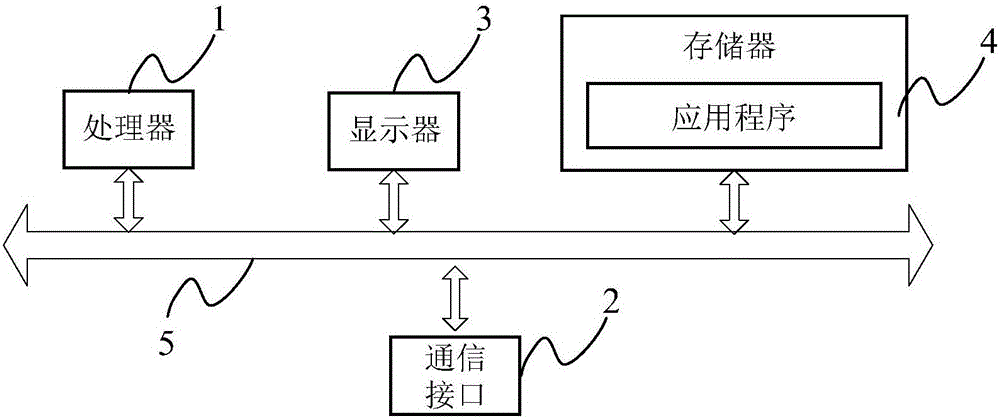
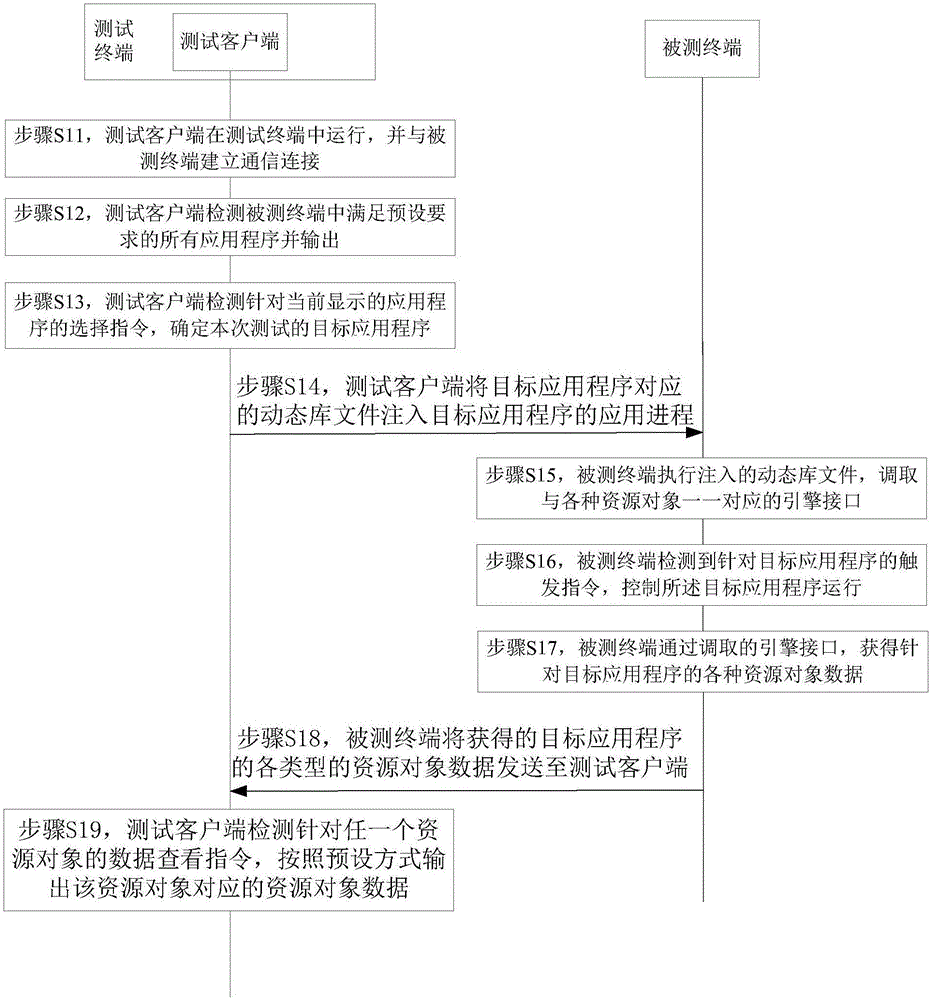
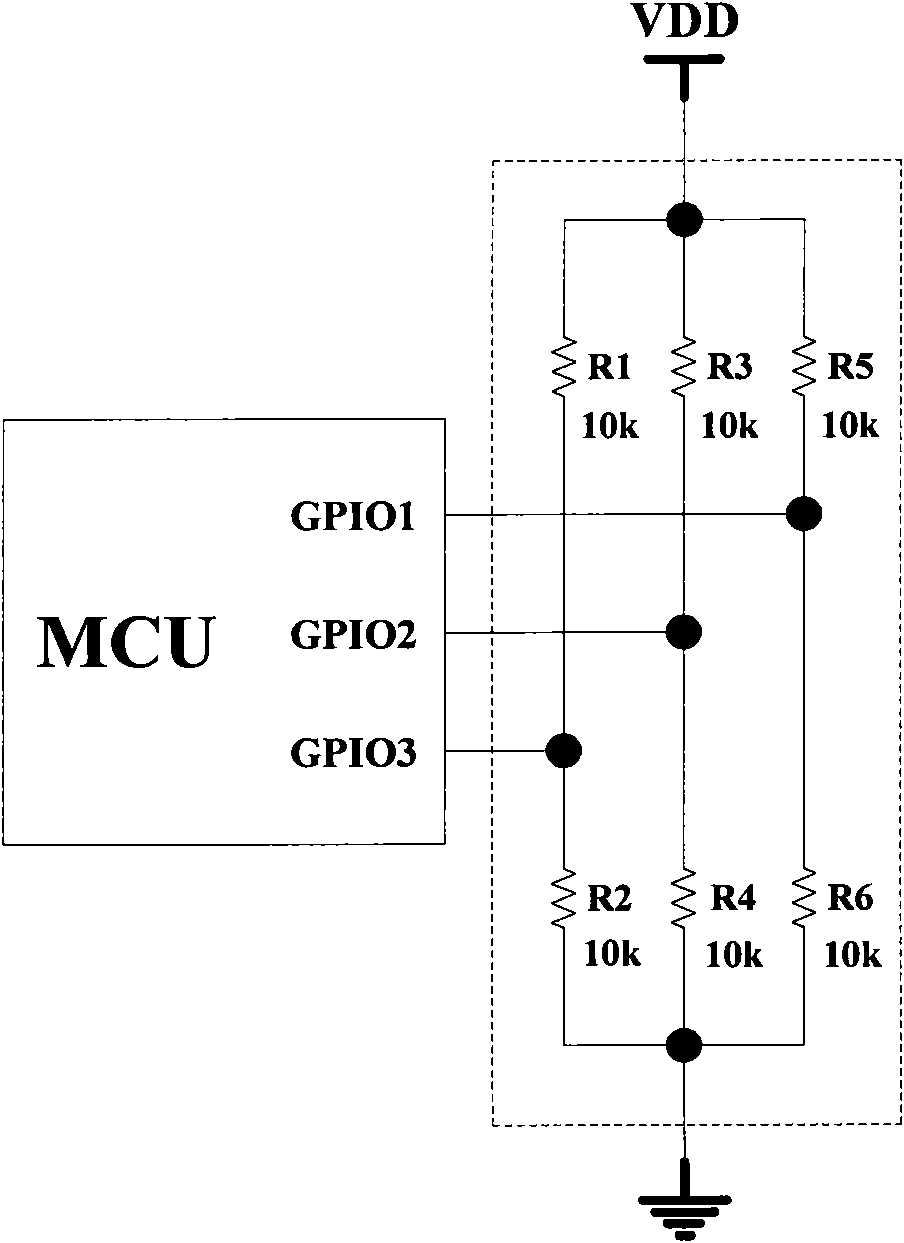
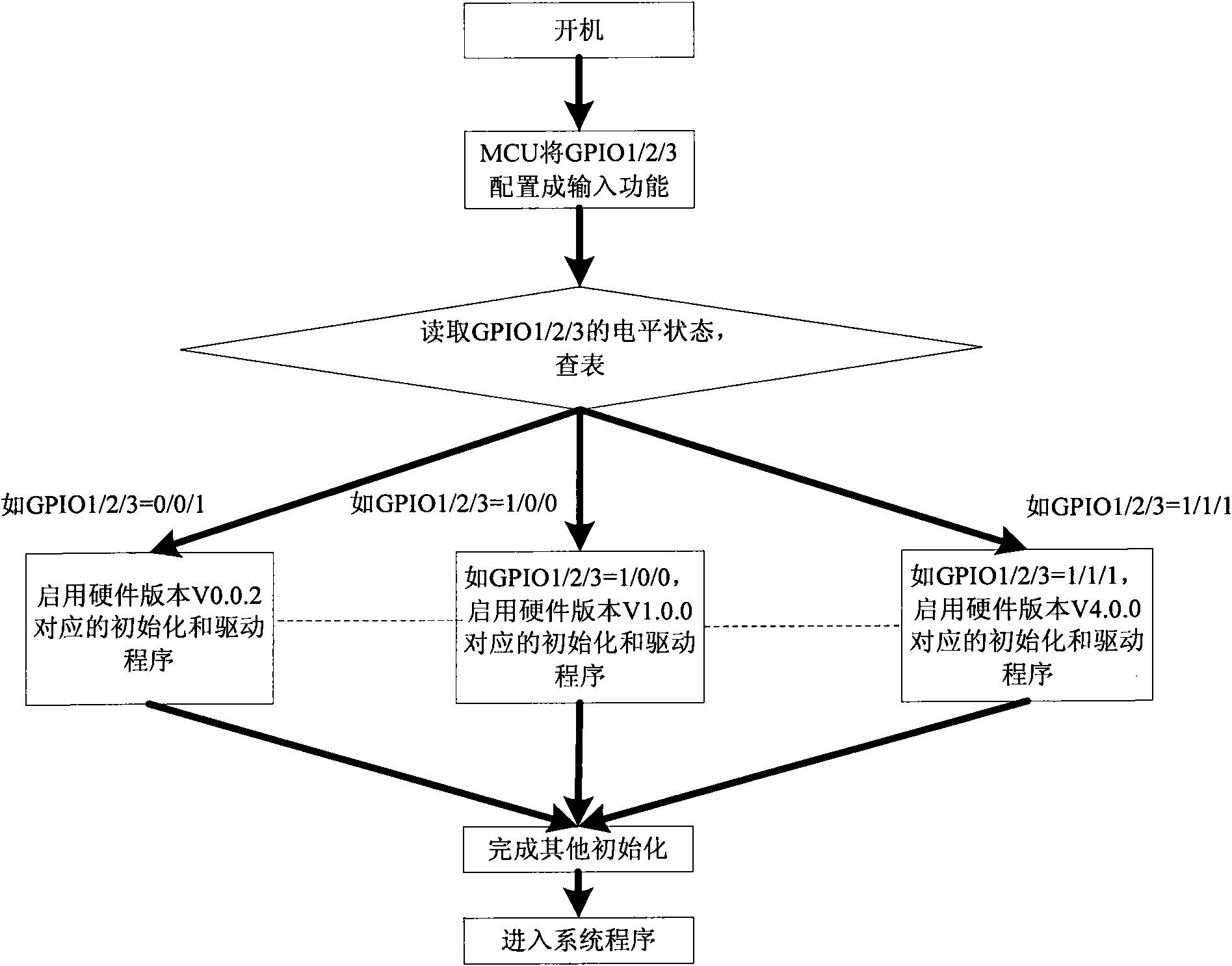
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
428 results about "Computer engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer engineering is a branch of engineering that integrates several fields of computer science and electronic engineering required to develop computer hardware and software. Computer engineers usually have training in electronic engineering (or electrical engineering), software design, and hardware-software integration instead of only software engineering or electronic engineering. Computer engineers are involved in many hardware and software aspects of computing, from the design of individual microcontrollers, microprocessors, personal computers, and supercomputers, to circuit design. This field of engineering not only focuses on how computer systems themselves work but also how they integrate into the larger picture.
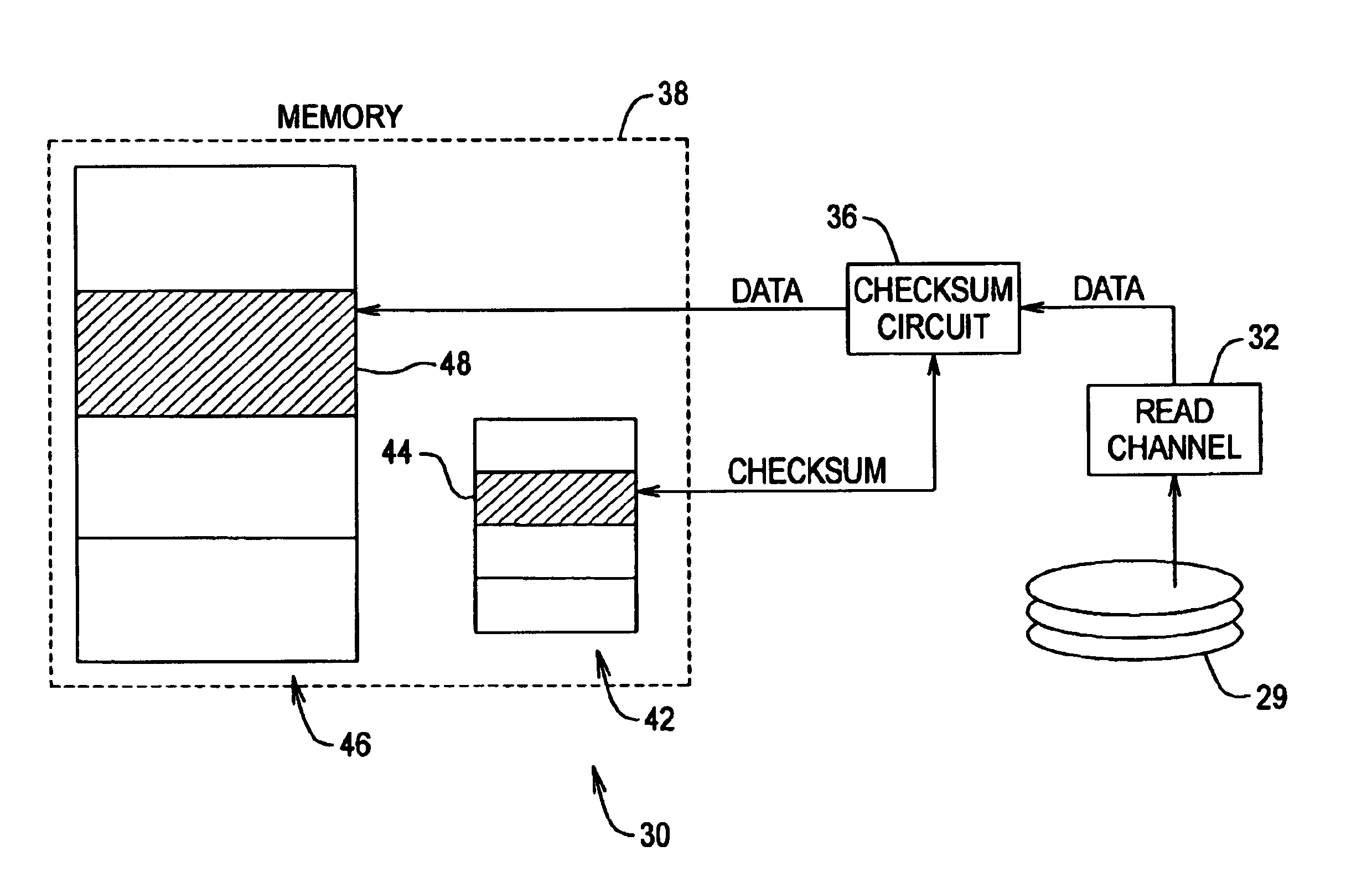
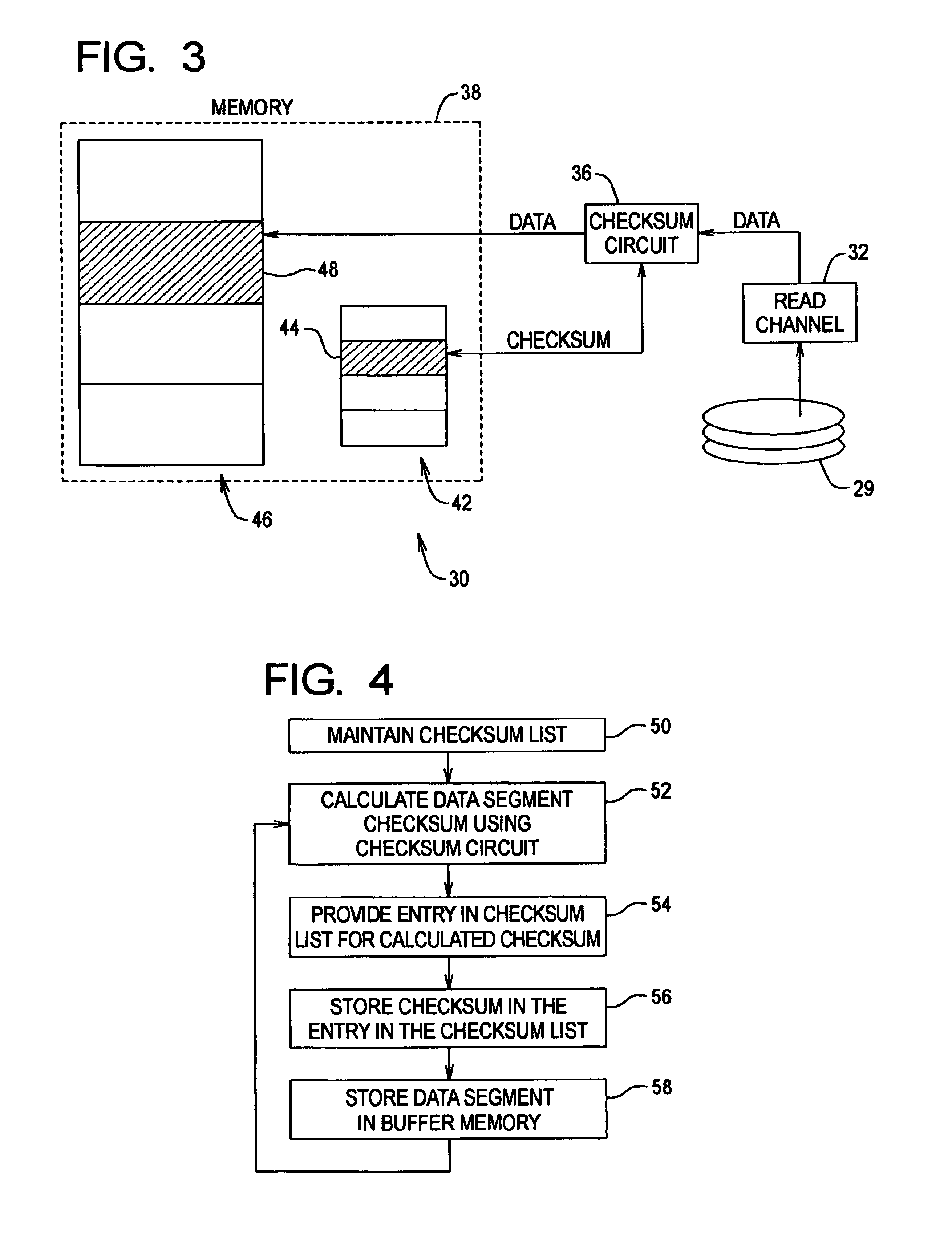
Data checksum method and apparatus
InactiveUS6964008B1Reduces memory bandwidth consumedReduce data transferCode conversionCoding detailsChecksumData store
A method and apparatus for generating checksum values for data segments retrieved from a data storage device for transfer into a buffer memory, is provided. A checksum list is maintained to contain checksum values, wherein the checksum list includes a plurality of entries corresponding to the data segments stored in the buffer memory, each entry for storing a checksum value for a corresponding data segment stored in the buffer memory. For each data segment retrieved from the storage device: a checksum value is calculated for that data segment using a checksum circuit; an entry in the checksum list corresponding to that data segment is selected; the checksum value is stored in the selected entry in the checksum list; and that data segment is stored in the buffer memory. Preferably, the checksum circuit calculates the checksum for each data segment as that data segment is transferred into the buffer memory.
Owner:MAXTOR
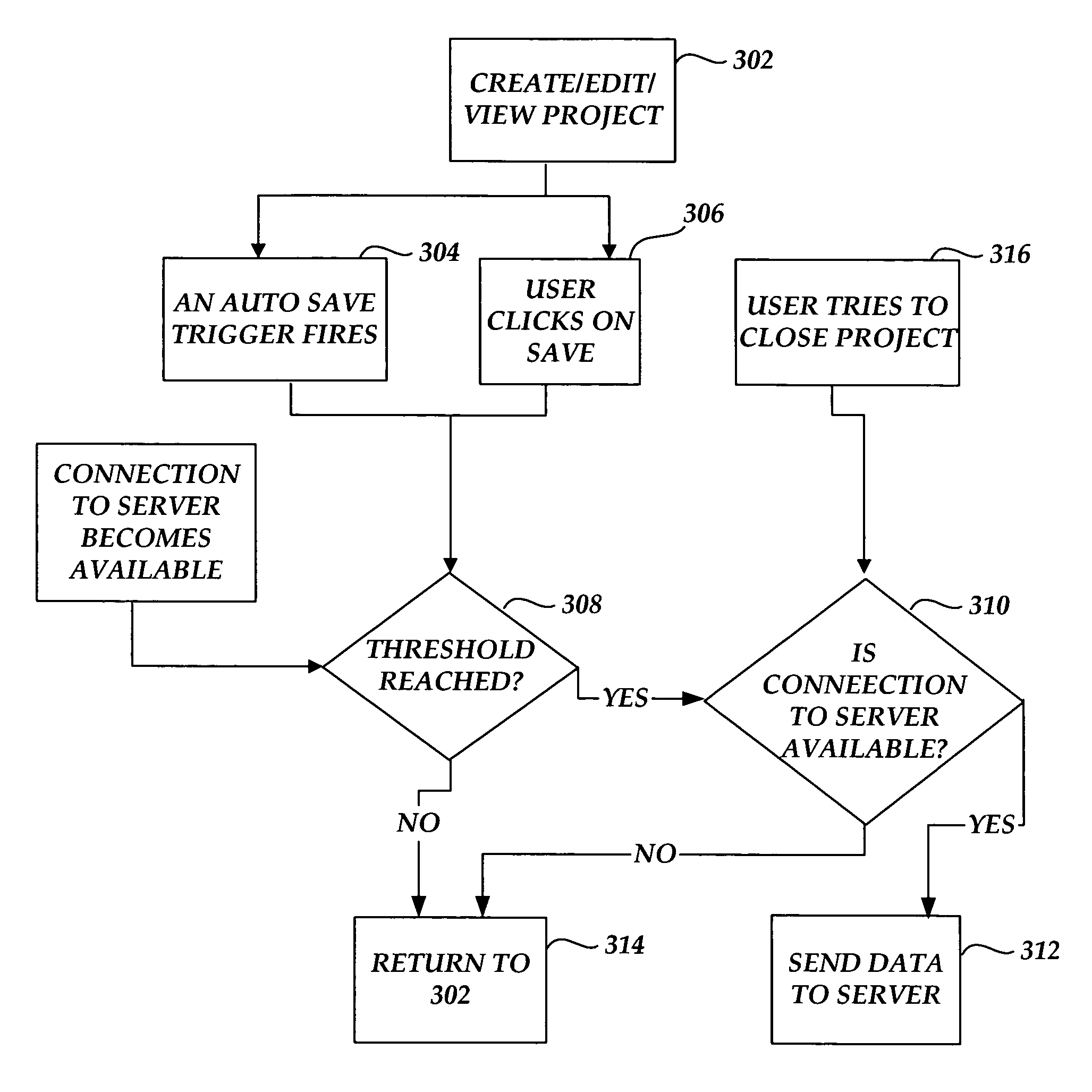
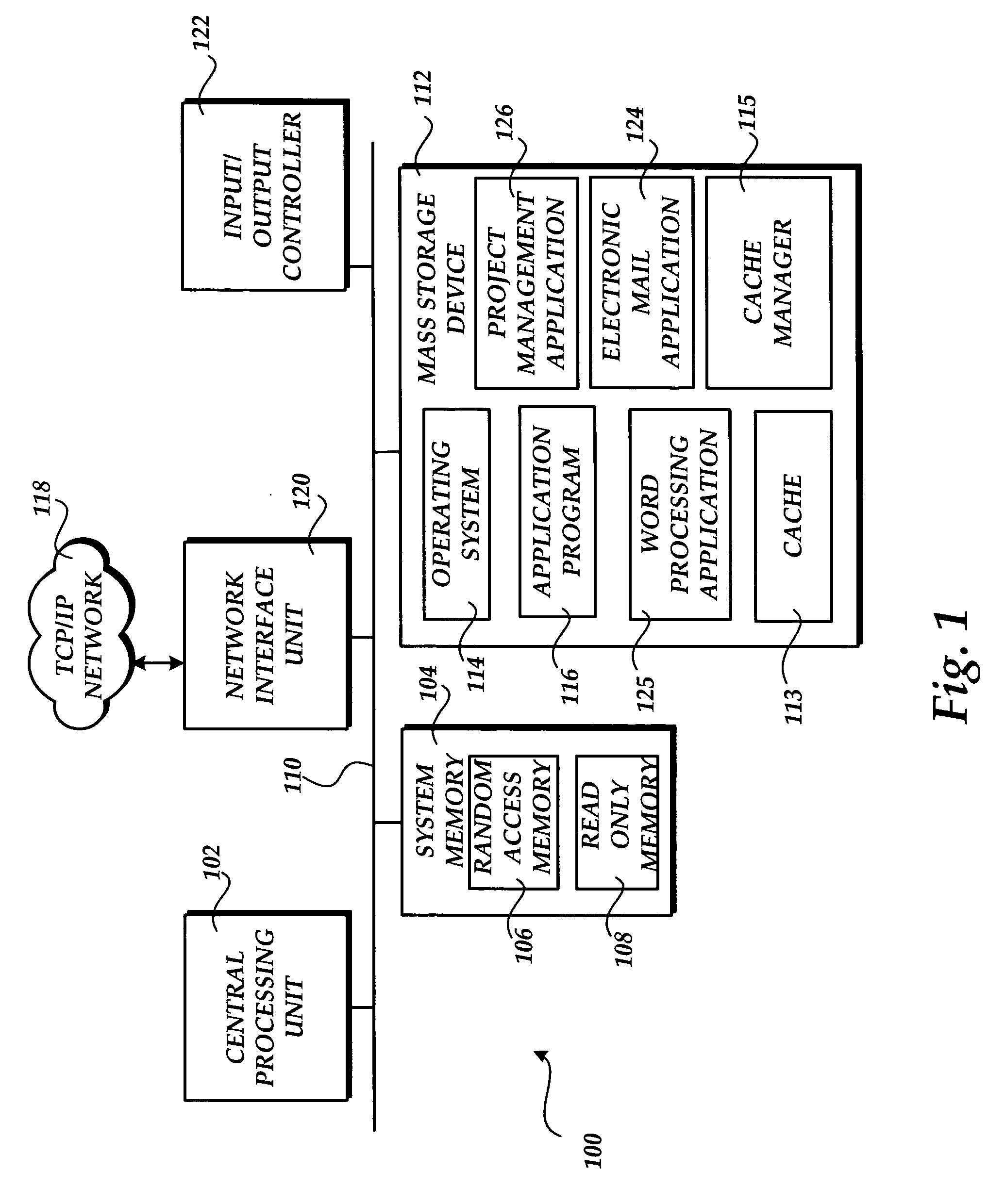
Methods and systems for caching and synchronizing project data
Methods and systems are provided for intelligently managing project data in a project management application. According to various aspects of the invention, project management data may be loaded and saved to a local cache of a client computer, such as a hard disk cache. The invention also provides a mechanism for reducing the size of data downloaded from and sent to a project server during load and save times.
Owner:MICROSOFT TECH LICENSING LLC
System and method for network communication of music data
InactiveUS20070163428A1Control interferenceElectrophonic musical instrumentsGraphical user interfaceRhythmic mode
A system, computer readable storage medium, and method for communicating musical data over a network, comprising: connecting one or more player modules to a network; providing an unassigned channel of prerecorded music data; providing an assigned channel of prerecorded music data; displaying the assigned channel; playing the unassigned channel while not playing the assigned channel; converting musical performance to music performance data; evaluating the music performance data in regard to the assigned channel; and simultaneously delivering a representation of the evaluation over the network. There may also be a graphical user interface, including a virtual instrument positioned substantially at a top portion of the graphical interface. Additionally, included are pluralities of musical notes in sequence, having a rhythmic pattern, each note being represented by a game object, wherein the game objects are directed upward, in substantially straight trajectories, toward the virtual keys on the virtual musical instrument corresponding to the musical notes.
Owner:SALTER HAL C
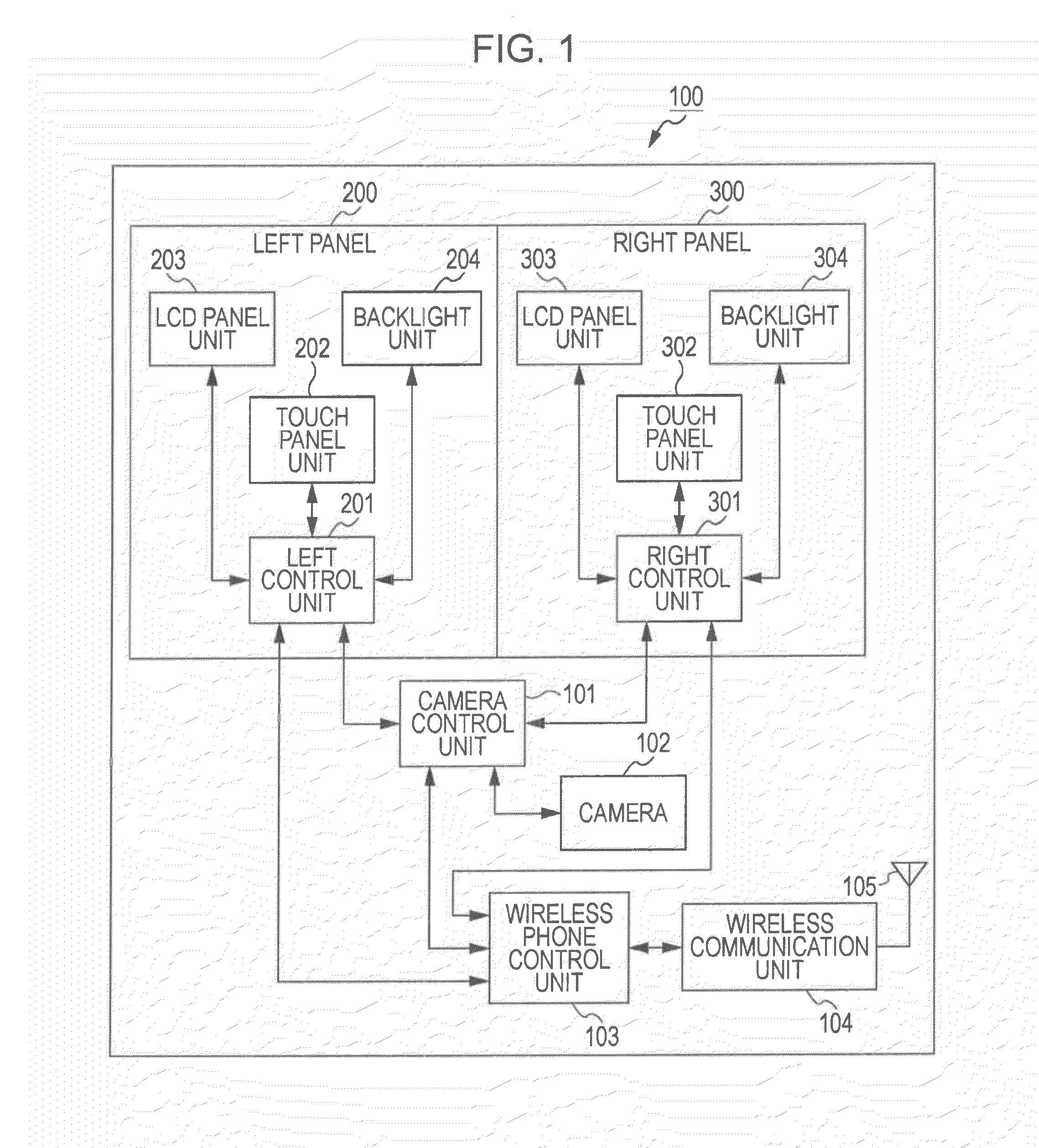
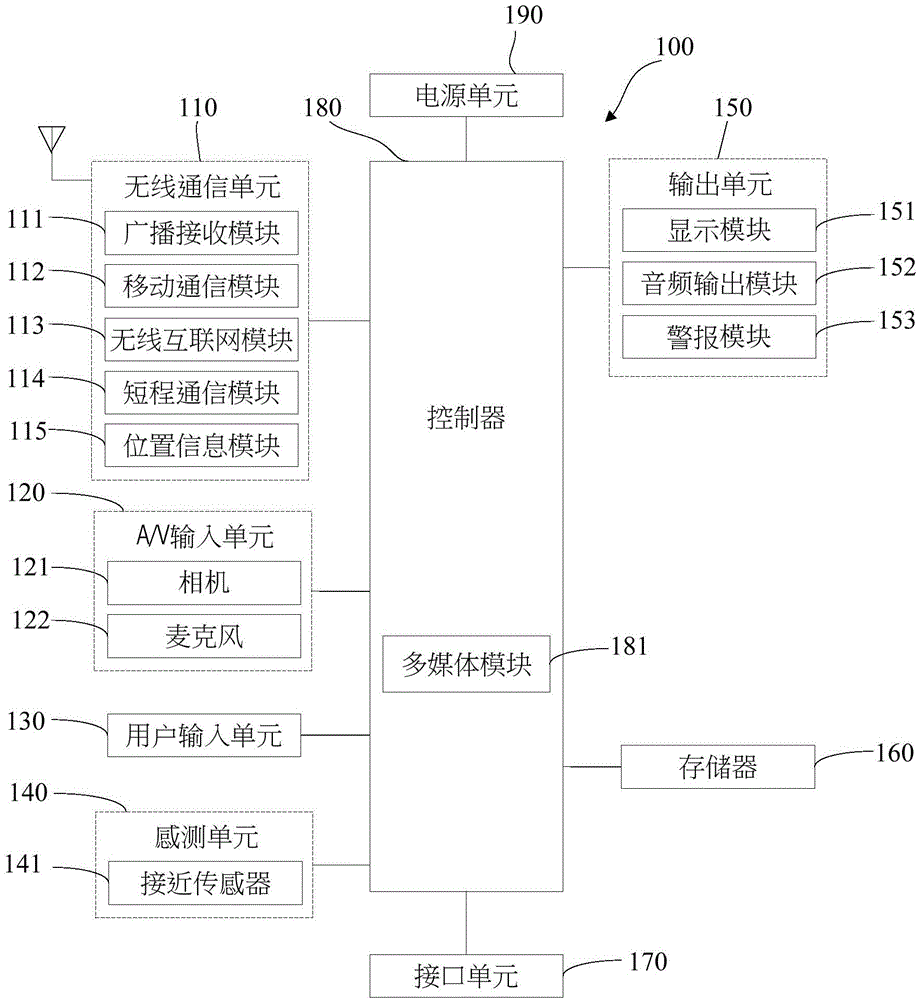
Terminal device, display method, and application computer program product
InactiveUS20110298826A1Reduce power consumptionNecessary electrical powerEnergy efficient ICTCathode-ray tube indicatorsApplication computersTerminal equipment
Owner:SONY CORP +1
Part size measurement method based on charge coupled device (CCD)
ActiveCN103063159AHigh speed measurementLow costCharacter and pattern recognitionUsing optical meansSize measurementHardware implementations
Owner:邳州市景鹏创业投资有限公司
Automated meter reading system
ActiveUS20080195562A1Data processing applicationsElectric devicesTelecommunications linkCommunication link
Owner:ELSTER ELECTRICTY LLC
Method for reducing power consumption of device, mobile terminal and system
ActiveCN105159816AReduce power consumptionImprove battery lifeHardware monitoringCurrent supply arrangementsTerminal equipmentComputer terminal
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method, device and mobile terminal for mobile terminal to download files
InactiveCN101127781ADownload to achieveDoes not affect other operationsRadio/inductive link selection arrangementsTransmissionFile serverComputer engineering
The utility model discloses to a method for mobile terminal to download files, which comprises the following steps: file searching request is sent to a searching server by the mobile terminal, and the search result comprising download address received by the mobile terminal from the feedback of the searching server. The mobile terminal then communicates with the designated file server and start file downloading. The utility model has advantages that network resource can be utilized really by applying the method. As the method is run in background, other operations of users are not affected, thereby the method is very convenient; the success rate of file downloading can be maximally ensured through optimal combined application of aggregation of addresses, proxy download and file segmentation; corresponding the method, the utility model also provides a device for file download, and a mobile terminal comprising the device.
Owner:BEIJING SOHU NEW ERA INFORMATION TECH CO LTD
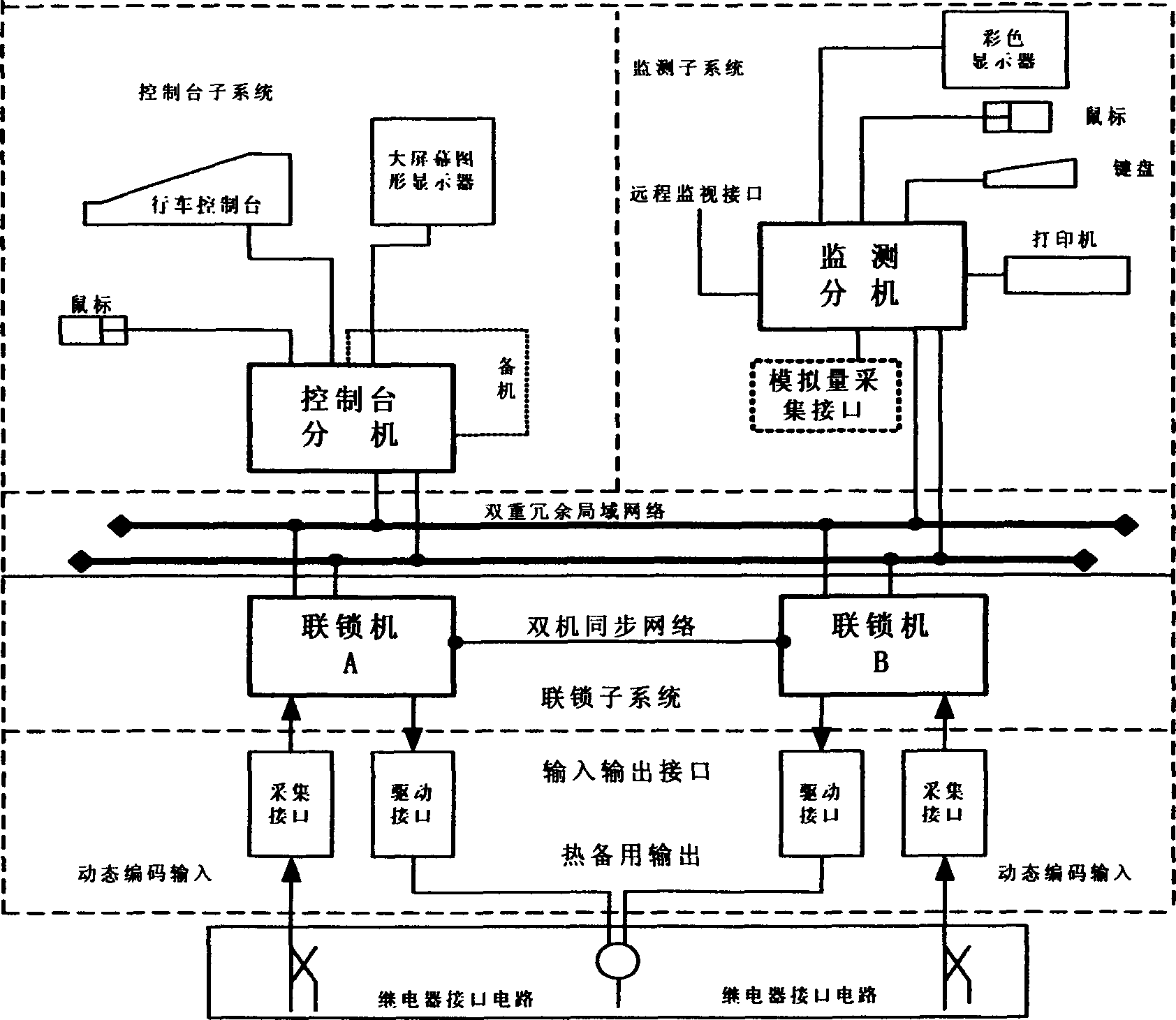
Computer interlock system
ActiveCN1803510AAvoid interferenceImprove accuracyData switching by path configurationRailway signalling and safetyControl systemNetwork communication
Owner:CRSC RESEARCH & DESIGN INSTITUTE GROUP CO LTD
Memory test method, tested terminal, test client and system
ActiveCN106557424AImprove performanceImprove optimization efficiencySoftware testing/debuggingClient-sideApplication software
Owner:TENCENT TECH (SHENZHEN) CO LTD
Terminal equipment software and hardware self-adaptive matching method and terminal equipment using same
Owner:LEADCORE TECH
Barcode generation system, barcode generation program, printing device, and test chart
InactiveUS20090072035A1Minimum usage amountPrintingRecord carriers used with machinesBarcodeImaging data
Owner:COPYER
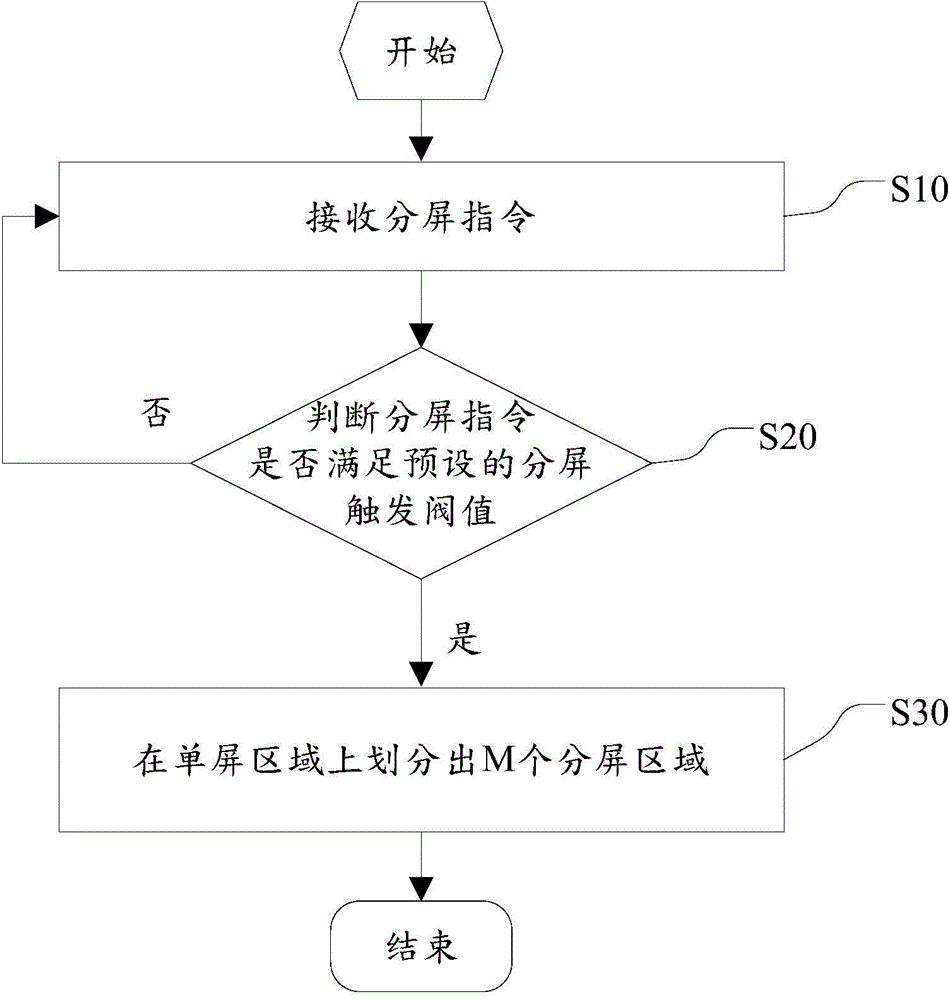
Screen division method and device of mobile terminal
InactiveCN104821988AImprove operating experienceEasy to openSubstation equipmentComputer terminalComputer engineering
Owner:NUBIA TECHNOLOGY CO LTD
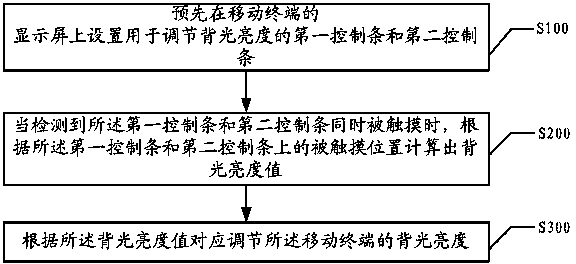
Backlight brightness adjustment method and system for mobile terminals
ActiveCN104182143ASolve the accuracy problemSolve the adjustmentInput/output processes for data processingLightnessBrightness perception
Owner:威海神舟信息技术研究院有限公司
Screen splitting configuration method and terminal
ActiveCN106557230AExecution for user interfacesSpecial data processing applicationsComputer engineering
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Configuration method of automobile diagnosis software and related equipment
InactiveCN111474921AImprove versatilityReduce difficultyProgramme controlElectric testing/monitoringDiagnostic equipmentServer
The invention provides a configuration method of automobile diagnosis software and related equipment. The method comprises the following steps: acquiring vehicle type information of a diagnosed vehicle; sending an acquisition request to a server, the acquisition request comprising vehicle model information of the diagnosed vehicle, the acquisition request being used for requesting to acquire a target diagnosis software package corresponding to the vehicle model information of the diagnosed vehicle; and receiving the target diagnosis software package sent by the server, and configuring diagnosis software on the automobile diagnosis equipment according to the target diagnosis software package. According to the scheme, the universality of the automobile diagnosis software can be improved, andthe configuration updating difficulty of the automobile diagnosis software is reduced.
Owner:LAUNCH TECH CO LTD
Apparatus for dividing bank in flash memory
InactiveUS6963502B2Shorten the lengthImprove the sense of speedRead-only memoriesDigital storageComputer sciencePage buffers
The present invention relates to an apparatus for dividing a bank in a flash memory. A block of the flash memory is divided into two banks and each page buffer is located between the two banks to share an input / output line. Therefore, it is possible to shorten the length of a bit line, improve a data sensing rate, and allow one bank to perform one operation while the other bank performs a read, write or erase operation.
Owner:SK HYNIX INC
Printing control device, storage medium storing printing control program, and printing control method
InactiveUS20130033714A1Digitally marking record carriersVisual presentation using printersControl equipmentPrint processor
Owner:CANON KK
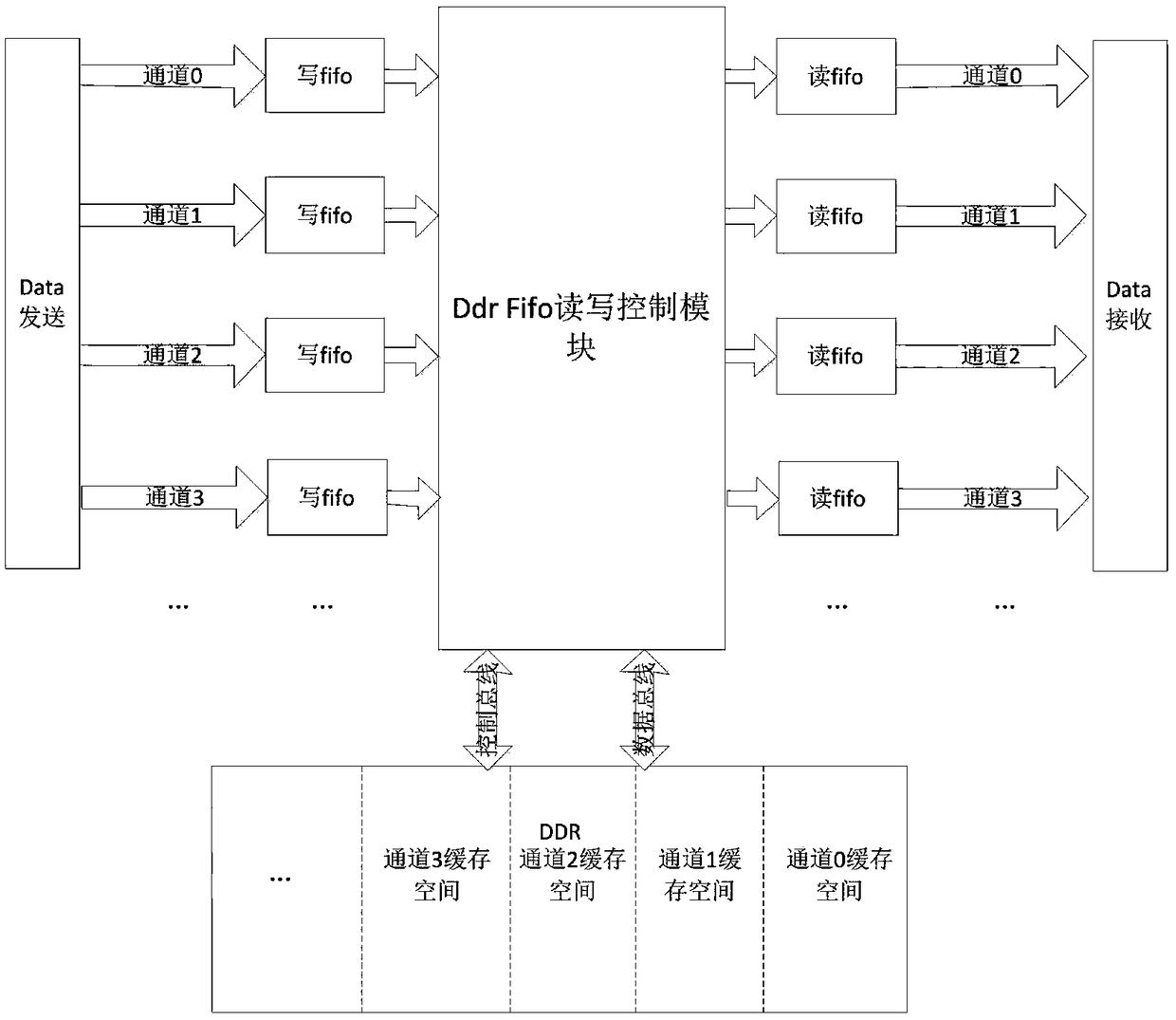
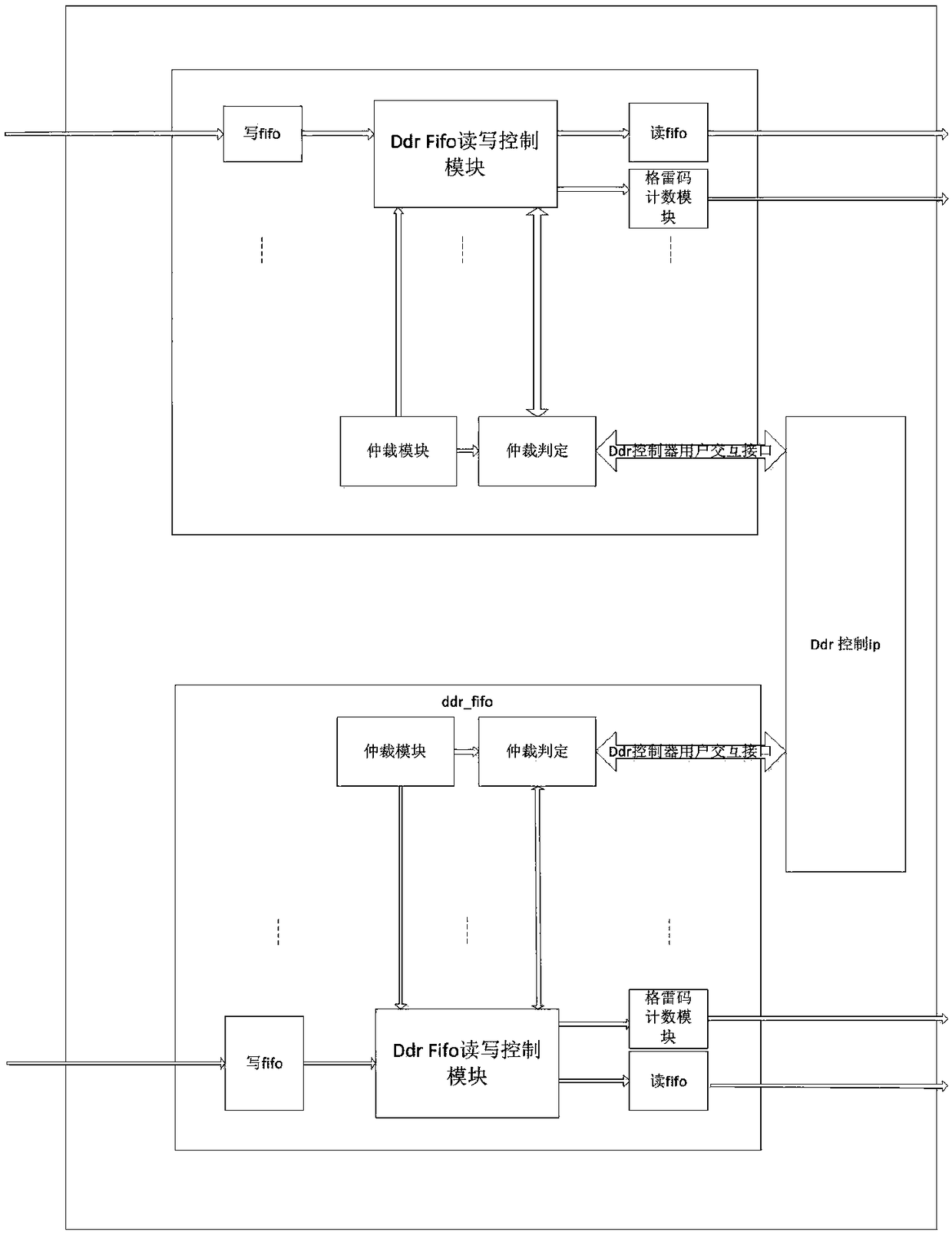
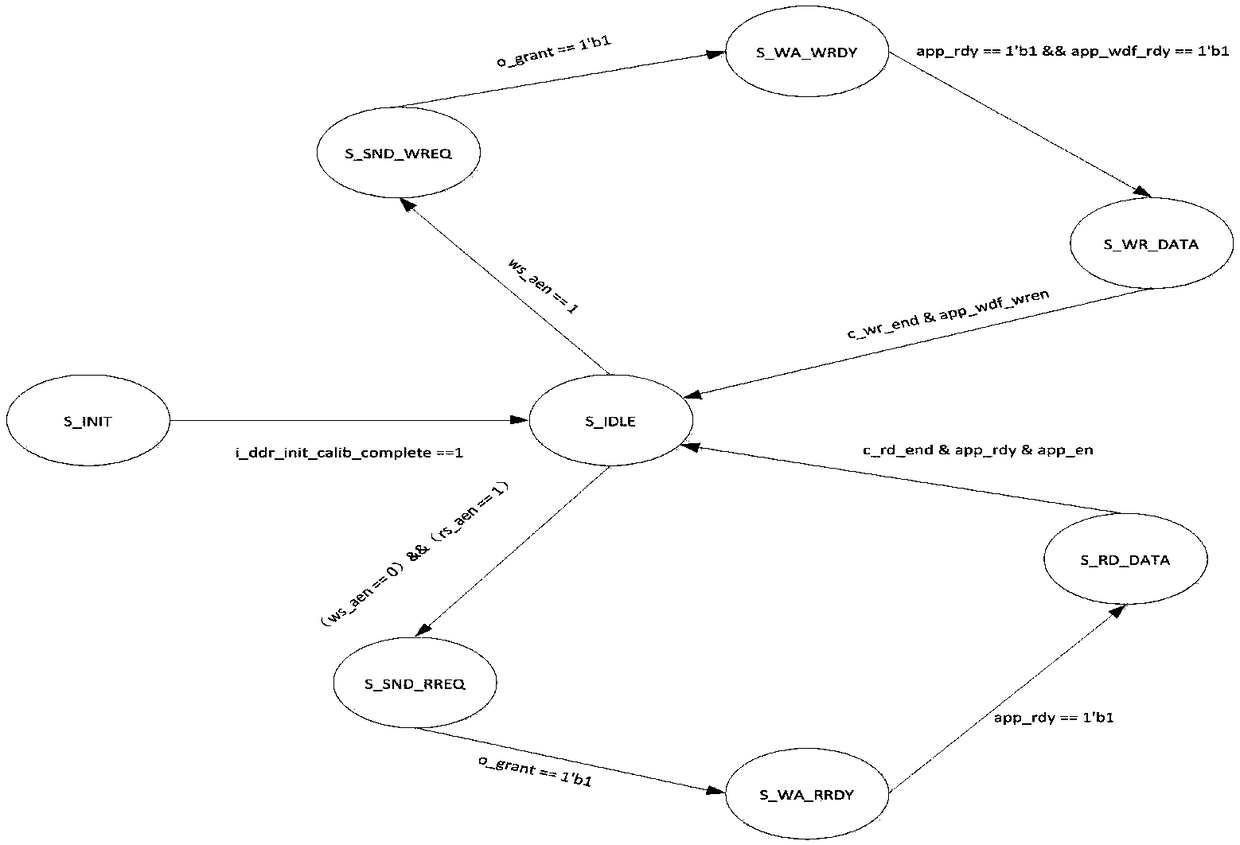
An FPGA implementation method of multi-channel data source DDR buffer
ActiveCN109271335AFlexible matching of address spaceFlexible change of memory spaceData conversionChannel dataFpga implementations
Owner:上海威固信息技术股份有限公司
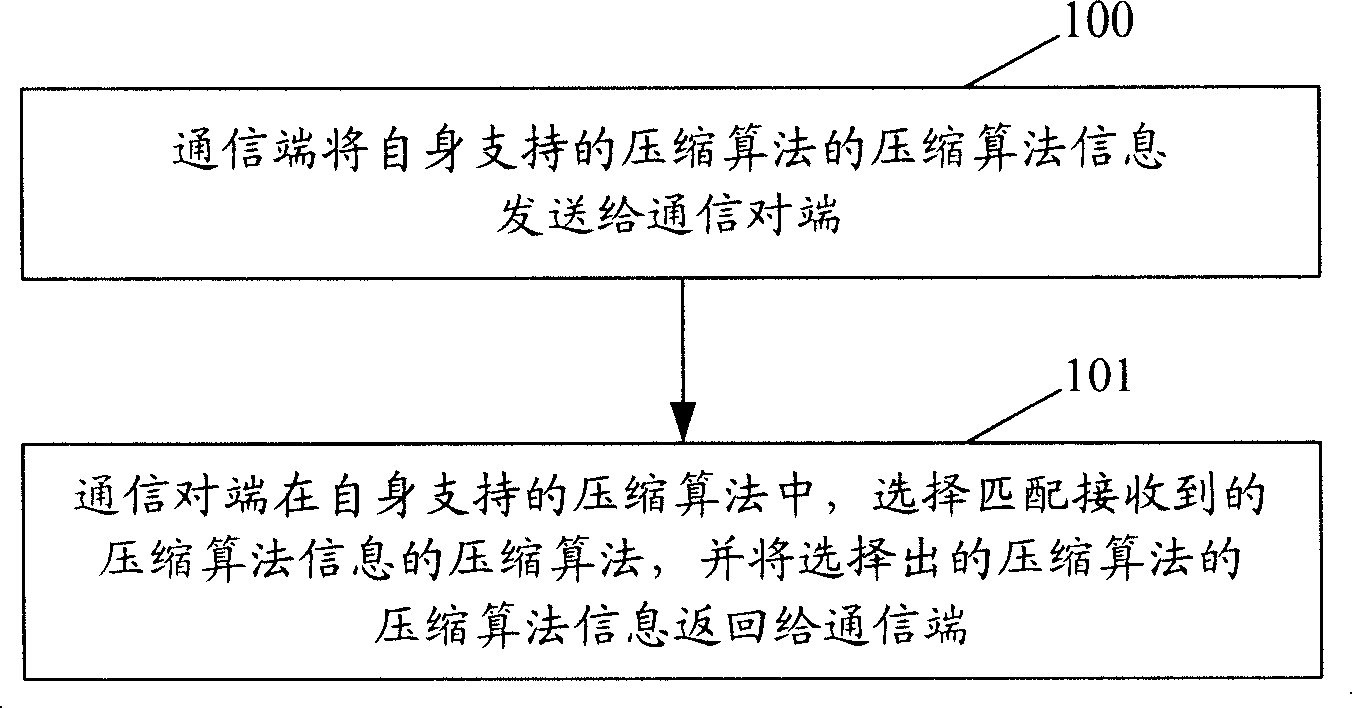
Method and system for confirming compression algorithm
InactiveCN101197824AReduce latencyReduce decompression timeData switching networksTime delaysComputer engineering
Owner:HUAWEI TECH CO LTD
Online teaching method and device, storage medium and terminal equipment
InactiveCN110673777ALow costCan't solveData processing applicationsWebsite content managementTerminal equipmentHuman–computer interaction
Owner:BEIJING DA MI TECH CO LTD
Resistance variable memory device performing program and verification operation
A variable resistance memory device includes: a memory cell array comprising a plurality of memory cells, a pulse shifter shifting a plurality of program pulses to generate a plurality of shifted program pulses, a write and verification driver receiving the plurality of shifted program pulses to provide a program current that varies with the plurality of shifted program pulses to the plurality of memory cells, and control logic providing the plurality of program pulses to the pulse shifter and the write and verification driver during a program / verification operation, such at least two write data bits are programmed to the memory cell array in parallel during the program / verification operation.
Owner:SAMSUNG ELECTRONICS CO LTD
Malicious software API call sequence detection method based on graph convolution
ActiveCN111259388AImprove bindingFlexible organizational structurePlatform integrity maintainanceNeural architecturesCall graphAlgorithm
Owner:SUN YAT SEN UNIV
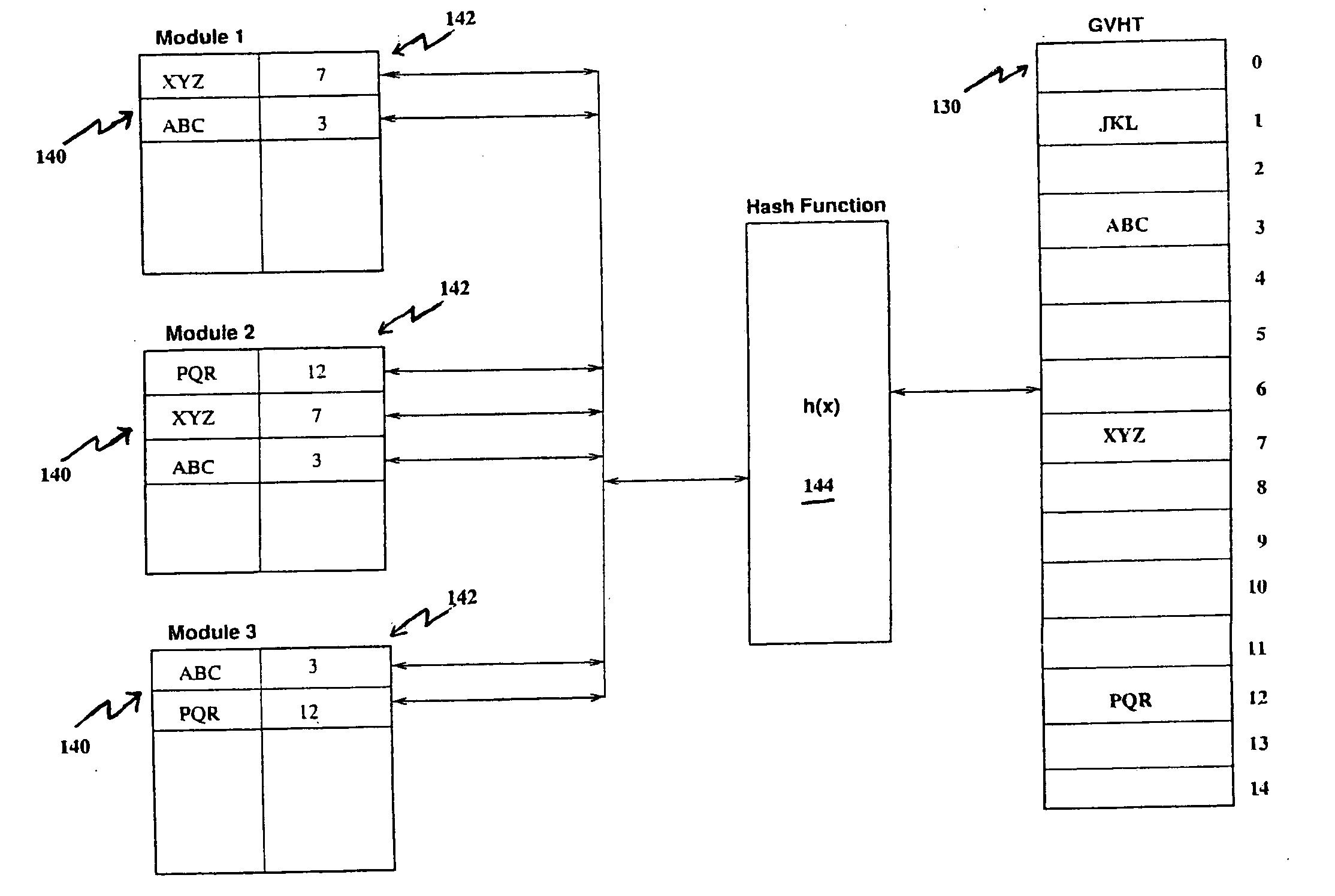
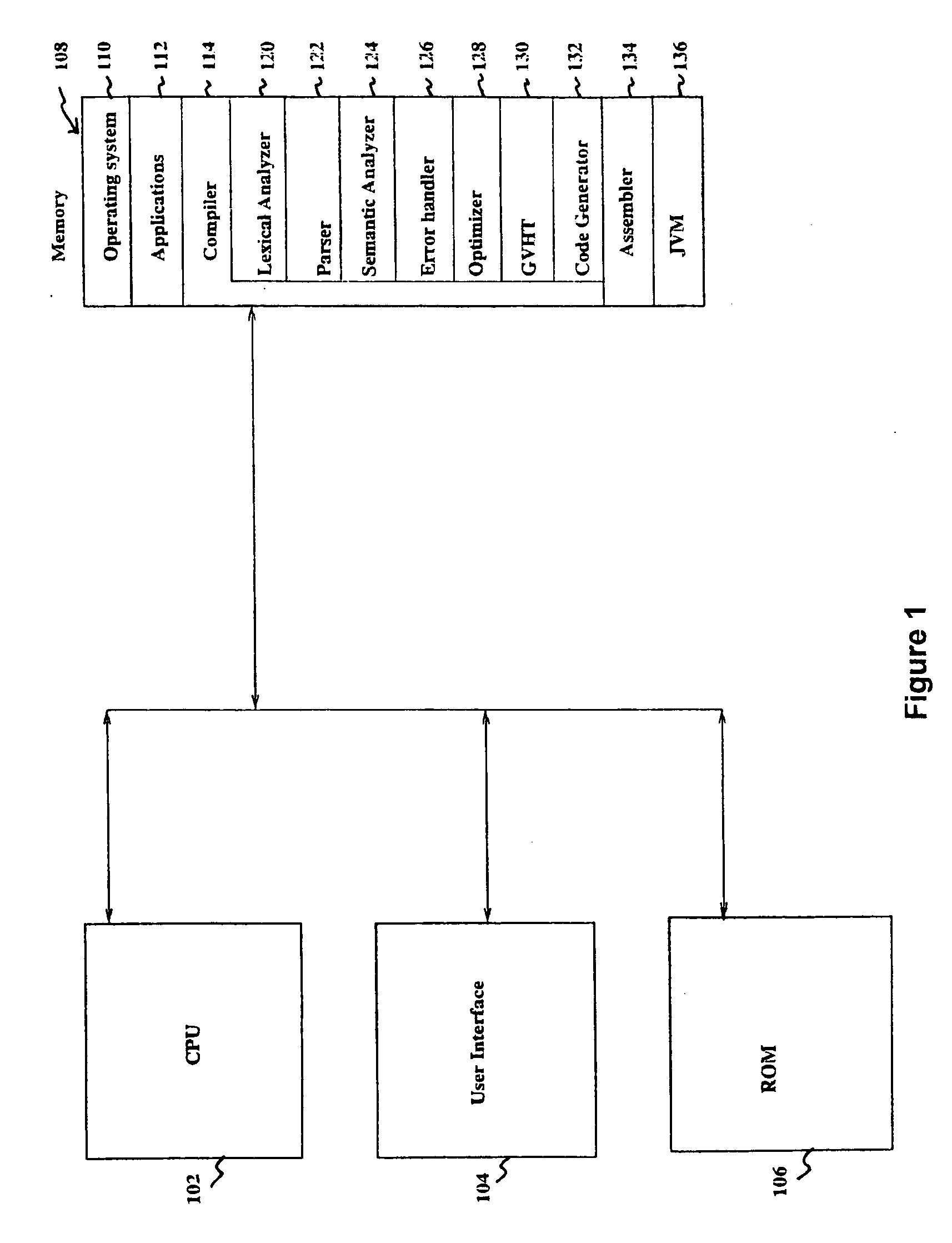
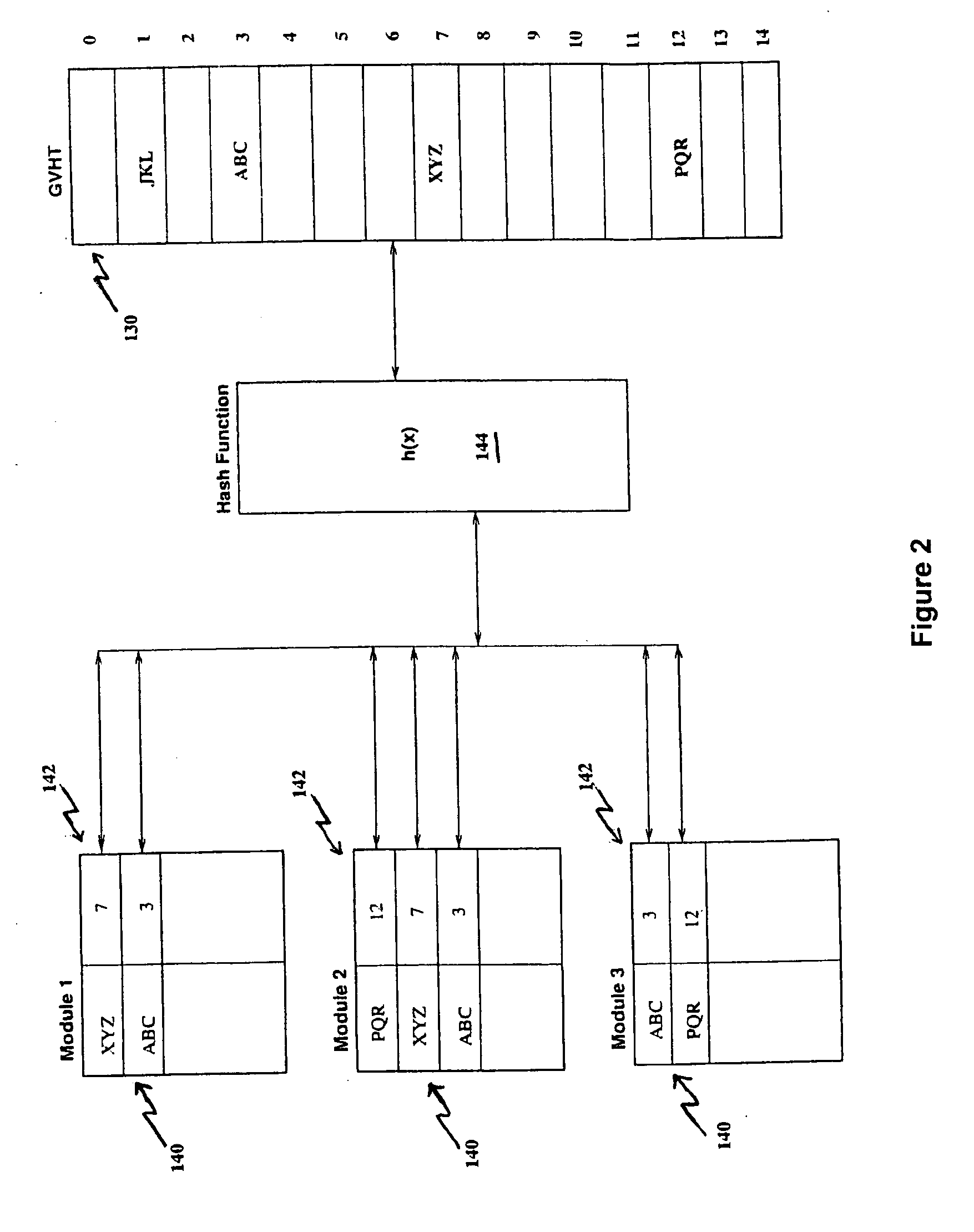
Compile time linking via hashing technique
InactiveUS20060130020A1Simple processRapid techniqueLink editingProgram controlAddress resolutionMachine code
A linker is usually used, in post processing of compiling high-level languages such as C into machine executable language, to bind separately compiled object files and resolve the addresses (142) of global variables (140) declared in the separate files. The invention proposes linking during compile time by using a special purpose hash table called global variables hash table (130) shared among the separate files. This results in a collection of processed object files that are coherent in terms of their addresses (142) for global variables (140) that could be further assembled correctly into machine executable code. This method is useful for compiling separate high level language source files to generate executable machine code employing a technique of address resolution across separate modules.
Owner:AXIOMATIC SOLUTIONS
Method for generating data in storage system having compression function
ActiveUS20140114936A1Improve performanceSuppressing unnecessary processingDigital data information retrievalDigital data processing detailsComputer engineeringProcess time
The present invention aims at improving the performance of a compression function in a storage system, and solves the prior art problem of having to decompress a whole compression unit even if a read request or a write request targets only a portion smaller than the compression unit, causing increase of overhead of decompression processing and elongation of processing time, and deteriorating performance The present invention prevents unnecessary decompression processing and reduces the overhead of processing by suppressing the range of decompression processing to a minimum portion according to the relationship between the read / write request range and the compression unit.
Owner:HITACHI LTD
Flexible software-defined networking (SDN) protocol for service provider networks
ActiveUS20190319876A1Facilitates to forward packetData switching networksOpenFlowComputer engineering
Methods and apparatuses for building a programmable dataplane are described. Specifically, the programmable dataplane can work on a list of identifiers, such as those part of OpenFlow 1.5. Specifically, the programmable dataplane can be built by creating a virtual network graph at a controller node using binary identifiers such that a node is broken into an n-ary tree and the tree has 1×2 or 1×1 nodes.
Owner:INDIAN INSTITUTE OF TECHNOLOGY BOMBAY +1
A credit record service method and system based on mobile terminal
InactiveCN101087329AEasy to useEasy to manageSpecial service for subscribersSerial codeComputer engineering
Owner:SHANGHAI GAOFEI INFORMATION TECH
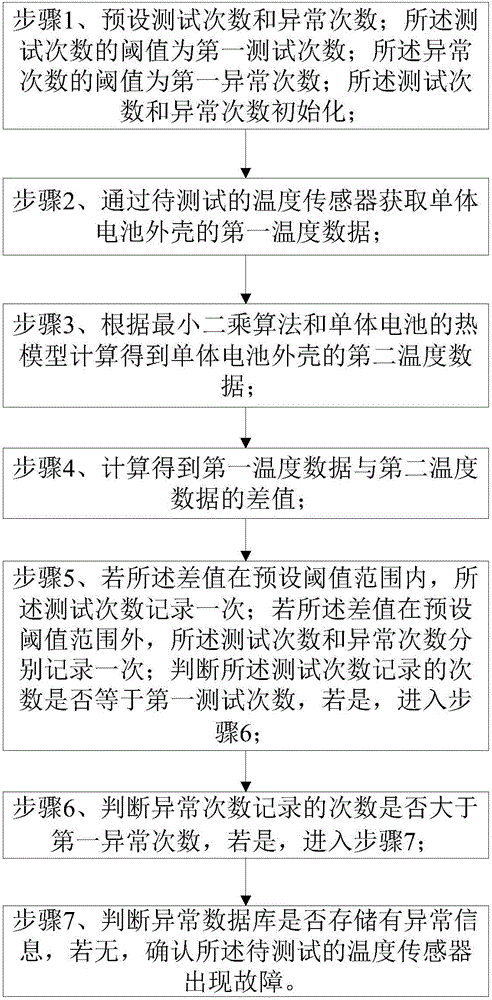
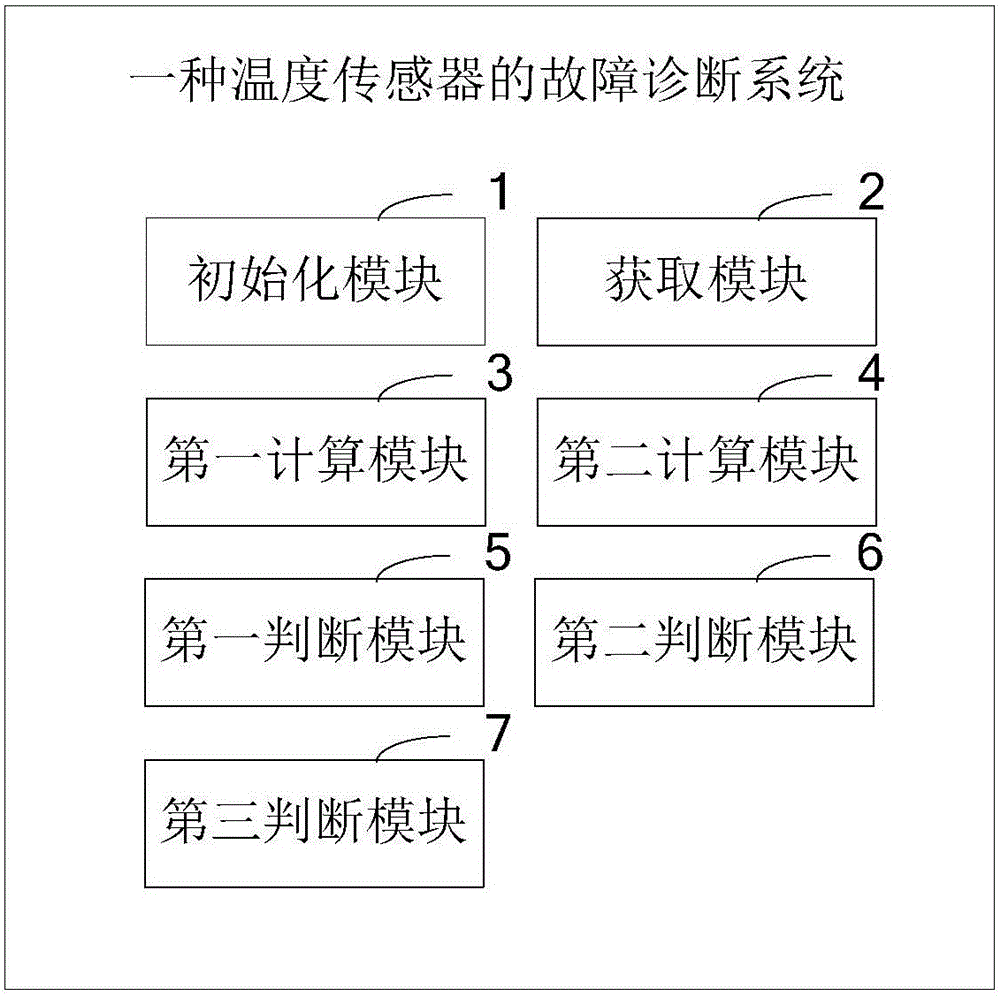
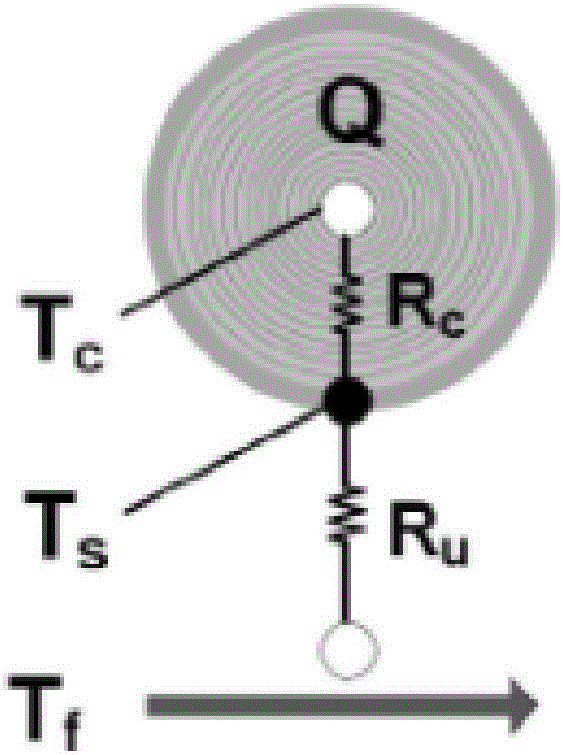
Temperature sensor fault diagnosis method and system
ActiveCN106017737AReduce the amount of redundancyAvoid Misjudging Battery StatusElectrical testingThermometer testing/calibrationTime rangeDiagnosis methods
Owner:FUZHOU DANLAW XICHENG ELECTRONICS TECH CO LTD
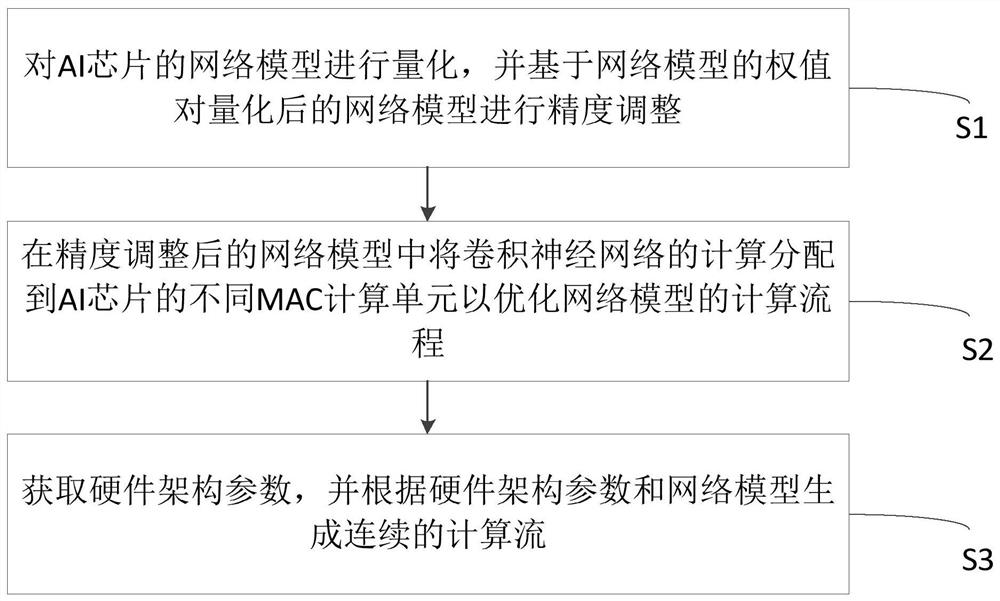
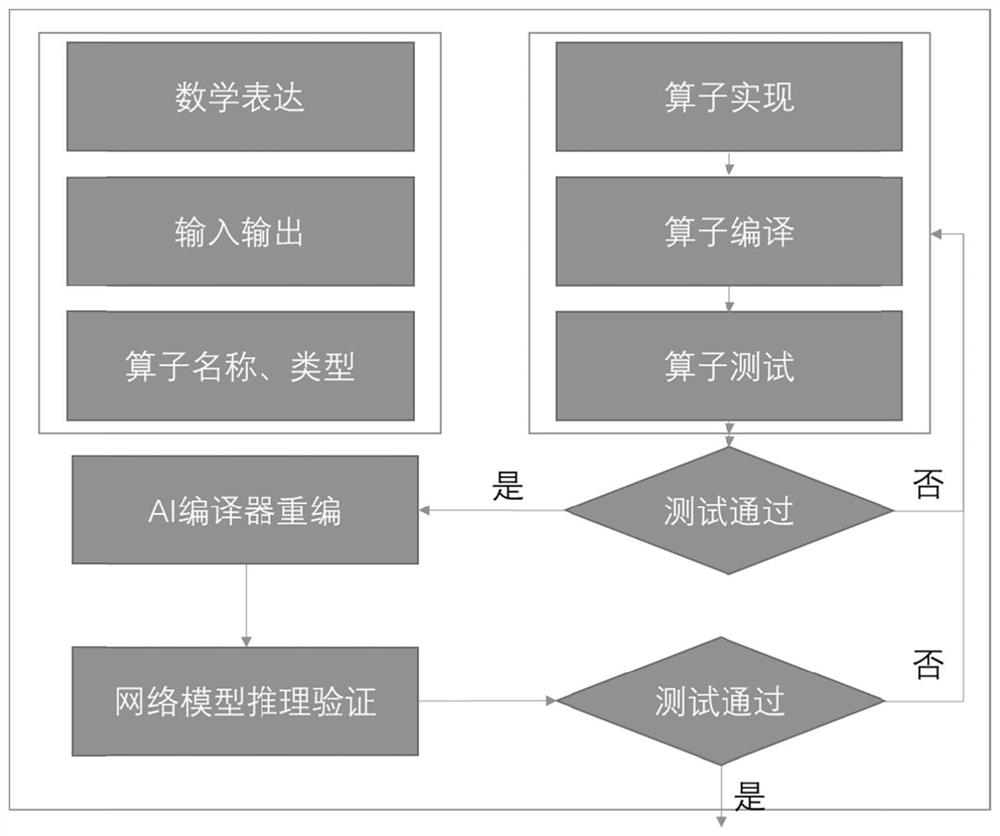
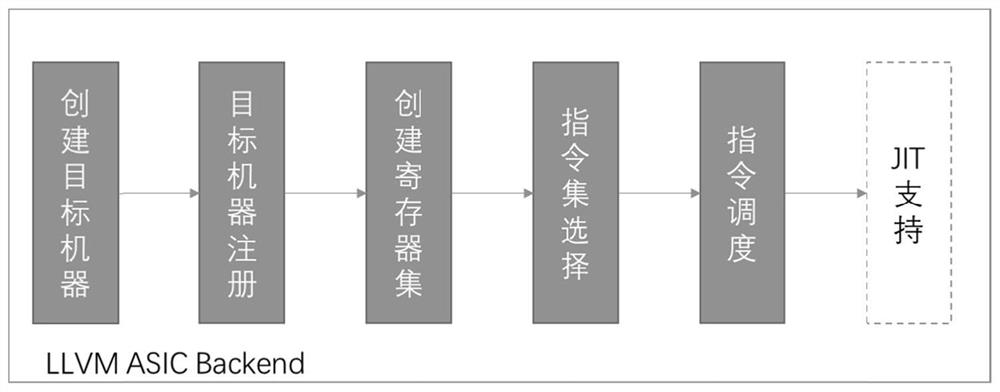
Method, system and device for compiling AI chip and medium
InactiveCN112232497ASolve interface problemsComprehensive and reliable quantification functionsPhysical realisationCode compilationHardware architectureAlgorithm
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
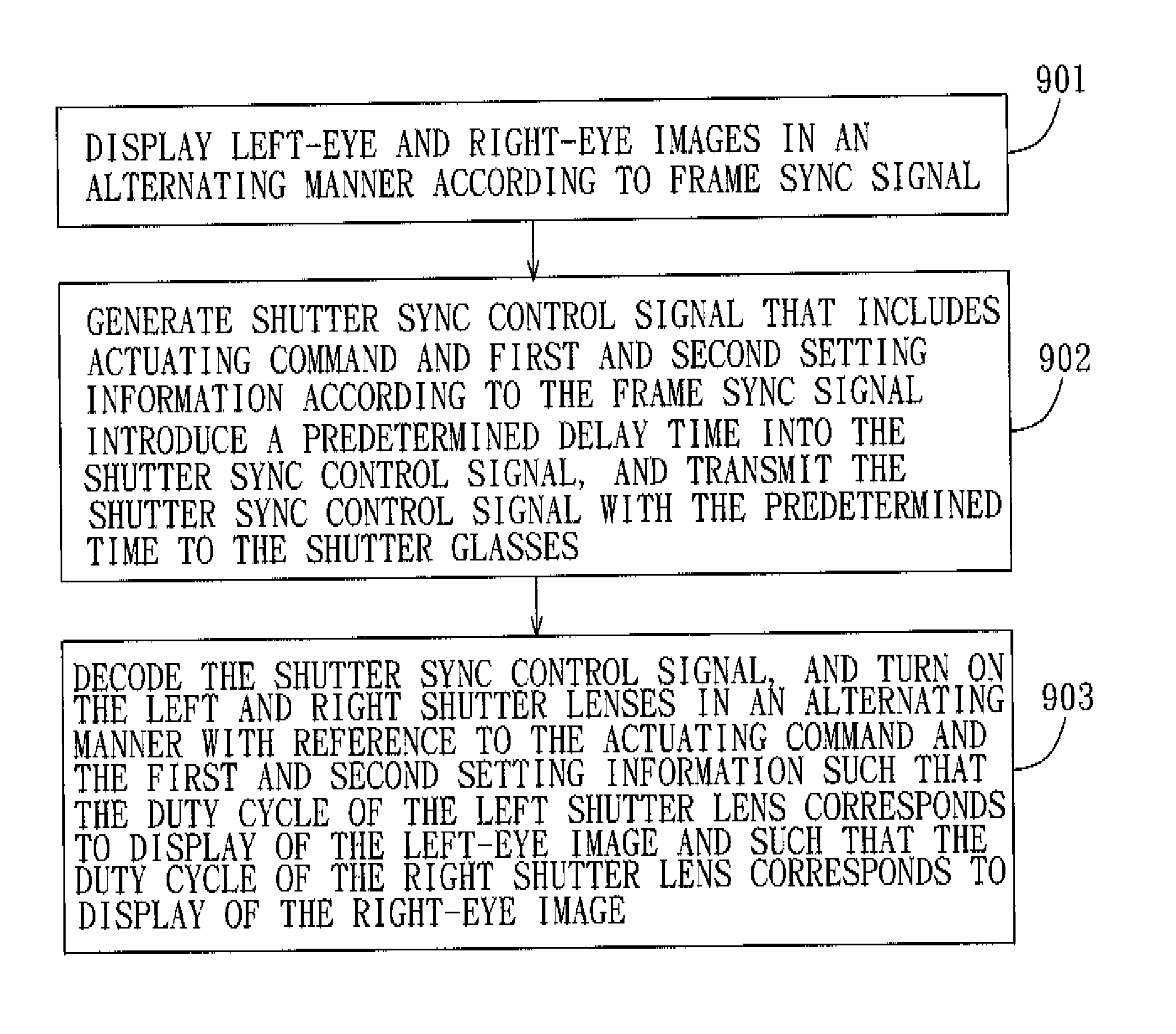
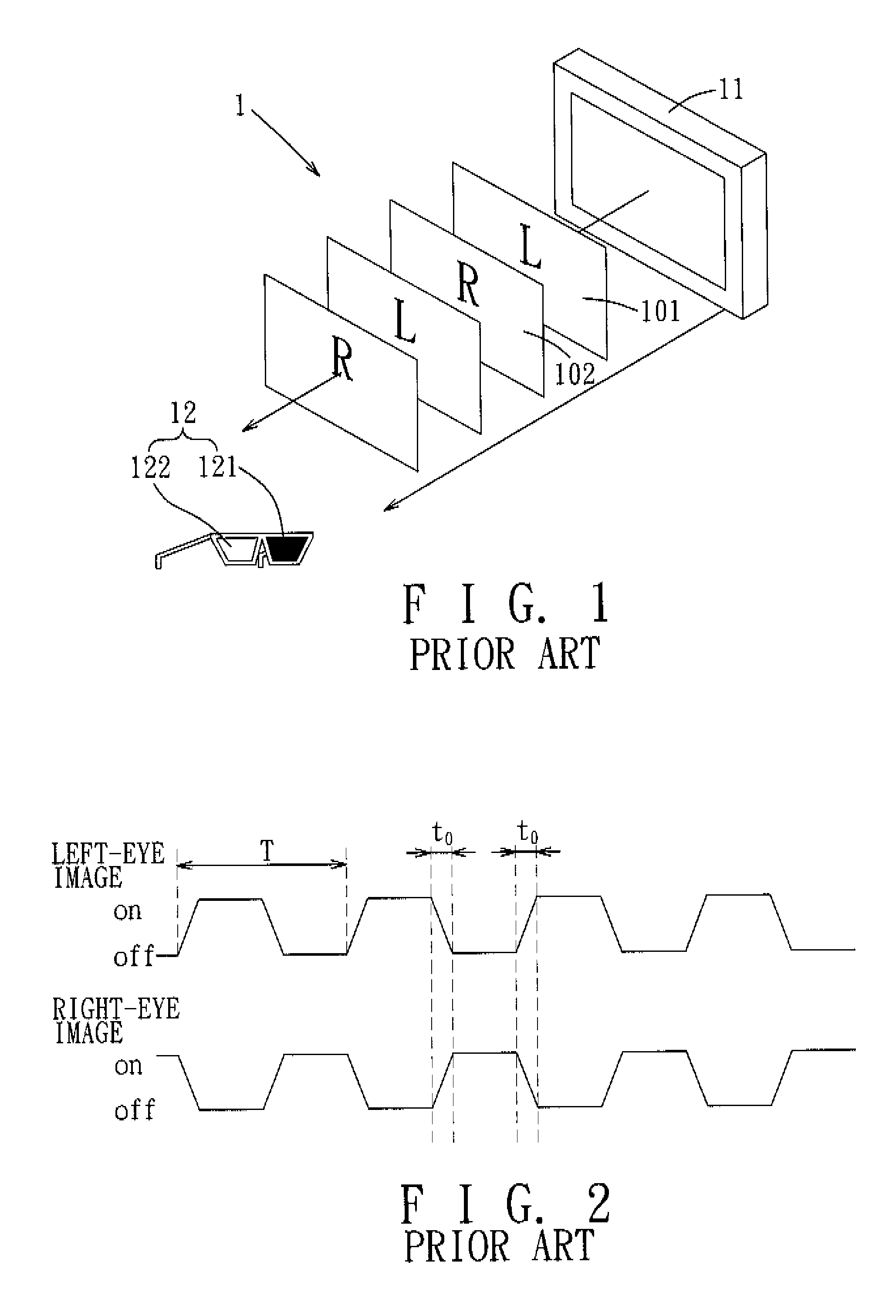
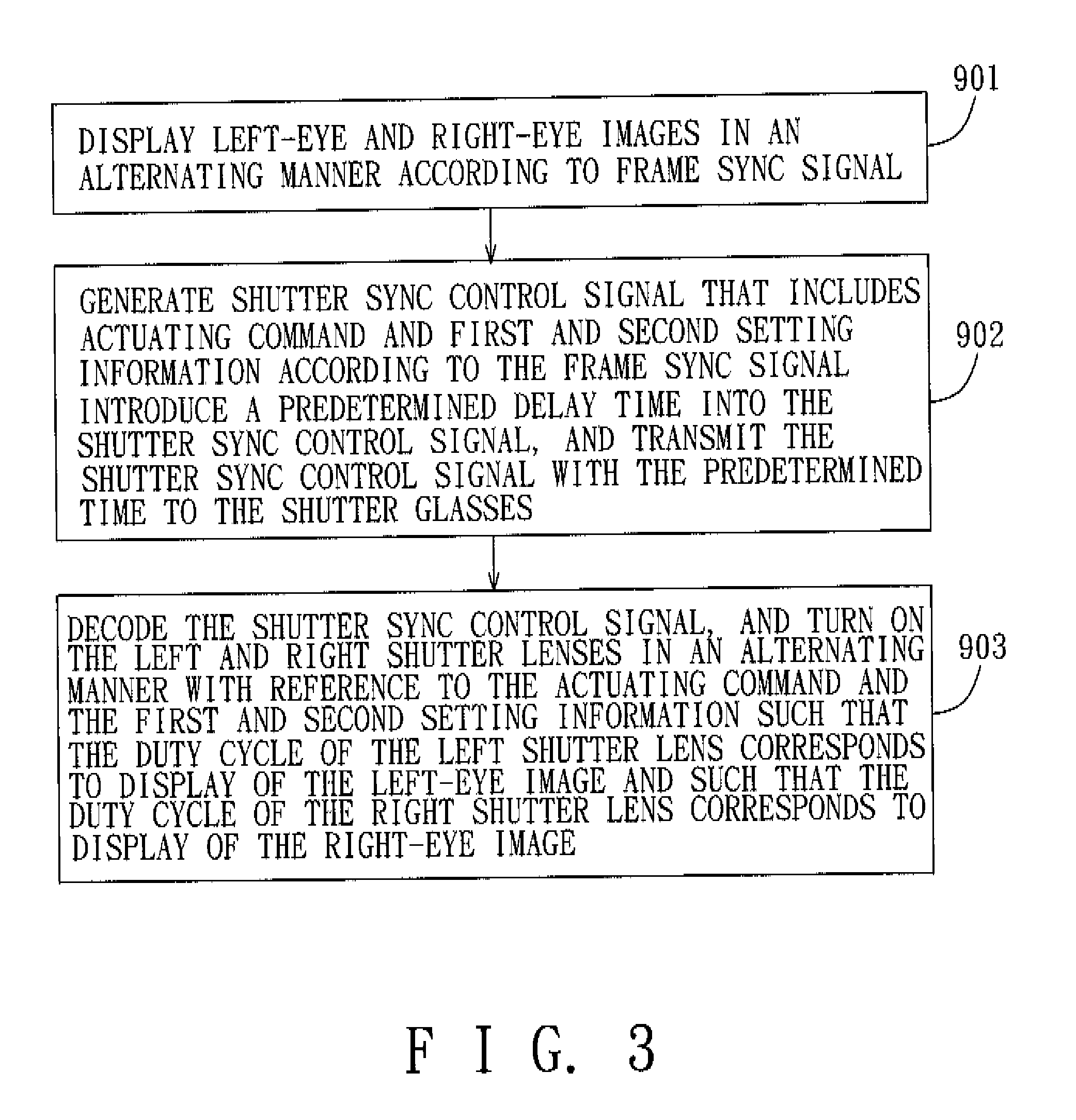
Active shutter stereoscopic image display system and method of controlling the same
Owner:THE VICTORY INVESTMENTS
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap