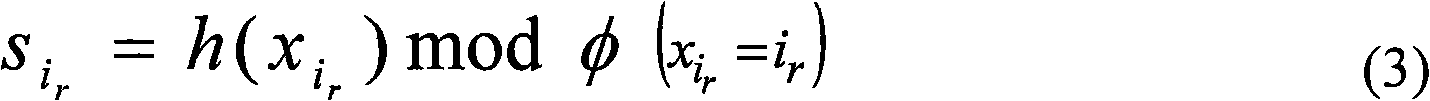Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
127results about "User identity/authority verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
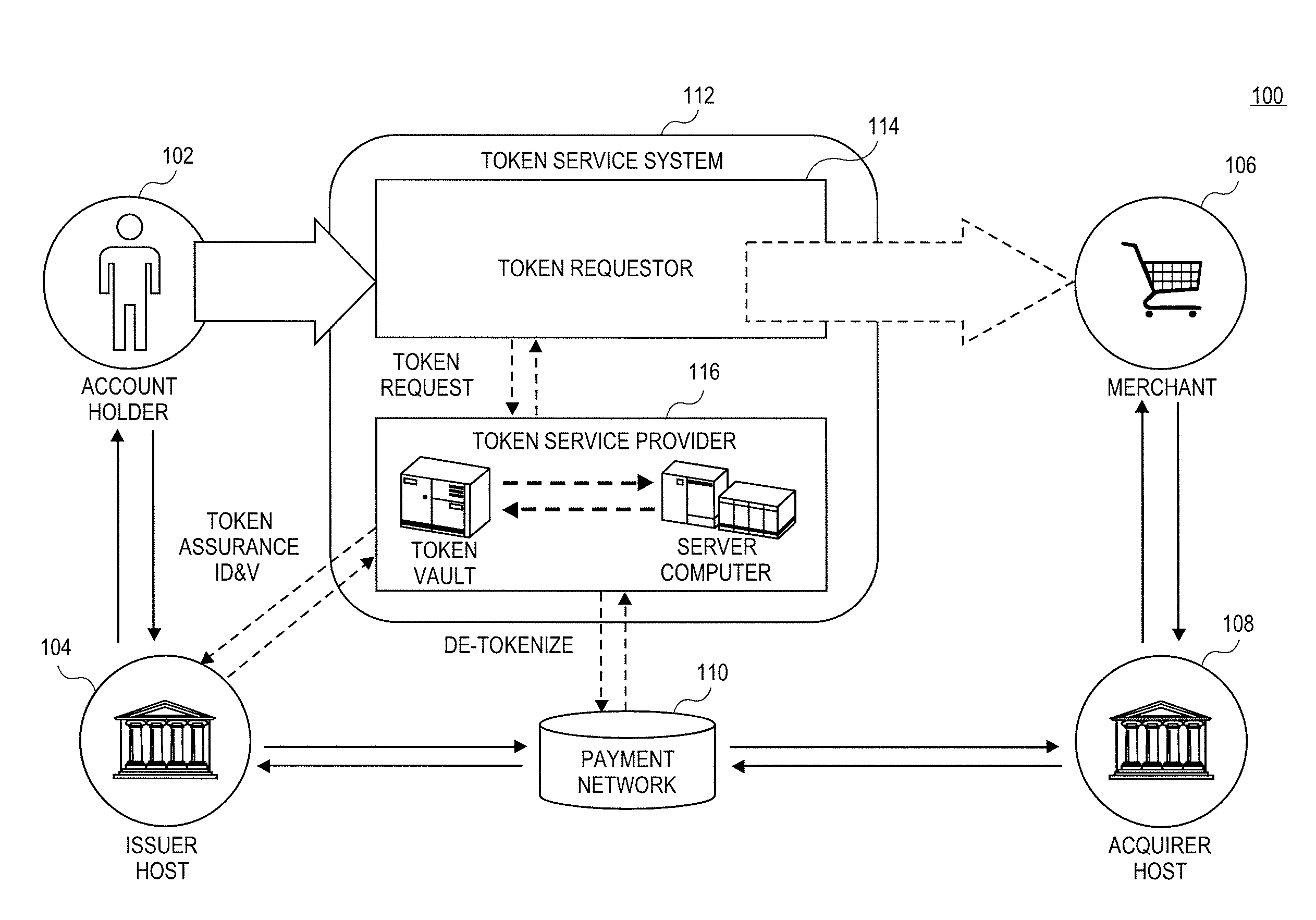
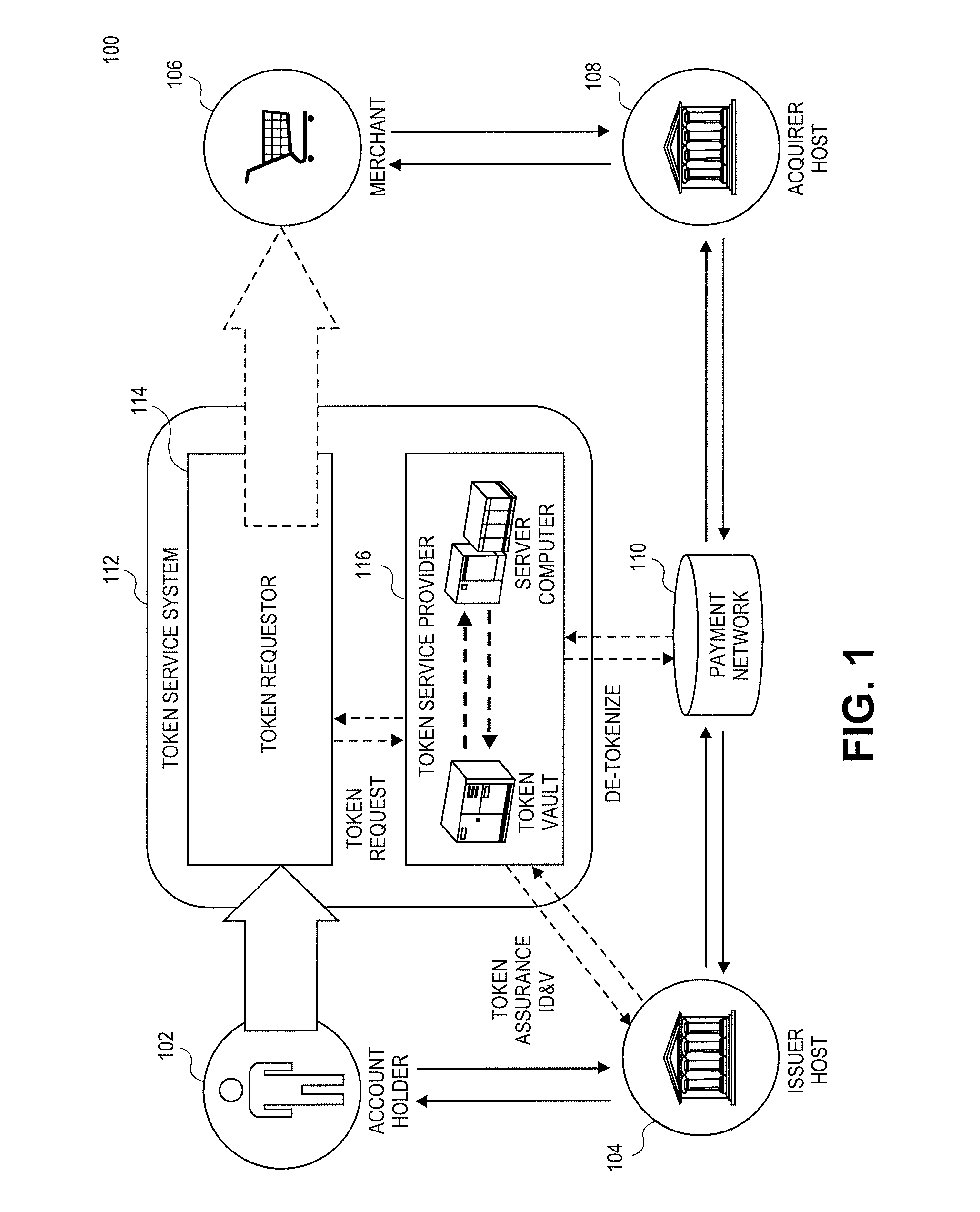
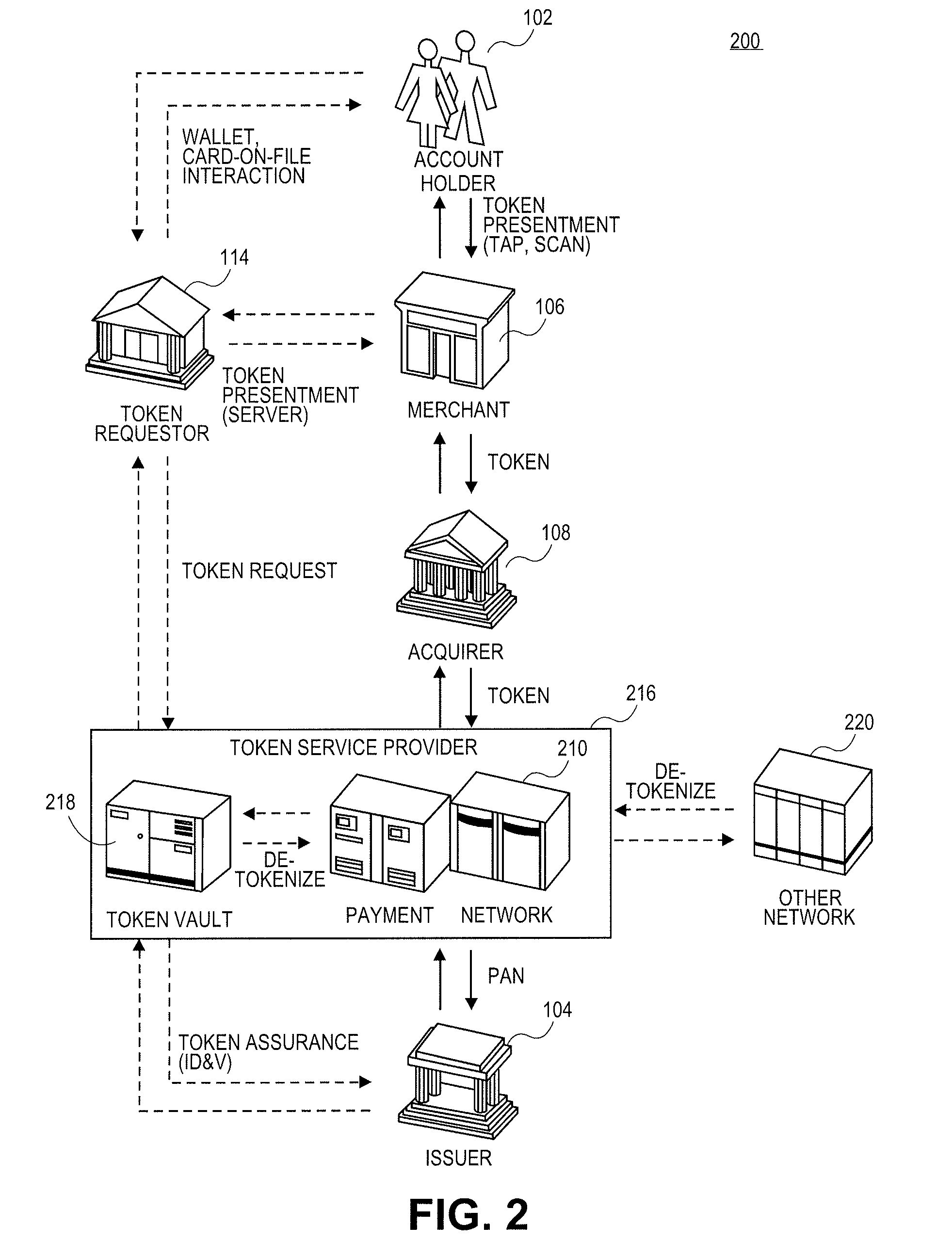
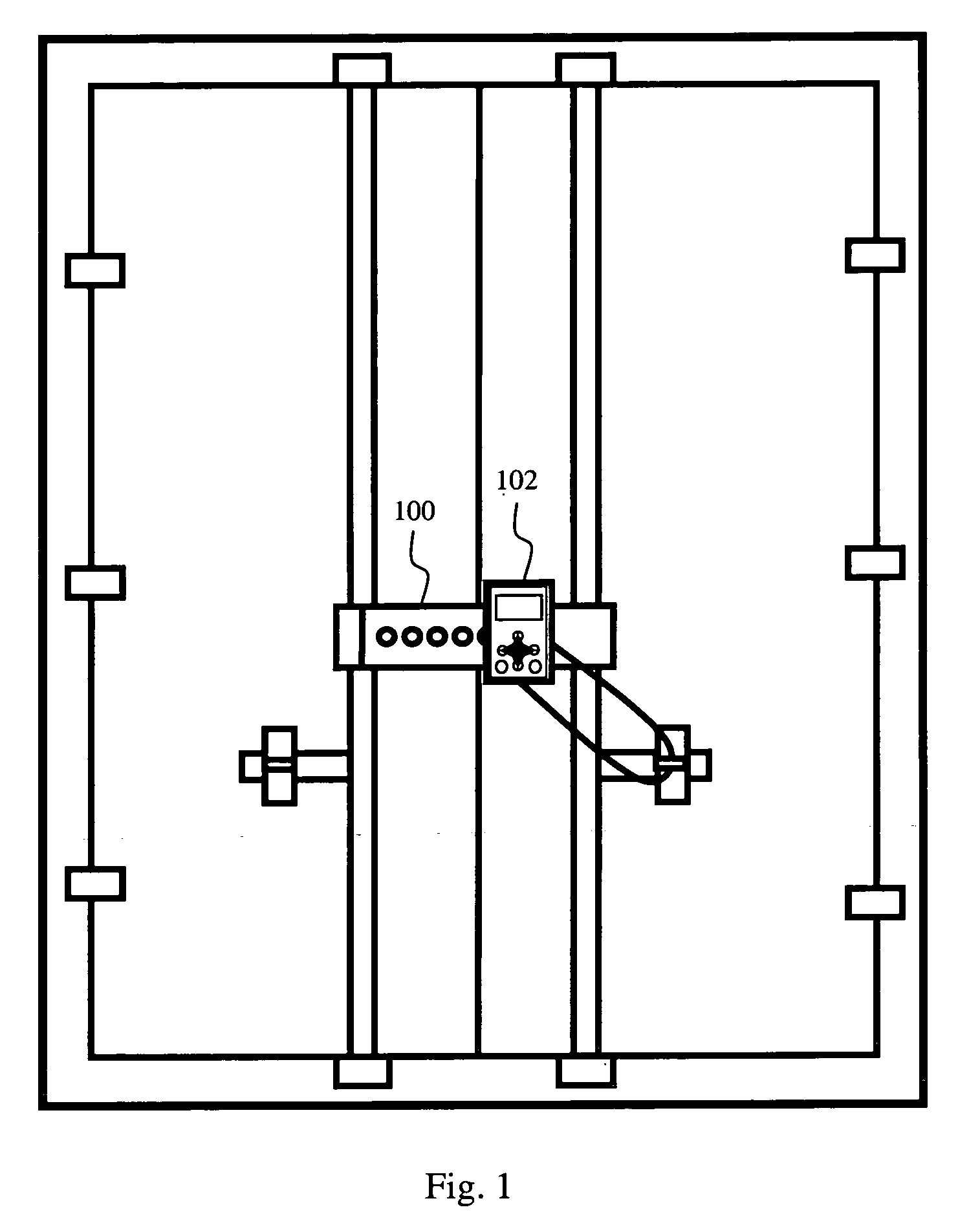
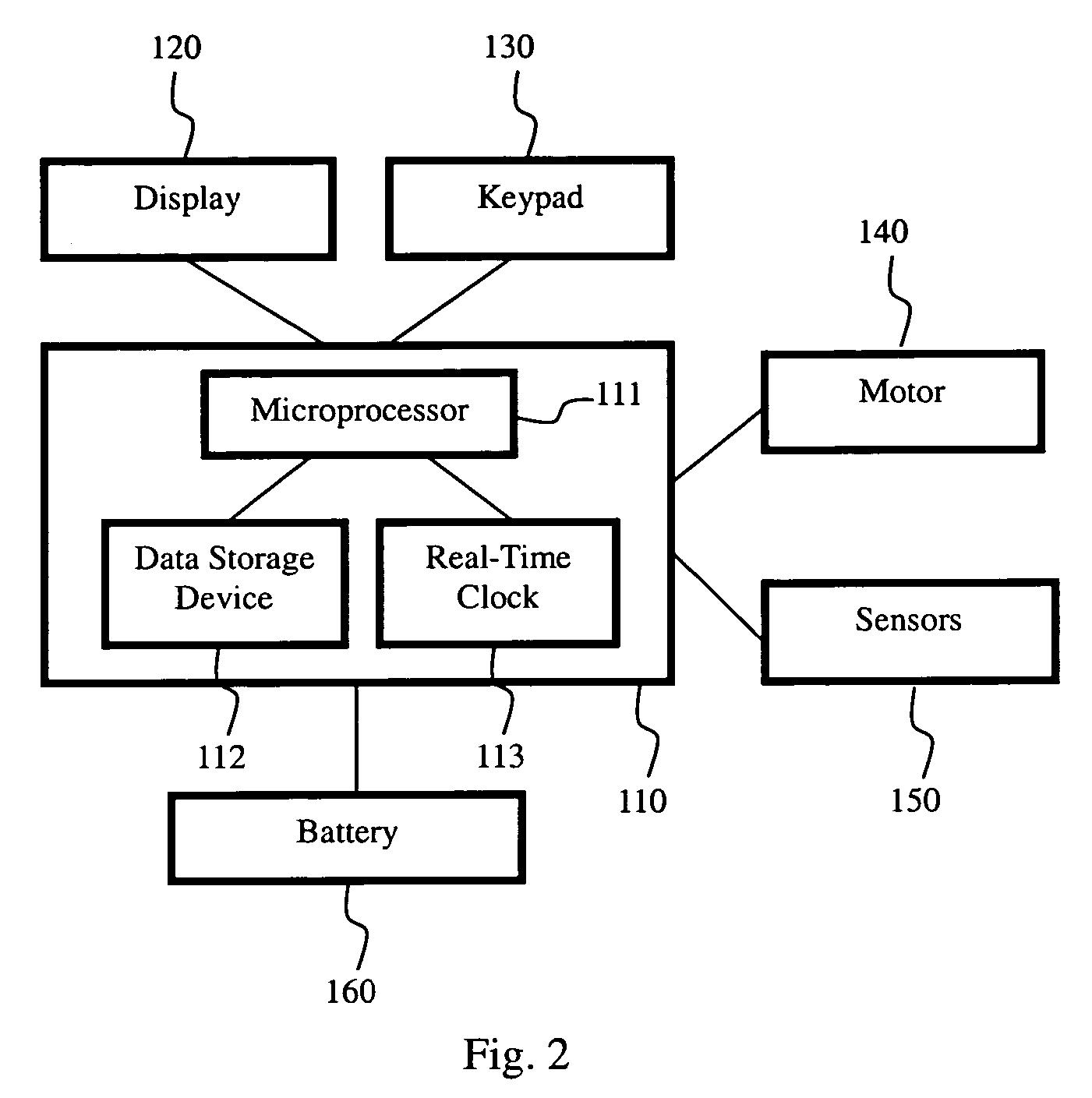
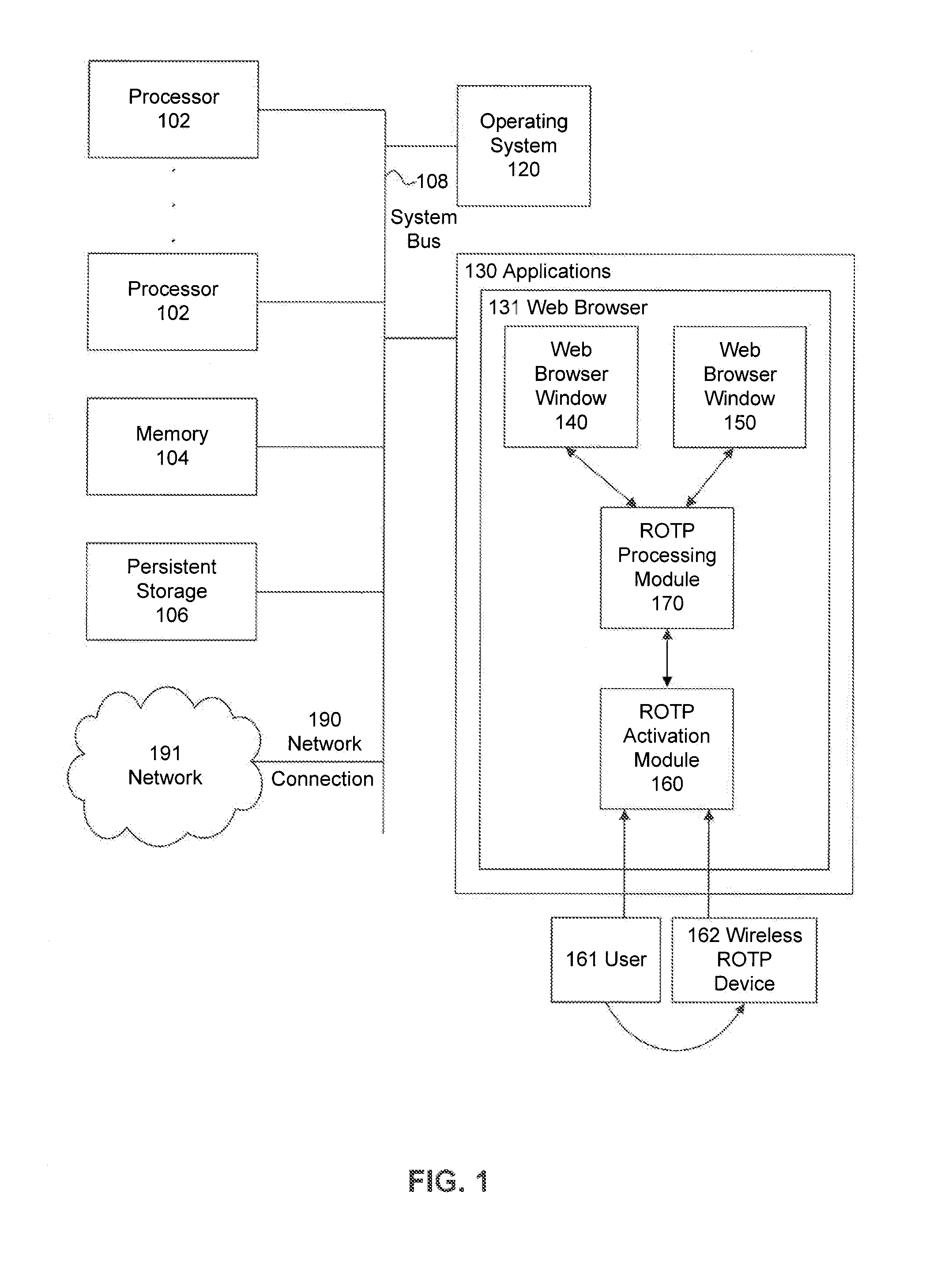
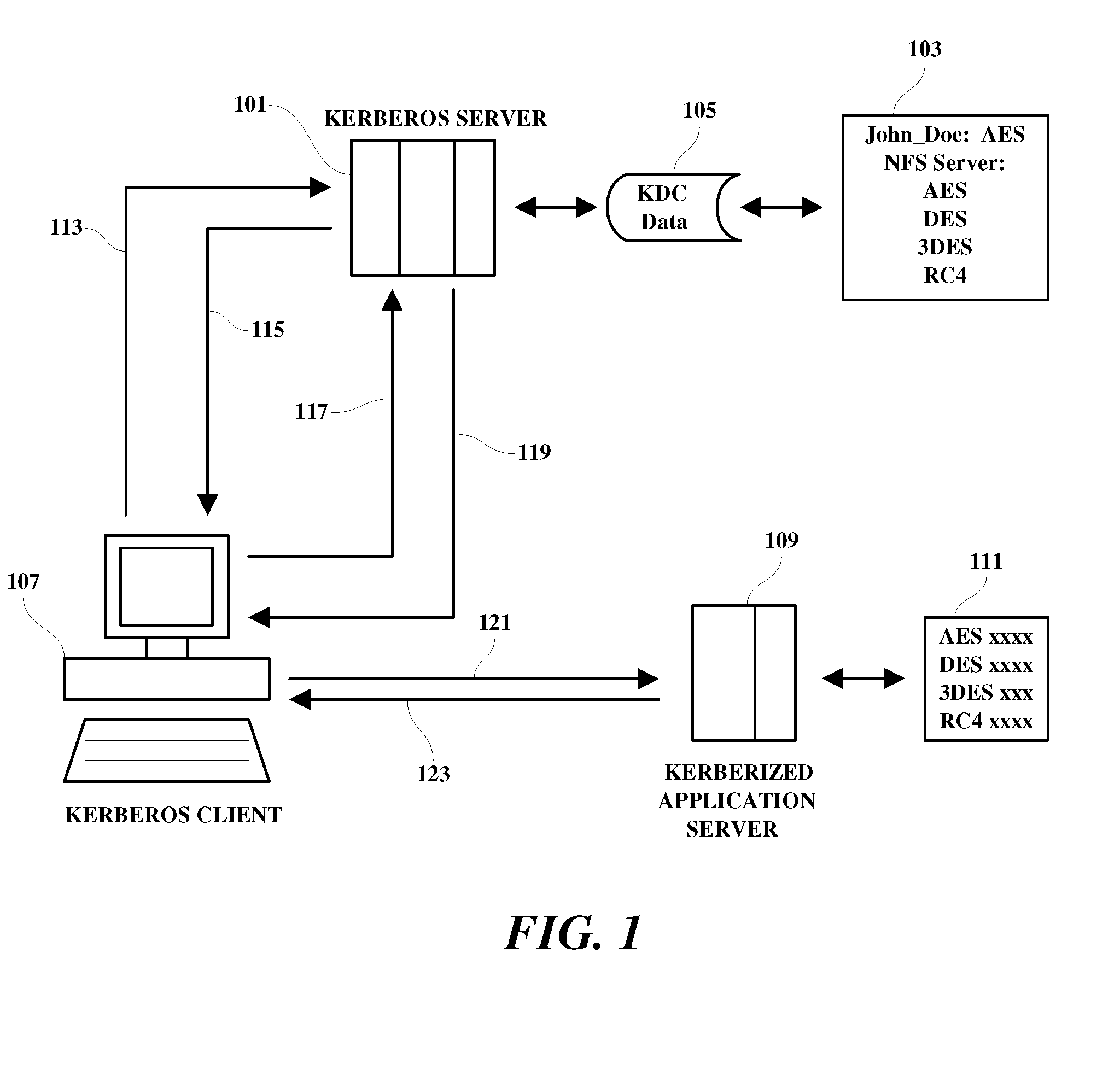
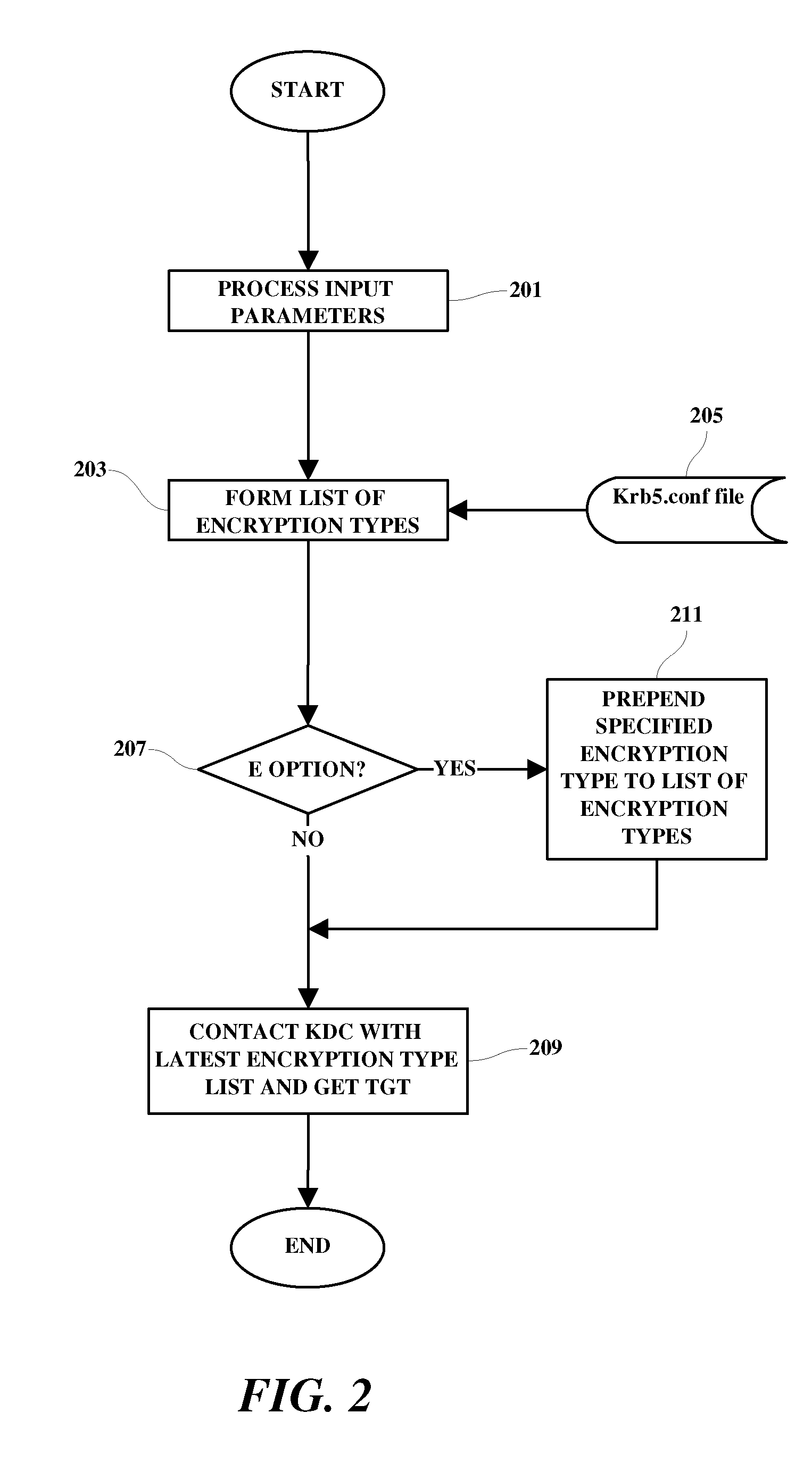
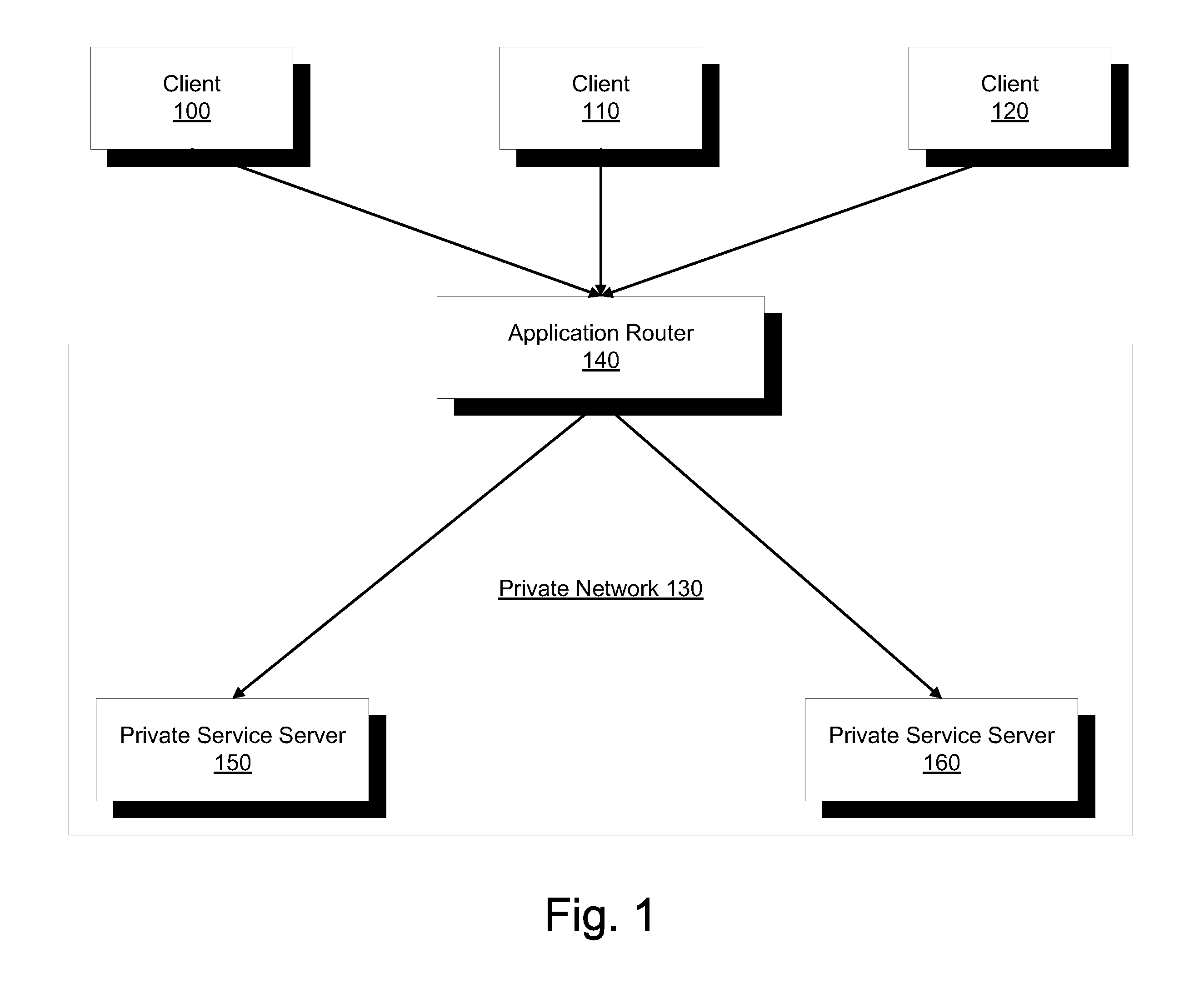
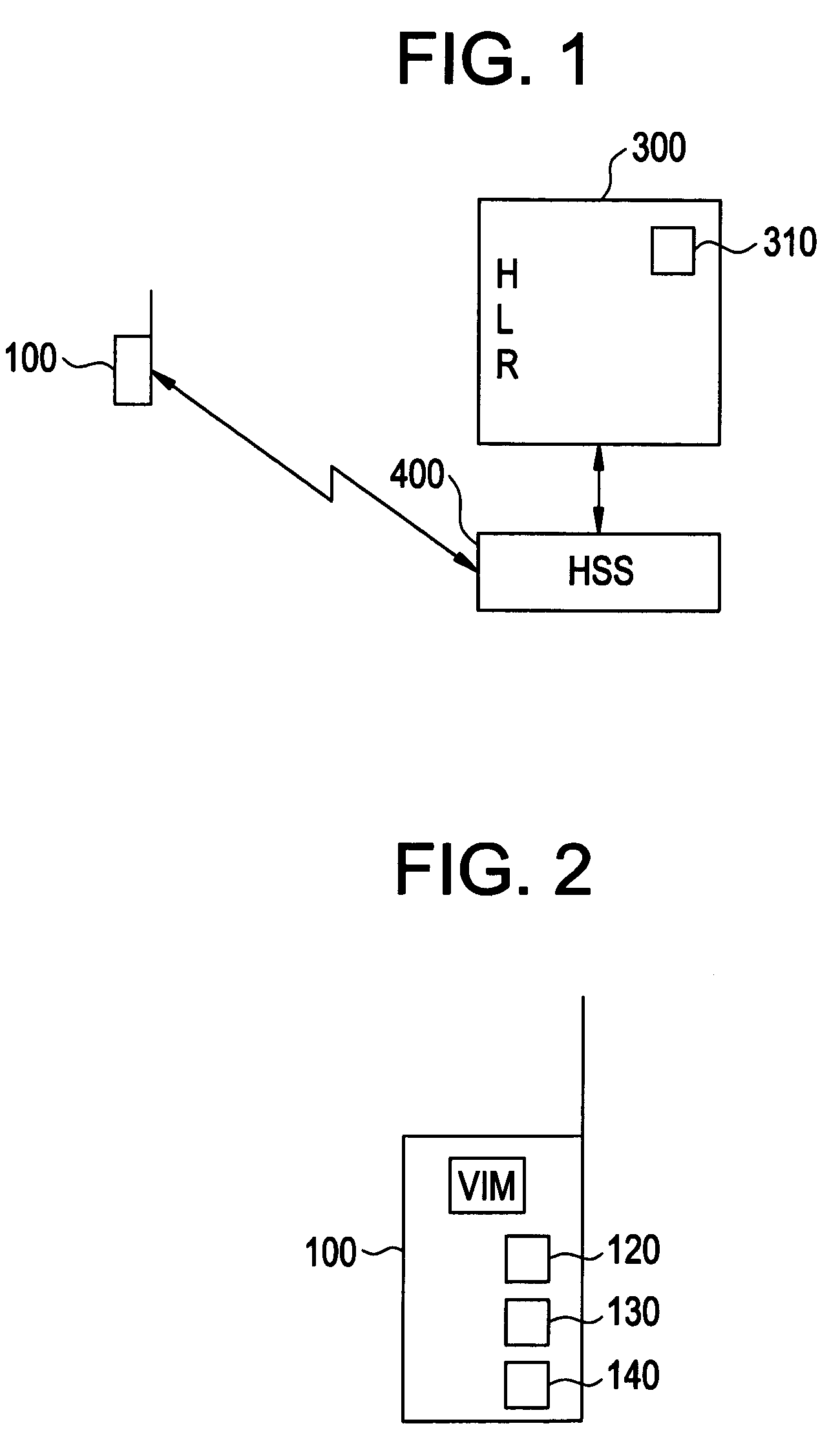
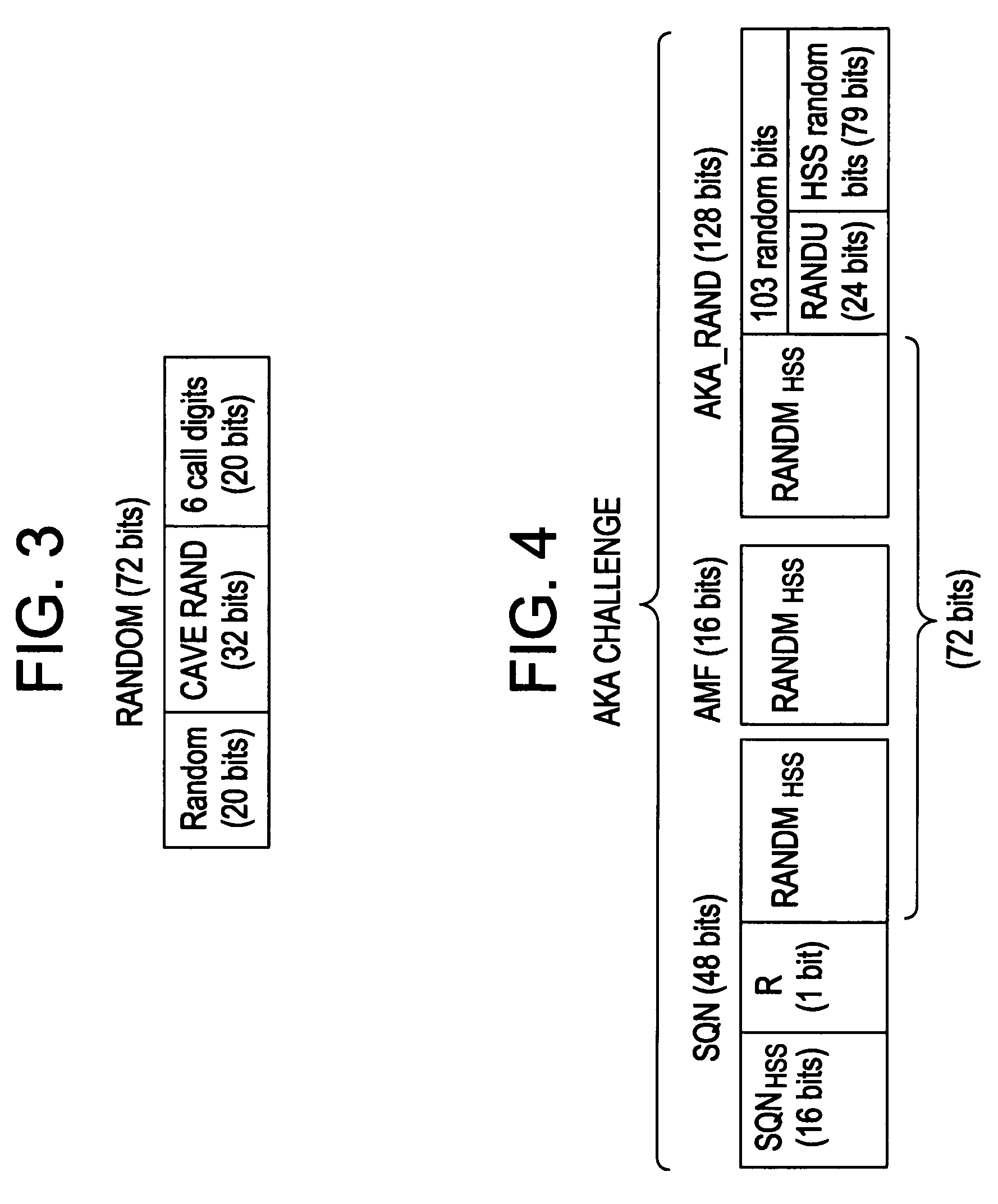
Network token system
ActiveUS20150127547A1User identity/authority verificationPoint-of-sale network systemsPayment transactionOperating system
Owner:MASTERCARD INT INC +1
Methods for combating malicious software
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
Efficient, Secure, Cloud-Based Identity Services
InactiveUS20110246765A1Improve securityUser identity/authority verificationWeb serviceSecurity Measure
An Identity Ecosystem Cloud (IEC) provides global, scalable, cloud-based, cryptographic identity services as an identity assurance mechanism for other services, such as data storage, web services, and electronic commerce engines. The IEC complements these other services by providing enhanced identity protection and authentication. An IEC performs identity services using surrogate digital certificates having encryption keys that are never exposed to the public. An individual requesting other services must meet an identity challenge before access to these other services is granted. Service requests to the IEC, and responses from the IEC, are securely encrypted. An IEC integrates smoothly into existing services by layering on top of, or being used in conjunction with, existing security measures. Identity transactions may be logged in a manner that complies with strict medical and financial privacy laws.
Owner:SURIDX
Methods for Single Signon (SSO) Using Decentralized Password and Credential Management
ActiveUS20130166918A1Decentralized credential managementShorten the timeUser identity/authority verificationComputer security arrangementsDistributed serversEnd to end security
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
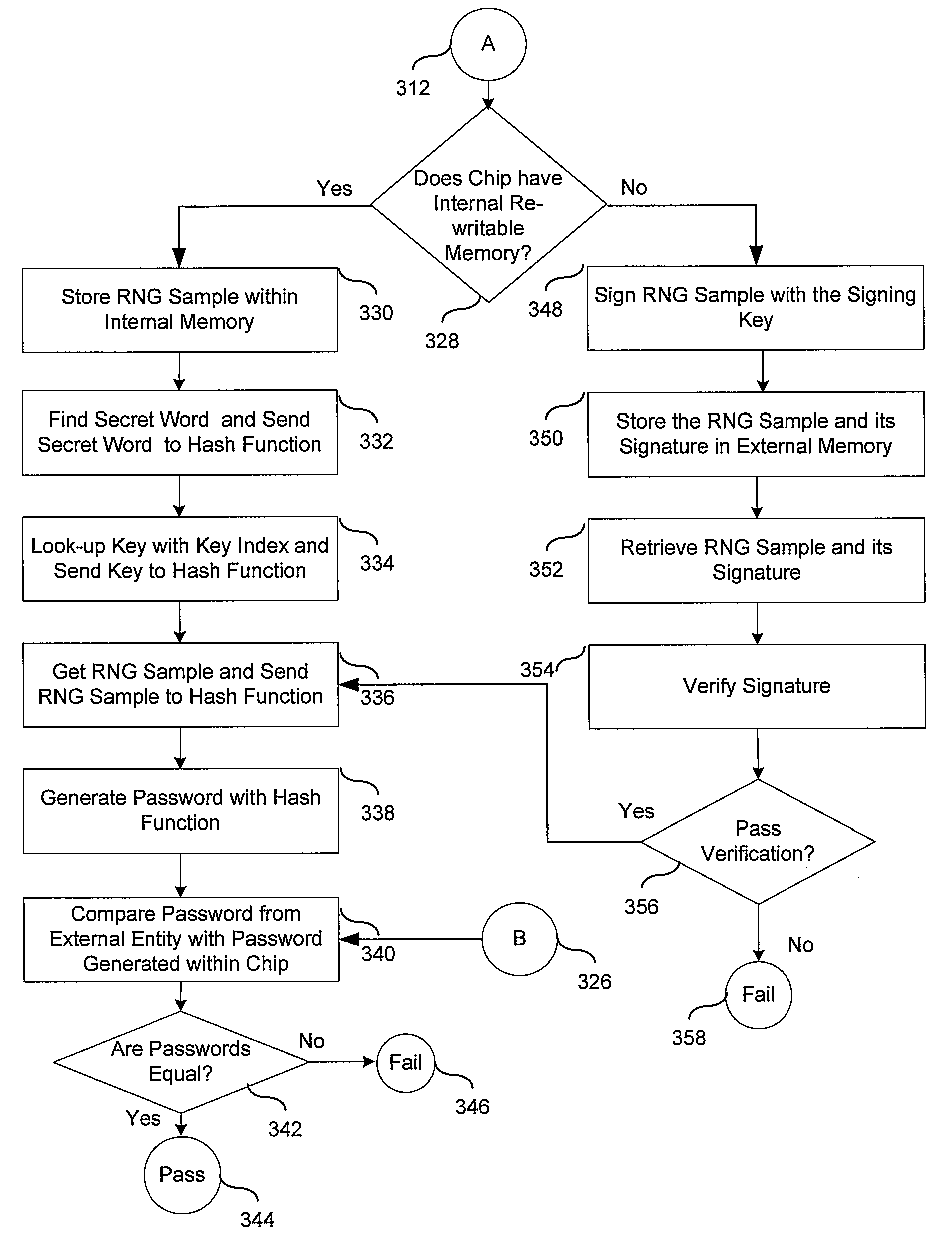
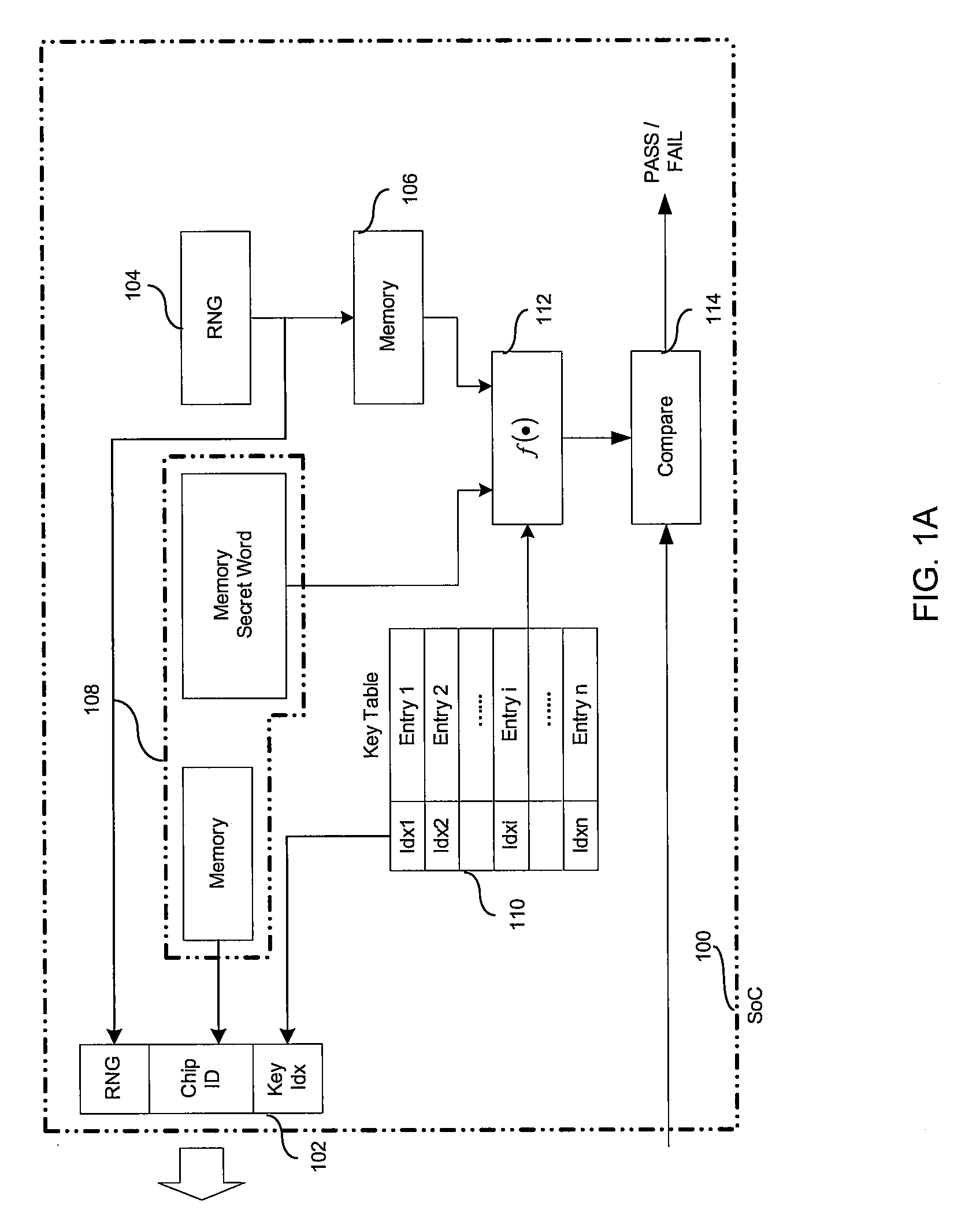
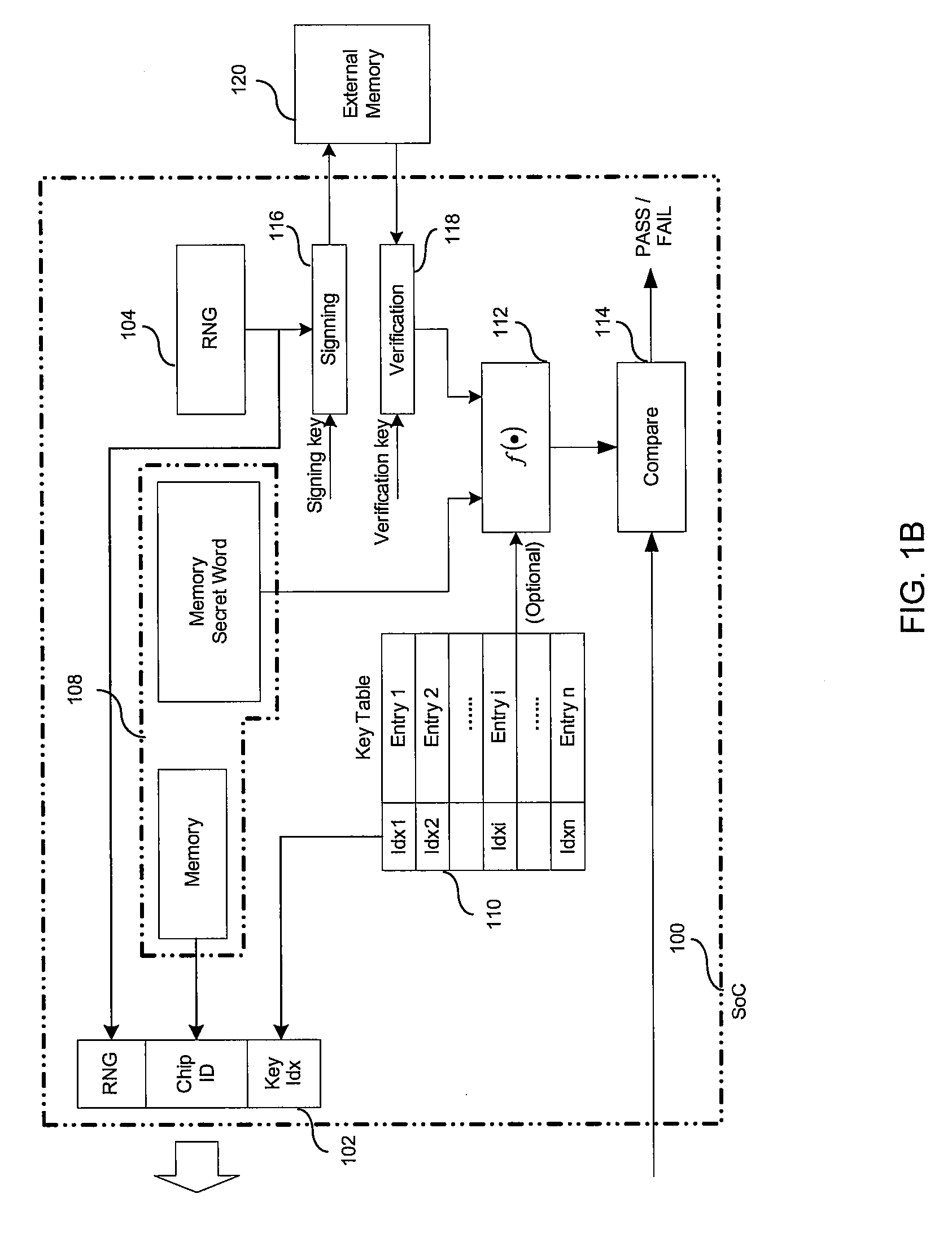
Method and apparatus of secure authentication for system on chip (SOC)
ActiveUS20080263362A1User identity/authority verificationInternal/peripheral component protectionSecurity functionComputer hardware
Owner:AVAGO TECH INT SALES PTE LTD
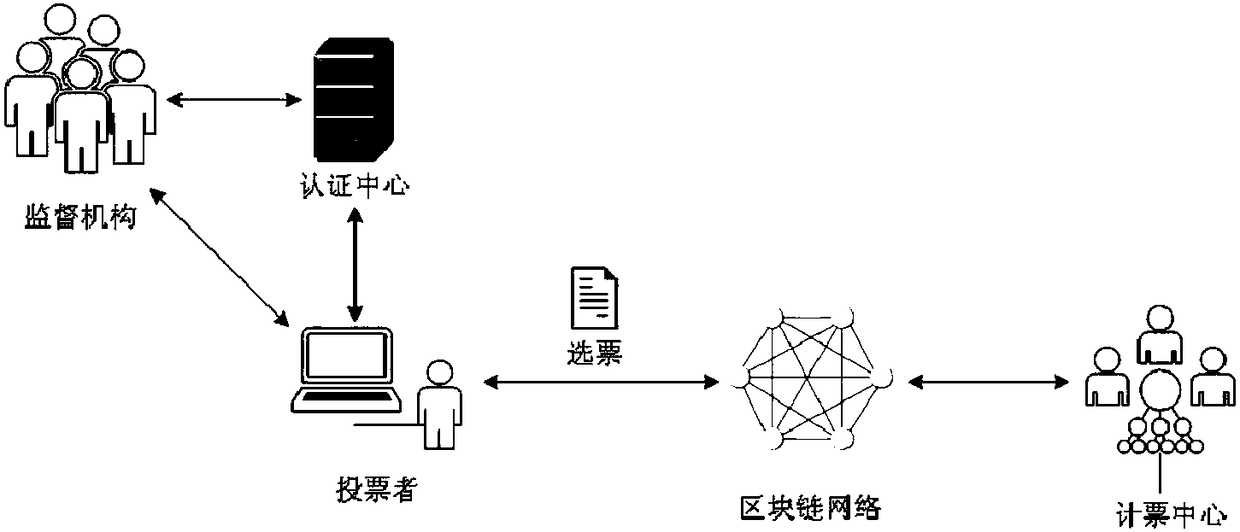
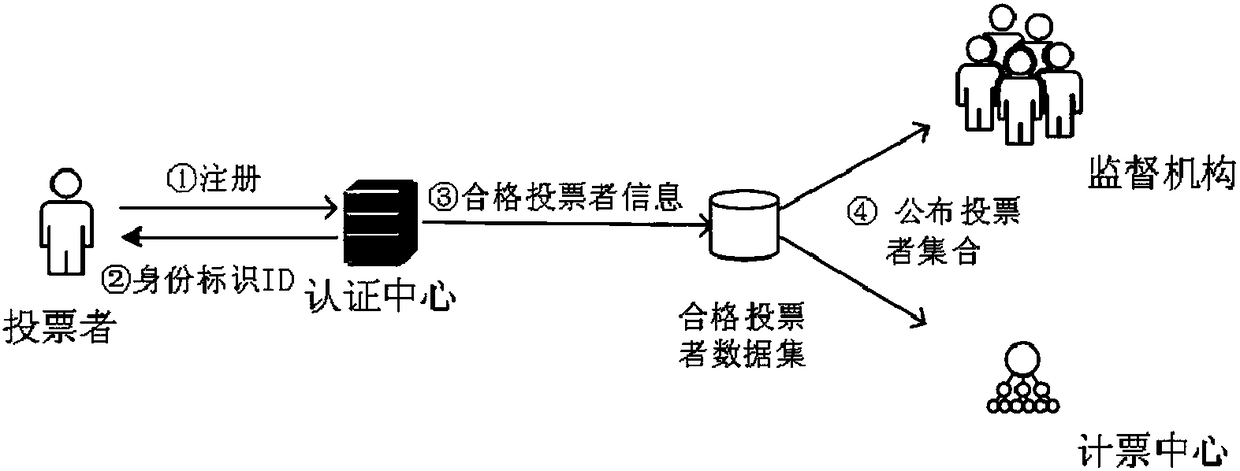
Anonymous electronic voting method based on blockchain
InactiveCN108109257AProtect anonymityPrivacy protectionVoting apparatusUser identity/authority verificationTransaction dataBlind signature
Owner:HANGZHOU DIANZI UNIV
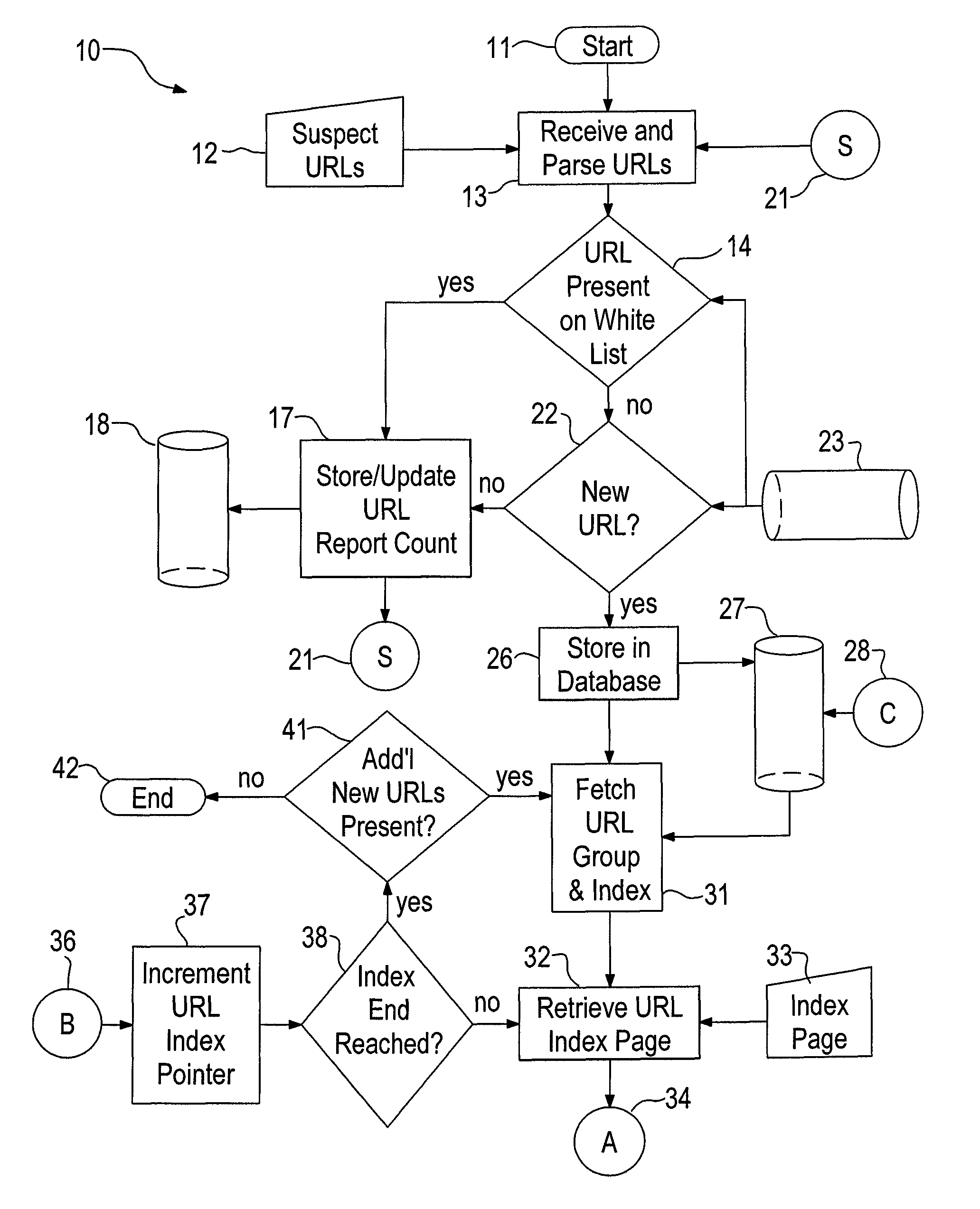
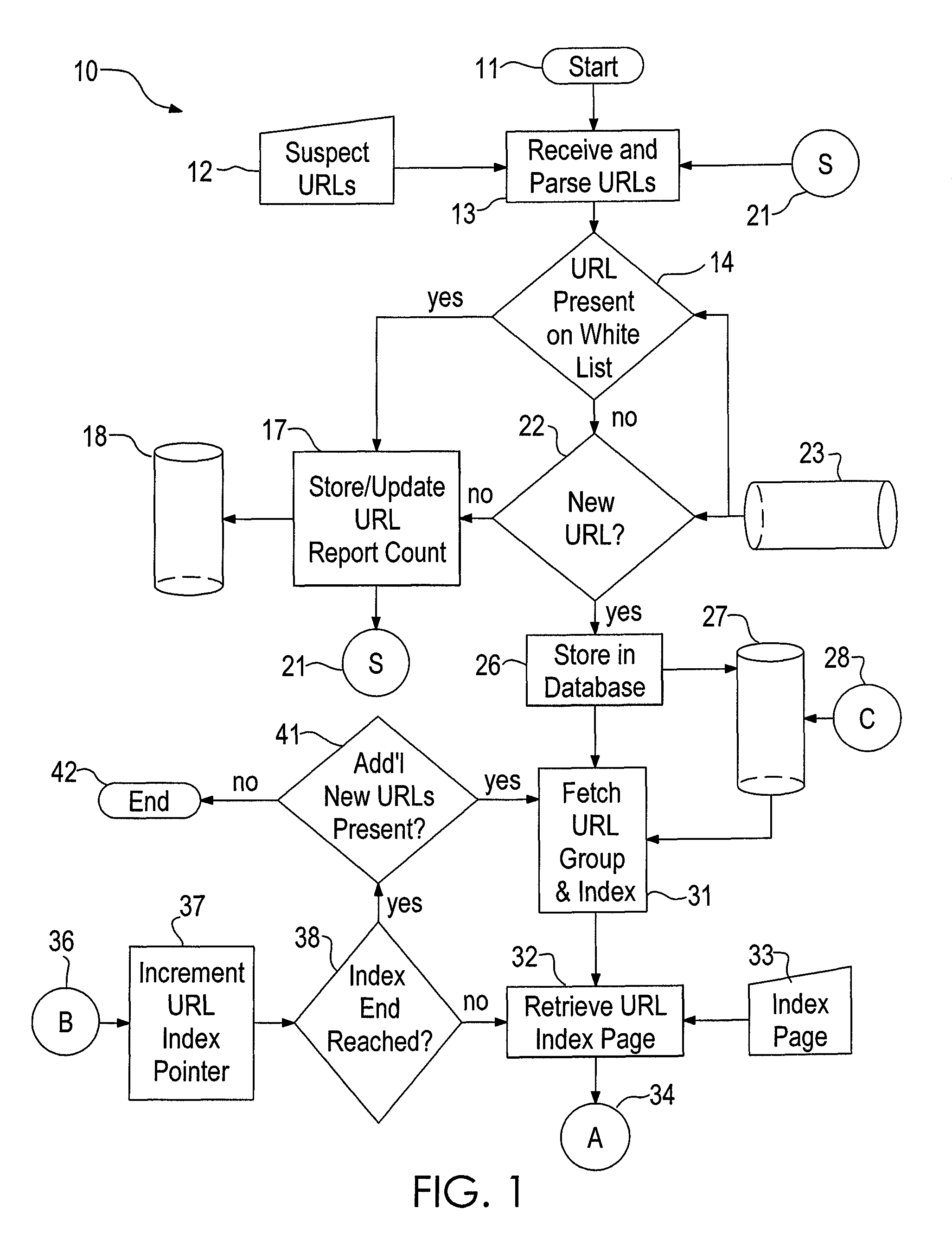
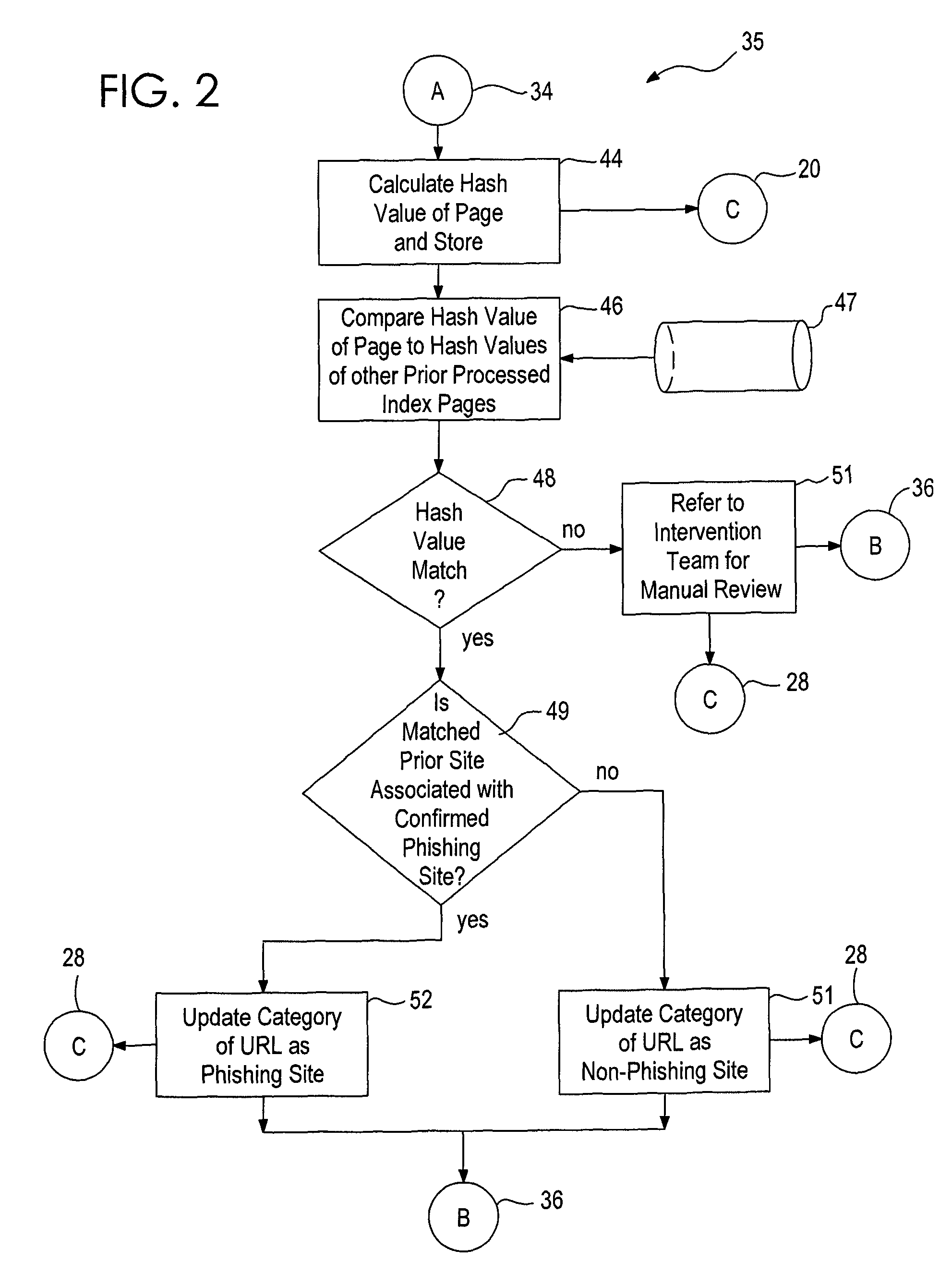
System and method for identifying a phishing website
ActiveUS8468597B1Volume/mass flow measurementUser identity/authority verificationPhishingData mining
Owner:UAB RES FOUND
Service licensing and maintenance for networks
InactiveUS20060036847A1Random number generatorsUser identity/authority verificationUnique identifierPhysical address
Owner:CISCO TECH INC
Method and system for verifying a client request
InactiveUS7293281B1Apparent advantageDigital data processing detailsUser identity/authority verificationClient-sideDistributed computing
Owner:IBM CORP
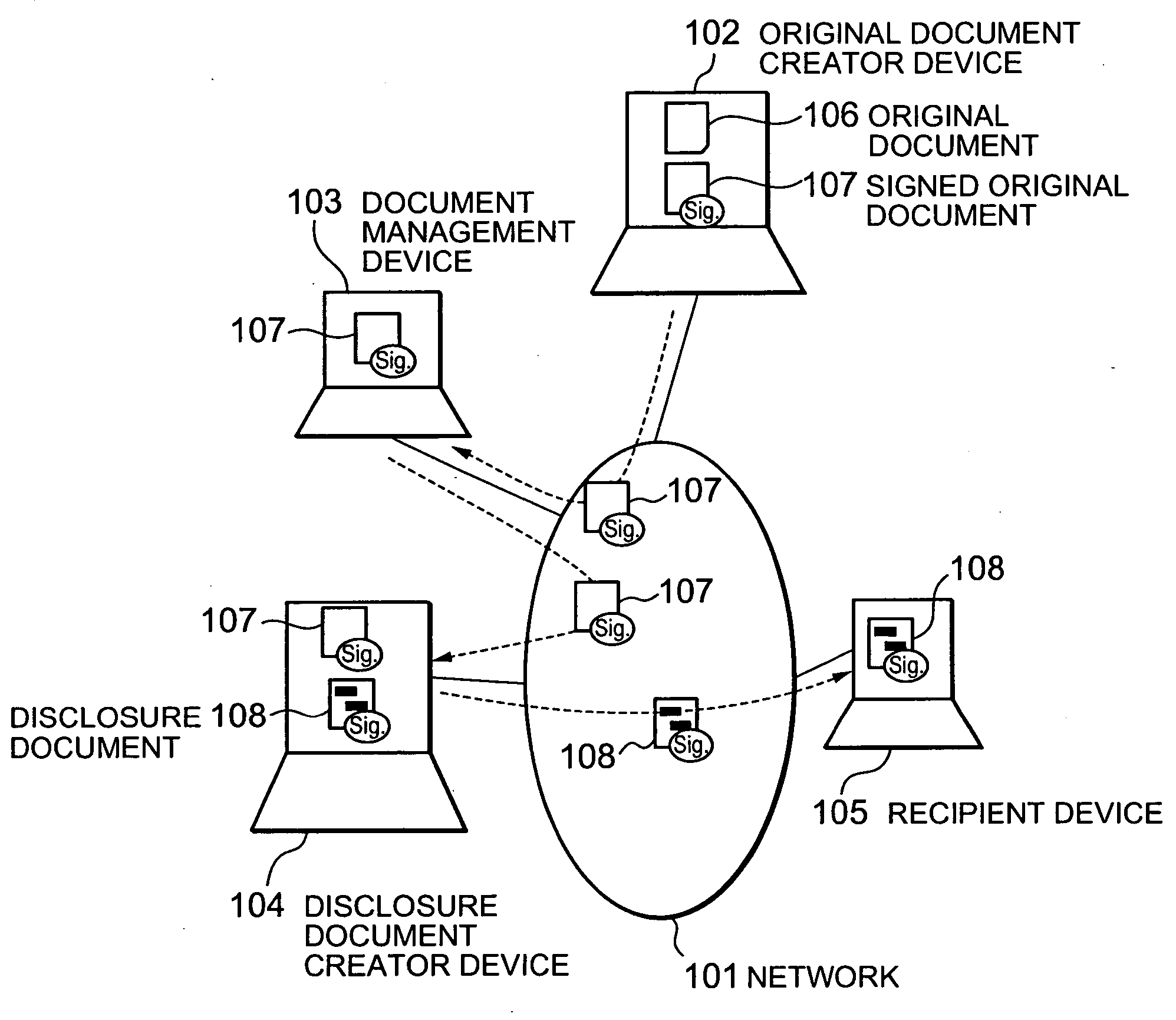
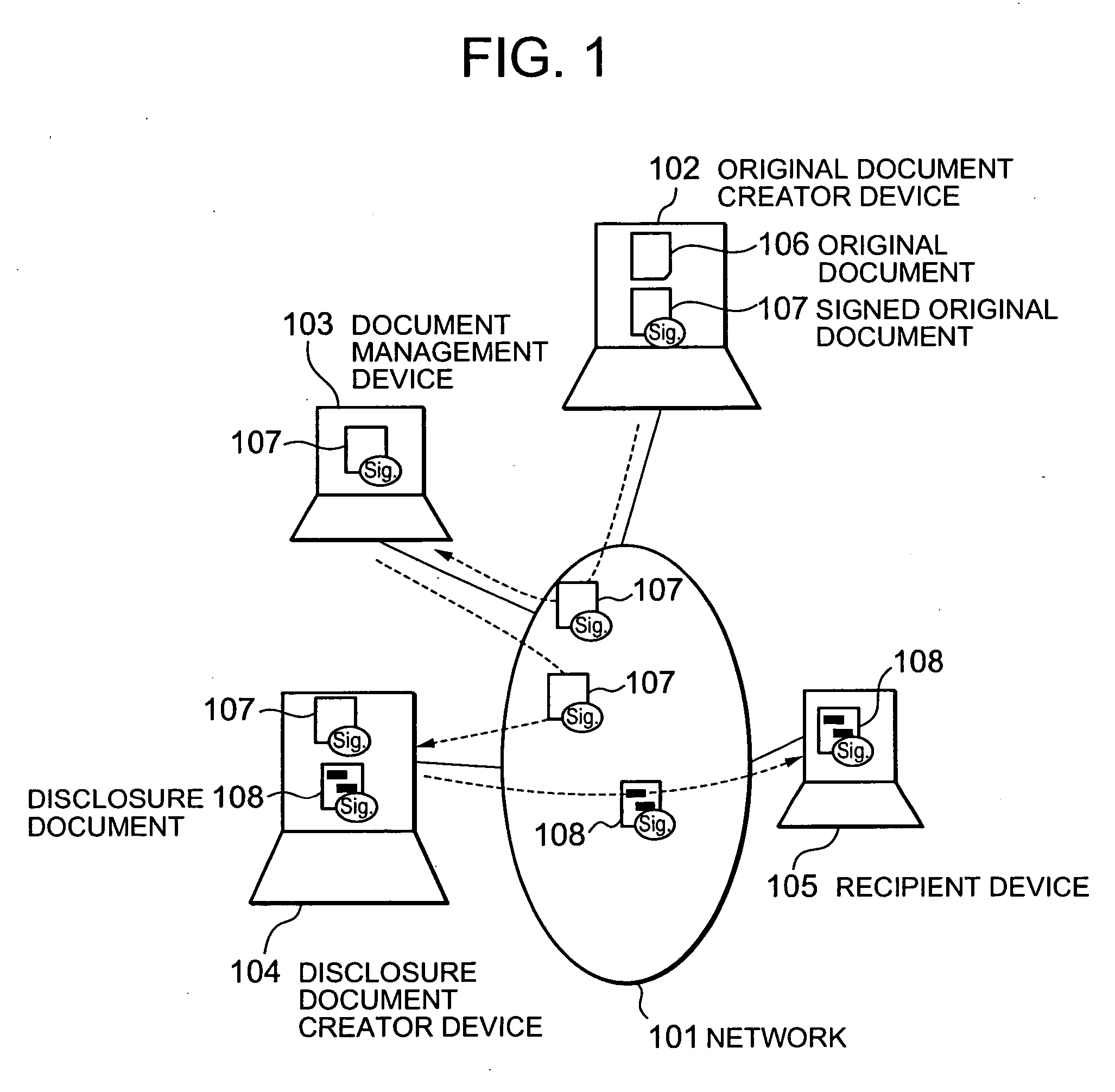
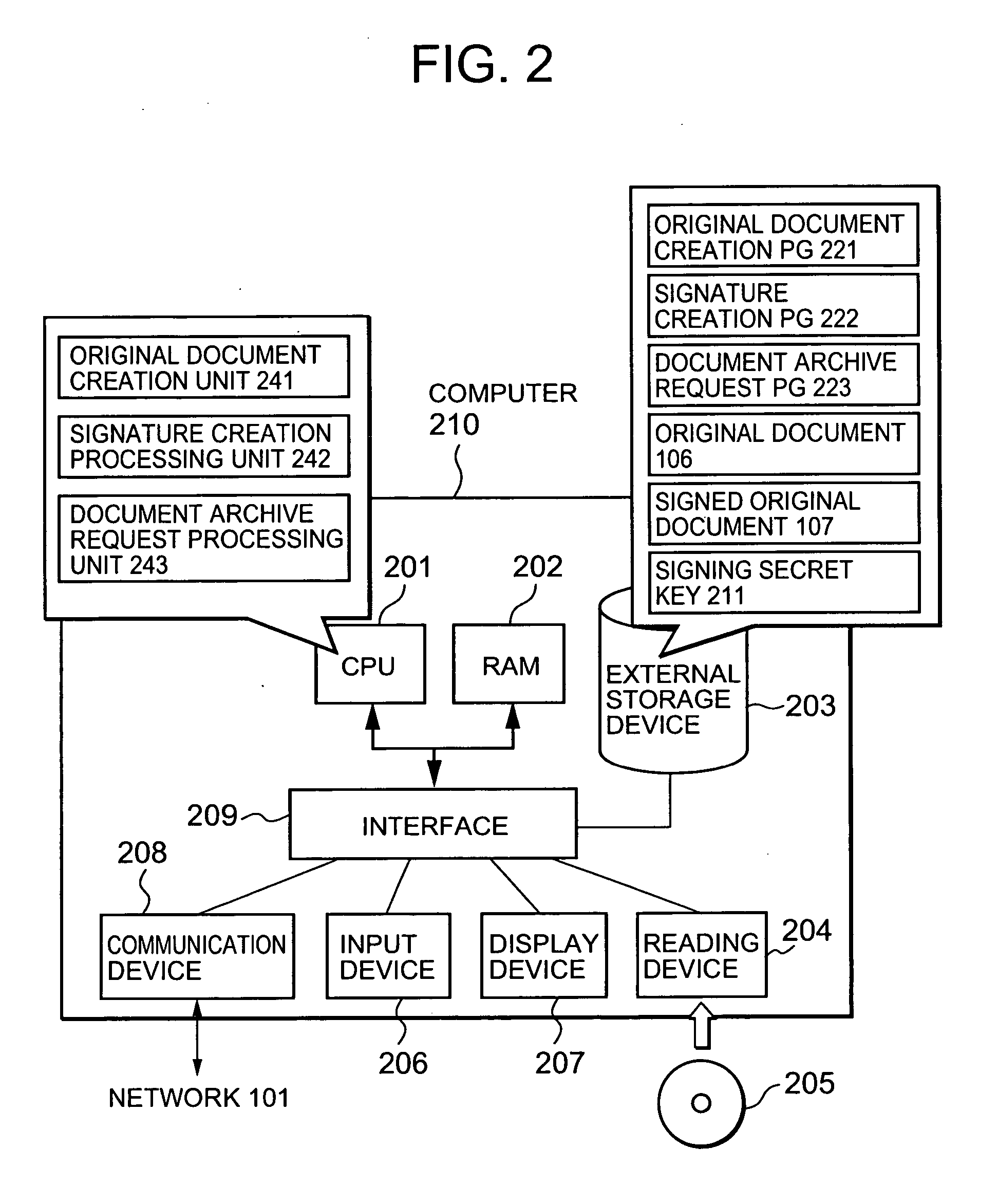
Electronic document authenticity assurance method and electronic document disclosure system
InactiveUS20050015600A1Verify authenticityUser identity/authority verificationUnauthorized memory use protectionPaper documentElectronic document
Owner:HITACHI LTD
Cargo theft prevention method and system
InactiveUS20050219037A1StampsKey distribution for secure communicationComputer hardwareCommunications system
Owner:HUANG TAO
Apparatus and Method for Variable Authentication Requirements
ActiveUS20120239950A1Volume/mass flow measurementUser identity/authority verificationState dependentAuthentication
Owner:LENOVO PC INT
Digital certificate safety lock device and digital certificate authentication system and method
InactiveCN102255730AImprove general performanceImprove applicabilityUser identity/authority verificationMicrocontrollerTablet computer
The invention relates to a digital certificate safety lock device and a digital certificate authentication system and method. The digital certificate safety lock device comprises a universal encryption and digital signature microcontroller, an audio plug and a first modulation and demodulation module, wherein the universal encryption and digital signature microcontroller is provided with an encryption and digital signature module and a storage for storing a digital certificate, a key of the digital certificate and encryption and decryption algorithms; and the first modulation and demodulation module is used for modulating data information from the encryption and digital signature module for transmitting through an MIC (Microphone) pole of the audio plug, demodulating a signal received from a first sound channel pole of the audio plug and transmitting the demodulated signal to the encryption and digital signature module. The digital certificate safety lock device is provided with a universal audio interface plug which has high university and adaptability and can support communication terminals such as mobile phones, tablet computers, PDAs (Personal Digital Assistants) or PCs (Personal Computers) and the like, with audio interfaces. Due to the functions of independent hardware signature, digital certificate encryption and the like, the security of application logon and transactions of Internet banks or enterprises can be ensured to the maximum extent.
Owner:吴沙林 +1
Controller regional network bus safety communication method, device and system
ActiveCN108965218AImprove securityReduce transmission overheadUser identity/authority verificationBus networksSecure communicationArea network
The present invention provides a controller regional network bus safety communication method, device and system which can effectively withstand attackers' eavesdropping, injection and attack replay. Agateway ECU (Electronic Control Unit) generates a random number and sends the random number to at least one CAN (Controller Area Network) bus ECU. A first CAN bus ECU obtains the random number sent by the gateway ECU and generates a first information authentication code based on secret keys of a first CAN identifier, the random number sent by the gateway ECU, a counting value of the first CAN identifier and data of a first CAN message. The first CAN bus ECU performs encryption operation based on the secret keys of the first CAN identifier and a second CAN message to obtain a first encryptionoperation result and perform equal length encryption operation for the first encryption operation result, the first information authentication code, the counting value of the first CAN identifier andthe data of the first CAN message so as to obtain the first CAN message with encryption authentication and send the first CAN message with encryption authentication.
Owner:HUAWEI TECH CO LTD
Method for the routing and control of packet data traffic in a communication system
InactiveUS20080198861A1Improve scalabilityEqually distributedDigital data processing detailsUser identity/authority verificationCommunications systemNetwork packet
Owner:CORE WIRELESS LICENSING R L
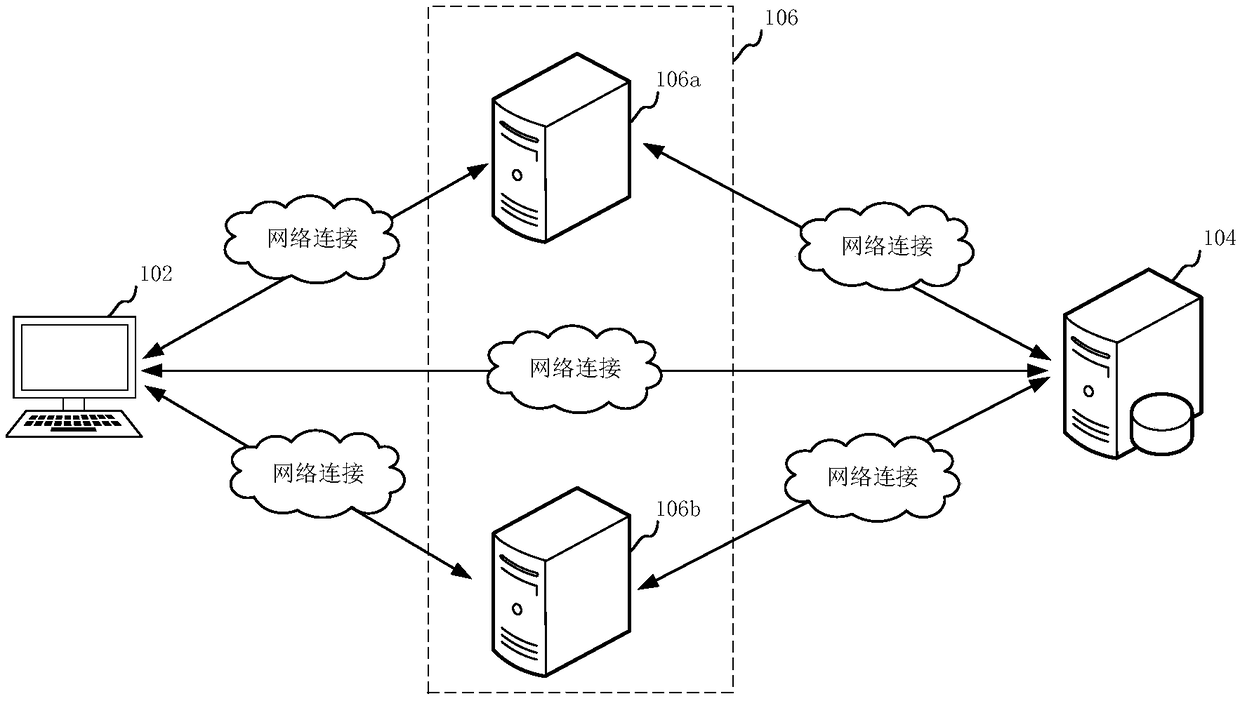
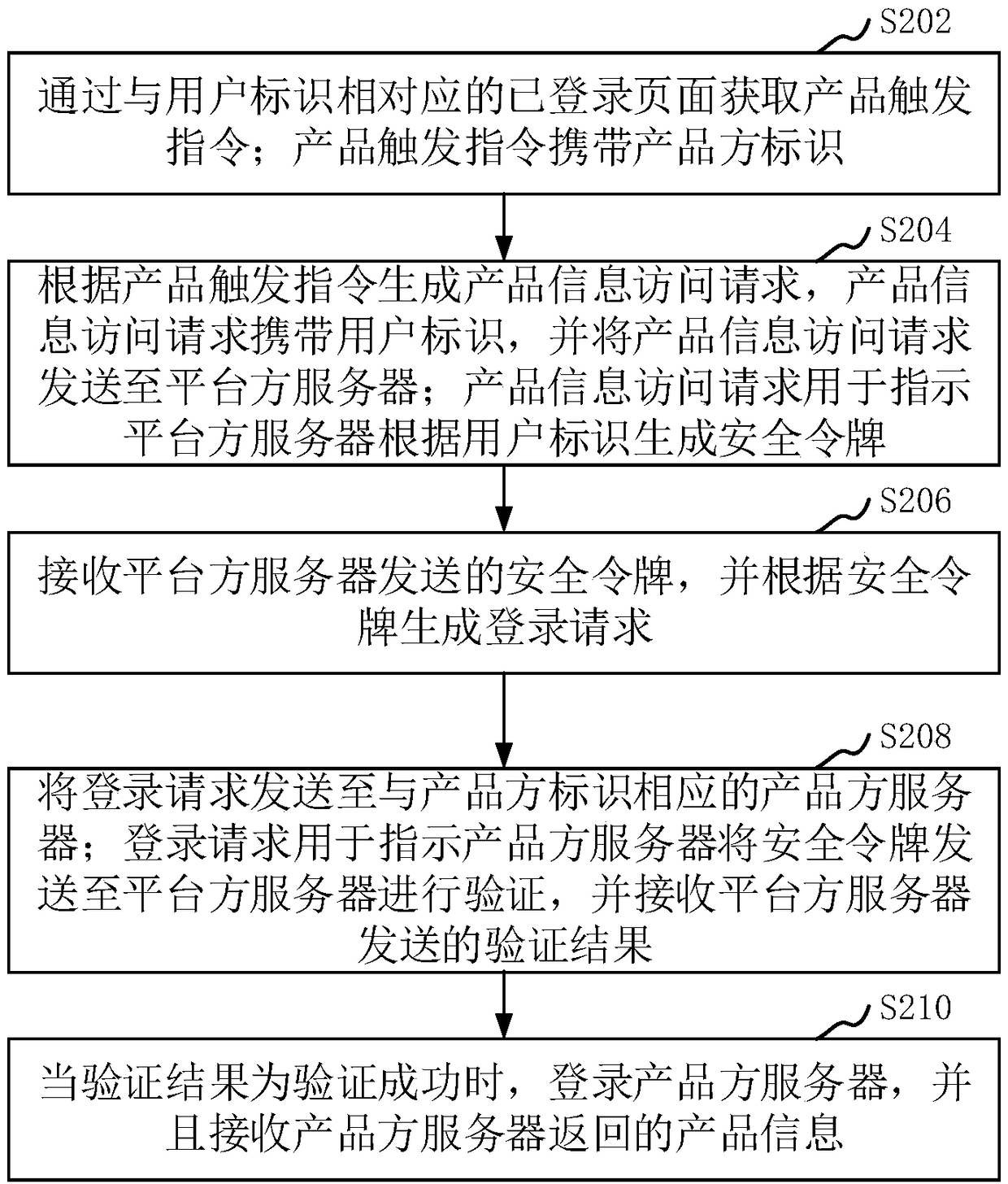
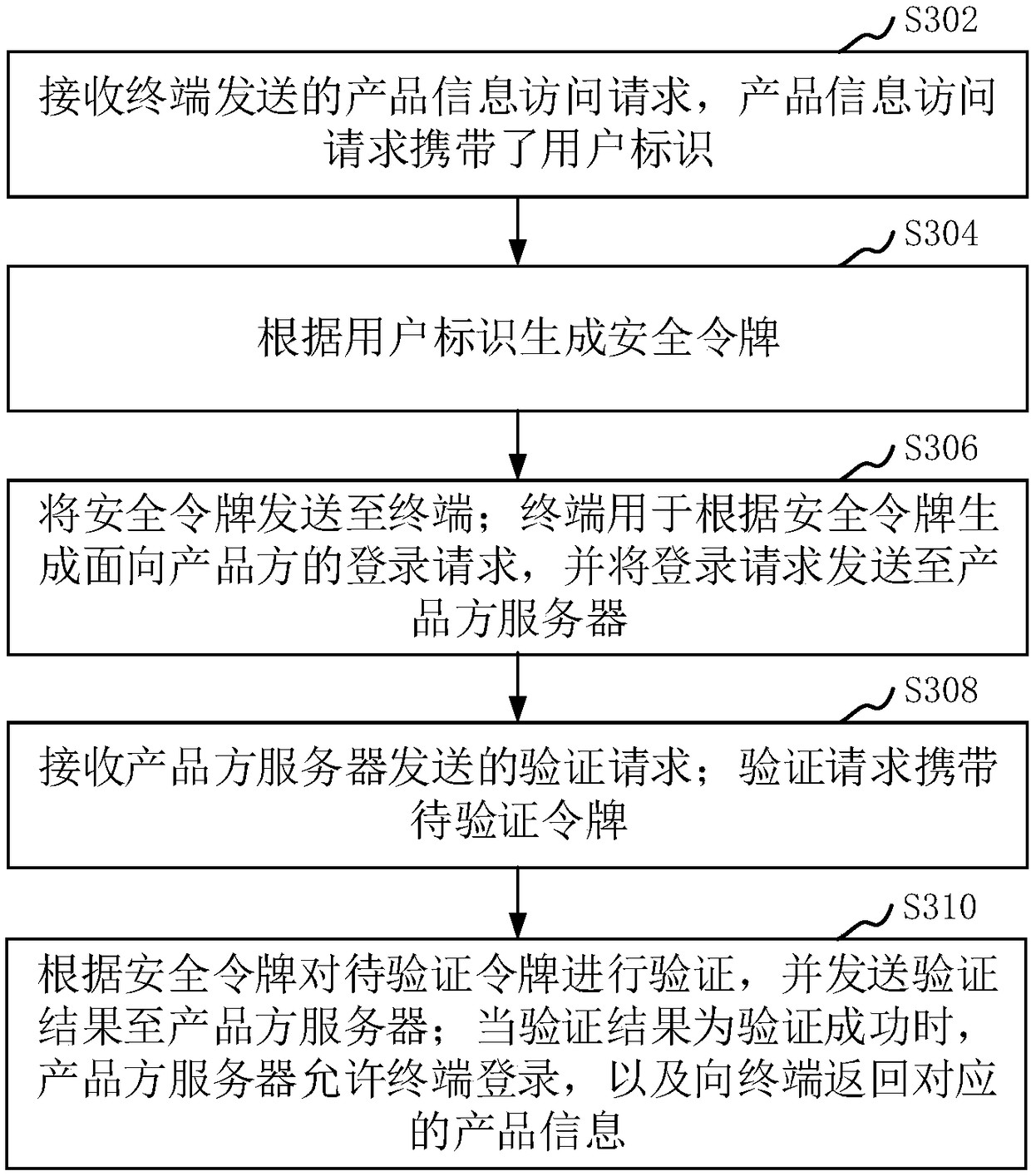
Login method and system, computer device and storage medium
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
User authentication method
ActiveUS8838973B1Digital data processing detailsUser identity/authority verificationClient-sideUser authentication
Owner:GOOGLE LLC
System and method for authentication
ActiveUS20050081064A1Digital data processing detailsUser identity/authority verificationAuthentication systemRead-only memory
Owner:TREK 2000 INT
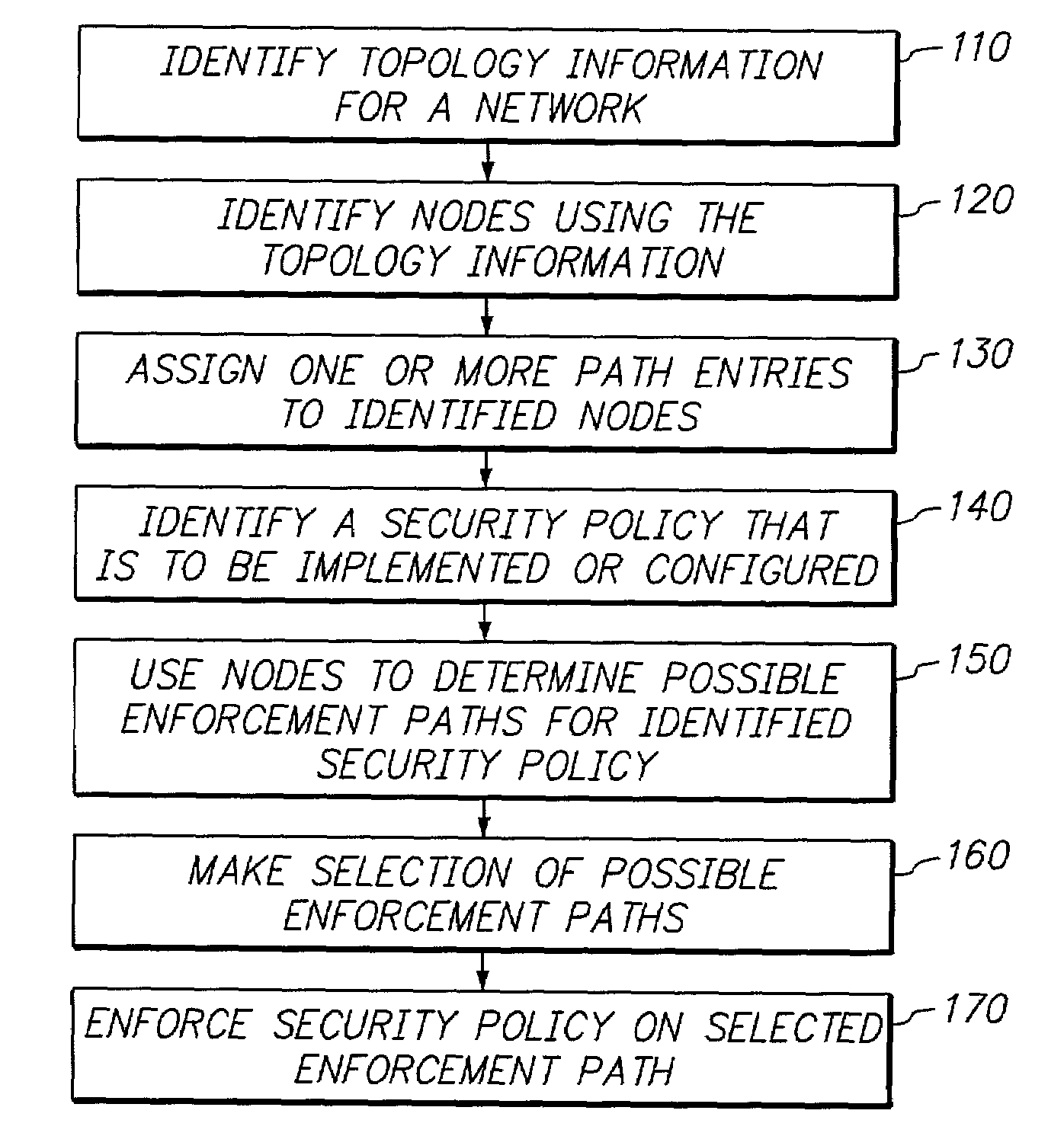
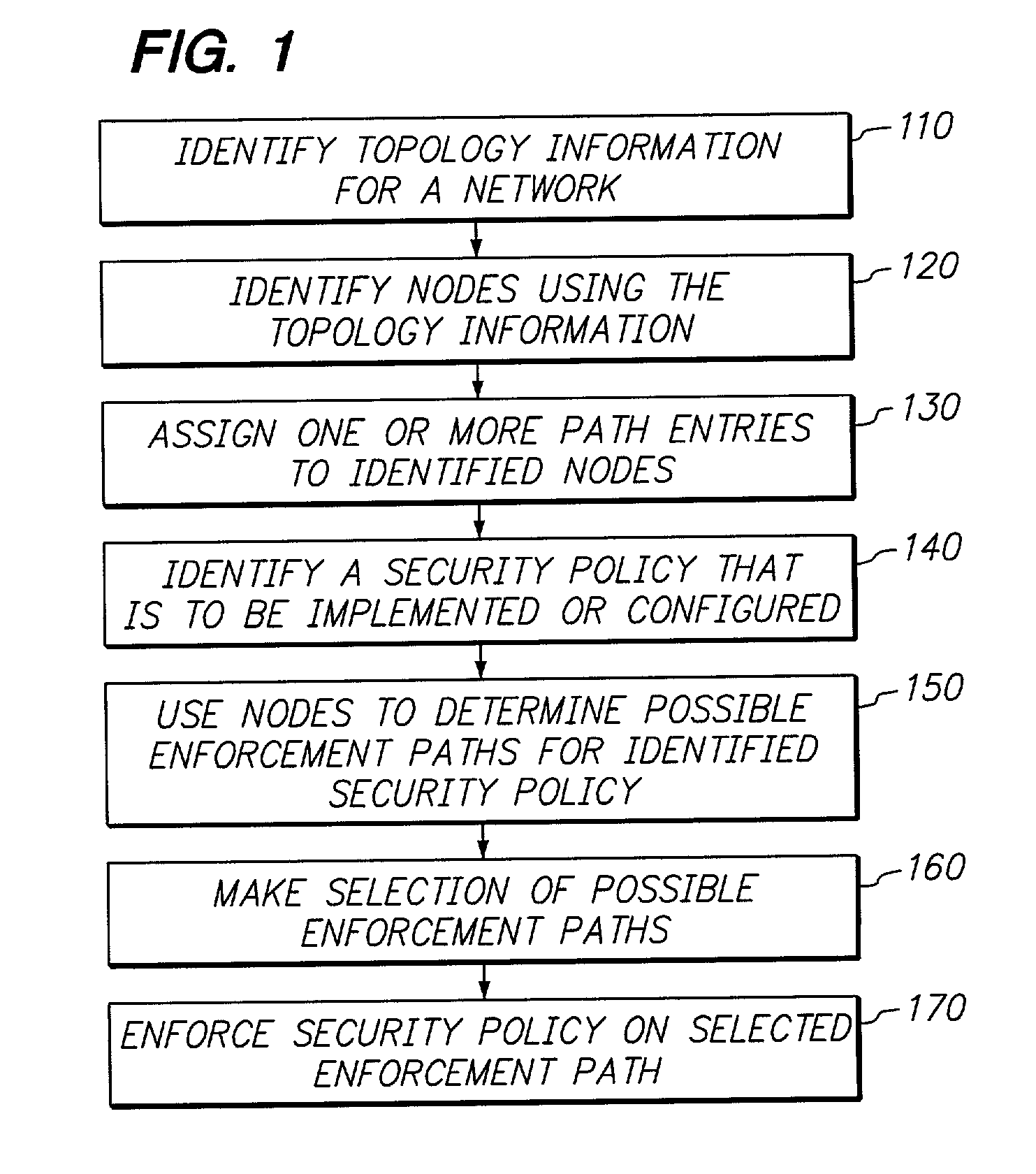
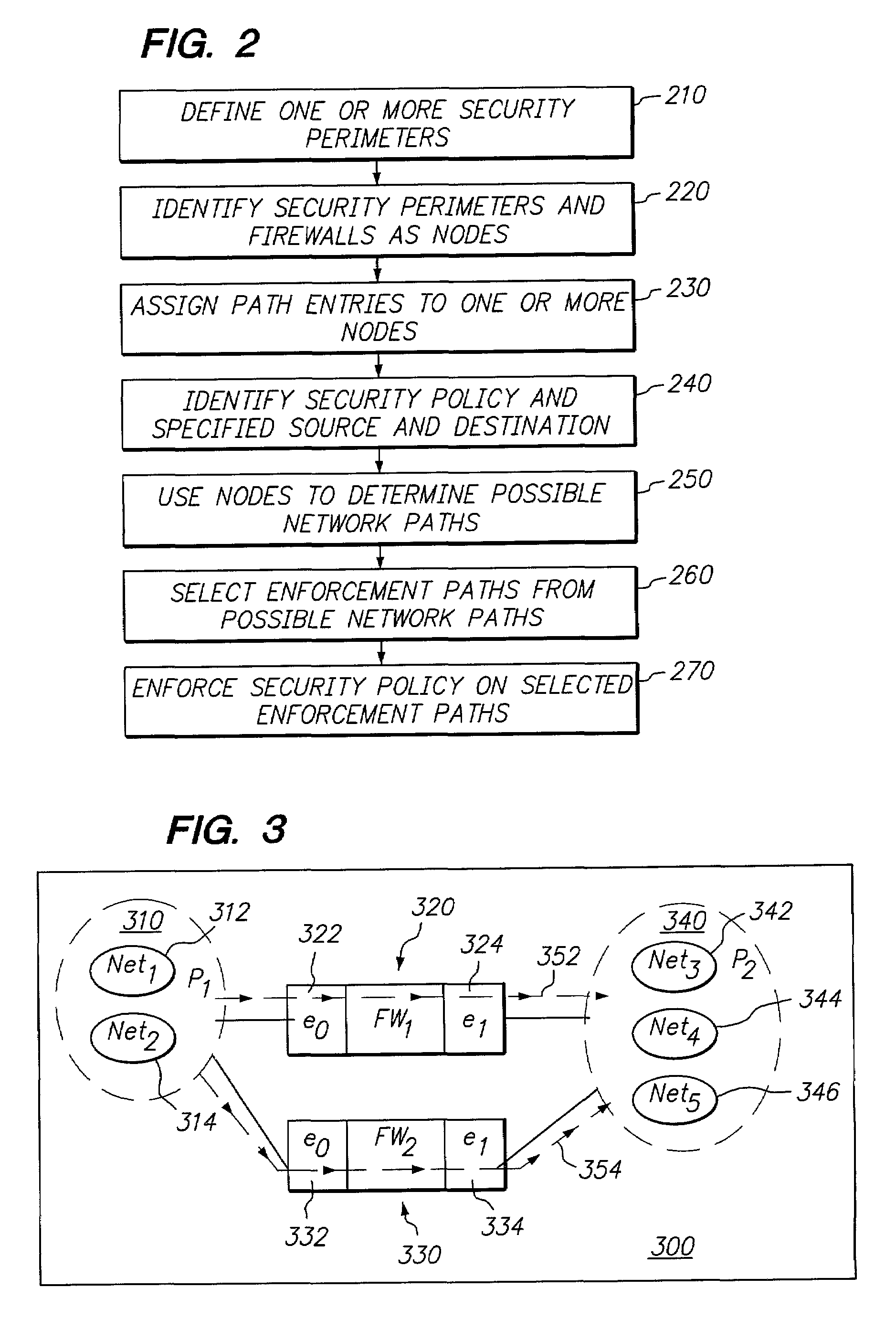
Simplifying the selection of network paths for implementing and managing security policies on a network
InactiveUS7143283B1Digital data processing detailsUser identity/authority verificationSecurity policyDistributed computing
Owner:CISCO TECH INC
Tunable encryption system
InactiveUS20100095127A1Communication securityUser identity/authority verificationSecure communicationApplication server
Owner:IBM CORP
Method for updating a firmware component and device of measurement and control technology
ActiveUS20170293484A1The encryption method is simpleLess resourcesProgramme controlMemory architecture accessing/allocationEncryptionAuthentication
Owner:ENDRESSHAUSER CONDUCTA GMBHCO
Authentication system for mobile terminal having electronic money function
InactiveUS20060160525A1Reduce usageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPasswordComputer terminal
Owner:FUJIFILM CORP
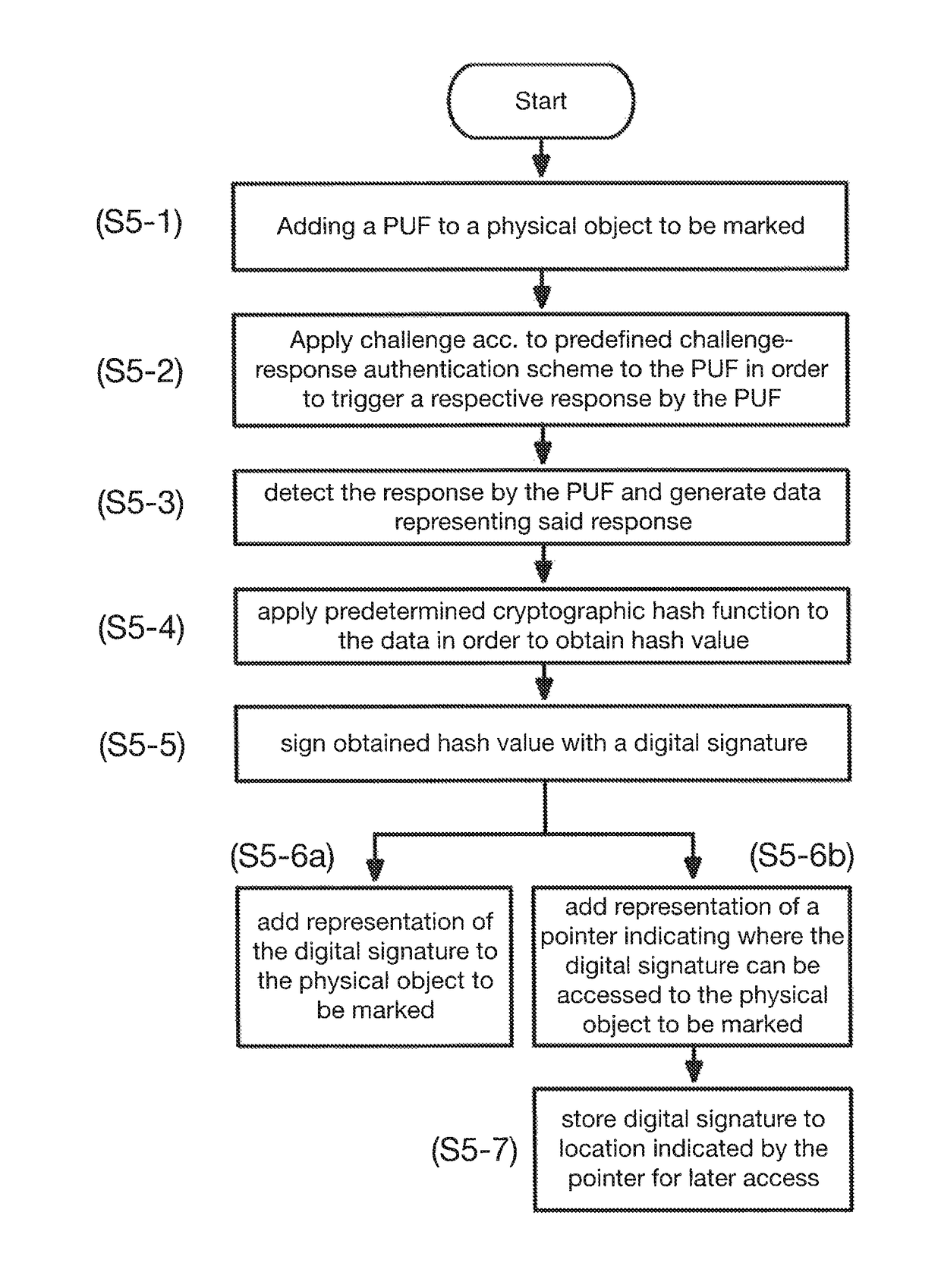
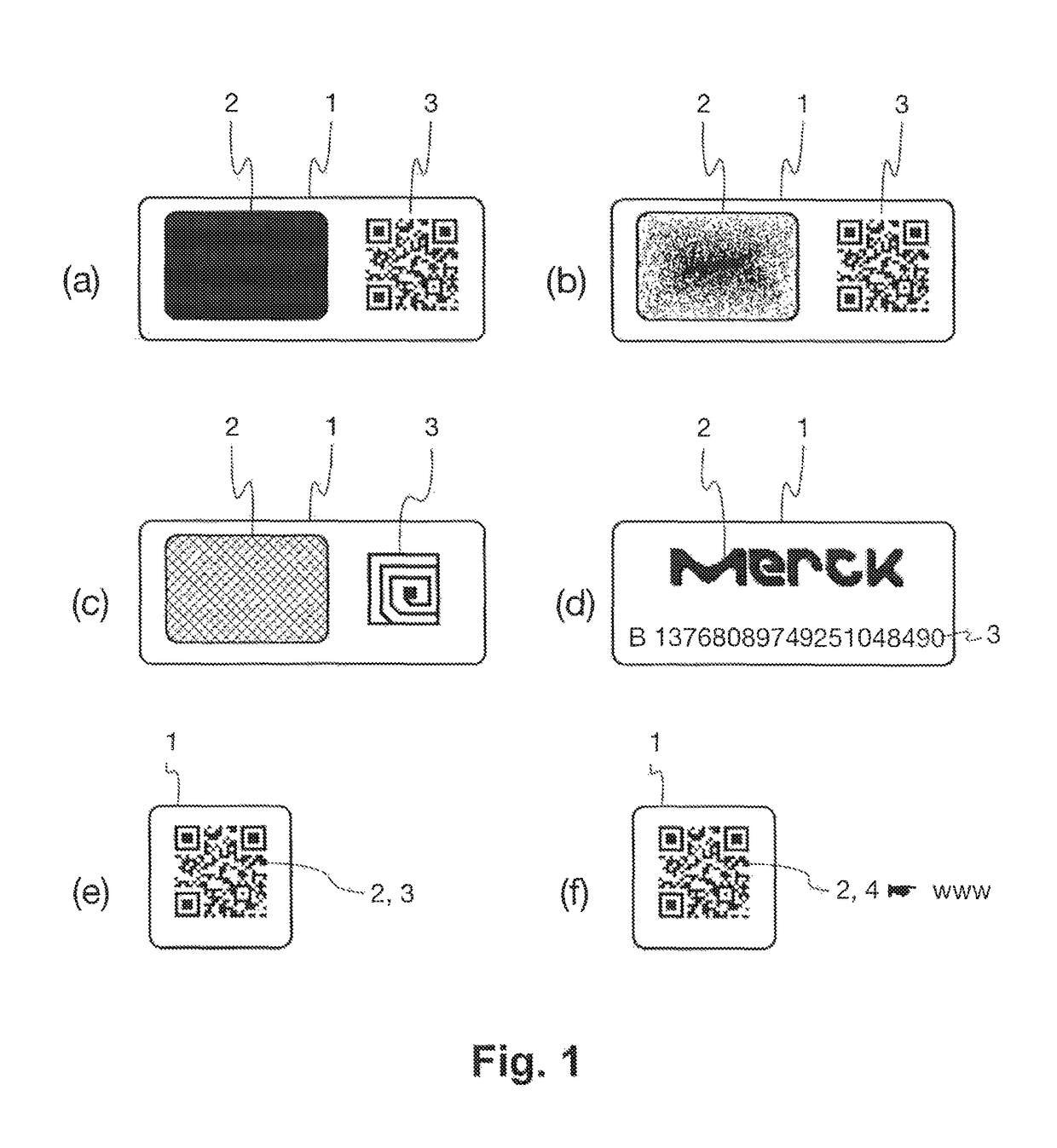
Composite security marking
ActiveUS10002362B1User identity/authority verificationCharacter and pattern recognitionCryptographic hash functionDigital signature
Owner:MERCK PATENT GMBH
Access authentication method of wireless mesh network
InactiveCN101494862AUser identity/authority verificationNetwork topologiesAuthorizationManagement system
Owner:BEIJING UNIV OF TECH
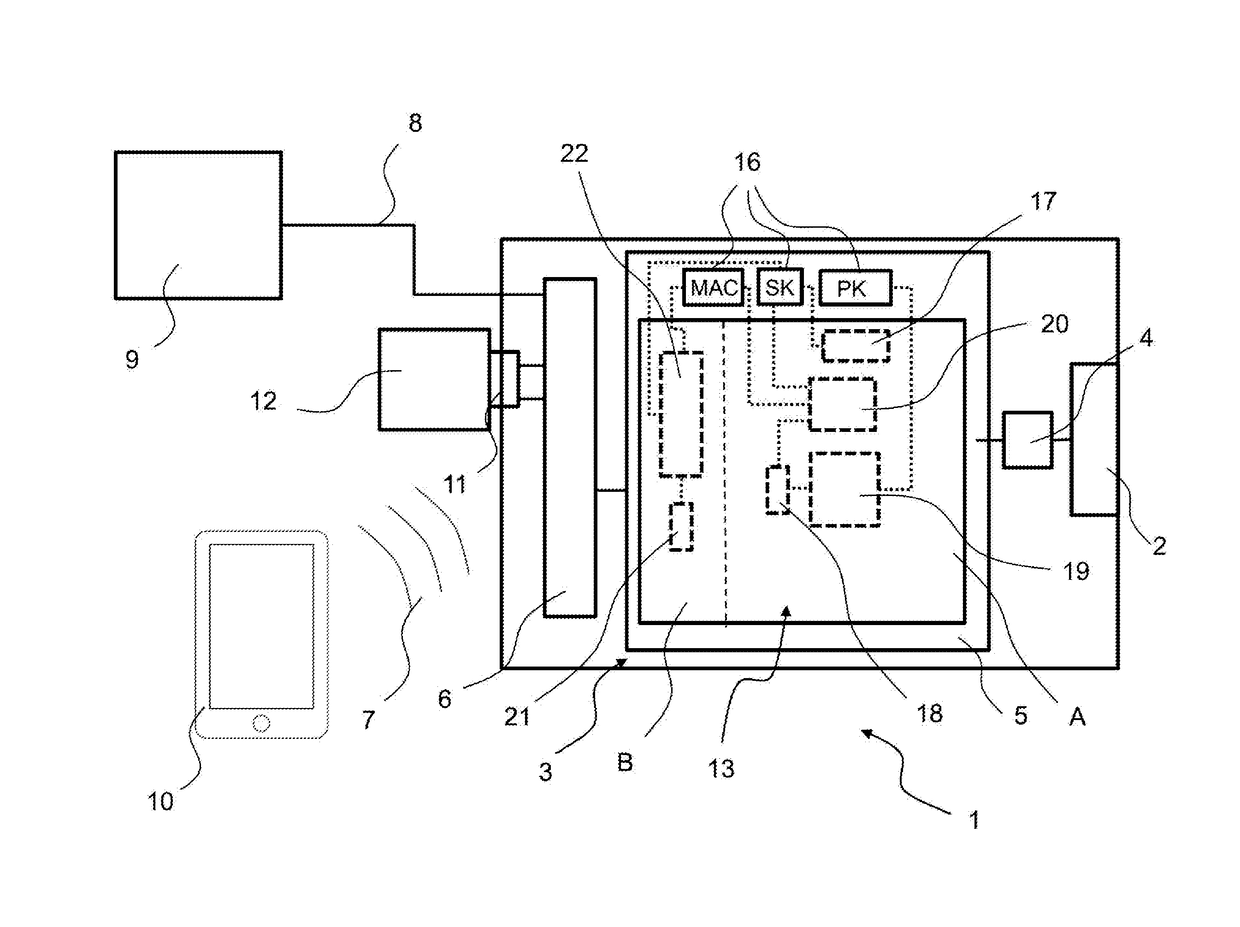
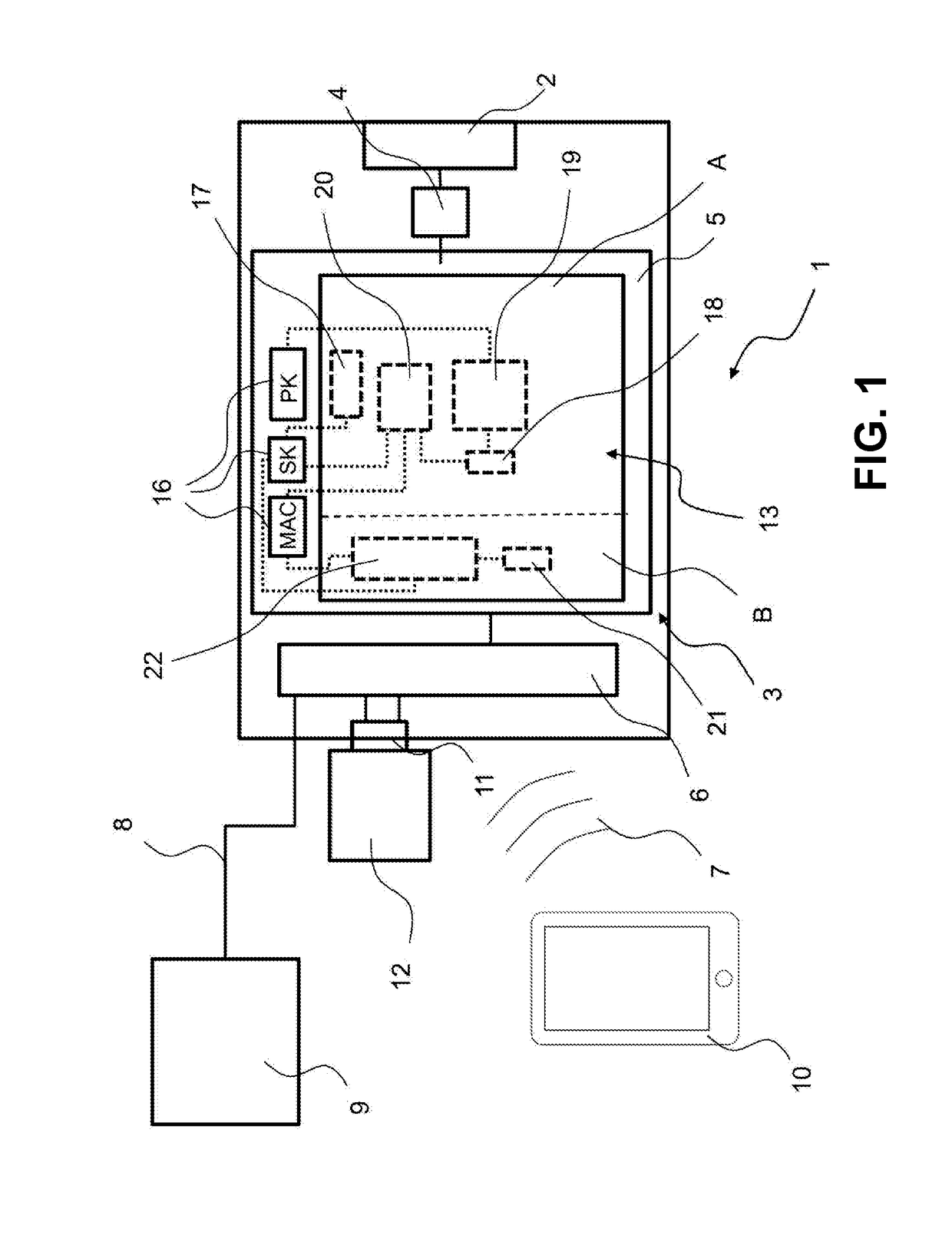
Physically unclonable function (PUF) circuits employing multiple puf memories to decouple a puf challenge input from a puf response output for enhanced security
InactiveUS20190342106A1User identity/authority verificationDigital storagePhysical unclonable functionChallenge response
Physically unclonable function (PUF) circuits employing multiple PUF memories to decouple a PUF challenge input from a PUF response output for enhanced security. The PUF circuit includes a PUF challenge memory and a PUF response memory. In response to a read operation, the PUF challenge memory uses a received PUF challenge input data word to address PUF challenge memory arrays therein to generate a plurality of intermediate PUF challenge output data words. The PUF response memory is configured to generate a second, final PUF response output data word in response to intermediate PUF challenge output data words. In this manner, it is more difficult to learn the challenge-response behavior of the PUF circuit, because the PUF challenge input data word does not directly address a memory array that stores memory states representing final logic values in the PUF response output data word.
Owner:QUALCOMM INC
Apparatus and method for authentication and method for registering a person
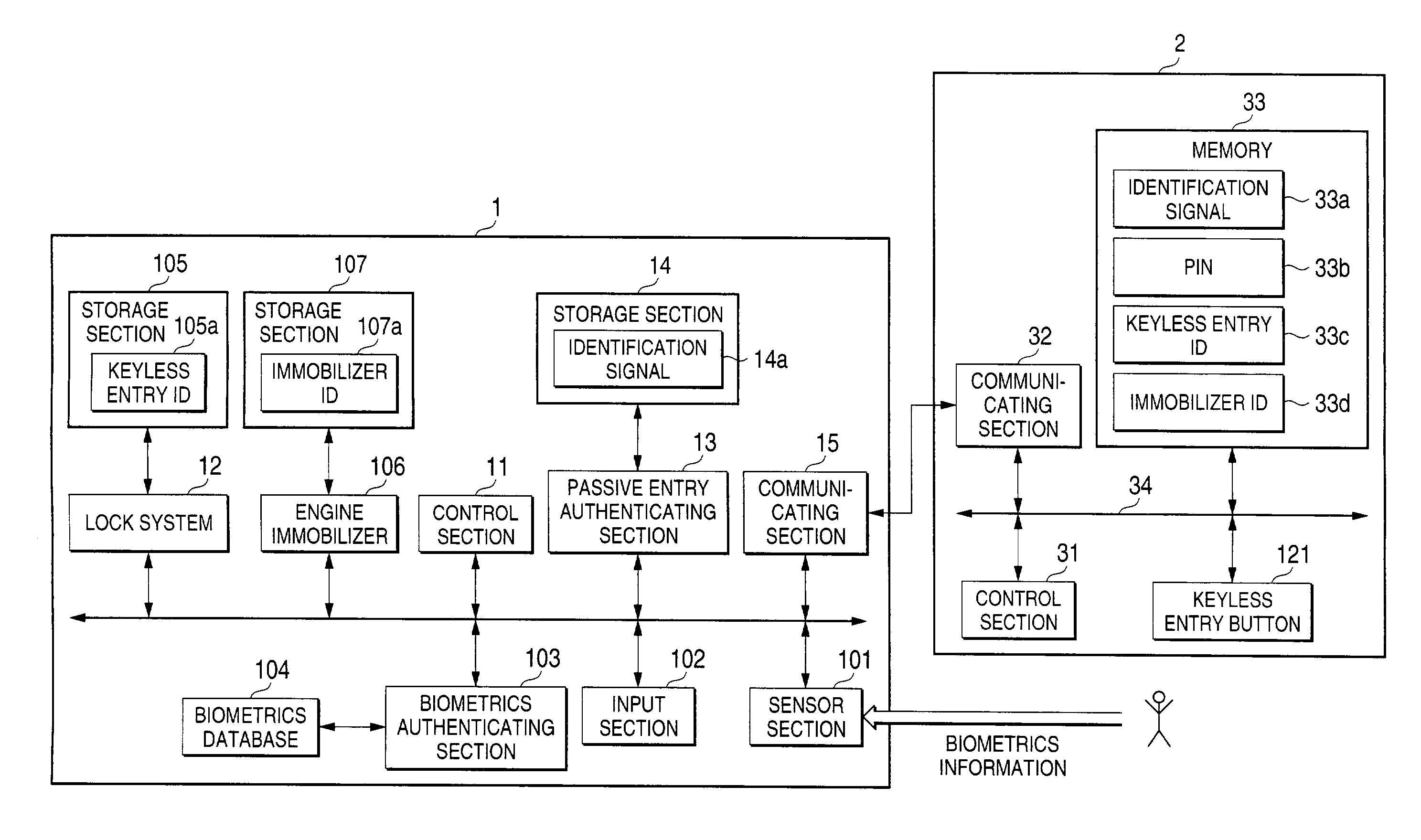
InactiveUS7185198B2Positively preventingGood effectDigital data processing detailsUser identity/authority verificationComputer hardwareBiometrics
Wrongful authentication process is prevented. A passive entry authenticating section compares an identification signal sent from a portable unit with an identification signal previously stored in a storage section. A biometrics authenticating section compares the biometrics information of a user inputted through a sensor section with the biometrics information registered in a biometrics database. A control section authenticates an authorized user when there is agreement in both the identification-signal comparison result and the biometrics-information comparison result, and controls a lock system to unlock the door lock of the automobile.
Owner:OMRON AUTOMOTIVE ELECTRONICS CO LTD
Secure wireless communication
ActiveUS20090103728A1Unauthorised/fraudulent call preventionDigital data processing detailsHash-based message authentication codeCryptographic protocol
Owner:ALCATEL LUCENT SAS
Granting an access to a computer-based object
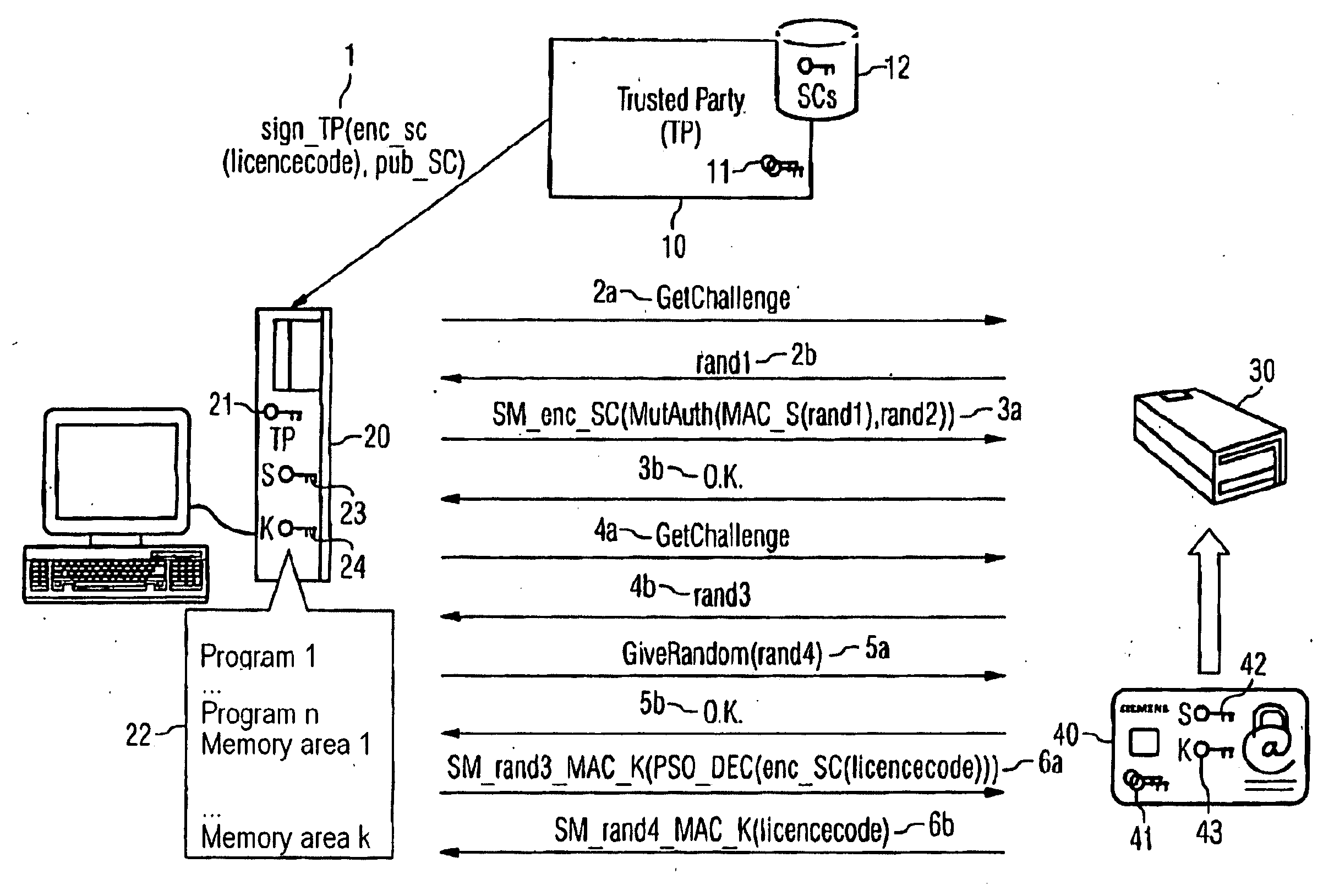
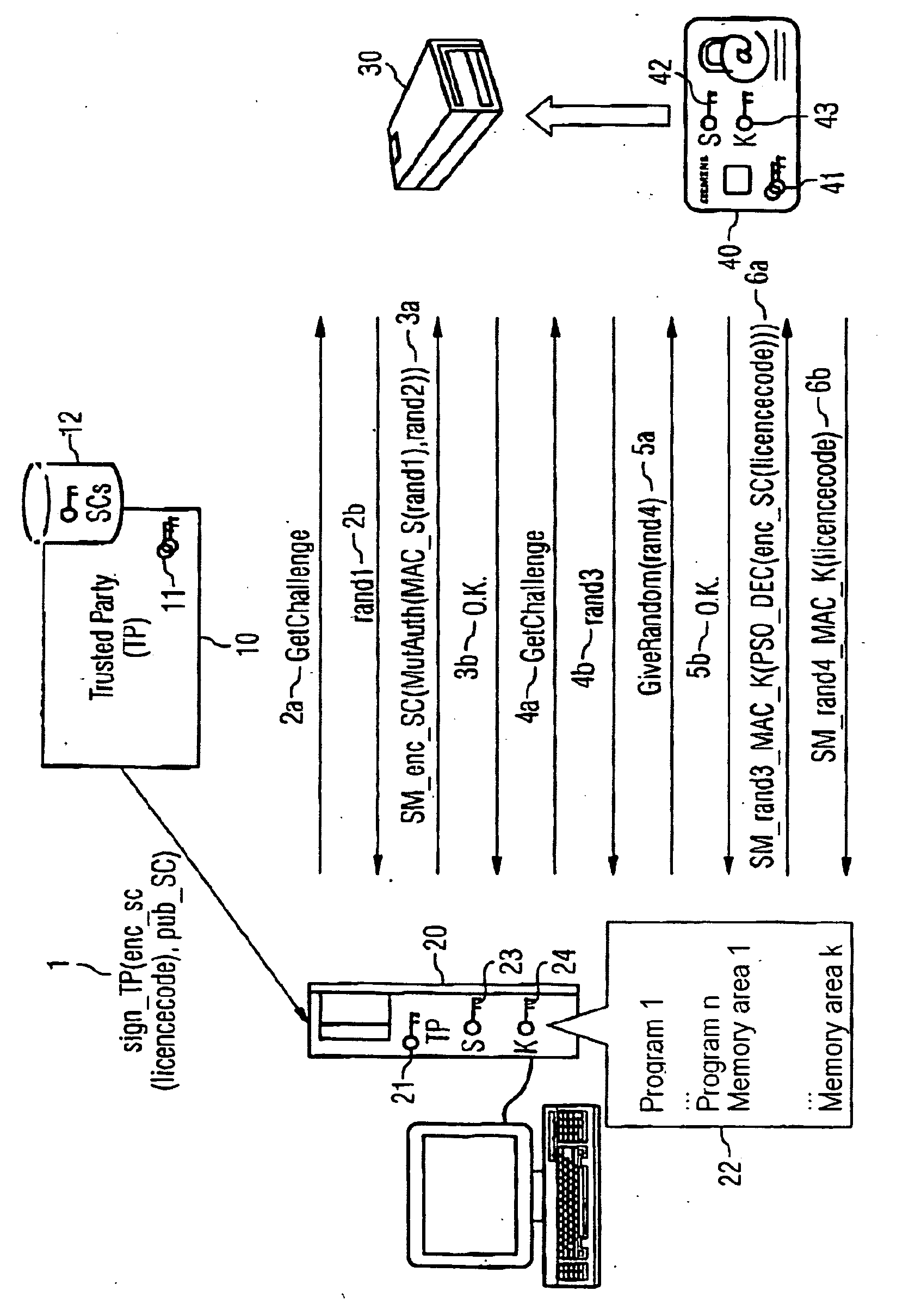
InactiveUS20060272004A1Improve protectionDigital data processing detailsUser identity/authority verificationComputer basedProgram code
Owner:SIEMENS AG
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap