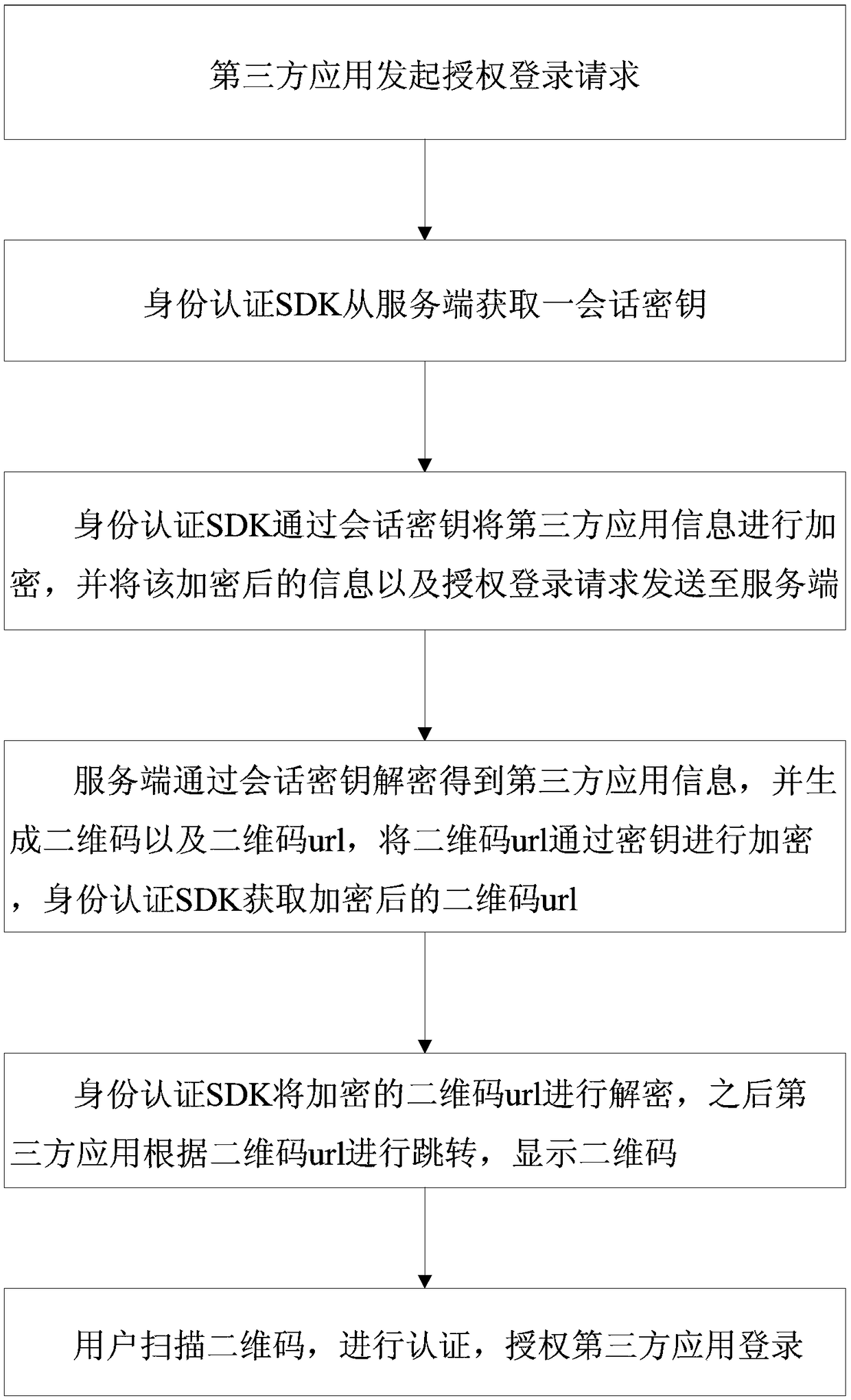
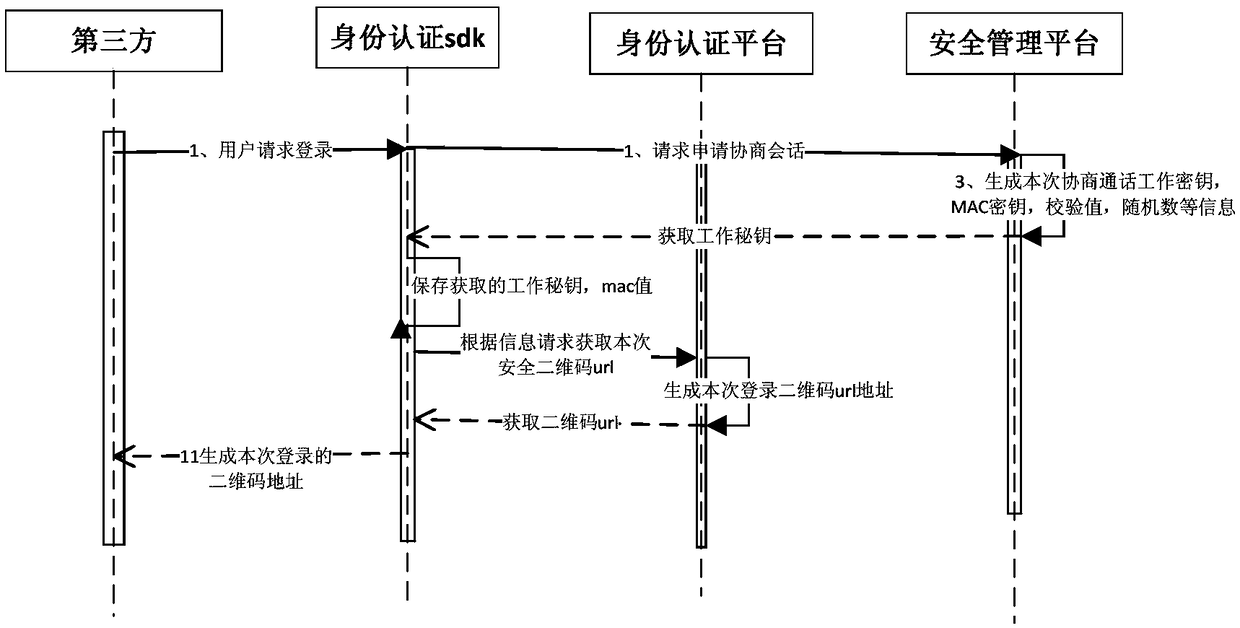
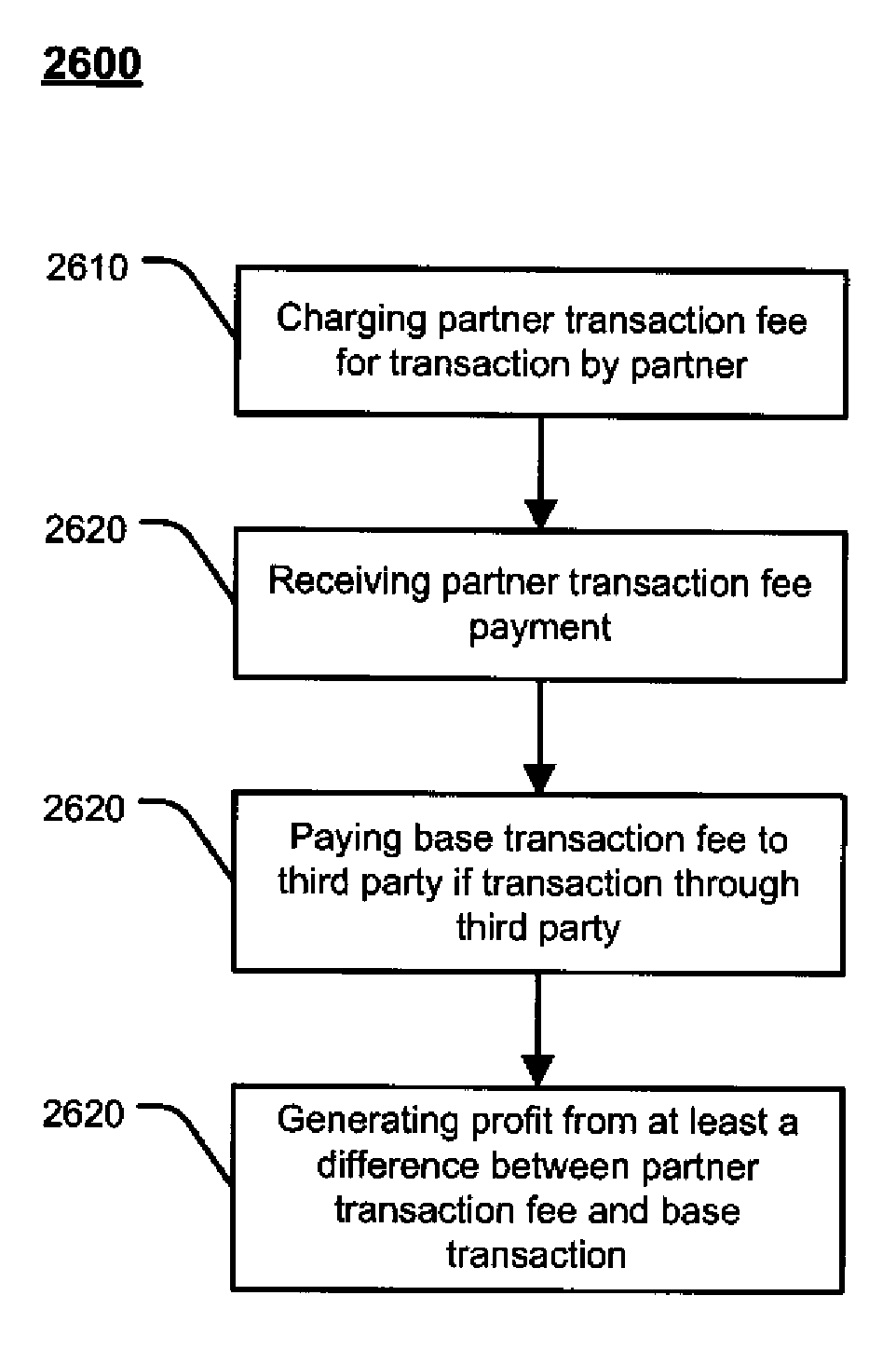
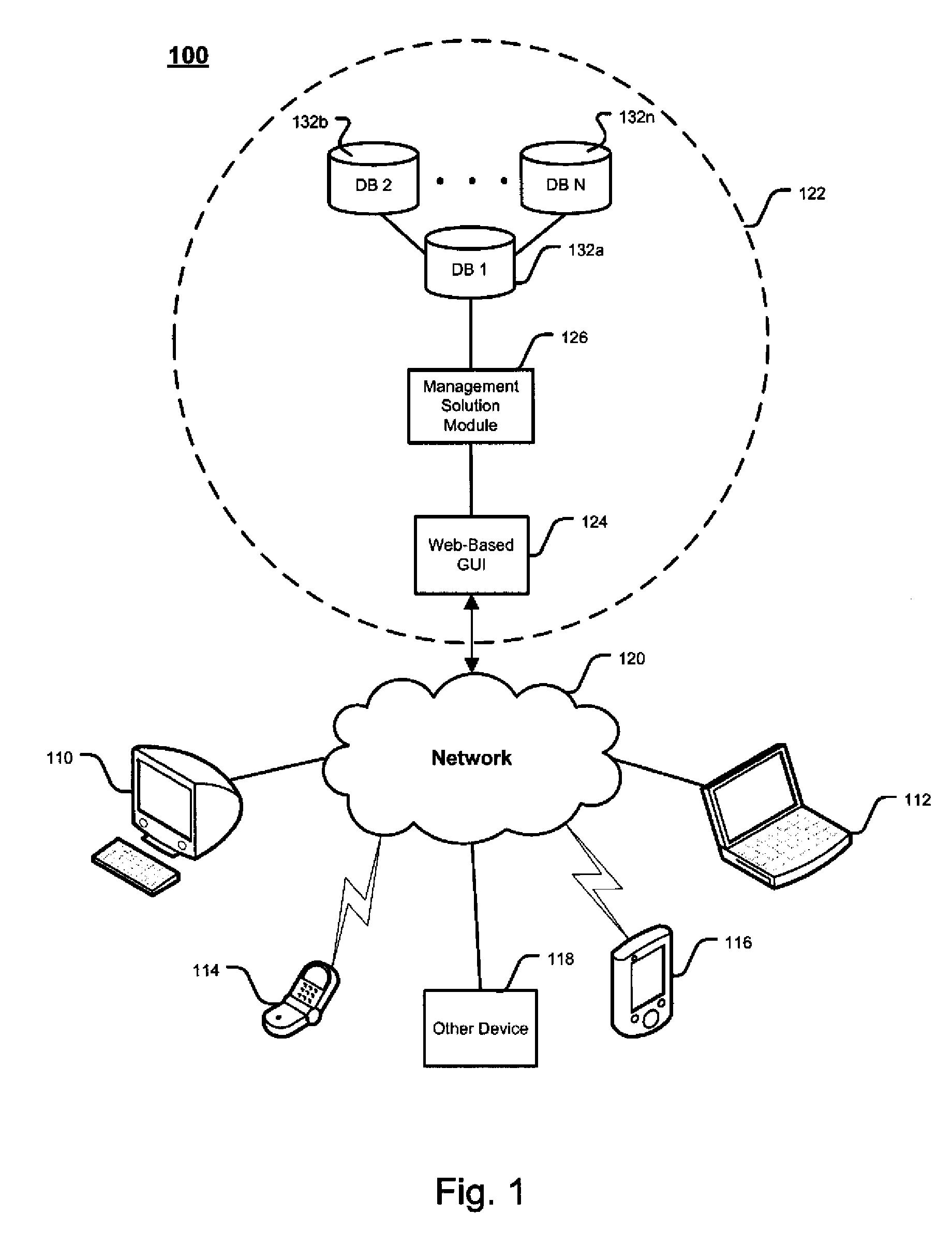
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
55 results about "Third party" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
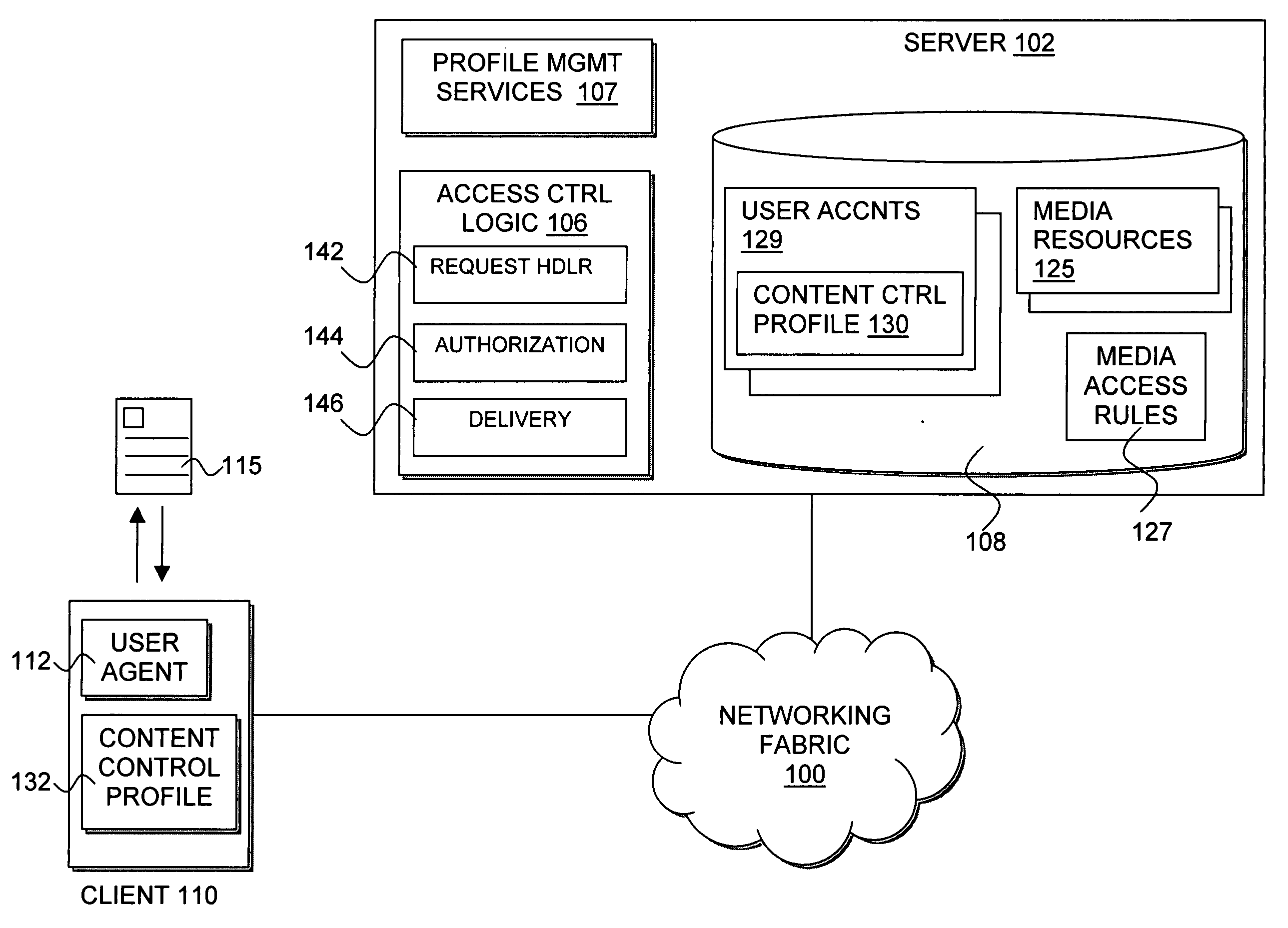
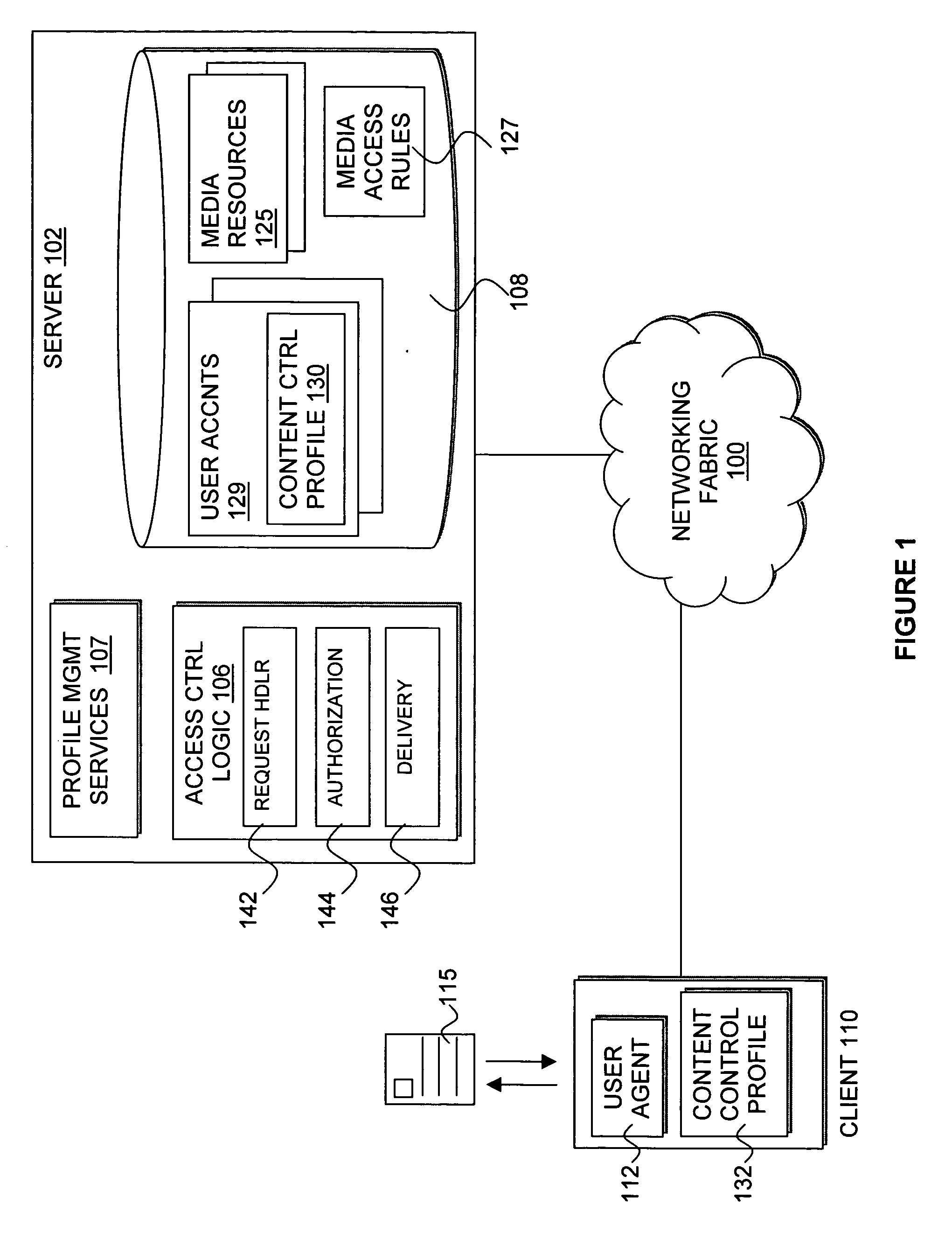
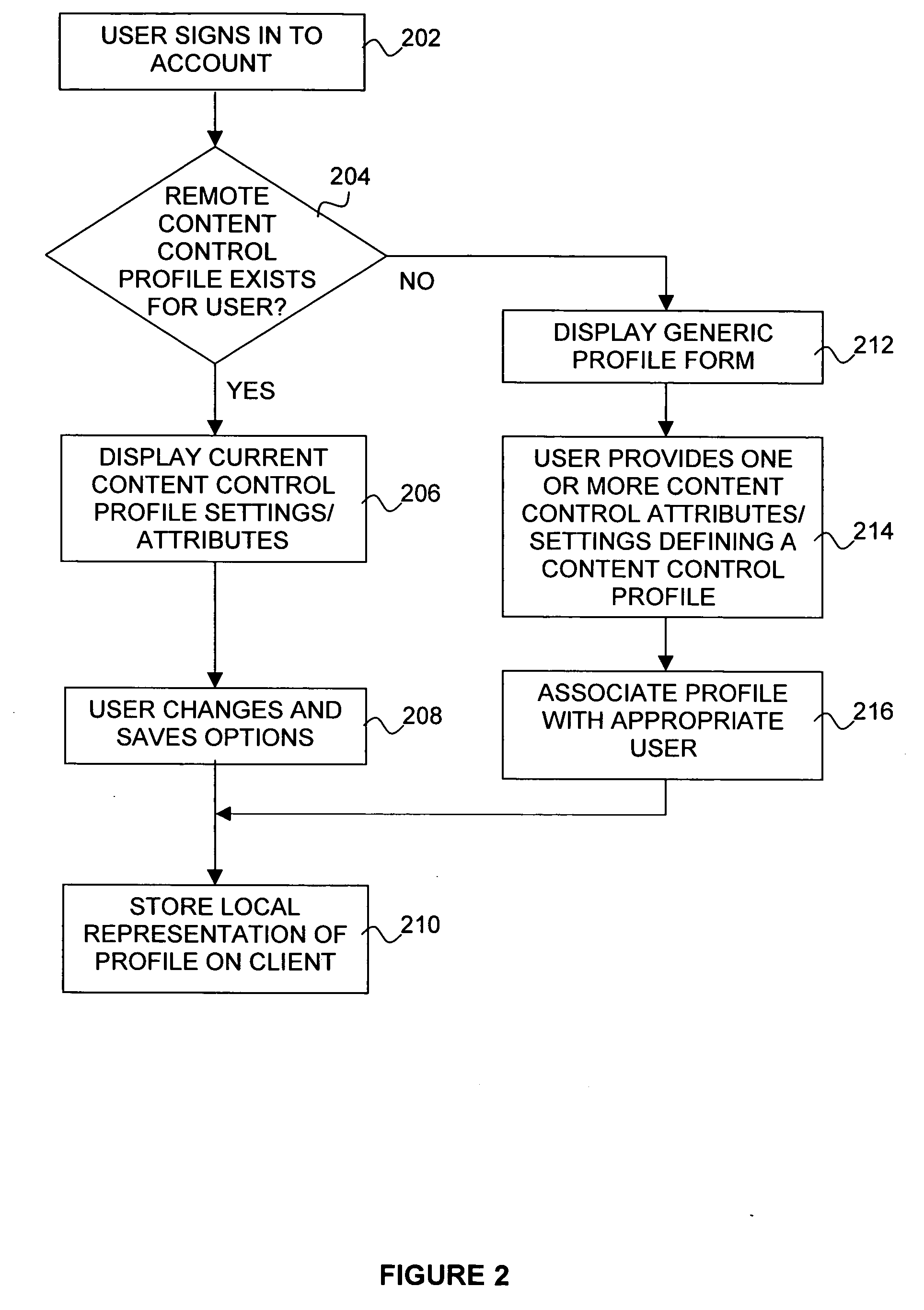
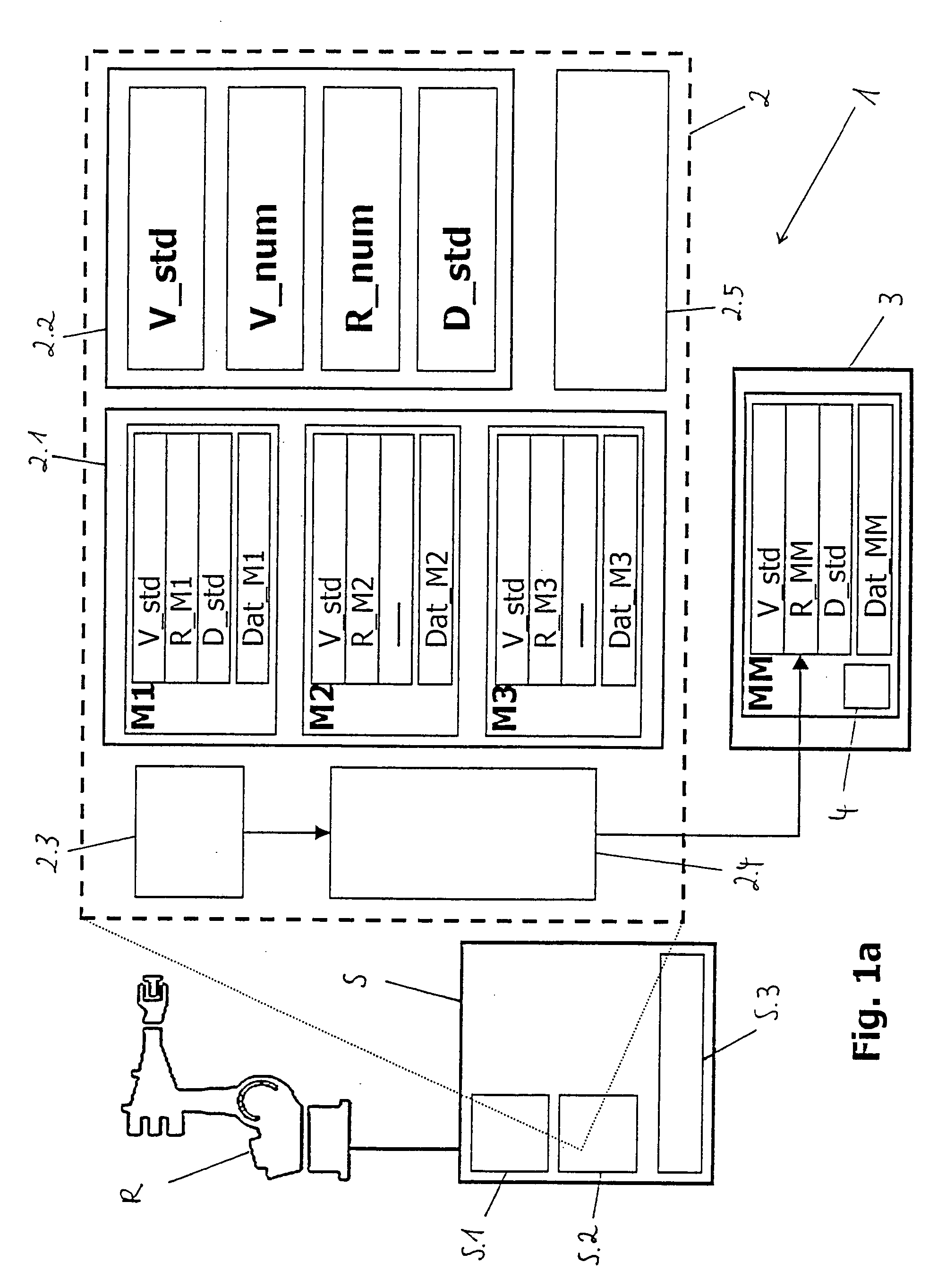
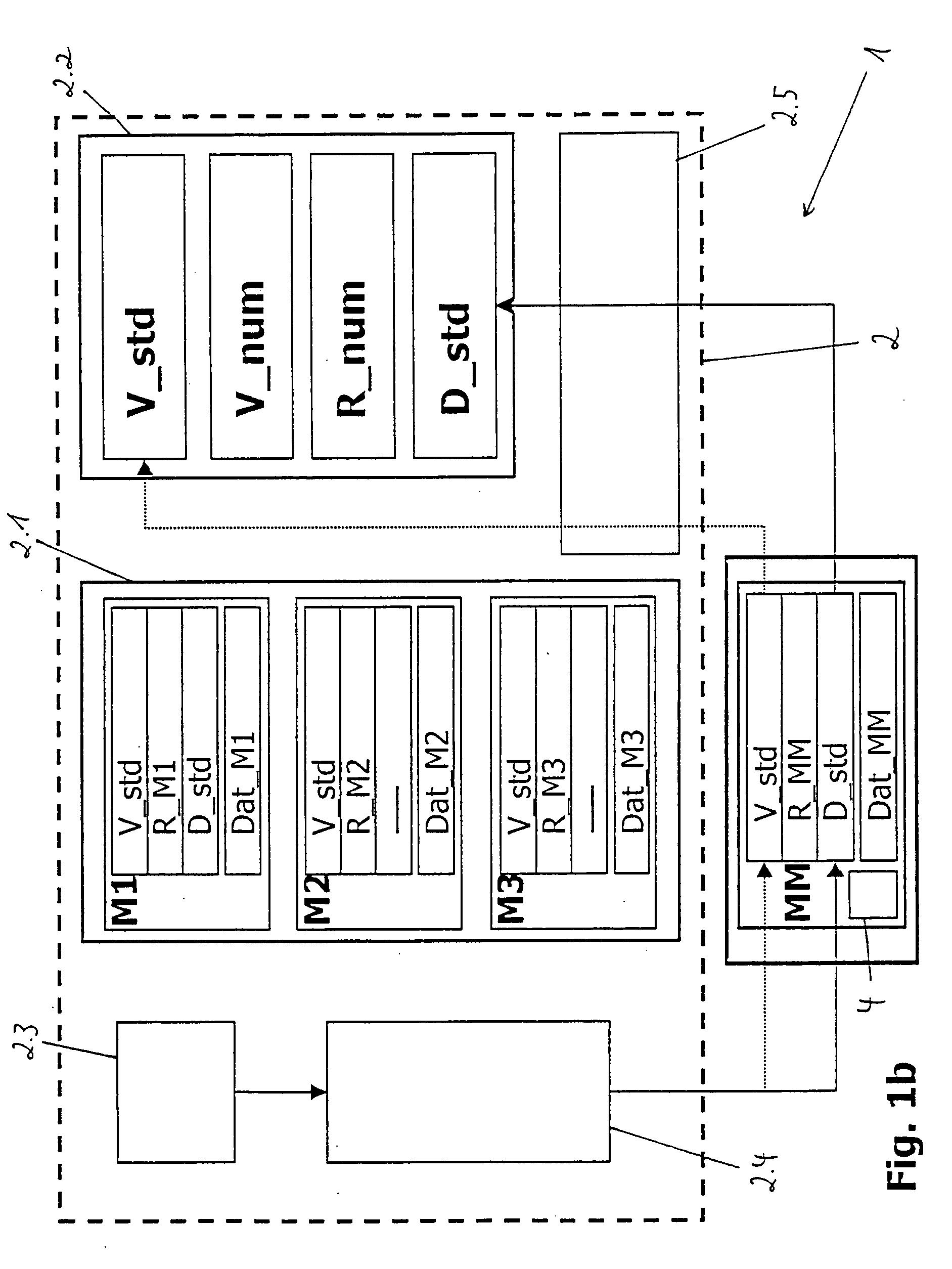
Multiple entity control of access restrictions for media playback
InactiveUS20050086683A1Digital data processing detailsAnalogue secracy/subscription systemsThird partyWorld Wide Web
Owner:INTEL CORP
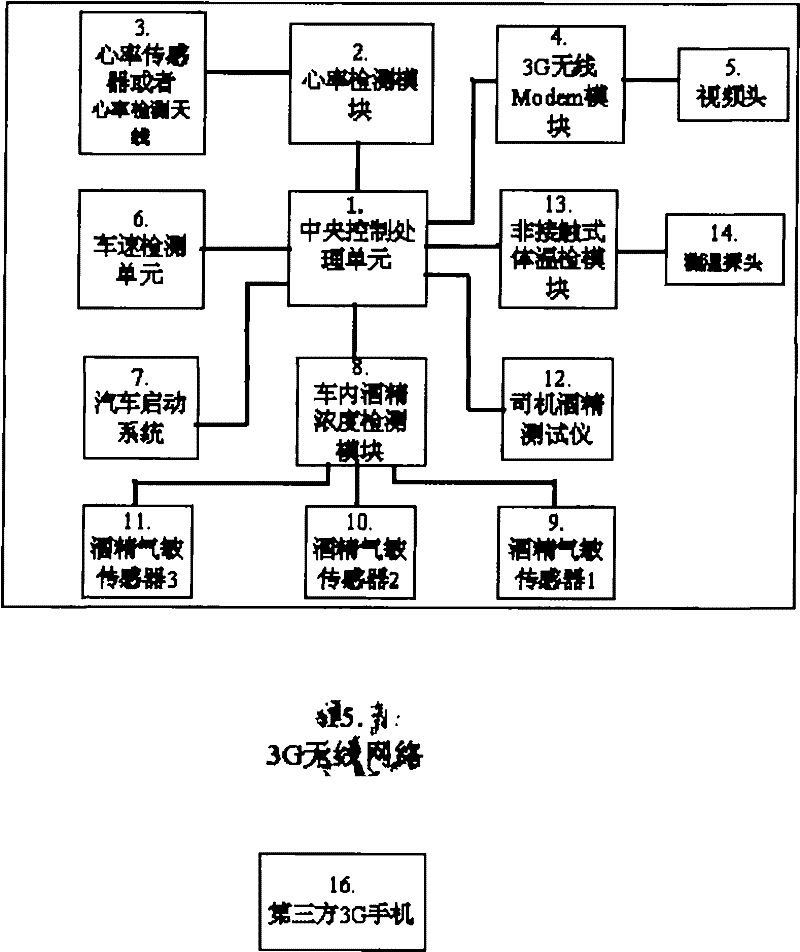
An anti-drunk driving and safe-health driving method
InactiveCN102163362AWays to Prevent Drunk DrivingGood for cardiovascular and cerebrovascular healthSensorsAlarmsThird partyDrunk driving
Owner:谢国华
Application program control method based on two-time signature verification technology
ActiveCN103886260AEnsure safetyProgram loading/initiatingPlatform integrity maintainanceThird partyApplication software
An application program control method based on a two-time signature verification technology is achieved by performing two times of signing and two times of signature verification on application programs on an android terminal. Security detection is performed on the application programs through a reliable third-party security detection mechanism, the application programs passing the detection will be signed by the third-party security detection mechanism, and then the signed applications are returned to developers. When the application programs are installed on the intelligent android terminal, security detection is performed on the application programs first to see whether the application programs are signed by the third-party security detection mechanism or not, and signatures are verified; if signatures of the third-party detection mechanism do not exist or the signatures cannot pass verification, installation of the application programs is refused. Through the technical scheme, the application program control method based on the two-time signature verification technology has the advantages that signature information is fixed through introduction of the third-party detection signatures and a security control module of the android terminal so that secure application programs can be downloaded and installed in an android system through multiple channels, and while security of the android terminal is guaranteed, a flexible and efficient application program verification scheme is provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
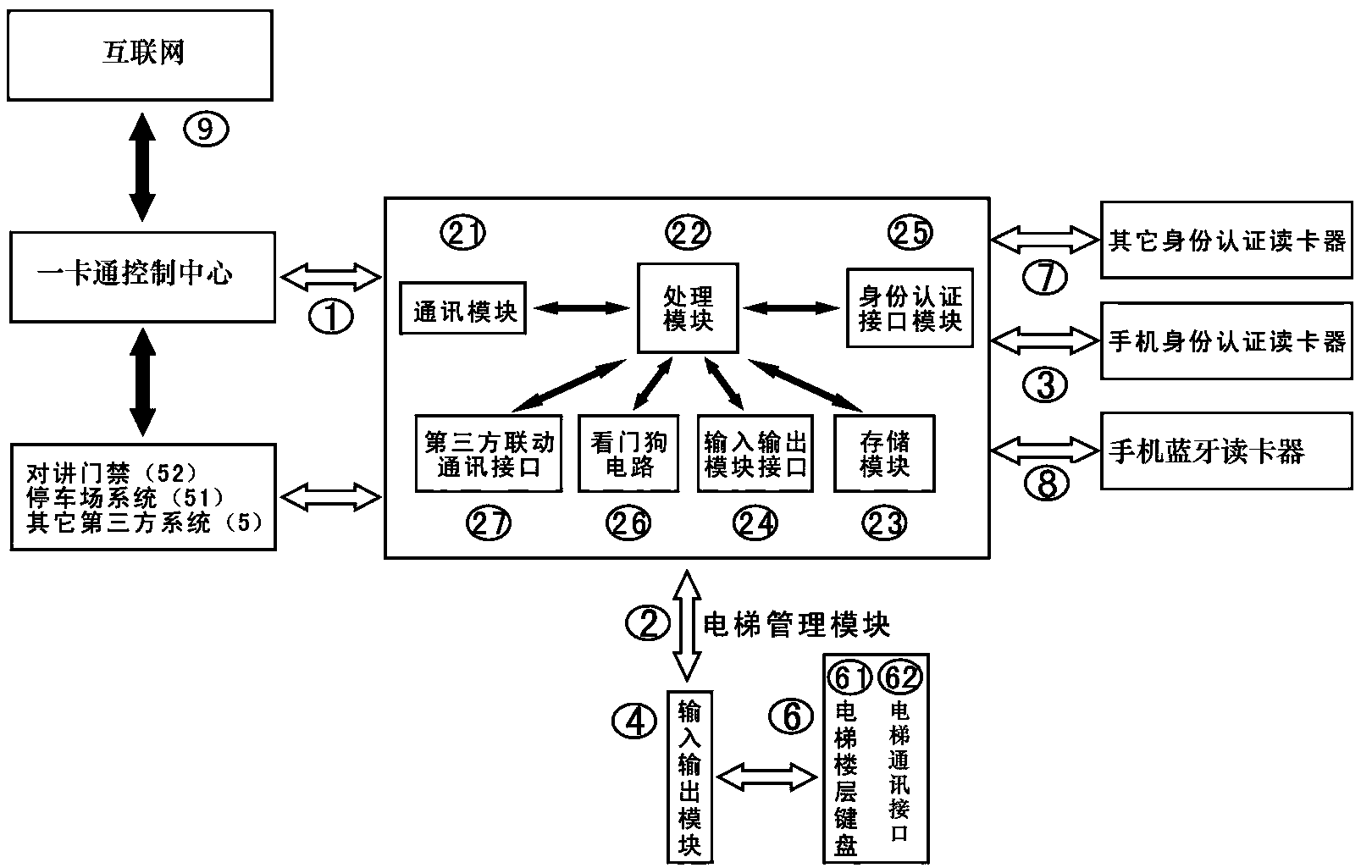
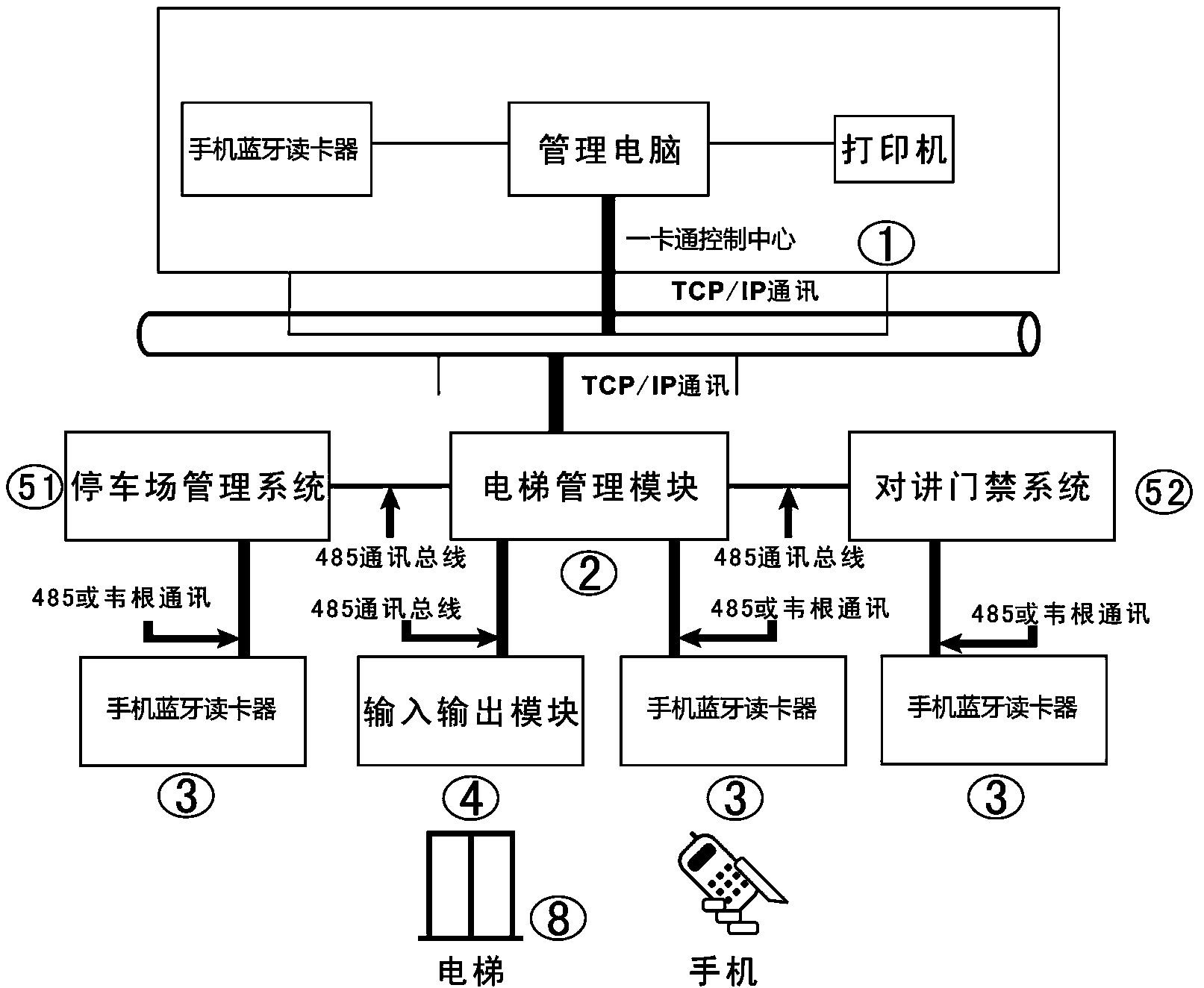
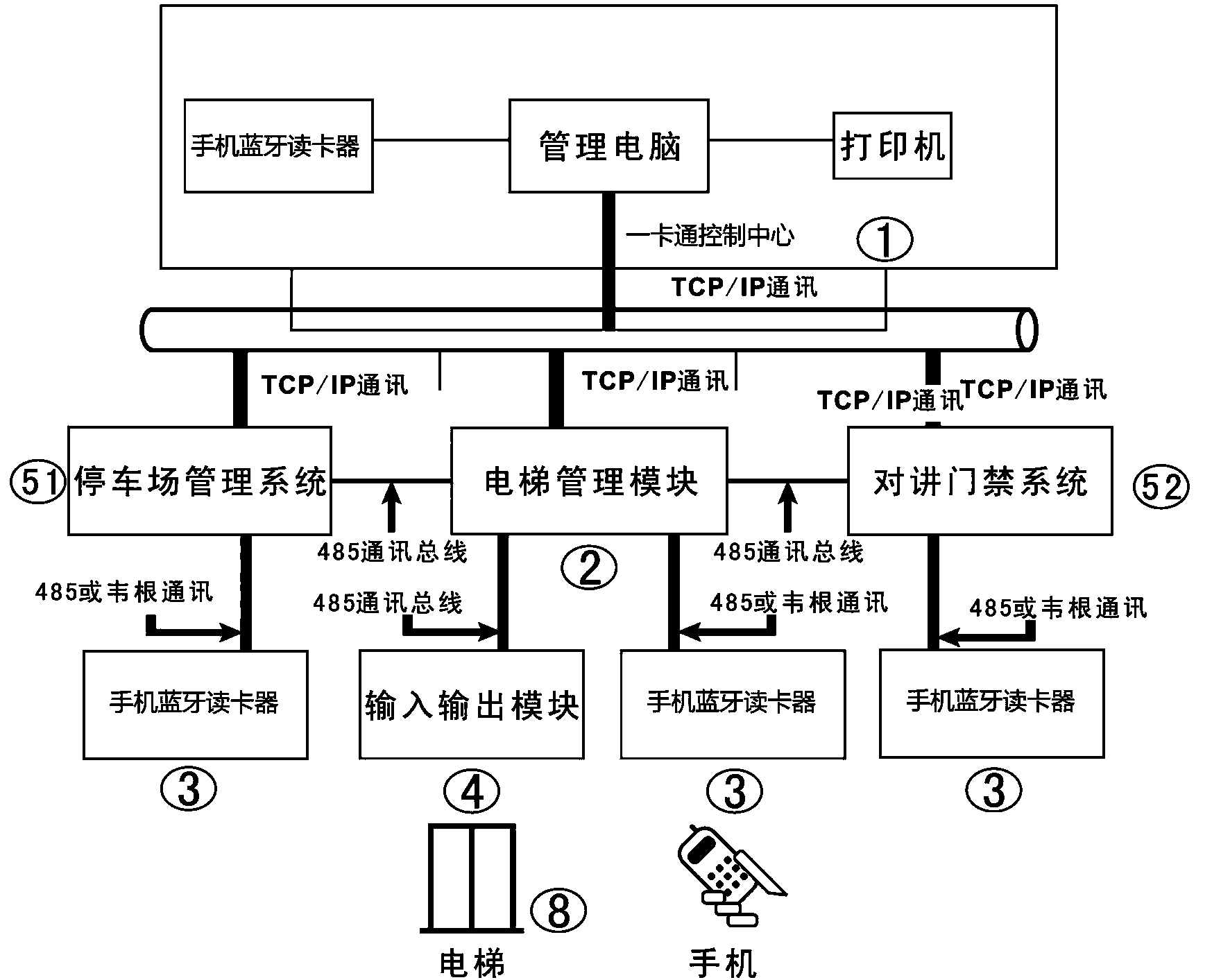
One-card control system and one-card control method of mobile phone Bluetooth swiping card
ActiveCN104340780ASolve the inflexibility of controlRealize integrated applicationElevatorsCard readerBluetooth
Owner:CHENGDU QIANFAN TECH DEV
Parking stall searching method and intelligent parking service system
Owner:深圳迅停科技发展有限公司
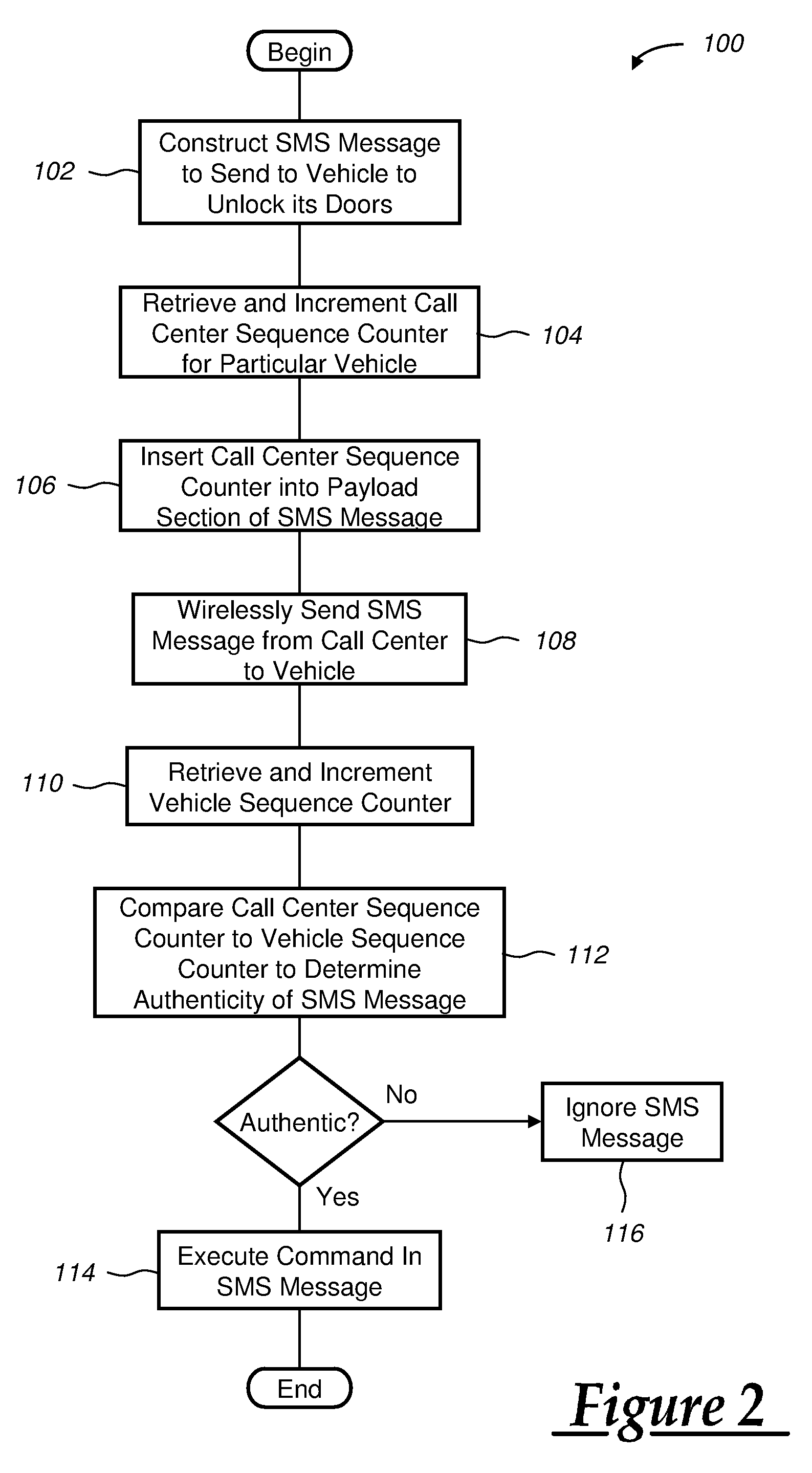
Preventing replay-type attacks on a vehicle communications system
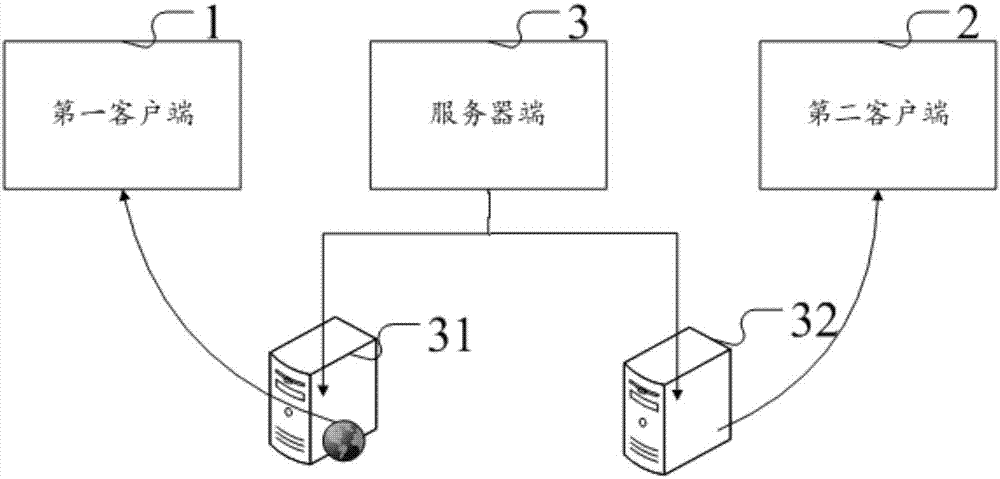
ActiveUS20090170539A1Avoid attackKey distribution for secure communicationSubstation equipmentThird partyCommunications system
Owner:GM GLOBAL TECH OPERATIONS LLC
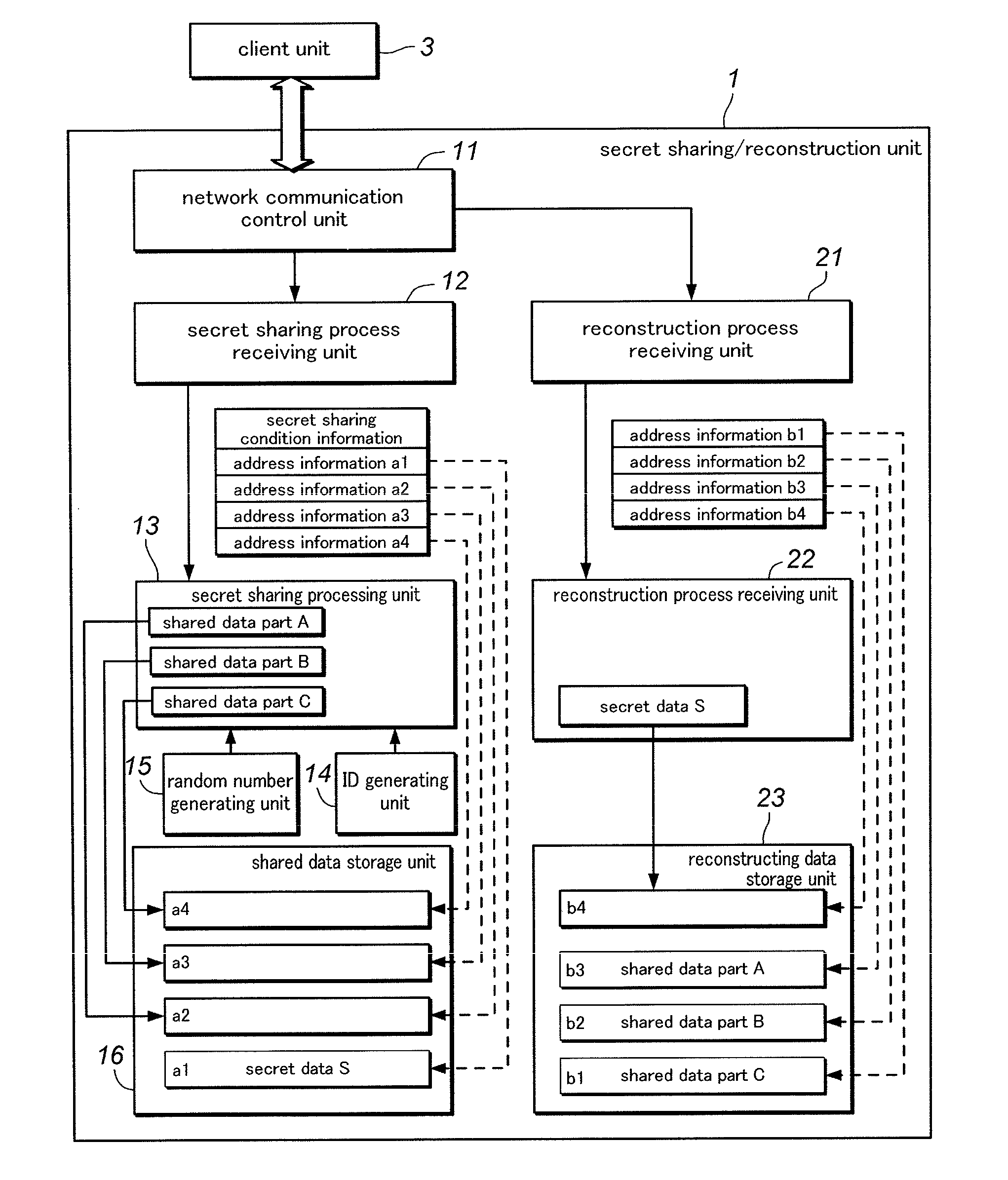
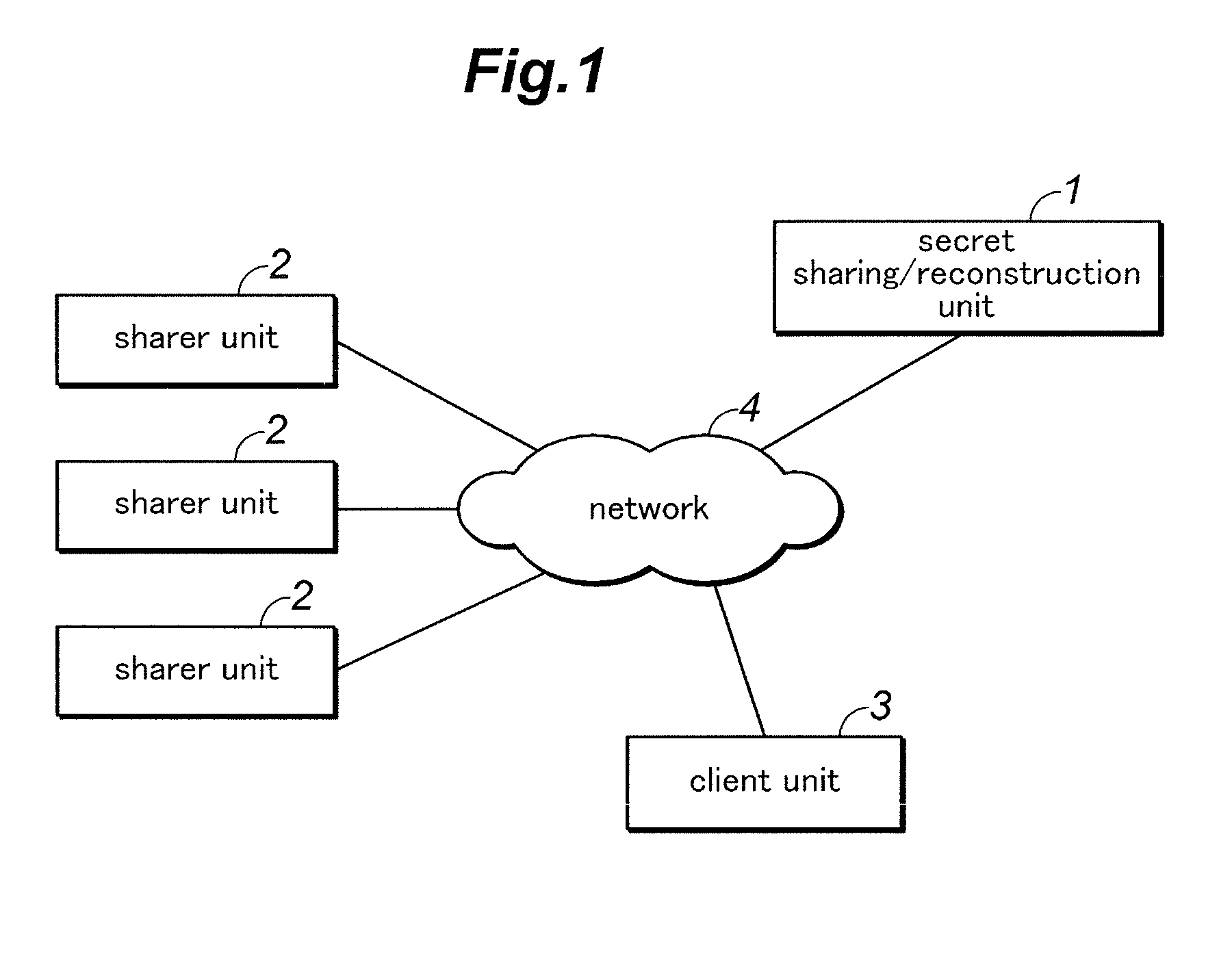
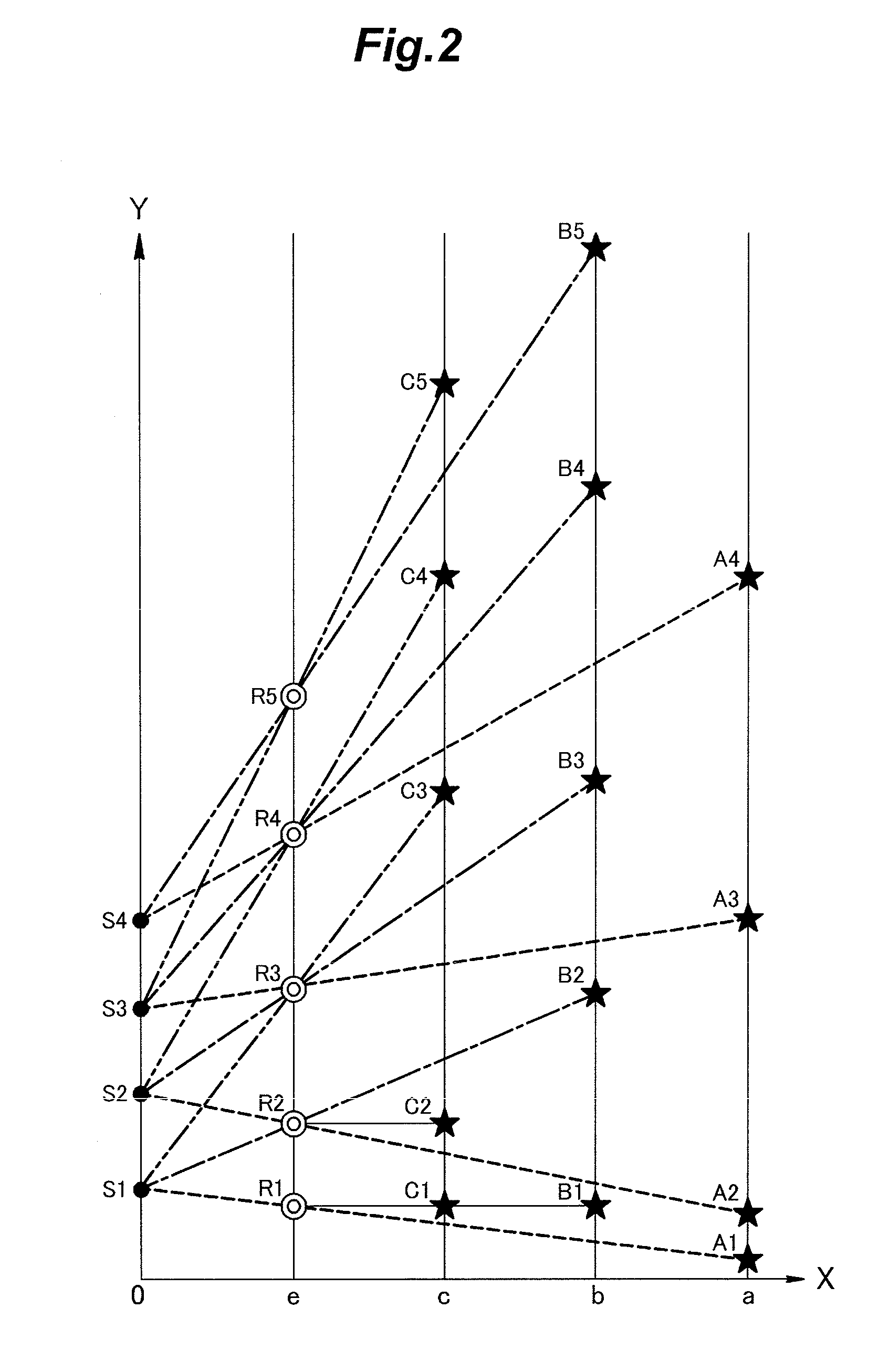
Secret sharing method and system
ActiveUS20140173270A1Difficult to knowKey distribution for secure communicationComputer securityThird party
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
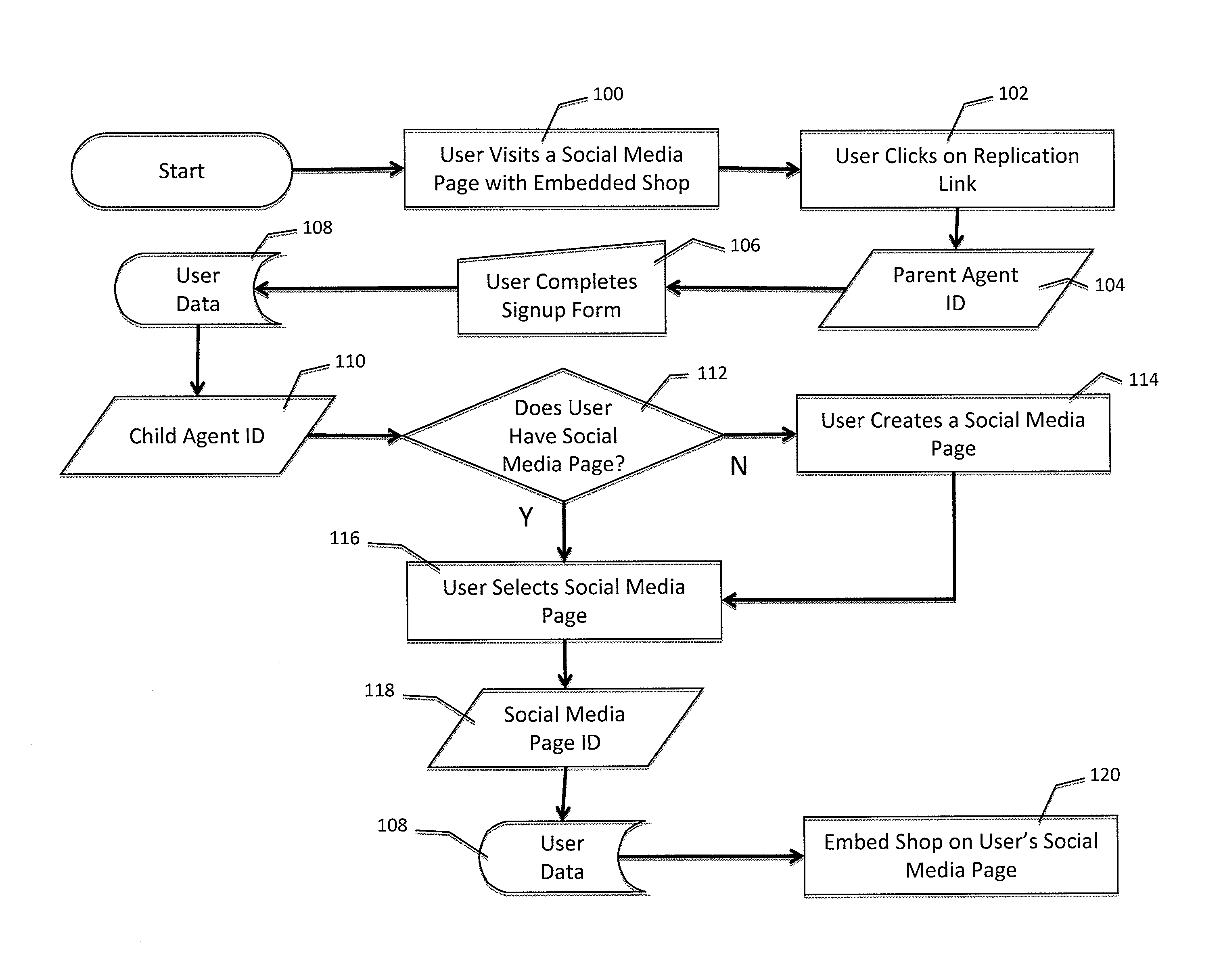
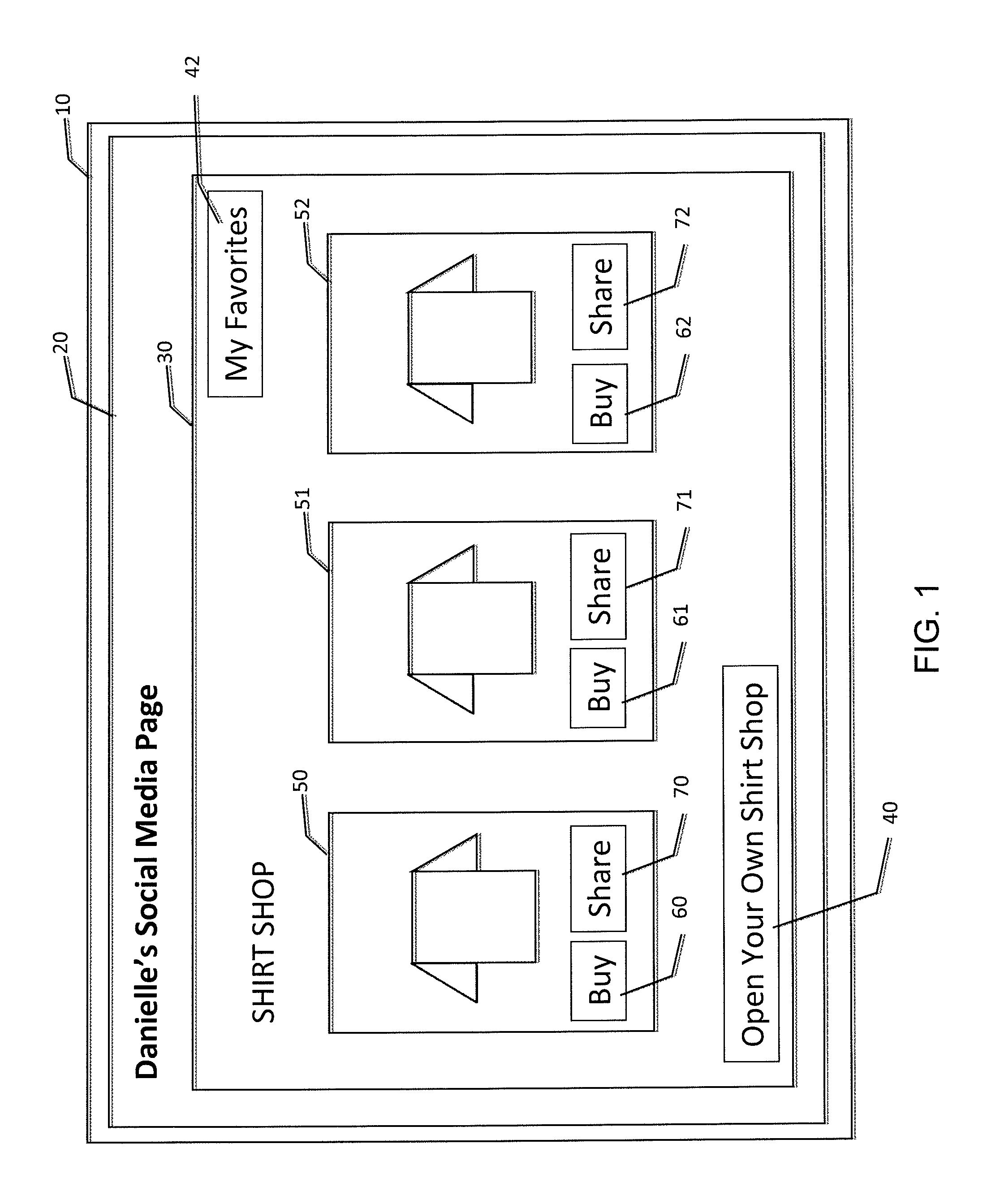
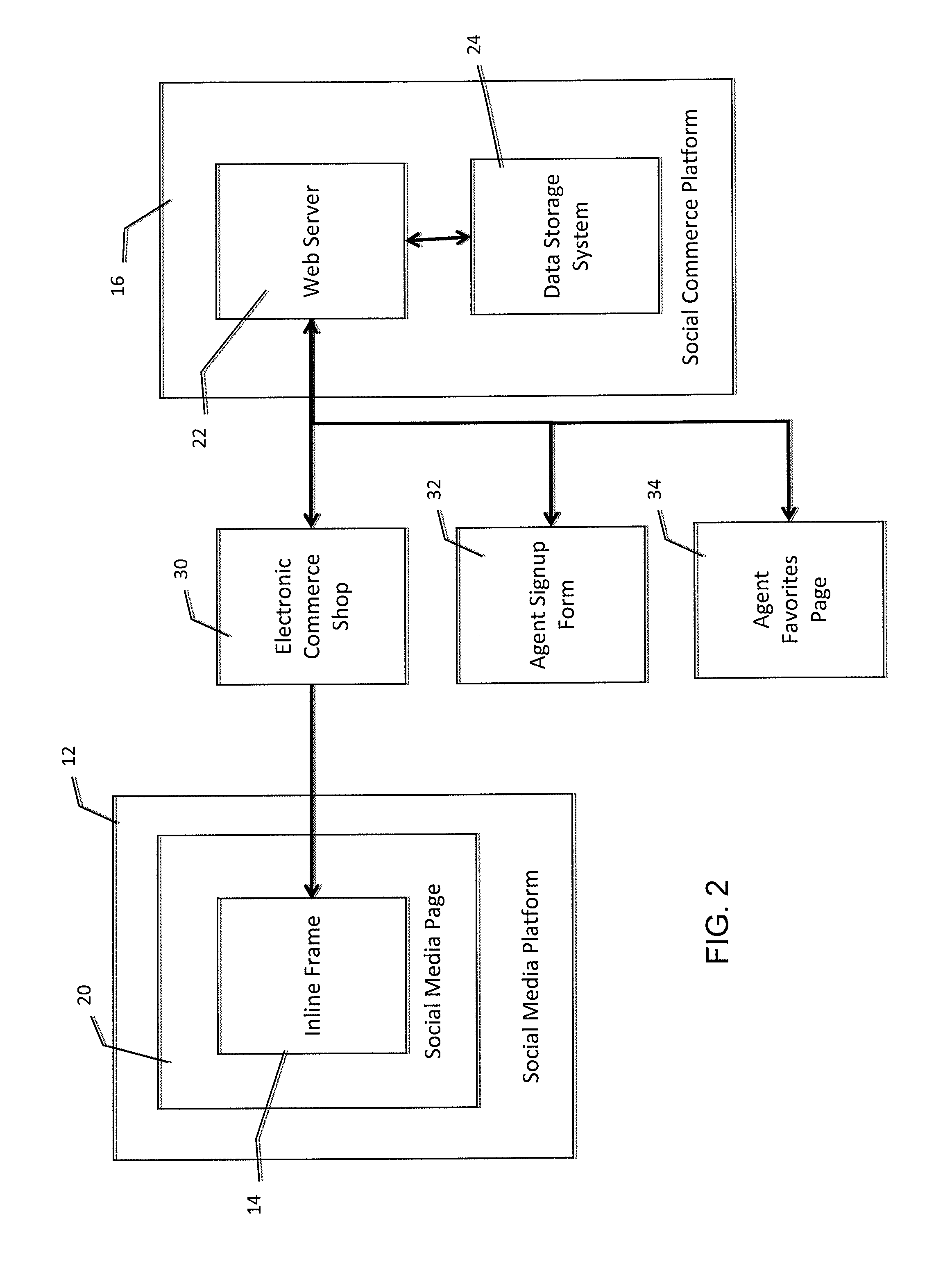
Social commerce agent store replication
Owner:ZINDIGO
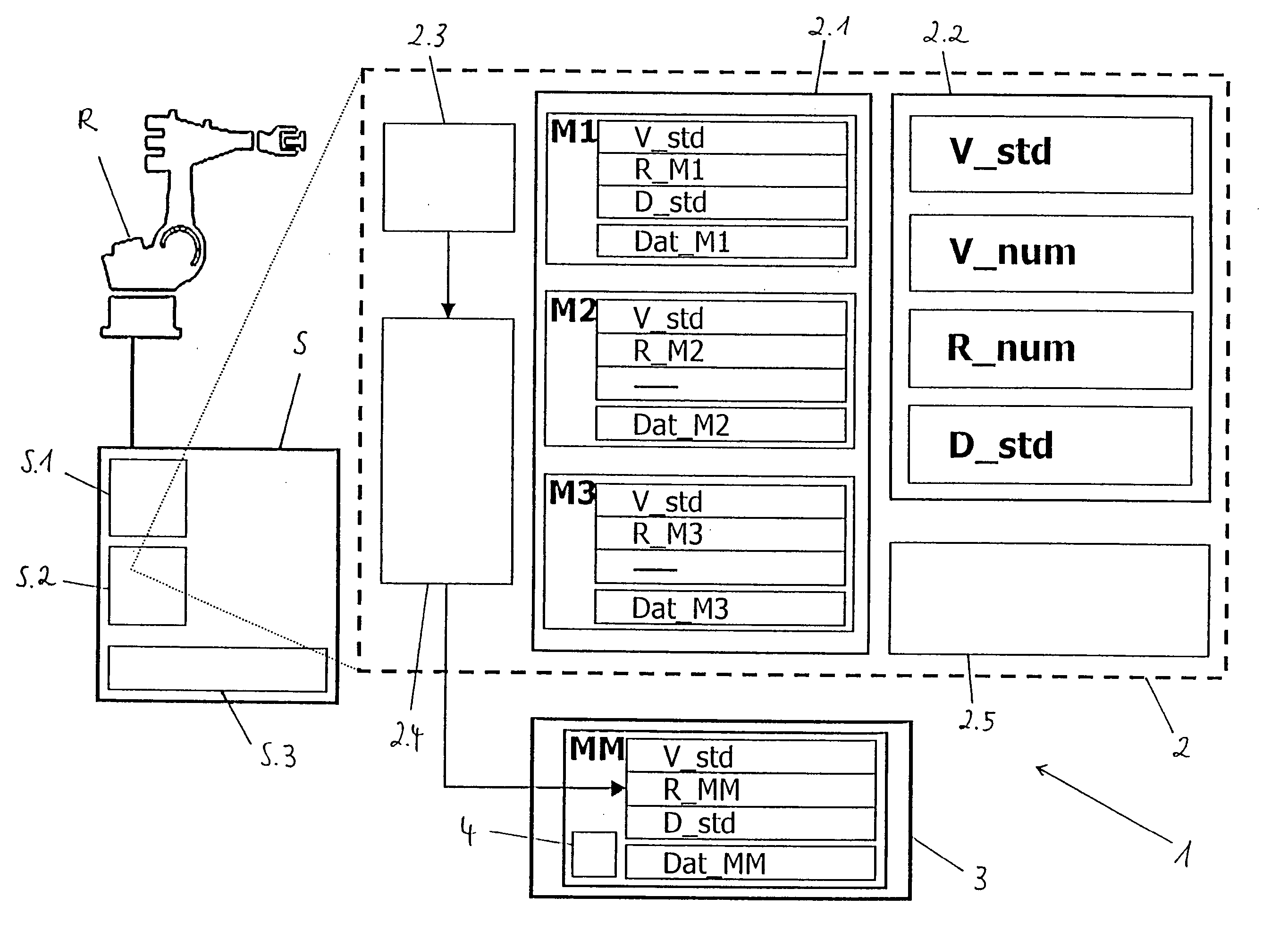
Process and device for controlling the robotal device
InactiveUS20060004489A1Avoid problemsImprove compatibilityProgramme-controlled manipulatorComputer controlThird partyKinematics
Owner:KUKA ROBOTER
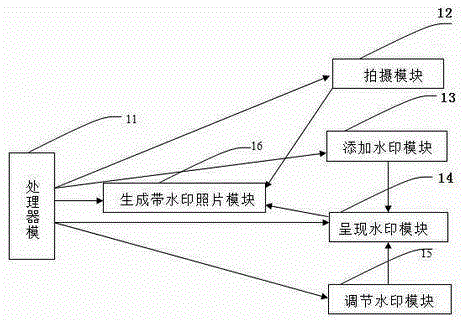
System and method for automatically adding watermarks to shot pictures
InactiveCN104144297AOvercome photo inconvenienceEasy to useTelevision system detailsColor television detailsThird partyComputer science
The invention provides a system and method for automatically adding watermarks to shot pictures. The method is characterized in that when a mobile terminal performs shooting, the watermarks are automatically added according to the setting of a user, the positions, the content and the sizes of the watermarks can be adjusted in the process of previewing, and finally the pictures with the watermarks are generated. According to the system and method, while shooting is achieved, the watermarks can be added, the effect of adding the watermarks can be previewed in advance, and besides, the content, the positions and the sizes of the watermarks can be modified in real time according to previewing results. In this way, the defect that the watermarks are not convenient to add by the utilization of a third party tool is overcome, besides, on the premise that mobile terminal hardware is not additionally arranged, the functions of the mobile terminal are added, and the competitiveness of the mobile terminal in the market is improved.
Owner:ARCHERMIND TECH NANJING
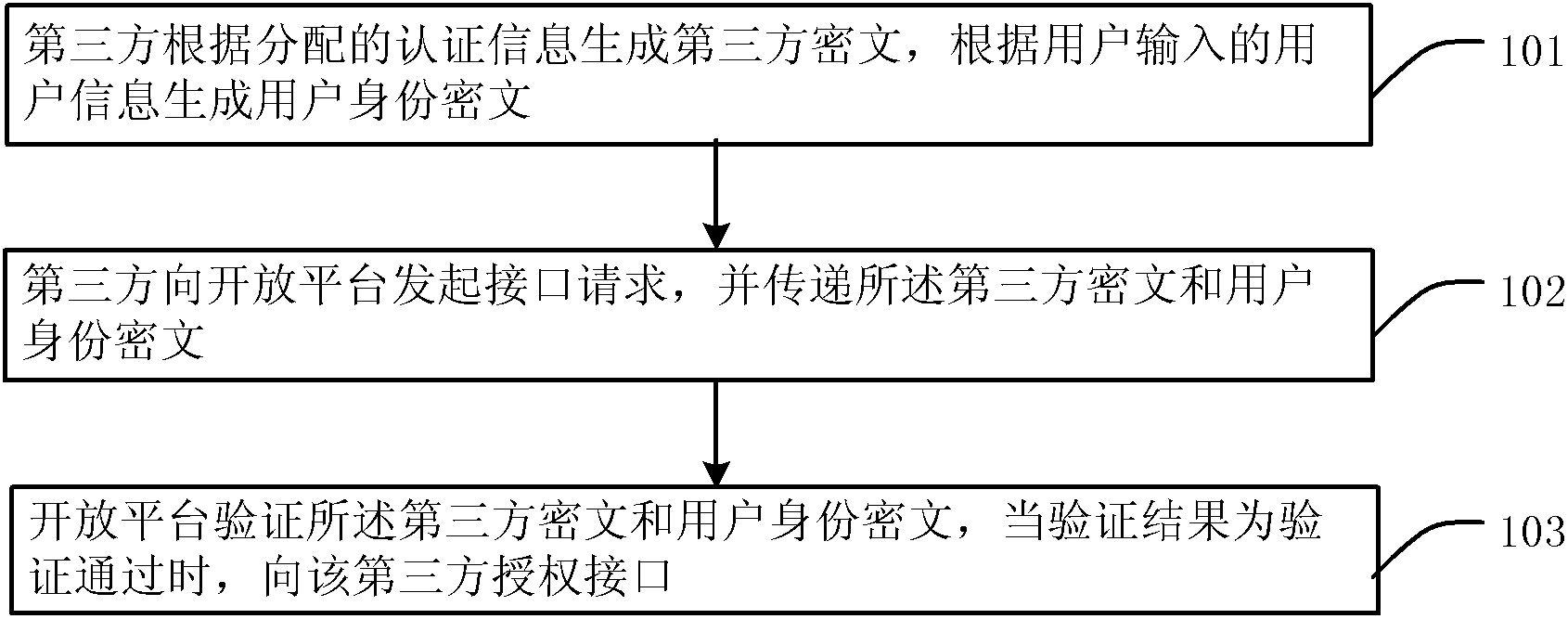
Method and system for third party application interface authorization
Owner:BEIJING FEINNO COMM TECH
NFC payment method and terminal
Owner:HUAWEI TECH CO LTD
Internet of Videos resource release method and Internet of Videos sharing platform server
InactiveCN109302472AImprove effective utilizationClosed circuit television systemsData switching networksThird partyTransmission protocol
Owner:VISIONVERA INFORMATION TECH CO LTD
Digital identity authentication method and system based on secure two-dimensional code
Owner:新大陆(福建)公共服务有限公司
Automatic design and type setting detail page manufacture method through visual identity combined with artificial intelligence
ActiveCN107622134AEliminate the hassle of repeated entryEasy to useBuying/selling/leasing transactionsSpecial data processing applicationsThird partyE-commerce
Owner:杭州时间线信息科技有限公司
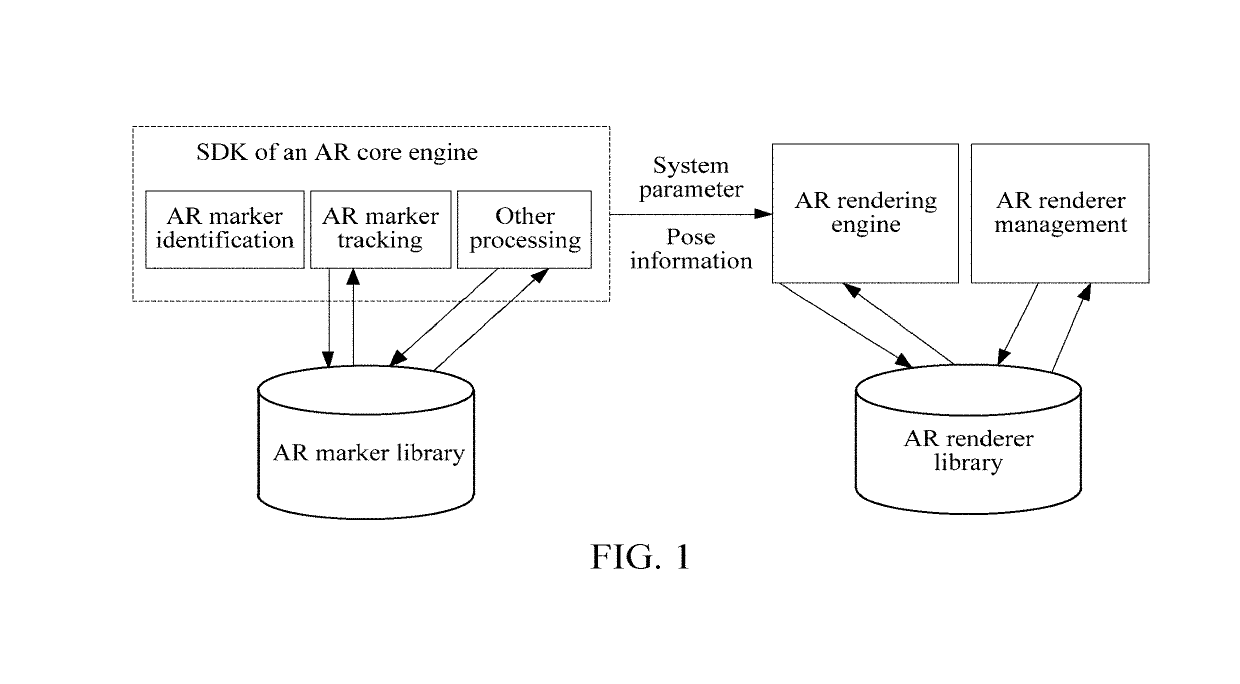
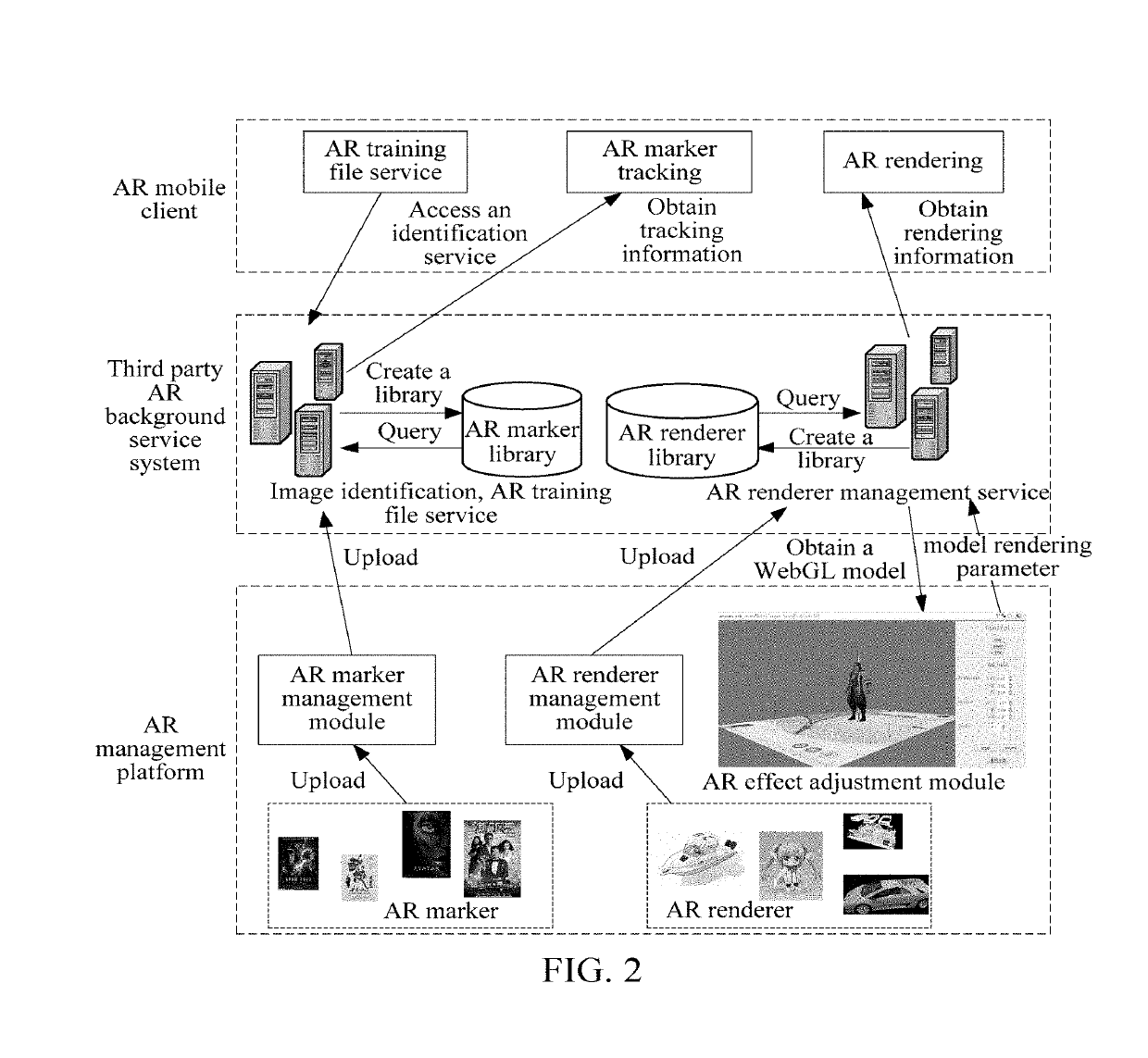
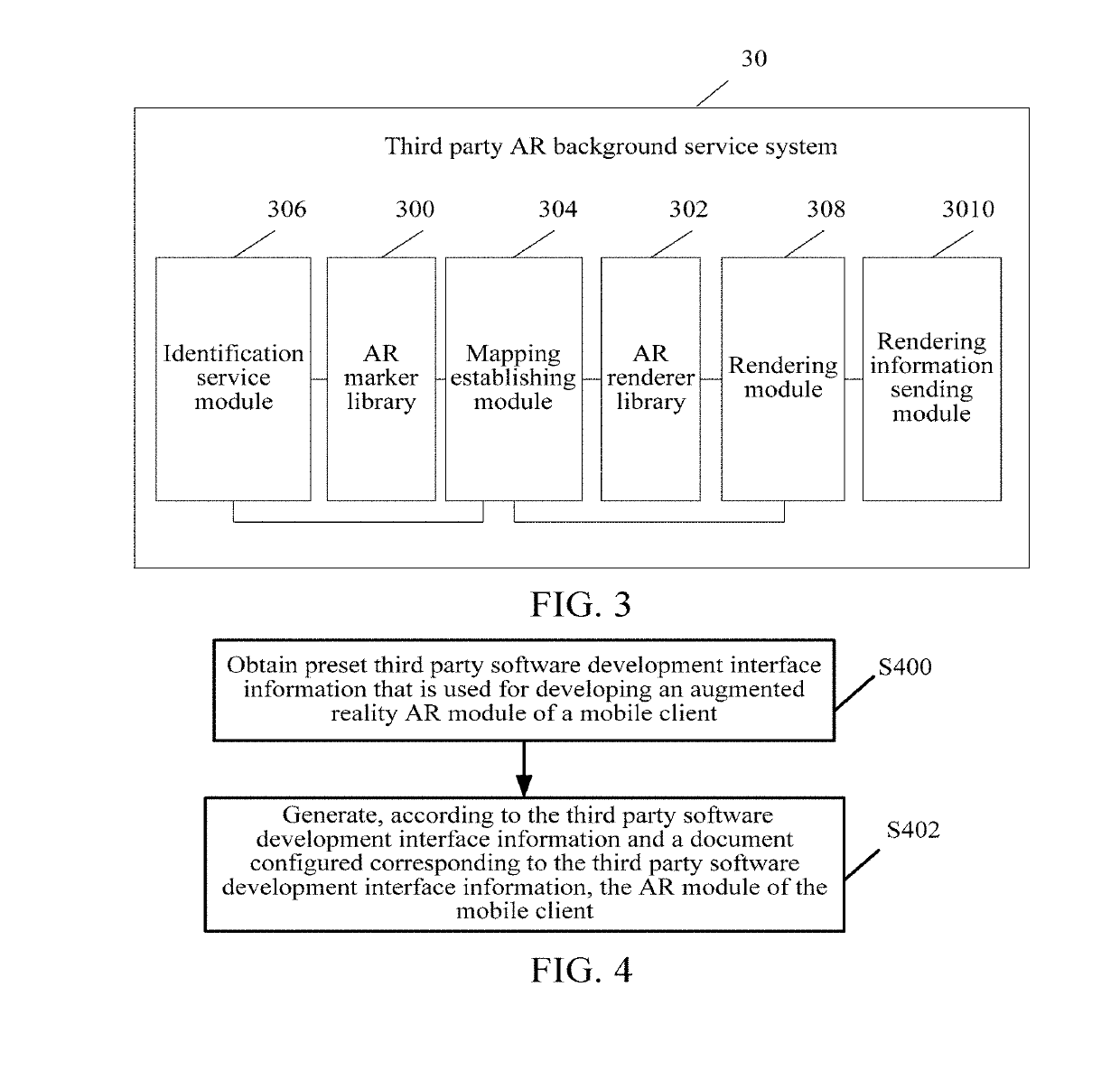
Method, apparatus and system for generating augmented reality module and storage medium
ActiveUS20190129715A1Shorten the overall cycleSimplify the development processVersion controlSoftware metricsThird partySoftware engineering
Owner:TENCENT TECH (SHENZHEN) CO LTD
GPS determined location based access to linked information and delivery thereof
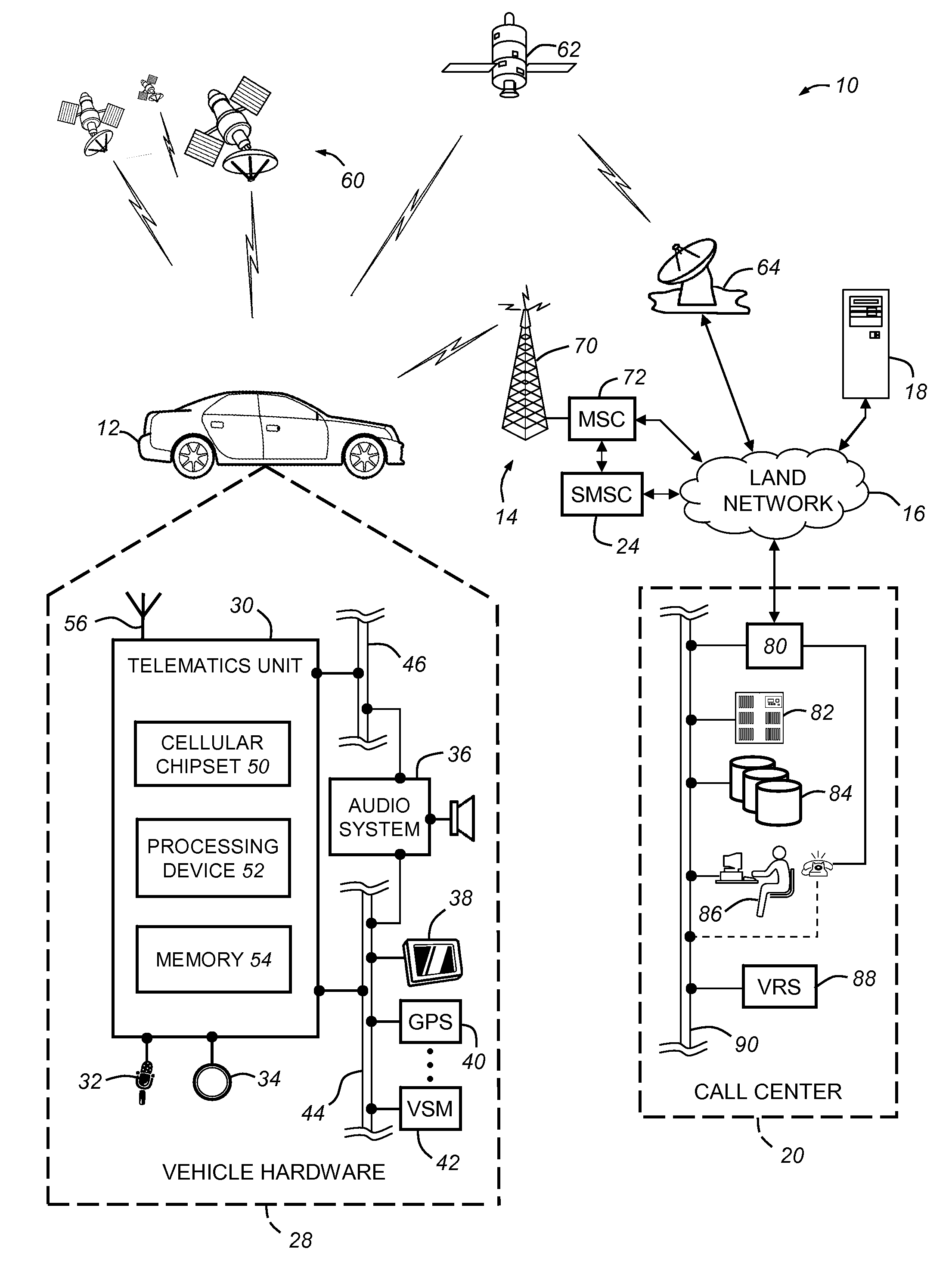
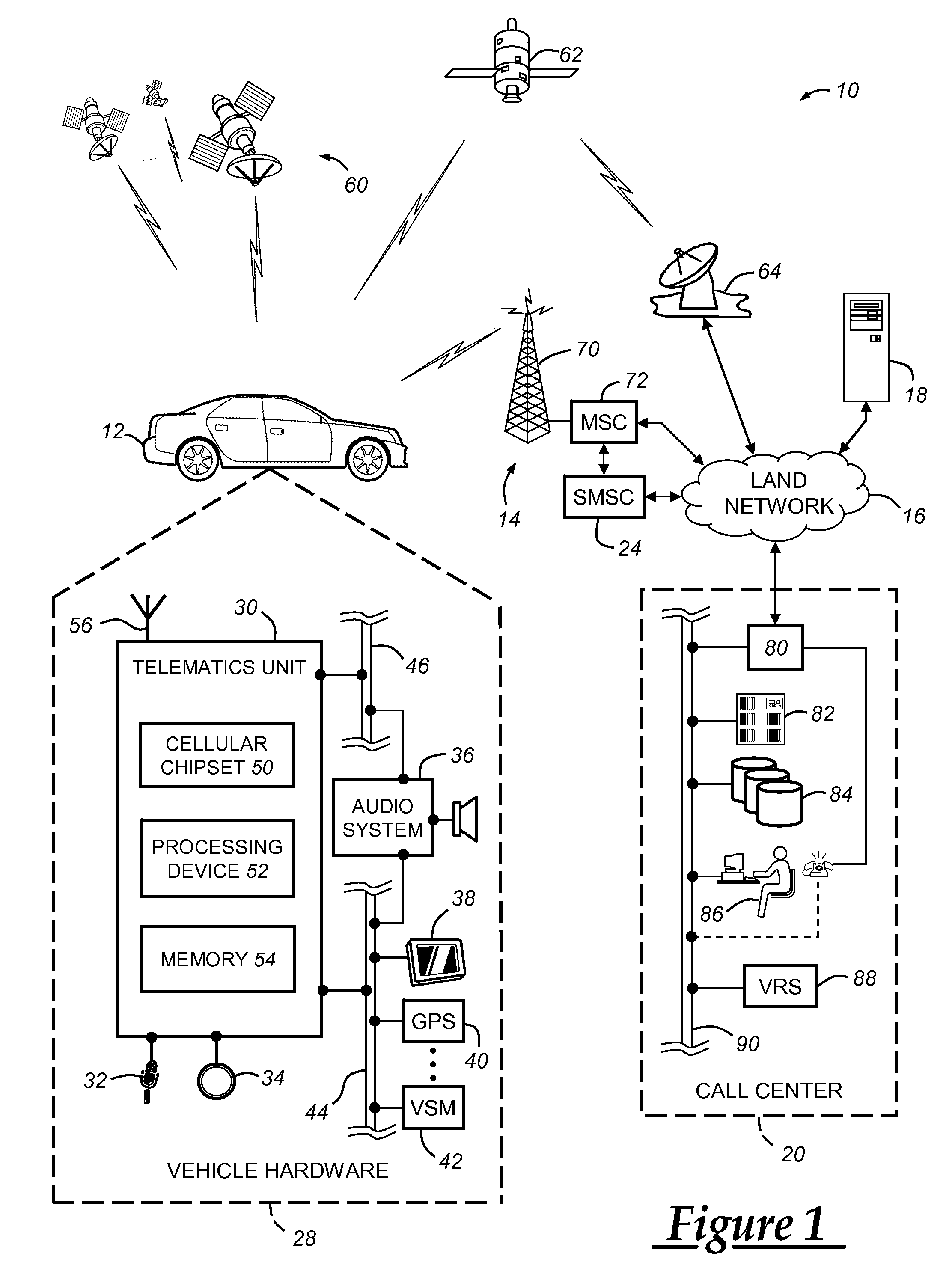
Various methods are provided for facilitating access to linked information to GPS or short-range wireless equipped devices. One example method may comprise receiving, via a network, an indication of an interaction between a primary device and a third-party device, the indication comprising at least a first element and a second element, the first element indicative of user identification information and the second element indicative of at least one of a location or a bounded region, determining, as a function of at least the first element and the second element, a data object that upon validation is configured for use a subsequent interaction, and transmitting, to a mobile device, an electronic communication comprising an indication, configured for rendering on the mobile device, of the data object.
Owner:GROUPON INC
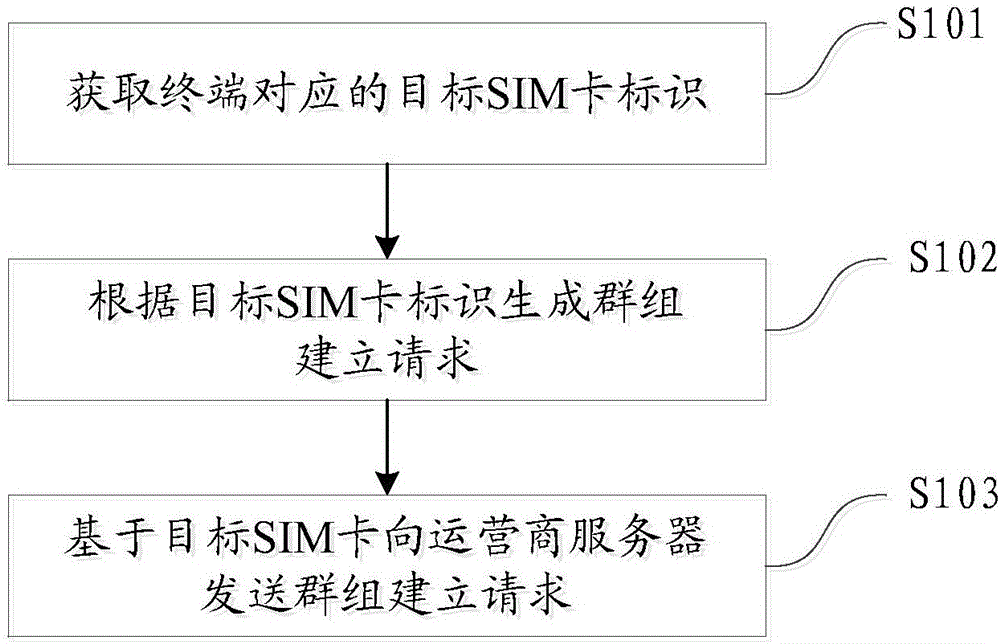
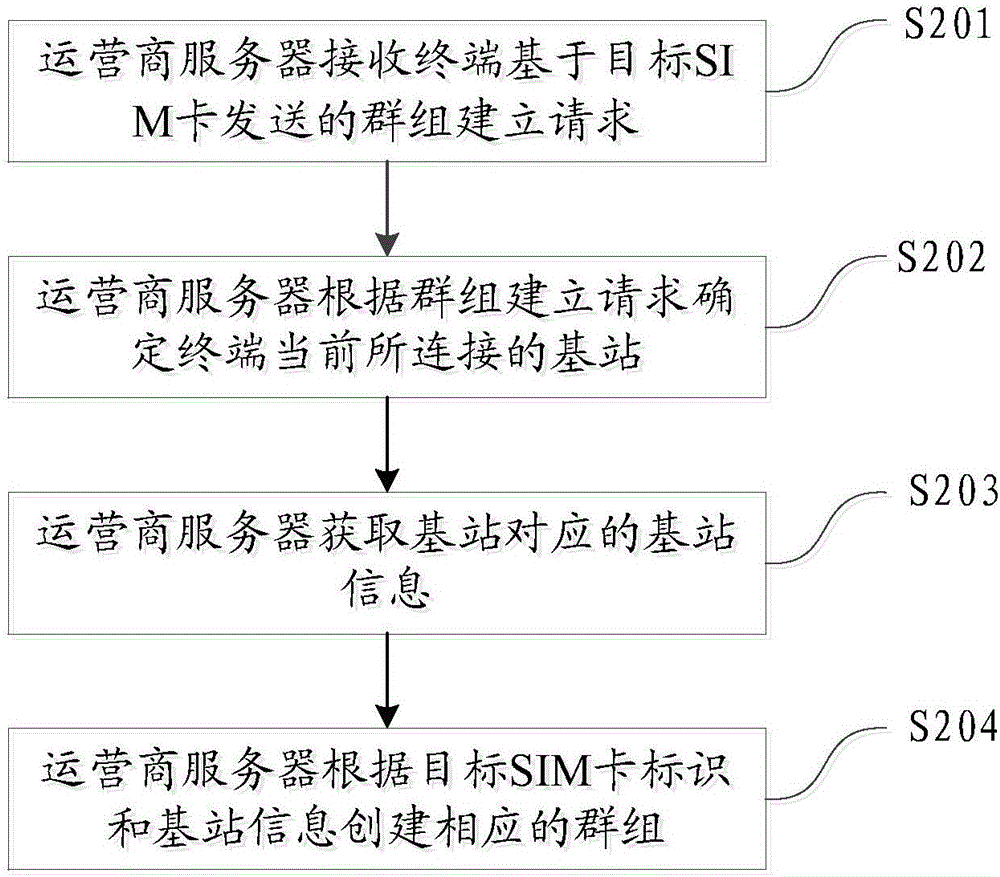
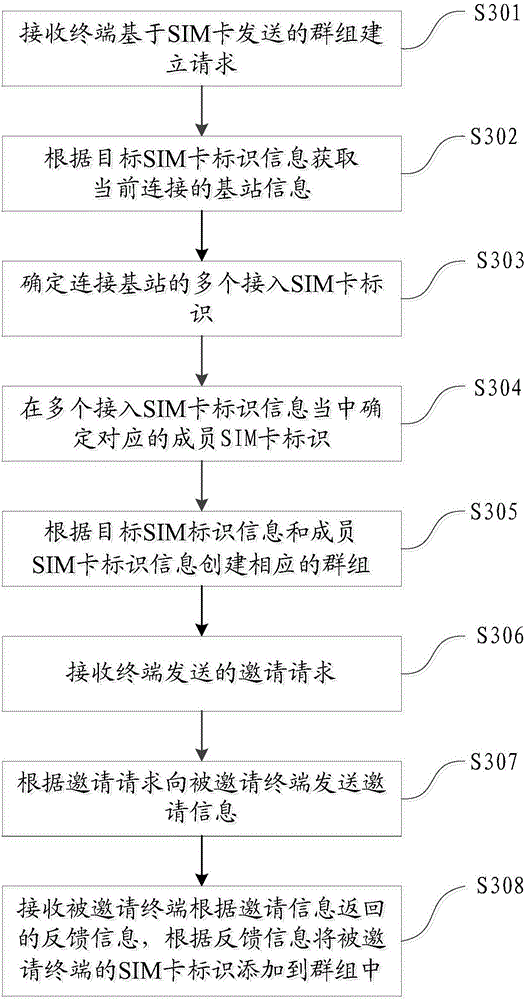
Group establishment method and device
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
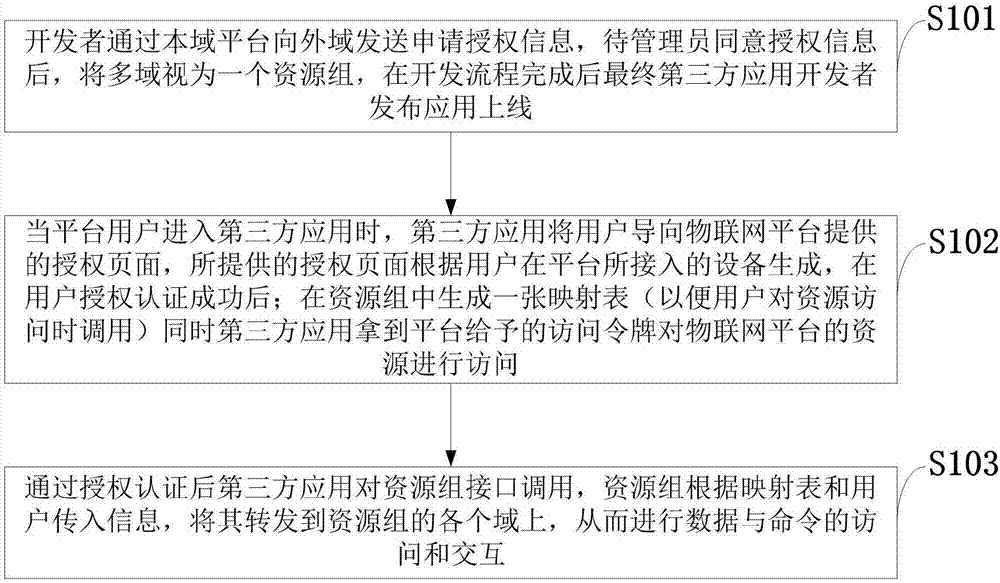
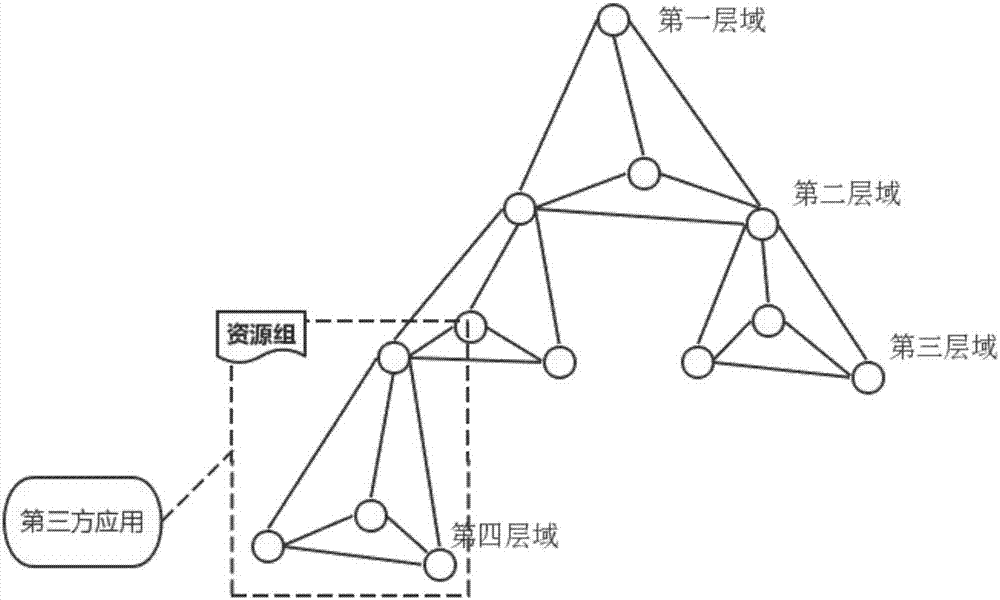
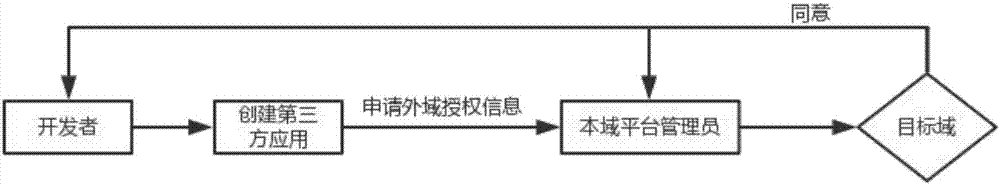
Third-party application authorization and authentication method based on multi-domain collaborative architecture
ActiveCN107018128ASafe and reliable authorized accessTroubleshoot authentication issuesTransmissionThird partySoftware engineering
Owner:陕西沃傲信息科技有限公司
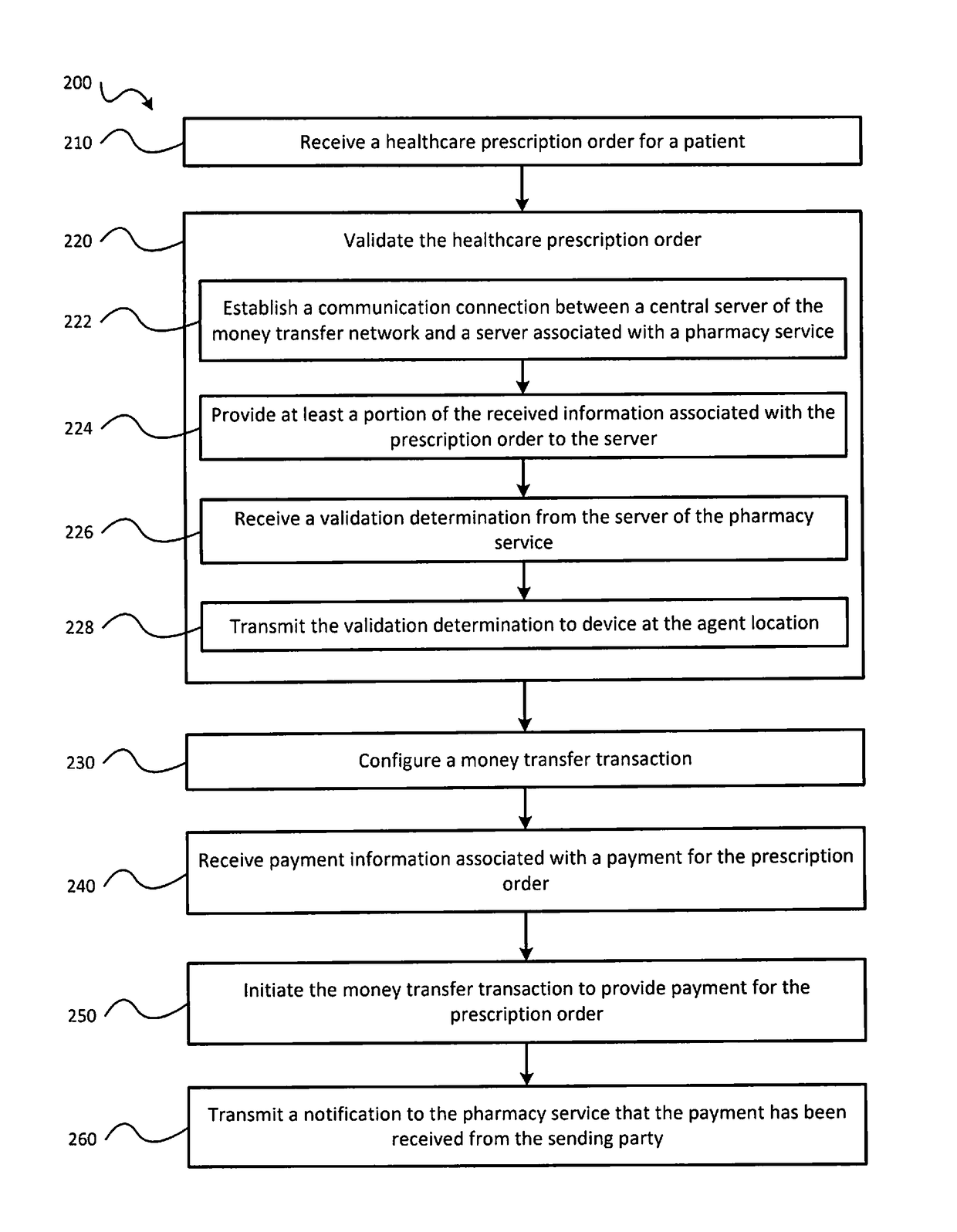
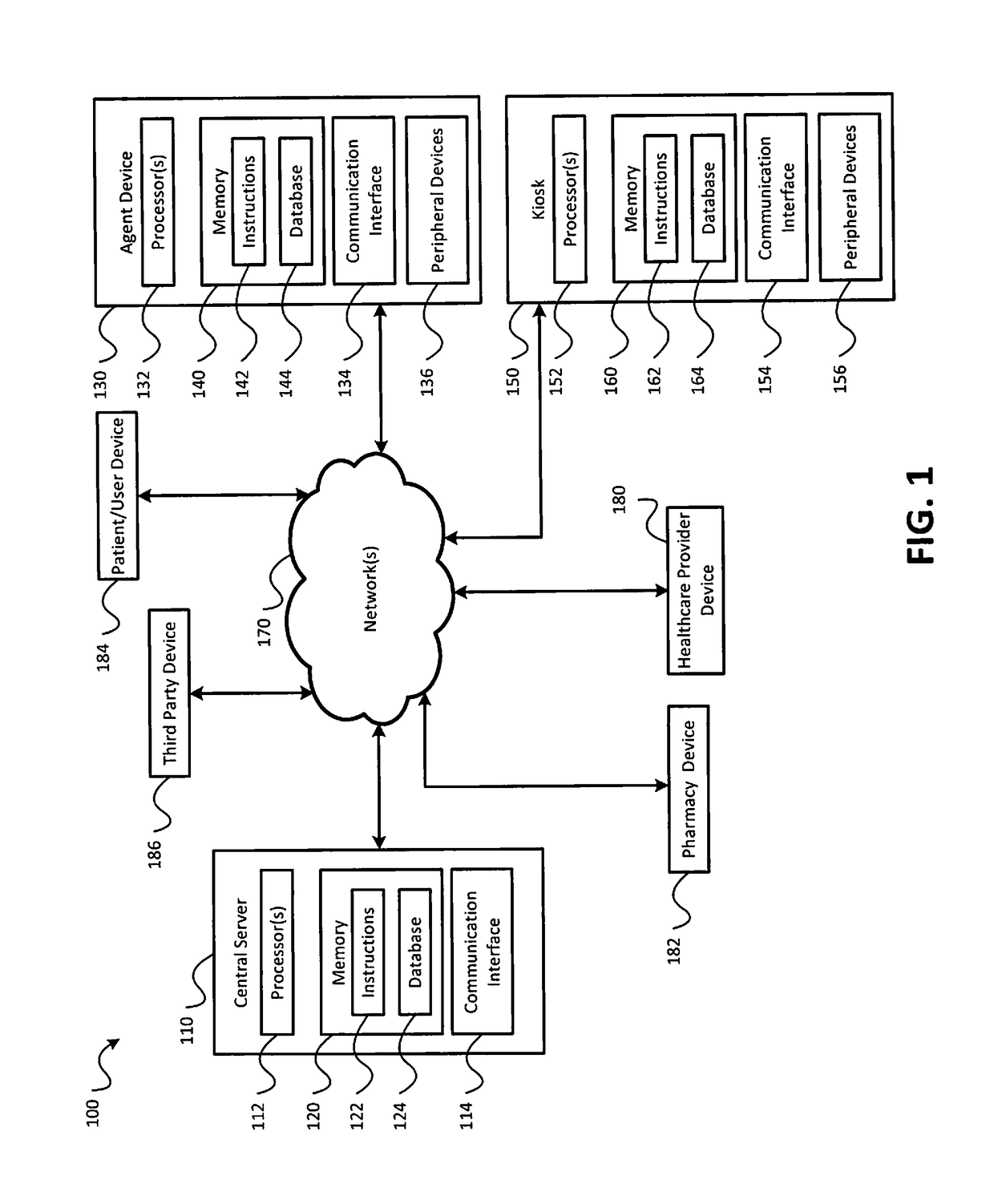
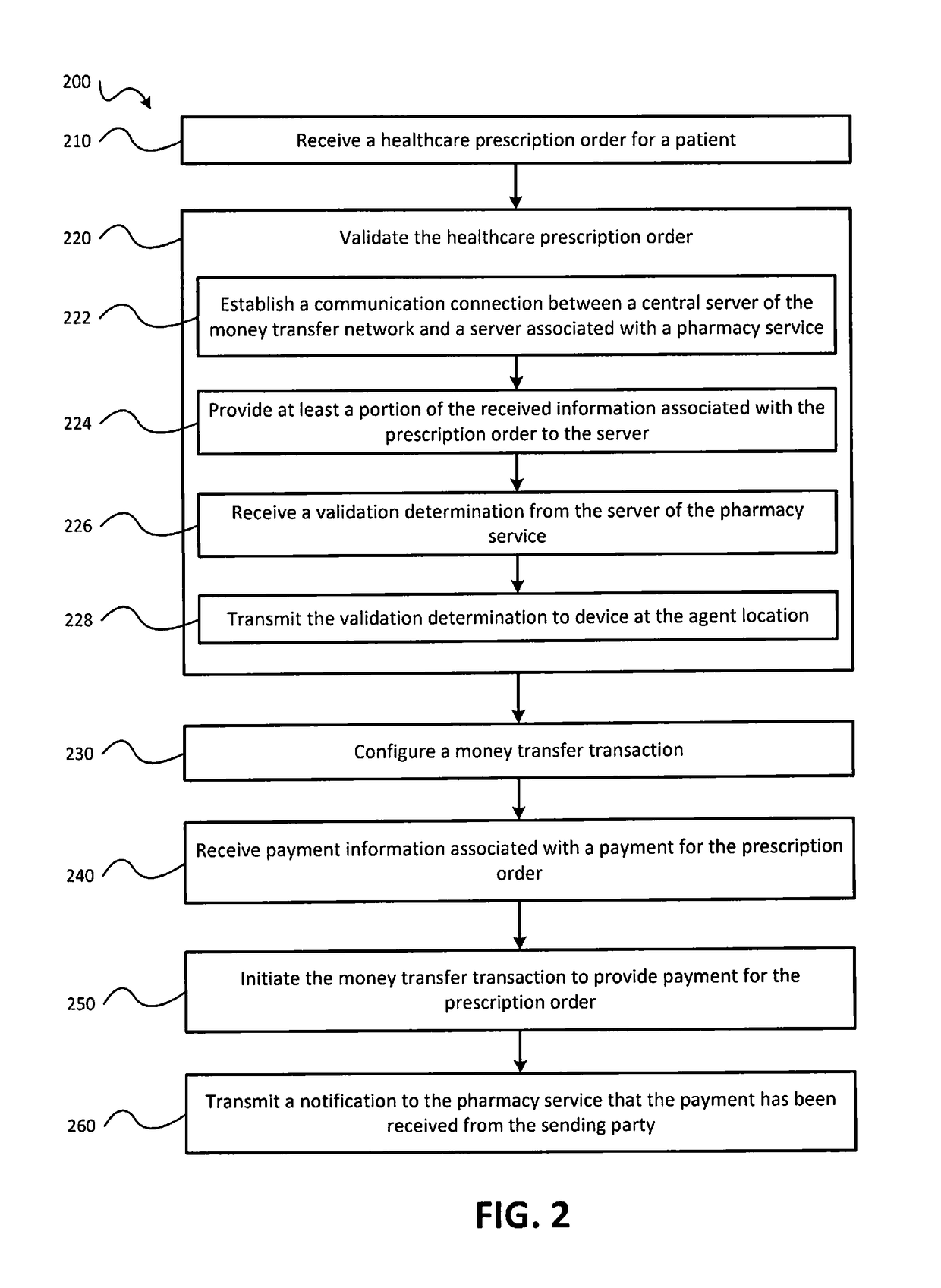
Healthcare prescription delivery techniques using a money transfer network
ActiveUS20170091414A1Optimize allocationEasy to payDrug and medicationsOffice automationThird partyPharmacy
Owner:MONEYGRAM INT
Session keeping method, session keeping device, readable storage medium and electronic equipment
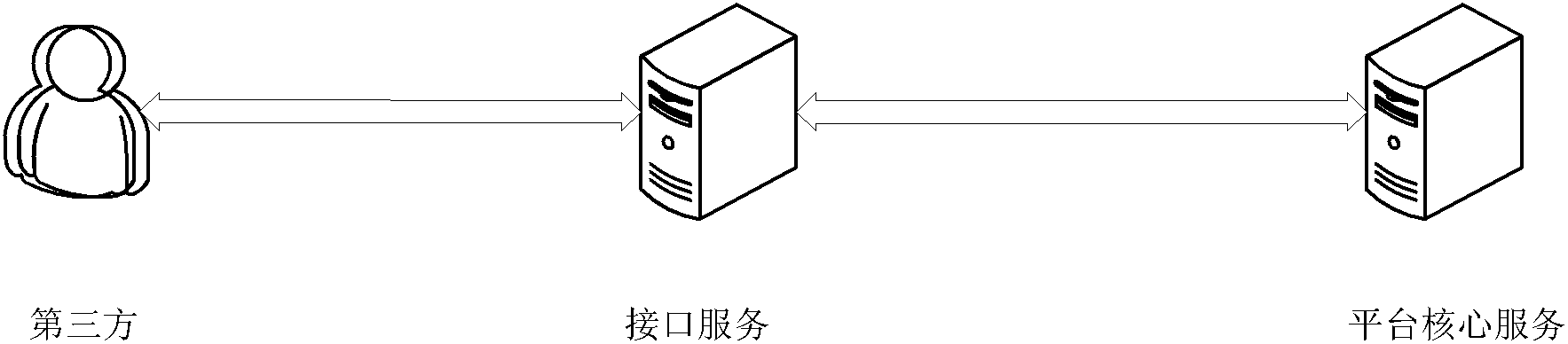
The invention relates to a session keeping method, a session keeping device, a readable storage medium and electronic equipment. The method is applied to a gateway, and comprises the following steps:when a first HTTP message carrying first Cookie information sent by a client is received, obtaining a gateway session ID and server session identification information from the first Cookie information; if determining that the first HTTP message is sent to the server according to the gateway session ID, determining a first target service node used for receiving the first HTTP message from a plurality of service nodes of the server; and if the identification information of the first target service node is matched with the identification information of the service node in the server session identification information, sending a first HTTP message carrying second Cookie information to the first target service node. Thus, a third-party middleware does not need to be additionally deployed to store the gateway session and the server session, and the gateway session and the server session do not need to be stored in the Cookie information, so that the problems in related technologies can be avoided, and the communication efficiency is ensured.
Owner:NEUSOFT CORP +1
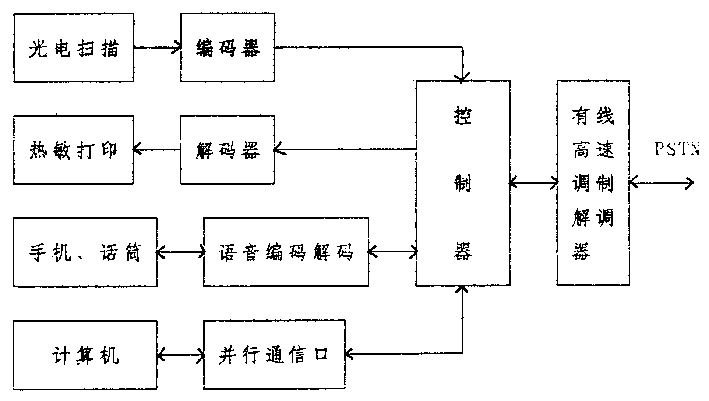
Multifunction facisimile apparatus
InactiveCN1409549AAdd voice codec technologyAdd parallel communication portPictoral communicationThird partyEncoder decoder
Owner:信息产业部电子第三十研究所
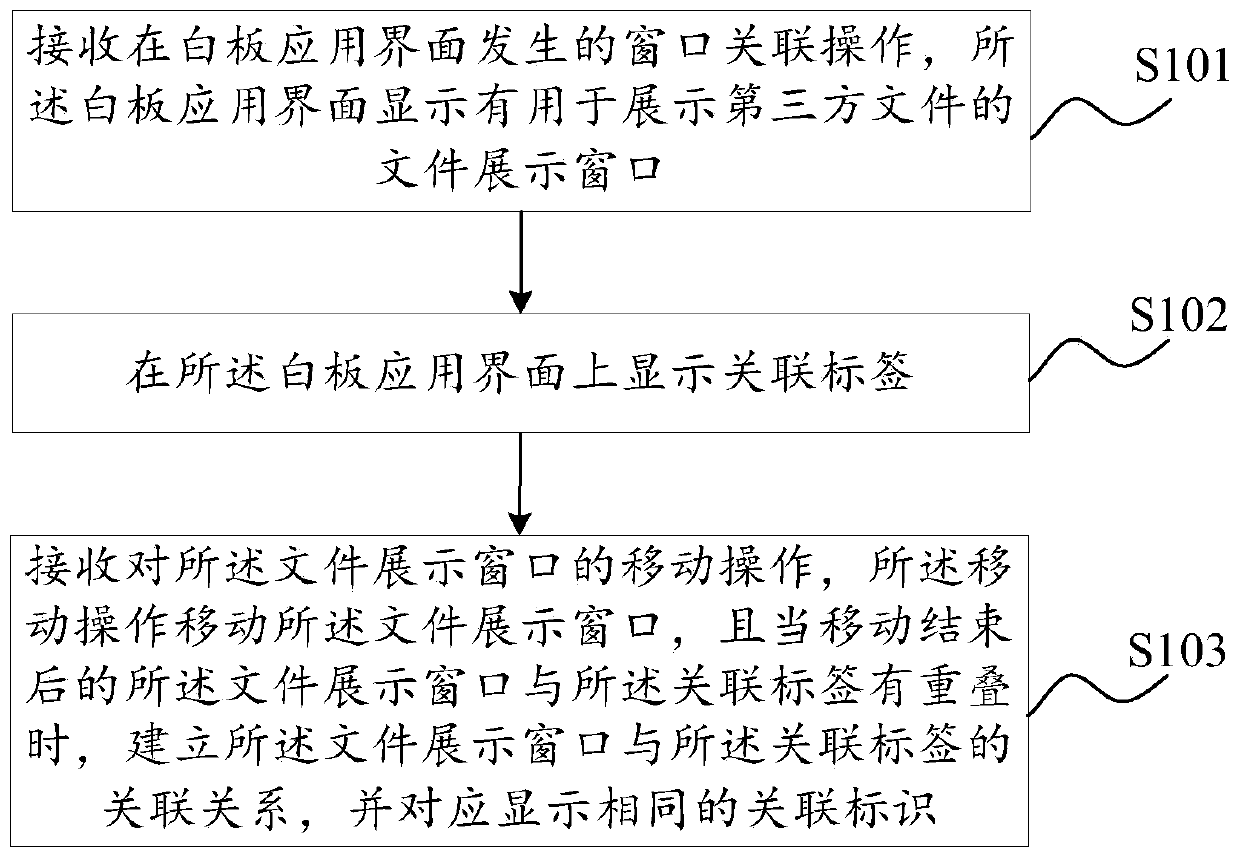
Interaction method and device of intelligent interaction panel computer, terminal equipment and storage medium
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD +1
Radio resource control connection method and device, and computer storage medium
ActiveCN108430070AEasy to useReduce transmission delayConnection managementHigh level techniquesThird partyAir interface
The embodiment of the invention discloses a radio resource control connection method and device, and a computer storage medium. The method is applied to a mobile terminal, and comprises the followingsteps: detecting an operation state of a third-party application, wherein the operation state is used for representing the operation condition of the three-party application; when the operation statemeets a preset acceleration policy, sending a random data packet to a base station, wherein the random data packet is an illegal internet protocol IP data packet sent by a packet data convergence protocol PDCP layer to the base station; and based on the response of the base station to the random data packet, maintaining the connection with the radio resource control RRC of the base station. Therefore, the transmission delay of data from the mobile terminal to an air interface is shortened, the instantaneity of data transmission is improved, and the use performance of the mobile terminal is improved as well.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
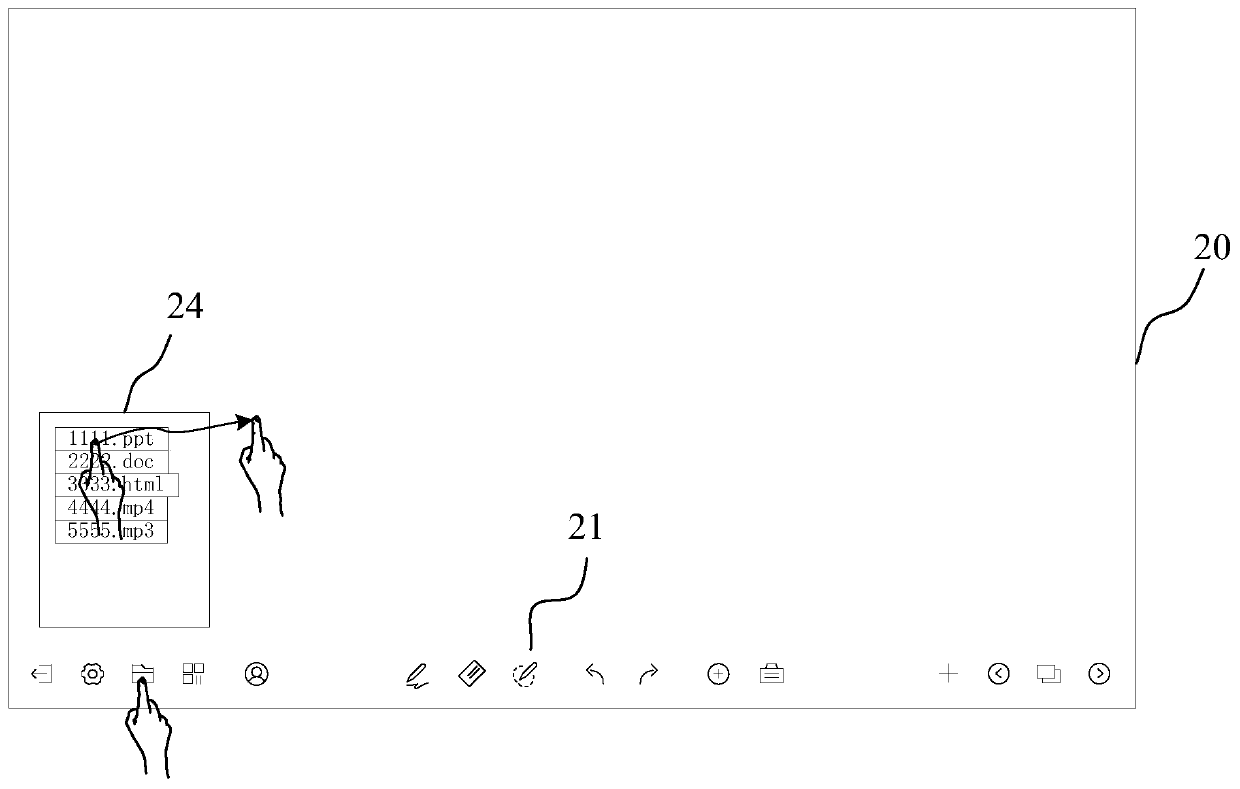
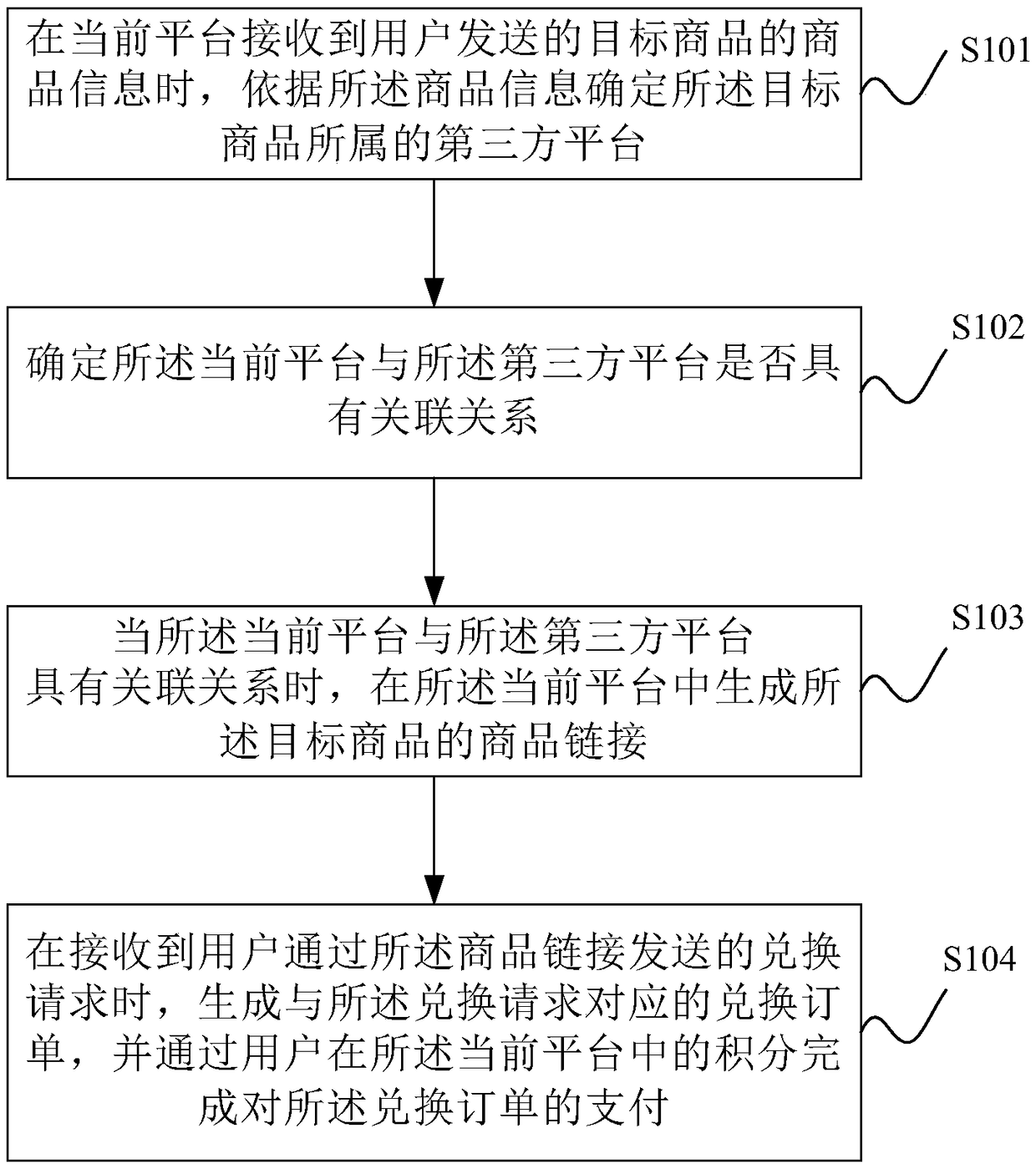
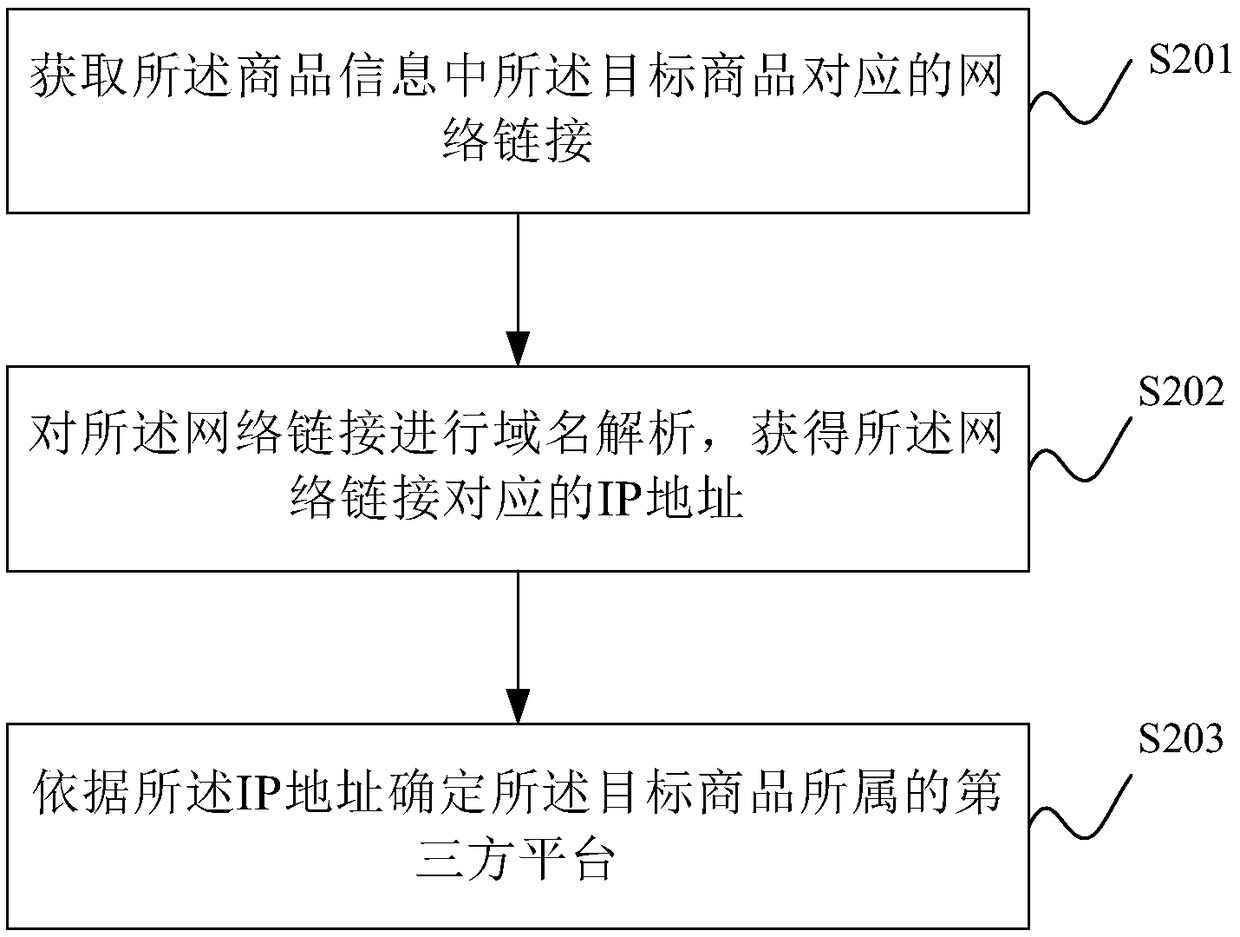
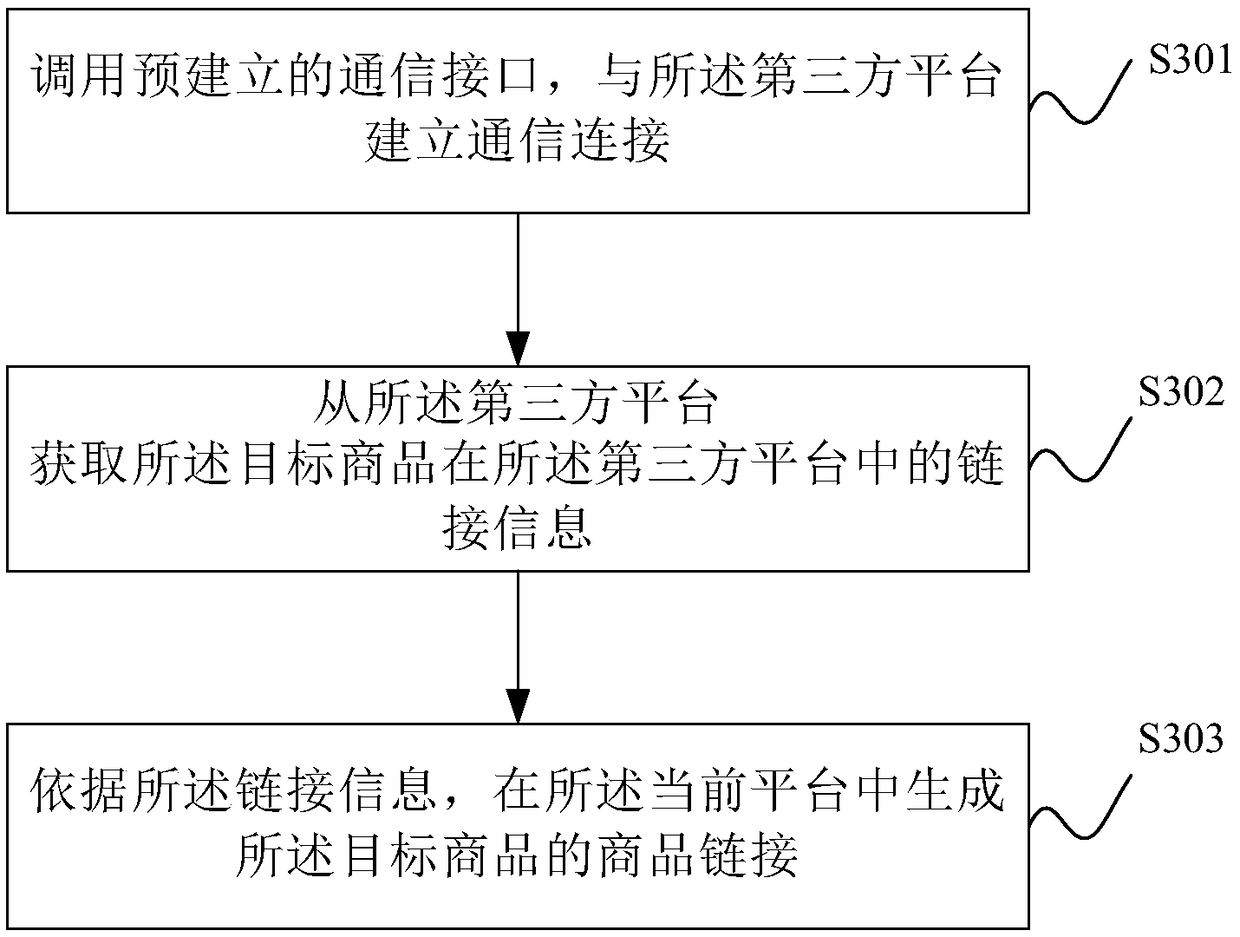
Method and device for exchanging platform integral
Owner:TAIKANG LIFE INSURANCE CO LTD +1
Methods and systems for monitoring a venue
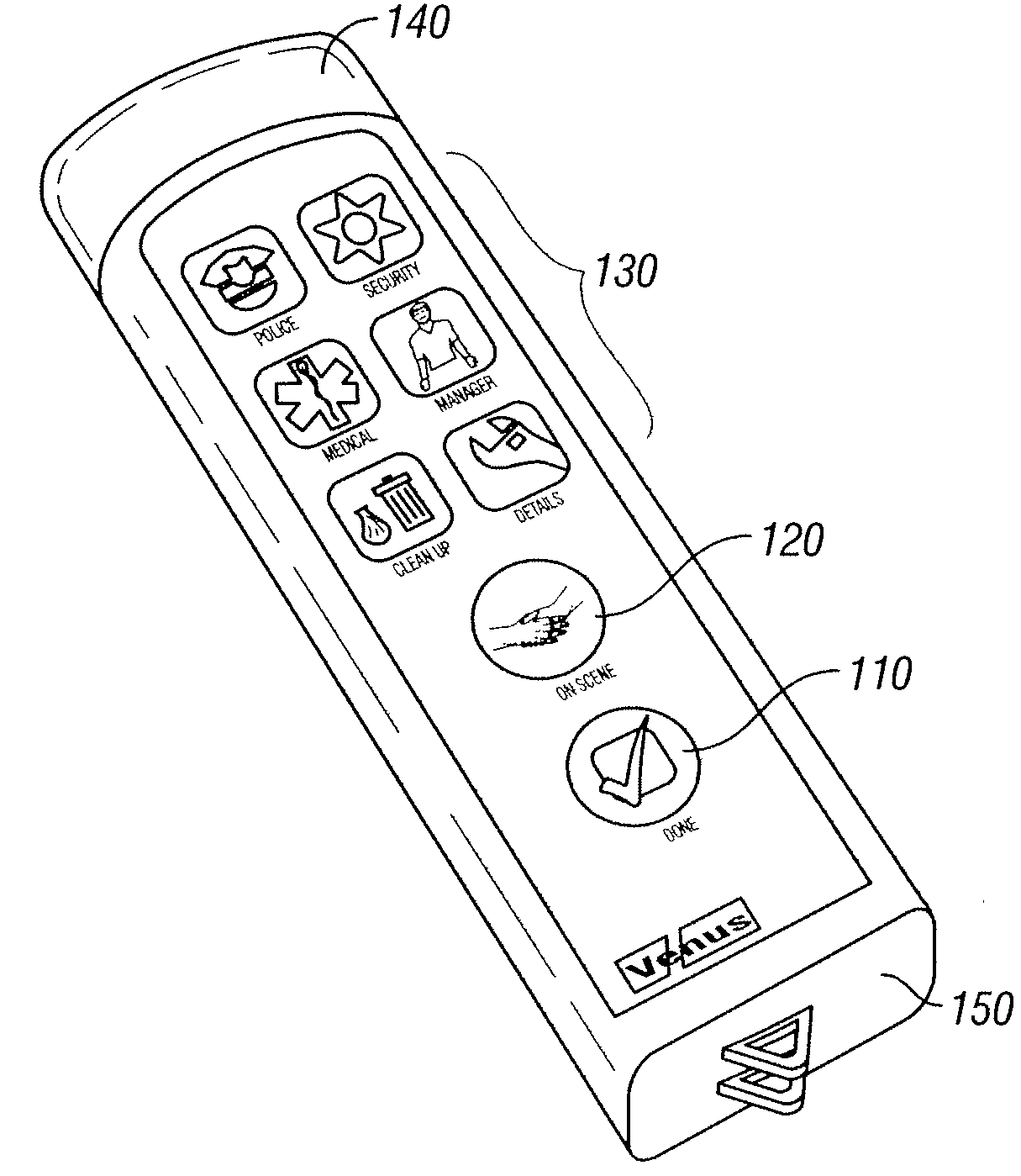
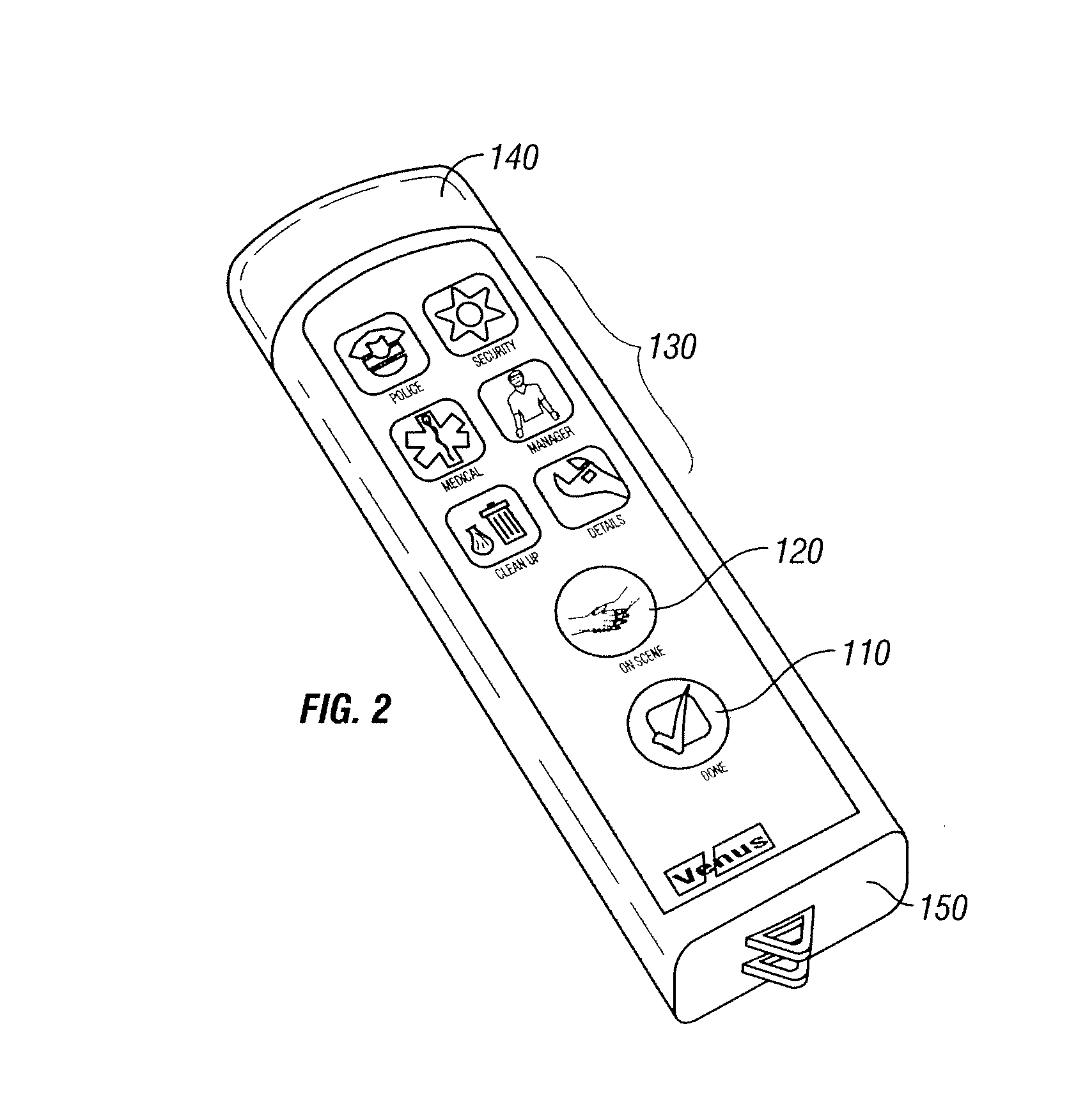
Owner:VENUESOFT
Methods and apparatus for a wireless terminal with third party advertising: dual authentication method
InactiveUS20060282384A1Improve receptivityIncrease exposureDigital data authenticationMarketingThird partyComputer hardware
Owner:MOCHIS INVESTMENT
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap