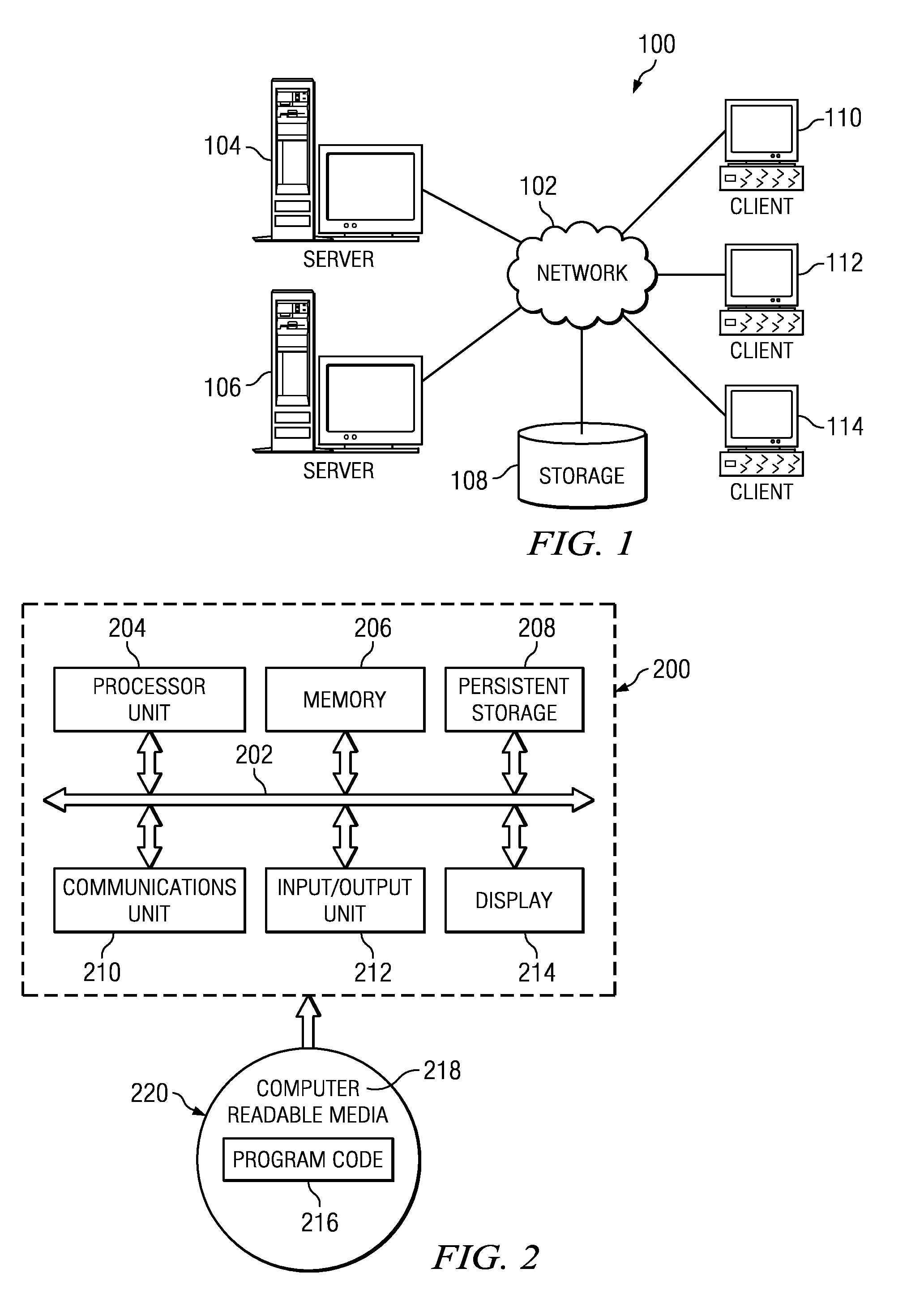
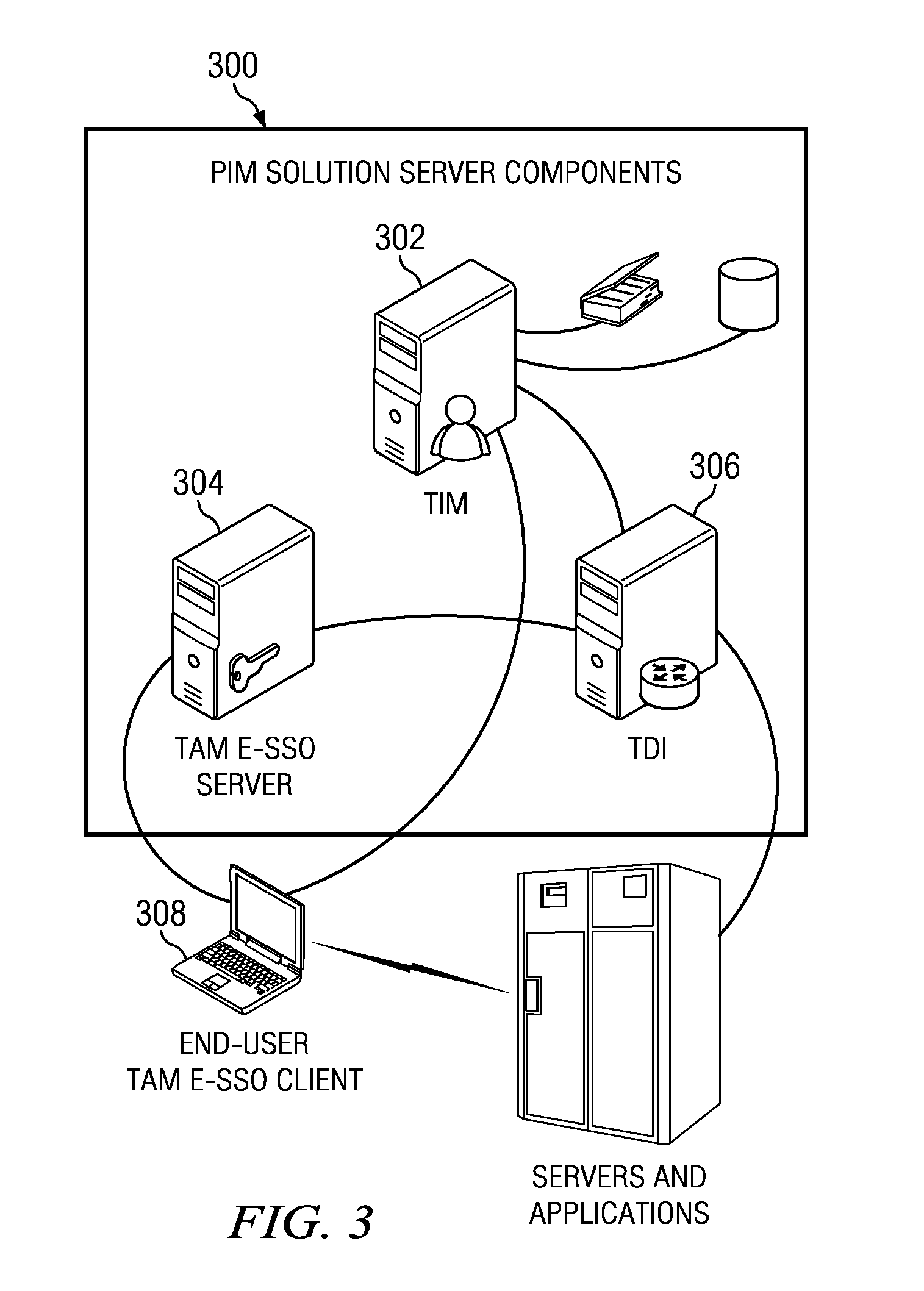
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1373results about "Special data processing applications" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
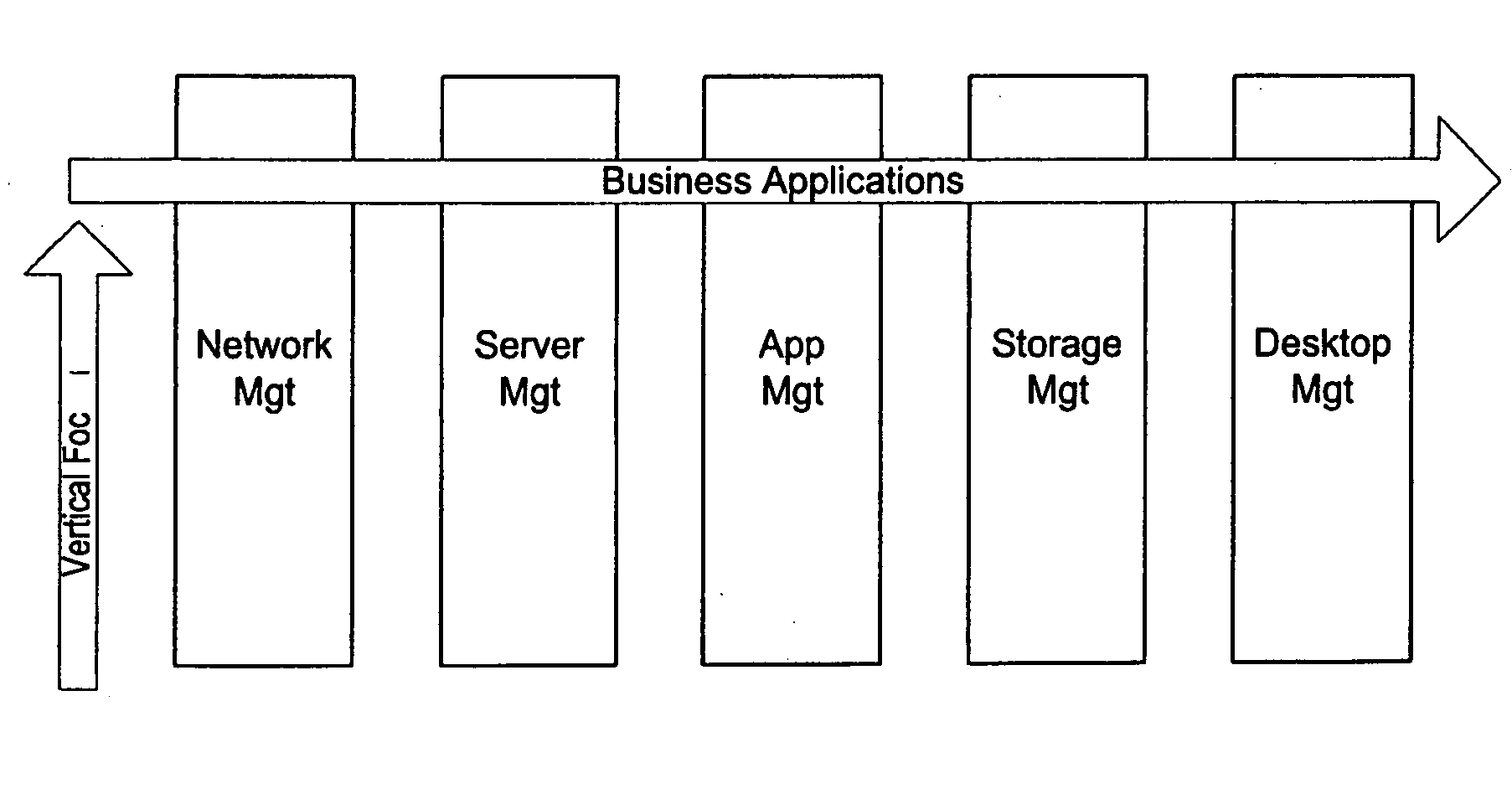
Room key based in-room player tracking
A disclosed authentication instrument is used to authorize various services at a hotel-casino complex, such as but not limited to in-room gaming, in-room sports wagering, room access, safe access, mini-bar access, Electronic Fund Transfers (EFT), player tracking services and in-room entertainment services (e.g., video games and movie channels). A smart card, an electronic token and a magnetic striped card are examples of hardware that may be used as authentication instruments. For in-room gaming, the authentication instrument may be used to authorize, in a secure and legal manner, in-room game play sessions on an entertainment terminal connected to a remote gaming machine.
Owner:IGT
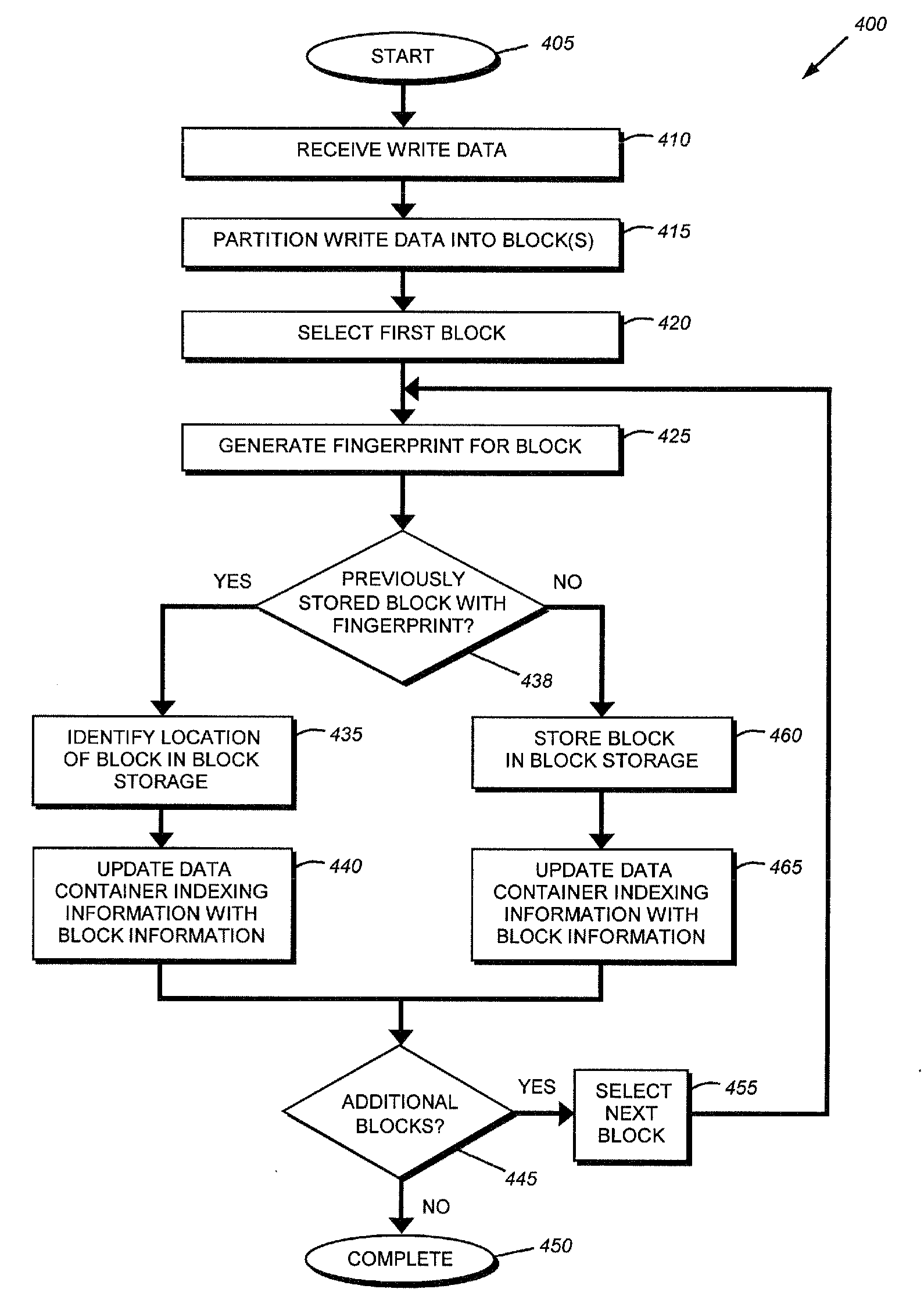
System and method for on-the-fly elimination of redundant data
ActiveUS20080294696A1Digital data information retrievalDigital data processing detailsOperational systemFile system
Owner:NETWORK APPLIANCE INC
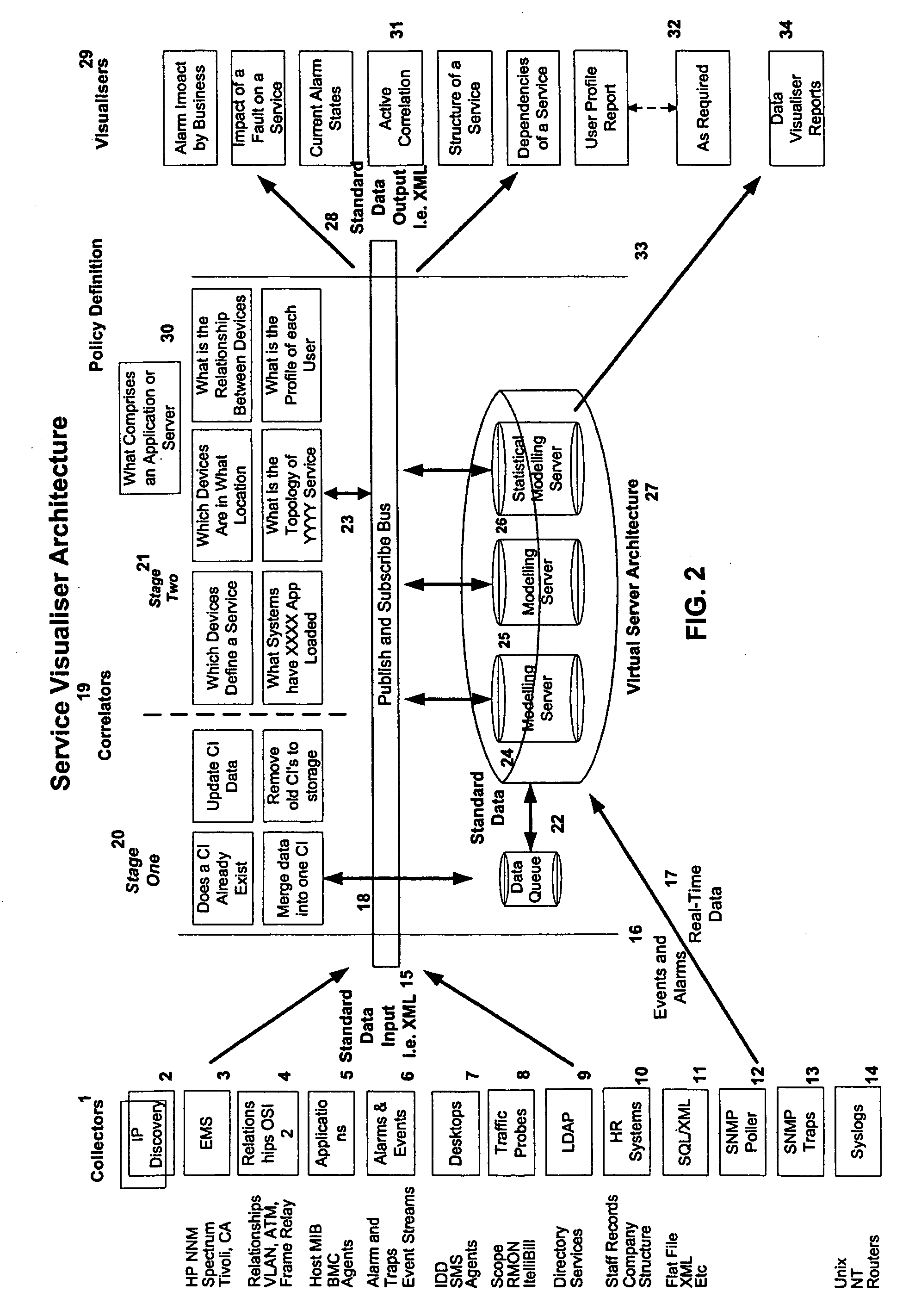
System and method for managing and presenting entity information
InactiveUS20060101005A1Easy to displayShorten the timeDigital data processing detailsMaps/plans/chartsTime rangeRunning time
Owner:YANG WENDY W +1
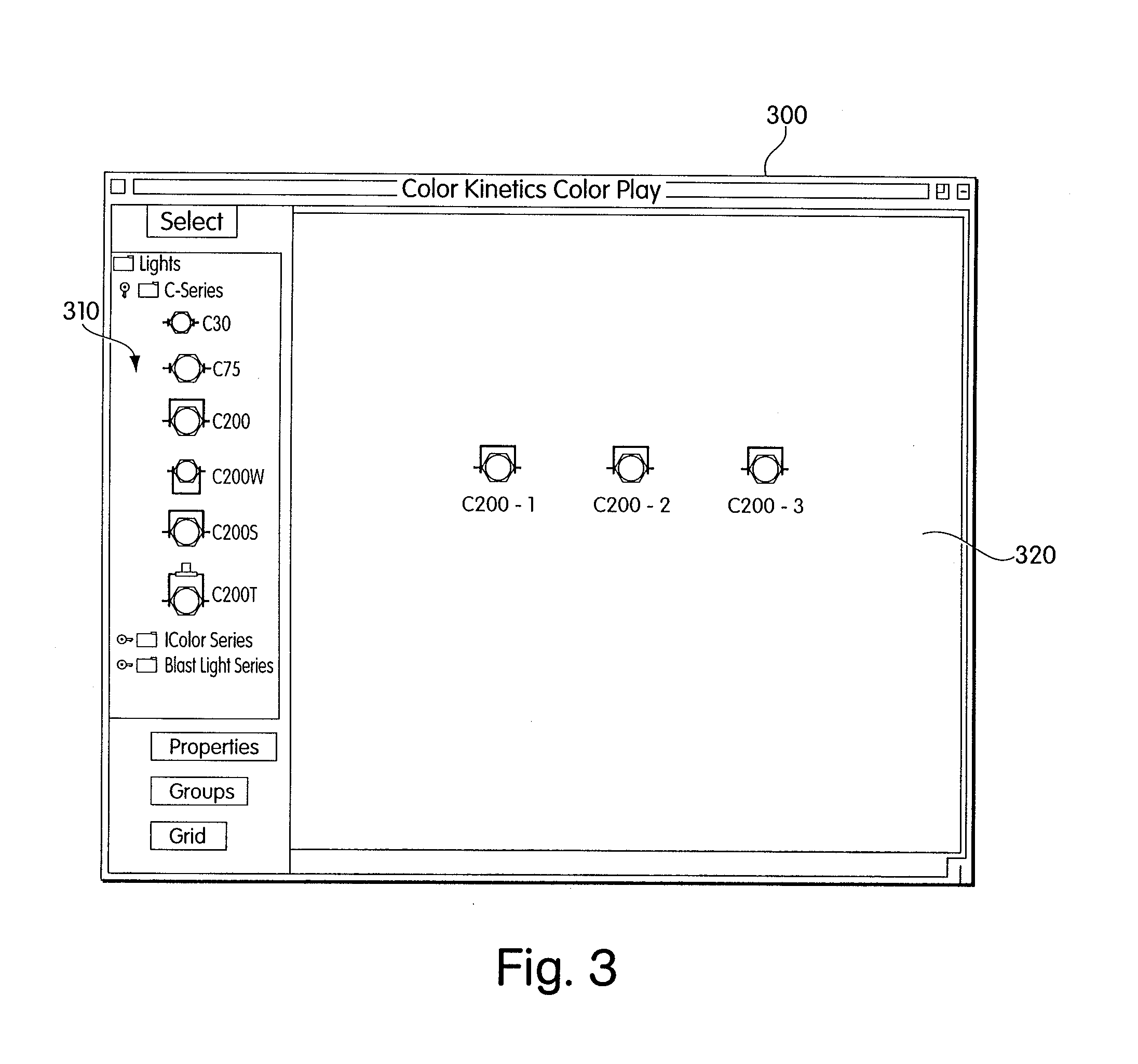
Method and apparatus for controlling a lighting system in response to an audio input
Owner:SIGNIFY NORTH AMERICA CORP
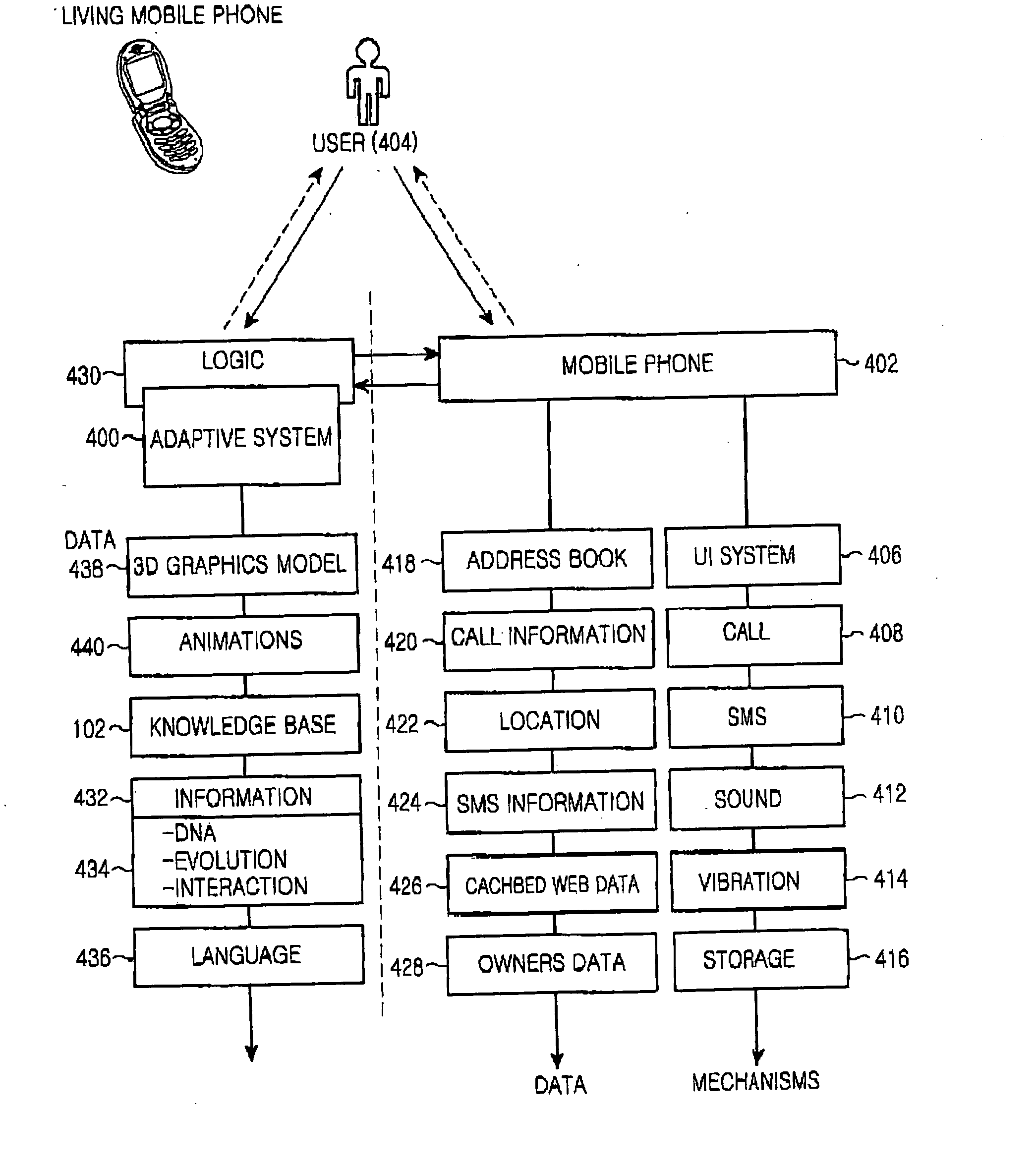
Proactive user interface including emotional agent
ActiveUS20050143138A1Increase sense of intelligenceDevices with sensorSubstation equipmentTouchscreenUser interface
Owner:SAMSUNG ELECTRONICS CO LTD
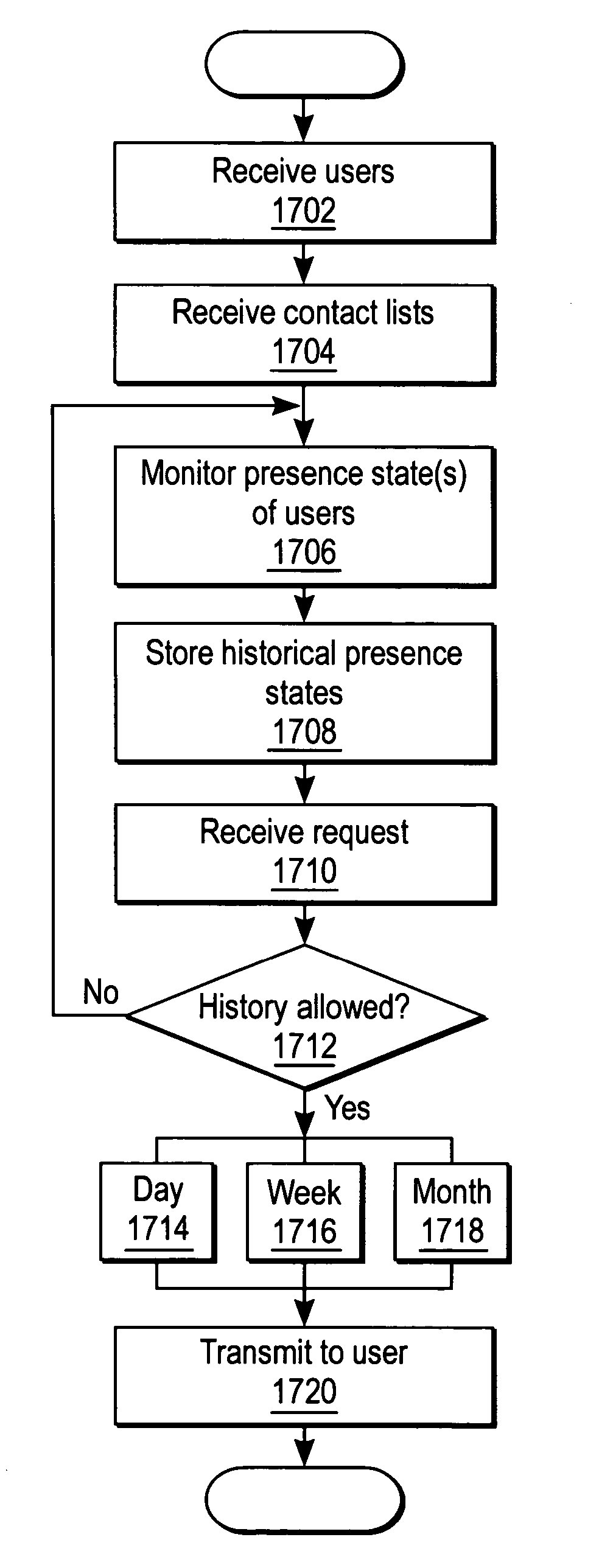
System and method for predicting availability
Owner:SIEMENS ENTERPRISE COMM GMBH & CO KG
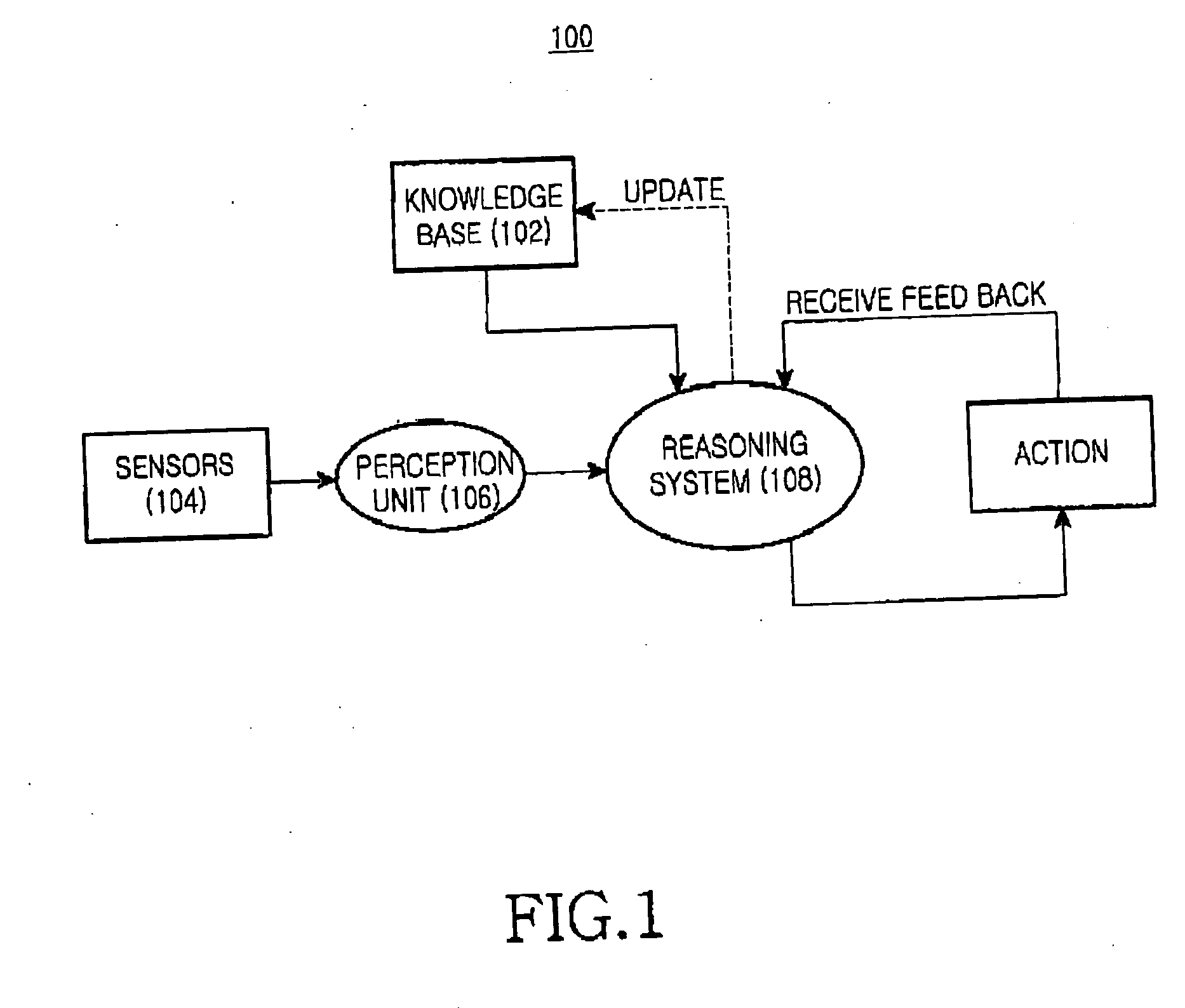
Methods for combating malicious software
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
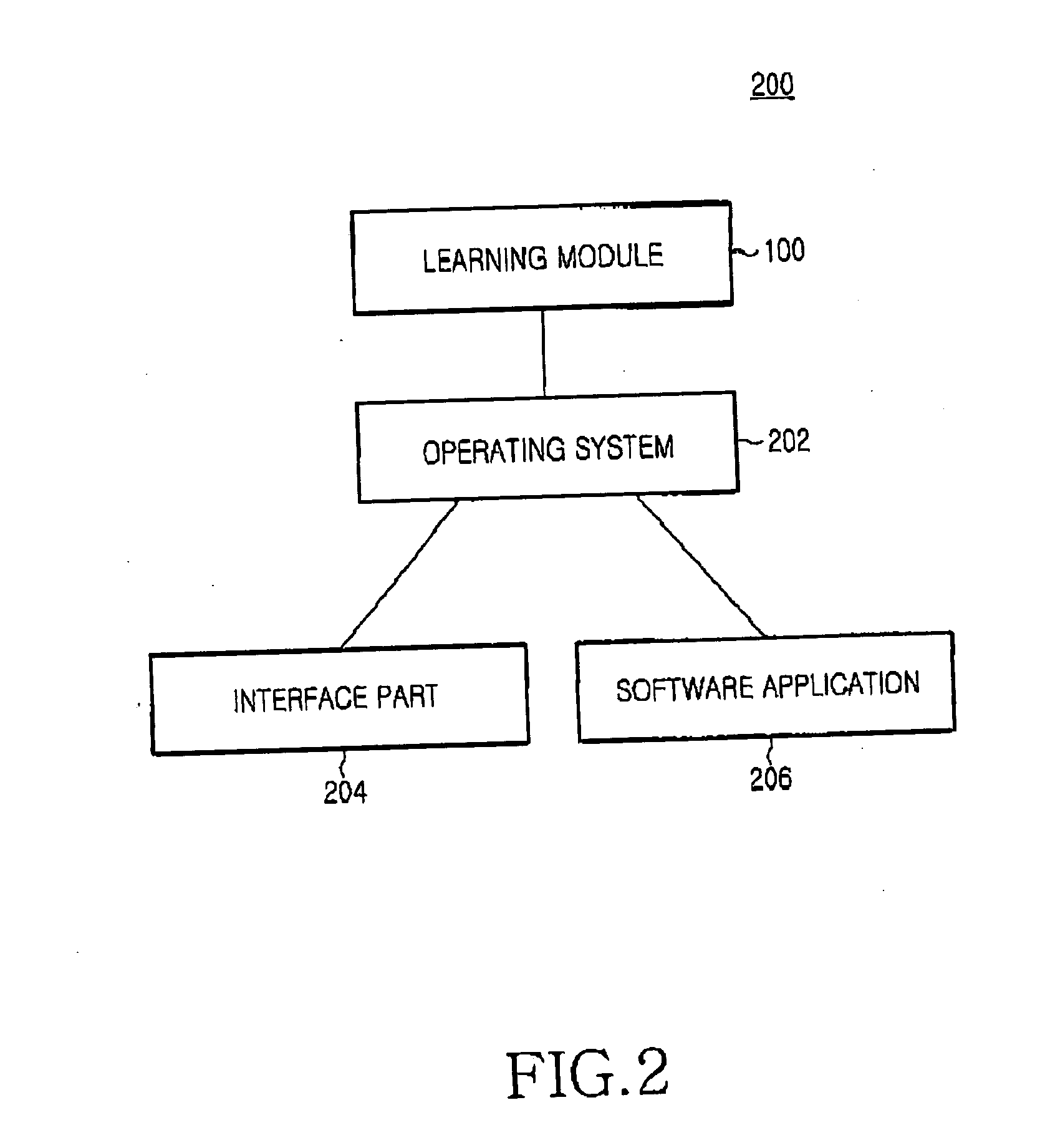
Dynamic identification and administration of networked clients
ActiveUS7568018B1Data resettingMultiple digital computer combinationsSubject matterDistributed computing
The present inventive subject matter relates to networked computing environments and more specifically to dynamic identification and administration of networked clients. Various embodiments of the present inventive subject matter include systems and methods for defining, on a server, a configuration of interest comprising one or more potential properties of a client, communicating the configurations of interest over a network to one or more clients, dynamically evaluating a client state relative to the configurations of interest, and communicating a representation of the client state in relation to the configuration of interest to the server. Further embodiments include automatically creating and displaying associations of clients based on configurations of interest. Yet further embodiments include clients requesting and receiving updates to the configurations of interest. Still further embodiments include actions associated with configurations of interest. Such actions, in various embodiments, include performing administrative actions on various networked clients.
Owner:NEW BOUNDARY TECH
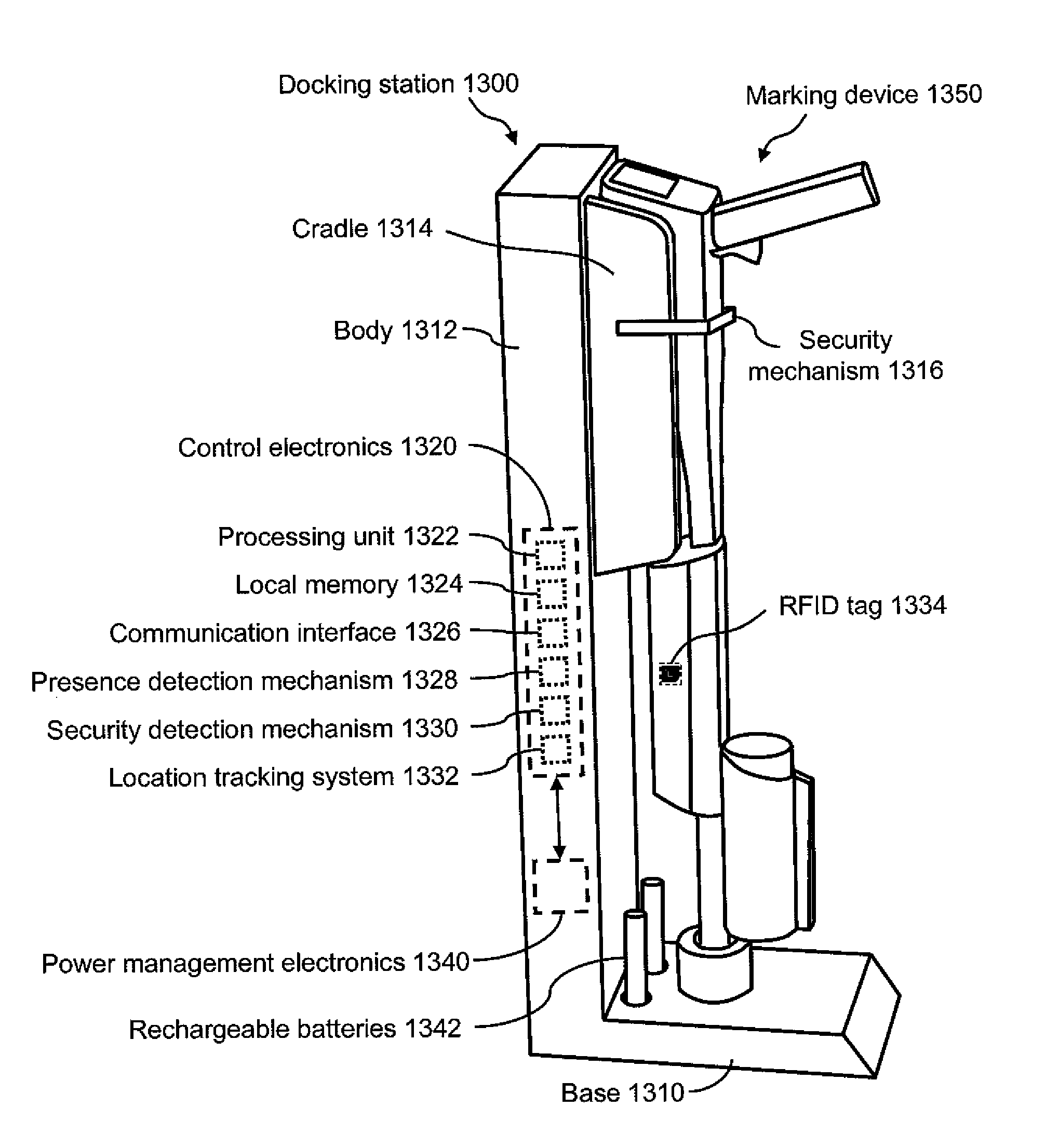
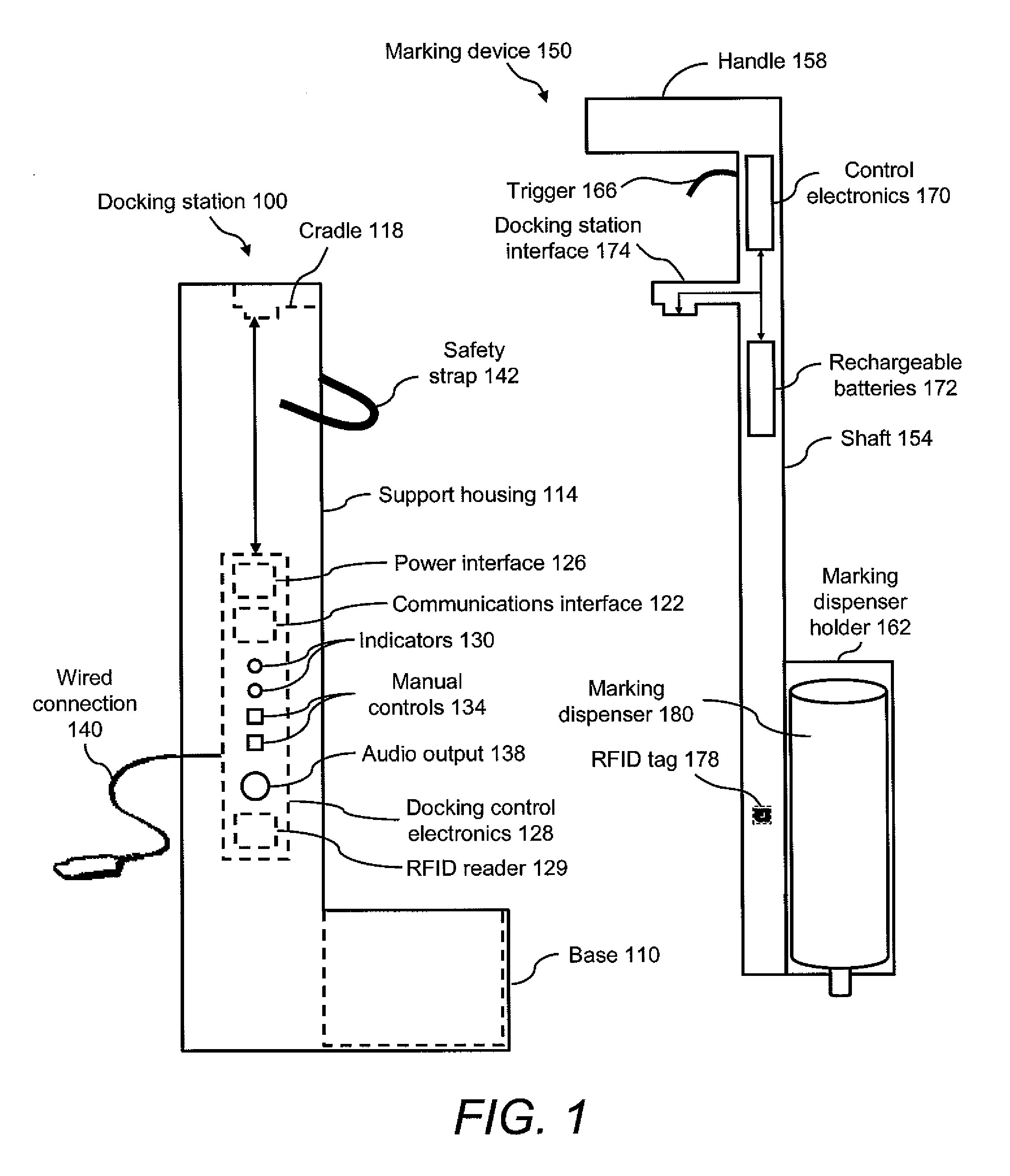
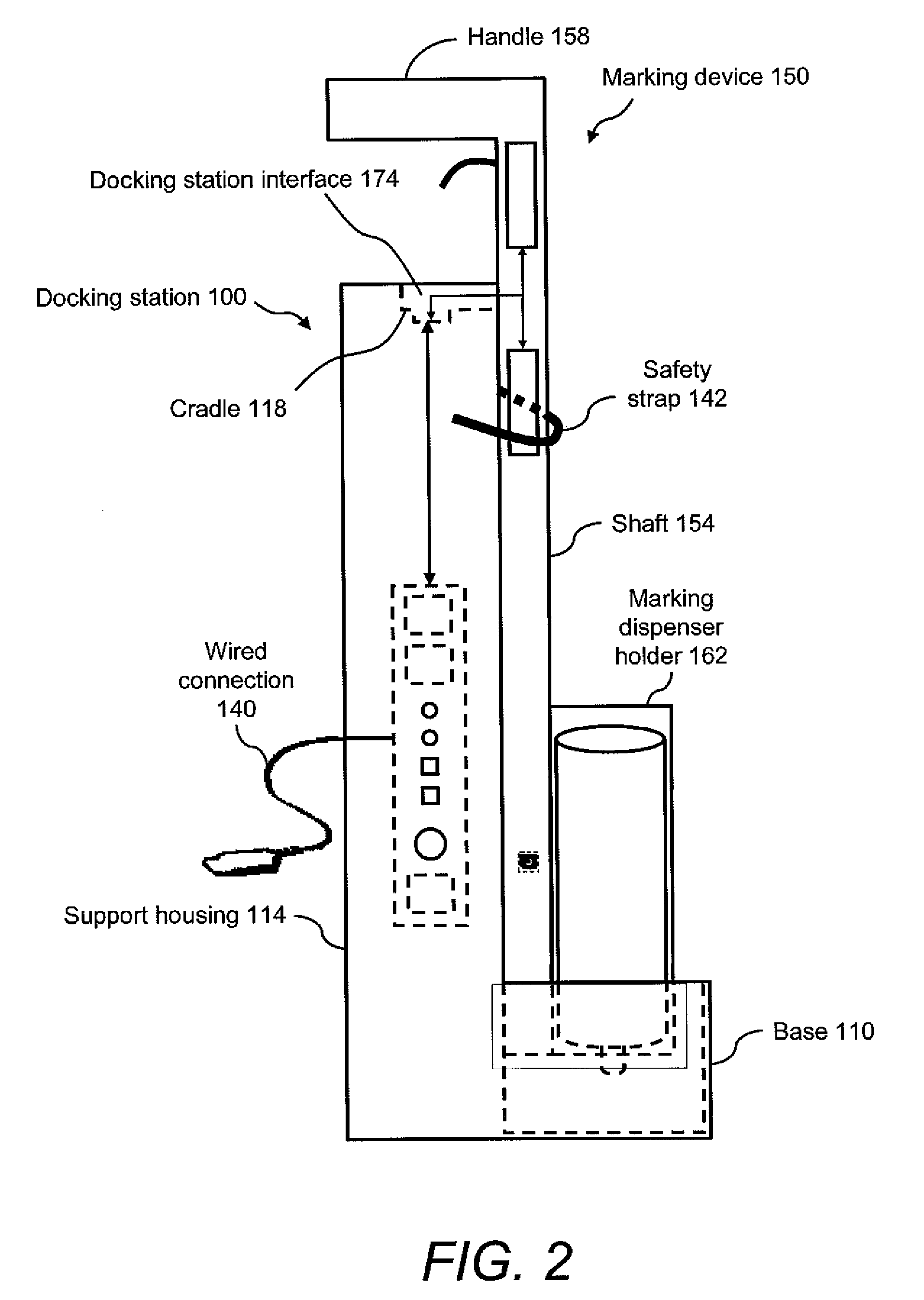
Marking device docking stations having security features and methods of using same
Owner:CERTUSVIEW TECH LLC
Systems, processes and apparatus for creating, processing and interacting with audiobooks and other media
InactiveUS20050276570A1Maximizing data compressionImprove playback qualityTelevision system detailsMetadata multimedia retrievalComputer hardwareSystematic process
Owner:INGRAM DV
Systems and methods for searching of storage data with reduced bandwidth requirements
InactiveUS20060059207A1Amount of data can be transmittedReduce the amount requiredDigital data information retrievalError detection/correctionTheoretical computer scienceLinearity
Owner:IBM CORP
Method and apparatus for consumer interaction based on spend capacity
InactiveUS20080228556A1Efficient use ofEfficient managementFinanceSpecial data processing applicationsBalance transferInsurance life
Owner:EXPERIAN MARKETING SOLUTIONS
Self-service platform for selling advertising
InactiveUS20050027594A1Low costImprove operational flexibilityAdvertisementsSpecial data processing applicationsThe InternetSelf-service
Owner:OATH INC
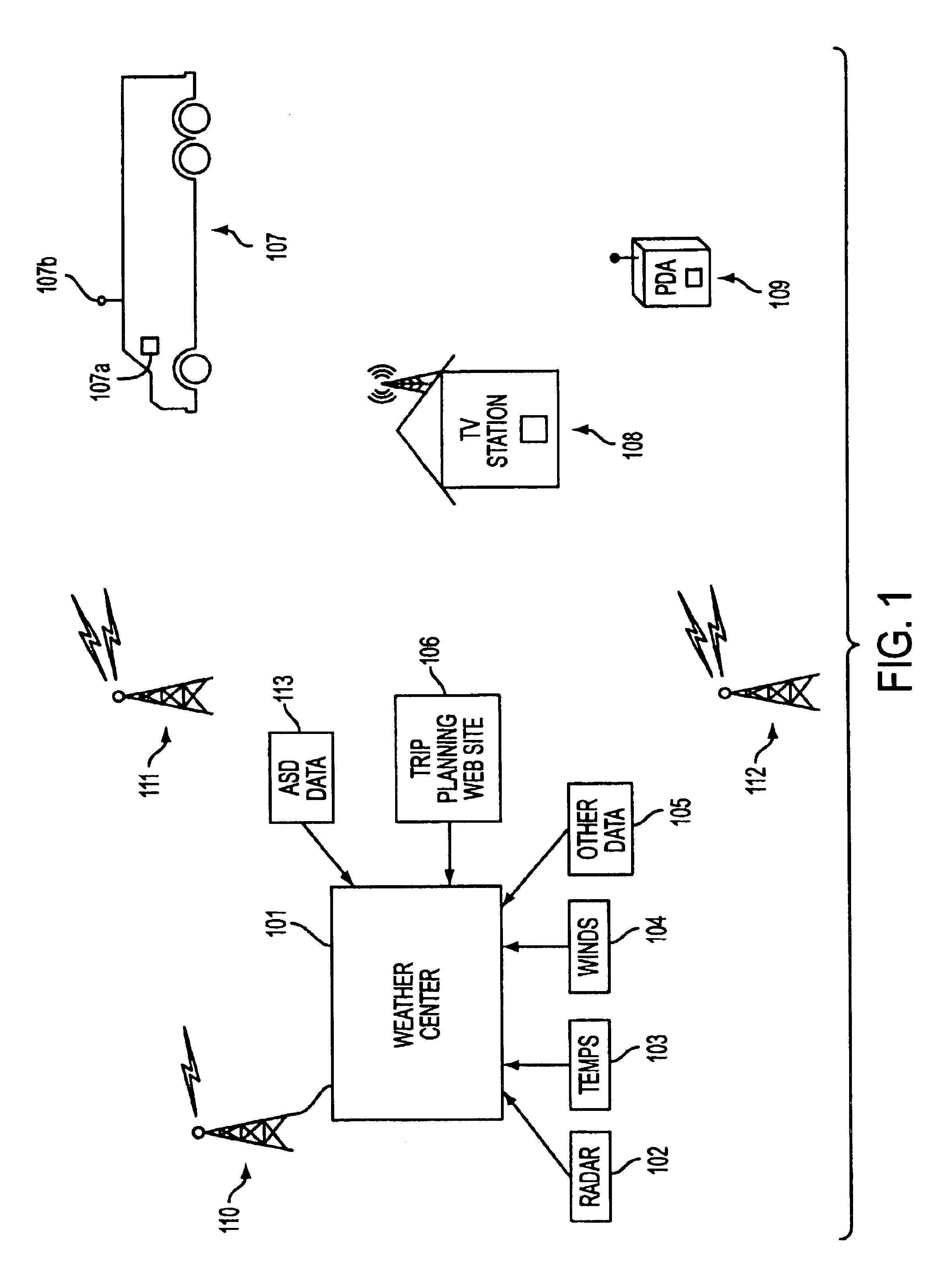
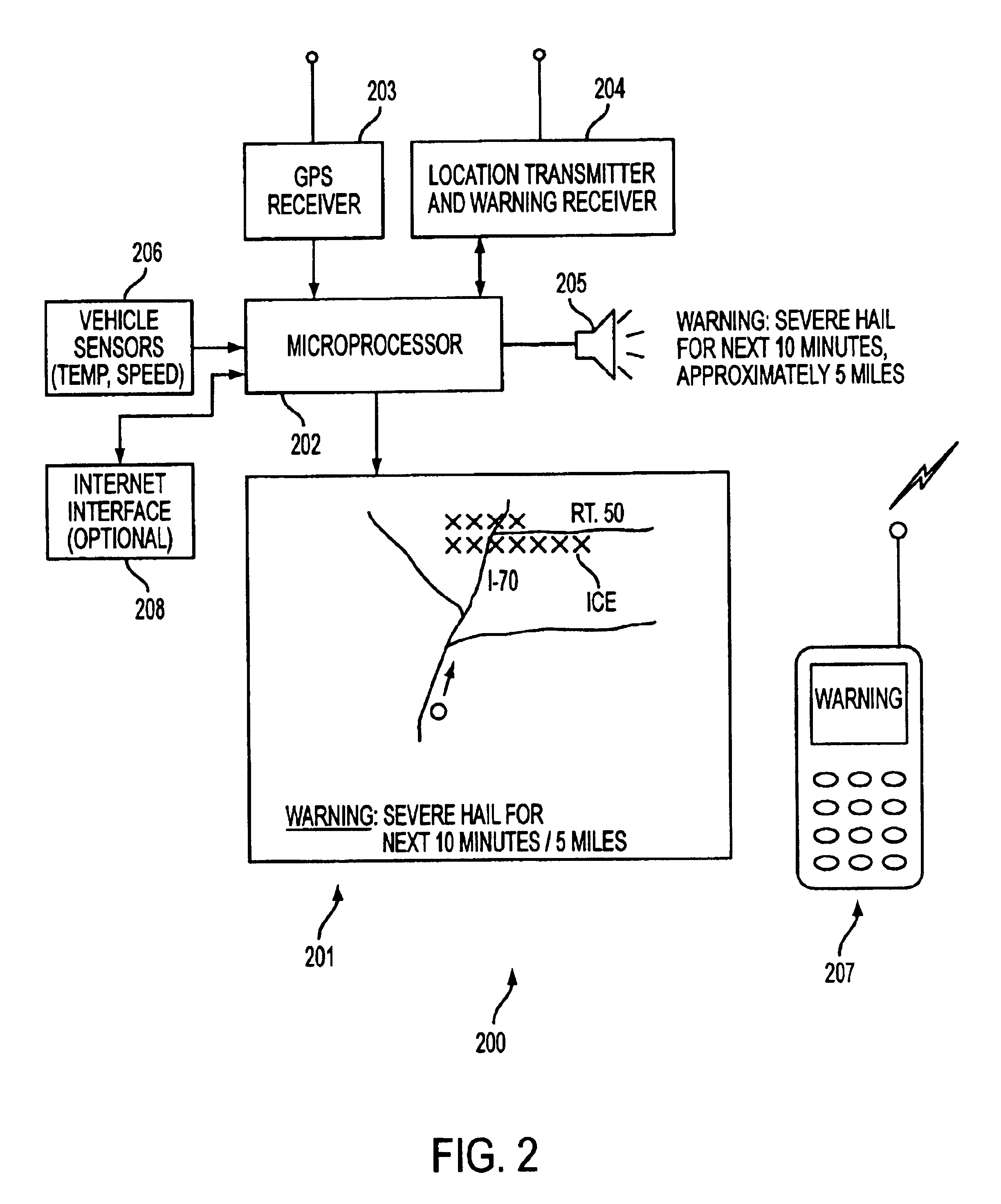
Rotating map and user-centric weather prediction
InactiveUS6845324B2Wide rangeDigital computer detailsAlarmsNumerical weather predictionAtmospheric sciences
Owner:USER CENTRIC IP
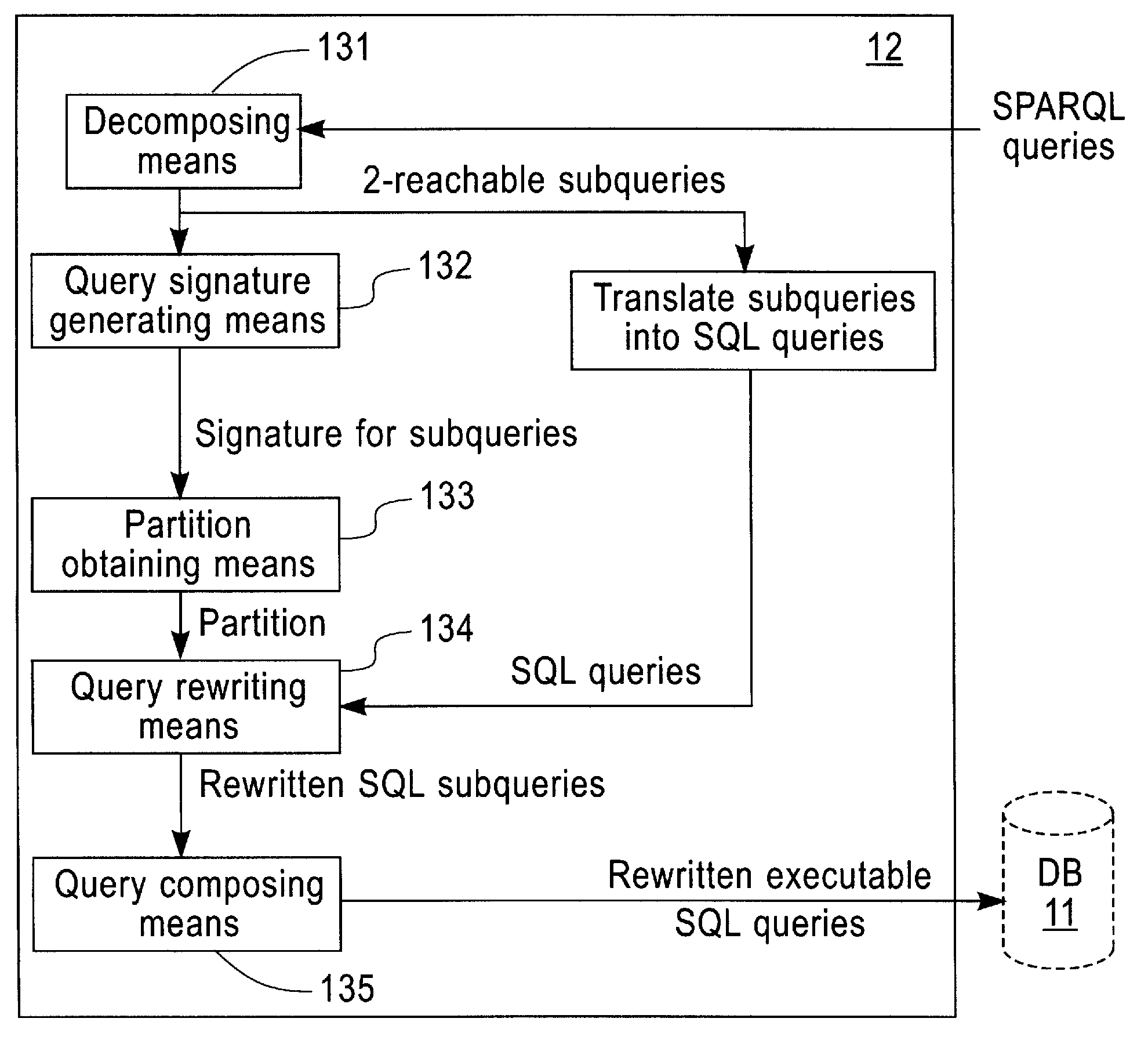
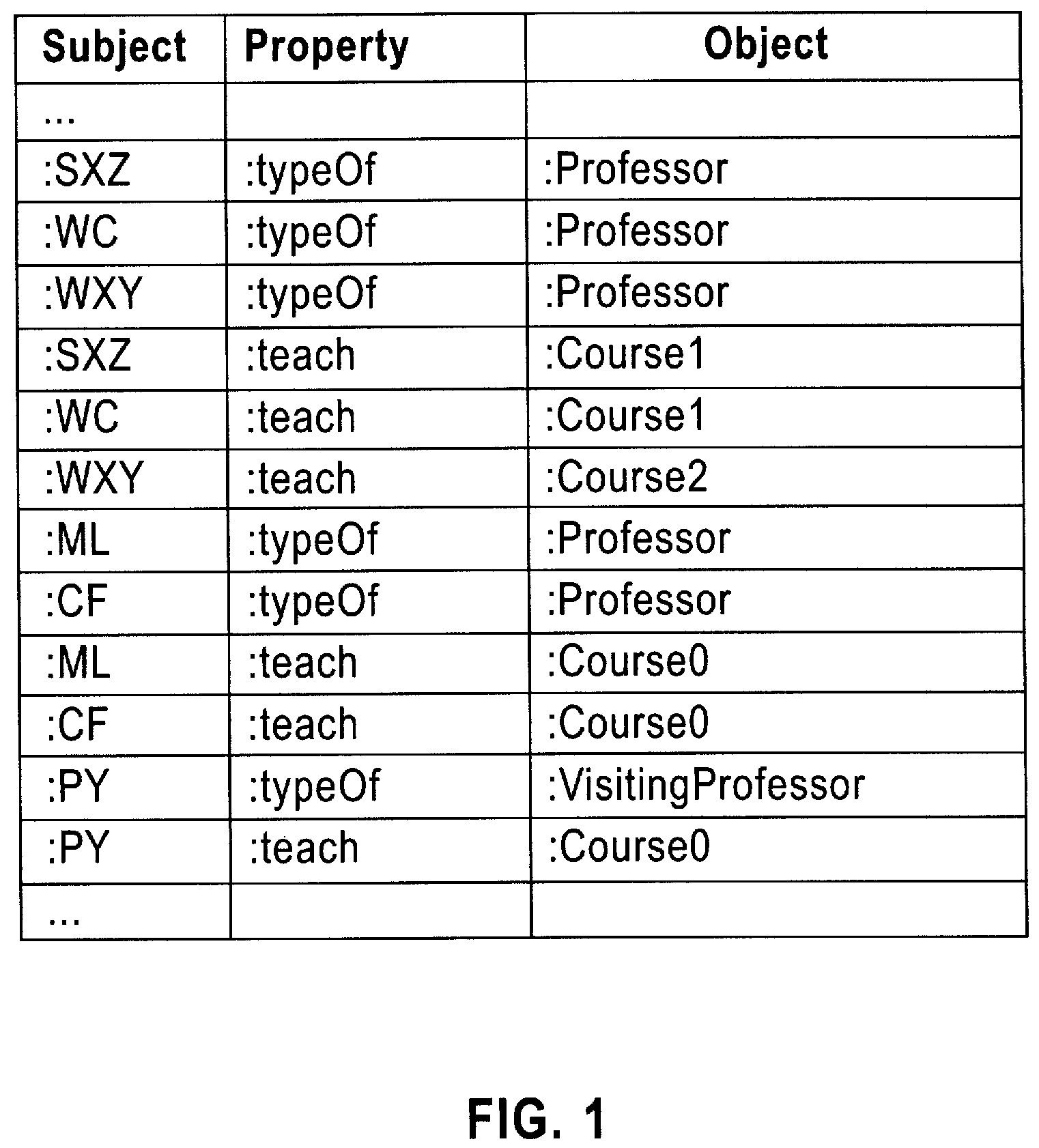
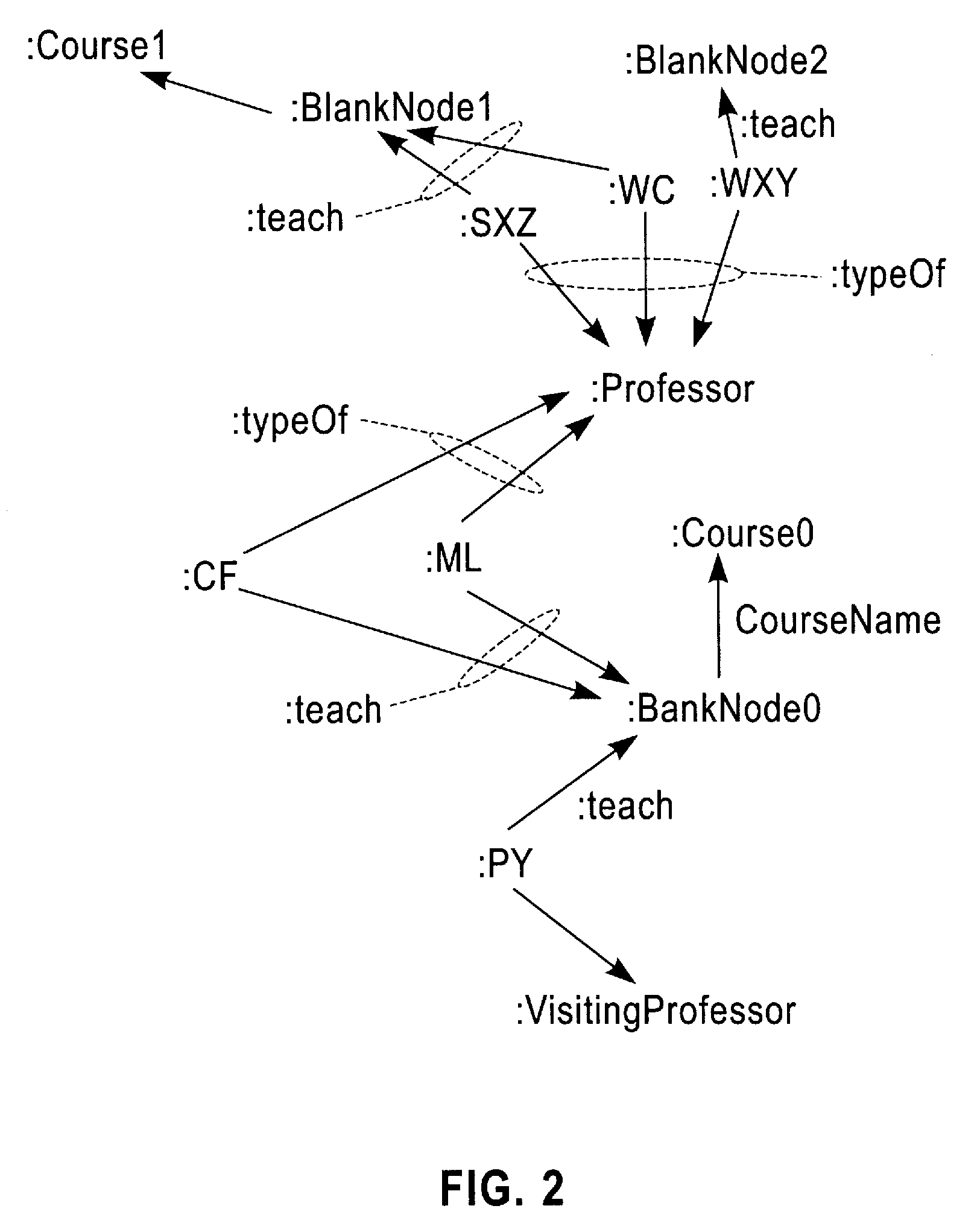
Method and Apparatus for Optimizing Queries over Vertically Stored Database
InactiveUS20090132474A1Good effectDigital data information retrievalDigital data processing detailsData miningComputer science
Owner:IBM CORP
Automated application discovery and analysis system and method
ActiveUS20060123022A1Digital data processing detailsObject oriented databasesSystems designMonitoring system
Owner:GLOBAL SAAS SOLUTIONS PTE LTD
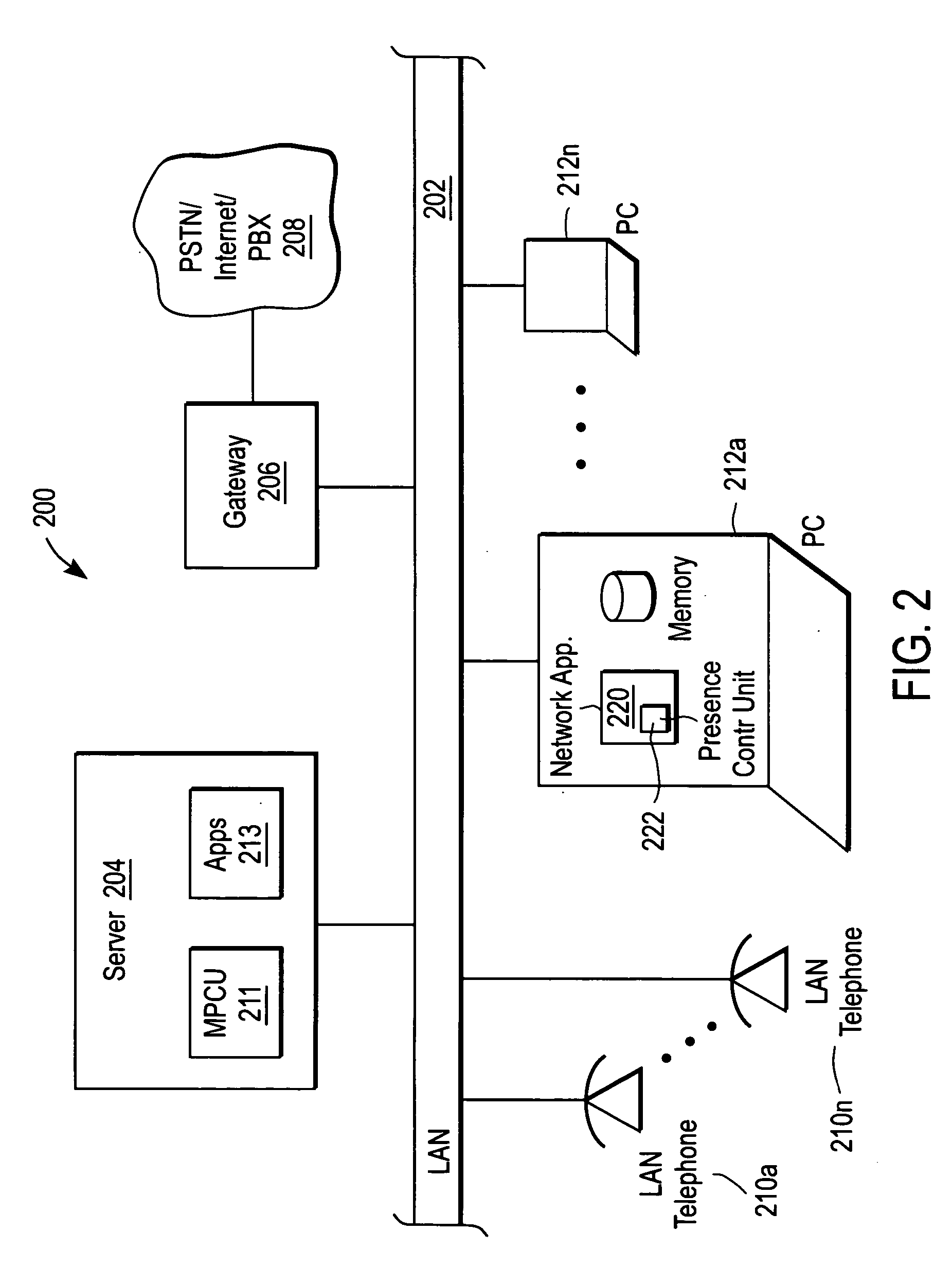
Method and apparatus for providing group calls via the internet
InactiveUS6865540B1Special service for subscribersOffice automationComputer networkService provision
Method and apparatus for implementing group calling are disclosed. In one embodiment, the method includes displaying a service provider, a service provider rate for communicating with the service provider, and a real-time indication of whether the service provider is available. The method may further include receiving a request from a first customer to communicate with the service provider and connecting the first customer to the service provider through a link capable of transmitting from the service provider to the first customer. The method may also further include receiving a request from a second customer to communicate with the service provider and connecting the second customer to the service provider through a link capable of transmitting from the service provider to the second customer while the first customer is coupled to the service provider.
Owner:THRYV INC
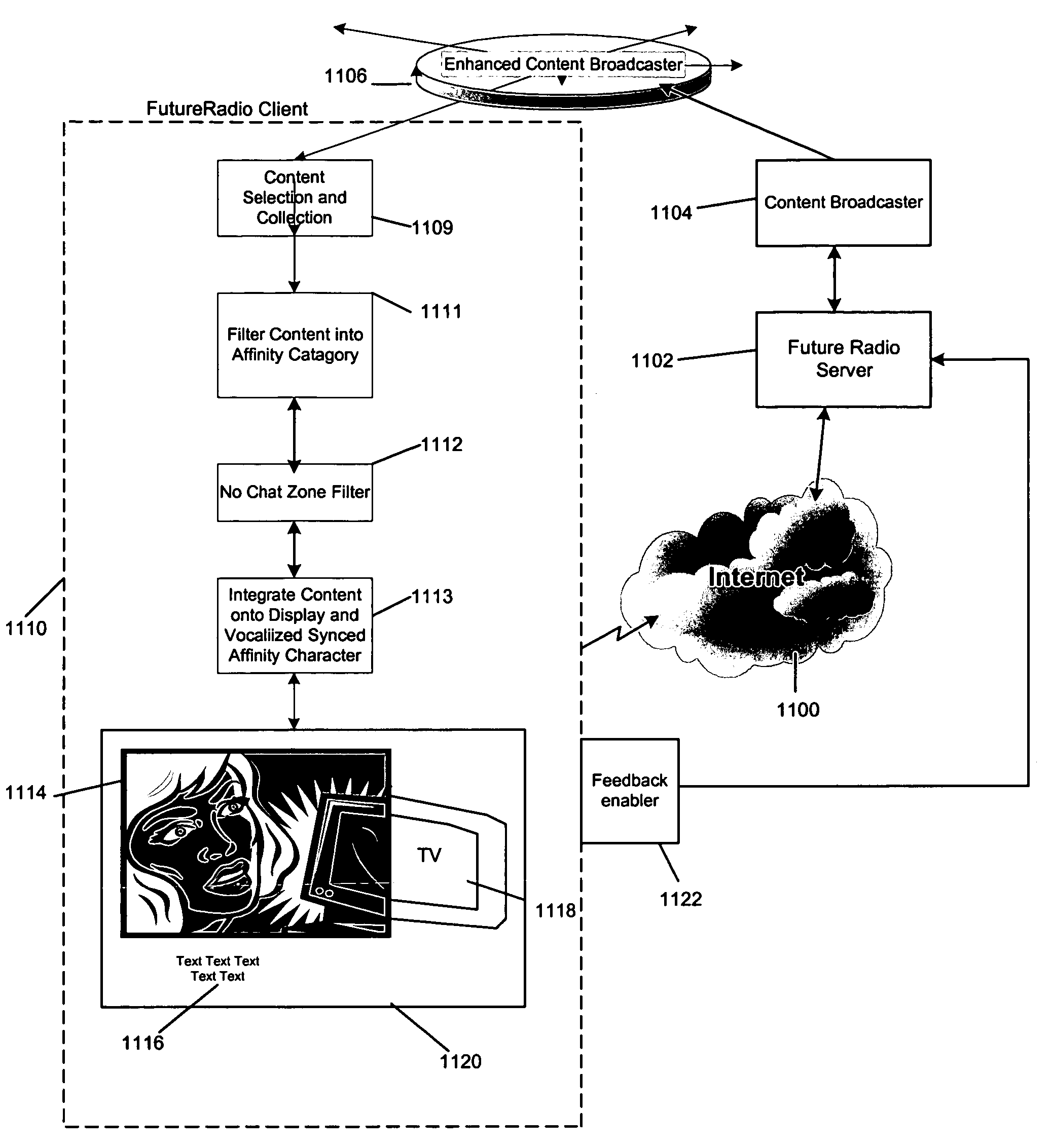
Interactive multi media user interface using affinity based categorization
InactiveUS7284202B1High communication latencyTelevision system detailsDigital data information retrievalThe InternetE-commerce
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for quantitative analysis of histopathology images using multiclassifier ensemble schemes
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
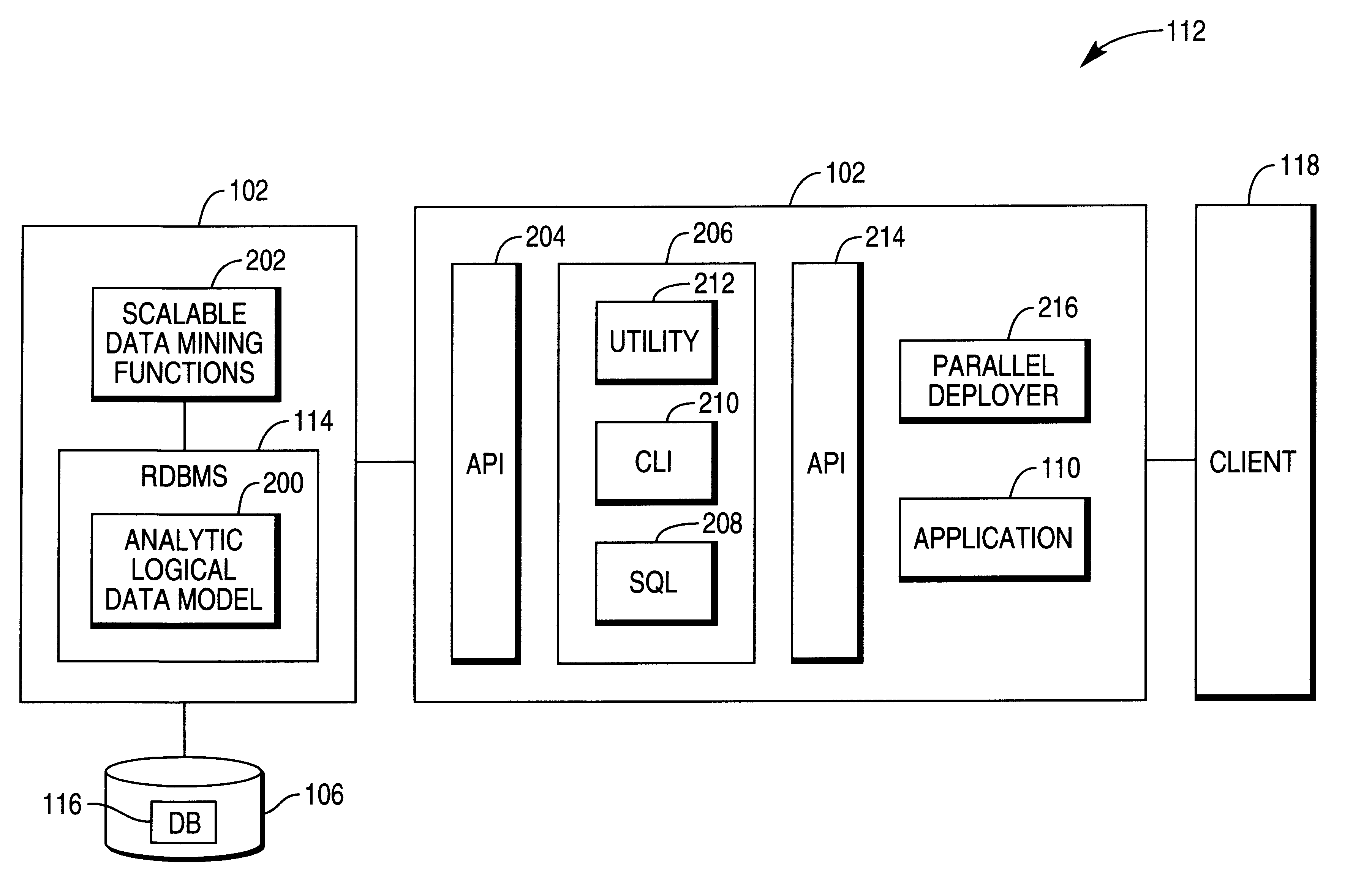
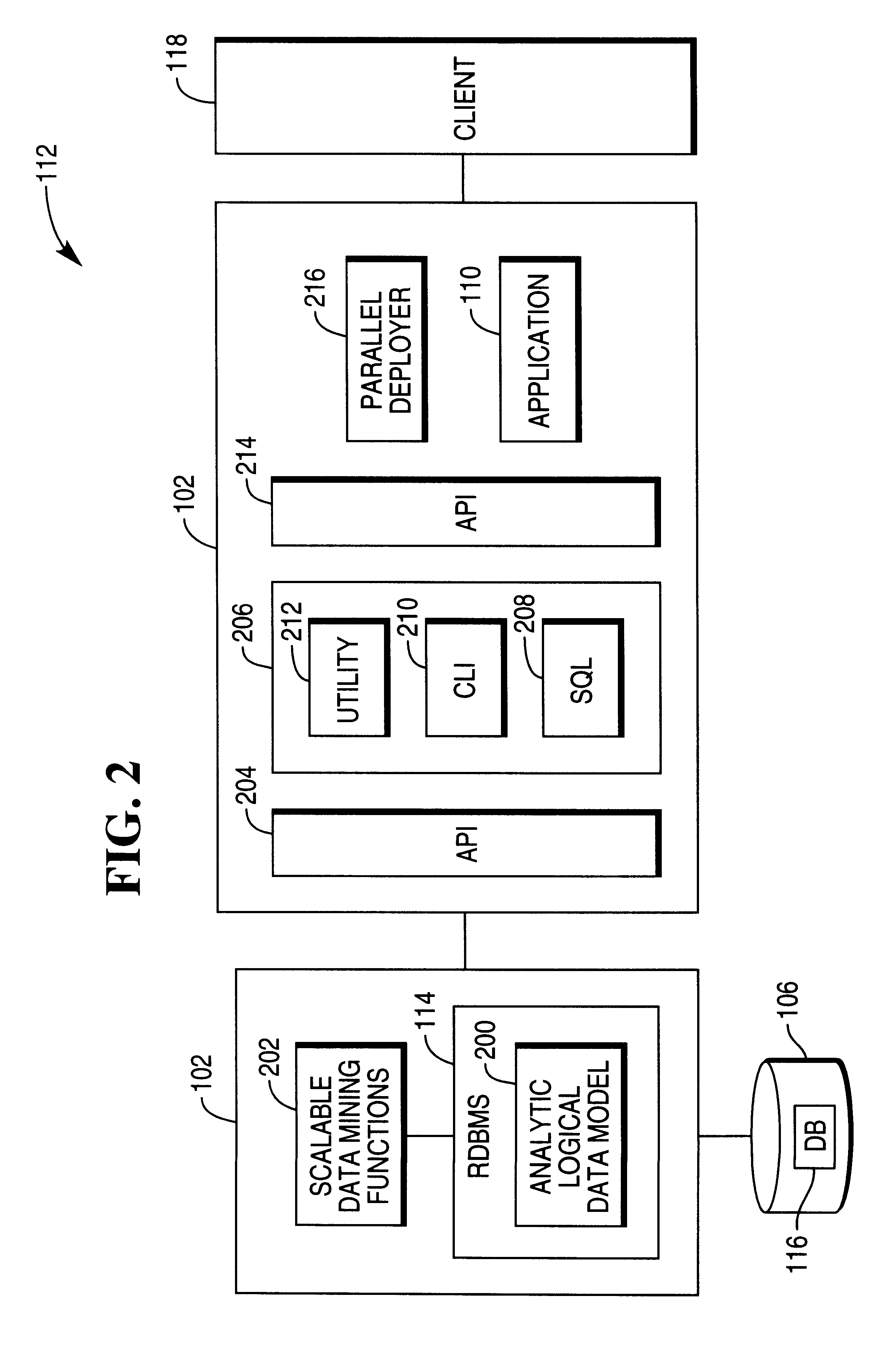
Analytic logical data model
InactiveUS6553366B1Data processing applicationsRelational databasesHigh level analysisRelational database management system
Owner:TERADATA US
Method and apparatus for data retention in a storage system
ActiveUS20050125411A1Digital data information retrievalMemory loss protectionRetention periodSoftware engineering
A system and method are provided for retention of data on a storage system. An application program provides the storage system with data to be stored on the storage system. The application program also provides the storage system with a retention period that indicates a period of time for which the data may not be deleted. When the storage system receives a request to delete the data, it first evaluates the retention period associated with that data to determine if the retention period has expired. If the retention period has not expired, the storage system denies the request to delete the data.
Owner:EMC IP HLDG CO LLC
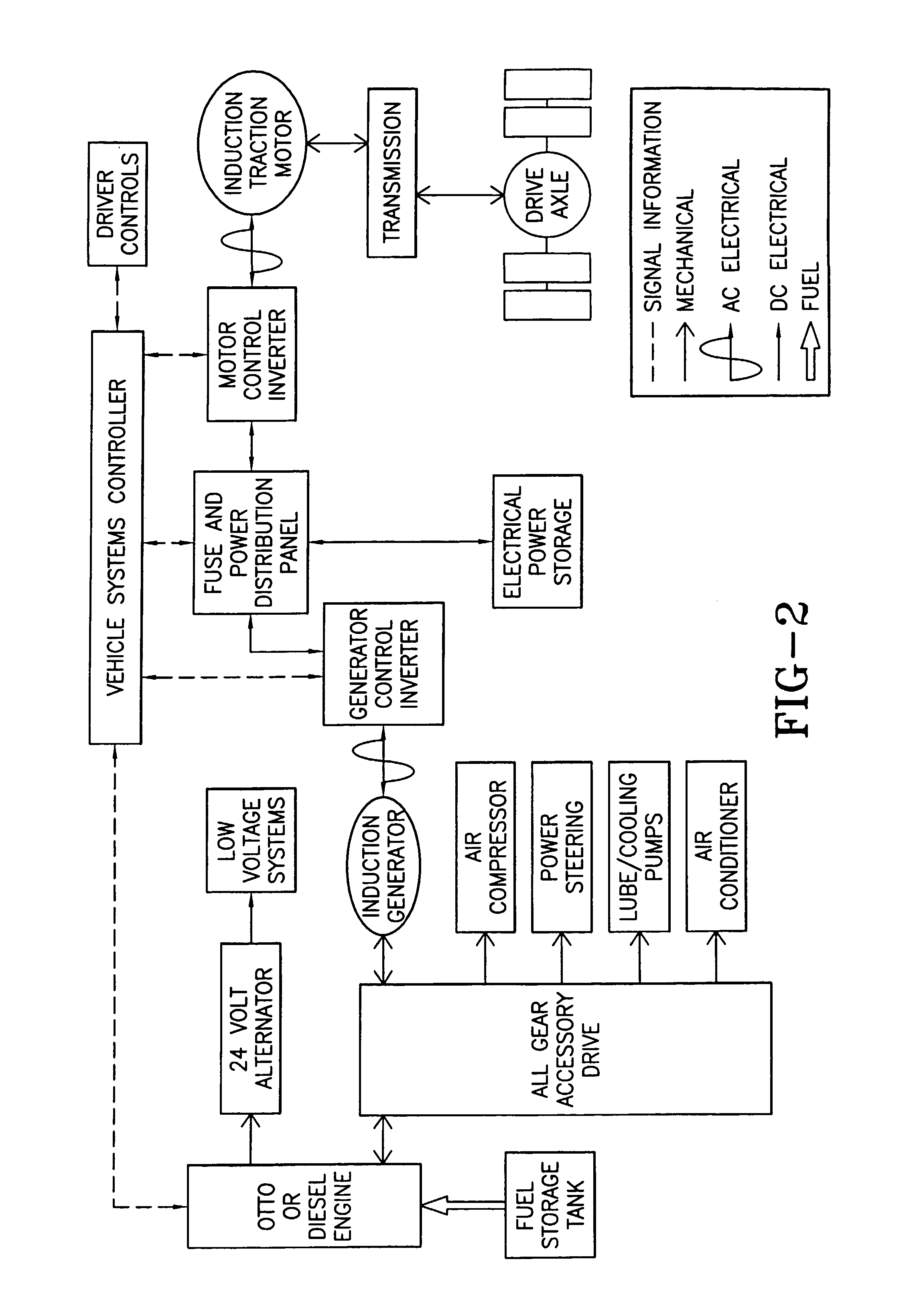
Hybrid electric vehicle
InactiveUS7252165B1Poor vehicle performanceImprove variationDigital data processing detailsVehicle sub-unit featuresLow voltageAuxiliary power unit
Owner:BOWLING GREEN STATE UNIV
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
System and process for network collaboration through embedded annotation and rendering instructions
ActiveUS20030023679A1Requires applicationCathode-ray tube indicatorsNatural language data processingWeb browserMessage delivery
A process for network collaboration using embedded annotations and rendering instructions allowing collaborators to generate, share, and render collaborative content over the internet without installing any applications other than a web browser is disclosed, which allows the recipients of such collaborative content to view the content without installing any application other than the web browser. The message containing collaborative content sent between collaborators is a URL and collaborative content elements, which not only contain the identity of the base document, but an encoded representation of the collaborative content itself. These URLs are self-contained, and can be distributed using synchronous or asynchronous messaging systems.
Owner:EPLUS CAPITAL
Formulation of daily weather observation
ActiveUS7379817B1Indication of weather conditions using multiple variablesSpecial data processing applicationsObservation dataObservation method
Owner:DTN LLC
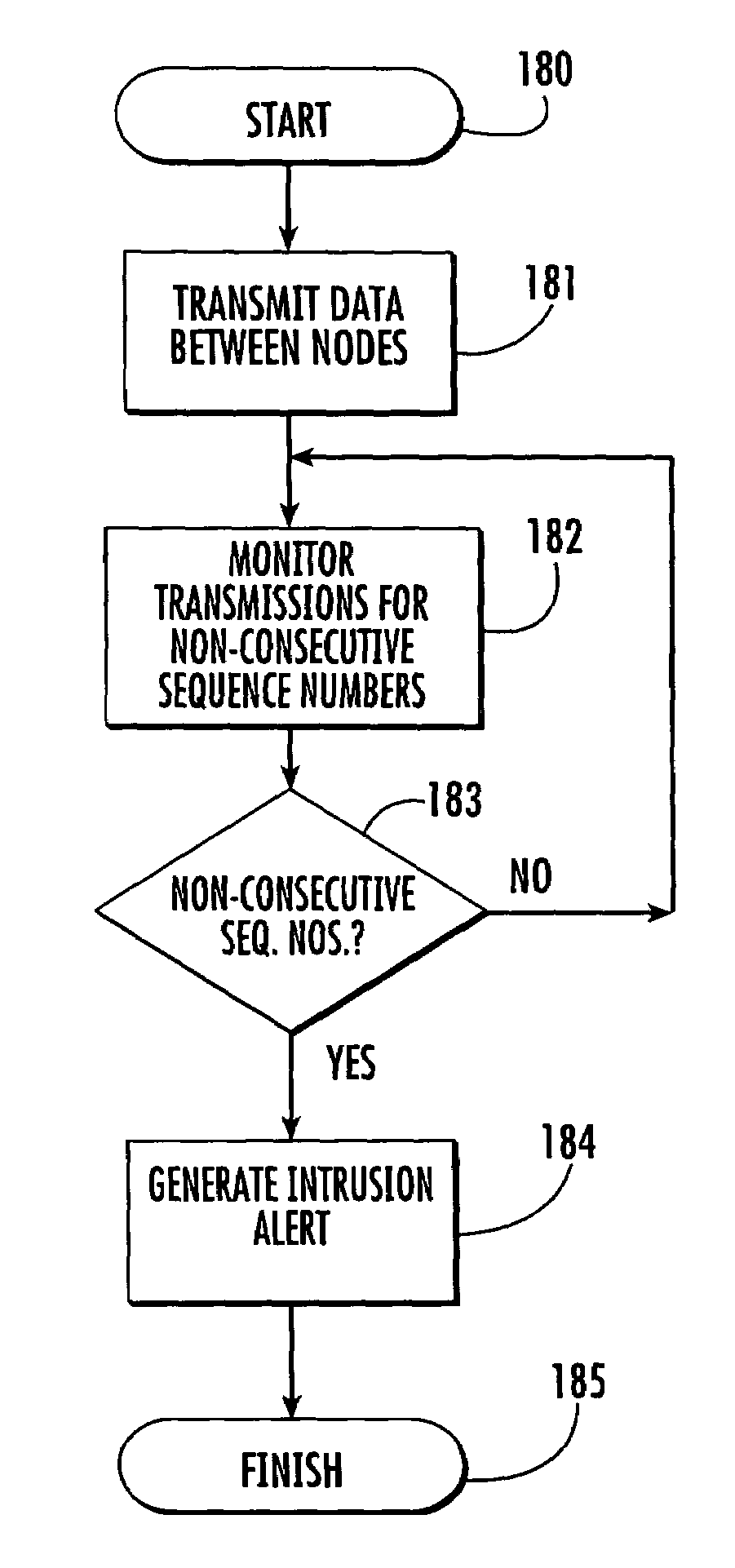
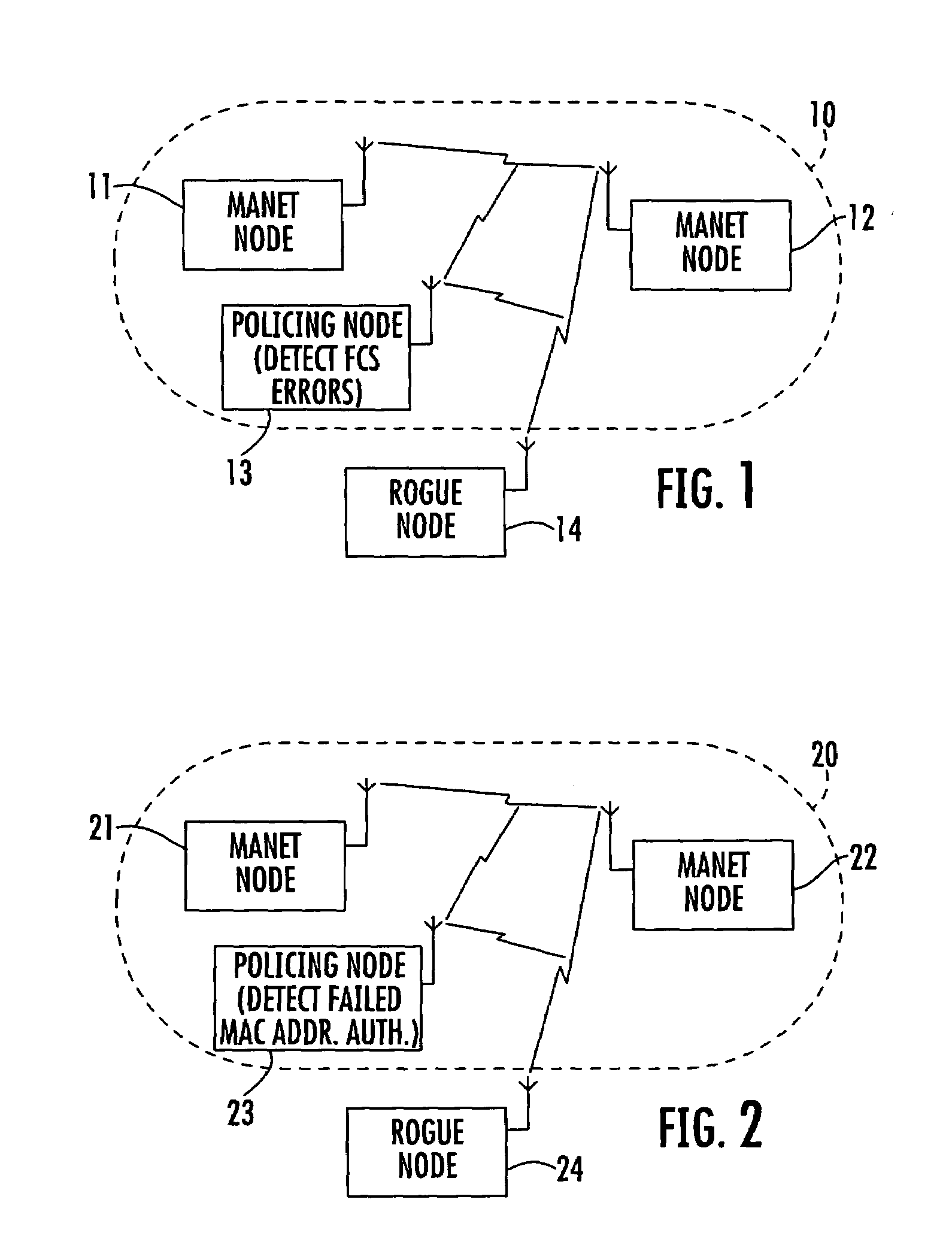
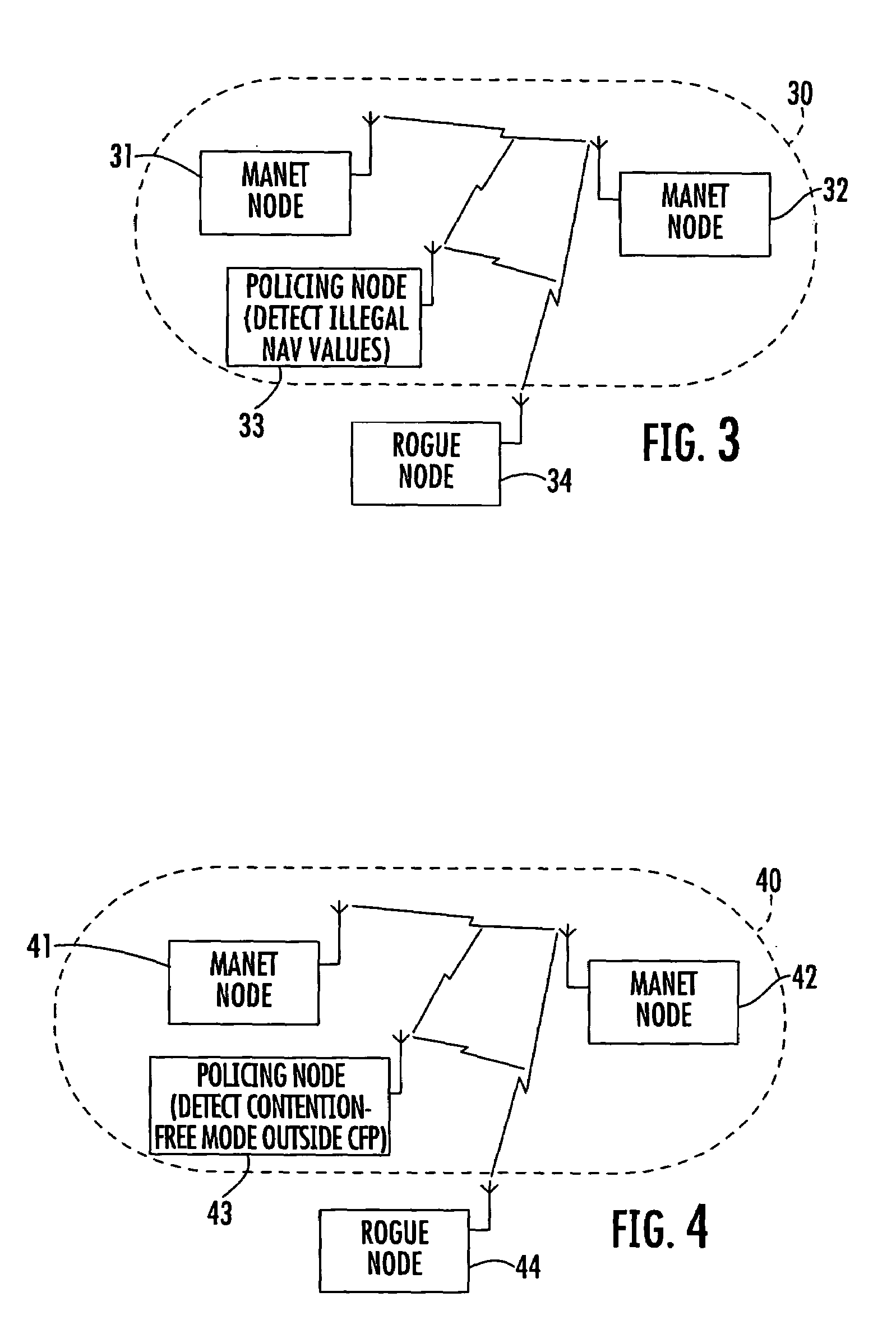
Mobile ad-hoc network with intrusion detection features and related methods
Owner:STINGRAY IP SOLUTIONS LLC
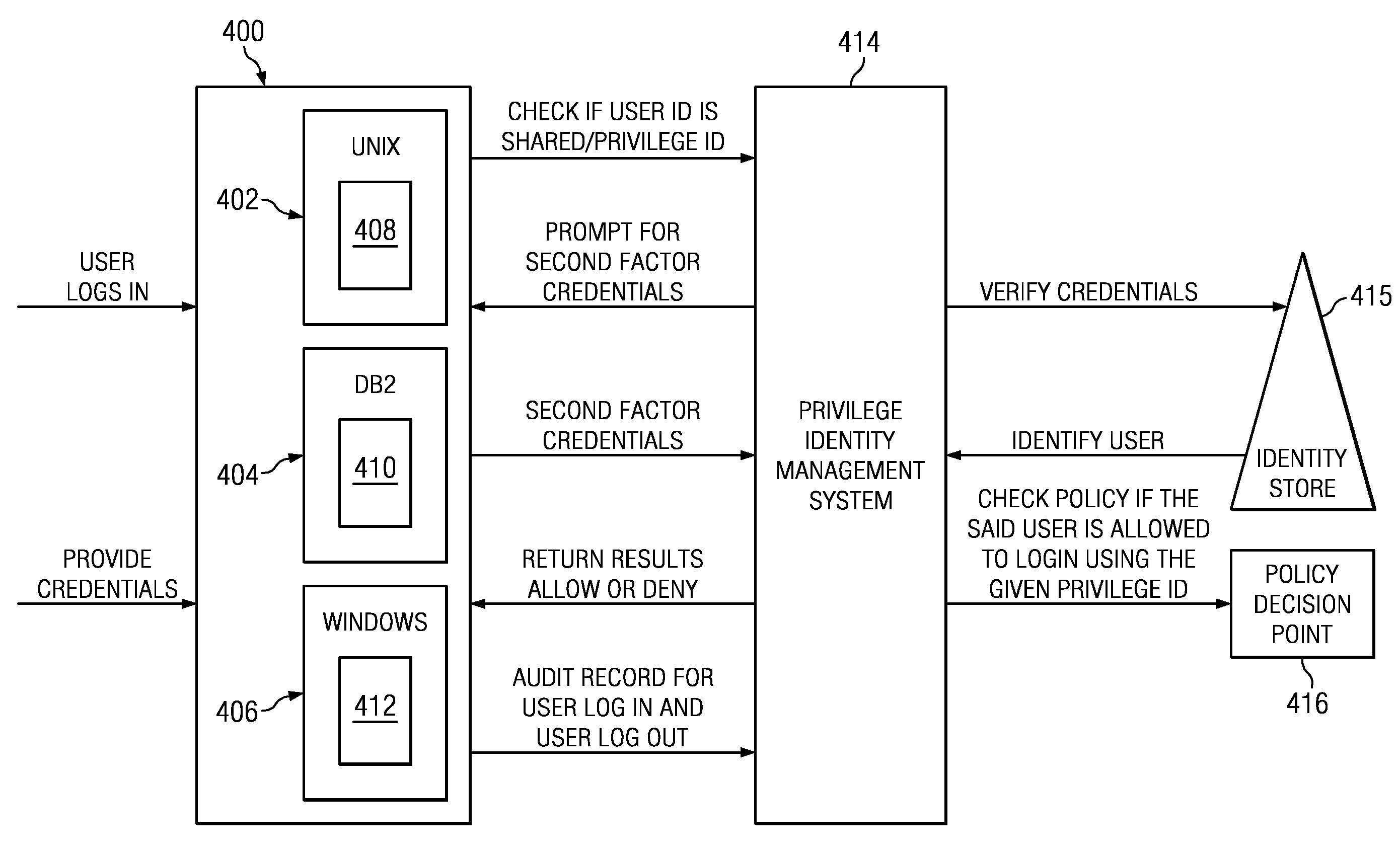
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
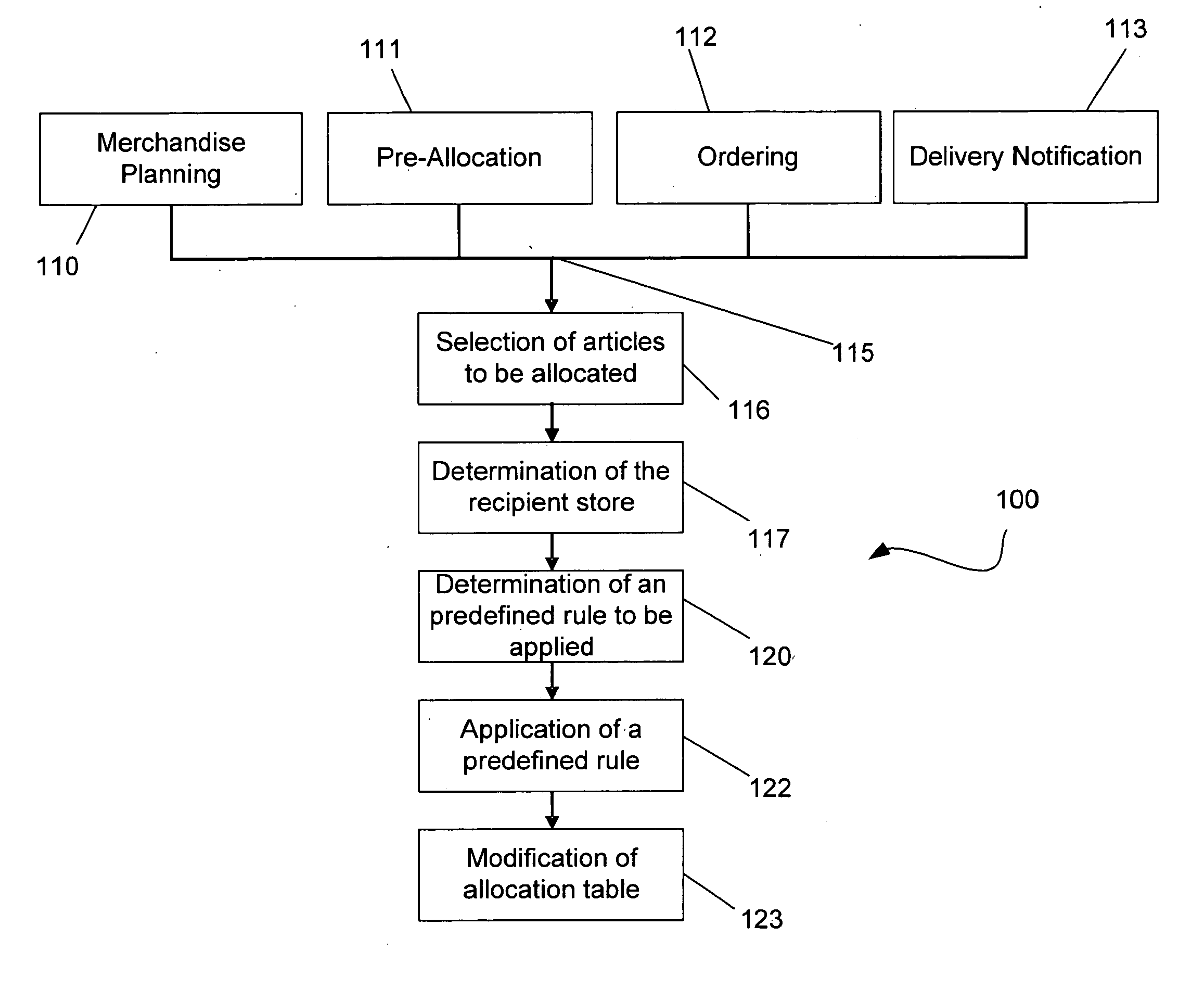
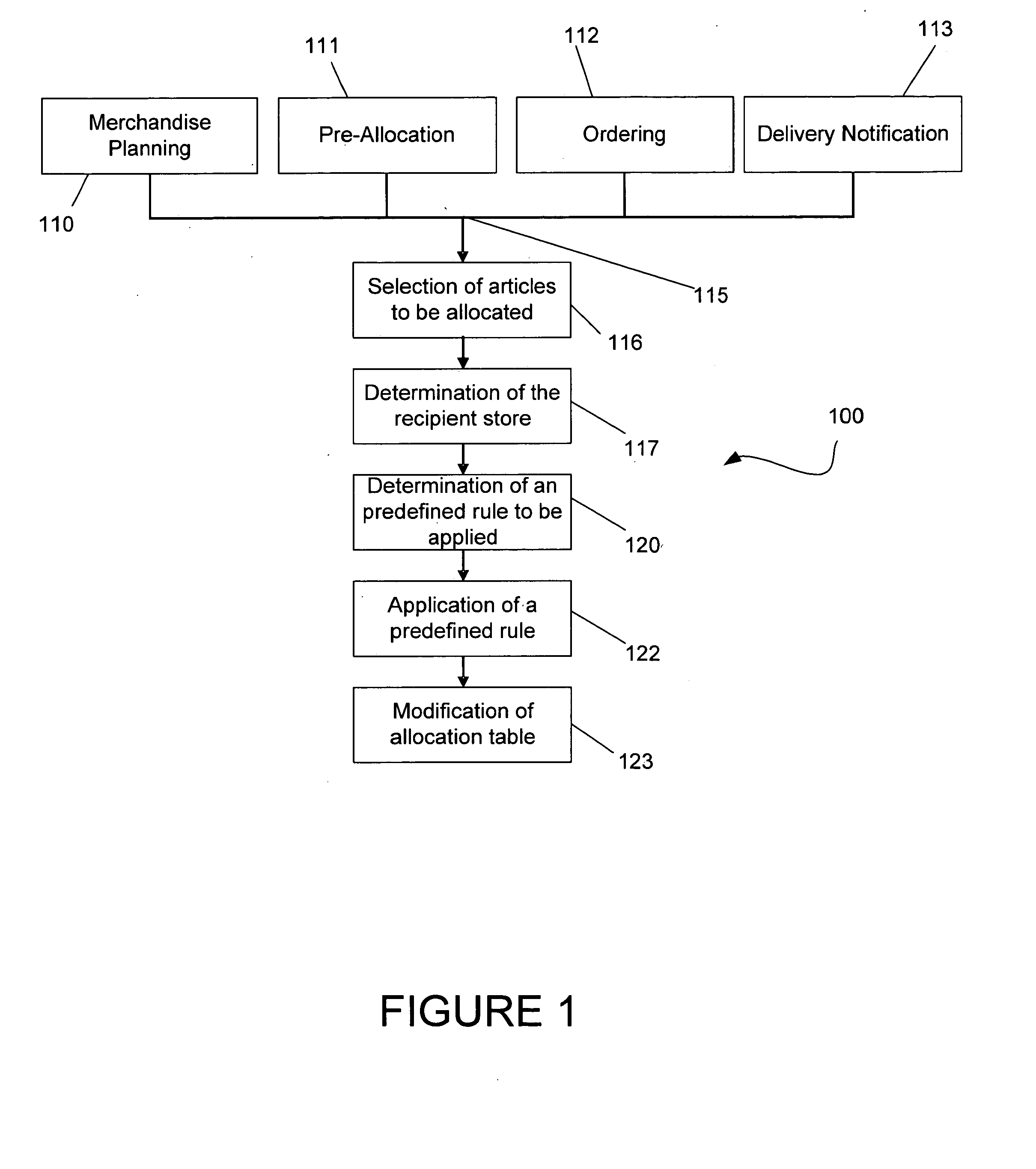
Allocation table generation from assortment planning
ActiveUS20050235020A1Promote generationResourcesSpecial data processing applicationsData miningPurchase order
Owner:SAP AG
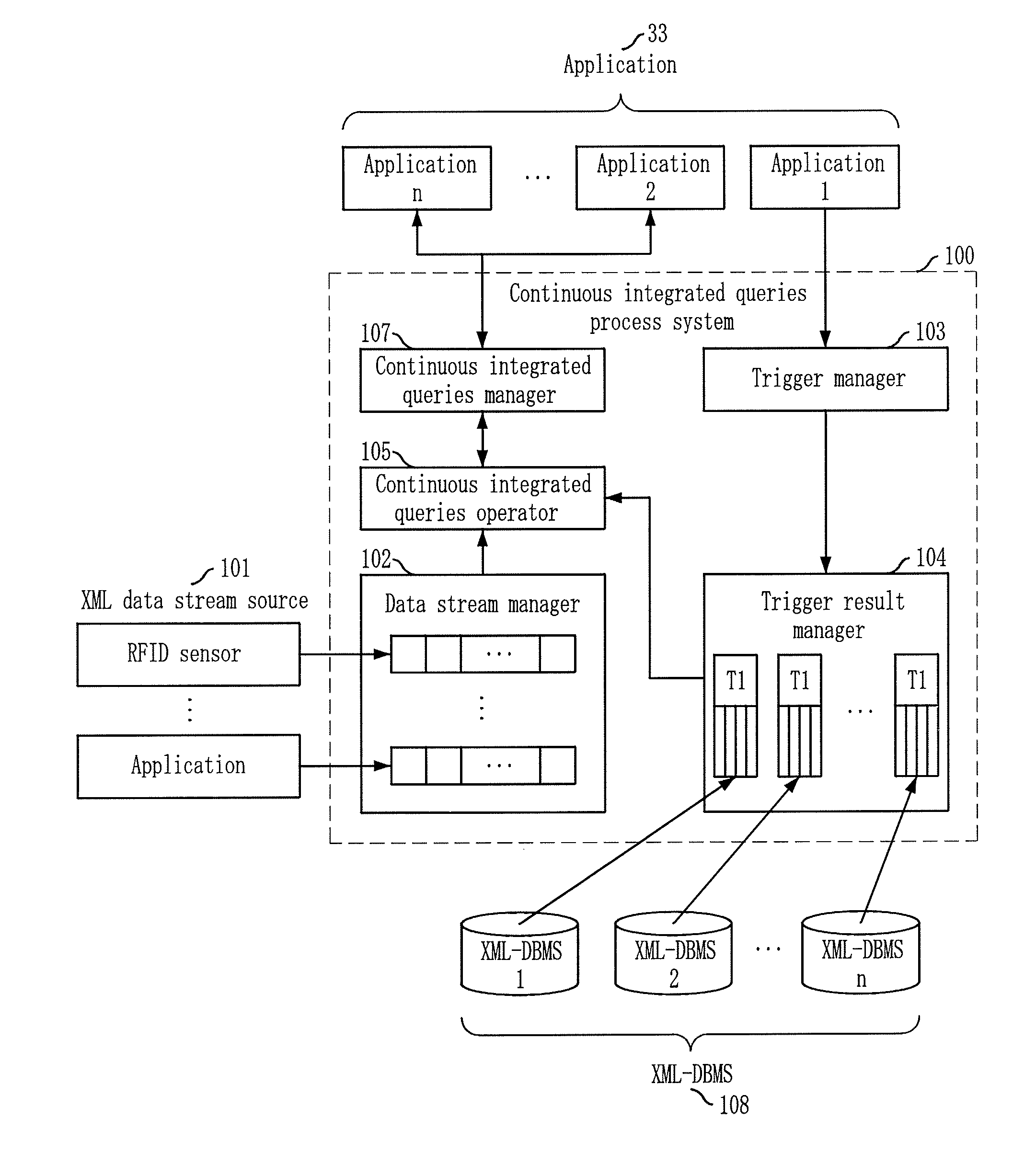
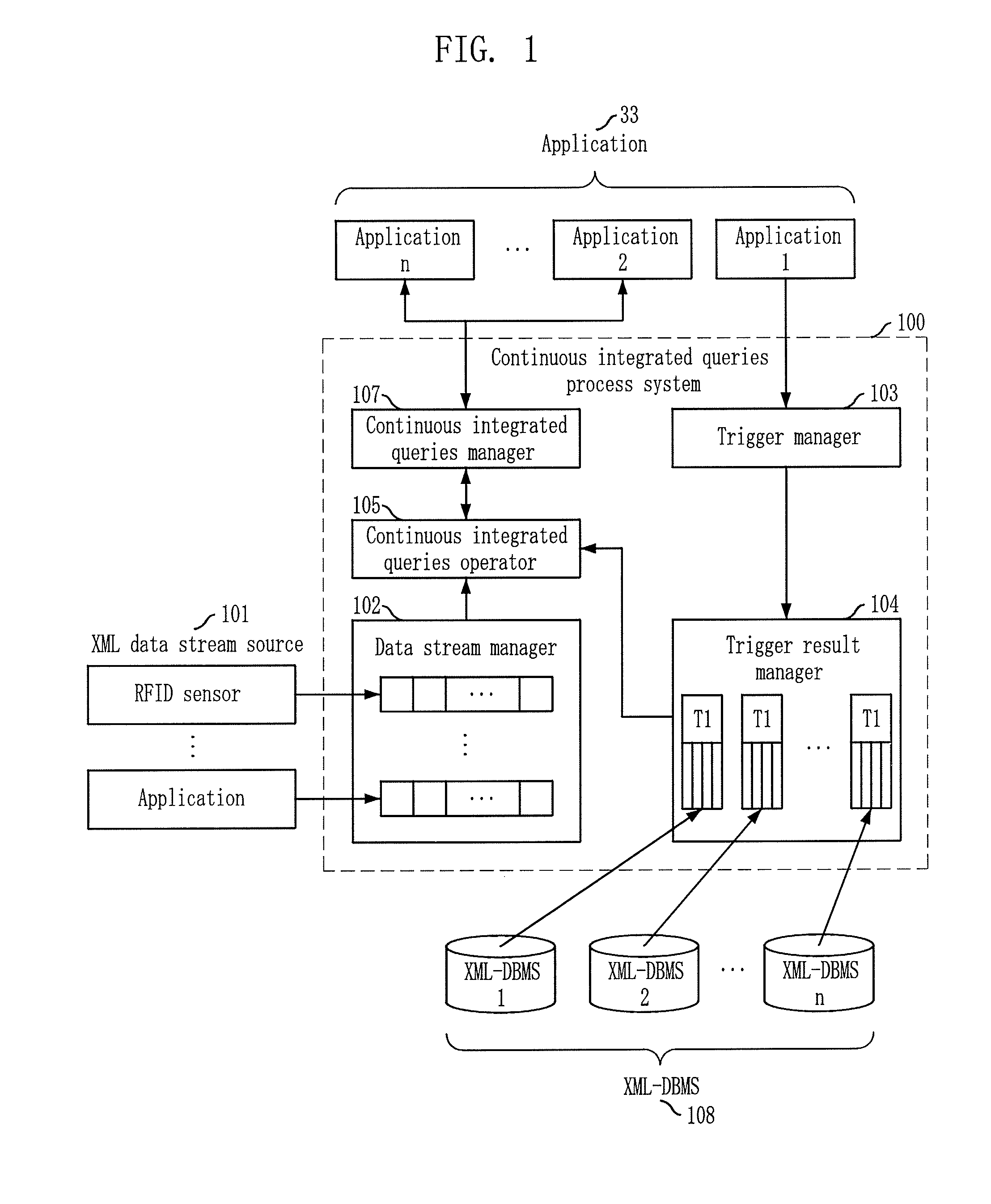
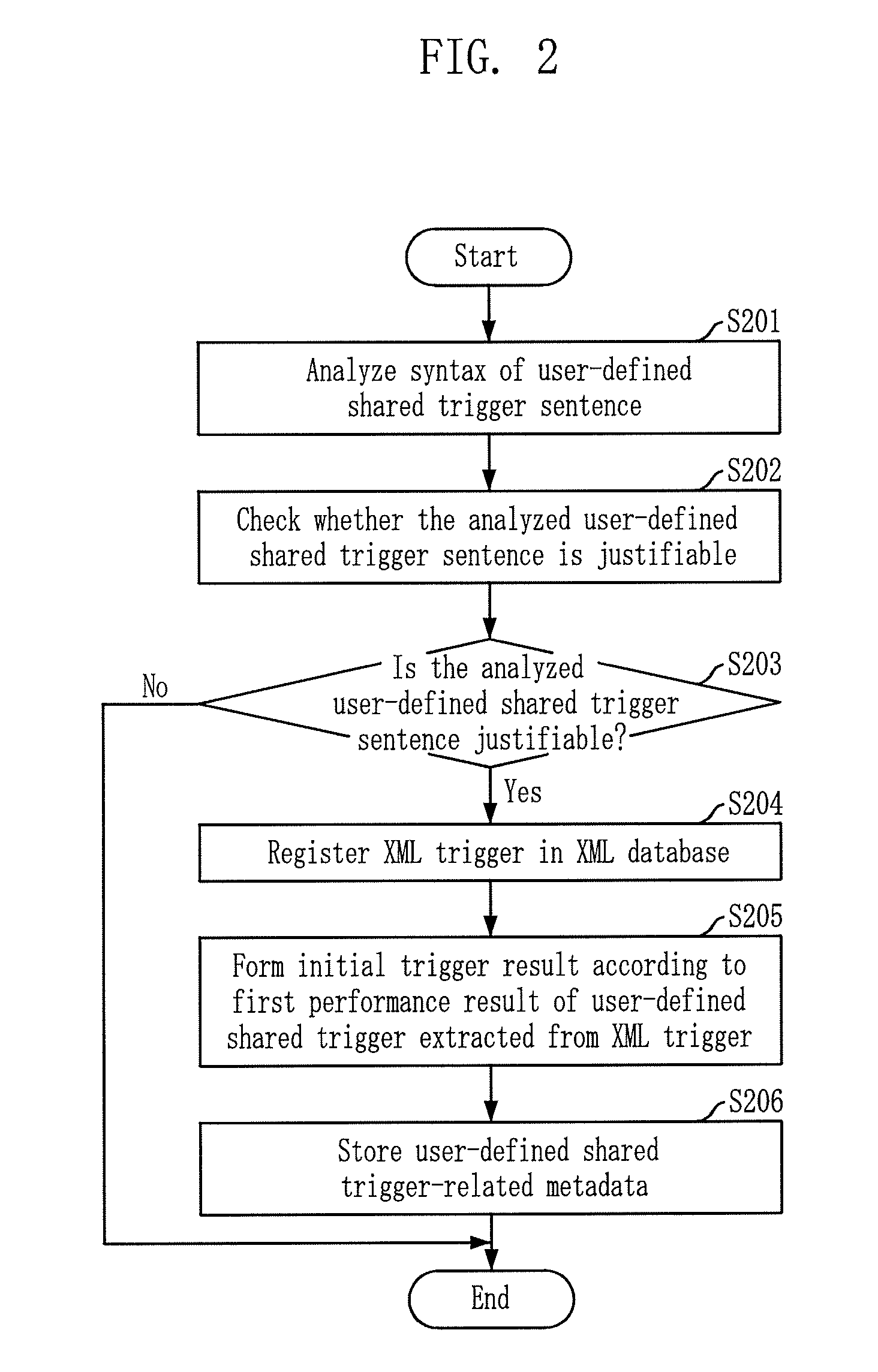
System and method for processing continuous integrated queries on both data stream and stored data using user-defined share trigger
InactiveUS20080046401A1Improve performanceDigital data information retrievalDigital data processing detailsExternal applicationData stream
Owner:ELECTRONICS & TELECOMM RES INST
Popular searches
Memory systems Input/output processes for data processing Transmission Electroluminescent light sources Energy saving control techniques Electric light circuit arrangement Radio/inductive link selection arrangements Execution for user interfaces Unauthorized memory use protection Analogue secracy/subscription systems
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap