Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9 results about "Malware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. Malware does the damage after it is implanted or introduced in some way into a target's computer and can take the form of directly executable code, scripts, so-called "active content" (Microsoft Windows), and other forms of data. Some kinds of malware are largely referred to in the media as computer viruses, worms, Trojan horses, ransomware, spyware, adware, and scareware, among other terms. Malware has a malicious intent, acting against the interest of the computer user—and so does not include software that causes unintentional harm due to some deficiency, which is typically described as a software bug.
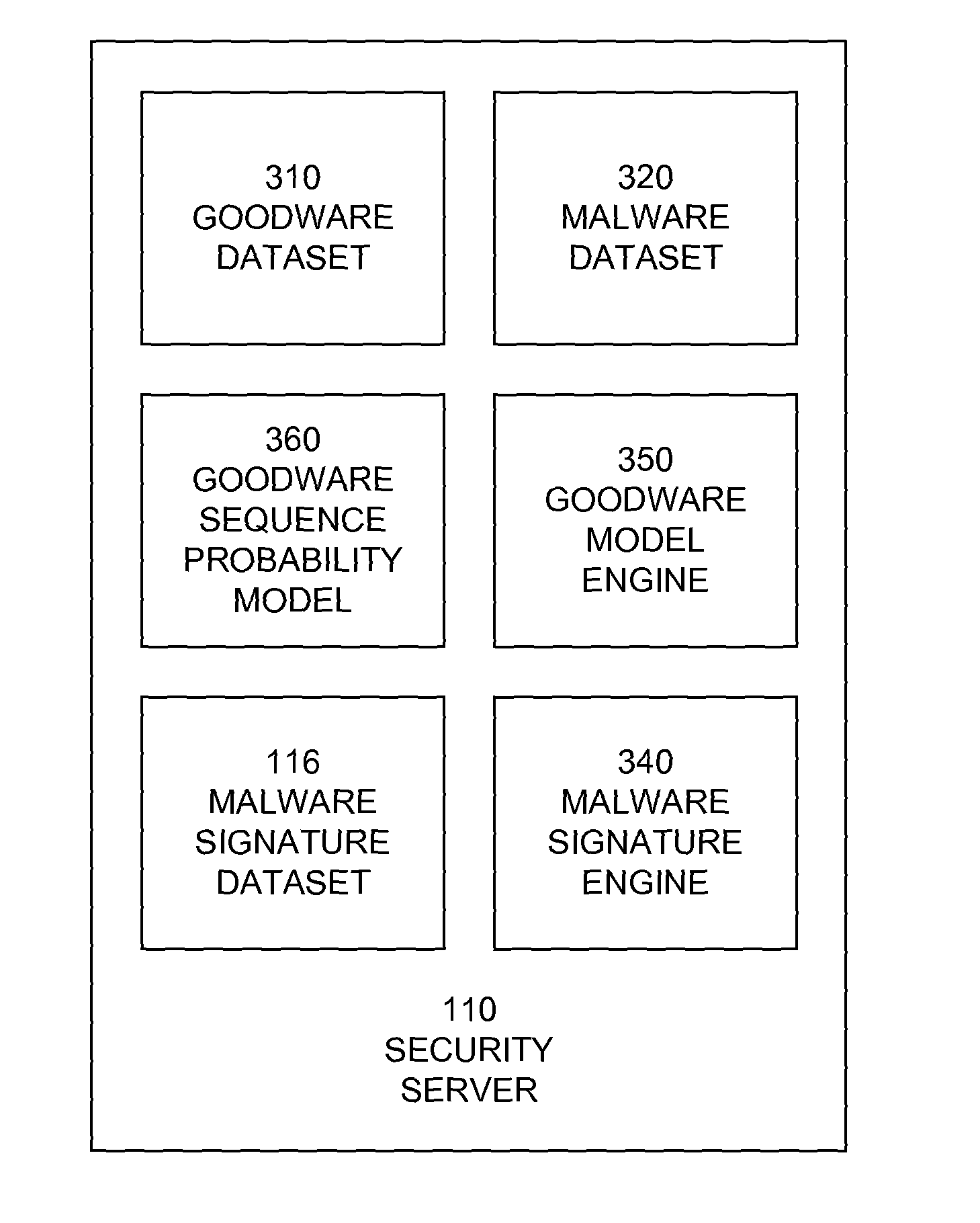
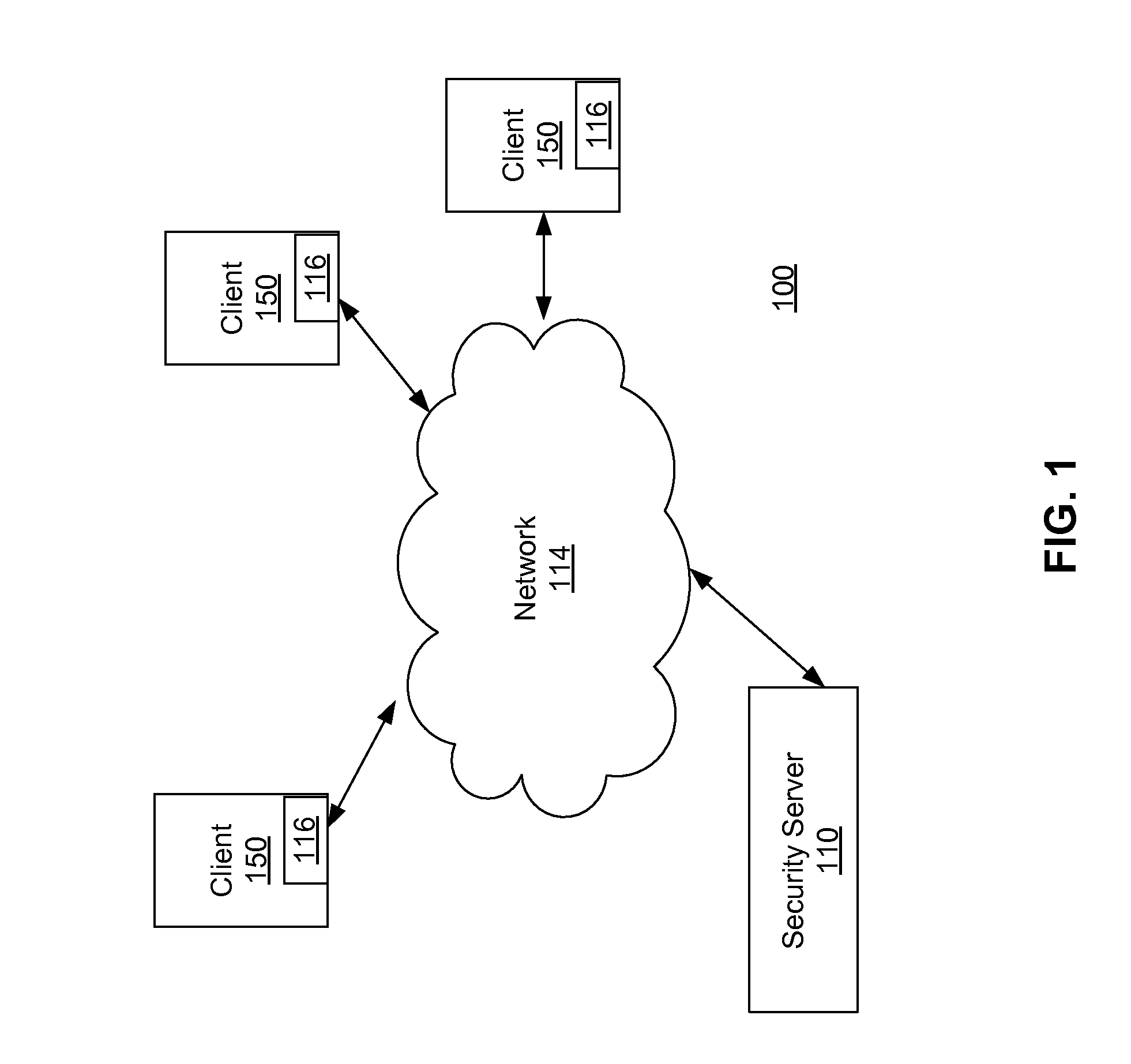
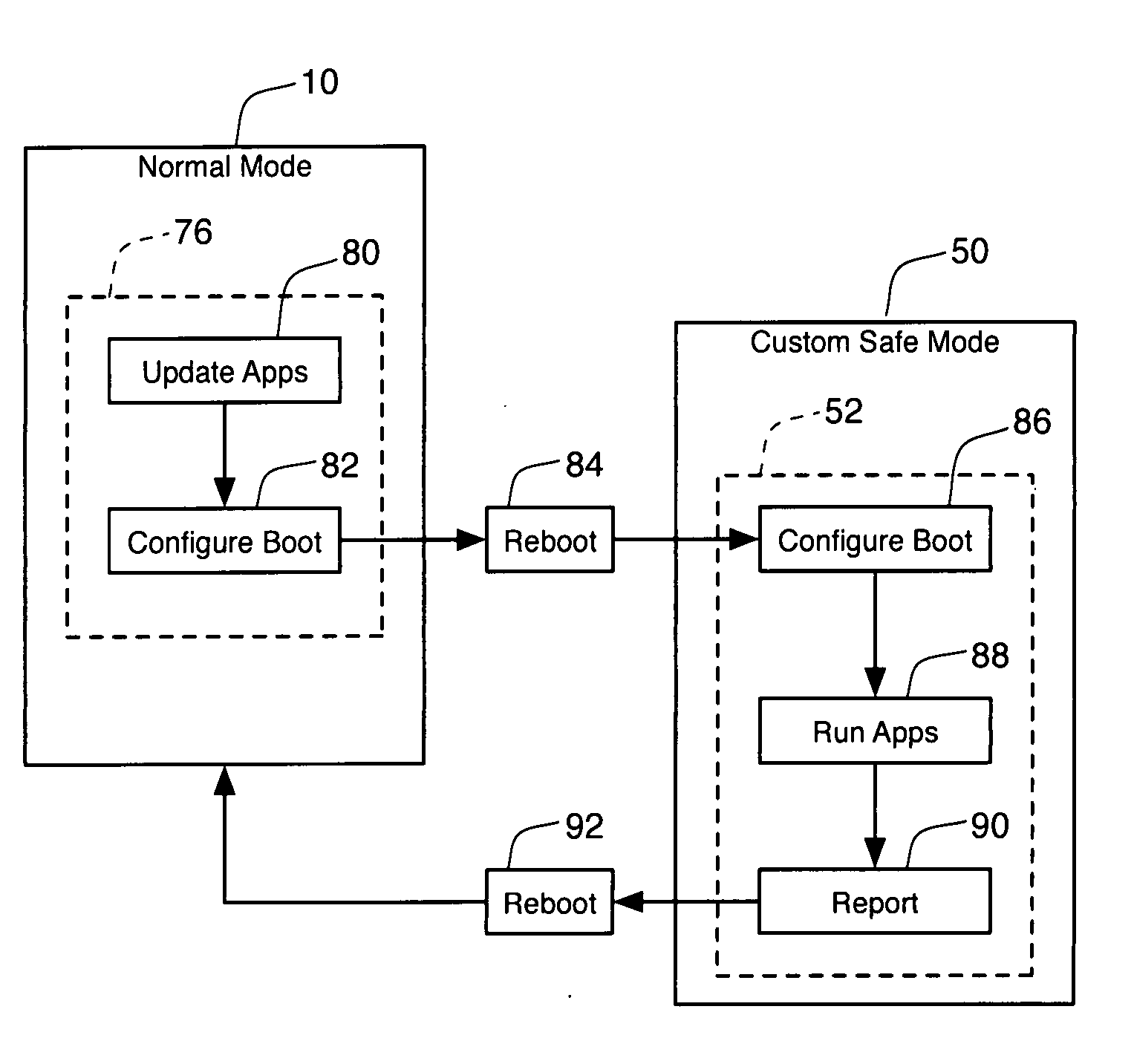
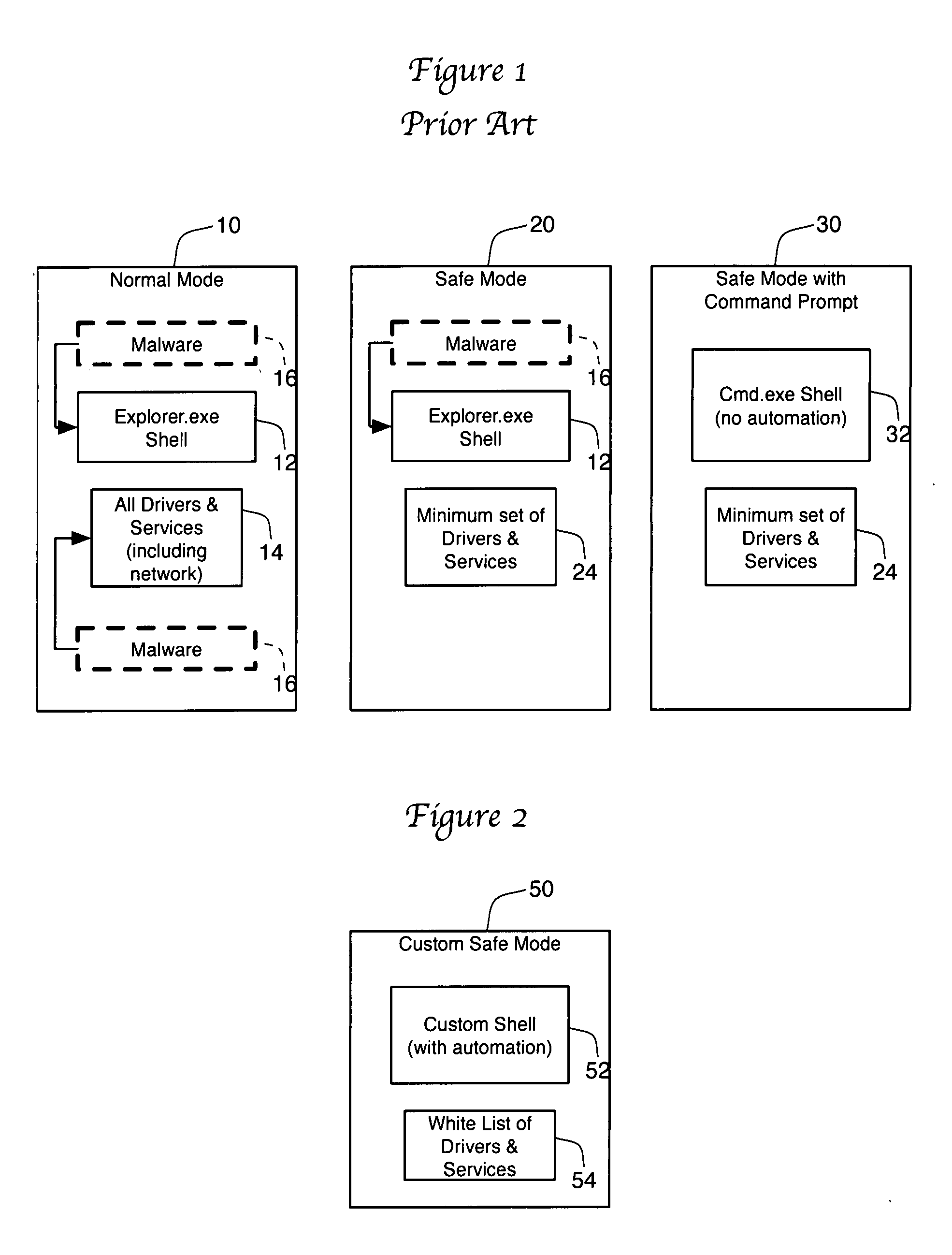
Methods for combating malicious software
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
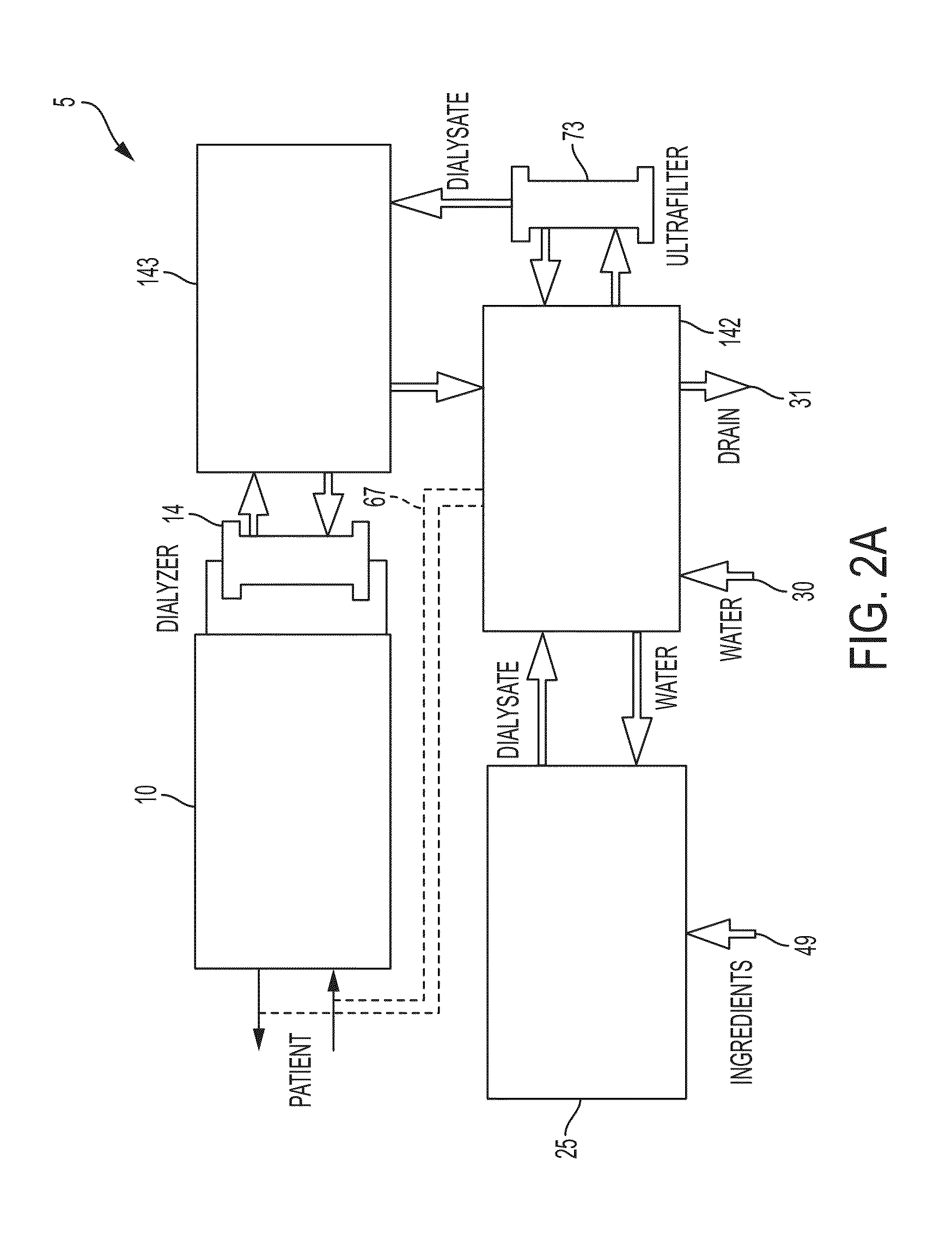
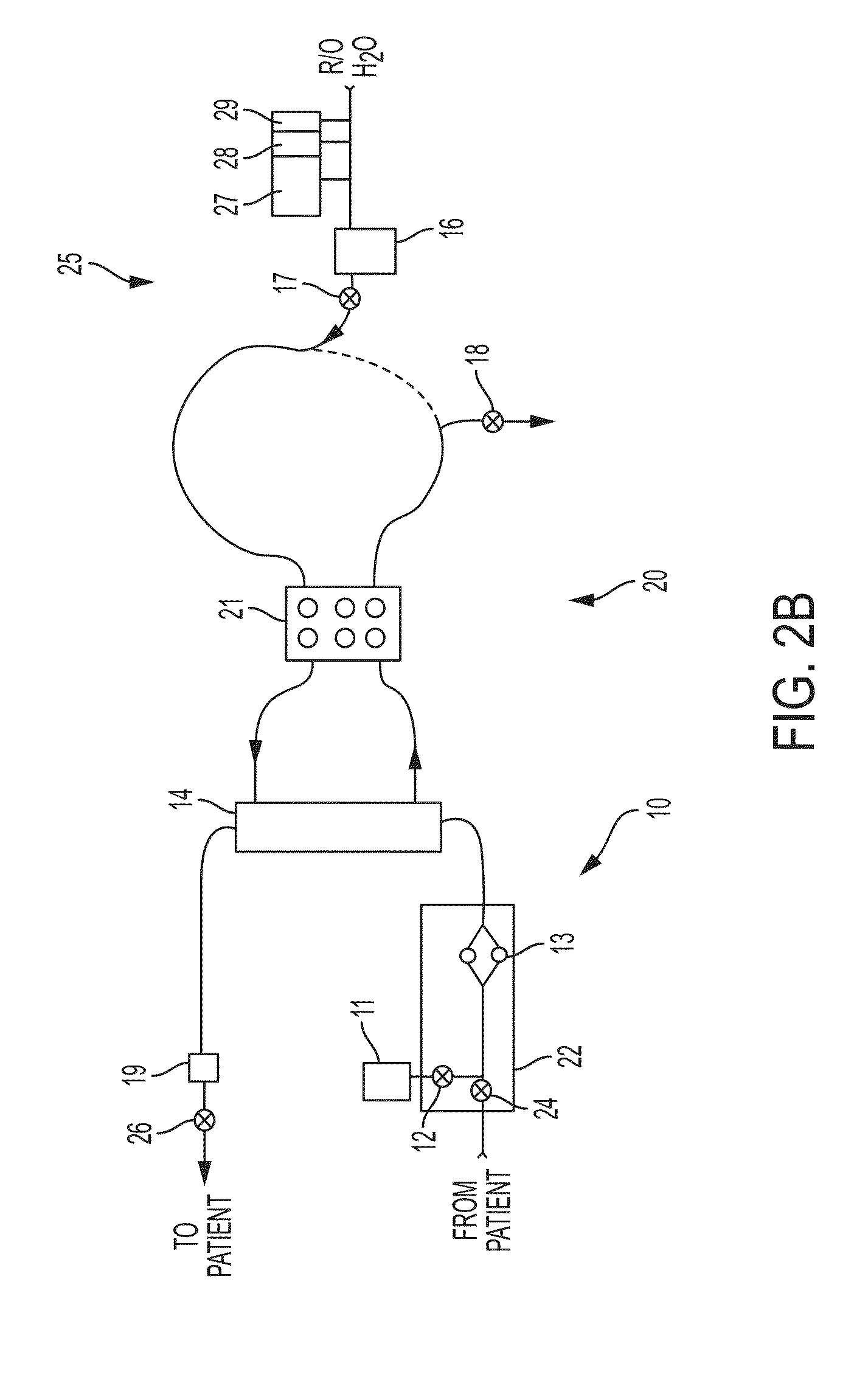
Control Systems and Methods for Blood or Fluid Handling Medical Devices
ActiveUS20160058933A1Prevention and therapyPreventing initiationMechanical/radiation/invasive therapiesOther blood circulation devicesMalwareControl software
Owner:DEKA PROD LLP
Malware automated removal system and method
ActiveUS20090013409A1Automate operationImprove software performanceMemory loss protectionError detection/correctionComputerized systemMalware
Owner:BBY SOLUTIONS
Malware detection system with contextual analysis
ActiveUS10581874B1Improve accuracyDecrease positive outcomeComputer security arrangementsSecuring communicationEngineeringMalware
A computerized method for detecting malware associated with an object. The method includes operations of analyzing an object to obtain a first set of attributes, where the first set of attributes include one or more characteristics associated with the object. Furthermore, the object is processed with a virtual machine to obtain a second set of attributes. The second set of attributes corresponds to one or more monitored behaviors of the virtual machine during processing of the object. Thereafter, a threat index is determined based, at least in part, on a combination of at least one attribute of the first set of attributes and at least one attribute of the second set of attributes. The threat index represents a probability of maliciousness associated with the object.
Owner:FIREEYE SECURITY HLDG US LLC
Malicious software API call sequence detection method based on graph convolution
ActiveCN111259388AImprove bindingFlexible organizational structurePlatform integrity maintainanceNeural architecturesCall graphAlgorithm
Owner:SUN YAT SEN UNIV
Link library function name identification method and device for computer binary program
Owner:NAT UNIV OF DEFENSE TECH
Cyber Resiliency of Application Data
ActiveUS20200366708A1Data applicationDecrease continuous network exposureInput/output to record carriersComputer security arrangementsMalwareWorkload
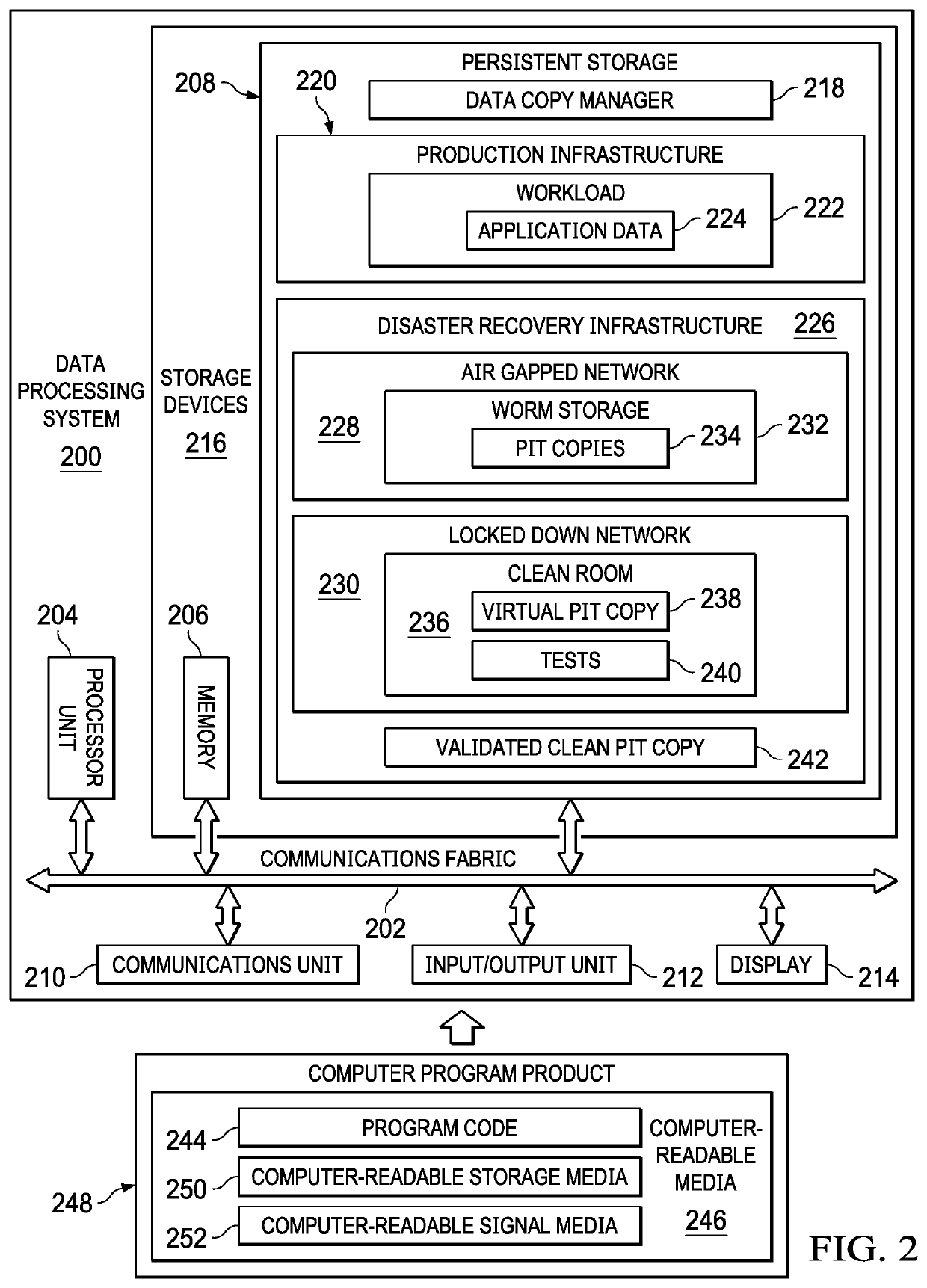
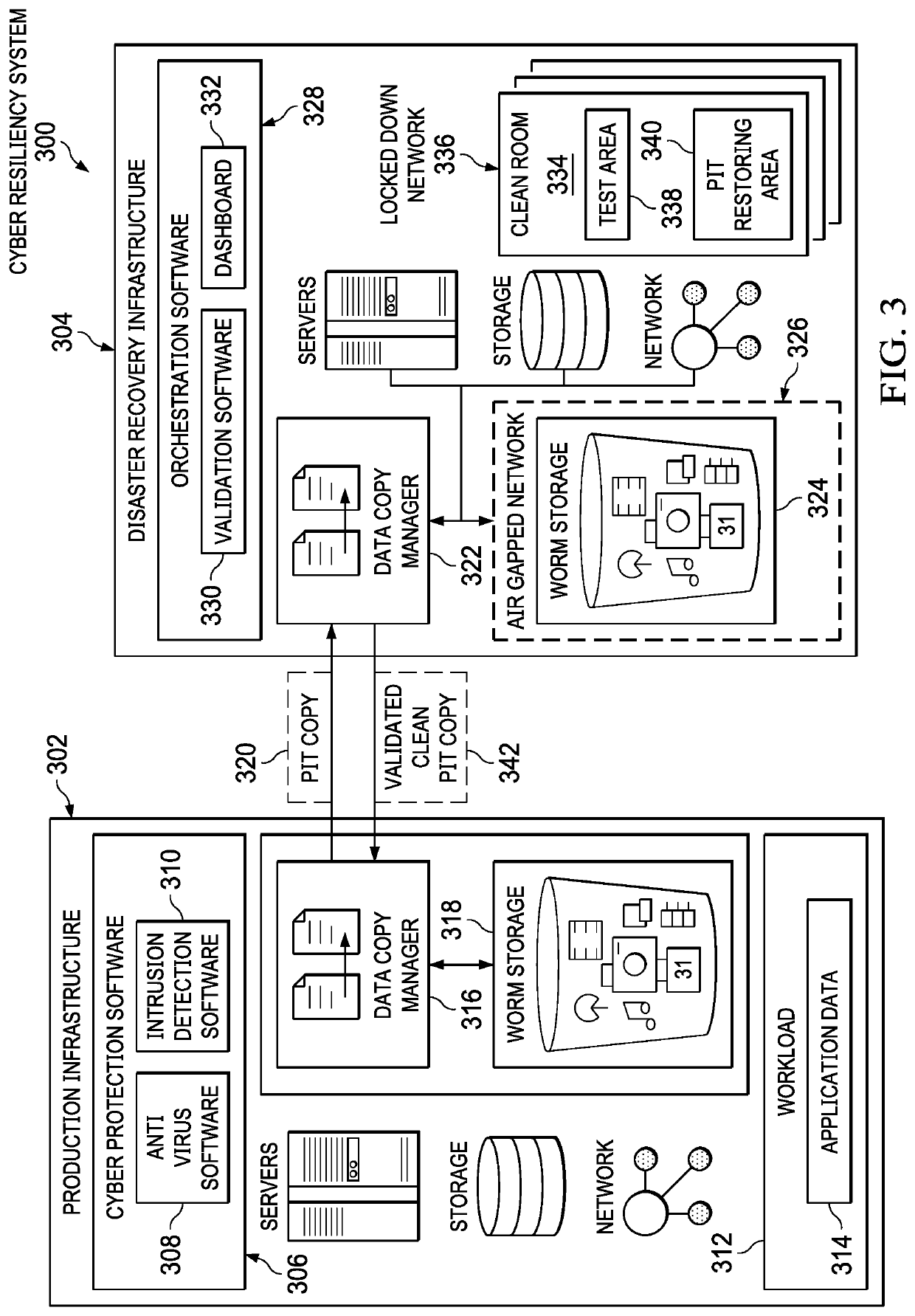
Cyber resiliency of application data is provided. An air gapped network is established for storing a point-in-time copy of application data corresponding to a workload running on a production infrastructure to decrease continuous network exposure of the point-in-time copy on a secondary infrastructure. A set of point-in-time copies is selected for testing the application data corresponding to the workload for validation on the secondary infrastructure. The set of point-in-time copies are validated on a periodic basis by applying cyberattack forensics, deep scanning, malware detection, and application level validation tests. An appropriate point-in-time copy is identified in the set of point-in-time copies to recover the application data corresponding to the workload. The application data corresponding to the workload are recovered to provide the cyber resiliency of the application data during cyberattack using the appropriate point-in-time copy.
Owner:KYNDRYL INC
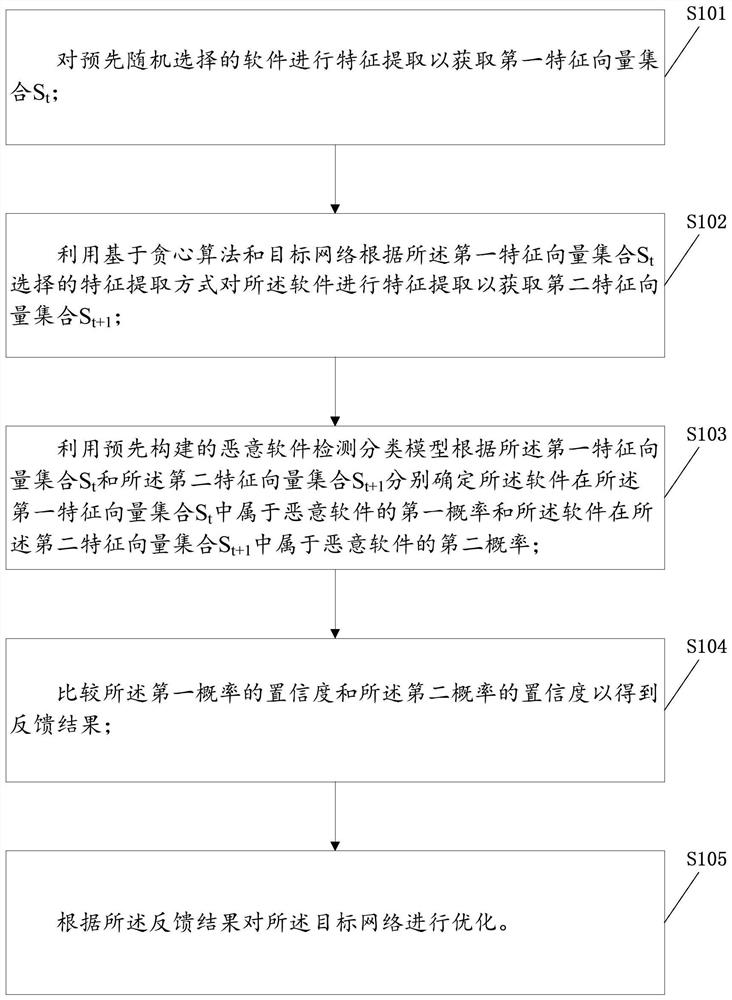
Malicious software detection network optimization method and device, electronic equipment and storage medium
ActiveCN112989342AImprove recognition accuracyImprove reliabilityCharacter and pattern recognitionPlatform integrity maintainanceFeature extractionGreedy algorithm
Owner:BEIJING UNIV OF POSTS & TELECOMM
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap