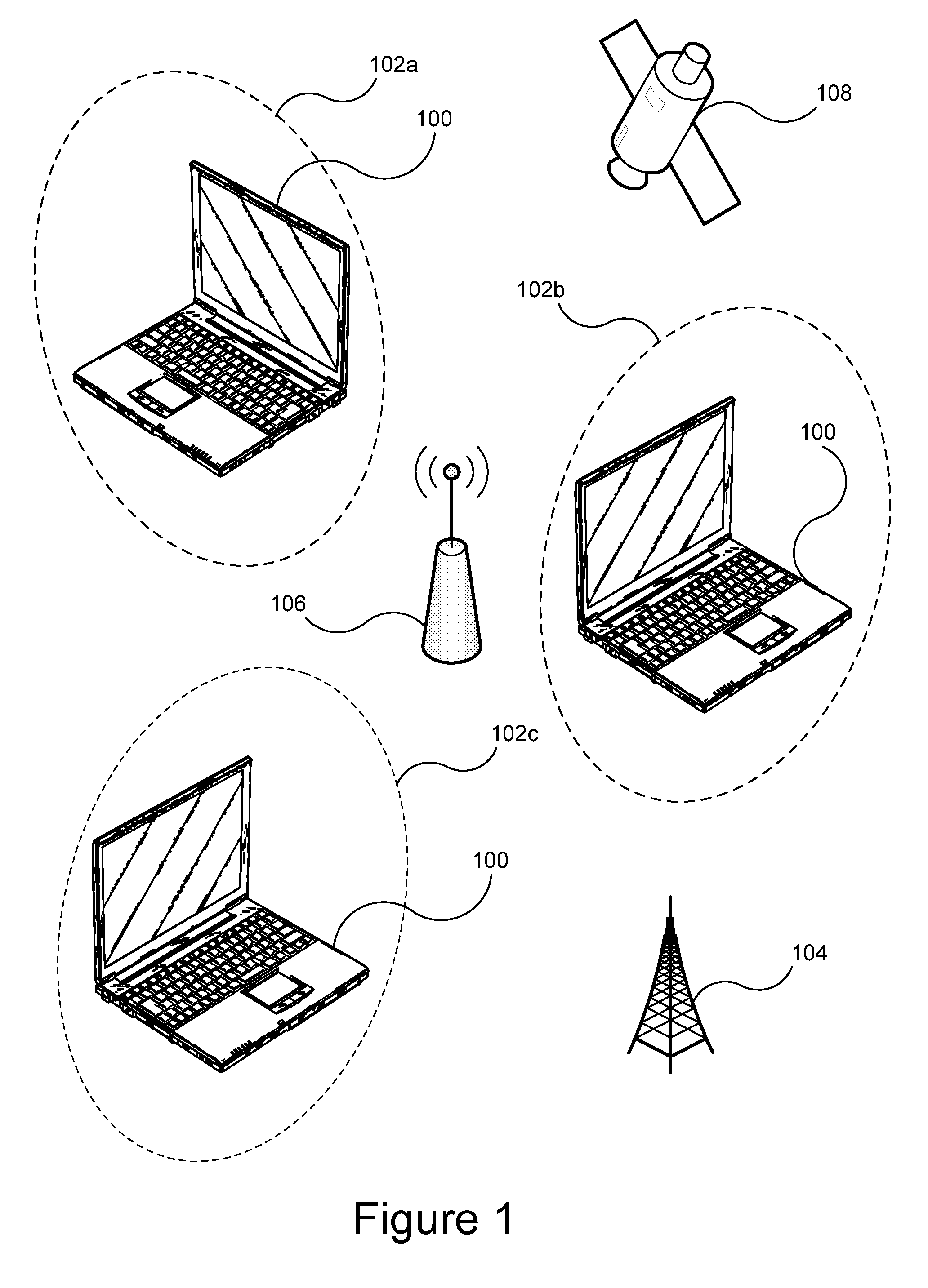
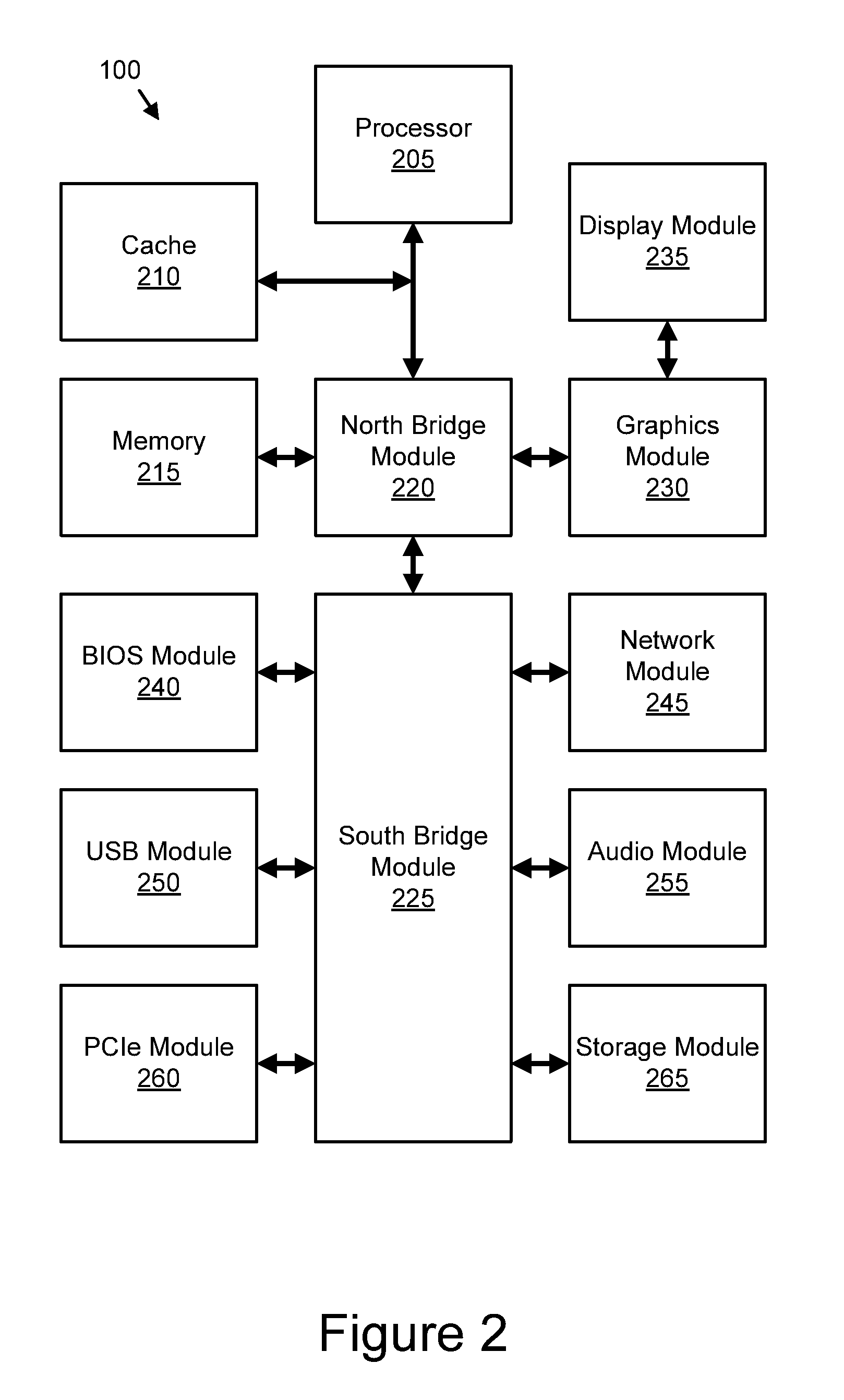
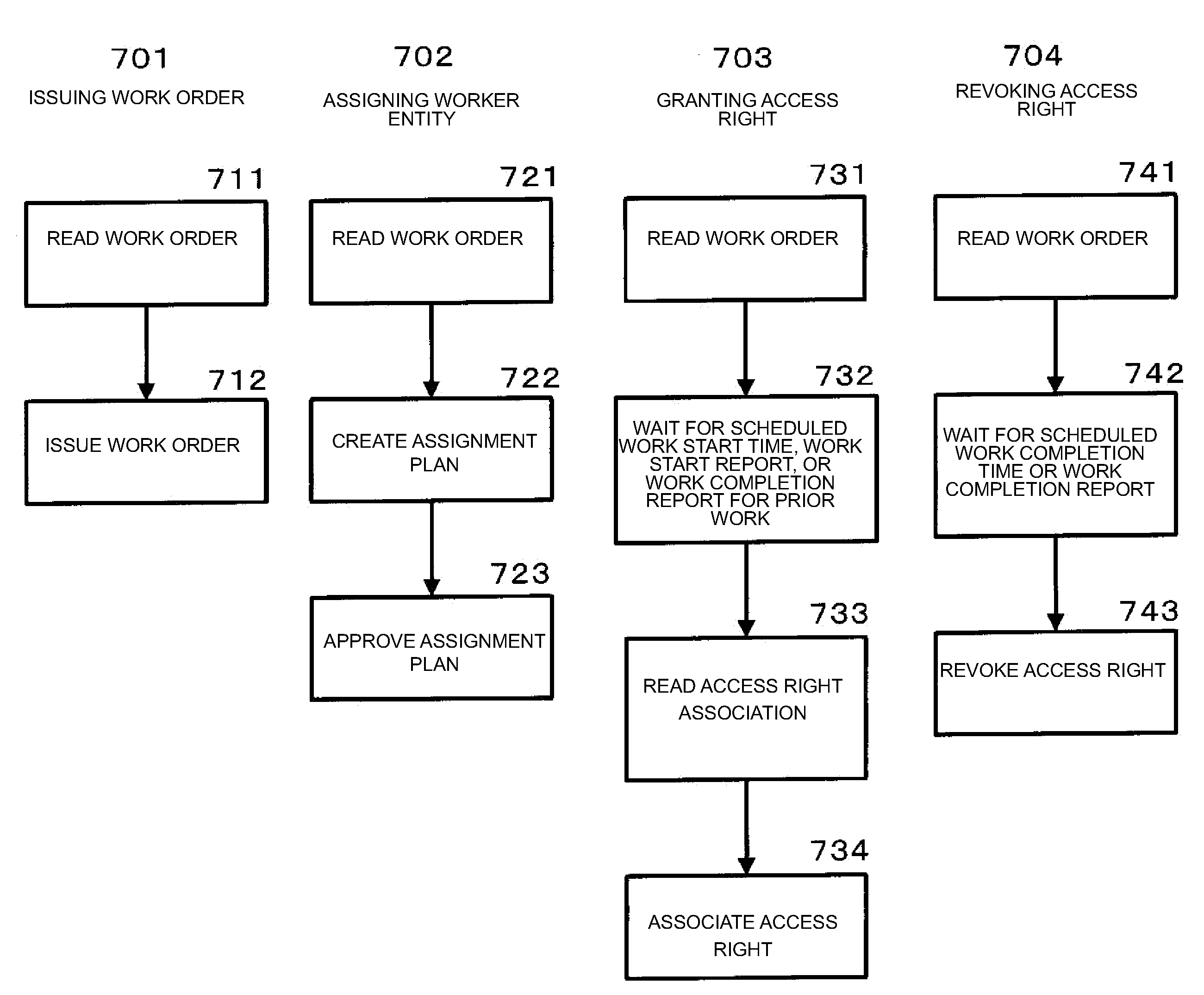
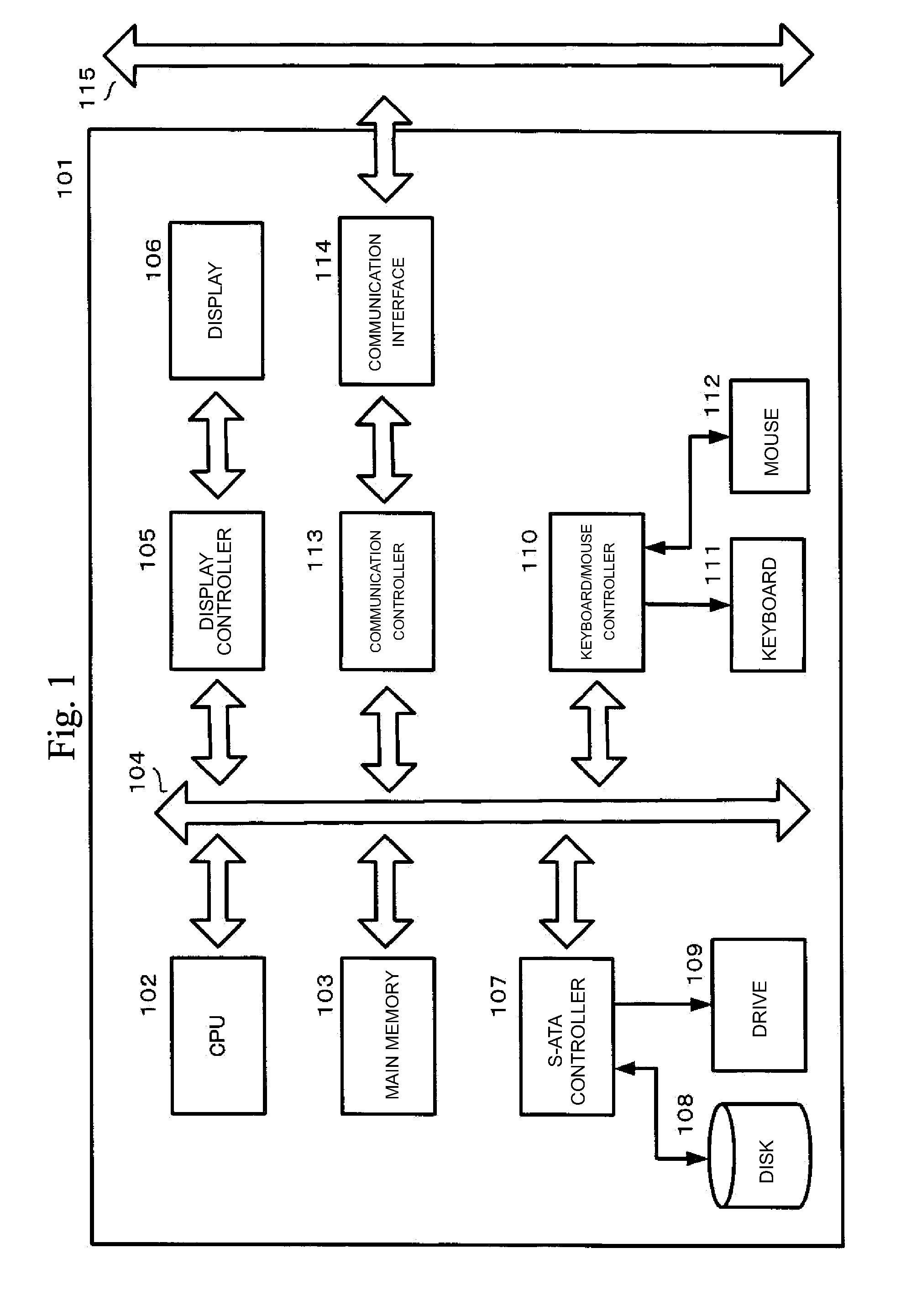
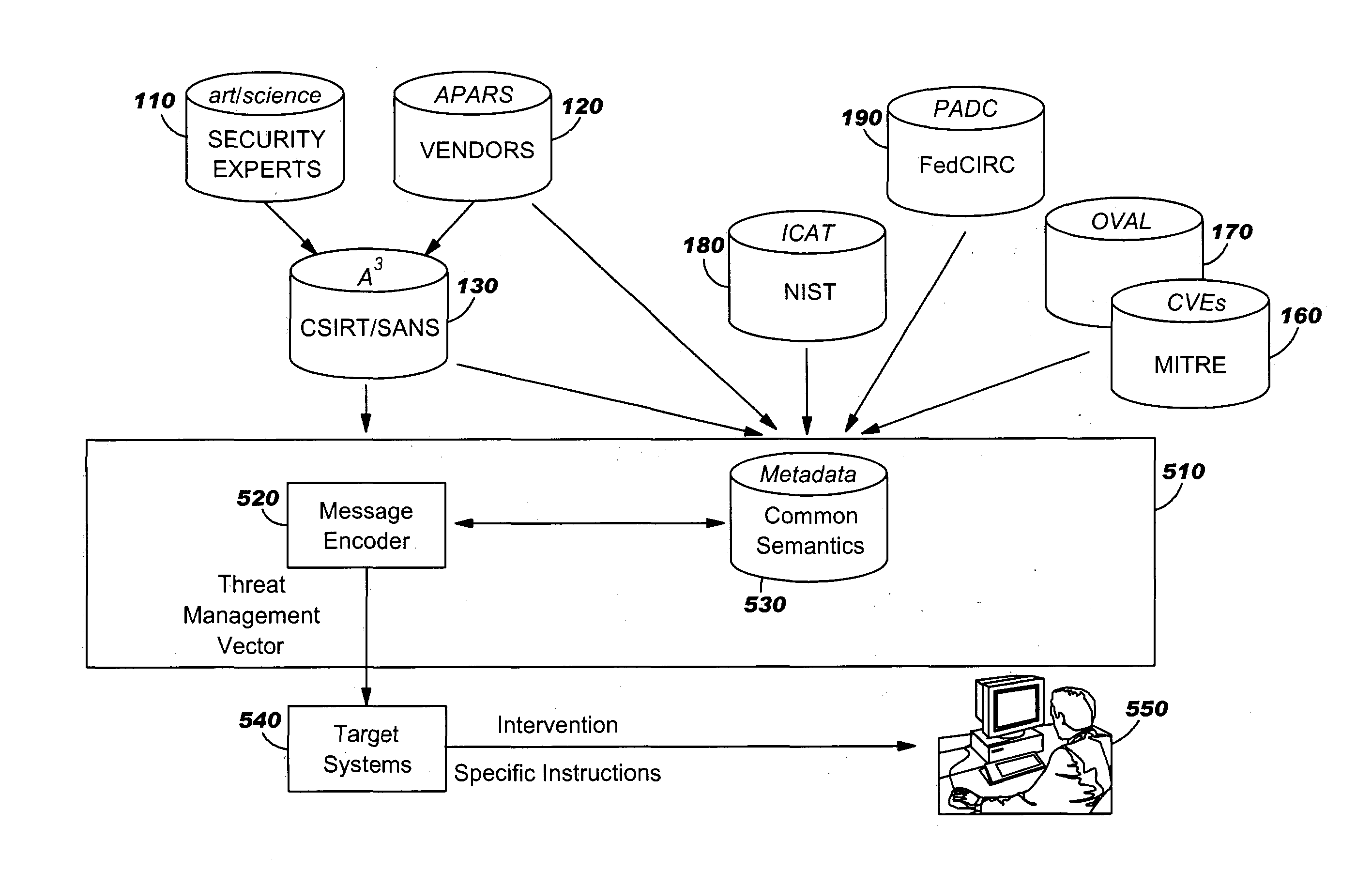
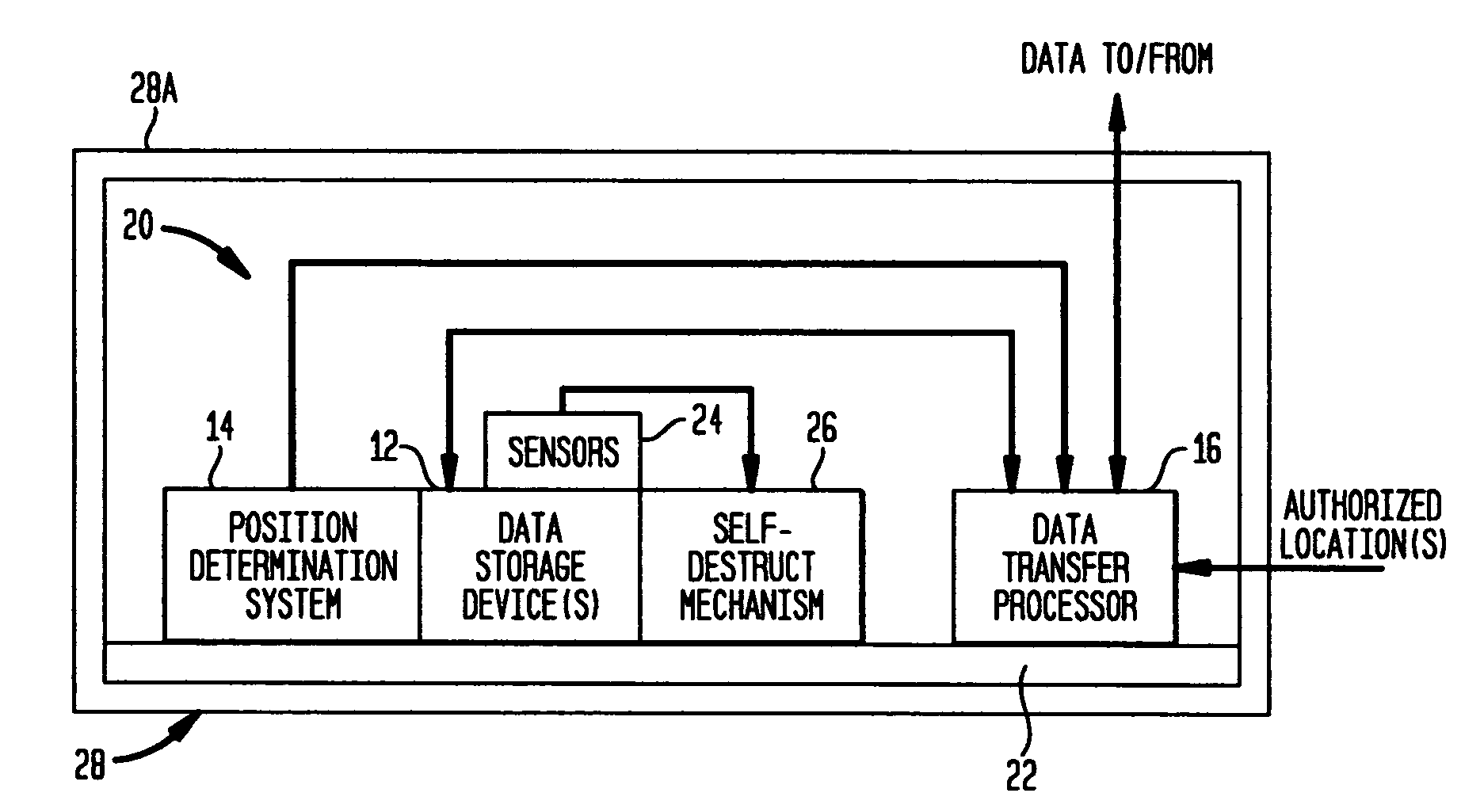
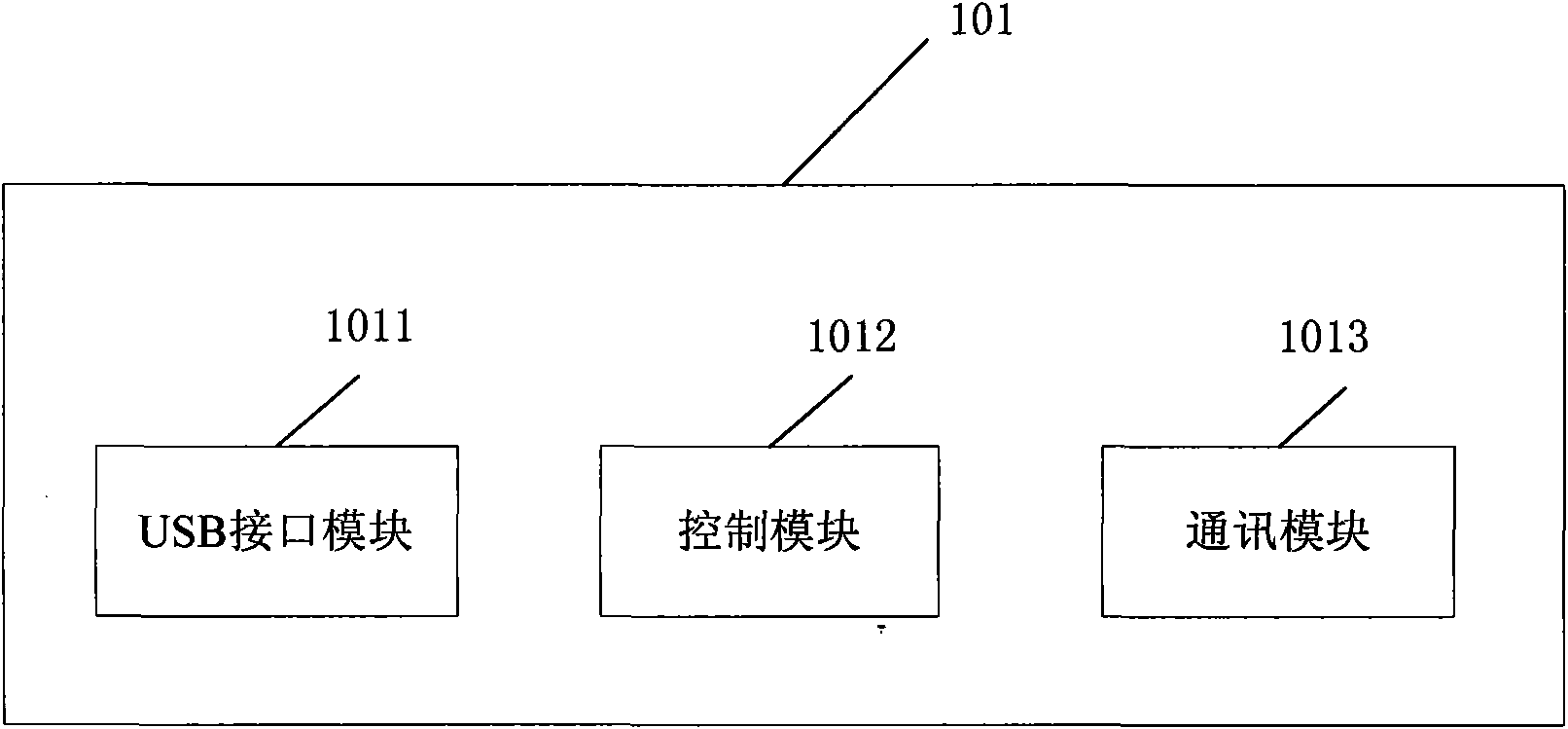
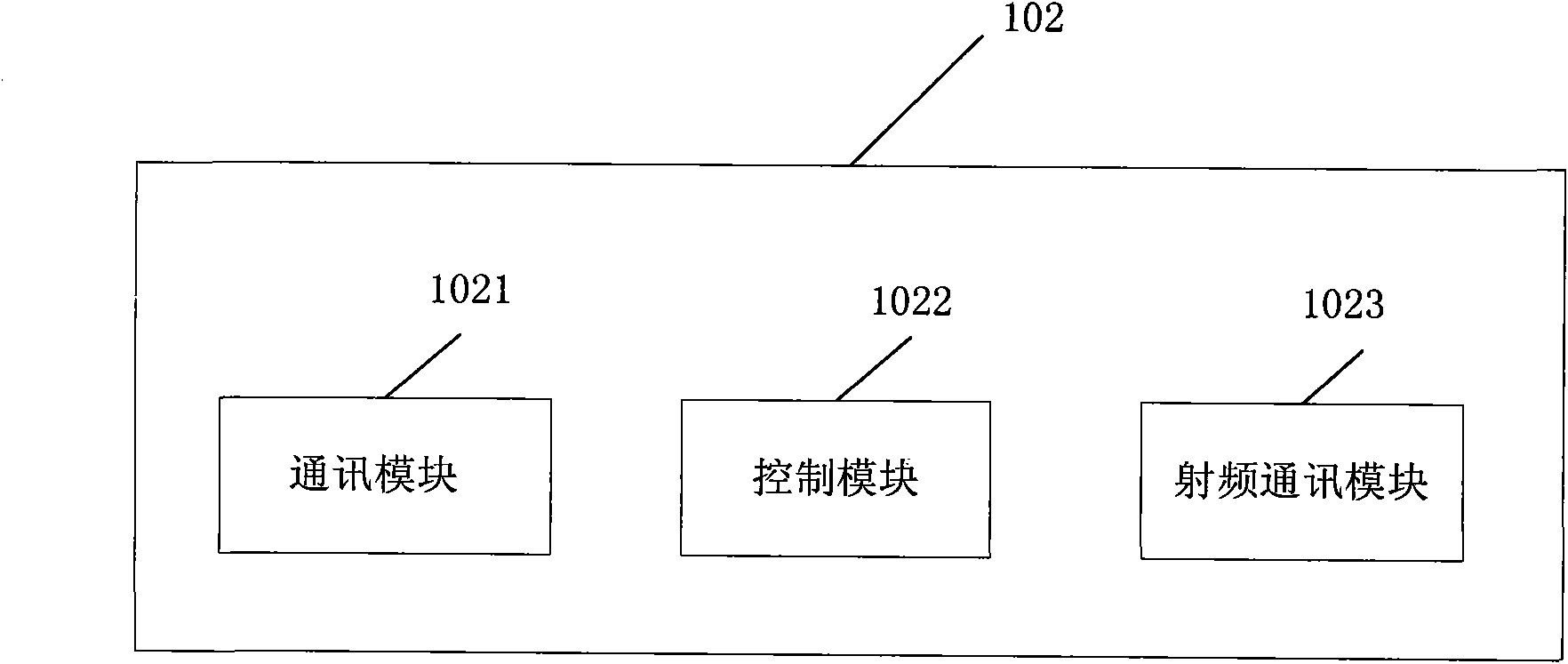
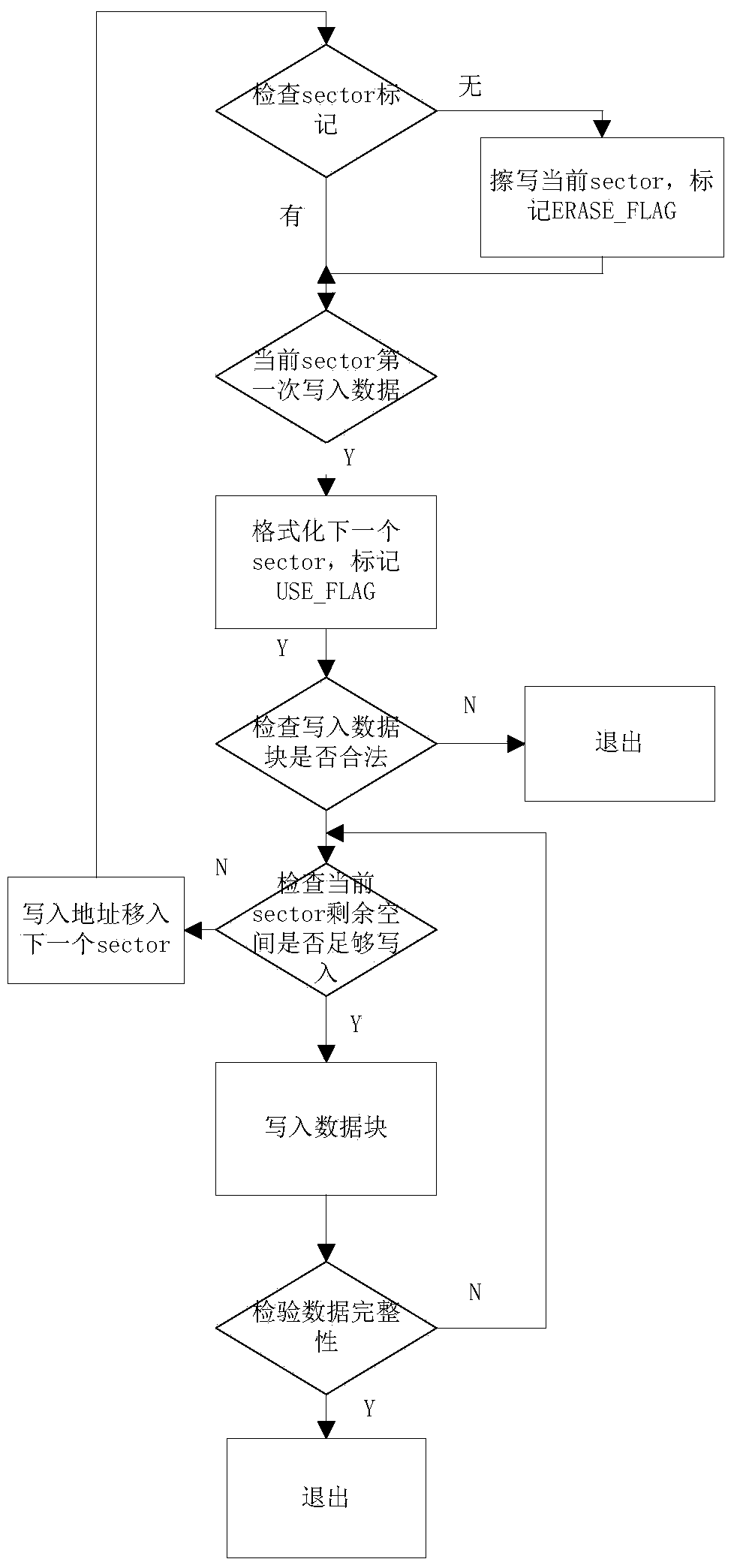
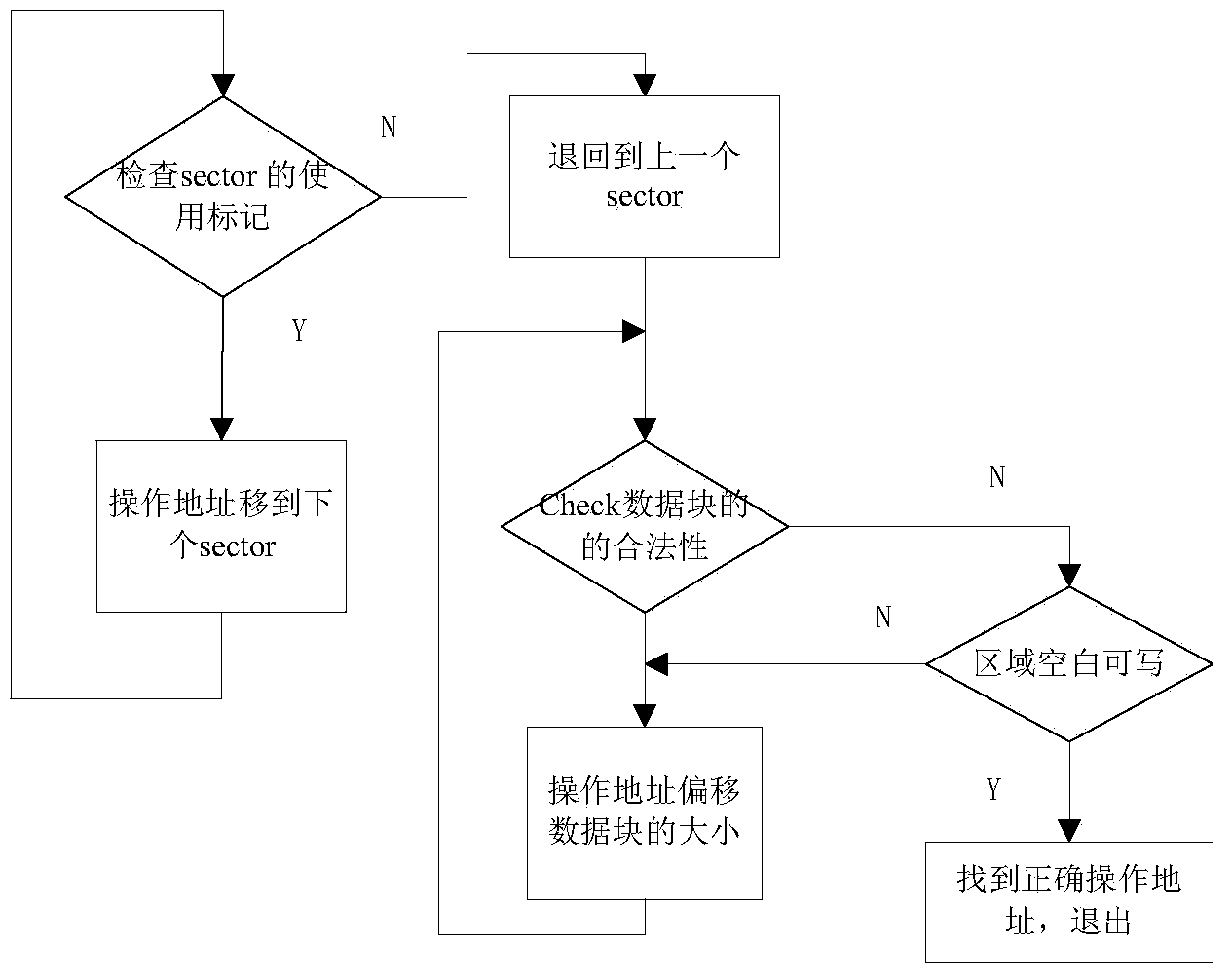
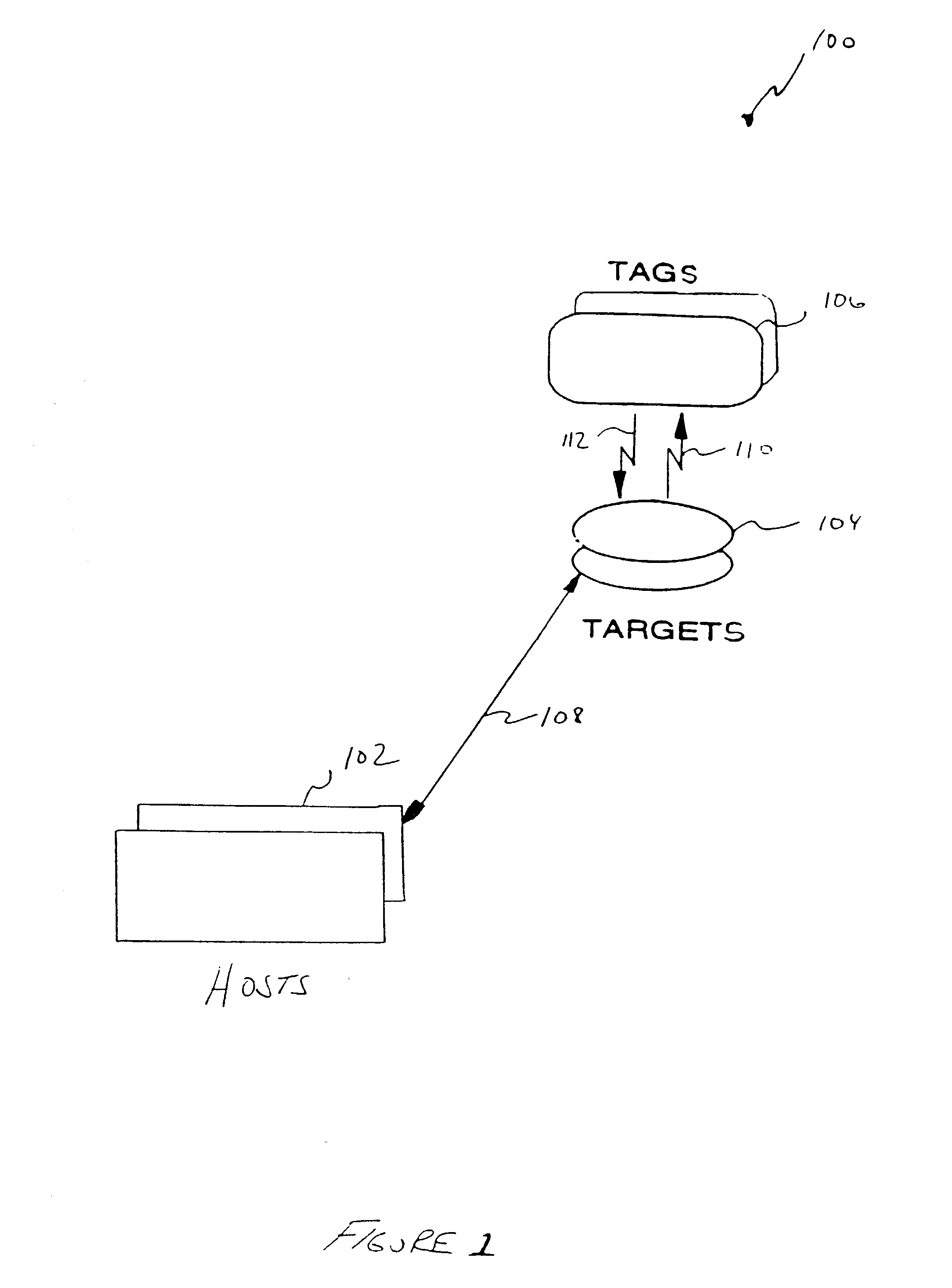
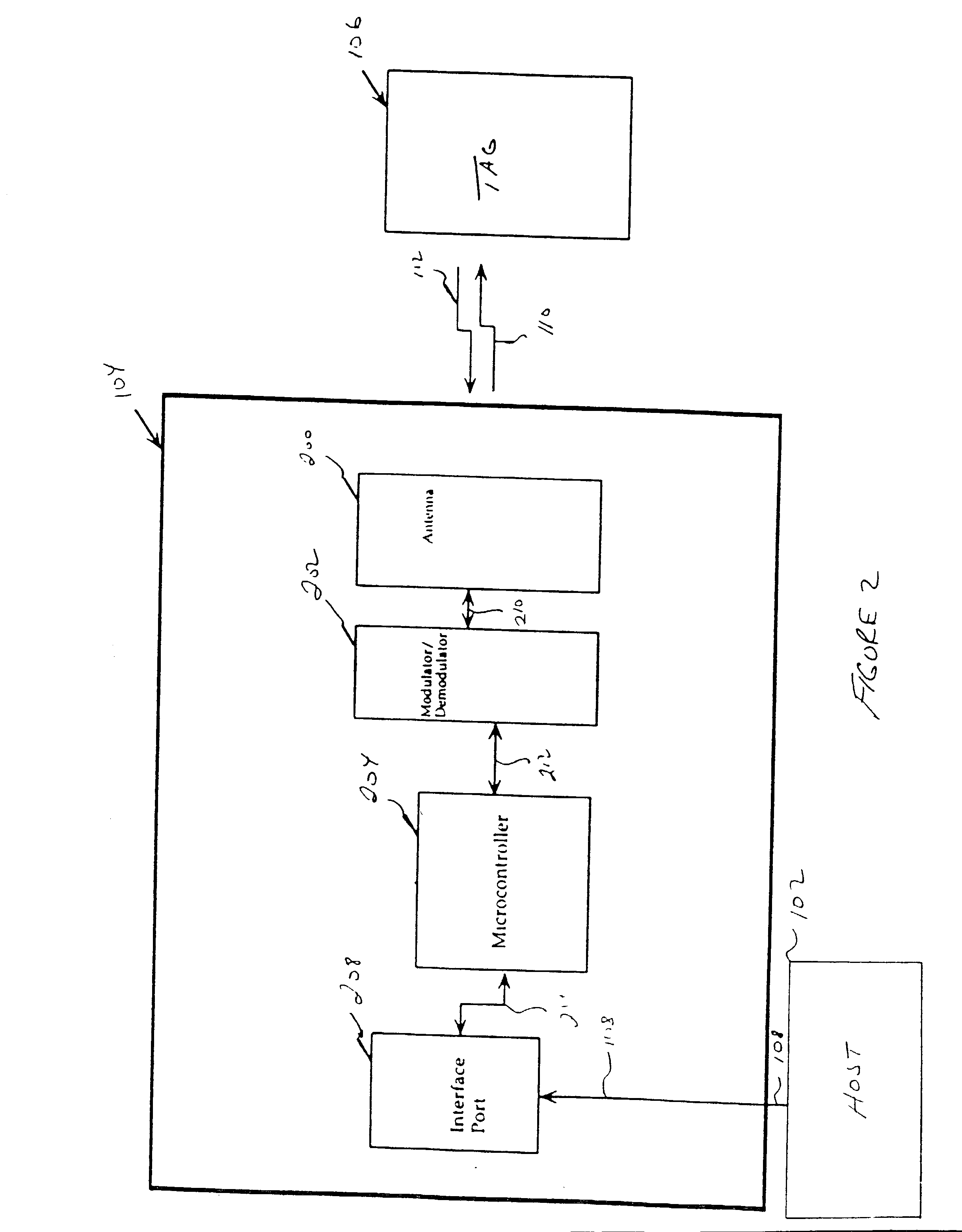
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
44results about "Unauthorized memory use protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Methods for combating malicious software
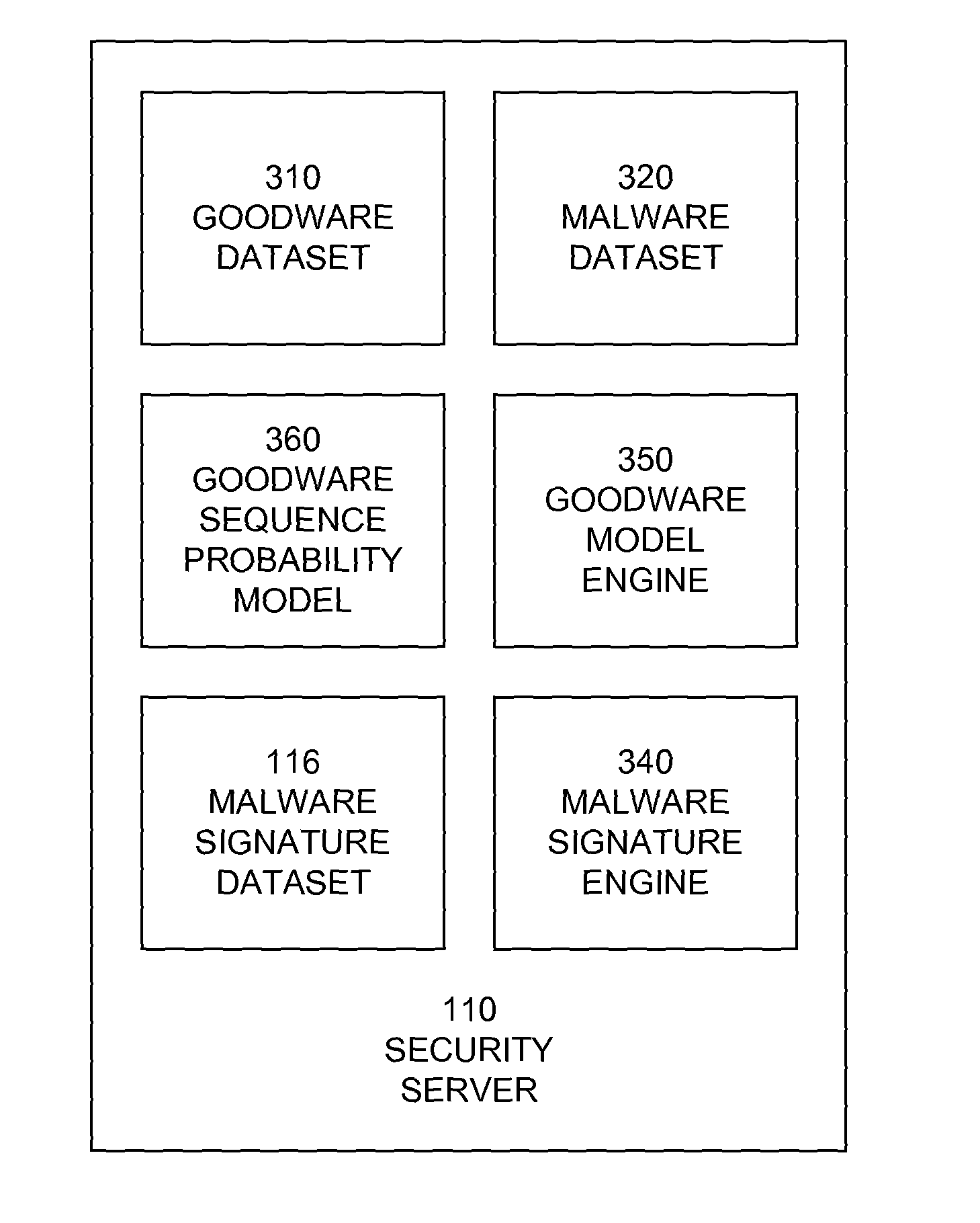
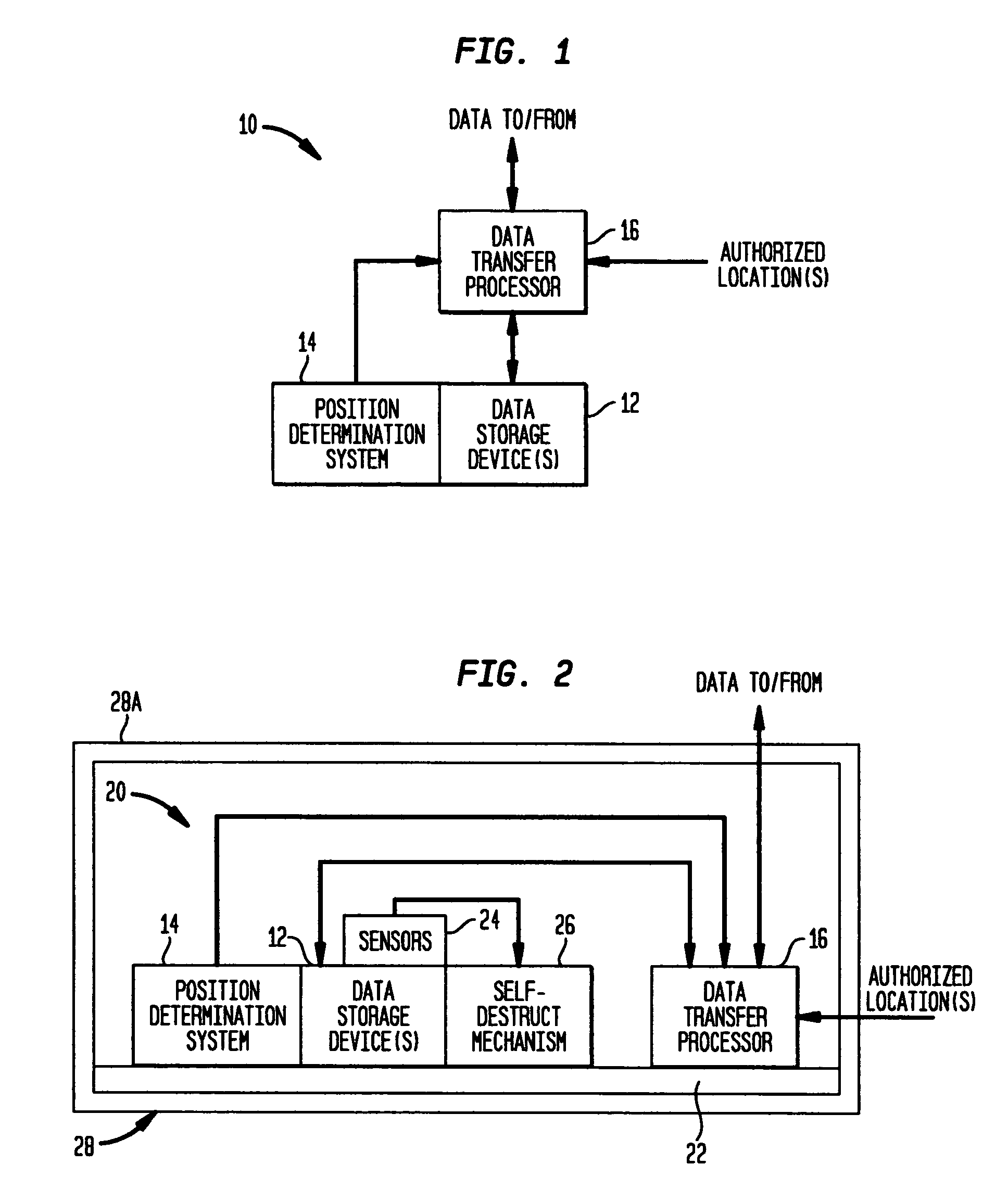
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
Method and apparatus for data retention in a storage system
ActiveUS20050125411A1Digital data information retrievalMemory loss protectionRetention periodSoftware engineering
A system and method are provided for retention of data on a storage system. An application program provides the storage system with data to be stored on the storage system. The application program also provides the storage system with a retention period that indicates a period of time for which the data may not be deleted. When the storage system receives a request to delete the data, it first evaluates the retention period associated with that data to determine if the retention period has expired. If the retention period has not expired, the storage system denies the request to delete the data.
Owner:EMC IP HLDG CO LLC
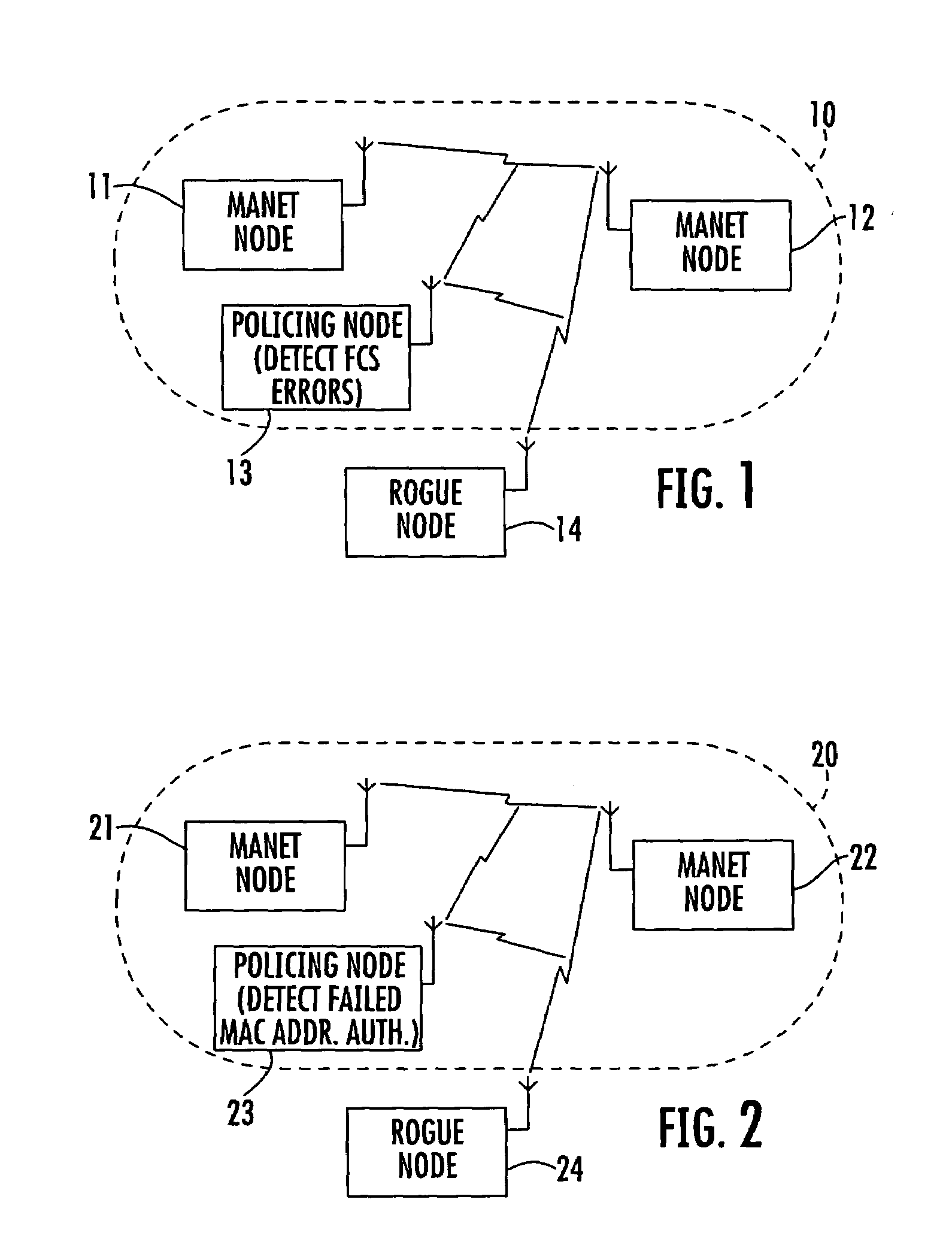
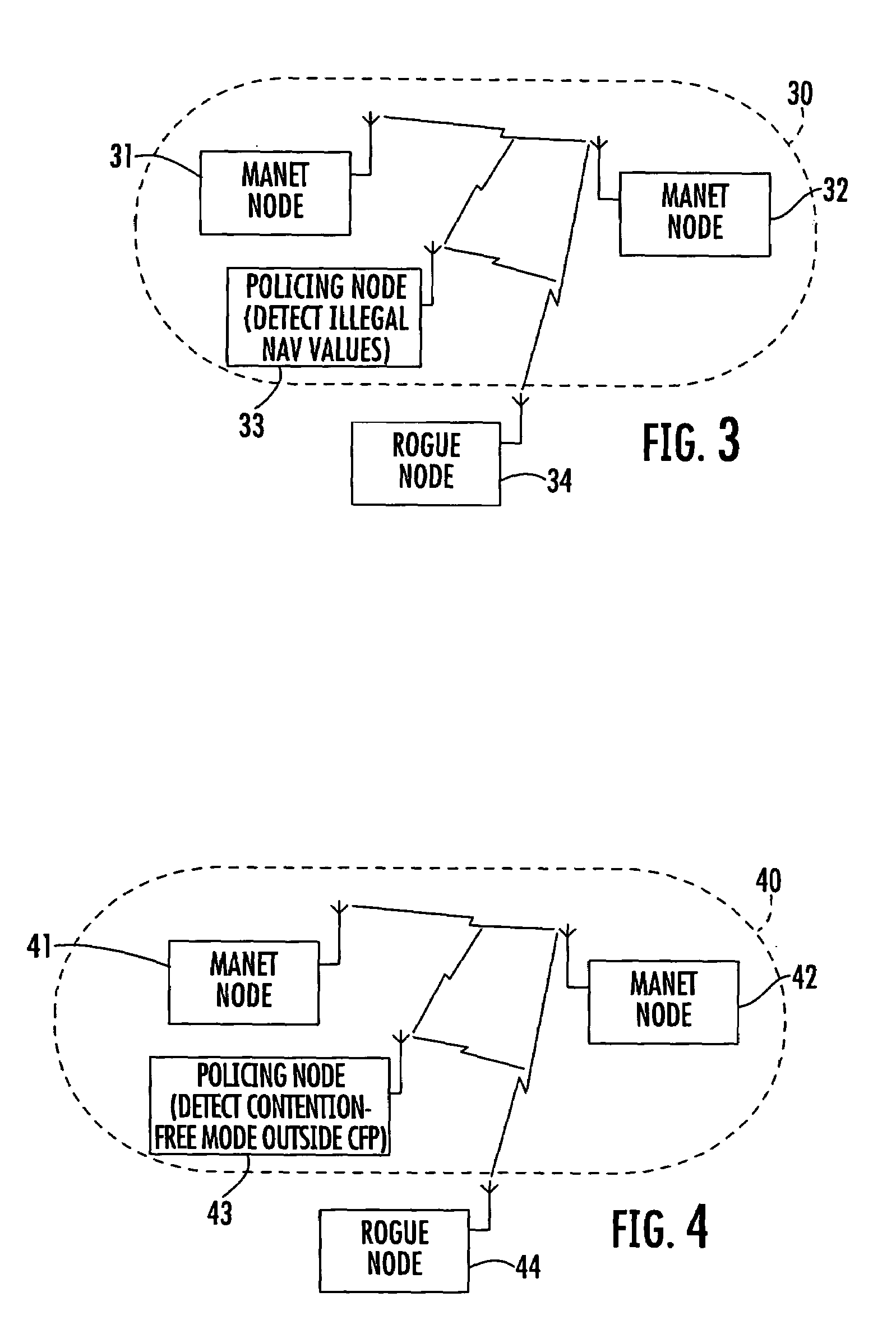
Mobile ad-hoc network with intrusion detection features and related methods
Owner:STINGRAY IP SOLUTIONS LLC
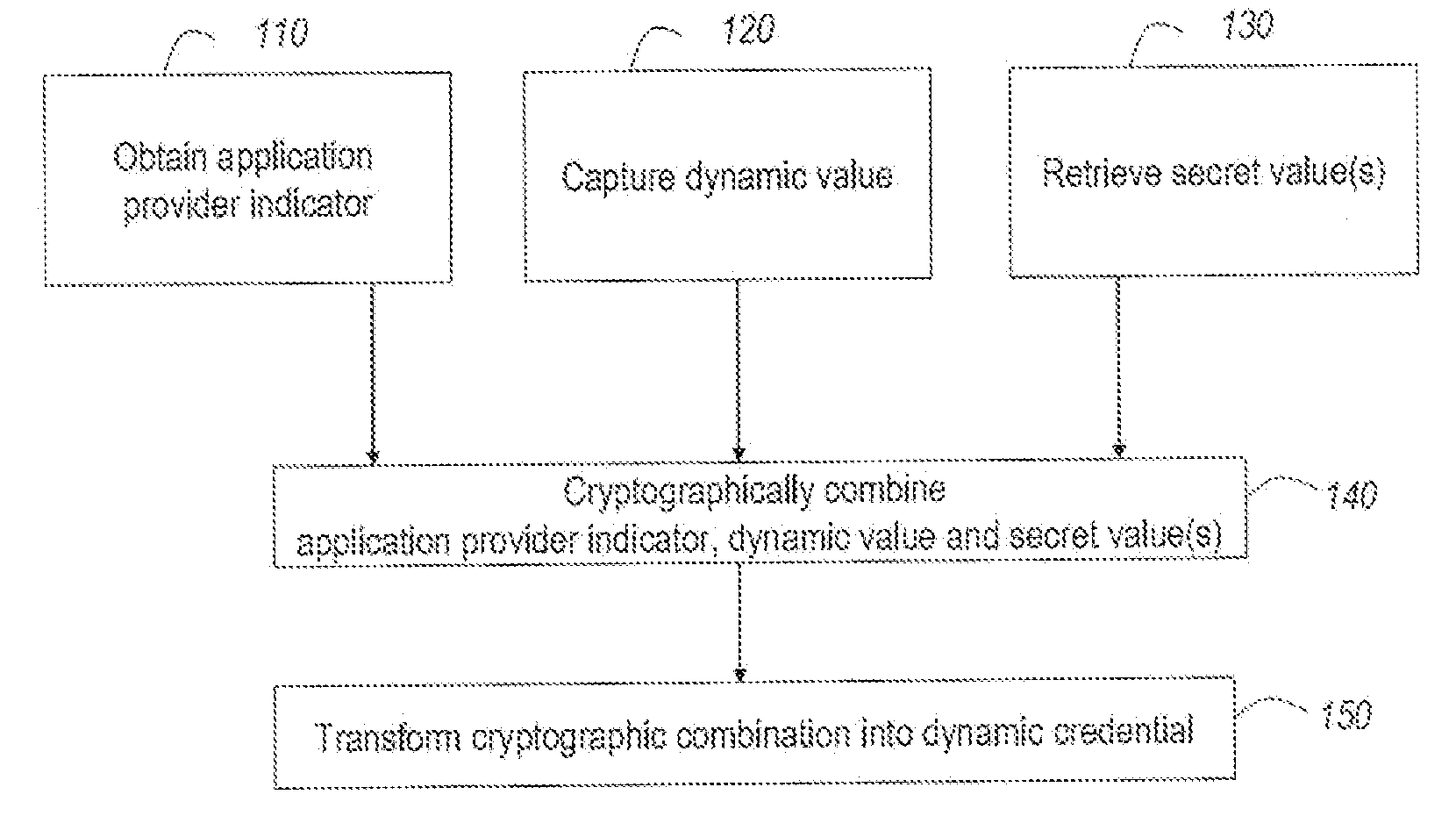
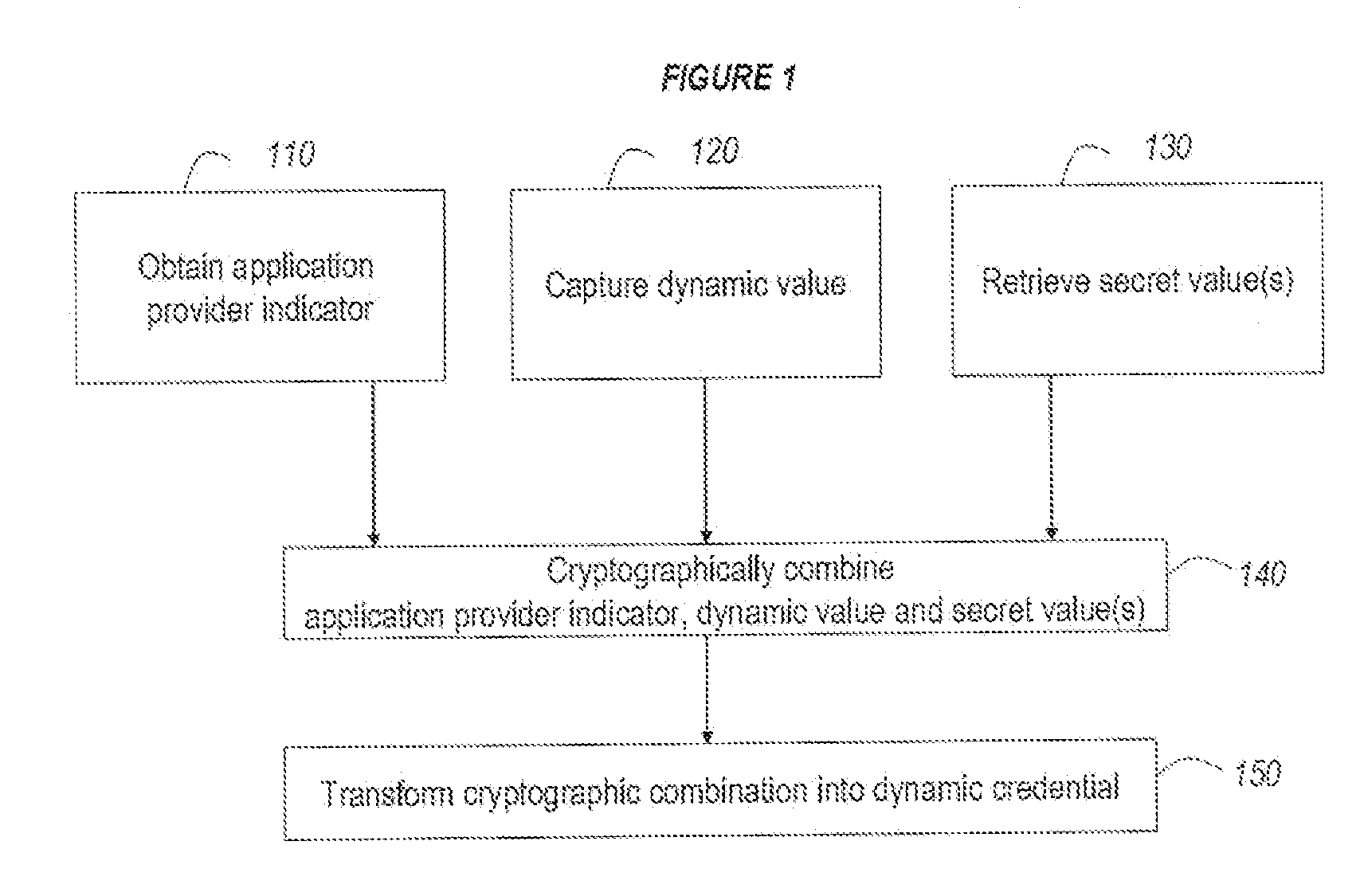
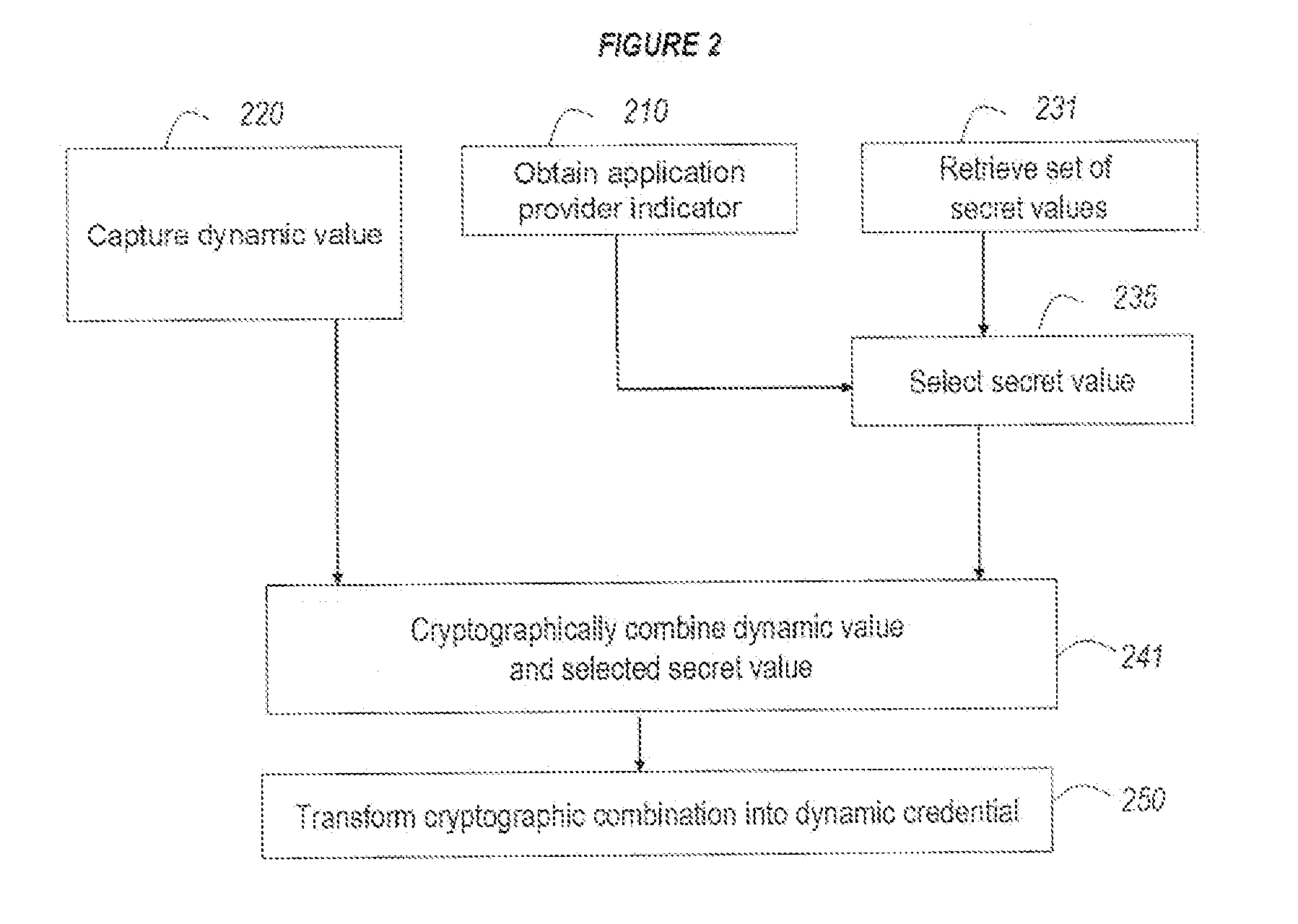
Strong authentication token usable with a plurality of independent application providers
ActiveUS20110099384A1Low costCost can be dividedMultiple keys/algorithms usageDigital data processing detailsPersonalizationUnique identifier
Owner:ONESPAN NORTH AMERICA INC
Virtual address pager and method for use with a bulk erase memory
ActiveUS20120239871A1Memory adressing/allocation/relocationUnauthorized memory use protectionVirtual memoryOperational system
A virtual address pager and method for use with a bulk erase memory is disclosed. The virtual address pager includes a page protection controller configured with a heap manager interface configured to receive only bulk erase memory-backed page requests for a plurality of memory pages. A RAM object cache controller is configured to store and bulk write data for a portion of the bulk erase memory. The page protection controller may have an operating system interface configured to generate a page memory access permission for each of the plurality of memory pages. The page protection controller may be configured to receive a virtual memory allocation request and generate the page memory access permission based on the virtual memory allocation request.
Owner:THE TRUSTEES OF PRINCETON UNIV
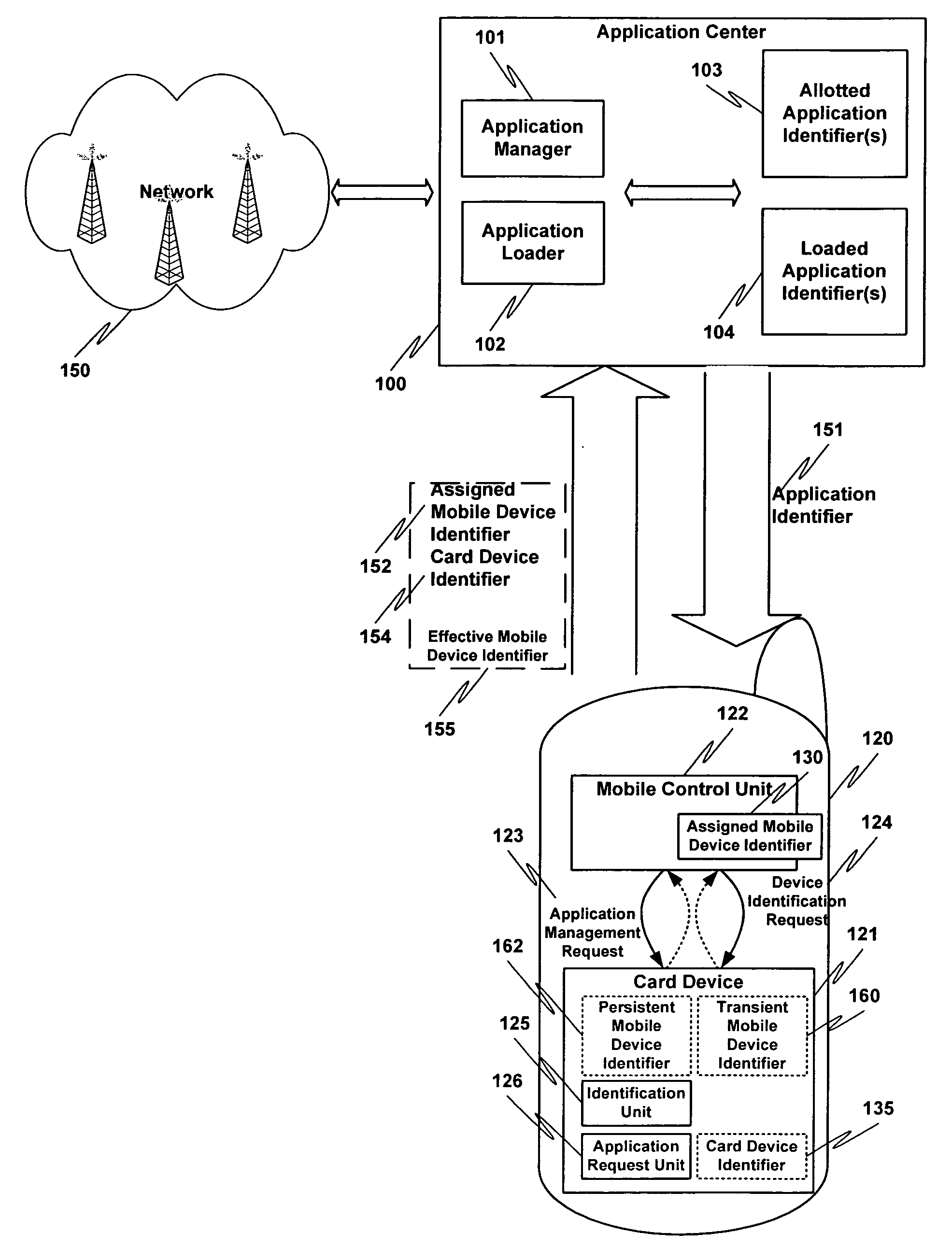
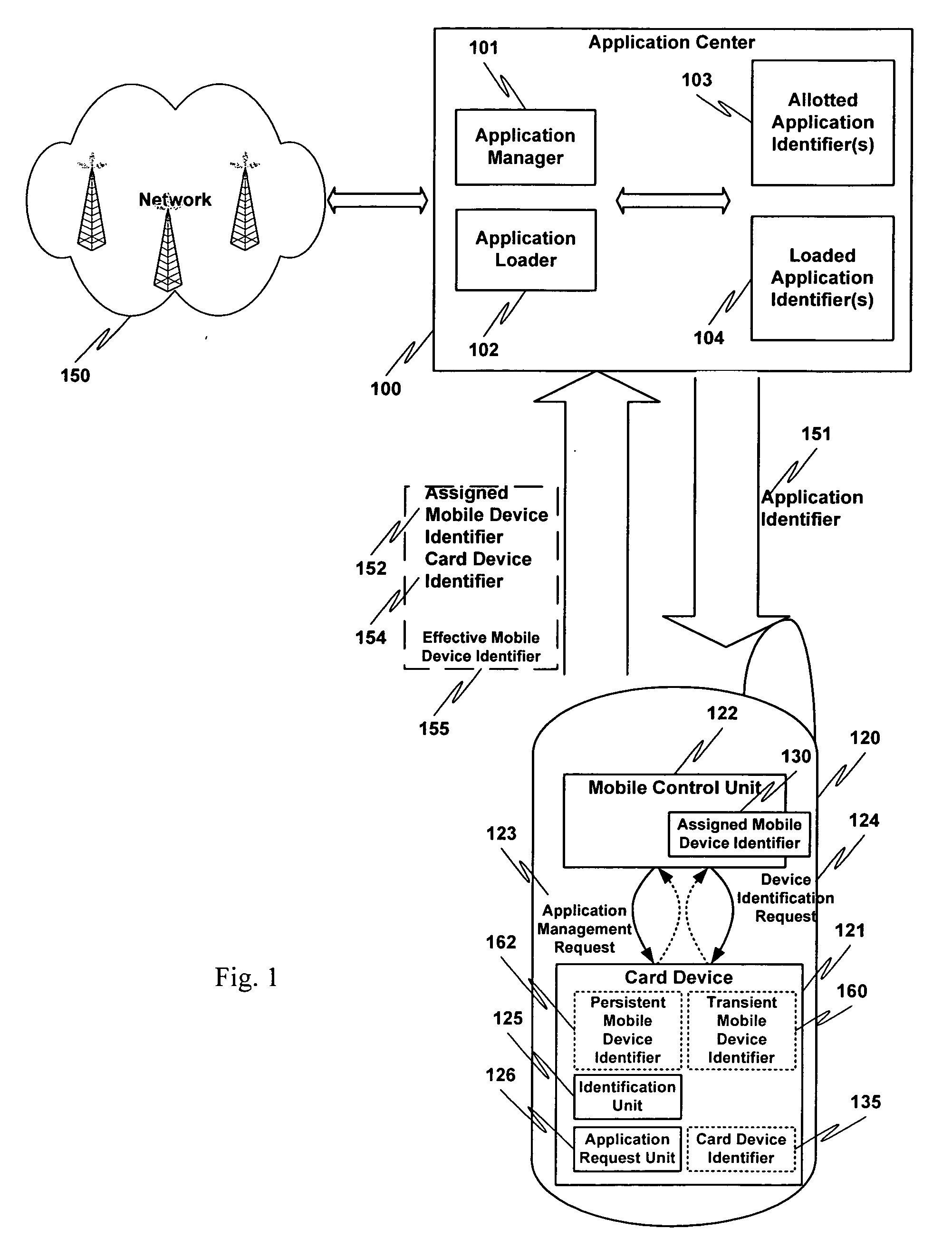
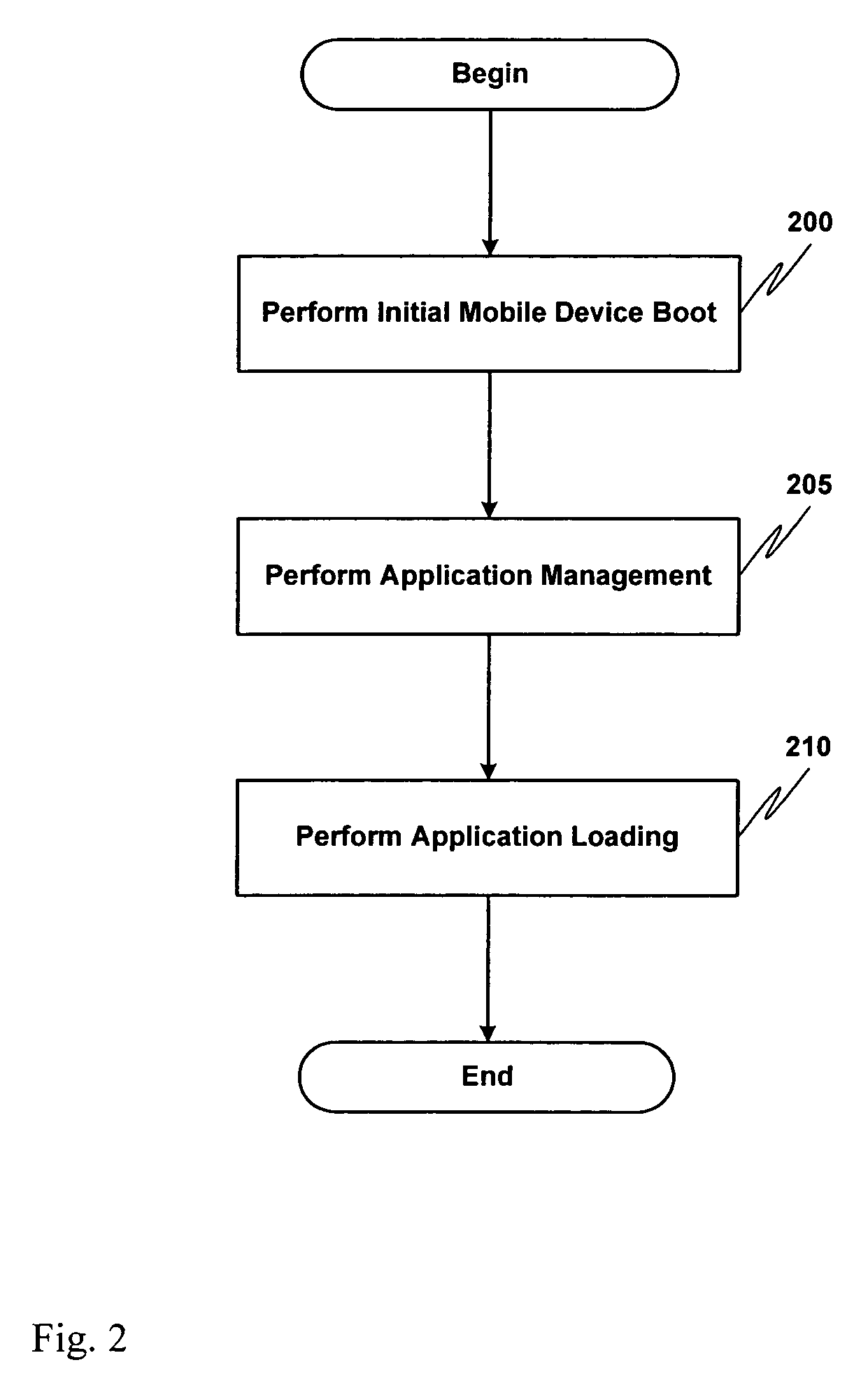
Card device for loading applications to a mobile device
ActiveUS20060212537A1Special service for subscribersUnauthorized memory use protectionEmbedded systemApplication Identifier
Owner:ORACLE INT CORP
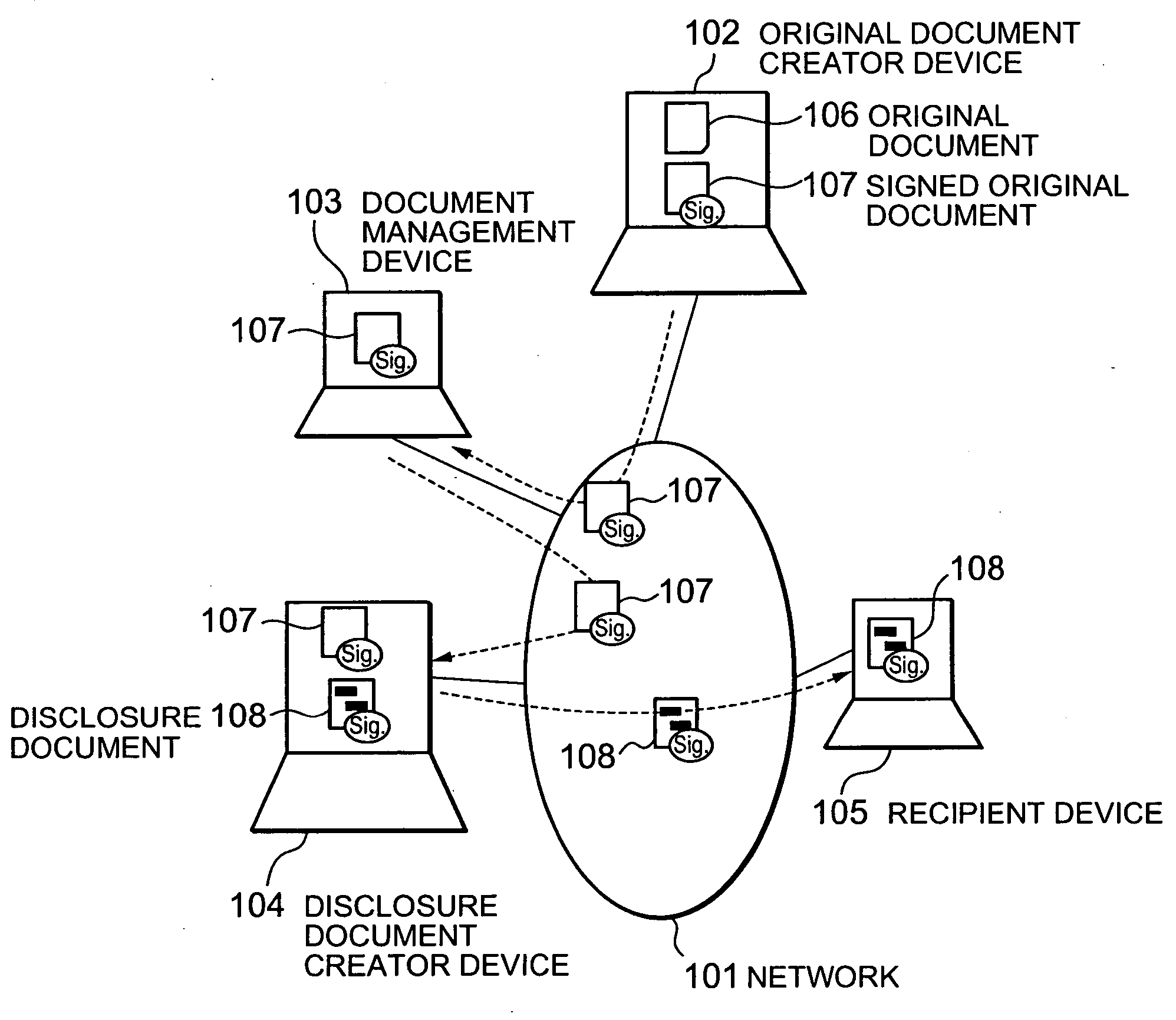
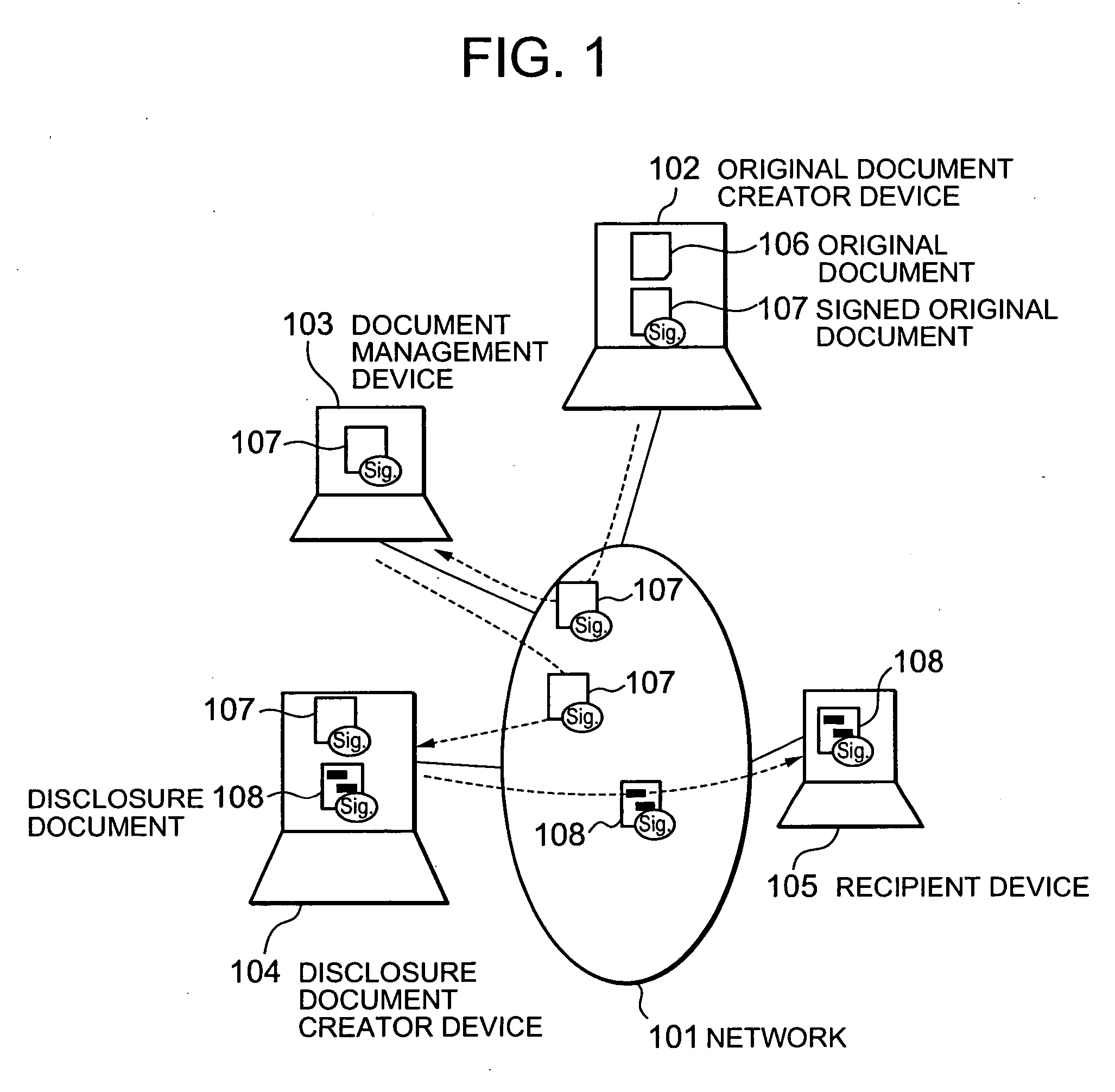
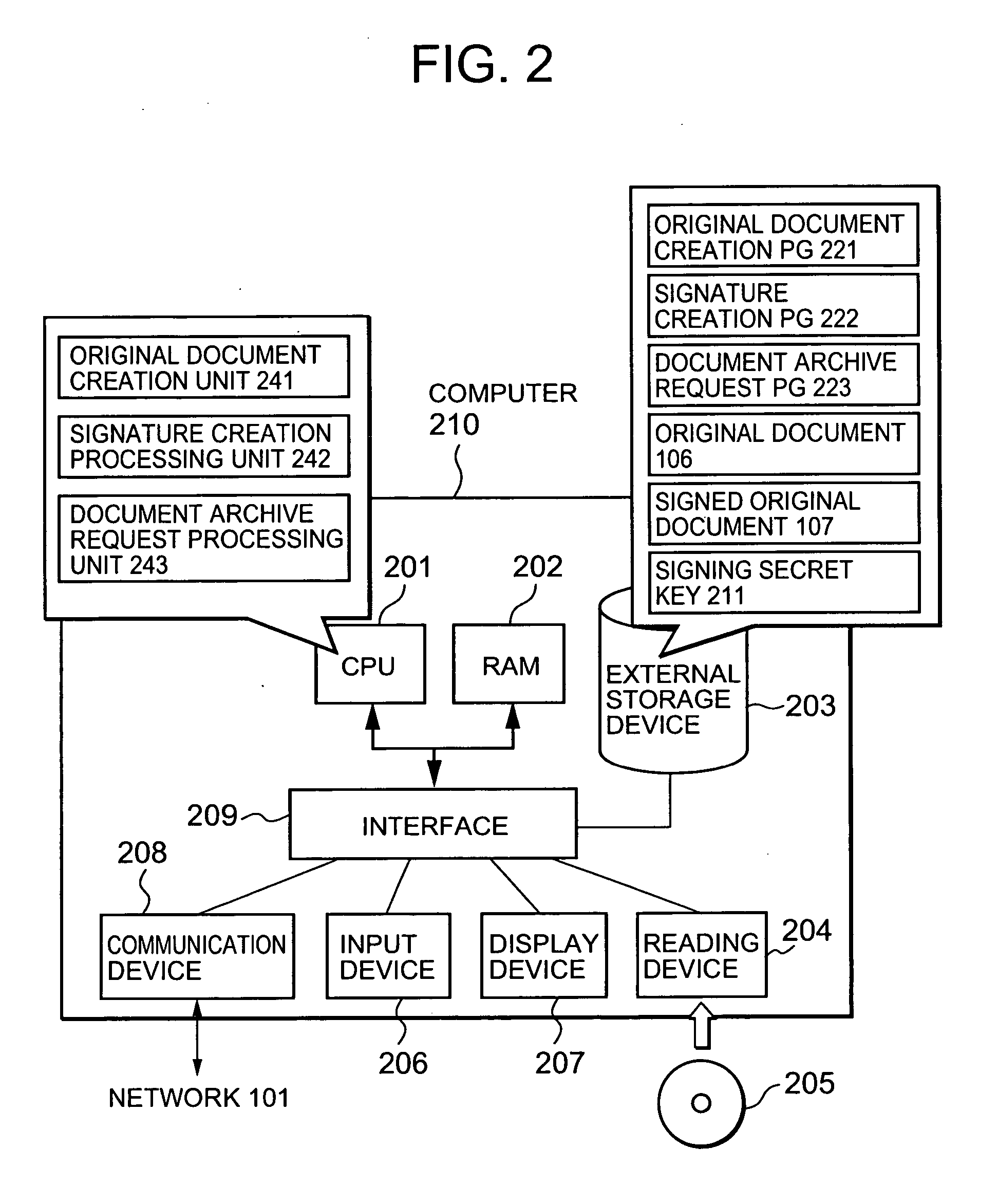
Electronic document authenticity assurance method and electronic document disclosure system
InactiveUS20050015600A1Verify authenticityUser identity/authority verificationUnauthorized memory use protectionPaper documentElectronic document
Owner:HITACHI LTD
Apparatus and Method for Variable Authentication Requirements
ActiveUS20120239950A1Volume/mass flow measurementUser identity/authority verificationState dependentAuthentication
Owner:LENOVO PC INT
Method of Managing Access Right, and System and Computer Program for the Same
InactiveUS20120095797A1Digital data processing detailsUnauthorized memory use protectionRights managementDigital work
Owner:IBM CORP
Centralized Device Virtualization Layer For Heterogeneous Processing Units
ActiveUS20100146620A1Operational speed enhancementResource allocationVirtualizationOperational system
A method for providing an operating system access to devices, including enumerating hardware devices and virtualized devices, where resources associated with a first hardware device are divided into guest physical resources creating a software virtualized device, and multiple instances of resources associated with a second hardware device are advertised thereby creating a hardware virtualized device. First and second permission lists are generated that specify which operating systems are permitted to access the software virtualized device and the hardware virtualized device, respectively. First and second sets of virtual address maps are generated, where each set maps an address space associated with either the software virtualized device or the hardware virtualized device into an address space associated with each operating system included in the corresponding permission list. The method further includes arbitrating access requests from each of the plurality of operating systems based on the permission lists and the virtual address maps.
Owner:NVIDIA CORP
Portable information processing device having data evacuation function and method thereof
InactiveUS7024698B2Volume/mass flow measurementUnauthorized memory use protectionInformation processingLocation status
A processor means is connected with other individual means, and controls those individual means. Storage means stores data to be processed by the processor means and the resultant data after the process. An important data in the storage means is transmitted to other devices for evacuation by using a wireless communication means, when a situating condition of a portable information-processing device is judged abnormal (e.g., when being stolen) based on an output of a status detector means. The data in the storage means is deleted, when the transmission is completed or the transmission is interrupted. Protection of the data and the confidentiality are thus achieved even if the portable information-processing device is stolen, since the data can be evacuated, and the data is erased after completion of the data evacuation or if the data evacuation becomes not attainable.
Owner:PANASONIC CORP
Malware automated removal system and method
ActiveUS20090013409A1Automate operationImprove software performanceMemory loss protectionError detection/correctionComputerized systemMalware
Owner:BBY SOLUTIONS
Systems, methods and computer program products for administration of computer security threat countermeasures to a computer system
InactiveUS20050039046A1Memory loss protectionDigital data processing detailsCountermeasureOperational system
Owner:TREND MICRO INC
System for securing the confidentiality of electronically stored data in the event of the physical theft thereof
InactiveUS7263190B1Secures confidentialityEasy data transferVolume/mass flow measurementUnauthorized memory use protectionConfidentialityData storing
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Use of policy levels to enforce enterprise control
InactiveUS20060225123A1Digital data processing detailsUnauthorized memory use protectionDistributed computingSoftware
Owner:TREND MICRO INC
Information processing apparatus and method, and program storing medium
InactiveUS7478437B2Disc-shaped record carriersDigital data processing detailsInformation processingComputer science
Owner:SONY CORP
Method for updating a firmware component and device of measurement and control technology
ActiveUS20170293484A1The encryption method is simpleLess resourcesProgramme controlMemory architecture accessing/allocationEncryptionAuthentication
Owner:ENDRESSHAUSER CONDUCTA GMBHCO
Digital data transparency protected safety read-write system and method
InactiveCN101042681AWon't worry about damageImprove usabilityUnauthorized memory use protectionInternal/peripheral component protectionDigital dataOperational system
Owner:LENOVO (BEIJING) CO LTD
System and Method for the Designation of Items in a Virtual Universe
InactiveUS20110055919A1Facilitates tracking and recoveryData processing applicationsDigital data processing detailsHuman–computer interactionVirtual universe
The present invention enables items in a Virtual Universe to be tagged as available for pickup by one or more designated users. The present invention permits a designated user to be alerted that there is an item designated for that user / avatar and available for pick-up at a location in the Virtual Universe. A user may designate another user (or user's avatar), for example, a minor for whom the designating user has responsibility, as an “item” to be tracked. For privacy and other reasons, this and other features may be implemented on an opt-in basis.
Owner:INT BUSINESS MASCH CORP
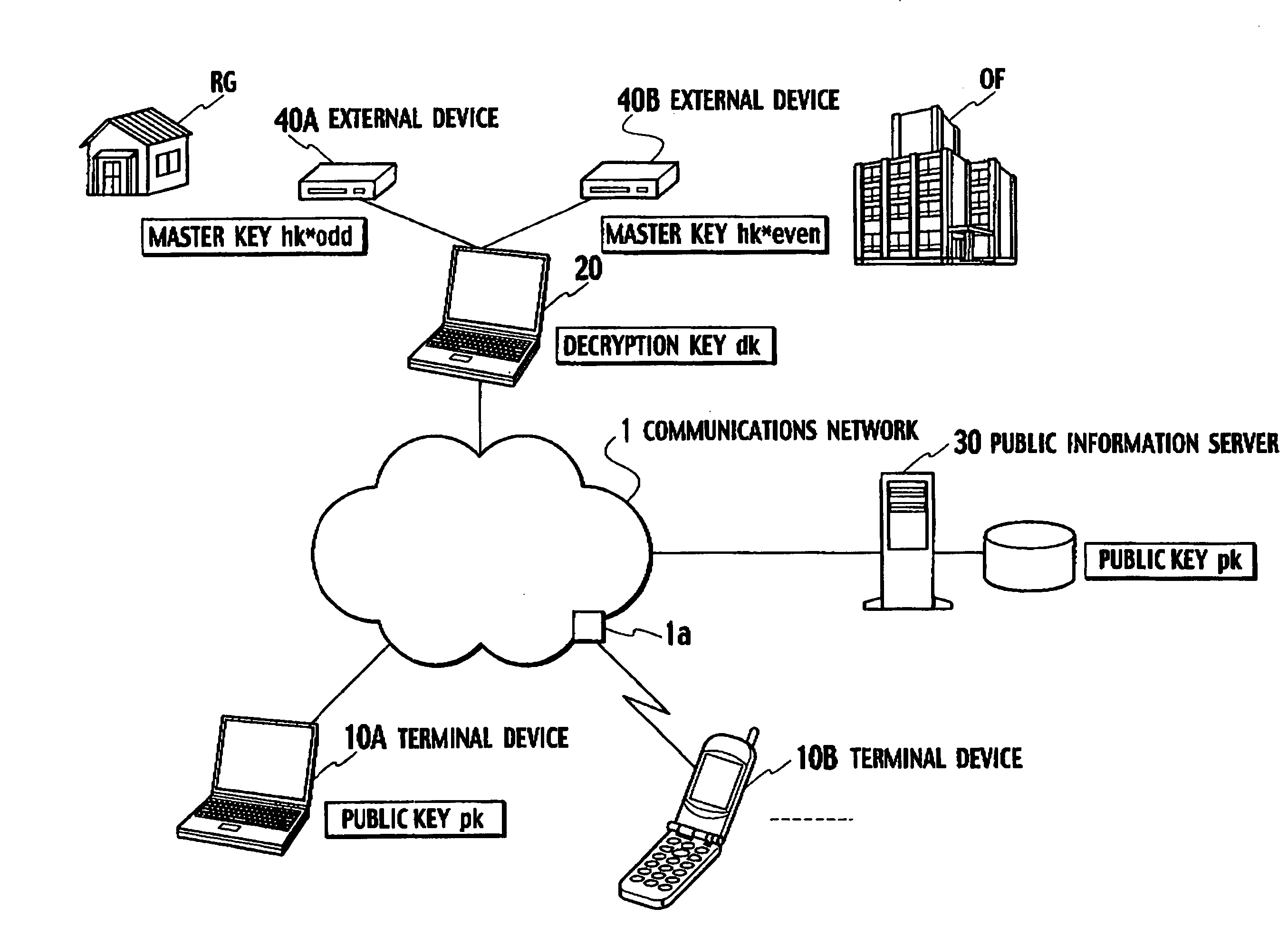
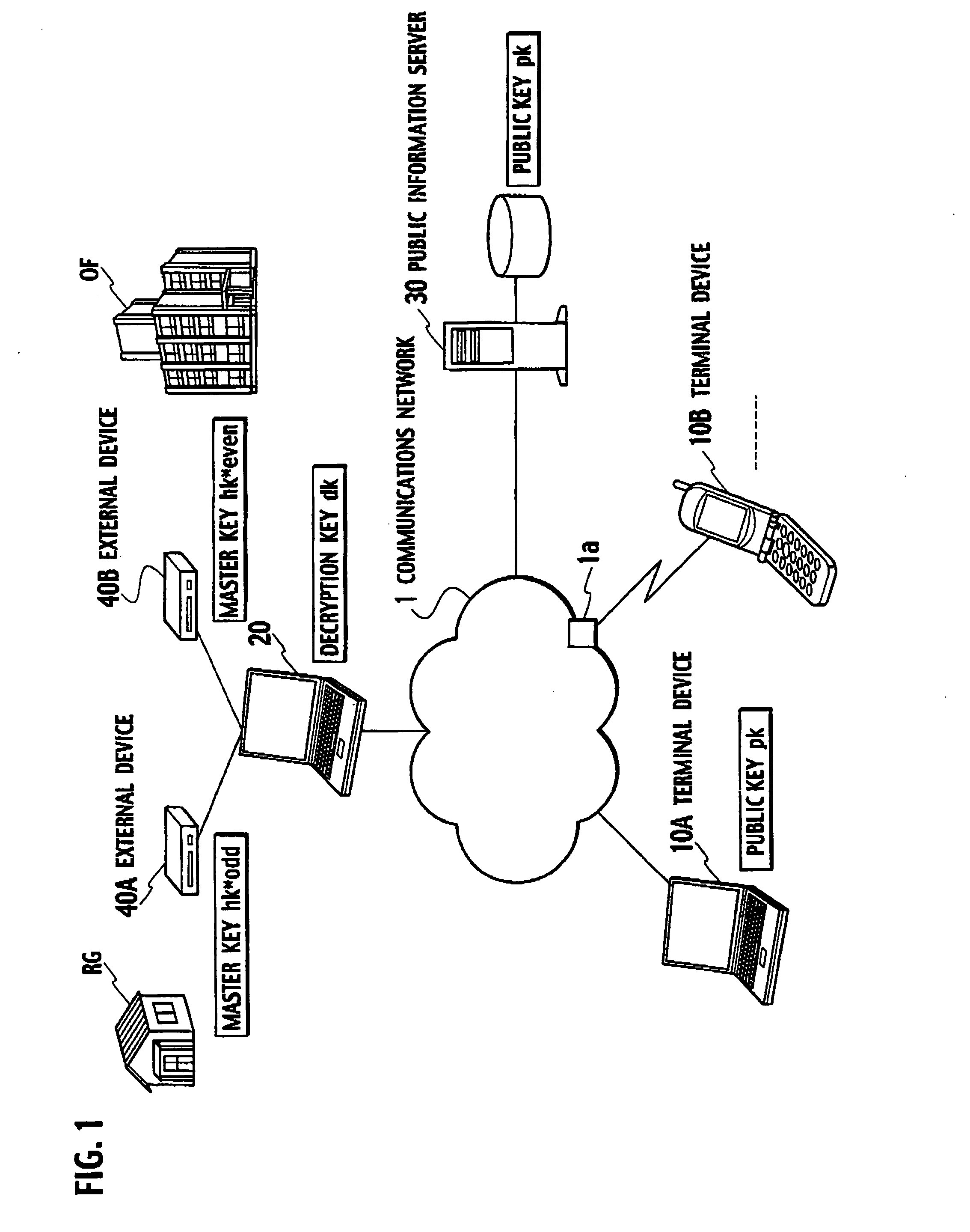
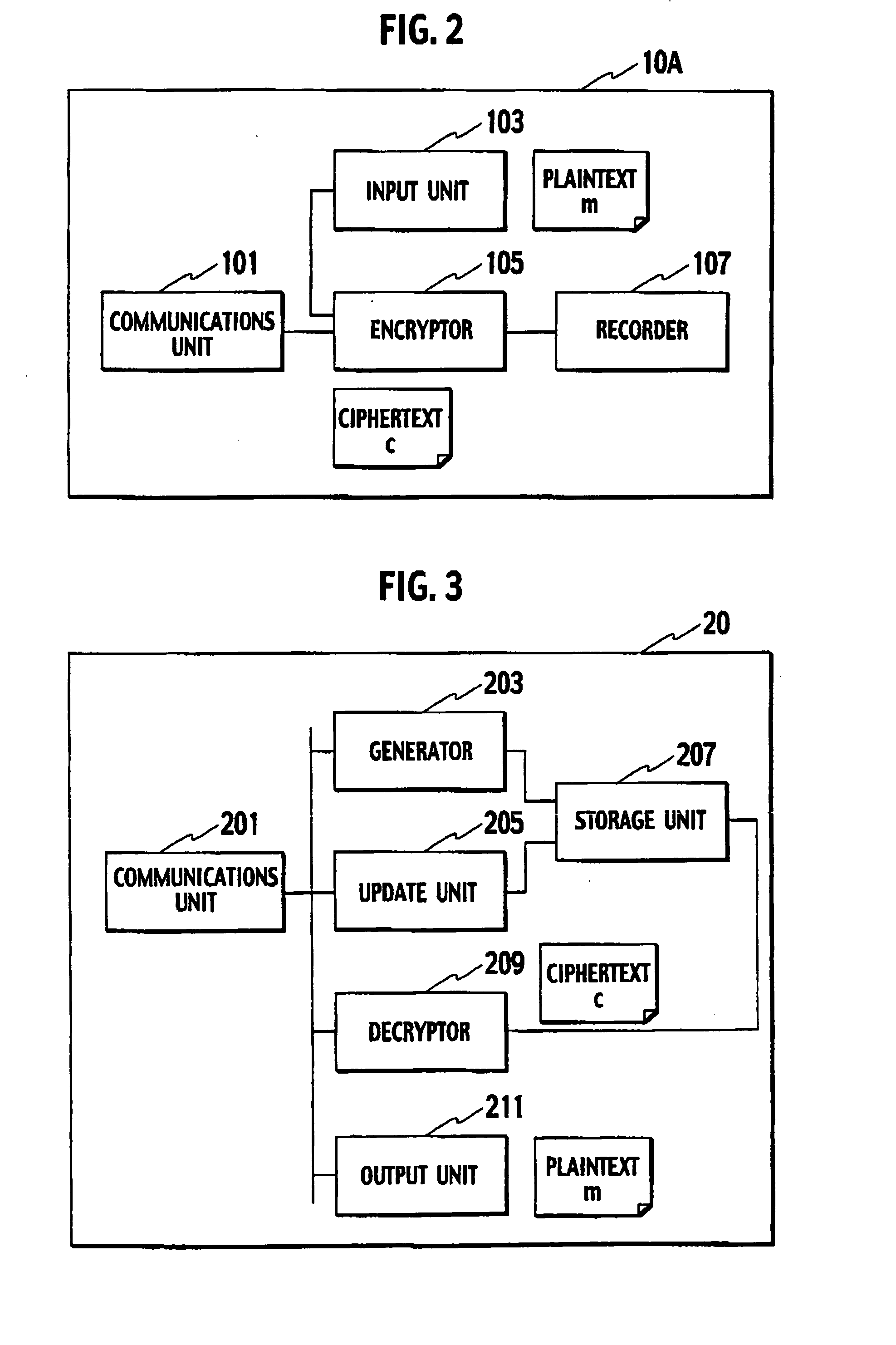
Key-updating method, encryption processing method, key-insulated cryptosystem and terminal device
InactiveUS20070230705A1Without deteriorating securityKey distribution for secure communicationUnauthorized memory use protectionCryptosystemComputer hardware
Owner:NTT DOCOMO INC
Removable storage device data protection
ActiveUS20130031376A1Unauthorized memory use protectionHardware monitoringFile systemRemovable media
Owner:LENOVO (SINGAPORE) PTE LTD
System and Method for Detecting and Evicting Malicious Vehicles in a Vehicle Communications Network
ActiveUS20110214178A1Improve performanceReduce impactMemory loss protectionError detection/correctionMathematical modelSimulation
In a vehicle communication network, some vehicles may be used by attackers to send false information to other vehicles which may jeopardize the safety of other vehicles. Vehicles should be able to detect malicious communications activities and to mitigate the impact of malicious vehicles by evicting (eliminating) suspected malicious vehicles from the system. Evicting a vehicle is to ignore the messages sent from the vehicle for a specified time period. Voting and sacrifice principles are combined using a mathematical model based on the “Mafia Game”. The Mafia Game model focuses on the relative size of the group of attackers within a neighborhood necessary to dominate the entire network in the neighborhood (i.e., to eventually evict all the innocent vehicles).
Owner:PERSPECTA LABS INC
Information processing system, method, and apparatus, and program
InactiveUS20070286423A1Unauthorized memory use protectionHardware monitoringInformation processingKey generator
Disclosed herein is an information processing system including: a first information processing apparatus for transmitting a content including video and audio signals; and a second information processing apparatus for receiving the content. The first apparatus includes: a first key generator configured to generate a first key; a video encryptor configured to encrypt the video signal with the first key; an audio encryptor configured to encrypt the audio signal with the first key; and a transmitter configured to transmit the content including the encrypted video and audio signals. The second apparatus includes: a receiver configured to receive the content; a second key generator configured to generate a second key corresponding to the first key; a video decryptor configured to decrypt the encrypted video signal with the second key; and an audio decryptor configured to decrypt the encrypted audio signal with the second key.
Owner:SONY CORP
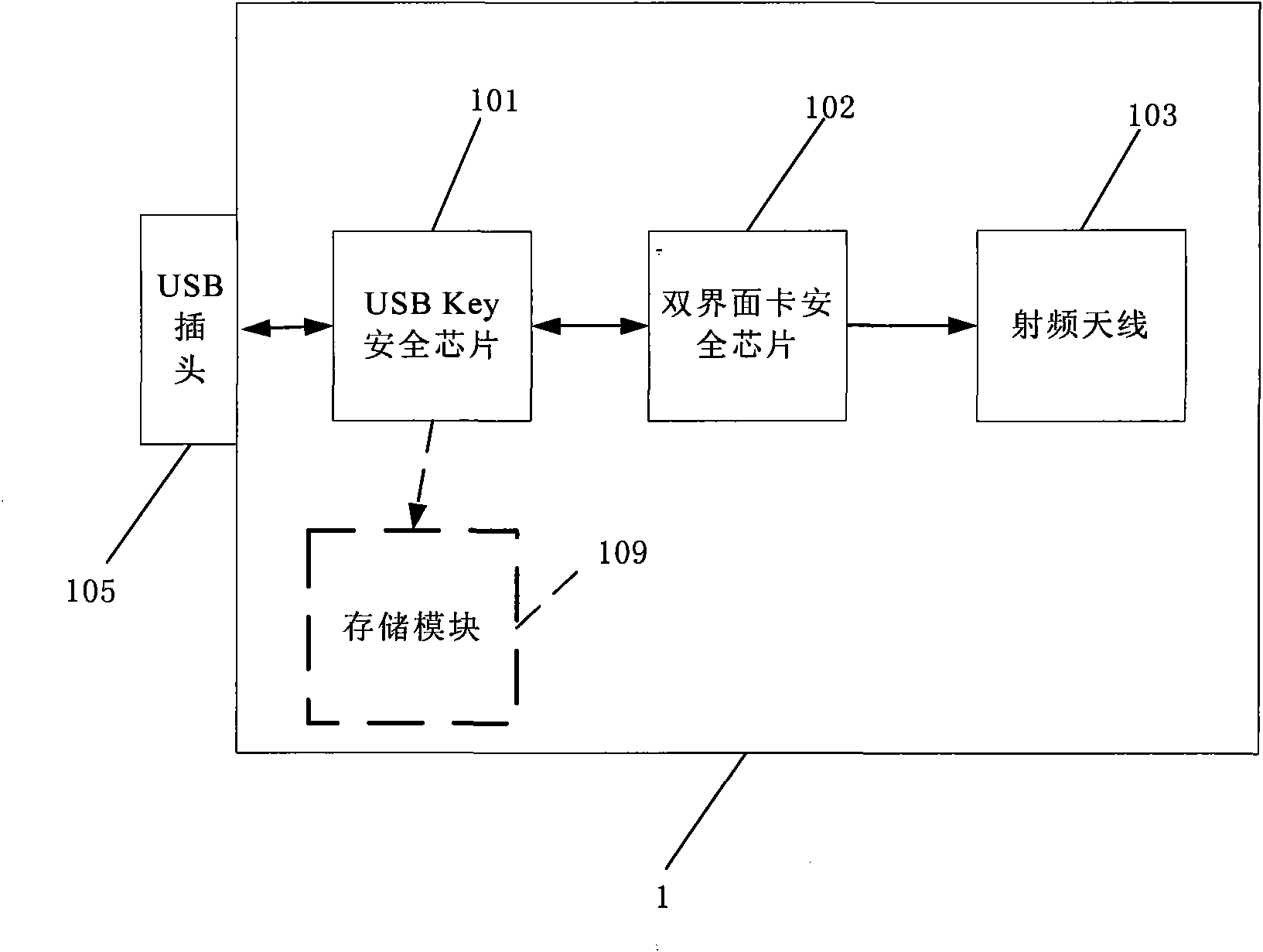
Encrypting and authenticating equipment with dual safety chips
InactiveCN101667163AUnauthorized memory use protectionComputer security arrangementsRadio frequencyEngineering
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
Alert transmission apparatus and method for policy-based intrusion detection and response
An alert transmission apparatus for a policy-based intrusion detection and response has a central policy server (CPS) and an intrusion detection and response system (IDRS). In the CPS, a policy management tool generates security policy information and then stores the generated security policy information in a policy repository. A COPS-IDR server sends the information to the IDRS and an IDMEF-XML-type alert transmission message to a high-level module. An IDMEF-XML message parsing and translation module stores a parsed and translated IDMEF-XML-type alert transmission message in an alert DB or provides the message to an alert viewer. In the IDRS, a COPS-IDR client generates the IDMEF-XML-type alert transmission message and provides the message to the CPS. An intrusion detection module detects an intrusion. An intrusion response module responds to the intrusion. An IDMEF-XML message building module generates an IDMEF-XML alert message and provides the message to the COPS-IDR client.
Owner:ELECTRONICS & TELECOMM RES INST
Method and system used for Flash balance storage
ActiveCN103823642AAverage erase timesExtended service lifeInput/output to record carriersUnauthorized memory use protectionNetwork packetComputer science
Owner:AUTEL HUNAN CO LTD
Network apparatus for accessing services over a network
ActiveUS7631192B1Improve securityTelevision system detailsTelemetry/telecontrol selection arrangementsComputer hardwareDisplay device
Owner:FUNAI ELECTRIC CO LTD
Anti-tear protection for smart card transactions
InactiveUS20030071718A1Memory record carrier reading problemsUnauthorized memory use protectionData transmissionCollection system
Owner:KELLY GUY M +3
System and method for securing computers against computer viruses
In one embodiment, an antivirus mechanism (e.g., antivirus program) in a computer initiates shielding procedures in response to a triggering event indicative of a presence of a virus in the computer, the virus being of a type not recognized by the antivirus program. The shielding procedures advantageously protect important components of the computer while the antivirus program does not have the requisite antidote to directly deal with the virus.
Owner:TREND MICRO INC
Popular searches
Alarms Analogue secracy/subscription systems Special data processing applications Input/output processes for data processing Digital data protection Data switching by path configuration Multiple digital computer combinations Wireless commuication services Security arrangement Network data management
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap