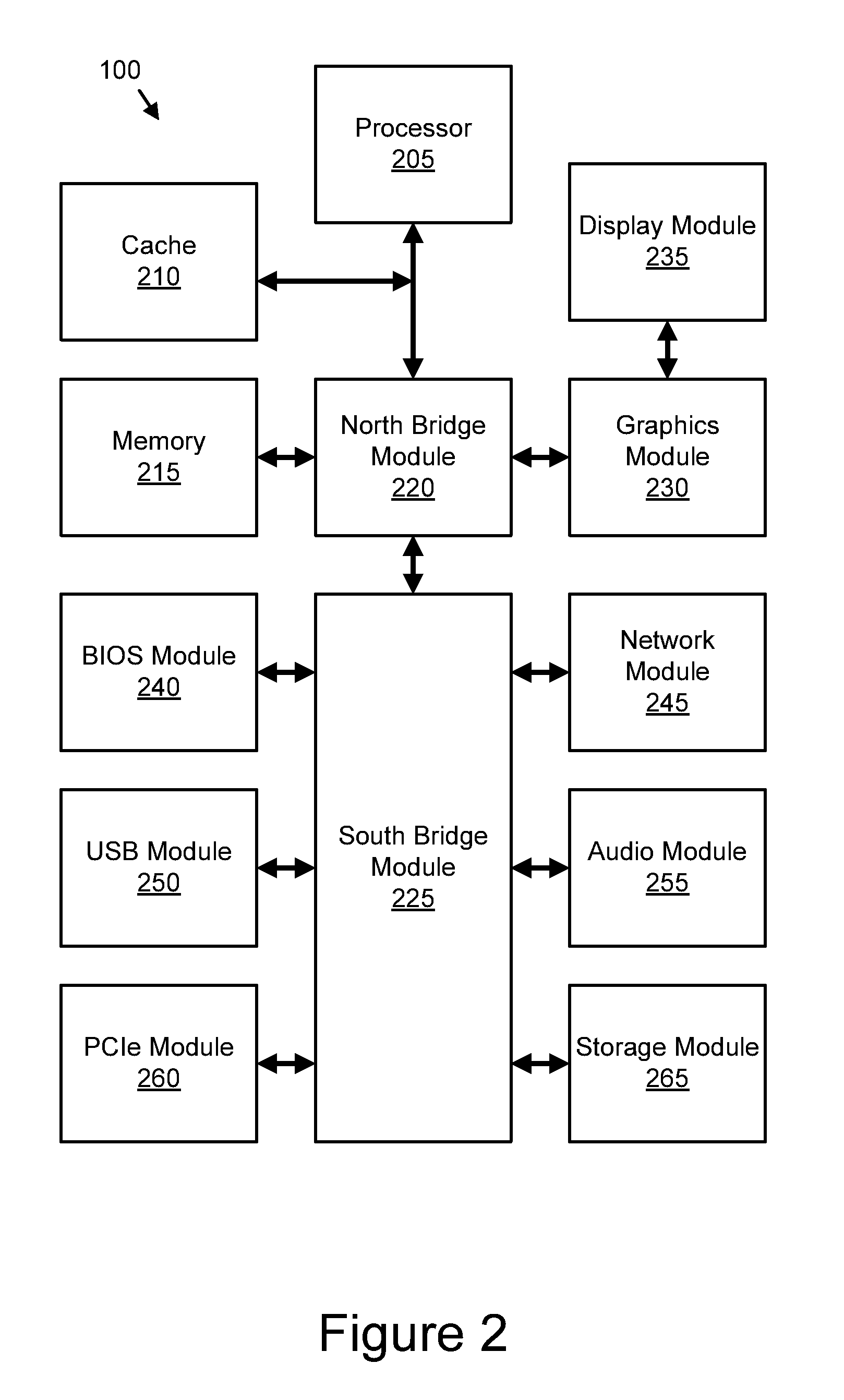
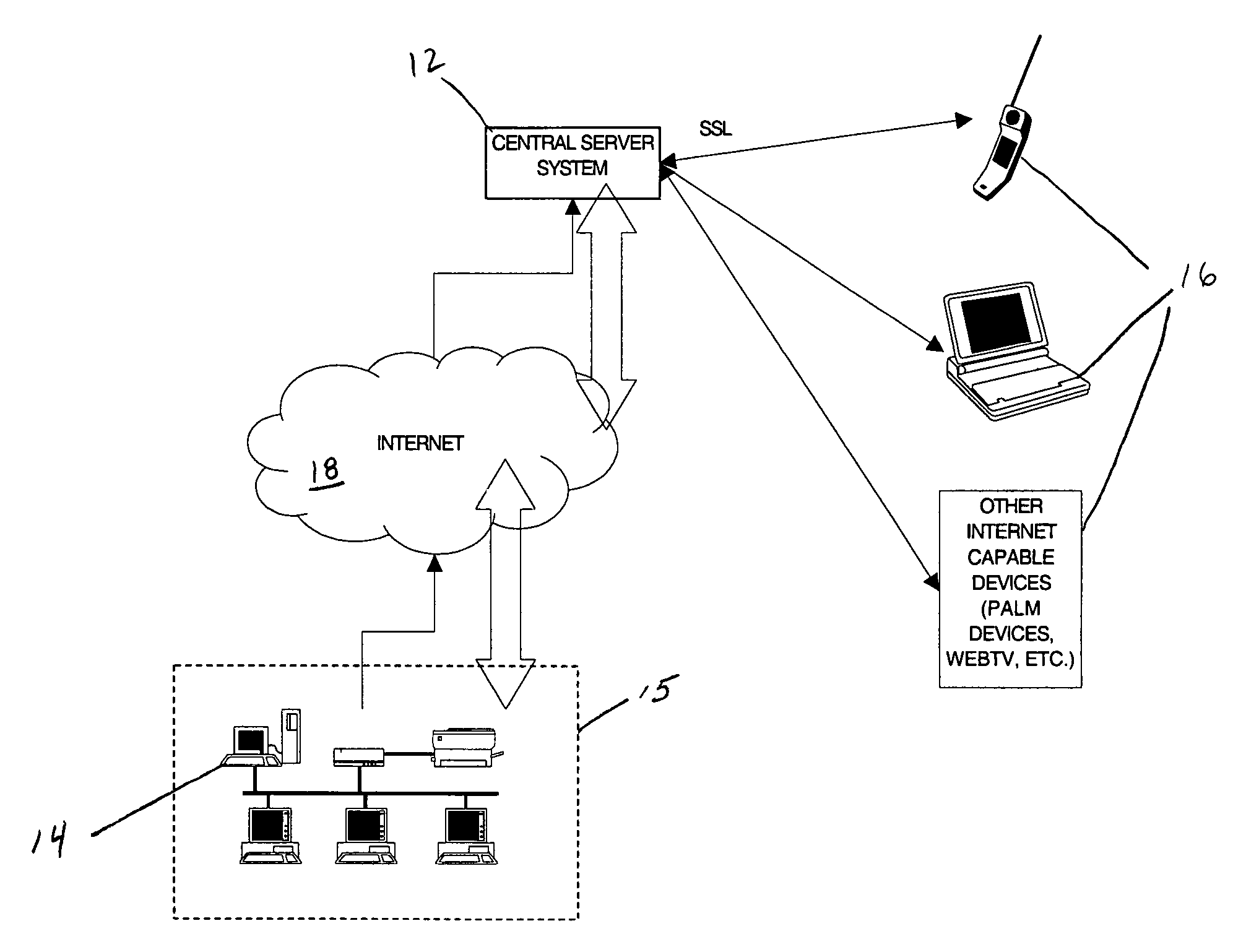
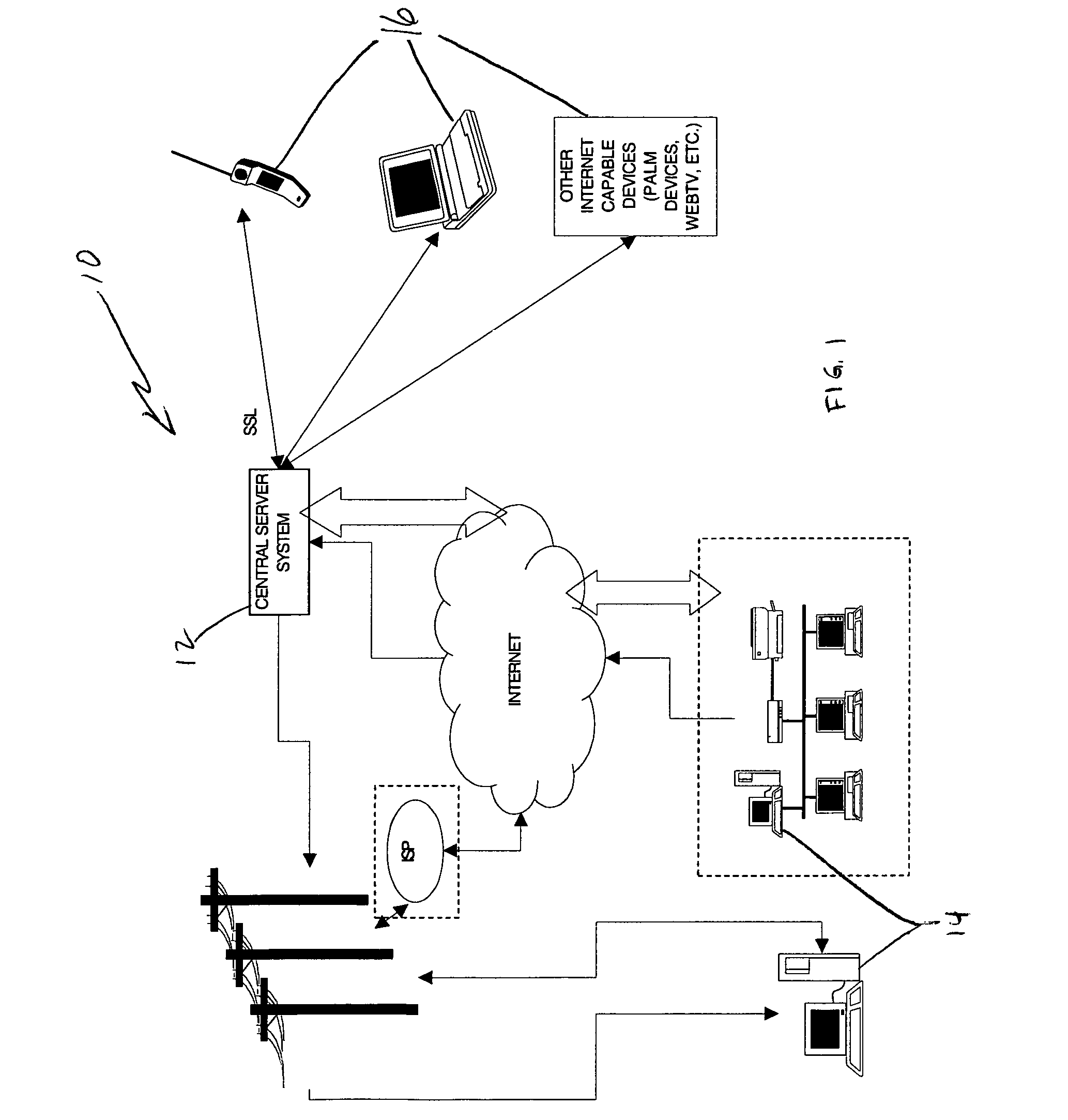
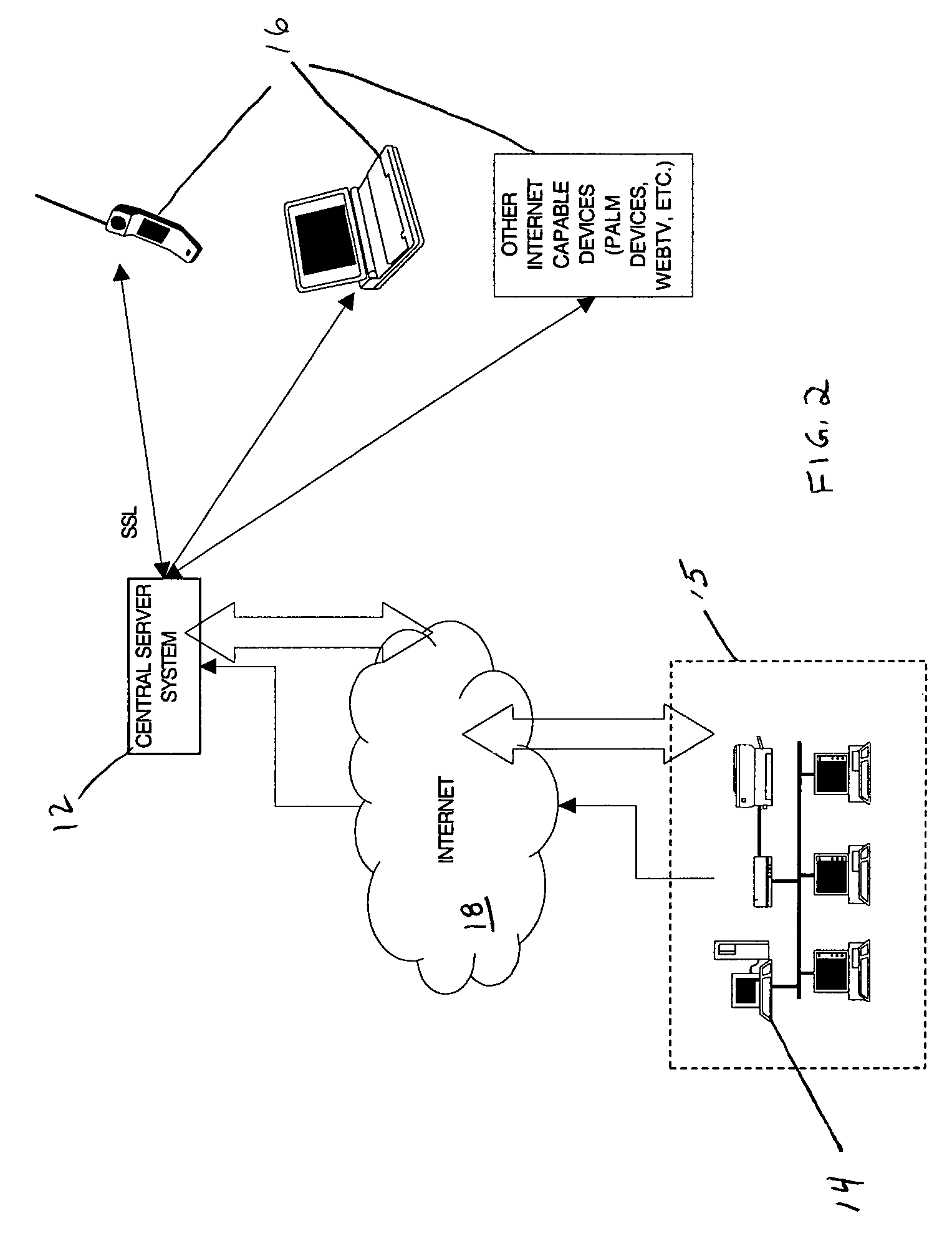
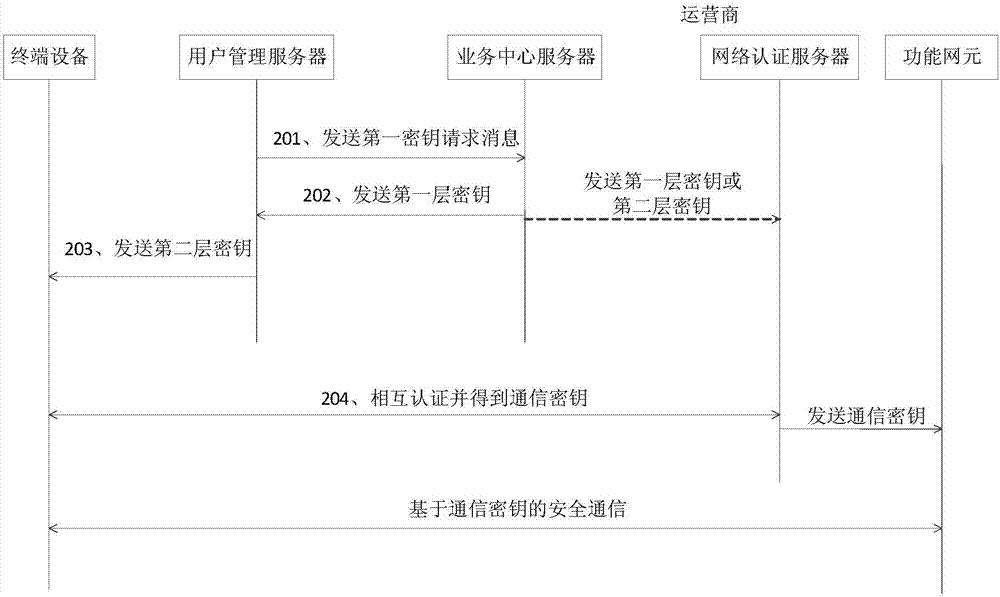
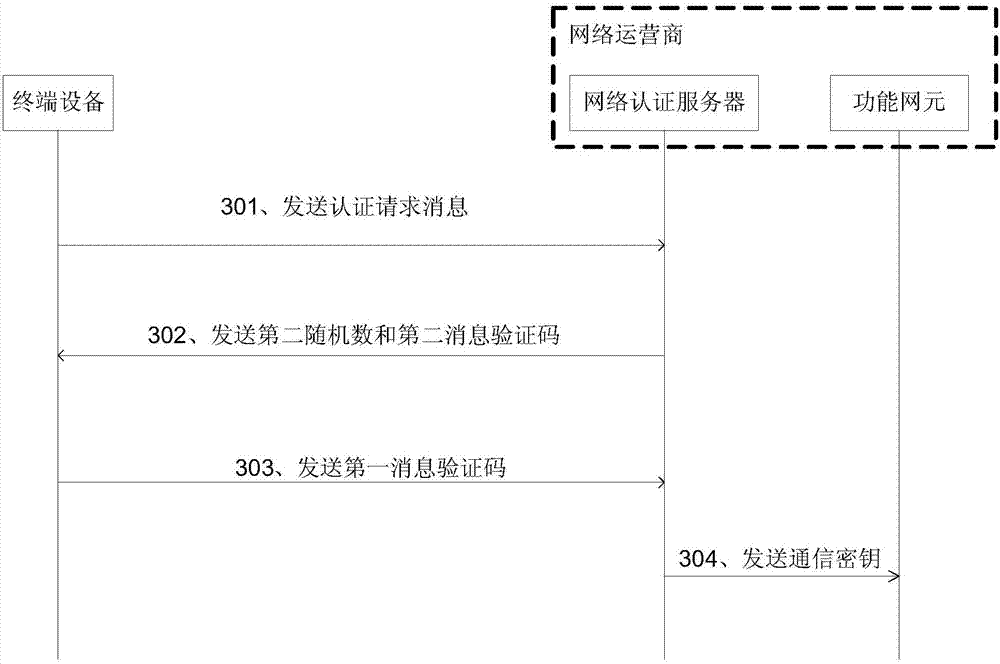
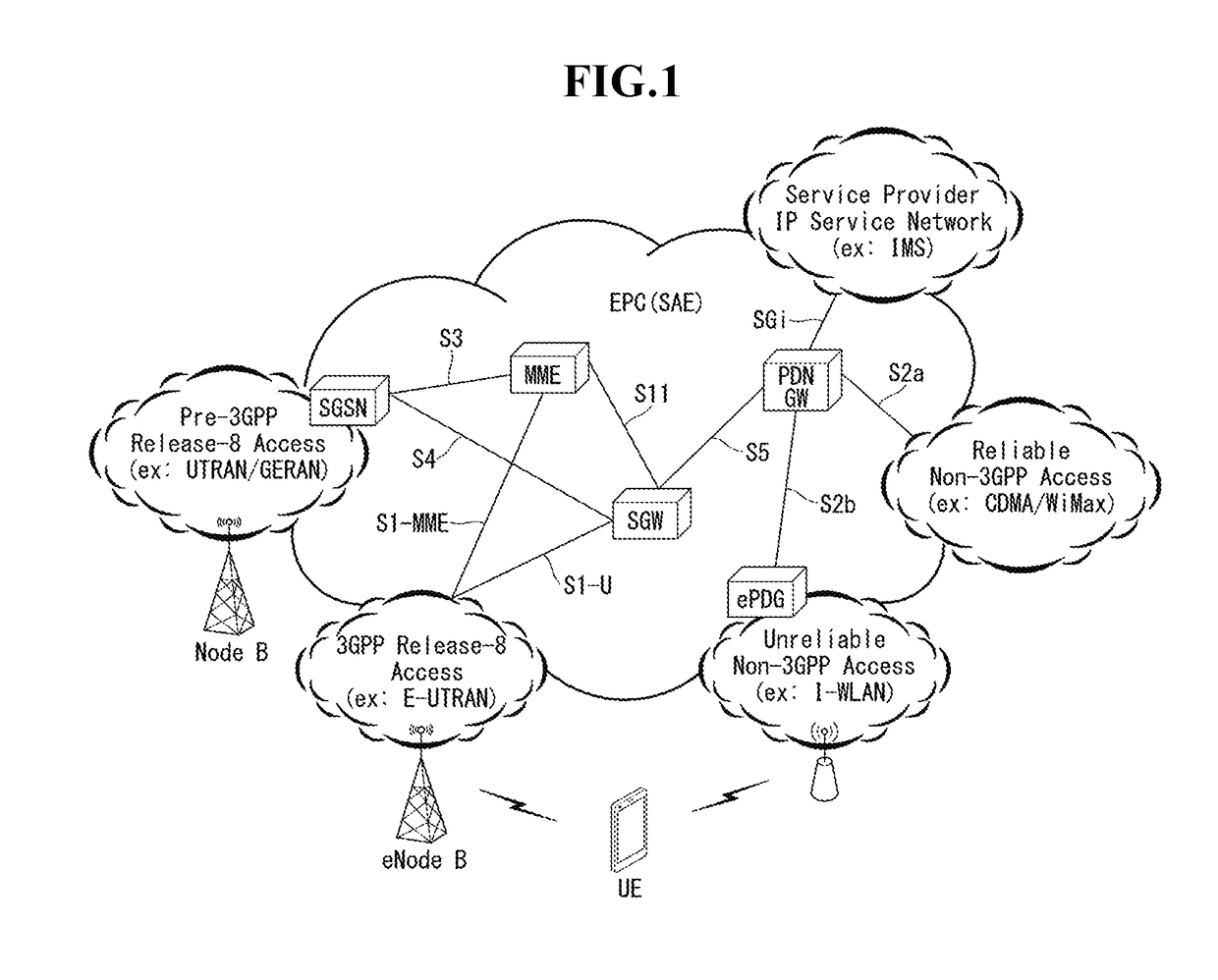
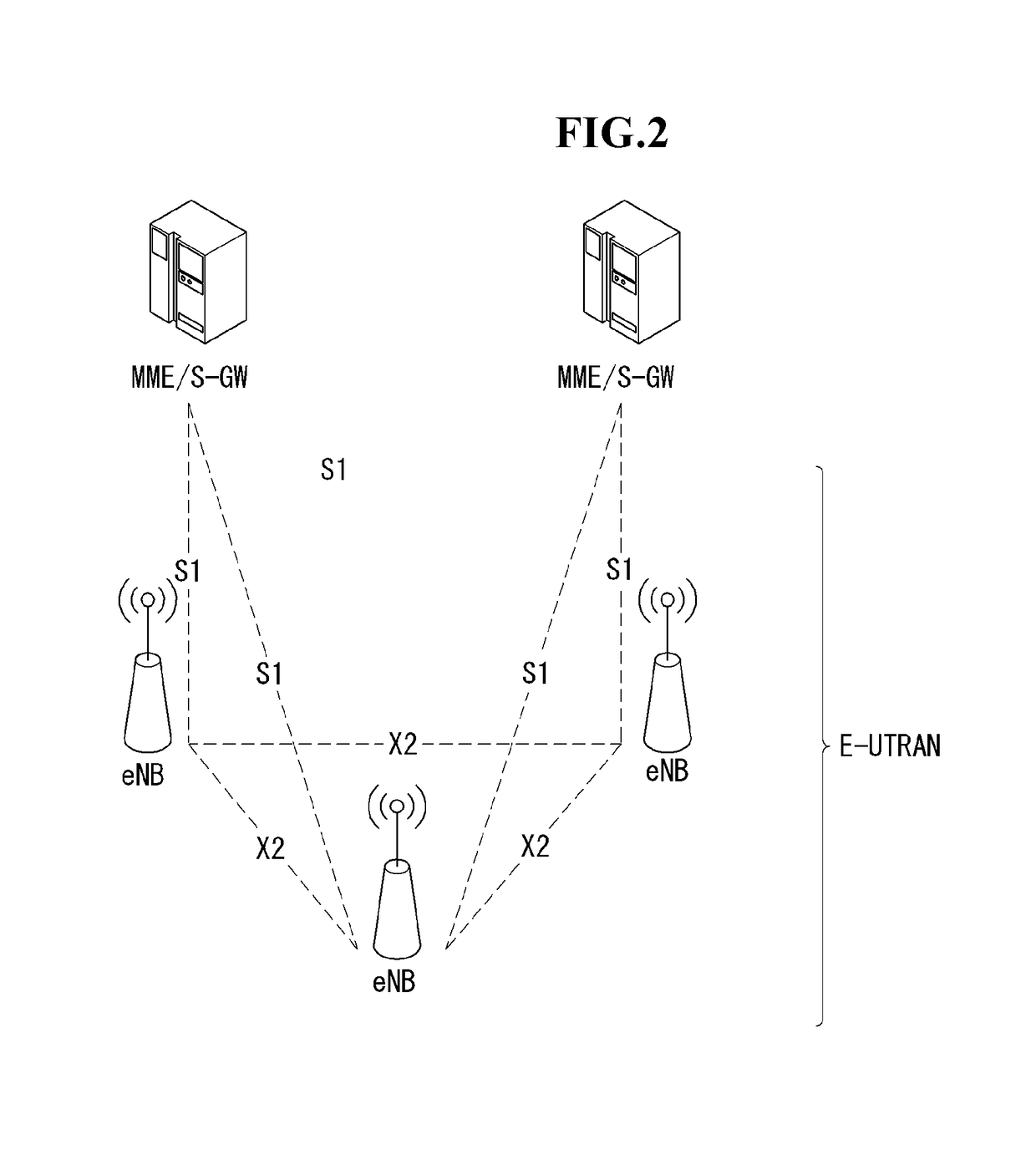
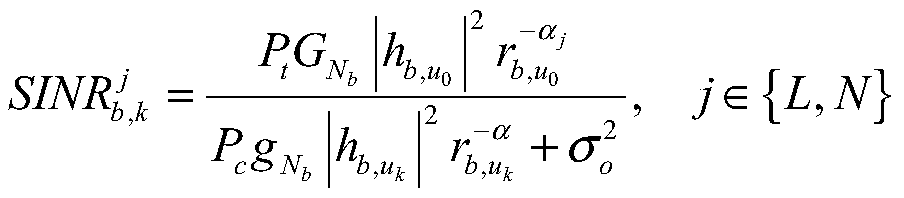Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
82results about "Security arrangement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
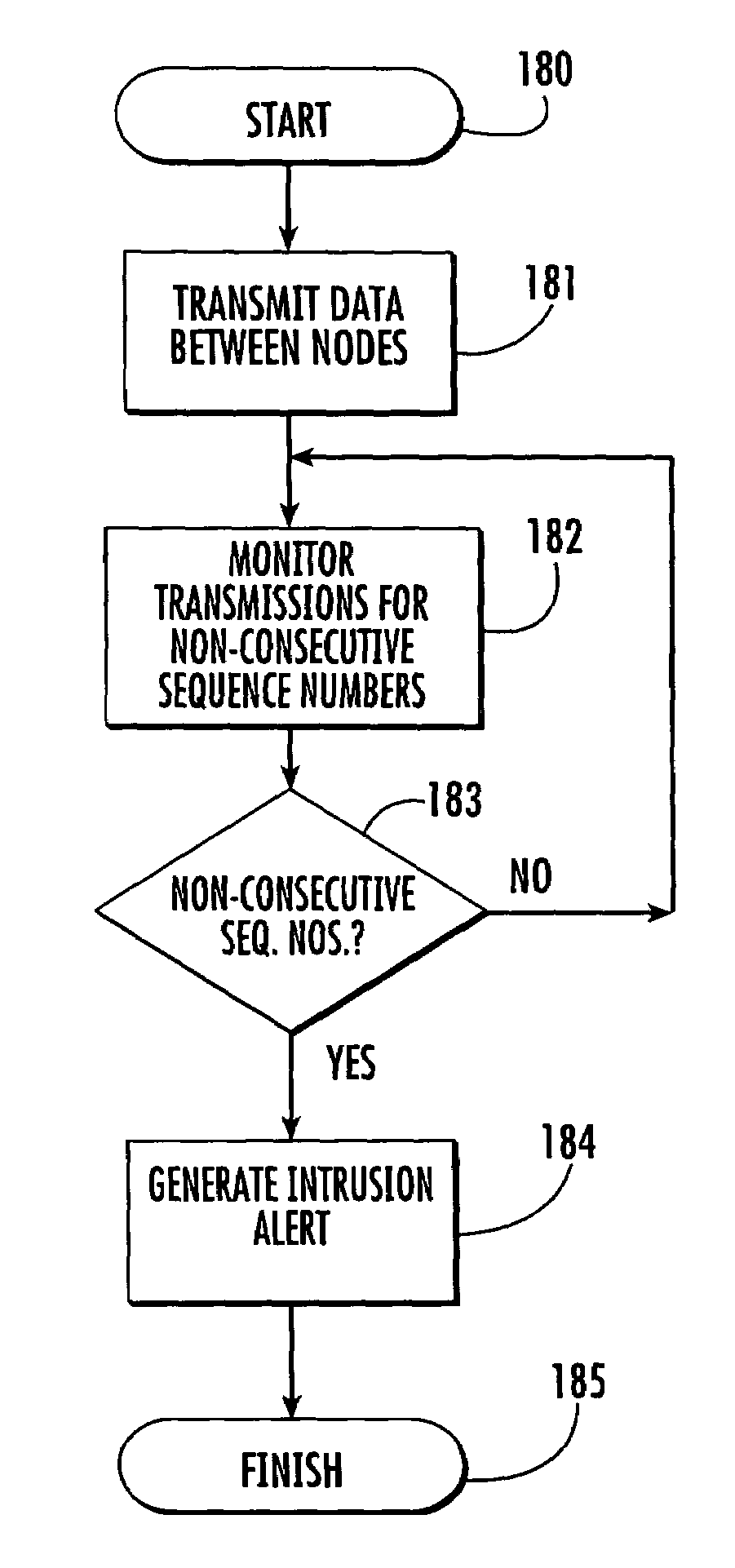
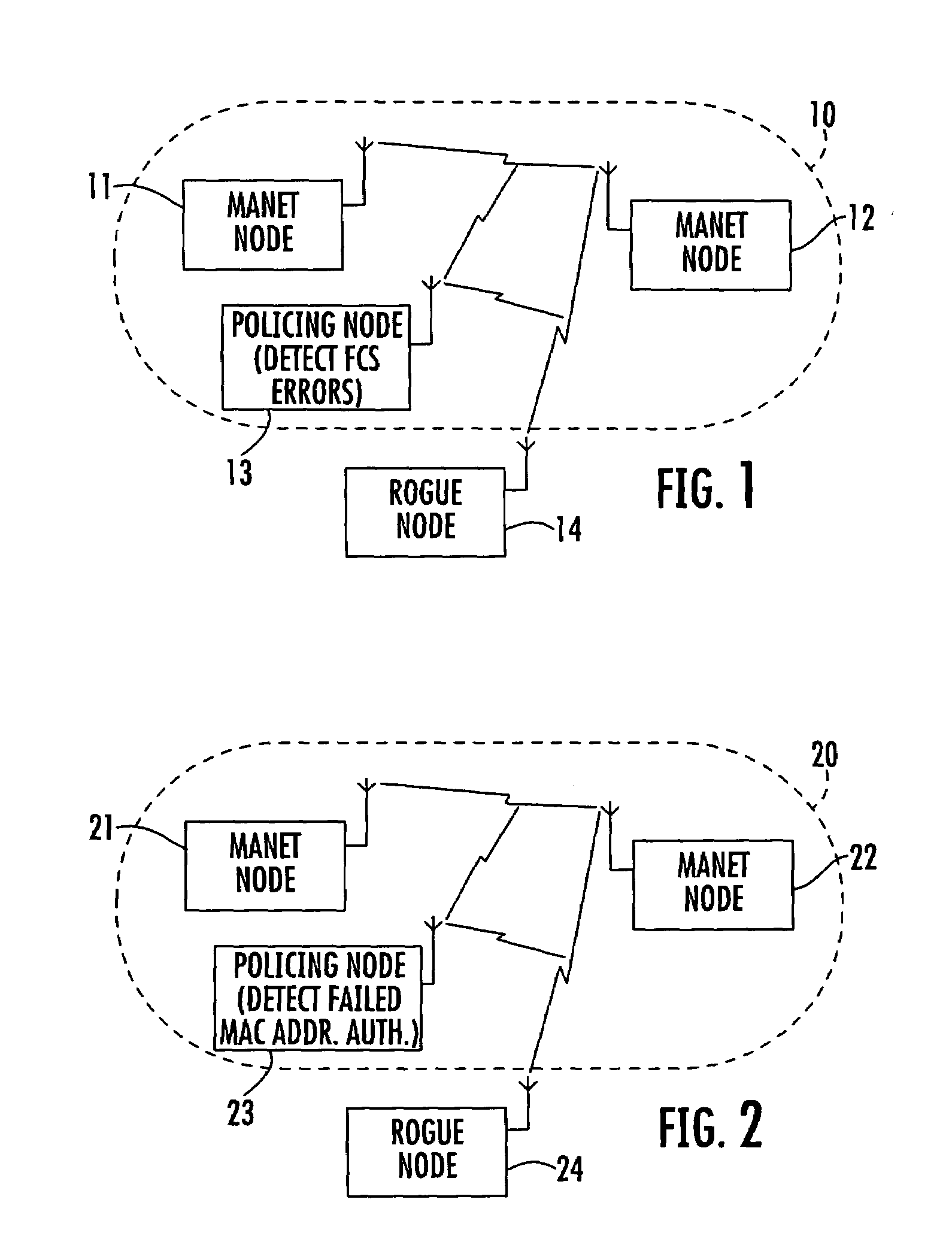
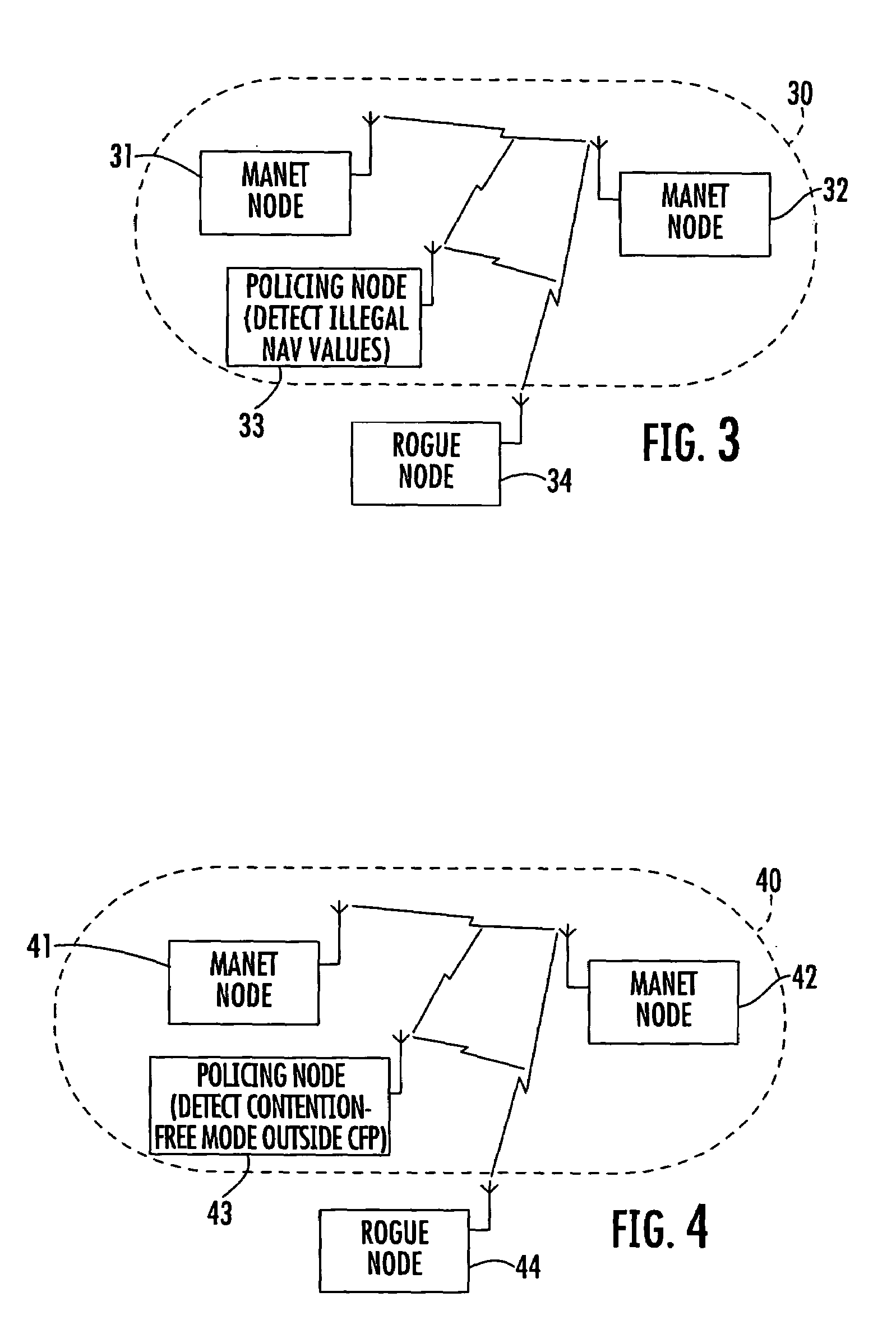
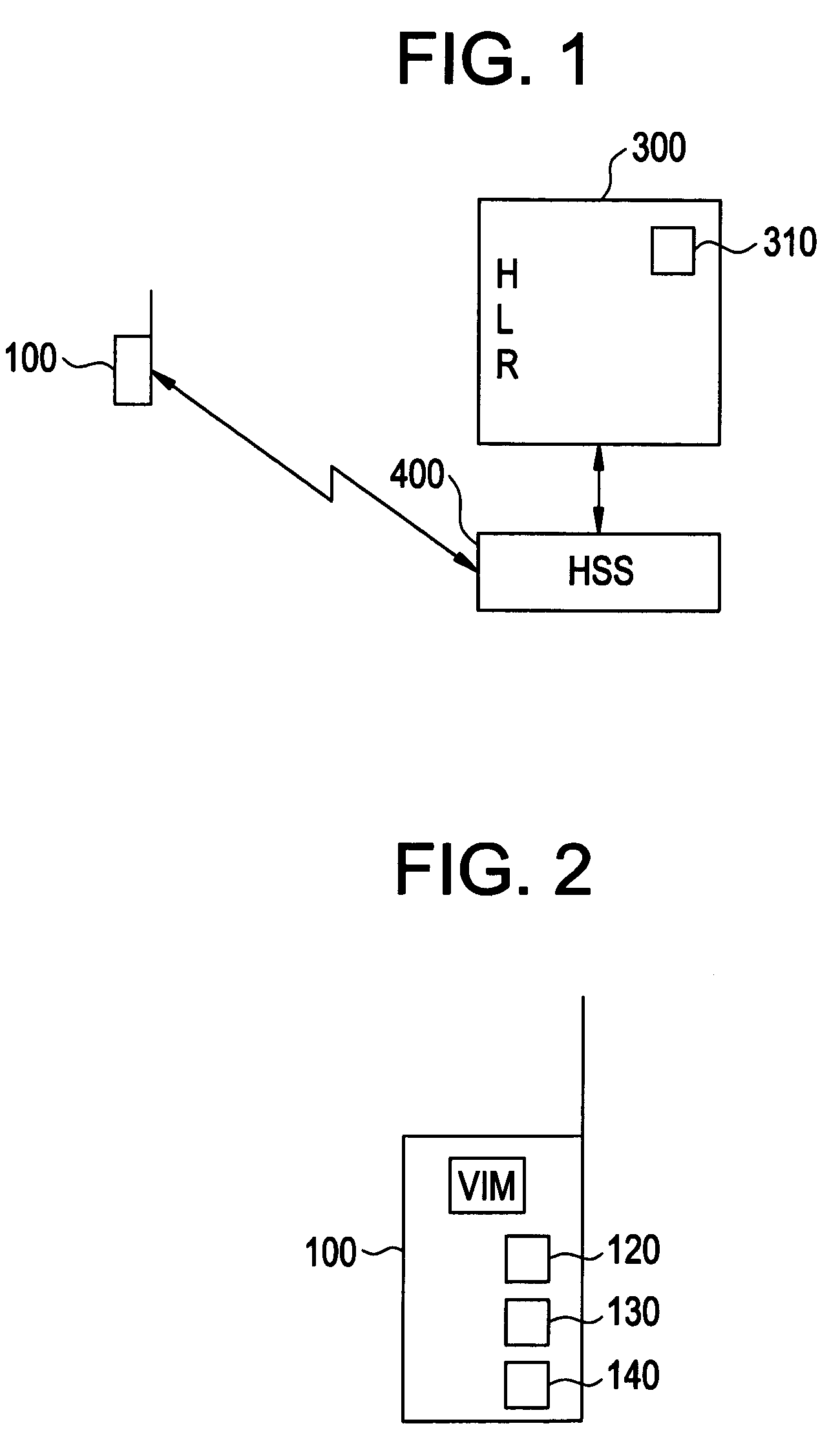
Mobile ad-hoc network with intrusion detection features and related methods
Owner:STINGRAY IP SOLUTIONS LLC
Communication System And Communication Device
InactiveUS20080020707A1Easy to identifyReduce riskKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCommunications system
Owner:SONY CORP
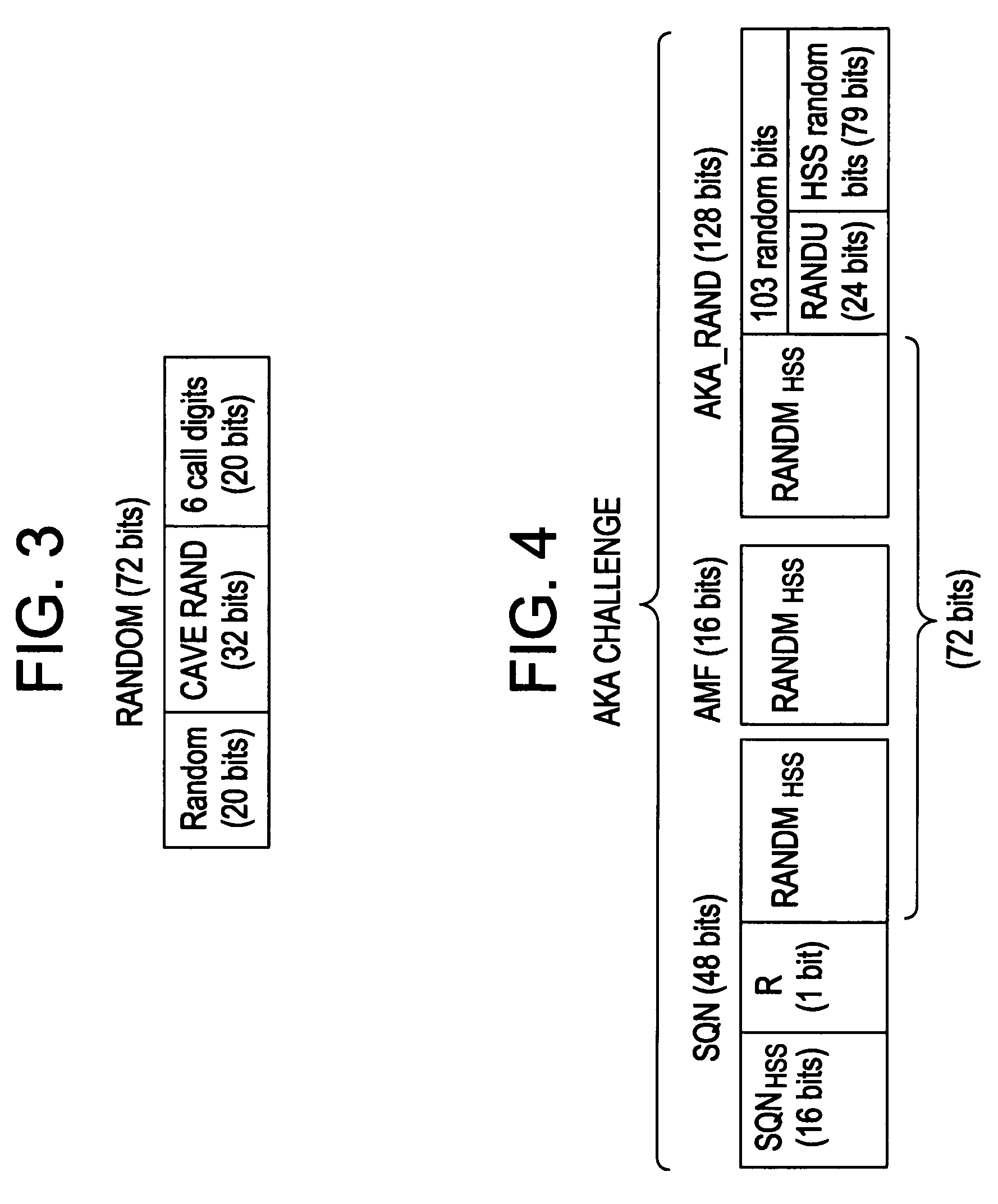
Apparatus and Method for Variable Authentication Requirements
ActiveUS20120239950A1Volume/mass flow measurementUser identity/authority verificationState dependentAuthentication
Owner:LENOVO PC INT
Remote access communication architecture apparatus and method
ActiveUS7895334B1Connection managementMultiprogramming arrangementsCellular telephoneComputer science
Owner:SYNCHRONOSS TECH
Method for the routing and control of packet data traffic in a communication system
InactiveUS20080198861A1Improve scalabilityEqually distributedDigital data processing detailsUser identity/authority verificationCommunications systemNetwork packet
Owner:CORE WIRELESS LICENSING R L
Key distribution and authentication methods, devices and systems
ActiveCN107317789AReduce the burden onSolve the problem that it cannot be applied to smart devices that do not support USIM cardsKey distribution for secure communicationSecurity arrangementSecure communicationWeb authentication
Owner:HUAWEI TECH CO LTD
Method and apparatus for security configuration in wireless communication system
InactiveUS20180083972A1Weak levelTransmissionSecurity arrangementCommunications systemUser equipment
Owner:LG ELECTRONICS INC
Mobile phone anti-theft system and method based on camera and GPS (Global Position System) of mobile phone
InactiveCN102638628AGood policeTimely and accurate recoverySubstation equipmentLocation information based serviceAnti theftMobile phone camera
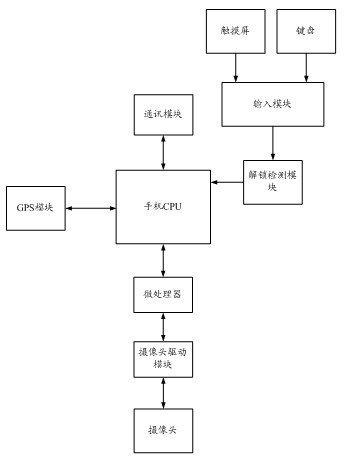
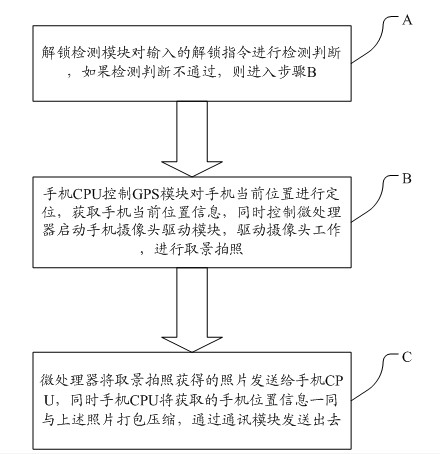
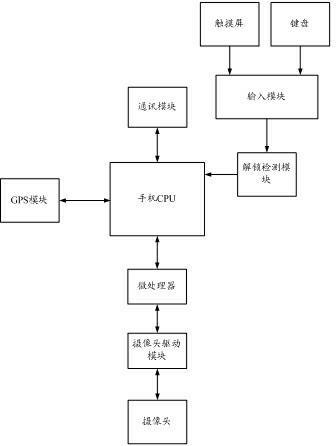
The invention discloses a mobile phone anti-theft system and method based on a camera and a GPS (Global Position System) of a mobile phone. The mobile phone anti-theft system comprises a mobile phone CPU (Central Processing Unit), a microprocessor, a camera driving module, an input module and an unlocking detection module, wherein the input module is connected with the unlocking detection module; the unlocking detection module is connected with the mobile phone CPU; and the mobile phone CPU is connected with the camera driving module through the microprocessor. Compared with the prior art, the mobile phone anti-theft system and method provided by the invention have the advantages as follows: an unlocking operation is carried out when the mobile phone is used after the mobile phone is lost or stolen, and a background operation program which is installed in the mobile phone is triggered and started when the unlocking operation is inaccurate; and a user who currently uses the mobile phone is positioned and photographed through a GPS module and the camera of the mobile phone; meanwhile, obtained information is sent to a mailbox or other addresses which are specified by the user in time, so that the user is convenient to alarm and can find the mobile phone back accurately in time, and the problems of the mobile phone loss and personnel information release of the user can be solved.
Owner:SHENZHEN GIONEE COMM EQUIP
Method for processing access request from ue, and network node
ActiveUS20190159107A1Efficient managementAssess restrictionSecurity arrangementRouting control planeUser equipment
Owner:LG ELECTRONICS INC
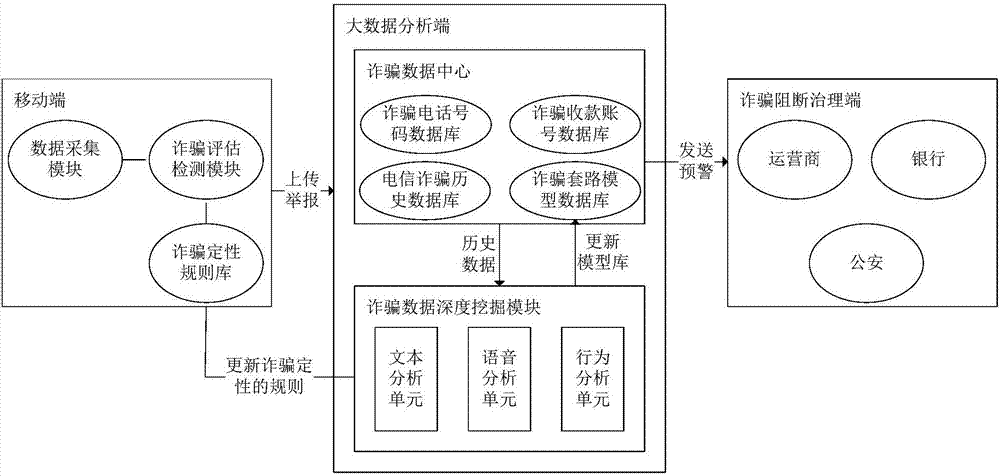
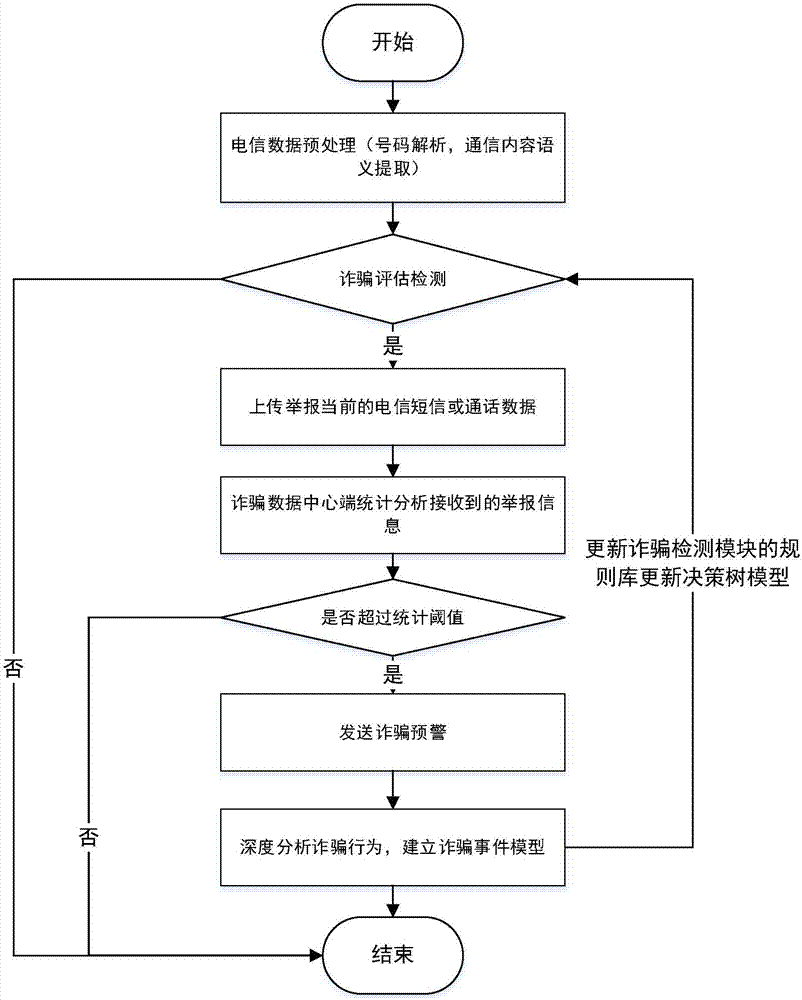
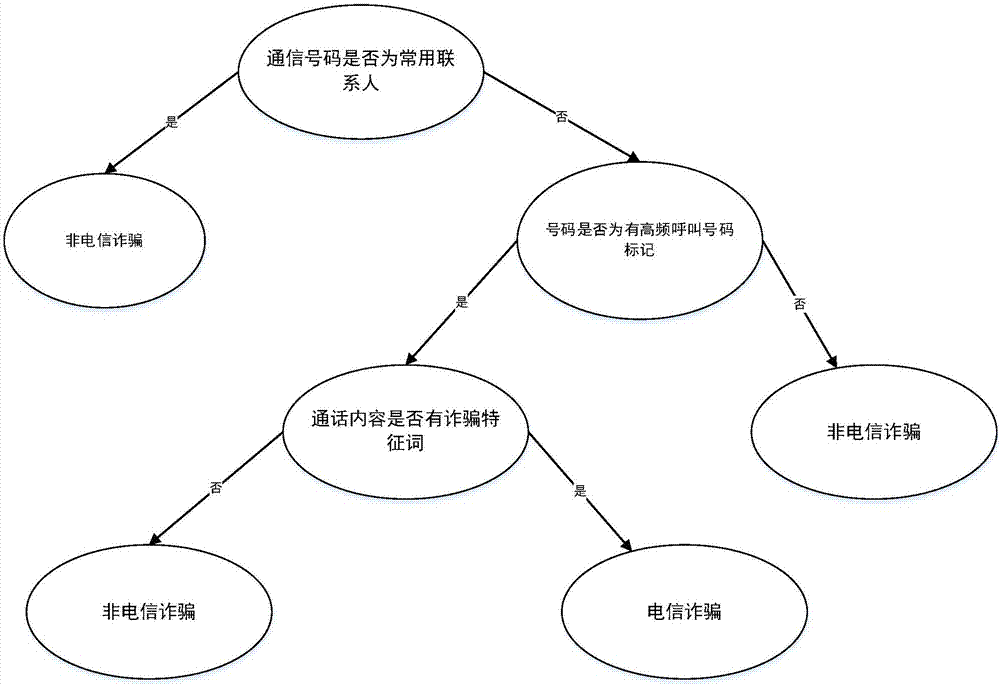
Telecommunication fraud prevention system and method based on big data and machine learning
InactiveCN106970911APrevent fraudulent incidentsCombating Telecom FraudSemantic analysisSubstation equipmentData informationMobile end
Owner:INST OF SOFTWARE APPL TECH GUANGZHOU & CHINESE ACAD OF SCI
CDMA port-to-port encryption communication system and key distribution method thereof
InactiveCN101635924AImprove securityReduce security risksSecurity arrangementCommunications securityCommunications system
The invention discloses a CDMA port-to-port encryption communication system and a key distribution method thereof, the CDMA port-to-port encryption communication system comprises a CDMA network and a terminal mobile telephone thereof, a public switched telephone network and a terminal fixed-line telephone thereof, a short message service center as well as the following three cipher processing units including a cipher chip of a mobile telephone terminal, a key distribution management center (KDMC) and a Firmware cipher module of a gateway mobile switching center. The key distribution management center is used for key distribution management of the communication system. The key distribution is realized by a layered distribution method, i.e. a first layer is an equipment key which is distributed in the process of initialization; a second layer is a key-encryption key and a short message service key which are distributed in startup of an enciphered mobile telephone; and a third layer is a session key which is distributed every time a session is launched between the enciphered mobile telephones. At the same time, by adopting a bidirectional certification technology for key distribution and combination of a key update and remote destroying method, the safety risk in key exposure is reduced, and the communication safety is improved.
Owner:CETC CYBERSPACE SECURITY TECH CO LTD
Safety authentication method and system for wireless network
Owner:HUAZHONG UNIV OF SCI & TECH
Secure wireless communication
ActiveUS20090103728A1Unauthorised/fraudulent call preventionDigital data processing detailsHash-based message authentication codeCryptographic protocol
Owner:ALCATEL LUCENT SAS
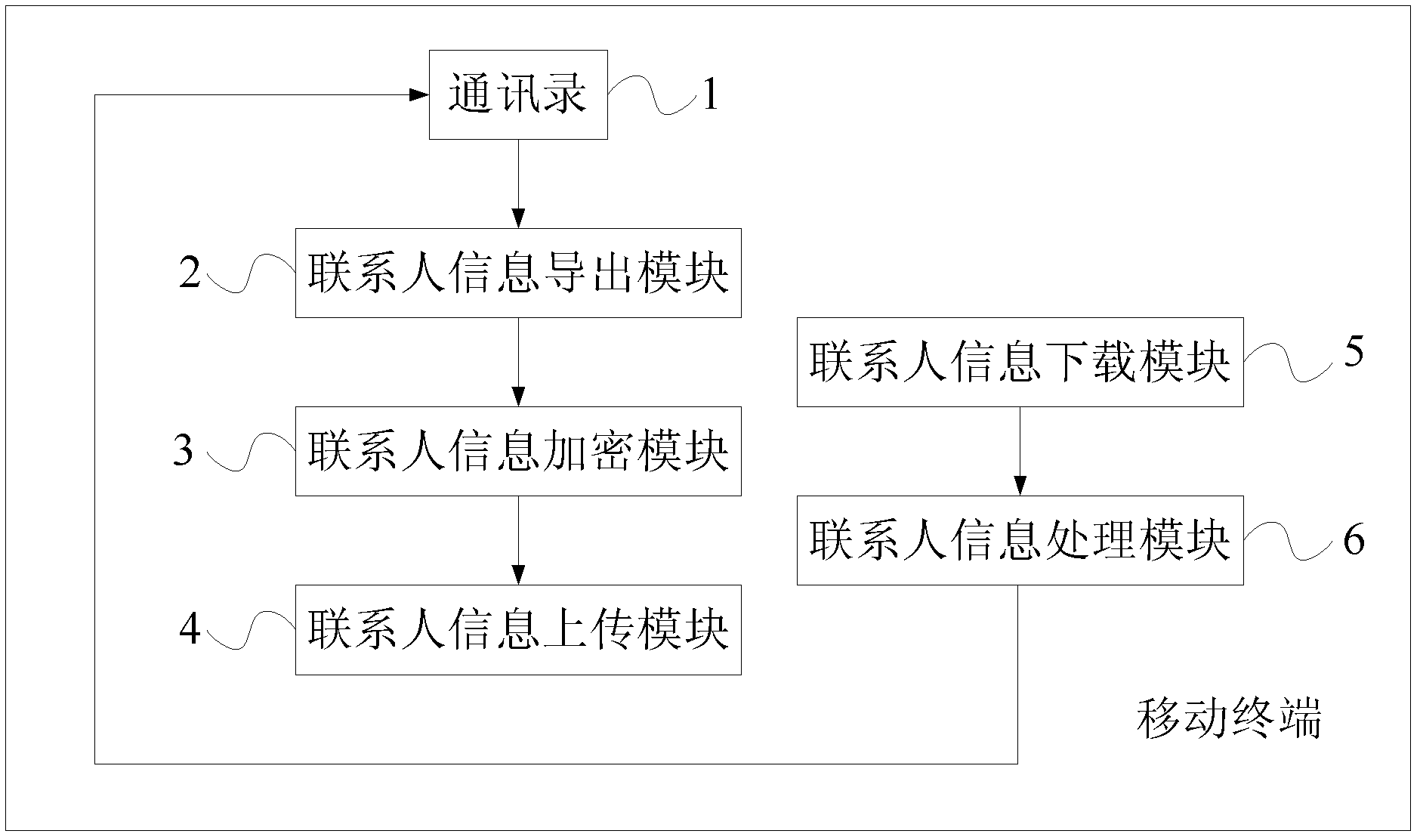
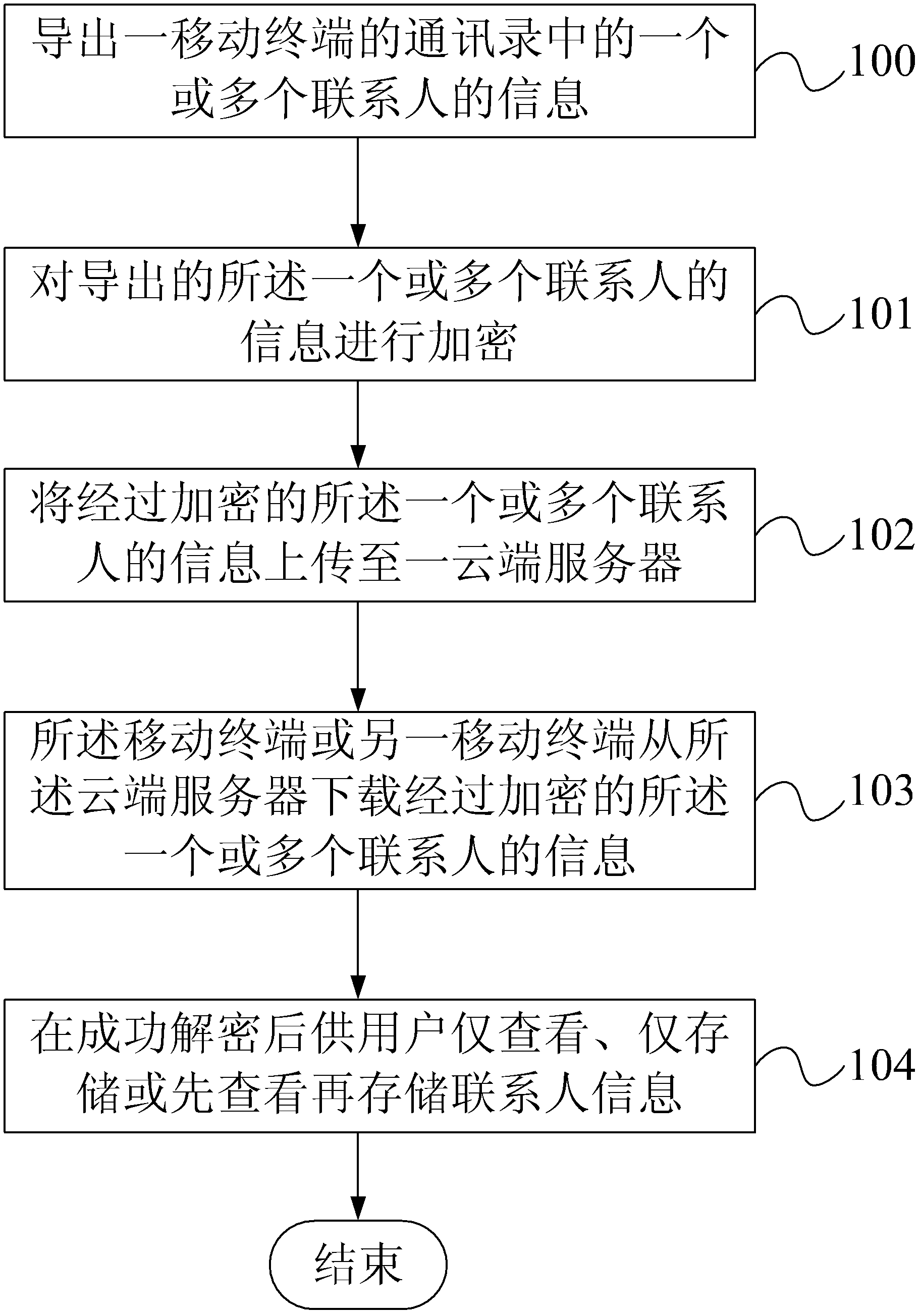
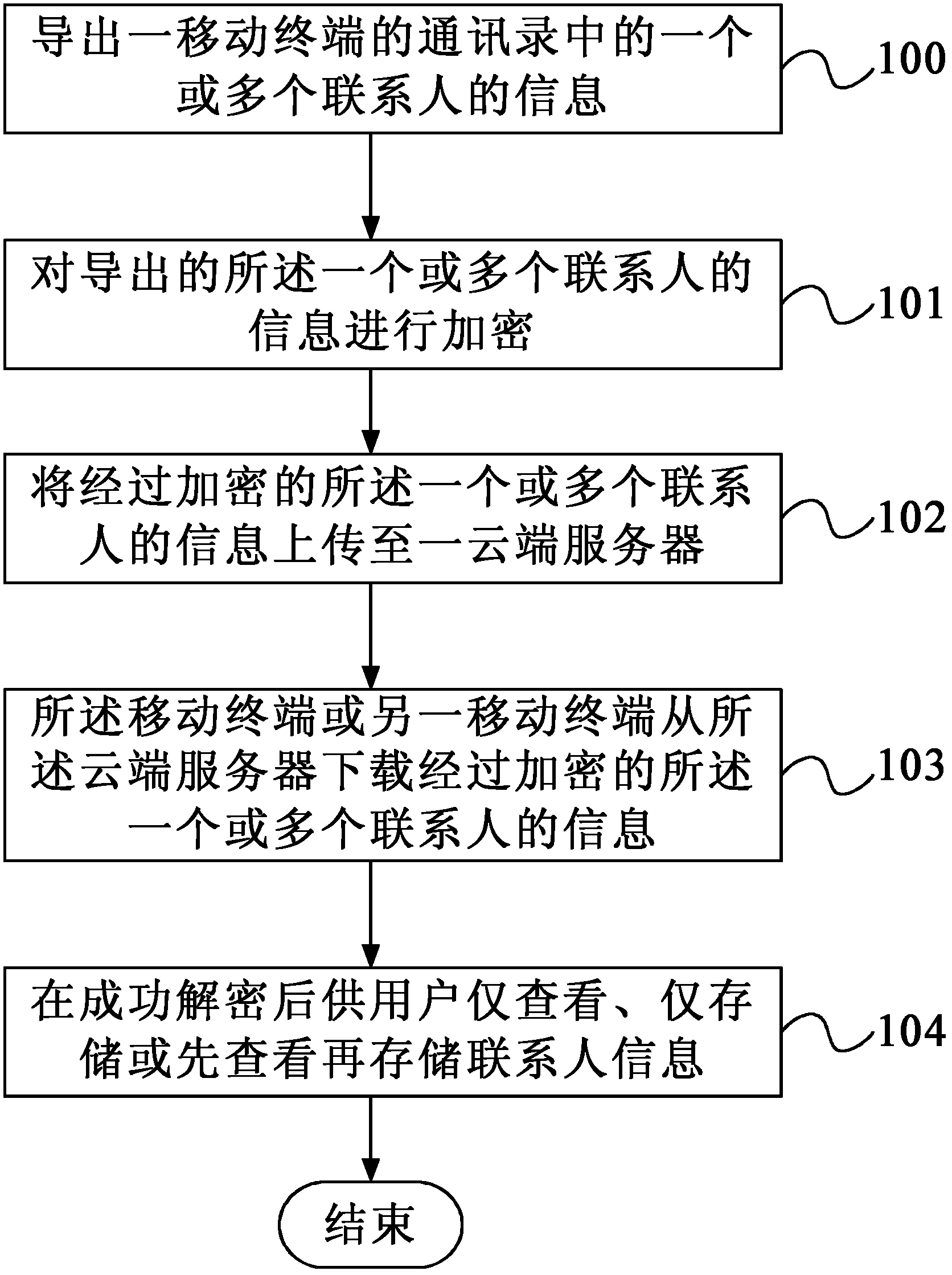
Backup method, mobile terminal and backup system for contact person information
ActiveCN102427581AAchieve sharingEnsure safetyTransmissionSecurity arrangementAddress bookComputer terminal
Owner:HUAQIN TECH CO LTD
System and Method for Detecting and Evicting Malicious Vehicles in a Vehicle Communications Network
ActiveUS20110214178A1Improve performanceReduce impactMemory loss protectionError detection/correctionMathematical modelSimulation
In a vehicle communication network, some vehicles may be used by attackers to send false information to other vehicles which may jeopardize the safety of other vehicles. Vehicles should be able to detect malicious communications activities and to mitigate the impact of malicious vehicles by evicting (eliminating) suspected malicious vehicles from the system. Evicting a vehicle is to ignore the messages sent from the vehicle for a specified time period. Voting and sacrifice principles are combined using a mathematical model based on the “Mafia Game”. The Mafia Game model focuses on the relative size of the group of attackers within a neighborhood necessary to dominate the entire network in the neighborhood (i.e., to eventually evict all the innocent vehicles).
Owner:PERSPECTA LABS INC
Authentication method and system
ActiveCN102123157AAvoid attackAvoid the authentication processUser identity/authority verificationSecurity arrangementAuthentication serverClient-side
Owner:SHANGHAI HUAWEI TECH CO LTD
Communication method between a handset device and IC cards
ActiveUS20100090000A1Small sizeQuick switchSensing record carriersRecord carriers used with machinesComputer hardwareHandset
Owner:STMICROELECTRONICS INT NV
Method for realizing the public wireless broadband network access and wireless network access equipment
InactiveCN101521878AOvercome the shortcomings of small range and being affected by obstaclesUniversal coverageNetwork topologiesConnection managementInformation processingAccess method
Owner:张泽华
System and method for biometric verification of ticket users
Techniques are disclosed for validating a ticket based on biometric data provided by a ticket holding user. A ticket controller device broadcasts an inquiry frame specifying a request for authentication data for a ticket user requesting access to a service hosted by the ticket controller. A mobile device may receive the inquiry frame and generate a response frame encapsulating a ticket identifier and biometric data associated with a user. The ticket controller receives the response frame including the ticket identifier and the biometric data. Upon determining that the ticket identifier and the biometric data encapsulated in the response frame matches a stored ticket identifier and biometric data, the ticket controller grants the user access to the service.
Owner:INT BUSINESS MASCH CORP
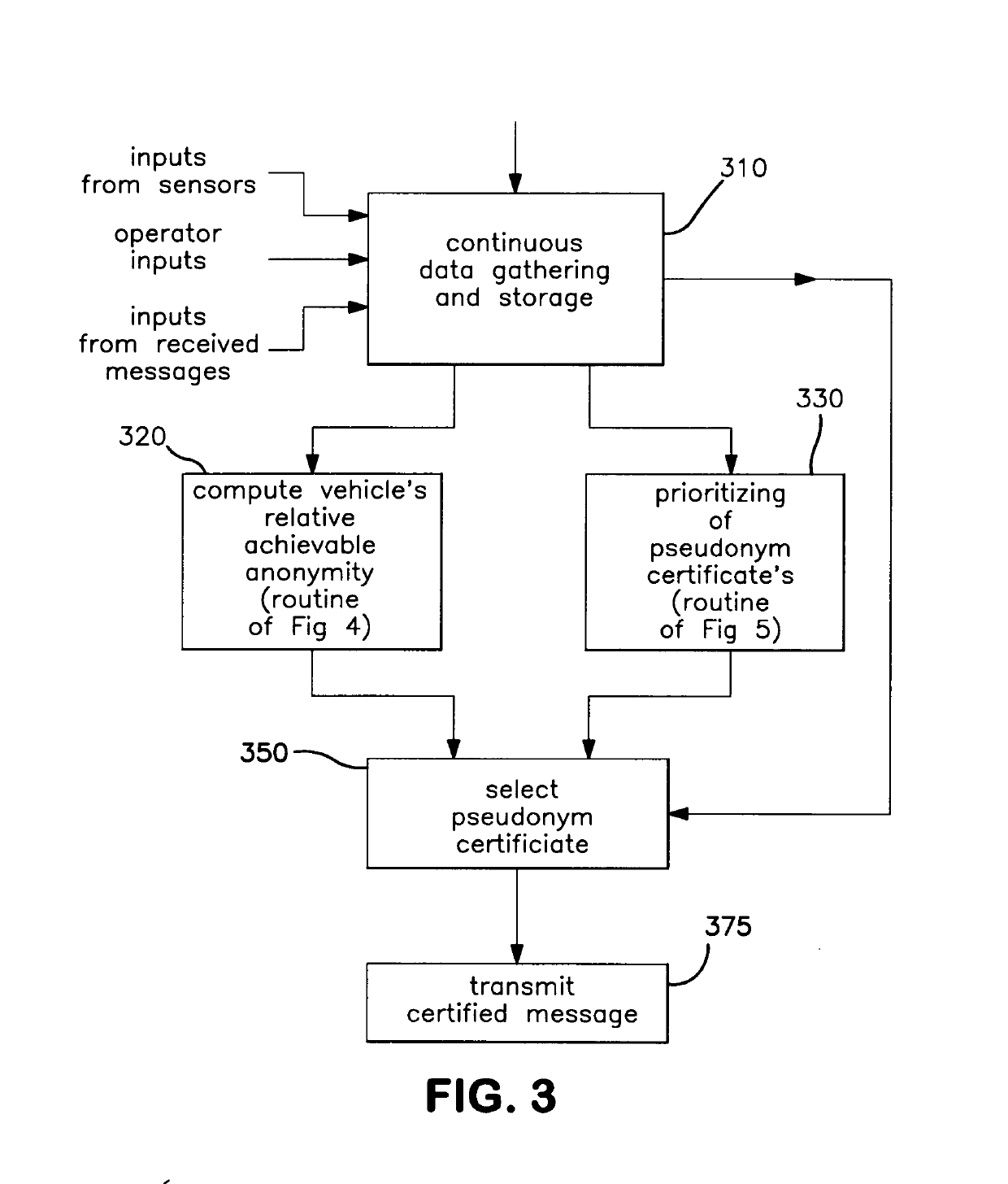
Method and system for connected vehicle communication
ActiveUS20190245831A1Improve privacyImprove securityParticular environment based servicesVehicle wireless communication serviceAnonymityLocation data
Owner:ONBOARD SECURITY INC
Session management with relaying and charging for indirect connection for internet of things appplications in 3gpp network
ActiveCN109997334AConnection managementData switching networksProcessing InstructionSession management
The application is at least directed to a core network including a non-transitory memory including instructions stored thereon for transferring infrequent small data to a service capability or application server on a 5G network. The core network also includes a processor operably coupled to the non-transitory memory. The processor is configured to execute the instructions of detecting a relay userequipment (UE) sending a data transfer request message to the core network based on uplink traffic generated at a remote UE and control information of the remote UE. The processor is also configuredto execute the instructions of querying a database in the core network for subscription information of the remote UE based on the control information. The processor is also configured to execute the instructions of receiving the subscription information from the database. The processor is further configured to execute the instructions of processing the received subscription information. The processor is even further configured to execute the instructions of selecting a network function for transmitting the uplink traffic to the server based on the processing instruction.
Owner:INTERDIGITAL PATENT HLDG INC
Device and system for cloud based mobile application virtualization
ActiveUS20180109624A1Increased app densityHigh densityTransmissionSecurity arrangementVirtualizationSession management
Owner:SIERRAWARE LLC
Communication method, device and system
ActiveCN109600339AAvoid the problem of large delayNetwork traffic/resource managementTransmissionQuality of serviceSession management
The invention relates to the technical field of wireless communication, in particular to a communication method, a communication system and communication equipment, which are used for realizing safetyprotection based on quality of service (QoS) flow so as to meet the safety requirements of different services and improve the flexibility of network safety. The method comprises the following steps that session management equipment receives a request, wherein the request is used for requesting session establishment or session modification; the session management equipment obtains a target security policy of the QoS flow according to the request; and the session management equipment sends indication information to a mobility management device, wherein the indication information is used for indicating a target security policy of the QoS flow.
Owner:HUAWEI TECH CO LTD
Wireless payment method between vehicles based on 5G communication network and system thereof
ActiveCN108307349AEnsure safetyImprove performanceCryptography processingParticular environment based servicesPaymentE communication
The invention relates to a wireless payment method between vehicles based on a 5G communication network. The method includes the steps that: a requesting vehicle sends a payment request to a base station; the base station retrieves vehicle information of a friend vehicle of the requesting vehicle based on the payment request; the base station encrypts the requesting information by using the vehicle information of the friend vehicle for broadcasting; the vehicle within the broadcast range of the base station decodes the broadcast information by utilizing the own vehicle information, the friendvehicle acquires the requesting information as a responding vehicle if the decoding is successful; the responding vehicle generates payment information based on the requesting information and sends the payment information to the base station, the base station sends the payment information to a payment platform, and the payment platform returns the payment result to the responding vehicle; the basestation assigns a D2D communication channel to the requesting vehicle and the responding vehicle, and the responding vehicle and the requesting vehicle communicate via the D2D communication channel.According to the invention, the communication between vehicles can be realized, and the security of payment can be ensured.
Owner:CHINA UNIONPAY
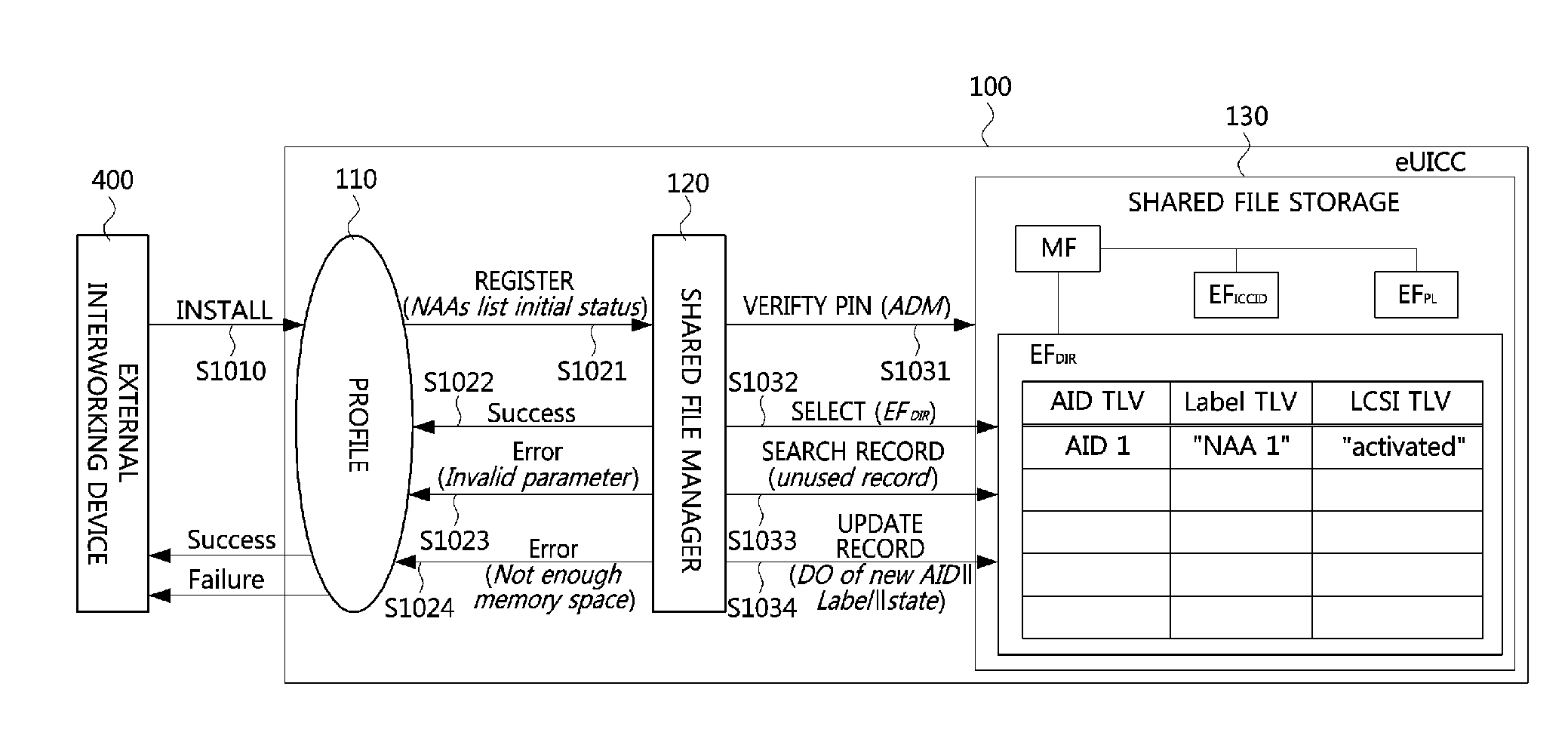
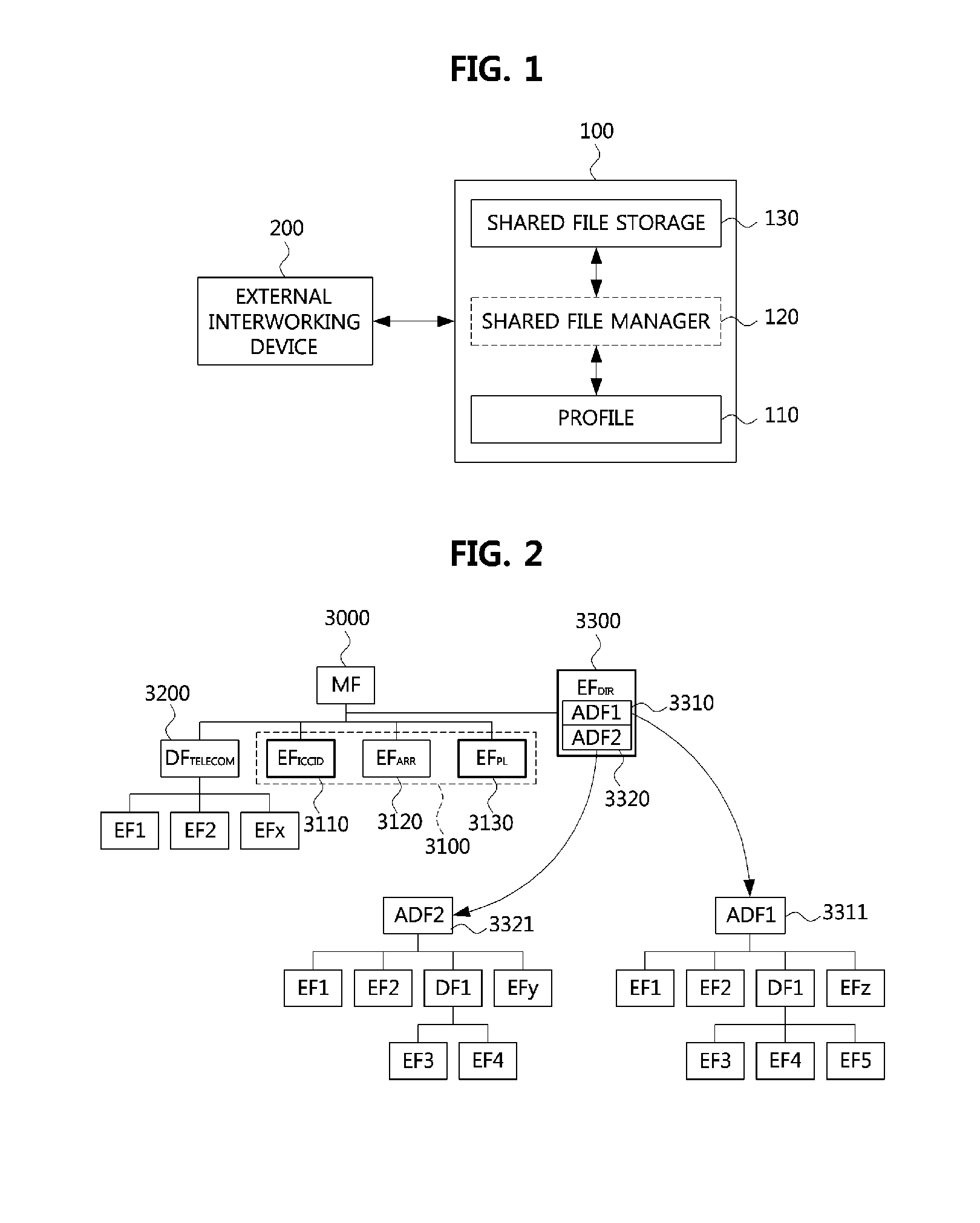
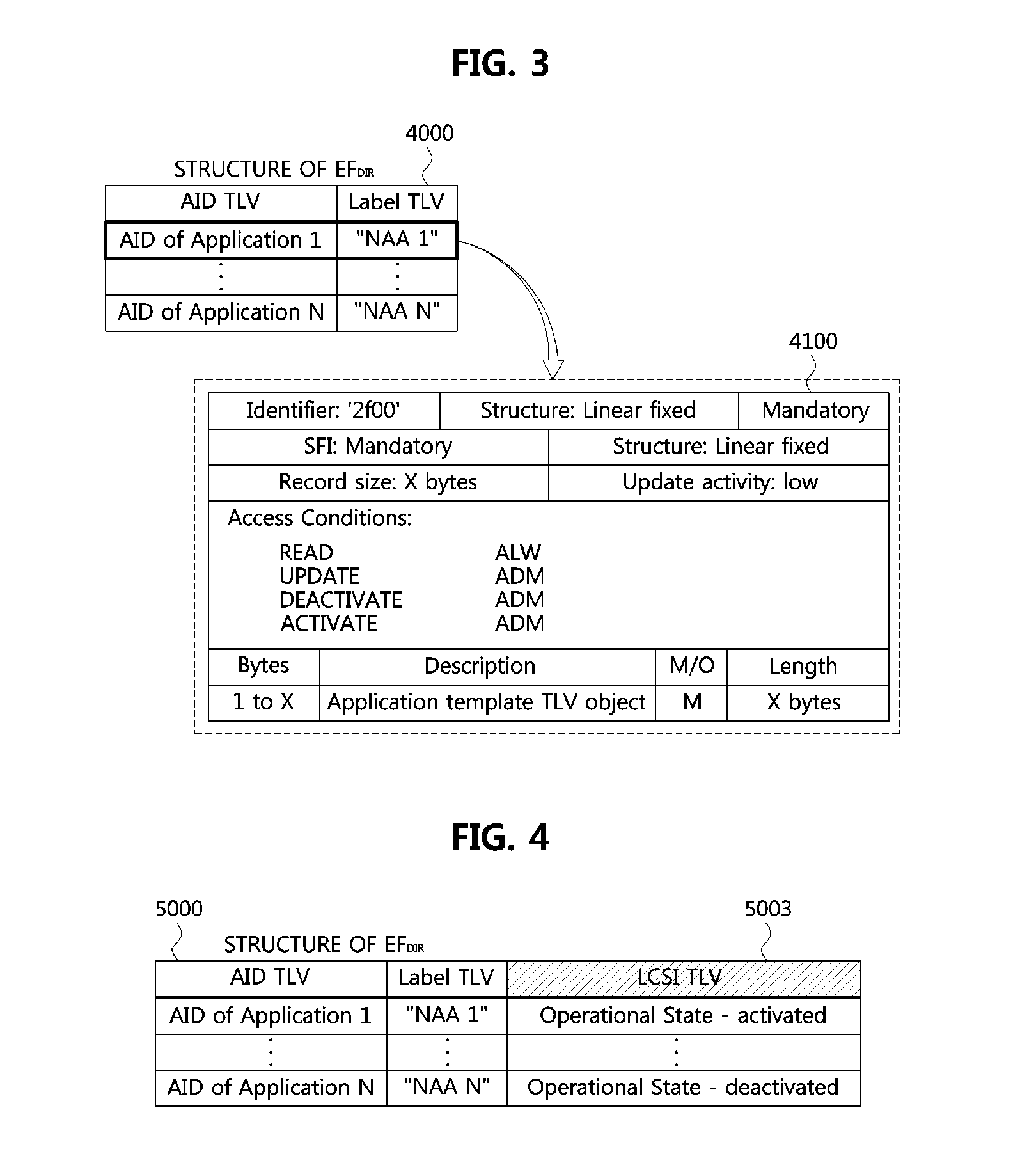
Method of managing shared file and device for authenticating subscriber by using same
InactiveUS20150271173A1Program control using stored programsDigital data processing detailsComputer moduleTerminal equipment
Owner:KT CORP
Modular cryptographic device and coupling therefor and related methods
InactiveUS20050213762A1High level securityEasy to adaptData switching by path configurationSecret communicationComputer hardwareModularity
Owner:HARRIS CORP
Method and System for Transmitting Control Data in a Manner that is Secured Against Manipulation
ActiveUS20130132730A1High protection levelLittle effortUser identity/authority verificationData switching networksControl dataSecret code
Owner:SIEMENS AG
Mesh communications network having mesh ports
A method for communicating over a mesh network established between a plurality of devices is disclosed. Each device has a wireless radio and the method involves launching a mesh service on each device, the mesh service being operable to cause a processor circuit of the device to provide functionality for controlling the wireless radio for communication between devices over the mesh network. Each device has at least one application running on the device, the at least one application being associated with a mesh port, the mesh port being used to designate data transmissions as being associated with instances of a specific application running on at least some of the devices in the plurality of devices, the at least one application and the mesh service on each device being in data communication. The method also involves, in response to a specific application running on a device requesting the mesh service to provide access to the mesh network for communication via a specific mesh port, causing the mesh service to determine whether the specific application is authorized for communications on the specific mesh port, and if the specific application is authorized, processing requests from the application to communicate on the specific mesh port over the mesh network and forwarding data transmissions associated with the specific mesh port to the specific application, and if the specific application is not authorized, declining requests from the application to communicate on the specific mesh port over the mesh network and preventing access by the specific application to data transmissions associated with the specific mesh port.
Owner:LEFT OF THE DOT MEDIA
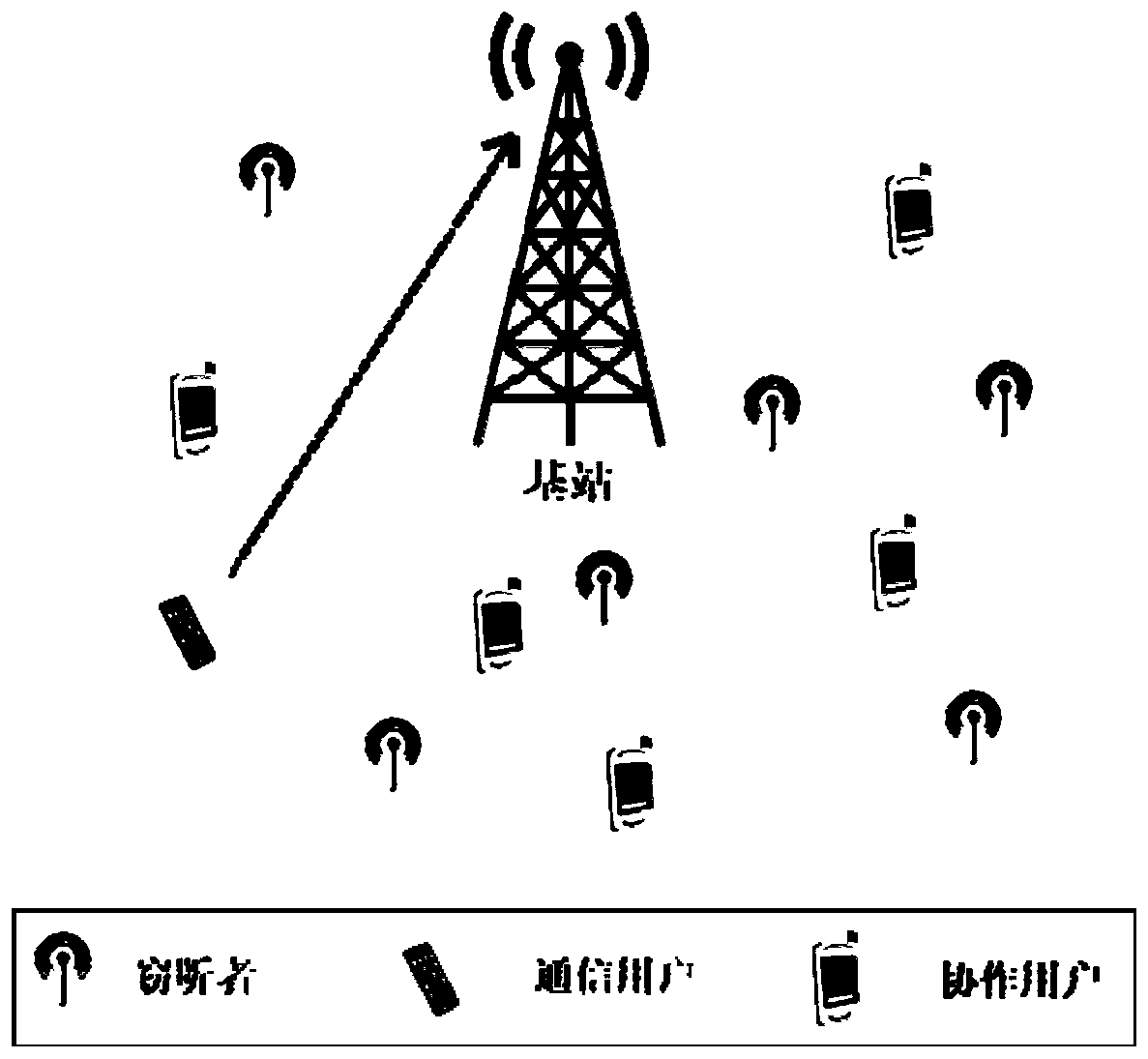
Interference blocking scheme switching method for millimeter wave cellular network uplink secure transmission
ActiveCN110381503AIncrease freedomGuaranteed transmission reliabilityCommunication jammingLocation information based serviceTelecommunications linkSecure transmission
Owner:XI AN JIAOTONG UNIV
Popular searches
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap