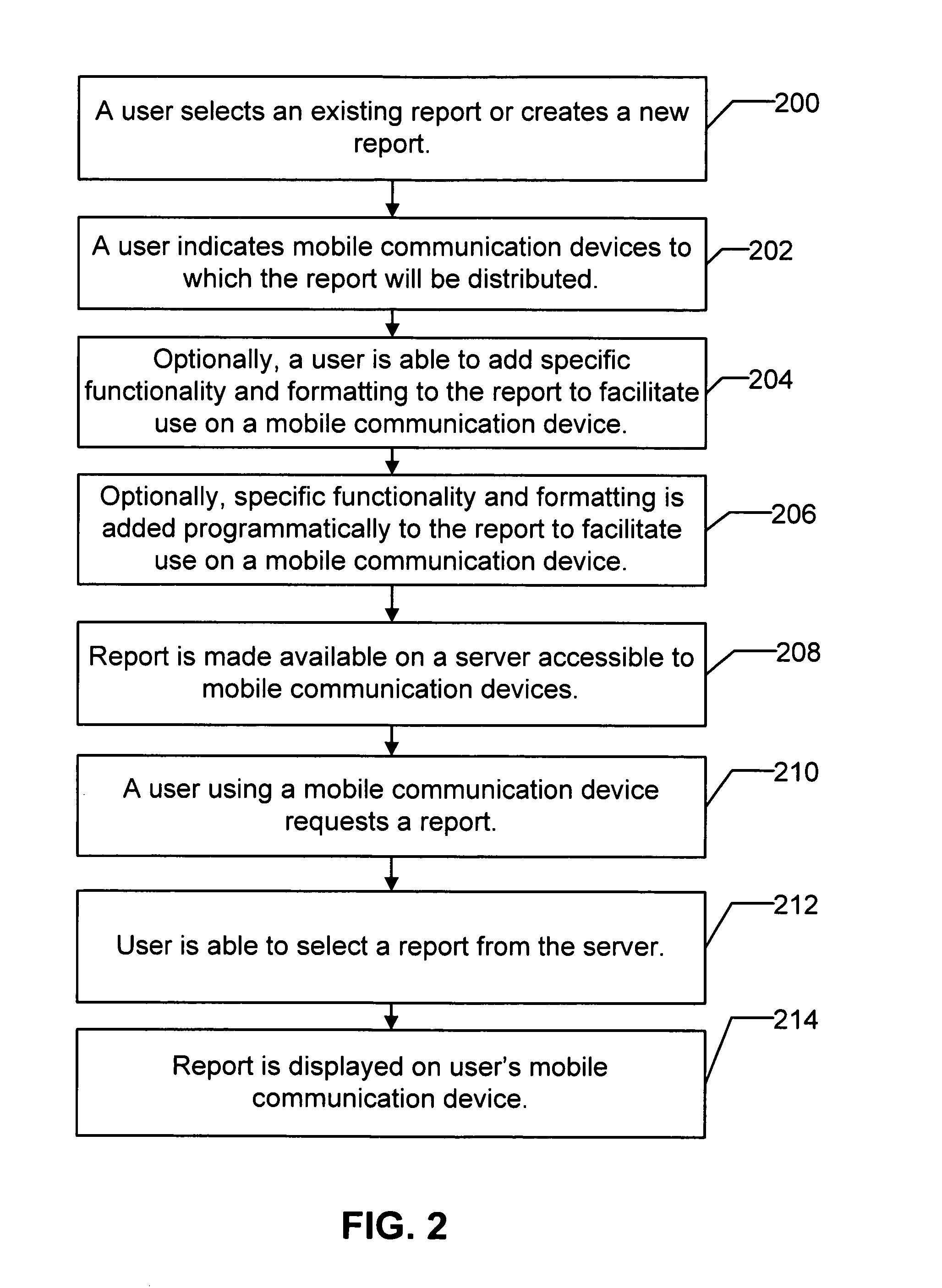
Apparatus and method for report invocation and manipulation on a mobile communication device
InactiveUS20080018928A1Designing can be facilitatedDigital data information retrievalComputer security arrangementsCommunication deviceWorld Wide Web
Owner:BUSINESS OBJECTS SOFTWARE
Network apparatus for accessing services over a network
ActiveUS7631192B1Improve securityTelevision system detailsTelemetry/telecontrol selection arrangementsComputer hardwareDisplay device
Owner:FUNAI ELECTRIC CO LTD
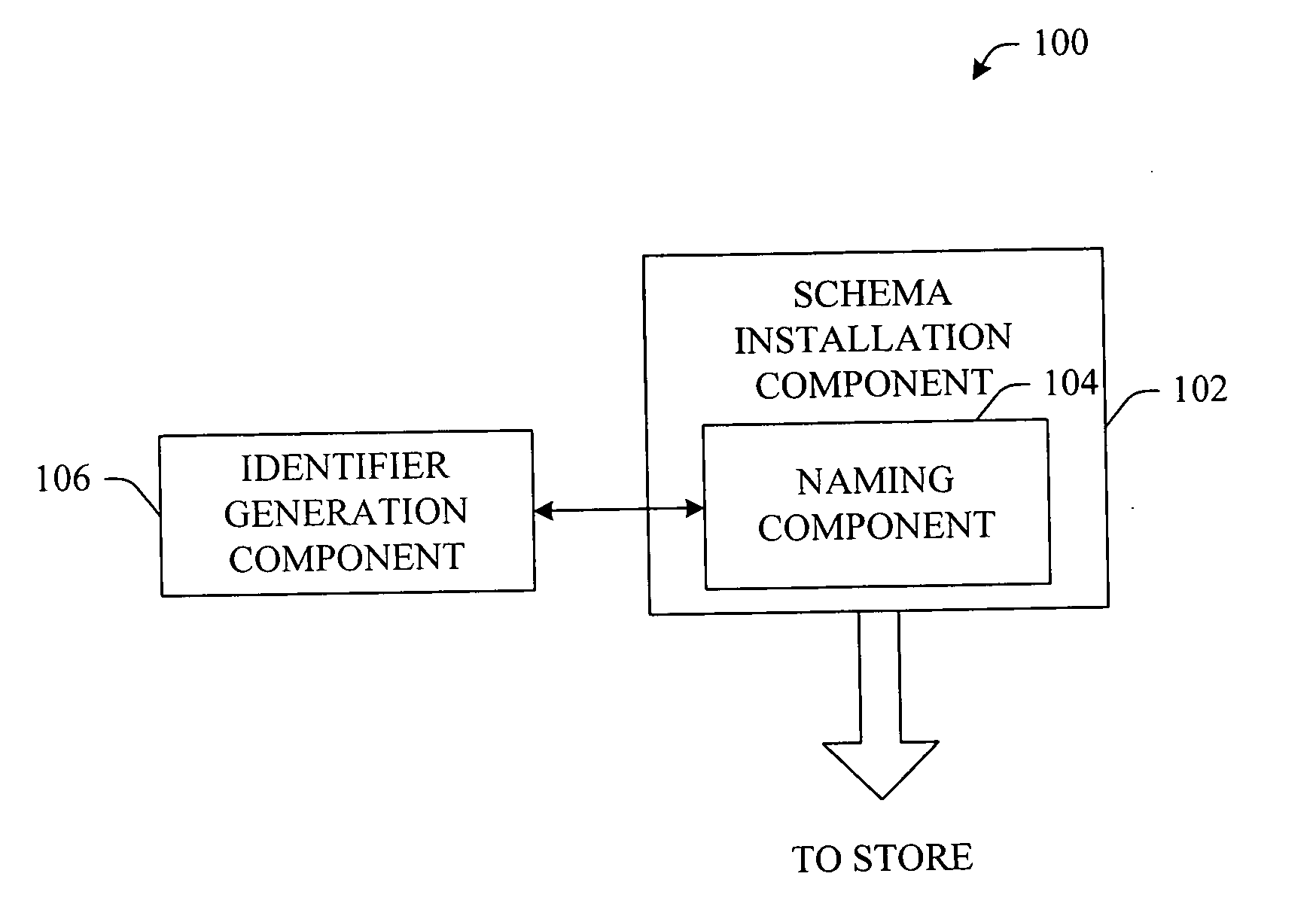
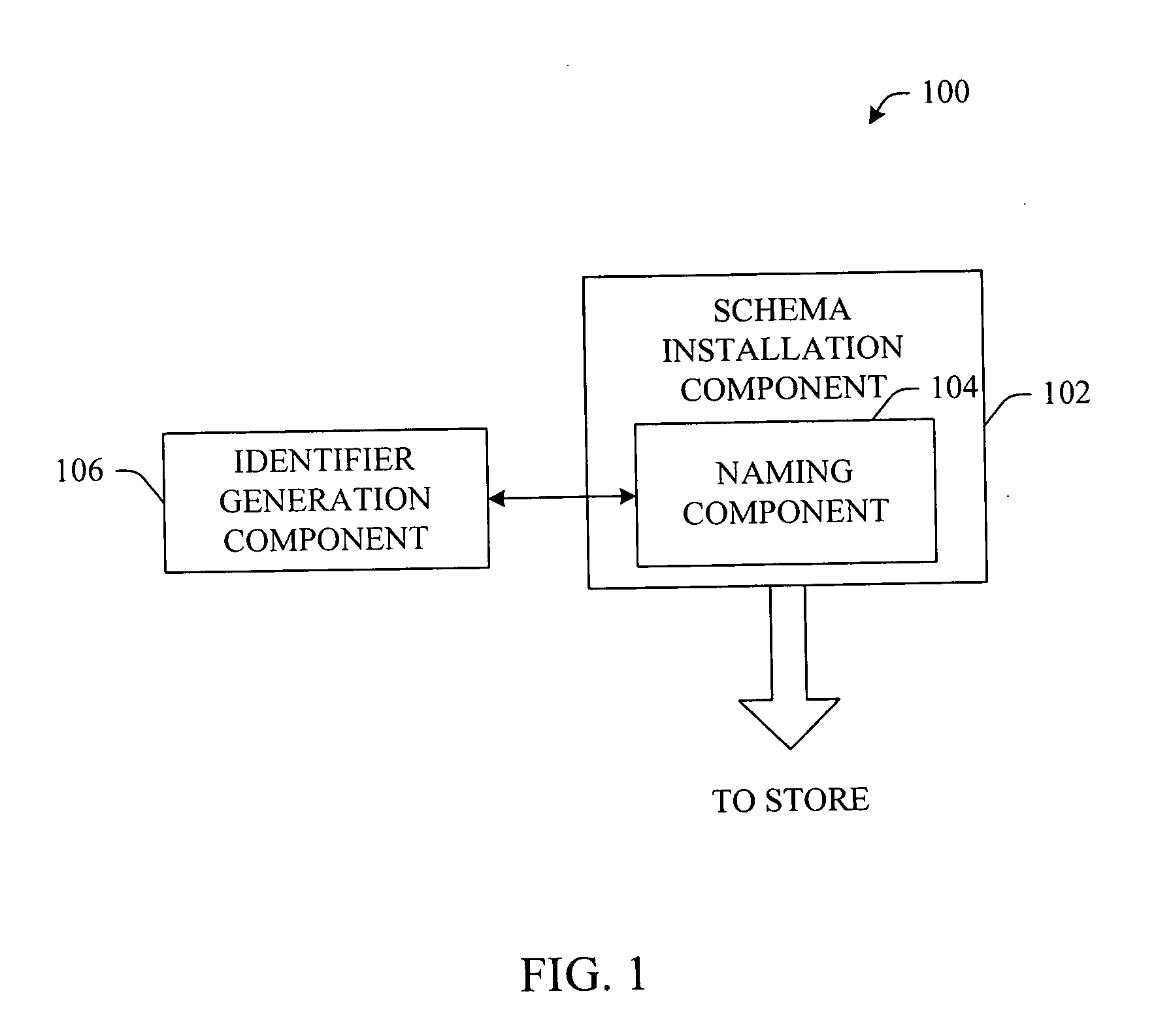
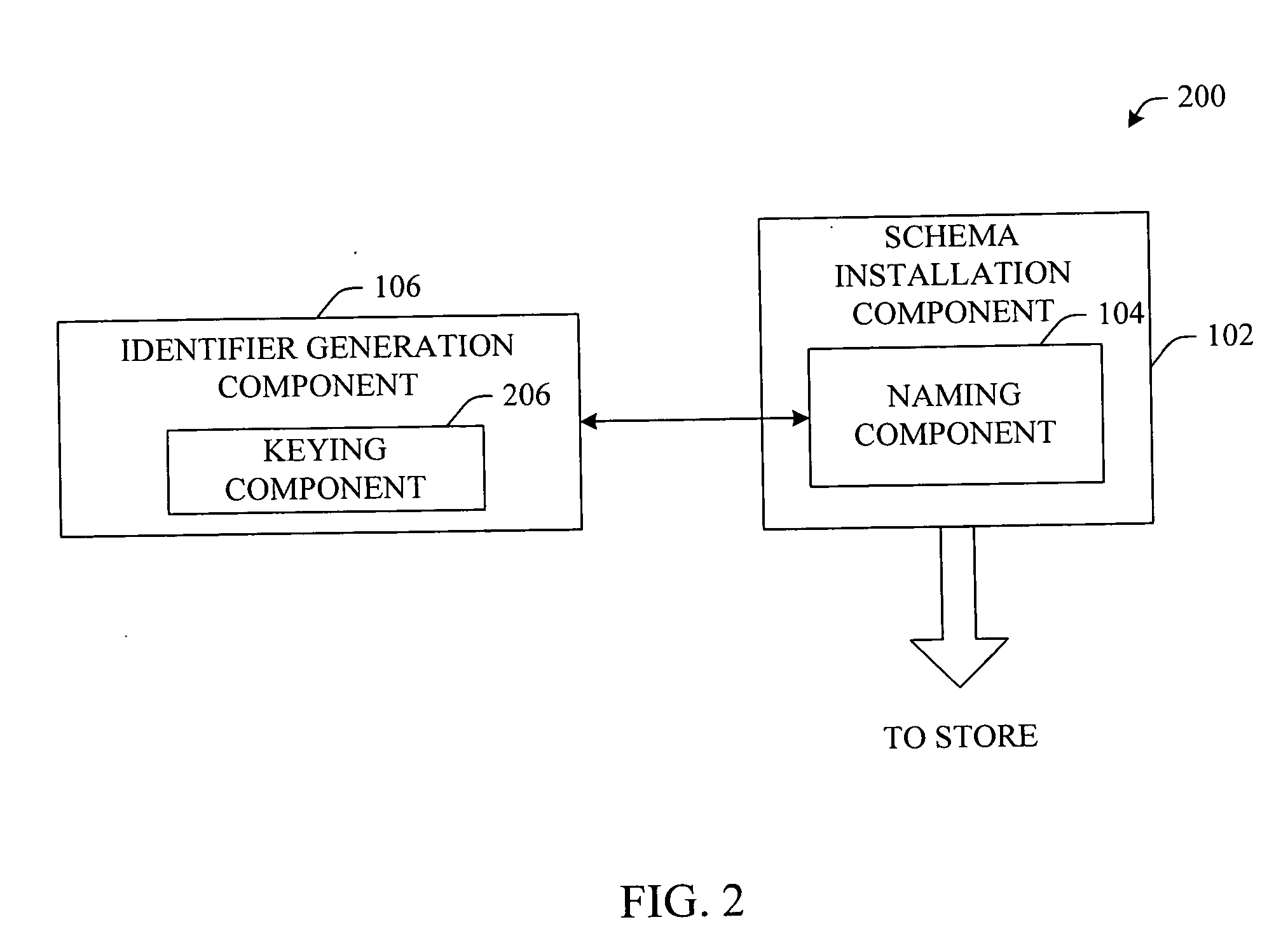
Secure schema identifier generation
InactiveUS20070050395A1Improve performanceDigital data processing detailsPublic key for secure communicationUnique identifierByte
Owner:MICROSOFT TECH LICENSING LLC
System and method for securing computers against computer viruses
In one embodiment, an antivirus mechanism (e.g., antivirus program) in a computer initiates shielding procedures in response to a triggering event indicative of a presence of a virus in the computer, the virus being of a type not recognized by the antivirus program. The shielding procedures advantageously protect important components of the computer while the antivirus program does not have the requisite antidote to directly deal with the virus.
Owner:TREND MICRO INC
Multimode Authentication
ActiveUS20120291098A1Digital data processing detailsComputer security arrangementsClient-sideDigital network
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Hand-hold terminal with handwriting recognition identity affirmation function and its implementing method
InactiveCN101482904AValid identificationGuaranteed privacyCharacter and pattern recognitionComputer security arrangementsUser needsHandwriting
Owner:SHANGHAI LINGRUI INFORMATION TECH
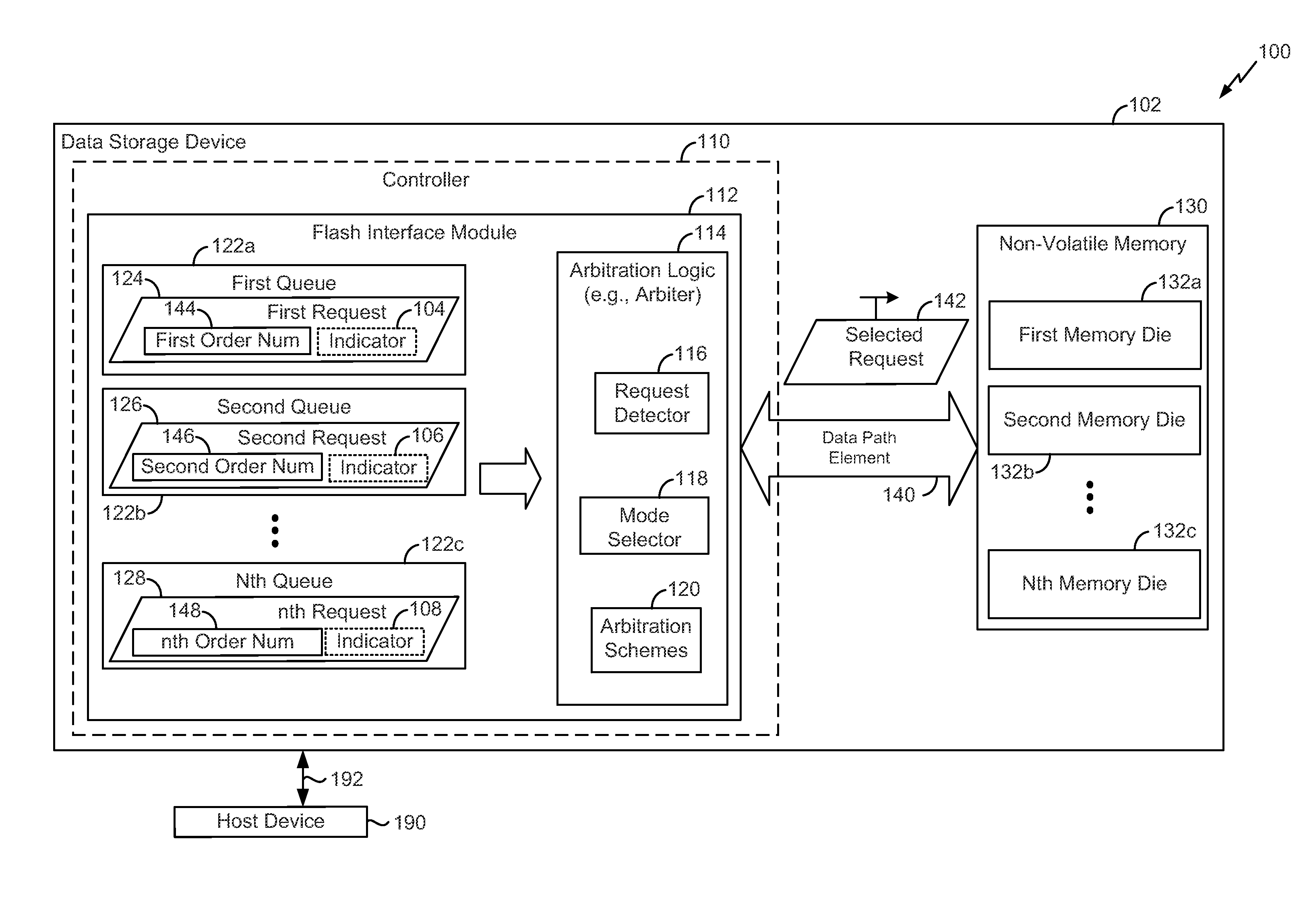
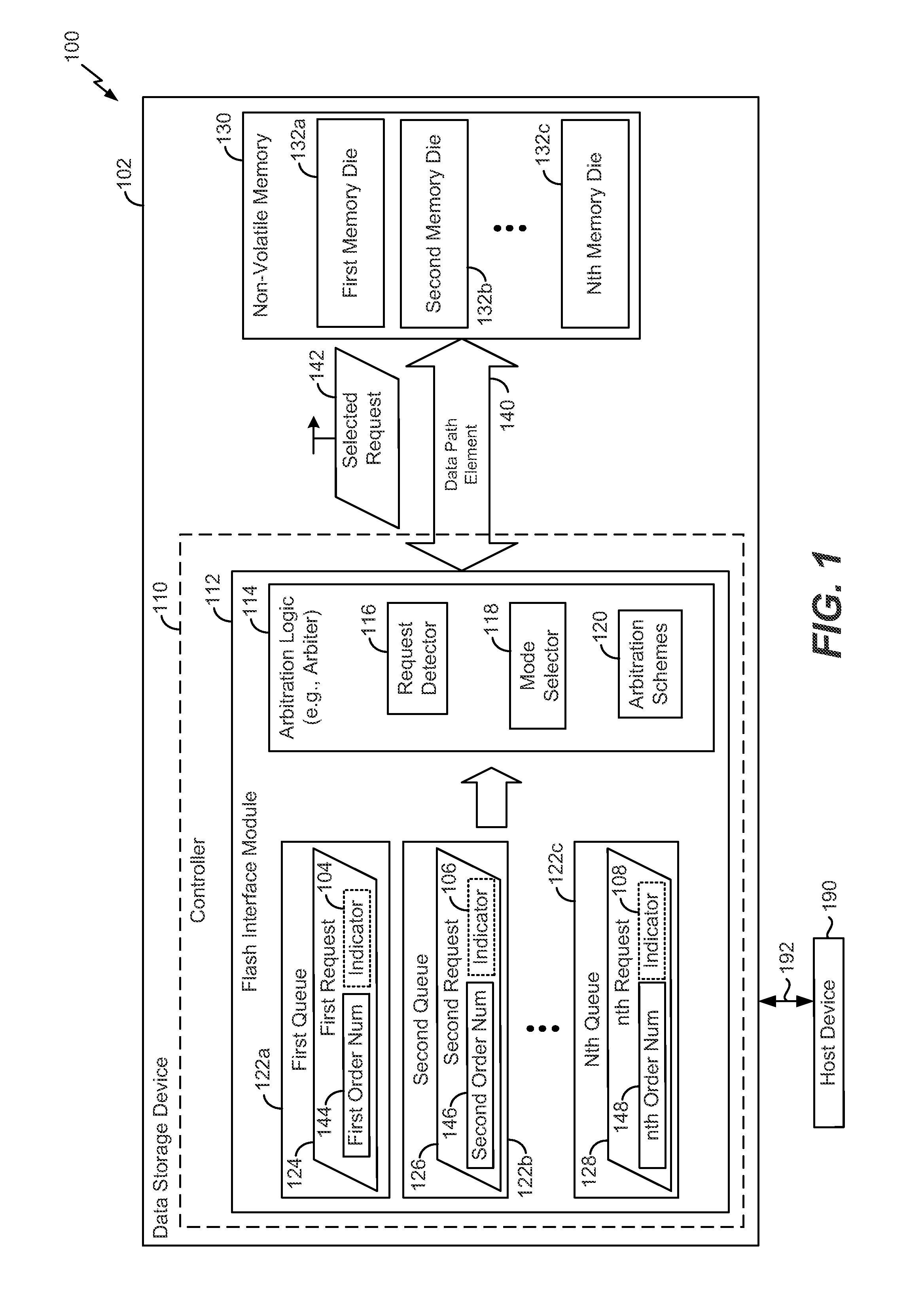
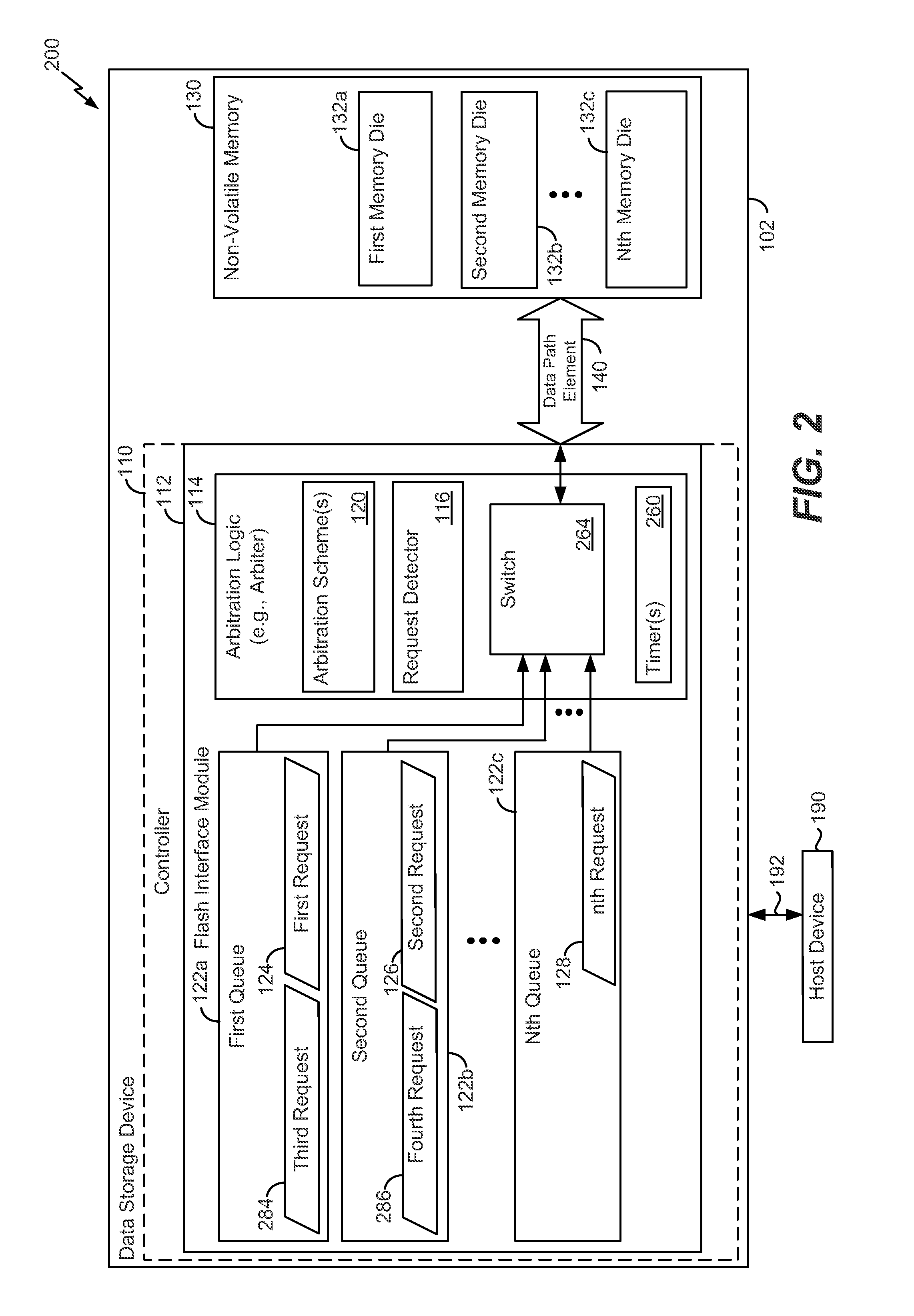
System and method of arbitration associated with a multi-threaded system
Owner:SANDISK TECH LLC
File encryption operation method and file encryption operation system
ActiveCN102819702AImprove efficiencyImprove securityComputer security arrangementsSecuring communicationComputer hardwarePassword
The invention discloses a file encryption operation method and a file encryption operation system. The method comprises the steps of: receiving a file operation instruction; transferring an encrypted target file according to the file operation instruction; carrying out memory decryption on the encrypted target file according to key information corresponding to the encrypted target file, and operating the encrypted target file after memory decryption. According to the scheme disclosed by the invention, the password of the encrypted target file does not need to be manually input; opening and operating of the file can be achieved by decrypting the file without a manual operation, and the operating efficiency of the key information is improved. On the other hand, the encrypted target file is decrypted by the key information in the memory; the decrypted file is stored in the memory, and a permanent file is not generated, therefore, the password is not stolen by the others, and the operating security of the encrypted file is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Determination of access checks in a mixed role based access control and discretionary access control environment
InactiveUS20080271139A1Digital data processing detailsUser identity/authority verificationDiscretionary access controlAuthorization
Owner:IBM CORP
Mesh communications network having mesh ports
A method for communicating over a mesh network established between a plurality of devices is disclosed. Each device has a wireless radio and the method involves launching a mesh service on each device, the mesh service being operable to cause a processor circuit of the device to provide functionality for controlling the wireless radio for communication between devices over the mesh network. Each device has at least one application running on the device, the at least one application being associated with a mesh port, the mesh port being used to designate data transmissions as being associated with instances of a specific application running on at least some of the devices in the plurality of devices, the at least one application and the mesh service on each device being in data communication. The method also involves, in response to a specific application running on a device requesting the mesh service to provide access to the mesh network for communication via a specific mesh port, causing the mesh service to determine whether the specific application is authorized for communications on the specific mesh port, and if the specific application is authorized, processing requests from the application to communicate on the specific mesh port over the mesh network and forwarding data transmissions associated with the specific mesh port to the specific application, and if the specific application is not authorized, declining requests from the application to communicate on the specific mesh port over the mesh network and preventing access by the specific application to data transmissions associated with the specific mesh port.
Owner:LEFT OF THE DOT MEDIA
Access permission control method, access permission control device and access permission control system
ActiveCN102750493AIncrease flexibilityGuaranteed uptimeComputer security arrangementsUser PrivilegeApplication programming interface
Owner:HUAWEI DEVICE CO LTD
Method for controlling production quantity of set-top boxes
InactiveCN101944195APrevent copyingCopyright protectionComputer security arrangementsResourcesStopped workCPUID
In order to solve the technical problem that a conventional set-top box is easy to crack and copy, the invention provides a method for controlling the production quantity of set-top boxes. The method comprises the following steps of: encrypting CPUid and a set-top box sequence number by adopting a DES algorithm; storing encrypted data into a server; and verifying whether pairing information is correct when the set-top box is turned on every time, if not correct, the set-top box stops working so as to limit the production quantity of the set-top boxes. The method has the advantages that: simple implementation, low cost and not easy cracking; and the quantity of the set-top boxes can be controlled by binding the CPUid and the set-top sequence number so as to prevent the software of the set-top box from being copied and protect the copyright of the software of the set-top box.
Owner:KONKA GROUP
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap