Method for securing access by software modules
a software module and access security technology, applied in the field of data security, can solve the problems of short lifetime, short lifetime, and limited ability to store a unique identity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
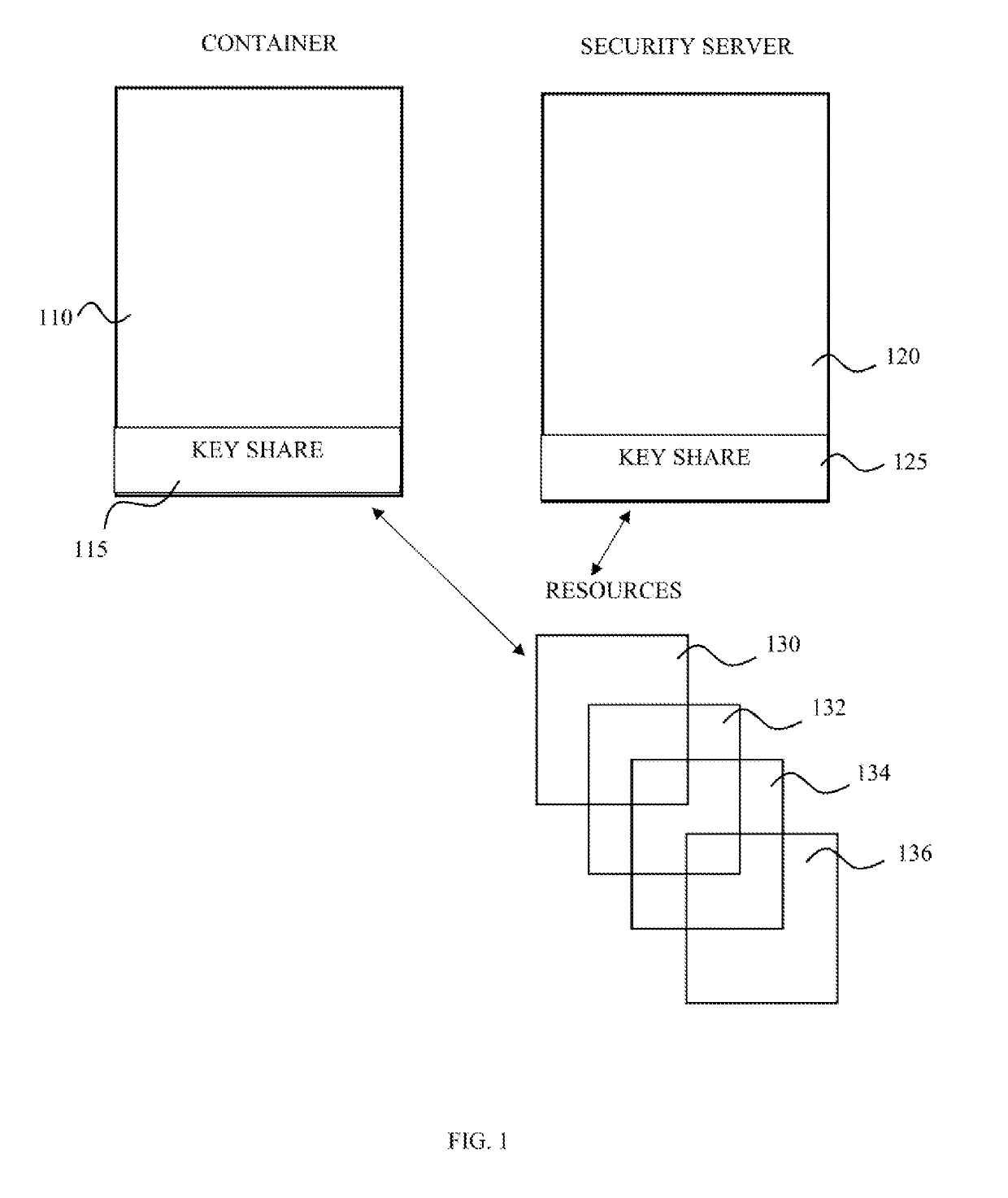
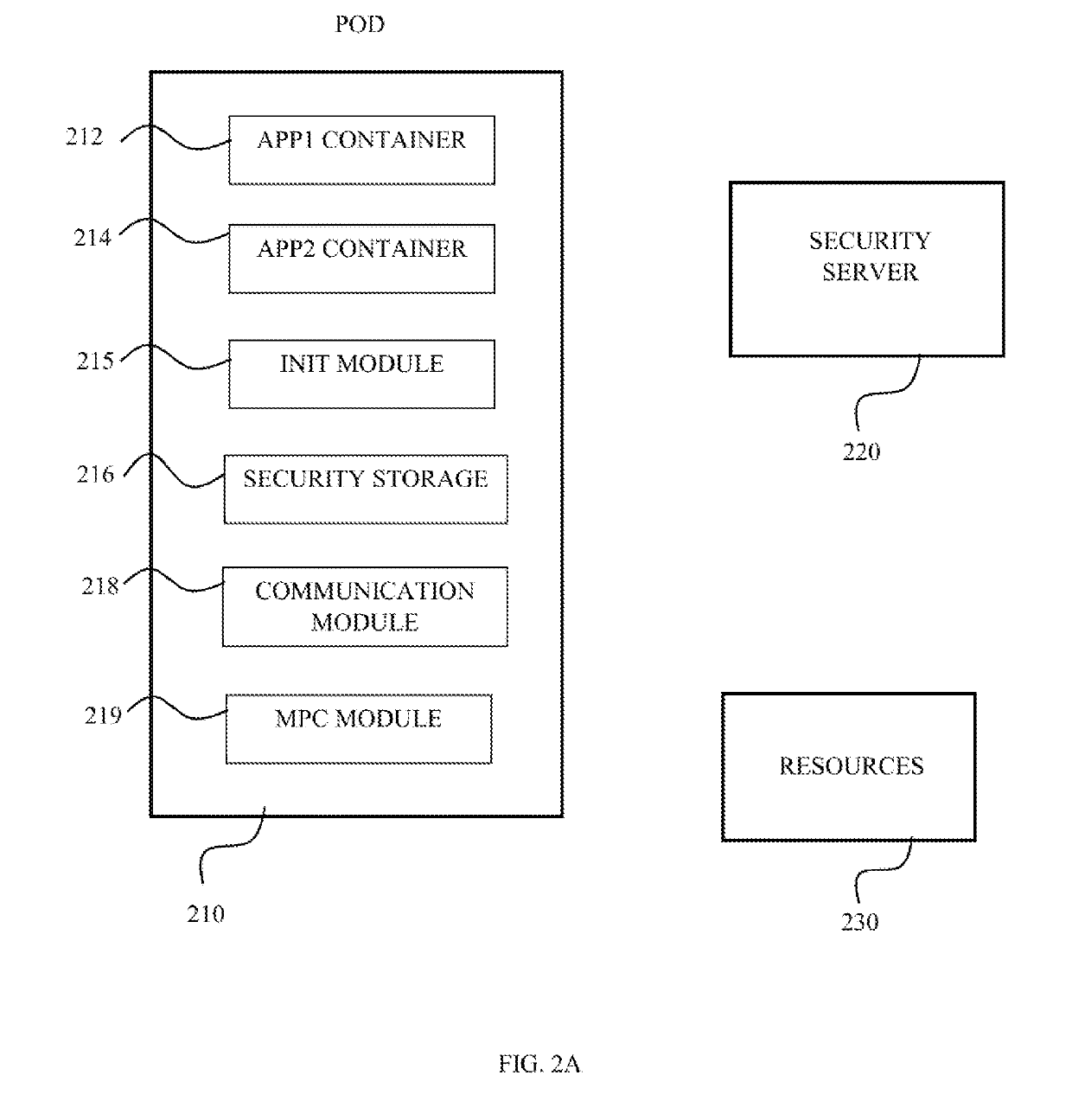
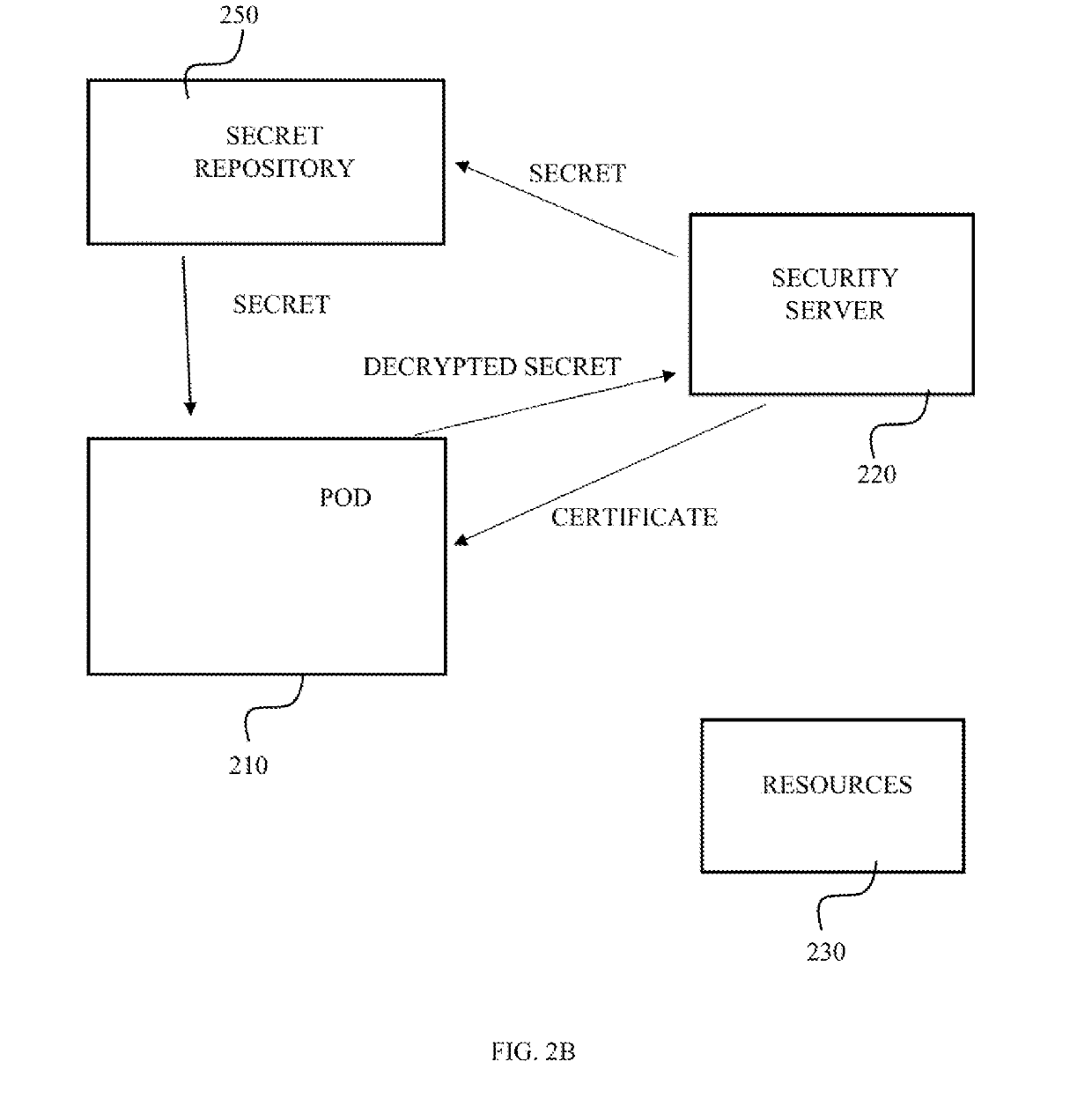
[0020]The present invention discloses a method for providing a cryptographically based identity to a software module having a memory, processing module and communication capabilities. Such software module may reside on a personal device, for example an application operating on a smartphone, tablet, laptop, server and the like. A software module may reside on an online server, for example a virtual machine (VM). For simplicity, and due to the short life cycle of containerized software modules, most of the examples below refer to containerized software modules, also defined below as container for simplicity. The container according to the present invention is defined as an operating system feature in which the kernel allows the existence of multiple isolated user-space instances, wherein such an isolated user-space instance is defined herein as a container. The container technology may be, but unlimited to a Docker, LXC, rkt, BSD jails, LXD, etc. An authentication scheme is required in c
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap