Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5 results about "Key distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In symmetric key cryptography, both parties must possess a secret key which they must exchange prior to using any encryption. Distribution of secret keys has been problematic until recently, because it involved face-to-face meeting, use of a trusted courier, or sending the key through an existing encryption channel. The first two are often impractical and always unsafe, while the third depends on the security of a previous key exchange.
Key distribution and authentication methods, devices and systems
ActiveCN107317789AReduce the burden onSolve the problem that it cannot be applied to smart devices that do not support USIM cardsKey distribution for secure communicationSecurity arrangementSecure communicationWeb authentication
Owner:HUAWEI TECH CO LTD
Quantum key distribution system and method based on quantum true random numbers
InactiveCN106209363ARemove true random number barriersSolve puzzles without the use of true random numbersKey distribution for secure communicationComputer moduleKey distribution
The invention discloses a quantum key distribution system based on quantum true random numbers. A quantum state measurement module is used for measuring quantum states of quantum light sources received from quantum channels by employing random numbers generated by a receiving end and the frequency same to that of a sending end quantum light source; a receiving end master control module is also used for numbering each time of measurement of the quantum state measurement module; a postprocessing module is used for carrying out basic information comparison on measurement results through classical channels according to a BB84 protocol; and the postprocessing module also is used for partially disclosing a key after the basic information comparison, estimates a bit error rate of this time of communication and carries out correction and secret keeping amplification processing on the surplus key, thereby enabling a transmitting end master control module and the receiving end master control module to generate and output the same safety key. The invention also discloses a quantum key distribution method based on the quantum true random numbers. According to the system, the difficult problem that the true random numbers are not employed in an existing high-speed quantum key distribution system is solved, and the true random number barrier of the quantum key distribution system with the higher speed in the future is removed.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
CDMA port-to-port encryption communication system and key distribution method thereof
InactiveCN101635924AImprove securityReduce security risksSecurity arrangementCommunications securityCommunications system
The invention discloses a CDMA port-to-port encryption communication system and a key distribution method thereof, the CDMA port-to-port encryption communication system comprises a CDMA network and a terminal mobile telephone thereof, a public switched telephone network and a terminal fixed-line telephone thereof, a short message service center as well as the following three cipher processing units including a cipher chip of a mobile telephone terminal, a key distribution management center (KDMC) and a Firmware cipher module of a gateway mobile switching center. The key distribution management center is used for key distribution management of the communication system. The key distribution is realized by a layered distribution method, i.e. a first layer is an equipment key which is distributed in the process of initialization; a second layer is a key-encryption key and a short message service key which are distributed in startup of an enciphered mobile telephone; and a third layer is a session key which is distributed every time a session is launched between the enciphered mobile telephones. At the same time, by adopting a bidirectional certification technology for key distribution and combination of a key update and remote destroying method, the safety risk in key exposure is reduced, and the communication safety is improved.
Owner:CETC CYBERSPACE SECURITY TECH CO LTD
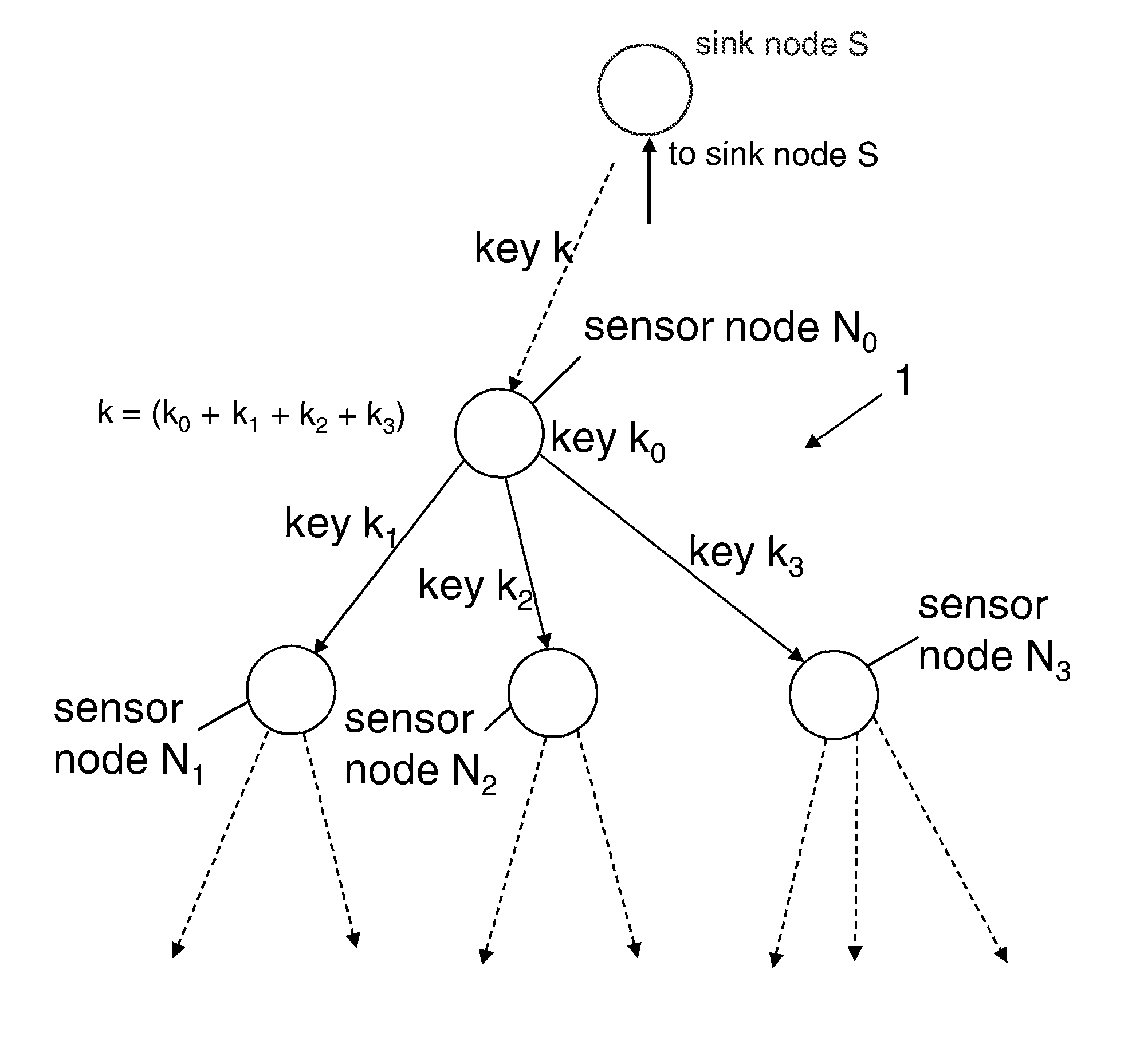
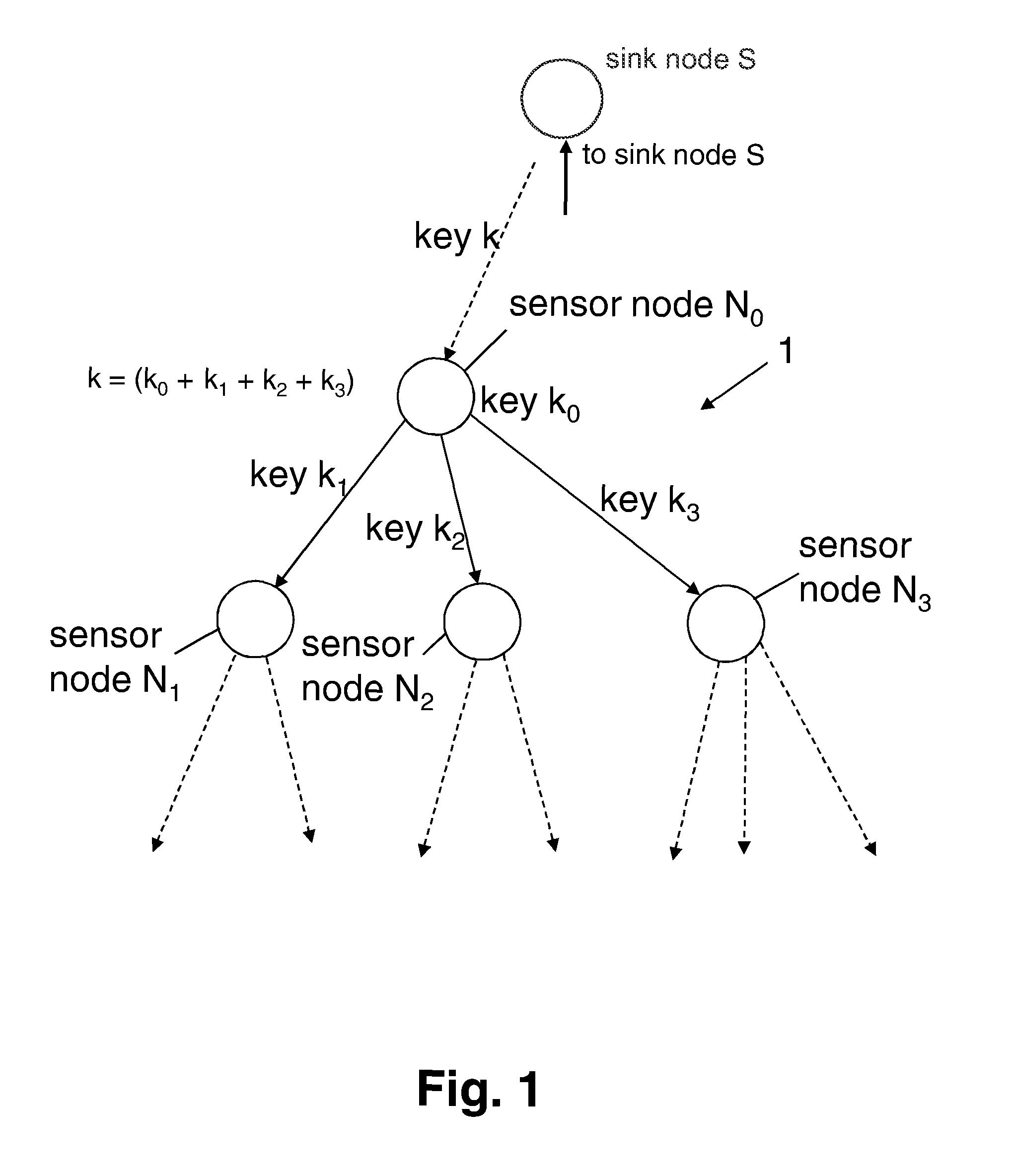
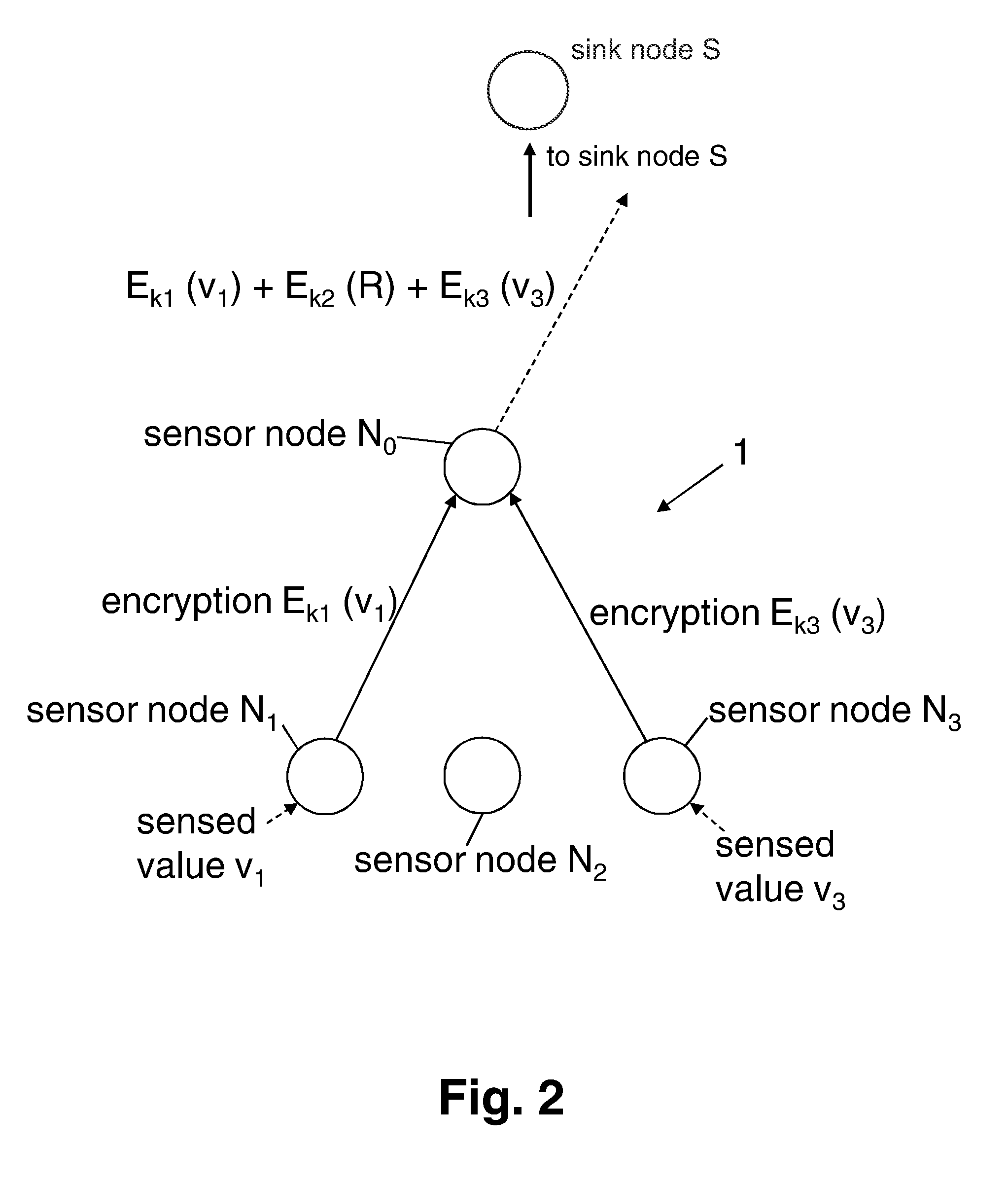
Method for aggregating data in a network
ActiveUS8295491B2Improve securityEasy to implementKey distribution for secure communicationSecret communicationWireless sensor networkingSensor node
Owner:NEC CORP
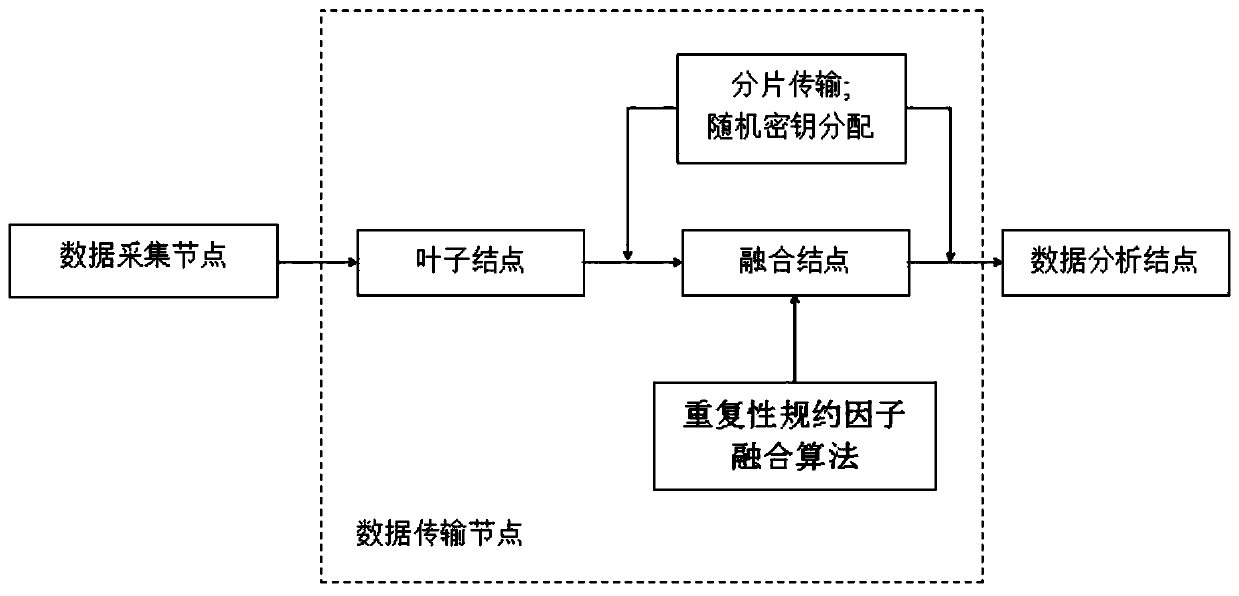
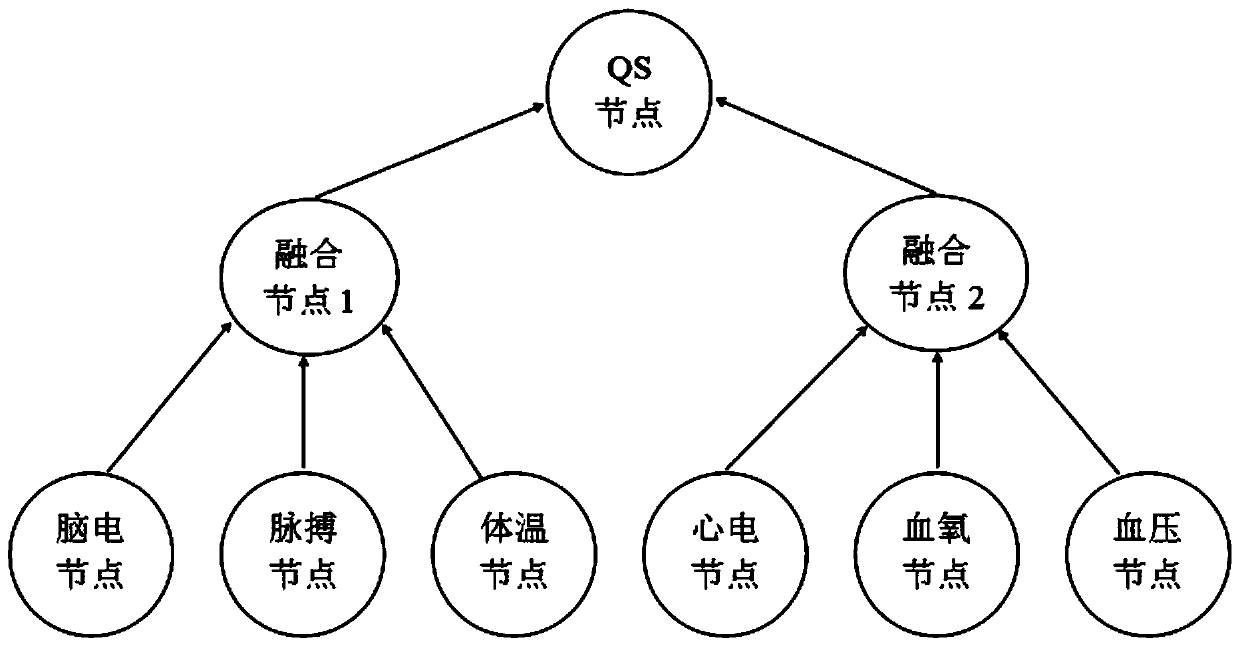
Data acquisition and analysis system based on wireless body area network and low-energy-consumption data fusion privacy protection algorithm
InactiveCN110545282AReduce data trafficImprove privacy protectionKey distribution for secure communicationSecurity arrangementStructure of Management InformationPrivacy protection
Owner:CHINA JILIANG UNIV
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap