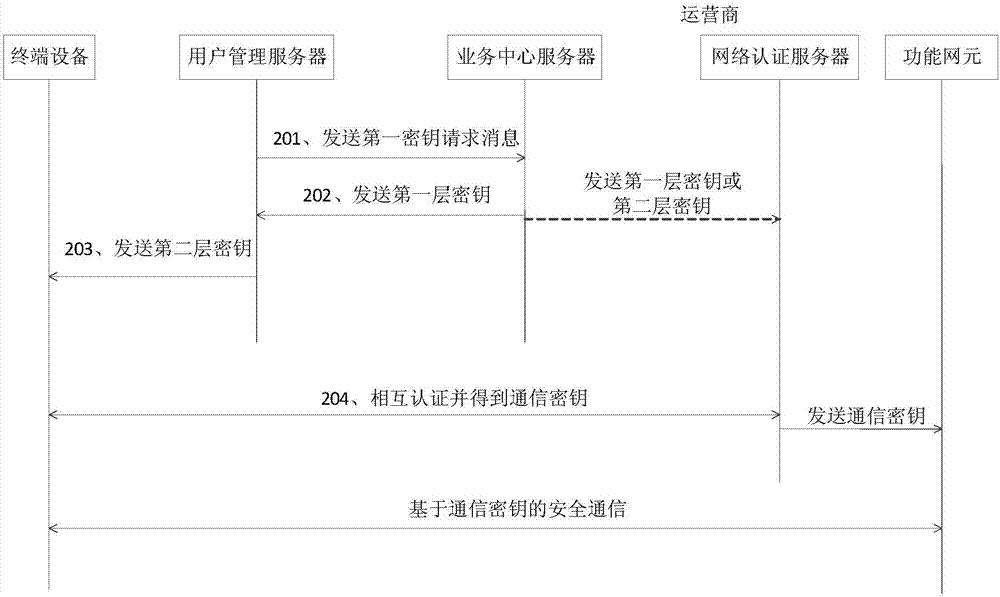
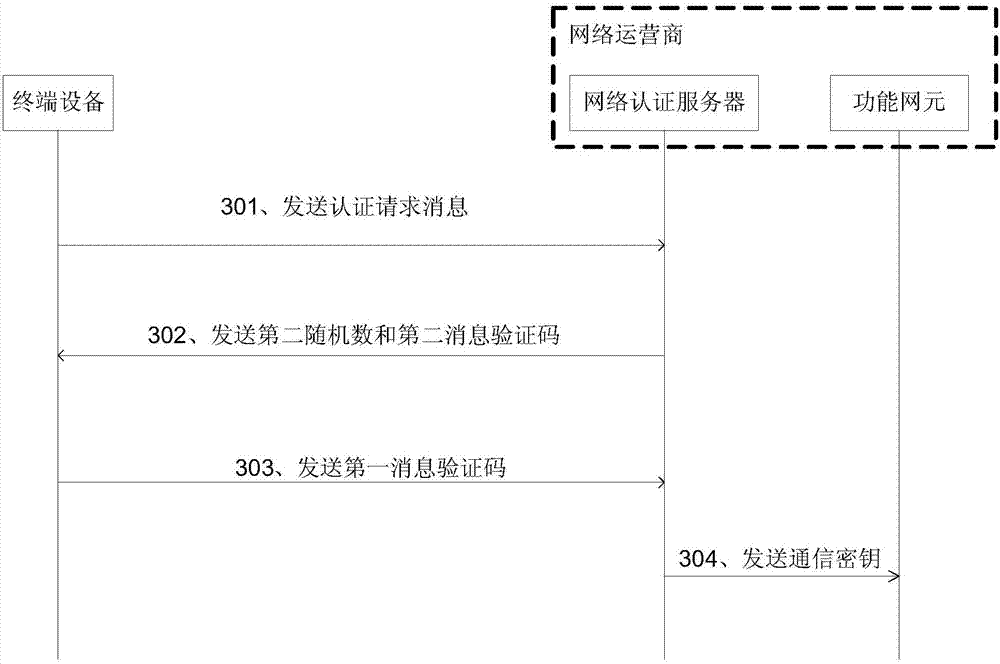
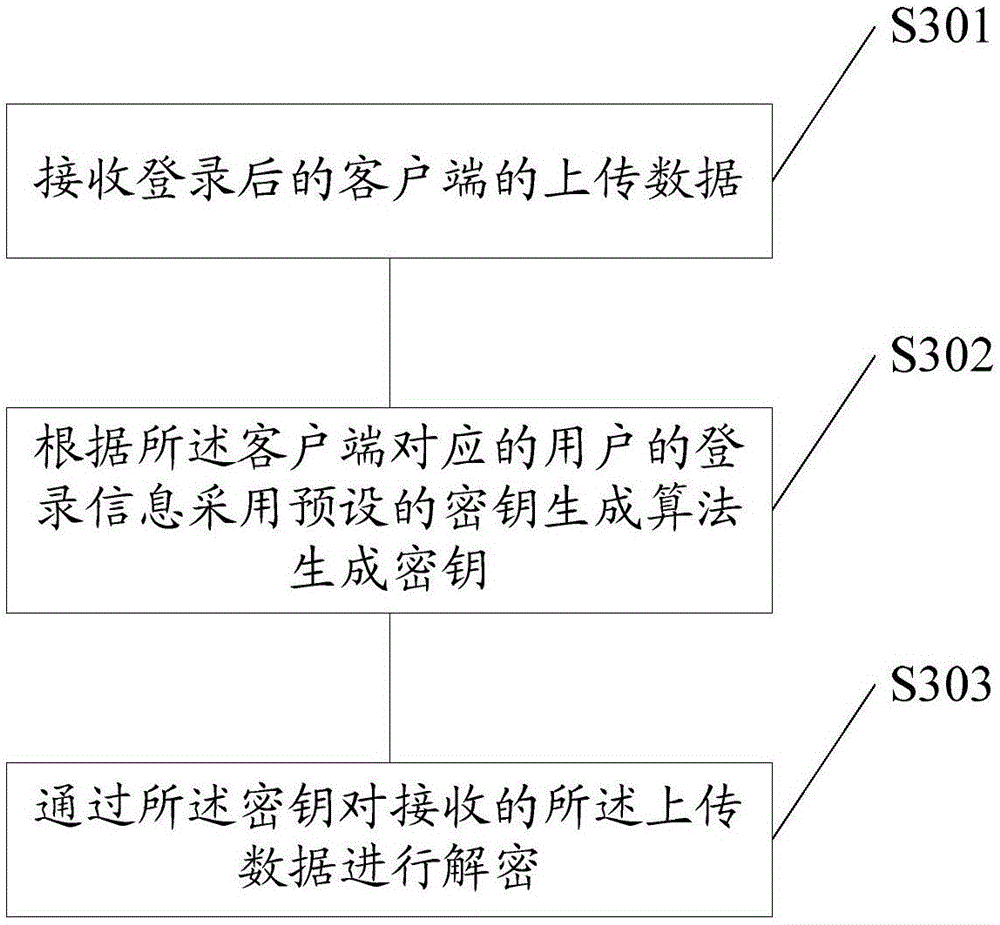
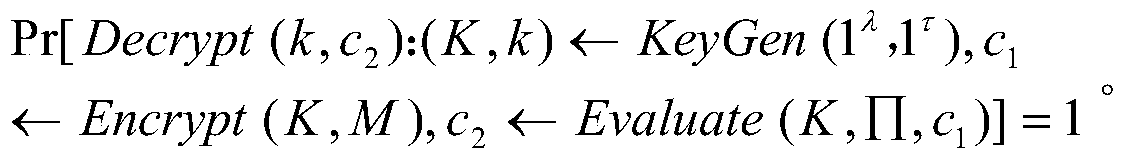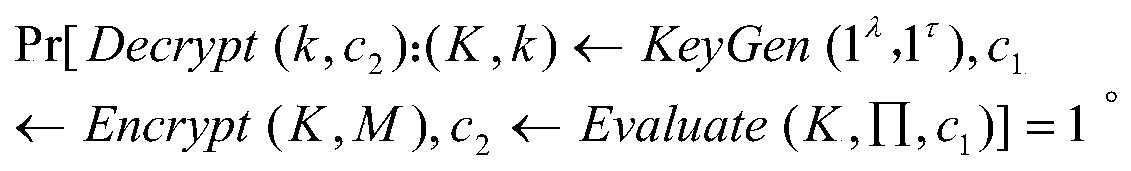Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
61results about "Key distribution for secure communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
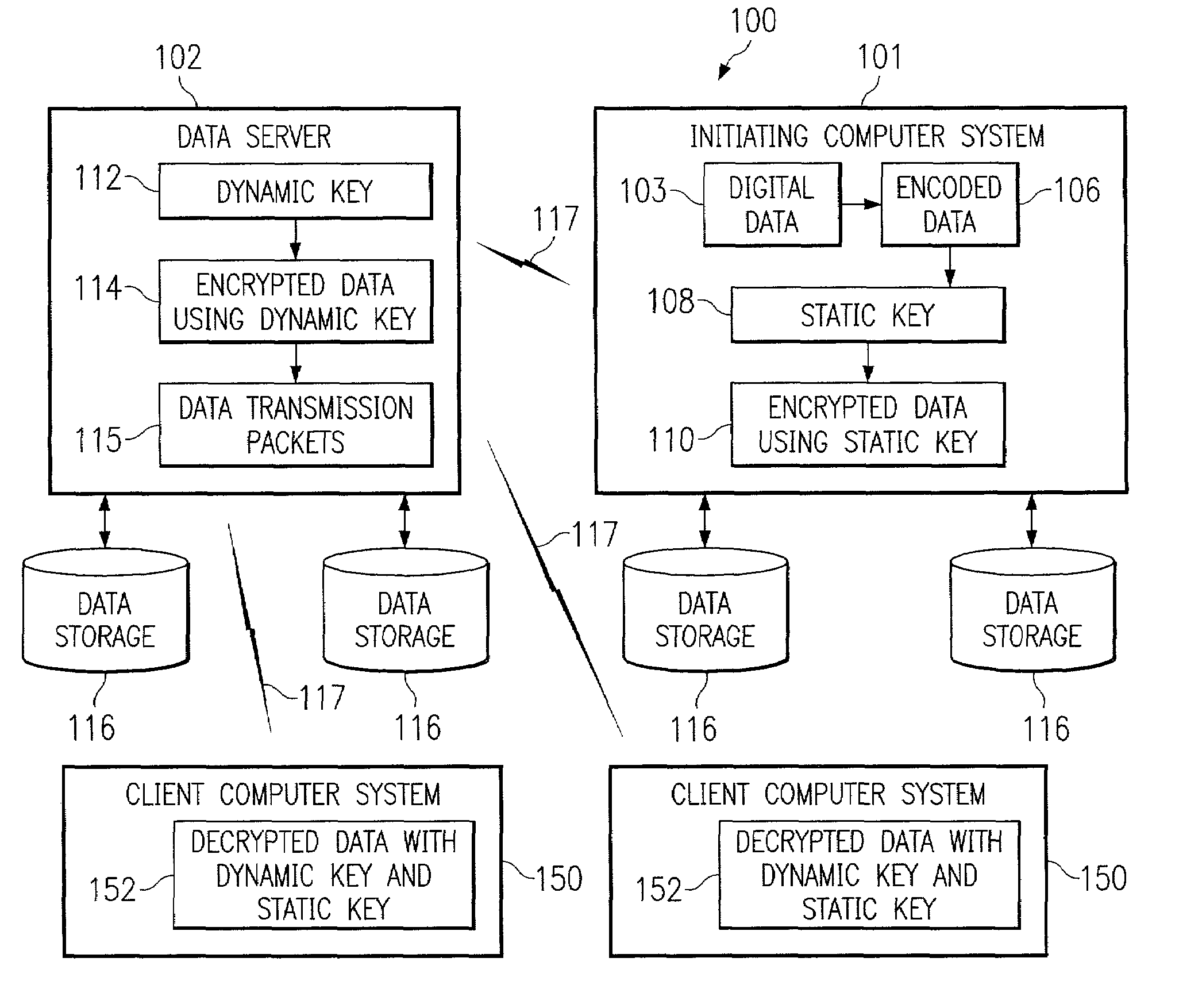
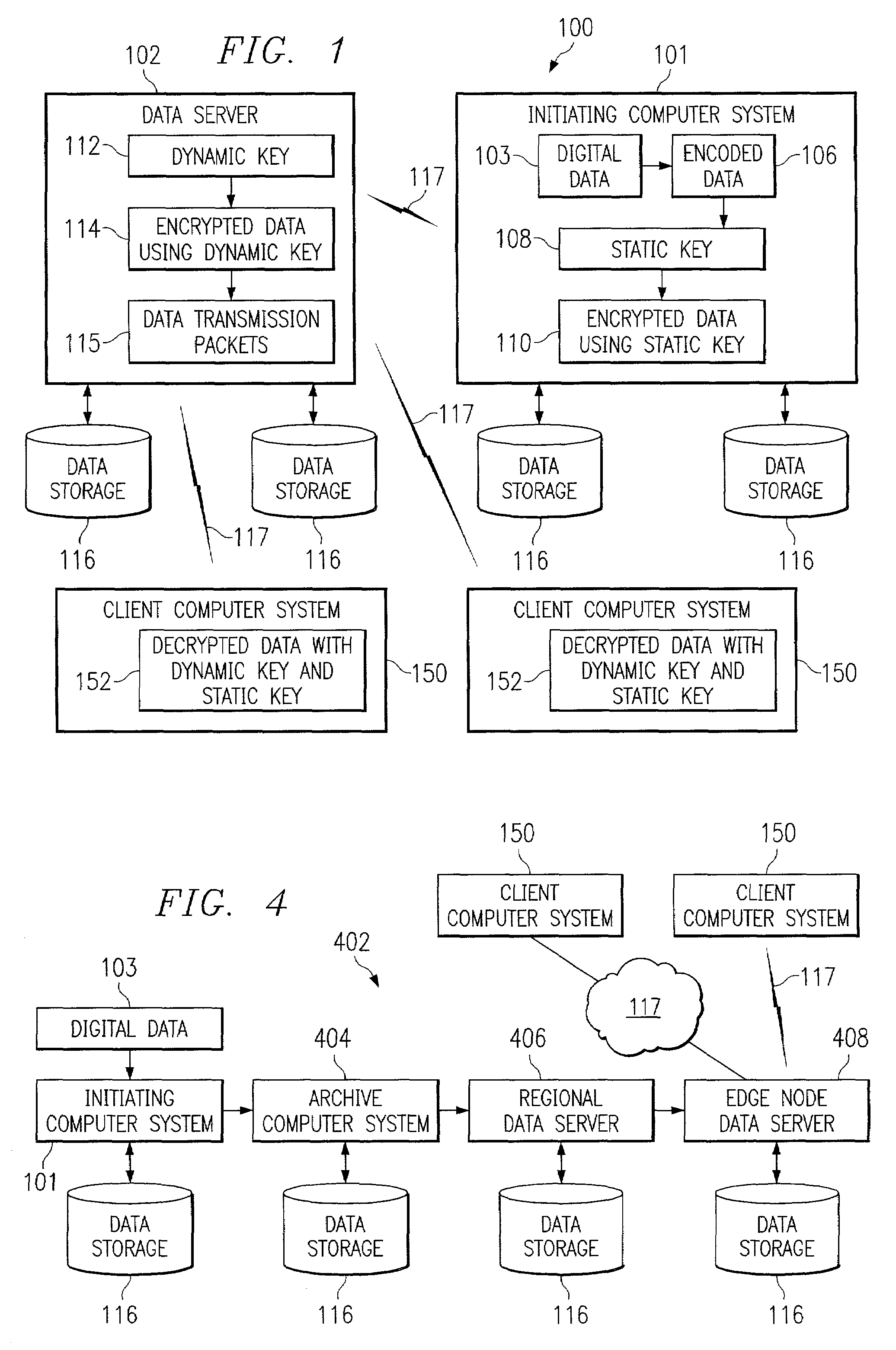
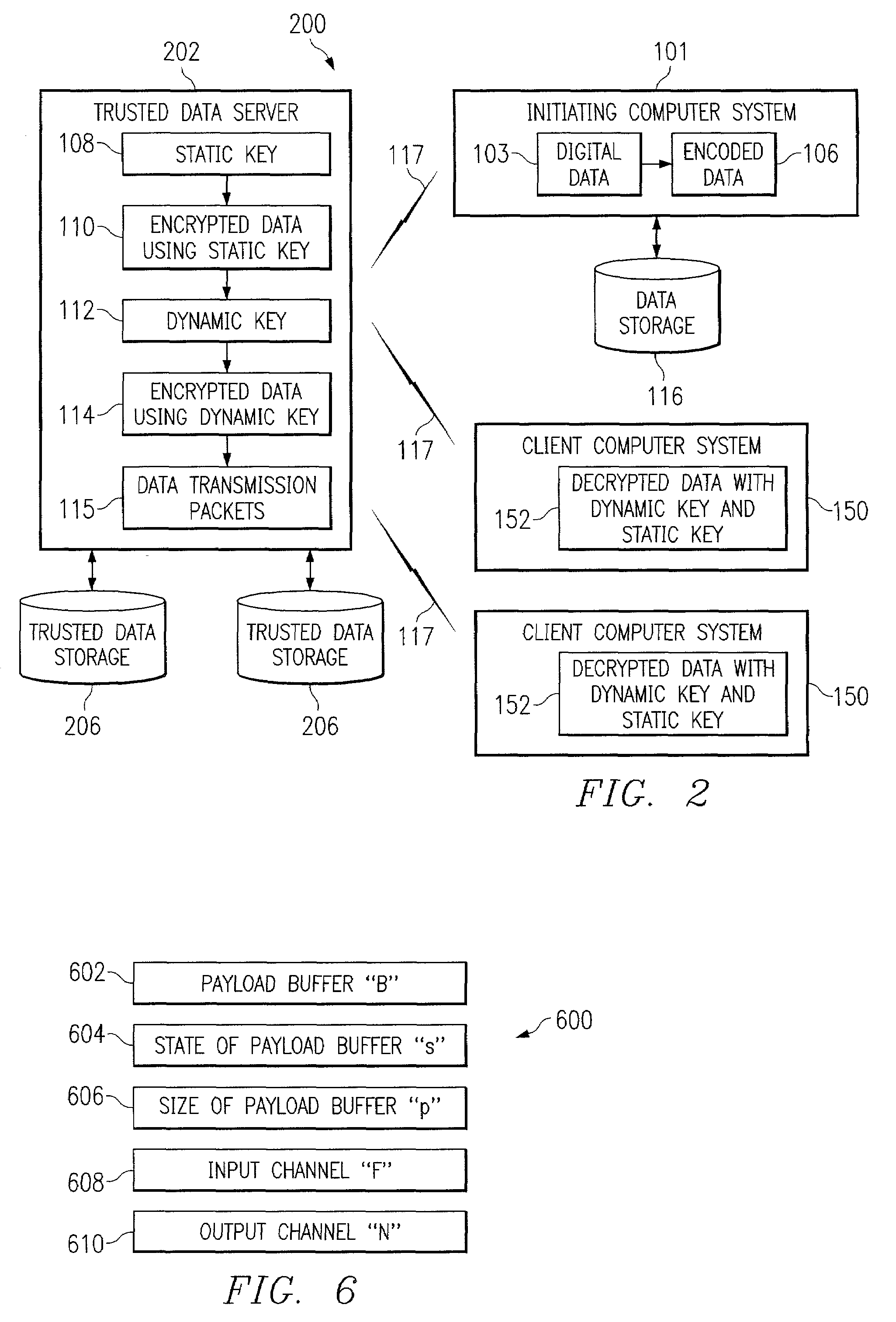
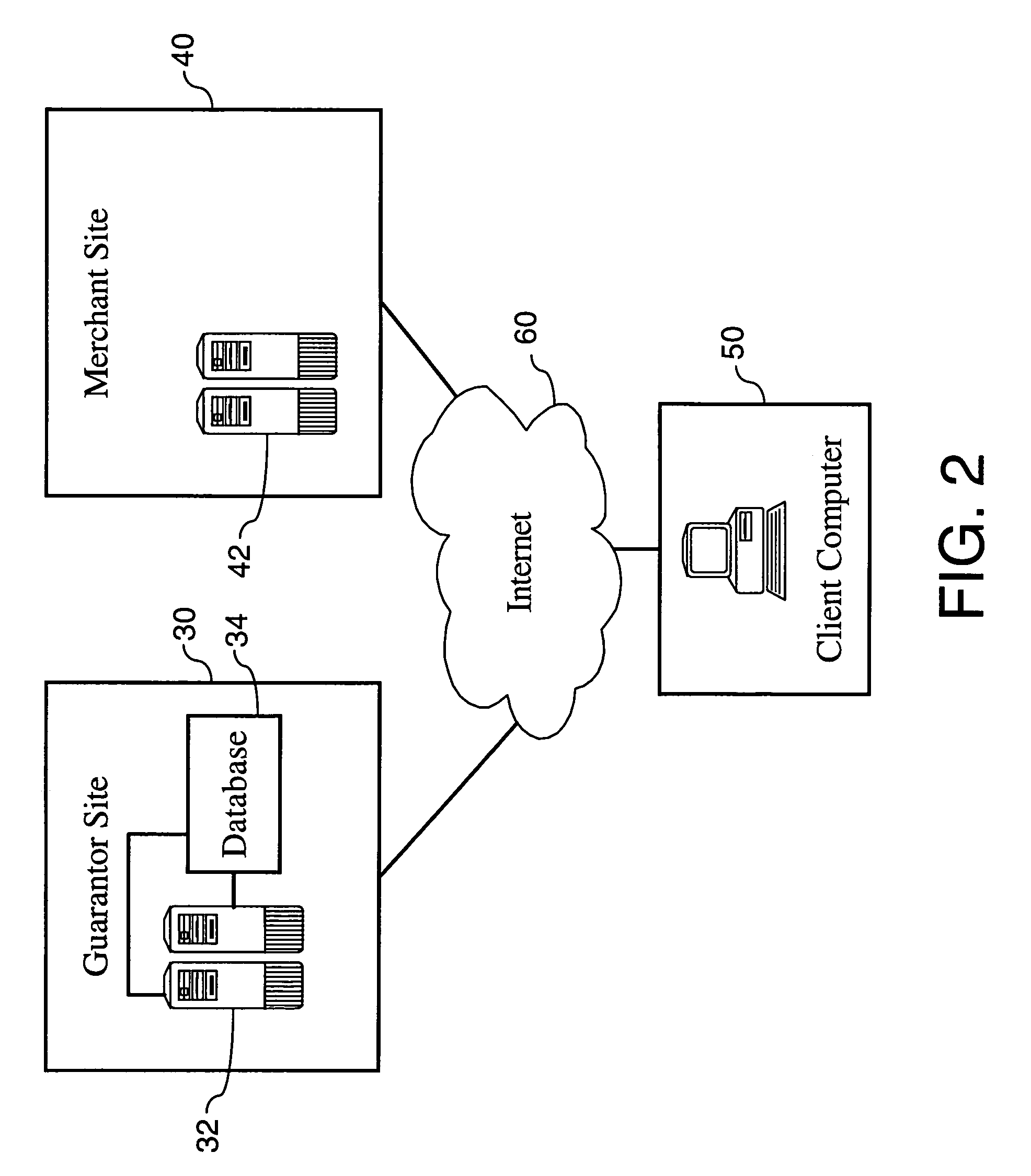
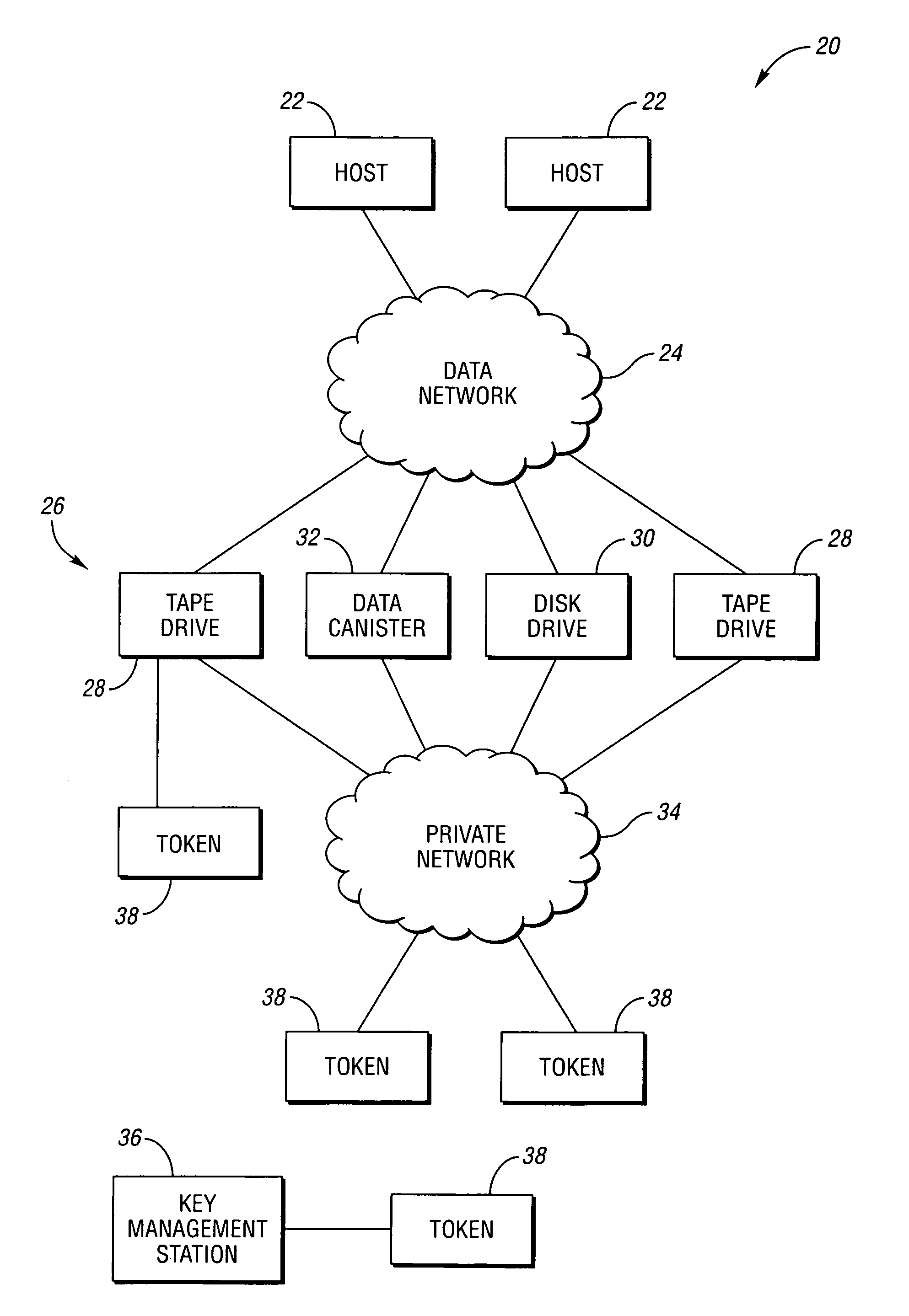
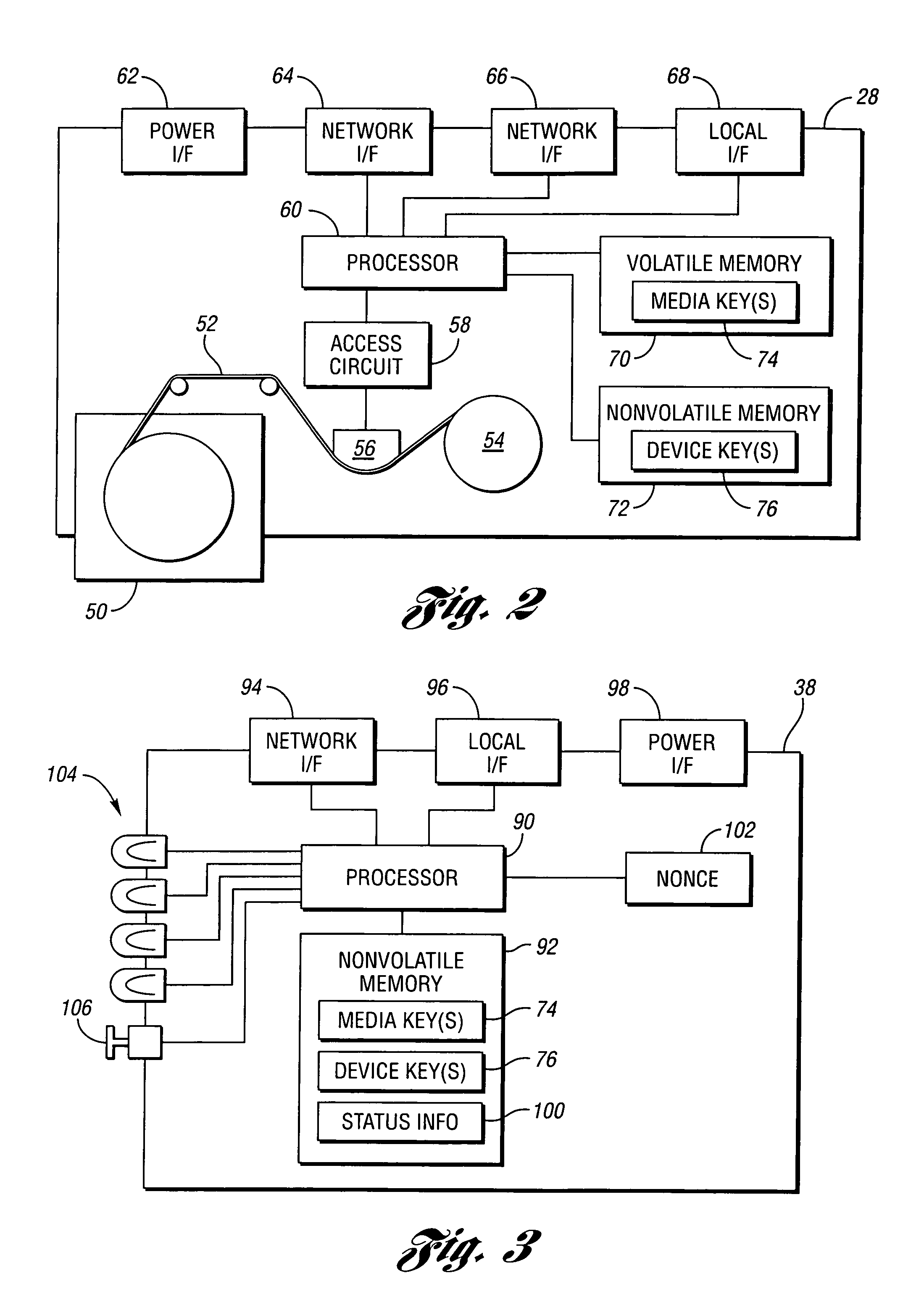
Systems, methods, and computer program products for accelerated dynamic protection of data
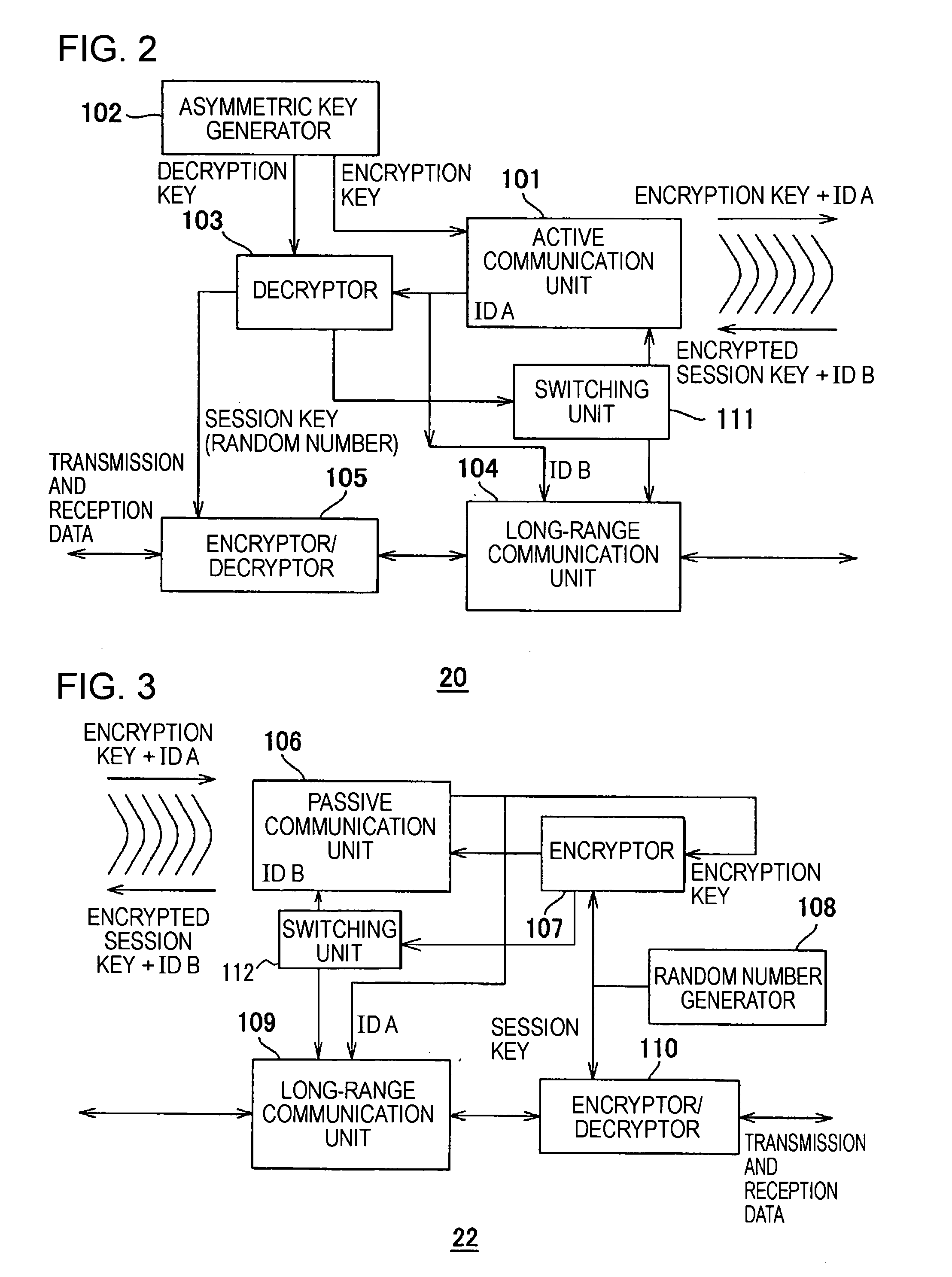
InactiveUS7280658B2Sufficient protectionKey distribution for secure communicationSecret communicationComputer resourcesEnd to end security
Owner:SNAP INC
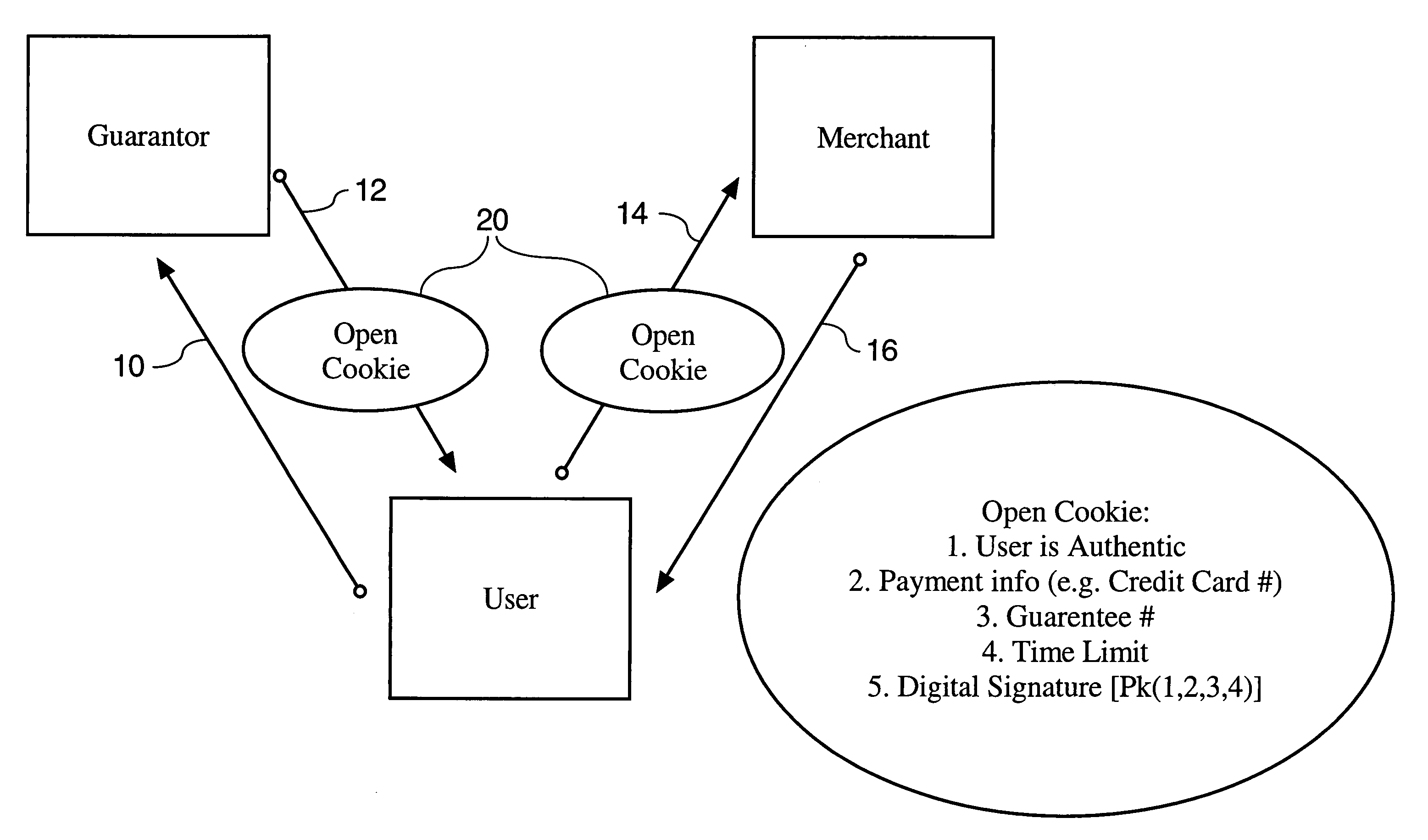
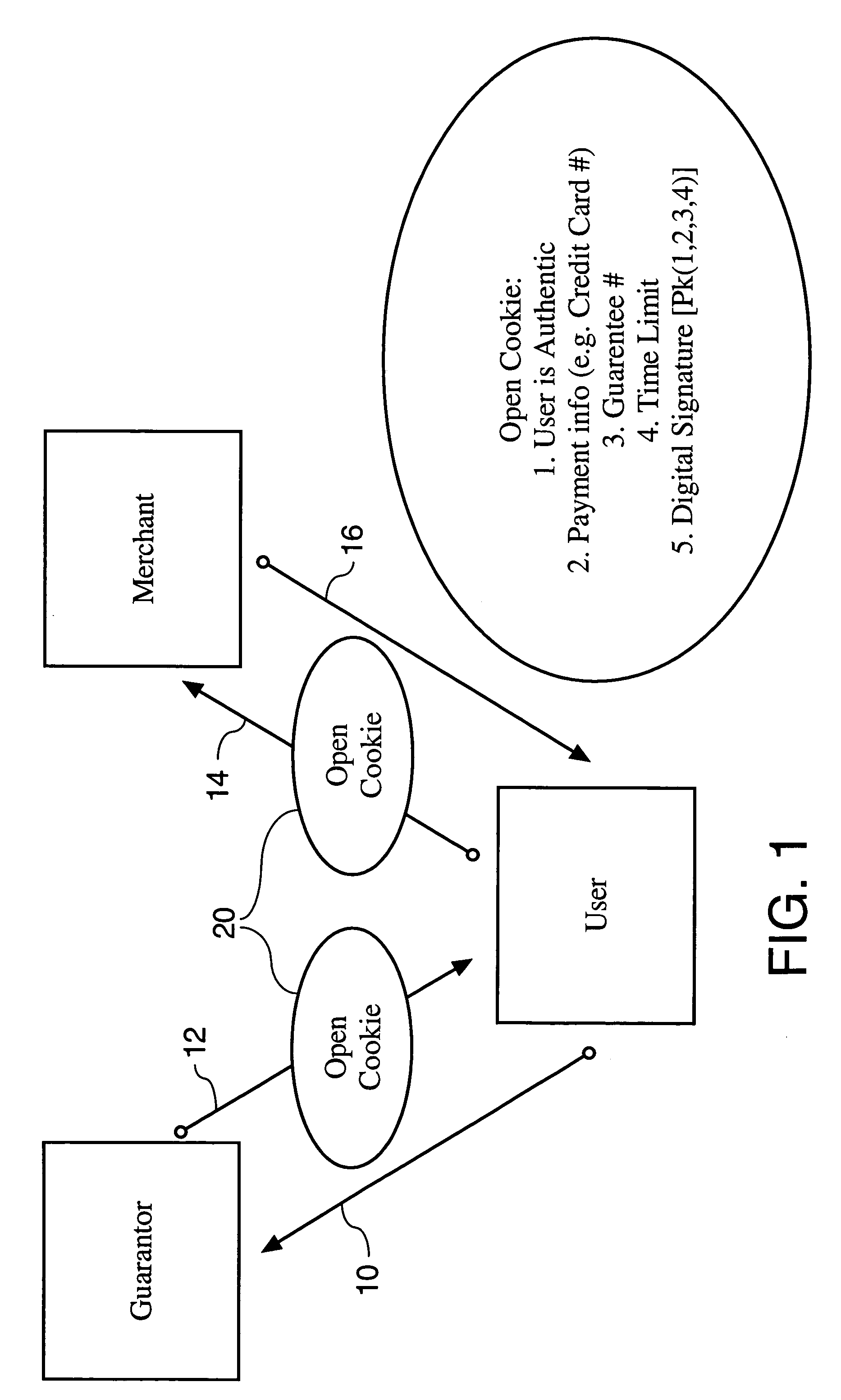
Method and system for secure guaranteed transactions over a computer network
InactiveUS6957334B1Minimize spreadingKey distribution for secure communicationVolume/mass flow measurementPaper documentAuthentication protocol
Owner:THE BRODIA GROUP
Communication System And Communication Device
InactiveUS20080020707A1Easy to identifyReduce riskKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCommunications system
Owner:SONY CORP
Cargo theft prevention method and system
InactiveUS20050219037A1StampsKey distribution for secure communicationComputer hardwareCommunications system
Owner:HUANG TAO
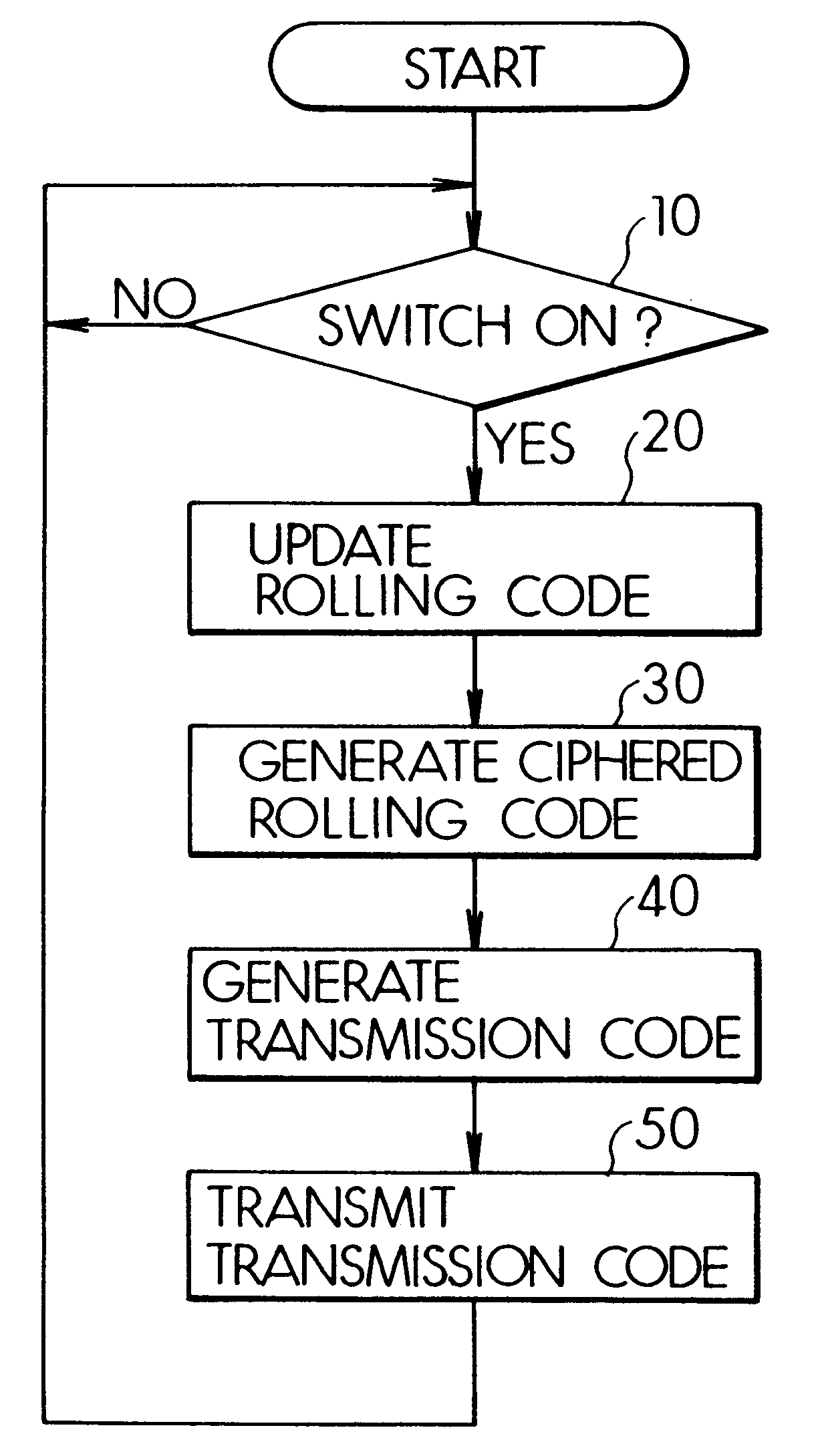
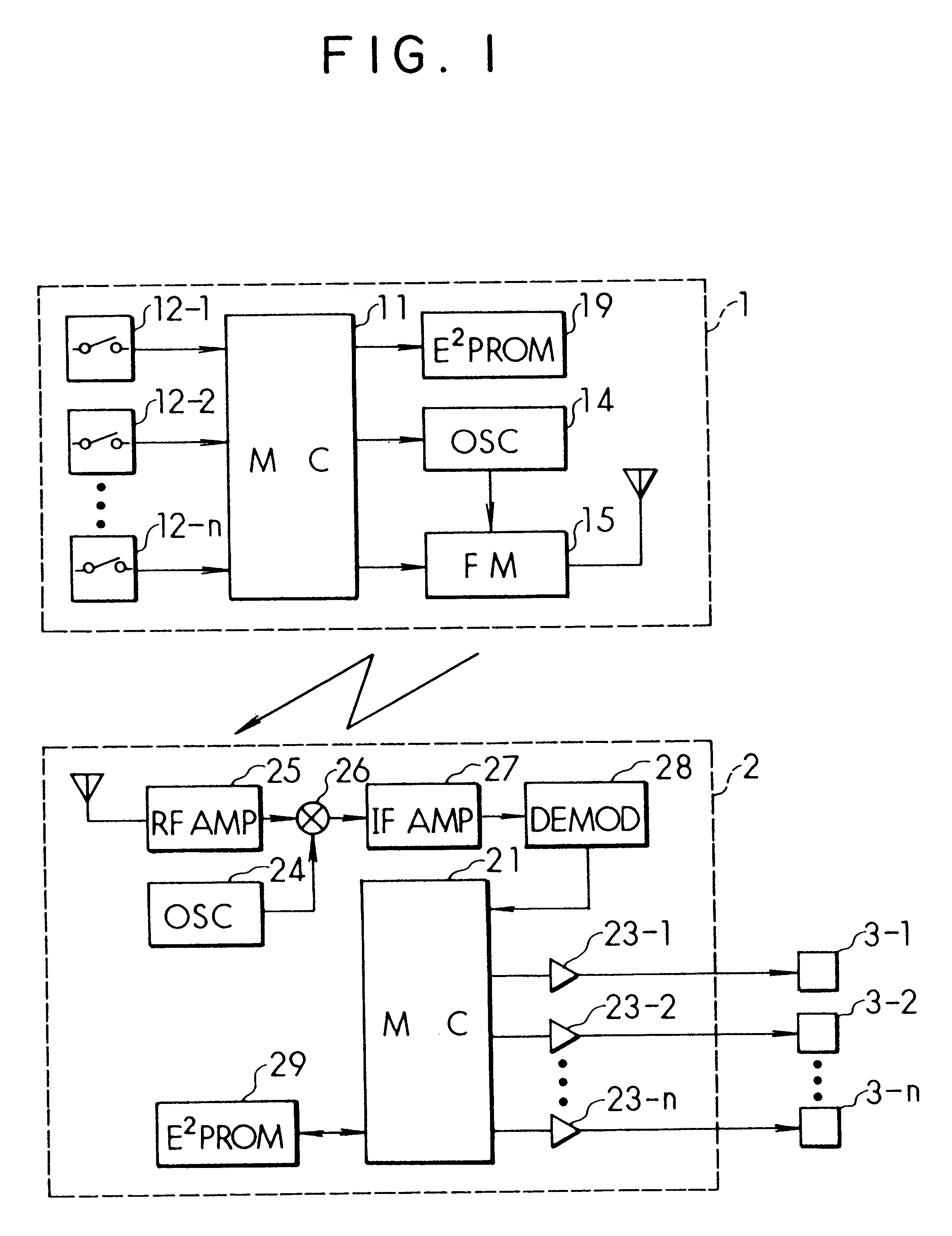
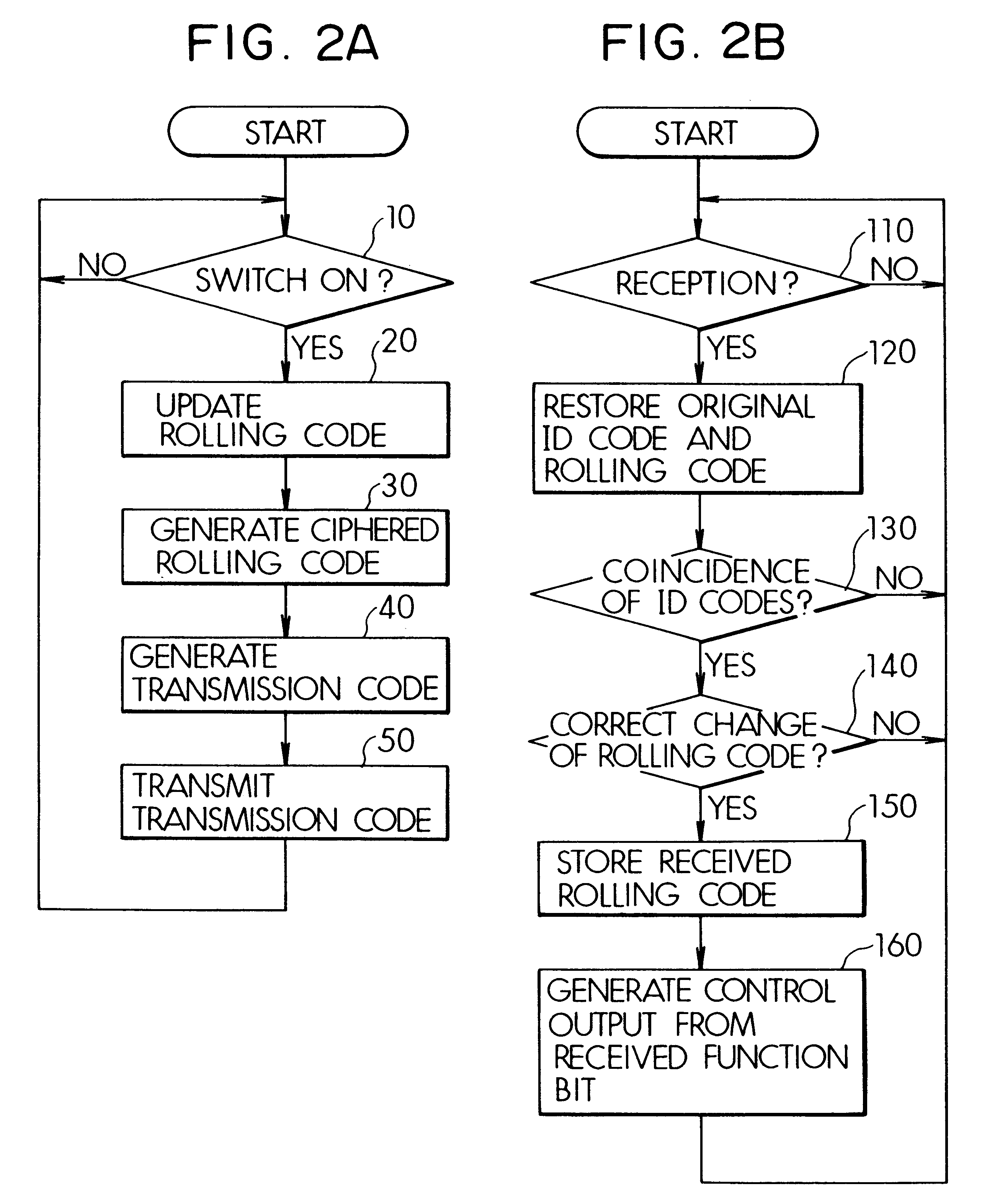
Remote control system and method having a system-specific code
InactiveUS6181252B1Key distribution for secure communicationElectric signal transmission systemsEEPROMRolling code
Owner:DENSO CORP
Key distribution and authentication methods, devices and systems
ActiveCN107317789AReduce the burden onSolve the problem that it cannot be applied to smart devices that do not support USIM cardsKey distribution for secure communicationSecurity arrangementSecure communicationWeb authentication
Owner:HUAWEI TECH CO LTD
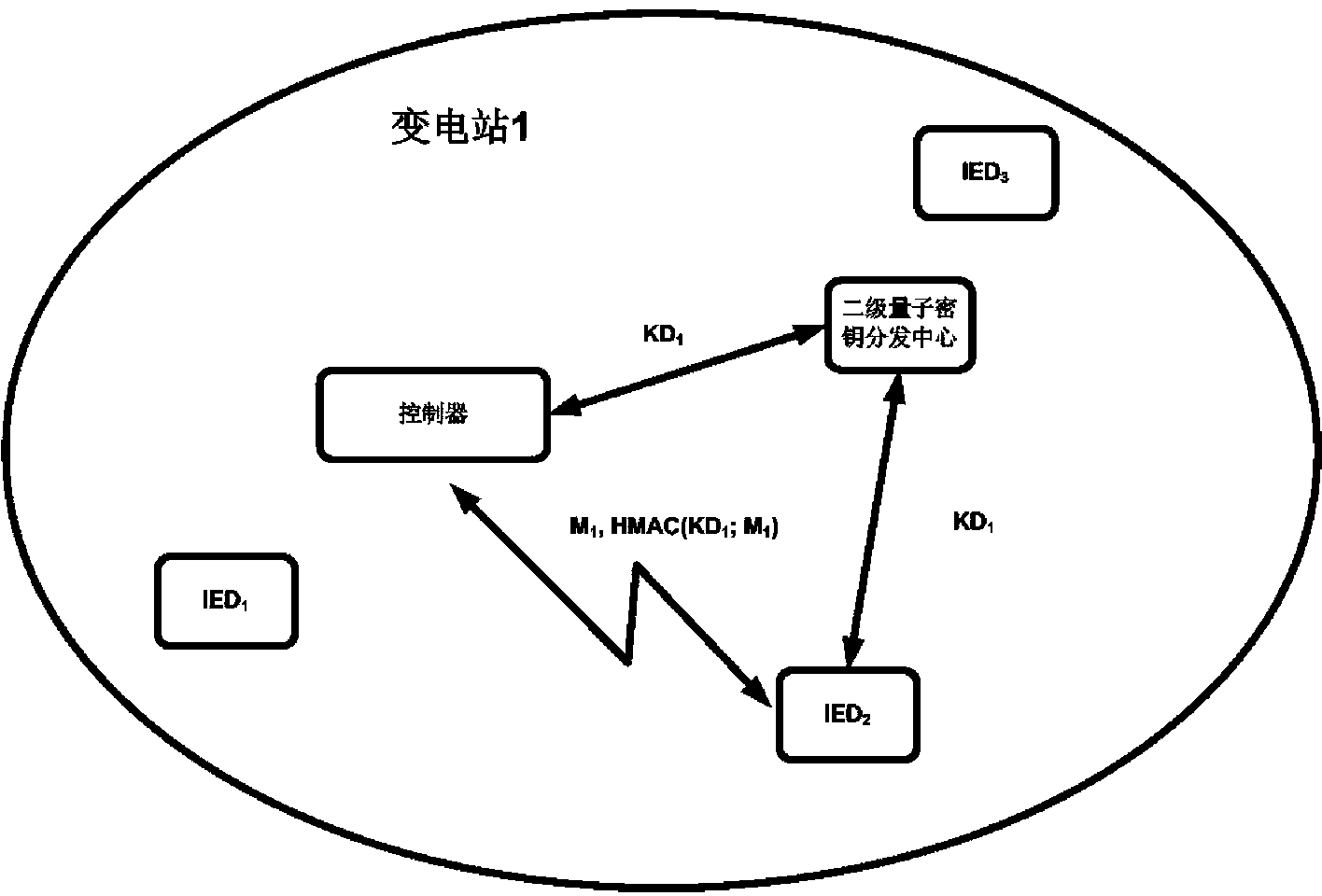
Transformer substation quantum communication model, quantum secret key distribution center and model achieving method
ActiveCN102983965AImprove securityImprove reliabilityKey distribution for secure communicationKey distribution centerQuantum key distribution
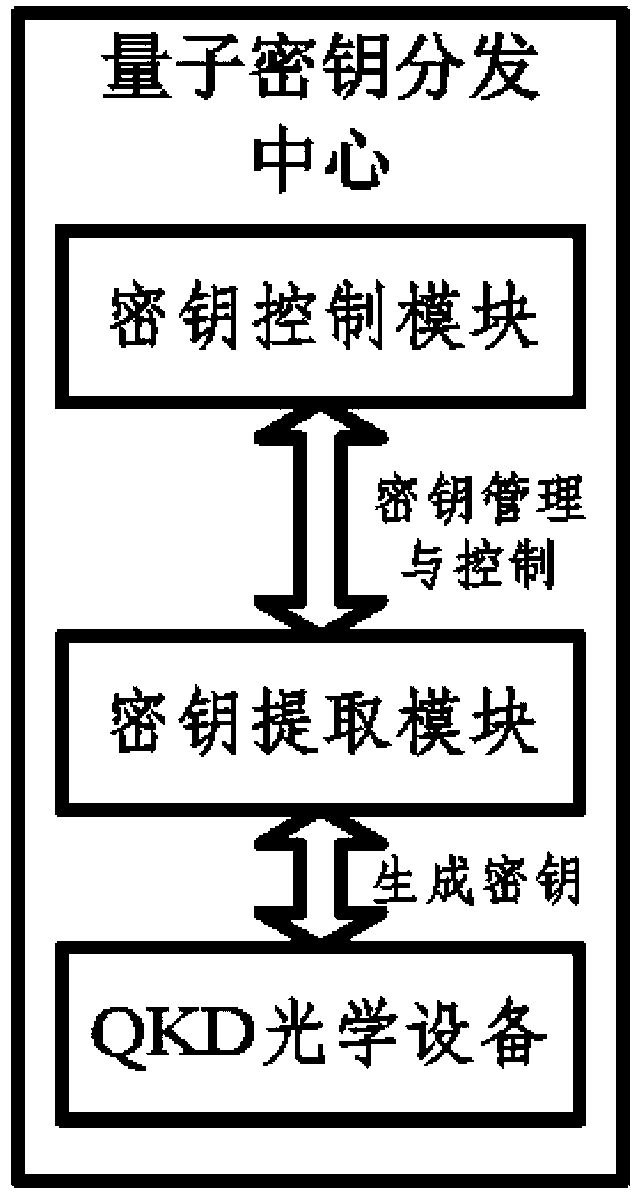
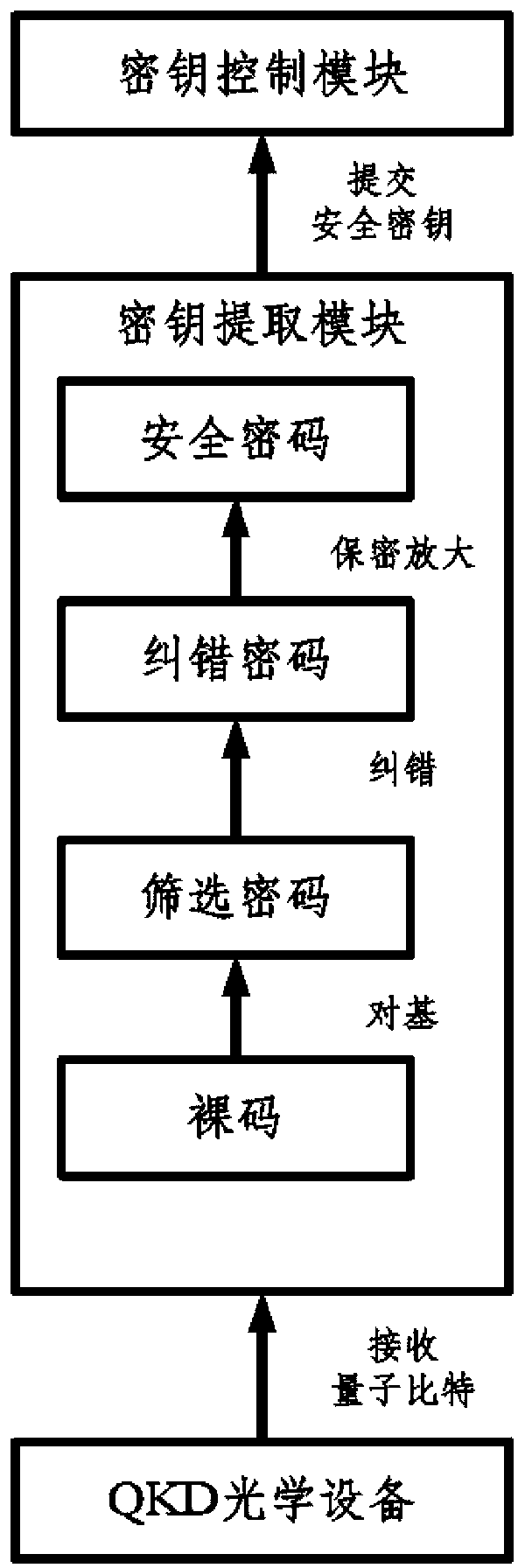
The invention relates to a transformer substation quantum communication model, a quantum secret key distribution center based on the model and a model achieving method. The communication model is a quantum secret key distribution system and comprises a quantum secret key distribution (QKD) optical device, a secret key obtaining module and a secret key control module. The secret key control module, the secret key obtaining module and the QKD optical device are connected in sequence. The quantum secret key distribution center comprises two levels. A primary quantum secret key distribution center (QKDC) is configured in a control center, and a second QKDC is configured at the controller end of a transformer substation. By defining a password suite compatible with secret key distribution protocol and designing a secret key distribution method, the safety and the efficiency of secret key distribution are improved, safe transmission of data is strengthened, and stability and safety of a power system network in operation are guaranteed.
Owner:CHINA ELECTRIC POWER RES INST +2
Token-based encryption key secure conveyance
ActiveUS7971062B1Key distribution for secure communicationDigital data processing detailsEncryptionControl logic
Owner:ORACLE INT CORP
Quantum key distribution system and method based on quantum true random numbers
InactiveCN106209363ARemove true random number barriersSolve puzzles without the use of true random numbersKey distribution for secure communicationComputer moduleKey distribution
The invention discloses a quantum key distribution system based on quantum true random numbers. A quantum state measurement module is used for measuring quantum states of quantum light sources received from quantum channels by employing random numbers generated by a receiving end and the frequency same to that of a sending end quantum light source; a receiving end master control module is also used for numbering each time of measurement of the quantum state measurement module; a postprocessing module is used for carrying out basic information comparison on measurement results through classical channels according to a BB84 protocol; and the postprocessing module also is used for partially disclosing a key after the basic information comparison, estimates a bit error rate of this time of communication and carries out correction and secret keeping amplification processing on the surplus key, thereby enabling a transmitting end master control module and the receiving end master control module to generate and output the same safety key. The invention also discloses a quantum key distribution method based on the quantum true random numbers. According to the system, the difficult problem that the true random numbers are not employed in an existing high-speed quantum key distribution system is solved, and the true random number barrier of the quantum key distribution system with the higher speed in the future is removed.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
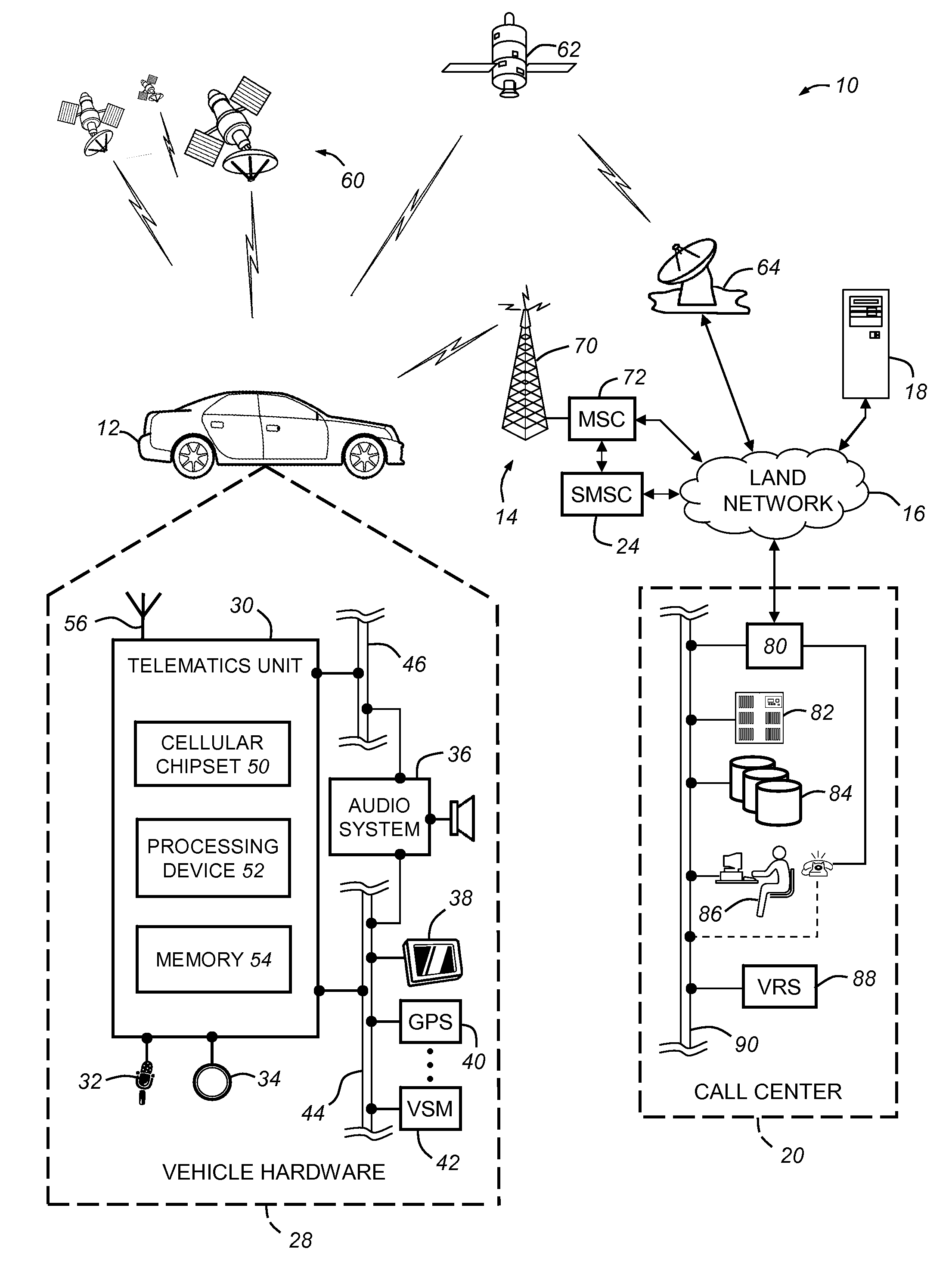
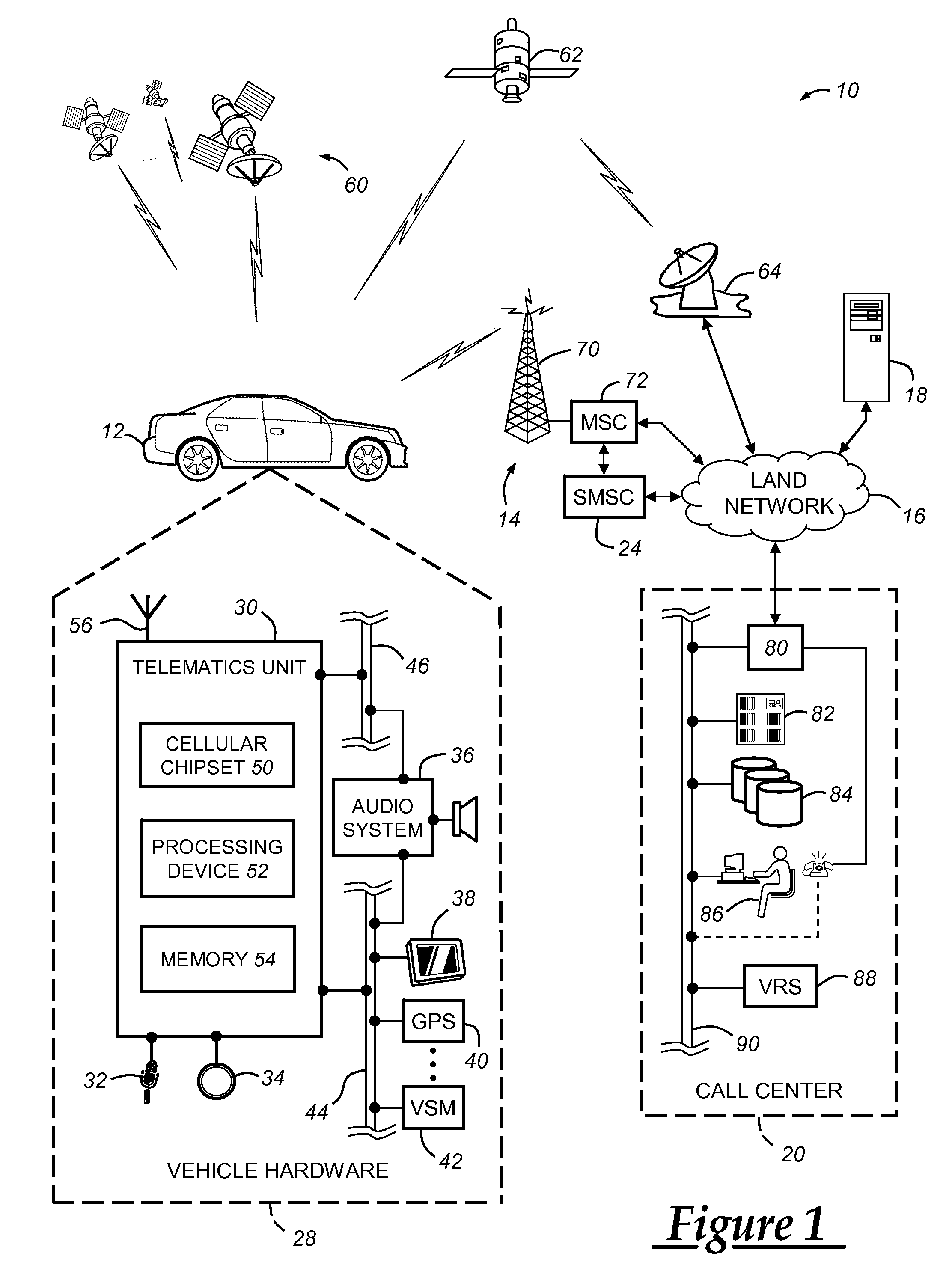
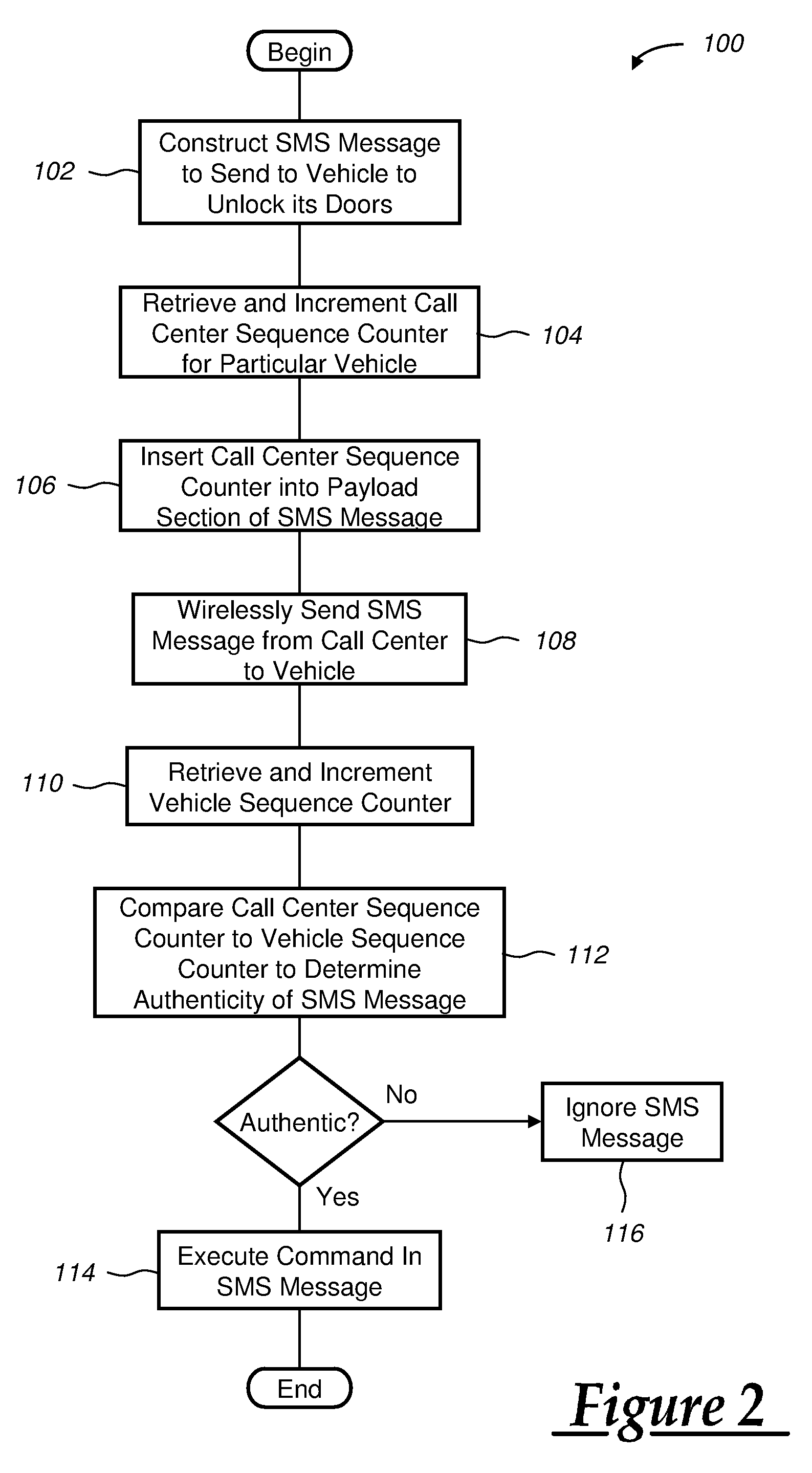
Preventing replay-type attacks on a vehicle communications system
ActiveUS20090170539A1Avoid attackKey distribution for secure communicationSubstation equipmentThird partyCommunications system
Owner:GM GLOBAL TECH OPERATIONS LLC
Key-updating method, encryption processing method, key-insulated cryptosystem and terminal device
InactiveUS20070230705A1Without deteriorating securityKey distribution for secure communicationUnauthorized memory use protectionCryptosystemComputer hardware
Owner:NTT DOCOMO INC
Secret sharing method and system
ActiveUS20140173270A1Difficult to knowKey distribution for secure communicationComputer securityThird party
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Off-line Internet control device, system and method
InactiveCN107248918AKey distribution for secure communicationUser identity/authority verificationSingle vehicleControl system
Owner:徐华静
Reusable public key certificate scheme based on public key infrastructure
InactiveCN106059747AImprove management efficiencyReduce in quantityKey distribution for secure communicationUser identity/authority verificationRelevant informationPassword
Owner:成都蓝海贝信息技术有限公司
Verification method combining static password and dynamic password and terminal equipment
InactiveCN105871546AEasy to rememberDon't worry about stealingKey distribution for secure communicationMultiple keys/algorithms usageValidation methodsPassword
Owner:张雪莱
Method for securing access by software modules
InactiveUS20190245857A1Key distribution for secure communicationPublic key for secure communicationSubject matterSoftware modules
Owner:UNBOUND TECH LTD
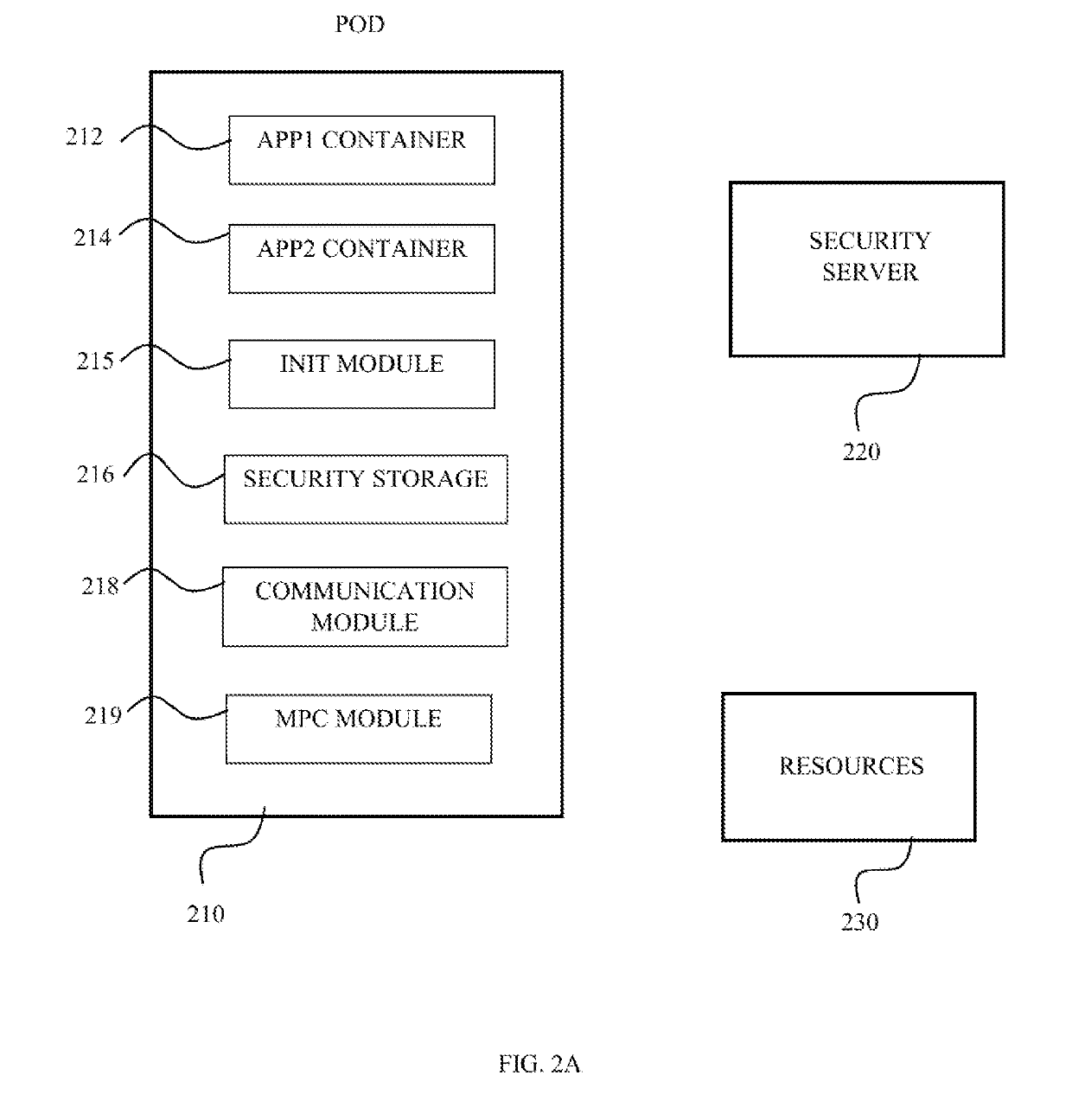
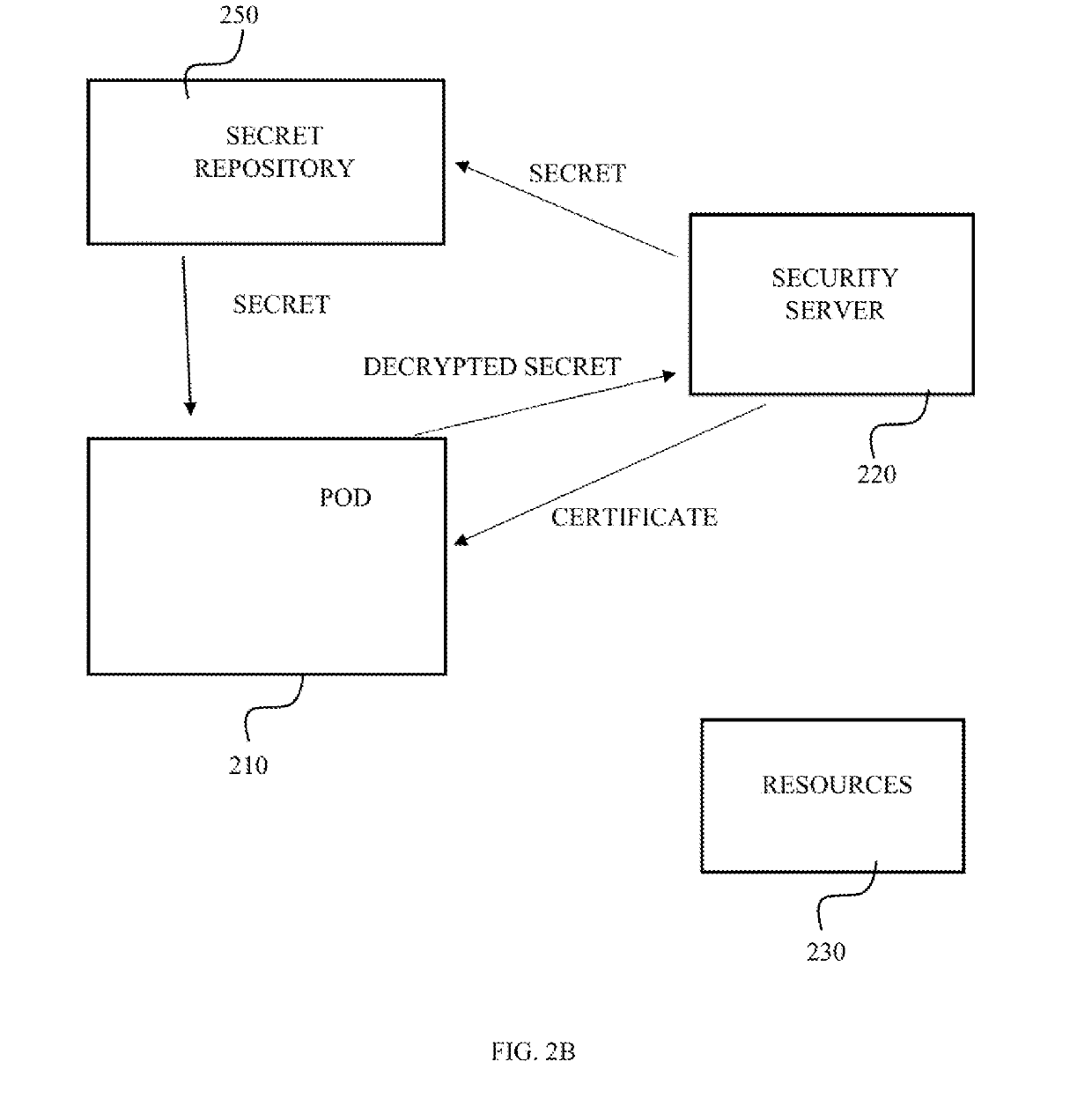
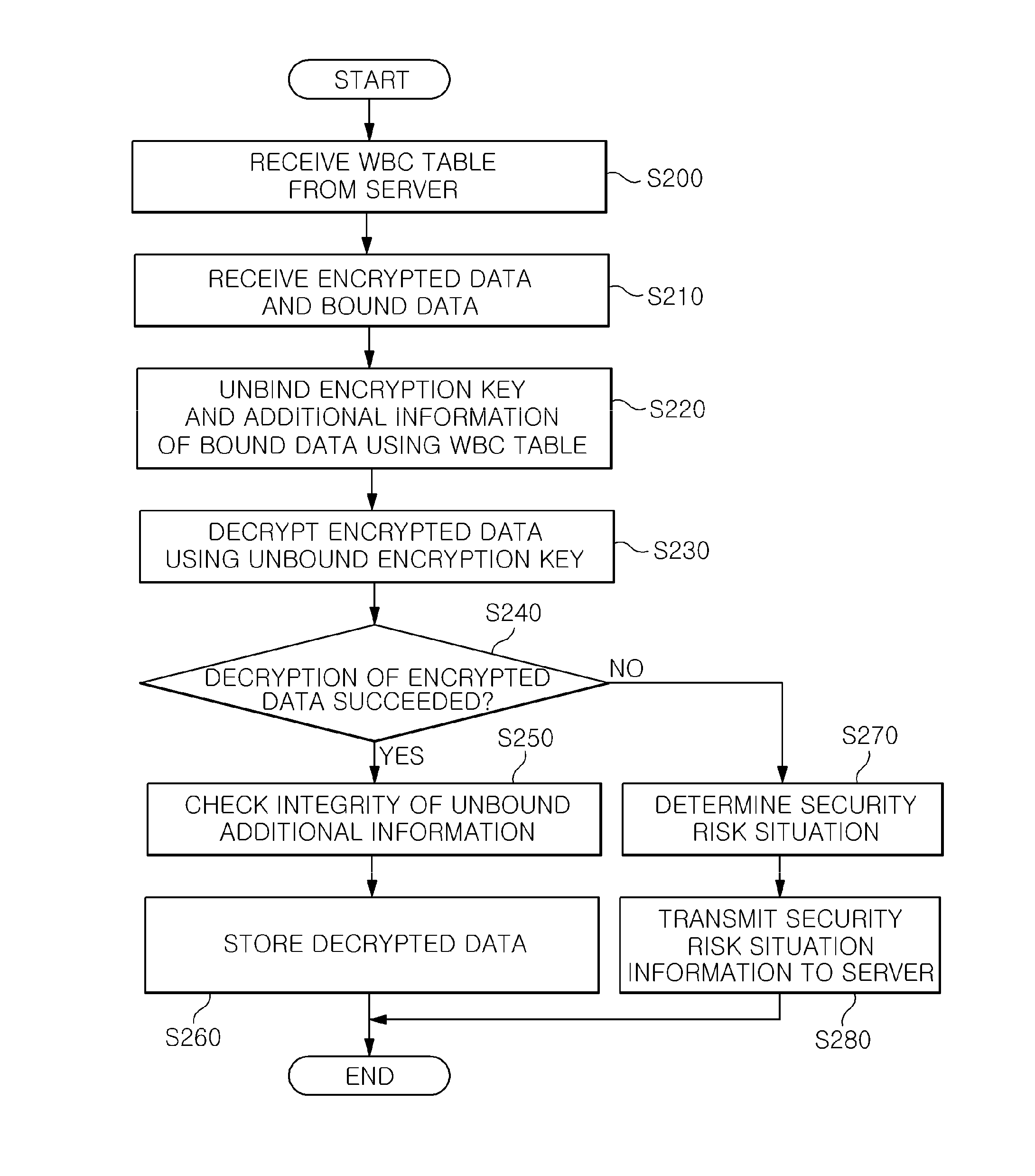
Content protection apparatus and method using binding of additional information to encryption key
InactiveUS20120099726A1Deciphering becomes impossibleKey distribution for secure communicationRandom number generatorsManagement unitProcessing element
Owner:ELECTRONICS & TELECOMM RES INST
Verification method for providing information verification for enterprise information server
ActiveCN106603225APrevent tamperingImprove anti-counterfeiting performanceKey distribution for secure communicationPublic key for secure communicationDomain nameValidation methods
The invention discloses a verification method for providing information verification for an enterprise information server. The verification method comprises the following steps: S1, spontaneously generating an asymmetrical key by an enterprise, and specifying a key name; S2, storing a private key in the enterprise, and storing a public key in a resource record of a domain name; S3, capturing an article event by the enterprise information server, computing an abstract of event information, and using a private key signature; S4, submitting the event information, a signature value, and the key name of the article event to a directory server (DS); S5, acquiring, by a client, a directory record of the article event from the directory server (DS), and querying the key name through a DNS (Domain Name Server) so as to obtain the public key; and S6, decrypting the signature value of the directory record by using the public key to obtain an original abstract value of the event information, accessing corresponding event information, computing an abstract value of the event information, determining whether the original abstract value and the computed abstract value are same or not through comparison, and if the original abstract value and the computed abstract value are same, passing the information verification. The verification method disclosed by the invention ensures that articles cannot be abused under an internet-of-things tag, and circulation information of the articles cannot be tampered.
Owner:JMIT CO LTD
Dynamic generation method for access key of automobile electronic information card
InactiveCN102833072AAchieving dynamismImprove read and write speedKey distribution for secure communicationUser identity/authority verificationData centerStructure of Management Information
Owner:天津广行科技有限公司
Method for aggregating data in a network
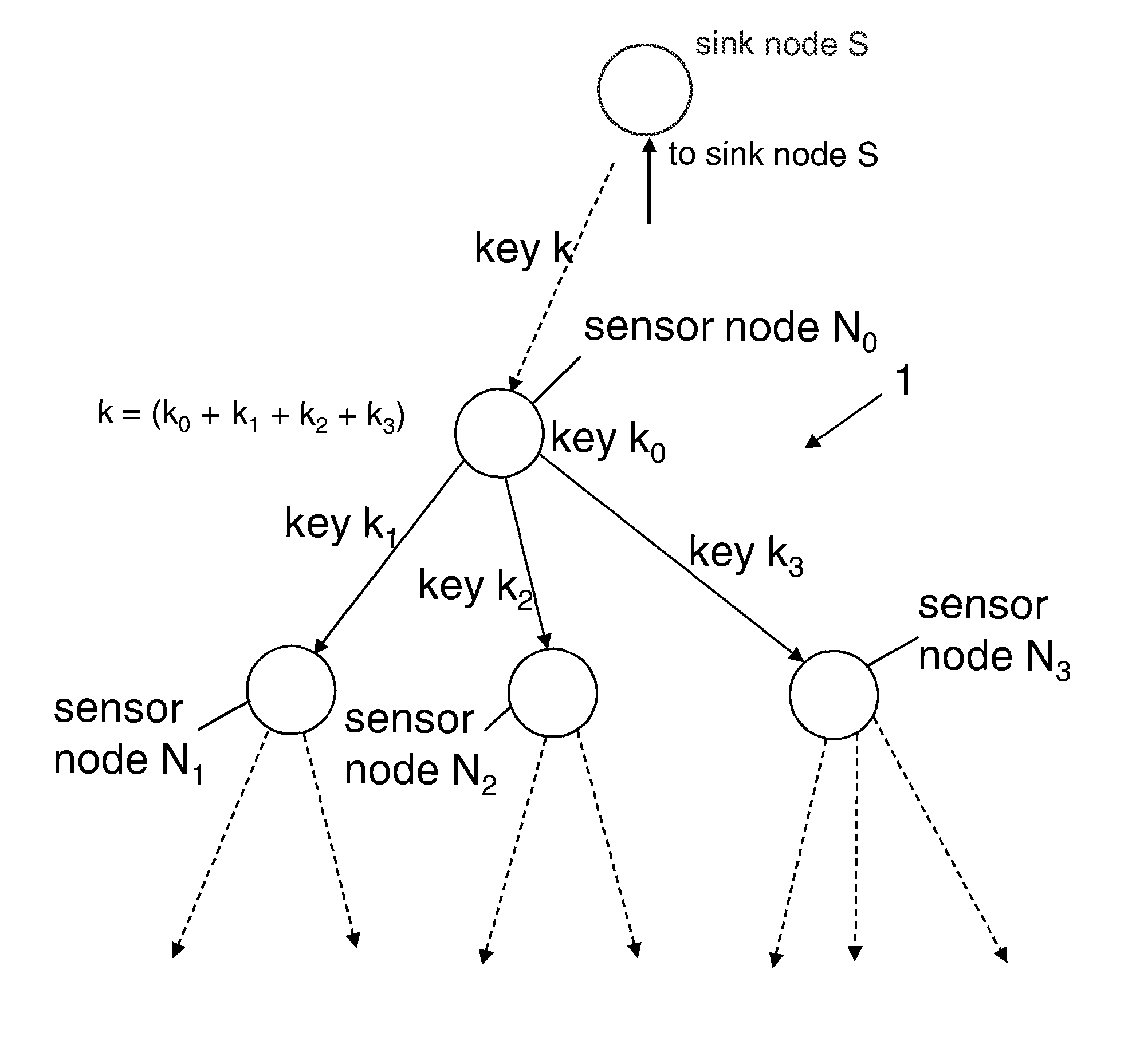
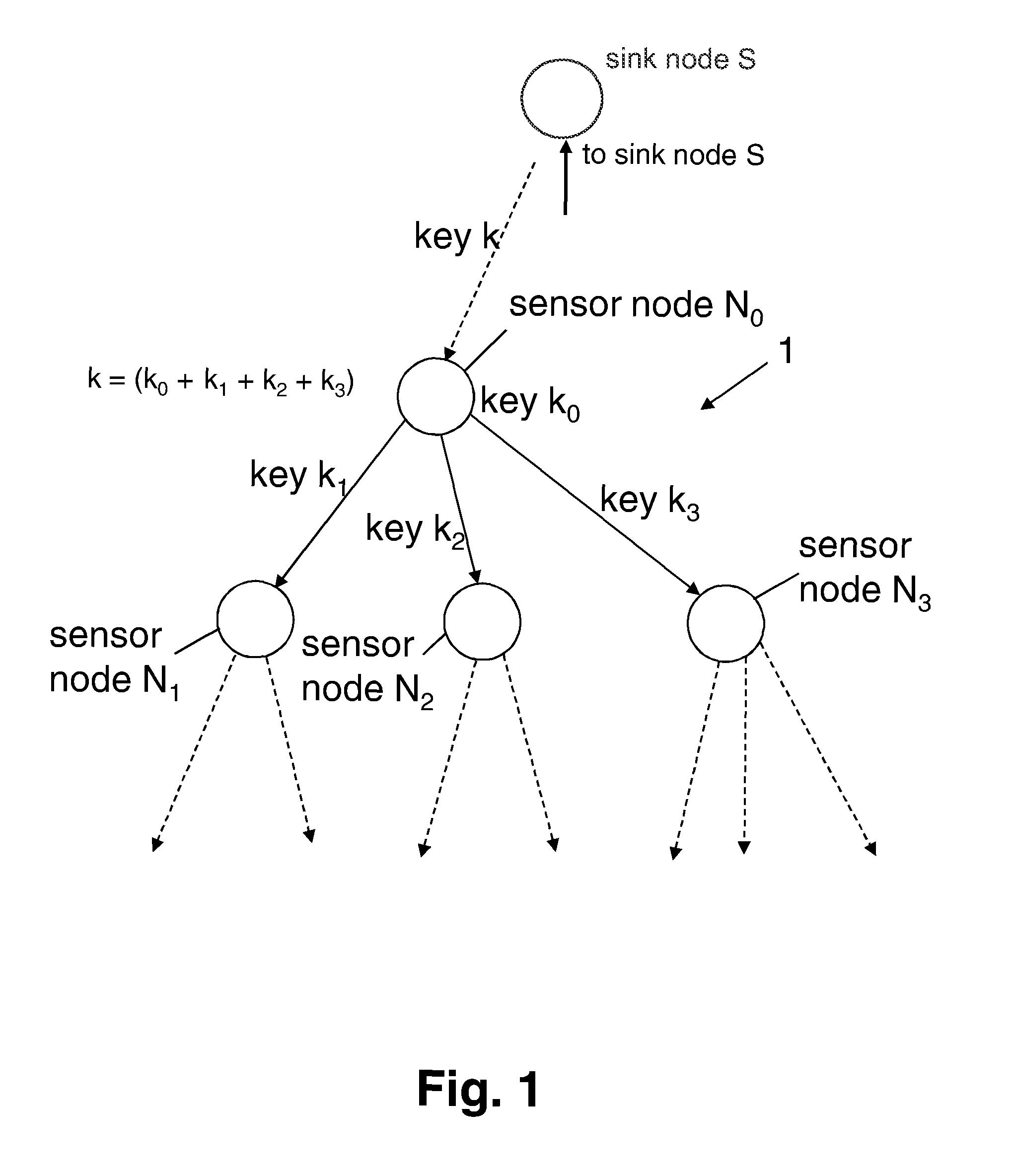
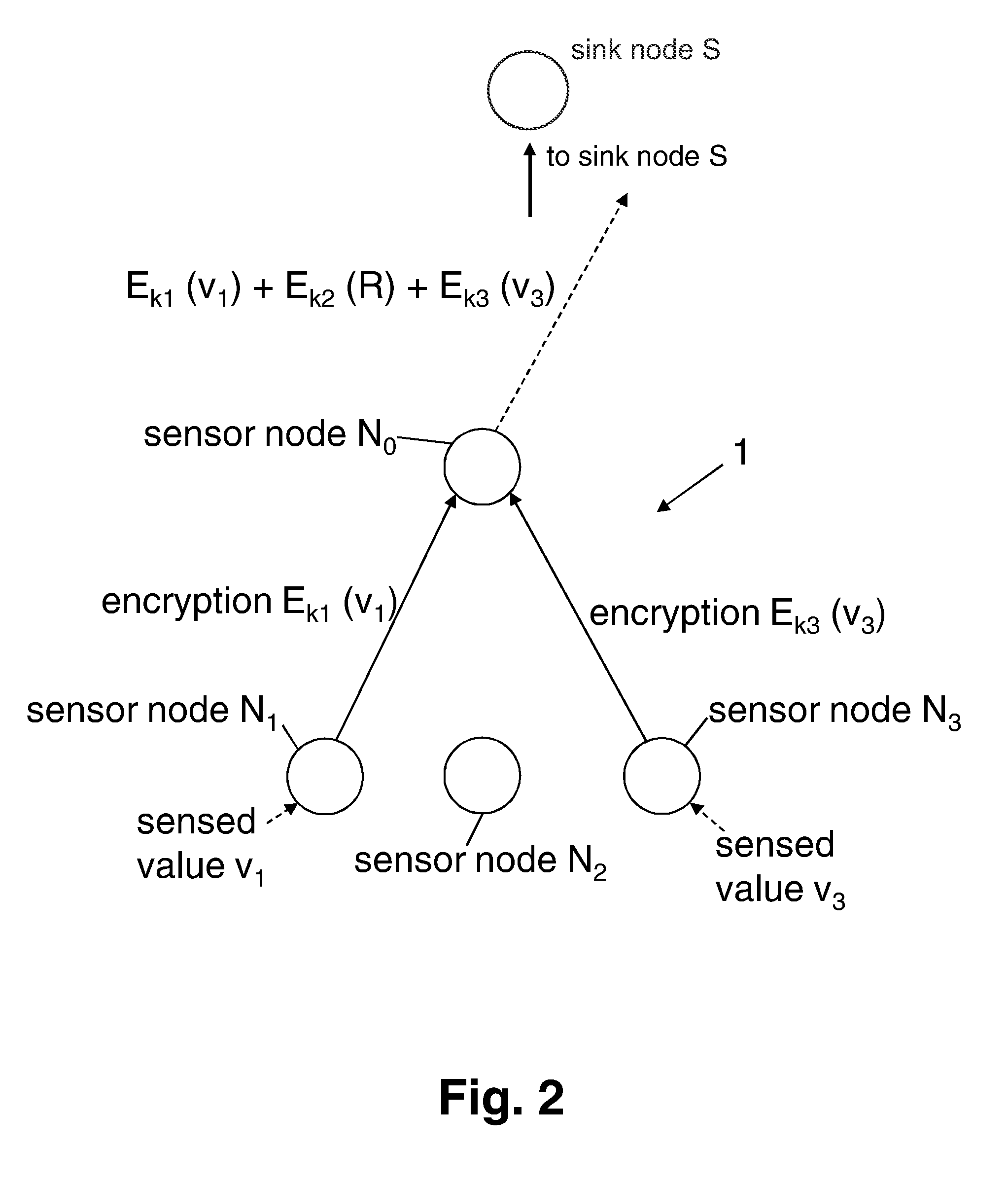
ActiveUS8295491B2Improve securityEasy to implementKey distribution for secure communicationSecret communicationWireless sensor networkingSensor node
Owner:NEC CORP
Data processing method, terminal, communication device and data processing system
InactiveCN106685948AAddress privacy threatsEnsure safetyKey distribution for secure communicationData processing systemTransfer procedure
Owner:SHENZHEN GIONEE COMM EQUIP
Authentication system and authentication method based on central node
Owner:ZHEJIANG QUANTUM TECH CO LTD
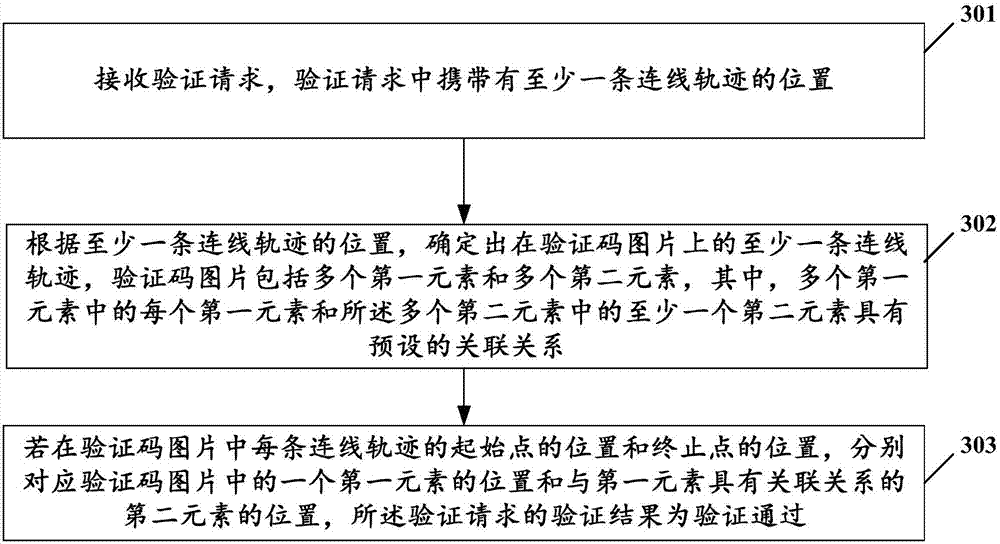
Generation and verification method and device of verification code picture
InactiveCN107483208AKey distribution for secure communicationUser identity/authority verificationValidation methodsParallel computing
Owner:CHINA MOBILE COMM LTD RES INST +1
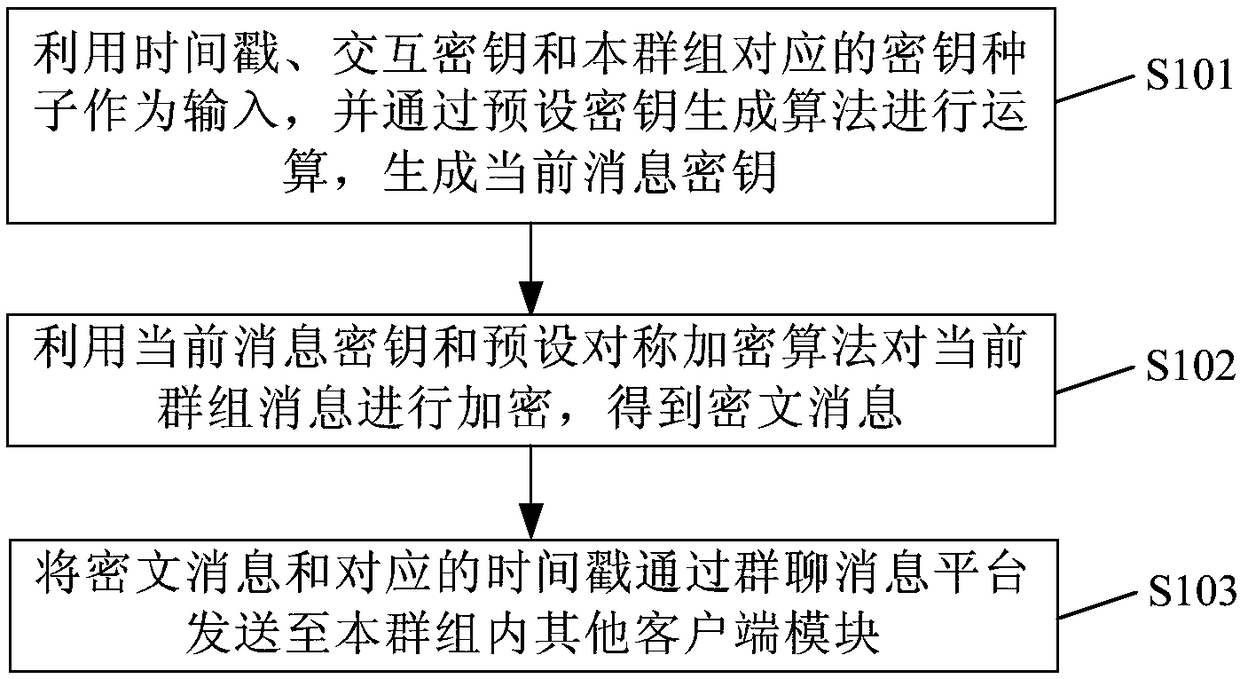
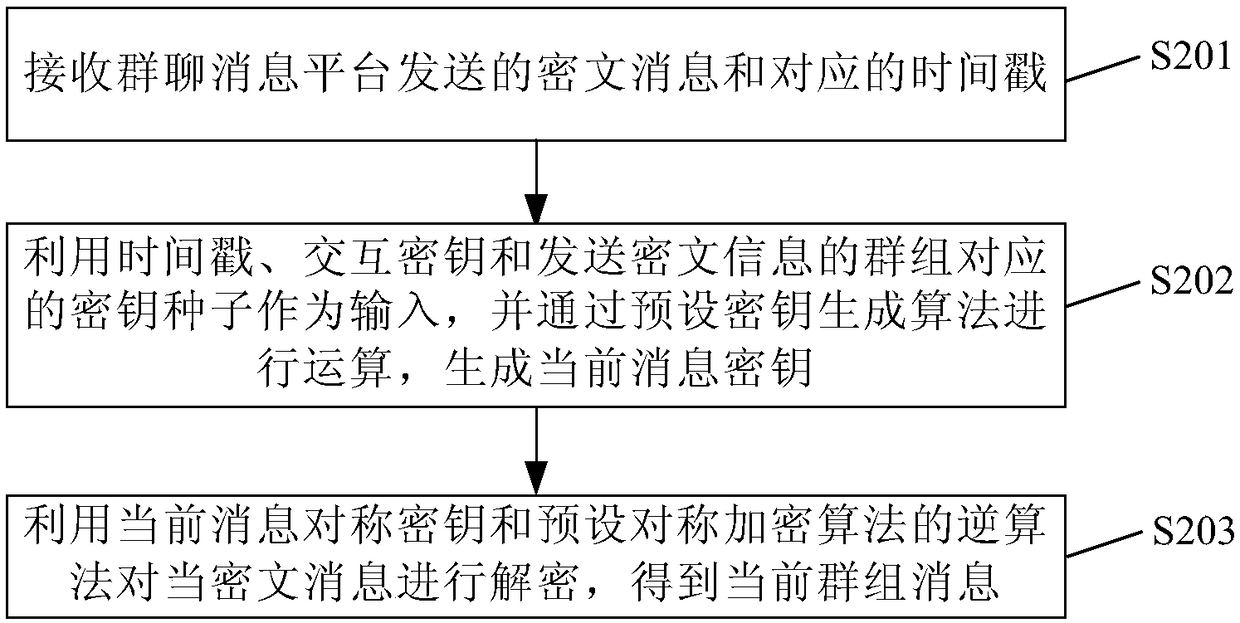
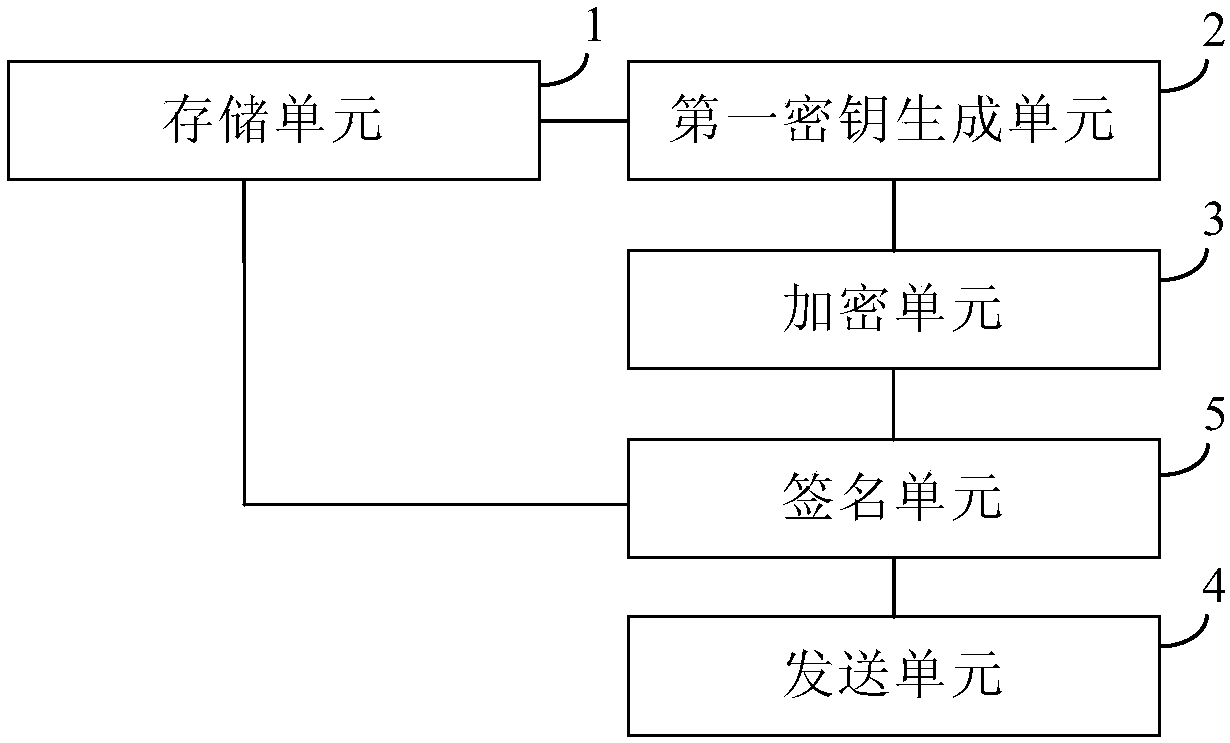
Group message sending method and system, group message receiving method and system and communication terminal
InactiveCN108155987AReduce the risk of breachImprove securityKey distribution for secure communicationSpecial service provision for substationComputer hardwareCiphertext
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
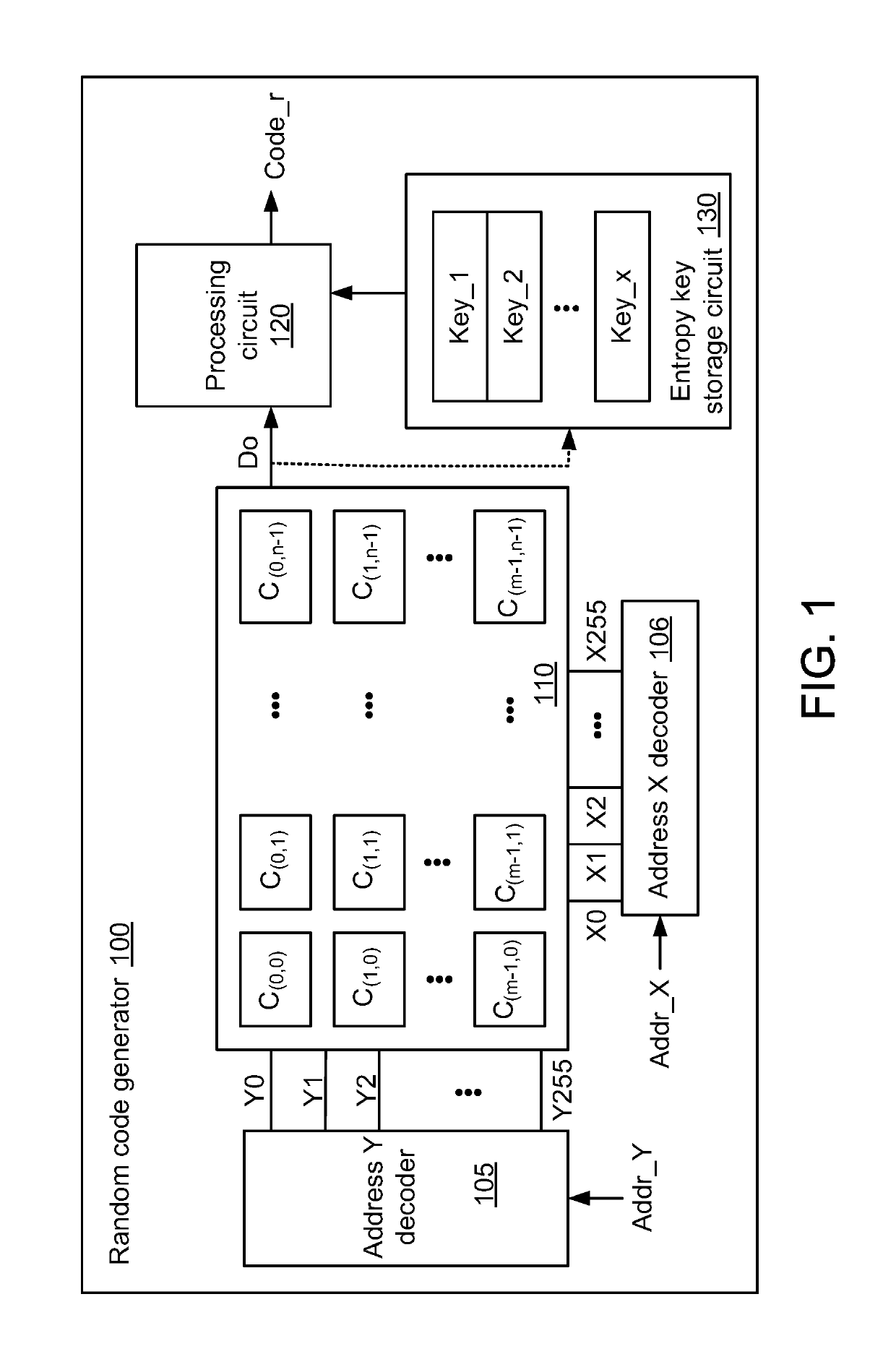
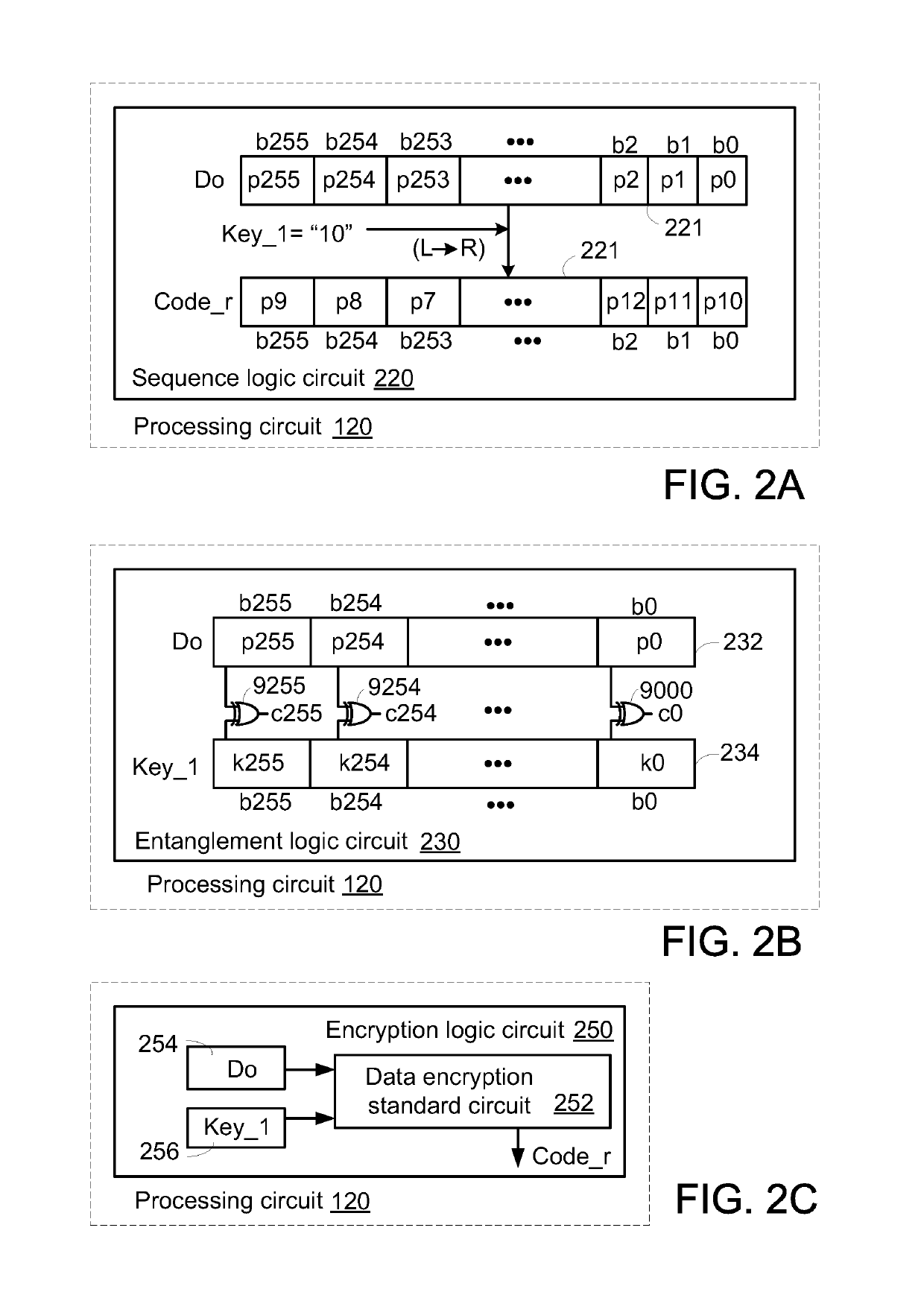
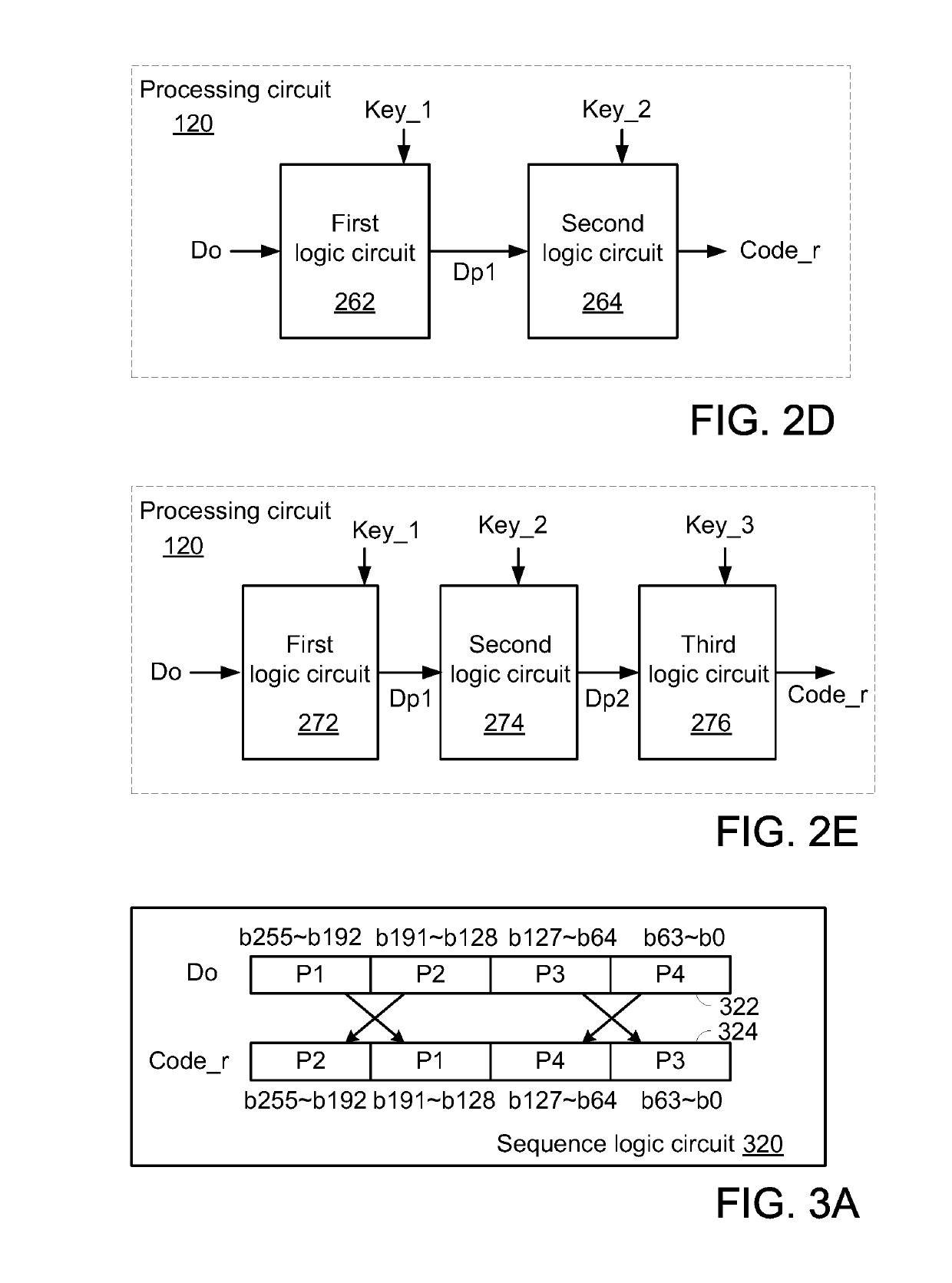
Random code generator
ActiveUS20190215168A1Key distribution for secure communicationDigital data processing detailsKey storageAddress decoder
Owner:EMEMORY TECH INC
Decentralized computing systems and methods for performing actions using stored private data
InactiveUS20220014367A1Key distribution for secure communicationPublic key for secure communicationEngineeringOne-time password
A distributed computing system is used to form a login network to perform an action for a user, using private data. The login network executes the verification using blockchain computing architecture, which is decentralized. The private data is stored on the blockchain in an obfuscated form. In order to compute the private data from the obfuscated form, multiple distributed private key shares are required to generate multiple decryption shares, which are combined to compute a One Time Pad (OTP). In turn, the OTP is used to obtain the private data from the obfuscated form.
Owner:LOGIN ID INC
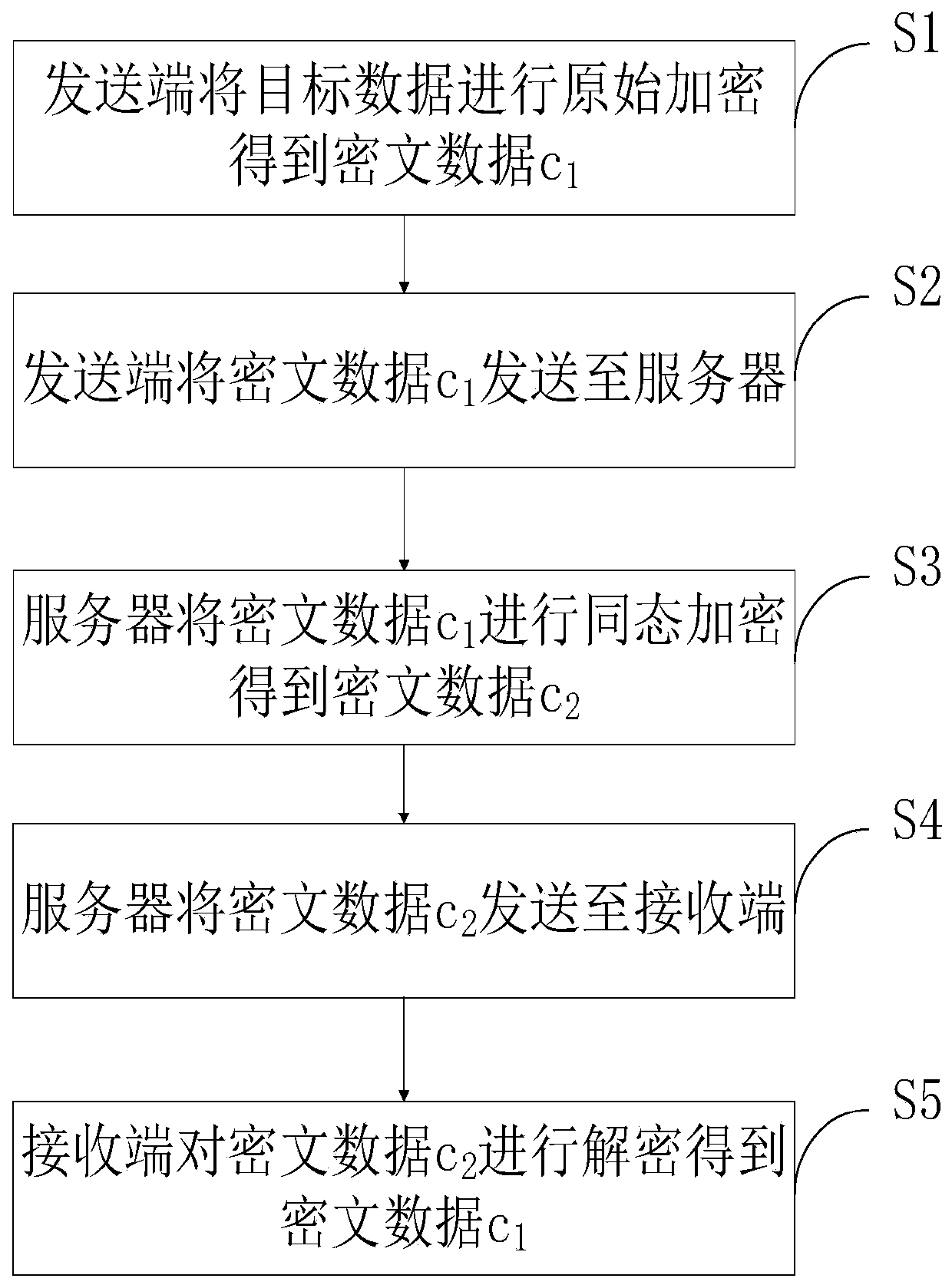
Proxy anonymous communication method based on homomorphic encryption scheme
ActiveCN110891066AHigh reliability and precisionCompactKey distribution for secure communicationCommunication with homomorphic encryptionCiphertextConfidentiality
Owner:CHONGQING JIAOTONG UNIVERSITY
Picture sharing method and system
ActiveCN109525559AEnsure safetyEnsure the efficiency of screen transmissionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareNetwork code
The invention discloses a picture sharing method and system. The picture sharing method comprises the following steps: a master device performs handshake with a slave device when receiving a picture sharing request initiated by the slave device; when the master device performs handshake with the slave device successfully, the master device performs network coding on a picture signal to be shared,outputs a TS bare stream signal to the slave device, and plays the picture to be shared; and the slave device receives and decodes the TS bare stream signal, and synchronously displays the current picture to be shared. Thus, the picture information of the master device can be displayed synchronously on other slave devices without delay and jamming; and a private protocol is used in network transmission, therefore, network security and picture transfer efficiency are ensured.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
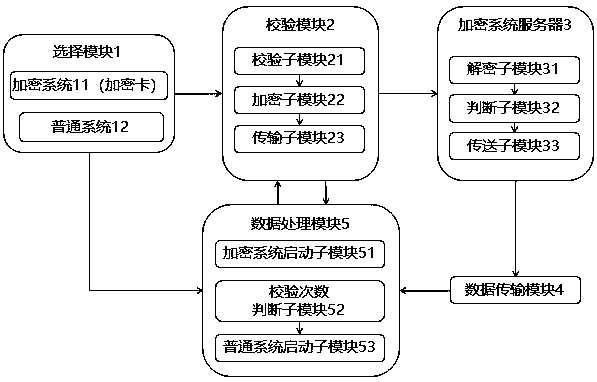
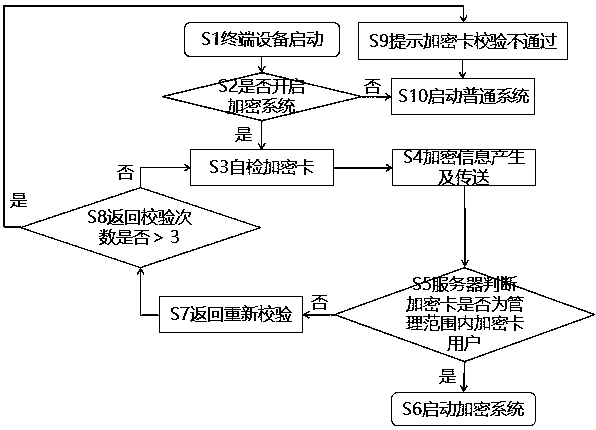
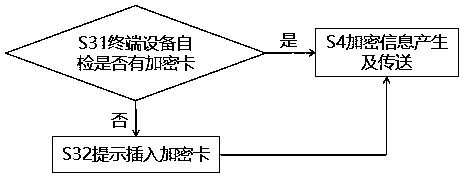
Terminal equipment with encryption system and system starting method of terminal equipment
InactiveCN108449181AImprove securityEasy to crackKey distribution for secure communicationComputer hardwareConfidentiality
Owner:POWER IDEA TECH (SHENZHEN) CO LTD
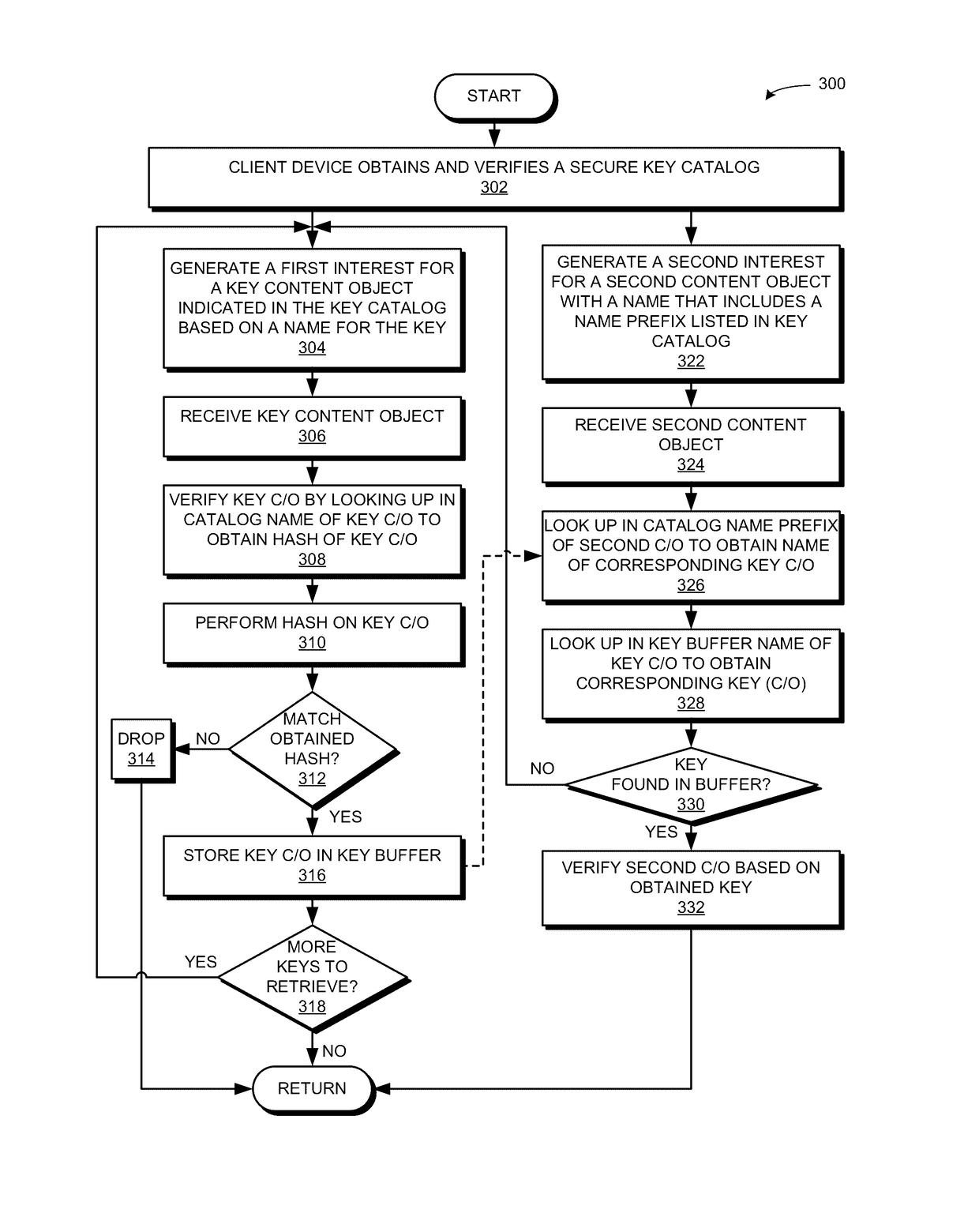
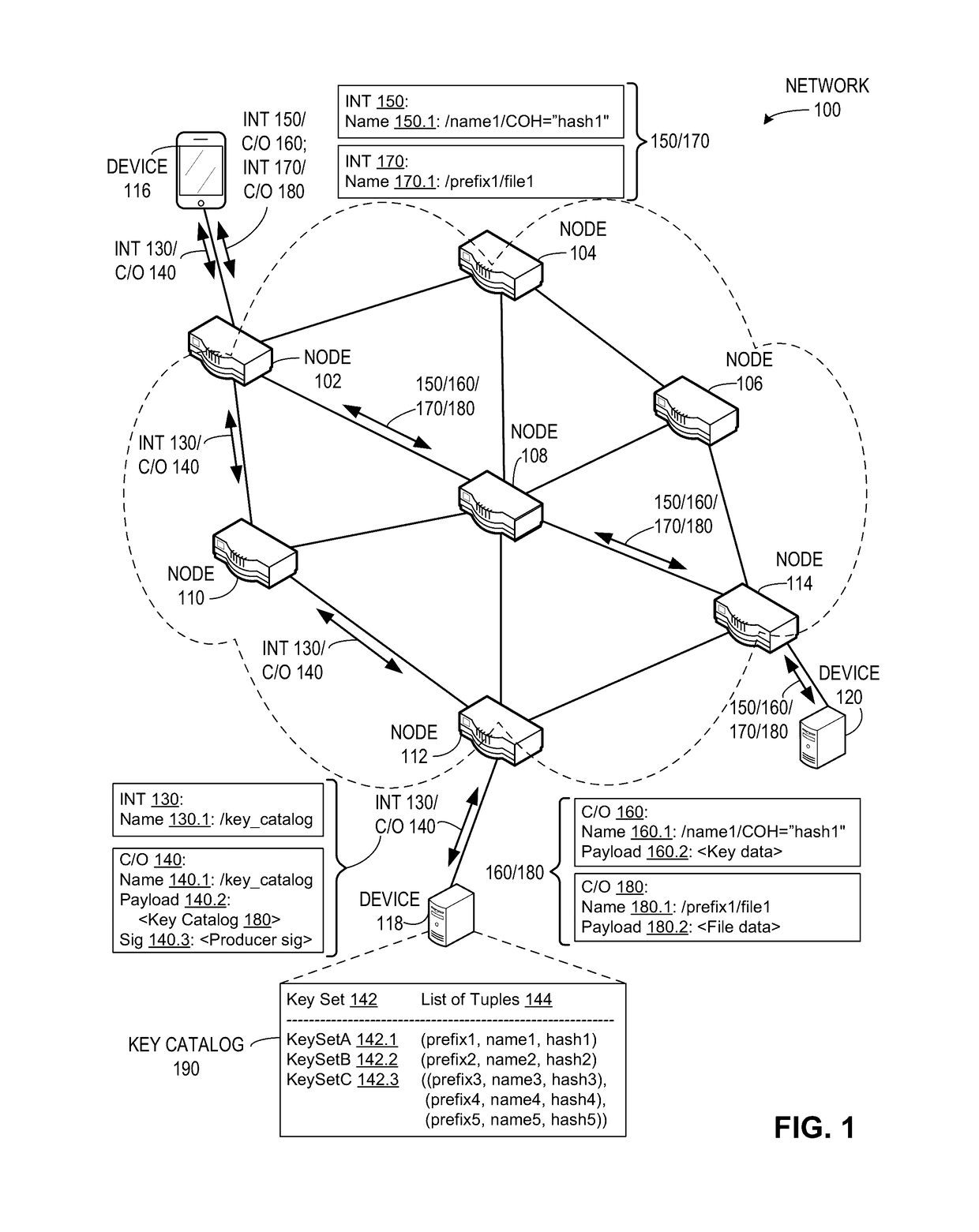
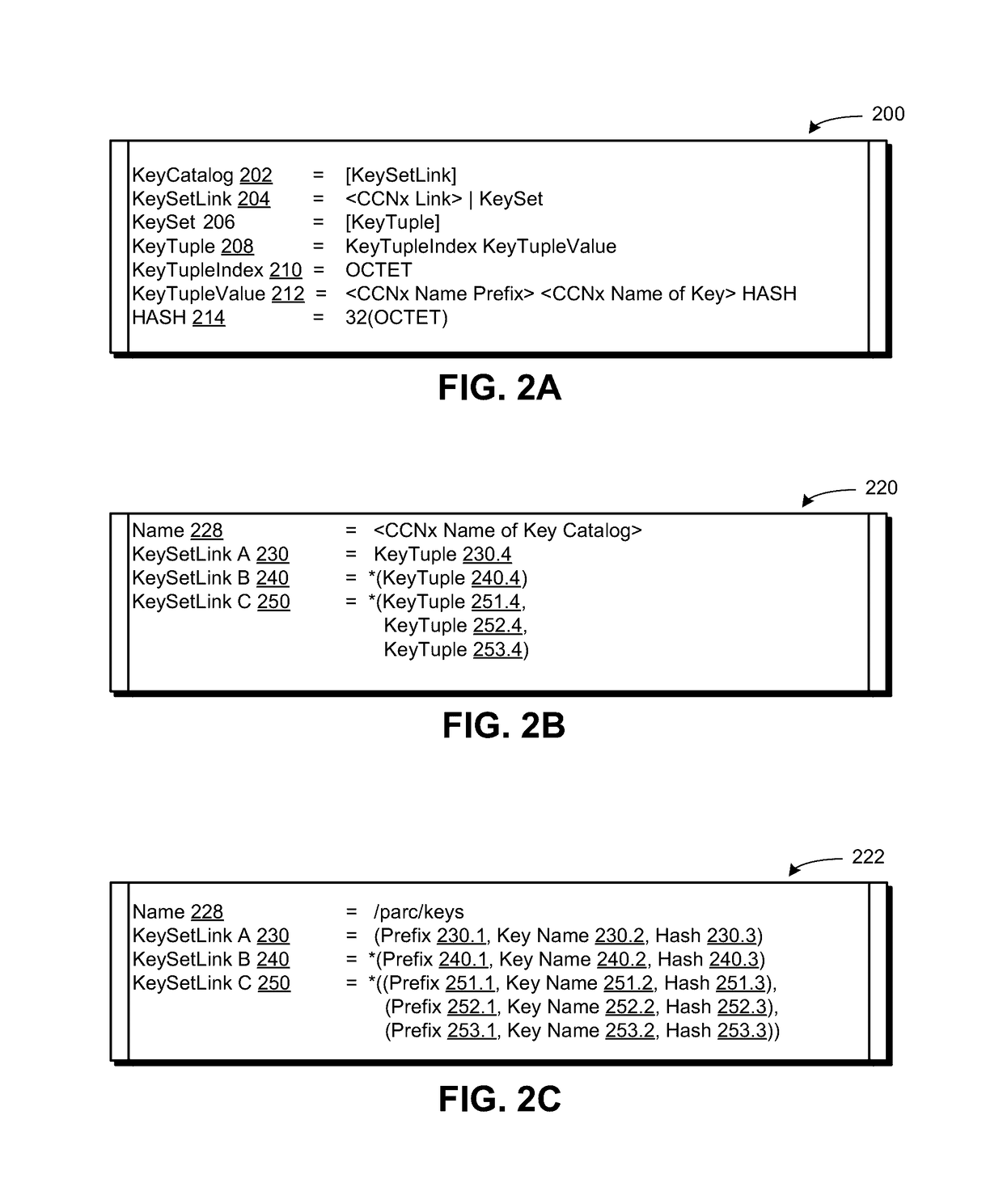
Key catalogs in a content centric network
ActiveUS20170170955A1Facilitates efficient key retrievalKey distribution for secure communicationUser identity/authority verificationComputer securityContent object
Owner:CISCO TECH INC
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap