Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58 results about "Password" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
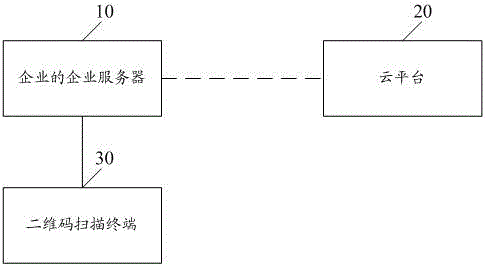
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A password, sometimes called a passcode, is a memorized secret used to confirm the identity of a user. Using the terminology of the NIST Digital Identity Guidelines, the secret is memorized by a party called the claimant while the party verifying the identity of the claimant is called the verifier. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant’s identity.
WIFI network configuration method and system
ActiveCN103825788AStable deliveryEasy to passSpecial service provision for substationData switching by path configurationPasswordIp address
Owner:SHENZHEN RUIKE HUILIAN TECH
Authentication system and method
InactiveUS20090193264A1Digital data authenticationCoded identity card or credit card actuationAuthentication systemStrong authentication
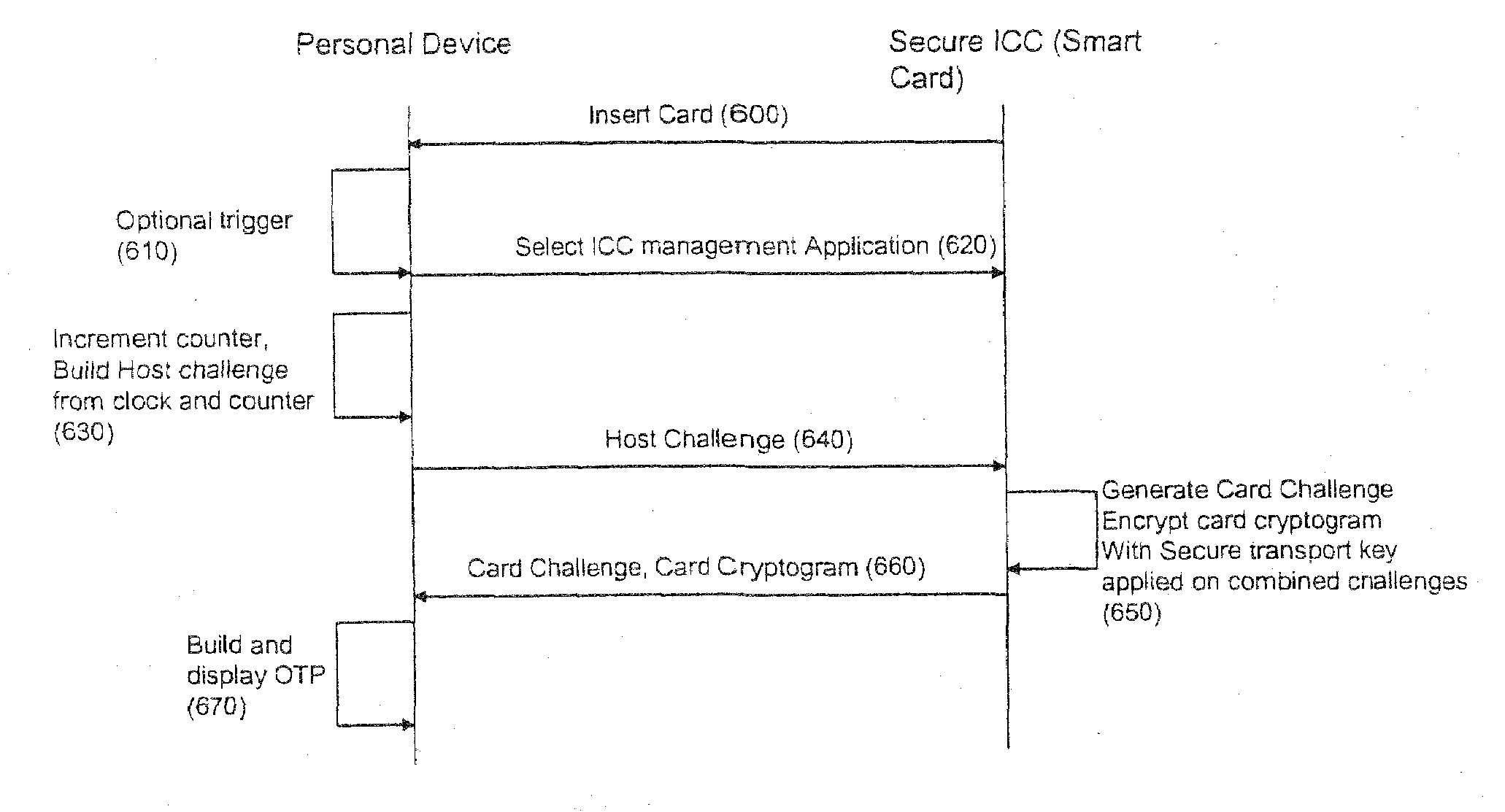
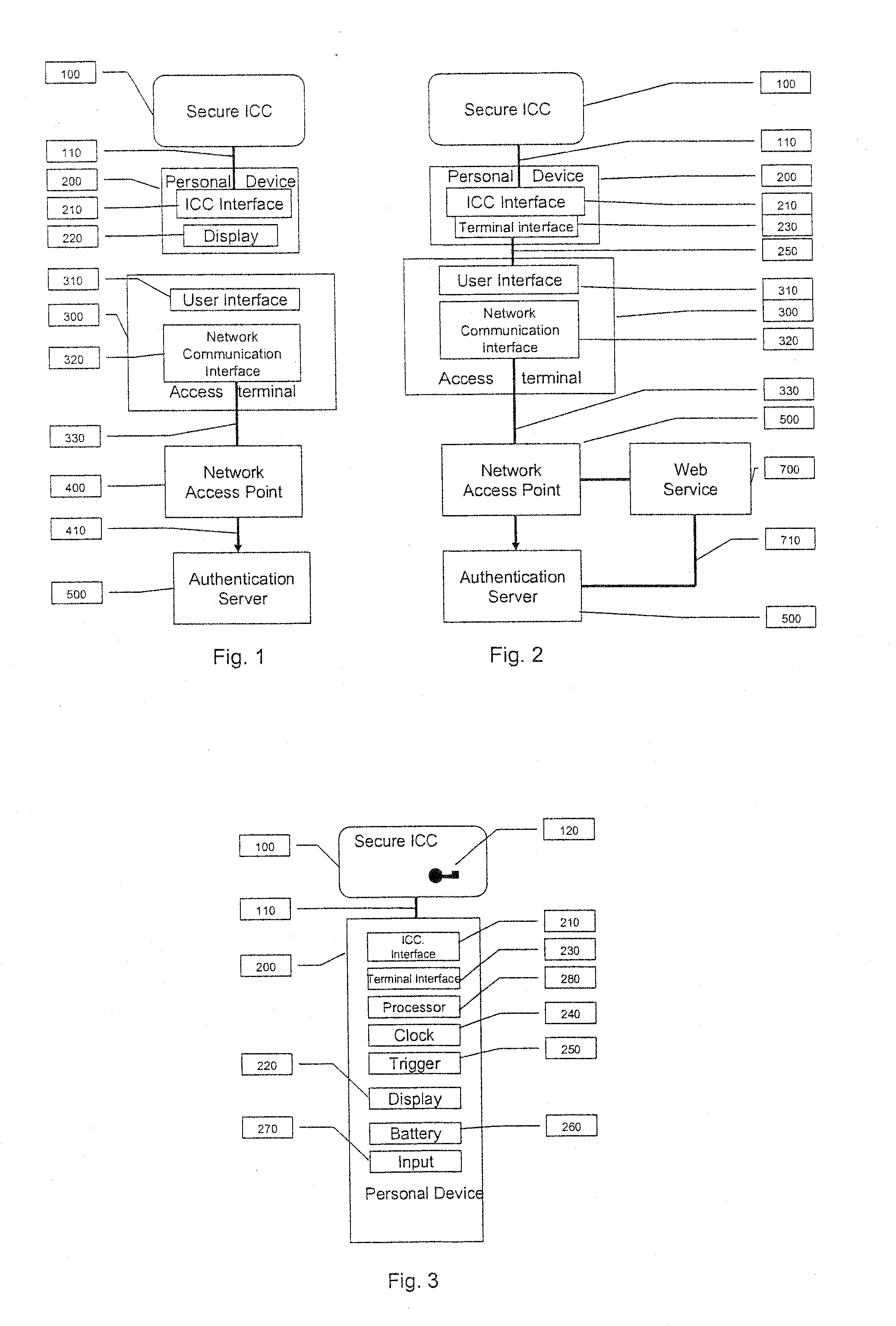
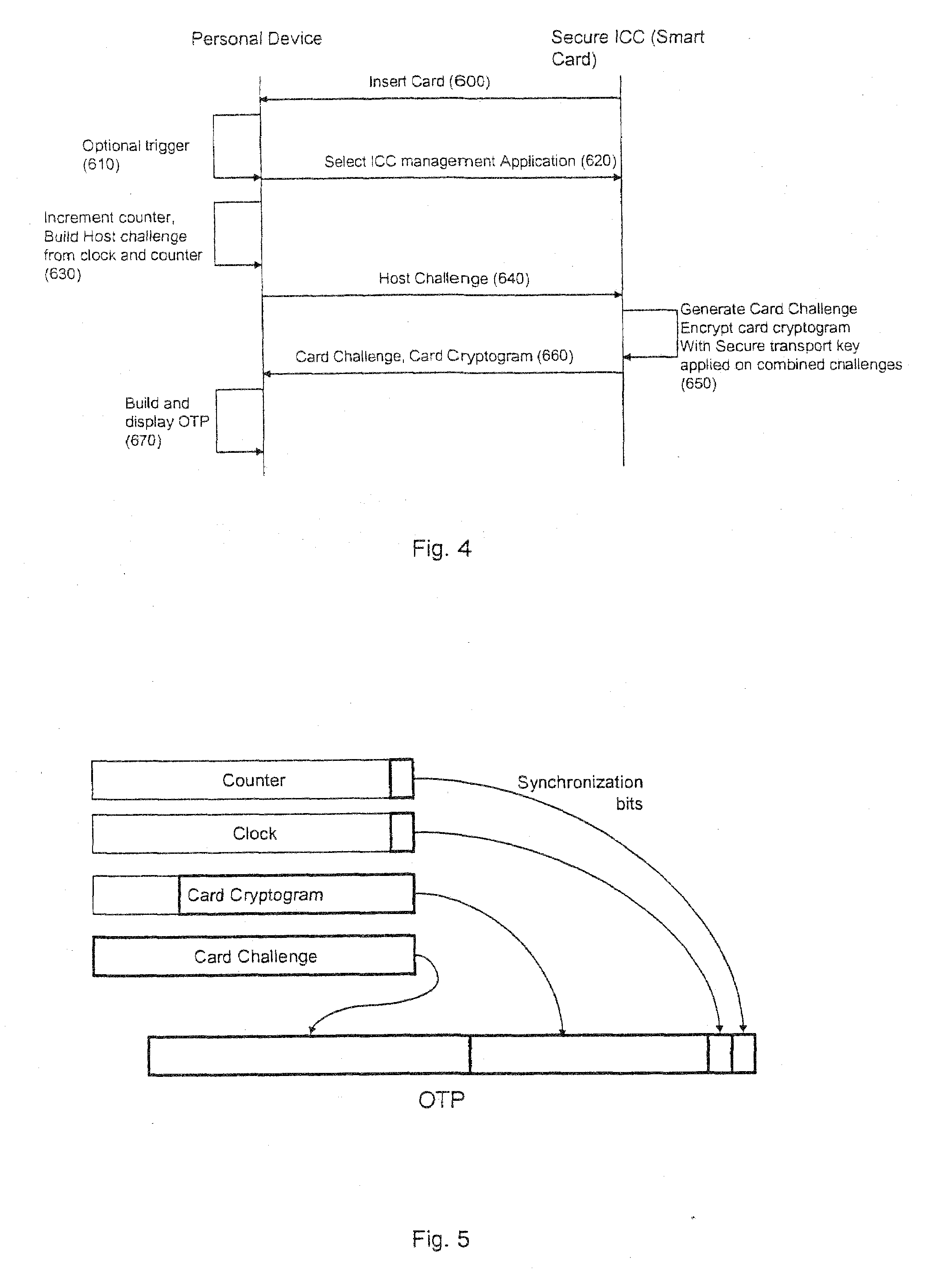
A strong authentication method and system using a Secure ICC component coupled with a Personal device, and relying on the existing cryptographic protocols and keys for managing the secure ICC to generate One-Time-Passwords when the necessary authentication keys or cryptographic protocols are not already present in the Secure ICC configuration for that purpose.
Owner:ACTIVIDENTITY
Payment method and payment system based on block chain
InactiveCN106600252AImprove efficiencyWill not affect normal operationPayment protocolsBuying/selling/leasing transactionsPasswordPayment system
Owner:MIGU CO LTD
Authentication system for mobile terminal having electronic money function
InactiveUS20060160525A1Reduce usageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPasswordComputer terminal
Owner:FUJIFILM CORP
Reusable public key certificate scheme based on public key infrastructure
InactiveCN106059747AImprove management efficiencyReduce in quantityKey distribution for secure communicationUser identity/authority verificationRelevant informationPassword
Owner:成都蓝海贝信息技术有限公司
Verification method combining static password and dynamic password and terminal equipment
InactiveCN105871546AEasy to rememberDon't worry about stealingKey distribution for secure communicationMultiple keys/algorithms usageValidation methodsPassword
Owner:张雪莱
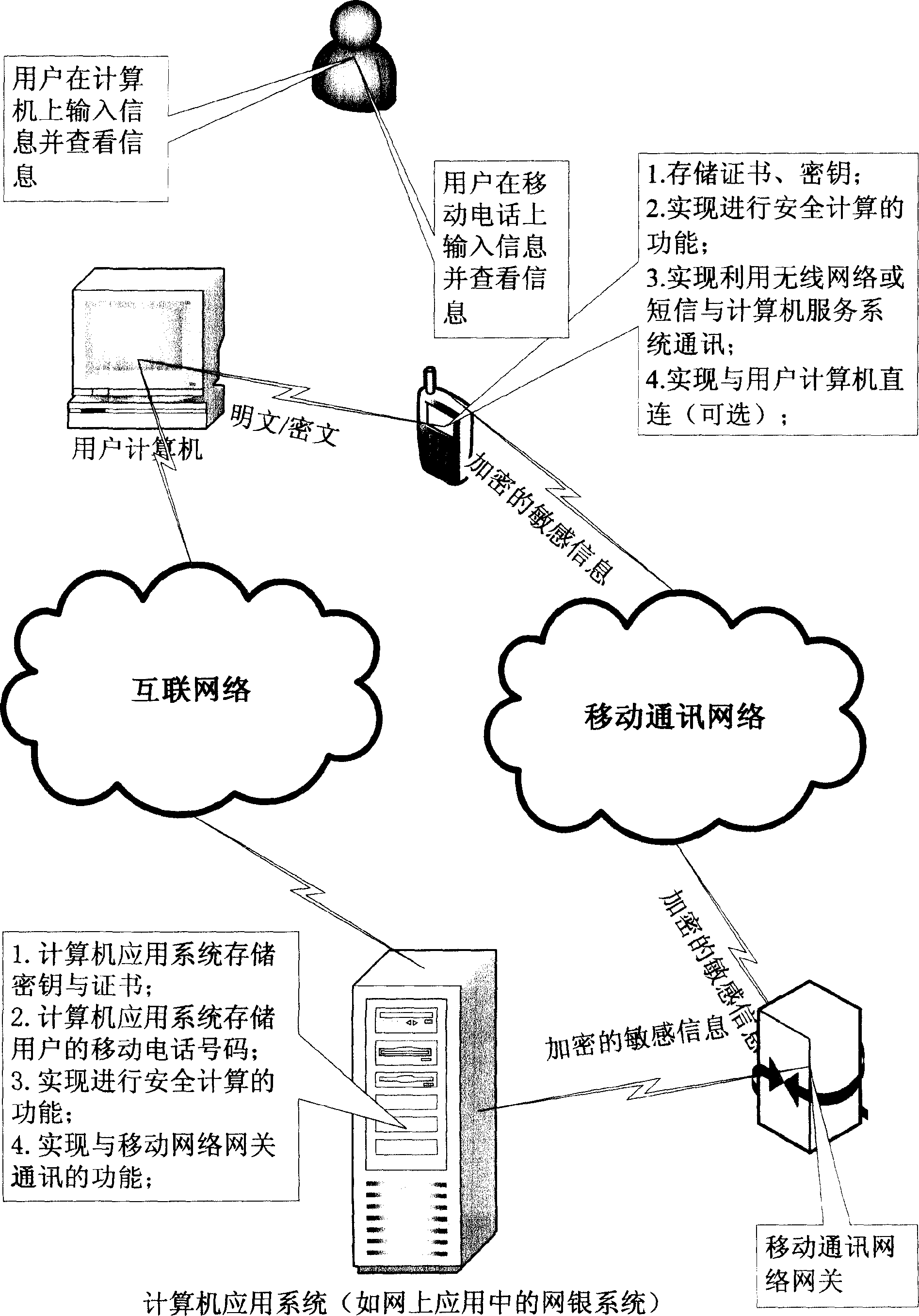
Technology for improving security of accessing computer application system by mobile phone
InactiveCN1838141APrevent leakageGuaranteed isolationDigital data authenticationPasswordPersonal computer
Owner:刘亚威
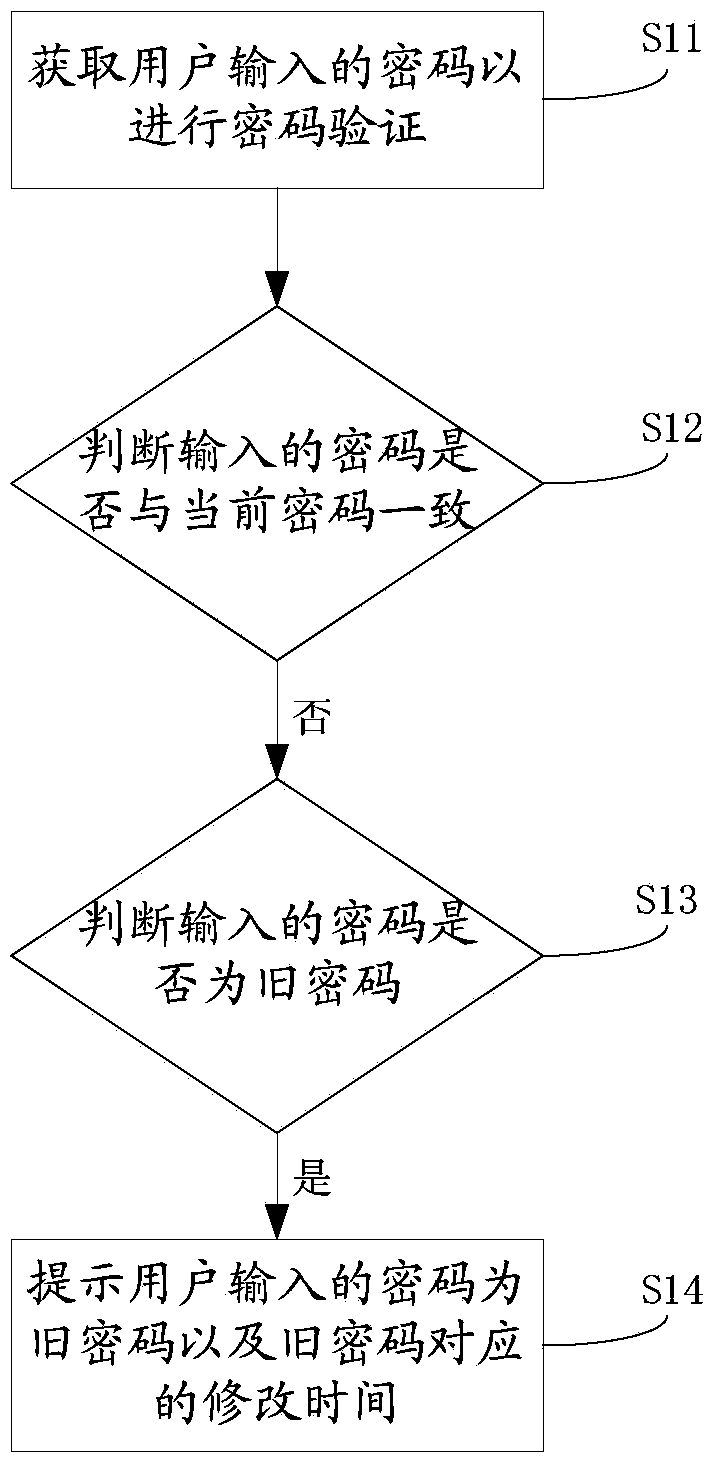
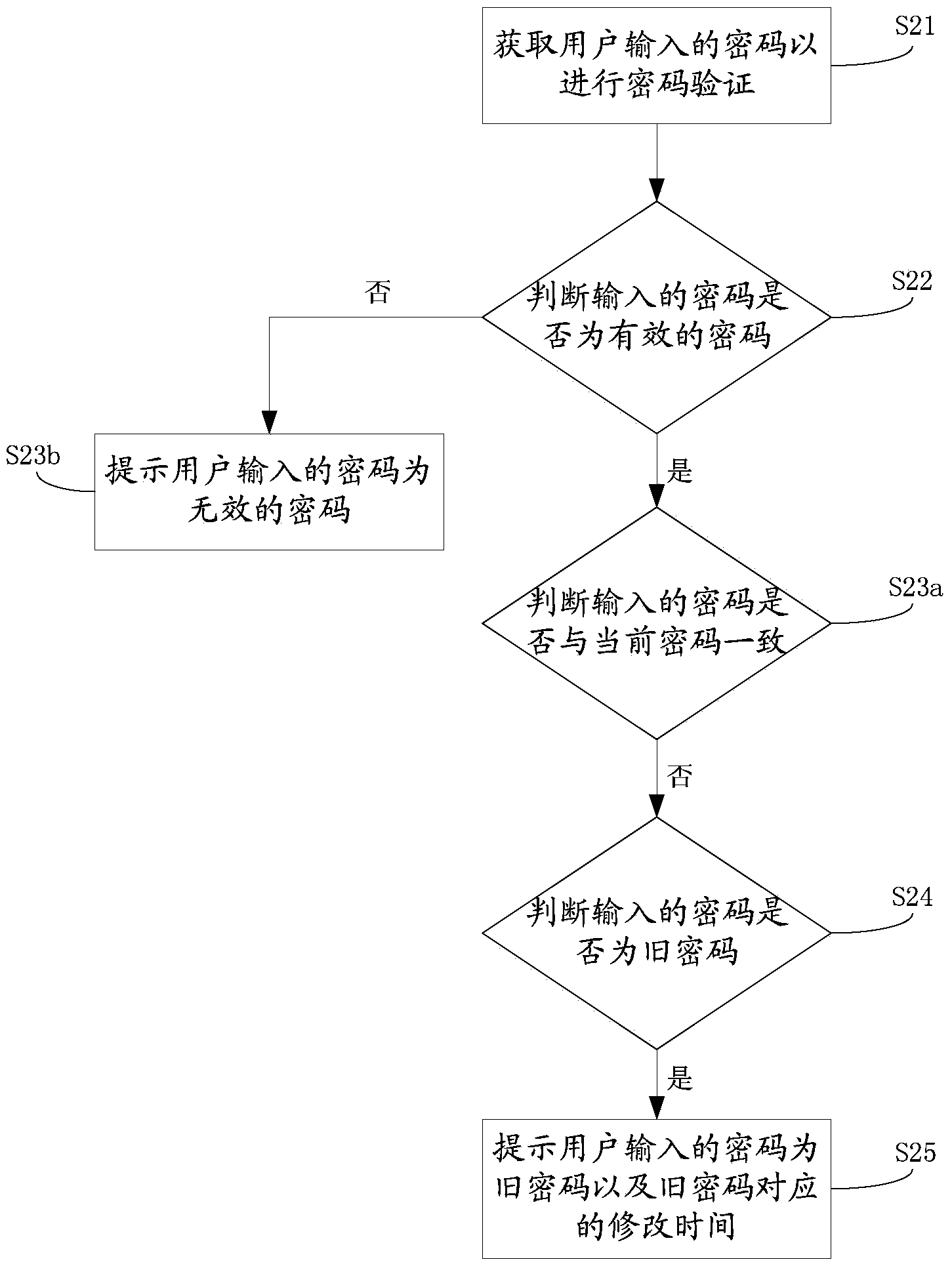
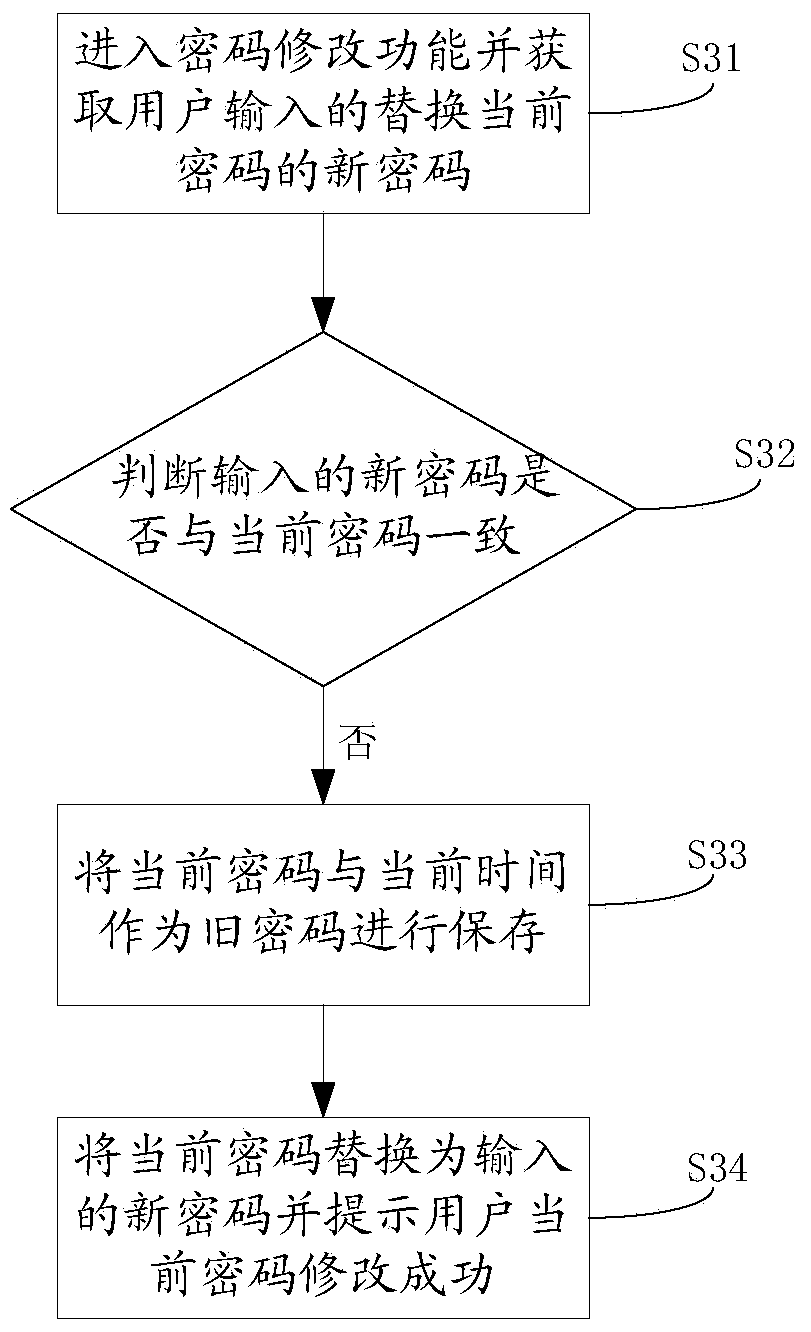
After-password-input prompt method, password modifying method and electronic equipment
ActiveCN103413081AImprove the efficiency of entering the correct passwordReduce the number of times you enter wrong passwordsDigital data authenticationUser inputPassword
Owner:威海神舟信息技术研究院有限公司
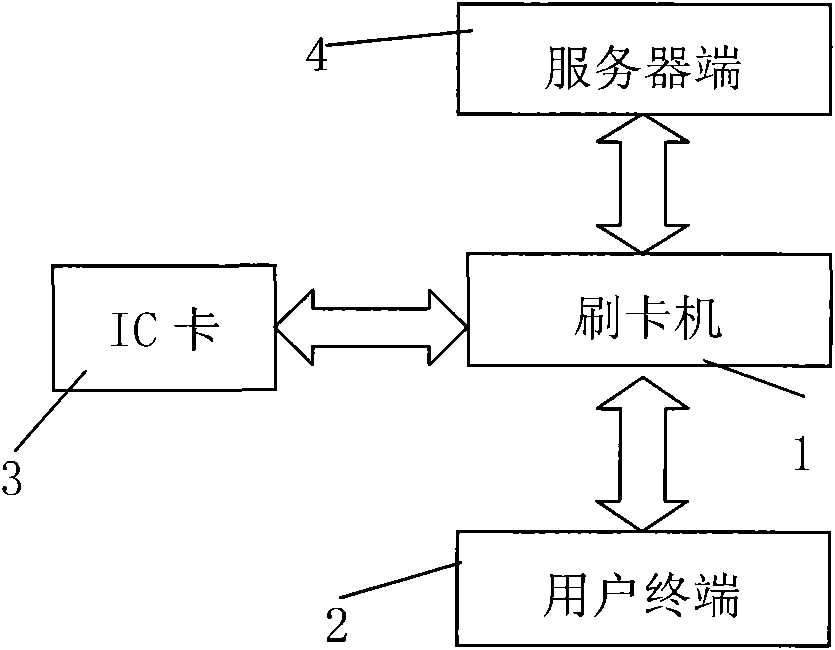
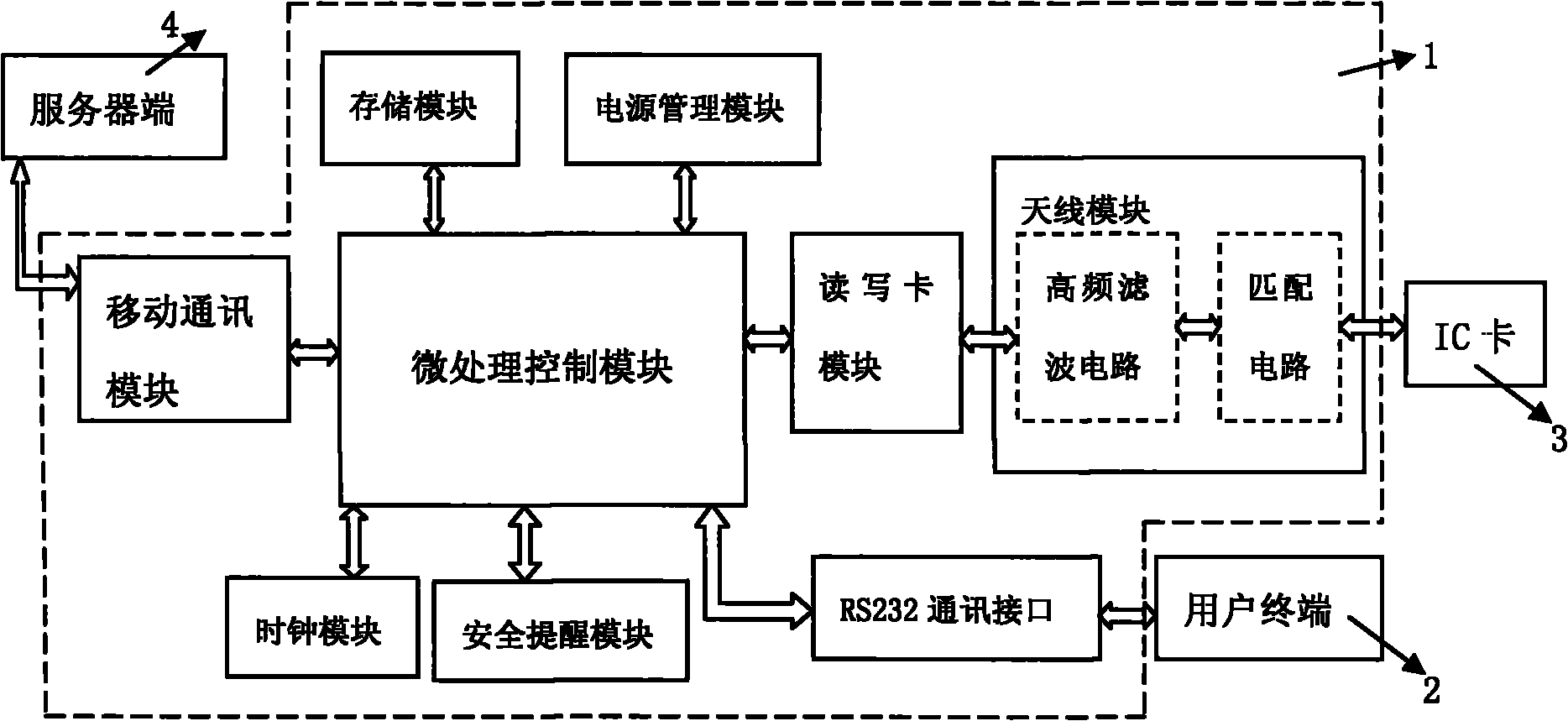
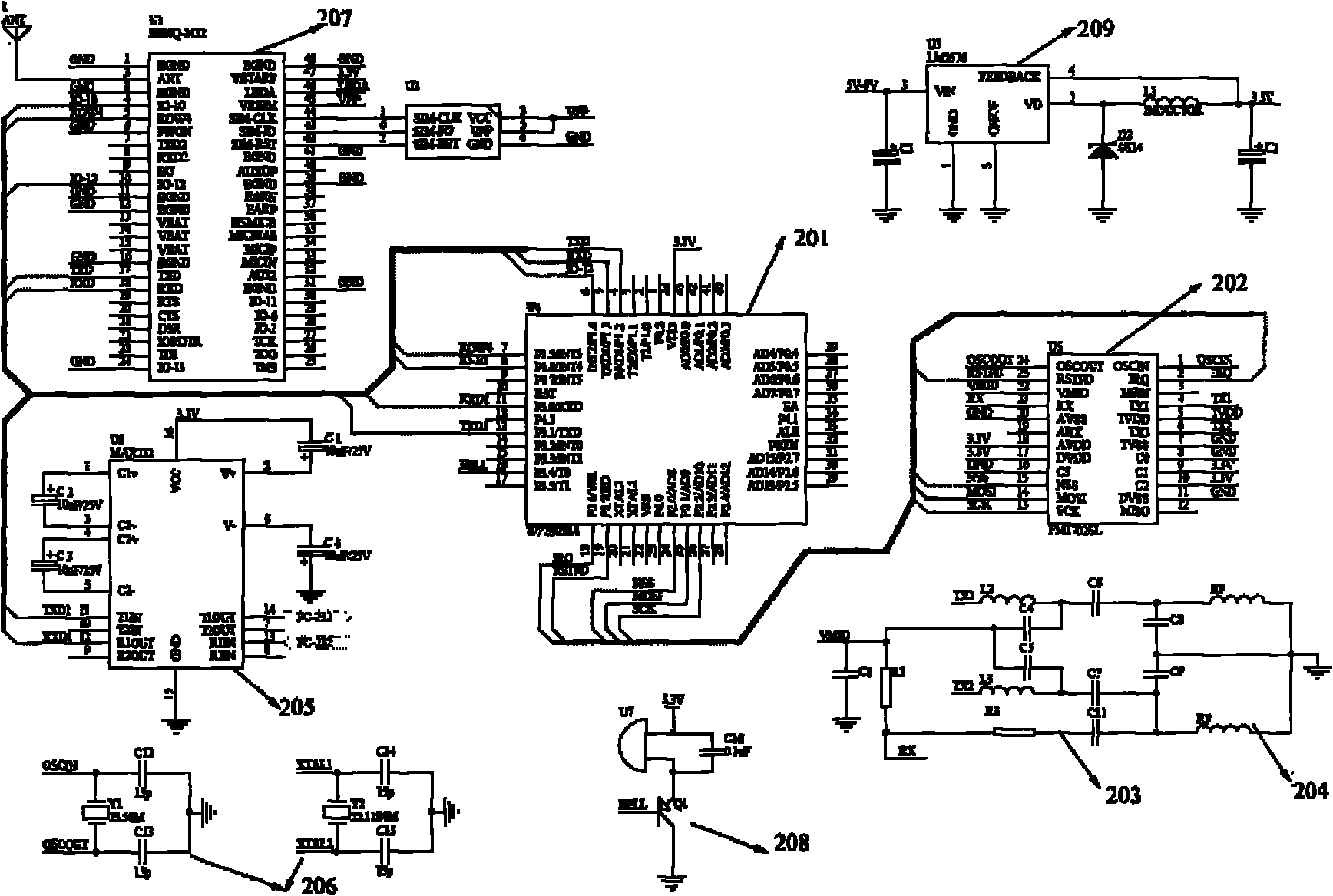
Smart card swipe machine and information exchange method
ActiveCN101783040AGuarantee authenticityMonitor usage in real timeCoded identity card or credit card actuationPasswordTerminal equipment
Owner:SHENZHEN CERTAINN TECH CO LTD
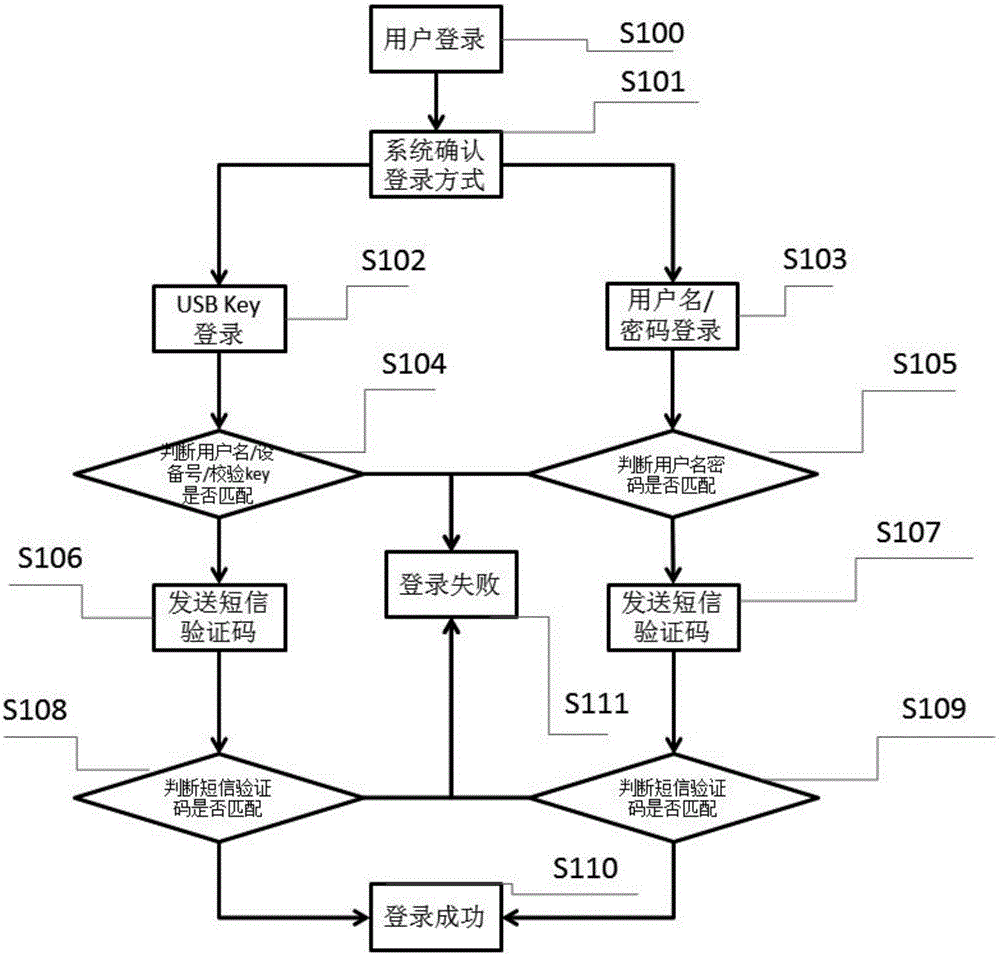
User logging-in method under system control
Owner:安徽天达网络科技有限公司
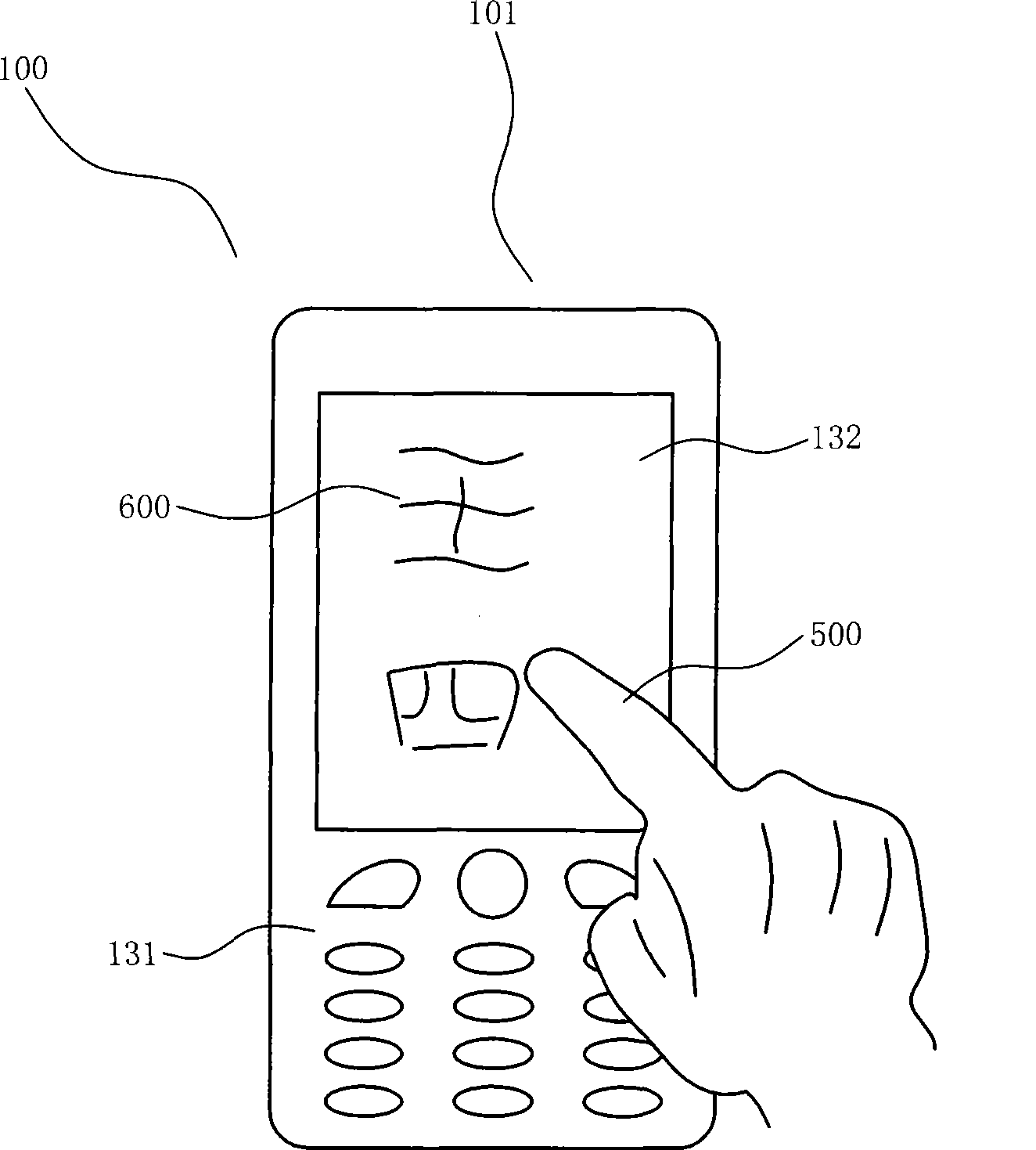
Hand-hold terminal with handwriting recognition identity affirmation function and its implementing method
InactiveCN101482904AValid identificationGuaranteed privacyCharacter and pattern recognitionComputer security arrangementsUser needsHandwriting
Owner:SHANGHAI LINGRUI INFORMATION TECH
File encryption operation method and file encryption operation system
ActiveCN102819702AImprove efficiencyImprove securityComputer security arrangementsSecuring communicationComputer hardwarePassword
The invention discloses a file encryption operation method and a file encryption operation system. The method comprises the steps of: receiving a file operation instruction; transferring an encrypted target file according to the file operation instruction; carrying out memory decryption on the encrypted target file according to key information corresponding to the encrypted target file, and operating the encrypted target file after memory decryption. According to the scheme disclosed by the invention, the password of the encrypted target file does not need to be manually input; opening and operating of the file can be achieved by decrypting the file without a manual operation, and the operating efficiency of the key information is improved. On the other hand, the encrypted target file is decrypted by the key information in the memory; the decrypted file is stored in the memory, and a permanent file is not generated, therefore, the password is not stolen by the others, and the operating security of the encrypted file is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
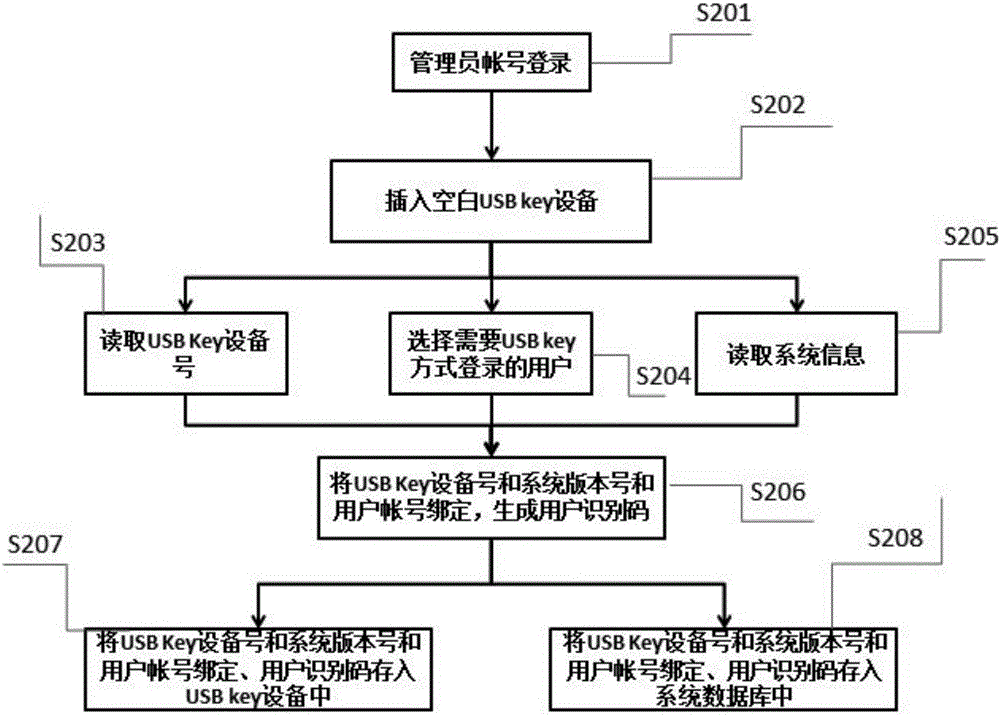
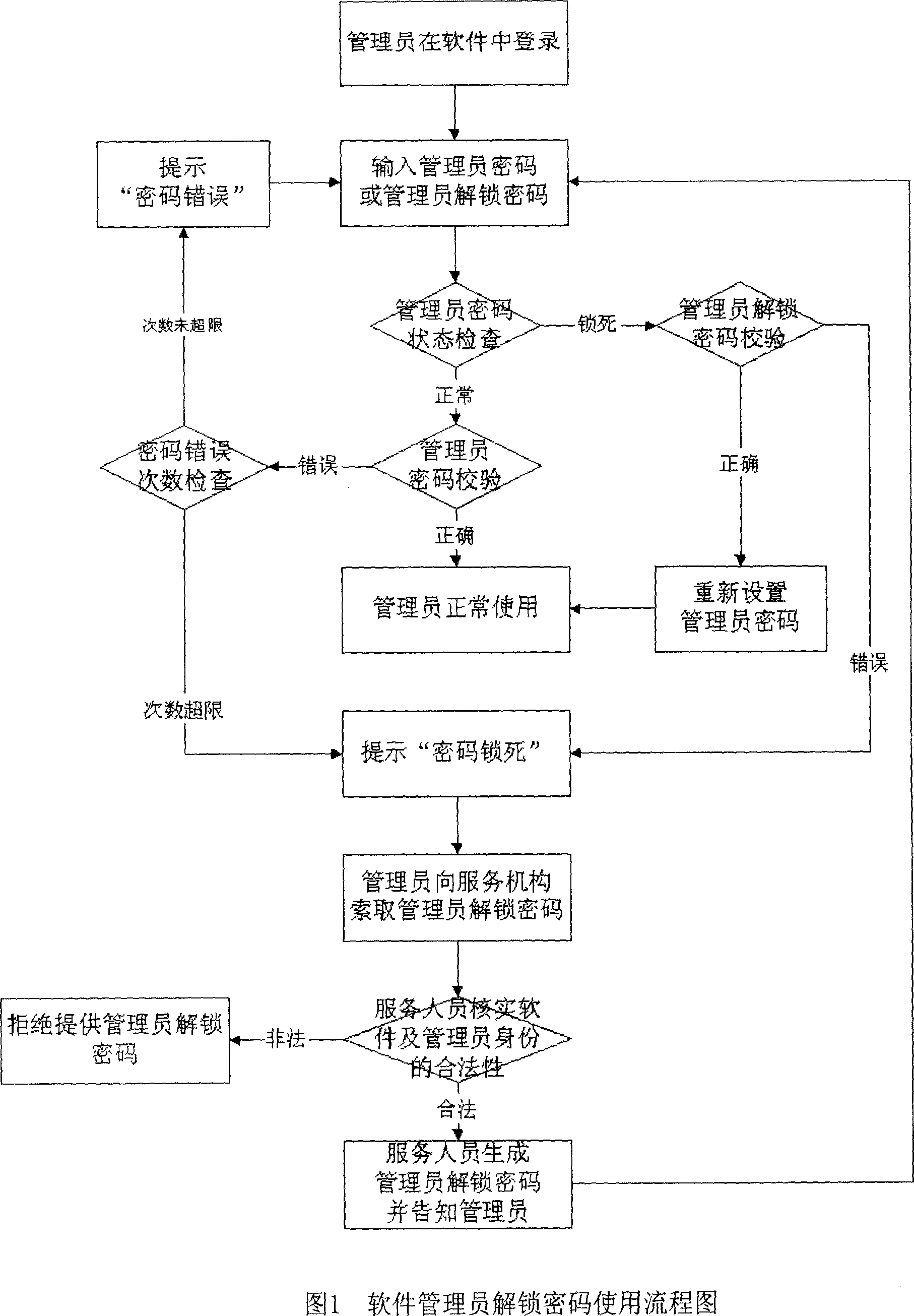
Method for administrator to unlock password
InactiveCN1967556AAvoid the disadvantages of easy leakageReduce lossesDigital data authenticationPasswordSoftware engineering
Owner:BEIJING ZHONGXINGTONG ELECTRONICS TECH
Dynamic displaying cipher keboard
InactiveCN101021756AProtection of rights and interestsPrevent password theftInternal/peripheral component protectionInput/output processes for data processingDriver circuitProcess dynamics
Owner:郭文 +1
Encrypted information processing method and terminal
ActiveCN1968539AImprove securityUser identity/authority verificationSubstation equipmentInformation processingEncrypted function
Owner:HUAWEI TECH CO LTD
Touch-screen-terminal customized lock screen system
InactiveCN104200151AEnough informationAdd funDigital data authenticationInput/output processes for data processingPersonalizationPassword
The invention relates to a touch-screen-terminal customized lock screen system which comprises a lock-screen attribute setting subsystem and a lock-screen password setting subsystem. The lock-screen attribute setting subsystem is used for setting personal attributes of a touch-screen terminal lock screen, and the lock-screen password setting subsystem is used for setting passwords for the touch-screen terminal lock screen; the lock screen attribute setting subsystem comprises password lock-screen background setting modules, a floating-window display content setting module and a password pattern setting module; the password lock-screen background setting modules include background image setting modules and a background music setting module which are used for setting background images and music of the password lock screen; the floating-window display content setting module is used for setting floating-window display content, the floating-window display content can be displayed in a floating-window displaying mode in the touch-screen terminal lock screen state, and the floating-window display content is used for reminding users of some important information content; the password pattern setting module is used for setting password patterns. By the arrangement, personalized touch-screen-terminal customized lock screen system high in interestingness can be customized.
Owner:SUZHOU TIANPING ADVANCED DIGITAL TECH
Two-dimensional code transmitting and activation method and system
ActiveCN105761090AImprove protectionSecure coding dynamic managementCommerceActivation methodComputer hardware
Owner:深圳中检网络传媒有限公司
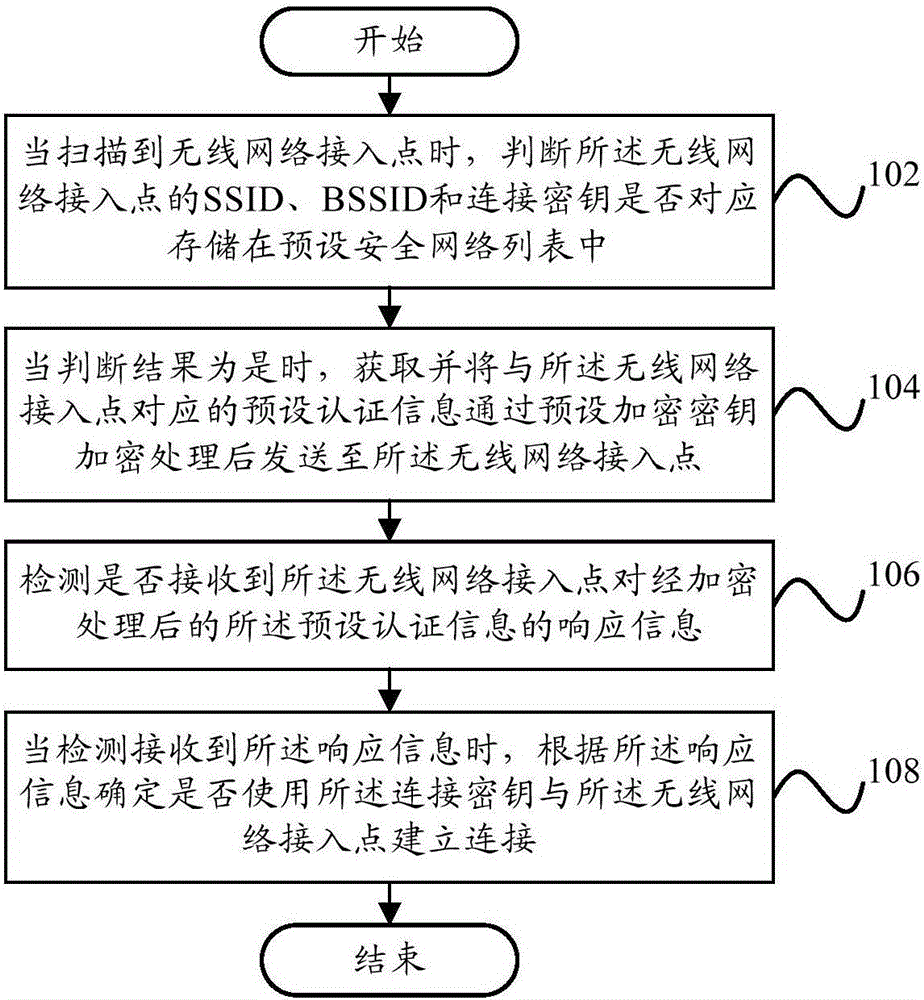
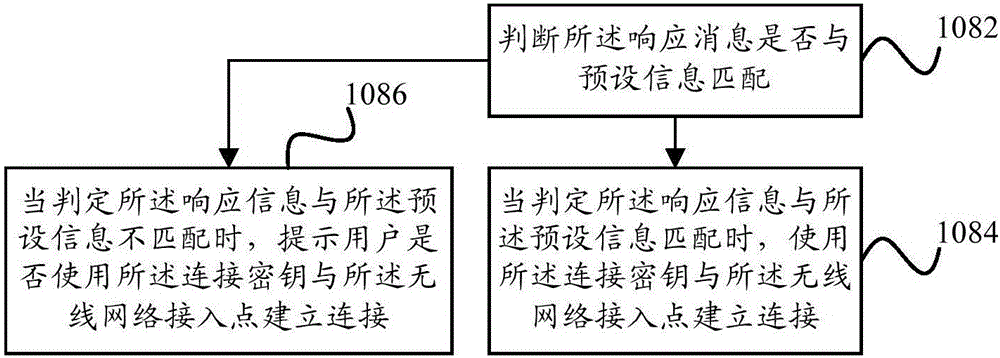
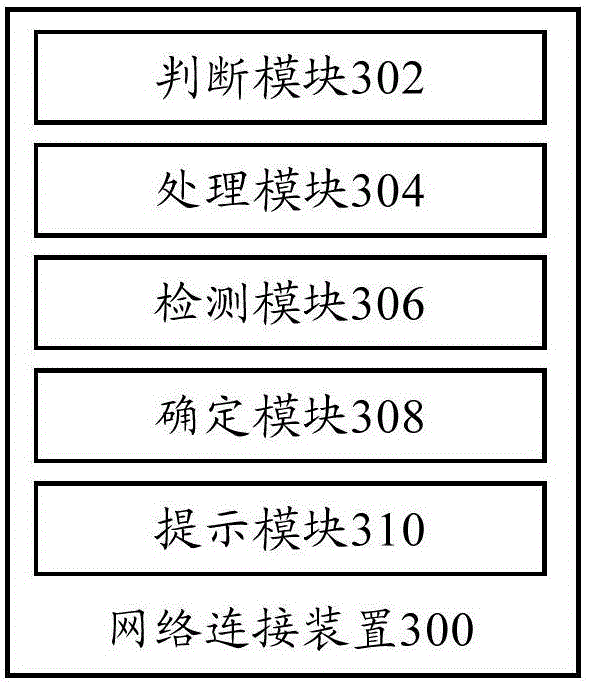
Network connection method, network connection device and terminal
ActiveCN106131834AImprove user security experienceImprove securitySecurity arrangementPasswordNetwork connection
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Authentication system and method using flash of smart mobile
ActiveUS20180262908A1Improve securityImprove stabilityClose-range type systemsSubstation equipmentPasswordMobile device
It is capable of authentication by transmitting through light emitted from a flash of a smart mobile according to foregoing solution of the problem, security and stability can be improved in comparison with other authentication systems such as an ID, a password and a public authentication which are necessary to a bank task, a personal authentication, an identity authentication and a transaction remittance. And, even if the smart mobile is lost or a stranger acquiring this are misappropriating, cryptography such as patterns cannot be solved thereby it is not available. Further, carrying is easy to use anywhere regardless of the place because the transaction is available using a flash equipped to the smart mobile.
Owner:B PLAT LLC
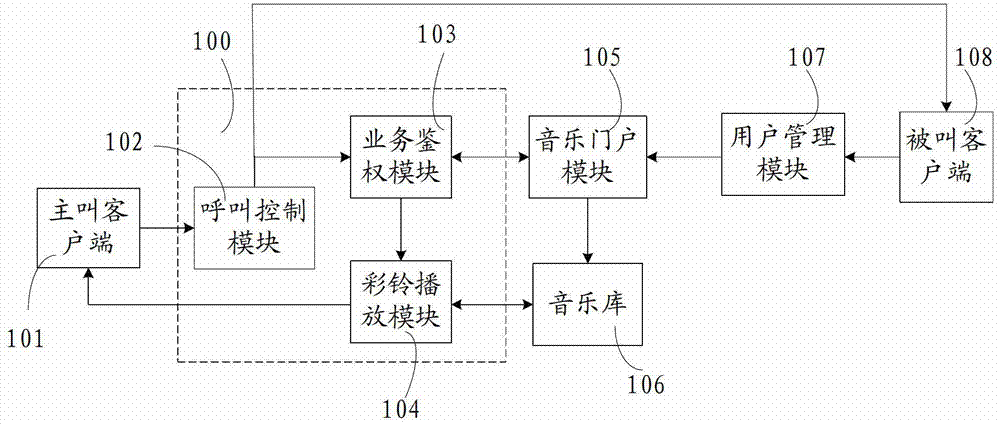
Polyphonic ringtone business system and implementation method based on converged communication
ActiveCN103037113ALow costProtection of rights and interestsSpecial service for subscribersWireless commuication servicesPersonalizationPassword
Owner:北京思特奇信息技术股份有限公司
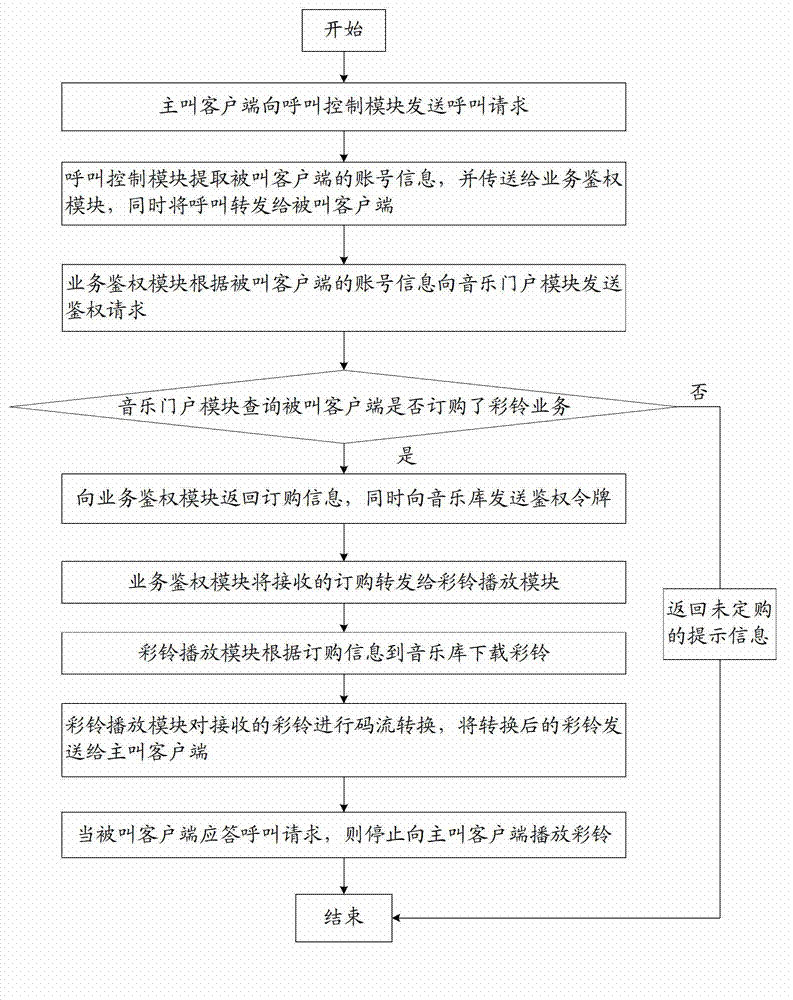
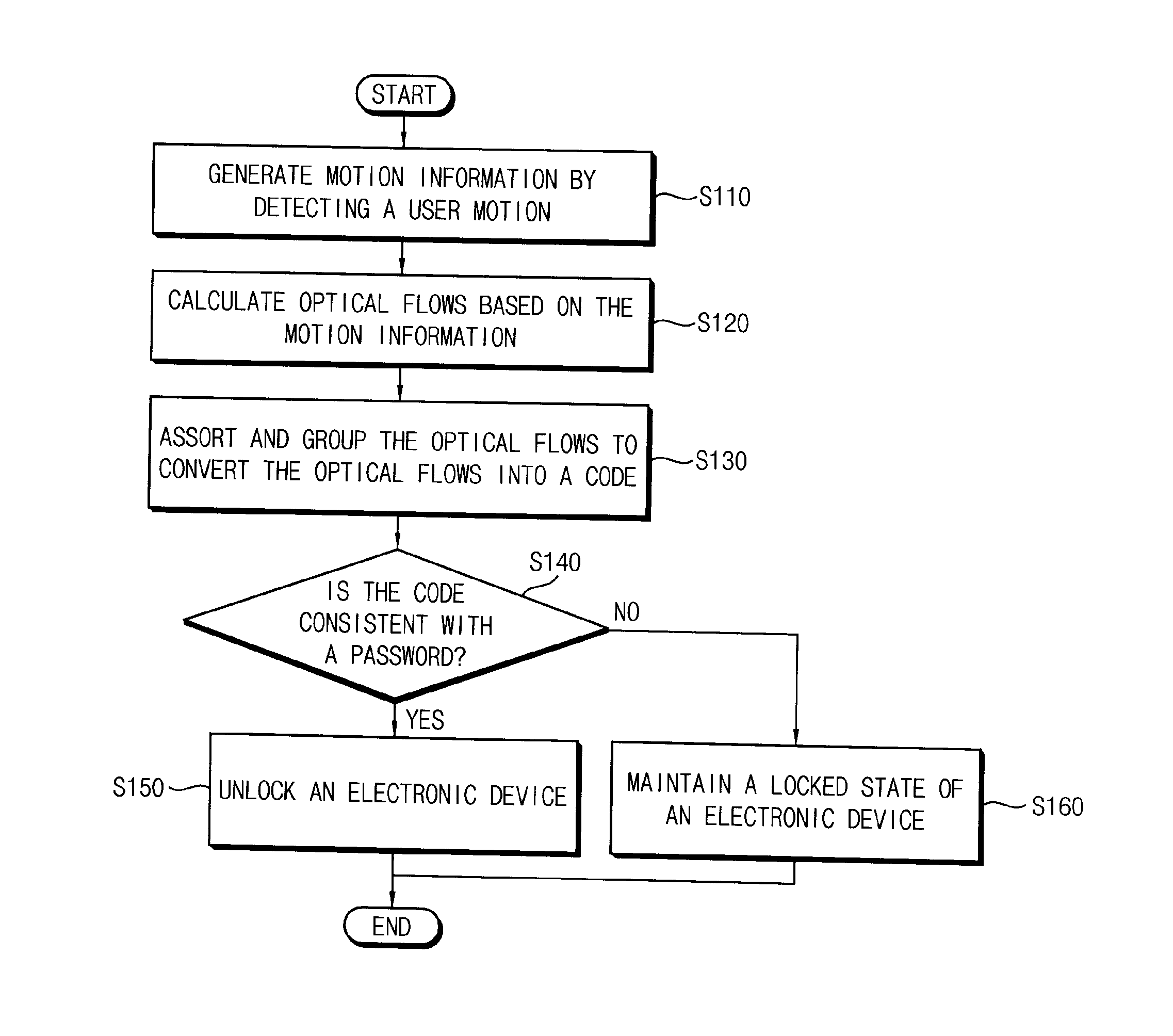
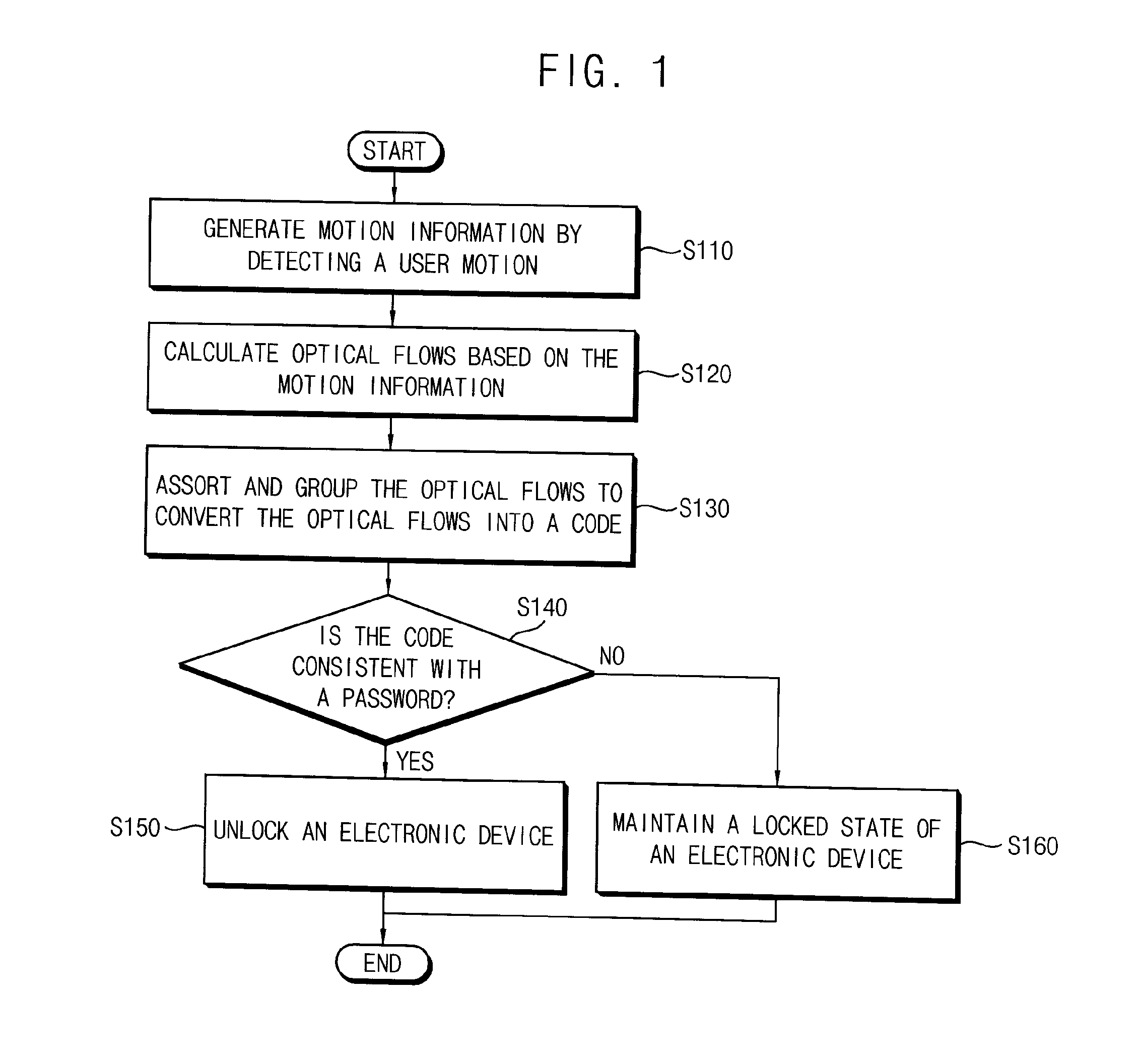
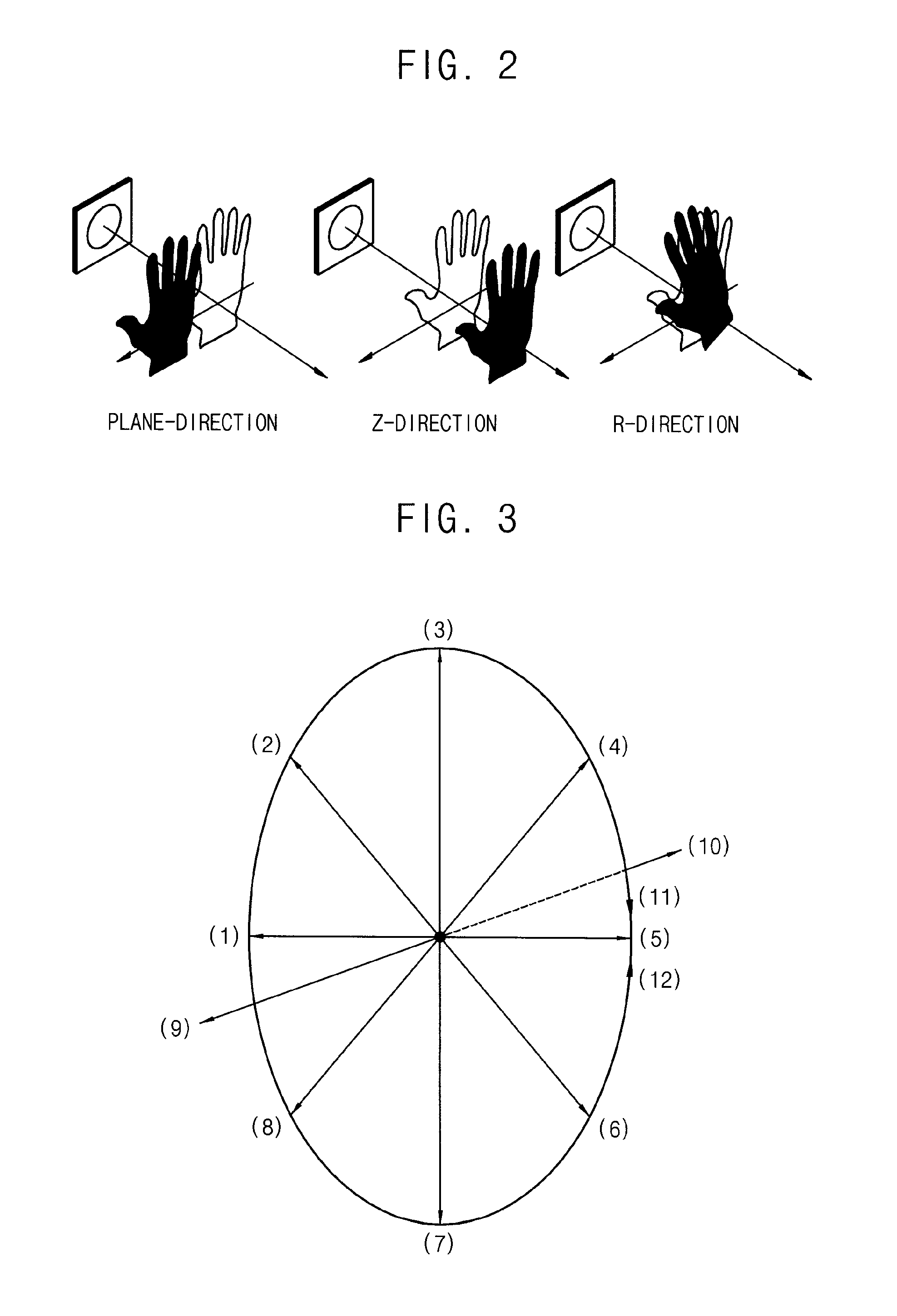
Method of unlocking an electronic device based on motion recognitions, motion recognition unlocking system, and electronic device including the same
InactiveUS20150248551A1Digital data processing detailsAnalogue secracy/subscription systemsPasswordSimulation
Owner:SAMSUNG ELECTRONICS CO LTD
Search method and apparatus
ActiveCN107180049AEasy to operateImprove search efficiencySpecial data processing applicationsWeb data retrieval using information identifiersPasswordWeb resource
Owner:ALIBABA GRP HLDG LTD
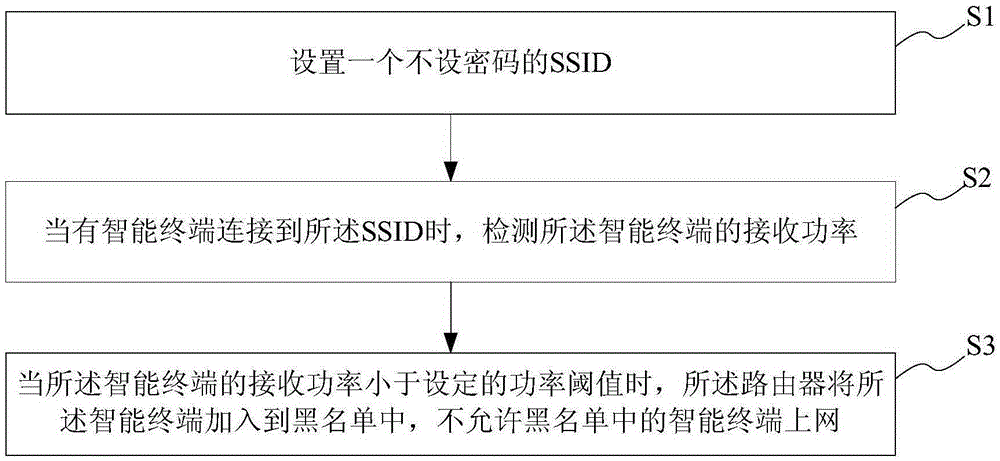
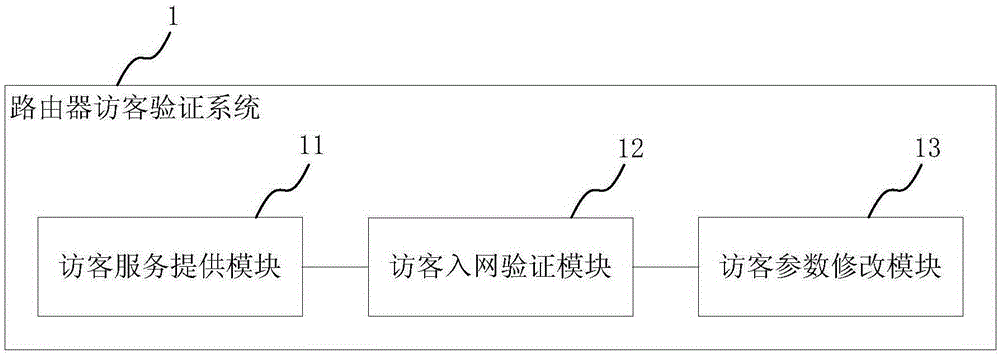
Router visitor verification method and system and router
InactiveCN105245539AEnsure safetyTransmission monitoringSecurity arrangementValidation methodsPassword
Owner:PHICOMM (SHANGHAI) CO LTD
Shared express bag
Owner:上海钊易数码科技有限公司
Unlocking device and method thereof
InactiveCN104077508AImprove securityIncreased confidentialityDigital data authenticationComputer hardwarePassword
Owner:苏州天鸣信息科技有限公司
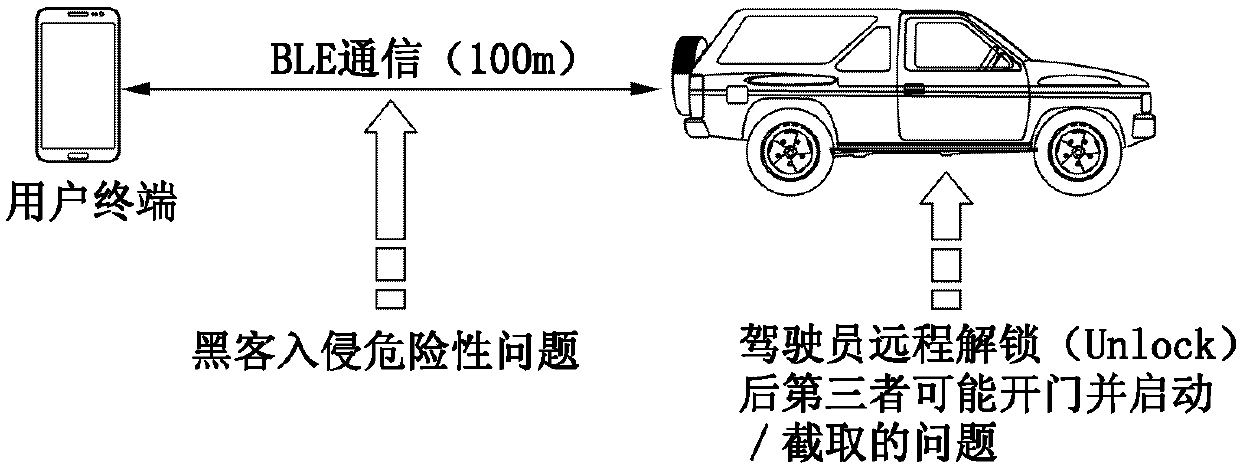
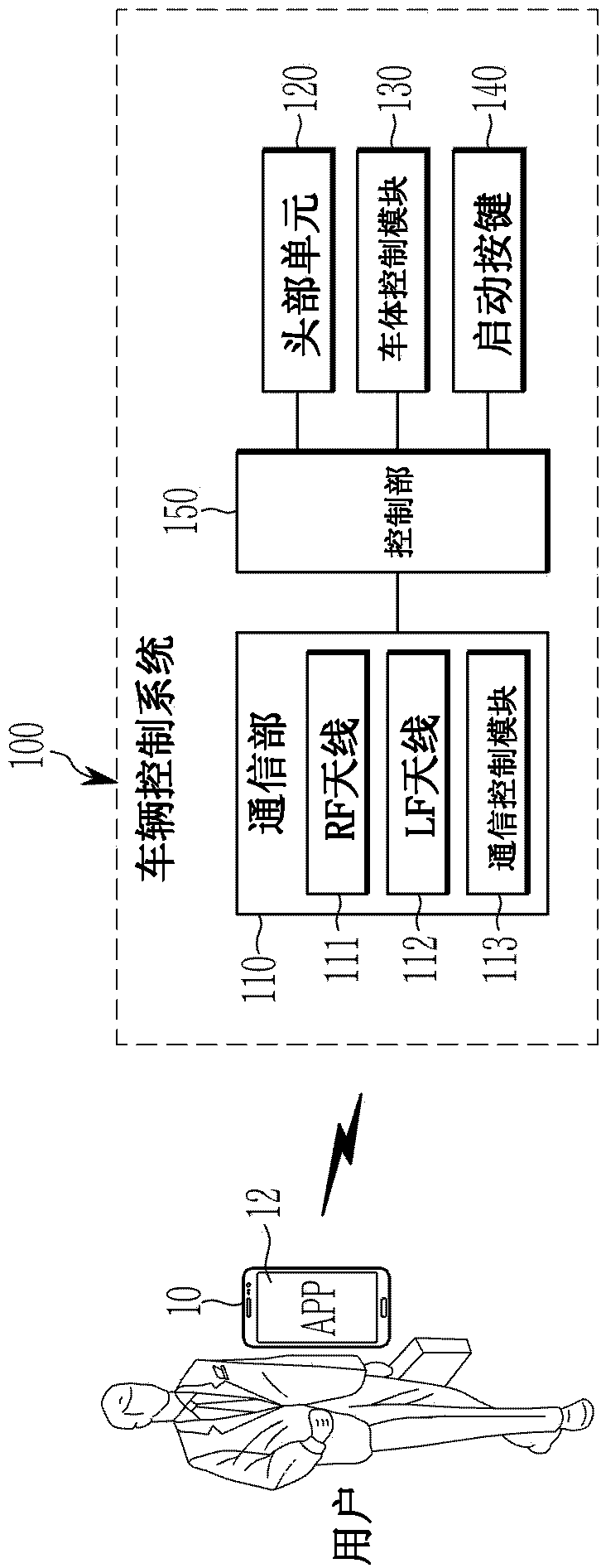
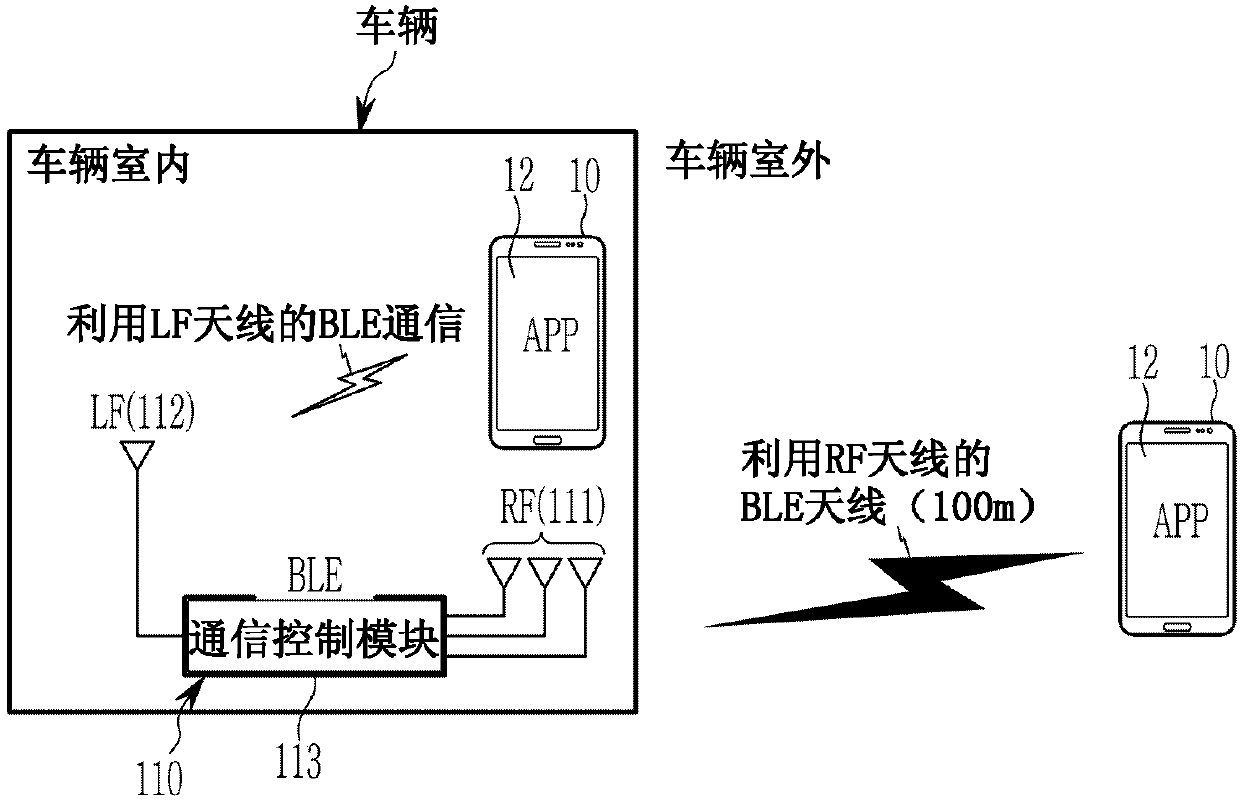
Smart-key-free vehicle control system and method
InactiveCN110027506ABlocking the possibility of intrusionImprove securityParticular environment based servicesAnti-theft devicesControl signalPassword
Owner:HYUNDAI MOTOR CO LTD +1
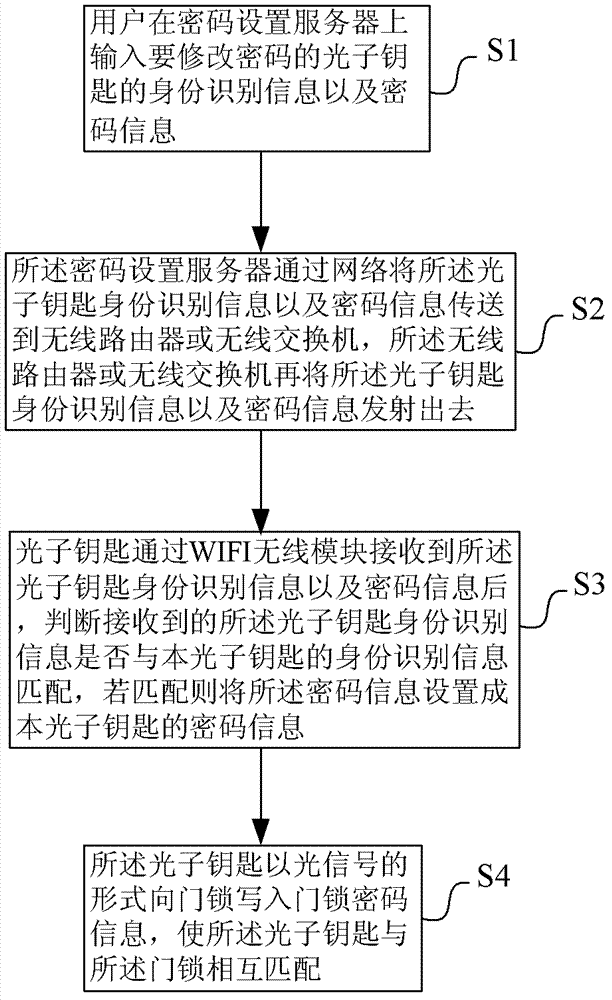
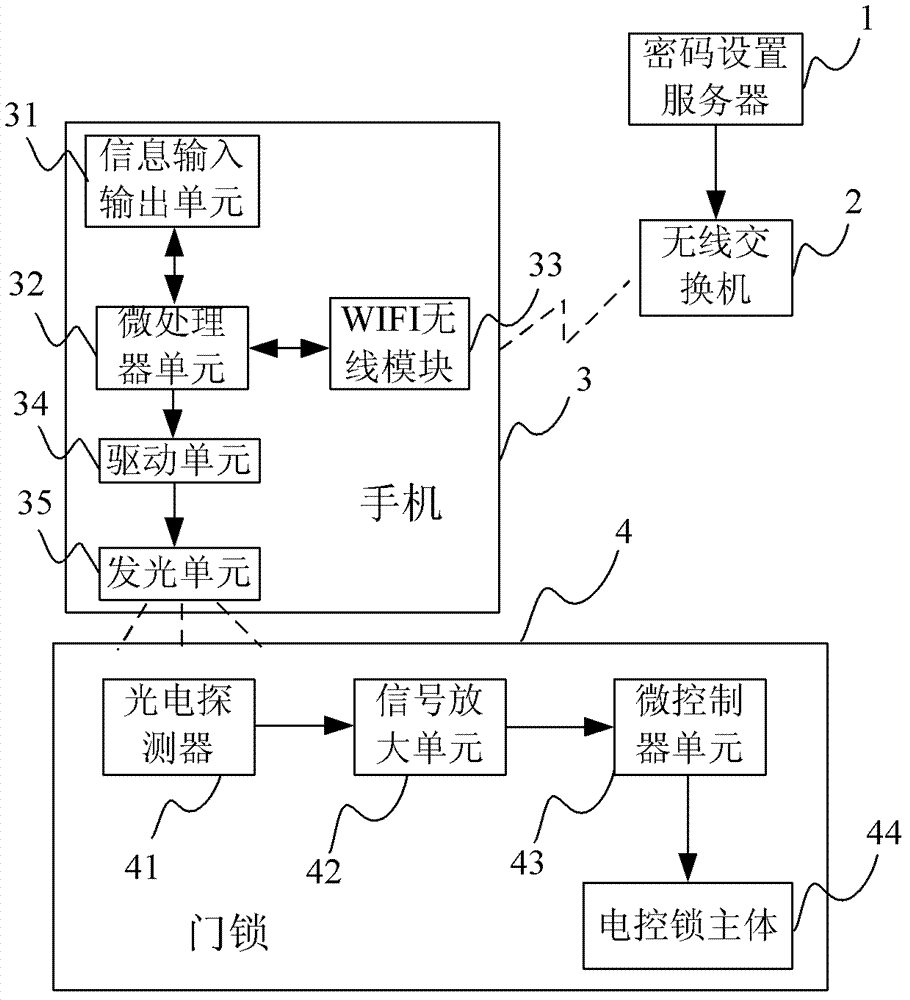
WIFI-based password setting method of light-operated access control system
Owner:KUANG CHI INTELLIGENT PHOTONIC TECH
Physical no-cloning technology based RFID card type intelligent door lock
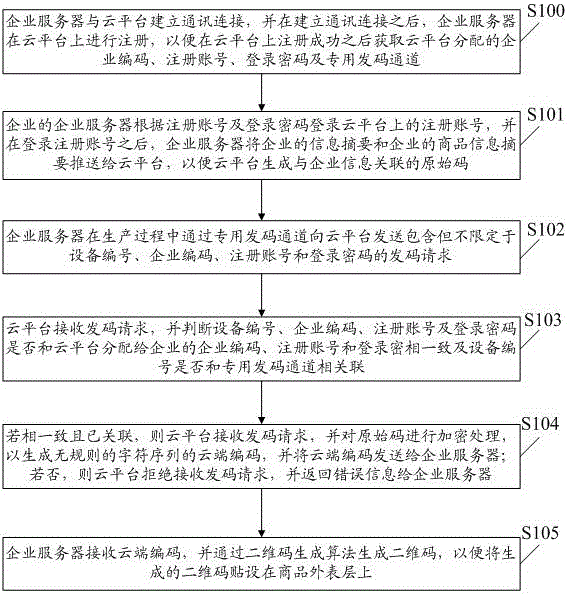
InactiveCN108921995AImprove protectionImprove securityUser identity/authority verificationInternal/peripheral component protectionPasswordThe Internet
The invention discloses a physical no-cloning technology based RFID card type intelligent door lock. The physical no-cloning technology based RFID card type intelligent door lock comprises RFID cards,a door lock and a database, wherein the database is arranged on a background server; while ID which corresponds to the RFID cards is received, data is compared with data in the database through an internet; the database is used for storing ID which corresponds to each RFID card; a door lock inner chip comprises a PUF circuit; the RFID chip comprises an RFID module which is used for generating motivation; after receiving the motivation, the PUF circuit generates a corresponding secret key; and the database provides a matching source and is compared with the secret key generated by the PUF circuit, so that authentication is realized, and therefore, unlocking is performed based on a door lock password authentication mode. The PUF circuit can resist probe attack and physical attack, and is not stored with the secret key information, so that other people cannot read a chip secret key through a probe and the like to steal inner information, and therefore, safety of the door lock is greatlyimproved.
Owner:HOHAI UNIV CHANGZHOU
Method for locking/unlocking bottle cap
Owner:YIFENG MFG
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap