Malicious software API call sequence detection method based on graph convolution
An API call and malware technology, applied in the field of network security, can solve the problems of not being able to make full use of API parameters, not considering various relationships of API calls, etc., to achieve the effect of flexible organizational structure and improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] This embodiment proposes a malware API call sequence detection method based on graph convolution, such as figure 1 As shown, it is a flow chart of the method for detecting malware API calling sequences based on graph convolution in this embodiment.
[0046] In the malware API call sequence detection method based on graph convolution proposed in this embodiment, the following steps are included:
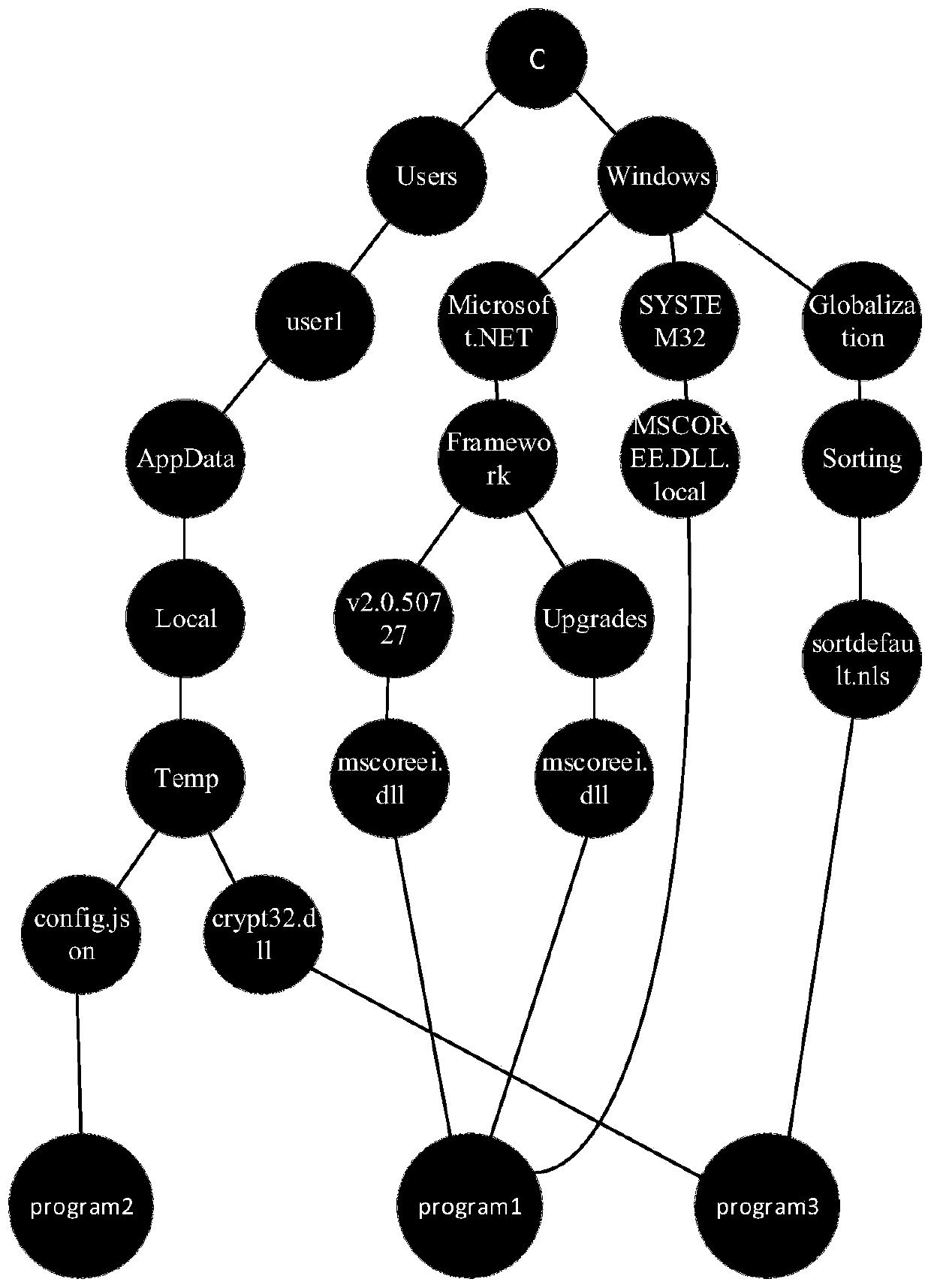
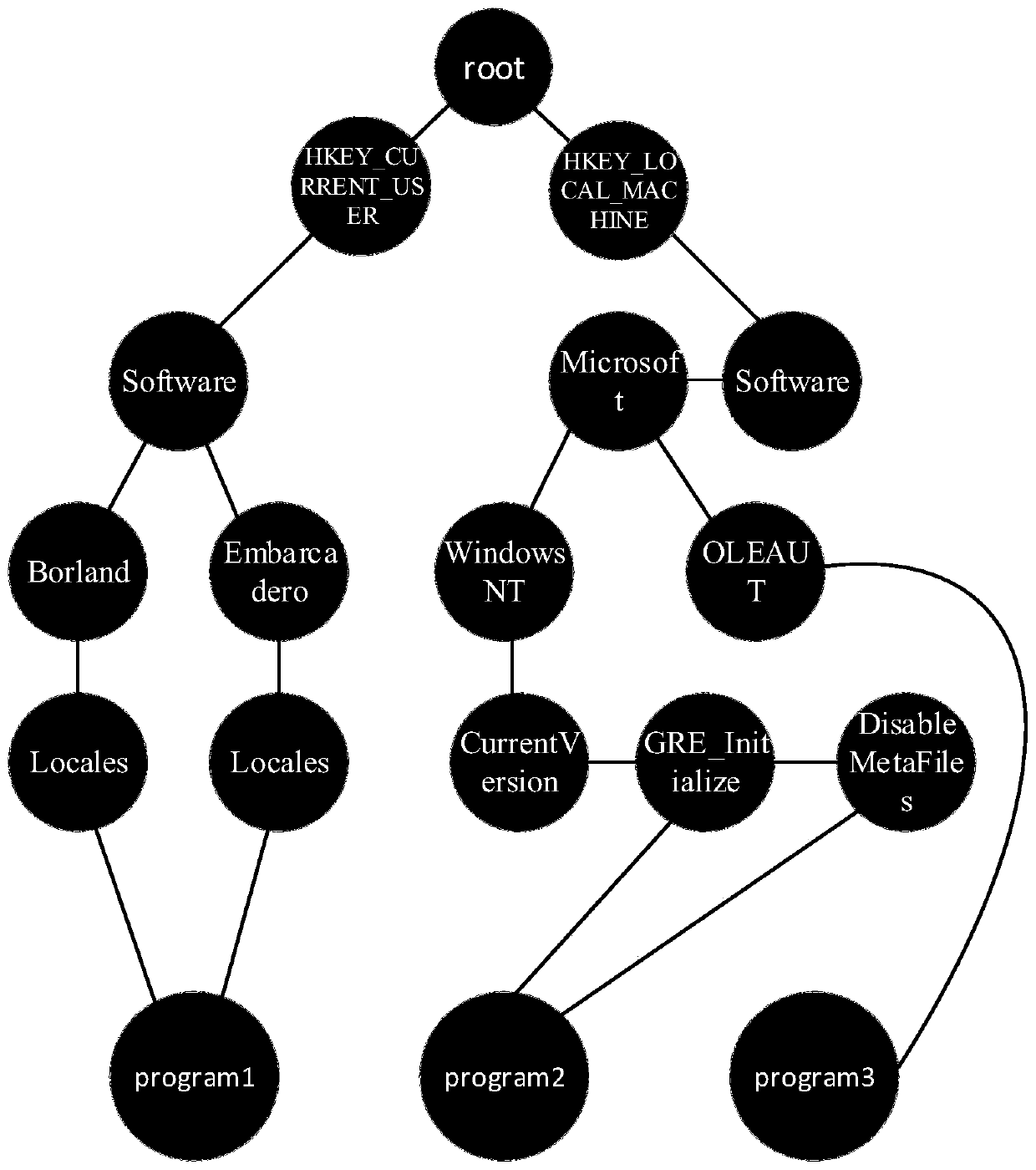
[0047] S1: Collect and record API call sequence information of processes and sub-processes of a large number of software samples when they are running, wherein the API call sequence information includes API functions and API parameters.
[0048] In this embodiment, a dynamic analysis tool is used to collect and record API call sequence information of a large number of running processes and sub-processes of software samples, and the tags of software samples are obtained and recorded through anti-virus engine or manual analysis. Among them, the API function in the call sequence in
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap