Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5 results about "Whitelist" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Whitelisting is the practice of explicitly allowing some identified entities access to a particular privilege, service, mobility, access or recognition. It is the reverse of blacklisting.
Reserved bandwidth allocation method and device based on dynamic network in high-speed industrial bus communication system
InactiveCN113098795AFlexible allocationData switching networksControl communicationsNetwork structure
The invention relates to a reserved bandwidth allocation method based on a dynamic network in a high-speed industrial bus communication system. According to the bandwidth allocation method and device under the dynamic network disclosed by the invention, bandwidth resources are flexibly allocated to the nodes according to the types of the nodes under the dynamic network. The high-speed industrial communication system is mainly used for solving the problems that a traditional bus in an industrial field is low in bandwidth, cannot bear real-time and non-real-time at the same time and is complex in network structure, and can support IPV6 address communication, time-triggered industrial control communication, TSN. And security mechanisms such as white list, deep detection and data encryption can be supported.
Owner:BEIJING NEURON NETWORK TECH CO LTD
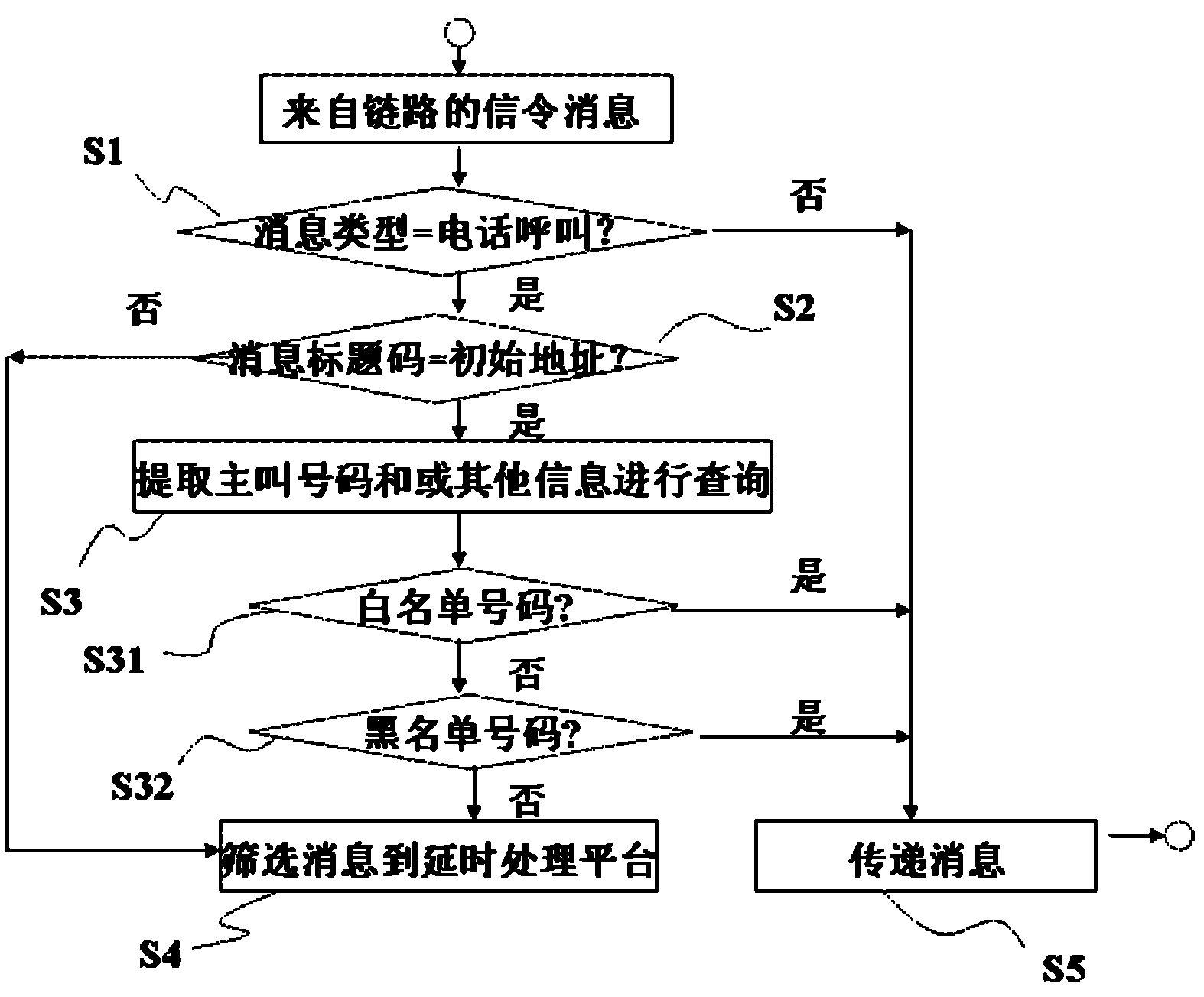
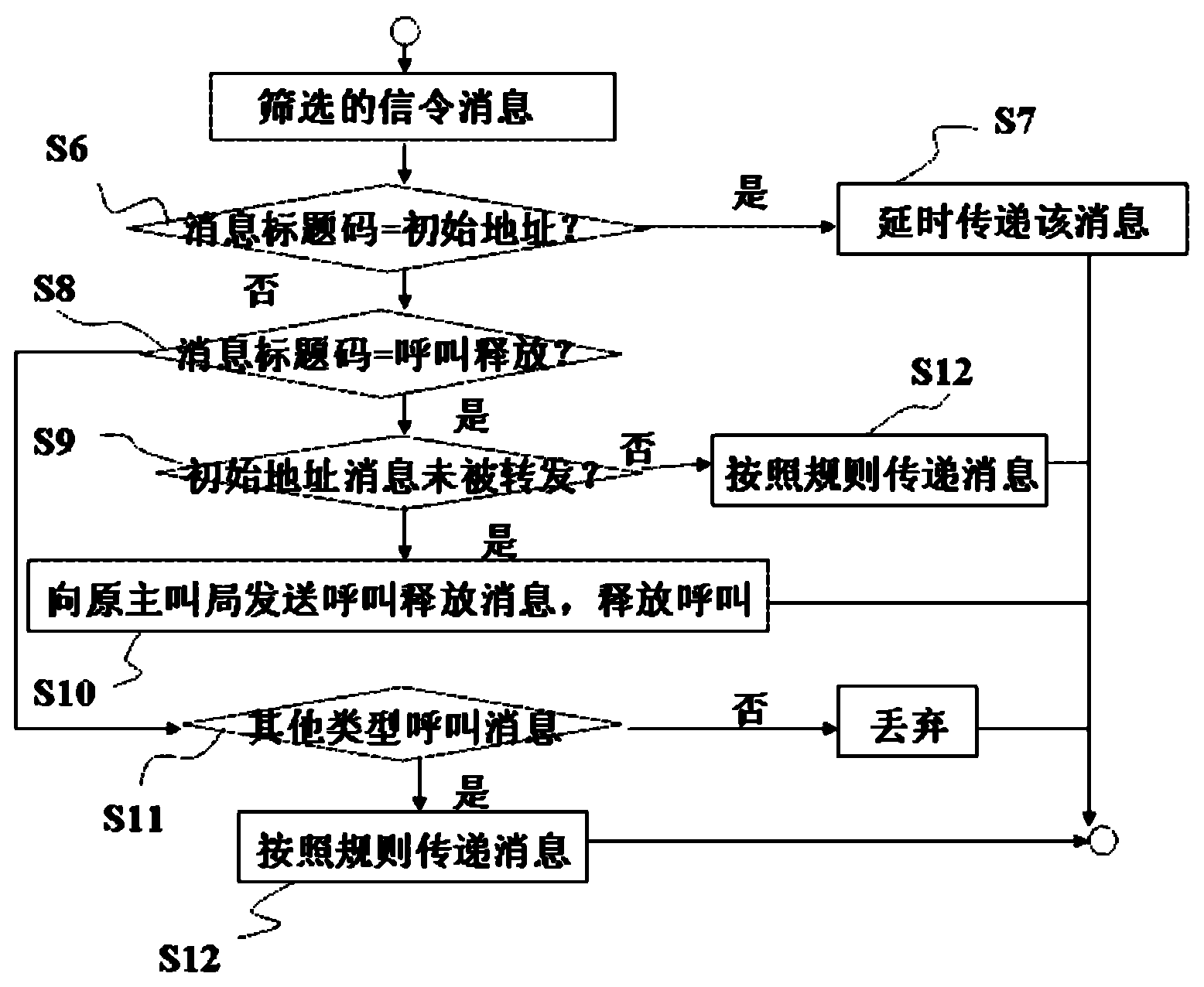
Processing method of time delay calling
InactiveCN103188675AAvoid Equipment UpgradesAvoid data modification problemsSecurity arrangementRelevant informationTime delays
Owner:SHANGHAI LIANGJIANG COMM SYST
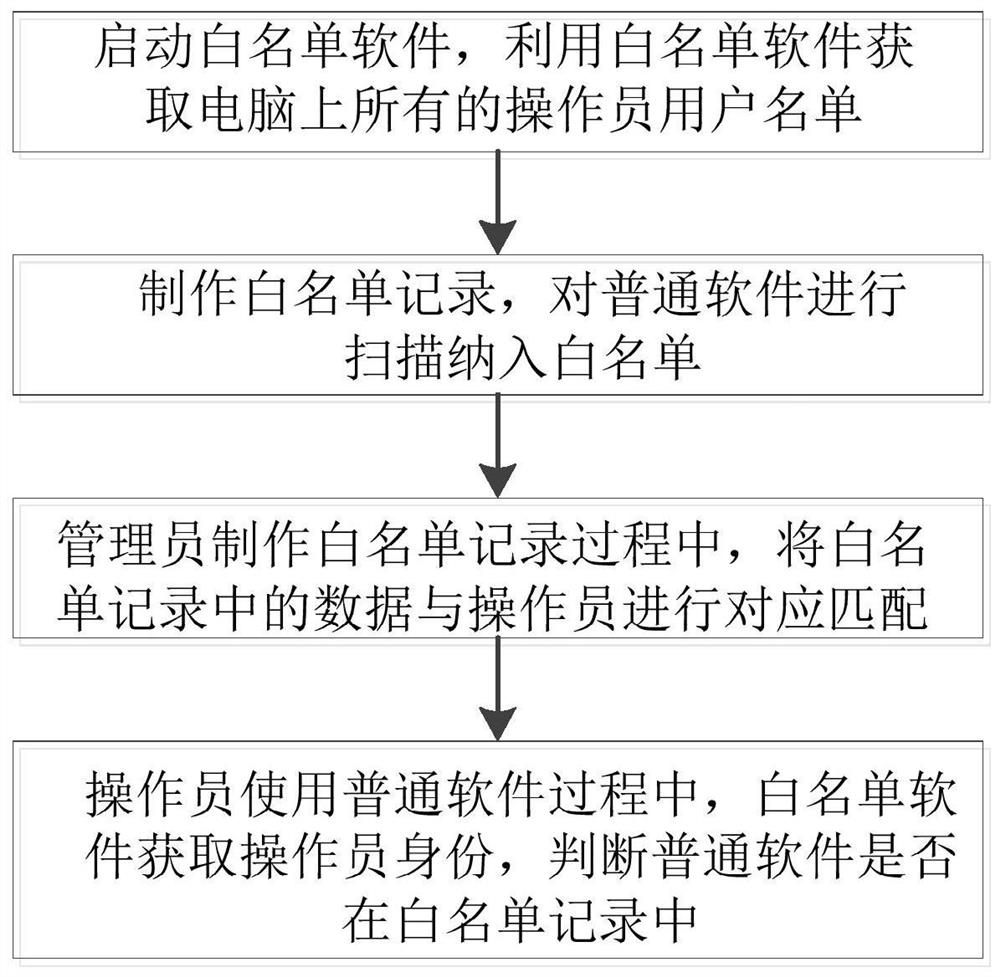
Process industry white list access method and system based on identity authentication
PendingCN113505351AReduce productionCharacter and pattern recognitionDigital data authenticationAccess methodSoftware engineering
Owner:湖南惠而特科技有限公司
Container security execution method and device and storage medium
PendingCN114662092ASolve the mutual access problemMutual access problemPlatform integrity maintainanceWhitelistCode segment
The invention provides a container security execution method and device and a storage medium, and the method comprises the steps: building a main monitor and a plurality of sub-monitors based on an SGX, and carrying out the management of a container through the main monitor and the plurality of sub-monitors; the method comprises the following steps: in response to the first starting of a container system, carrying out integrity measurement on a structural file of the container system, calculating an integrity measurement value of the structural file of the container system, and storing the integrity measurement value as an integrity measurement base value of the container system to a main monitor. The problem that containers in the same Network Namespace can access each other is solved, the problem of isolation between the containers is solved, and malicious attack behaviors of untrusted containers are prevented by setting a container network white list and limiting the access capability of other containers to the running containers. The problems that the integrity and legality of a code segment and a stack function return address are verified when a container runs, the code segment is tampered when the container runs, and the stack function return address overflows are solved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
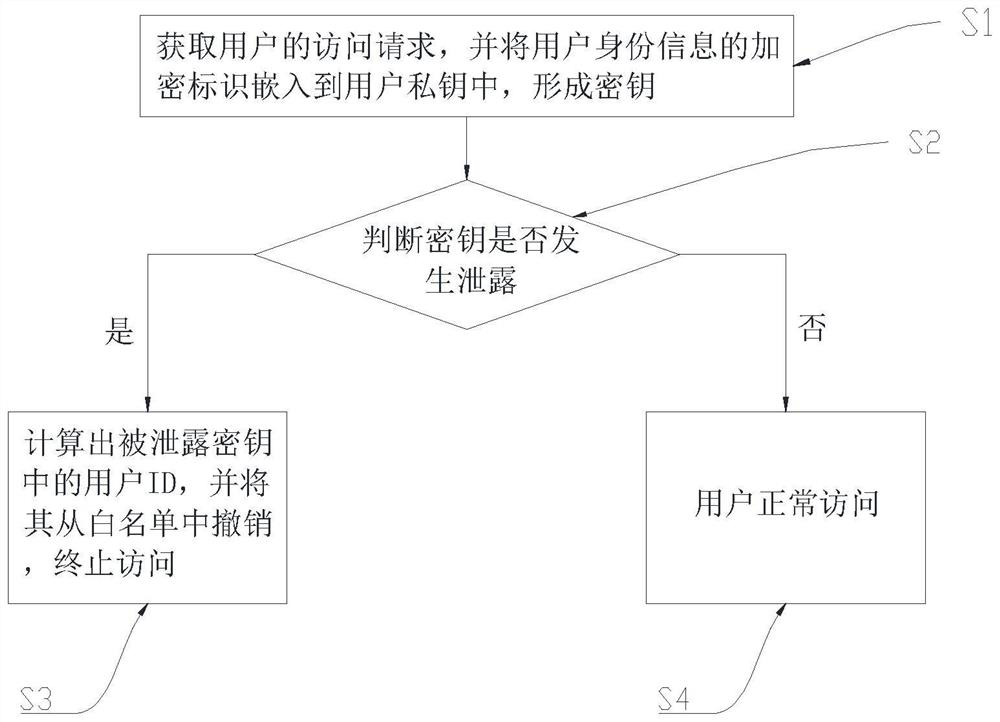
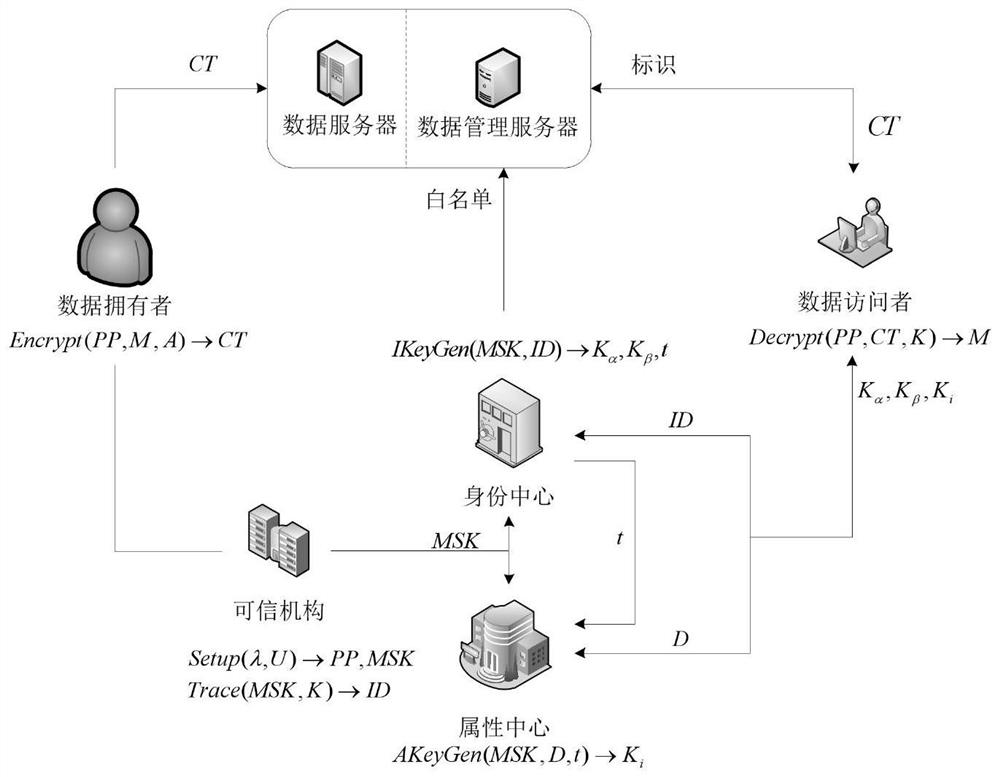
Attribute encryption method and device for resisting key abuse on lattice, computer equipment and storage medium
PendingCN114866239AKey distribution for secure communicationInformation technology support systemComputer equipmentWhitelist
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap