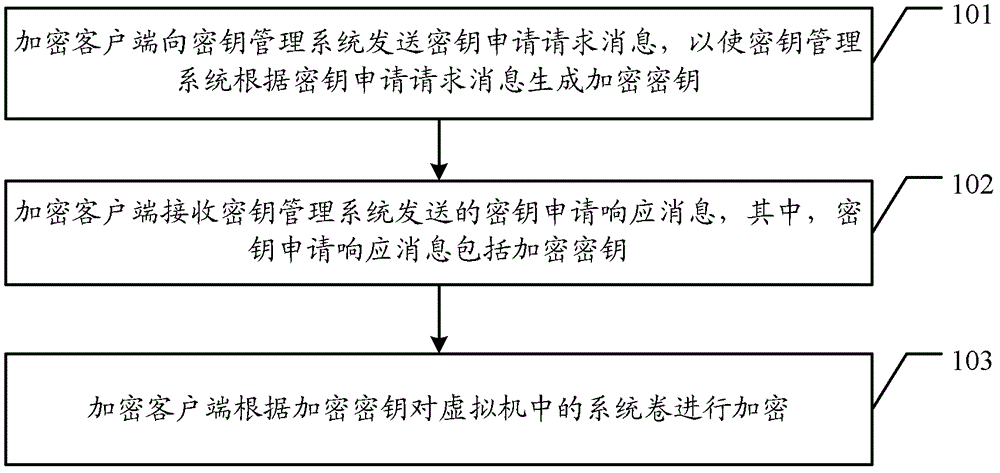
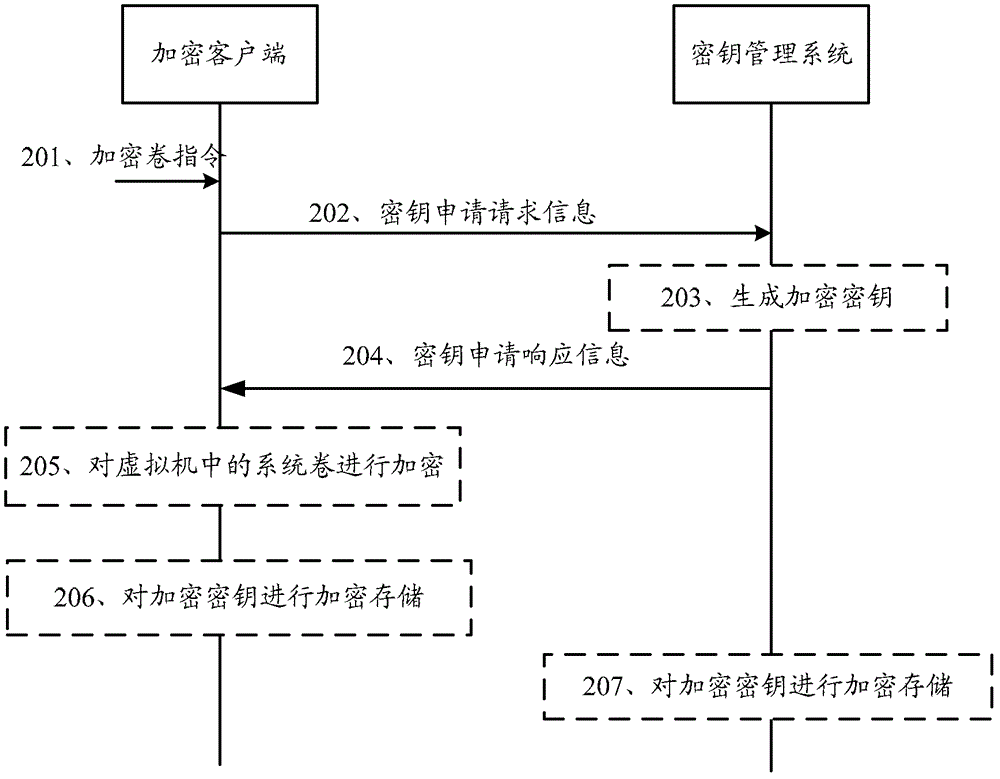
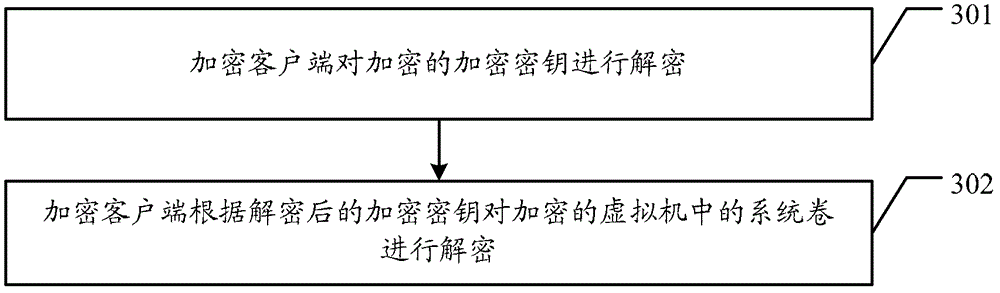
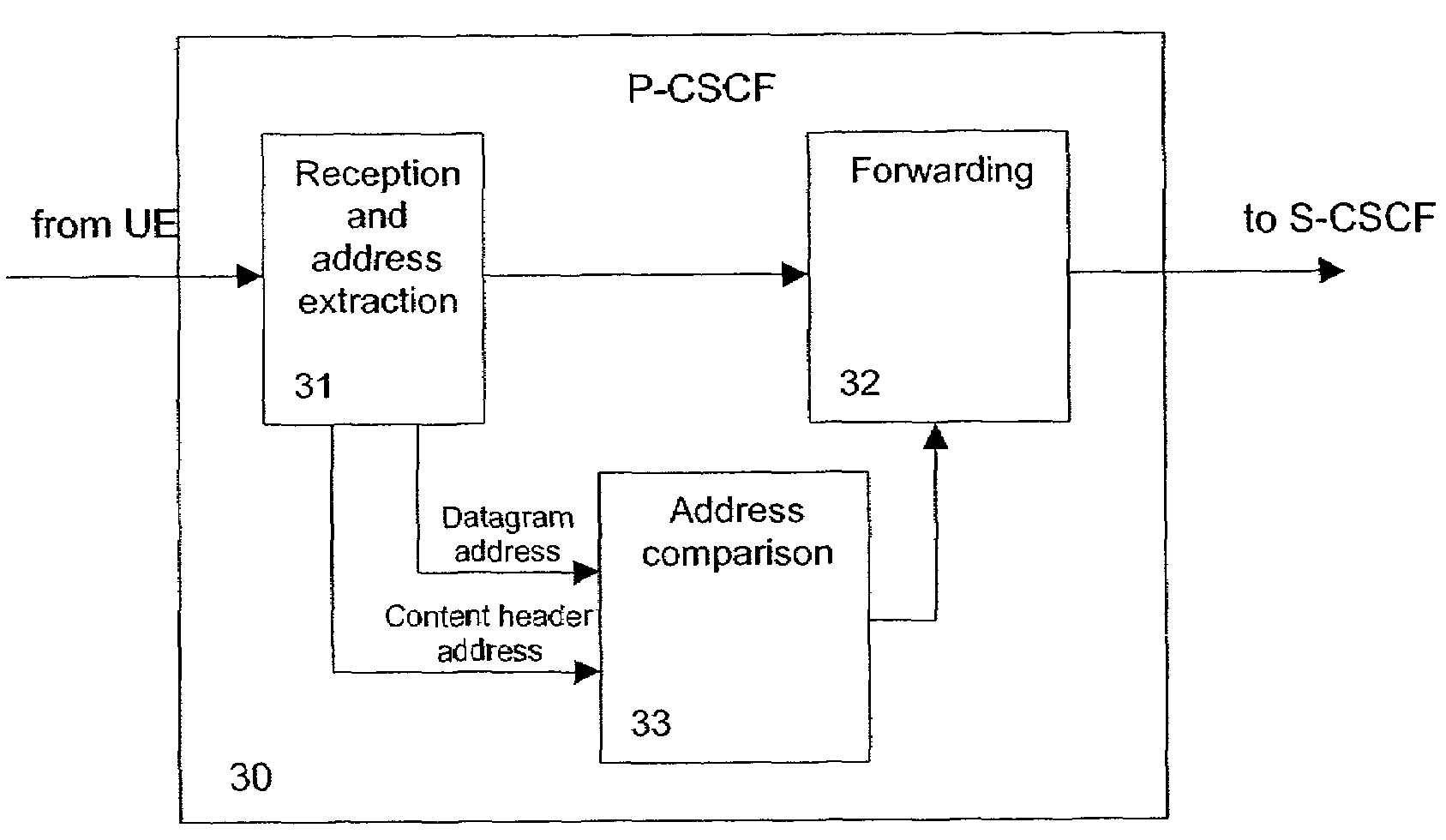
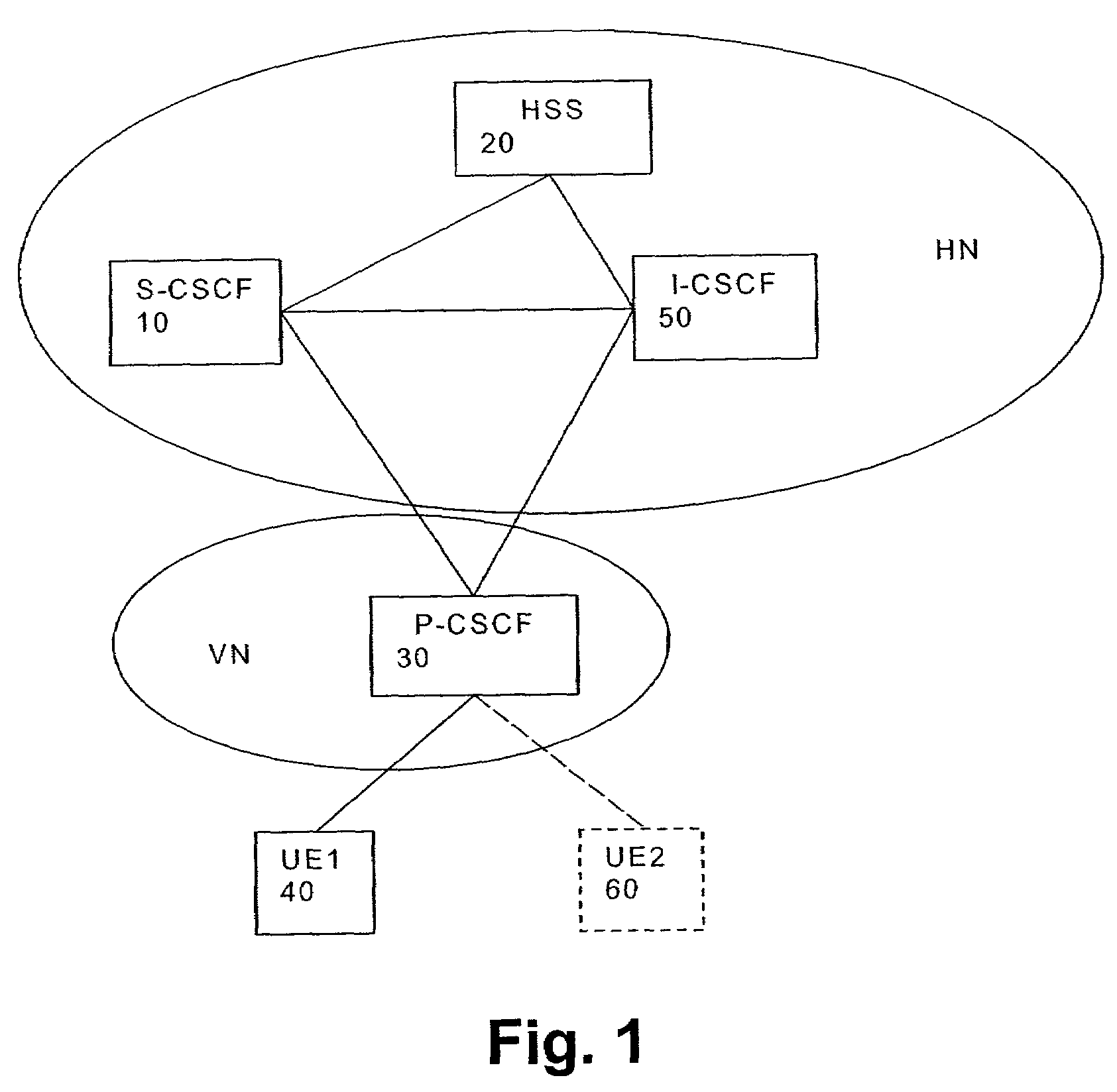
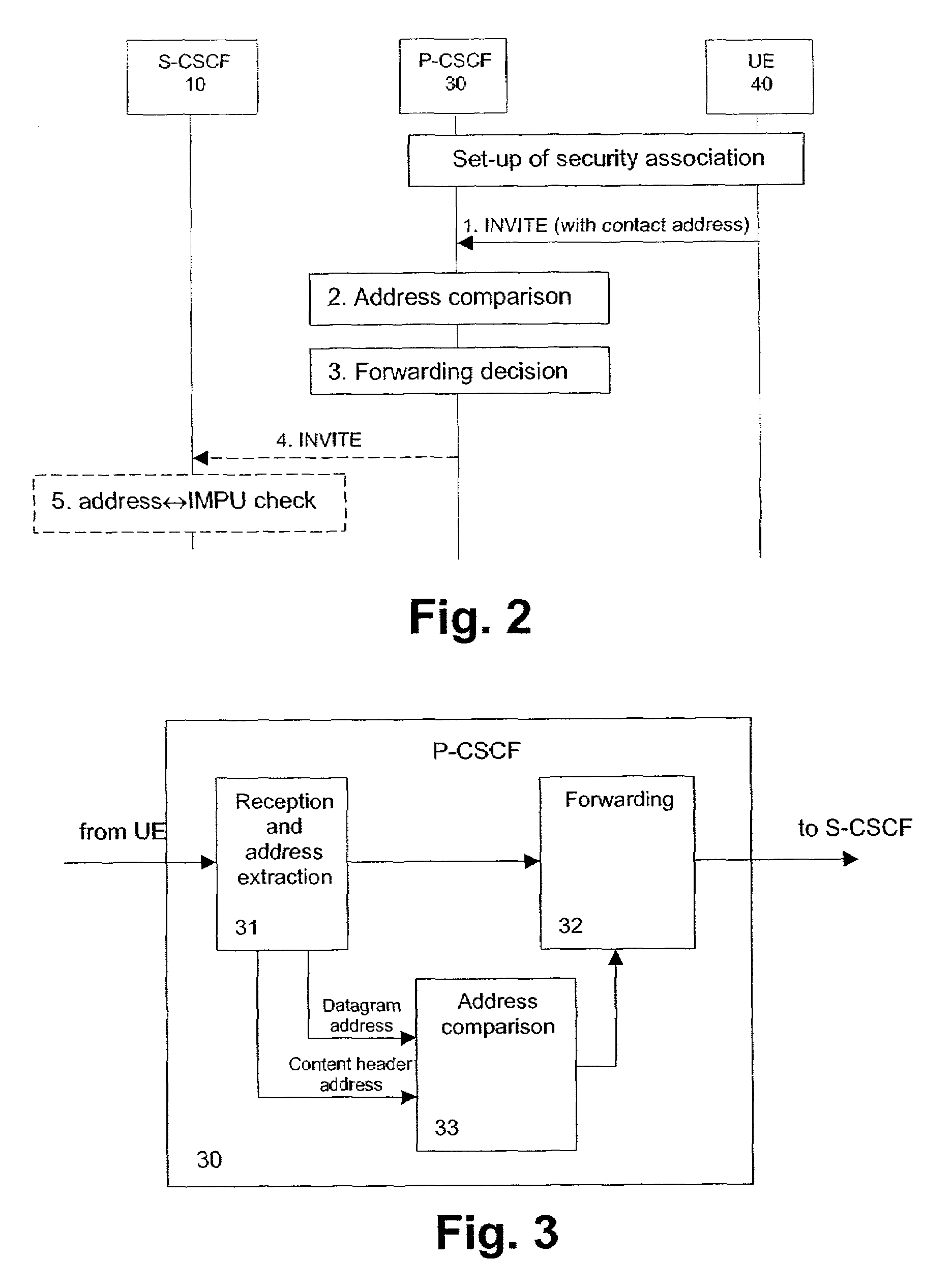
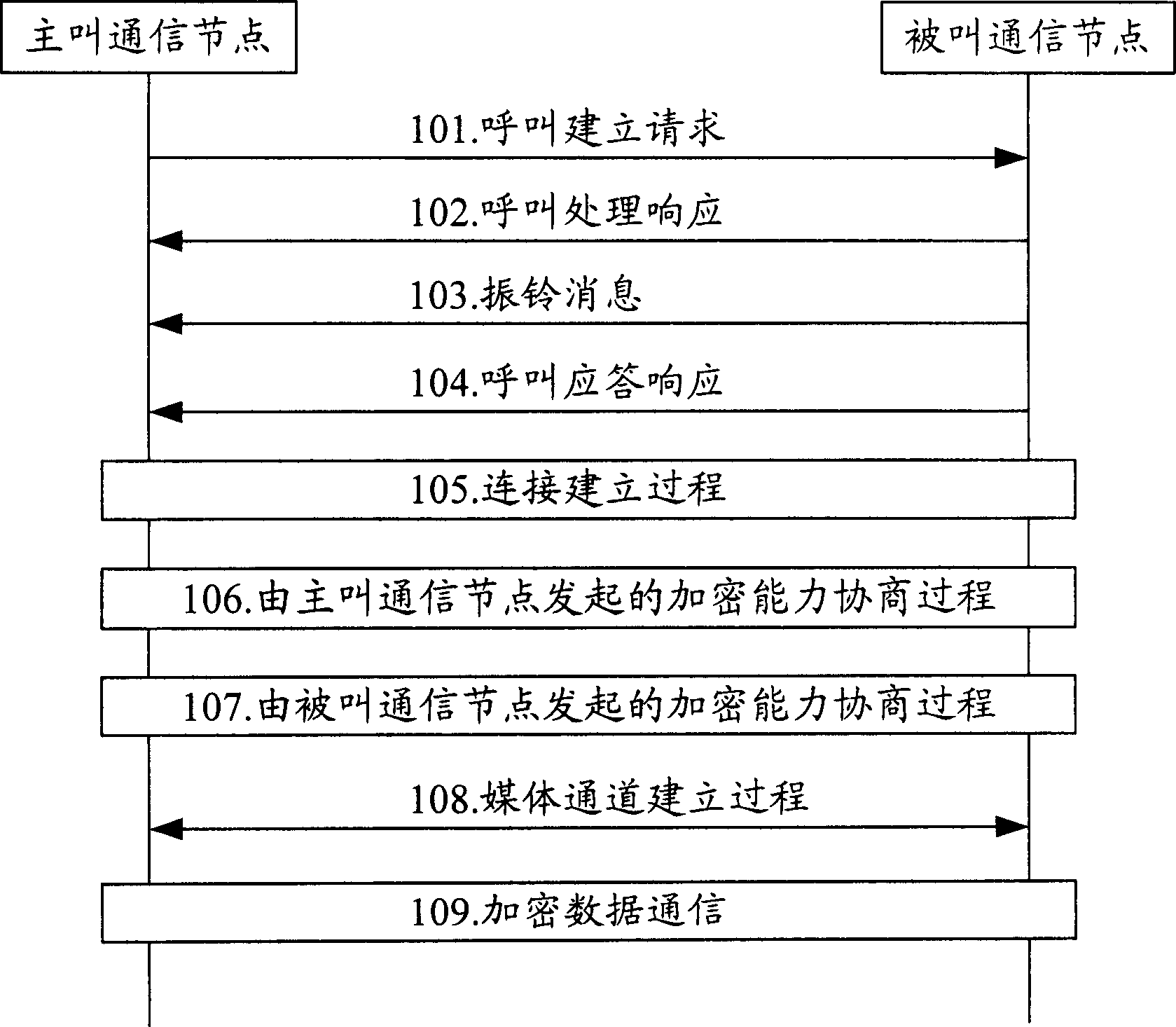
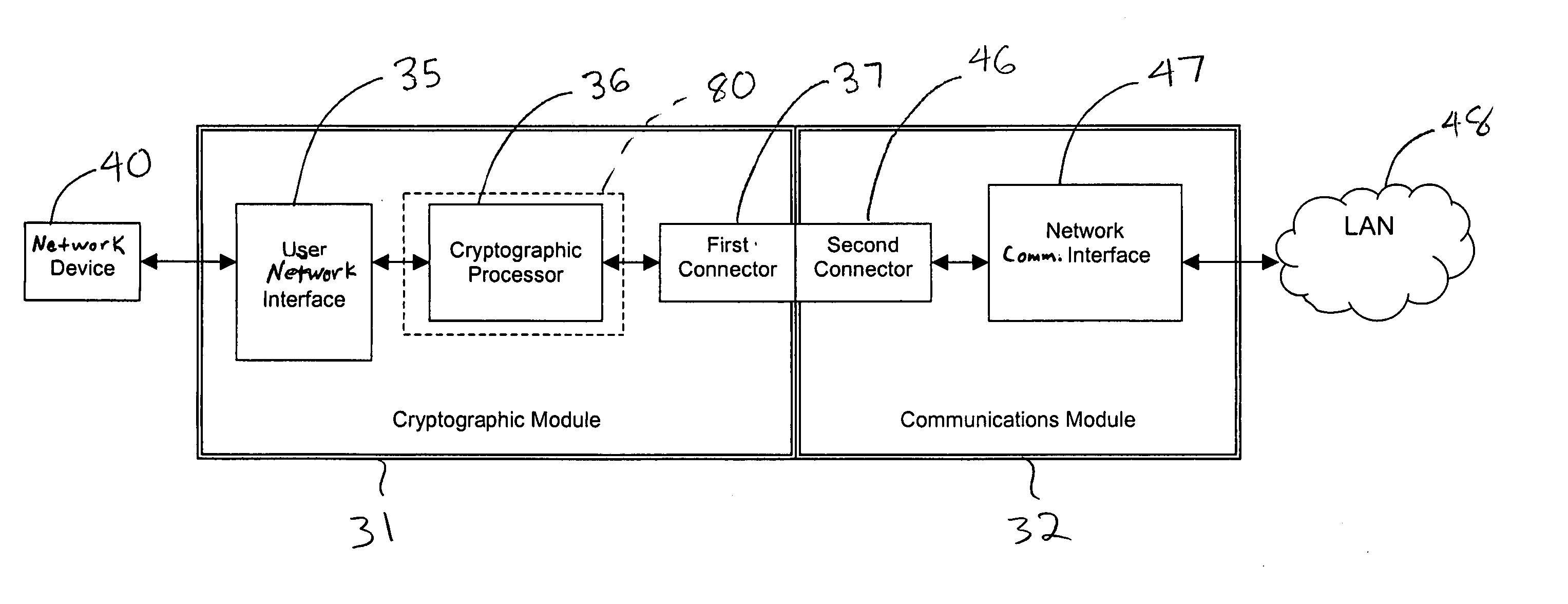
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
61results about "Securing communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
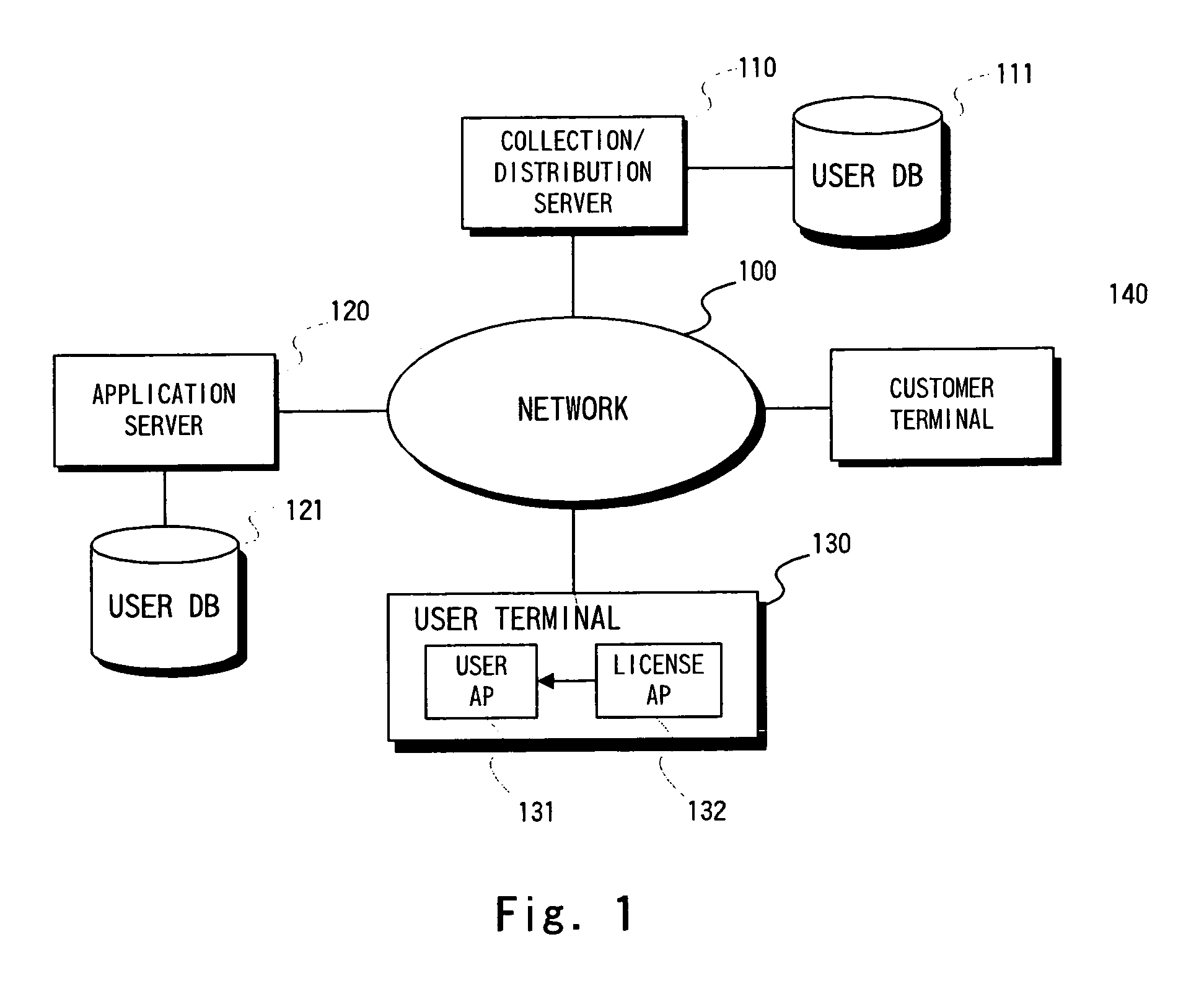
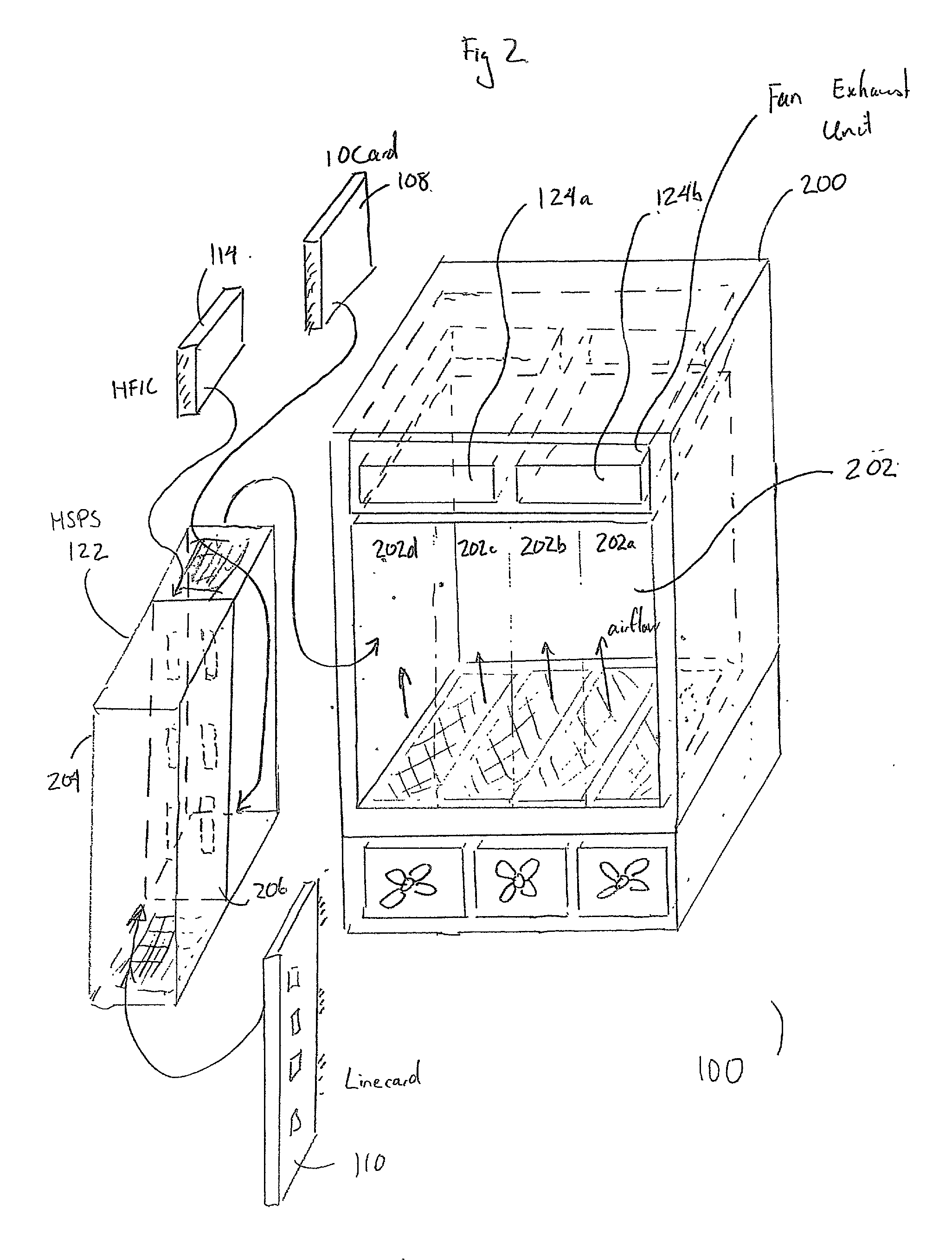
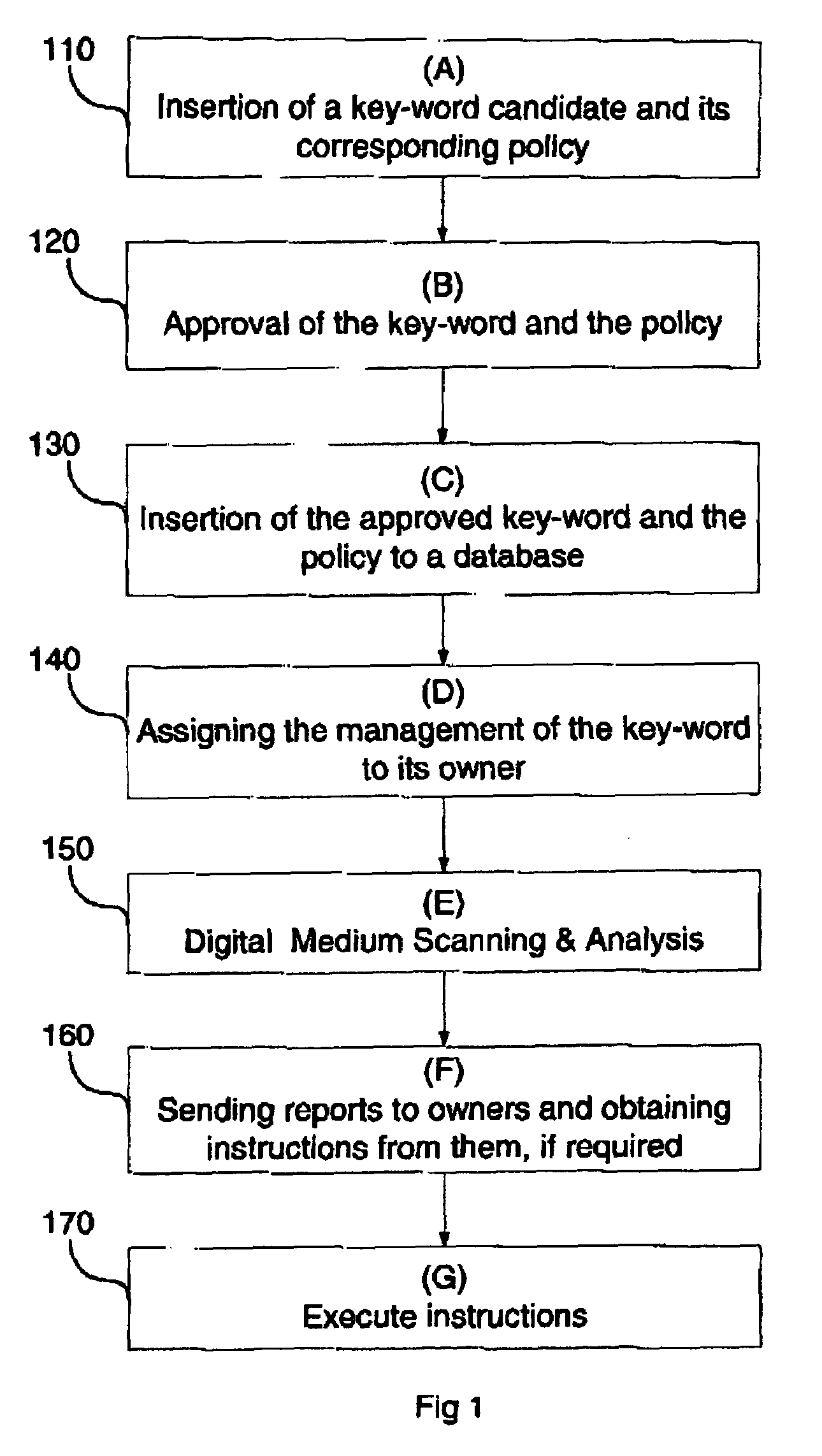
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
File sharing system with data mirroring by storage systems
InactiveUS7281032B2Reduce CPU loadLoad balancingData processing applicationsMultiple digital computer combinationsClustered file systemFile system
A system for optimizing data access is provided. The system includes a cluster file system server, a number of cluster file system clients, and a storage system. The storage system includes disk drives organized as paired master disk drive and one or more mirrored disk drives having copies of the data stored on the master disk drive. When a file is needed, the server determines which pair has the needed file, and then determines which disk drive within the pair should be accessed. The determination is made to balance the access load within the pair, and can select to retrieve the file from the drive which is least frequently accessed. The identification of the disk drive to be accessed is then forwarded to the client thereby allowing the client to access the appropriate disk drive to retrieve the file.
Owner:HITACHI LTD
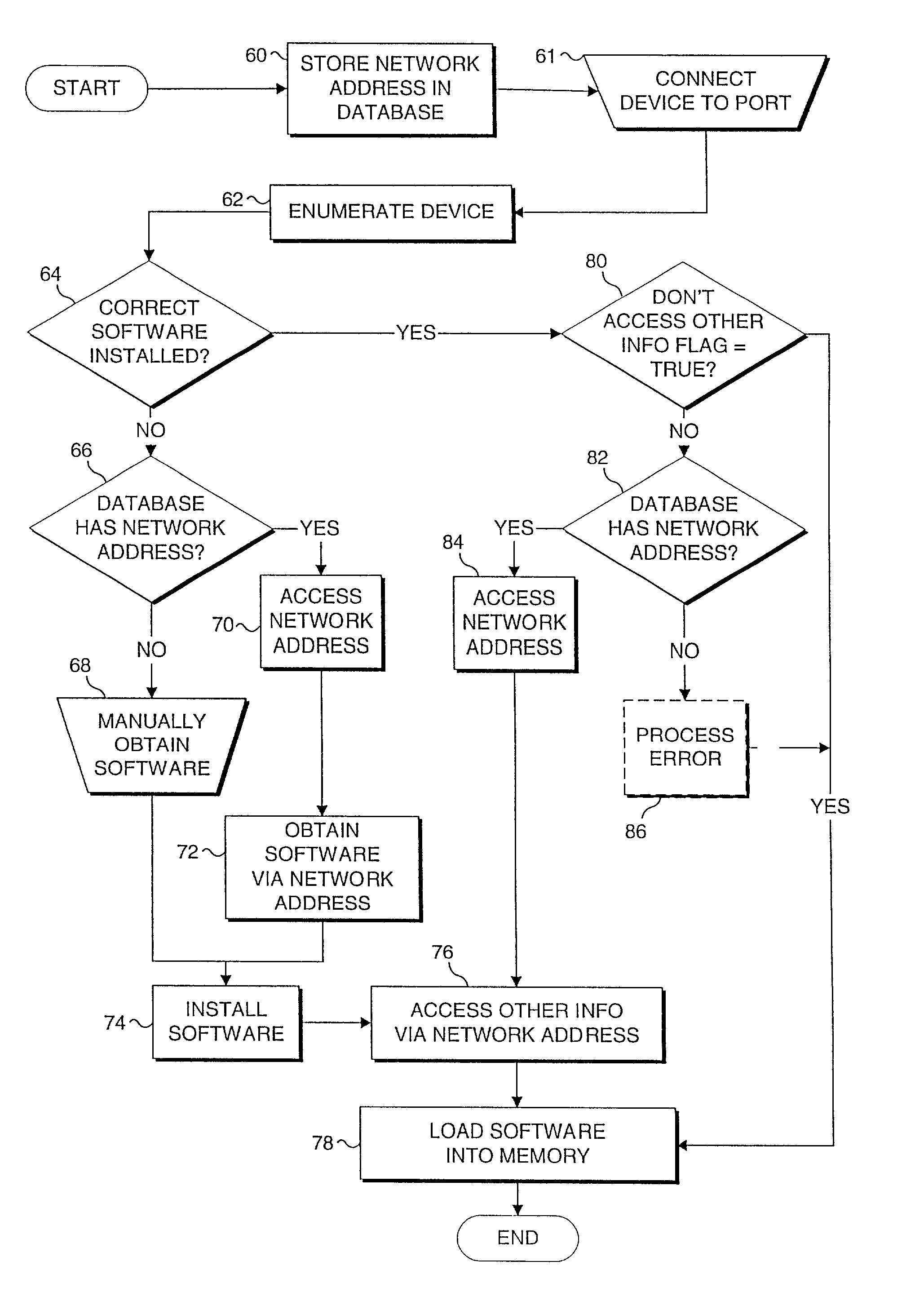
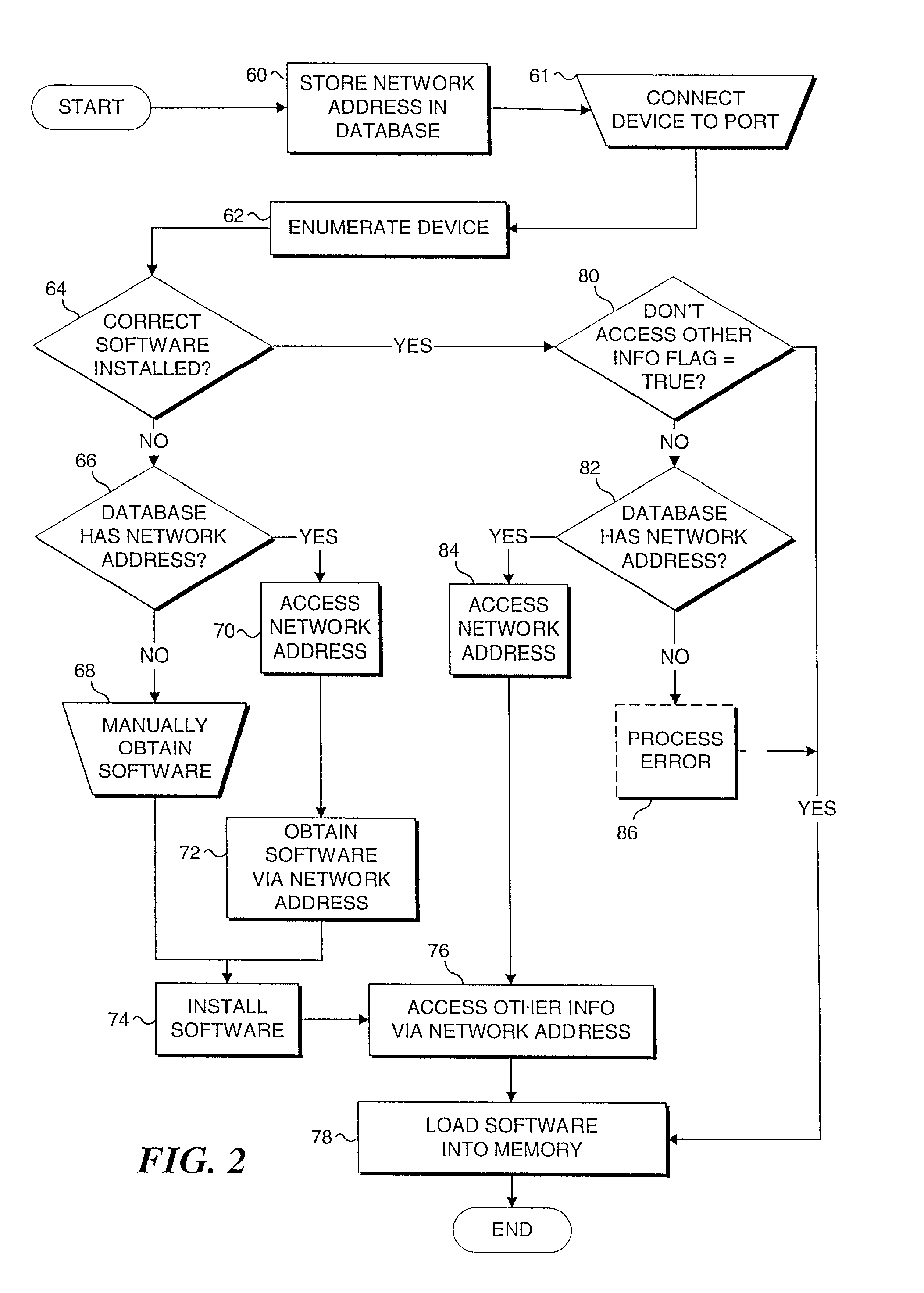
Method and system to access software pertinent to an electronic peripheral device at an address based on a peripheral device identifier
InactiveUS7076536B2Digital computer detailsProgram loading/initiatingNetwork addressingNetwork address
Owner:MICROSOFT TECH LICENSING LLC
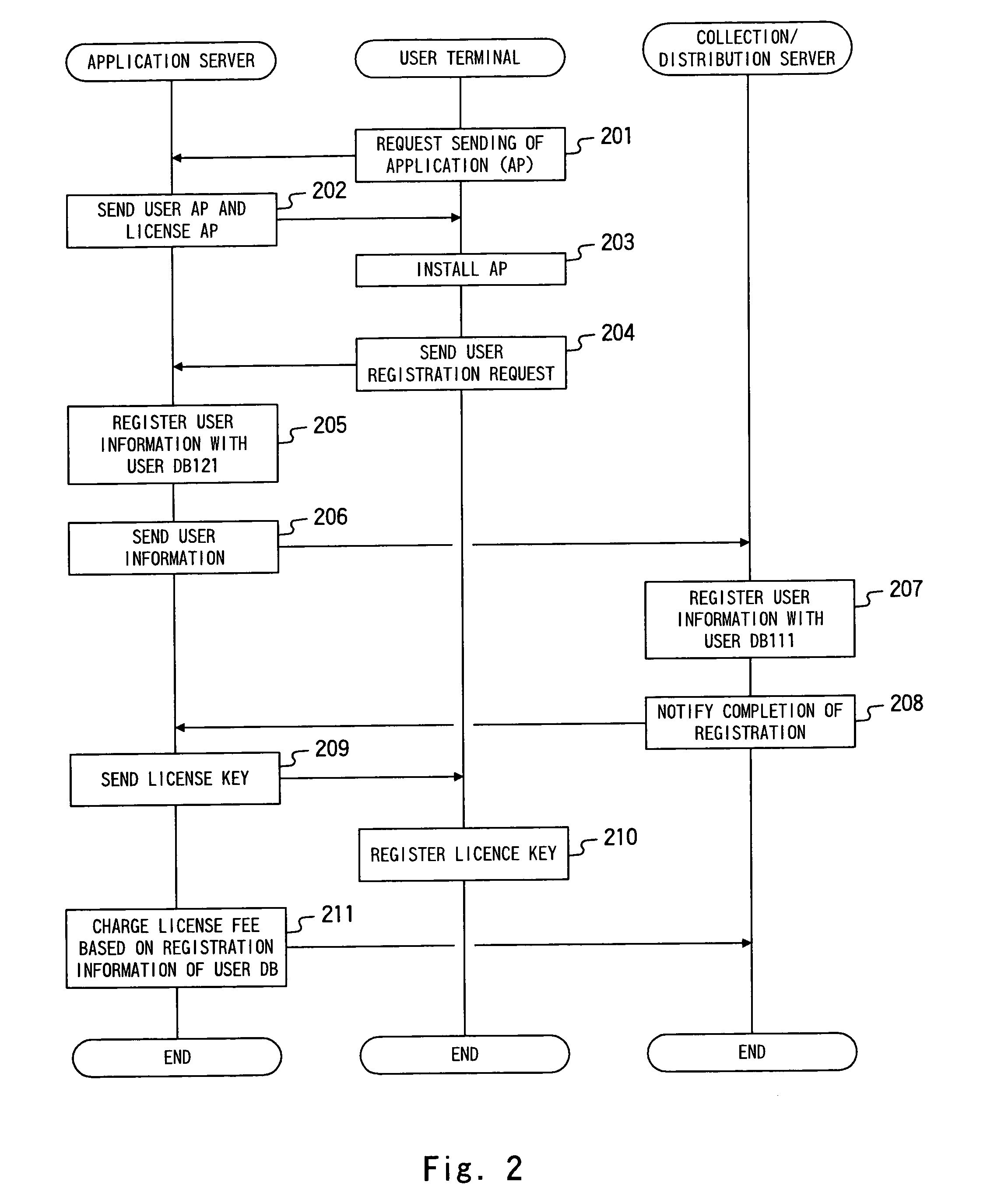
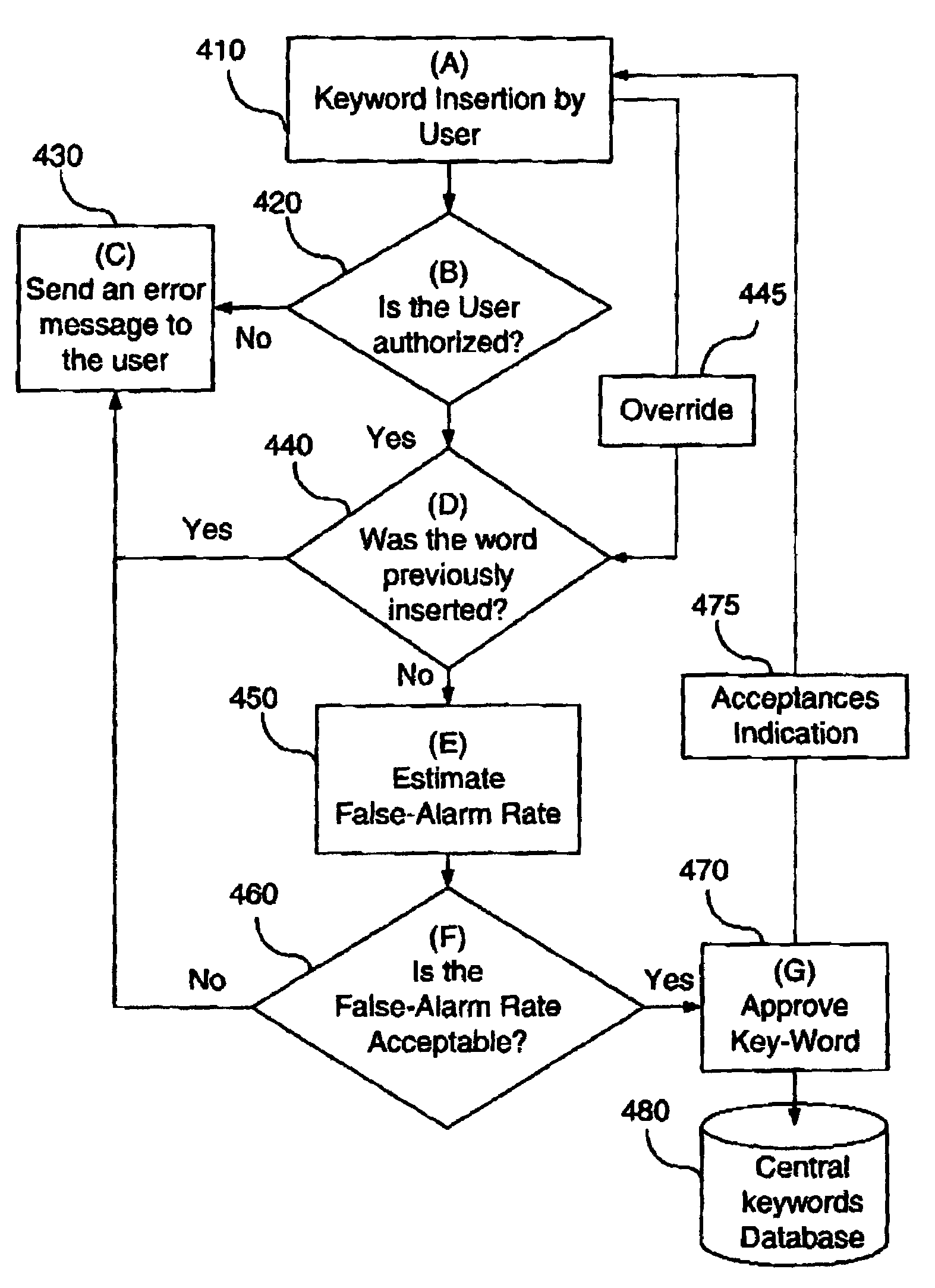
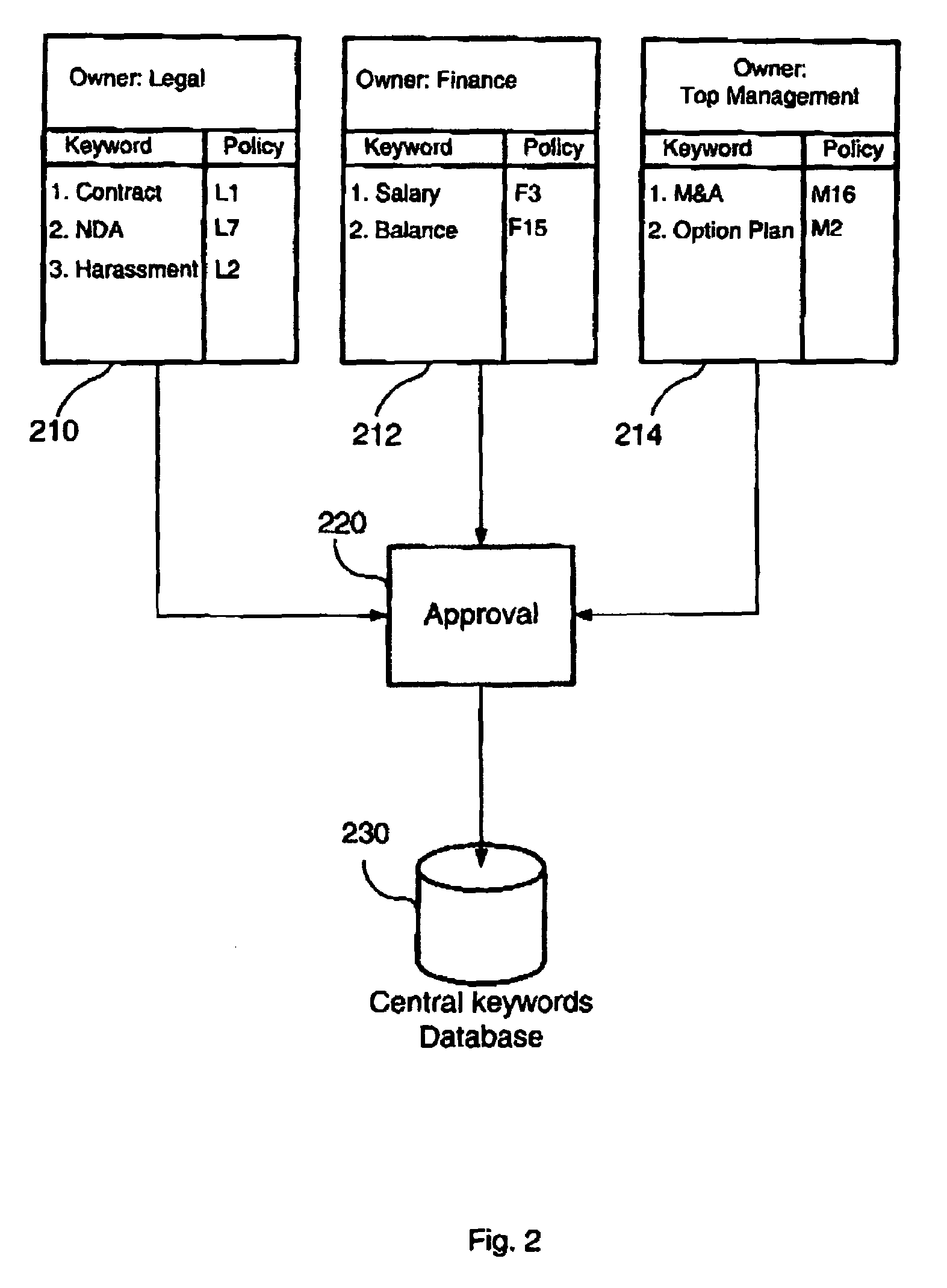
Method, device and system for securing payment data for transmission over open communication networks
ActiveUS20130191290A1Minimize the numberOpportunities decreasePoint-of-sale network systemsSecuring communicationData connectionPayment
A method for securing payment data for transmission over open communication networks is disclosed. The method comprises establishing a data connection between a first and a second transceiver device, the first transceiver device configured as a merchant device and the second transceiver device configured as a customer transceiver device. The merchant device transmits a first data package which comprises a unique merchant identifier and transaction request data, to the customer transceiver device over the data connection. The merchant device receives a cryptogram from the customer transceiver device. The cryptogram having been generated from using a secret key and a counter value together with the received unique merchant identifier and the transaction request data. The method comprises forming an authorisation request comprising the received cryptogram, merchant identifier and the transaction request data and submitting said authorisation request to at least one of an issuer and an acquirer to facilitate authorisation and processing of said transaction request data.
Owner:BLUECHAIN PTY LTD
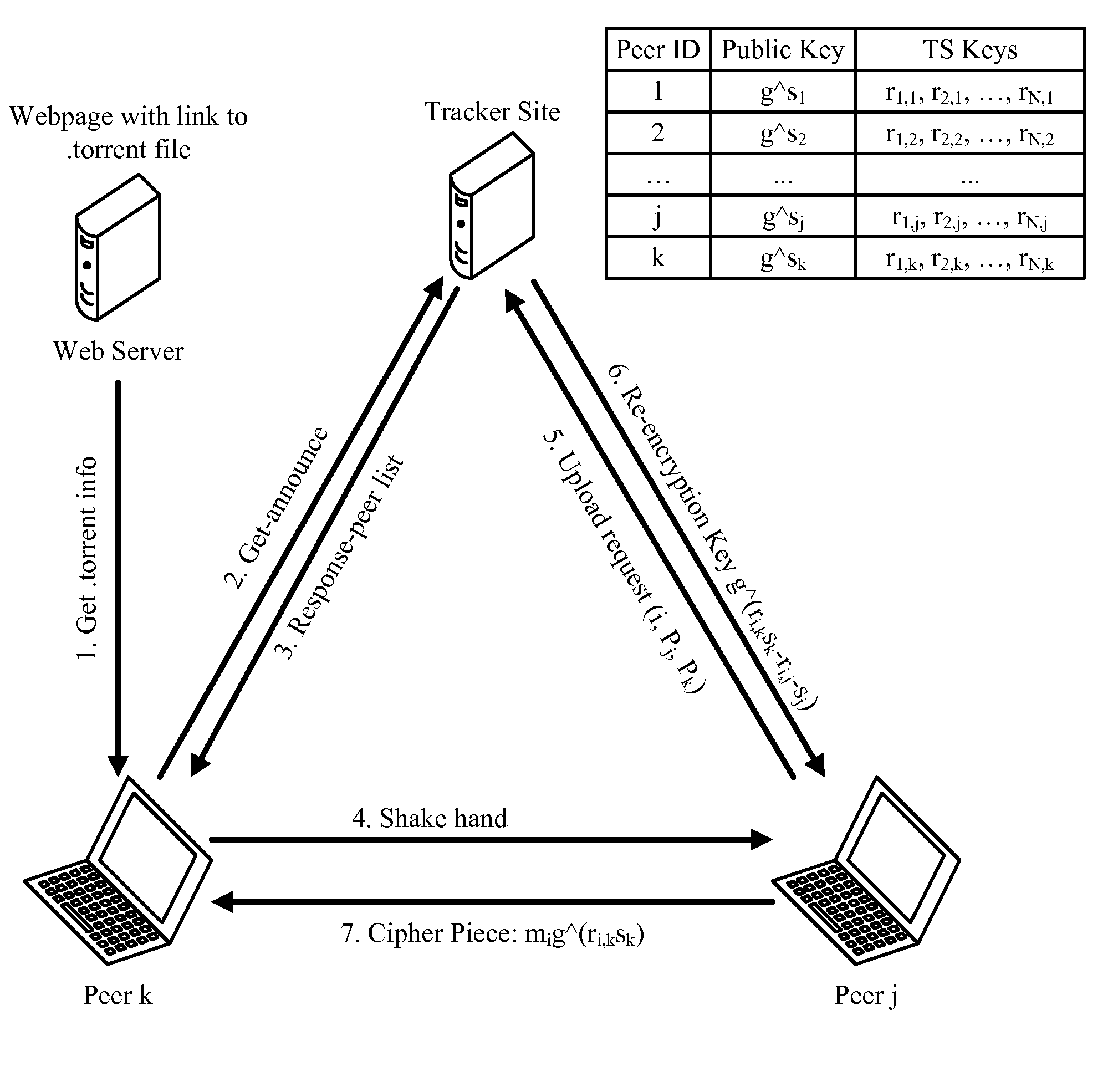
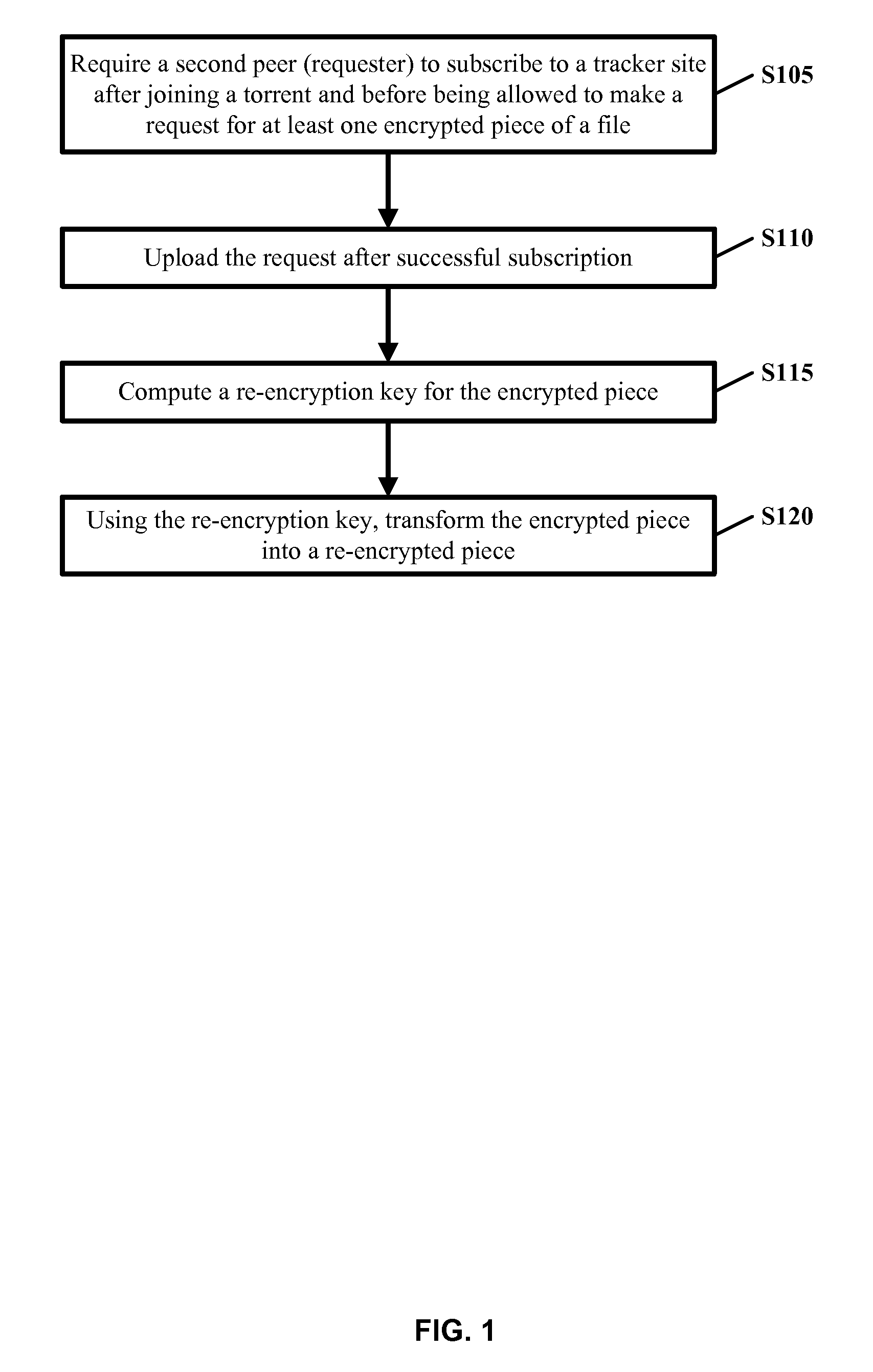
Digital Rights Protection in BitTorrent-like P2P Systems
Owner:GEORGE MASON INTPROP INC
Adaptive device-initiated polling
InactiveUS20070078976A1Error preventionFrequency-division multiplex detailsSelf adaptiveEnterprise system
A method includes periodically sending a polling call to an enterprise system outside the firewall at a first polling rate during normal operating conditions, monitoring for a fault condition, periodically sending polling calls to the device outside the firewall at a second polling rate when a fault condition is detected, the second polling rate being higher than the first polling rate. The second polling rate is used as result of a fault condition. The method also includes sending a problem report with the polling calls when the fault condition is detected.
Owner:PARAMETRIC TECH CORP
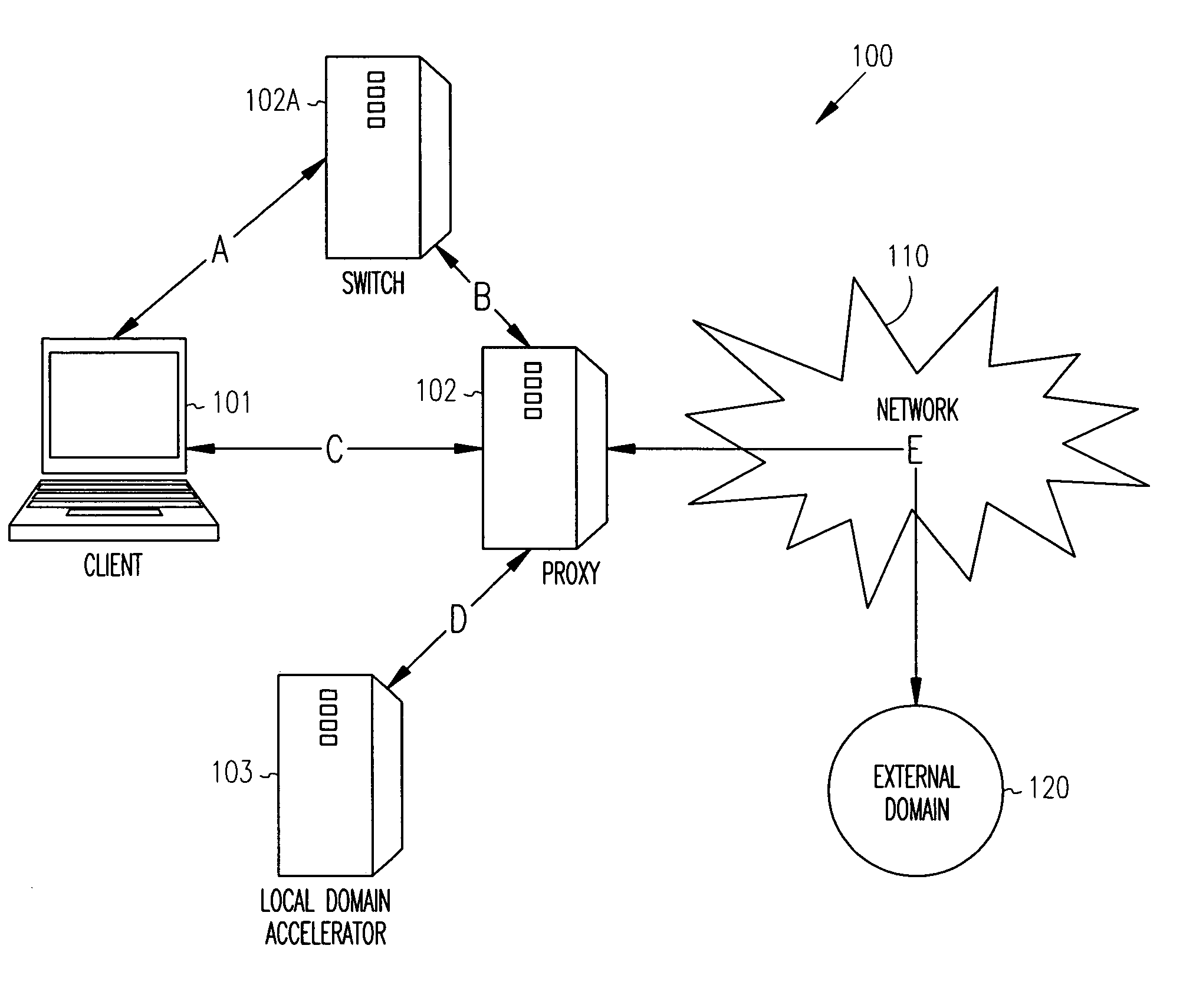
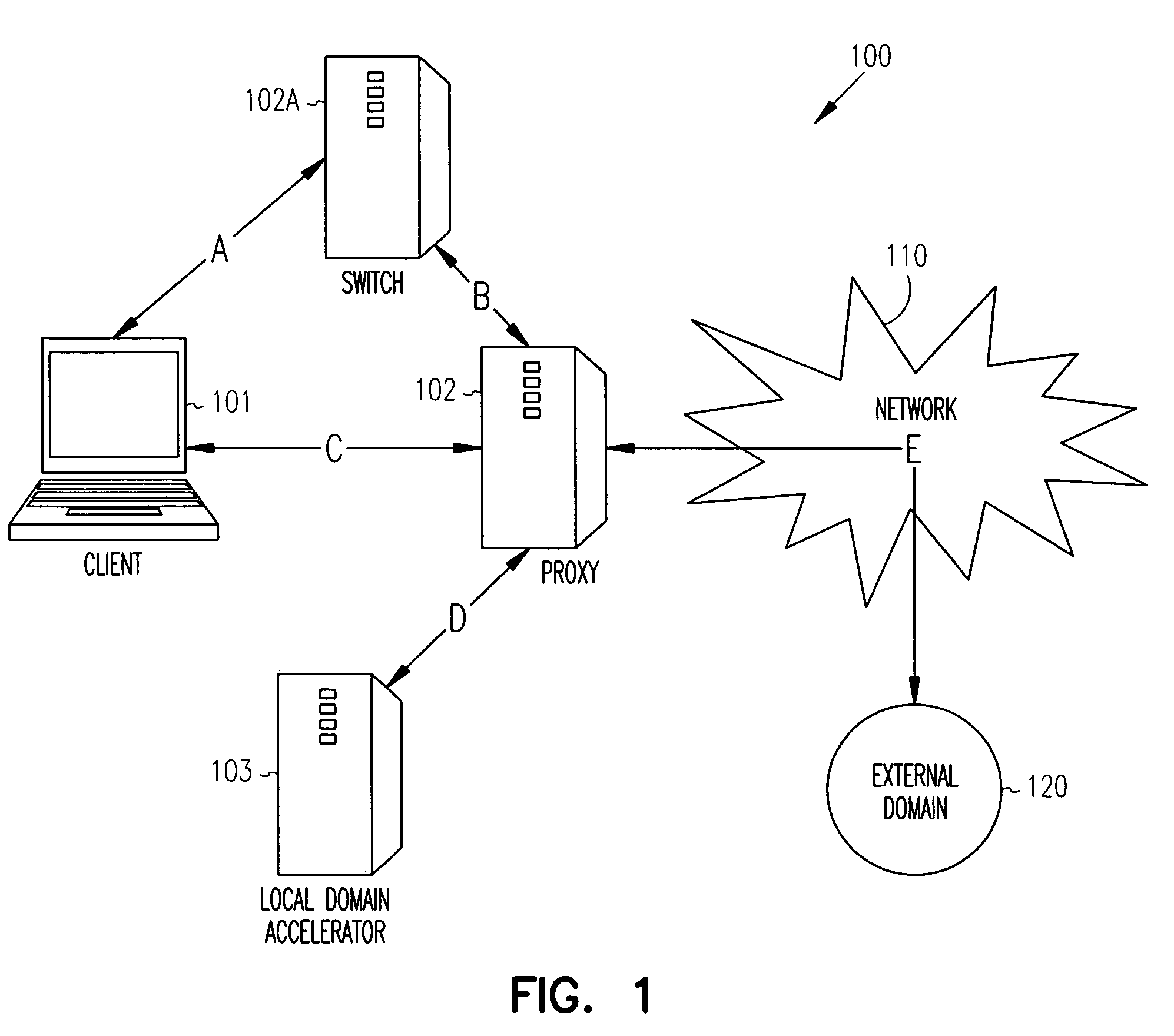
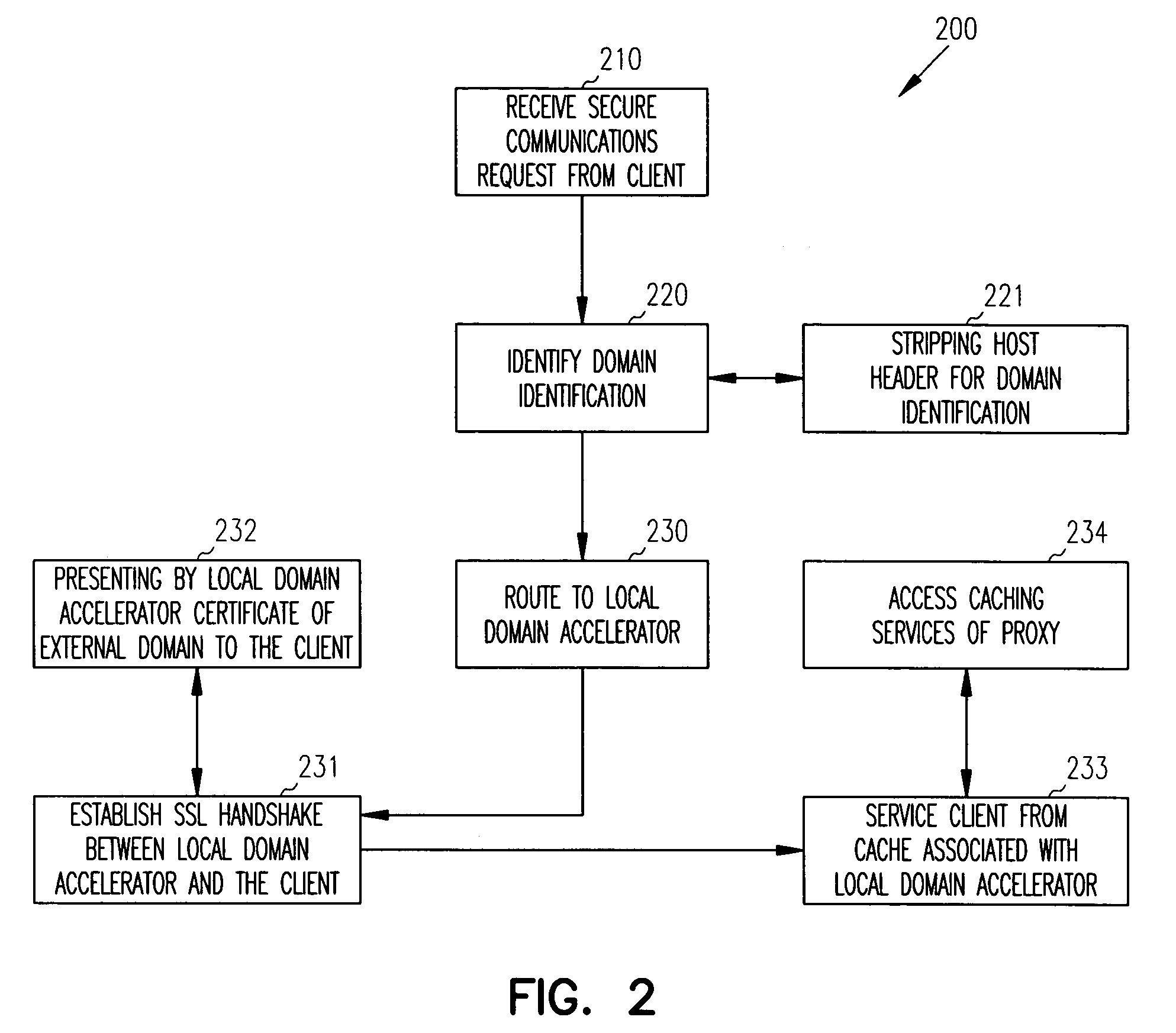
Techniques for securely accelerating external domains locally
InactiveUS7904951B1Multiple digital computer combinationsProgram controlSecure communicationInternet privacy
Owner:RPX CORP
System, communication network and method for transmitting information
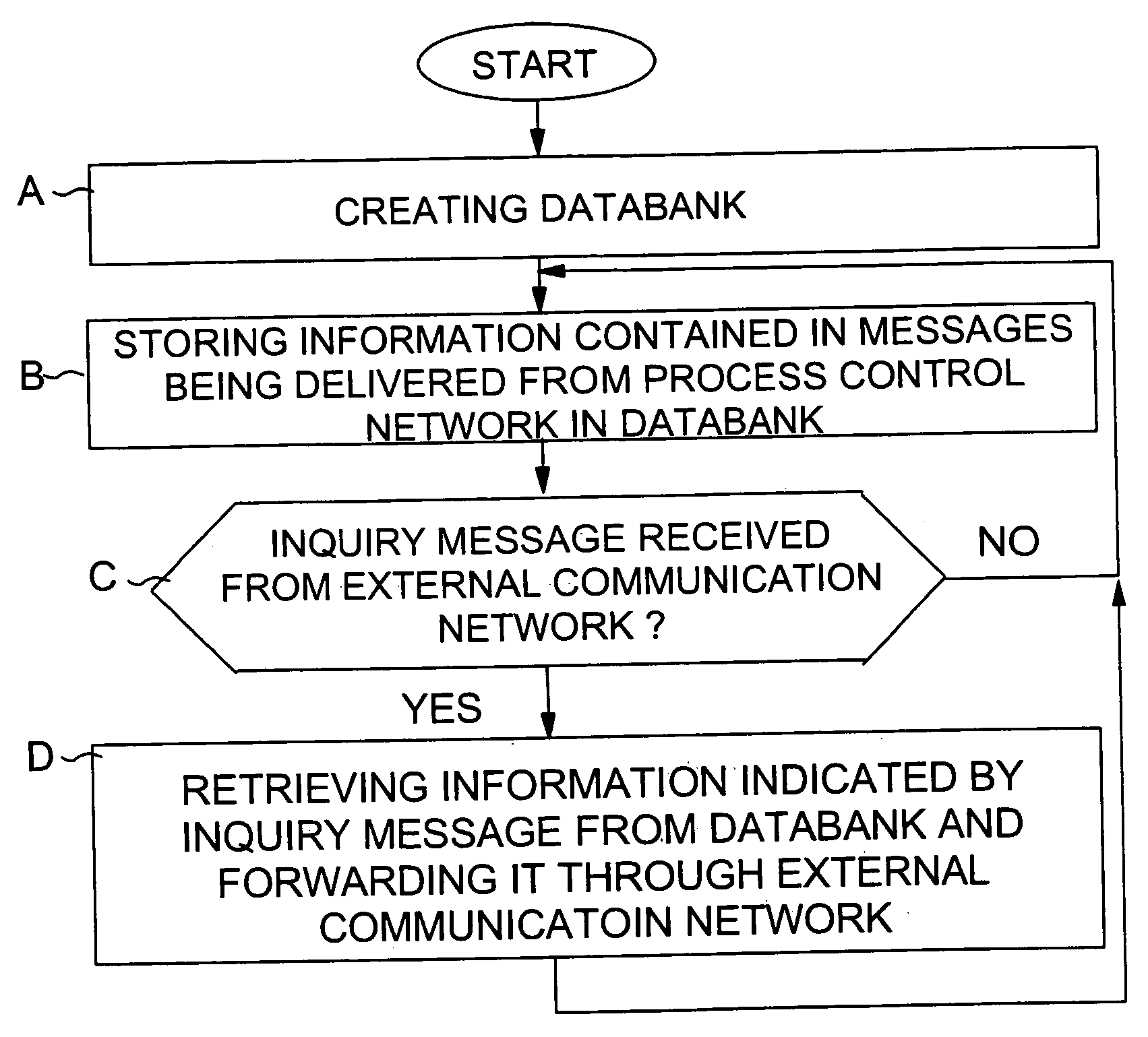
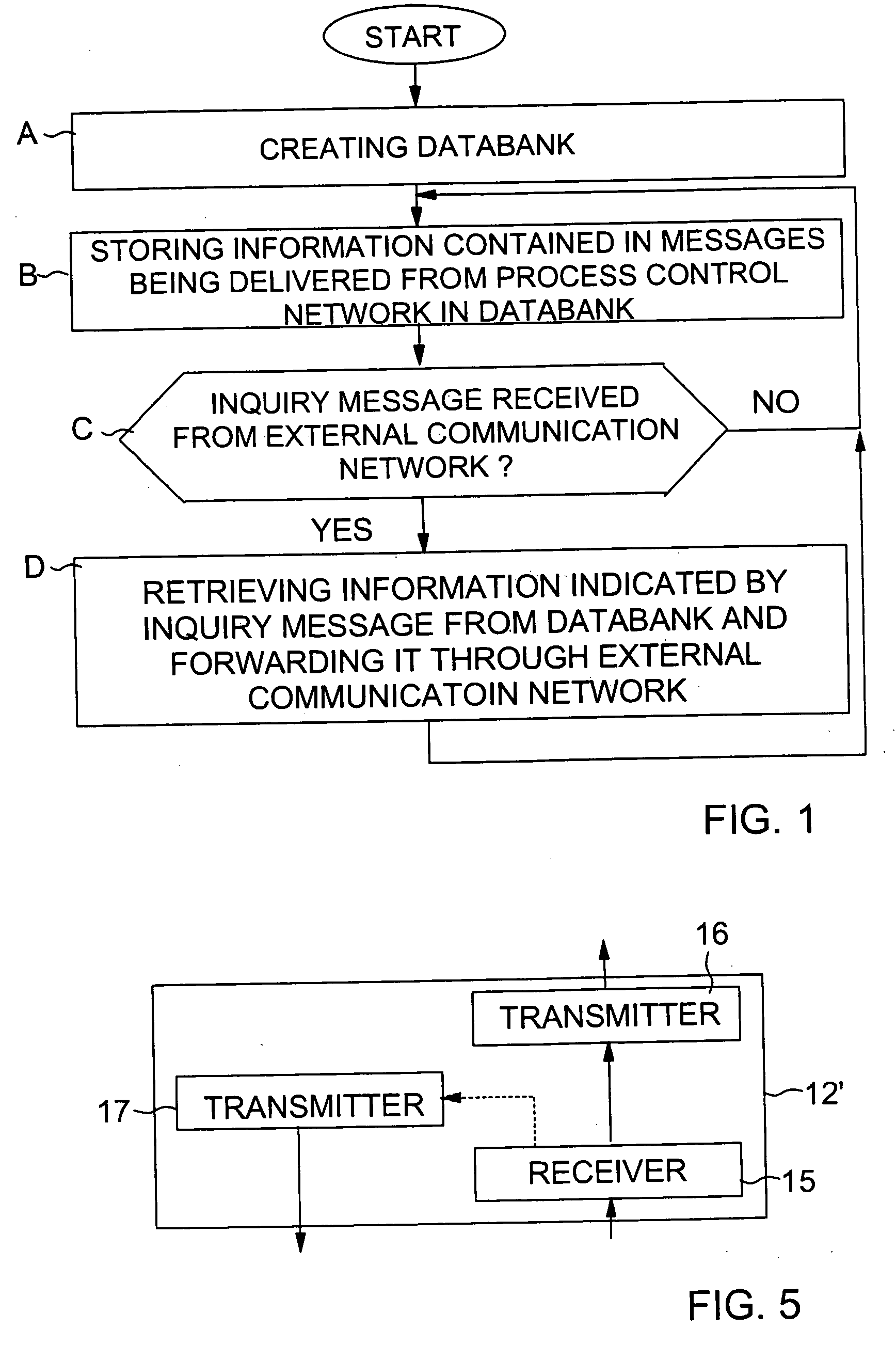
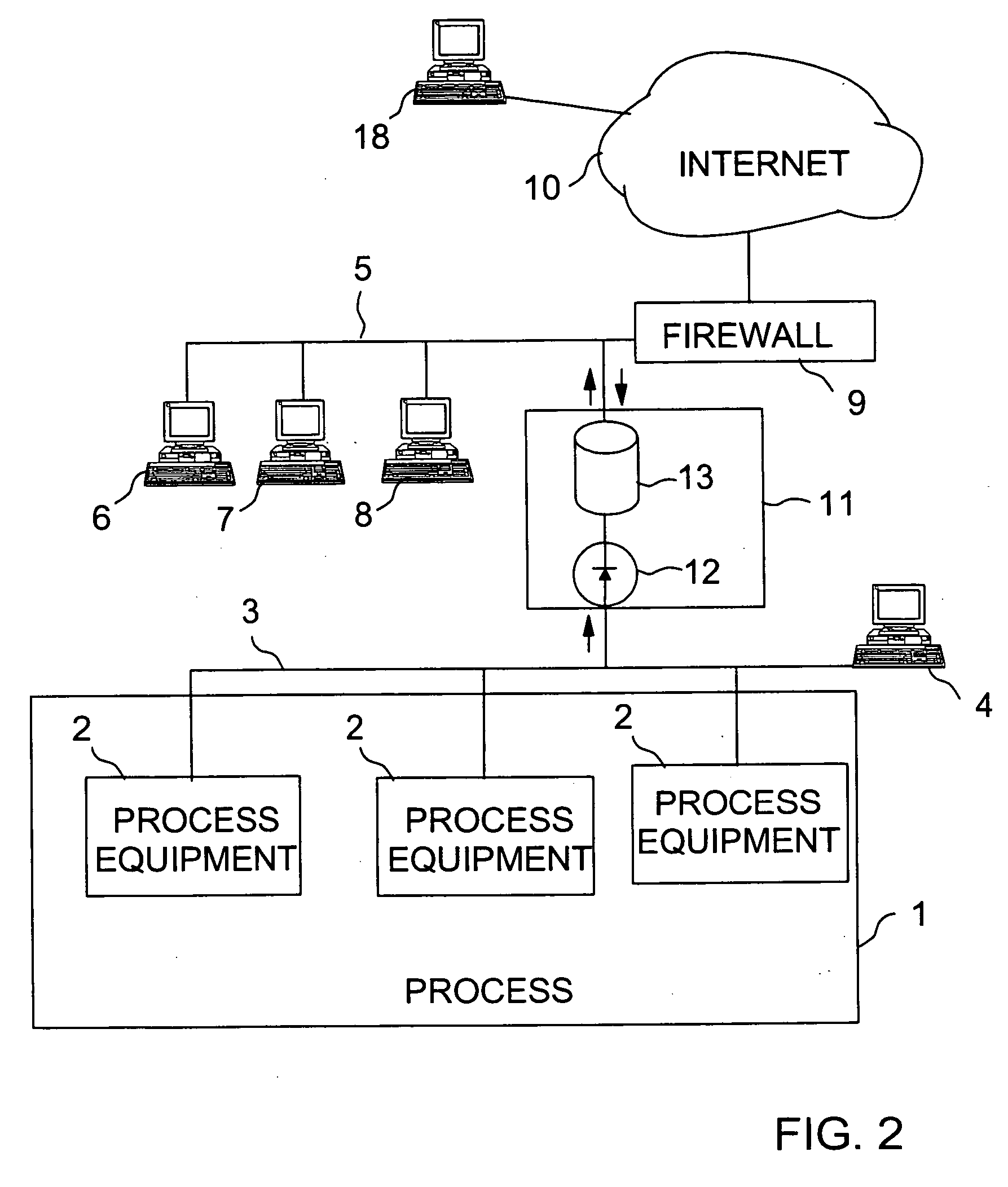
InactiveUS20050165939A1Control safetyProgramme controlComputer controlProcess control networkProcess equipment
Owner:METSO AUTOMATION OY
System and data structure for account management
InactiveUS20050187881A1Convenient and efficient accessPayment architectureOffice automationRelevant informationDecision taking
Owner:ACCENTURE GLOBAL SERVICES LTD
Systems, methods and computer program products for administration of computer security threat countermeasures to a computer system
InactiveUS20050039046A1Memory loss protectionDigital data processing detailsCountermeasureOperational system
Owner:TREND MICRO INC
Malware detection system with contextual analysis
ActiveUS10581874B1Improve accuracyDecrease positive outcomeComputer security arrangementsSecuring communicationEngineeringMalware
A computerized method for detecting malware associated with an object. The method includes operations of analyzing an object to obtain a first set of attributes, where the first set of attributes include one or more characteristics associated with the object. Furthermore, the object is processed with a virtual machine to obtain a second set of attributes. The second set of attributes corresponds to one or more monitored behaviors of the virtual machine during processing of the object. Thereafter, a threat index is determined based, at least in part, on a combination of at least one attribute of the first set of attributes and at least one attribute of the second set of attributes. The threat index represents a probability of maliciousness associated with the object.
Owner:FIREEYE SECURITY HLDG US LLC
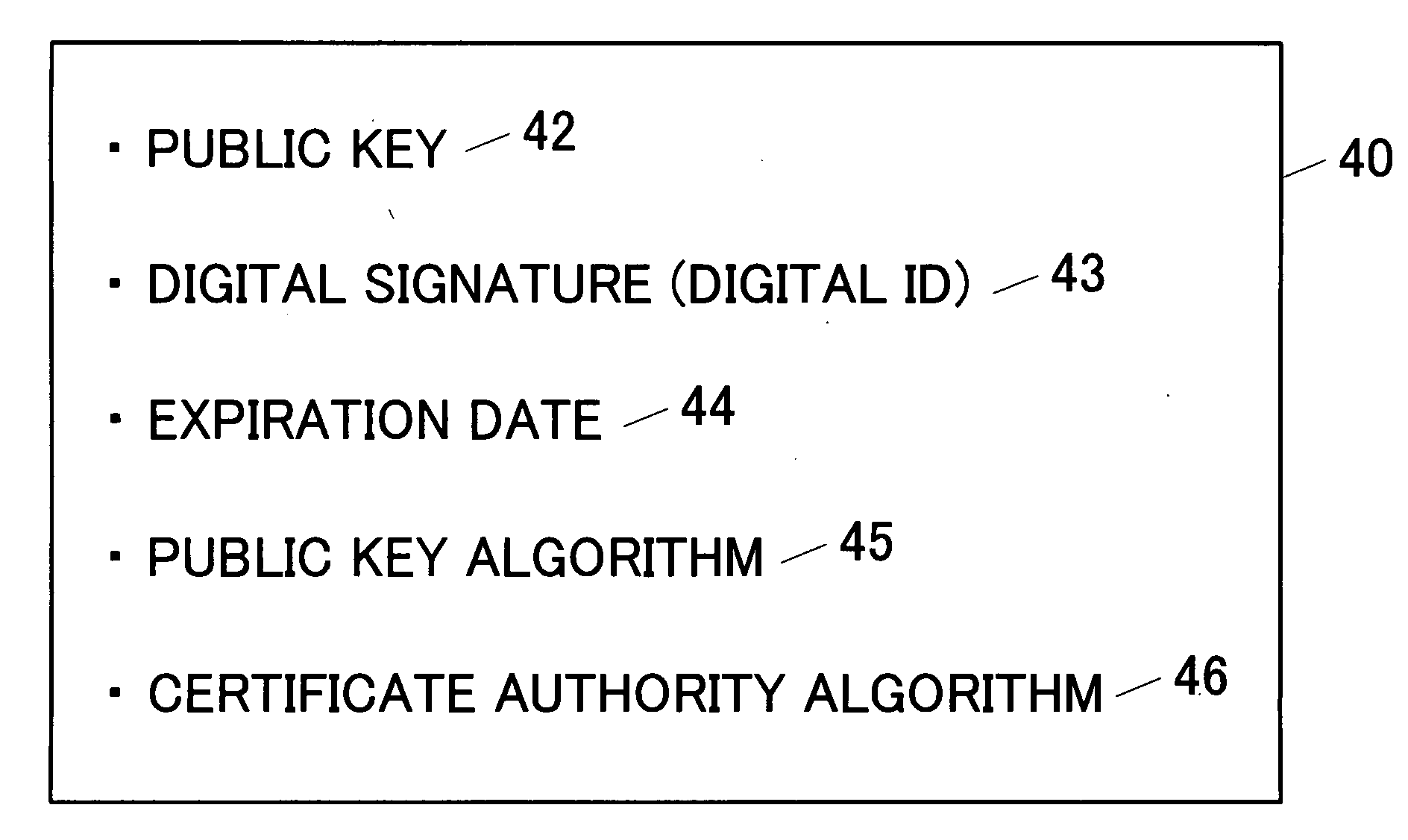
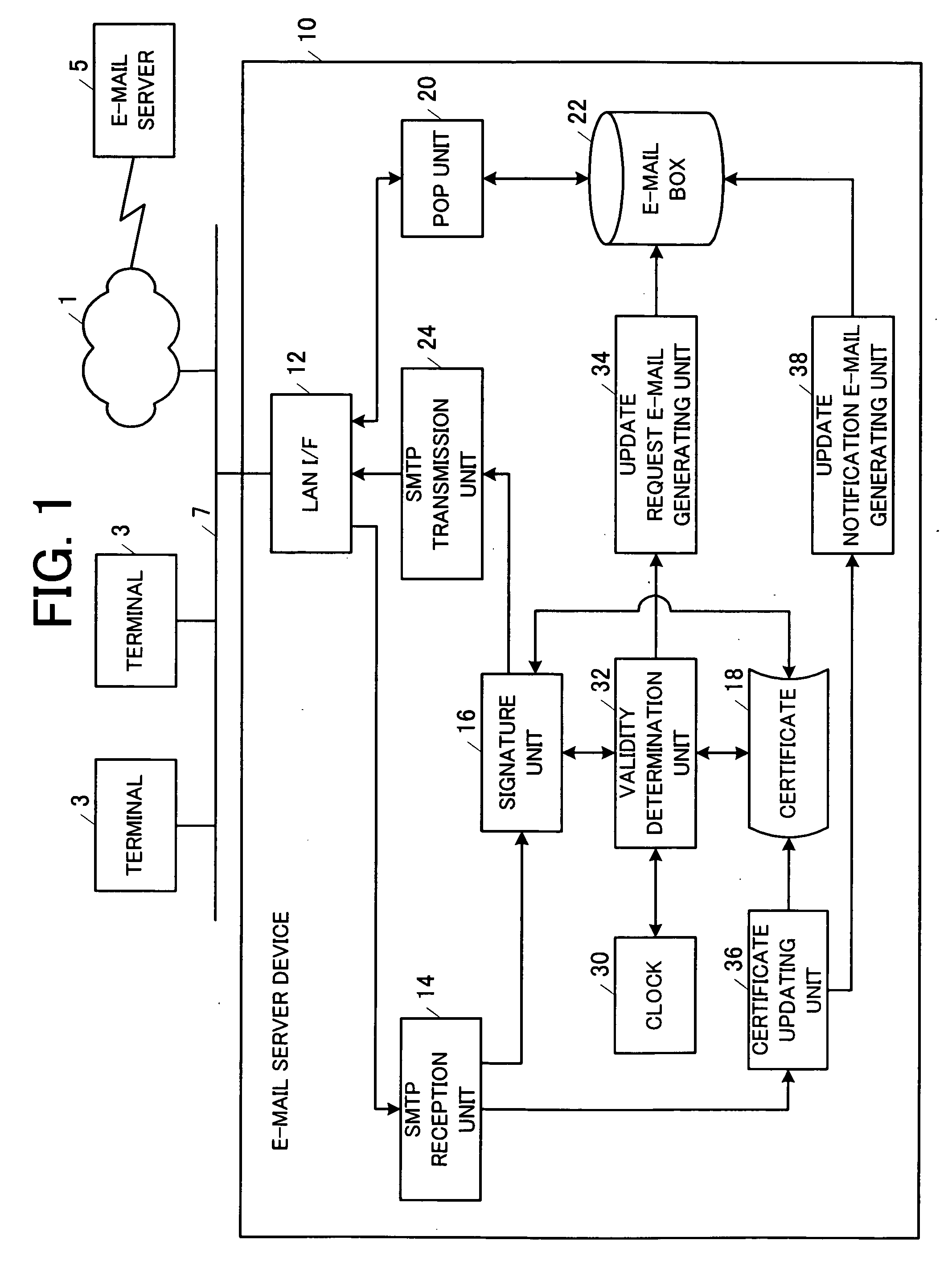
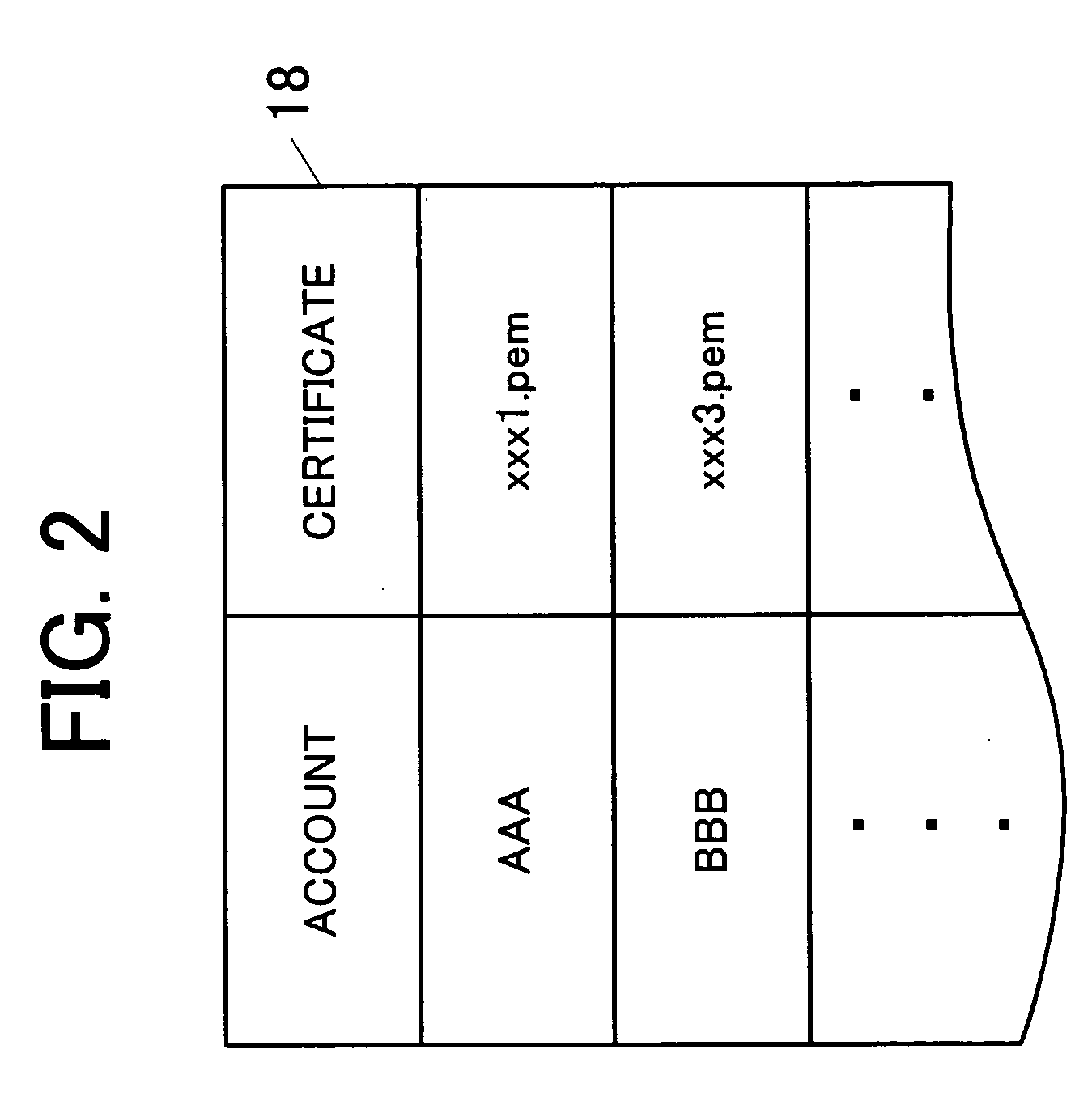
E-mail server device and certificate management method of the e-mail server device
InactiveUS20060259762A1Facilitate performance improvementsHigh reliability and safetyData switching networksSecuring communicationDigital signatureComputer science
Owner:MURATA MASCH LTD
Distributed processing system, method of the same
InactiveUS7031944B2Increase valueResource allocationMultiple digital computer combinationsApplication serverComputer terminal
Owner:NEC CORP
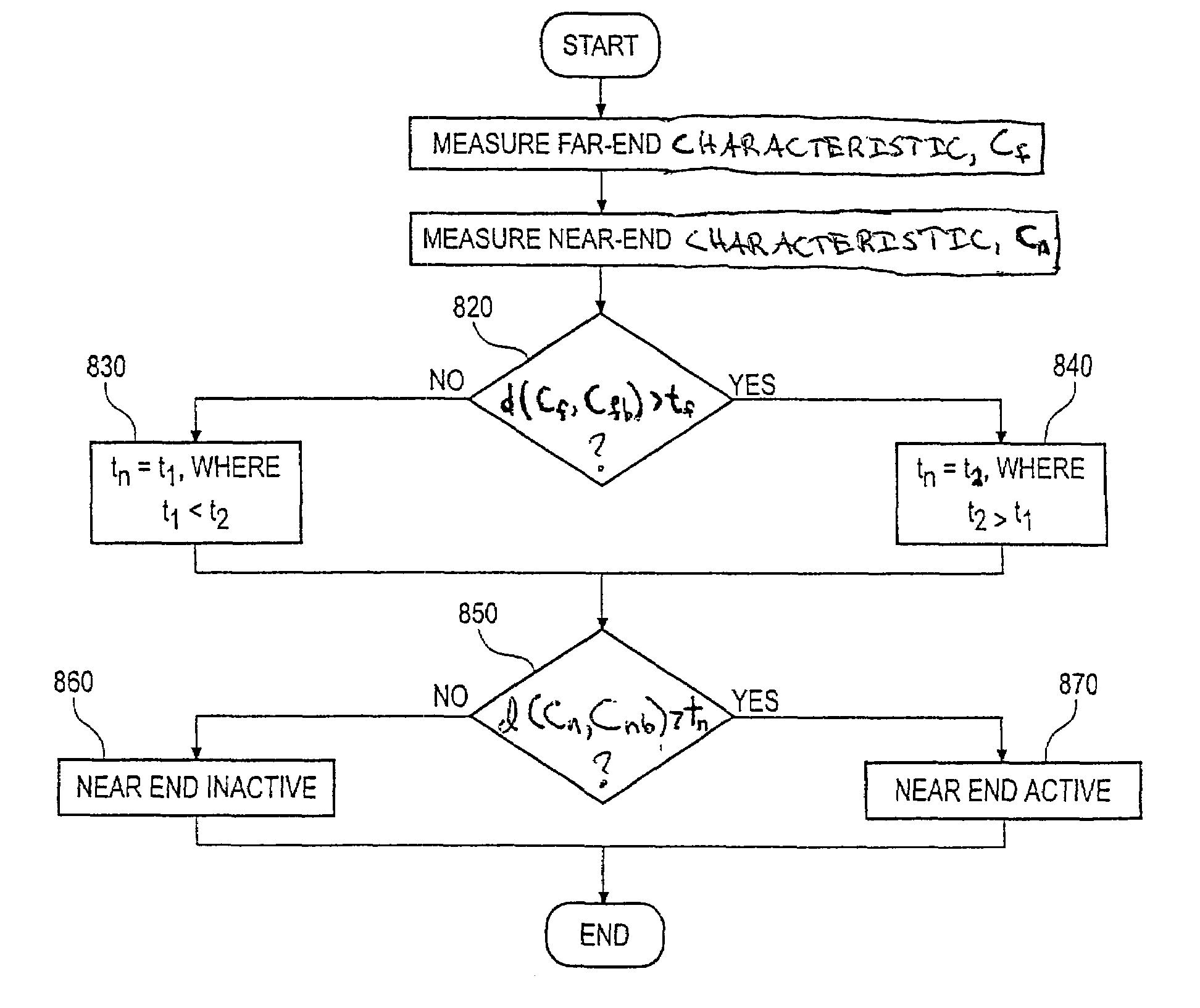
Voice activity detection based on far-end and near-end statistics
InactiveUS7263074B2Improve the level ofLower levelBroadband local area networksTime-division multiplexCommunications systemProximal point
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and Method for Detecting and Evicting Malicious Vehicles in a Vehicle Communications Network
ActiveUS20110214178A1Improve performanceReduce impactMemory loss protectionError detection/correctionMathematical modelSimulation
In a vehicle communication network, some vehicles may be used by attackers to send false information to other vehicles which may jeopardize the safety of other vehicles. Vehicles should be able to detect malicious communications activities and to mitigate the impact of malicious vehicles by evicting (eliminating) suspected malicious vehicles from the system. Evicting a vehicle is to ignore the messages sent from the vehicle for a specified time period. Voting and sacrifice principles are combined using a mathematical model based on the “Mafia Game”. The Mafia Game model focuses on the relative size of the group of attackers within a neighborhood necessary to dominate the entire network in the neighborhood (i.e., to eventually evict all the innocent vehicles).
Owner:PERSPECTA LABS INC
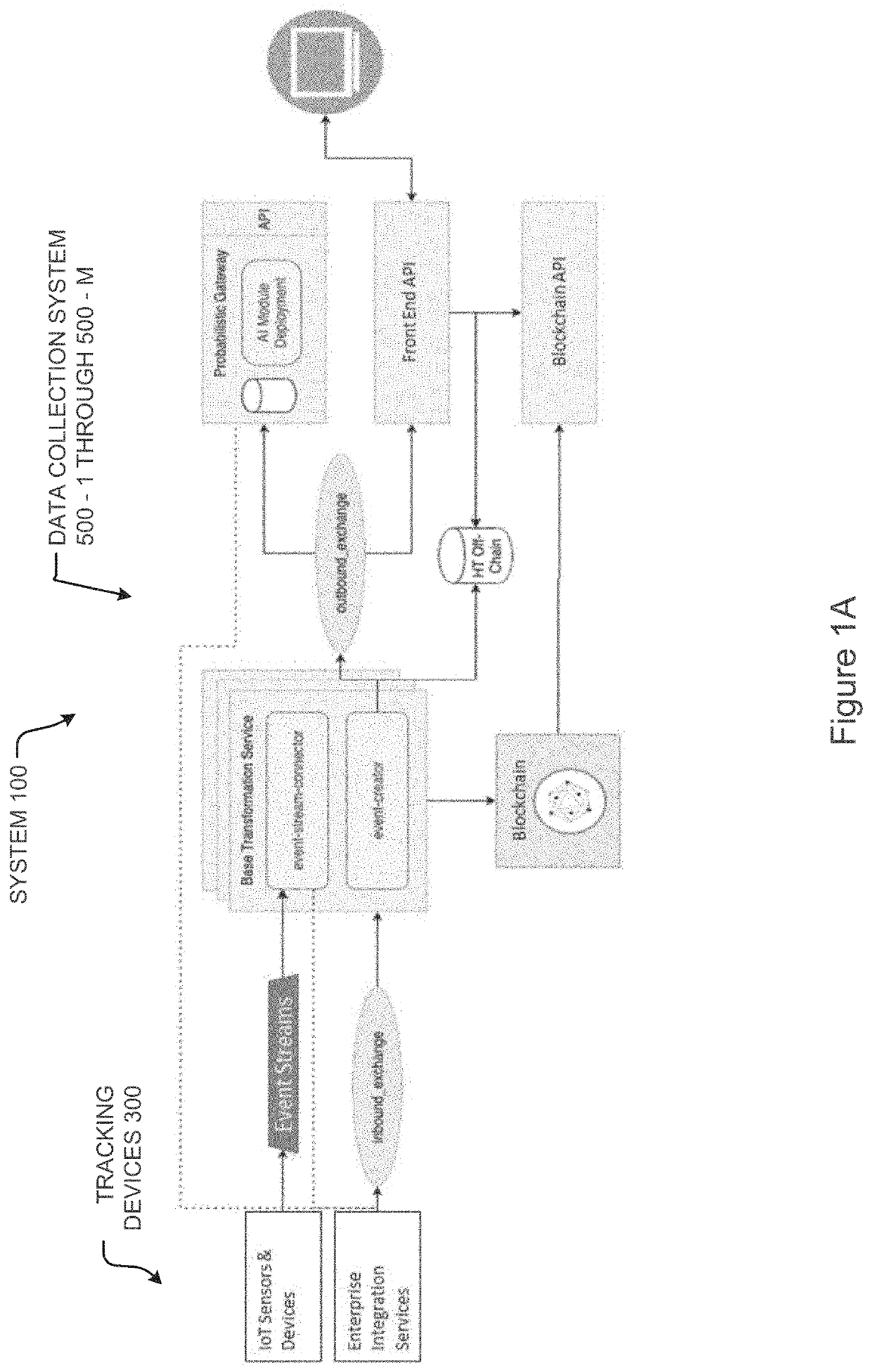
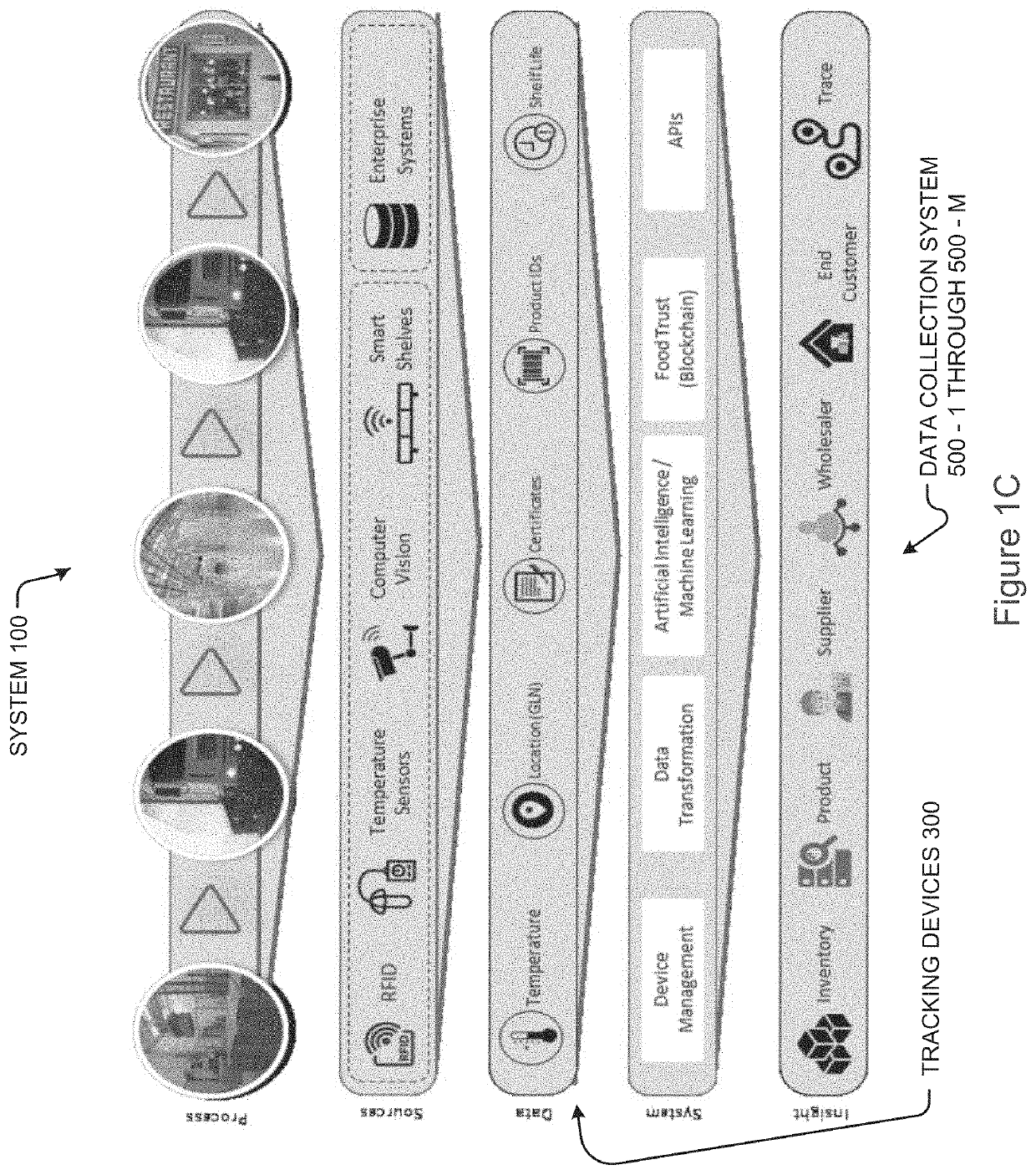
System, device, and process for tracking product
Owner:GOLDEN STATE FOODS CORP
Information processing system, method, and apparatus, and program
InactiveUS20070286423A1Unauthorized memory use protectionHardware monitoringInformation processingKey generator
Disclosed herein is an information processing system including: a first information processing apparatus for transmitting a content including video and audio signals; and a second information processing apparatus for receiving the content. The first apparatus includes: a first key generator configured to generate a first key; a video encryptor configured to encrypt the video signal with the first key; an audio encryptor configured to encrypt the audio signal with the first key; and a transmitter configured to transmit the content including the encrypted video and audio signals. The second apparatus includes: a receiver configured to receive the content; a second key generator configured to generate a second key corresponding to the first key; a video decryptor configured to decrypt the encrypted video signal with the second key; and an audio decryptor configured to decrypt the encrypted audio signal with the second key.
Owner:SONY CORP
Encryption method, decryption method, and corresponding device and system
InactiveCN102726028APrevent leakageImprove securityInternal/peripheral component protectionSecuring communicationComputer hardwareClient-side
Owner:HUAWEI TECH CO LTD
Method and network element for providing secure access to a packet data network
ActiveUS7574735B2Multiple digital computer combinationsProgram controlProtection mechanismSecurity association
Owner:NOKIA TECHNOLOGLES OY
A secure communication method of utilizing an amplitude to realize chaos synchronization
InactiveCN102170346AHigh speed transmissionGuaranteed transmission bandwidth utilizationSecuring communicationSynchronising arrangementSecure communicationBinary information
The invention discloses a secure communication method of utilizing an amplitude to realize chaos synchronization of the information security technology field, and the method is used for overcoming the disadvantages that the signal transmission rate in a CSK method is restricted by a synchronization time and the bandwidth utilization rate in a DCSK method is low. The method comprises the steps of modulating a chaos signal generated by a chaos system to generate a sending signal at a sending end, according to a binary information symbol value; recovering the chaos signal prior to the modulation by employing a chaos synchronization system at a receiving end; carrying out an operating of the recovered chaos signal prior to the modulation and the sending signal; and demodulating the binary information symbol value. By the secure communication method of utilizing the amplitude to realize chaos synchronization, a high-speed transmission of the information symbol is realized, meanwhile, the utilization rate of the transmission bandwidth is guaranteed.
Owner:NORTH CHINA ELECTRIC POWER UNIV
Wireless payment method between vehicles based on 5G communication network and system thereof
ActiveCN108307349AEnsure safetyImprove performanceCryptography processingParticular environment based servicesPaymentE communication
The invention relates to a wireless payment method between vehicles based on a 5G communication network. The method includes the steps that: a requesting vehicle sends a payment request to a base station; the base station retrieves vehicle information of a friend vehicle of the requesting vehicle based on the payment request; the base station encrypts the requesting information by using the vehicle information of the friend vehicle for broadcasting; the vehicle within the broadcast range of the base station decodes the broadcast information by utilizing the own vehicle information, the friendvehicle acquires the requesting information as a responding vehicle if the decoding is successful; the responding vehicle generates payment information based on the requesting information and sends the payment information to the base station, the base station sends the payment information to a payment platform, and the payment platform returns the payment result to the responding vehicle; the basestation assigns a D2D communication channel to the requesting vehicle and the responding vehicle, and the responding vehicle and the requesting vehicle communicate via the D2D communication channel.According to the invention, the communication between vehicles can be realized, and the security of payment can be ensured.
Owner:CHINA UNIONPAY
Method for realizing encryption communication
Owner:HUAWEI TECH CO LTD
Modular cryptographic device and coupling therefor and related methods
InactiveUS20050213762A1High level securityEasy to adaptData switching by path configurationSecret communicationComputer hardwareModularity
Owner:HARRIS CORP
File encryption operation method and file encryption operation system
ActiveCN102819702AImprove efficiencyImprove securityComputer security arrangementsSecuring communicationComputer hardwarePassword
The invention discloses a file encryption operation method and a file encryption operation system. The method comprises the steps of: receiving a file operation instruction; transferring an encrypted target file according to the file operation instruction; carrying out memory decryption on the encrypted target file according to key information corresponding to the encrypted target file, and operating the encrypted target file after memory decryption. According to the scheme disclosed by the invention, the password of the encrypted target file does not need to be manually input; opening and operating of the file can be achieved by decrypting the file without a manual operation, and the operating efficiency of the key information is improved. On the other hand, the encrypted target file is decrypted by the key information in the memory; the decrypted file is stored in the memory, and a permanent file is not generated, therefore, the password is not stolen by the others, and the operating security of the encrypted file is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Master-slave communications system and method for a network element
InactiveUS20030091059A1Error preventionFrequency-division multiplex detailsCommunications systemTelecommunications link
Owner:ALCATEL LUCENT SAS
Methods of authenticating a user for data exchange
A method of facilitating the exchange of data between a user having a computing device, and a remote entity, where a first connection has been established between the user and the remote entity, and where the user has associated data exchange information with an application on the computing device, the data exchange information defining properties of the data to be exchanged between the user and the remote entity. The method comprises establishing, at a server, a second connection to the computing device; enabling retrieval of a user authentication attribute associated with the data exchange information; enabling retrieval of a device authentication attribute associated with the data exchange information;enabling authentication of the user using the user authentication attribute; and enabling authentication of the computing device using the device authentication attribute, where data may be exchanged between the computing device and the remote entity in accordance with the data exchange information following authentication of the user and the computing device.
Owner:ECKOH UK
Mesh communications network having mesh ports
A method for communicating over a mesh network established between a plurality of devices is disclosed. Each device has a wireless radio and the method involves launching a mesh service on each device, the mesh service being operable to cause a processor circuit of the device to provide functionality for controlling the wireless radio for communication between devices over the mesh network. Each device has at least one application running on the device, the at least one application being associated with a mesh port, the mesh port being used to designate data transmissions as being associated with instances of a specific application running on at least some of the devices in the plurality of devices, the at least one application and the mesh service on each device being in data communication. The method also involves, in response to a specific application running on a device requesting the mesh service to provide access to the mesh network for communication via a specific mesh port, causing the mesh service to determine whether the specific application is authorized for communications on the specific mesh port, and if the specific application is authorized, processing requests from the application to communicate on the specific mesh port over the mesh network and forwarding data transmissions associated with the specific mesh port to the specific application, and if the specific application is not authorized, declining requests from the application to communicate on the specific mesh port over the mesh network and preventing access by the specific application to data transmissions associated with the specific mesh port.
Owner:LEFT OF THE DOT MEDIA
Apparatus and method for electronic mail filtering
ActiveUS7636947B2Digital data processing detailsAnalogue secracy/subscription systemsSecurity policyElectronic mail
Owner:FORCEPOINT LLC
Method for controlling single board to be safely started and method and device for upgrading software package
ActiveCN105117651AStartup does not affectImprove securityVersion controlPlatform integrity maintainanceElectricitySingle plate
The invention discloses a method for controlling a single board to be safely started. The method comprises the steps that after the single board is powered on, the resigned name of a software package to be loaded to the single board is acquired, the resigned name of the software package is obtained by using a single plate private key of the single board for resigning the software package, and is made after the original signature of the software package passes verification through a software package public key of the software package, and the original signature is obtained by signing the software package through a software package private key of the software package; the resigned name of the software package is verified through a single board public key paired with the single board private key; after the resigned name passes verification, the single board is started. According to the method for controlling the single board to be safely started, it can be guaranteed that the single board can still be safely started when the private key of the software package is leaked.
Owner:SHANGHAI HUAWEI TECH CO LTD
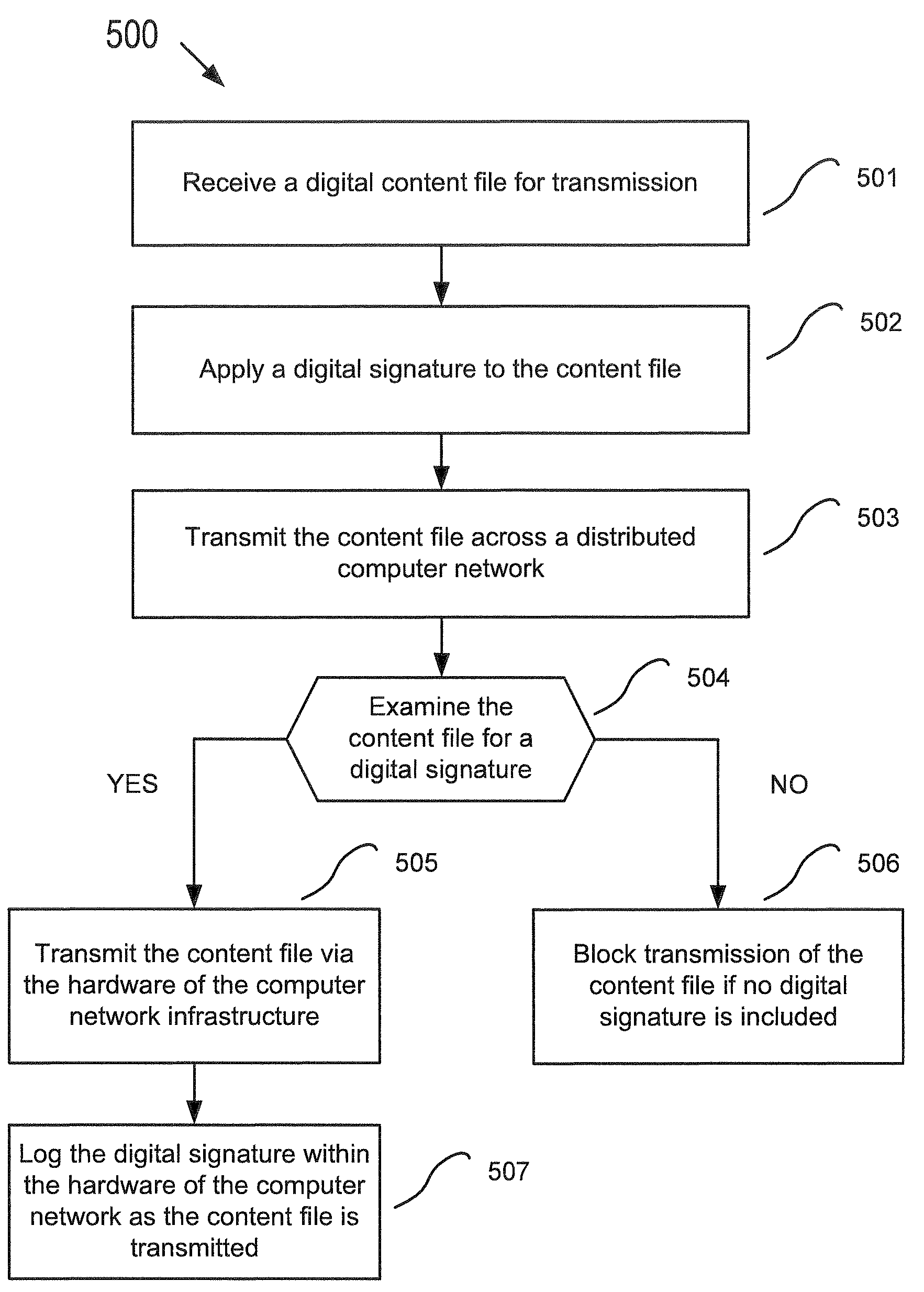
Copy protection built into a network infrastructure
InactiveUS7516322B1Copy protection is reinforcedPrevent easy circumventionMultiple digital computer combinationsProgram controlDigital contentDigital signature
Owner:CISCO TECH INC
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap