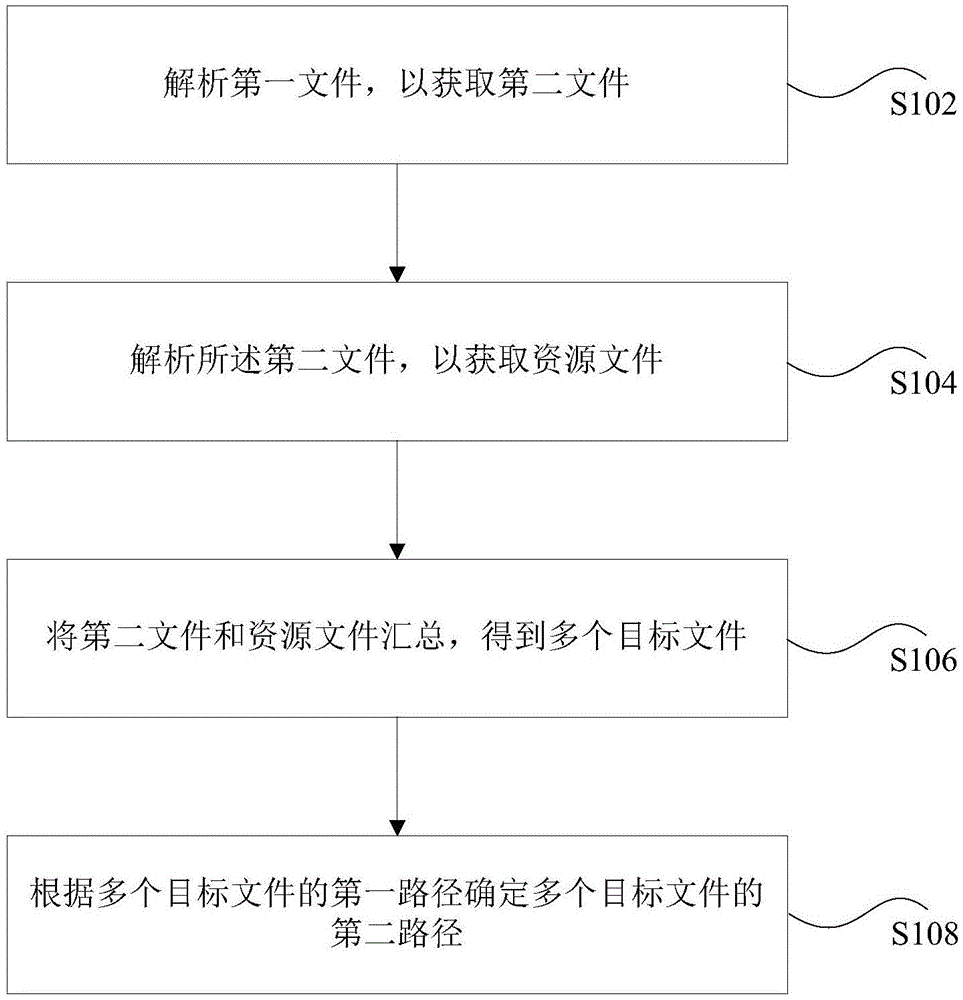
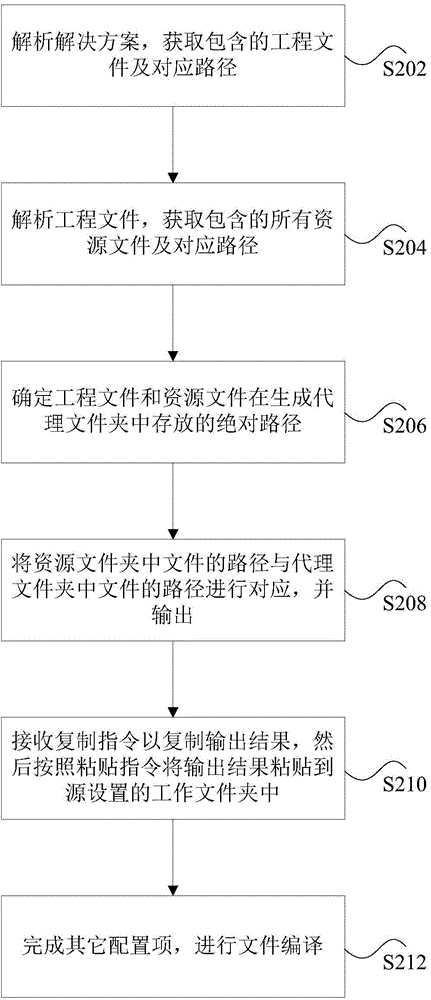
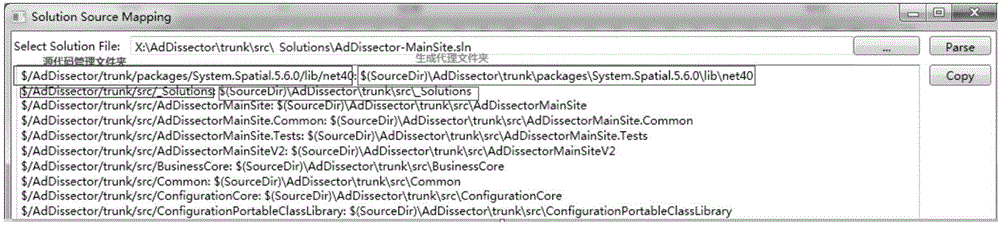
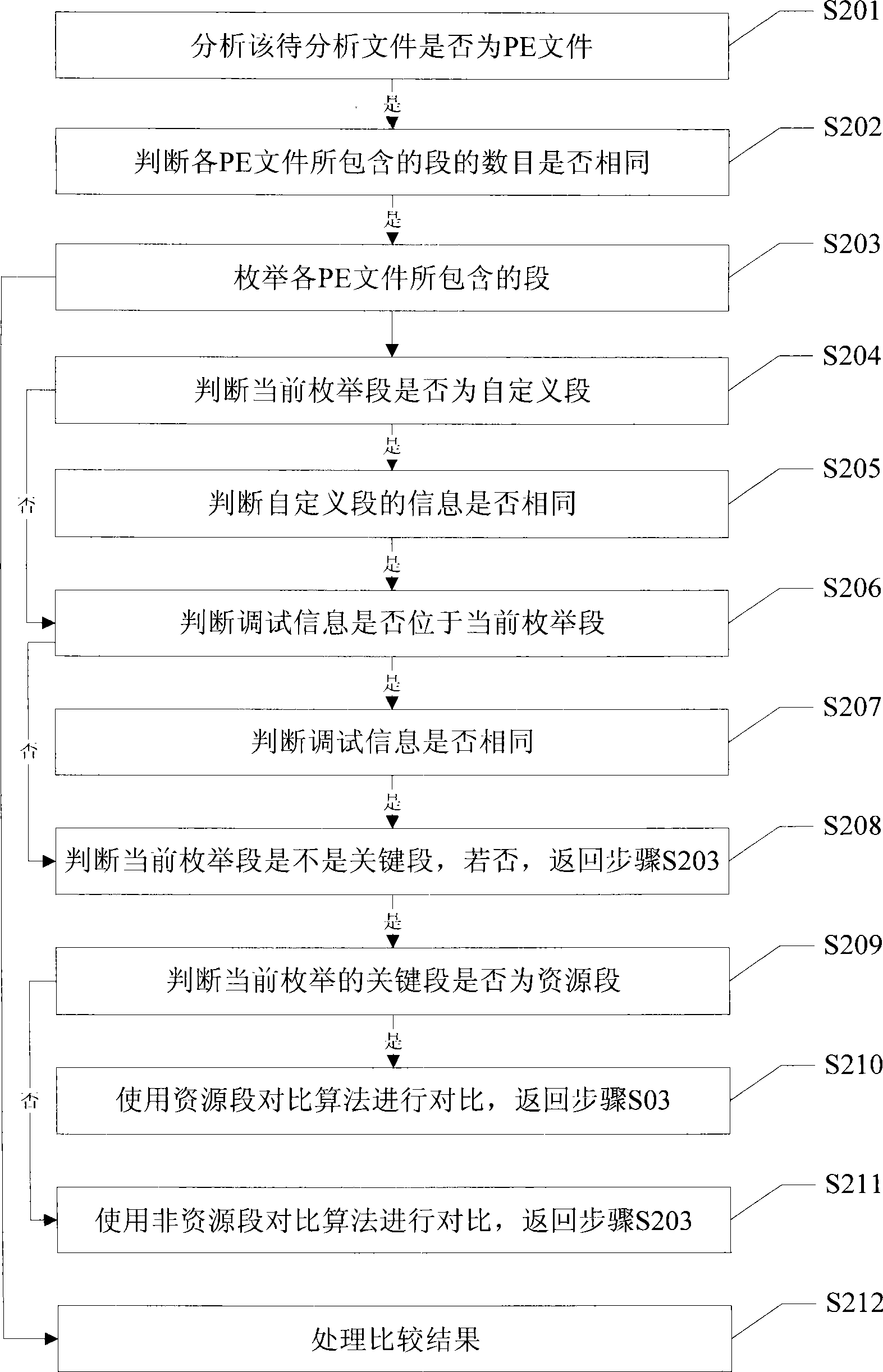Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
50results about "Program control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
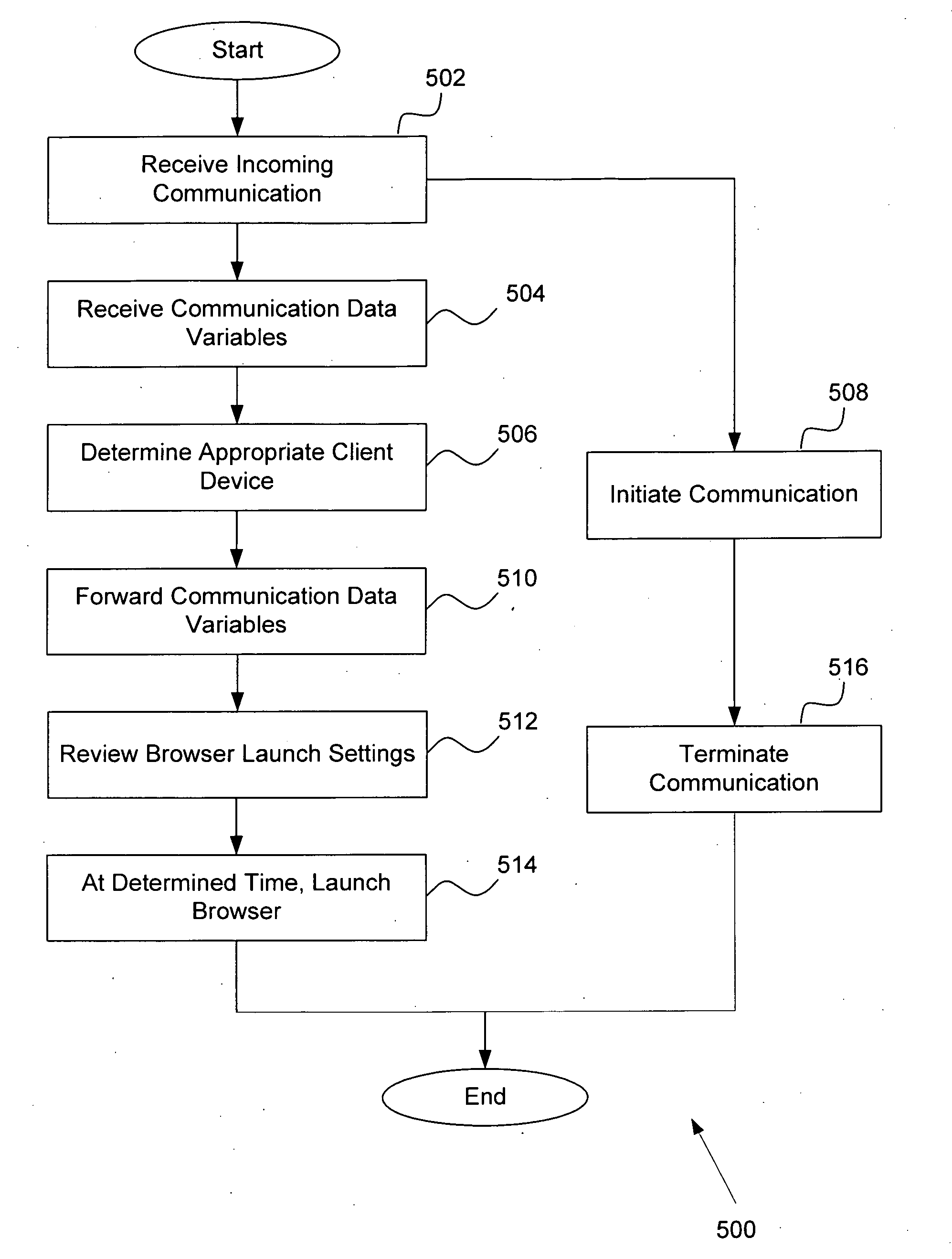
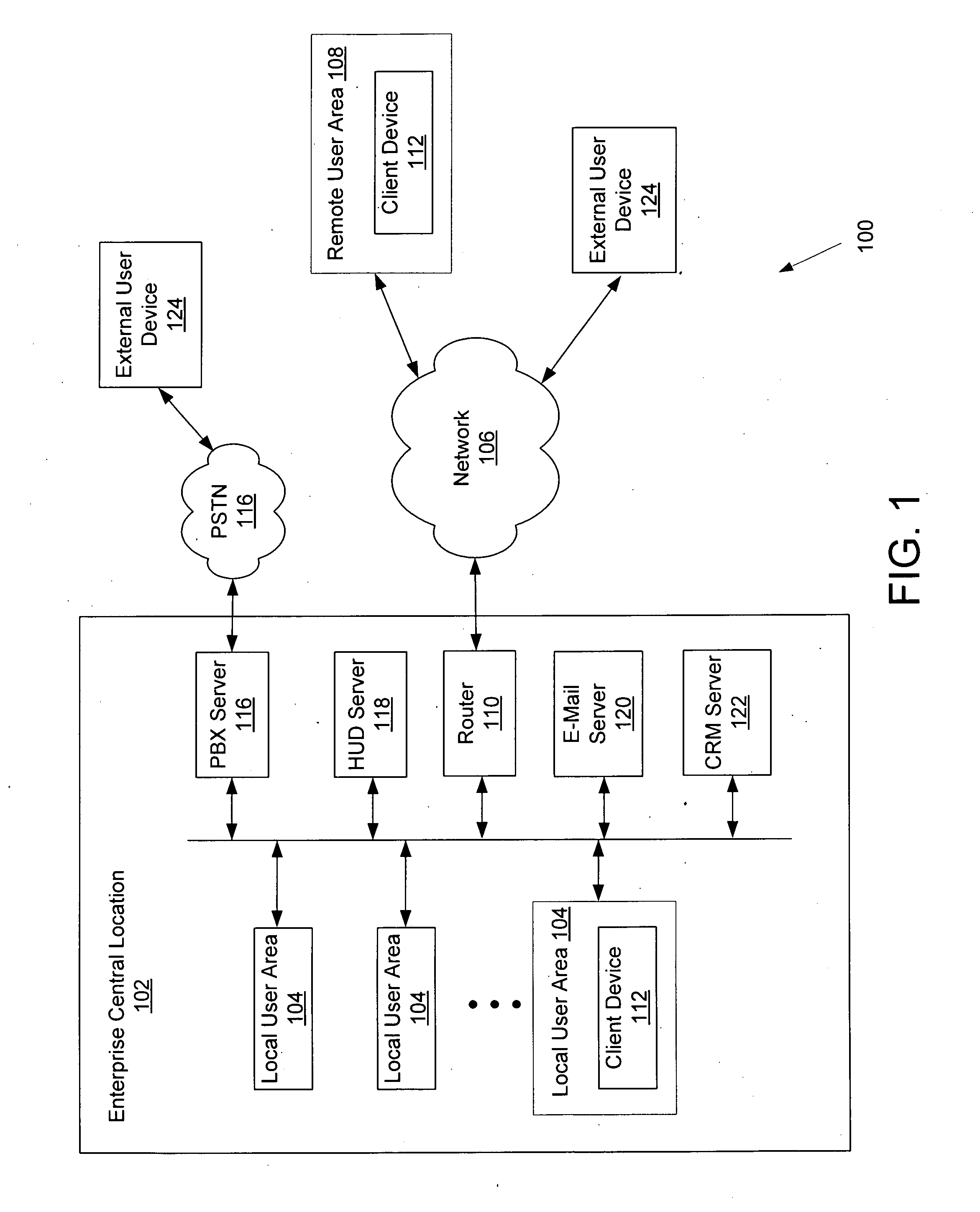
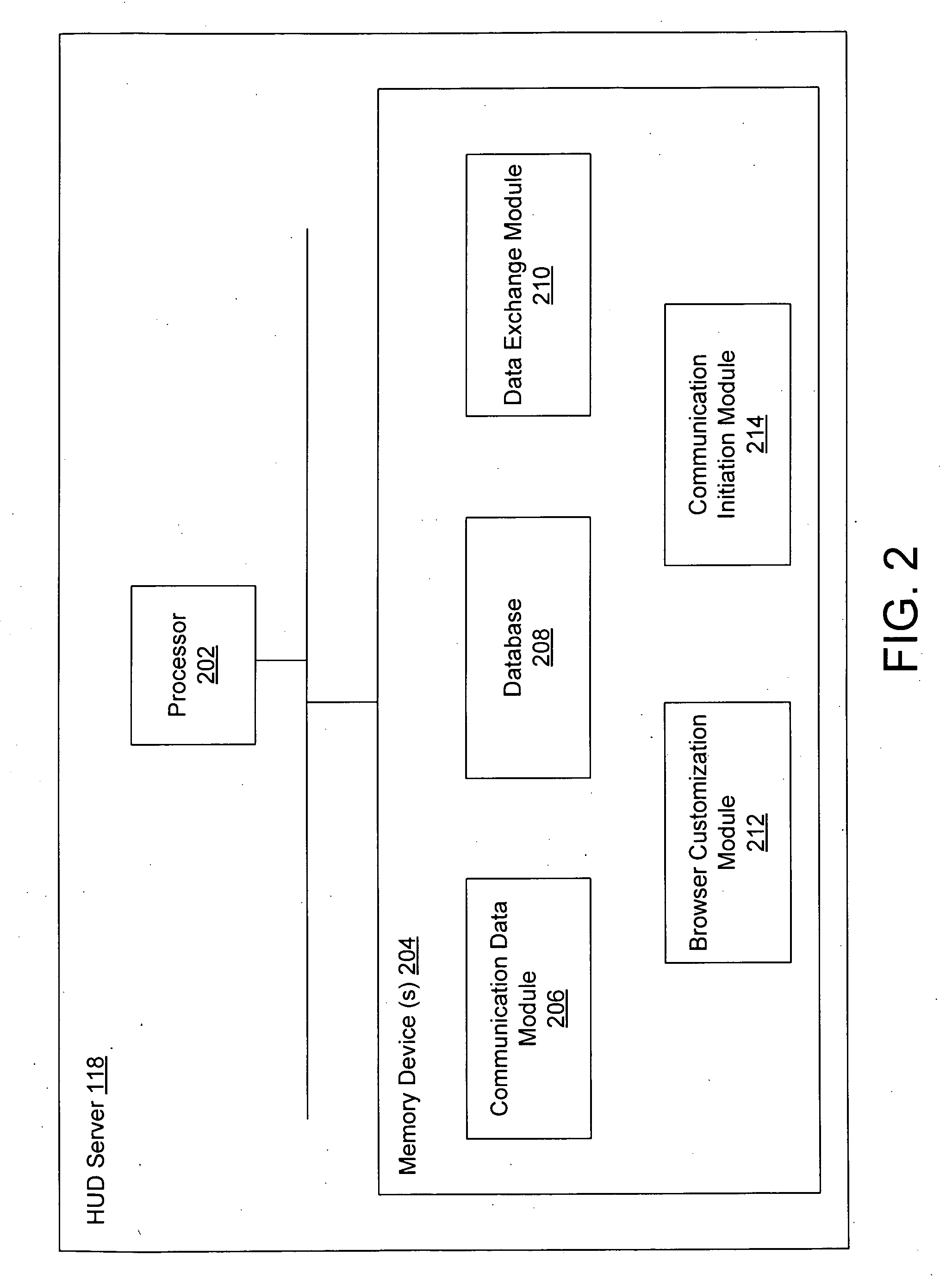
System and method for event driven browser launch
ActiveUS20080222656A1Interconnection arrangementsAutomatic exchangesUniform resource locator
Owner:SANGOMA US INC
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
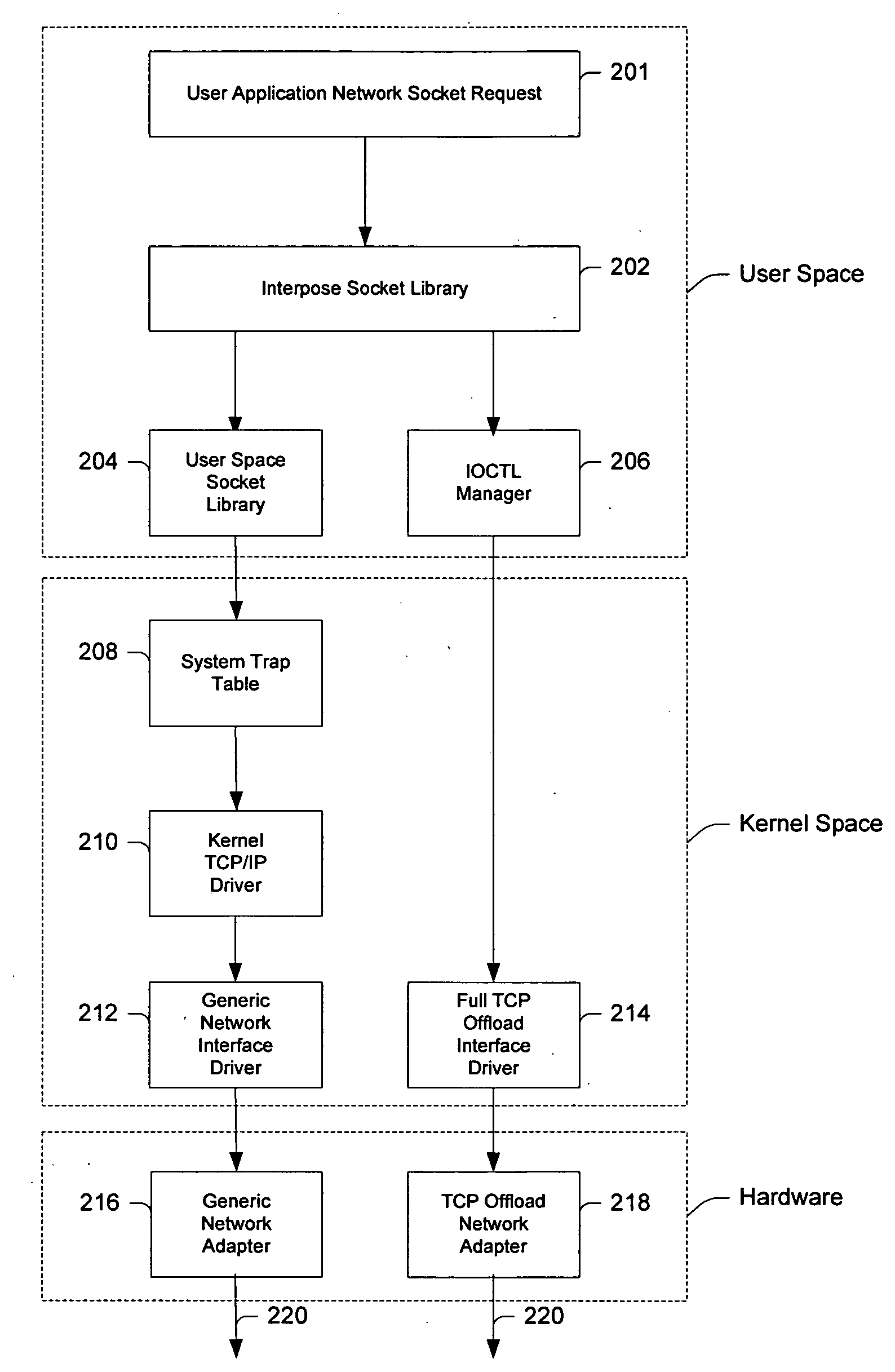
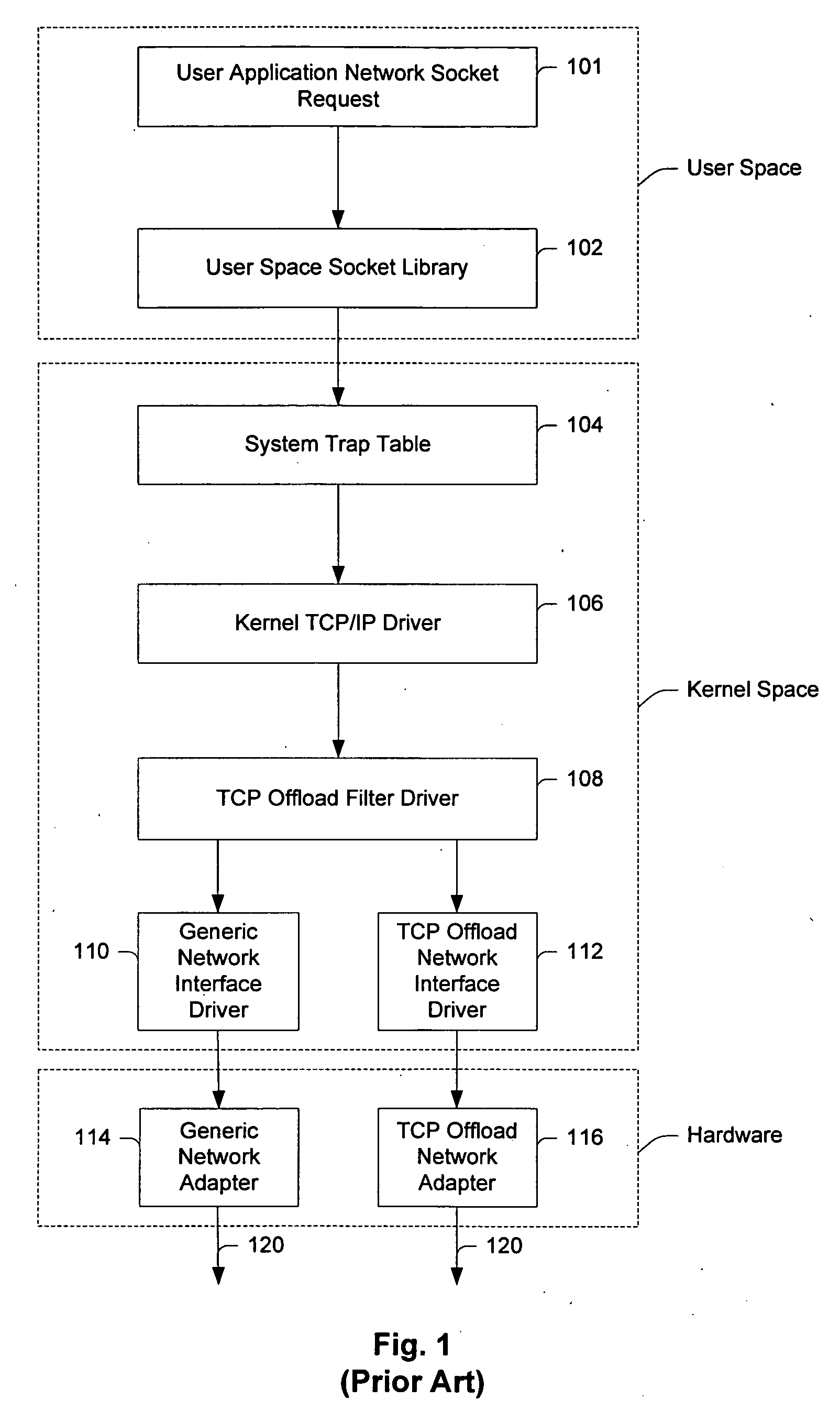
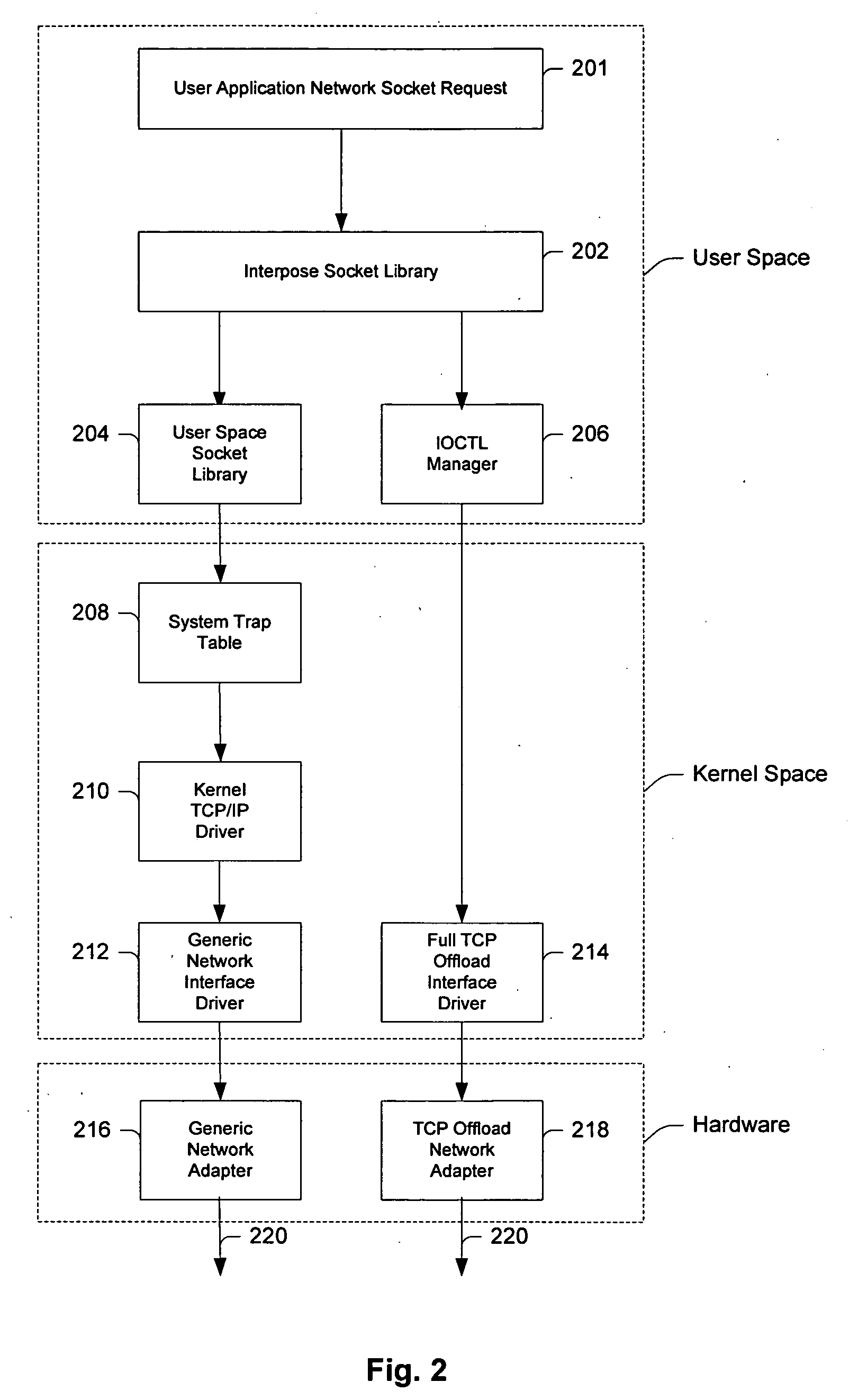
System and method for interfacing TCP offload engines using an interposed socket library
InactiveUS20050021680A1Improve system performanceReduce CPU utilizationMultiple digital computer combinationsProgram controlOperational systemNetwork socket
Owner:CENATA NETWORKS
Management system, management program-recorded recording medium, and management method
InactiveUS20070180117A1Save energyEnergy efficient ICTError detection/correctionData ingestionManagement system
Owner:FUJITSU LTD
Service licensing and maintenance for networks
InactiveUS20060036847A1Random number generatorsUser identity/authority verificationUnique identifierPhysical address
Owner:CISCO TECH INC
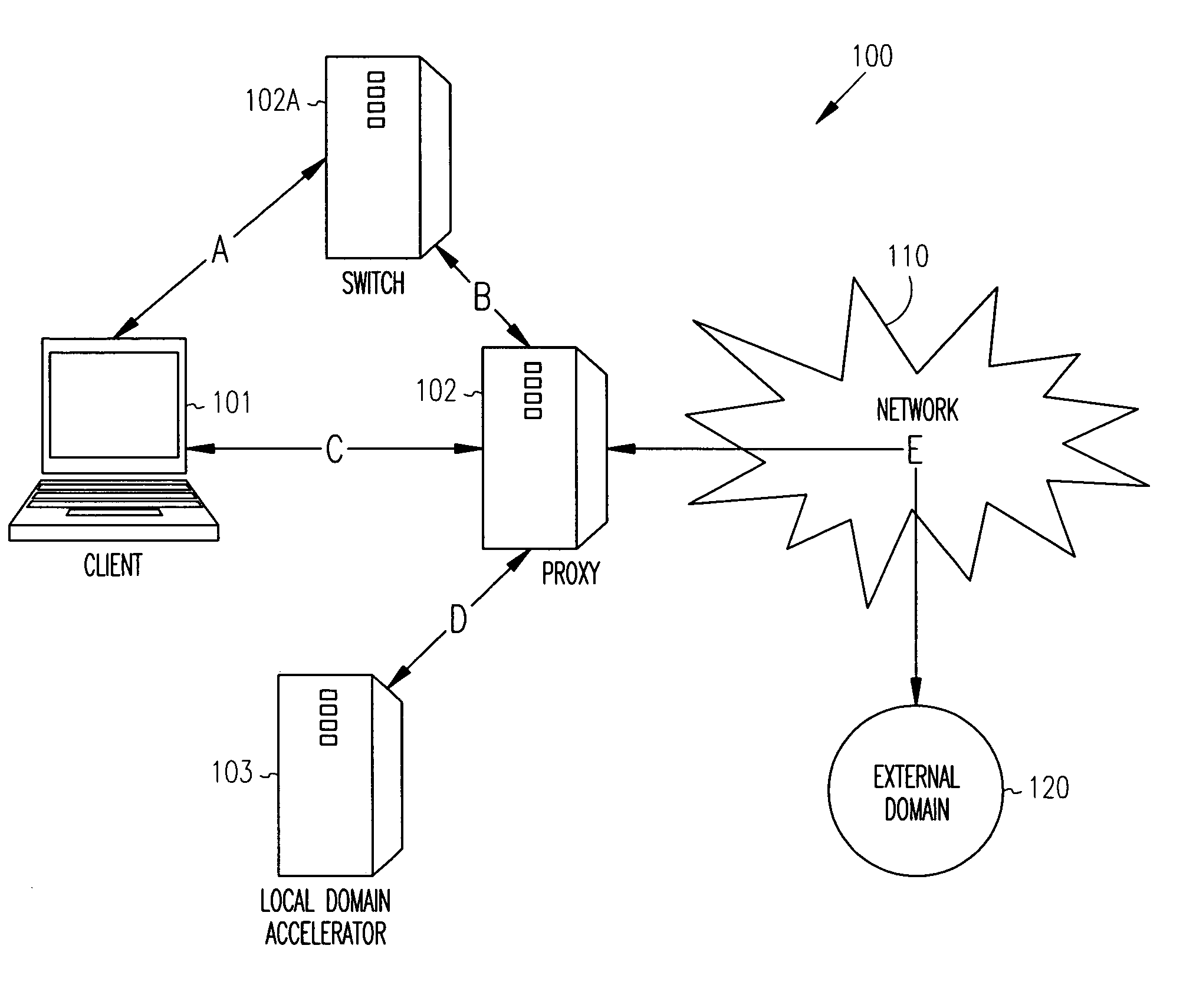
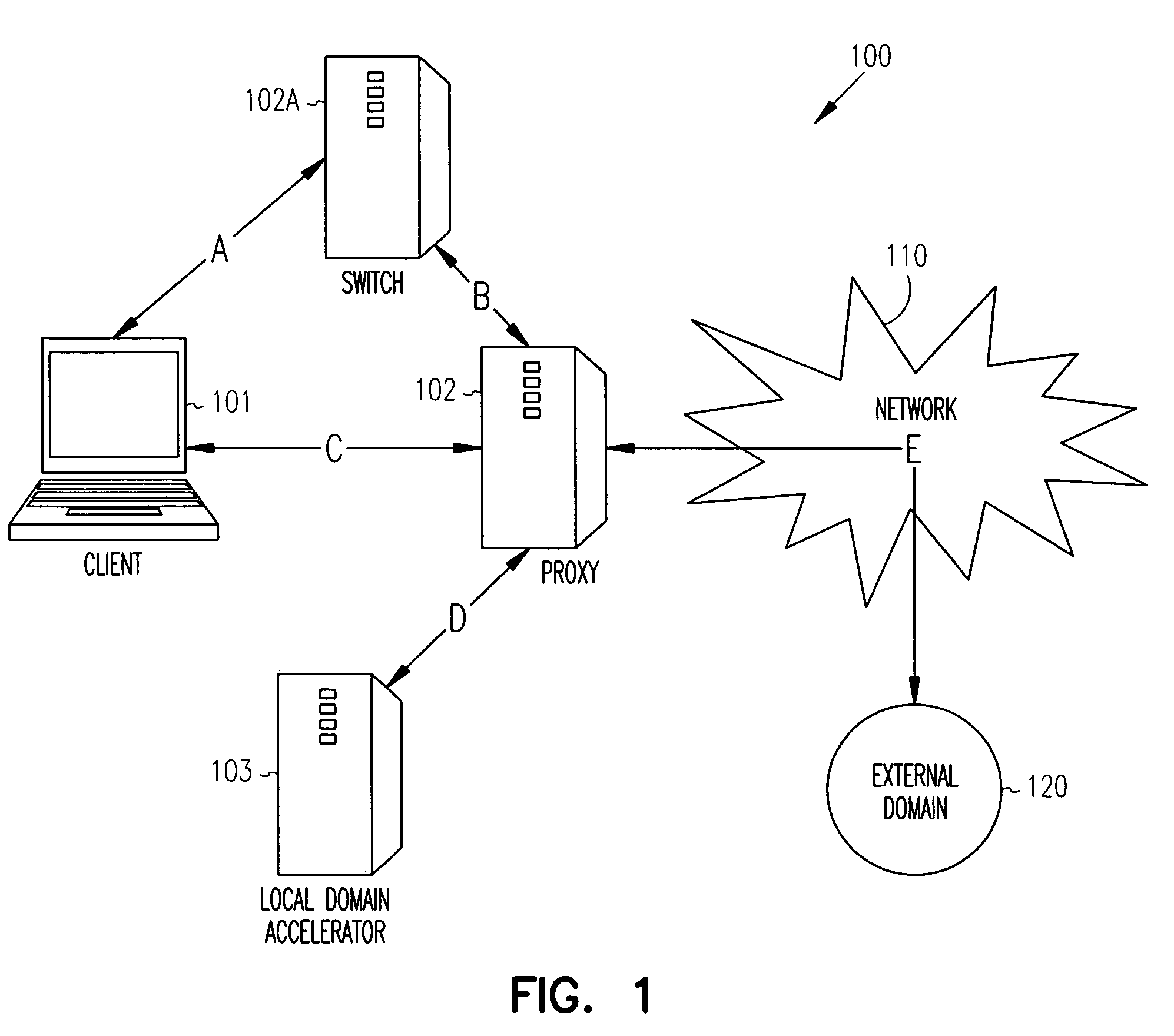
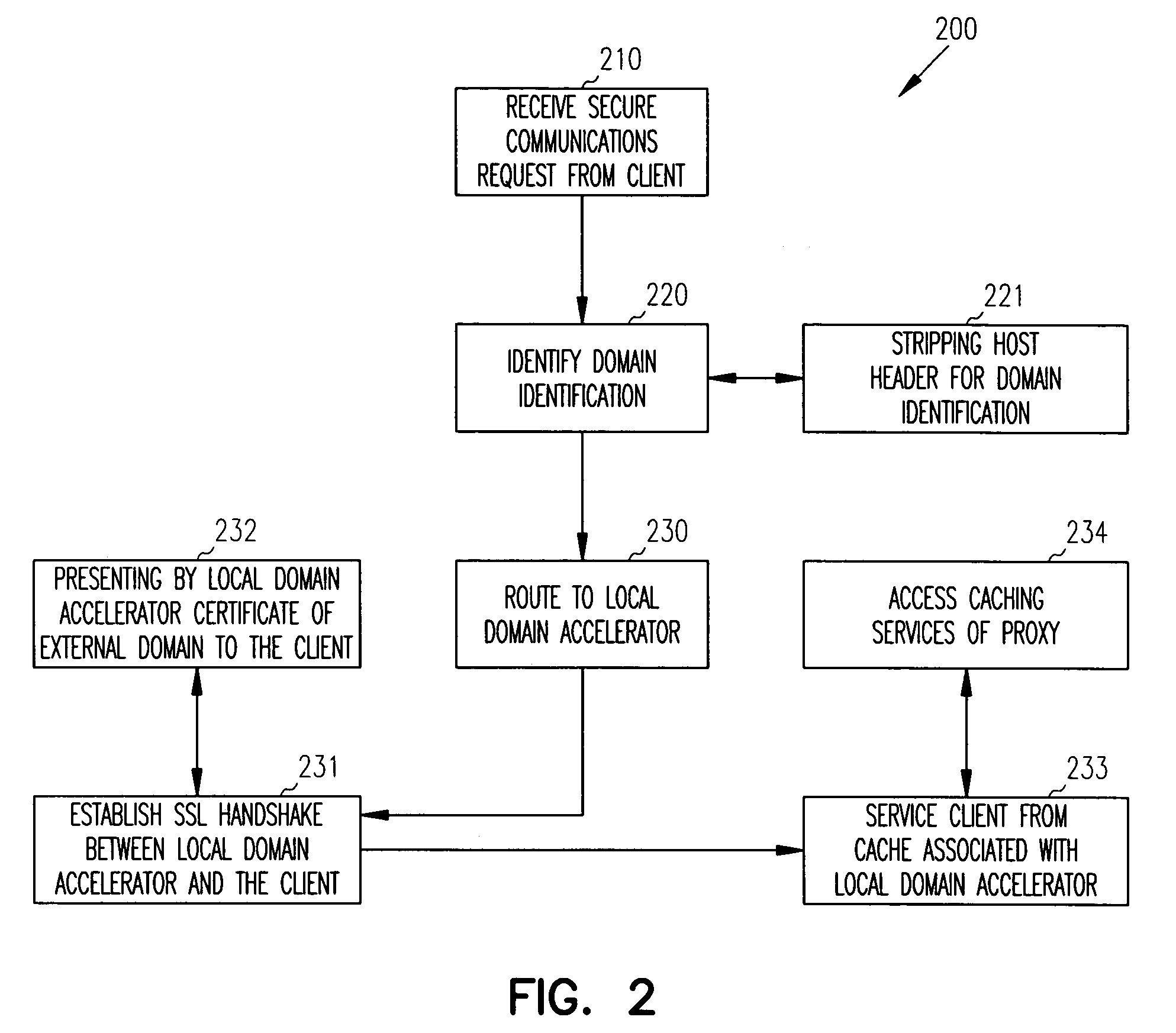
Techniques for securely accelerating external domains locally
InactiveUS7904951B1Multiple digital computer combinationsProgram controlSecure communicationInternet privacy
Owner:RPX CORP
Real-time analytics for large data sets
InactiveUS20130191523A1Fast processing of queryWithout impacting read performanceDigital computer detailsProgram controlData setSerialization
Owner:EVOAPP
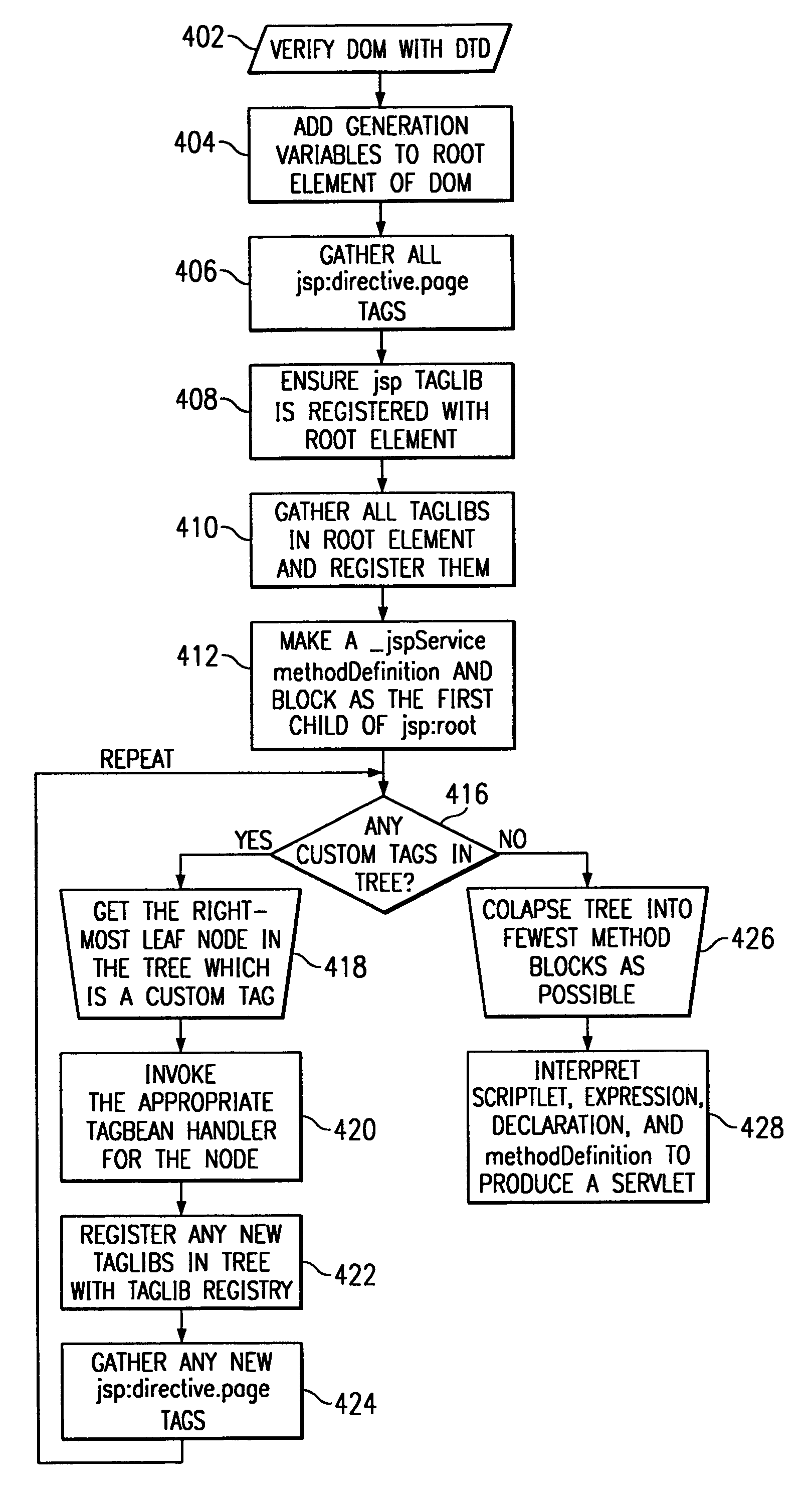
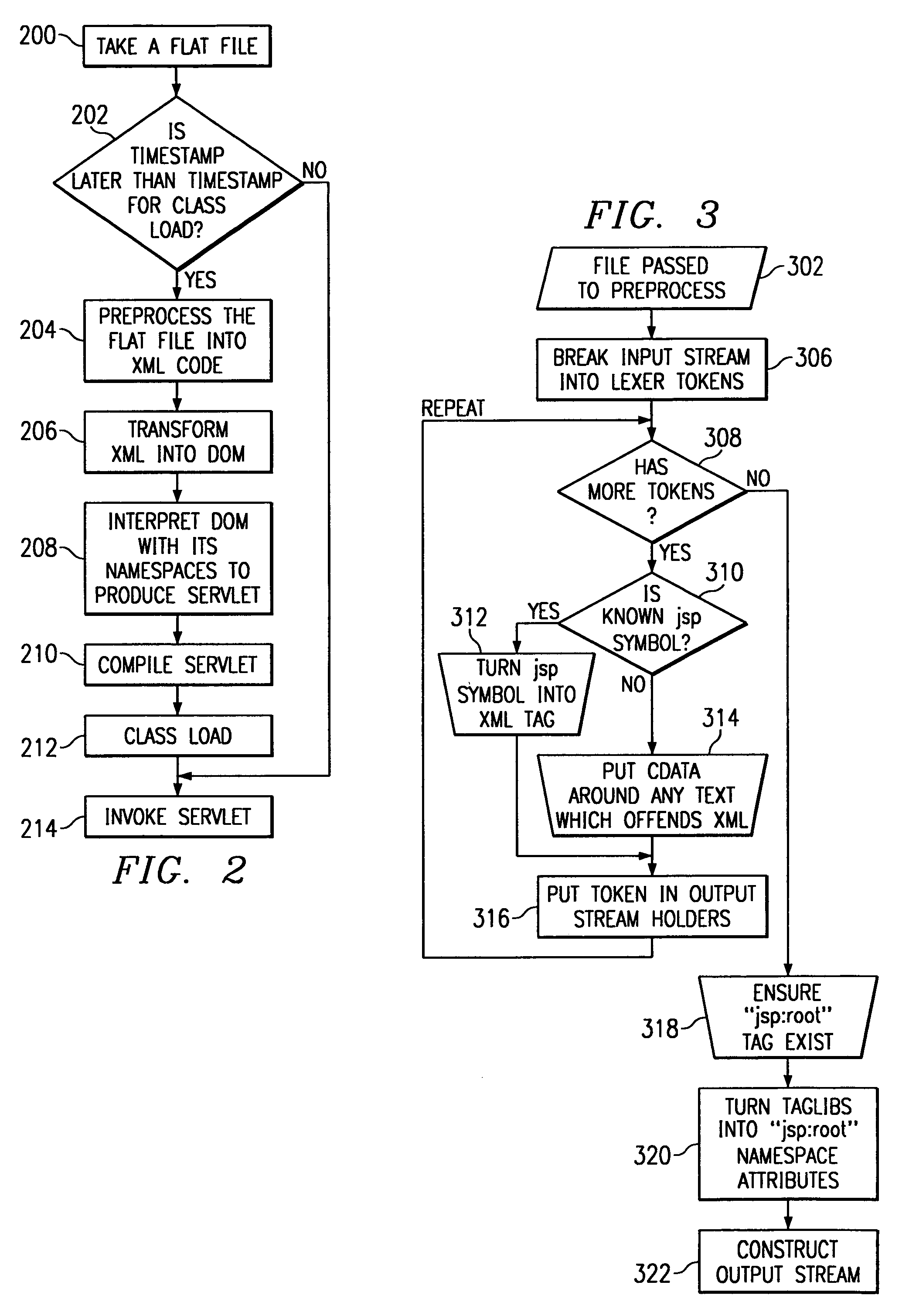
Method for processing a document object model (DOM) tree using a tagbean
InactiveUS6981211B1Easy to replaceDigital computer detailsSemi-structured data mapping/conversionComponent Object ModelTheoretical computer science
Owner:IBM CORP
Method for Weighted Voting in a Public Safety Distributed Ledger
A computer-implemented method and apparatus allow for weighted voting in a public safety distributed ledger. A first node operating in a distributed ledger network receives an incident data record of one or more other nodes to maintain a distributed ledger. The first node reviews the incident data record to determine a vote. The vote indicates whether the incident data record should be entered into the distributed ledger. The vote is sent to a second node operating in the distributed ledger network. Votes are received from the one or more other nodes, and weights are determined for each node operating in the distributed ledger network node. A weighted vote result is calculated utilizing the votes and the weights. The distributed ledger is updated with the incident data record when the weighted vote result is greater than or equal to a predetermined threshold.
Owner:MOTOROLA SOLUTIONS INC
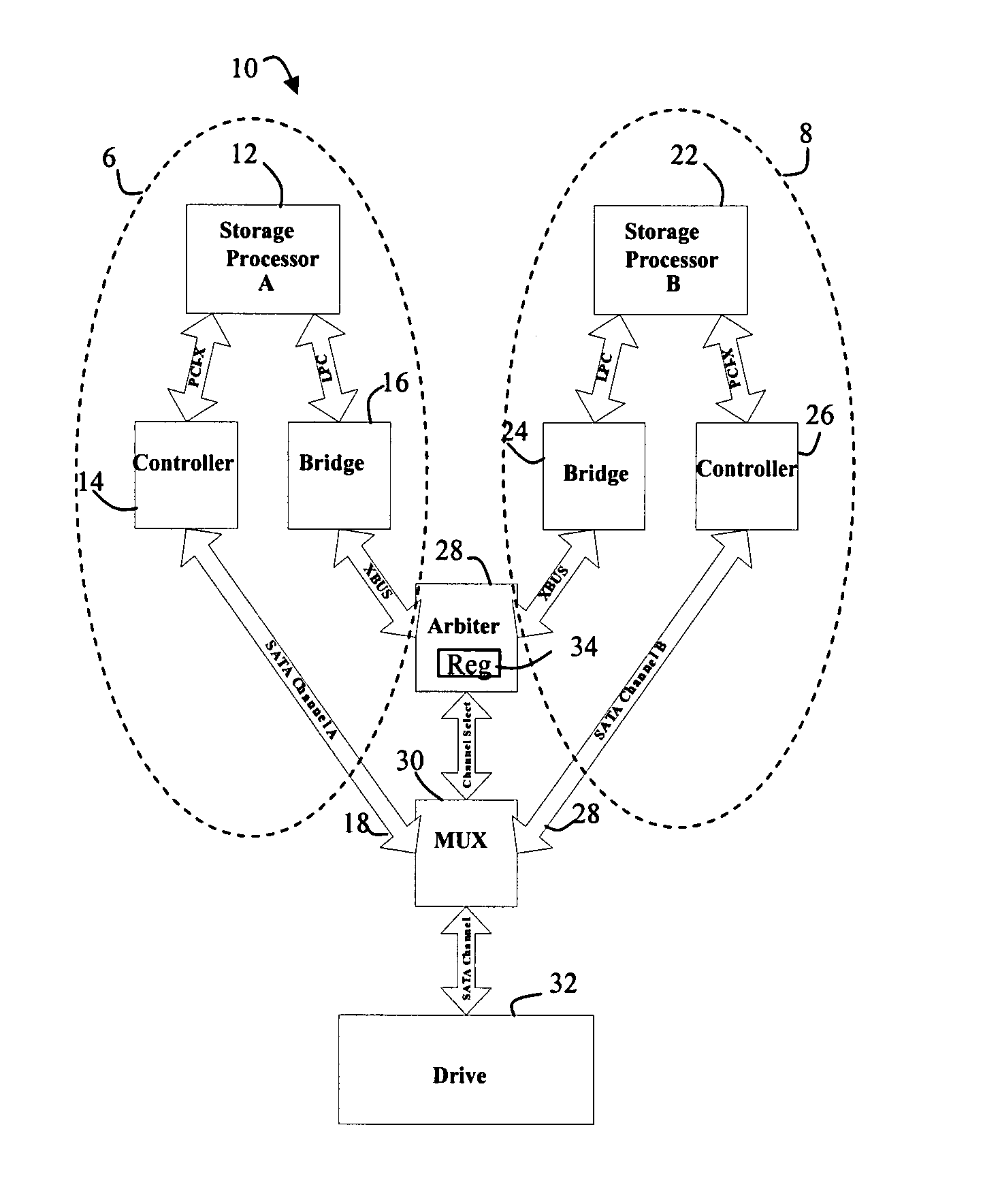
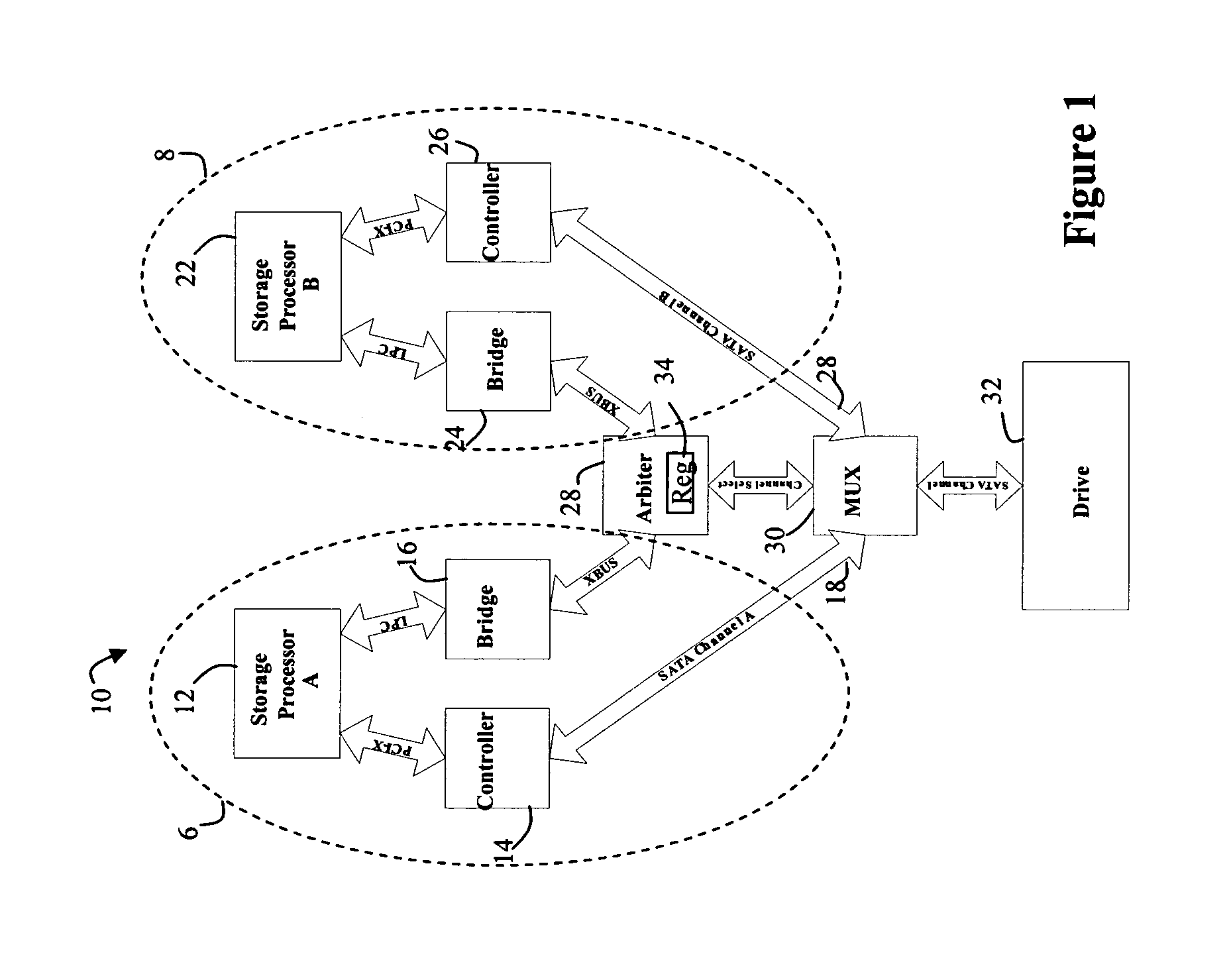
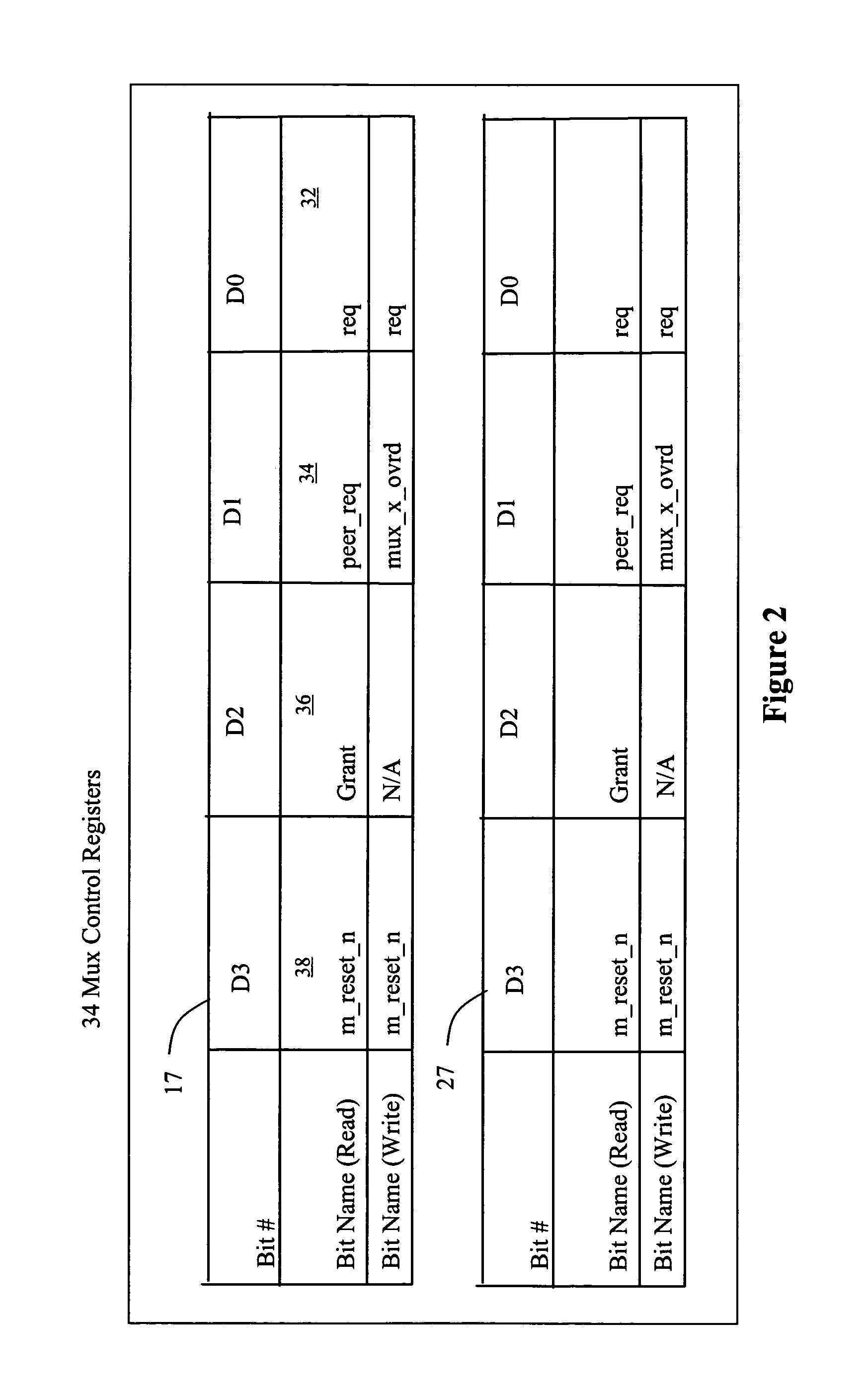
Method and apparatus for resource arbitration
Owner:EMC IP HLDG CO LLC
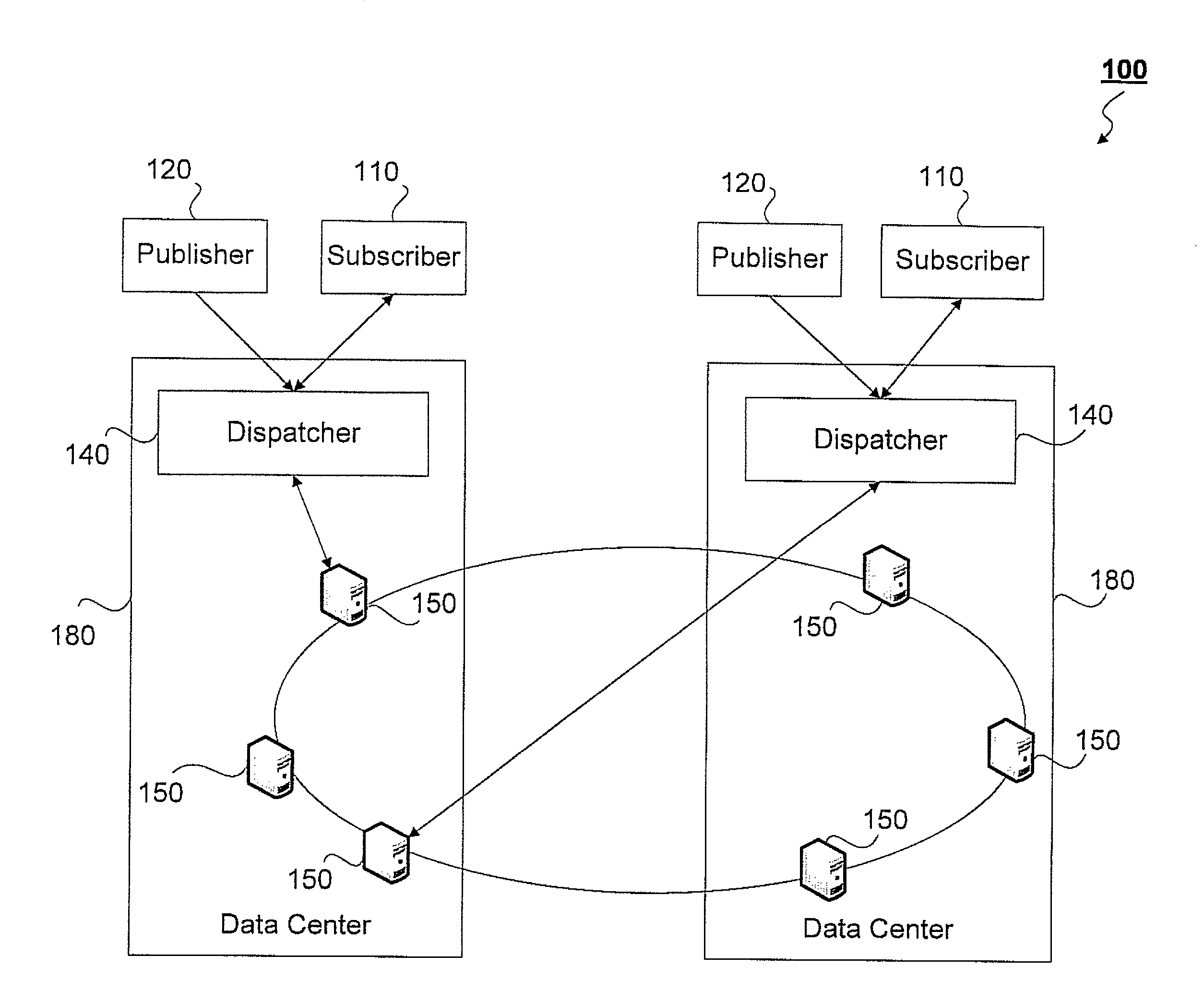
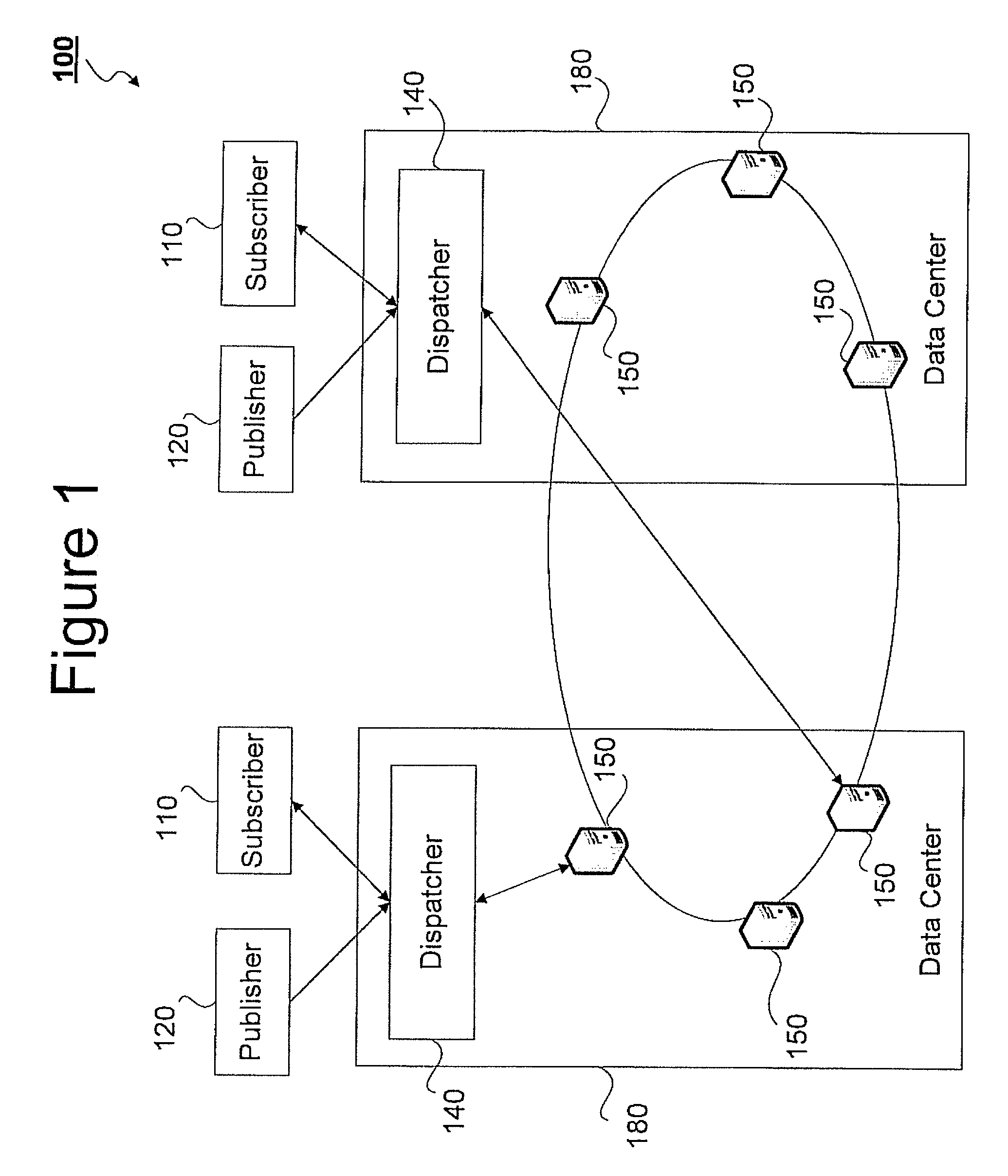
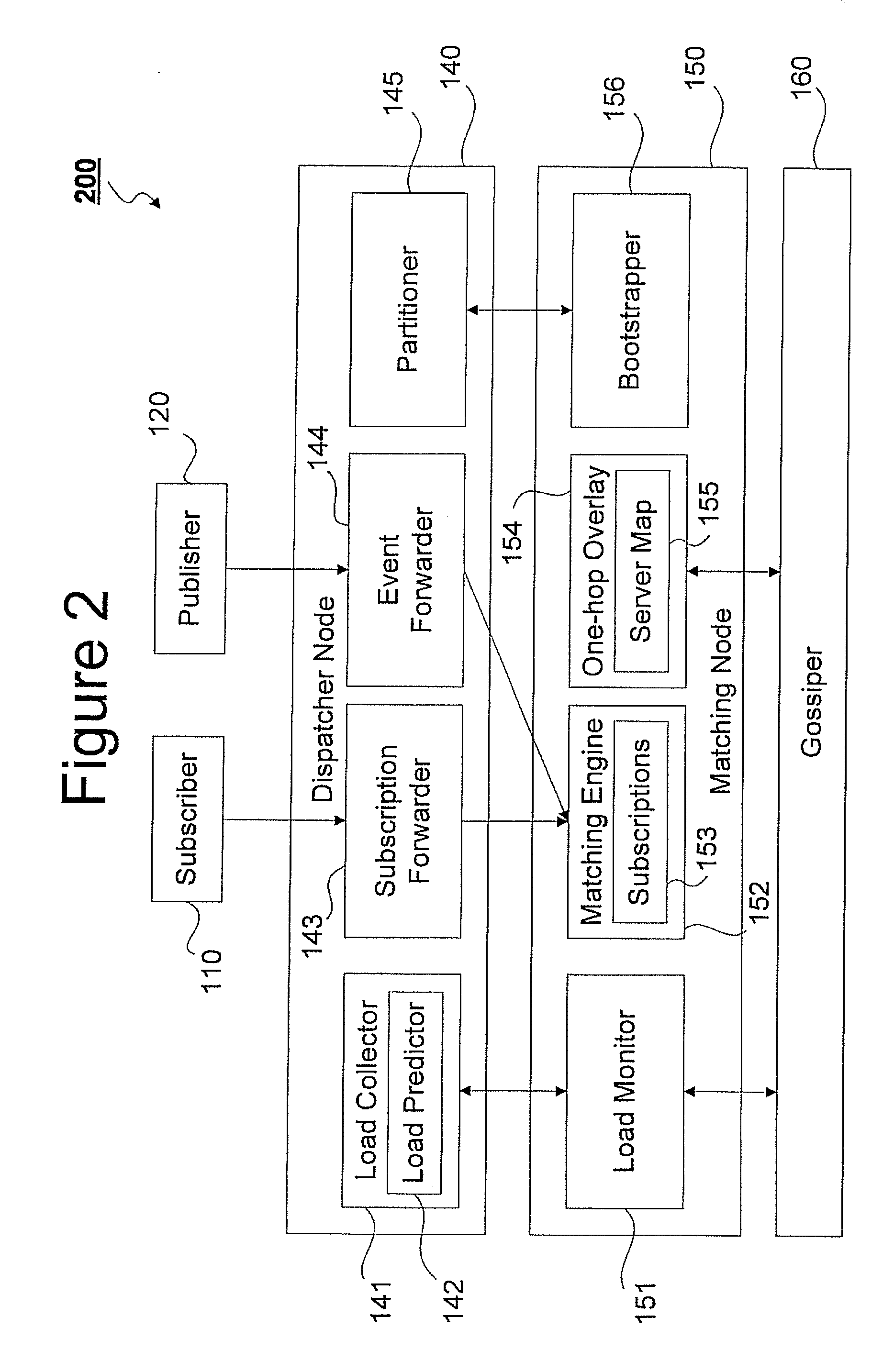
Elastic and scalable publish/subscribe service
Owner:IBM CORP
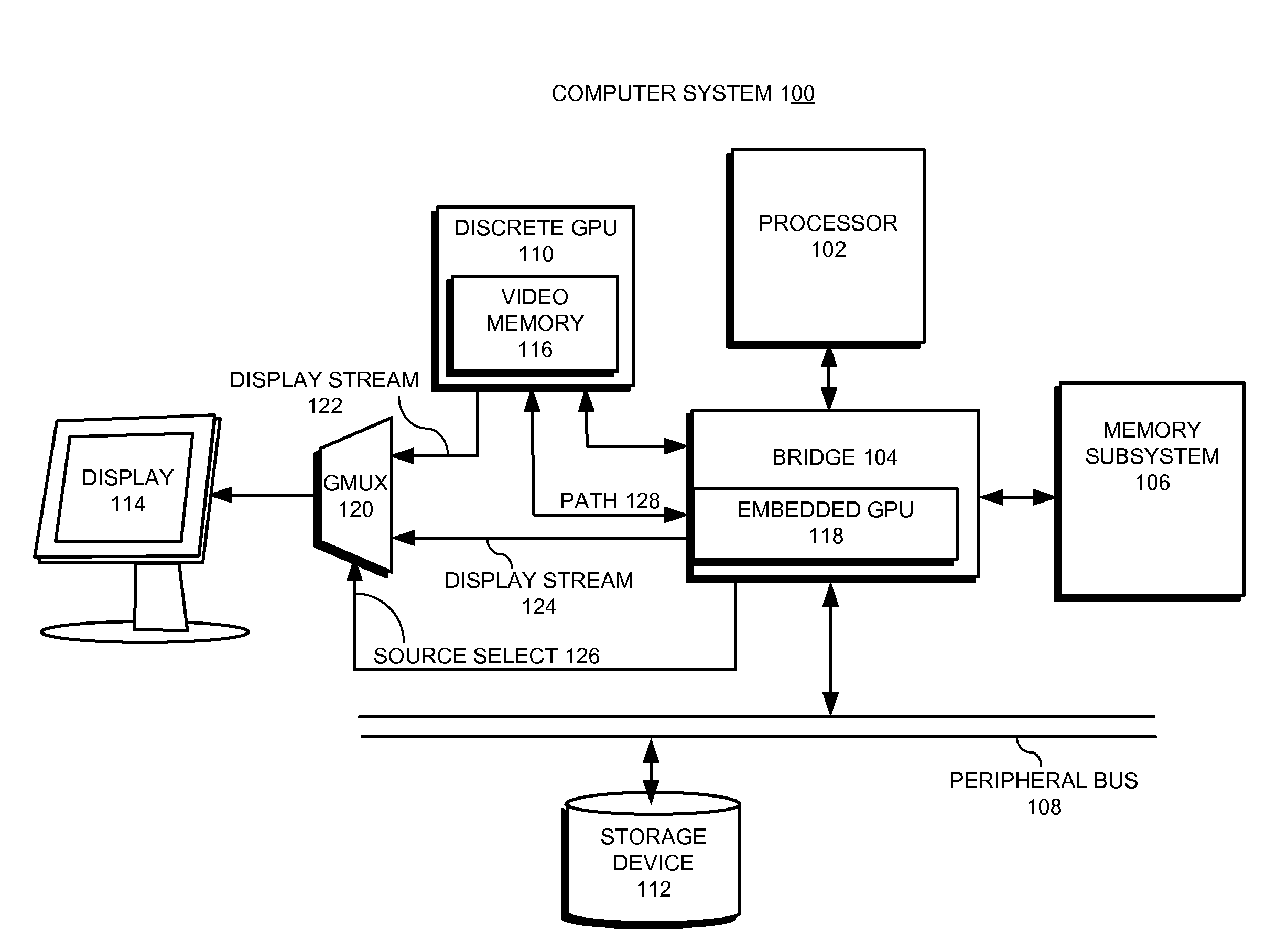
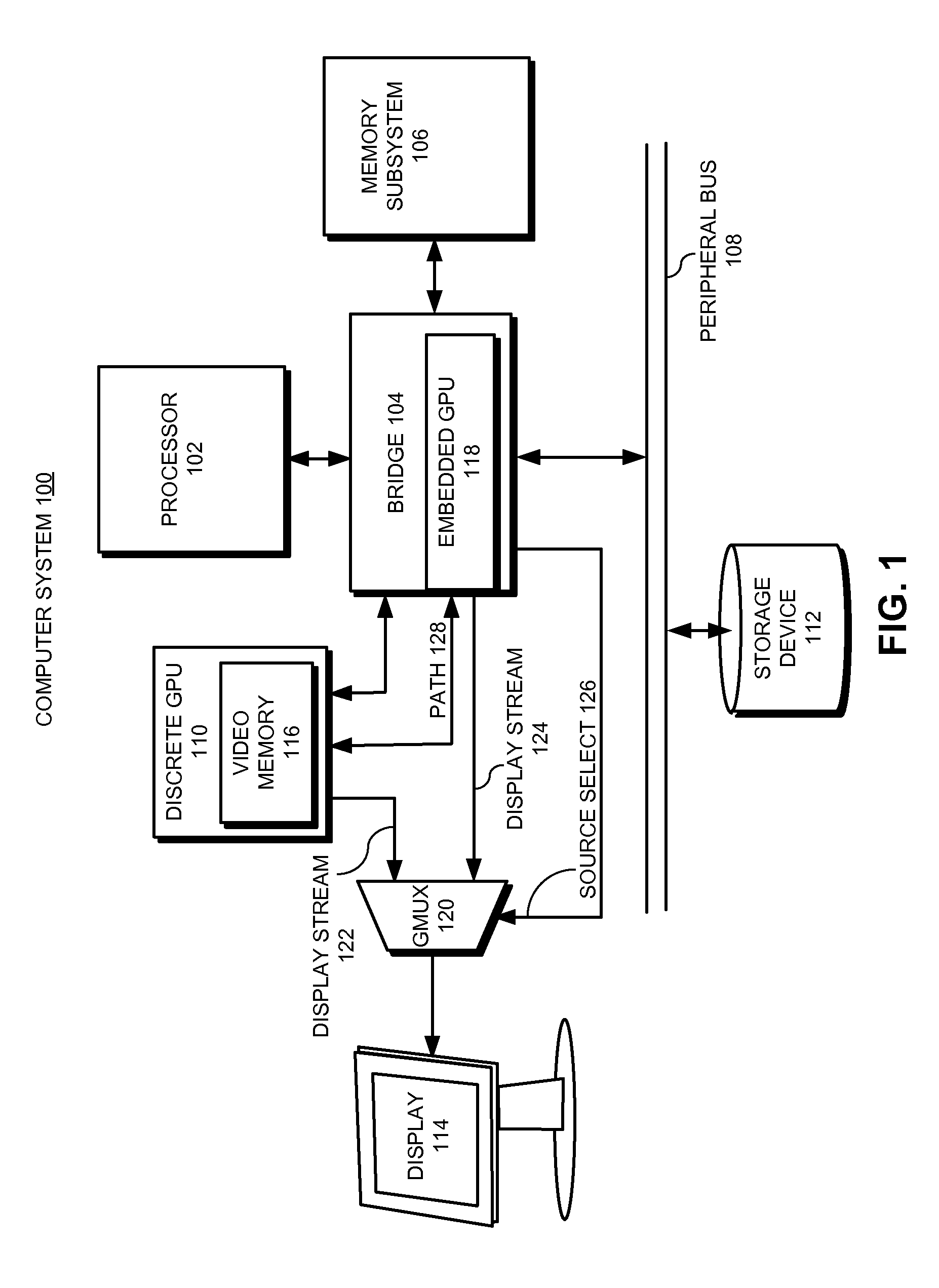
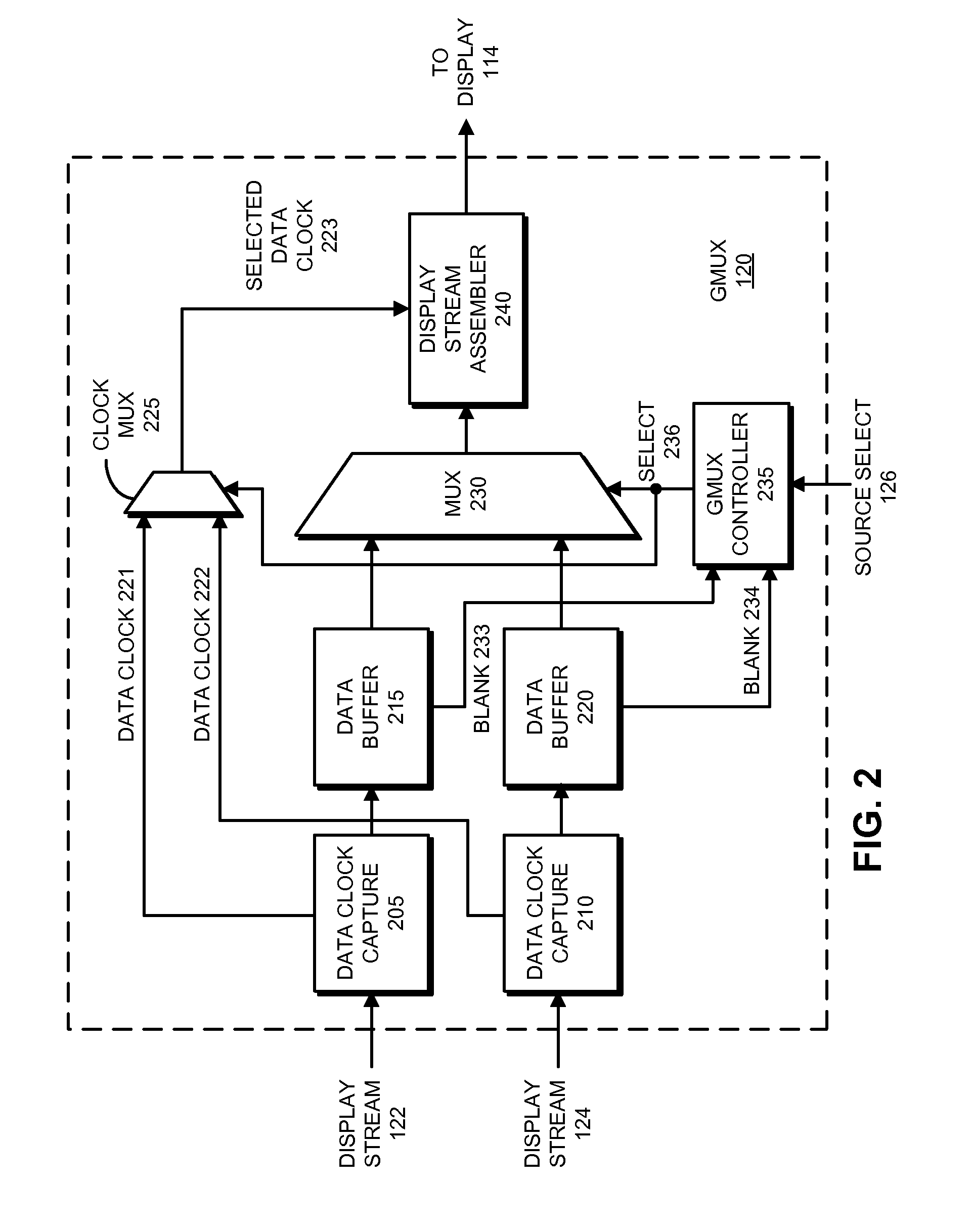
Facilitating atomic switching of graphics-processing units
InactiveUS20120092351A1Configure on switchCathode-ray tube indicatorsProgram controlGPU switchingComputational science
Owner:APPLE INC
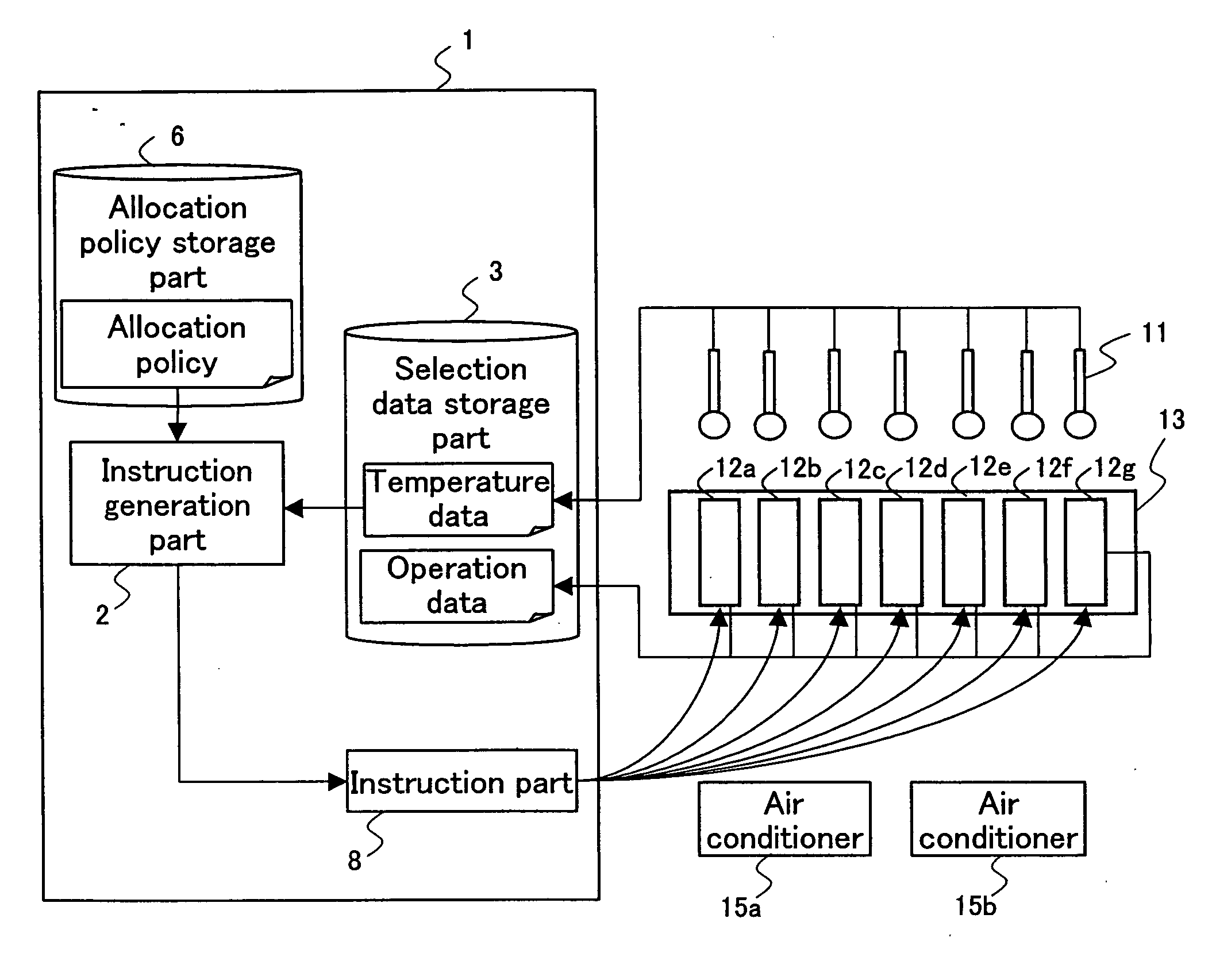
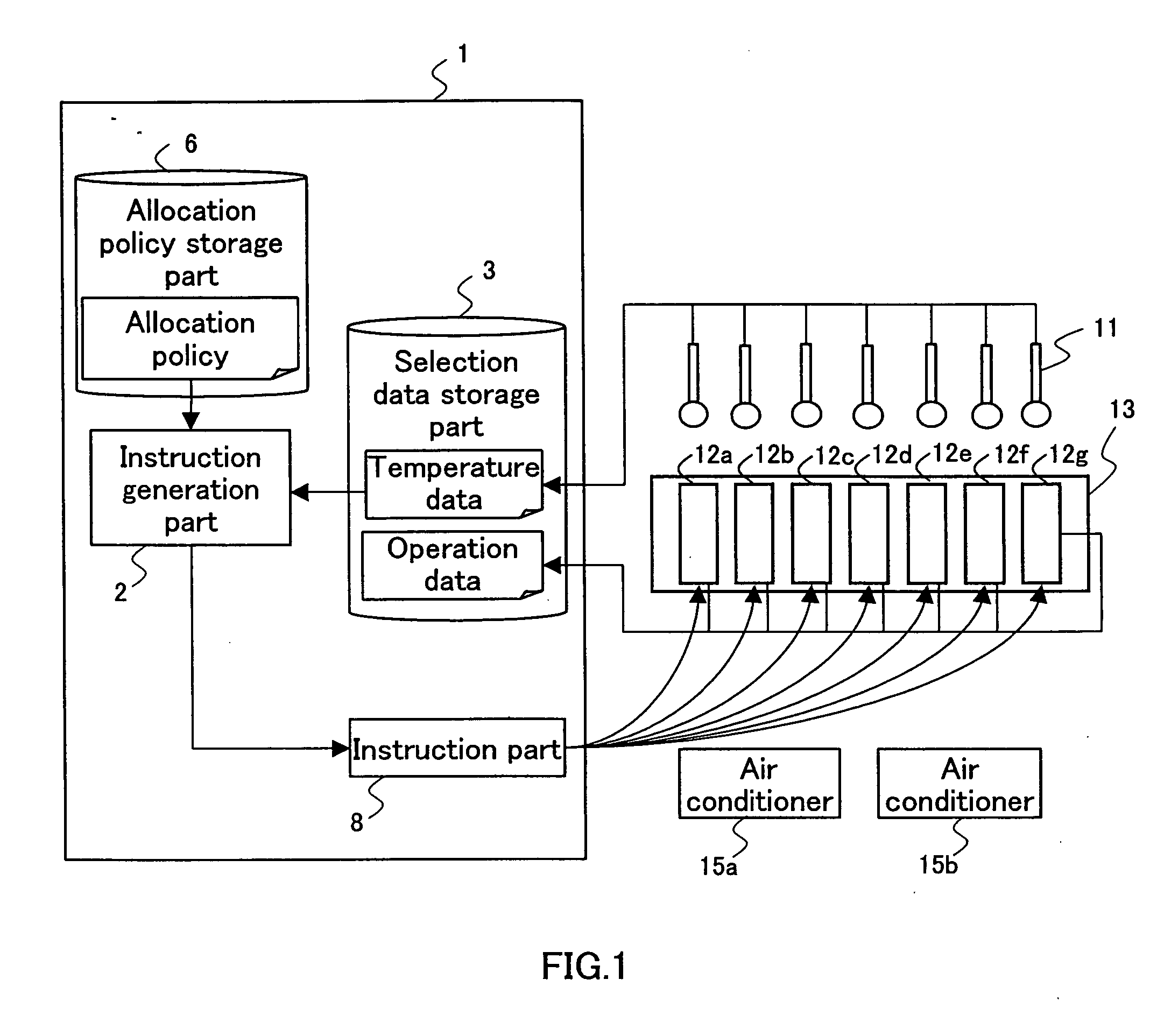
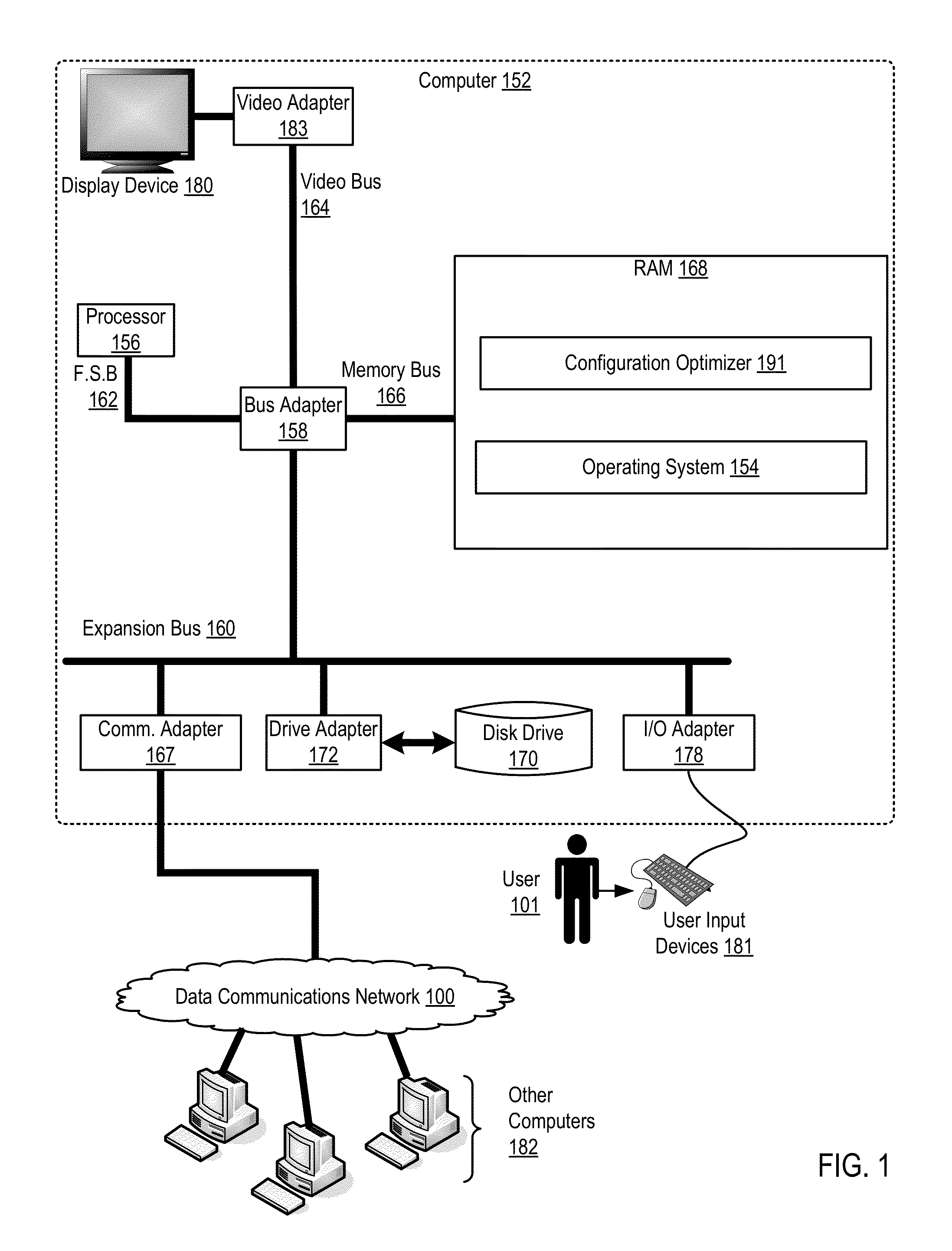
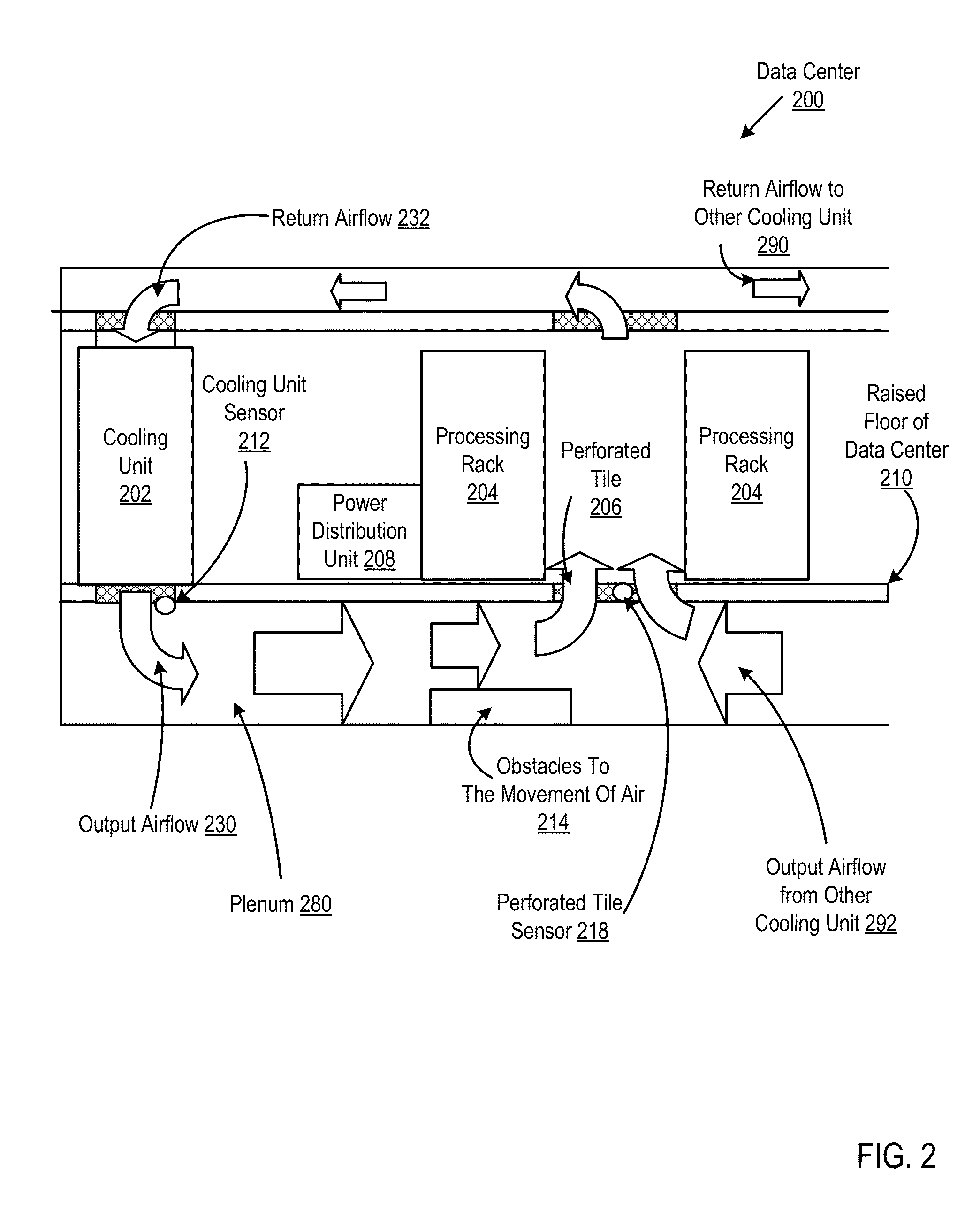
Provisioning aggregate computational workloads and air conditioning unit configurations to optimize utility of air conditioning units and processing resources within a data center
InactiveUS20130103218A1Improve overall utilizationConsume least amount of energyMechanical power/torque controlProgramme controlData centerParallel computing
Owner:IBM CORP
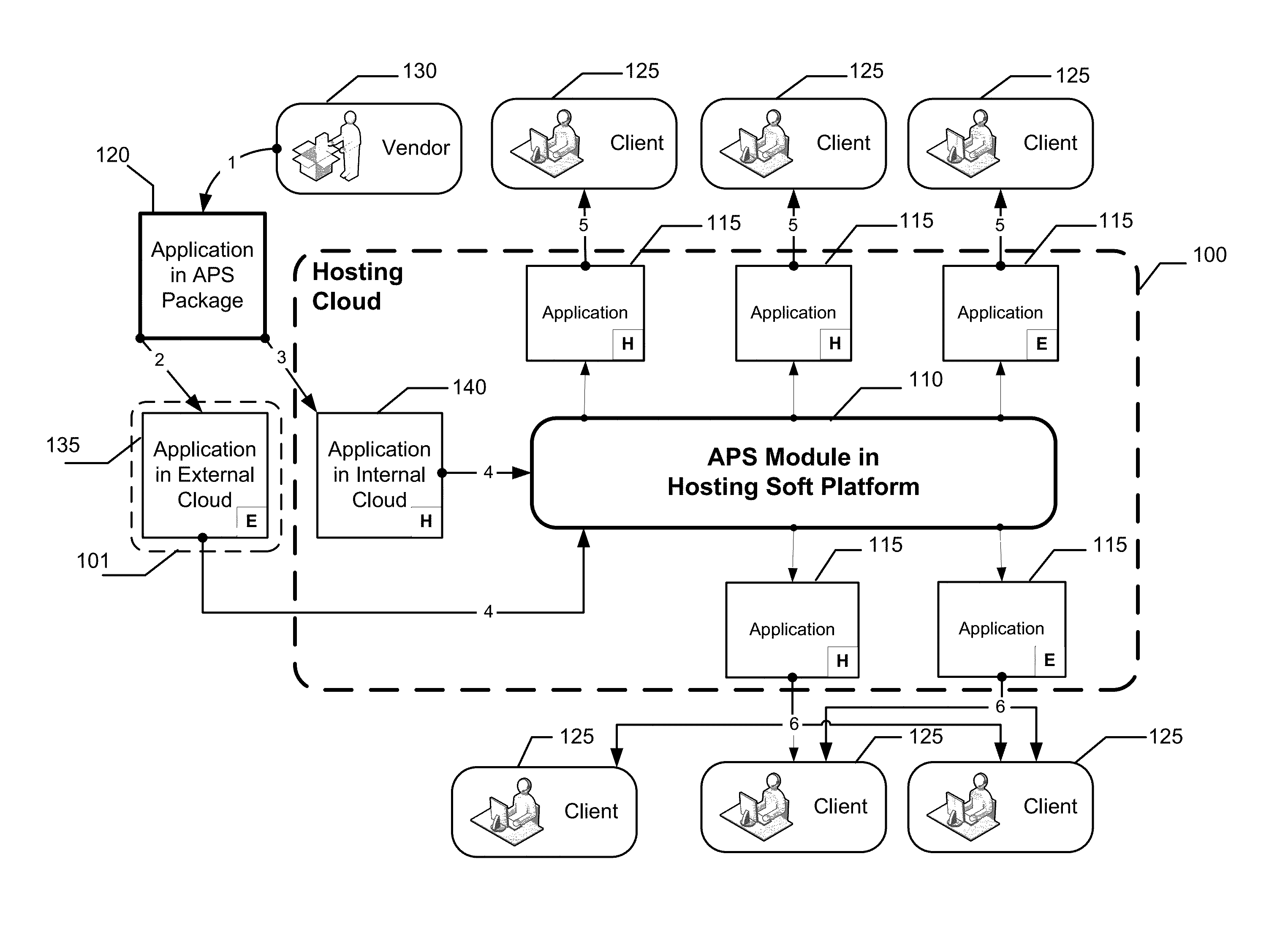
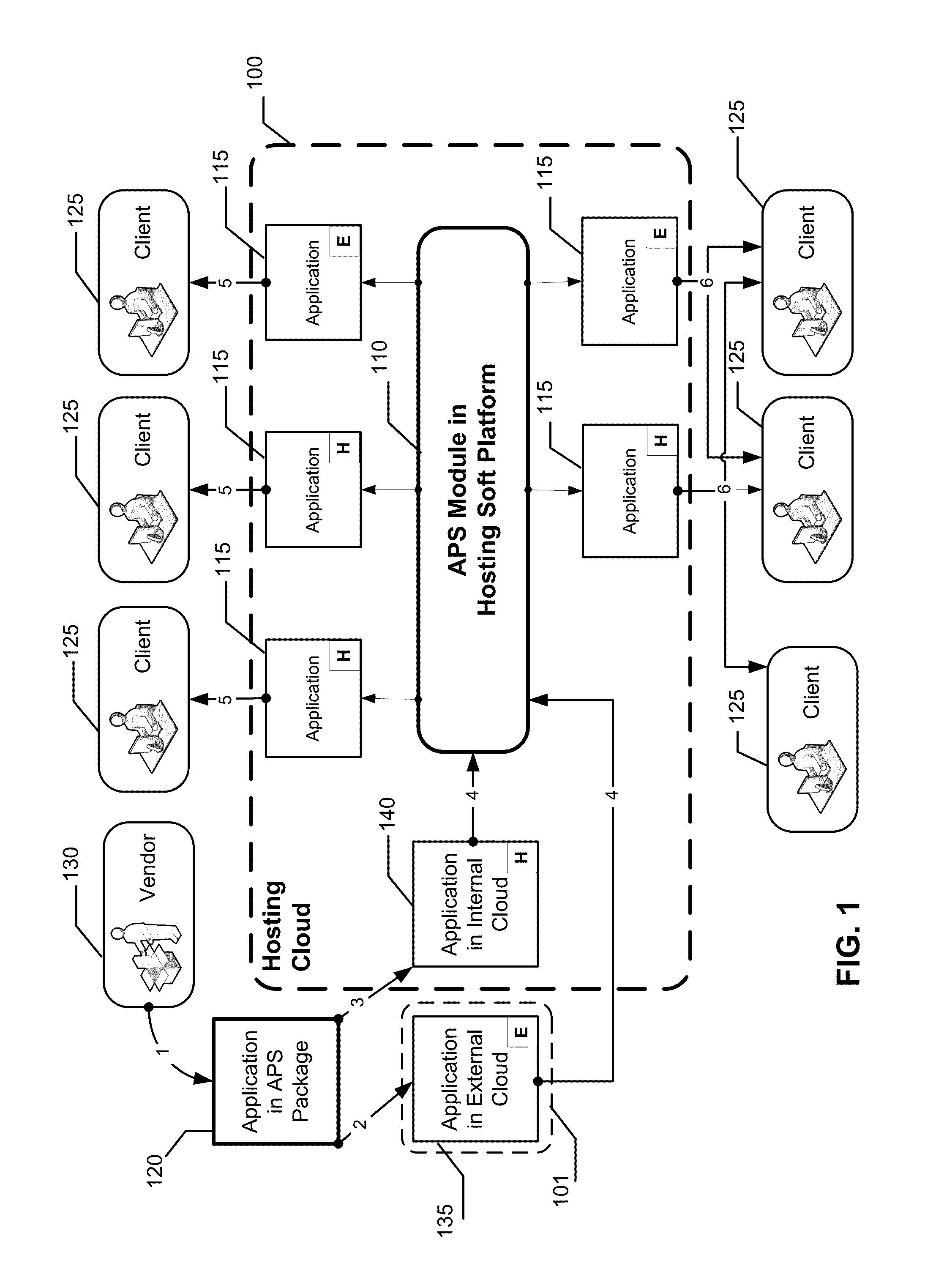
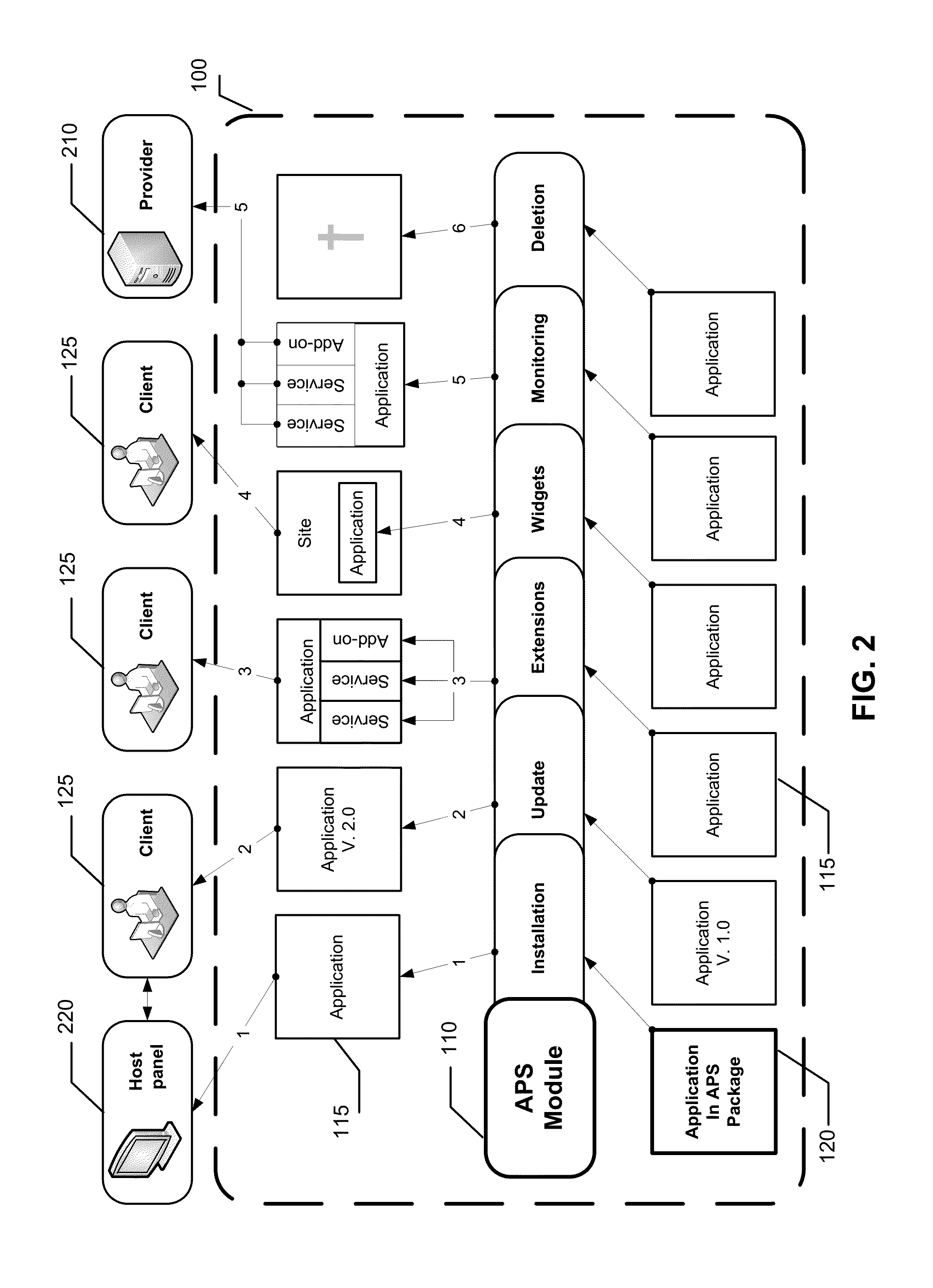
Method and standard for integrating applications into a cloud
ActiveUS9455876B1Efficient integrationDigital computer detailsProgram controlClient-sideProgram code
Owner:CLOUDBLUE LLC
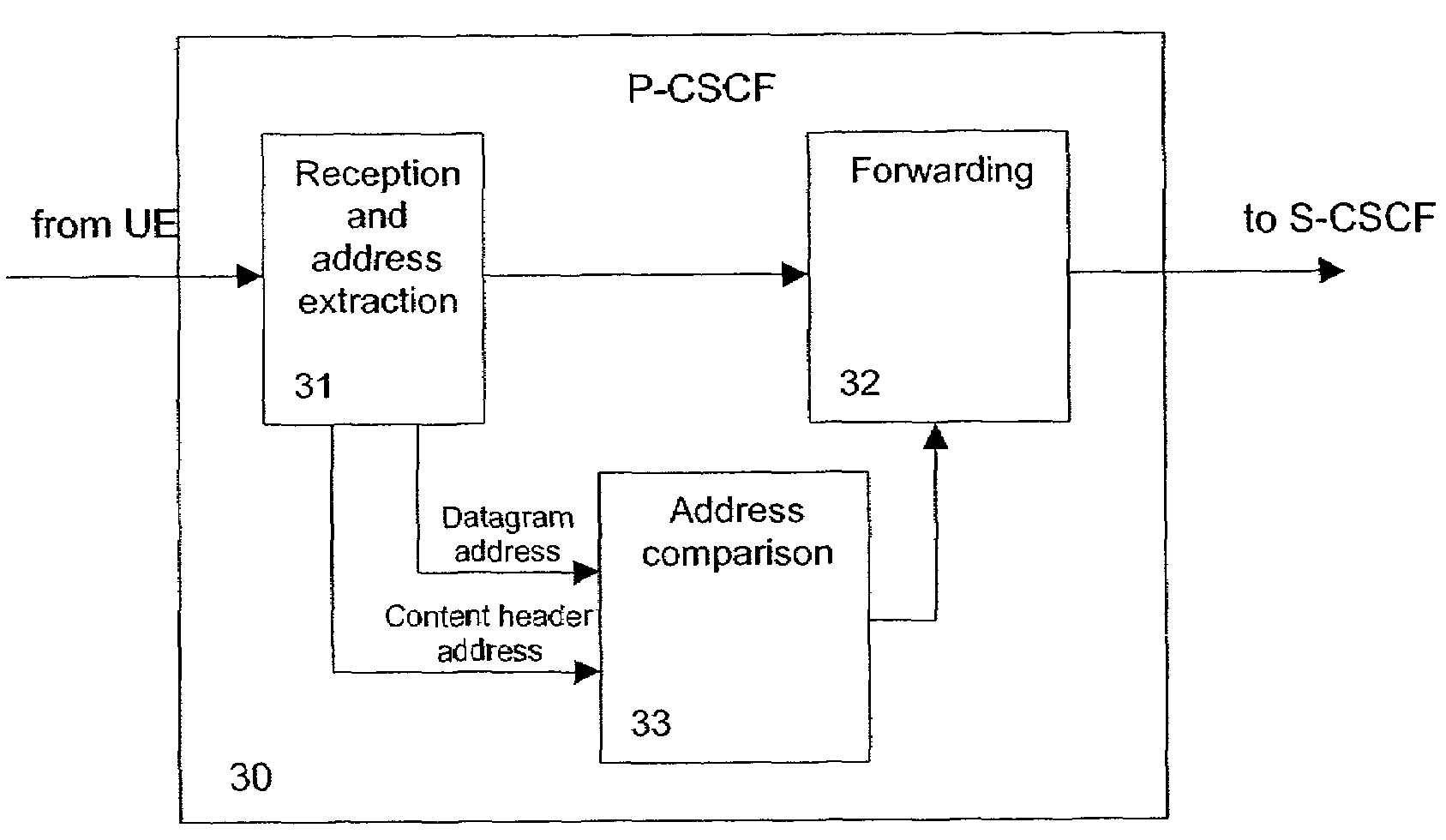
Method and network element for providing secure access to a packet data network
ActiveUS7574735B2Multiple digital computer combinationsProgram controlProtection mechanismSecurity association
Owner:NOKIA TECHNOLOGLES OY
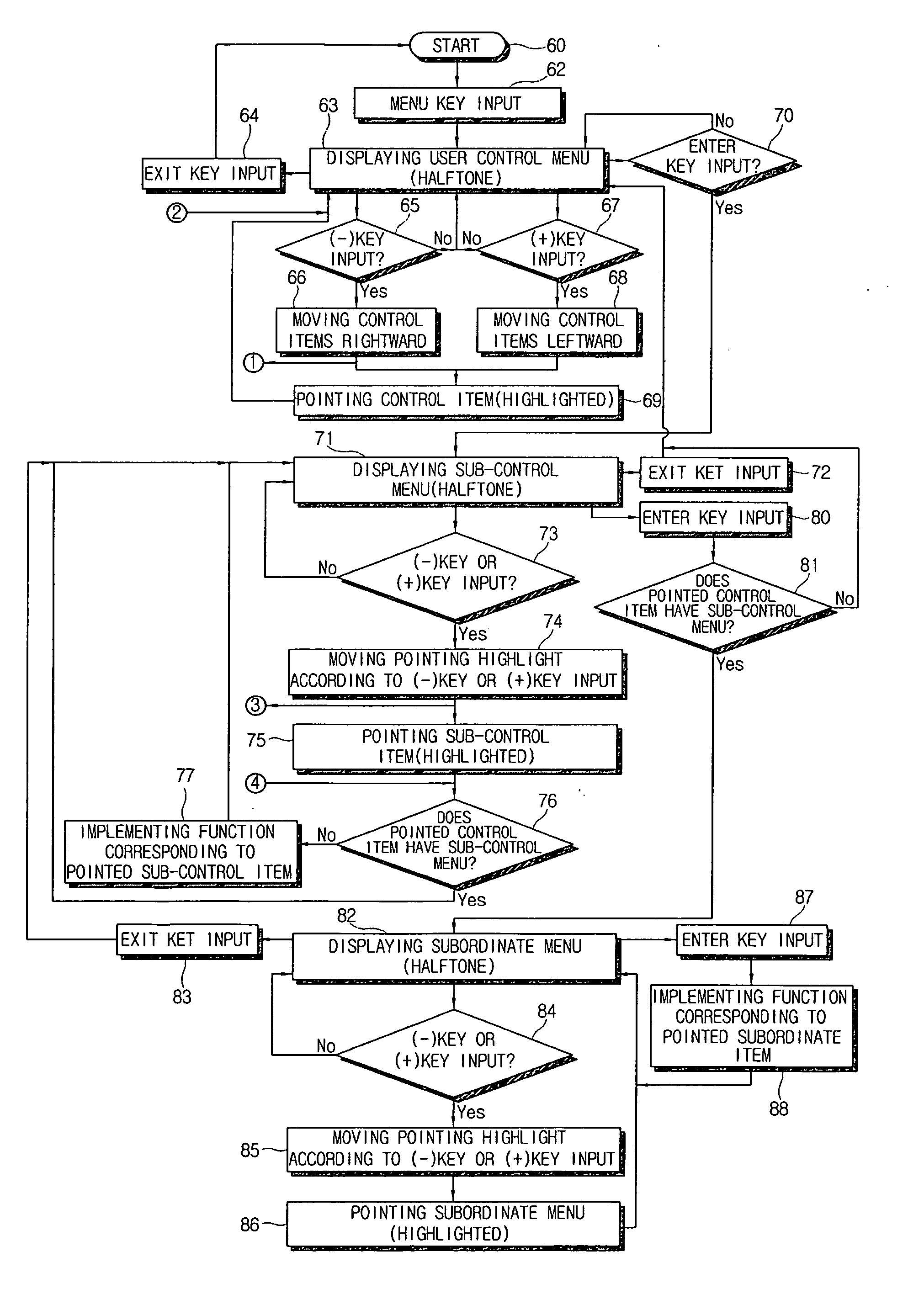
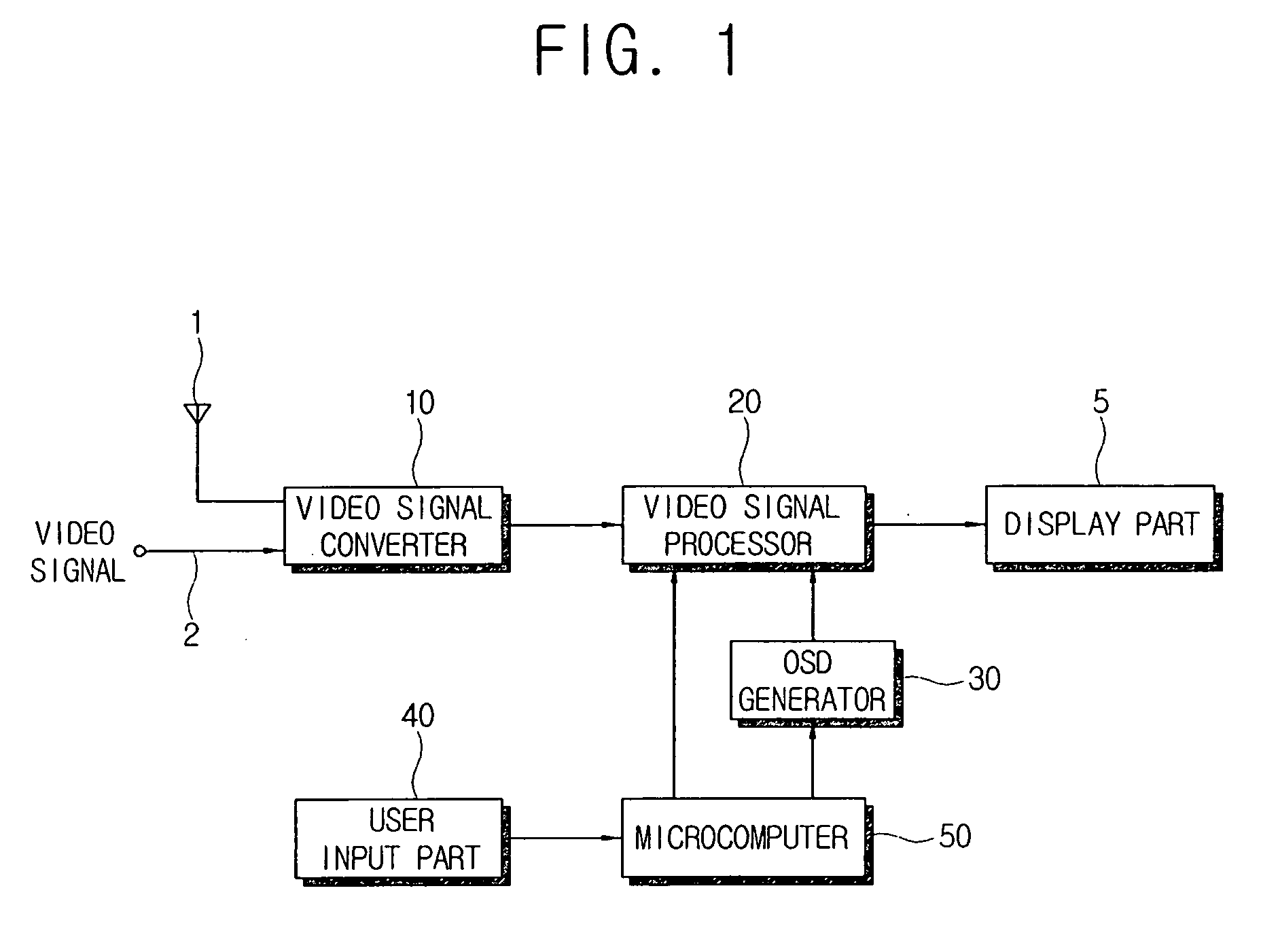
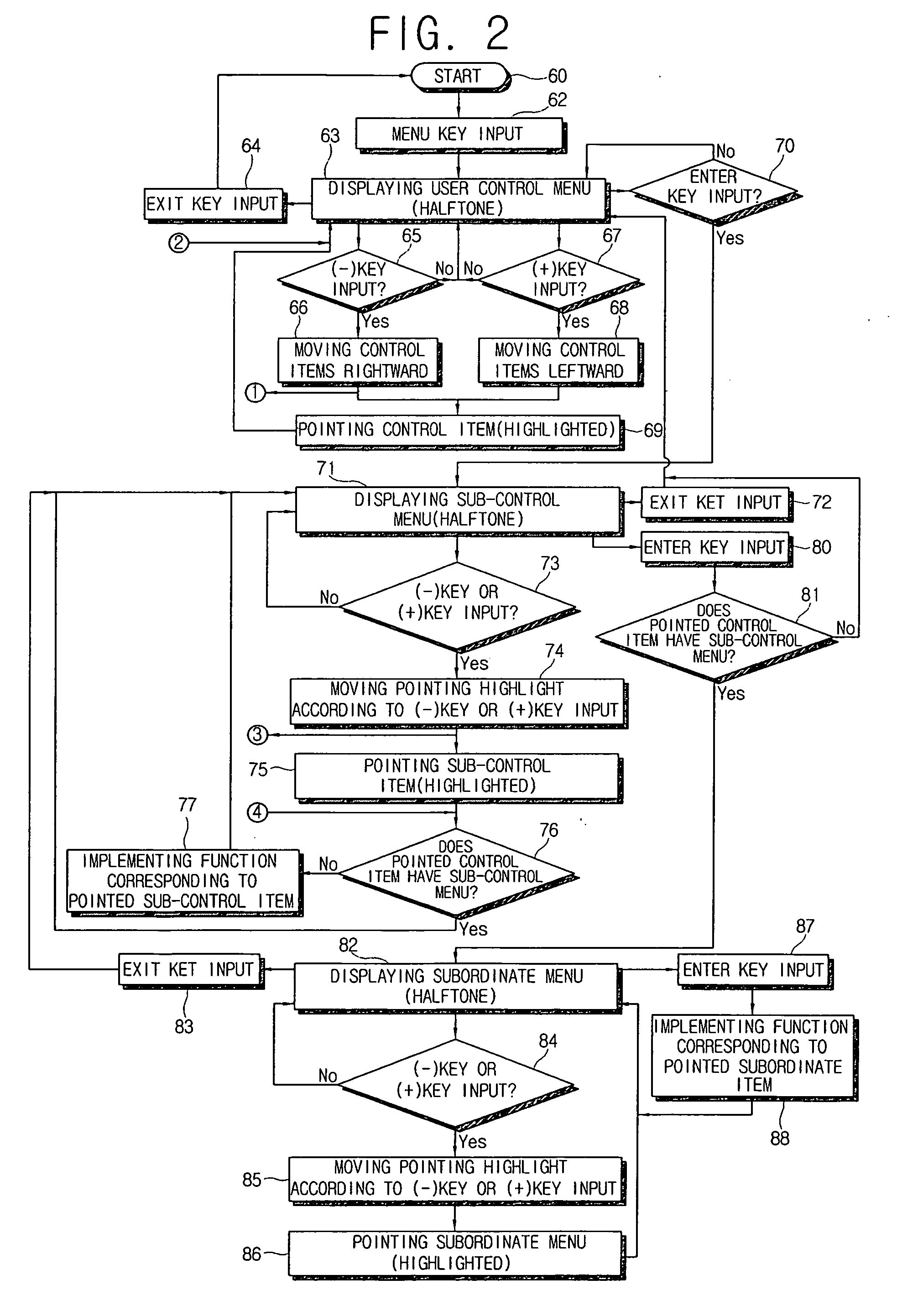
Display apparatus and control method thereof
InactiveUS20060190841A1Television system detailsColor television detailsUser inputHuman–computer interaction
Owner:SAMSUNG ELECTRONICS CO LTD
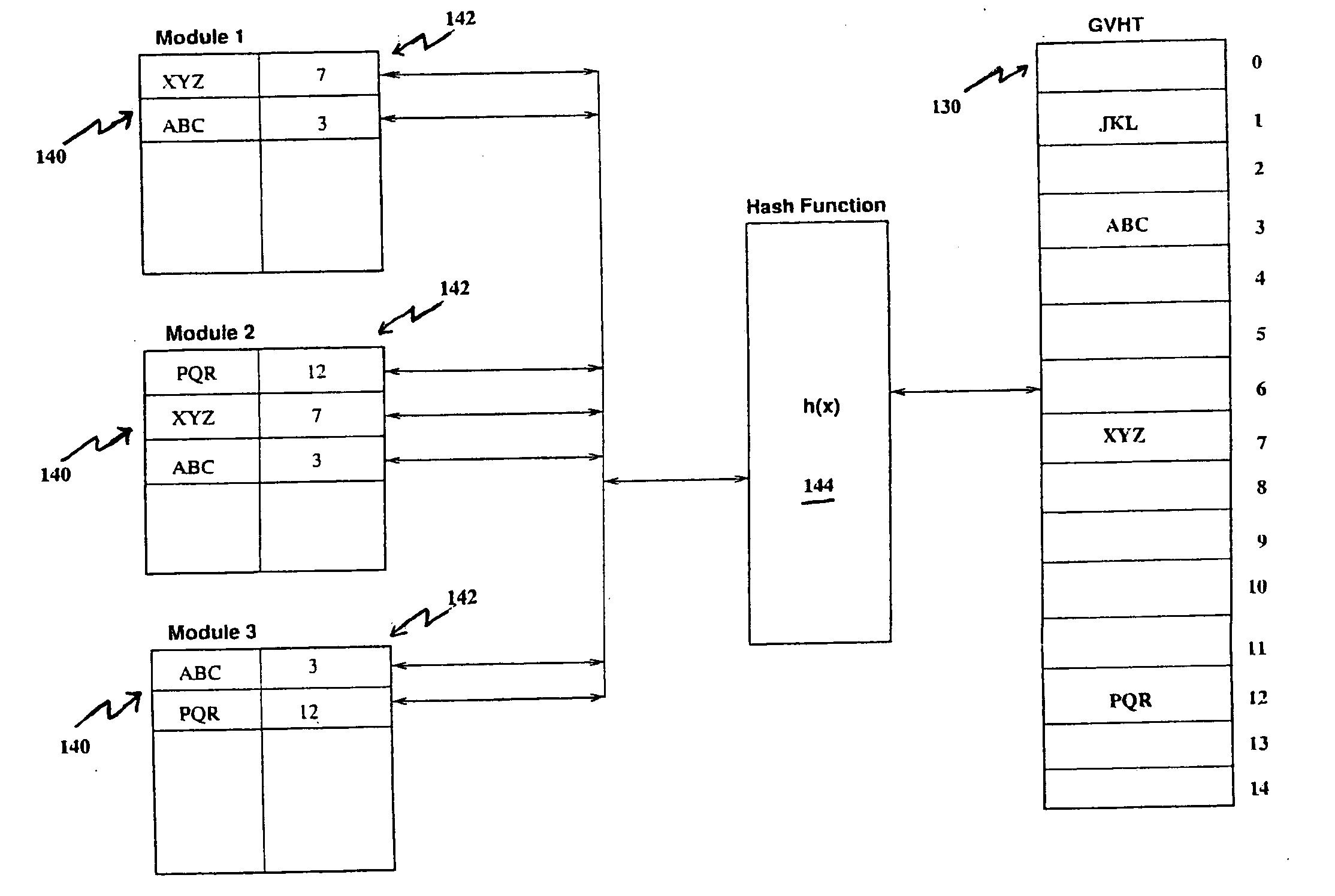
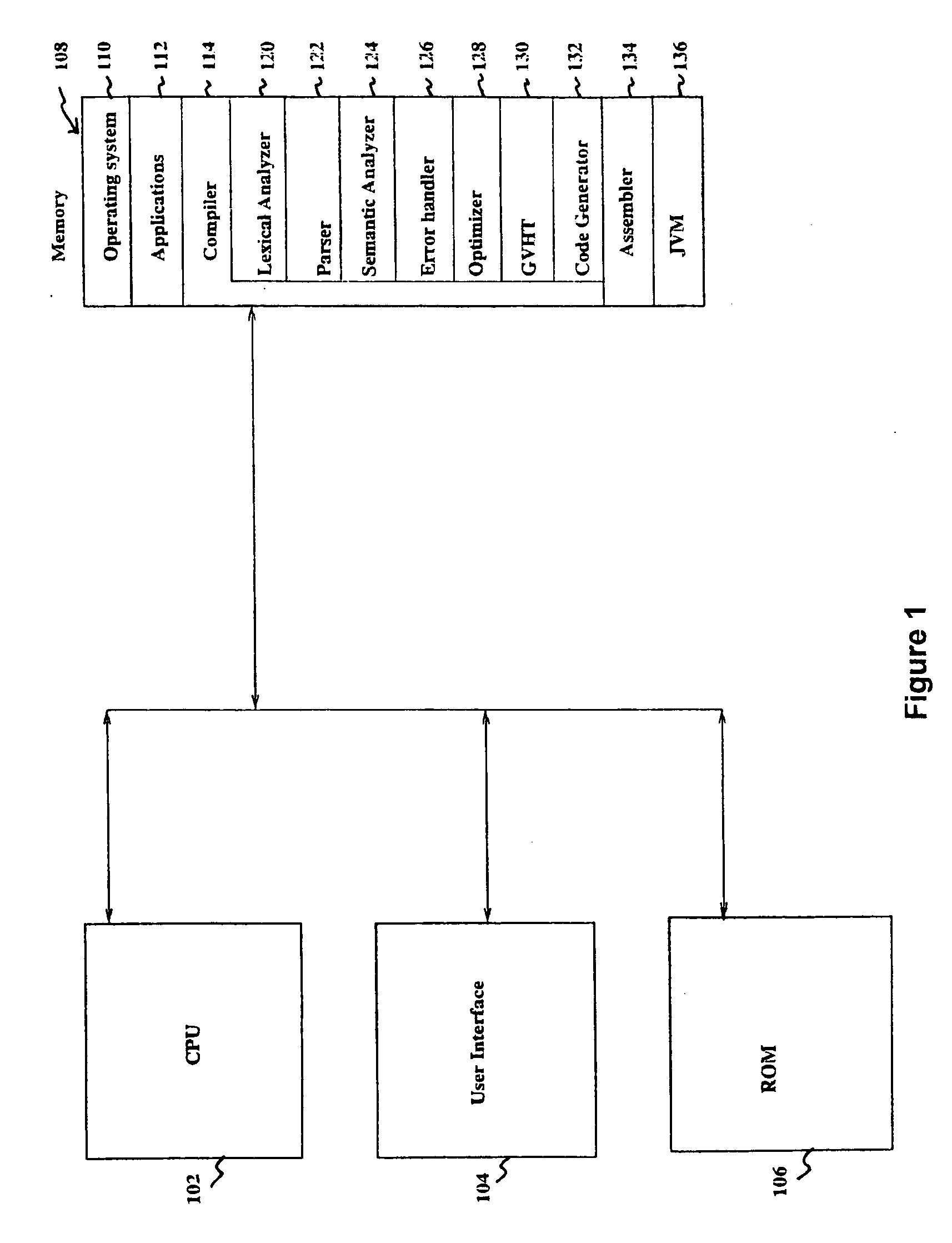
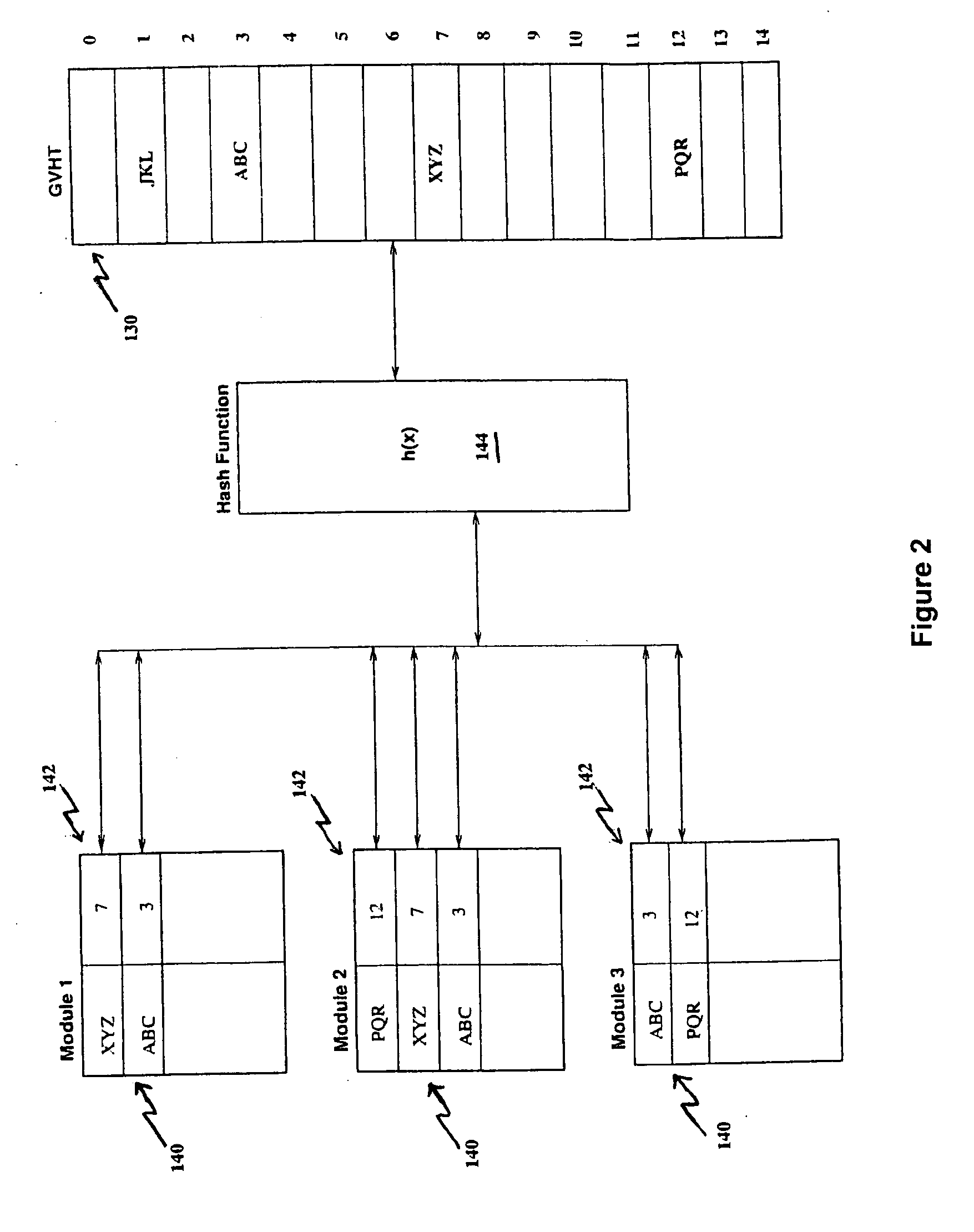
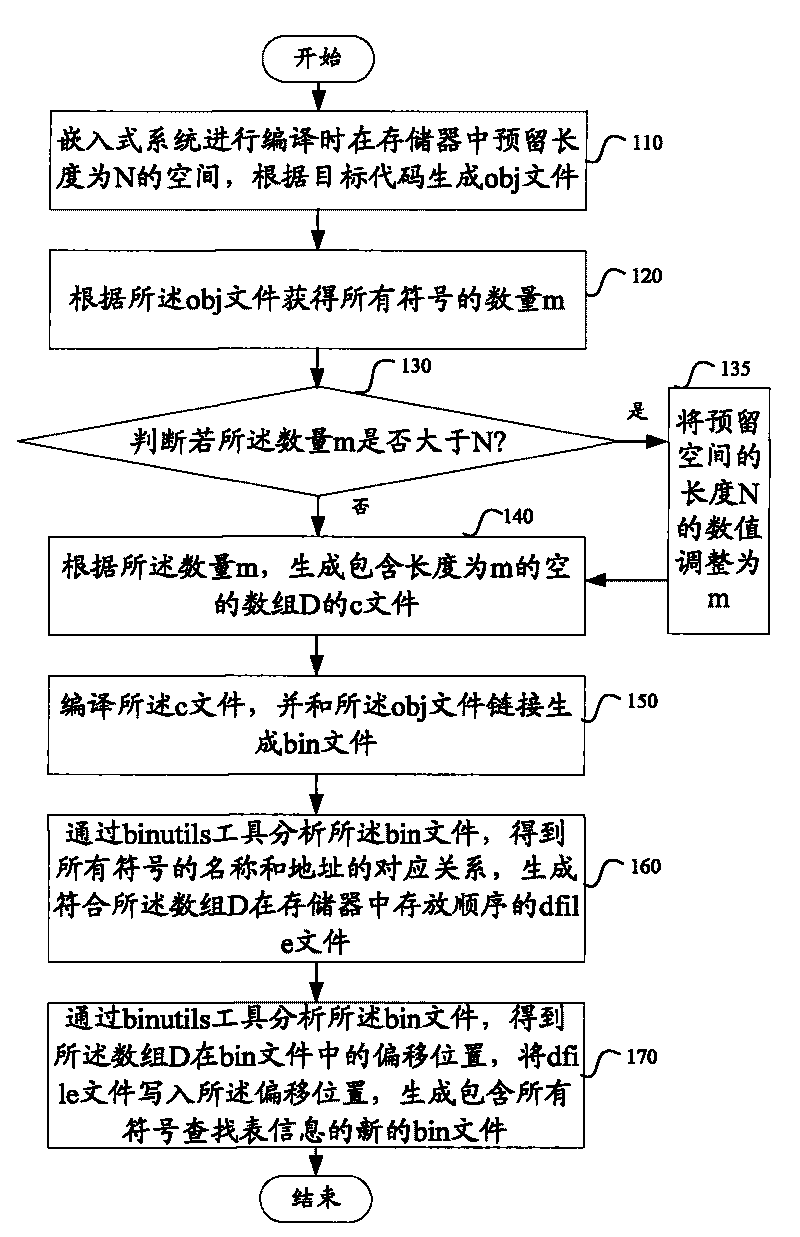
Compile time linking via hashing technique
InactiveUS20060130020A1Simple processRapid techniqueLink editingProgram controlAddress resolutionMachine code
A linker is usually used, in post processing of compiling high-level languages such as C into machine executable language, to bind separately compiled object files and resolve the addresses (142) of global variables (140) declared in the separate files. The invention proposes linking during compile time by using a special purpose hash table called global variables hash table (130) shared among the separate files. This results in a collection of processed object files that are coherent in terms of their addresses (142) for global variables (140) that could be further assembled correctly into machine executable code. This method is useful for compiling separate high level language source files to generate executable machine code employing a technique of address resolution across separate modules.
Owner:AXIOMATIC SOLUTIONS
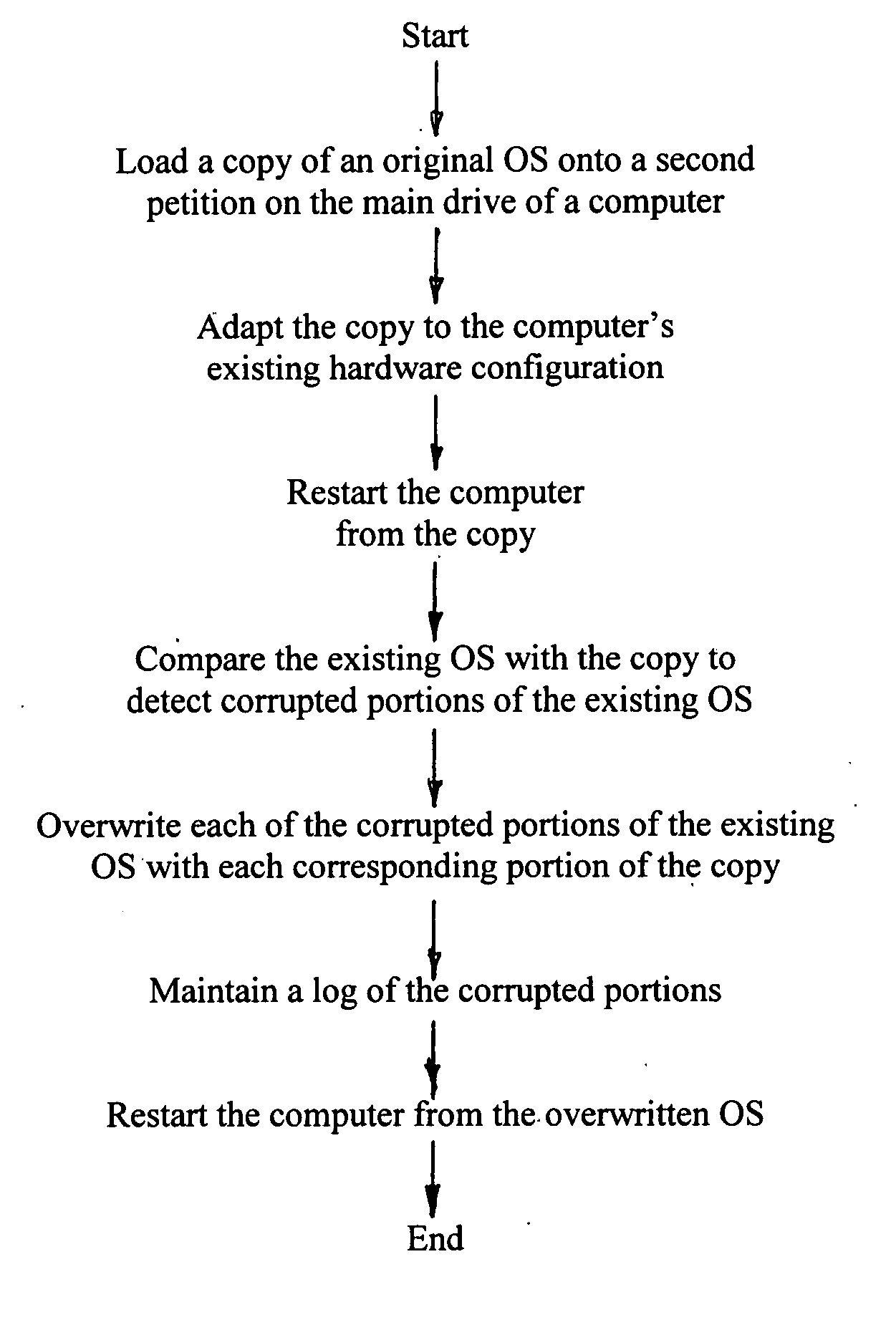
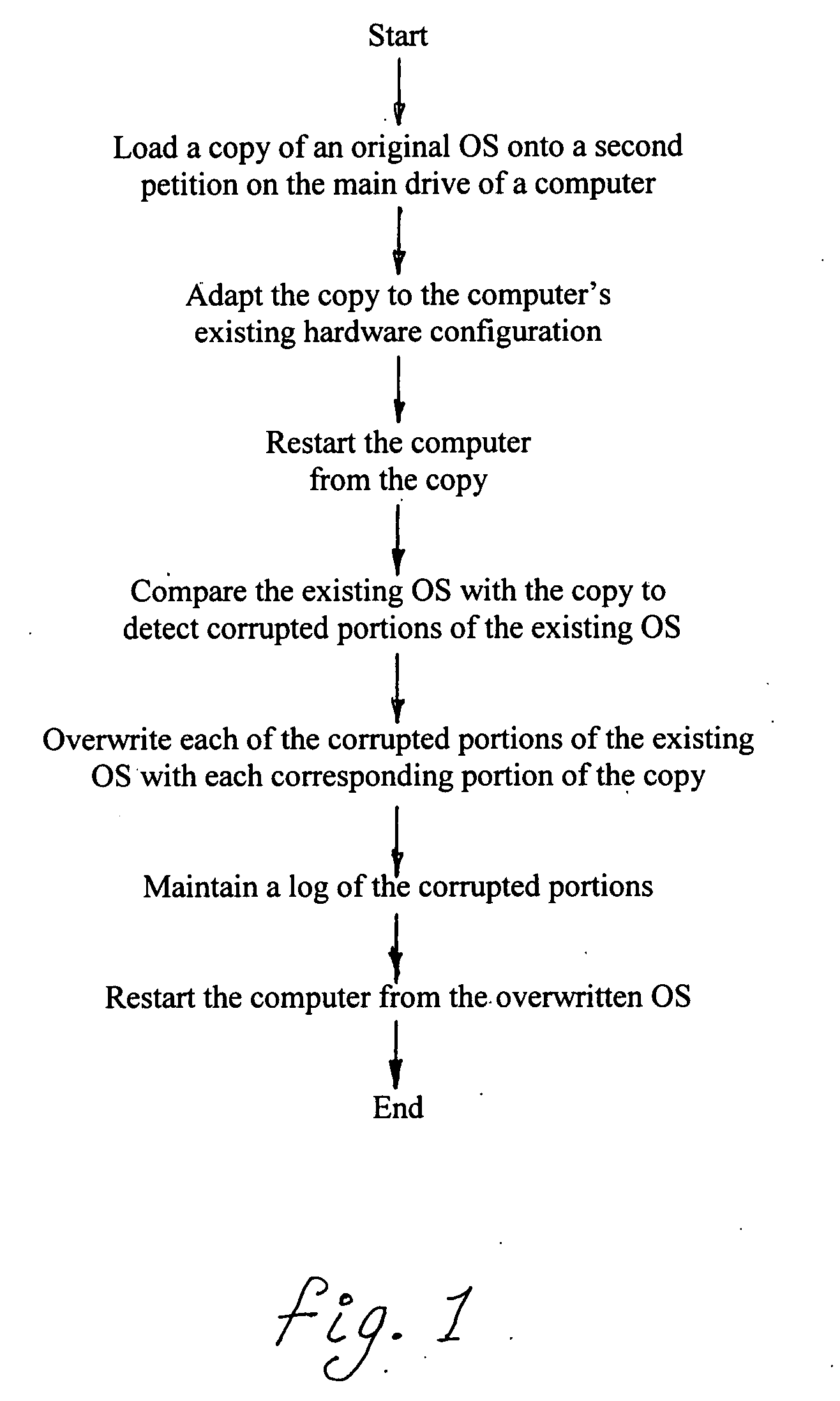
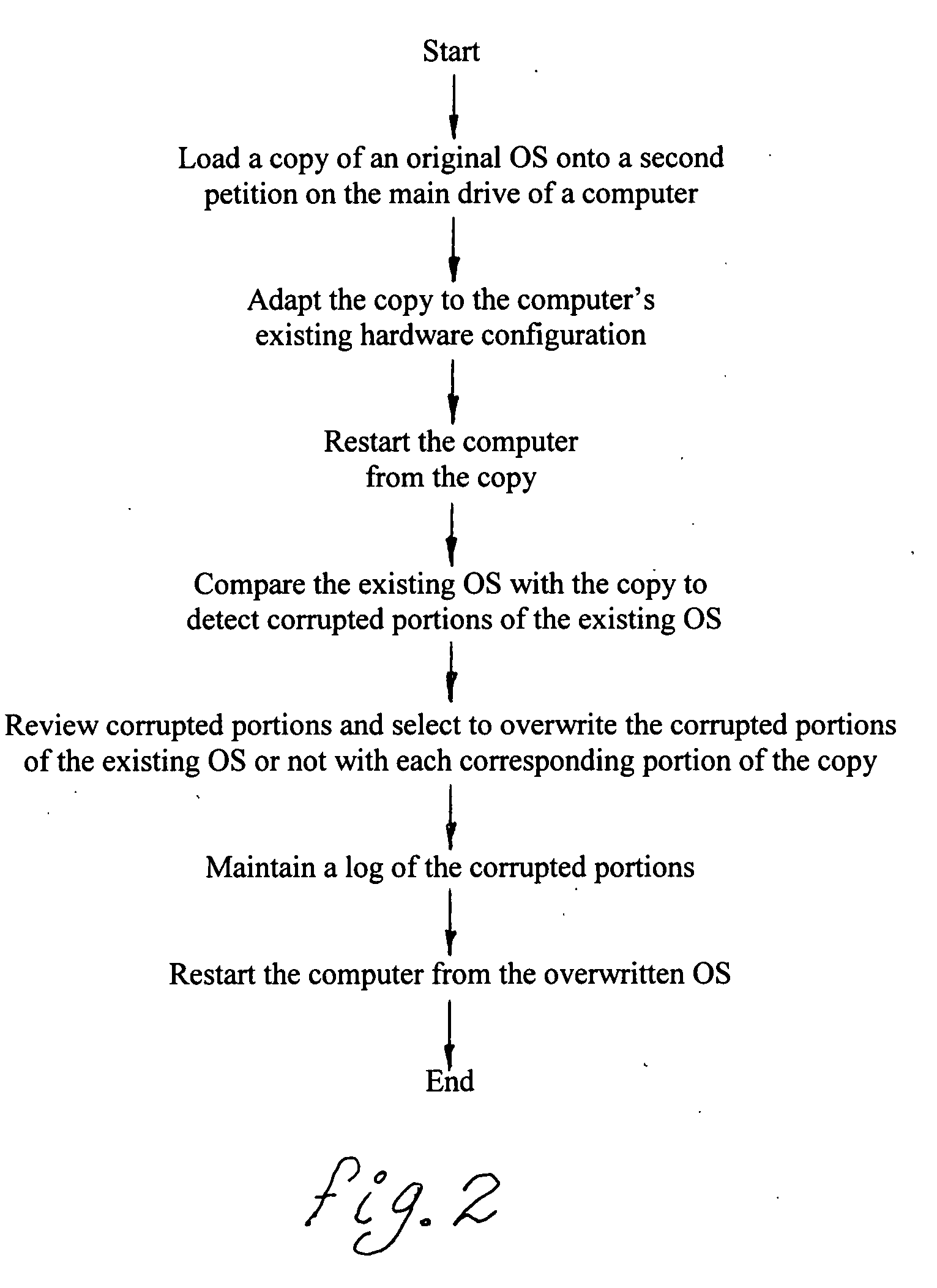
Method for non-destructive restoration of a corrupted operating system
InactiveUS20070143591A1Easy to checkError detection/correctionDigital computer detailsNon destructiveOperational system
Owner:HOME FREE ENTERPRISES
System and method for securing computers against computer viruses
In one embodiment, an antivirus mechanism (e.g., antivirus program) in a computer initiates shielding procedures in response to a triggering event indicative of a presence of a virus in the computer, the virus being of a type not recognized by the antivirus program. The shielding procedures advantageously protect important components of the computer while the antivirus program does not have the requisite antidote to directly deal with the virus.
Owner:TREND MICRO INC
Recording of inter-application data flow
ActiveUS20170005897A1Easy transitionError detection/correctionProgram controlData streamAsynchronous communication
Owner:MICROSOFT TECH LICENSING LLC
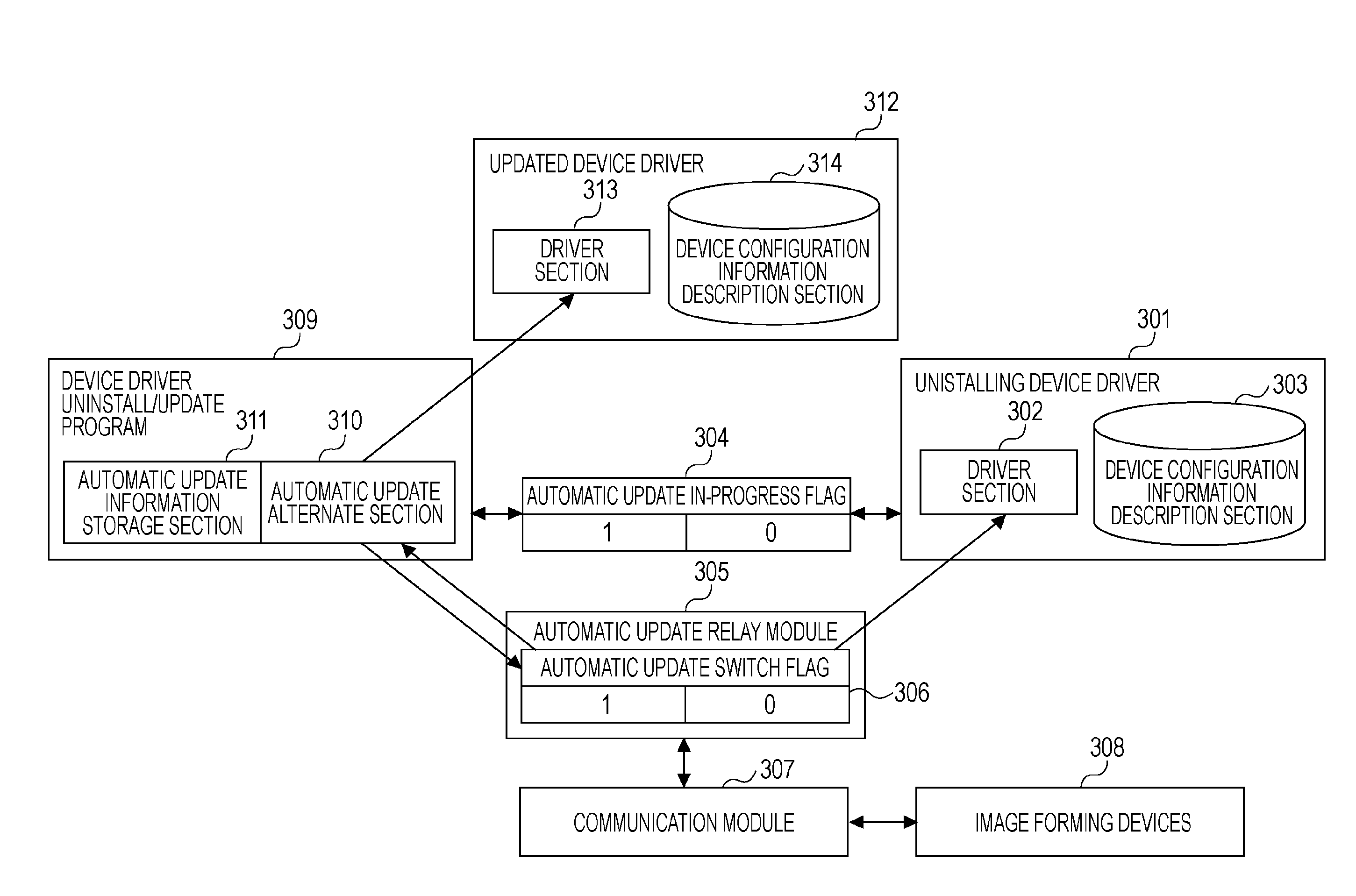
Information processing apparatus and driver control method
InactiveUS20080231868A1Digitally marking record carriersDigital computer detailsInformation processingComputer hardware
Owner:CANON KK
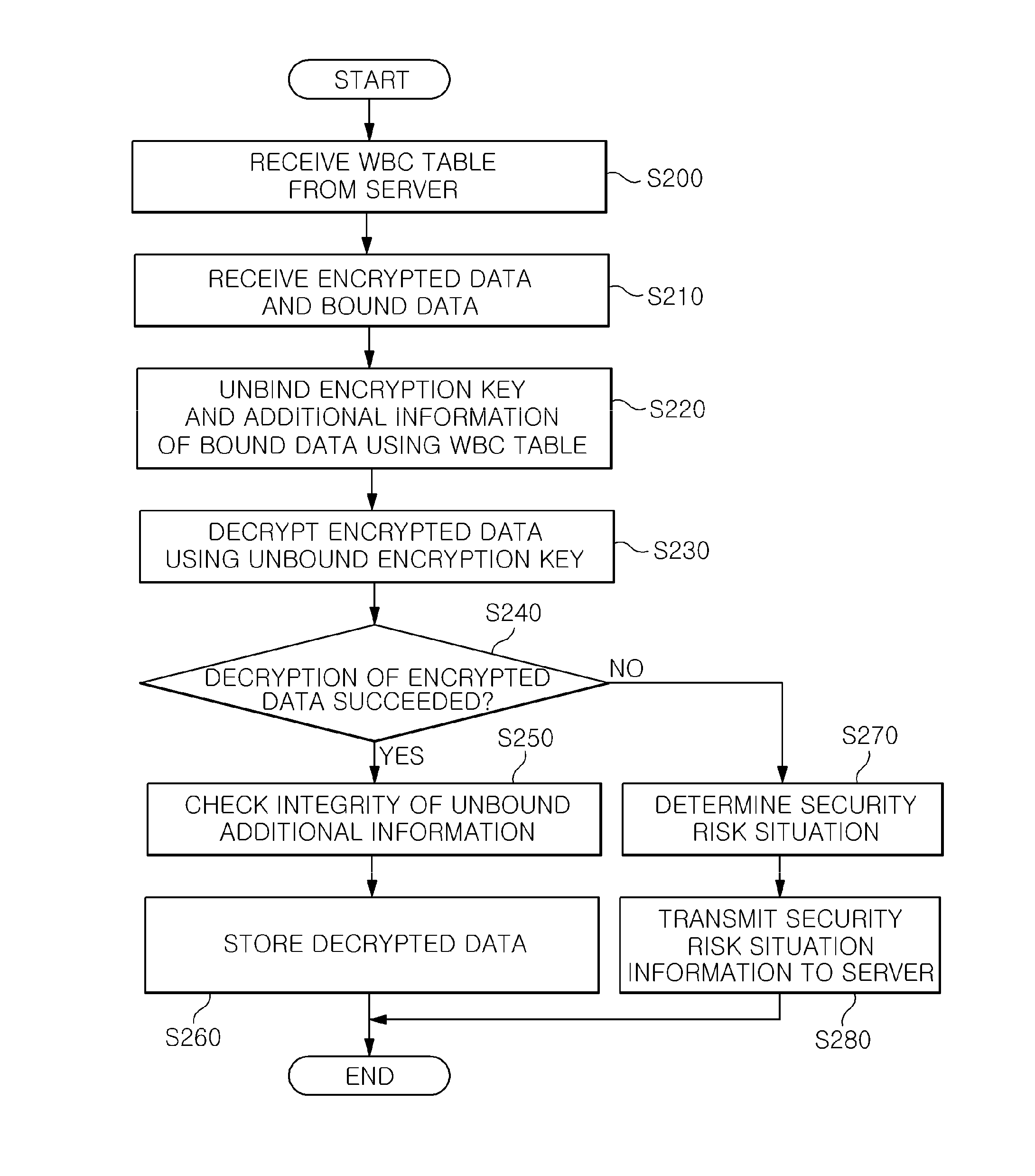
Content protection apparatus and method using binding of additional information to encryption key
InactiveUS20120099726A1Deciphering becomes impossibleKey distribution for secure communicationRandom number generatorsManagement unitProcessing element
Owner:ELECTRONICS & TELECOMM RES INST
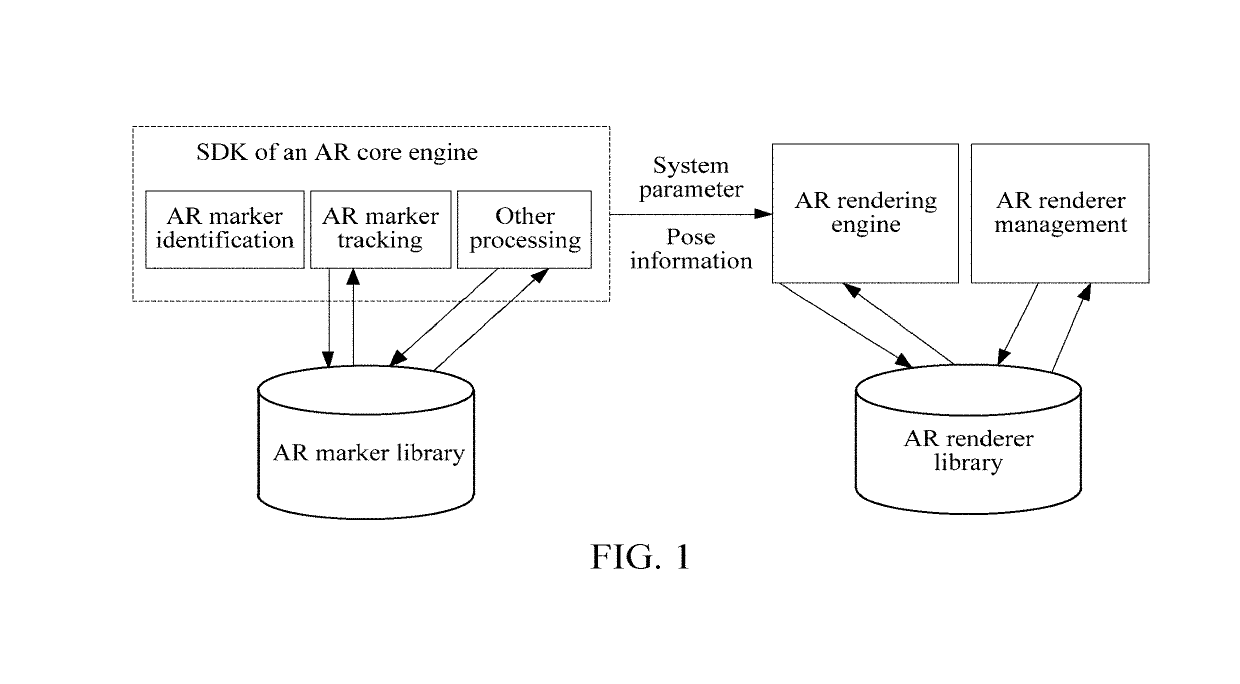
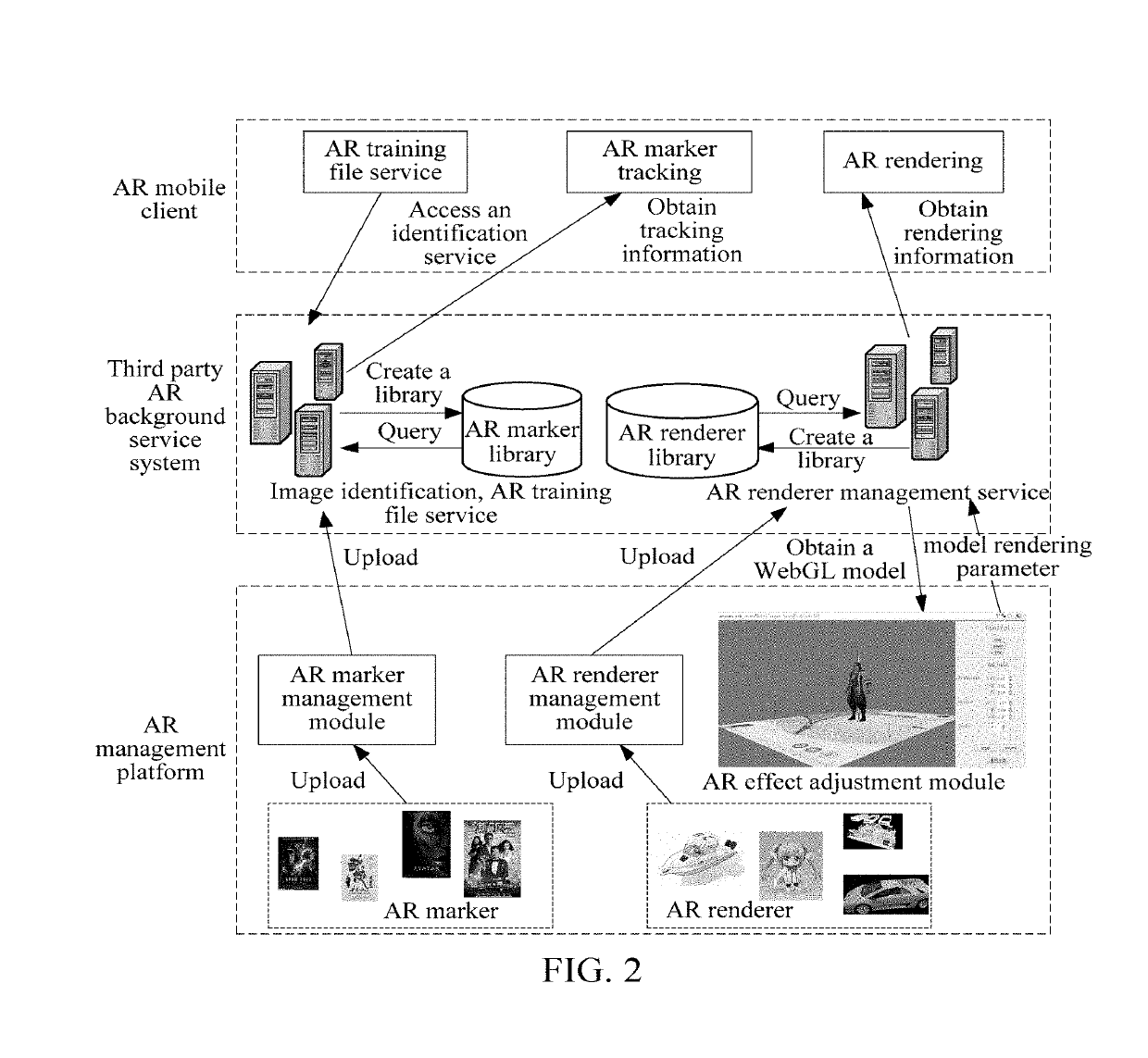
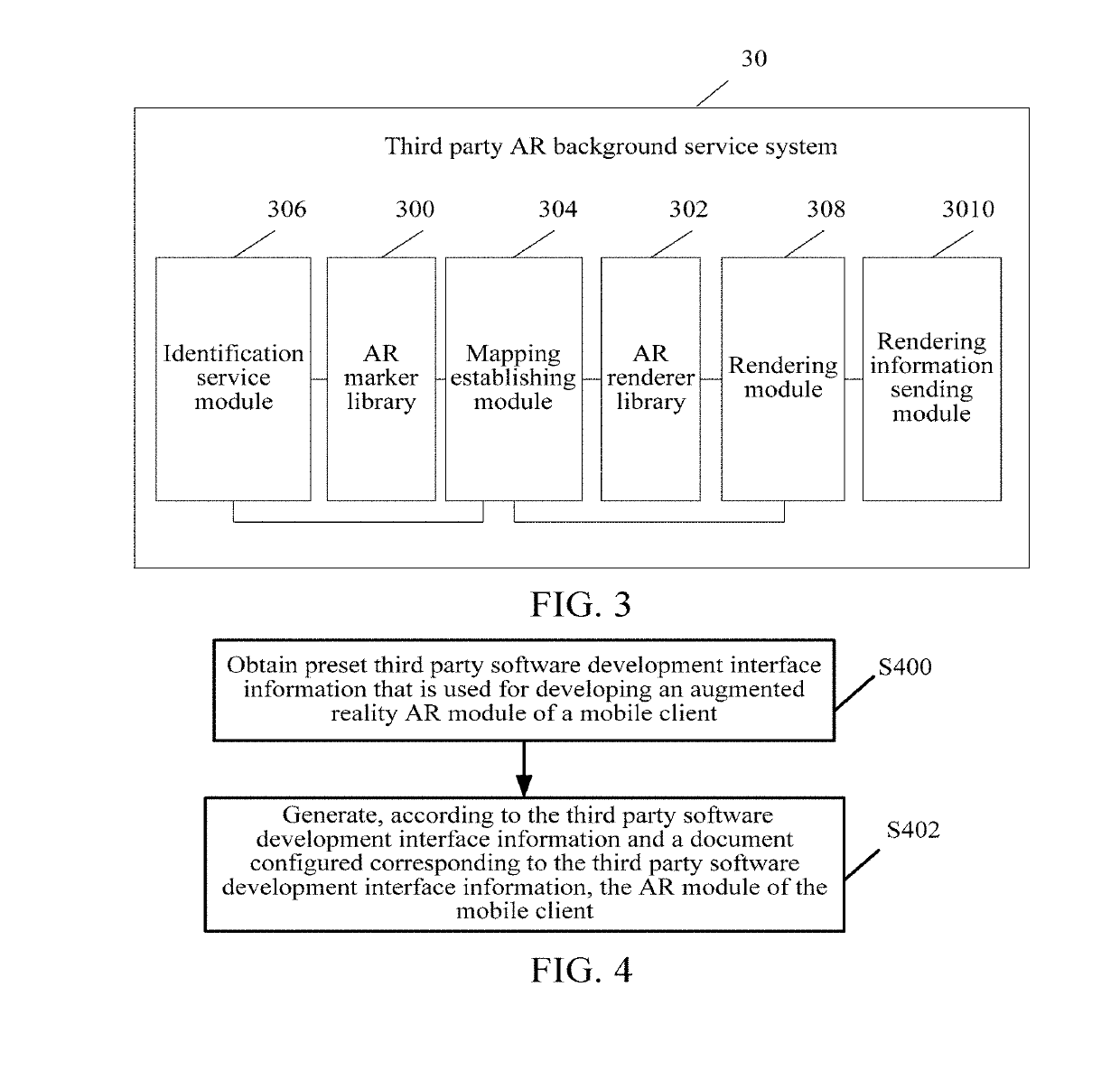
Method, apparatus and system for generating augmented reality module and storage medium
ActiveUS20190129715A1Shorten the overall cycleSimplify the development processVersion controlSoftware metricsThird partySoftware engineering
Owner:TENCENT TECH (SHENZHEN) CO LTD
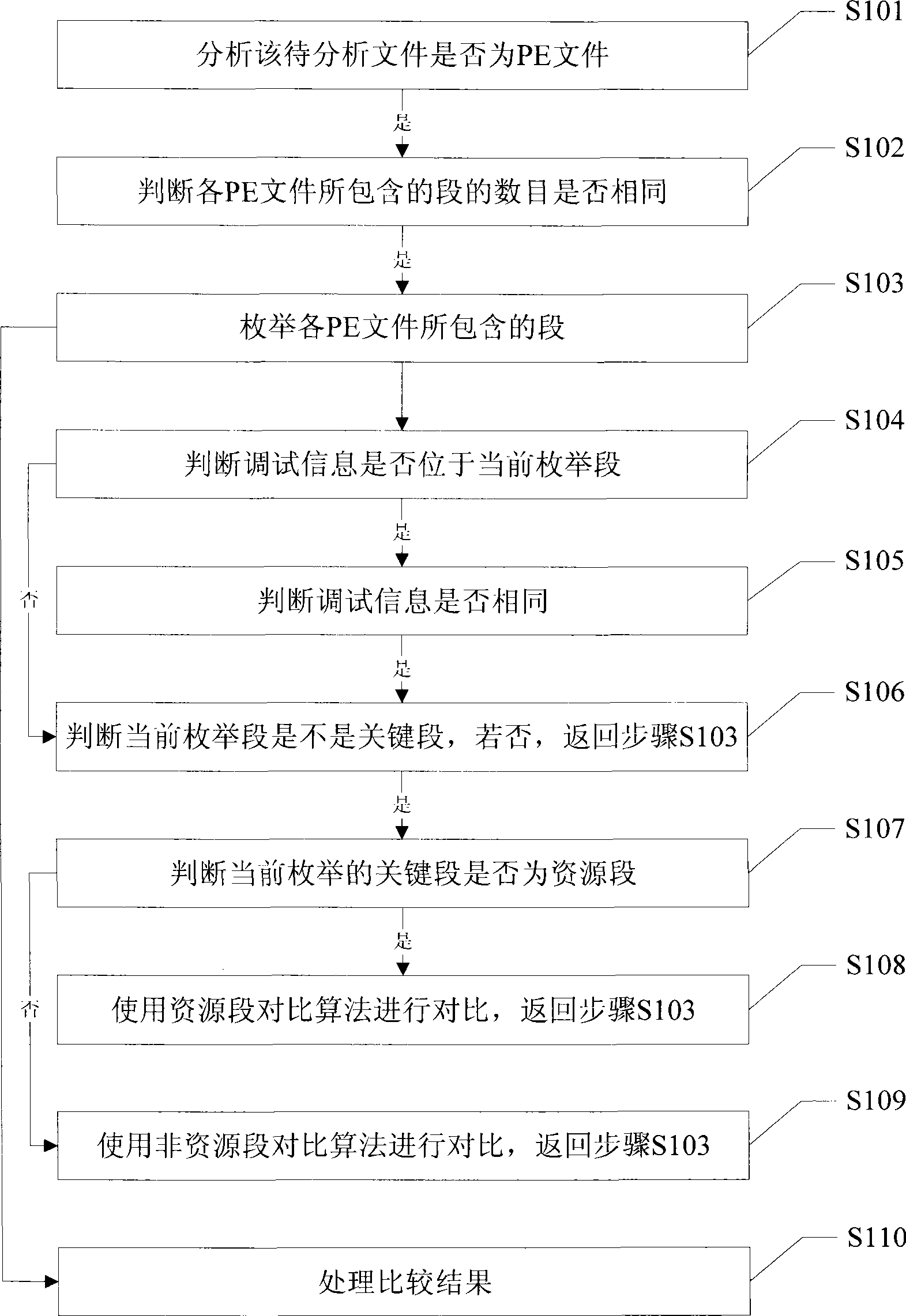
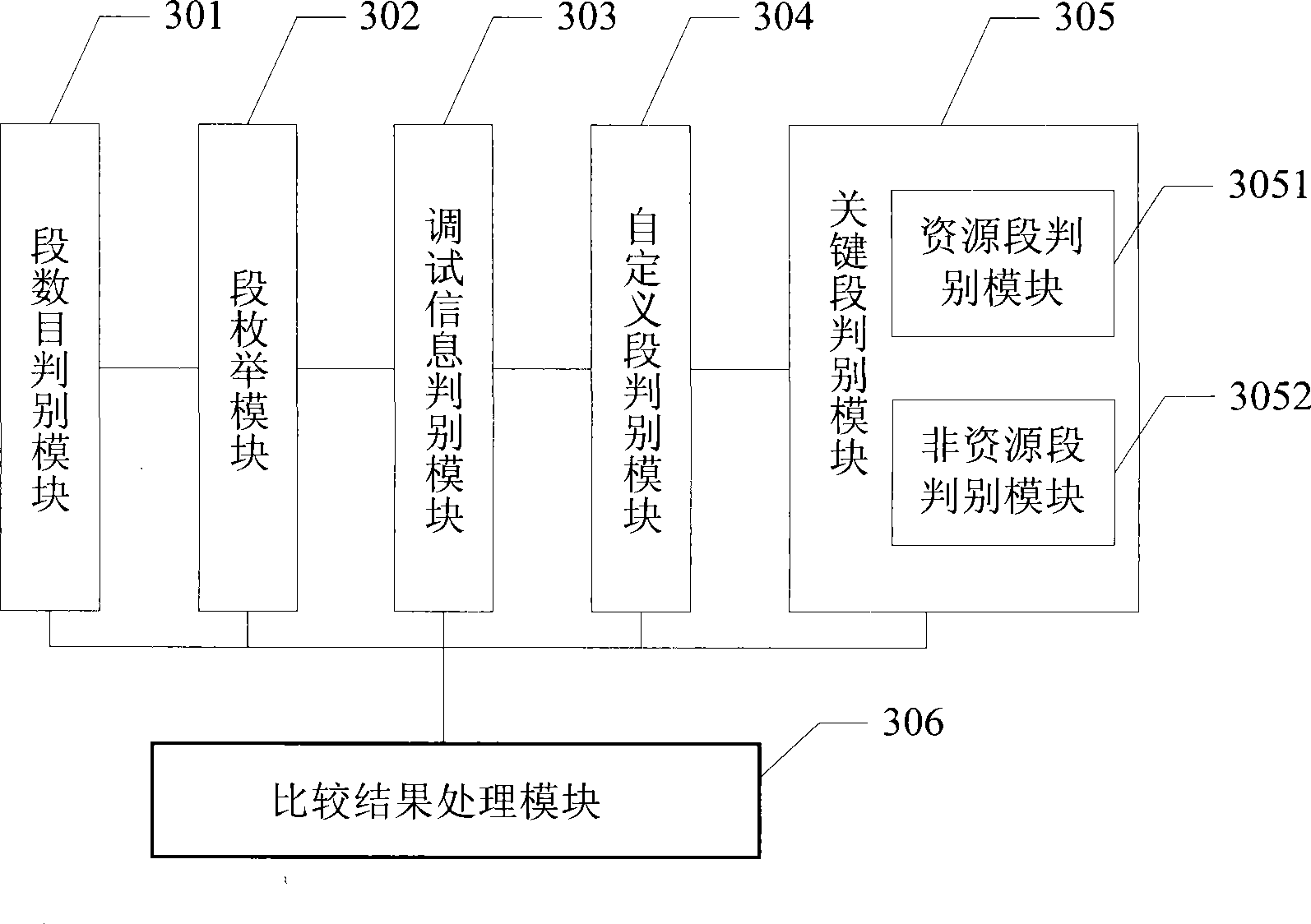
Method and apparatus for judging PE file source code consistency
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
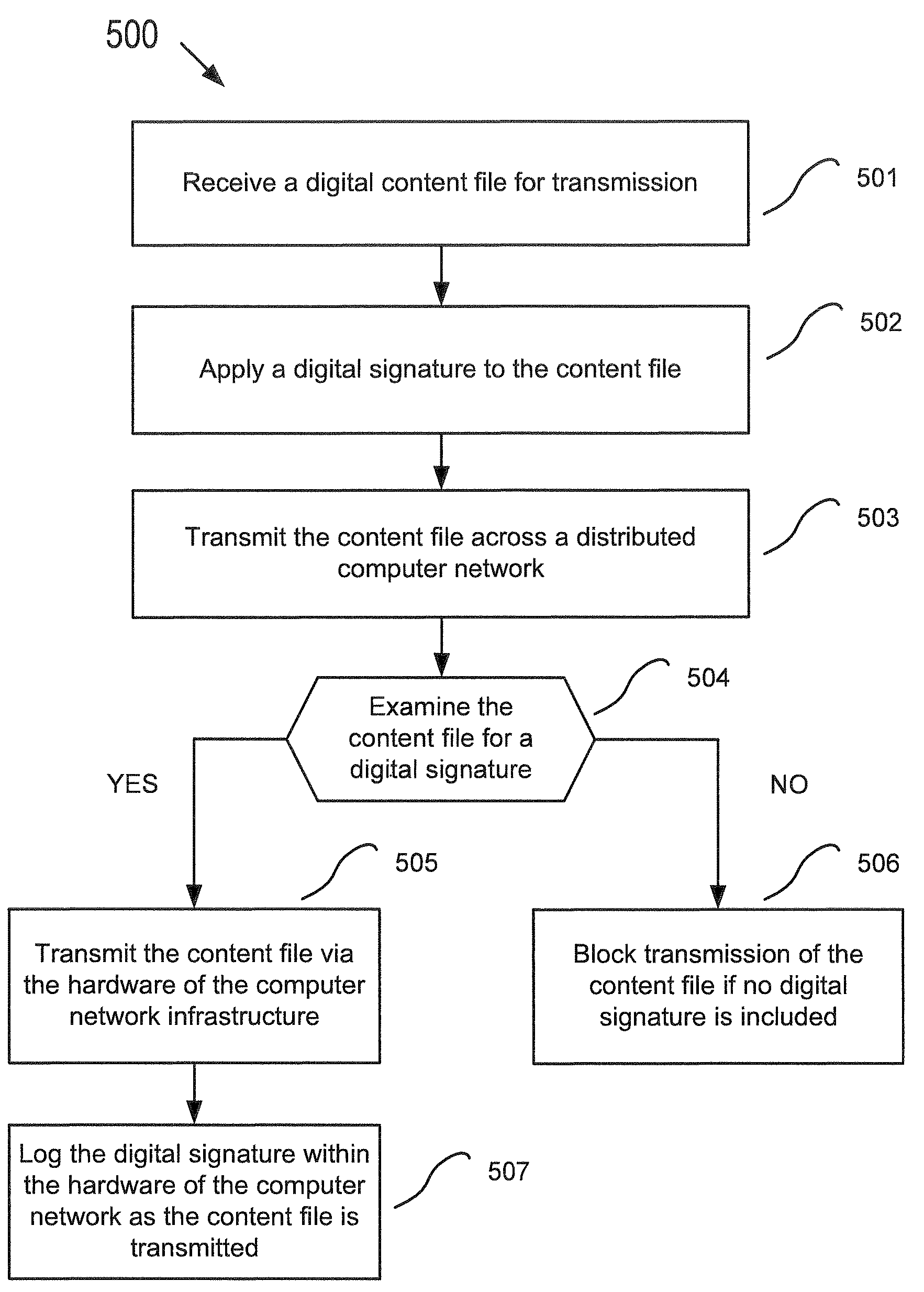
Copy protection built into a network infrastructure
InactiveUS7516322B1Copy protection is reinforcedPrevent easy circumventionMultiple digital computer combinationsProgram controlDigital contentDigital signature
Owner:CISCO TECH INC
Memory resource optimization method and device
InactiveCN104572493AImplementing Collaborative Partitioning StrategiesReduce mutual interferenceMemory architecture accessing/allocationError detection/correctionOperational systemMultilevel memory
Embodiments of the present invention relate to the field of computer. Provided are a memory resource optimization method and an apparatus, solving a mutual impact problem between existing multi-level memory resources and optimizing an existing unitary division mechanism. A specific scheme is: obtaining performance data of each program in a working set through a page coloring technology, obtaining a category of the each program by incorporating memory access frequency, selecting a page coloring division policy corresponding to the working set based on the category of the each program, inputting the page coloring division policy into an operating system kernel, and completing corresponding coloring division processing. The present invention is used for incorporating features of the working set to eliminate or reduce mutual interference of processes and threads on memory resources, improving overall performance of a computer.
Owner:HUAWEI TECH CO LTD +1
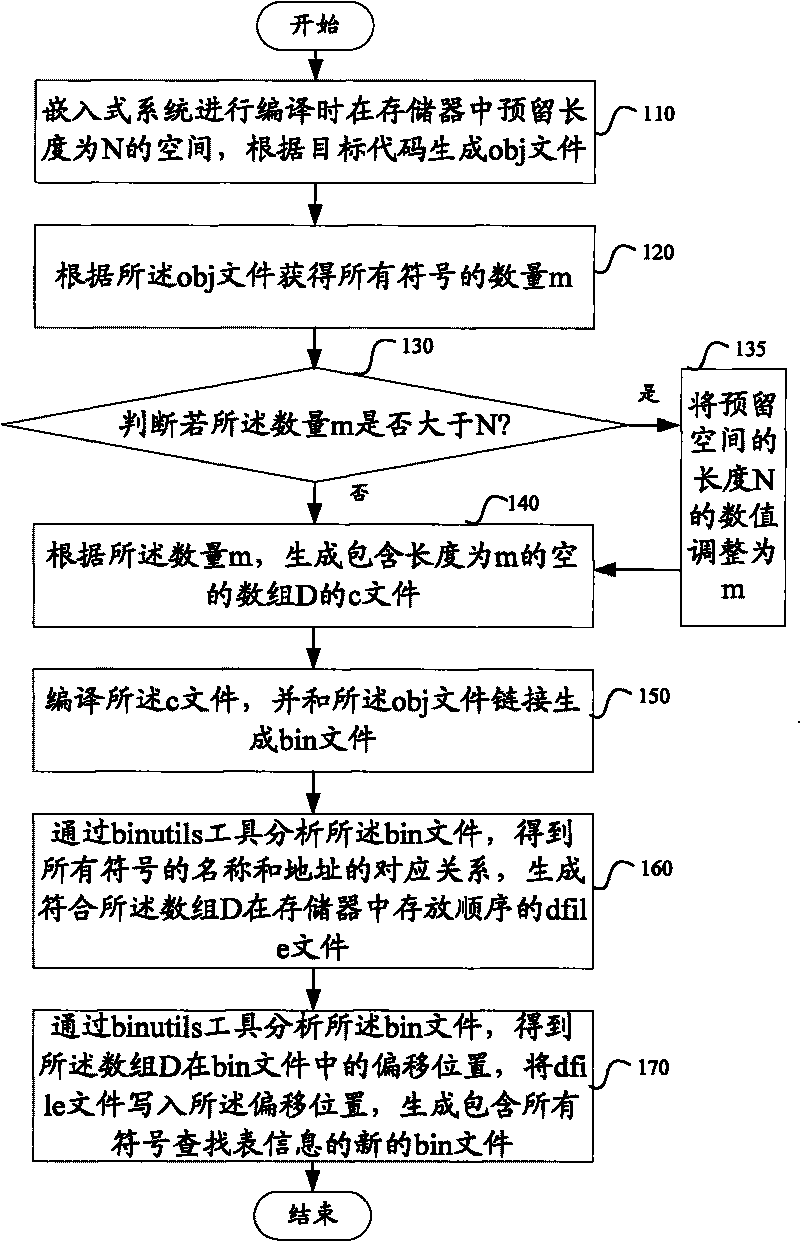
Method and device for determining paths for compiling files
Owner:BEIJING GRIDSUM TECH CO LTD
Popular searches
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap