Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30results about "Program/content distribution protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
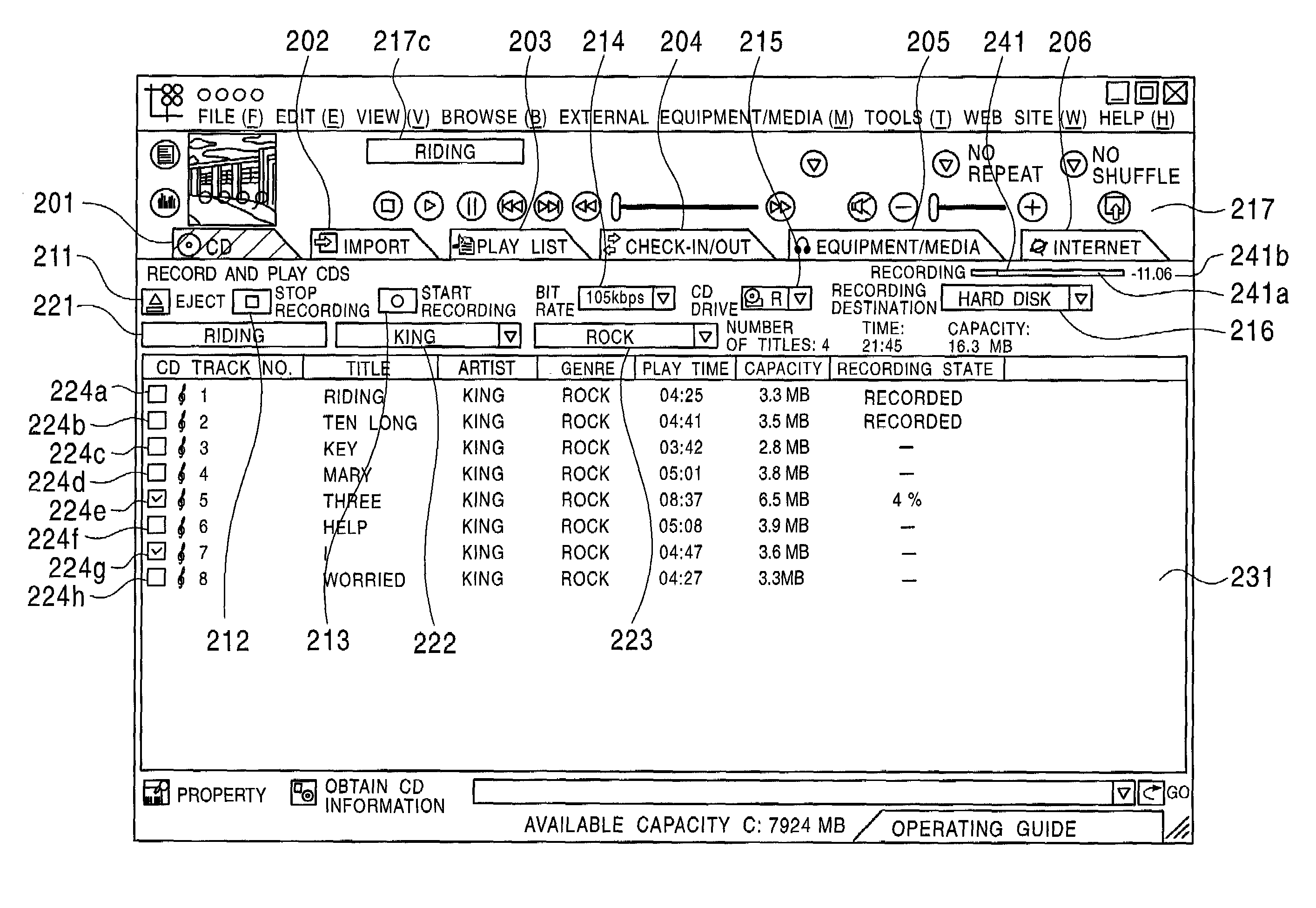
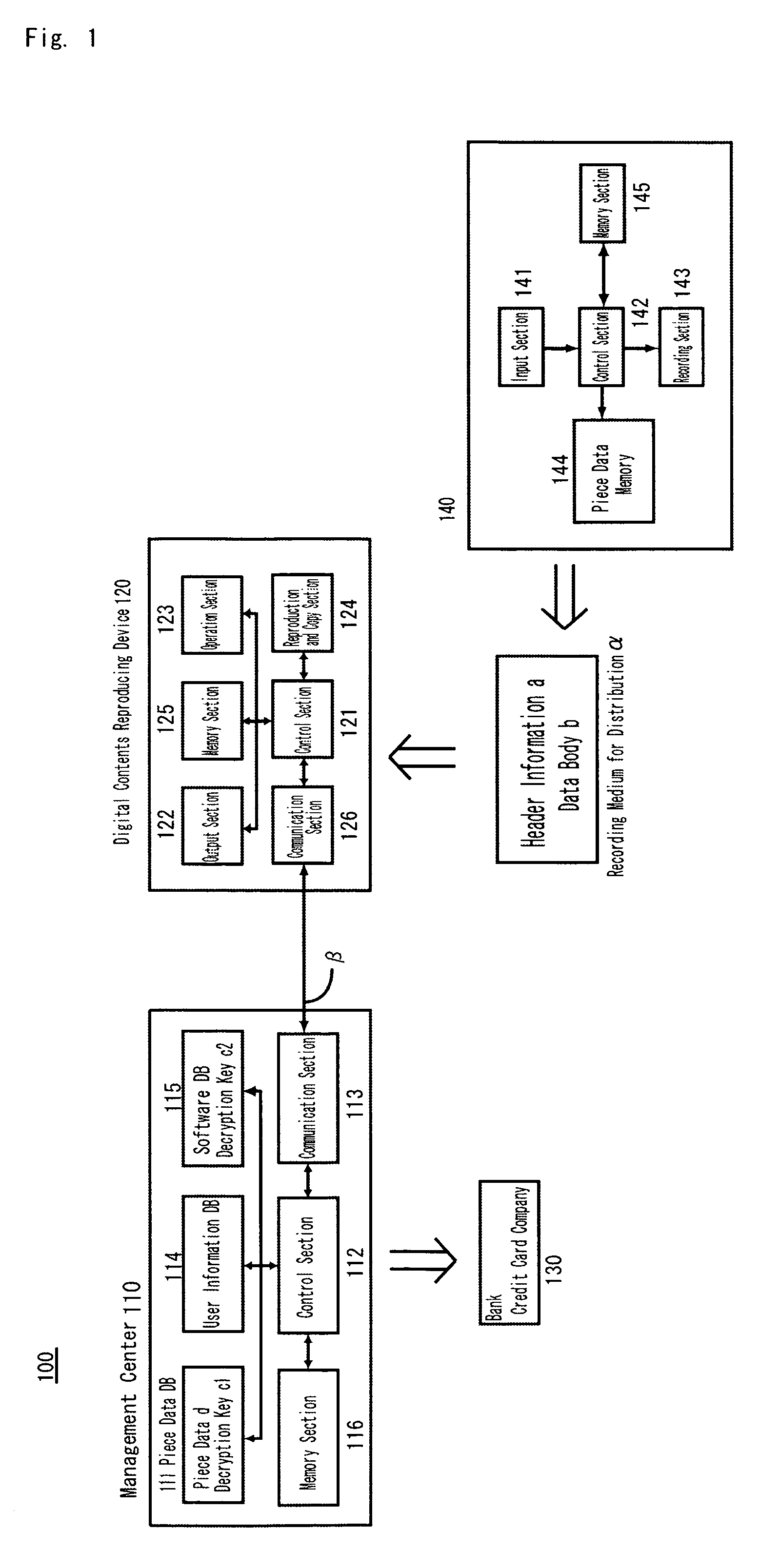
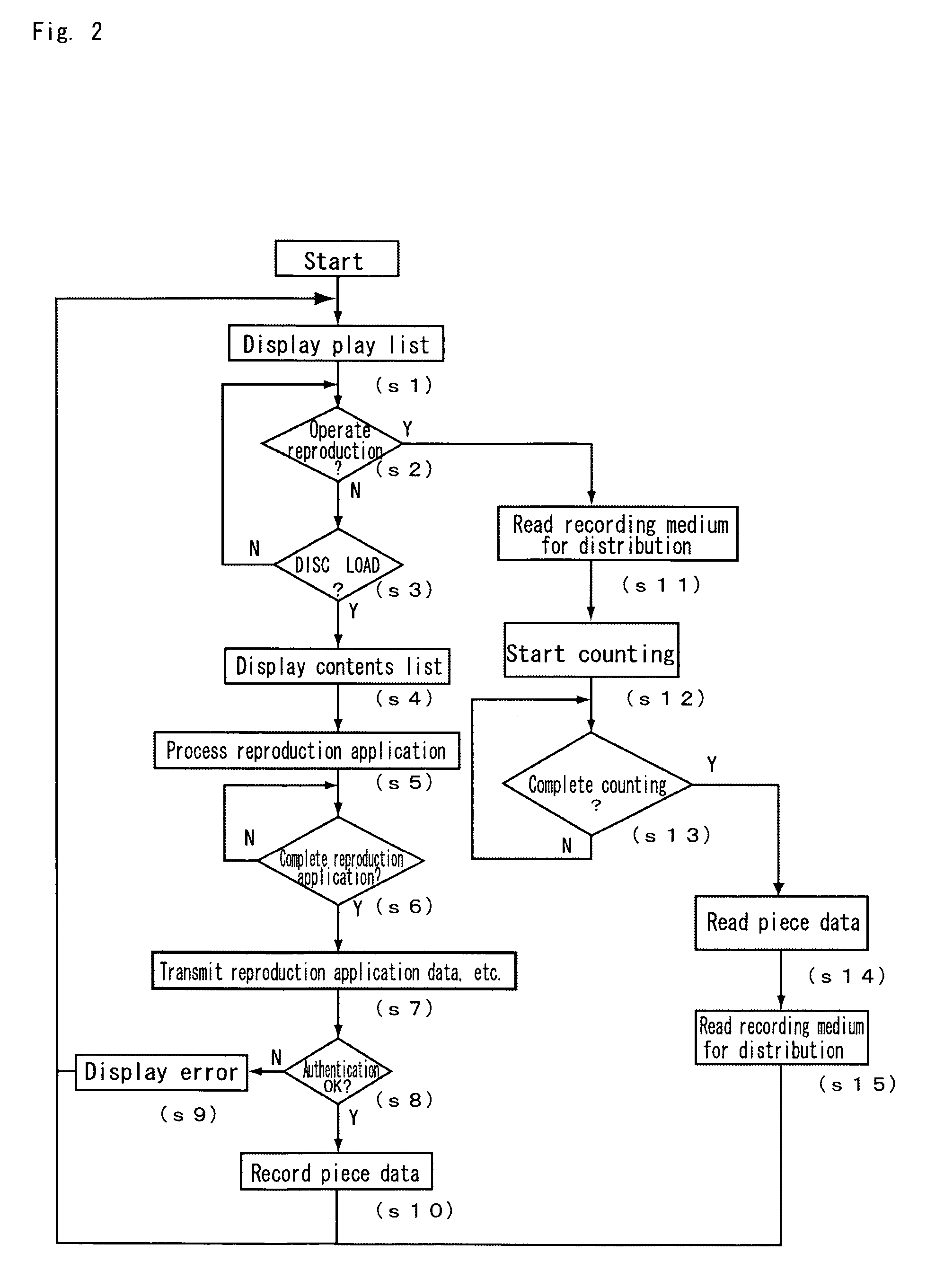
Information processing system, information processing method, computer program executed in information processing system
InactiveUS20070009232A1Television system detailsRecording carrier detailsInformation processingRelevant information
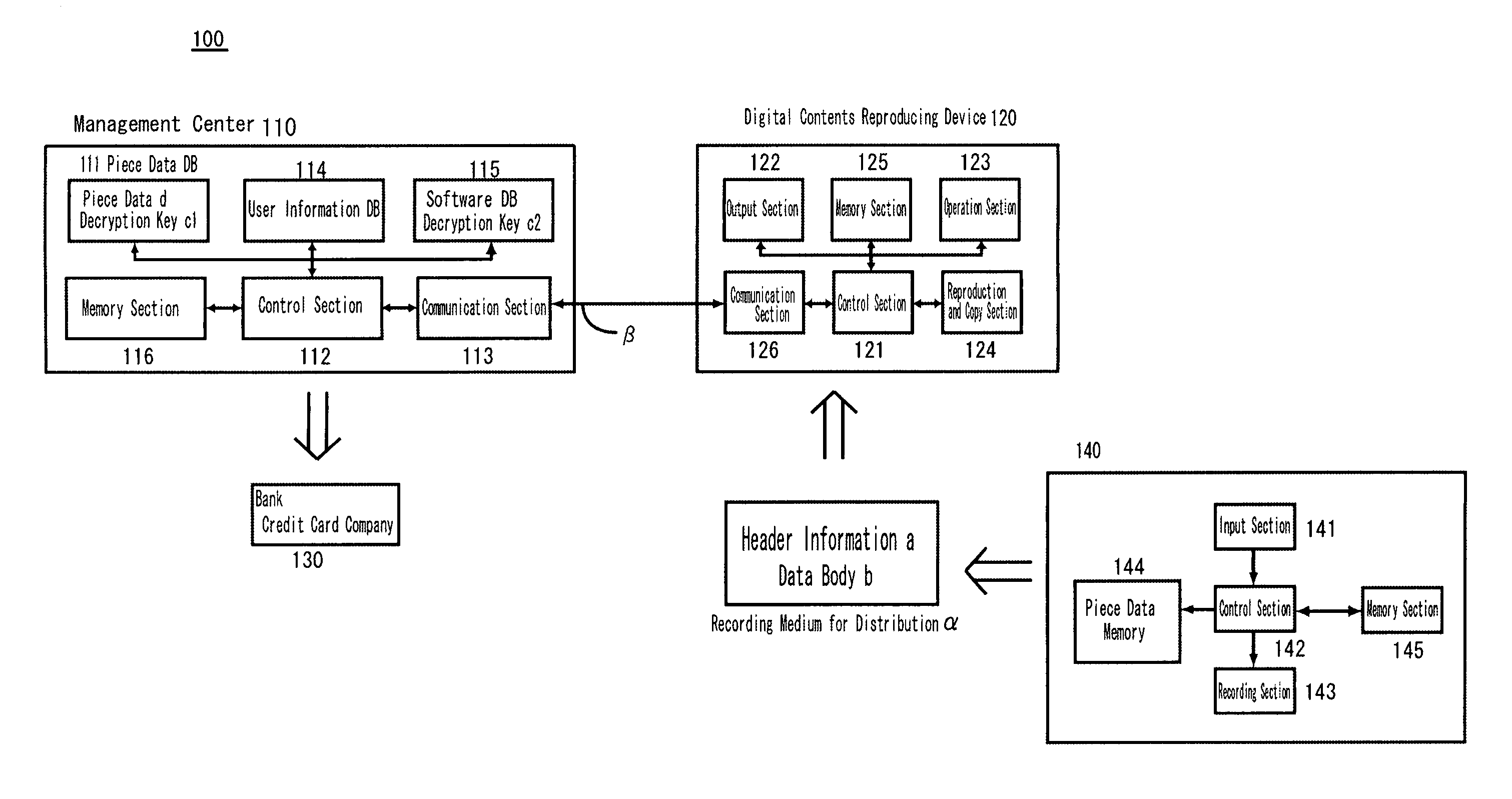
An information processing system includes a stream getting section for getting a data stream representing a content and a recording processing section for generating output control information and writing the data stream and the output control information on a medium. The output control information defines an appropriate output method, which is compatible with the output format of the content, following a rule that defines what type of processing should be done according to the type of input source of the content and the output format of the content and in accordance with source related information on the input source of the content. By reference to the output control information, a device that is going to play back the content from this medium can output the content without considering its input source.
Owner:PANASONIC CORP
Information processing apparatus and method, and program storing medium
InactiveUS7478437B2Disc-shaped record carriersDigital data processing detailsInformation processingComputer science
Owner:SONY CORP
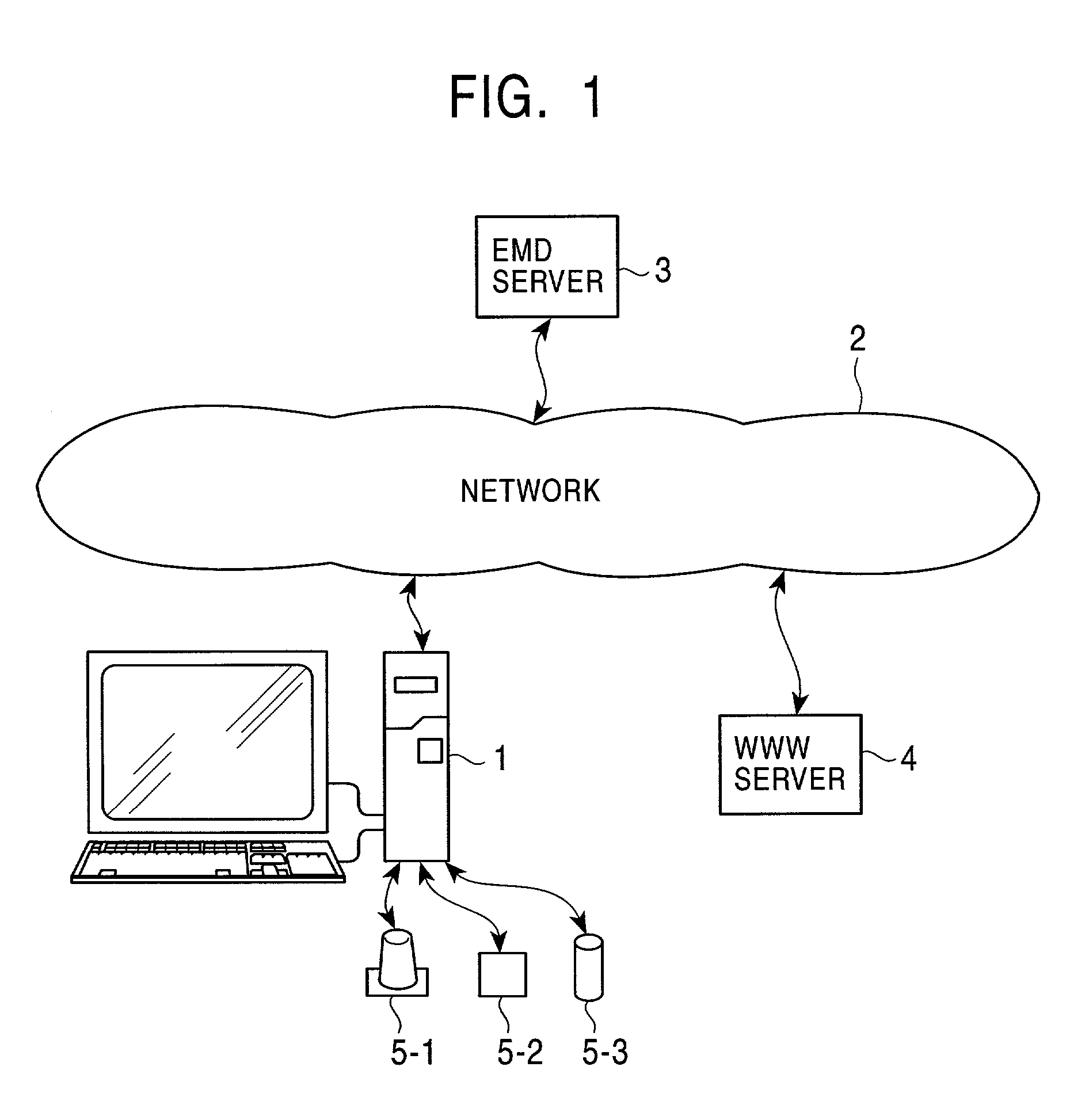
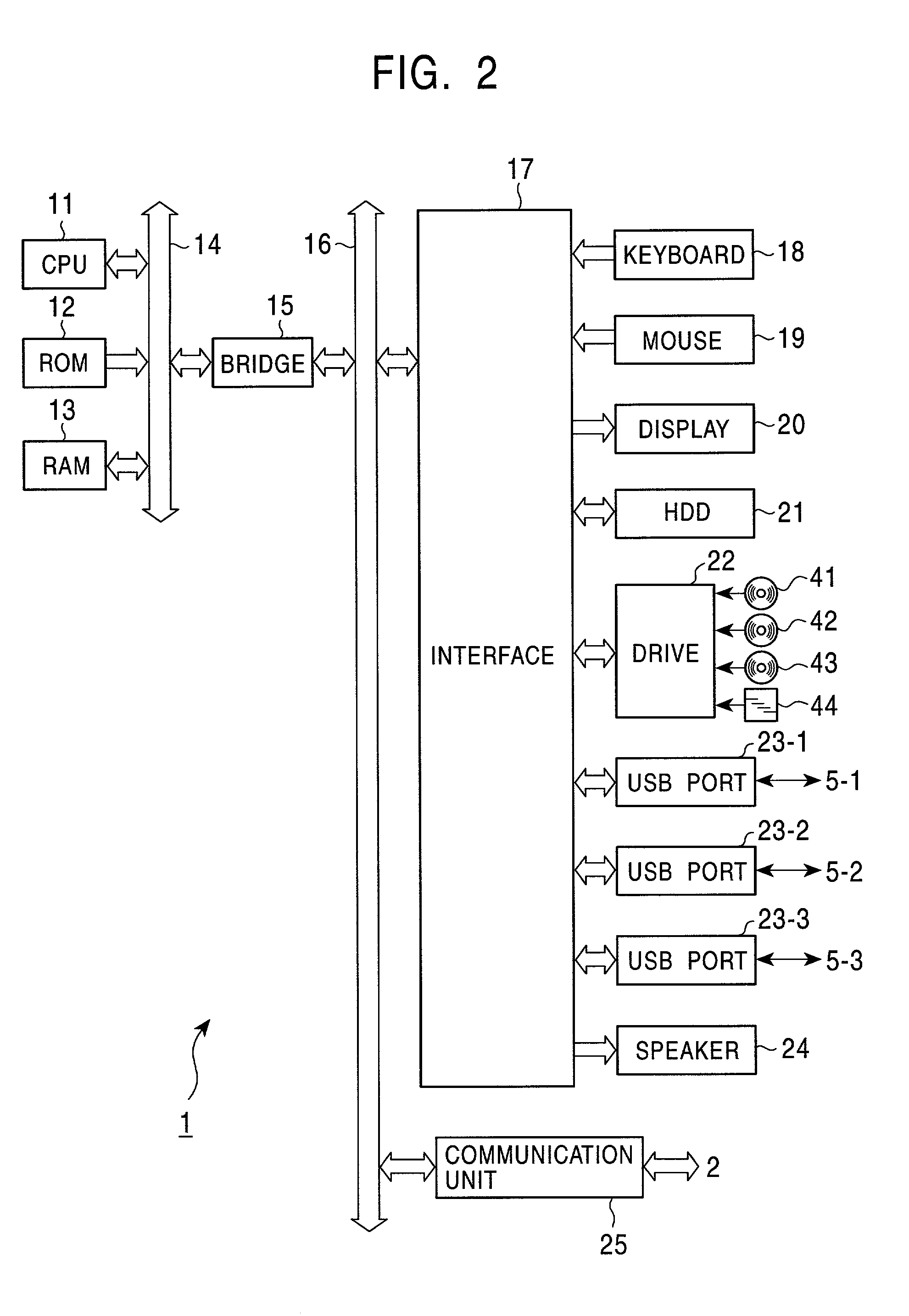
Method and system for transferring video and audio files to portable computing devices
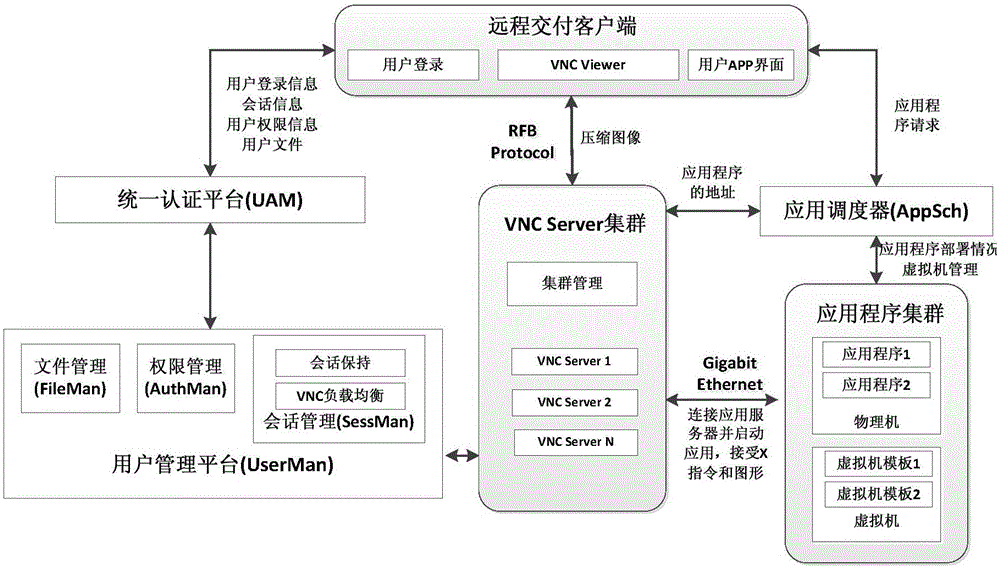
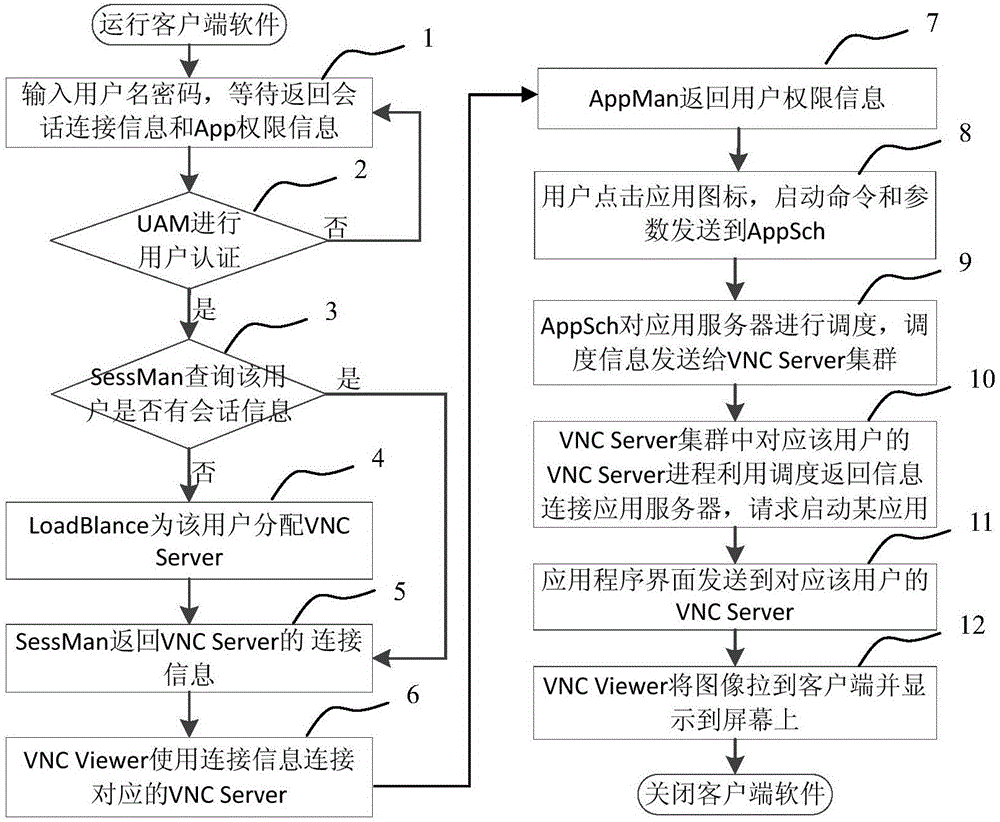
InactiveUS20050076057A1Short timeSmall componentProgram/content distribution protectionSpecial data processing applicationsComputer hardwarePayment
Owner:HEWLETT PACKARD DEV CO LP
System and Method for the Designation of Items in a Virtual Universe
InactiveUS20110055919A1Facilitates tracking and recoveryData processing applicationsDigital data processing detailsHuman–computer interactionVirtual universe
The present invention enables items in a Virtual Universe to be tagged as available for pickup by one or more designated users. The present invention permits a designated user to be alerted that there is an item designated for that user / avatar and available for pick-up at a location in the Virtual Universe. A user may designate another user (or user's avatar), for example, a minor for whom the designating user has responsibility, as an “item” to be tracked. For privacy and other reasons, this and other features may be implemented on an opt-in basis.
Owner:INT BUSINESS MASCH CORP
Information signal recording device having accounting function, and accounting terminal device
InactiveUS20050232595A1Television system detailsHybrid switching systemsComputer hardwareTerminal equipment
Owner:SONY CORP
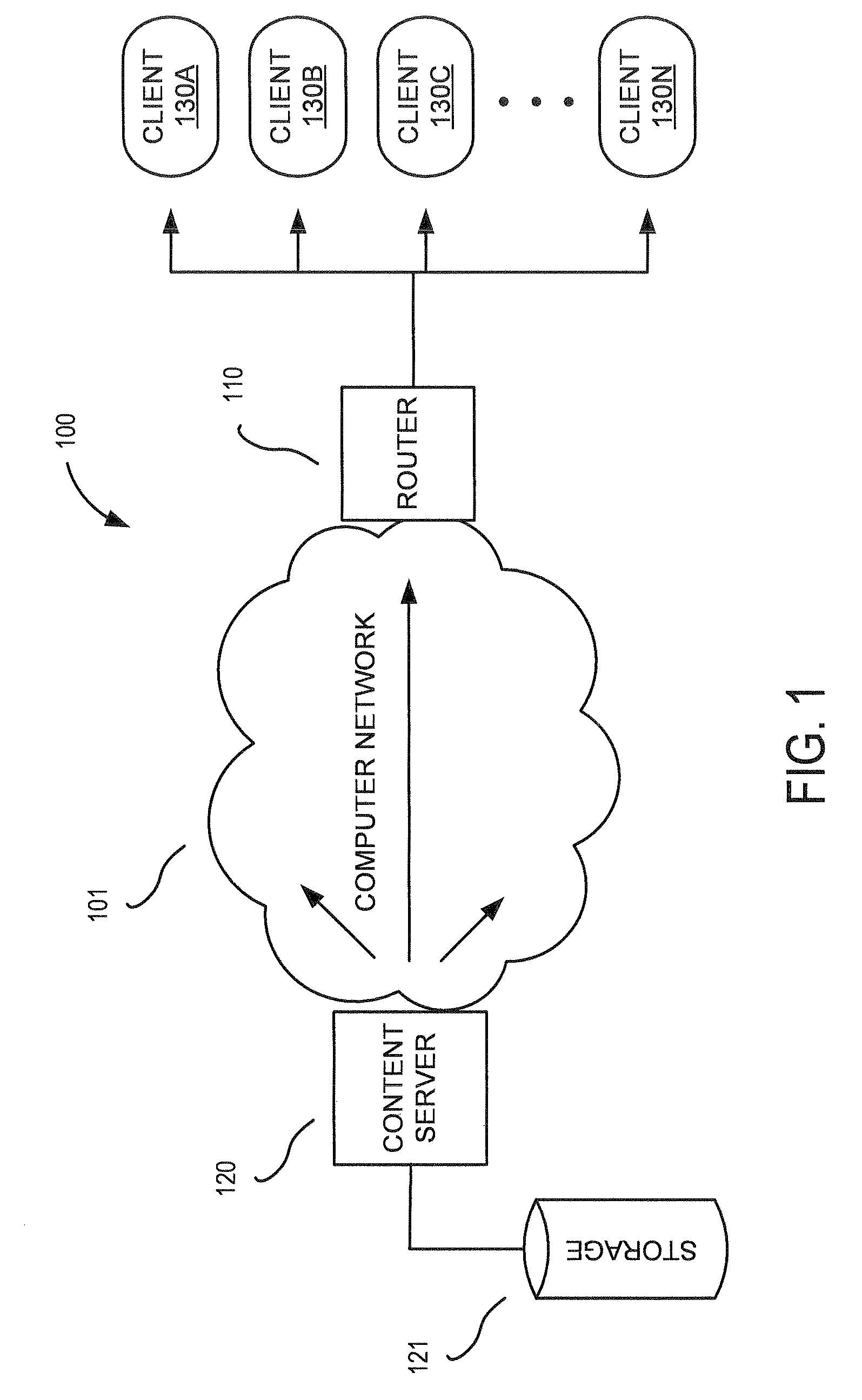
Distributed processing system, method of the same
InactiveUS7031944B2Increase valueResource allocationMultiple digital computer combinationsApplication serverComputer terminal
Owner:NEC CORP
File tamper detecting and repairing method and system
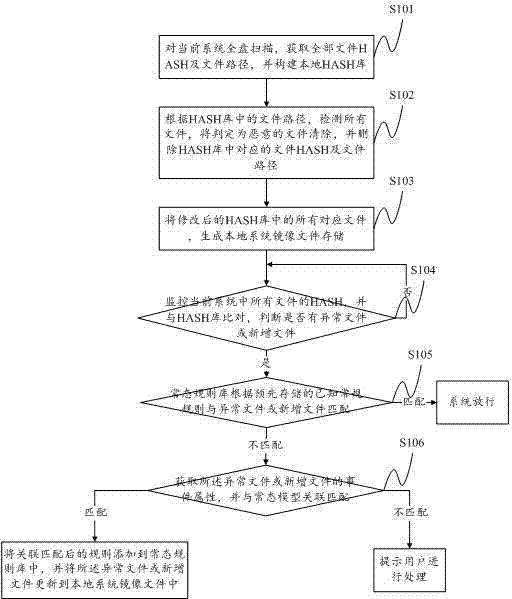
ActiveCN103902855APlatform integrity maintainanceProgram/content distribution protectionOperating systemNormal state
Owner:HARBIN ANTIY TECH
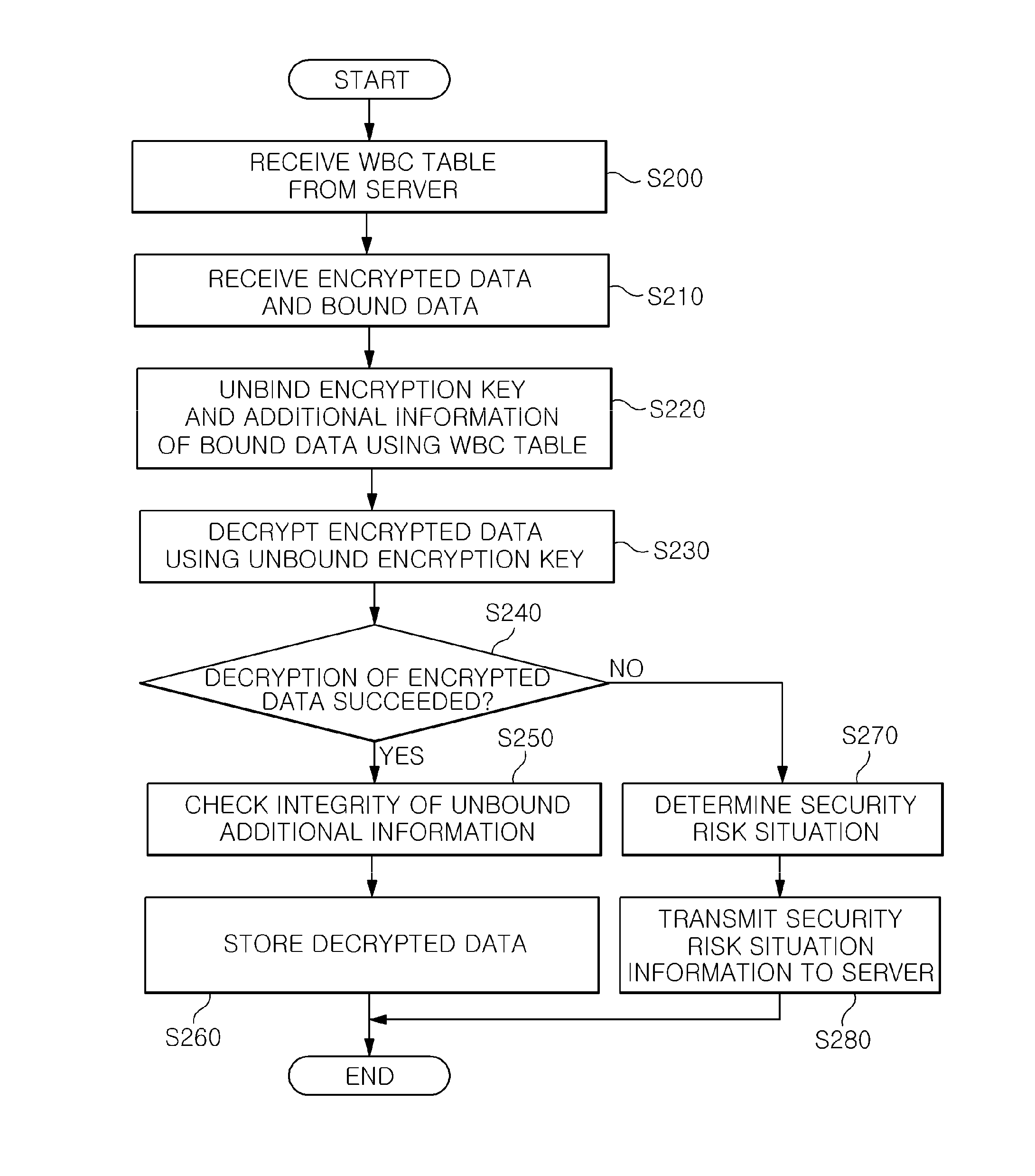
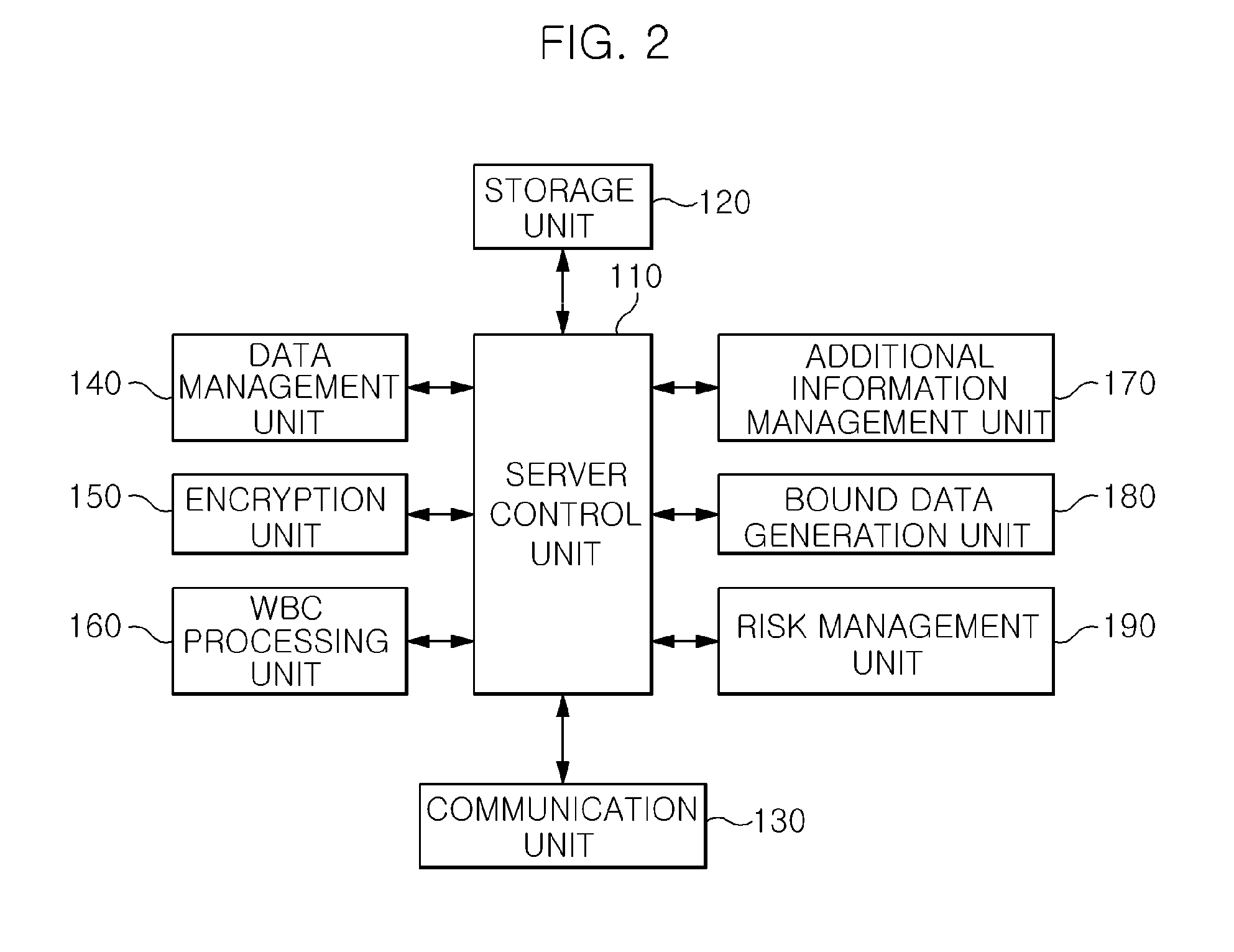
Content protection apparatus and method using binding of additional information to encryption key
InactiveUS20120099726A1Deciphering becomes impossibleKey distribution for secure communicationRandom number generatorsManagement unitProcessing element
Owner:ELECTRONICS & TELECOMM RES INST
Program protection method and device
ActiveCN103853943ADigital data authenticationProgram/content distribution protectionCiphertextSource code
Owner:BEIJING AUTONAVI YUNMAP TECH CO LTD
Application program copyright protection method and digital copyright protection system
ActiveCN102194077ASelf-protectiveImprove your own securityUser identity/authority verificationProgram/content distribution protectionDependabilityProtection system
Owner:ZTE CORP
Method and device for protecting derived symbol in so file
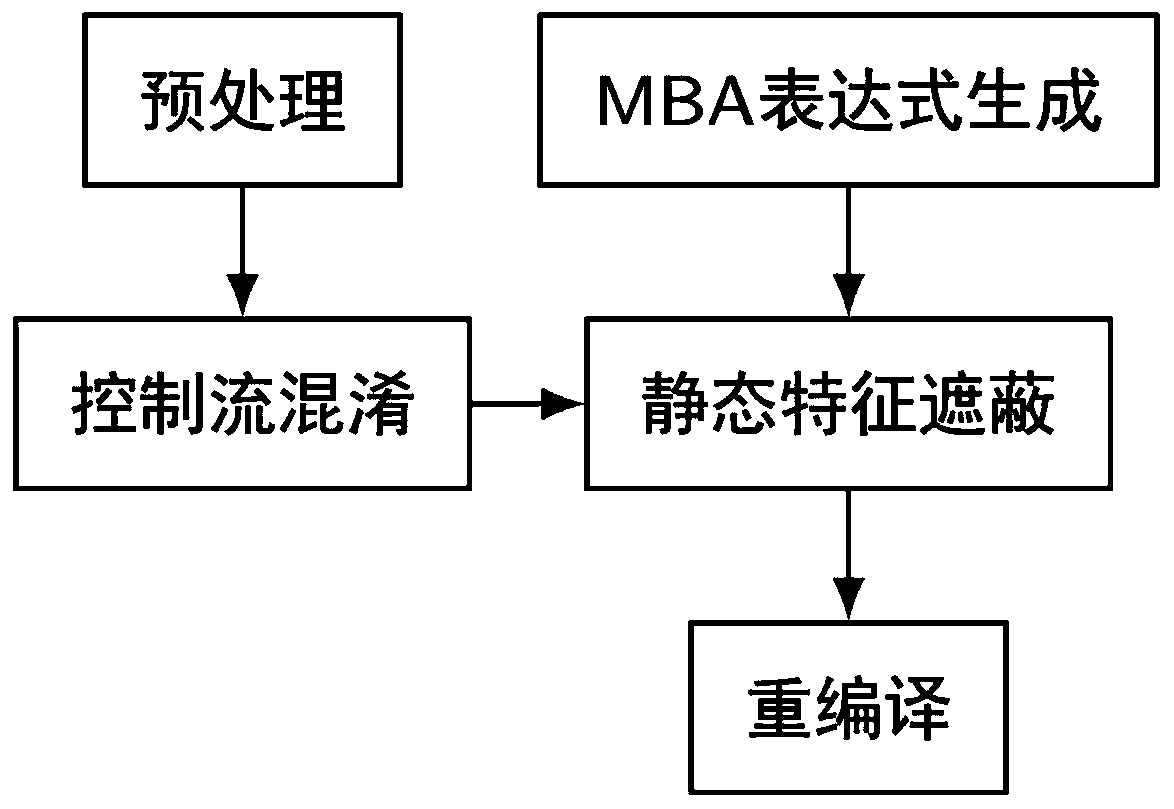
InactiveCN105447349AAchieve protectionImprove securityProgram/content distribution protectionAlgorithmTheoretical computer science
Owner:ZHUHAI DUOWAN INFORMATION TECH CO LTD
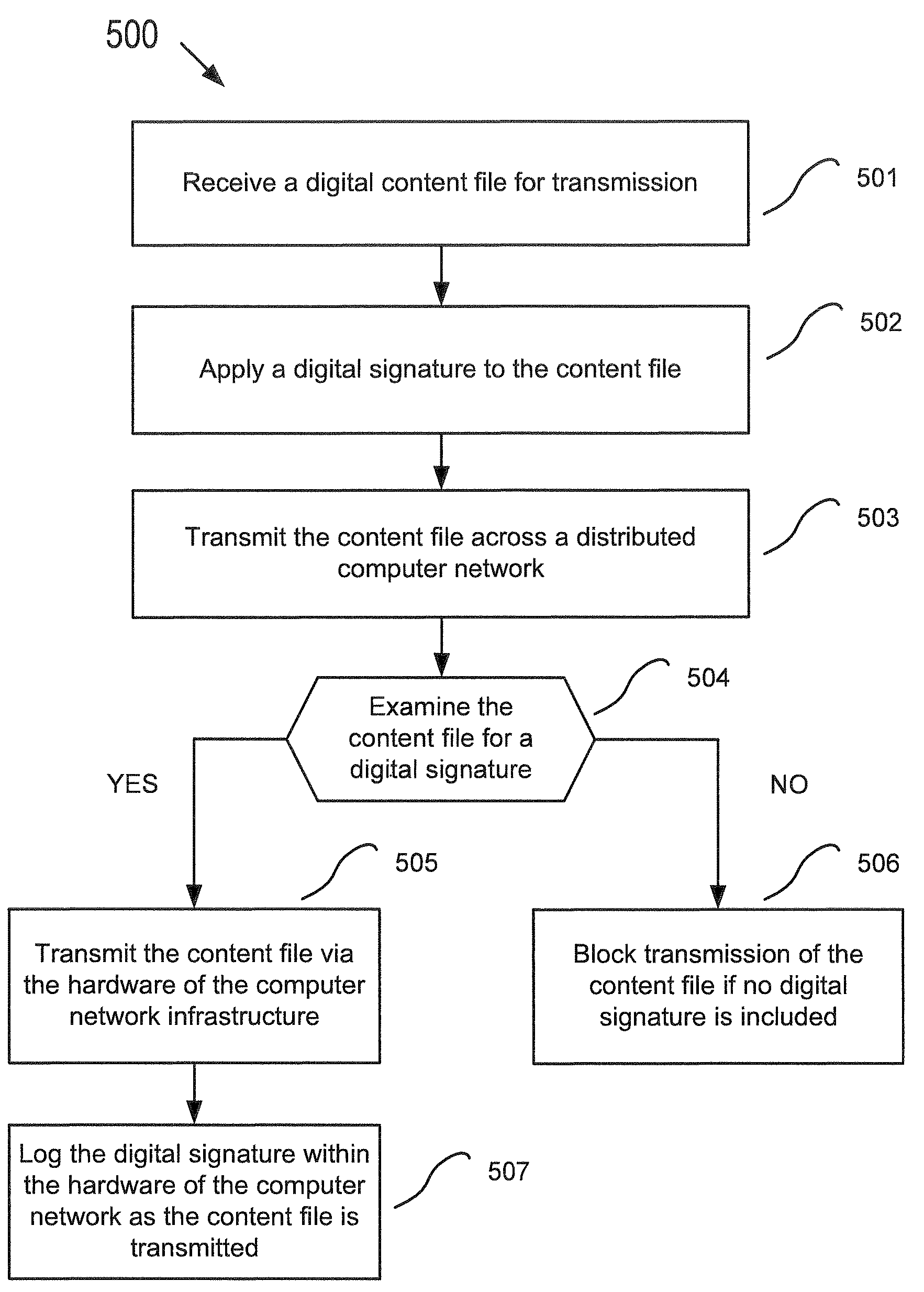
Copy protection built into a network infrastructure
InactiveUS7516322B1Copy protection is reinforcedPrevent easy circumventionMultiple digital computer combinationsProgram controlDigital contentDigital signature
Owner:CISCO TECH INC
Apparatus and method for blocking ransome ware using access control to the contents file
The present application relates to the apparatus for blocking Ransome ware using access control to the contents file, it includes an access permission program checking unit for checking whether a program of a process detected as being started in an user's computer is a reliable program, checking whether a parent process of the program is a reliable program, and determining whether the program is the program that is allowed to access the contents file; a whitelist registration unit for registering information of the contents file to be protected; and a contents file access control unit for allowing the process to access the contents file registered in the whitelist registration unit when the program of the process is the program that is allowed to access the contents file determined by the access permission program checking unit, and blocking the process from accessing the contents file registered in the whitelist registration unit when the program of the process is not the program that is allowed to access the contents file determined by the access permission program checking unit.
Owner:WITHNETWORKS CO LTD
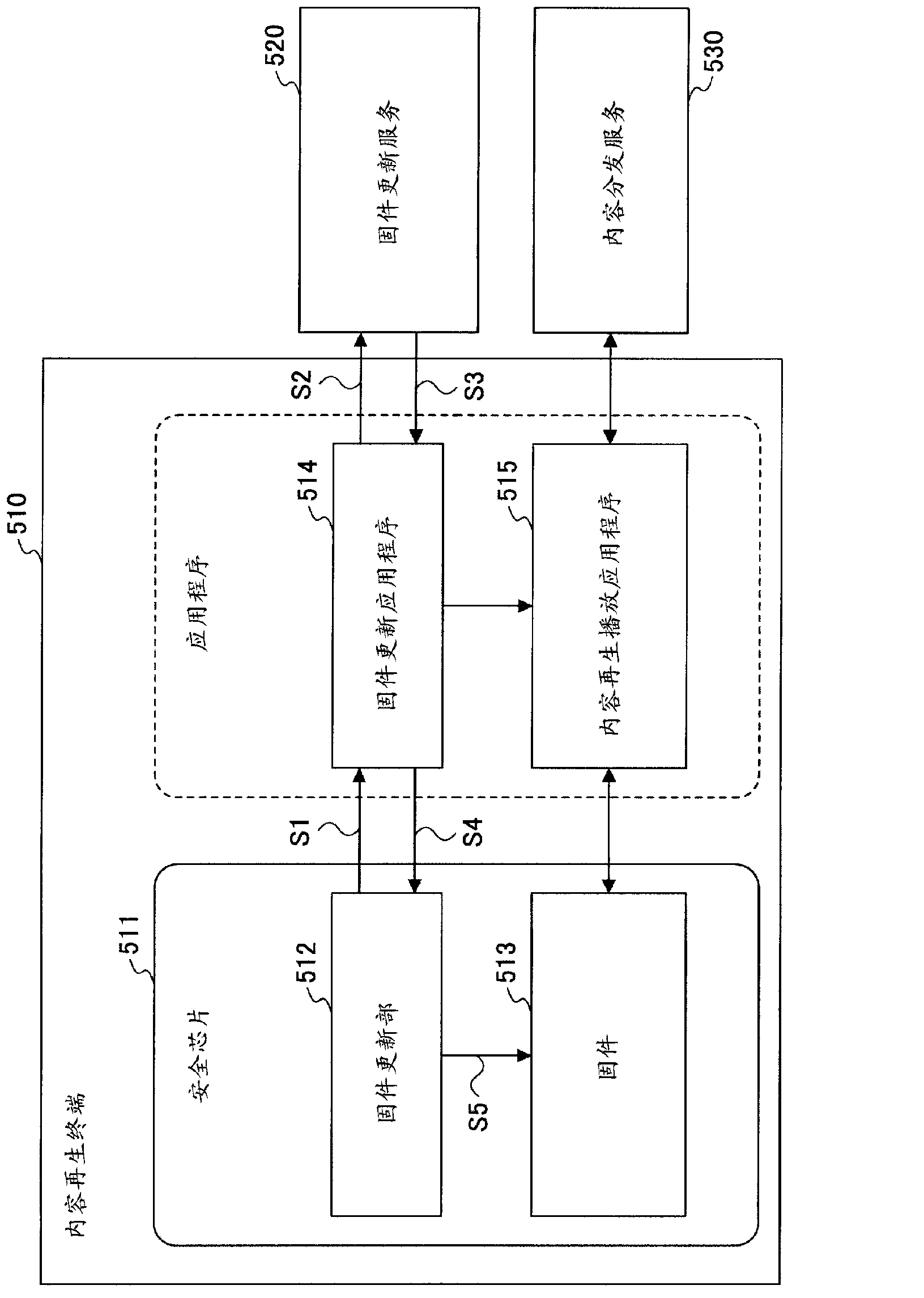
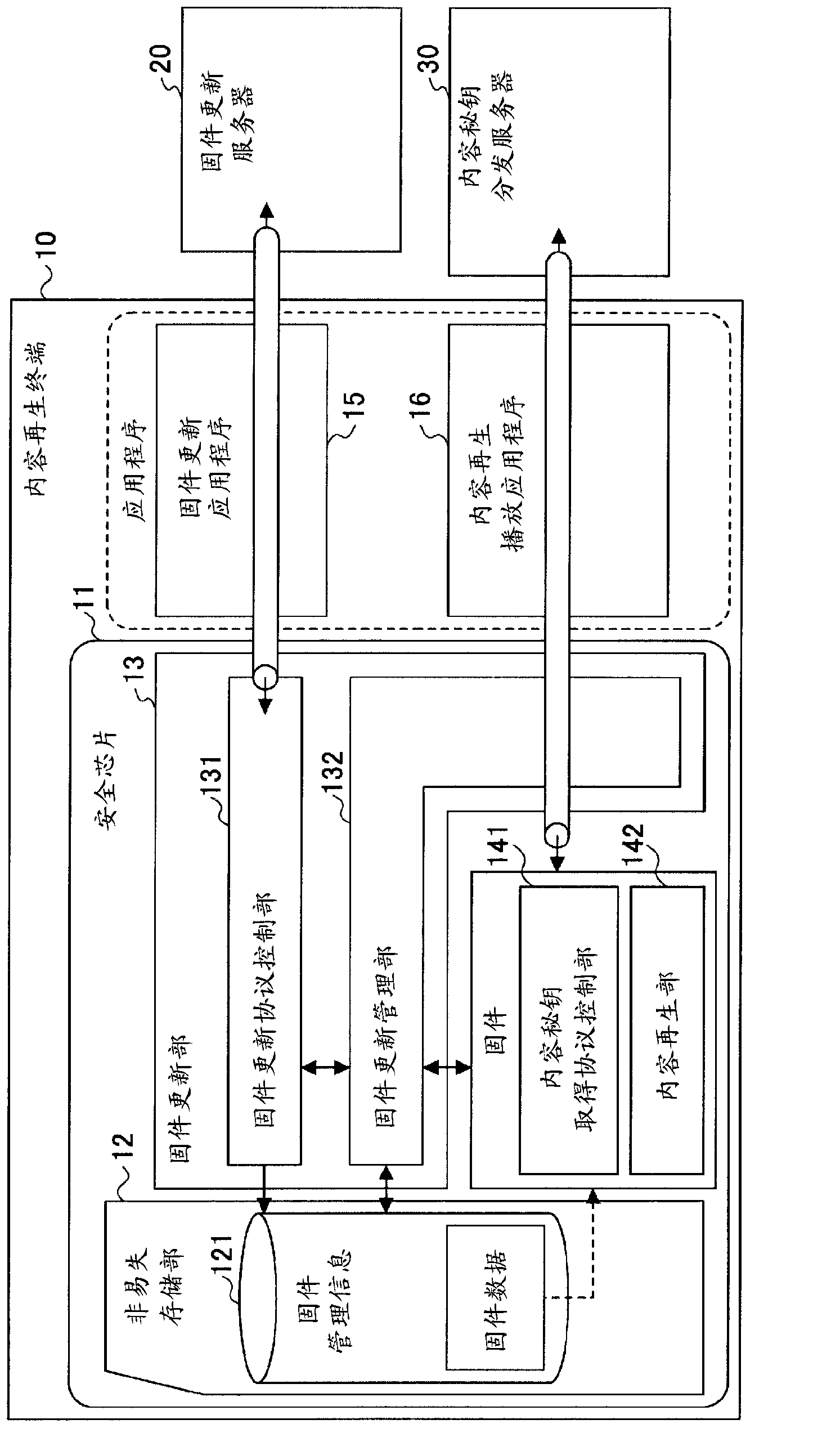
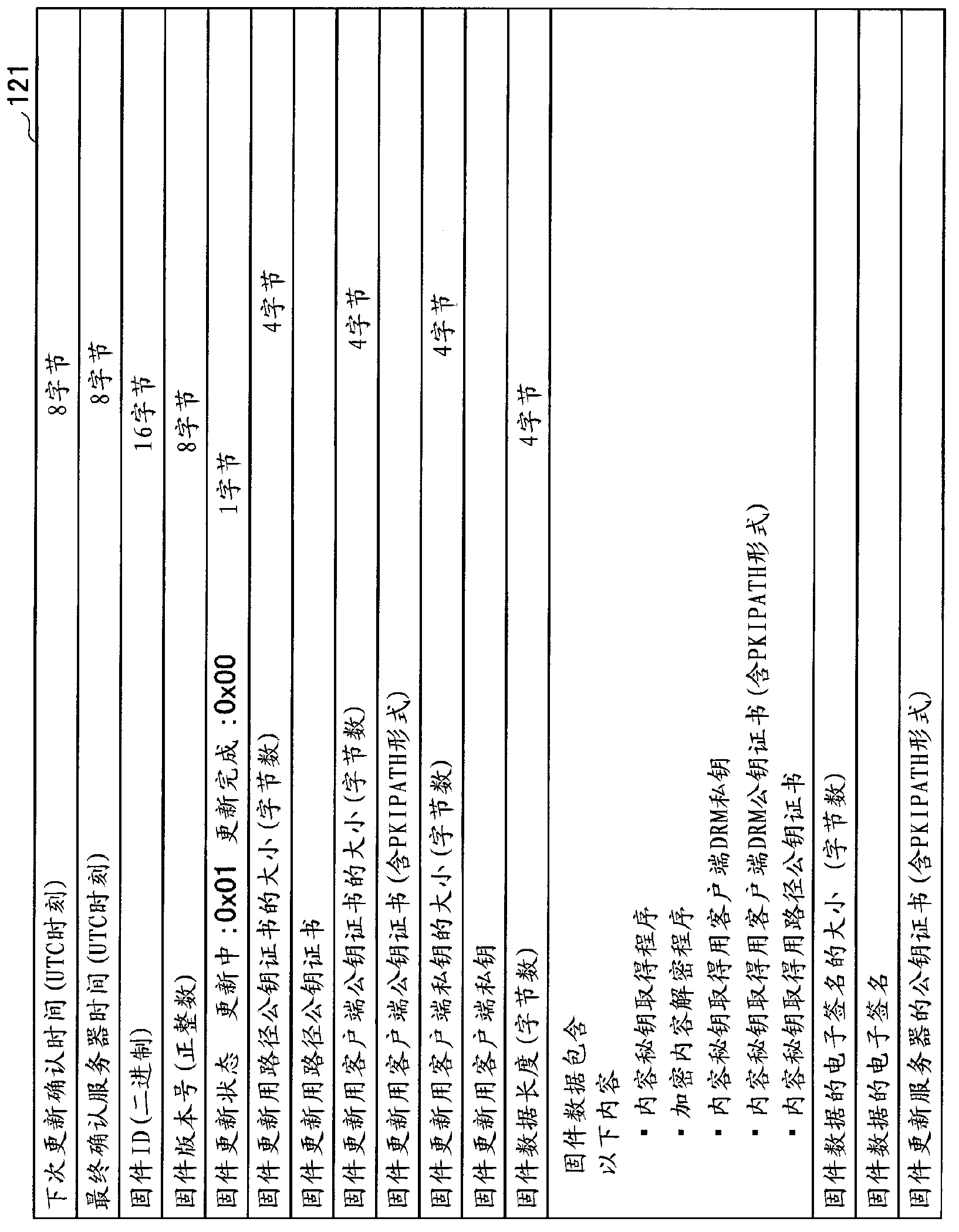
Content data playback device, update management method, and update management program
ActiveCN103154964ADigital data protectionProgram/content distribution protectionTime informationManagement unit
Owner:FUJITSU LTD
System and method for device authorization and remediation
ActiveUS20150281190A1Digital data processing detailsUser identity/authority verificationDiagnostic dataRestoration device
A method is provided for authorizing a device for consuming content. In method includes the steps of generating an authorization request, the authorization request for authorization data including device diagnostic data (instructions) an device remedial data (instructions), transmitting the authorization request from the device to an authorizing service, and authorizing or remediating the device according to an authorization response to the authorization request received from an authorization server.
Owner:ARRIS ENTERPRISES LLC
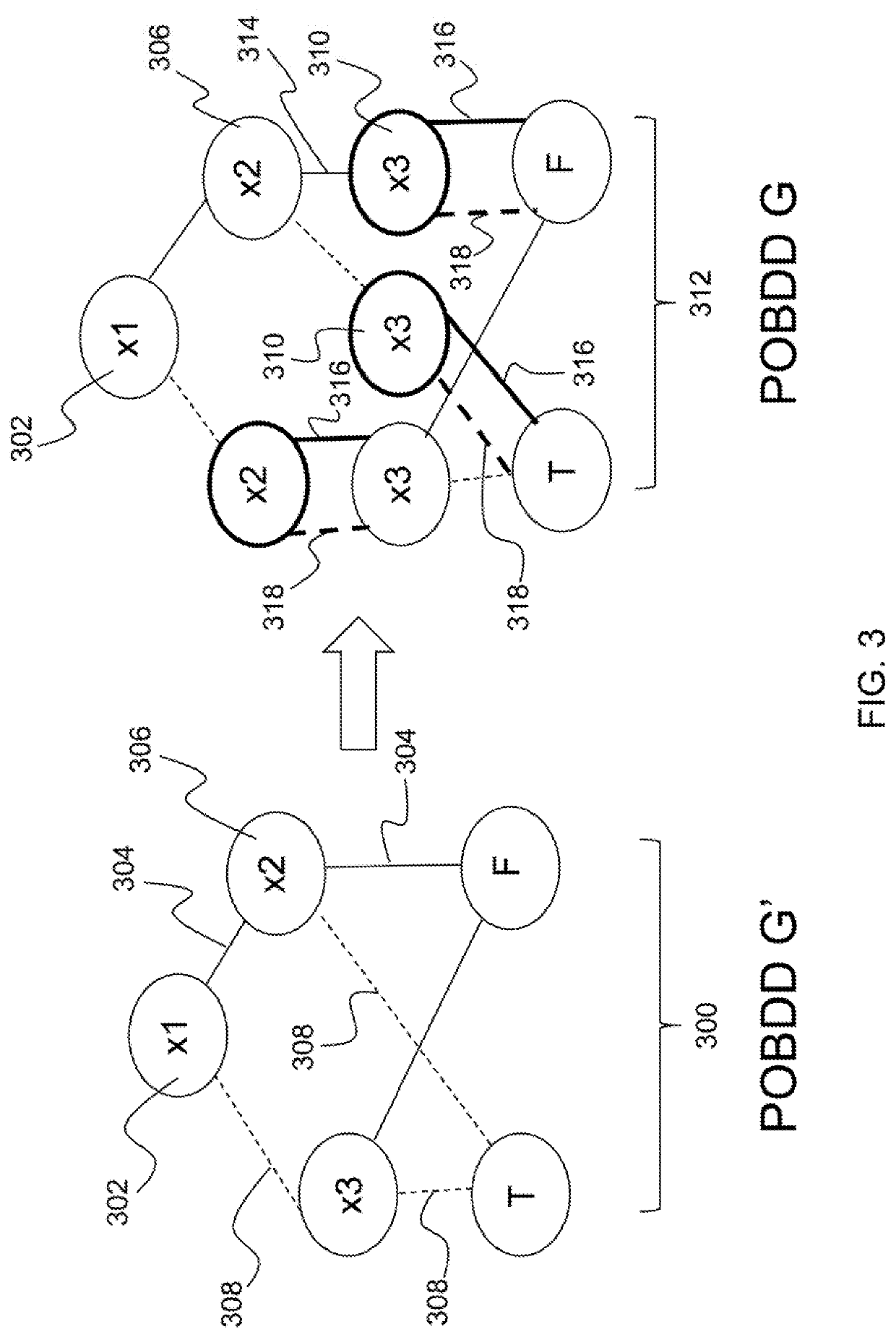
One-time obfuscation for polynomial-size ordered binary decision diagrams (POBDDs)
ActiveUS10509918B1User identity/authority verificationDigital data protectionObfuscationBinary decision diagram
Owner:HRL LAB
Software watermarking method based on collatz conjecture
Owner:XIDIAN UNIV +1
Remote payment system and remote payment method of application program
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Web page processing method and apparatus, and storage medium
The present disclosure provides a web page processing method. The method includes obtaining web page elements after web page rendering is performed on a to-be-accessed web page; detecting whether an abnormal element exists in the web page elements; generating and displaying an interaction entrance on the to-be-accessed web page if an abnormal element exists in the web page elements; and obtaining a trigger operation on the interaction entrance and filtering out the abnormal element in response to the trigger operation.
Owner:TENCENT TECH (SHENZHEN) CO LTD
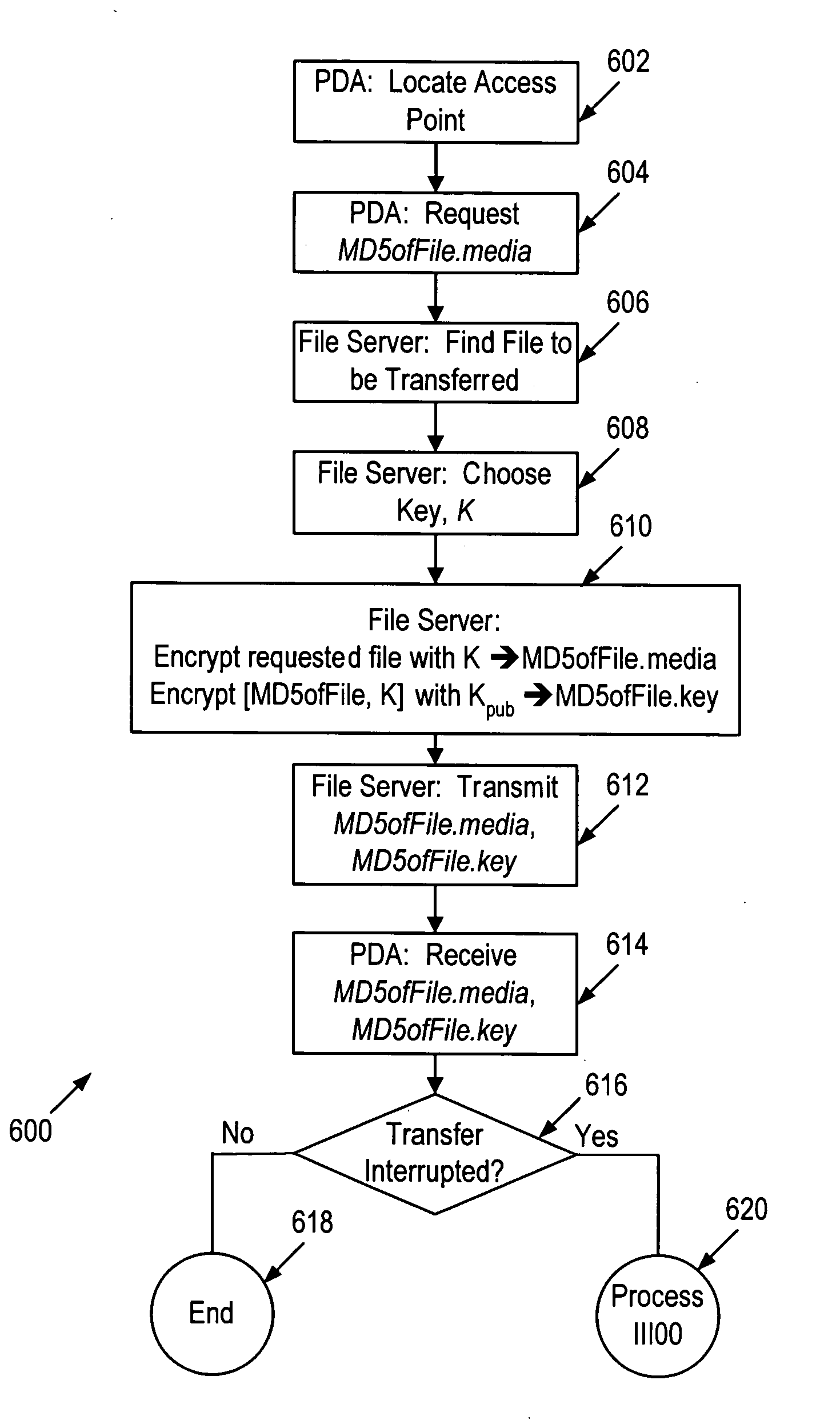
Data processing method and data reading method
InactiveUS20070136605A1Prevent illegal useMethod is hinderedKey distribution for secure communicationData taking preventionDigital contentUsage data
Owner:PHU SANG LTD
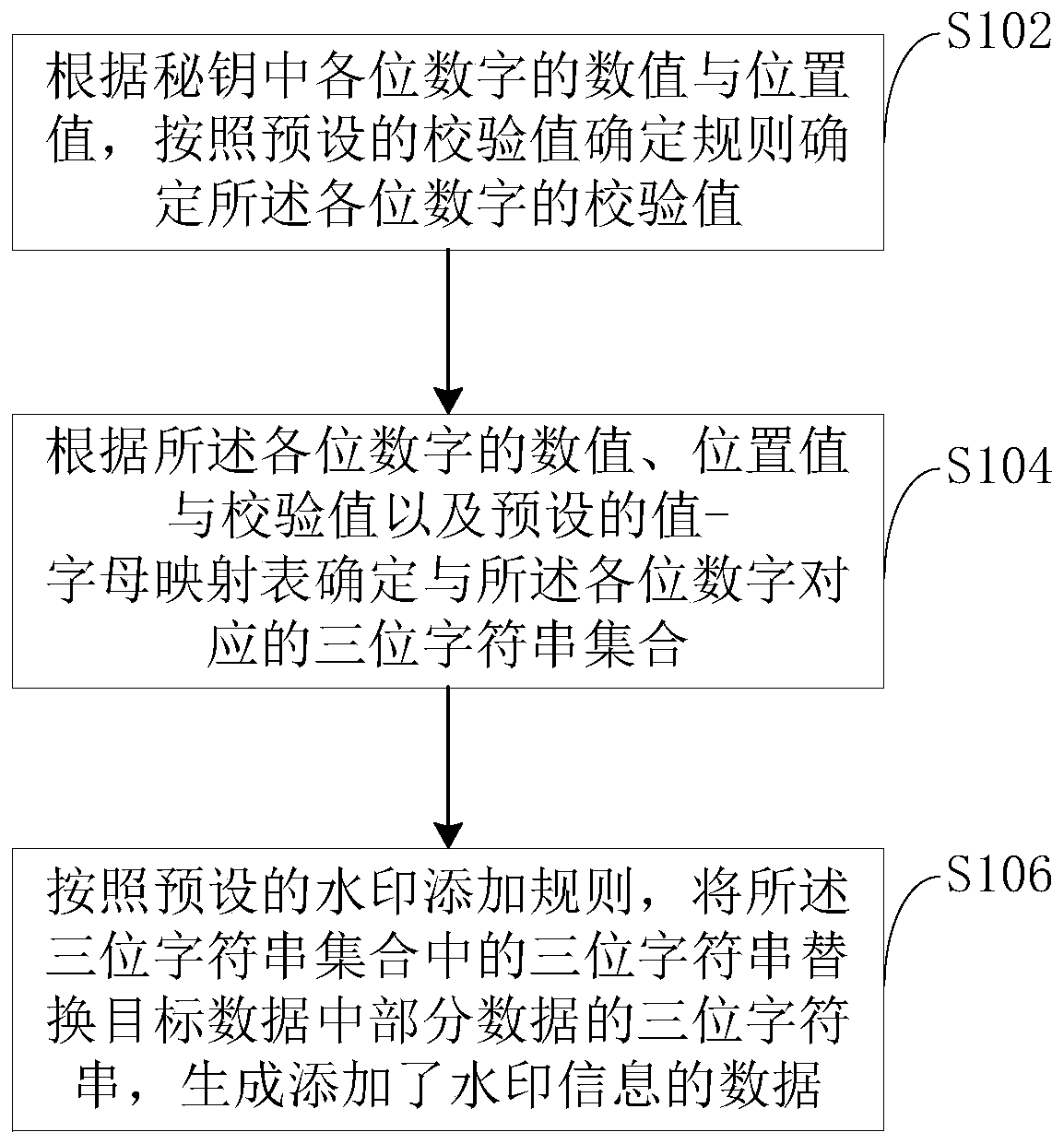
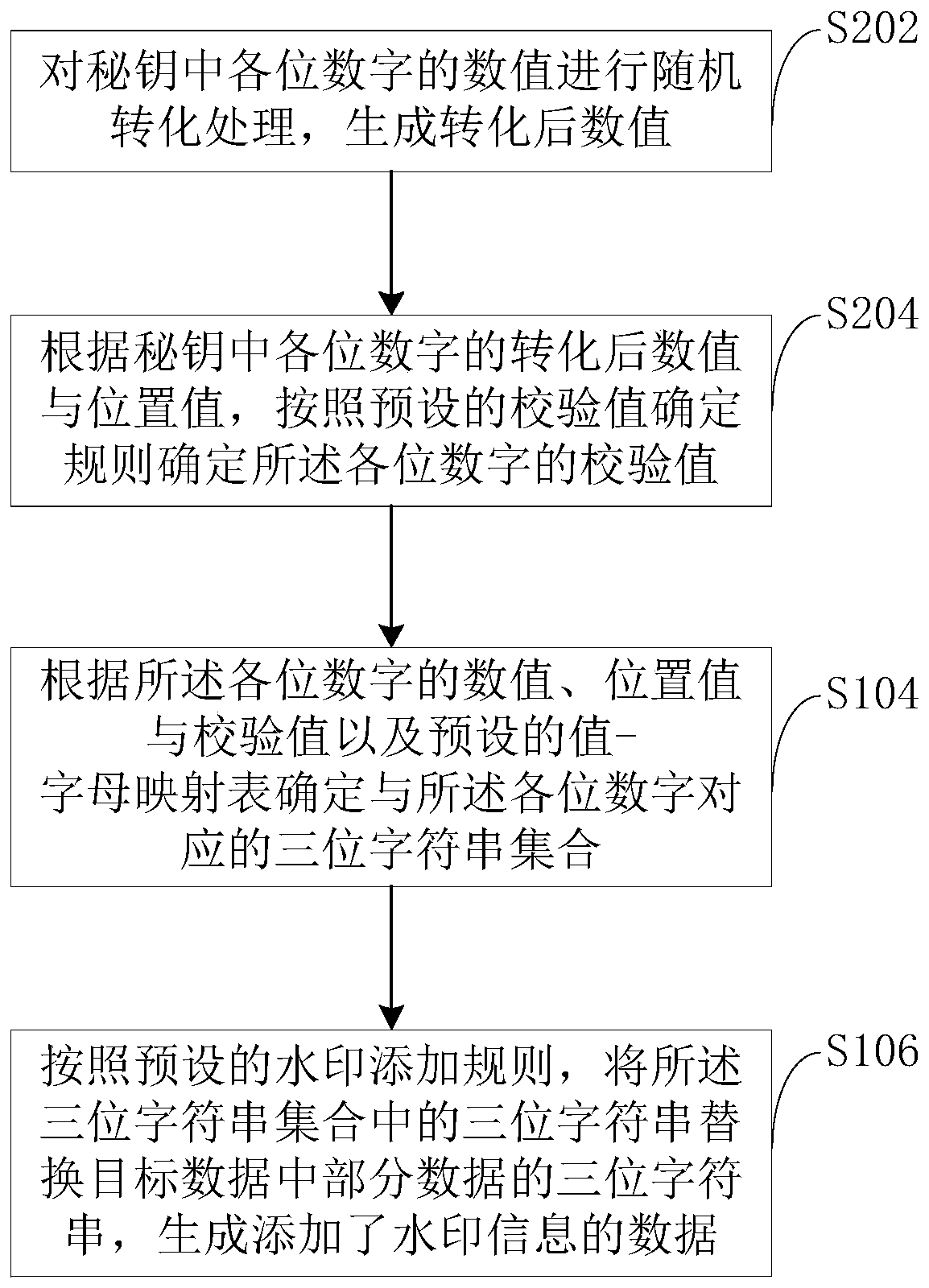
Watermark adding method, device and equipment and storage medium
PendingCN111400670ASecretiveImprove anti-interference abilityKey distribution for secure communicationDigital data protectionAlgorithmConfidentiality
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +1
Media file copyright protection method and system
ActiveCN110348177AEnsure the spreadImprove protectionDigital data protectionProgram/content distribution protectionPersonal accountProtection system
Owner:福建省天奕网络科技有限公司
Man-machine interaction multistage password setting method
ActiveCN111159655ARealization of interactive protectionRealization of delayed interactive protectionDigital data authenticationProgram/content distribution protectionPasswordTouchscreen
The invention discloses a man-machine interaction multi-level password setting method. The method comprises the steps that man-machine interaction protection is preset into a plurality of levels, level parameters and interface parameters through man-machine interaction upper configuration; an interactive touch screen acquires the interface parameters and displays an equipment interface according to the interface parameters; wherein the man-machine interaction upper configuration is in communication connection with a plurality of pieces of sub-equipment and acquires interaction time informationand state information of the plurality of pieces of sub-equipment in real time; if the interaction time is greater than the current level protection time, the man-machine interaction upper configuration sends a locking instruction to control the interaction touch screen to execute a locking operation so as to lock the interaction touch screen; through inputting an unlocking instruction or a time-delay instruction, unlocking or time-delay interaction locking protection is realized. According to the man-machine interaction multistage password setting method provided by the invention, multiple stages of interaction protection, delay interaction protection and multiple unlocking modes can be set, so that delay man-machine interaction protection is dynamically realized before the interaction protection is executed.
Owner:SHENZHEN CITY SAMKOON TECH
Application processing method and related product
Owner:OPPO CHONGQING INTELLIGENT TECH CO LTD
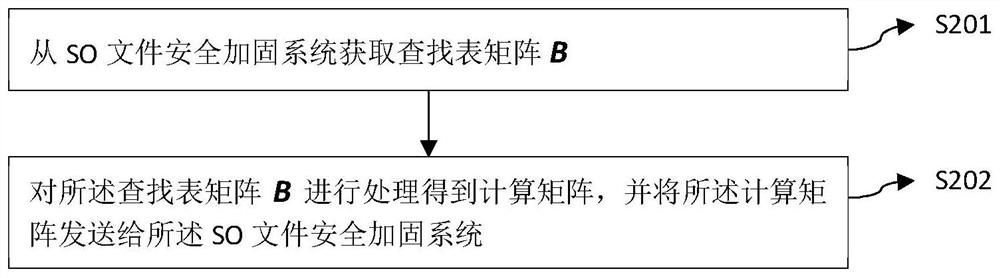
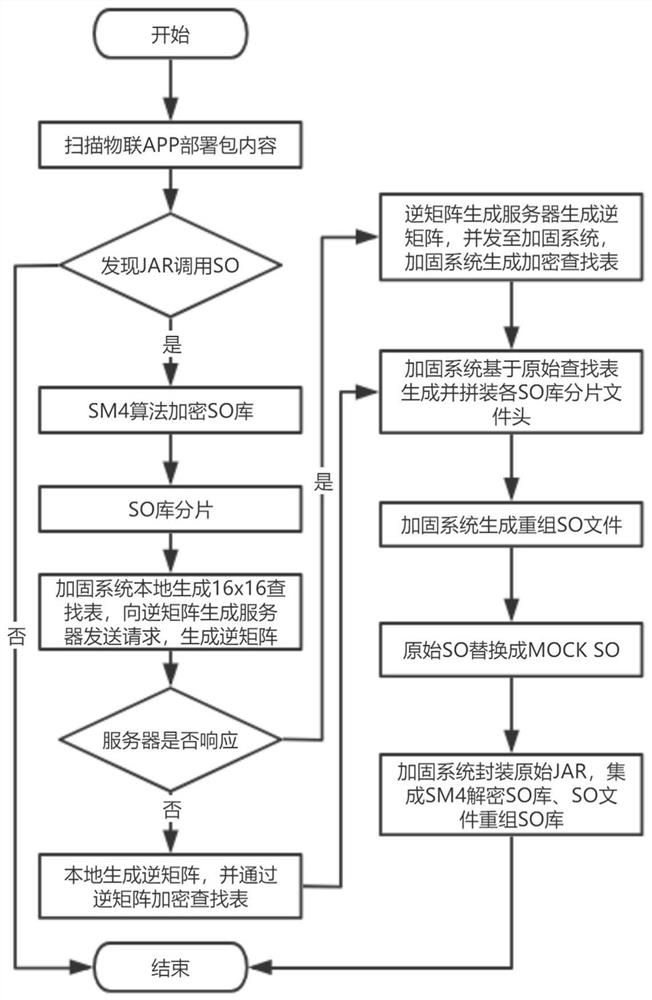
SO file security reinforcement/calling method and system and reversible matrix generation server
PendingCN113849780AIncrease the difficulty of decipheringProgram controlProgram/content distribution protectionShardReverse analysis
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
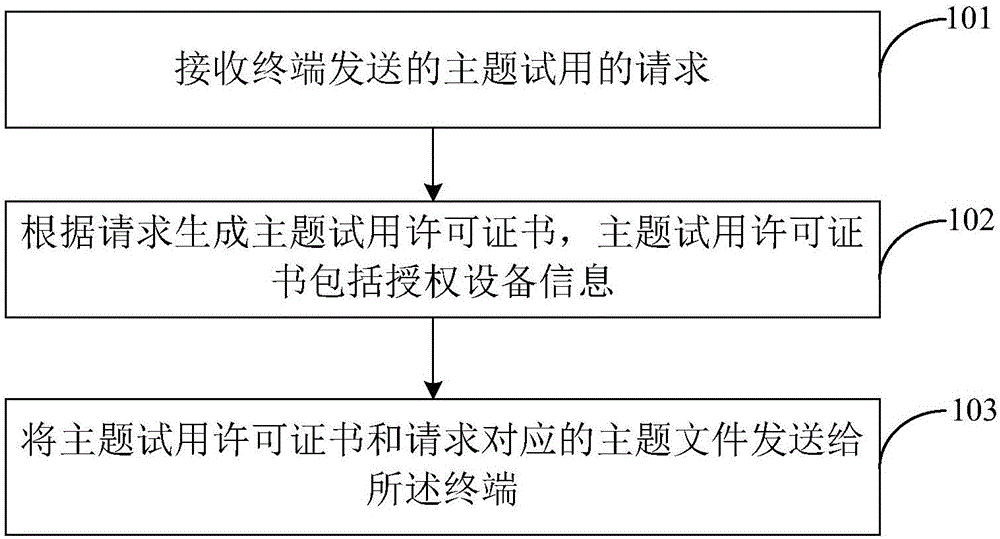
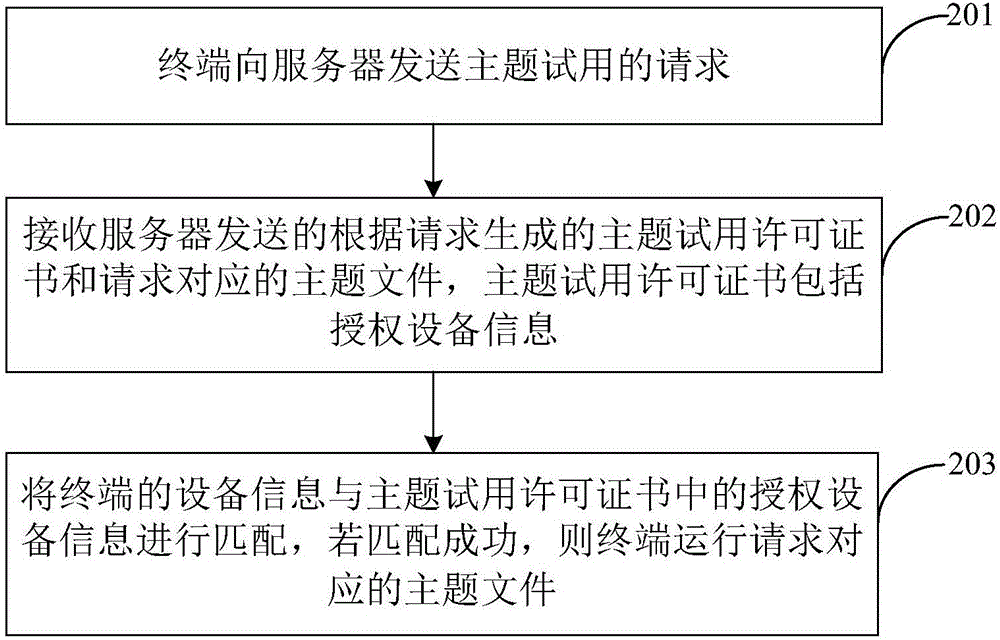
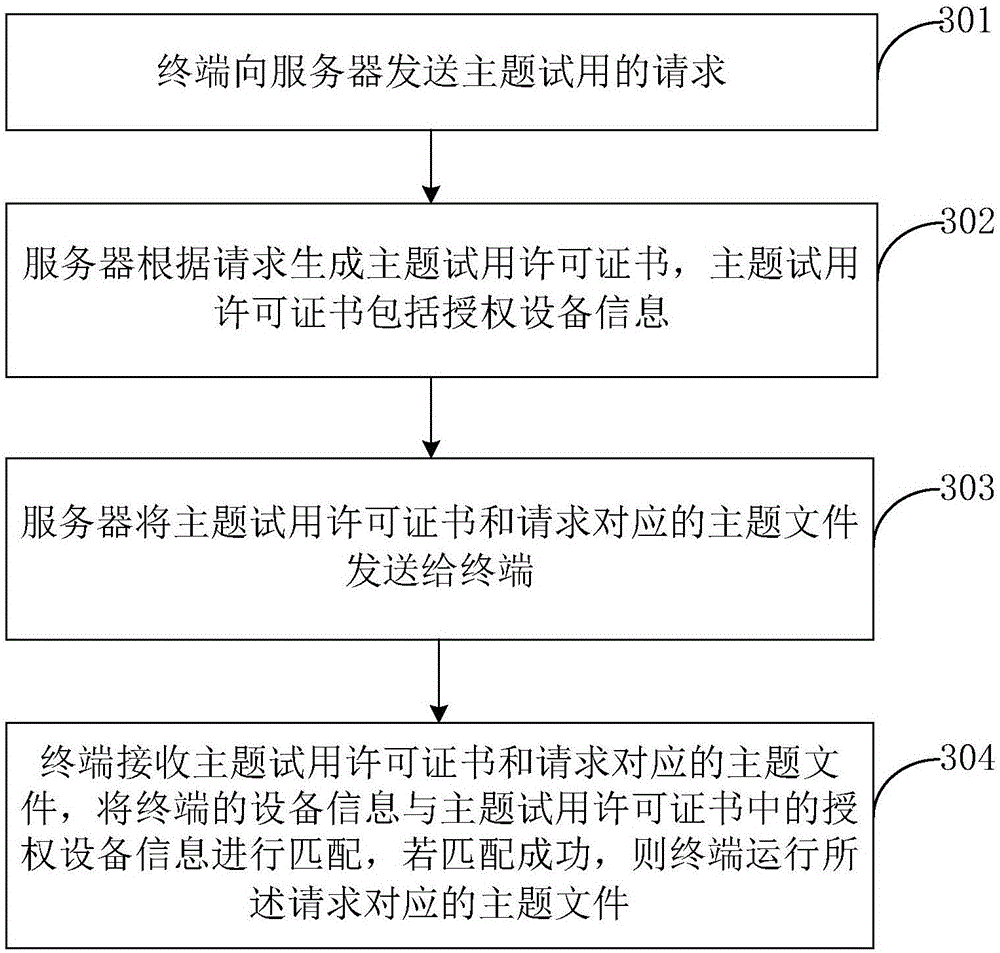
Subject trial method and device
Owner:MEIZU TECH CO LTD
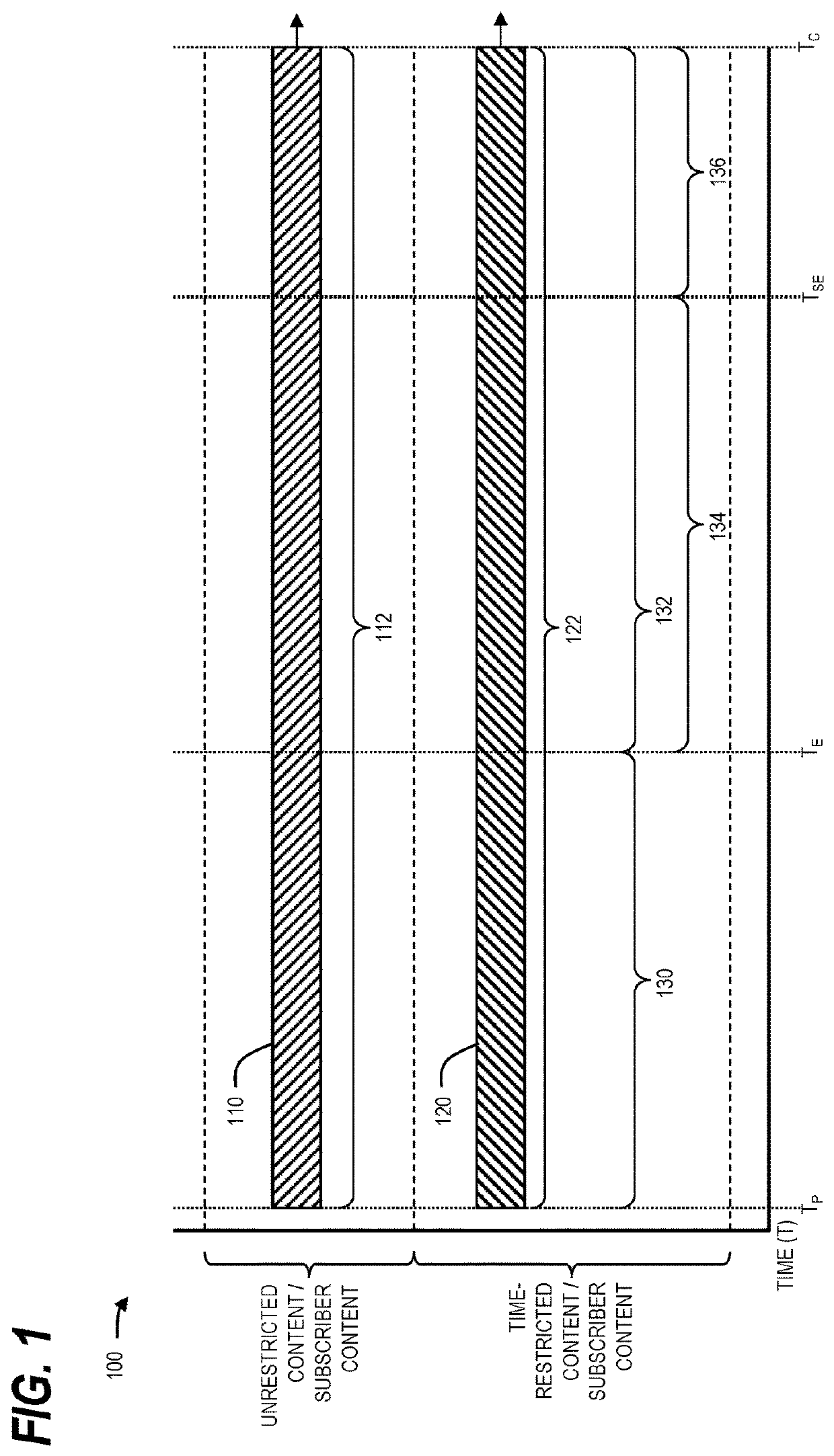
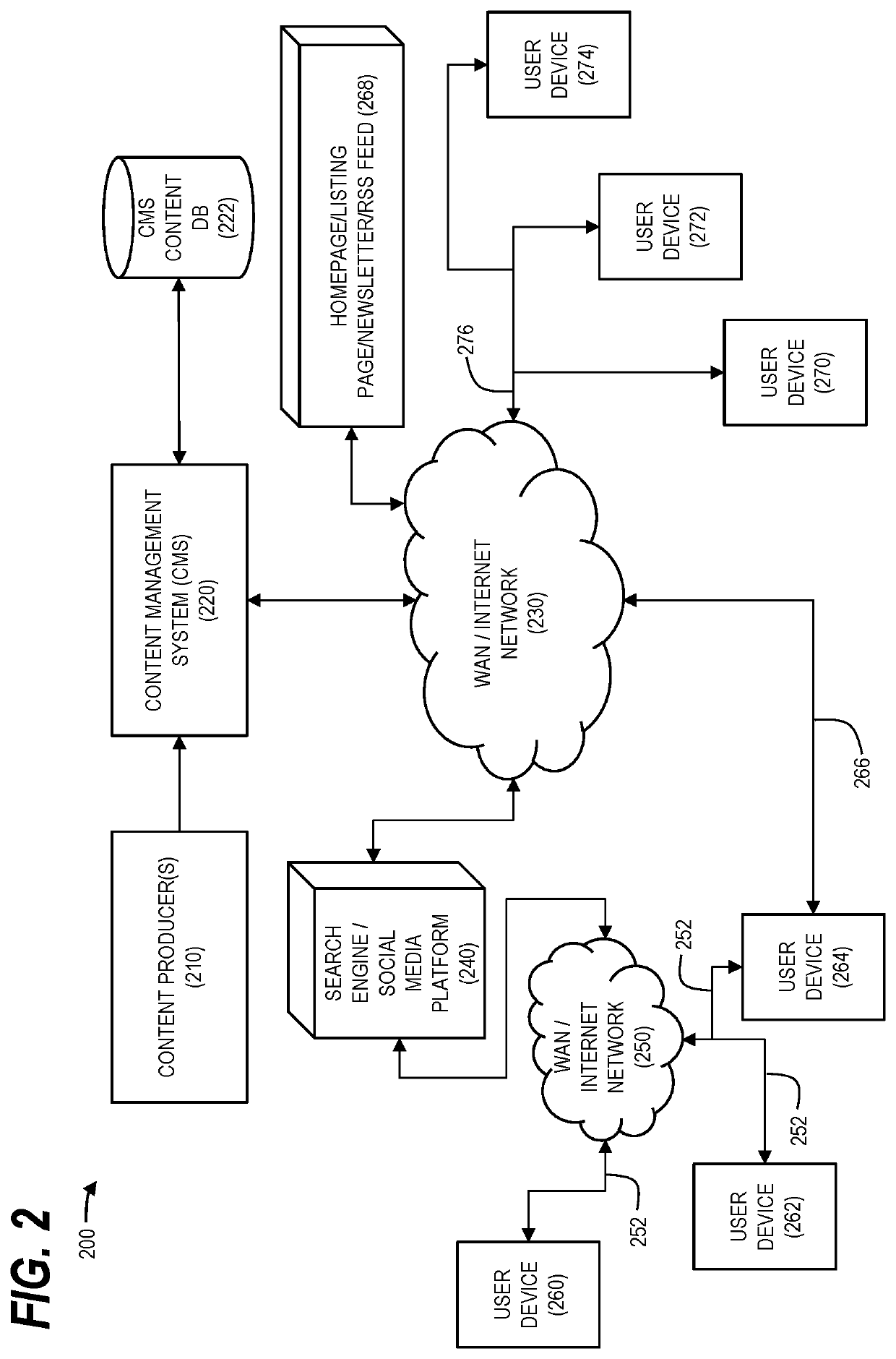
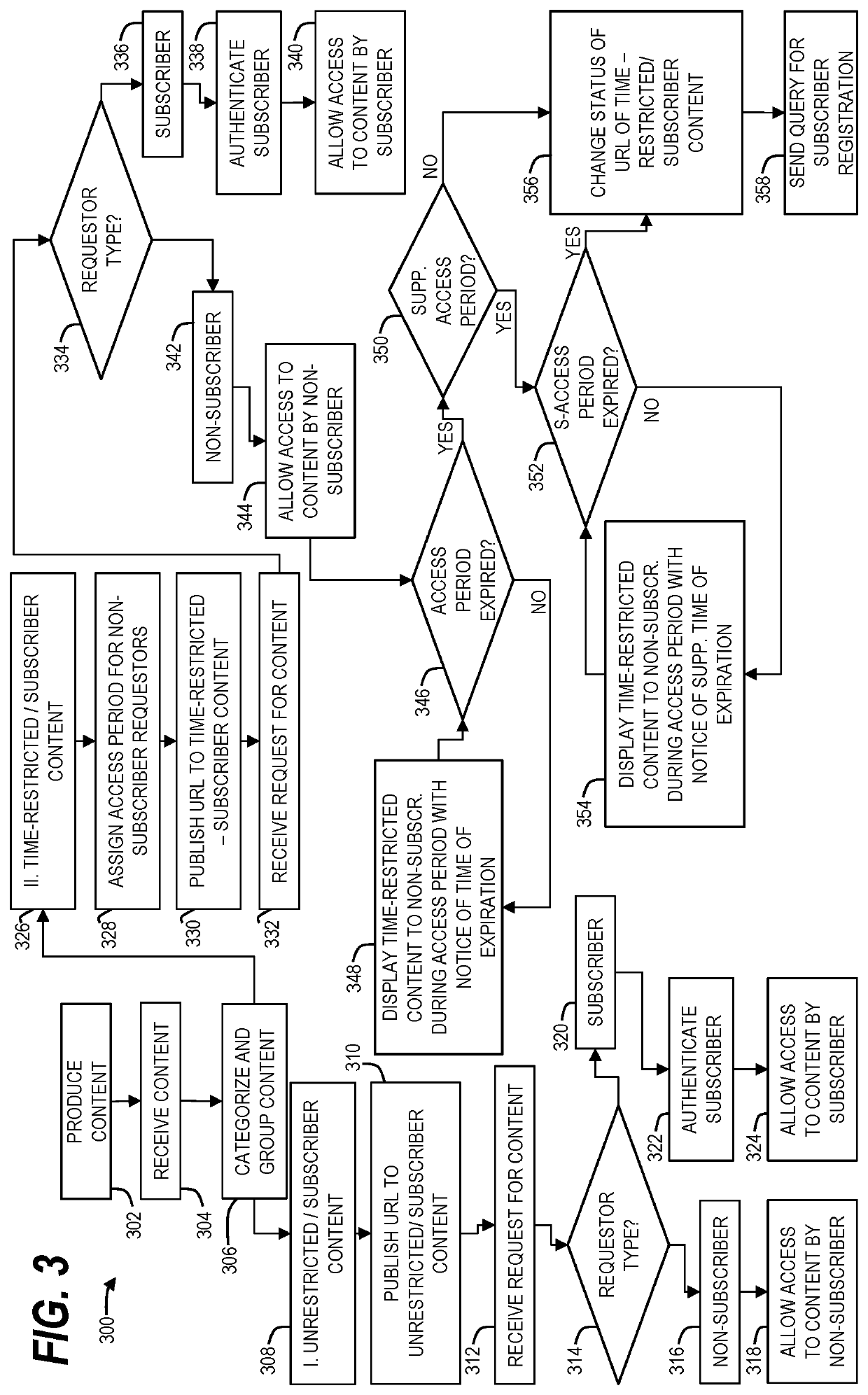
System and method of managing access to time-restricted content
PendingUS20220101287A1Well formedDigital data protectionPayment architectureUniform resource locatorElectronic media
Owner:MOTORSPORT NETWORK
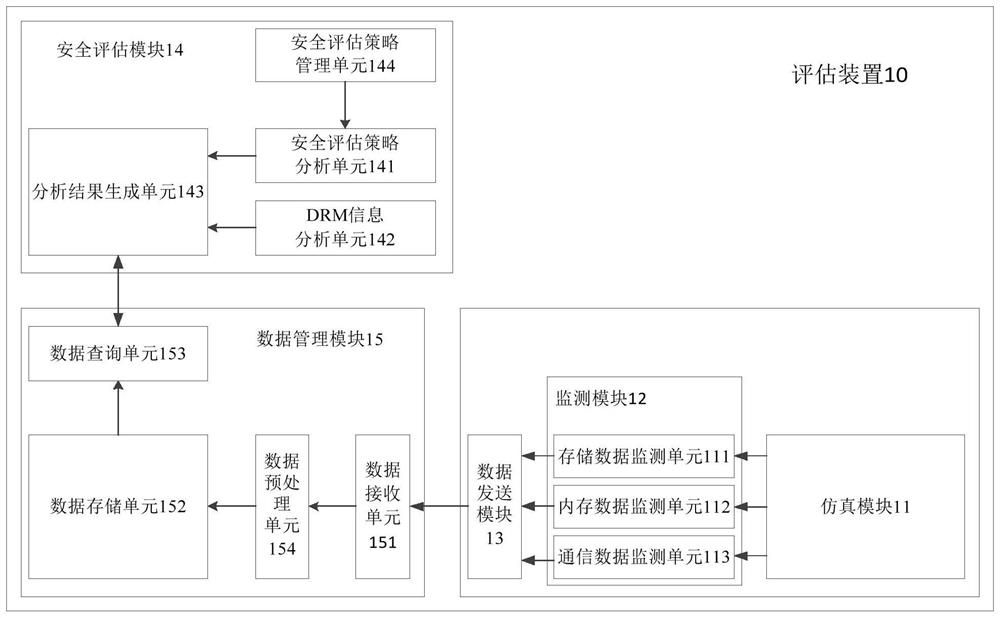
Digital rights management evaluation device for intelligent terminal
Owner:ACADEMY OF BROADCASTING SCI STATE ADMINISTATION OF PRESS PUBLICATION RADIO FILM & TELEVISION
APP extension method based on java remote authorization
InactiveCN106250722APrevent theftRealize one-to-one correspondenceProgram/content distribution protectionPersonal computerMedia access control
Owner:SUZHOU MAIN GOAL SOFTWARE TECH CO LTD
An encryption system for accounting software
PendingCN109214147AEnsure safetyUniqueness guaranteedDigital data protectionProgram/content distribution protectionMicrocontrollerMultiple encryption
Owner:INNER MONGOLIA NORMAL UNIVERSITY +1
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap