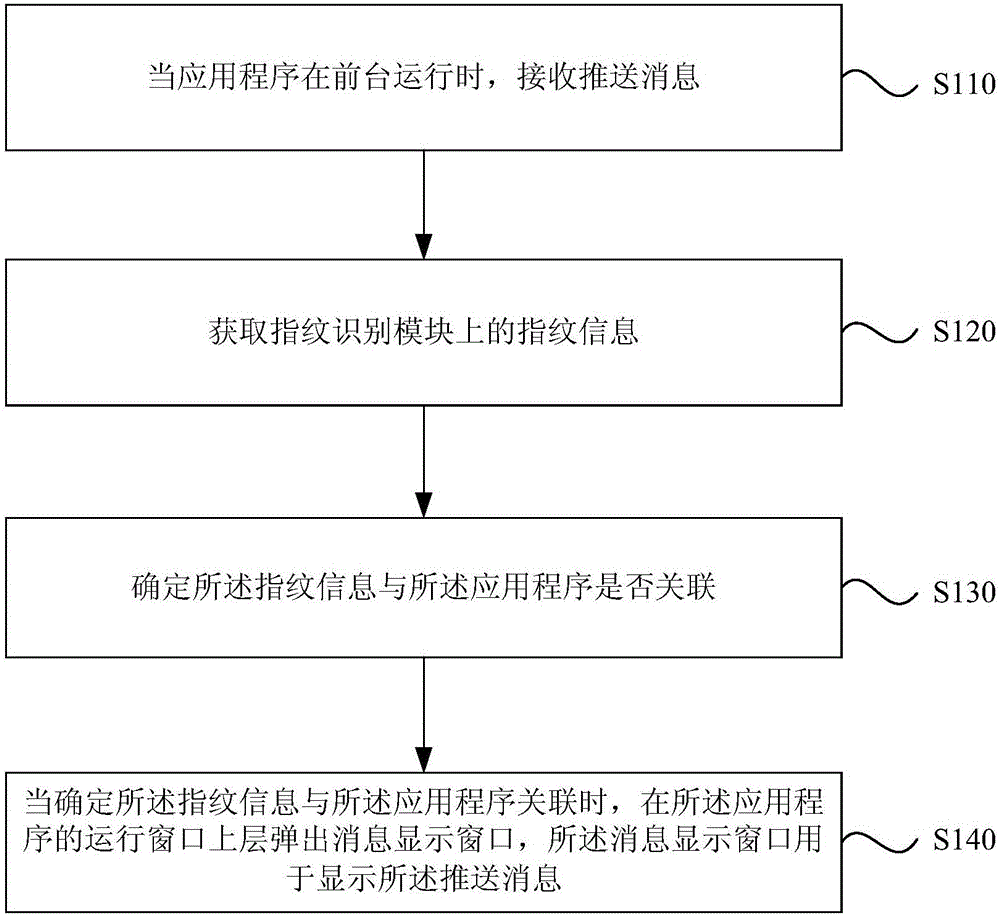
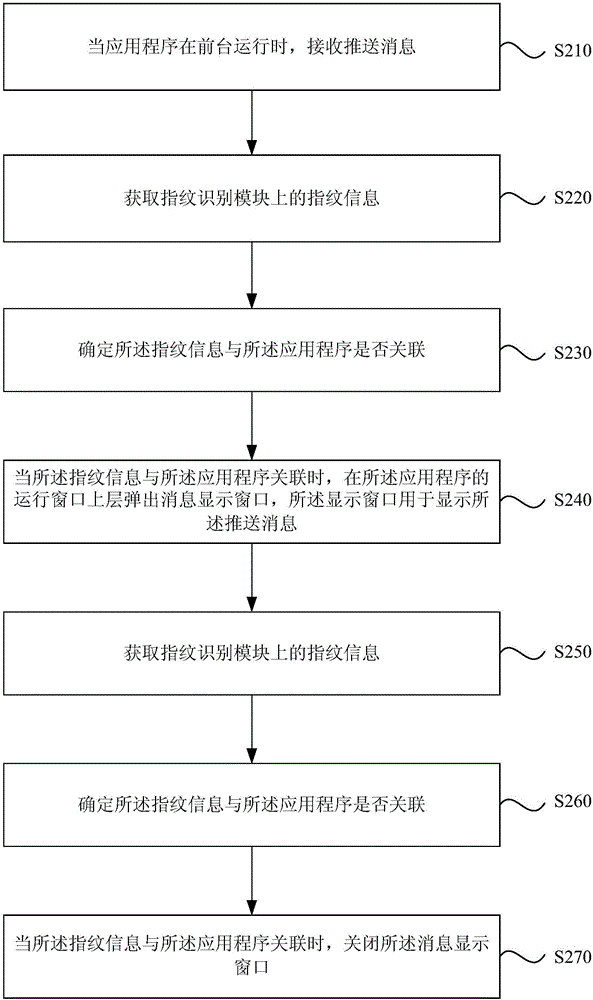
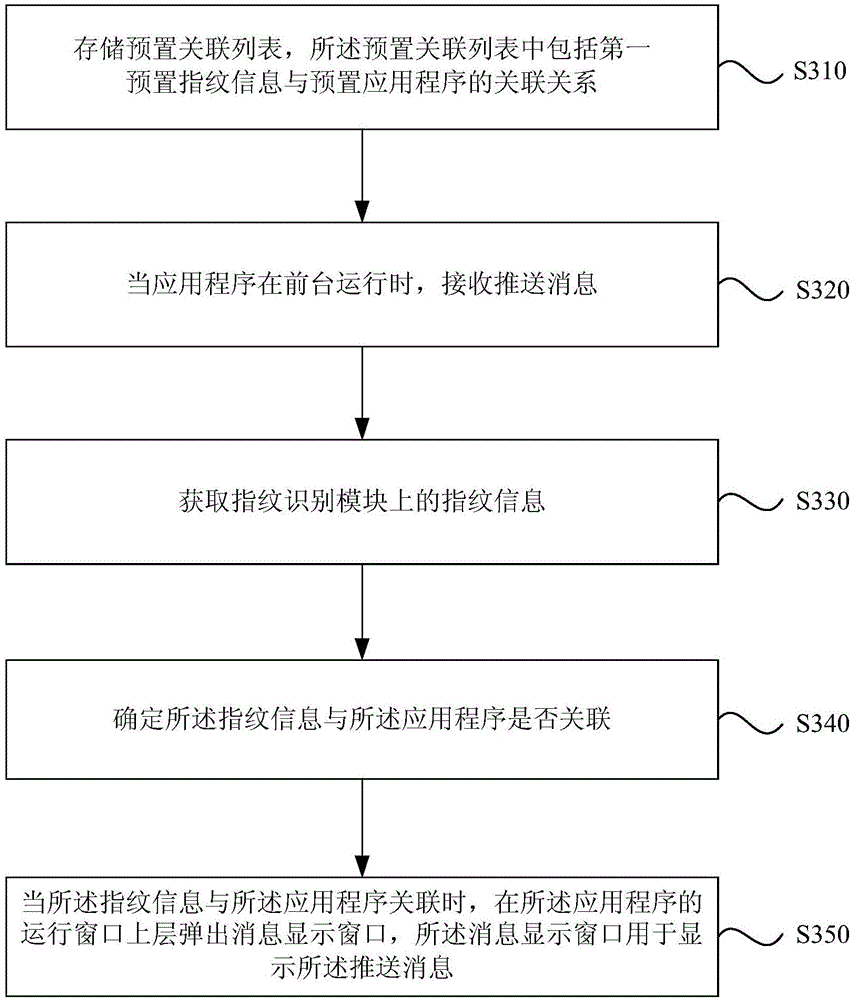
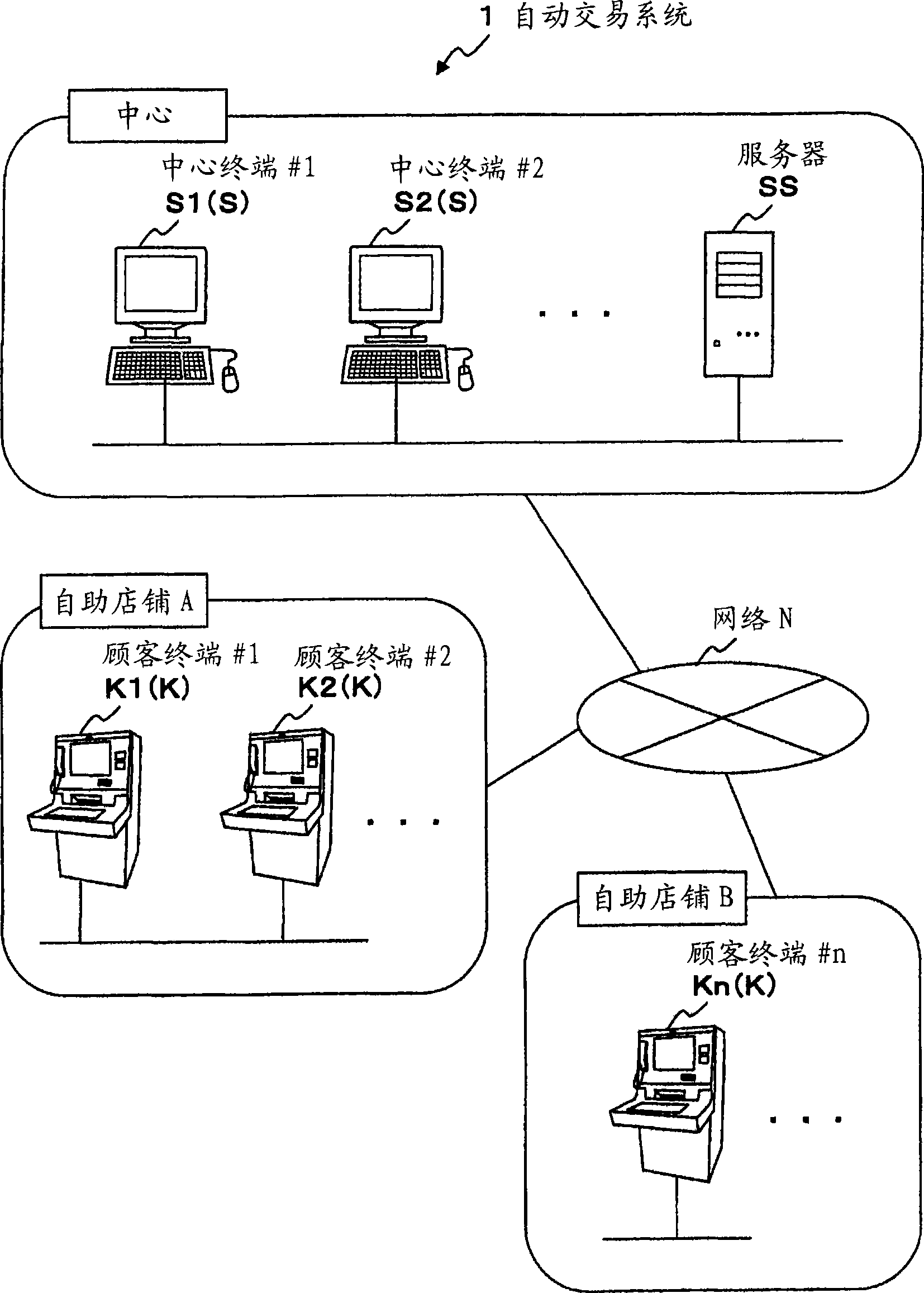
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
122results about "Digital data authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
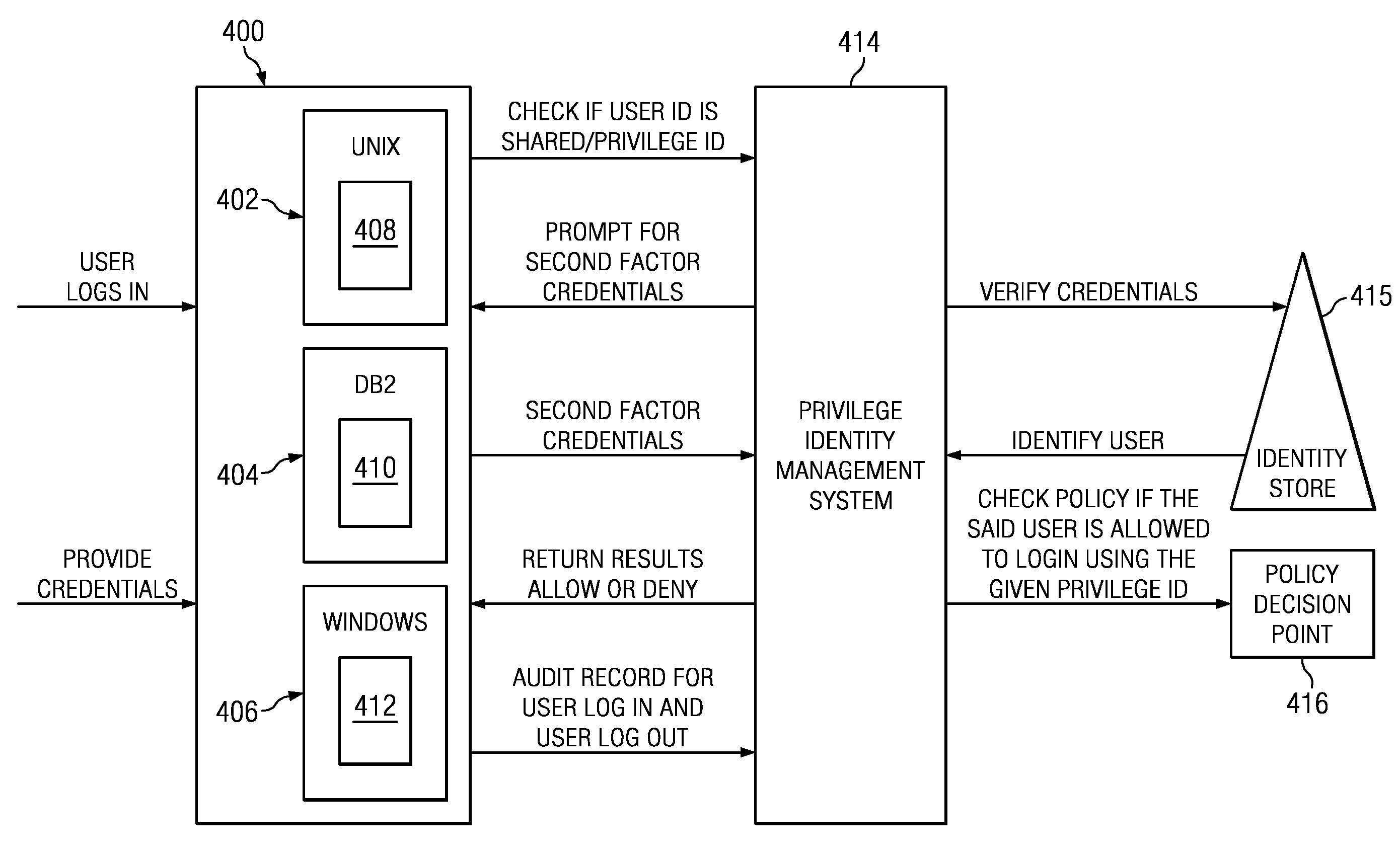
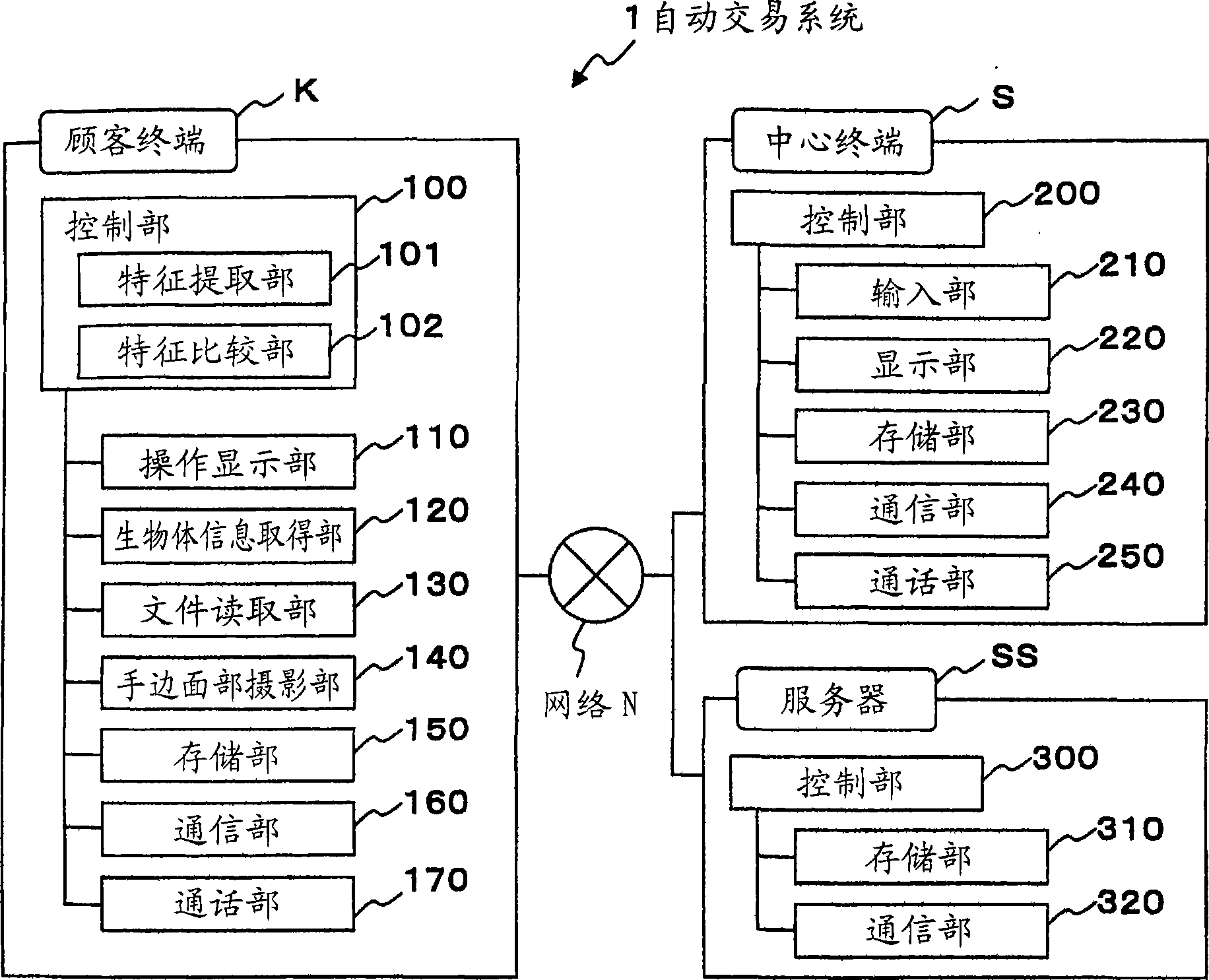
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
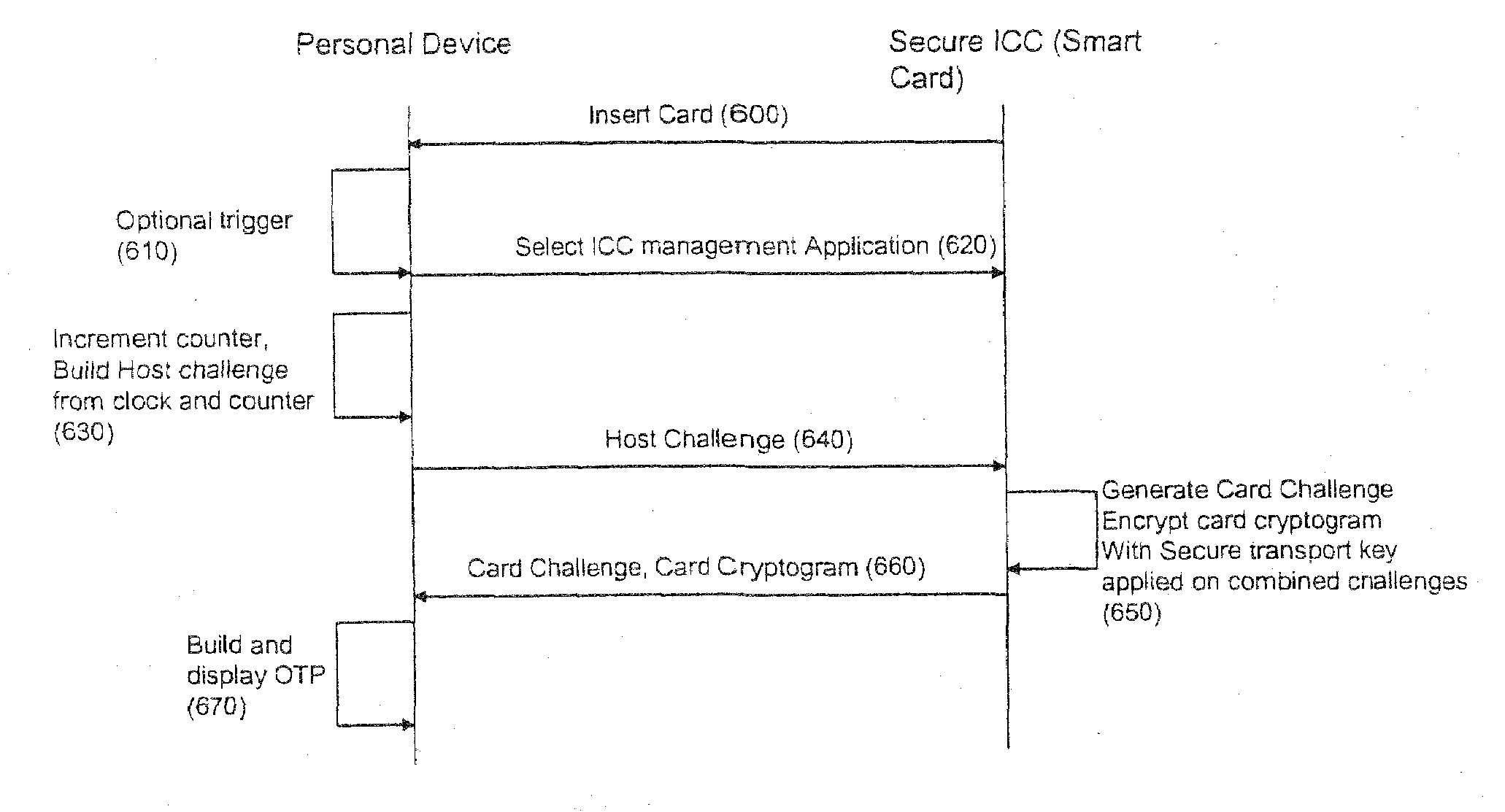
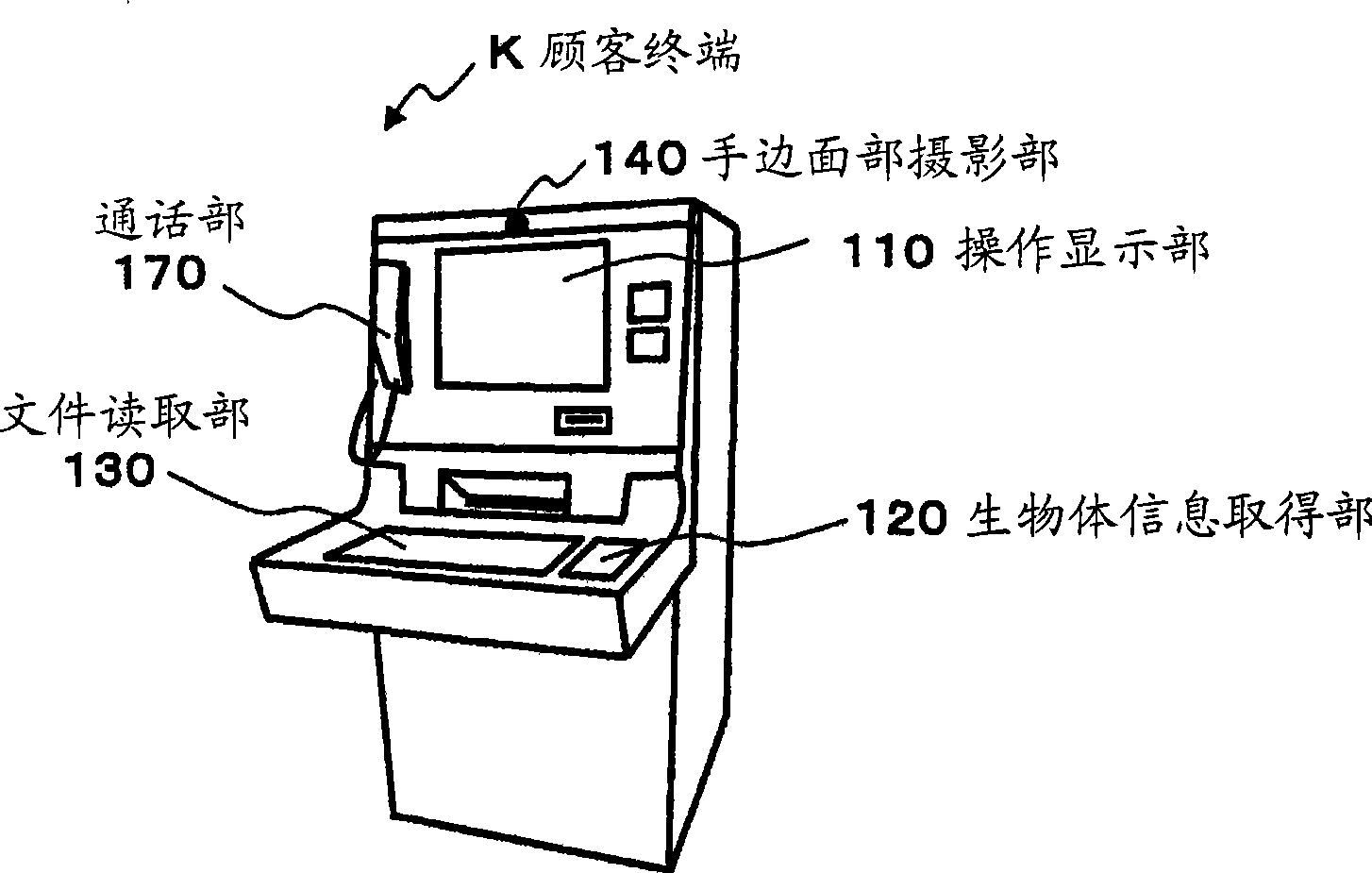
Authentication system and method
InactiveUS20090193264A1Digital data authenticationCoded identity card or credit card actuationAuthentication systemStrong authentication
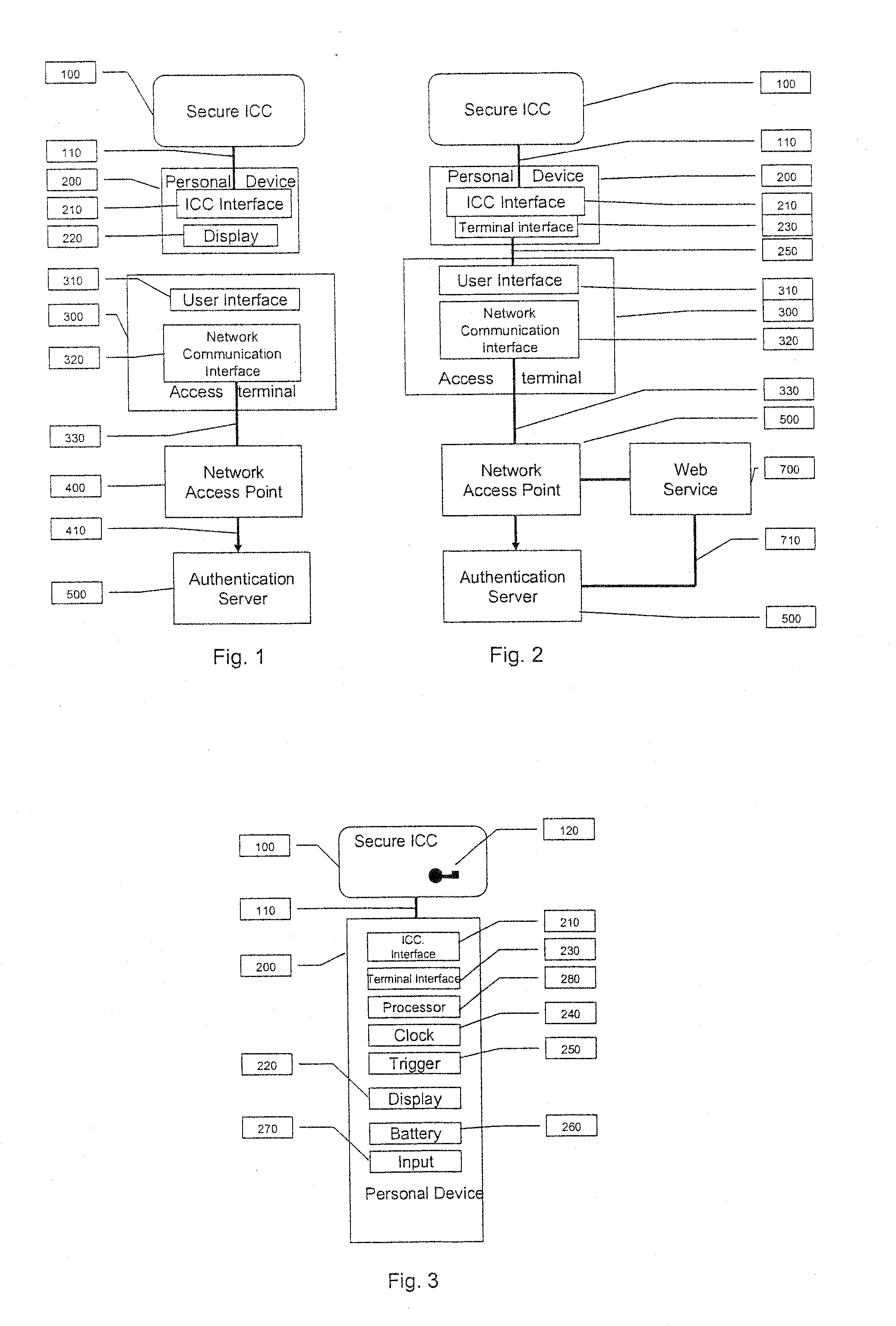
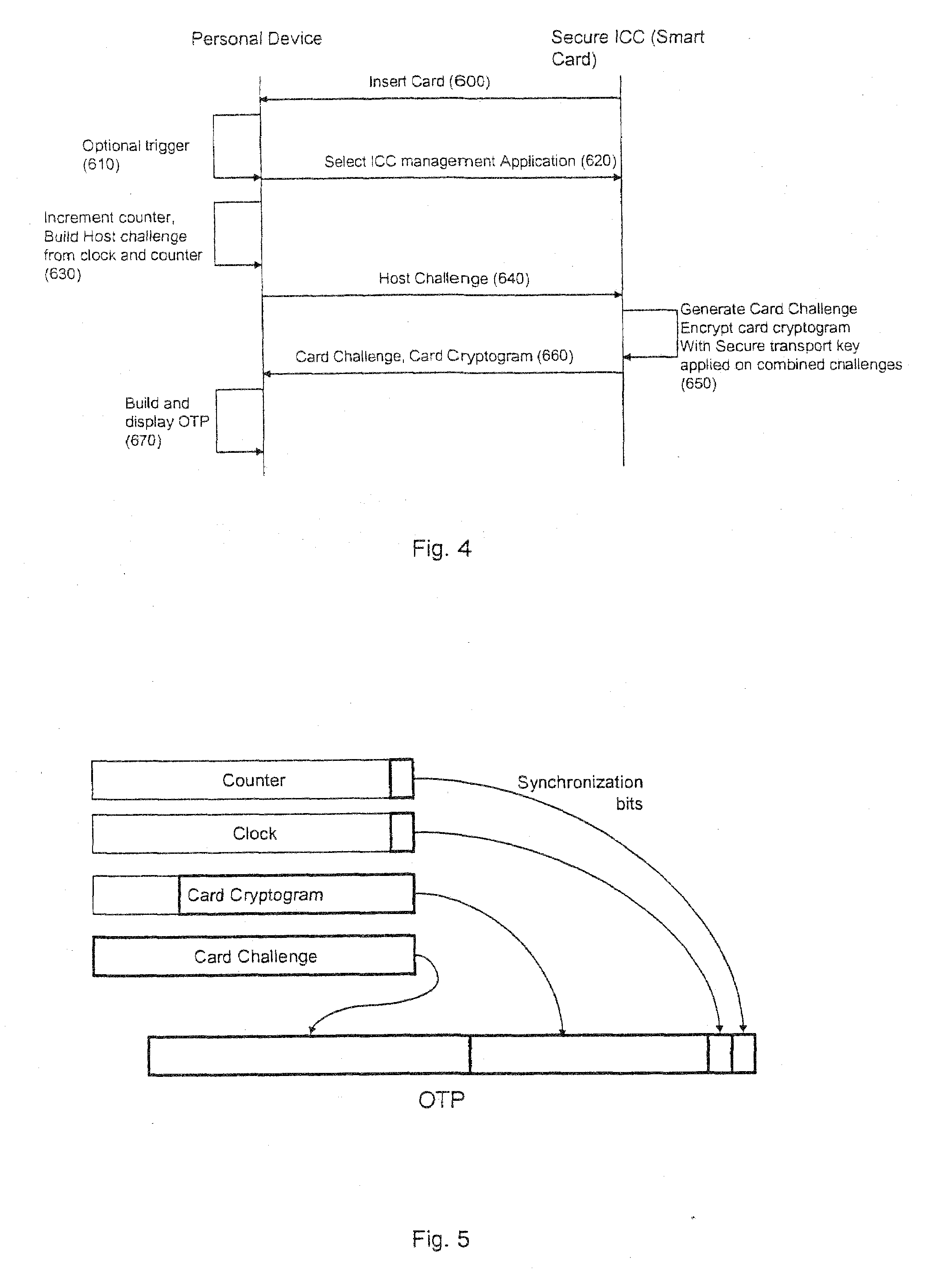
A strong authentication method and system using a Secure ICC component coupled with a Personal device, and relying on the existing cryptographic protocols and keys for managing the secure ICC to generate One-Time-Passwords when the necessary authentication keys or cryptographic protocols are not already present in the Secure ICC configuration for that purpose.
Owner:ACTIVIDENTITY
Apparatus and Method for Variable Authentication Requirements
ActiveUS20120239950A1Volume/mass flow measurementUser identity/authority verificationState dependentAuthentication
Owner:LENOVO PC INT
Method of Managing Access Right, and System and Computer Program for the Same
InactiveUS20120095797A1Digital data processing detailsUnauthorized memory use protectionRights managementDigital work
Owner:IBM CORP
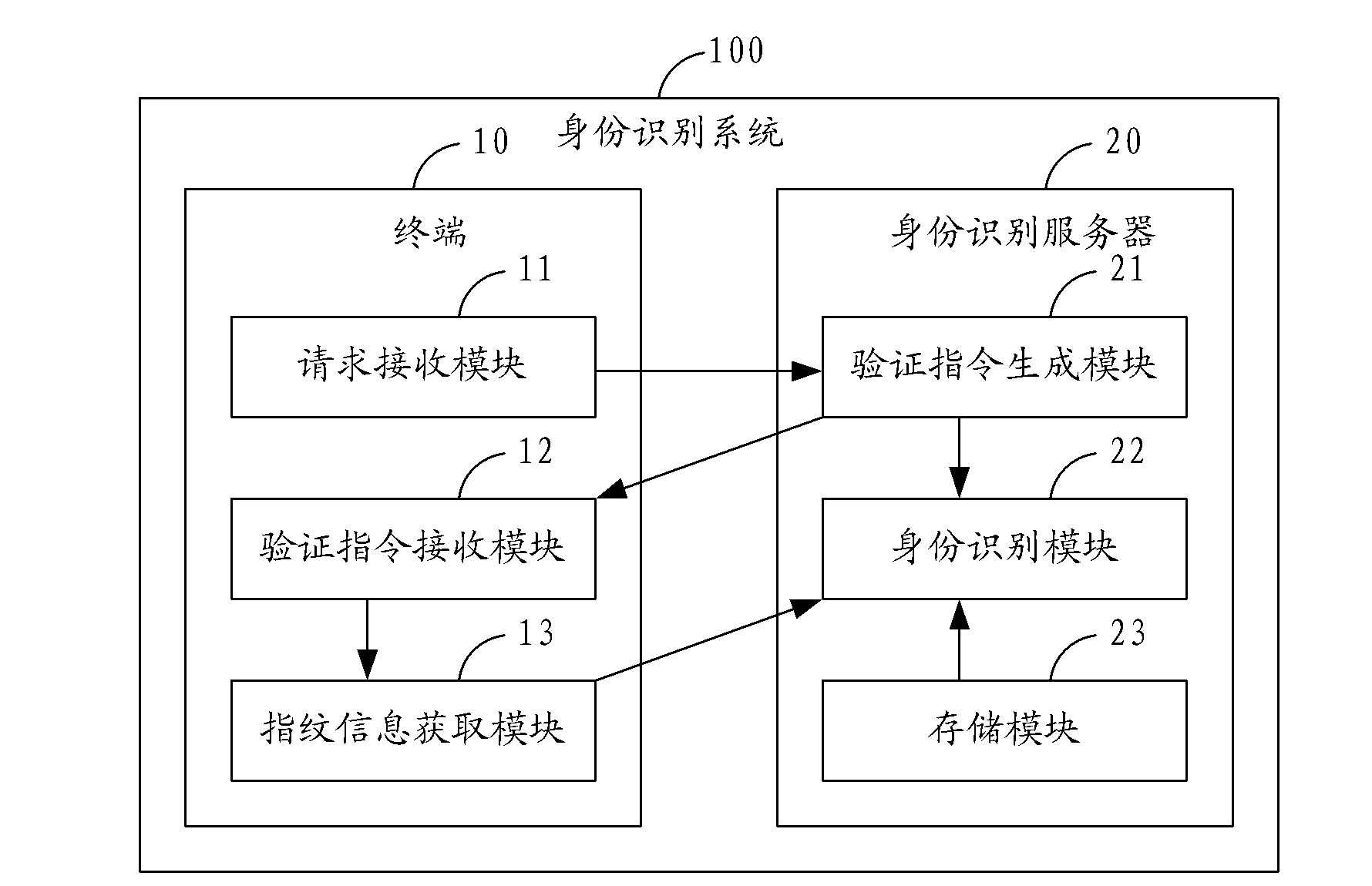
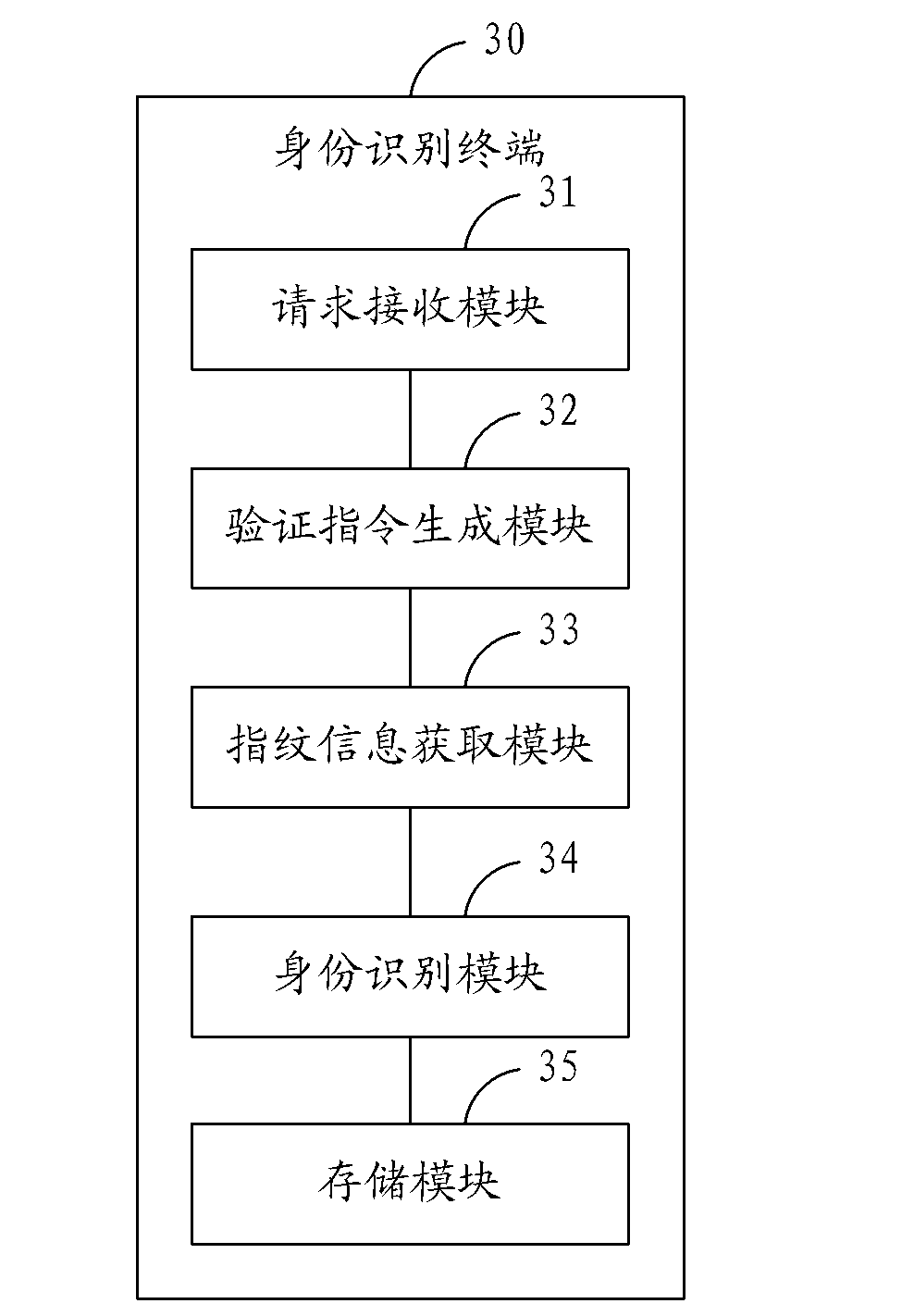
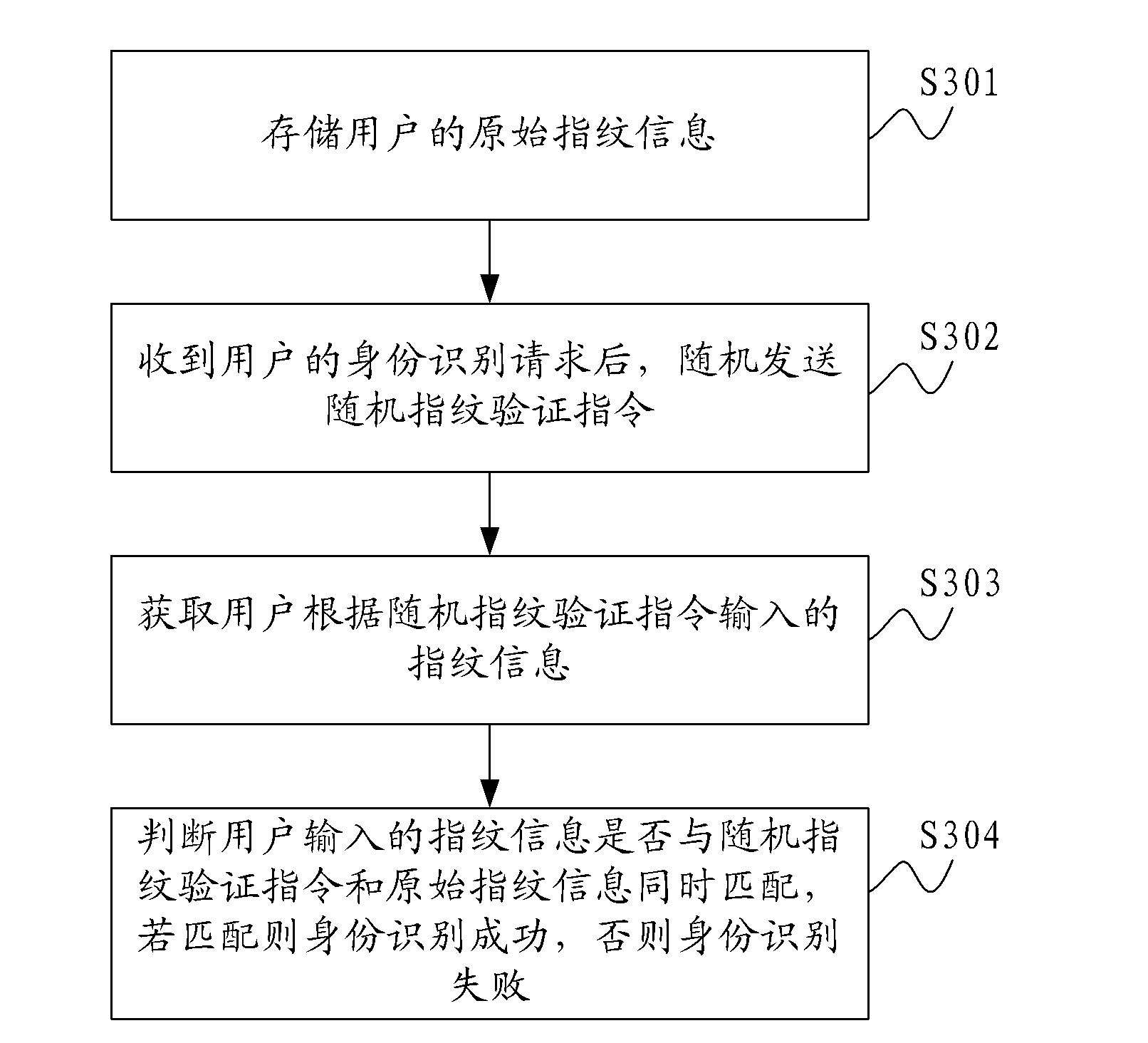
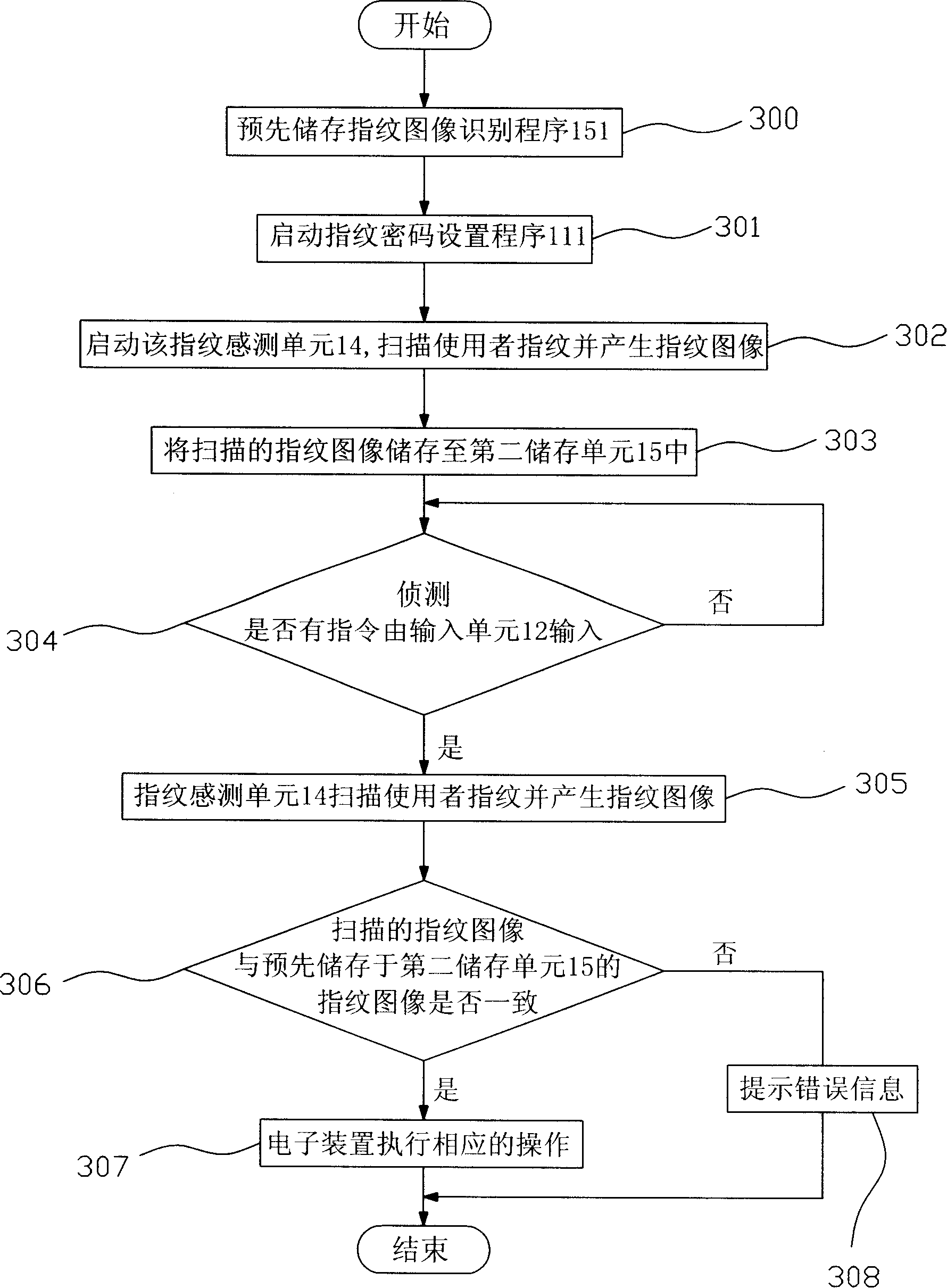
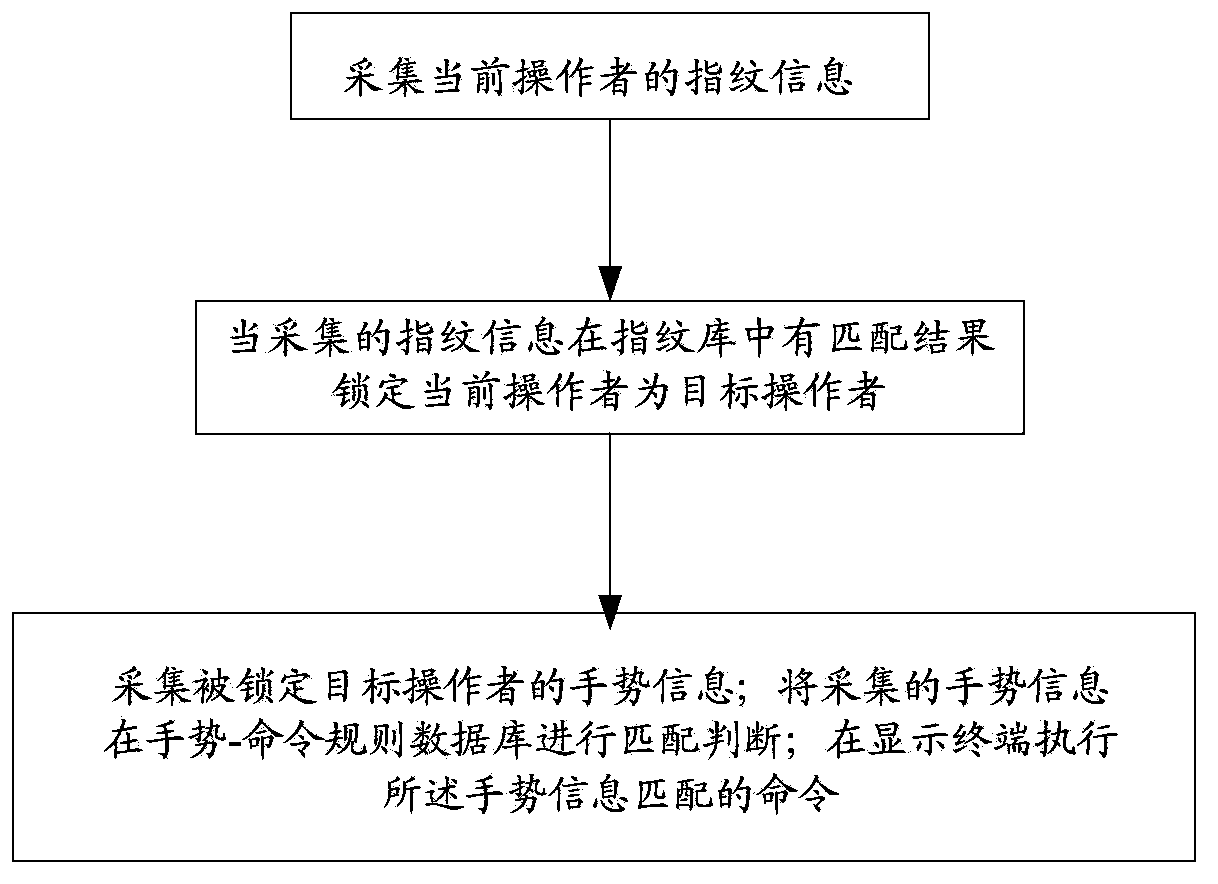
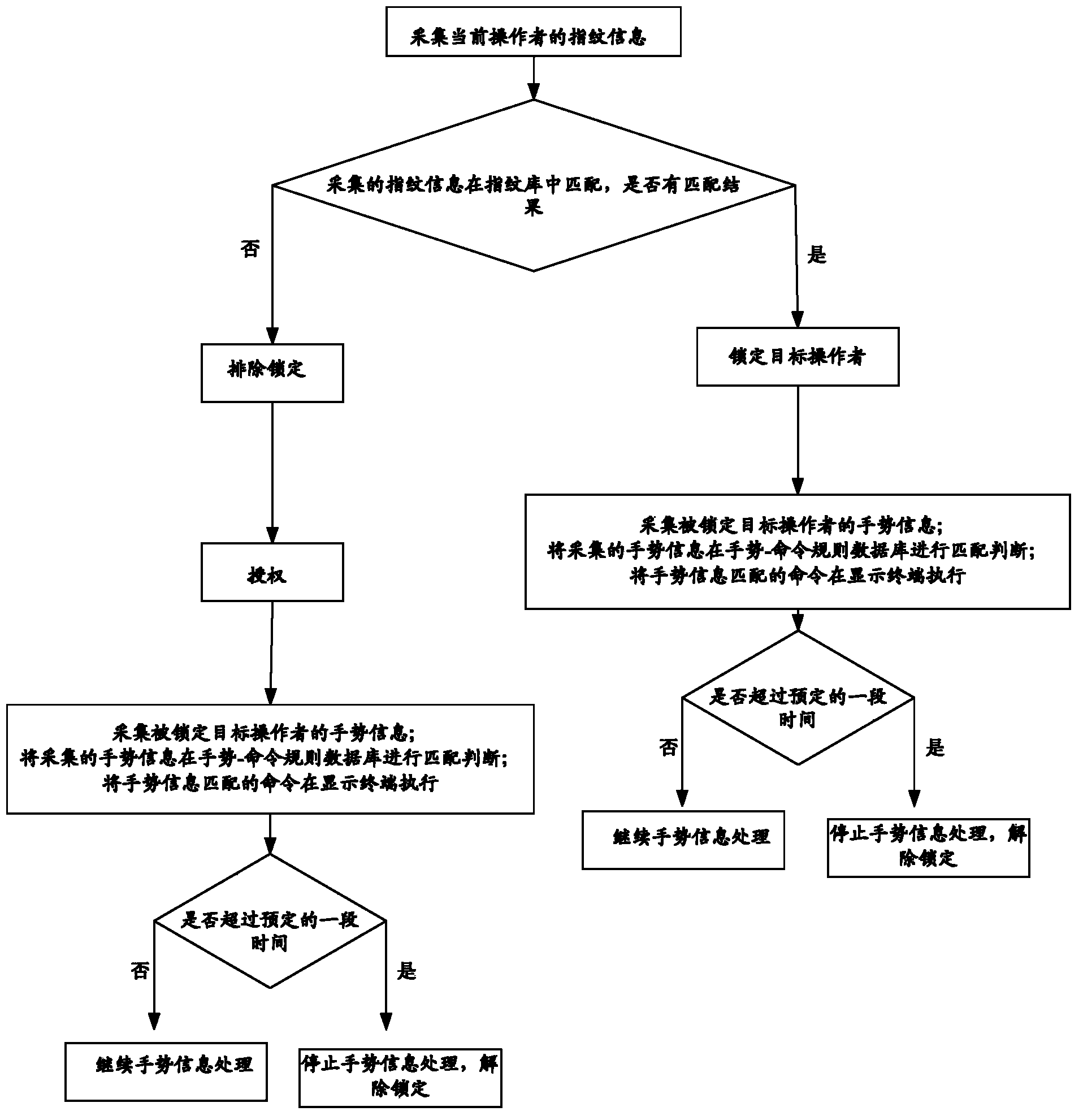
Identity recognition method, identity recognition system and identity recognition terminal
InactiveCN102306286AAvoid illegally stealing user's static fingerprint informationAvoid identificationCharacter and pattern recognitionDigital data authenticationPattern recognitionUser input
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
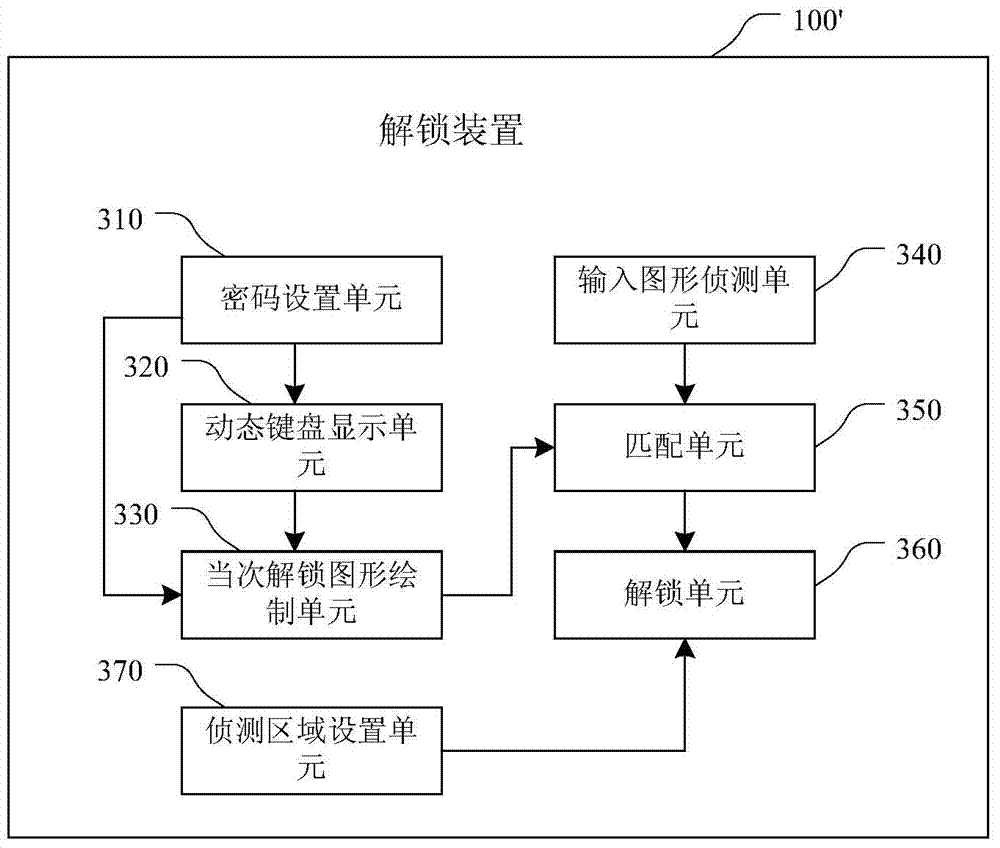
Method and device for unlocking
ActiveCN104766002AReduce risk of leakageEasy to operateDigital data authenticationGraphicsComputer hardware
Owner:NUBIA TECHNOLOGY CO LTD
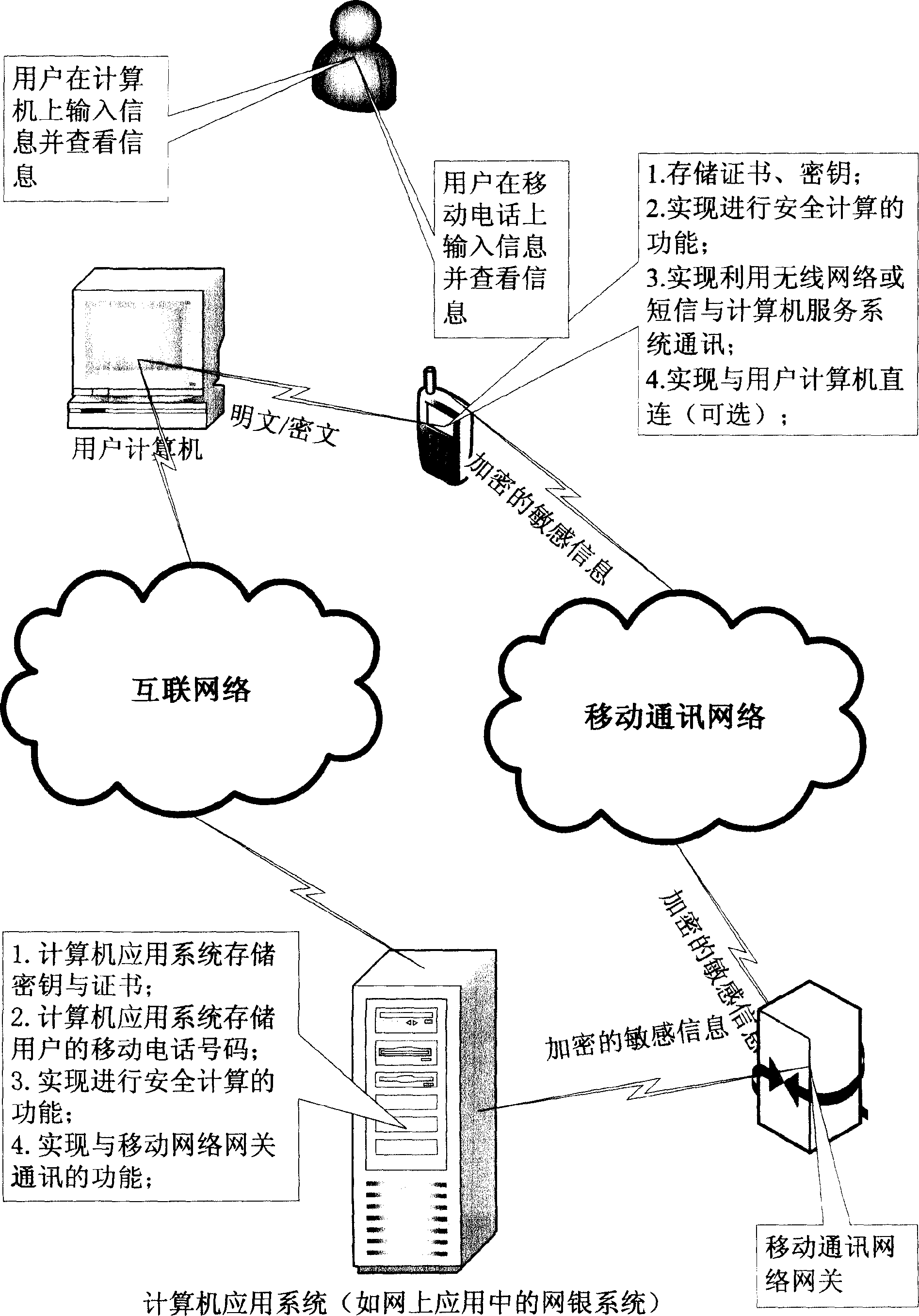
Technology for improving security of accessing computer application system by mobile phone
InactiveCN1838141APrevent leakageGuaranteed isolationDigital data authenticationPasswordPersonal computer
Owner:刘亚威
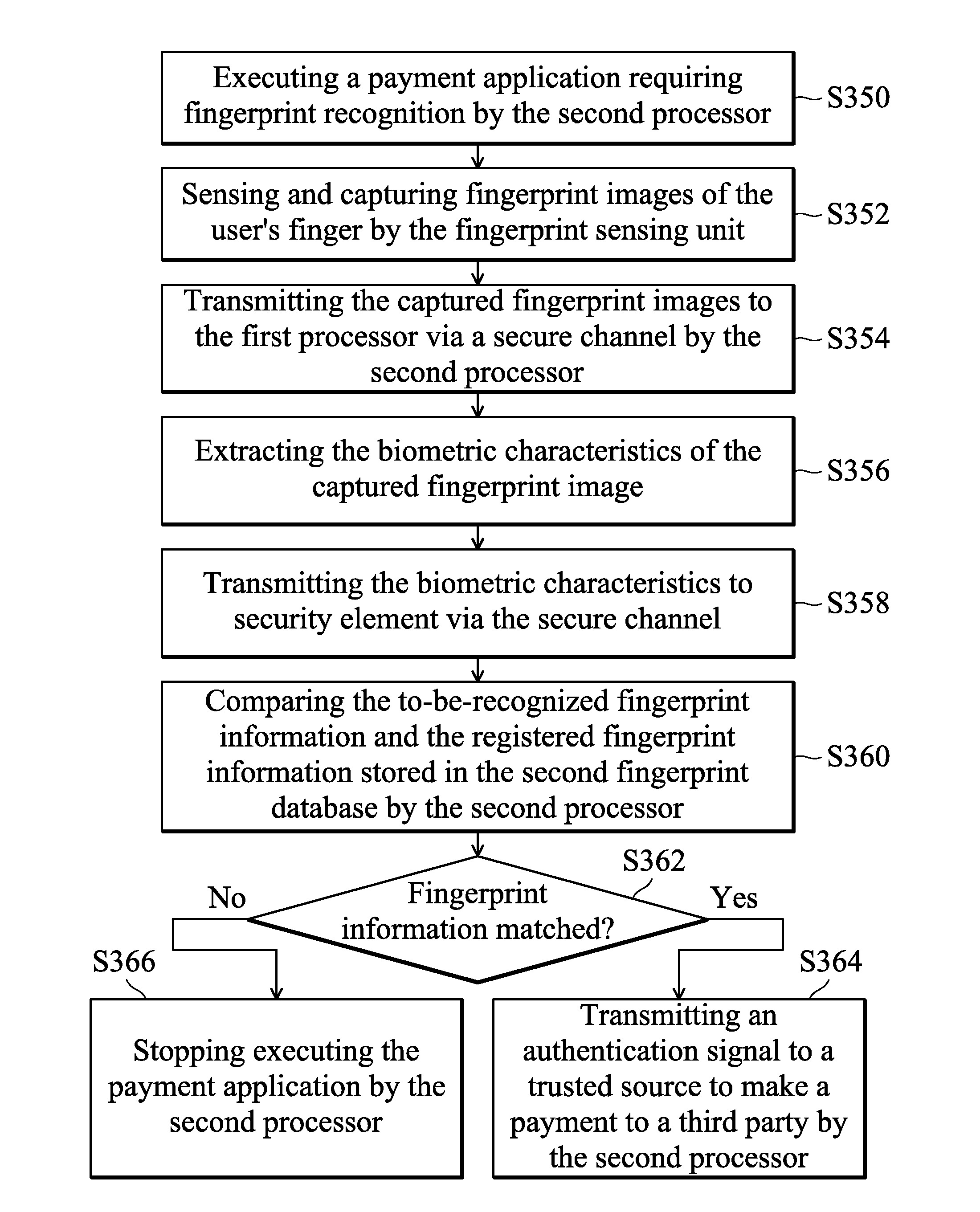
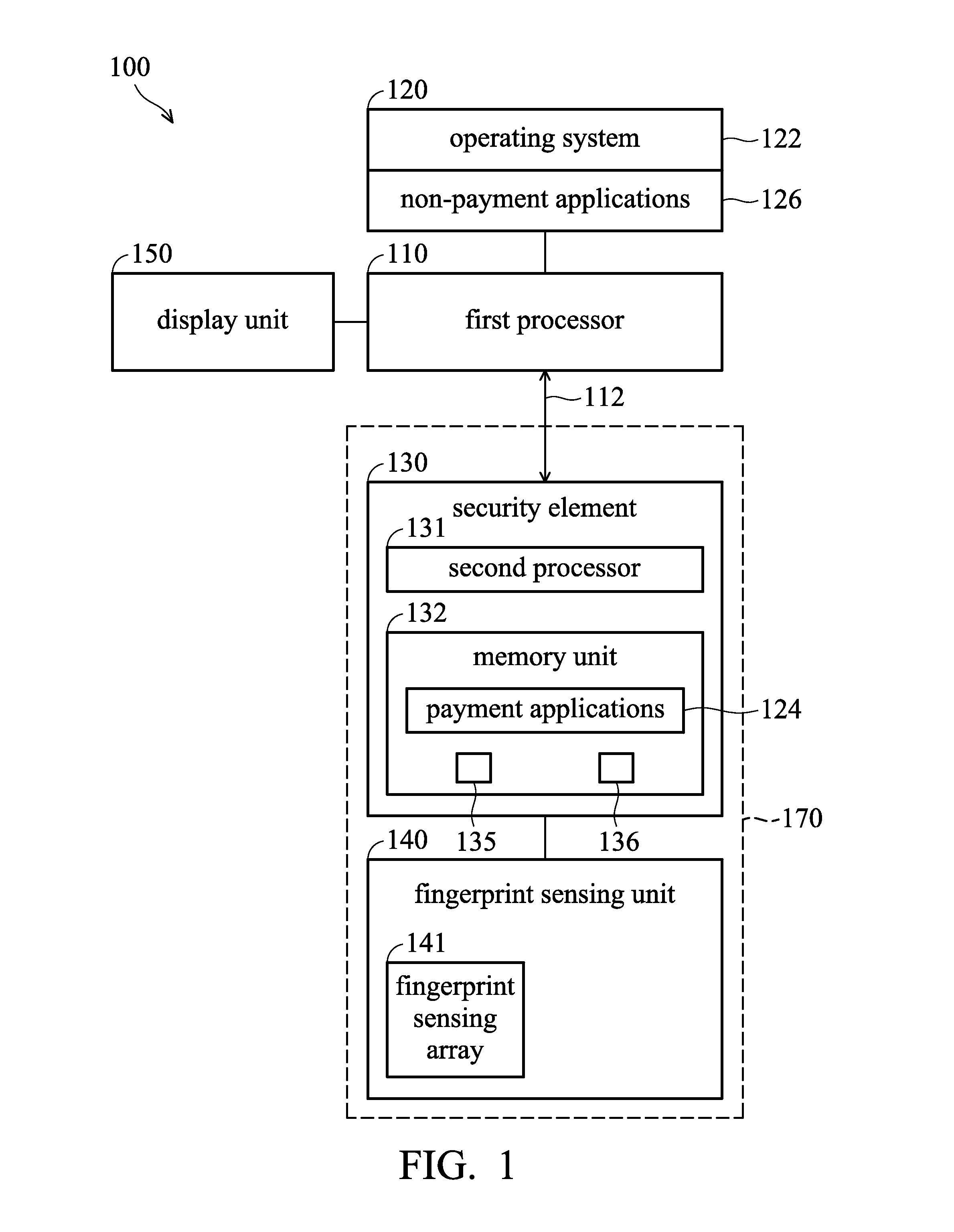
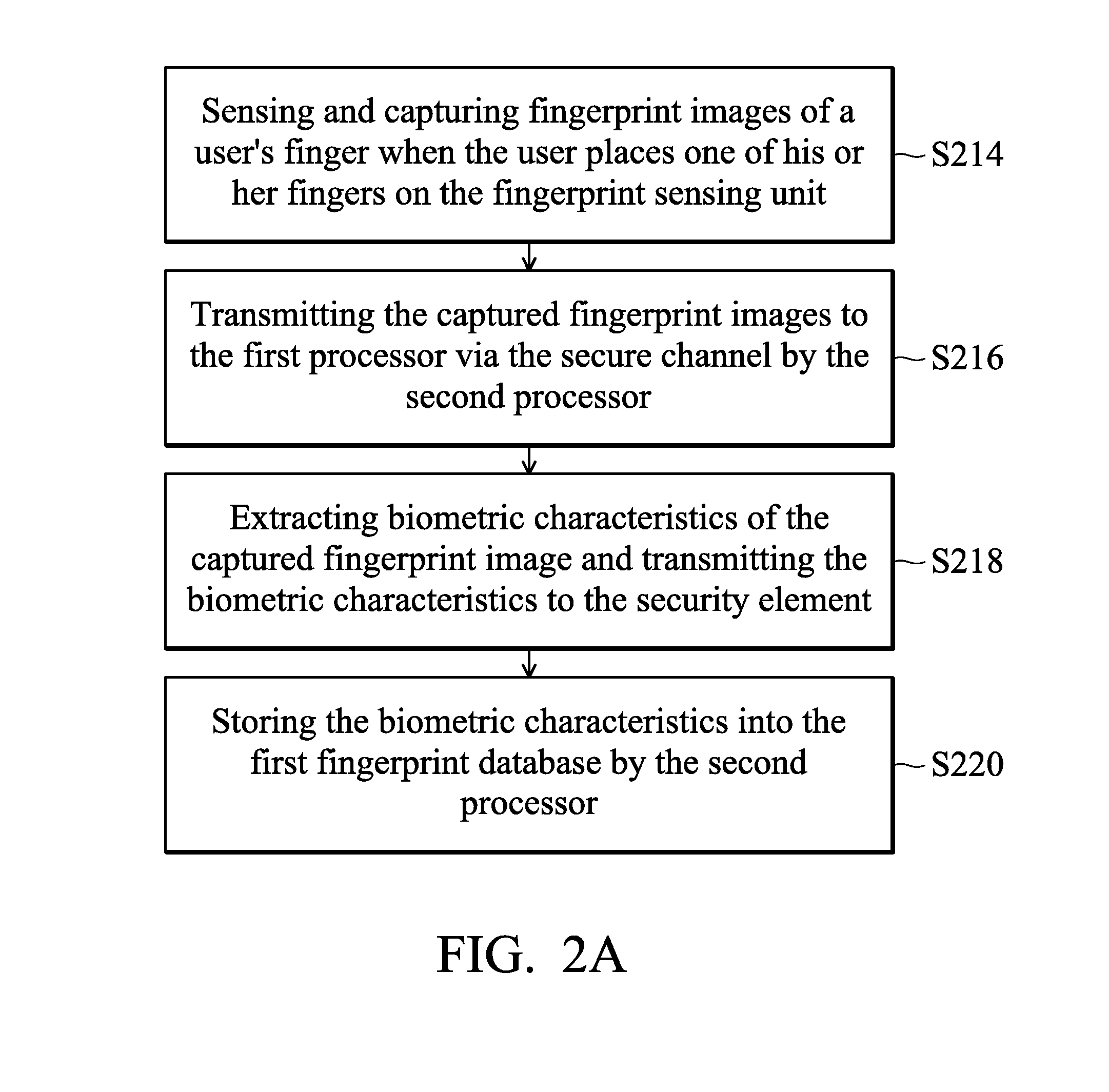
Fingerprint recognition control methods for payment and non-payment applications
ActiveUS20160048840A1Internal/peripheral component protectionDigital data authenticationPayment transactionComputer hardware
Owner:EGIS TECH
Electronic device possessing fingerprint identification system and its usage method
InactiveCN101169810ACharacter and pattern recognitionDigital data authenticationFingerprintFingerprint image
Owner:HUANDA COMPUTER (SHANGHAI) CO LTD
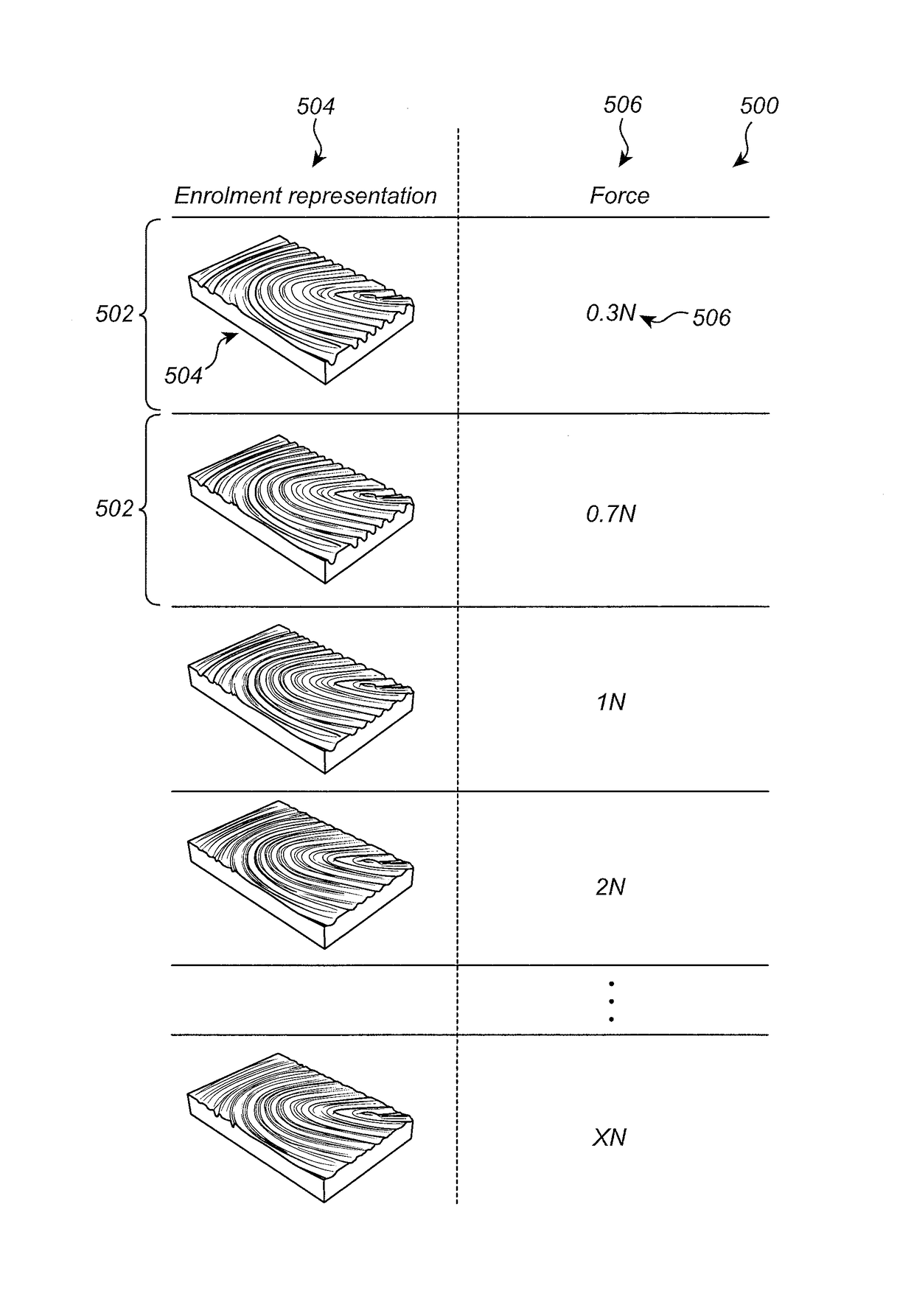
Fingerprint sensor with force sensor
Owner:FINGERPRINT CARDS ANACATUM IP AB
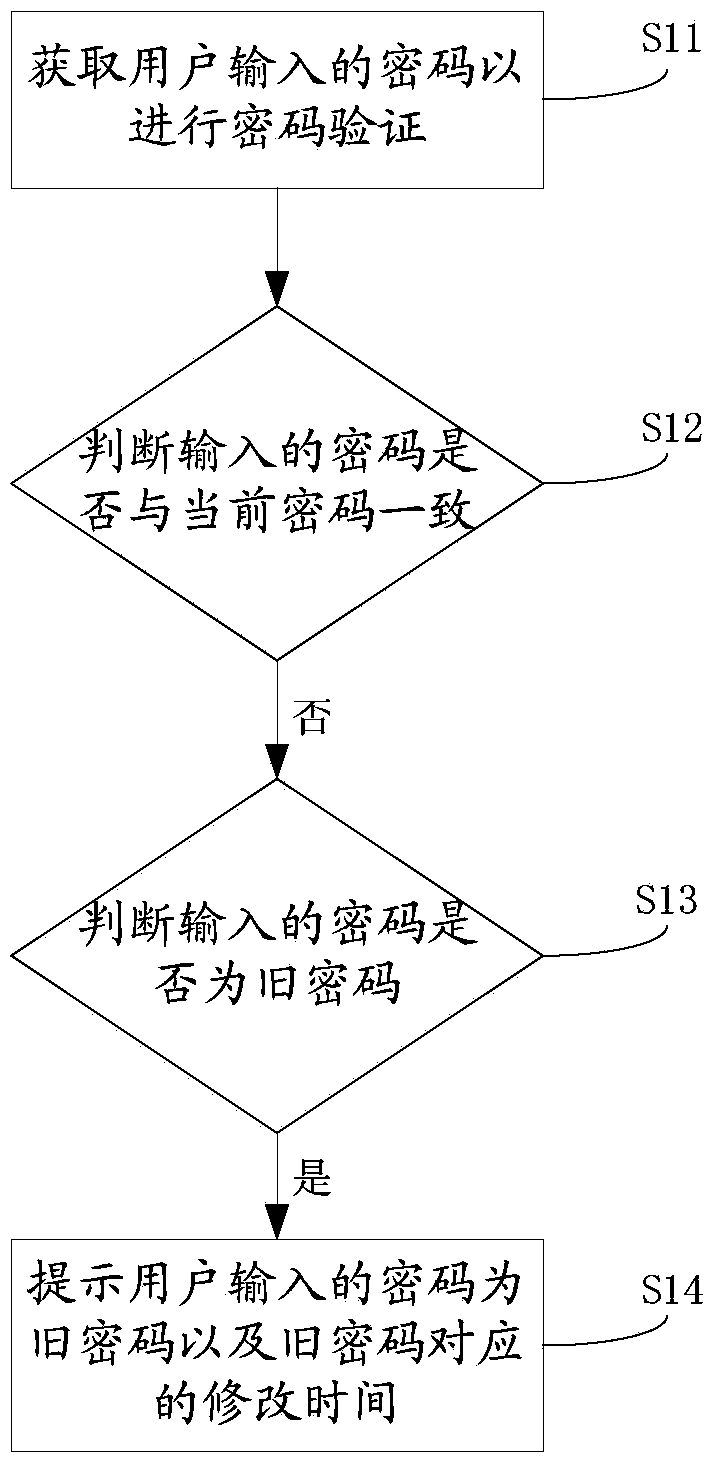
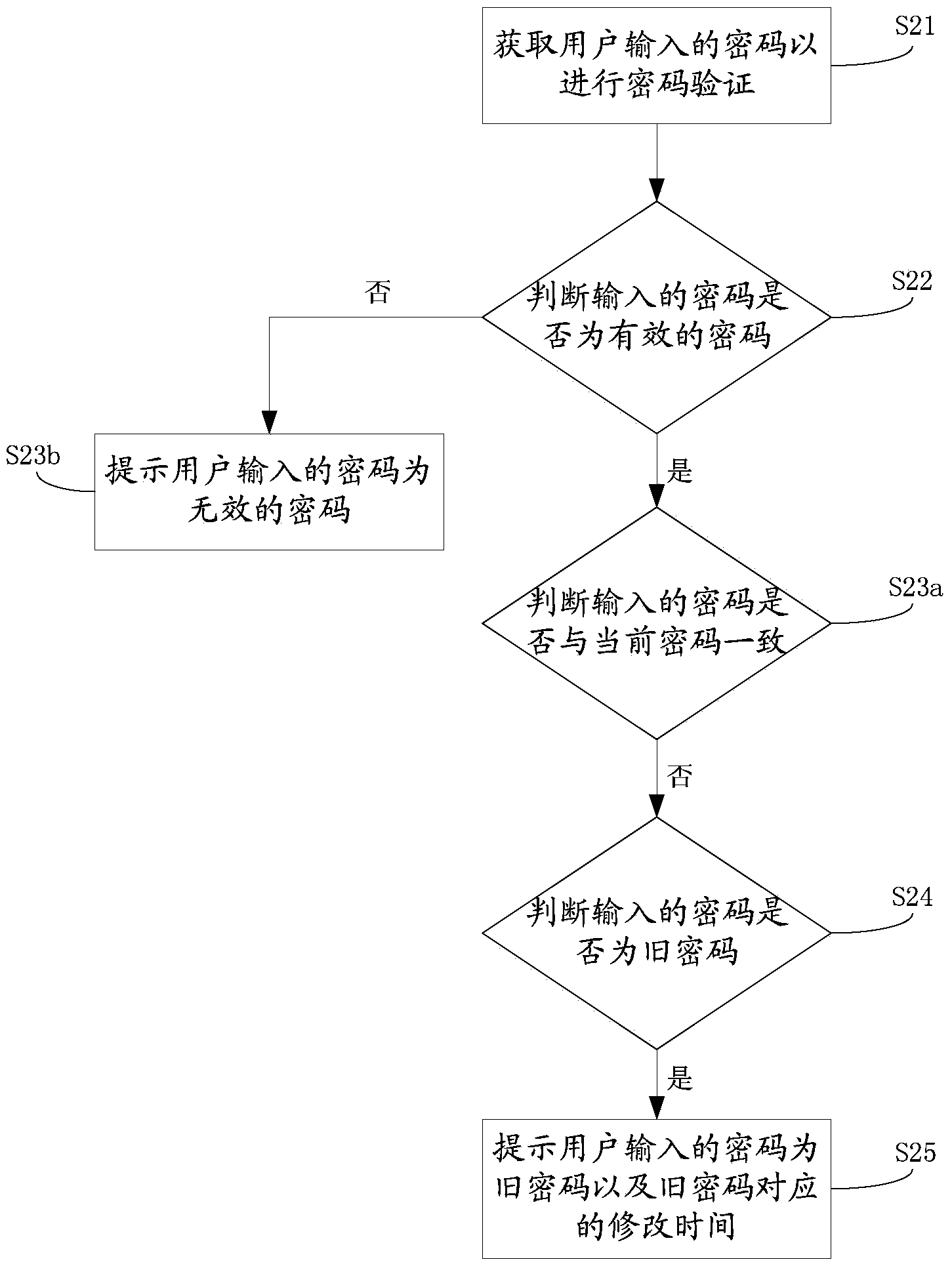
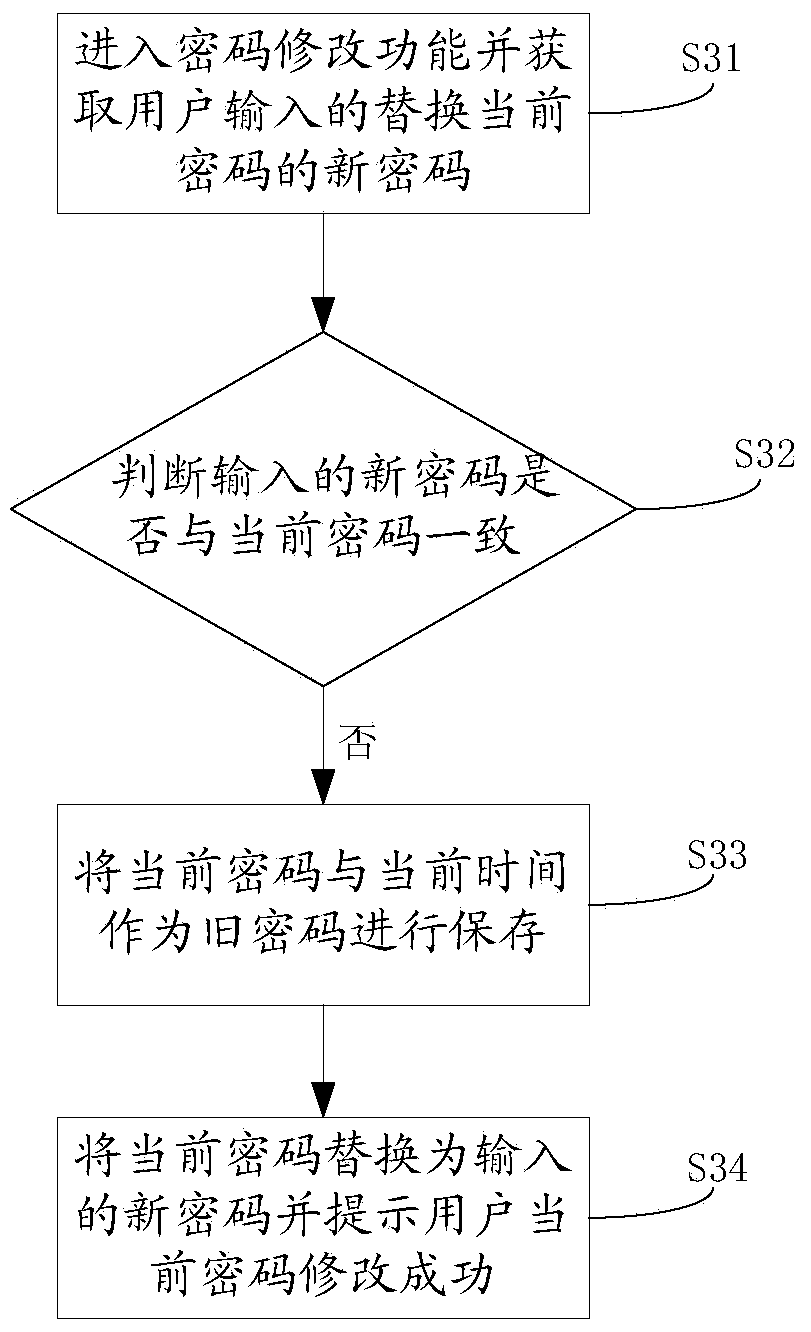
After-password-input prompt method, password modifying method and electronic equipment
ActiveCN103413081AImprove the efficiency of entering the correct passwordReduce the number of times you enter wrong passwordsDigital data authenticationUser inputPassword
Owner:威海神舟信息技术研究院有限公司
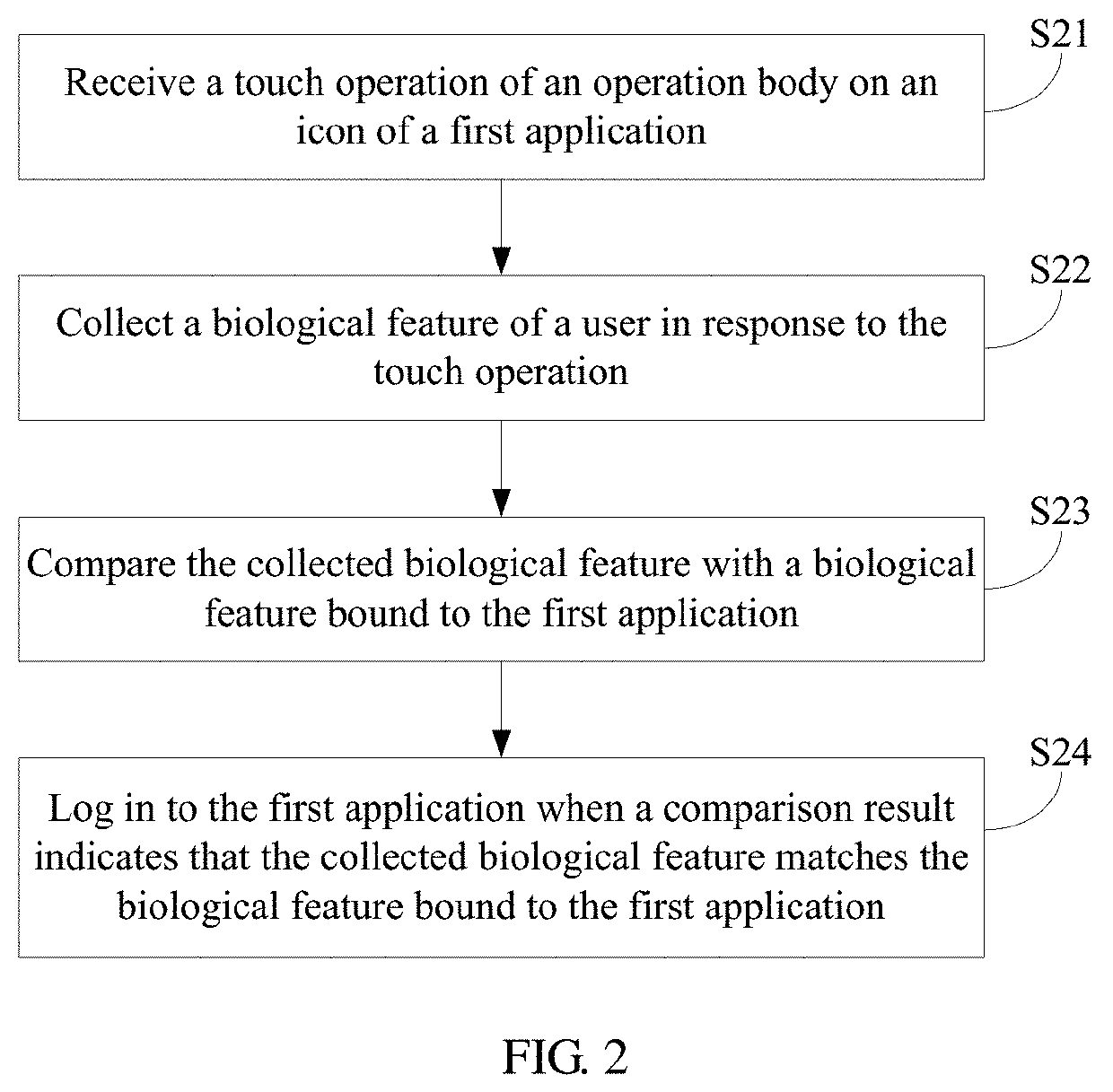
Authentication Method and Electronic Device
ActiveUS20190354661A1Complicated operationInternal/peripheral component protectionDigital data authenticationHuman–computer interactionAuthentication
Owner:HUAWEI TECH CO LTD
Method of managing shared file and device for authenticating subscriber by using same
InactiveUS20150271173A1Program control using stored programsDigital data processing detailsComputer moduleTerminal equipment
Owner:KT CORP
Methods of authenticating a user for data exchange
A method of facilitating the exchange of data between a user having a computing device, and a remote entity, where a first connection has been established between the user and the remote entity, and where the user has associated data exchange information with an application on the computing device, the data exchange information defining properties of the data to be exchanged between the user and the remote entity. The method comprises establishing, at a server, a second connection to the computing device; enabling retrieval of a user authentication attribute associated with the data exchange information; enabling retrieval of a device authentication attribute associated with the data exchange information;enabling authentication of the user using the user authentication attribute; and enabling authentication of the computing device using the device authentication attribute, where data may be exchanged between the computing device and the remote entity in accordance with the data exchange information following authentication of the user and the computing device.
Owner:ECKOH UK
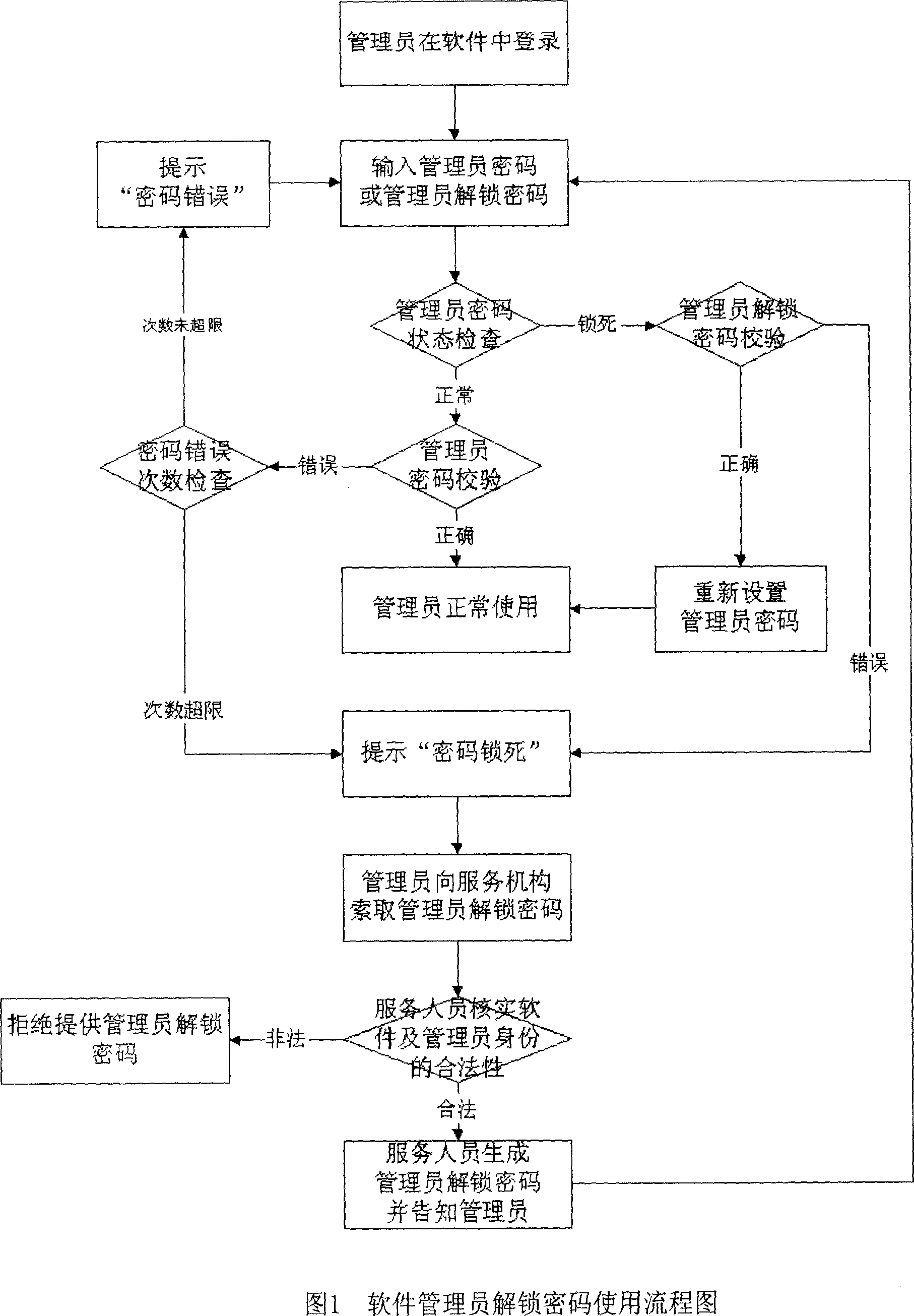
Method for administrator to unlock password
InactiveCN1967556AAvoid the disadvantages of easy leakageReduce lossesDigital data authenticationPasswordSoftware engineering
Owner:BEIJING ZHONGXINGTONG ELECTRONICS TECH
Program protection method and device
ActiveCN103853943ADigital data authenticationProgram/content distribution protectionCiphertextSource code
Owner:BEIJING AUTONAVI YUNMAP TECH CO LTD
Touch-screen-terminal customized lock screen system
InactiveCN104200151AEnough informationAdd funDigital data authenticationInput/output processes for data processingPersonalizationPassword
The invention relates to a touch-screen-terminal customized lock screen system which comprises a lock-screen attribute setting subsystem and a lock-screen password setting subsystem. The lock-screen attribute setting subsystem is used for setting personal attributes of a touch-screen terminal lock screen, and the lock-screen password setting subsystem is used for setting passwords for the touch-screen terminal lock screen; the lock screen attribute setting subsystem comprises password lock-screen background setting modules, a floating-window display content setting module and a password pattern setting module; the password lock-screen background setting modules include background image setting modules and a background music setting module which are used for setting background images and music of the password lock screen; the floating-window display content setting module is used for setting floating-window display content, the floating-window display content can be displayed in a floating-window displaying mode in the touch-screen terminal lock screen state, and the floating-window display content is used for reminding users of some important information content; the password pattern setting module is used for setting password patterns. By the arrangement, personalized touch-screen-terminal customized lock screen system high in interestingness can be customized.
Owner:SUZHOU TIANPING ADVANCED DIGITAL TECH
Man-machine identification method and device based on sliding track and electronic device
InactiveCN109977651AImprove accuracyCharacter and pattern recognitionDigital data authenticationHuman behaviorControl engineering
The invention discloses a man-machine identification method and device based on a sliding track and an electronic device, and the method comprises the steps: collecting a sliding track point of a current sliding operation, and judging whether the current sliding operation meets a preset verification rule or not; if the current sliding operation meets the verification rule, multi-dimensional feature information of the current sliding operation is obtained; processing the multi-dimensional feature information according to a pre-established man-machine identification model, and determining a classification result of the multi-dimensional feature information; and judging whether the current sliding operation is a machine simulation operation or not according to a classification result of the multi-dimensional feature information. According to the method and the device, the accuracy of identifying human behaviors and machine behaviors can be improved.
Owner:GUANGZHOU DUOYI NETWORK TECH +2
Safety control method and system of mobile terminal
Owner:CHINA GREATWALL TECH GRP CO LTD
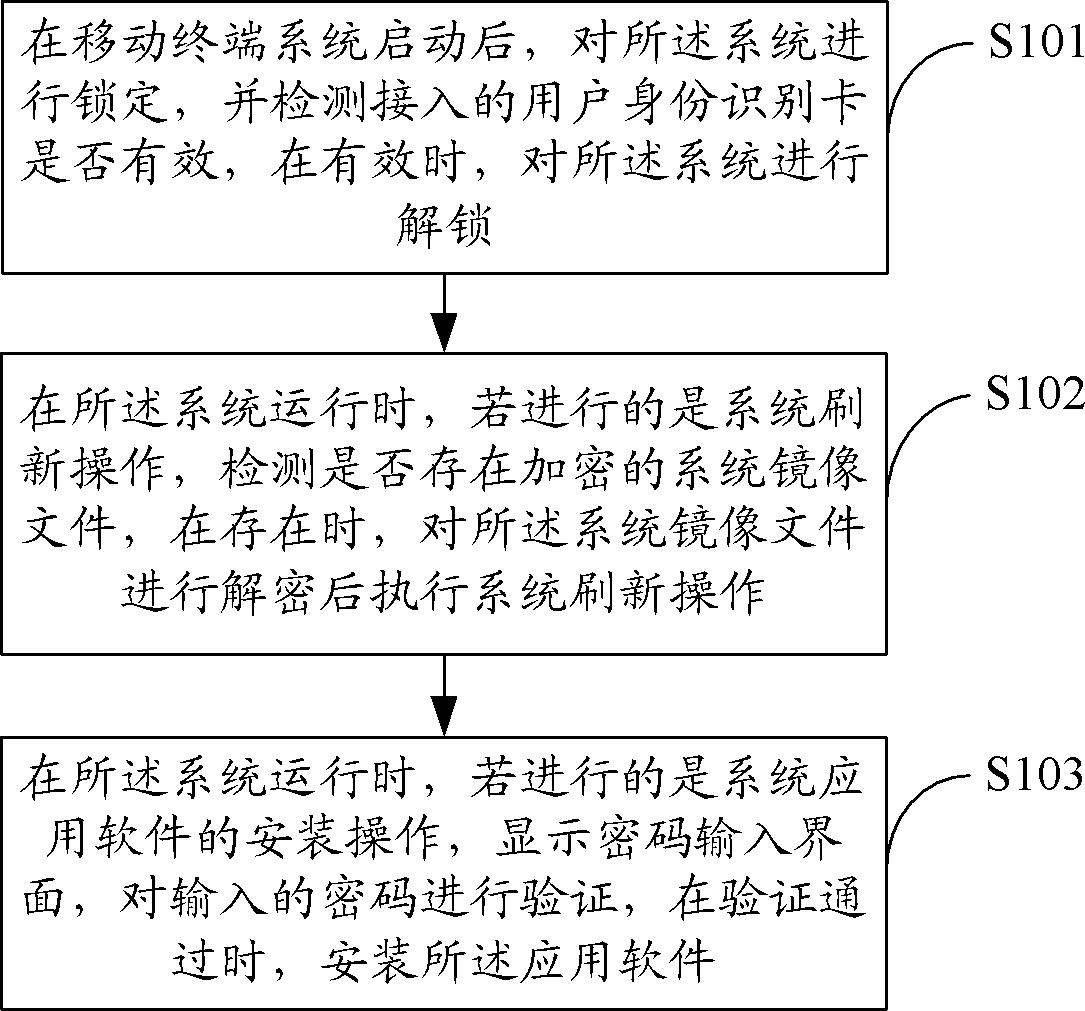
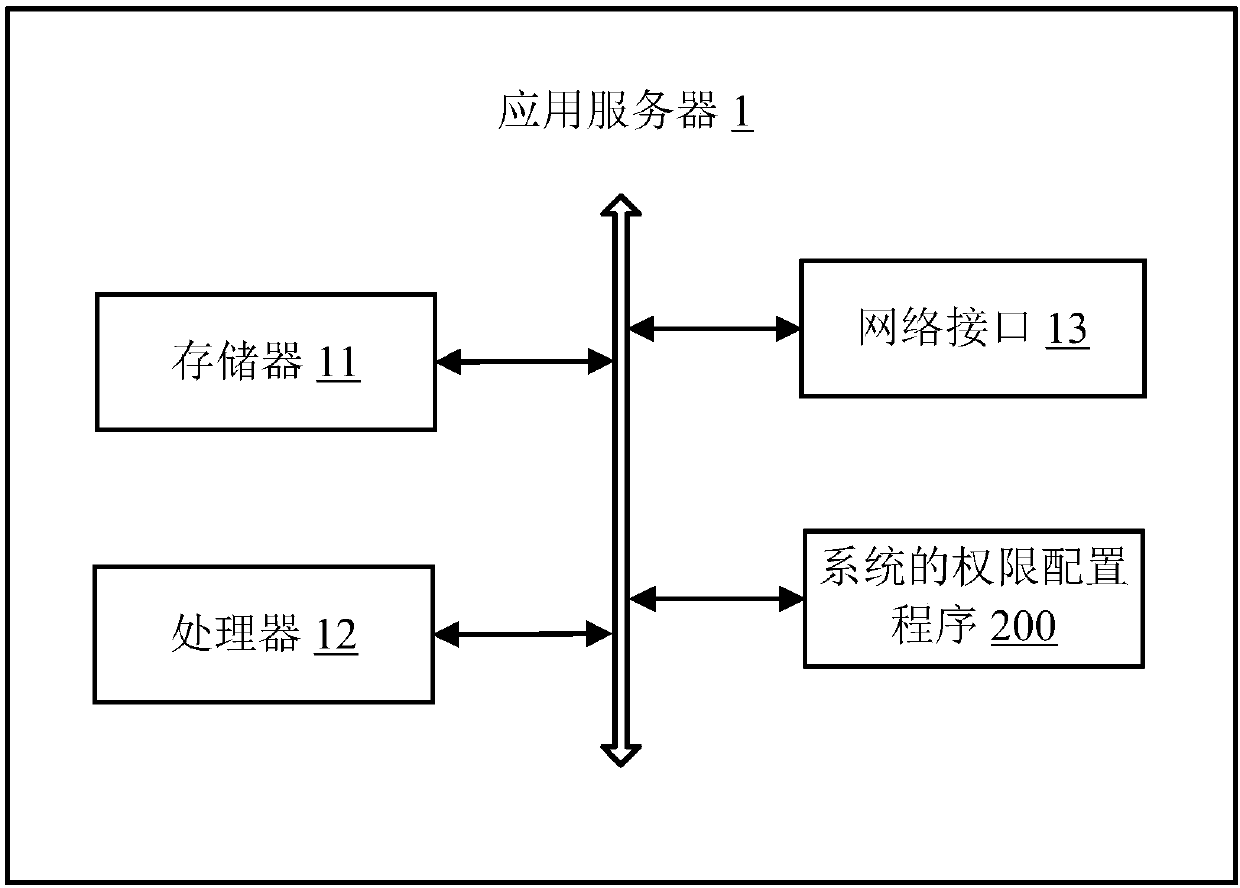
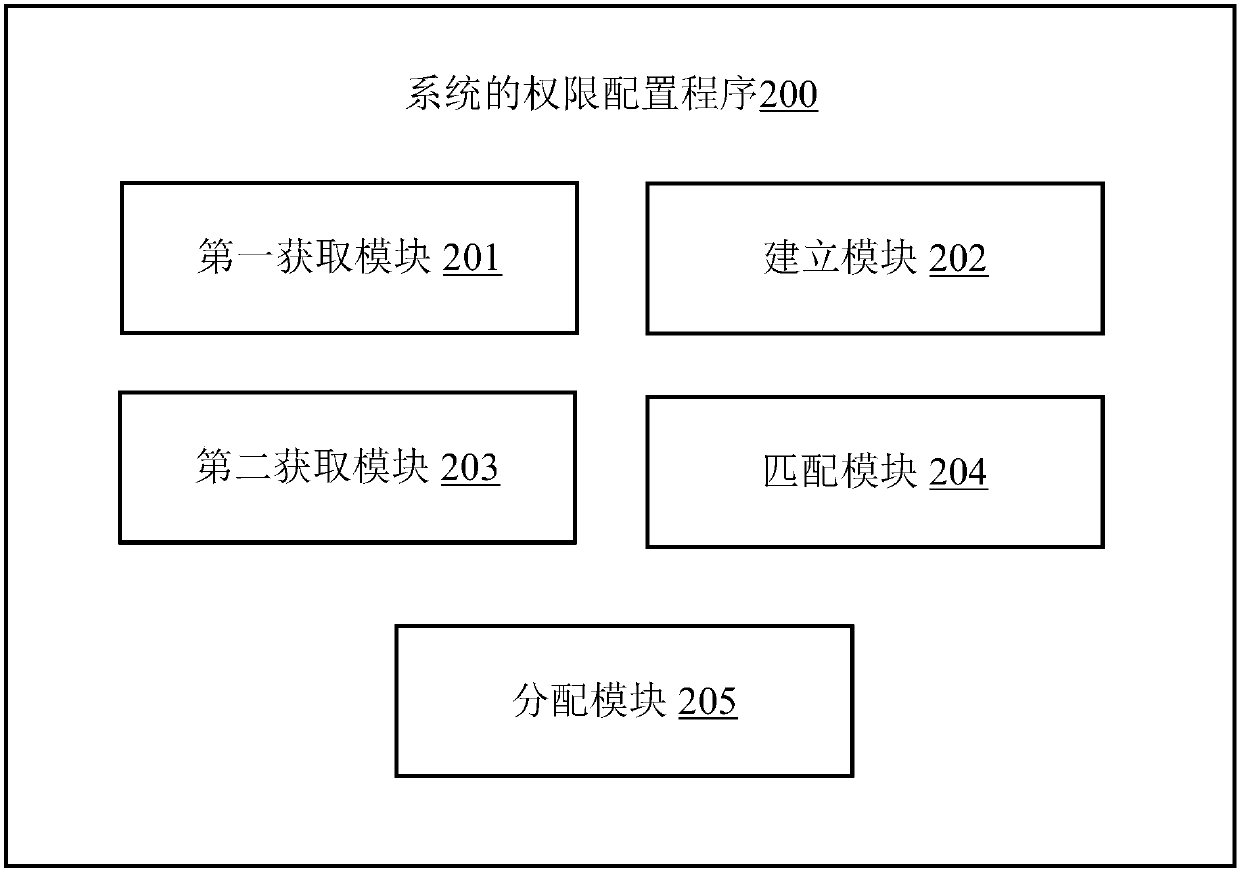
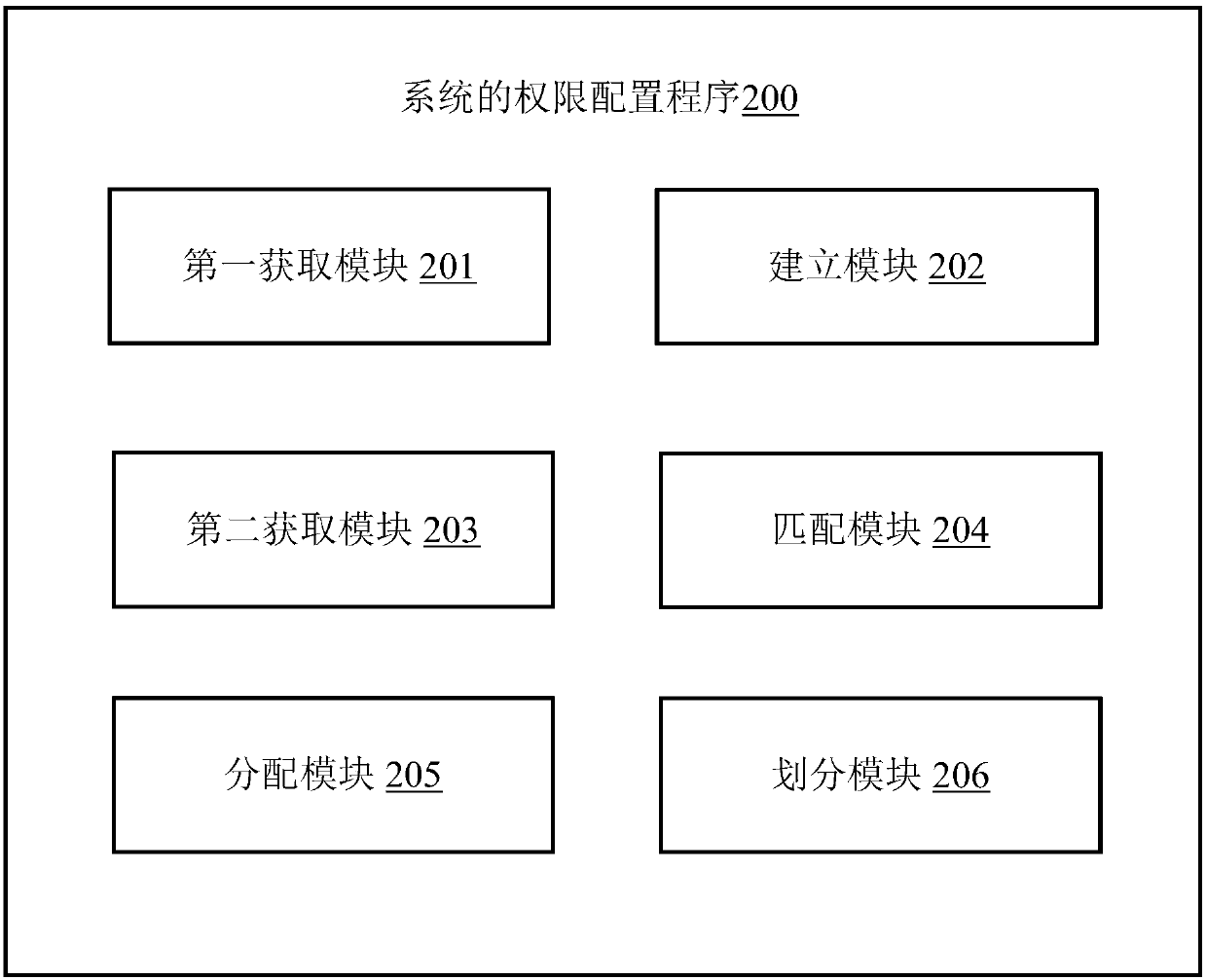
Authority configuring method of system, application server and computer-readable storage medium
InactiveCN107944254AFlexible configurationAvoid the disadvantages of inconvenient operationDigital data authenticationApplication serverComputer science
Owner:PING AN TECH (SHENZHEN) CO LTD
Hand gesture recognition method and device
InactiveCN103366159ADigital data authenticationAcquiring/reconising fingerprints/palmprintsFingerprintPattern recognition
Owner:BOE TECH GRP CO LTD
Information processing apparatus, method for controlling information processing apparatus, and storage medium
ActiveUS20170013170A1Digital data authenticationInput/output processes for data processingInformation processingInternet privacy
Owner:CANON KK
Authentication device including template validation and related methods
ActiveUS20130121542A1Less processing intensiveDigital data authenticationMatching and classificationTemplate basedComputer science
Owner:APPLE INC
Display method and device of push message and terminal
ActiveCN106293711ADigital data authenticationExecution for user interfacesApplication softwareFingerprint recognition
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Automatic traction apparatus and automatic traction system
InactiveCN101499197APrevent wrongdoingComplete banking machinesImage analysisTraction systemFeature extraction
Owner:OKI ELECTRIC IND CO LTD
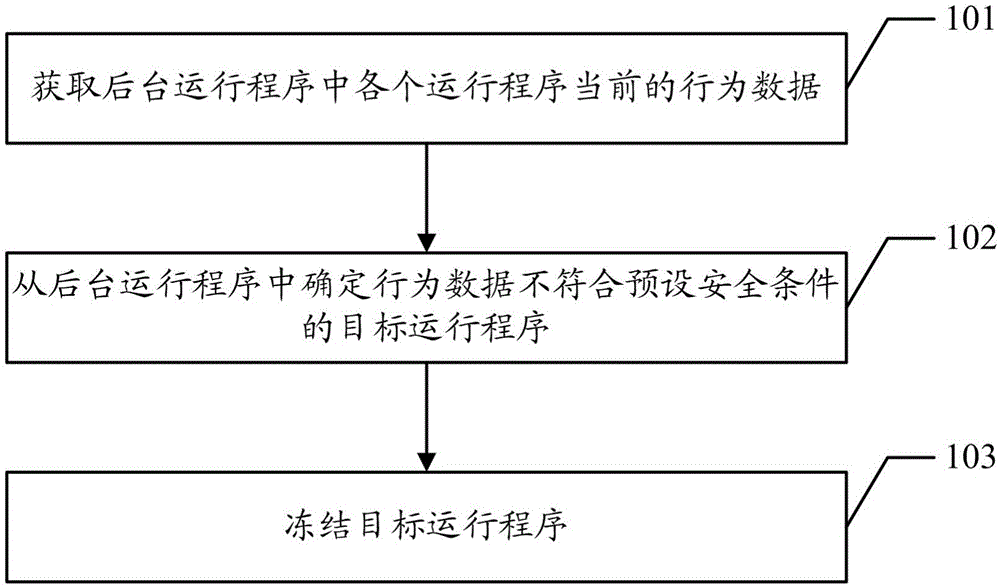
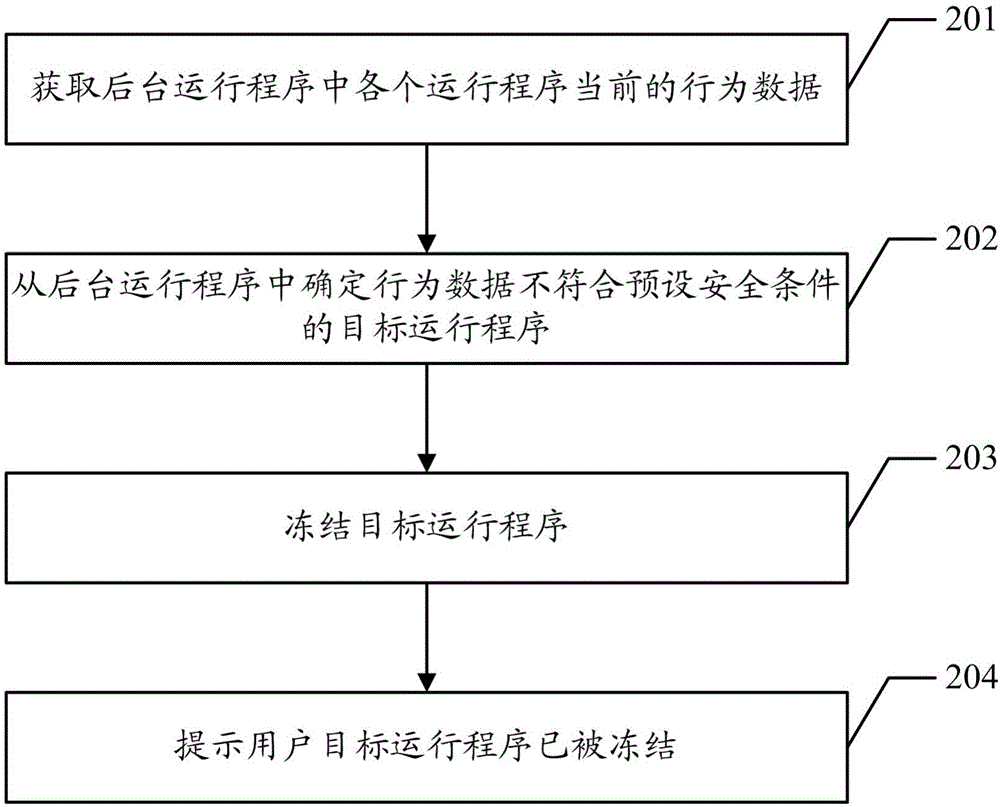
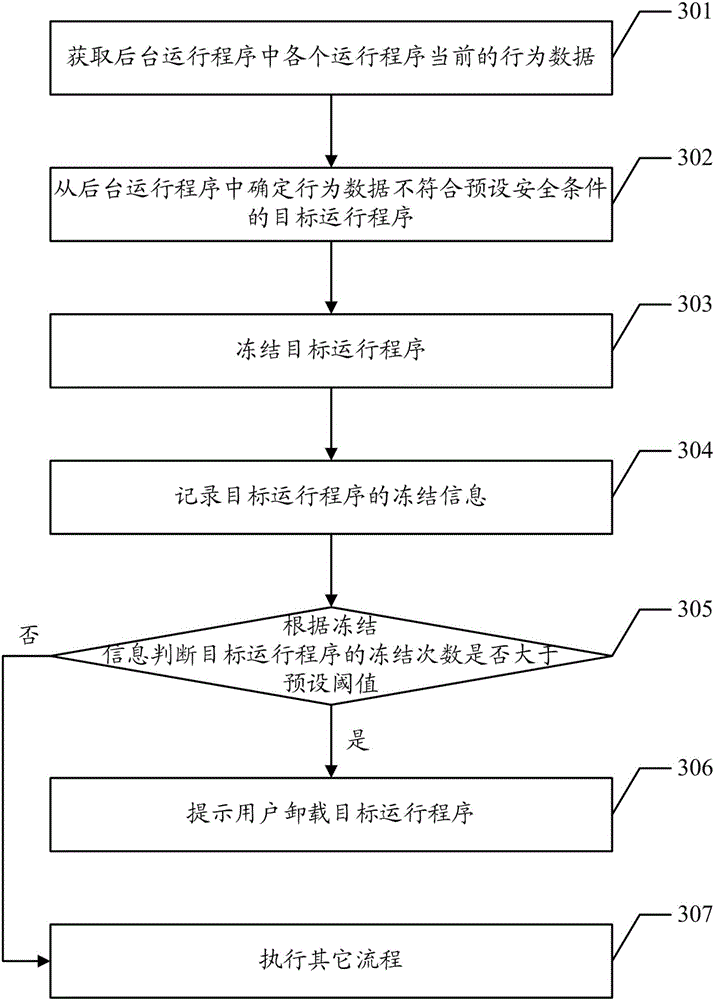
Freezing method of application program and terminal
InactiveCN106325993APrevent leakageImprove securityProgram initiation/switchingDigital data protectionSecurity specificationComputer terminal
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Identity identification method and identity identification system based on electrocardiosignals
InactiveCN105469037ASmall amount of calculationFast recognitionDigital data authenticationPhysiological signal biometric patternsEcg signalIdentity recognition
Owner:KUNSHAN BRANCH INST OF MICROELECTRONICS OF CHINESE ACADEMY OF SCI
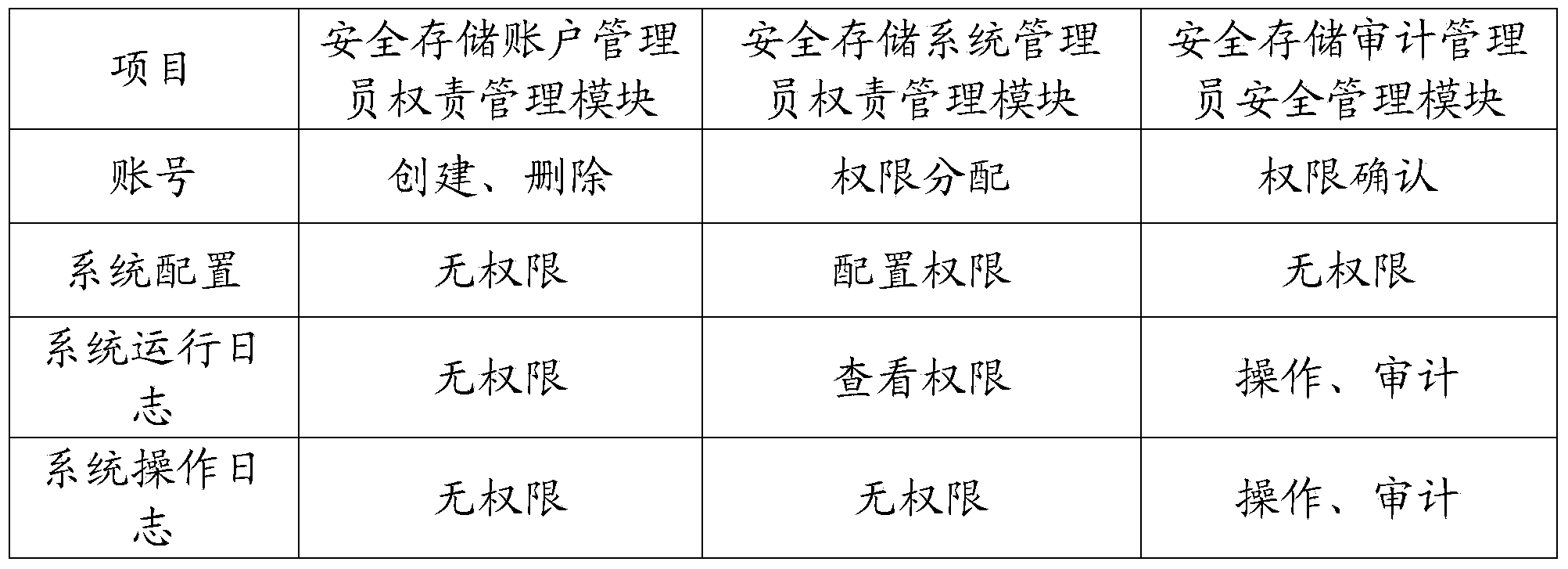
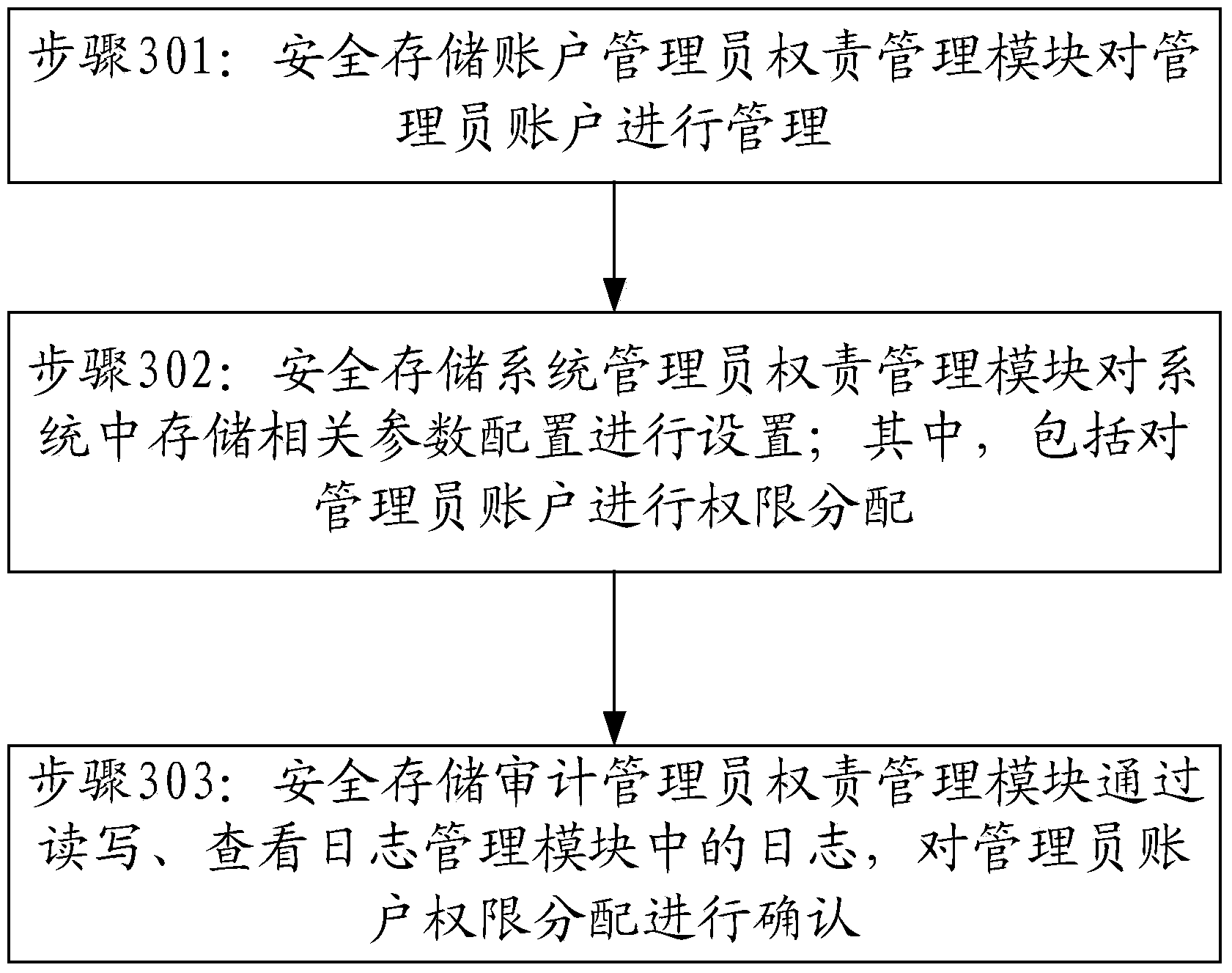
Safety storage management method and system based on checks and balances
ActiveCN103729582AImprove data securityIncreased level of protectionDigital data authenticationStorage managementComputer science
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
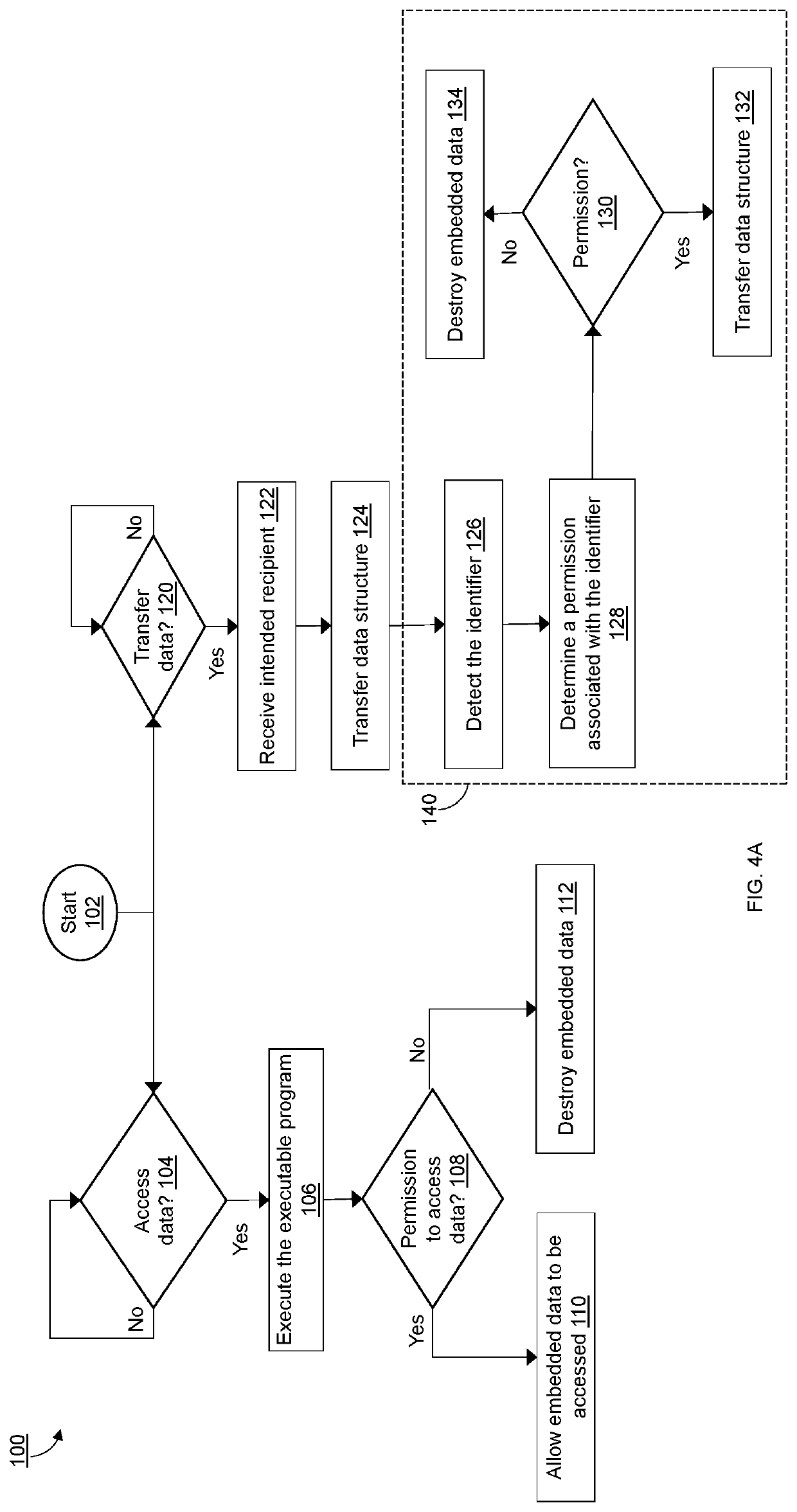
Securing Electronic Data by Automatically Destroying Misdirected Transmissions
PendingUS20200117800A1Digital data protectionDigital data authenticationData miningSoftware engineering
Owner:BOTTOMLINE TECH
Automated monitoring, detection, and reporting of unauthorized movement and/or theft of vehicles and cargo
A method and an enhanced electronic logging device (ELD) enable a load lock feature of a vehicle that assists with automated theft detection, reporting, and tracking of stolen vehicles / cargo. The processor of the ELD enables the ELD to register the operator MCD to receive notifications generated by a load lock module and present on a display of the ELD at least one selectable option for activating a load lock of the vehicle, the load lock identifying that the operator has parked the vehicle and has triggered the ELD to report any movement of the vehicle that occurs while the load lock is activated. The processor generates and transmits a notification of unauthorized movement or a potential theft of the vehicle in response to receiving an input from the movement detection device indicating that the vehicle is moving or being moved from a parked location while the load lock is activated.
Owner:OVERHAUL GRP INC
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap