Strong authentication token usable with a plurality of independent application providers
a technology of strong authentication and application providers, applied in the field of electronic transaction security, can solve the problems that passwords or signatures can in general not convey all the information contained in cryptograms to the authentication server, and achieve the effect of reducing their costs and high costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
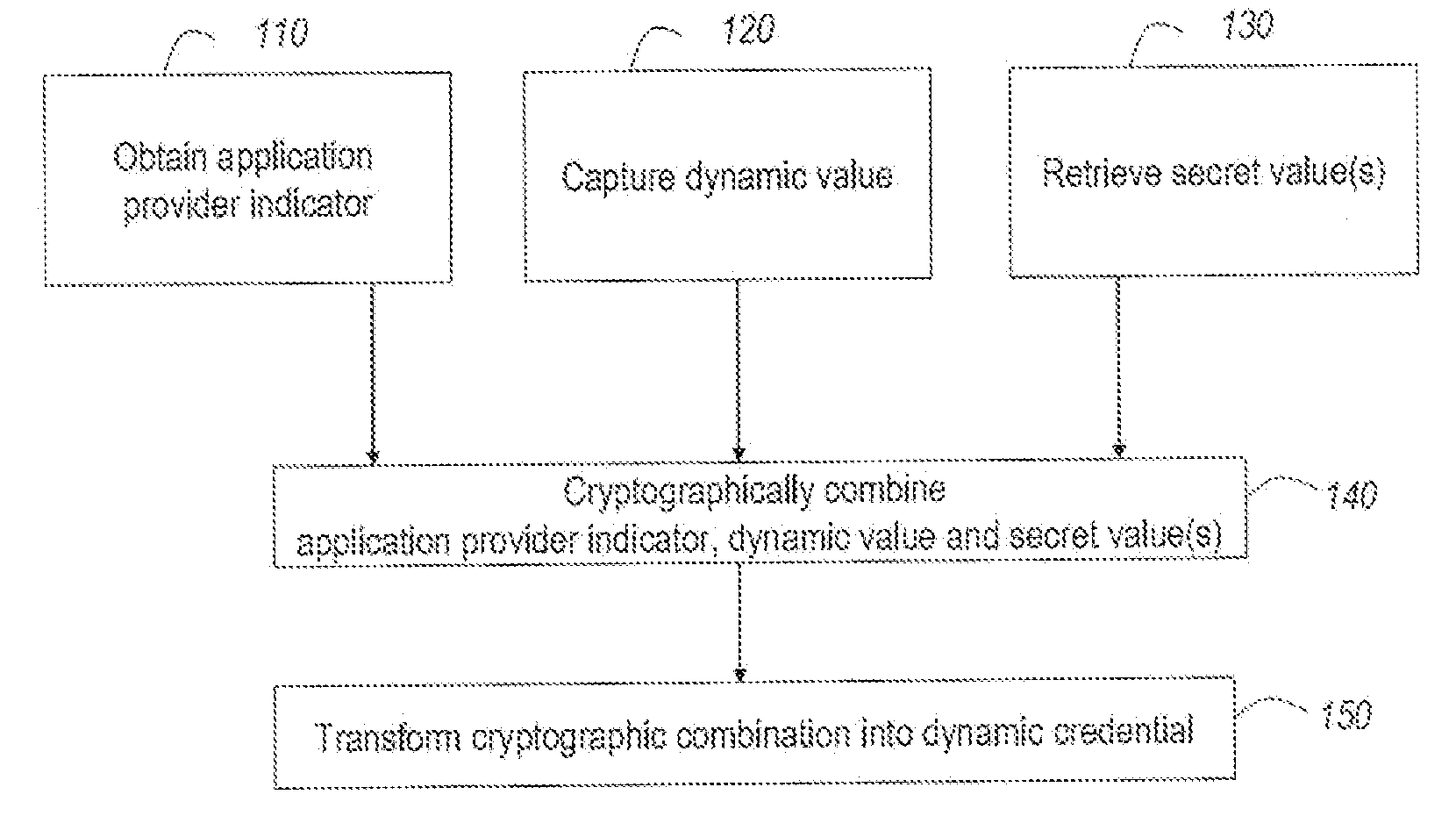
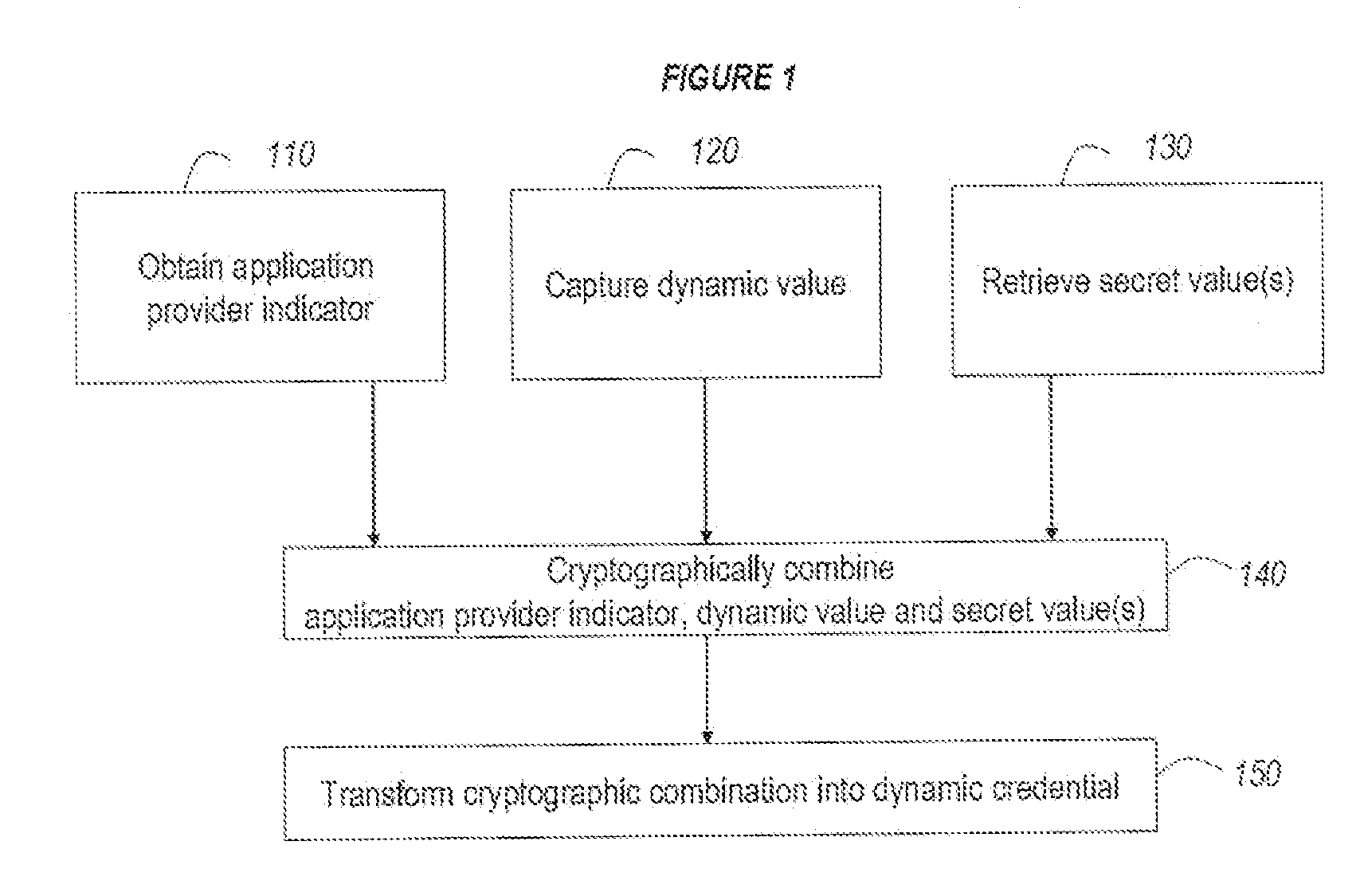
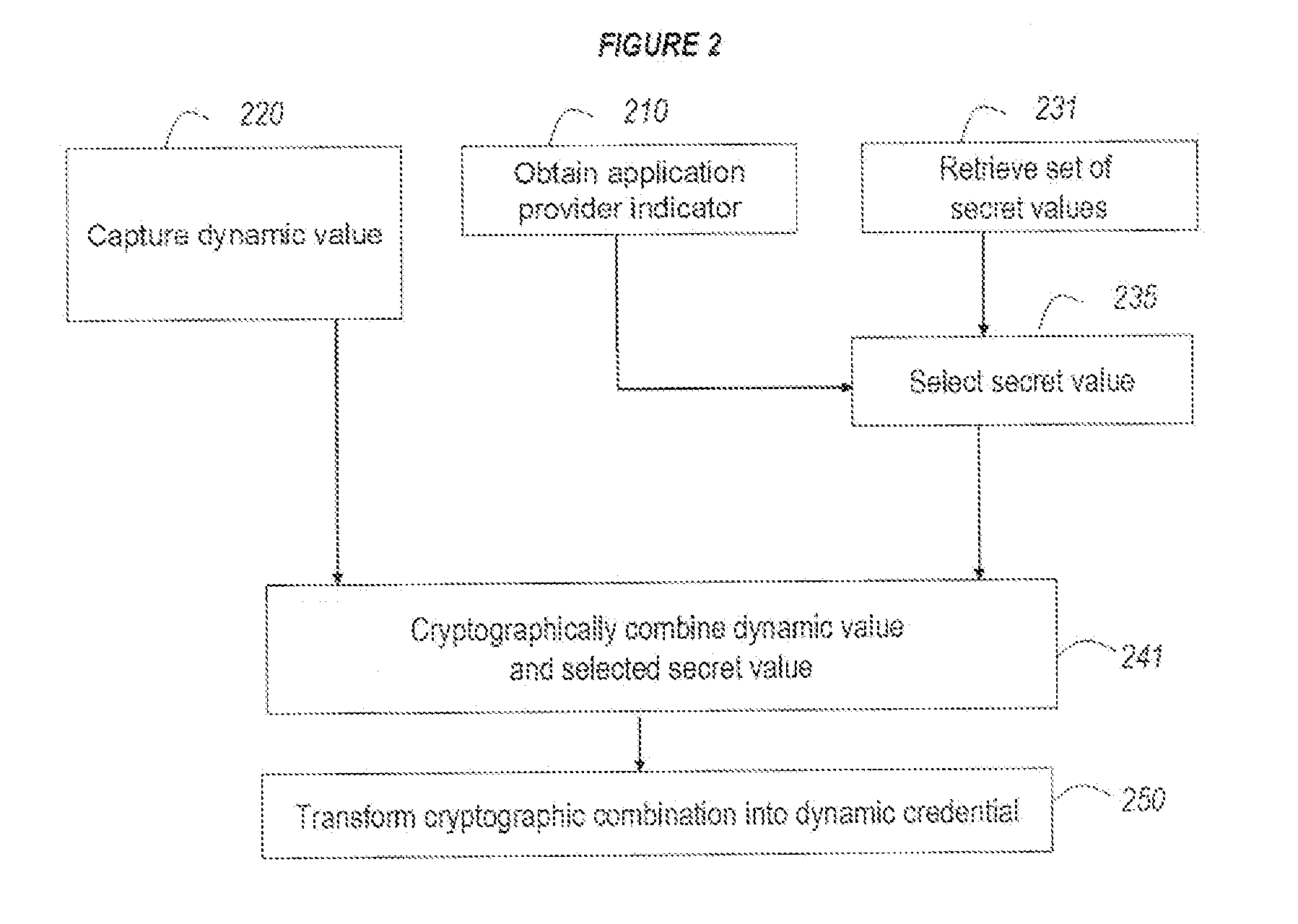
[0049]FIG. 1 illustrates a preferred method according to the invention to generate a dynamic credential for a specific application provider or application provider group comprising the steps of:[0050]obtaining an indicator of the application provider or application provider group (step 110);[0051]capturing the value of at least one dynamic variable (step 120);[0052]retrieving one or more secret values (step 130);[0053]cryptographically combining said application provider indicator, said dynamic value and said one or more secret values (step 140) using a symmetric cryptographic algorithm; and[0054]transforming the result of said cryptographic combination into a dynamic credential (step 150) which in a typical case is different from the result of the cryptographic combination.
[0055]In one embodiment the dynamic variable may comprise a time related value. In a specific embodiment the dynamic variable comprises the value of a real-time clock. In another embodiment the dynamic variable comp
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap