Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5 results about "Attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer and computer networks an attack is any attempt to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset.
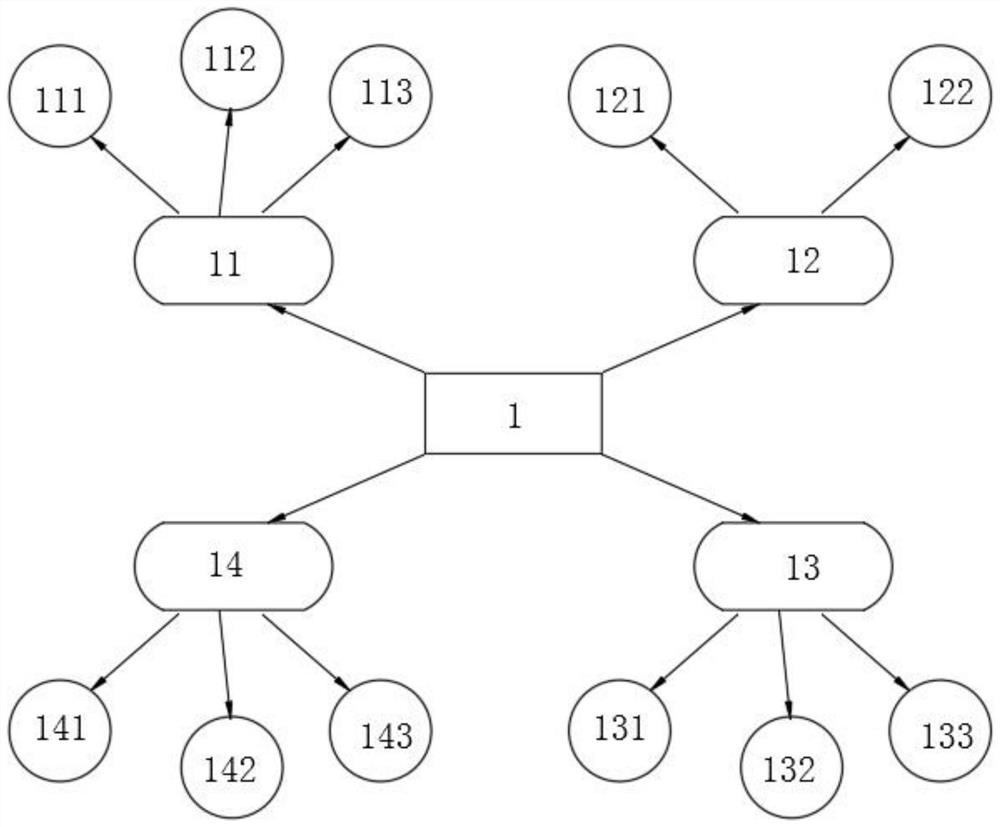
Industrial control safety auditing system and method based on artificial intelligence
ActiveCN112437041AImprove securityMeet industry compliance audit requirementsTransmissionTotal factory controlInformation transmissionAttack
Owner:北京珞安科技有限责任公司
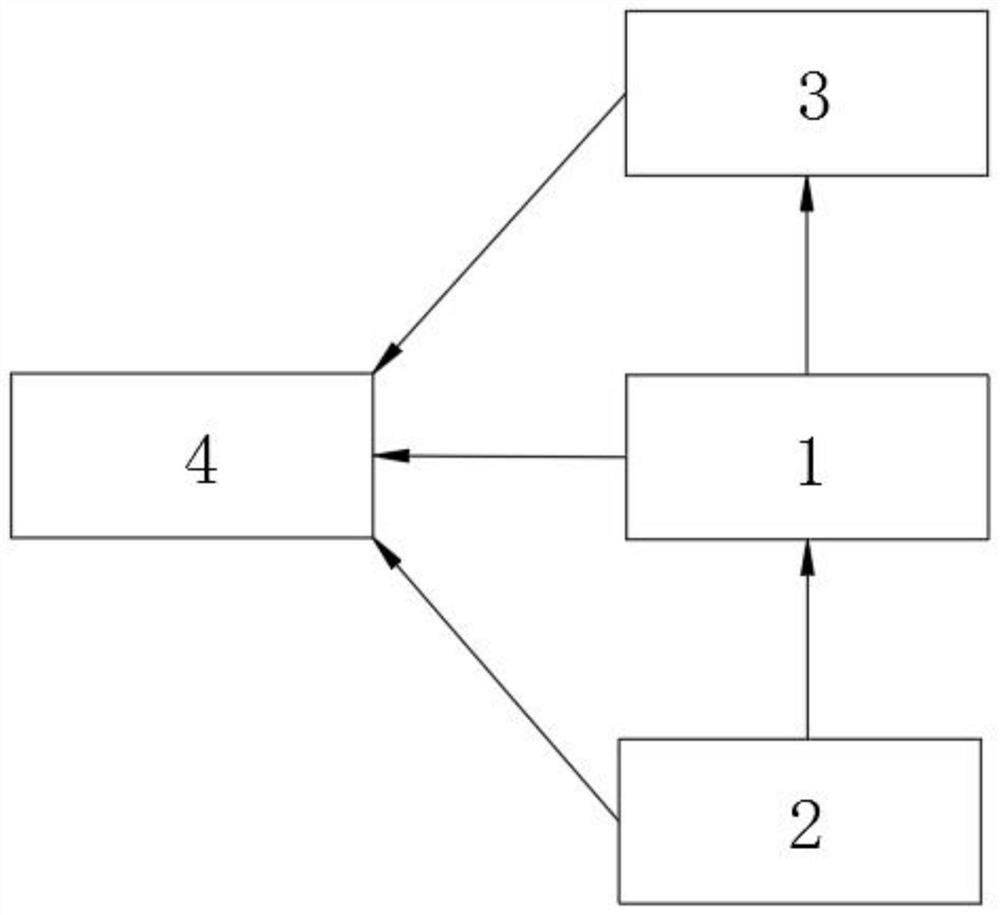
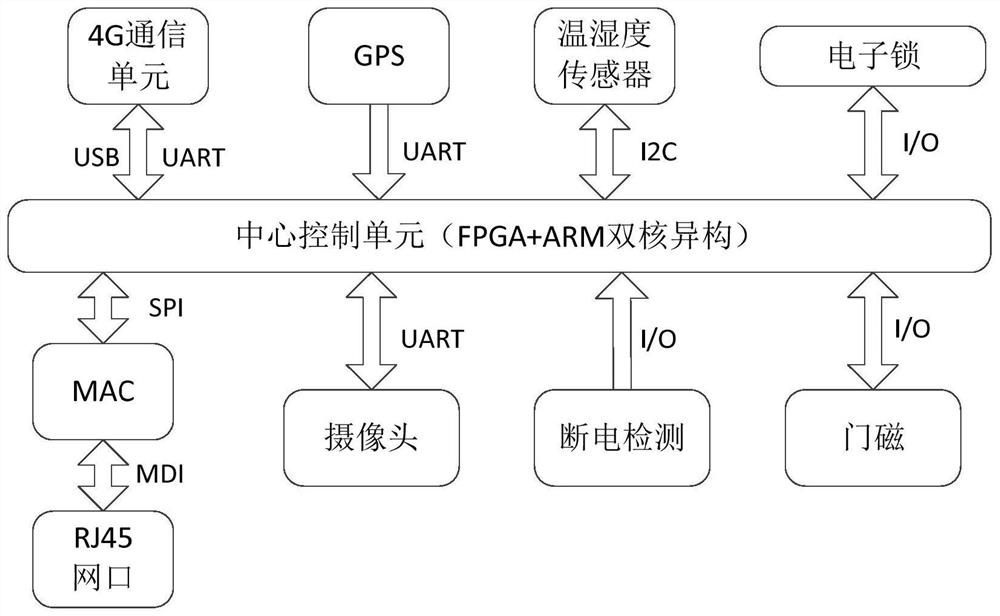
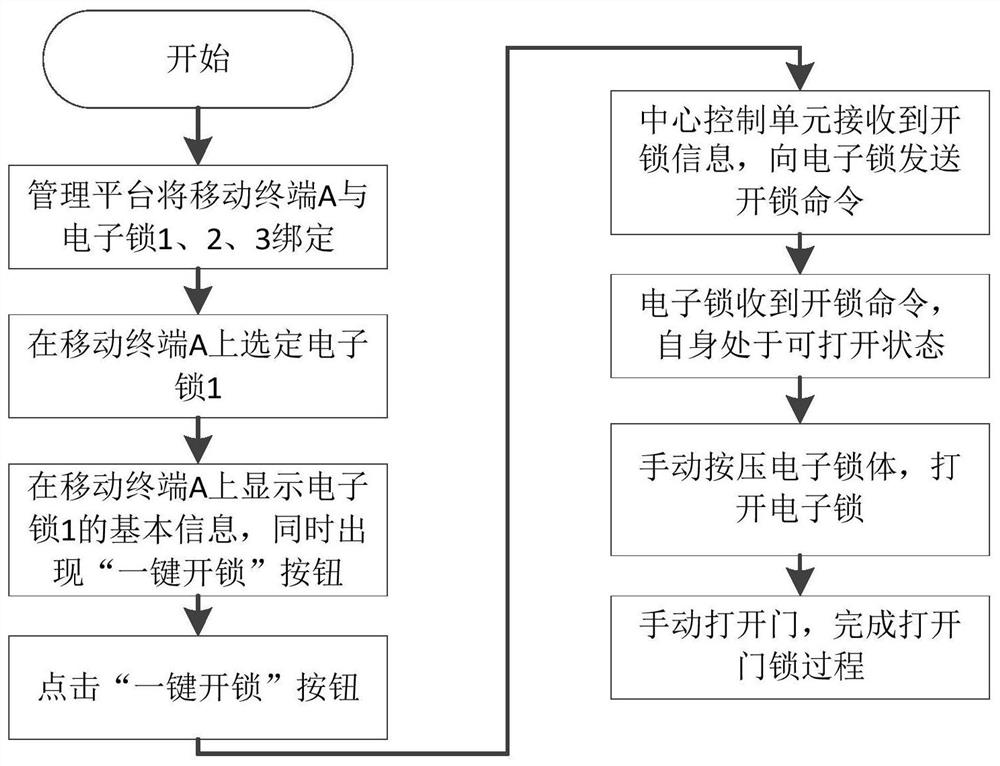
Intelligent door lock system capable of automatically judging abnormal state of door lock
ActiveCN112150672AAchieve protectionEasy to implementIndividual entry/exit registersComputer hardwareAttack
Owner:NANJING LES CYBERSECURITY & INFORMATION TECH RES INST CO LTD
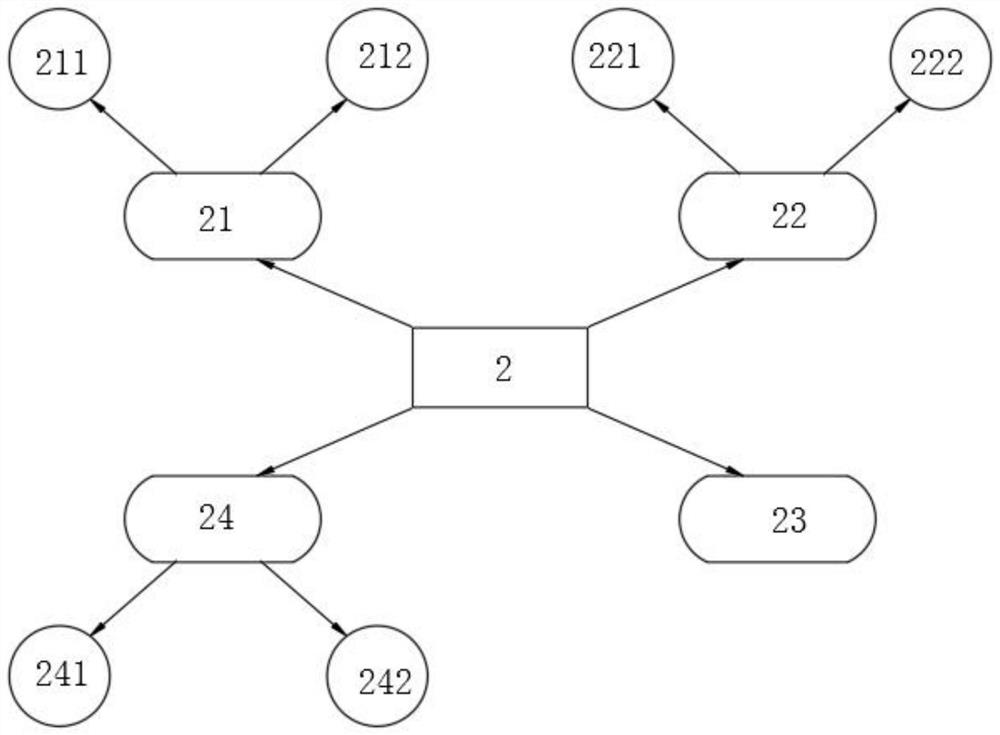
CSRF attack protection method and device
ActiveCN112866265ASolve the attack problemRelieve pressureUser identity/authority verificationThird partyInternet privacy
The present invention provides a CSRF attack protection method and device. The background server generates the token under the condition that the user request does not carry the token and writes the generated token into the browser cookie and the page request, and the token does not need to be stored in the background server, so that the pressure of the background server is reduced. When the user sends the user request again, the front-end preset script is triggered to run to write the token in the browser cookie and the page request into the user request, the background server realizes CSRF verification by judging whether the cookie in the user request is the same as the token in the parameter or not due to the fact that the browser cookie cannot be captured by a third party, the verification logic for binding the token with the user does not need to be added, and therefore, the CSRF attack problem can be simply and effectively solved.
Owner:HUNAN HAPPLY SUNSHINE INTERACTIVE ENTERTAINMENT MEDIA CO LTD
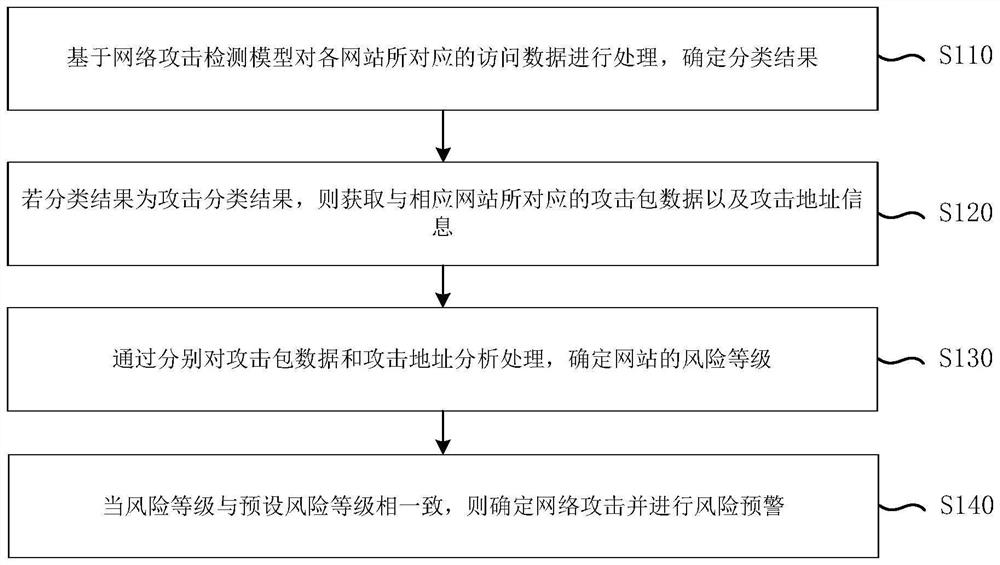
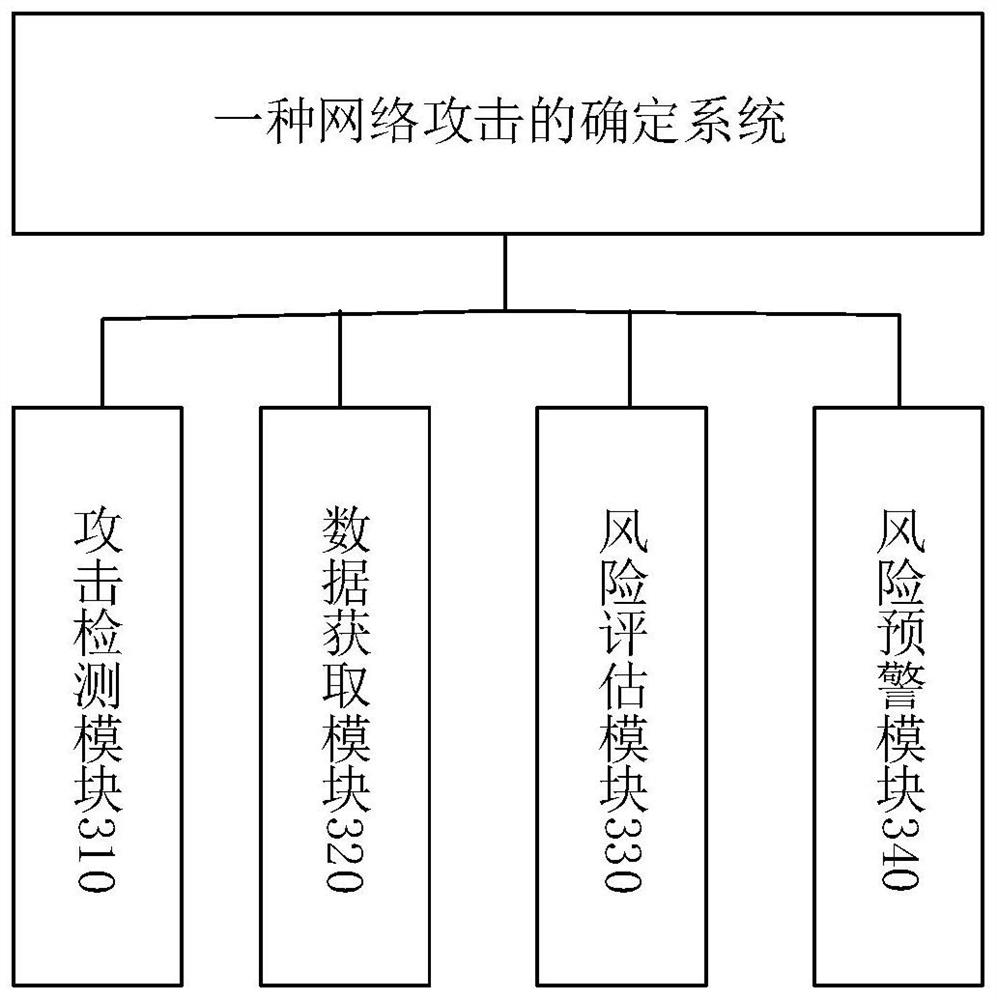
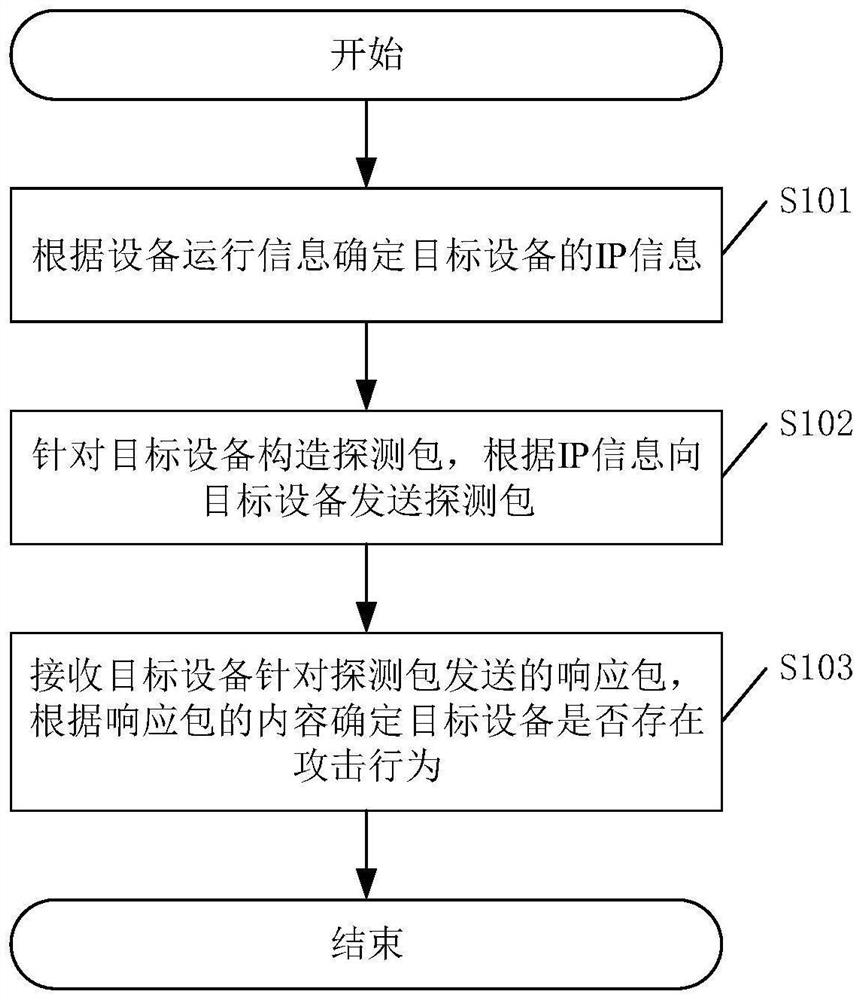
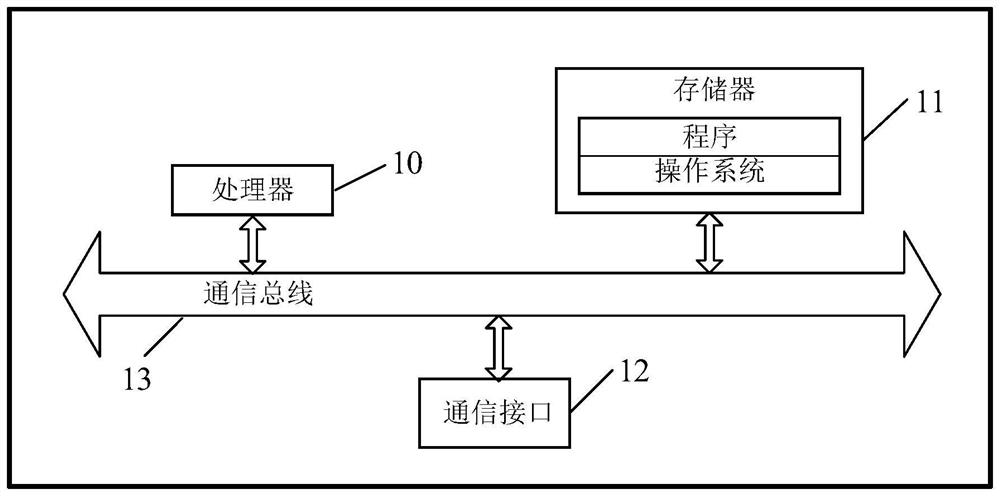
Network attack determination method and system, electronic equipment and storage medium
Owner:EVERSEC BEIJING TECH
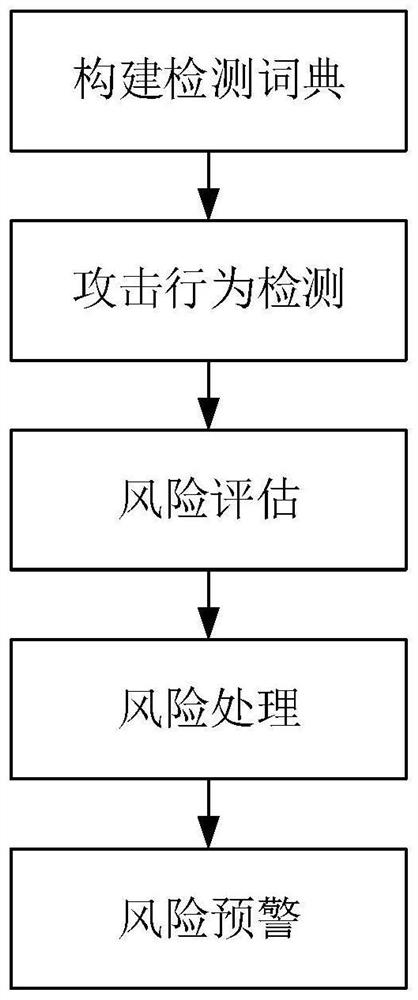
Attack identification method and device and related equipment
PendingCN114363059AEasy to detectAchieving identifiabilitySecuring communicationComputer networkAttack
Owner:SANGFOR TECH INC
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap