Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Internet privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information pertaining to oneself via the Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing.
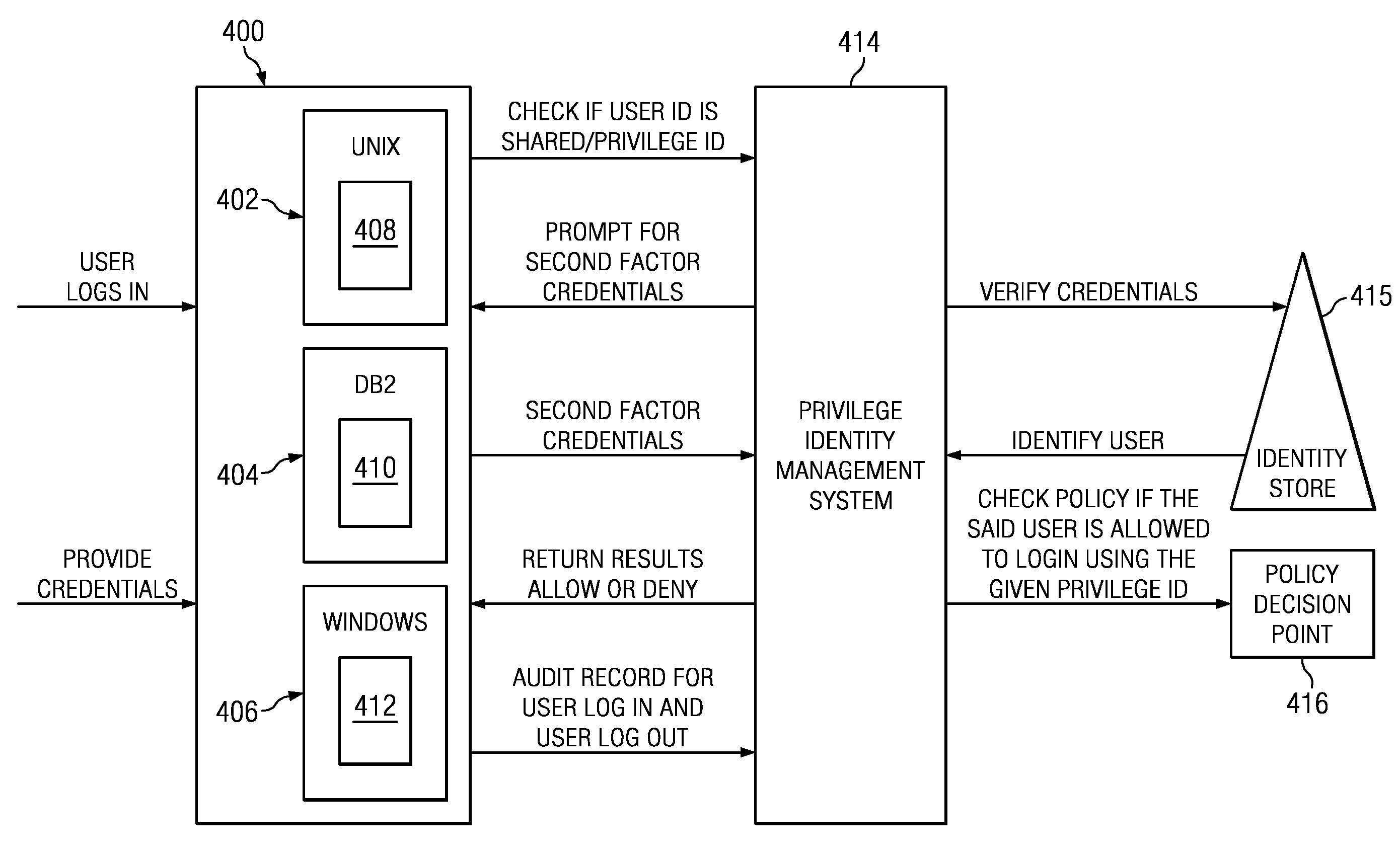
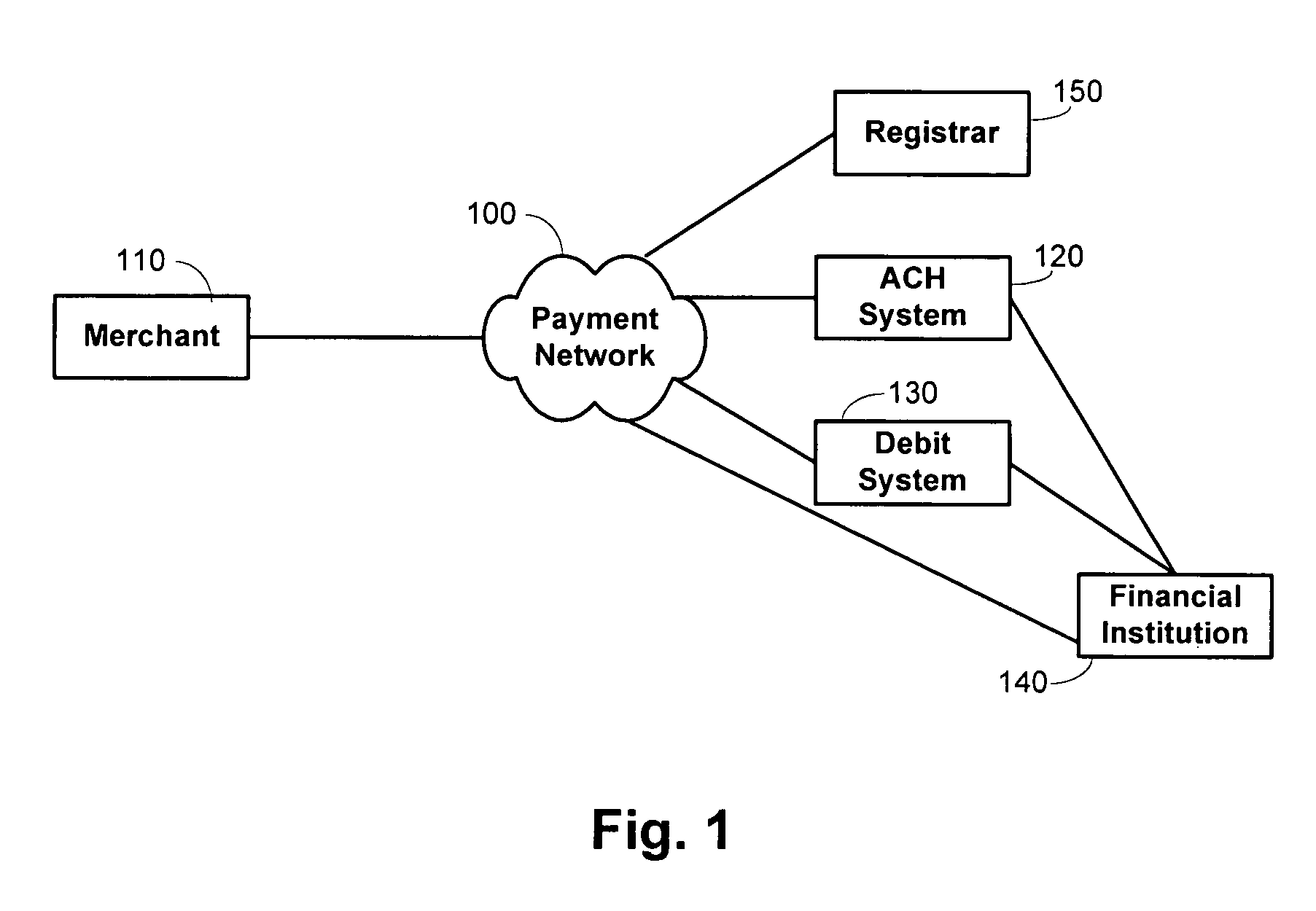
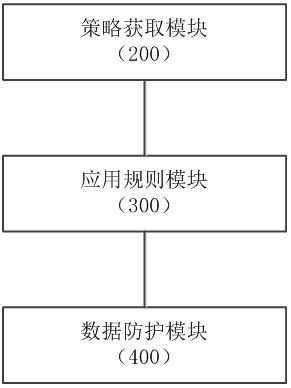
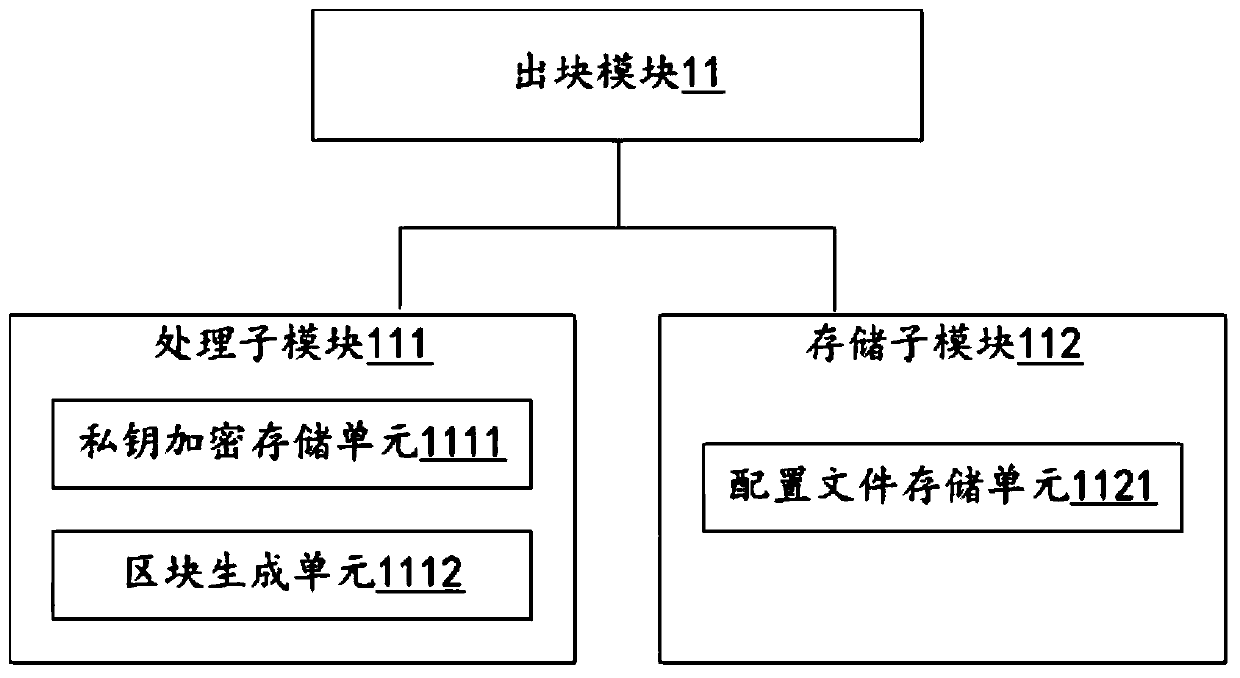
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
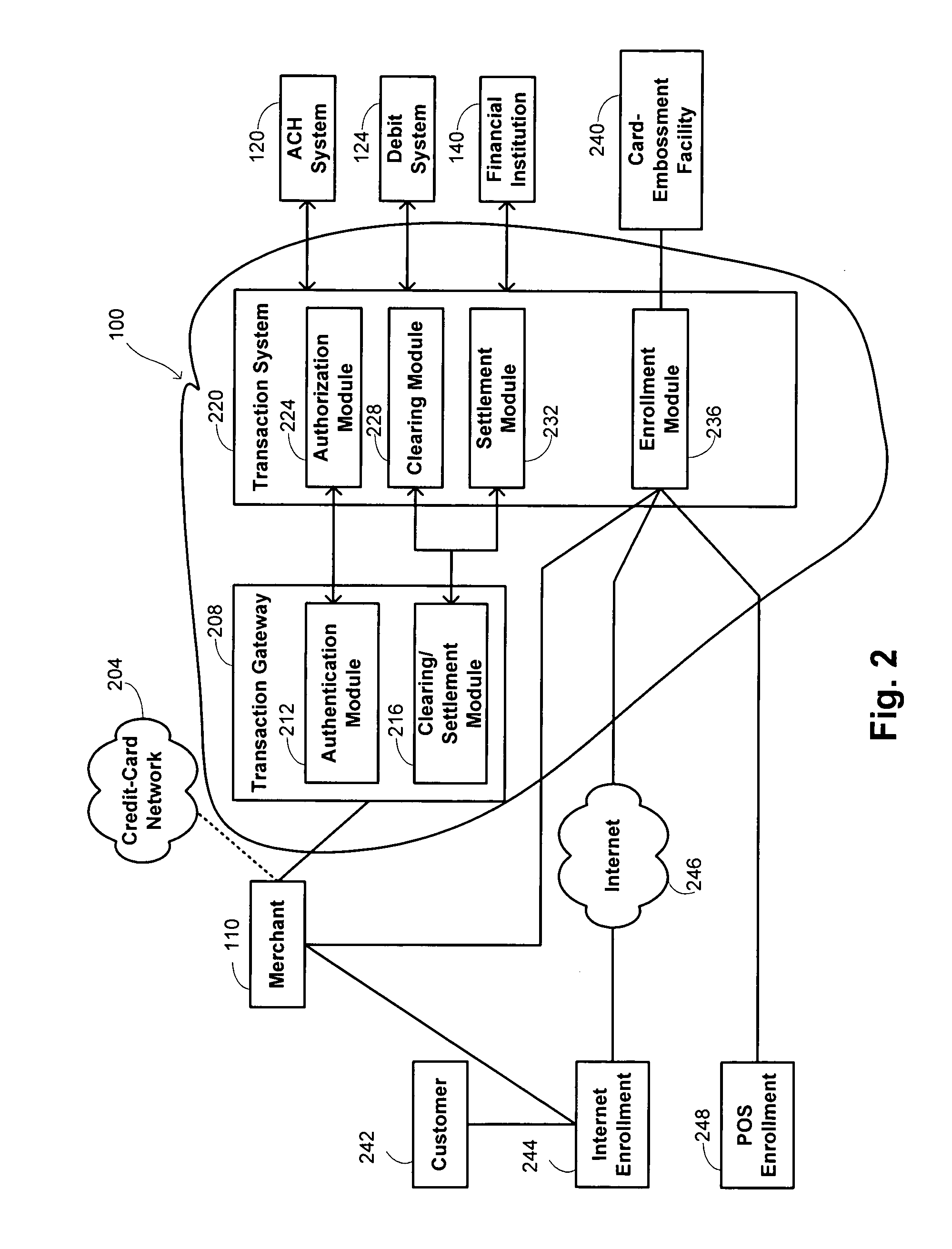
Methods and systems for private label transaction processing
Owner:FIRST DATA
System and method of providing an interface to the internet
InactiveUS20030187739A1AdvertisementsSpecial data processing applicationsInternet privacyApplication software
Owner:POWERS ARTHUR C
Authentication system and method
InactiveUS20090193264A1Digital data authenticationCoded identity card or credit card actuationAuthentication systemStrong authentication
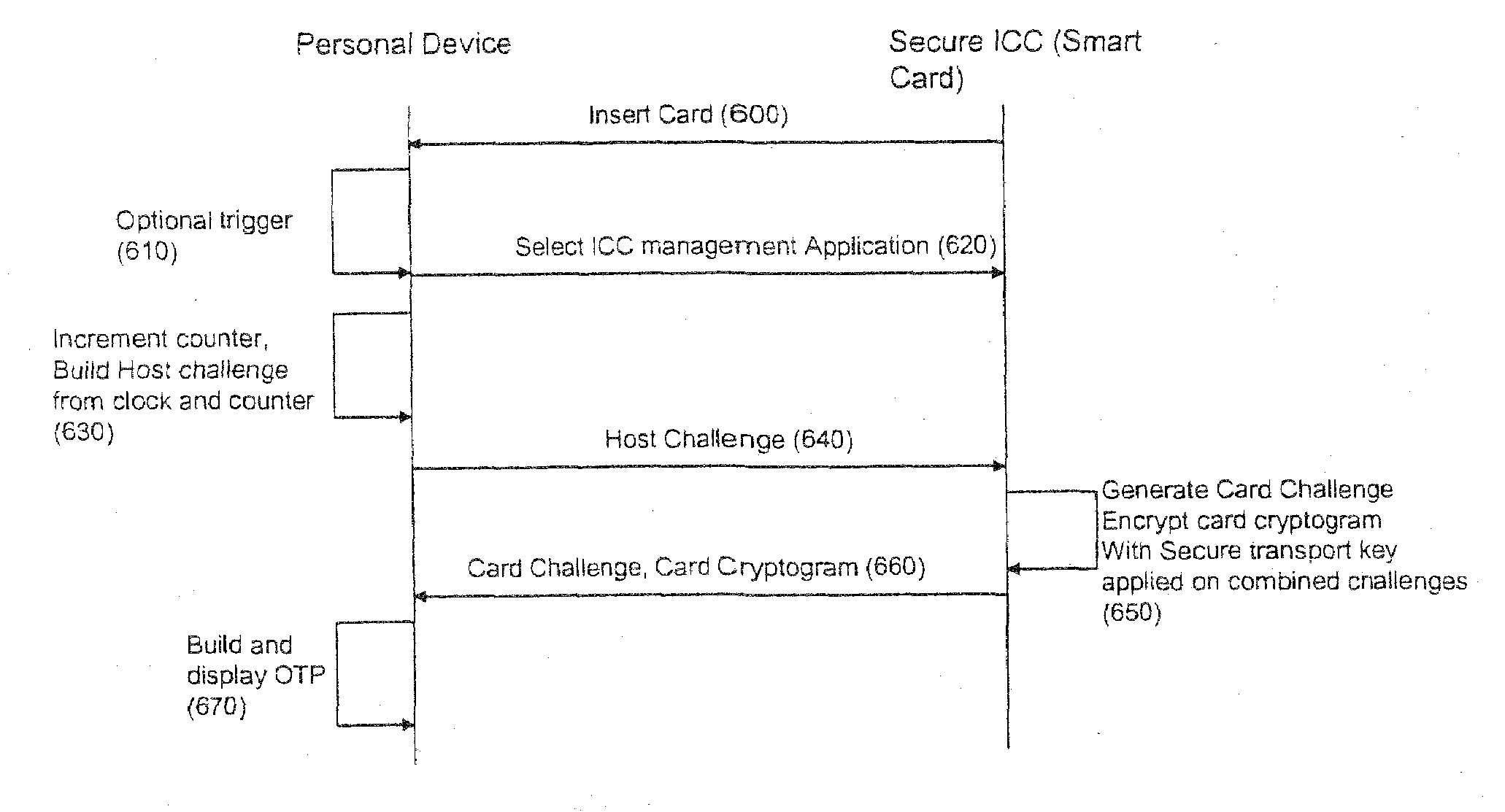
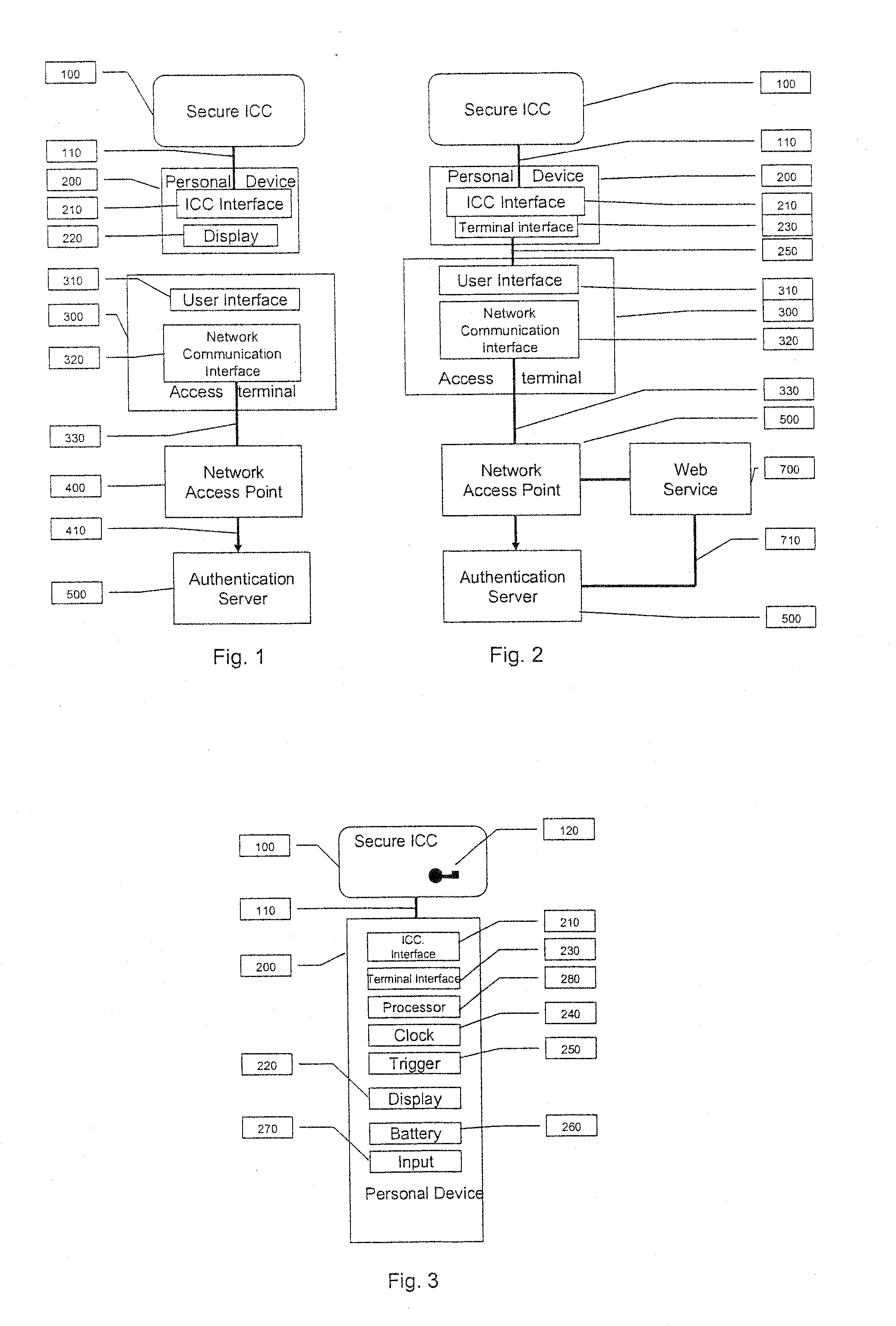
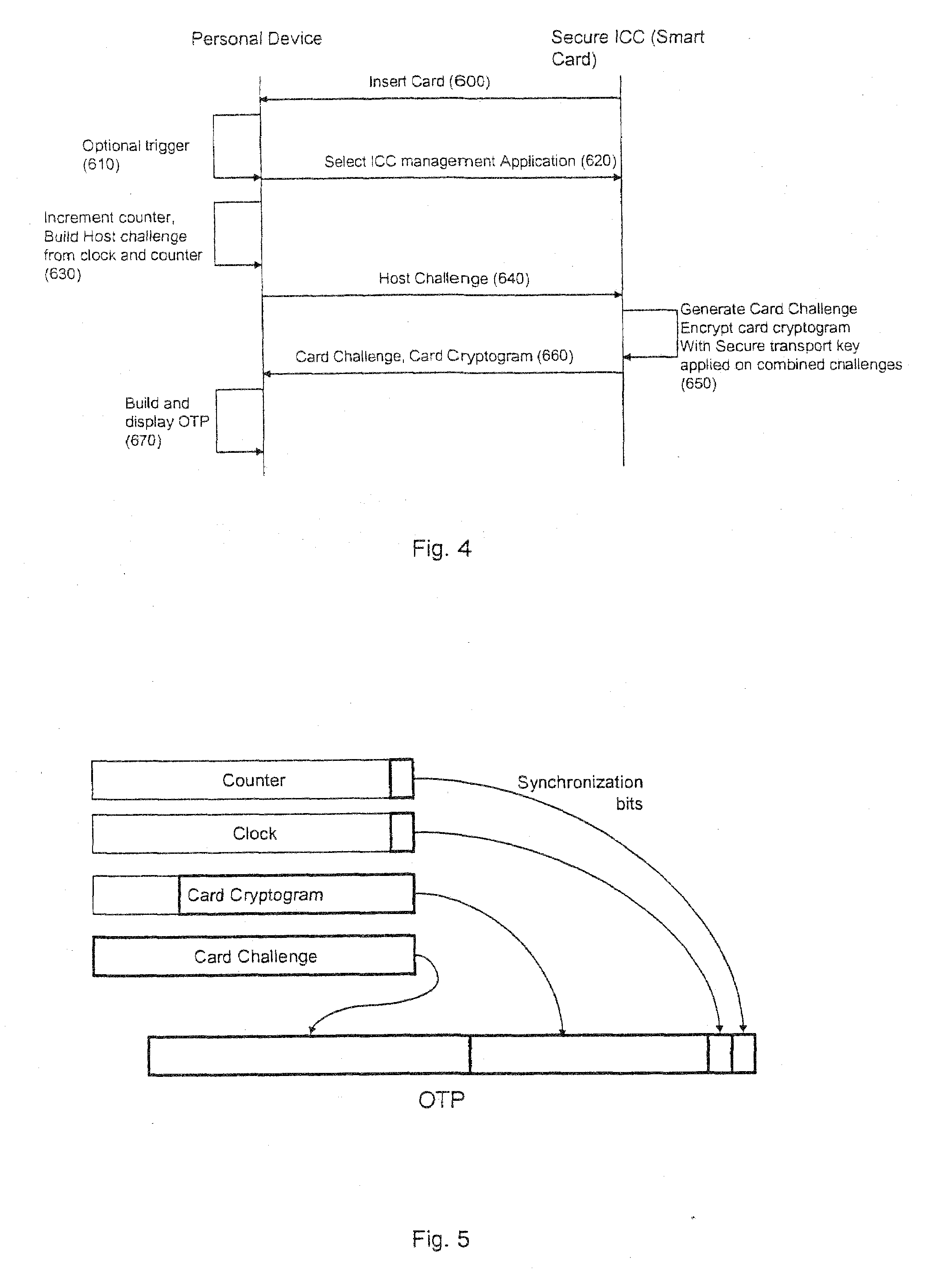
A strong authentication method and system using a Secure ICC component coupled with a Personal device, and relying on the existing cryptographic protocols and keys for managing the secure ICC to generate One-Time-Passwords when the necessary authentication keys or cryptographic protocols are not already present in the Secure ICC configuration for that purpose.
Owner:ACTIVIDENTITY
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS20090182873A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyNetwork behavior
Owner:CONNEXITY AUDIENCE INC
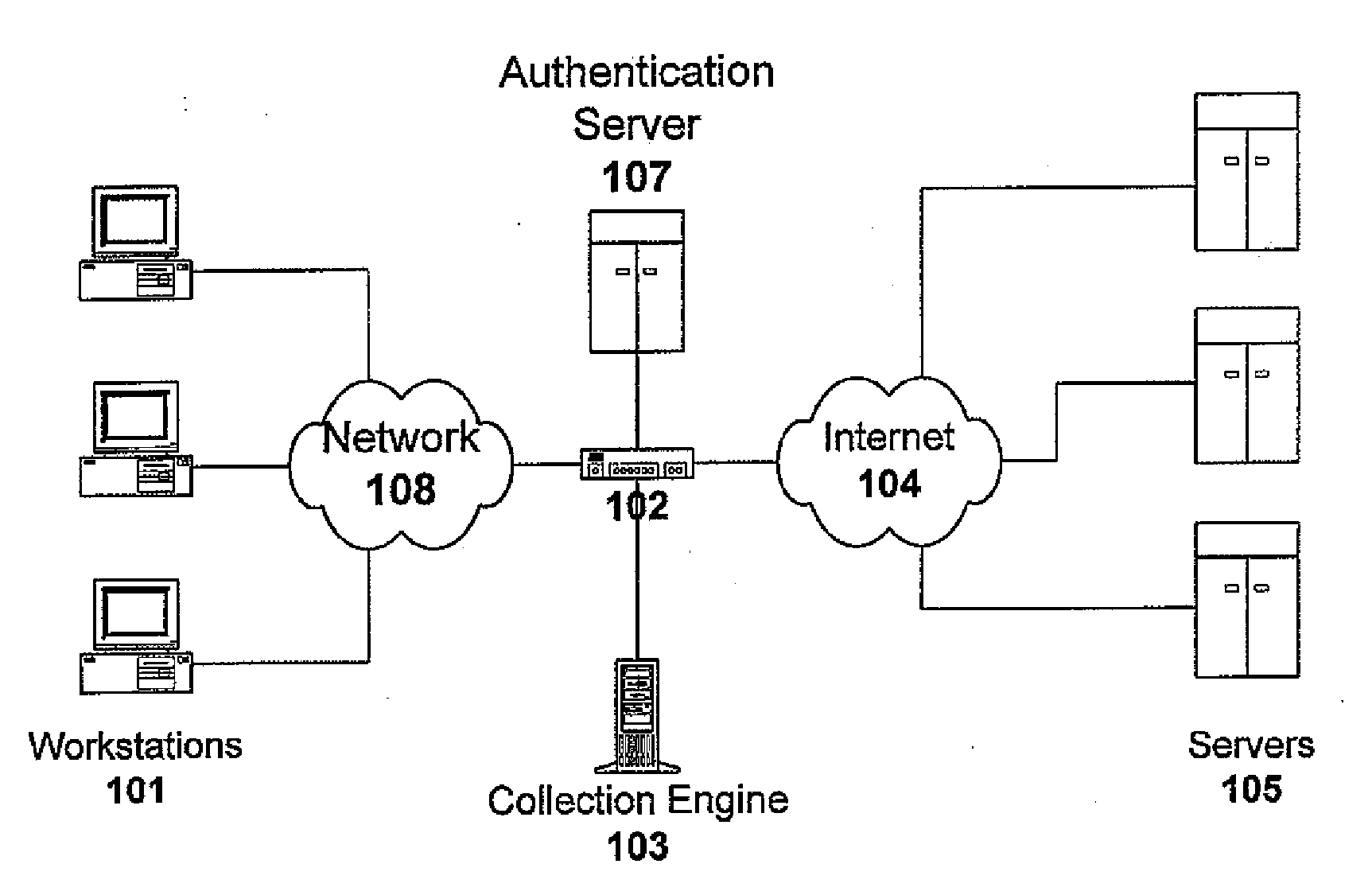
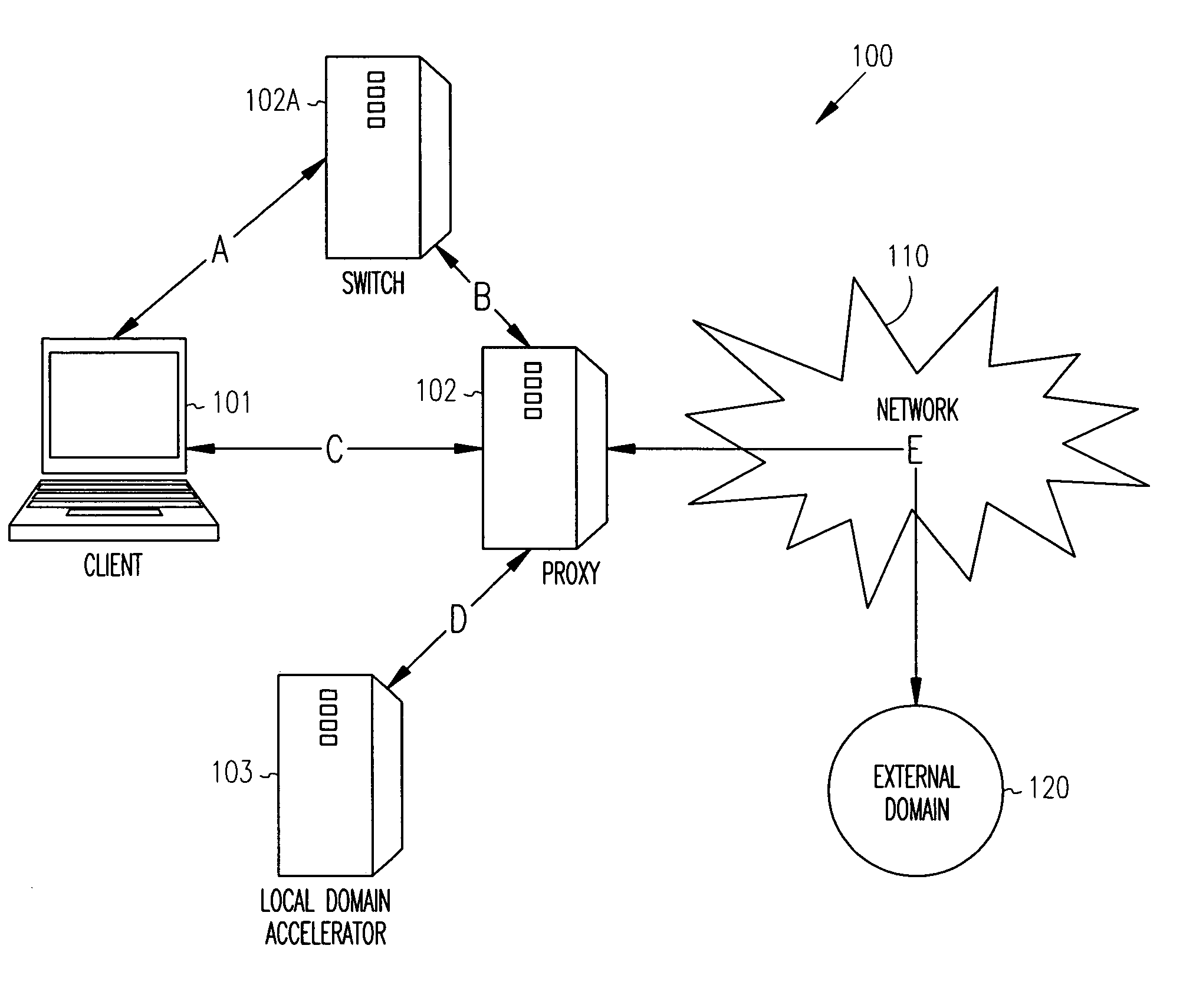
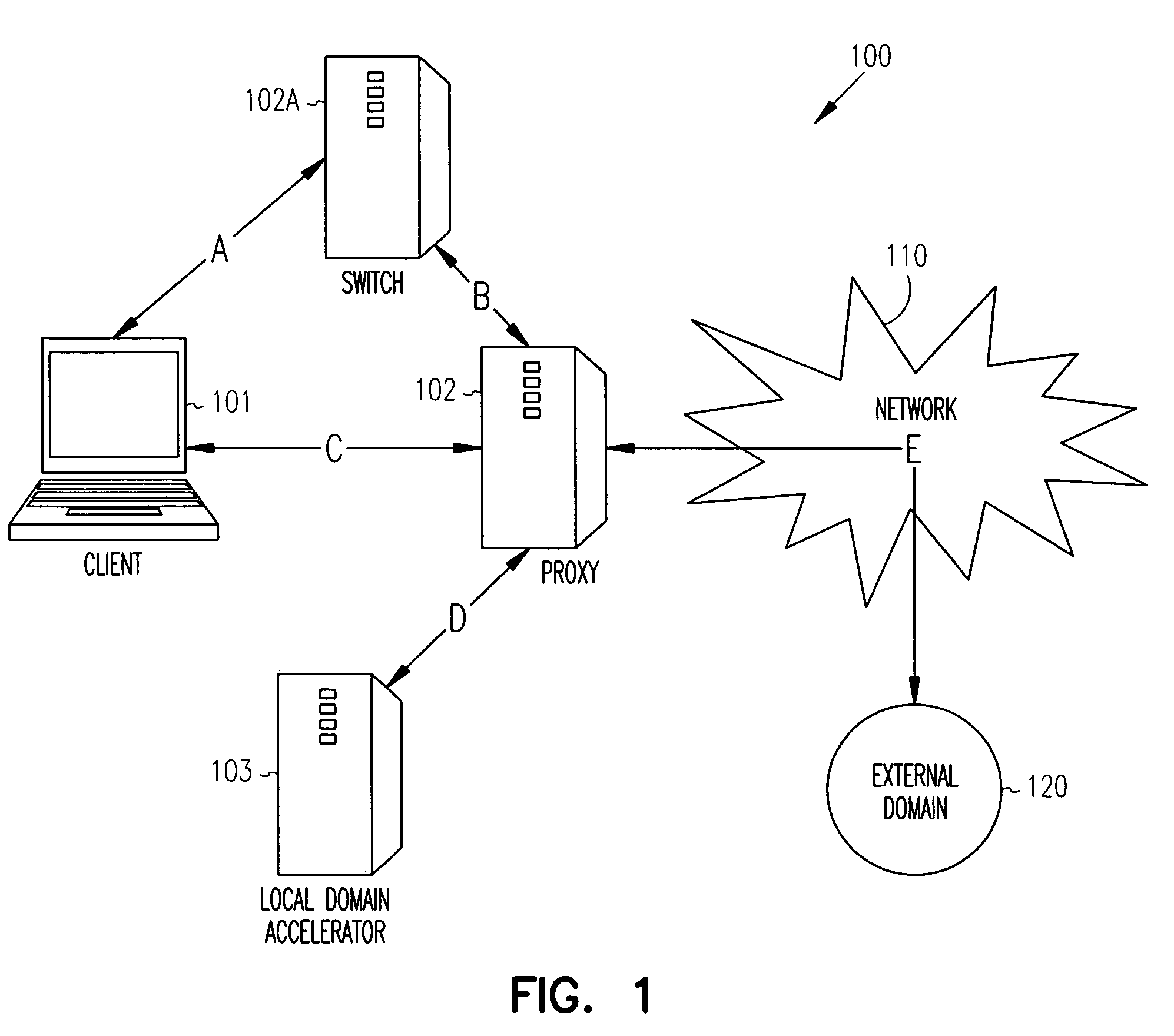
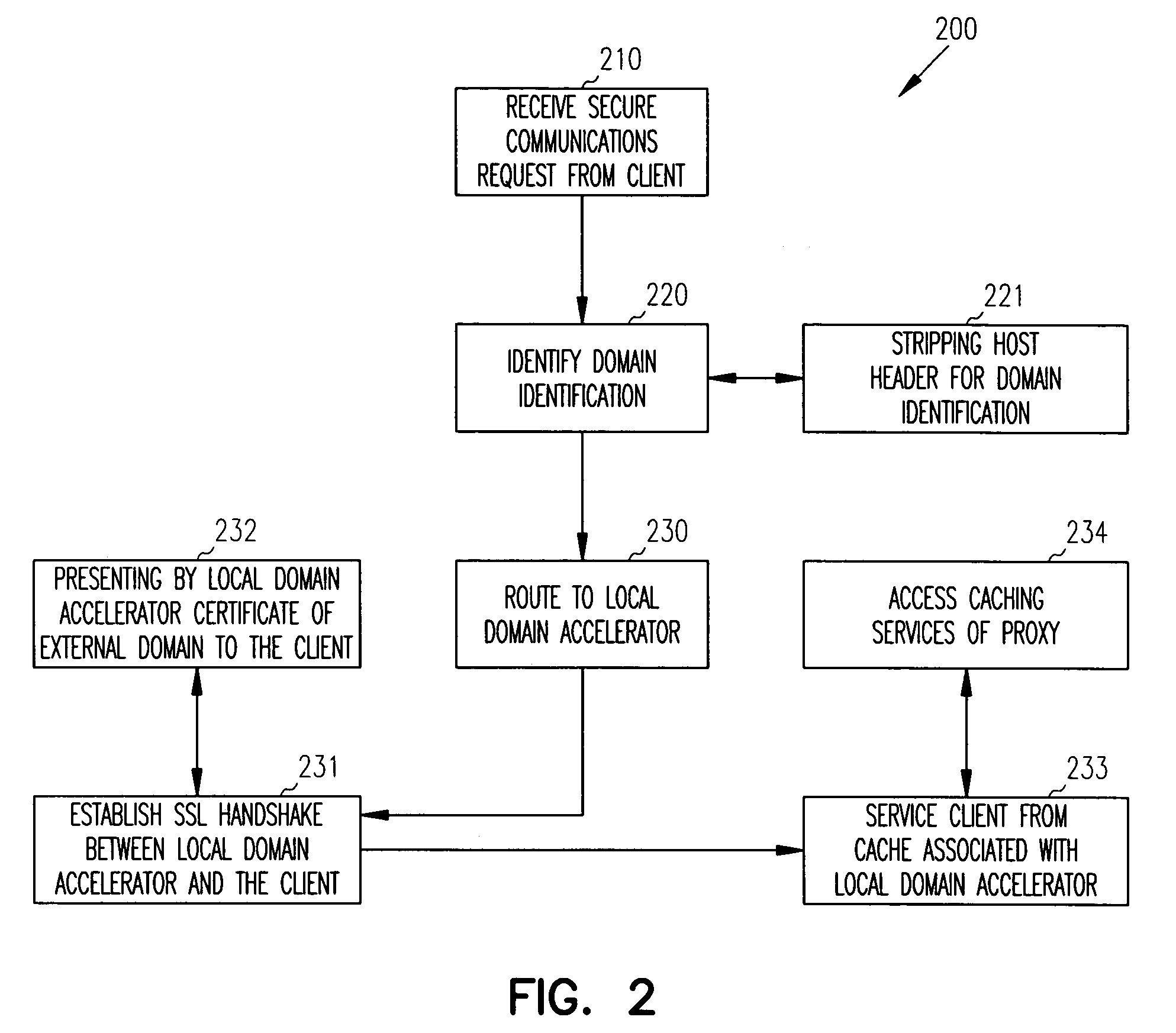
Techniques for securely accelerating external domains locally
InactiveUS7904951B1Multiple digital computer combinationsProgram controlSecure communicationInternet privacy
Owner:RPX CORP
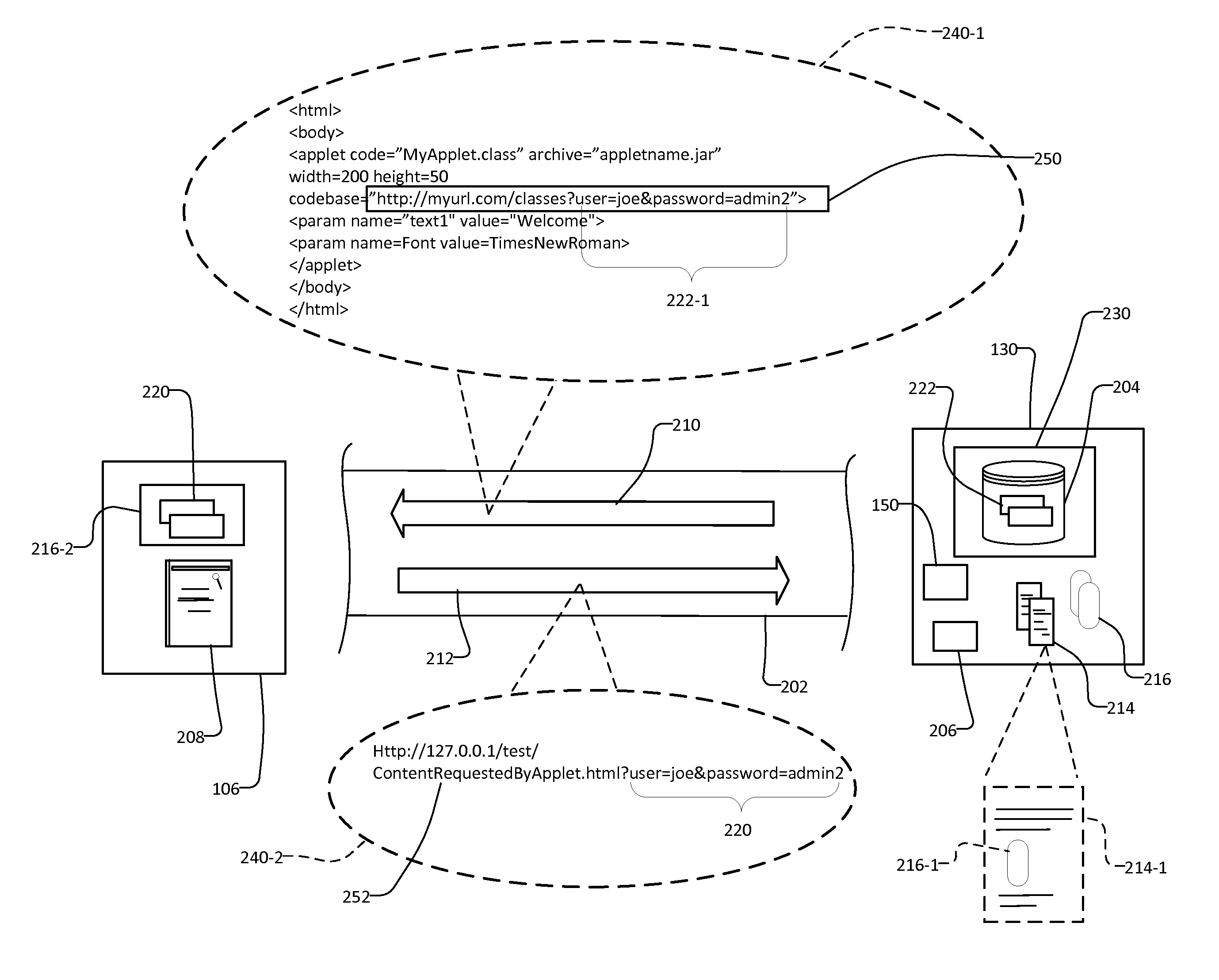
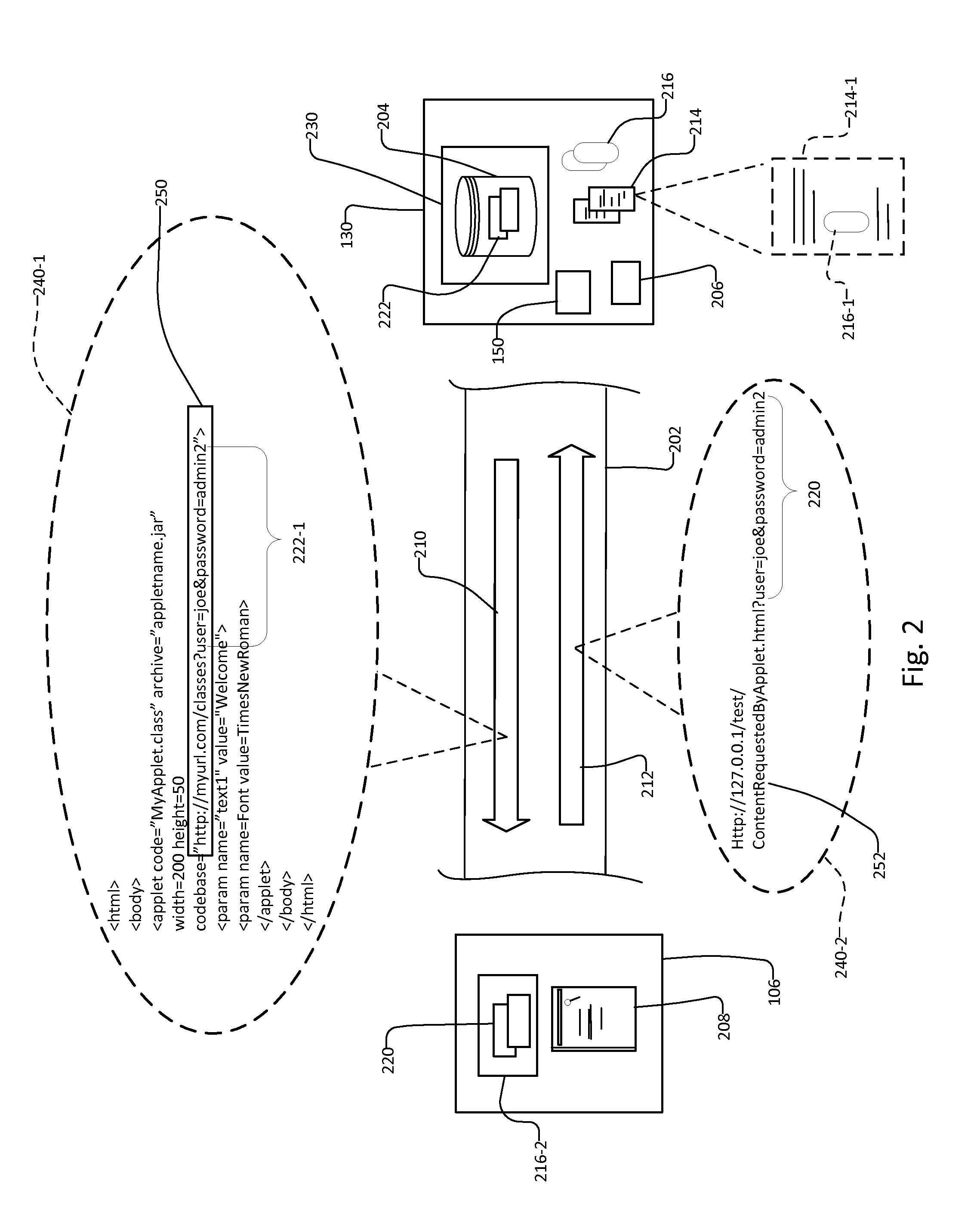
Authentication system and method for embedded applets
ActiveUS20140325627A1Avoiding security pitfallEliminate needDigital data processing detailsMultiple digital computer combinationsUser deviceInternet privacy
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
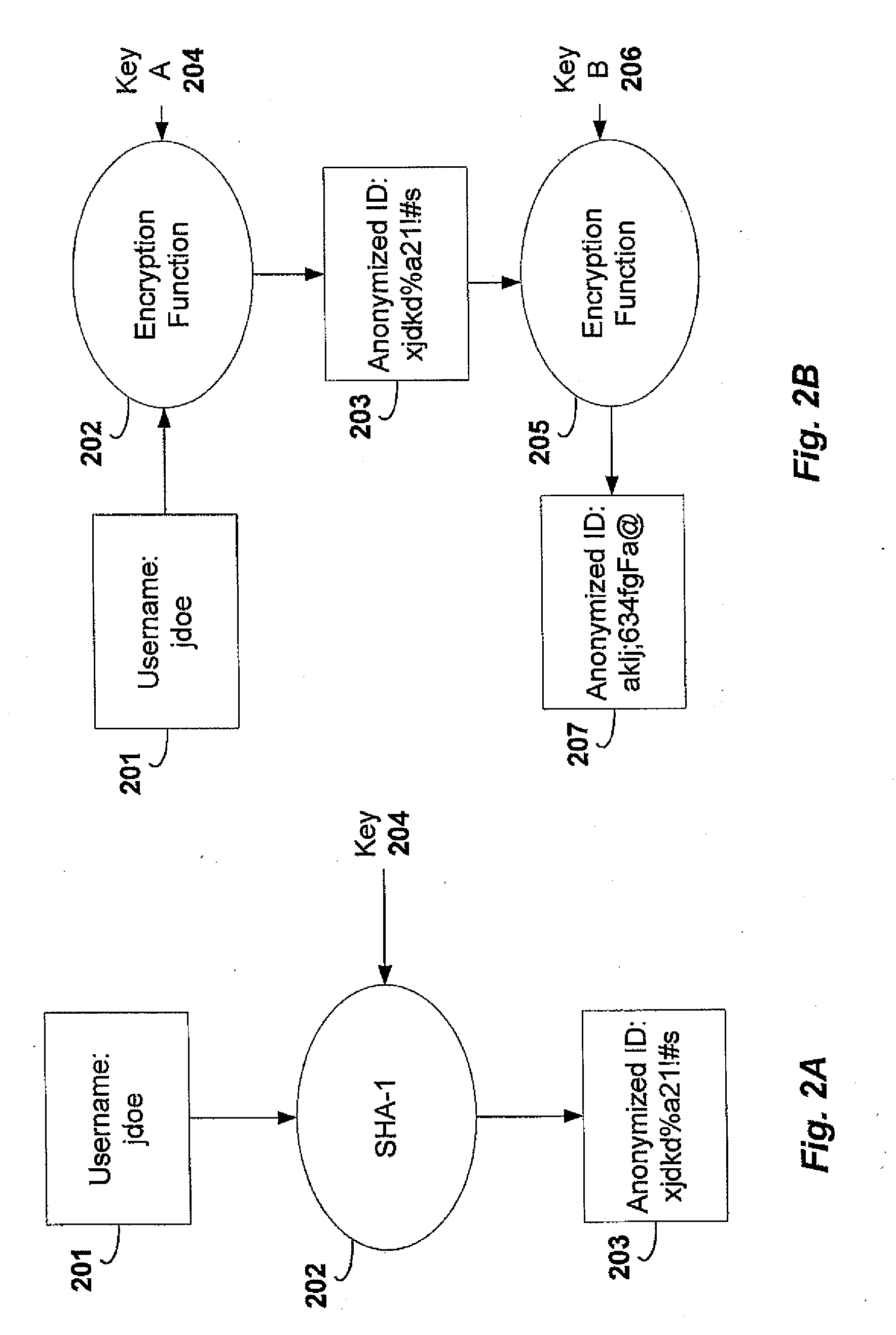
Method for authenticating user's ID in safety communication service of public network based on cryptotechnique of identification
ActiveCN1697379APublic key for secure communicationUser identity/authority verificationHandsetInternet privacy
Owner:SHENZHEN OLYM INFORMATION SECURITY TECHOLOGY CO LTD
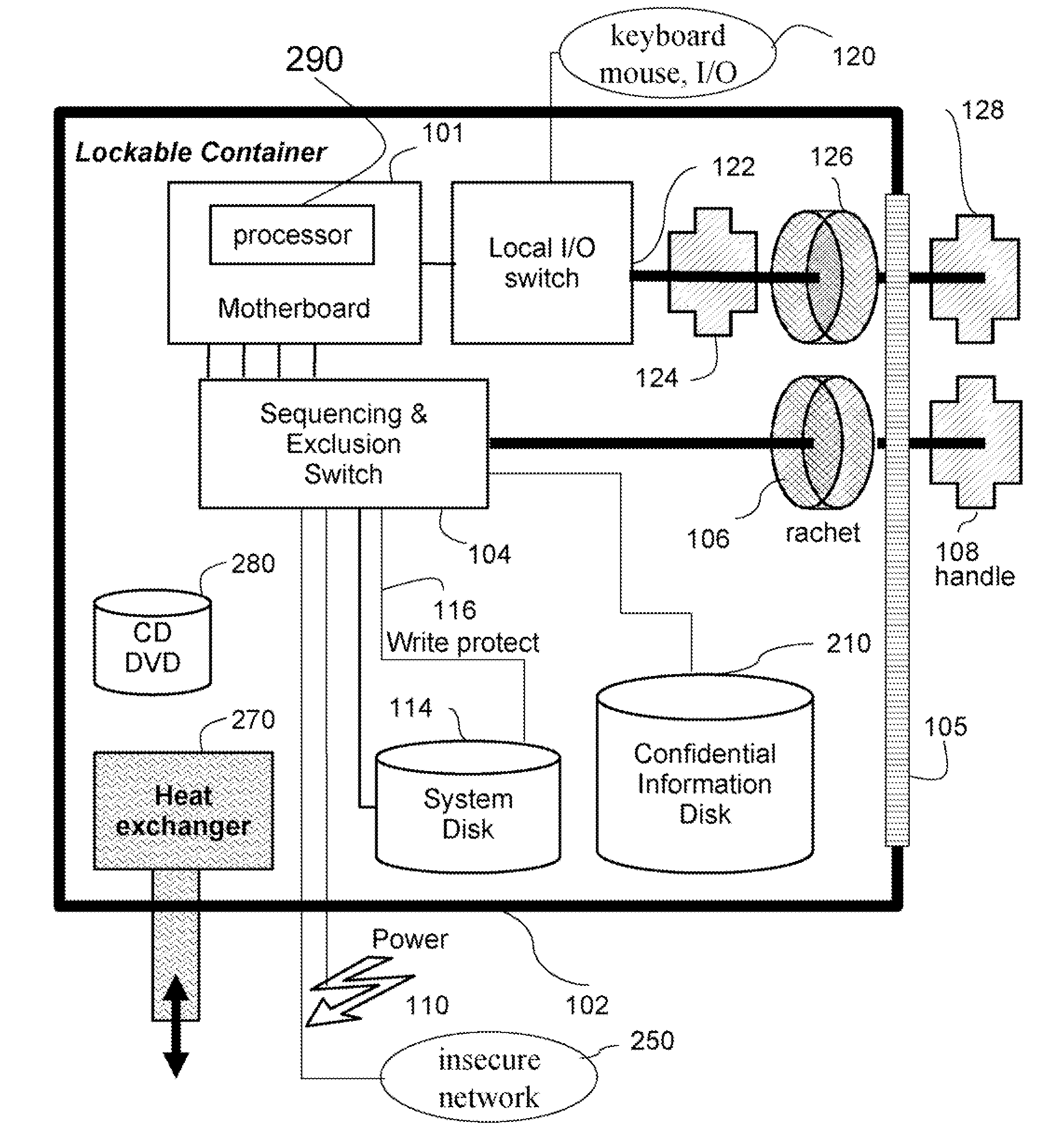
Secure Computer System and Method
InactiveUS20090165139A1Desired secure computing propertiesDigital data processing detailsAnalogue secracy/subscription systemsMagnetic disksInternet privacy
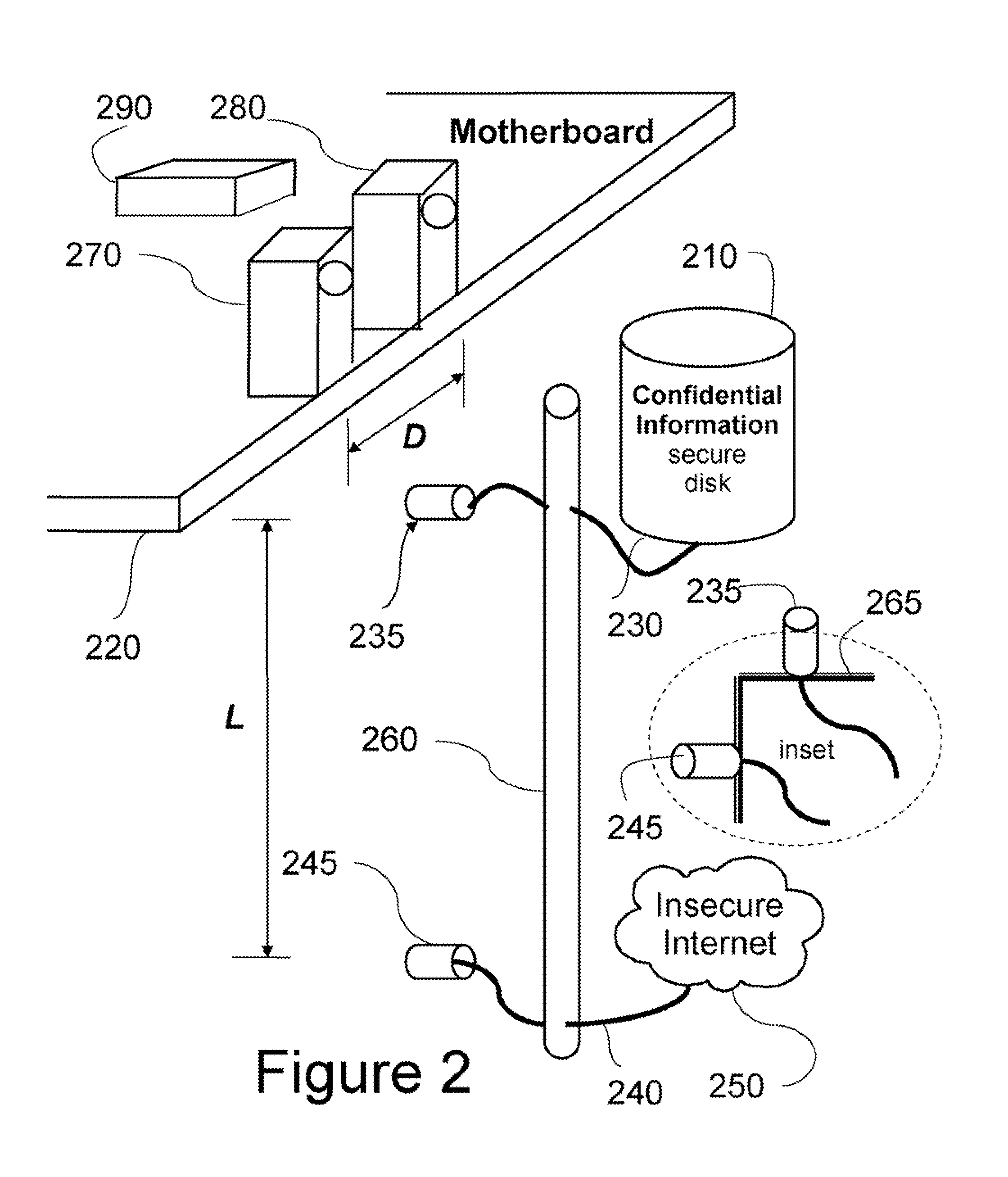
An apparatus is configured to perform secure processing of confidential information. The apparatus comprises a secure disk configured to store confidential information arranged inside a lockable container; a processor configured to process the confidential information arranged inside the lockable container; an insecure network arranged outside the lockable container; and means for connecting the processor only to the secure disk or alternatively to the insecure network at any one time, but not to both the secure disk and the insecure network at the same time.
Owner:MITSUBISHI ELECTRIC RES LAB INC
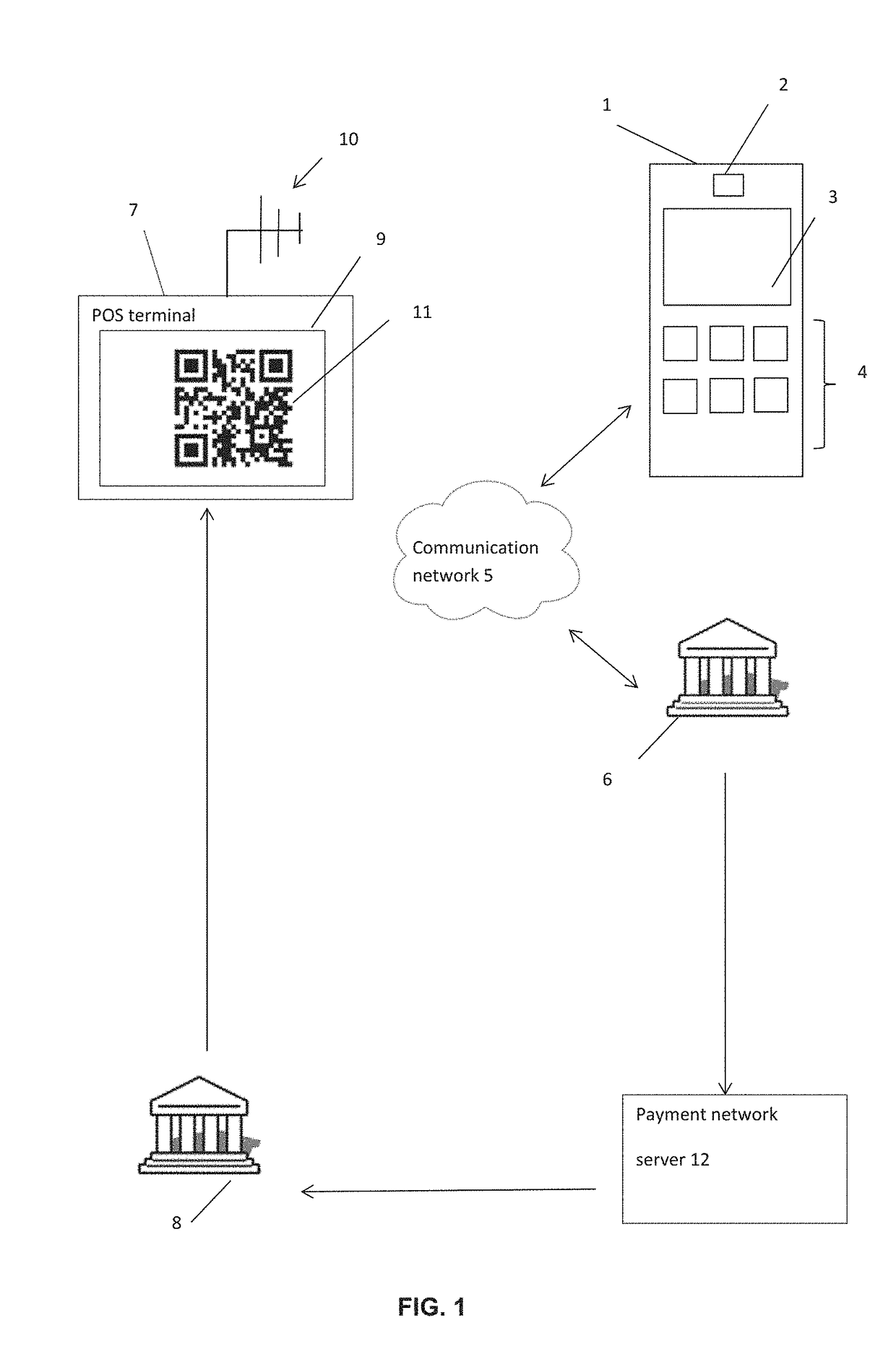
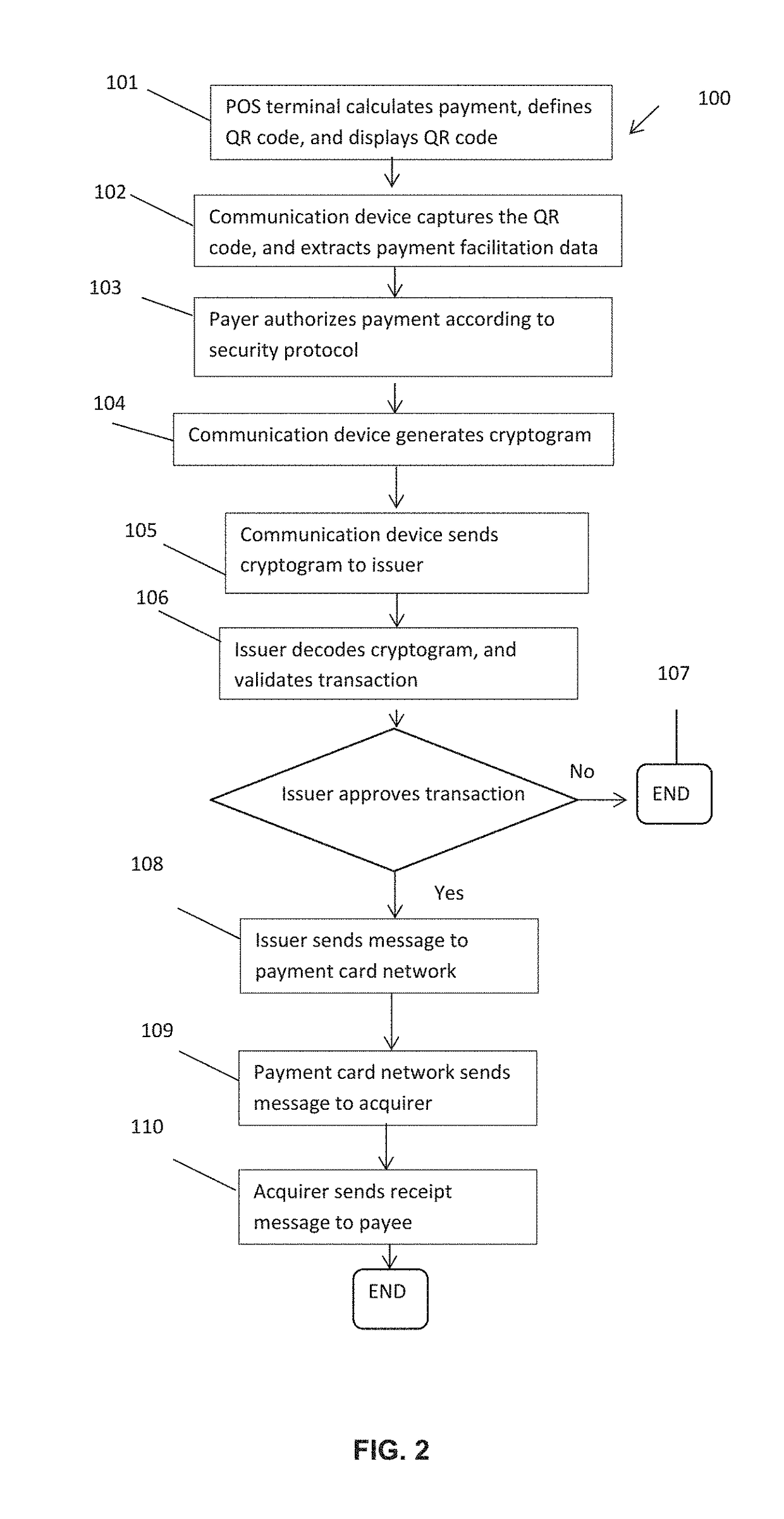
Methods and systems for making a payment
ActiveUS20170178097A1Lighten the computational burdenOvercome expensiveBuying/selling/leasing transactionsPoint-of-sale network systemsInternet privacyMonetary Amount
Owner:MASTERCARD INT INC
Register and login system and method for biological characteristic distributed identity authentication
Owner:掌握科技无锡有限公司
Systems and methods for managing data items using structured tags
InactiveUS20130346405A1Digital data processing detailsMultiple digital computer combinationsInternet privacyComputerized system
Owner:APPSENSE
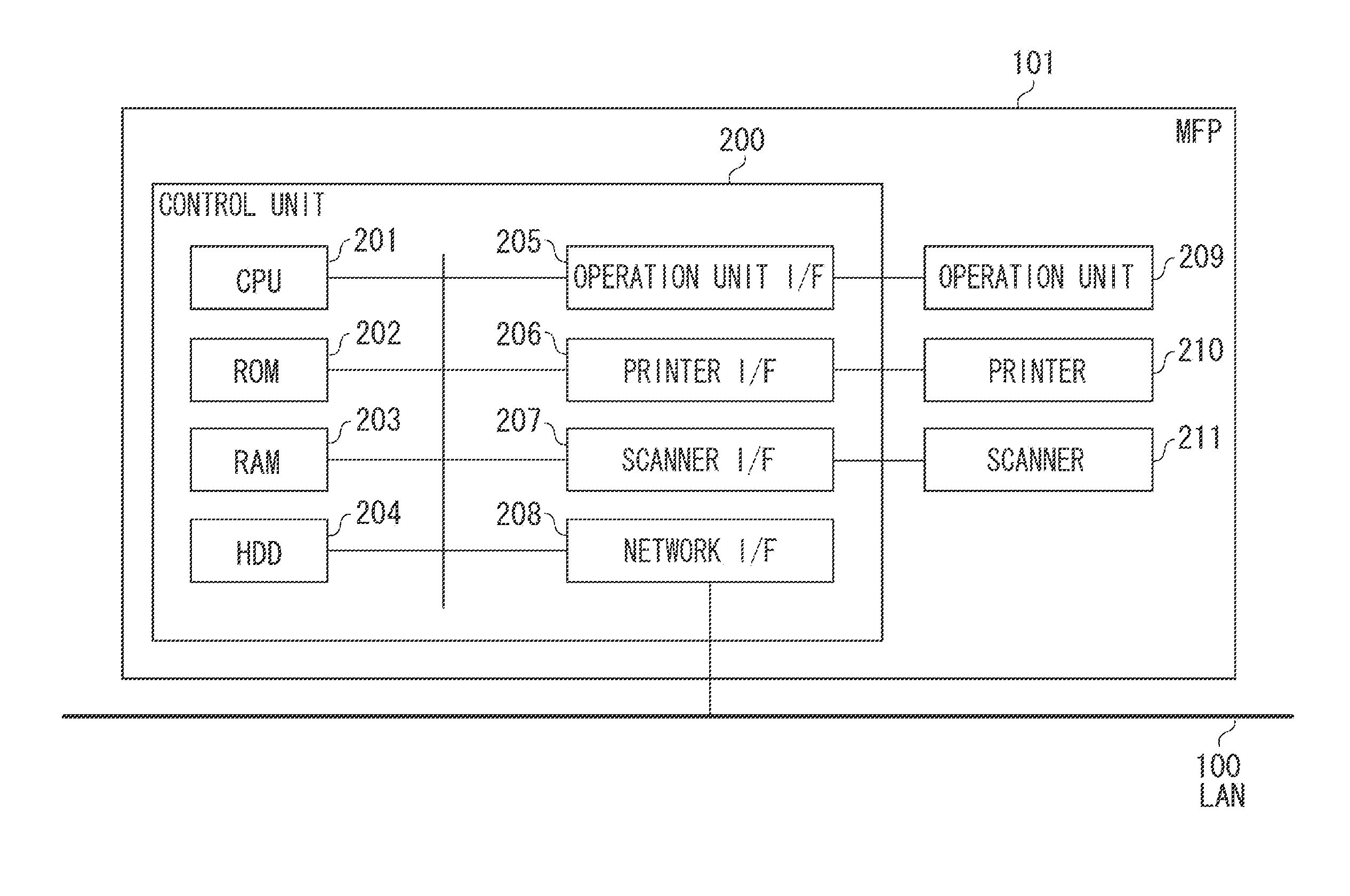
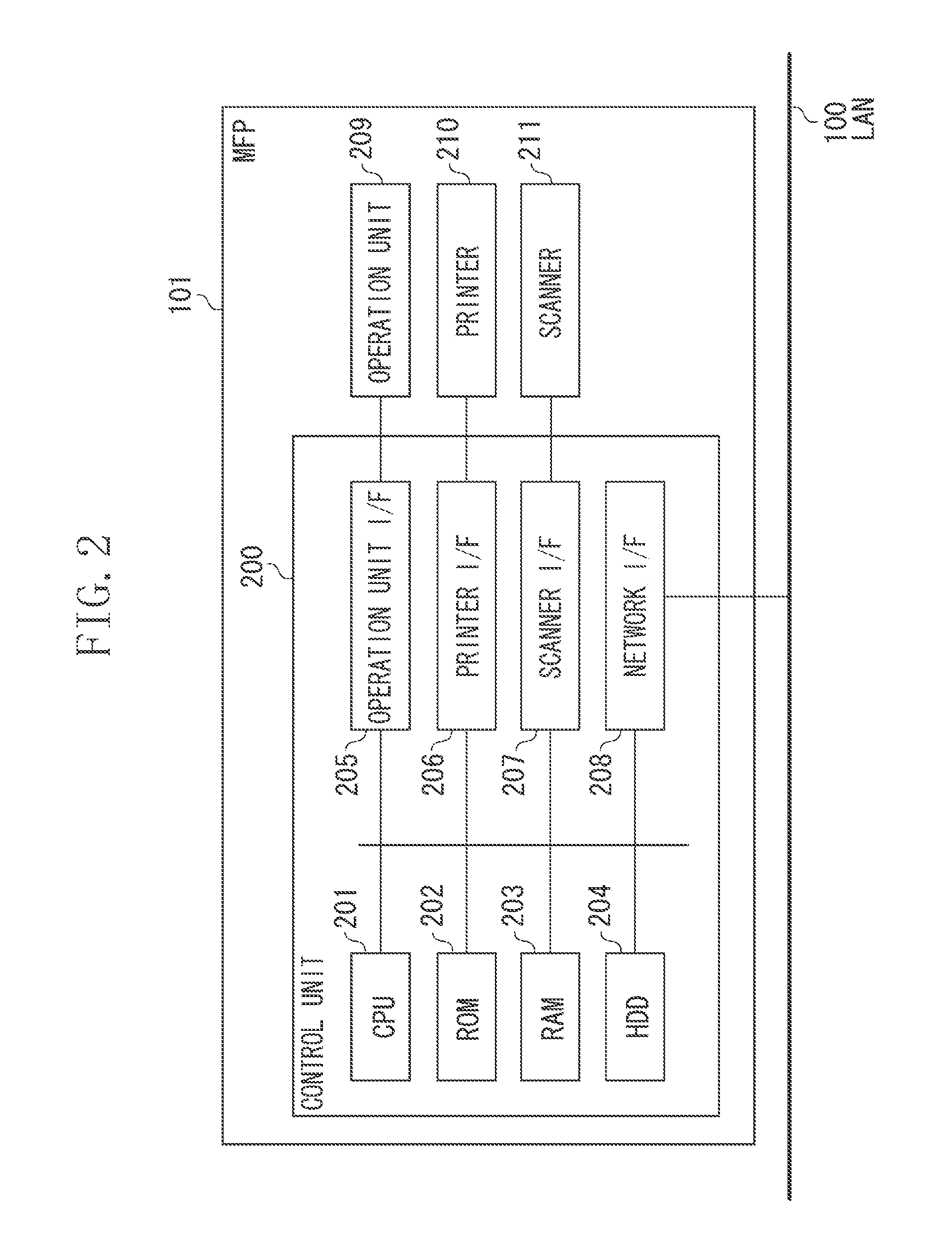
Information processing apparatus, method for controlling information processing apparatus, and storage medium
ActiveUS20170013170A1Digital data authenticationInput/output processes for data processingInformation processingInternet privacy
Owner:CANON KK
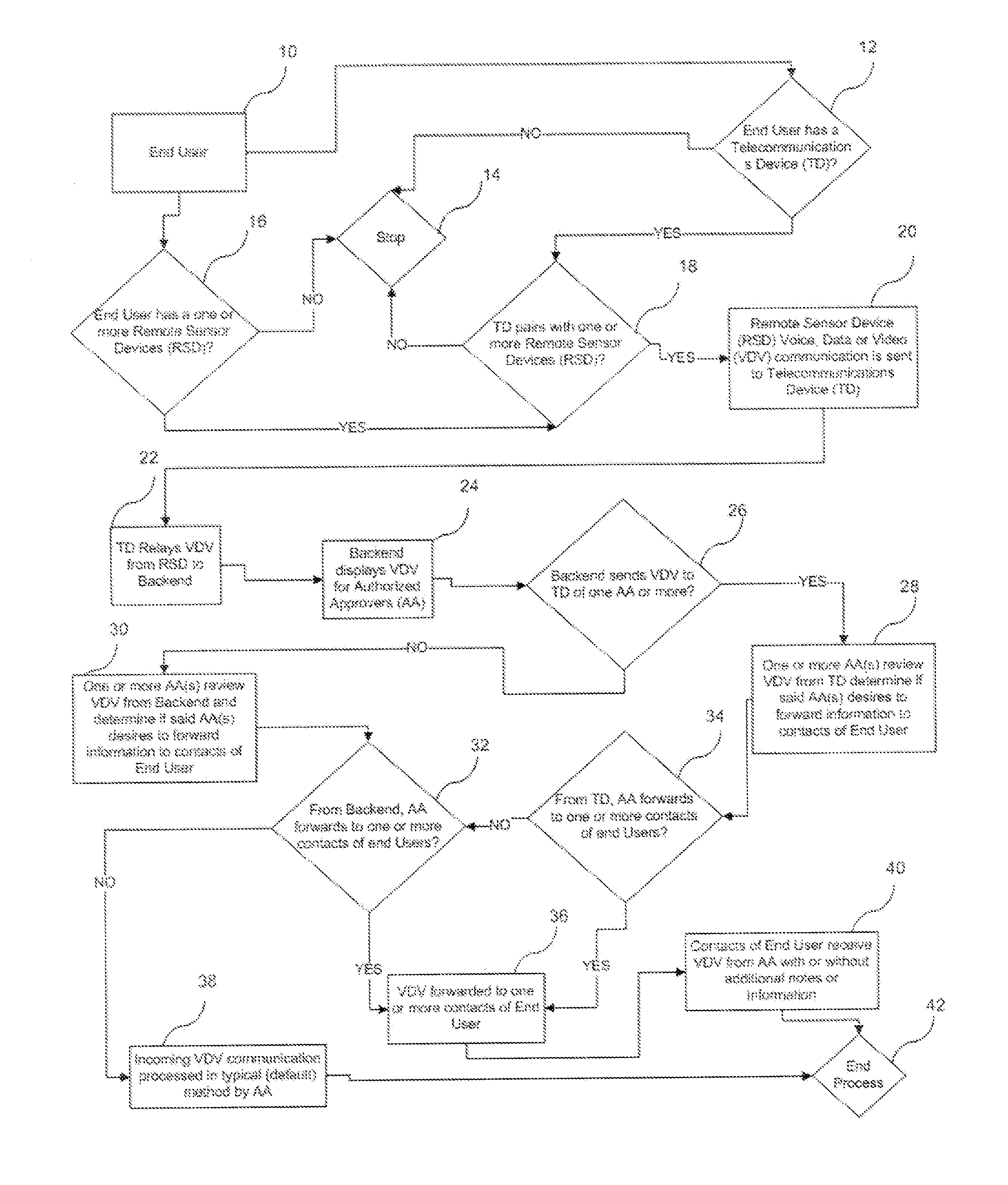
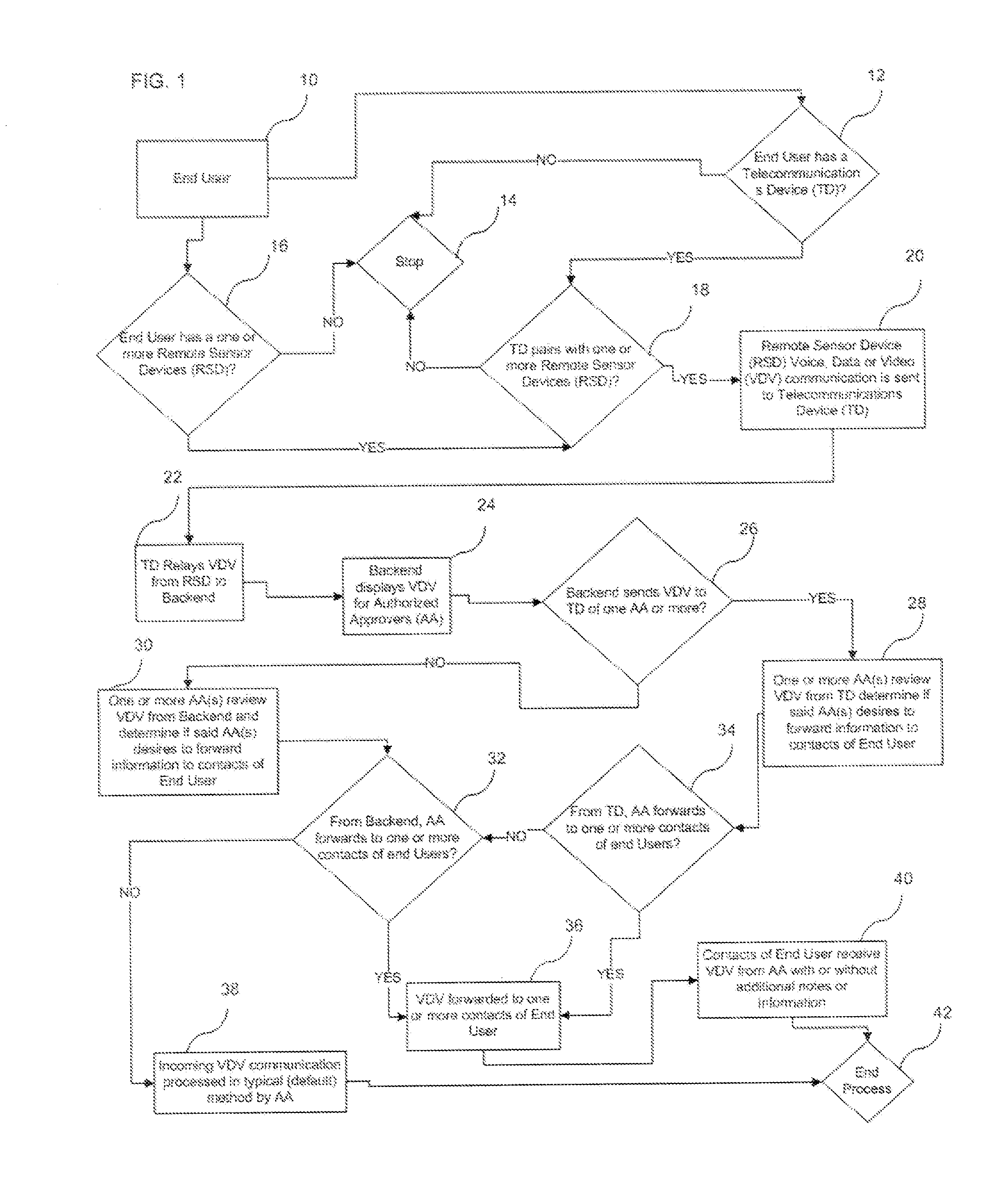
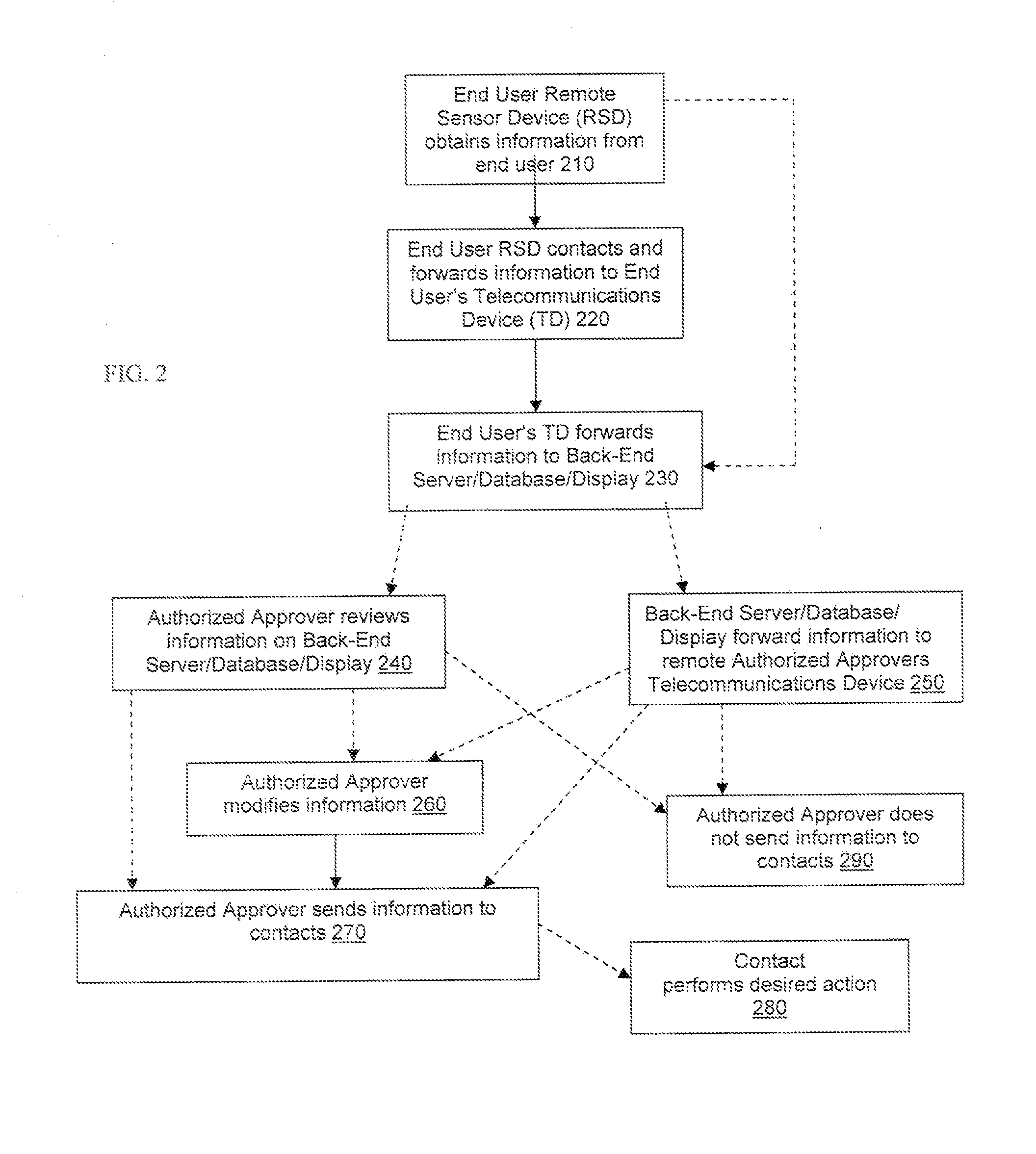
System and Method for Transmitting User Data Received by an Authorized Approver
Owner:RICORDI CAMILLO +2
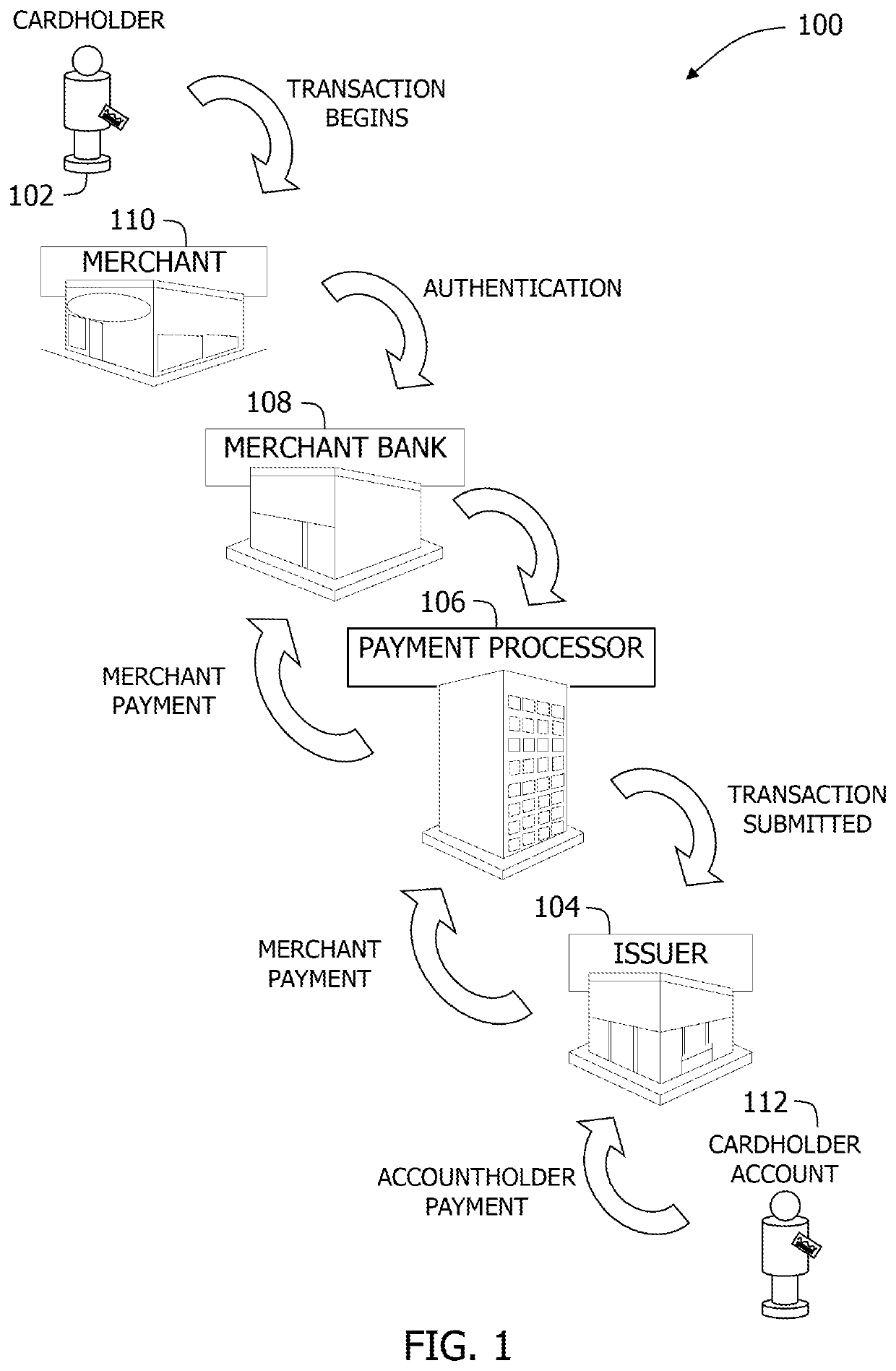
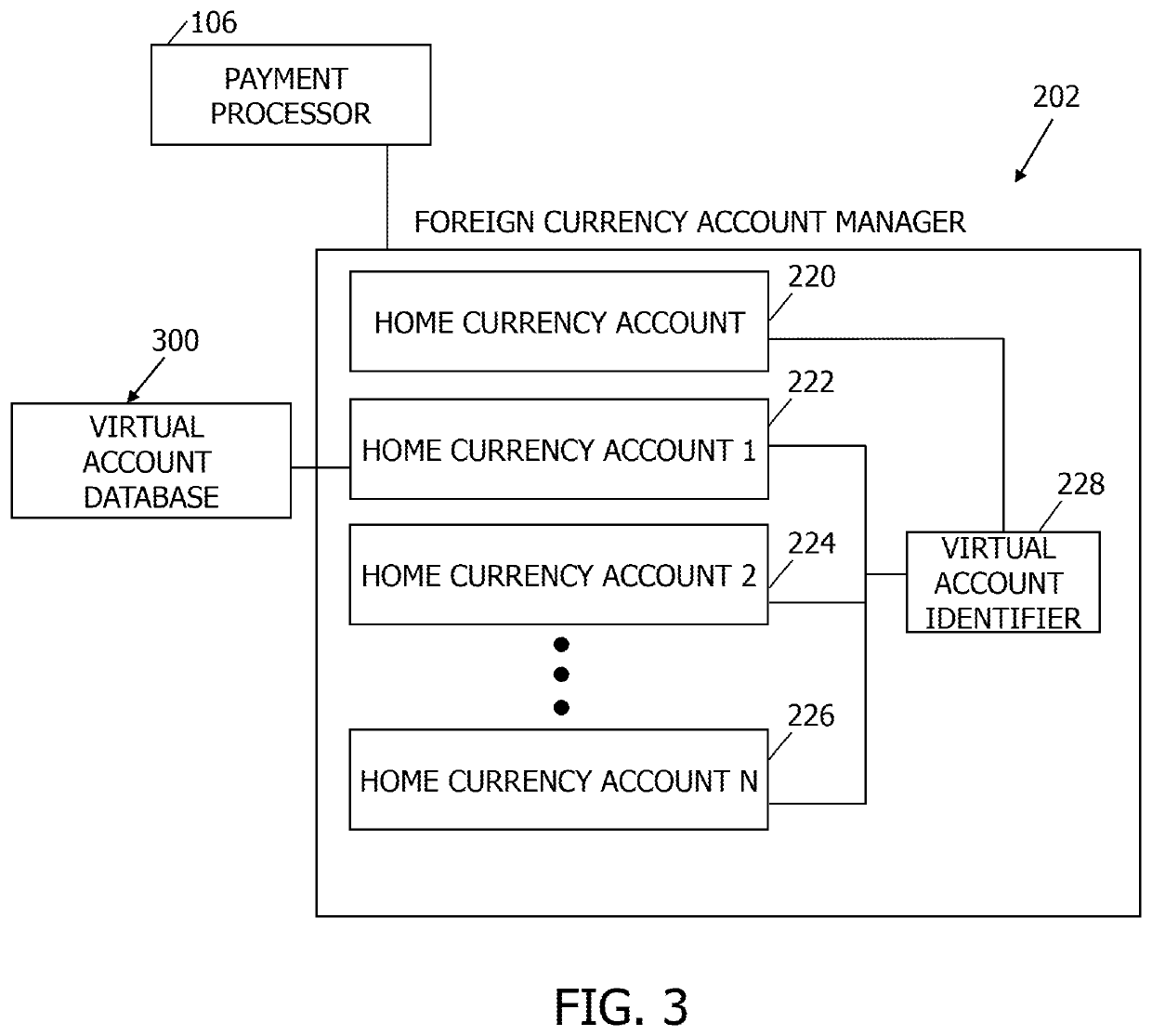
Multi-party payment card processing systems and methods including virtual prepaid foreign currency account management
Owner:MASTERCARD INT INC
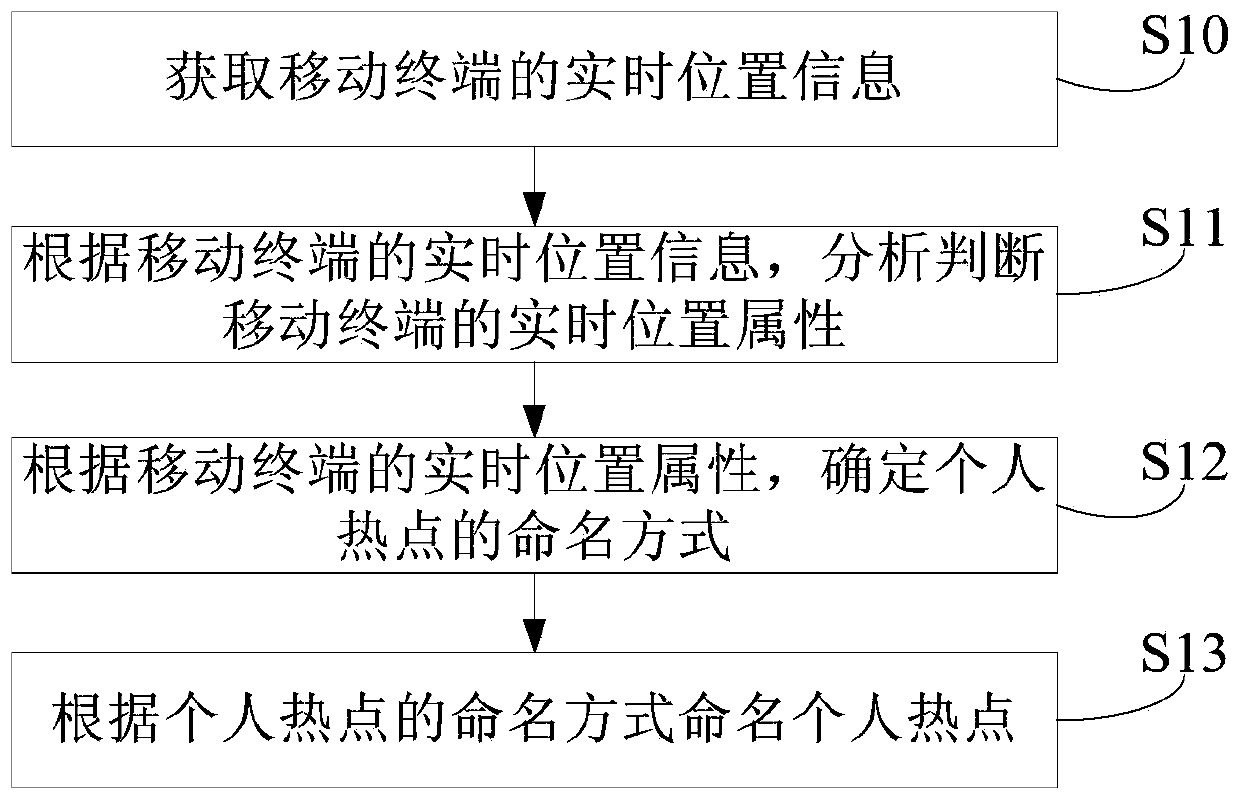
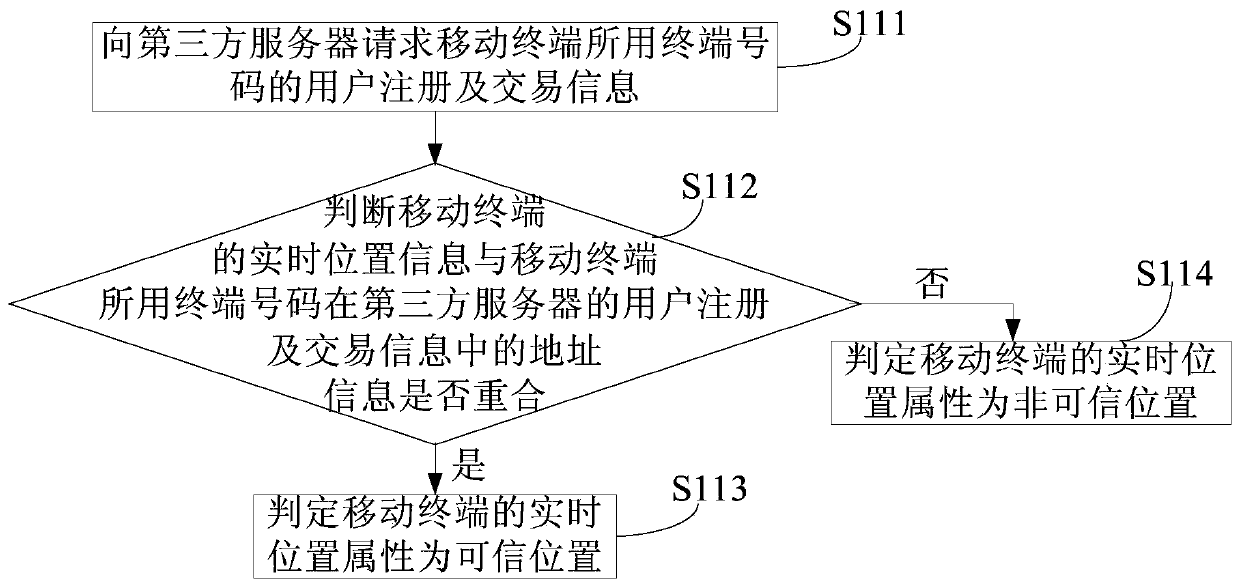
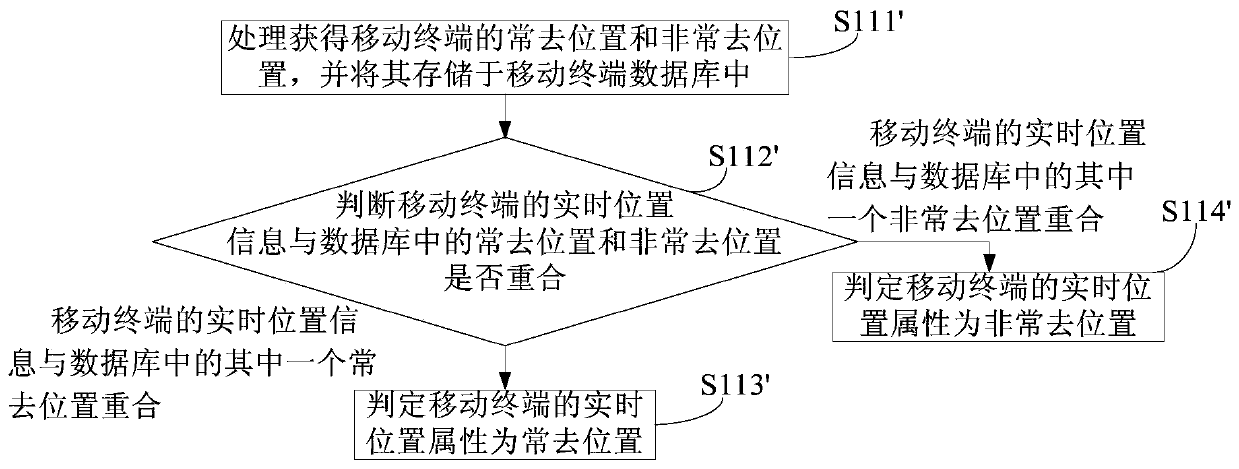
Personal hotspot naming method, mobile terminal and personal hotspot naming system
ActiveCN110636524AReduce the need to manually modify the name of the Personal HotspotImprove user experienceLocation information based servicePersonalizationComputer network
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
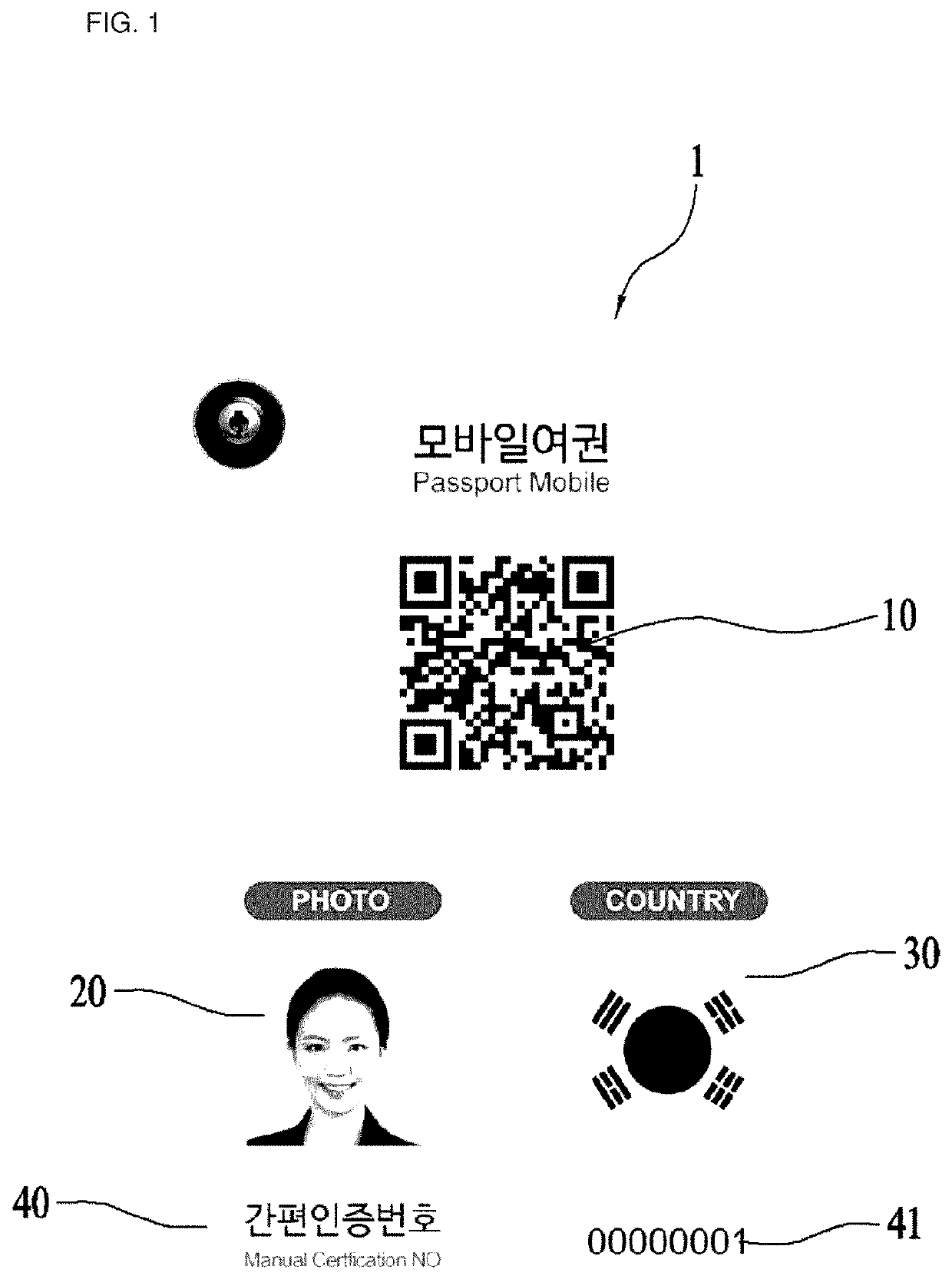
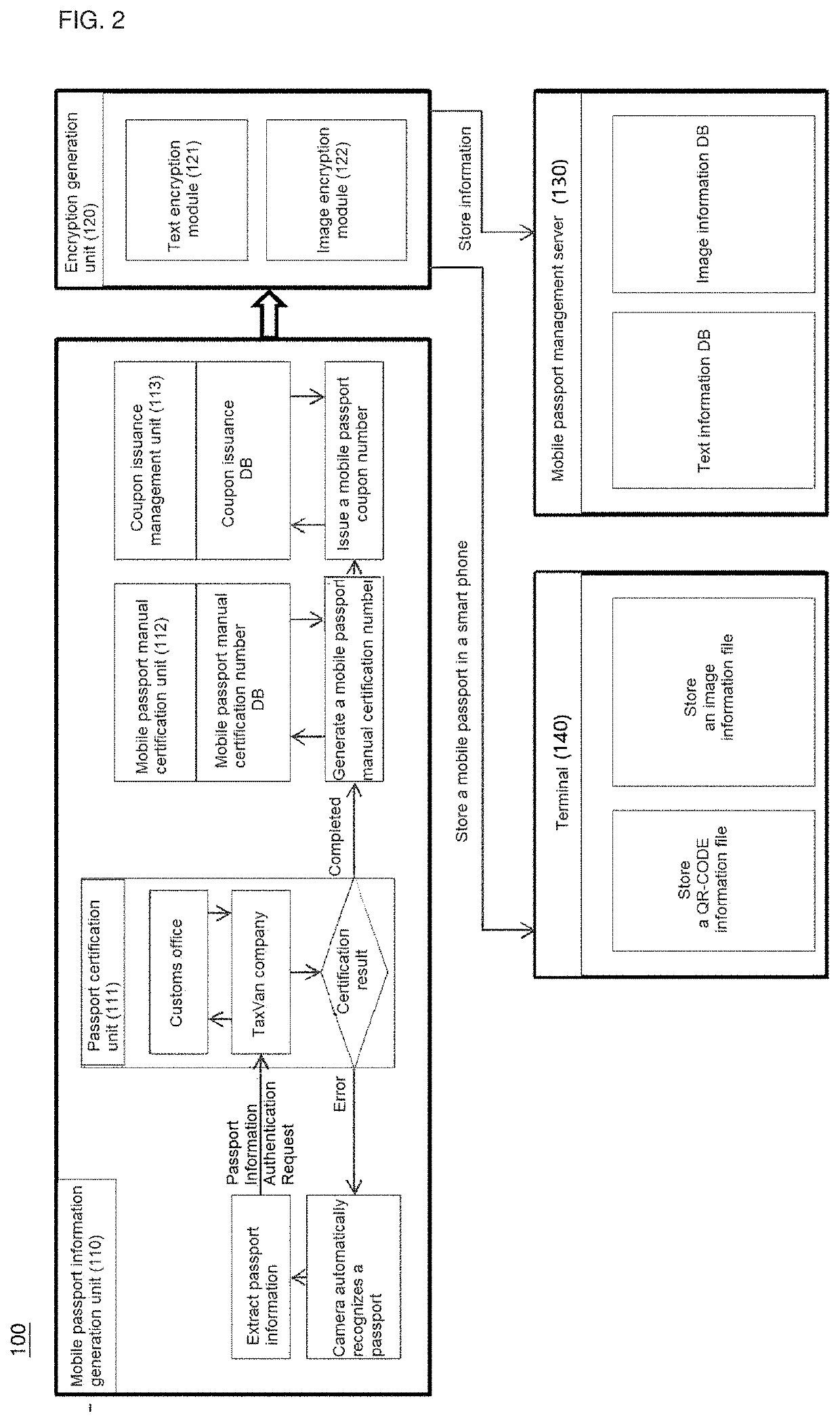
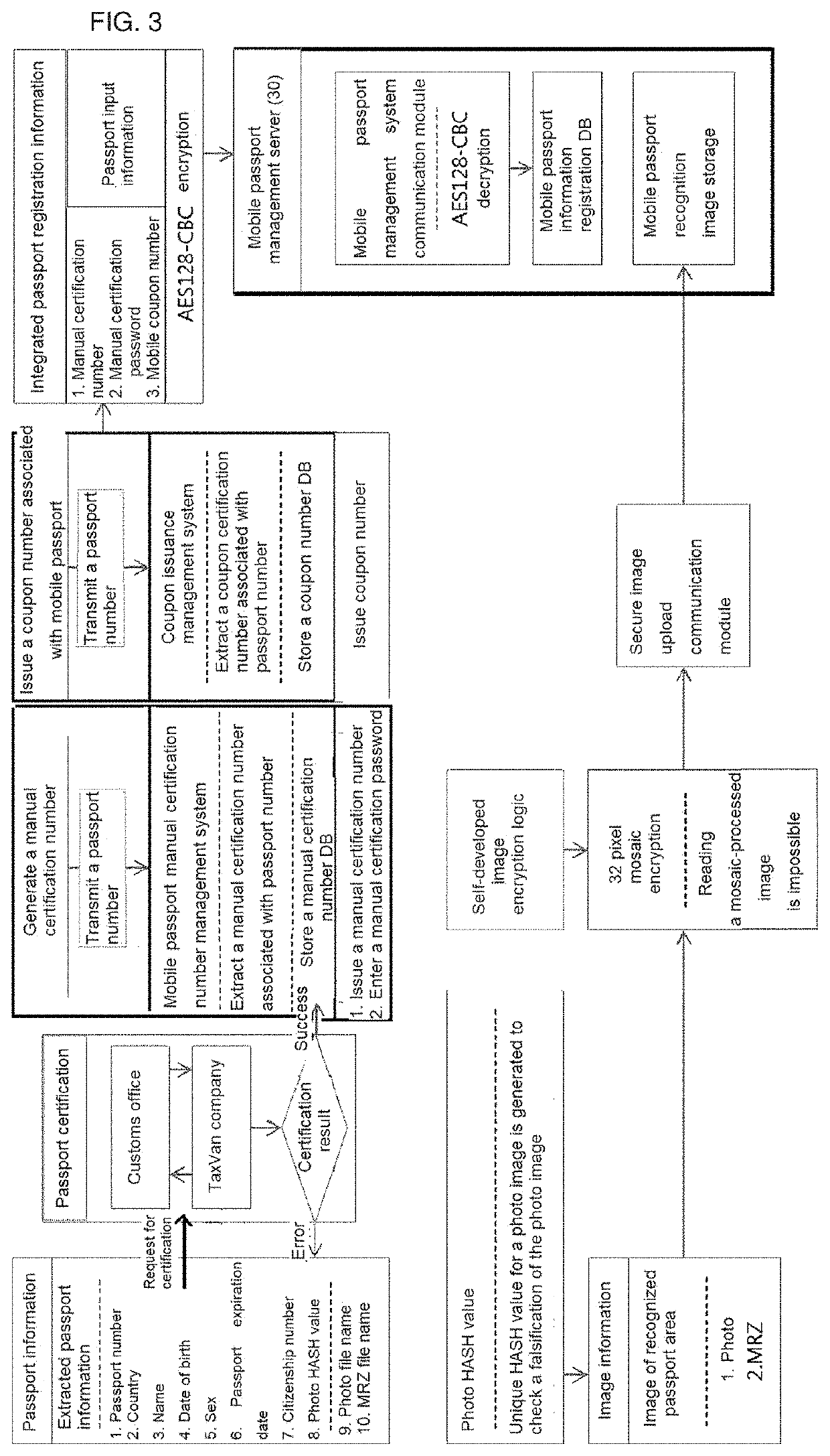
Mobile passport, mobile passport generation system for generating same, and mobile passport certifcation method
PendingUS20210042600A1Easy extractionPromote generationFinanceEncryption apparatus with shift registers/memoriesInternet privacyEngineering
Owner:LORDSYST CO LTD
Information encryption, decryption and control method and device and electronic equipment
InactiveCN112260832AImplement the encryption functionImplement the decryption functionKey distribution for secure communicationTelevision conference systemsStationInternet privacy
Owner:南京易科腾信息技术有限公司
Smart home control methods and smart home control system
Owner:星络智能科技有限公司
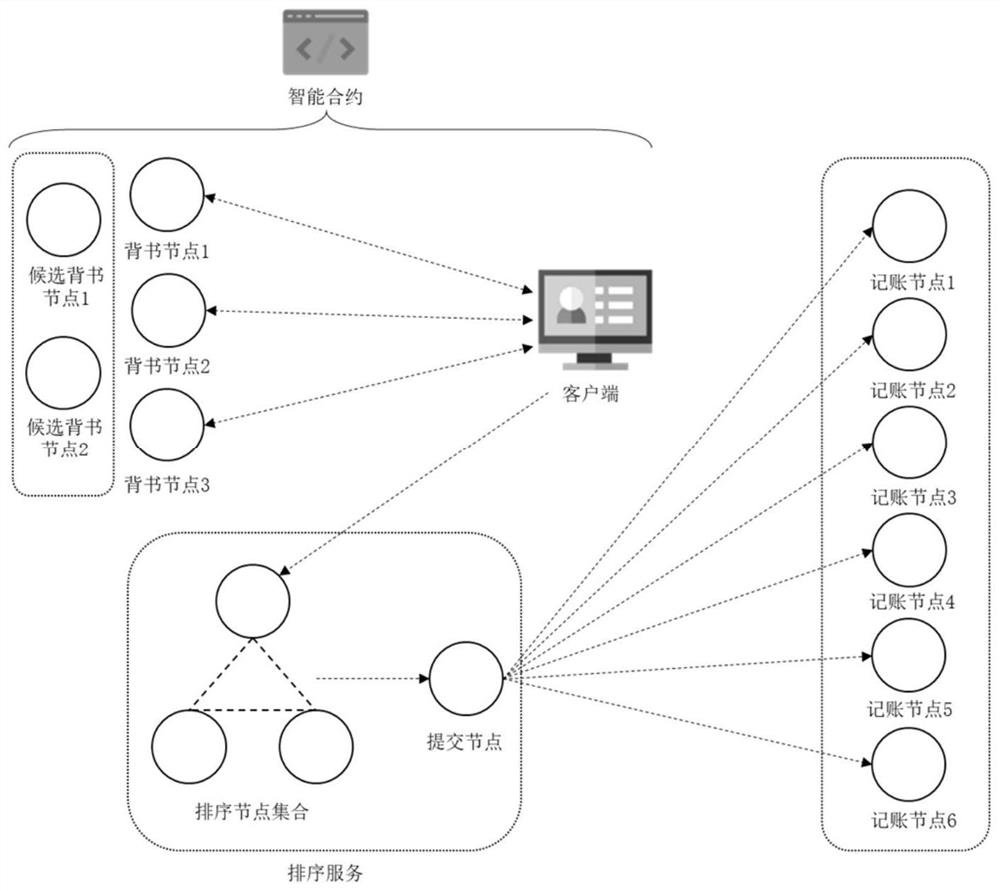
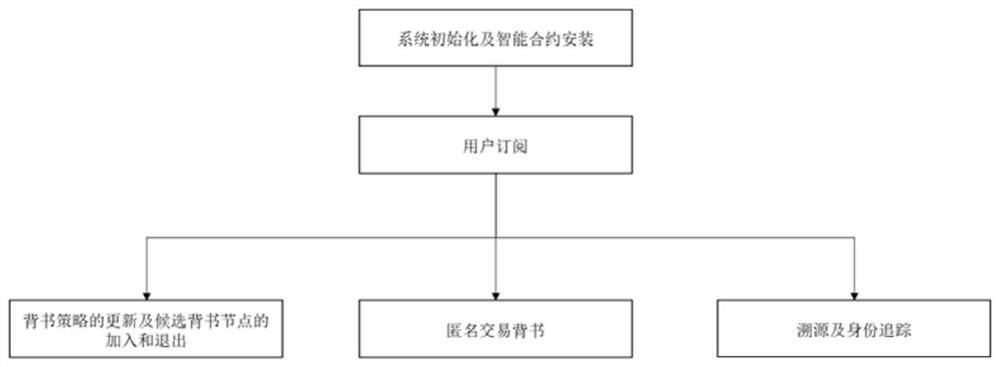
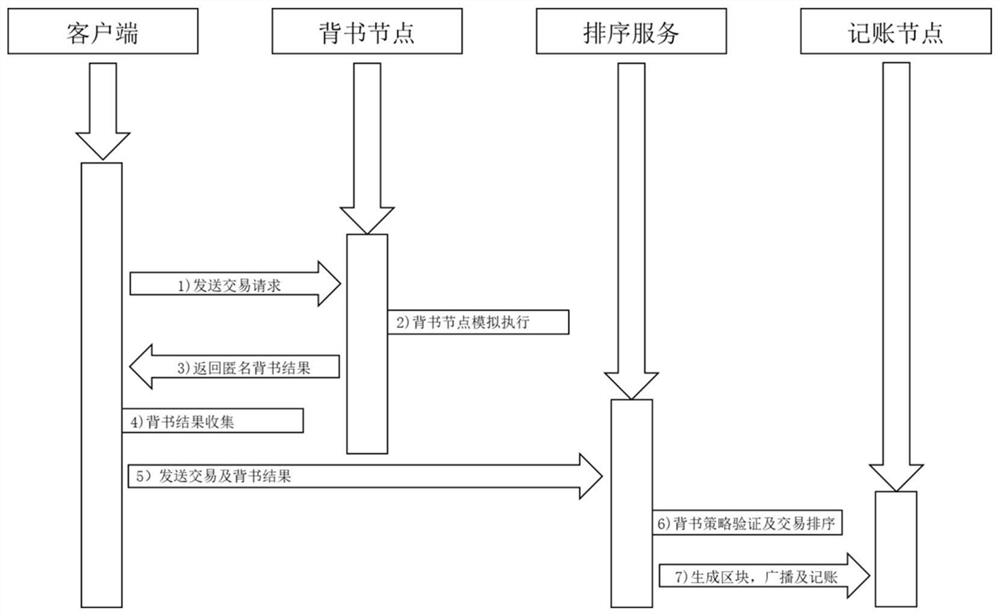
Permitted block chain anonymous transaction endorsement system and method
ActiveCN113222601AResolve to joinSolve the problem of exit inefficiencyDatabase distribution/replicationPayment protocolsInternet privacyFinancial transaction
Owner:HUBEI UNIV OF TECH
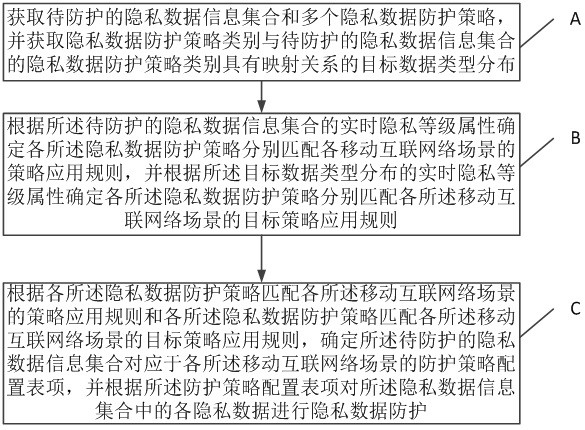
Private data protection method and system in mobile internet
The invention provides a privacy data protection method and system in a mobile internet, and the method comprises the steps: obtaining a to-be-protected privacy data information set and a plurality of privacy data protection strategies, and obtaining the distribution of target data types in which the types of the privacy data protection strategies have a mapping relation with the to-be-protected privacy data information set; then determining a corresponding strategy application rule according to a real-time privacy level attribute of a privacy data information set to be protected, and determining that each privacy data protection strategy is respectively matched with a target strategy application rule of each mobile internet scene according to the real-time privacy level attribute; and finally, according to each privacy data protection strategy, matching a strategy application rule of each mobile internet scene and matching a target strategy application rule of each mobile internet scene, and determining a corresponding protection strategy configuration table item. Therefore, privacy data protection is carried out on each privacy data in the privacy data information set according to the protection strategy configuration table item.
Owner:苏州远略知识产权运营有限公司
Method and apparatus for managing private data in multi-function products
ActiveUS20070043953A1Prevent unauthorized accessDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
Owner:HEWLETT PACKARD DEV CO LP
CSRF attack protection method and device
ActiveCN112866265ASolve the attack problemRelieve pressureUser identity/authority verificationThird partyInternet privacy
The present invention provides a CSRF attack protection method and device. The background server generates the token under the condition that the user request does not carry the token and writes the generated token into the browser cookie and the page request, and the token does not need to be stored in the background server, so that the pressure of the background server is reduced. When the user sends the user request again, the front-end preset script is triggered to run to write the token in the browser cookie and the page request into the user request, the background server realizes CSRF verification by judging whether the cookie in the user request is the same as the token in the parameter or not due to the fact that the browser cookie cannot be captured by a third party, the verification logic for binding the token with the user does not need to be added, and therefore, the CSRF attack problem can be simply and effectively solved.
Owner:HUNAN HAPPLY SUNSHINE INTERACTIVE ENTERTAINMENT MEDIA CO LTD
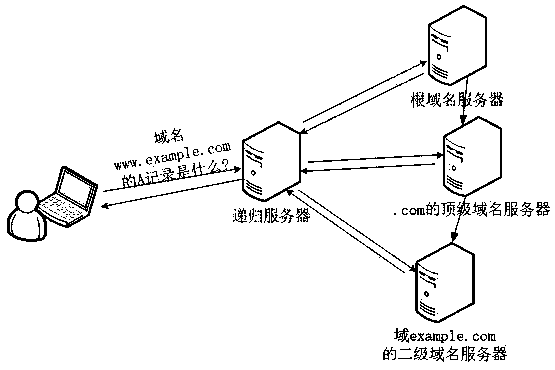
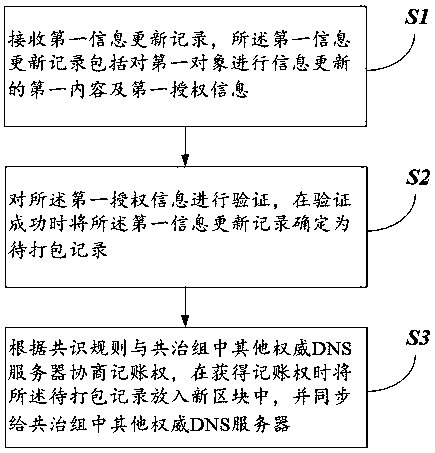
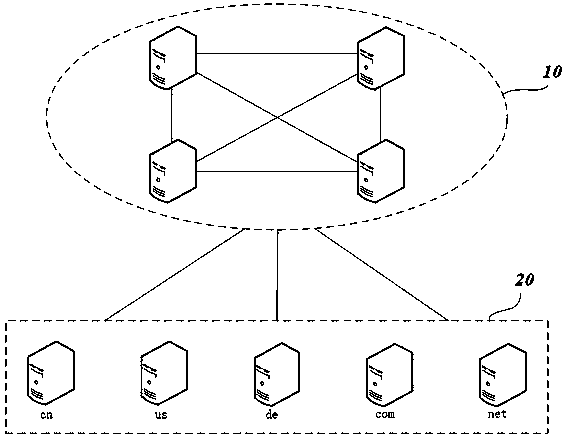
Authoritative DNS server information updating method and system
Owner:广州根链国际网络研究院有限公司
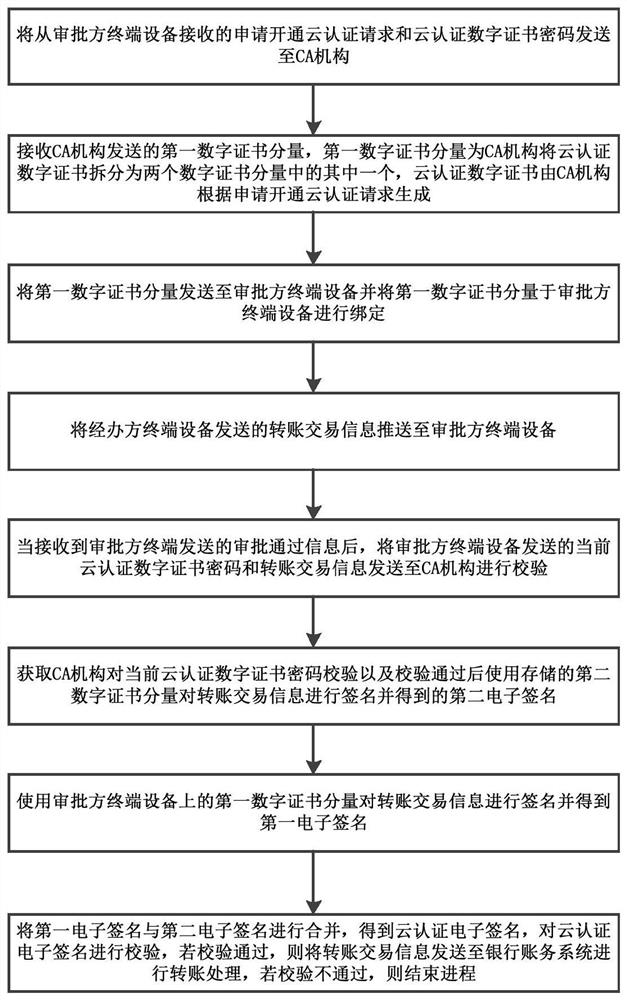
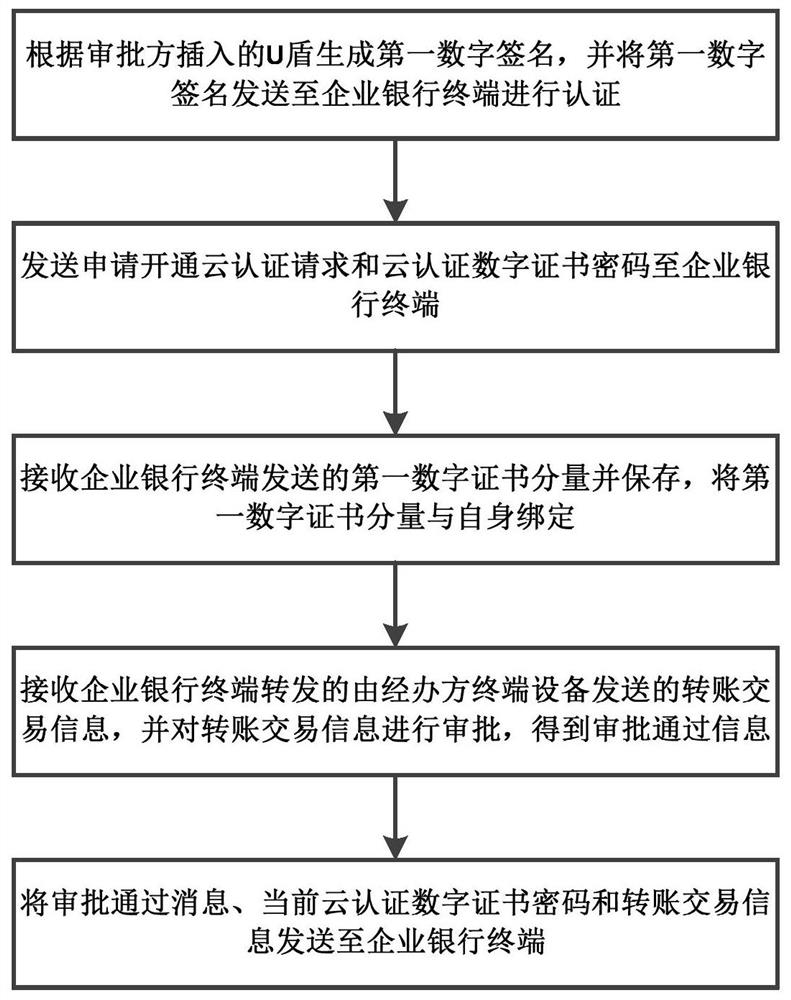
Fund payment approval method and equipment based on enterprise cloud authentication and medium
PendingCN113240423AImprove convenienceImprove securityDigital data authenticationProtocol authorisationInternet privacyEngineering
The invention provides a fund payment examination and approval method based on enterprise cloud authentication. The method comprises the steps of forwarding an application for opening a cloud authentication request, receiving a first digital certificate component, forwarding the first digital certificate component, pushing an examination and approval message, forwarding a current cloud authentication digital certificate password, obtaining a second electronic signature, and obtaining a first electronic signature and verifying the electronic signature. According to the fund payment examination and approval method based on the enterprise cloud authentication, when the examination and approval party of the enterprise customer examines and approves the to-be-examined and approved transfer transaction information sent by the handler, a USB key does not need to be inserted, and the examination and approval can be carried out in a cloud authentication mode of directly inputting the current cloud authentication digital certificate password, so the problems that a USB key is not convenient to carry and the USB key is damaged and the like are solved, and the convenience of handling mobile finance is improved; in the aspect of safety, a scattered digital certificate storage scheme is adopted, a cloud authentication digital certificate password is used for access protection, and the safety is higher compared with file certificate storage.
Owner:GUANGDONG HUAXING BANK CO LTD
Private communication service in a public cloud environment
A private communication set-up service enables scalable private connectivity between producers and consumers residing within a public cloud environment. A producer exposes metadata information about a new or updated resource within the public cloud environment using a tag. The system monitors the public cloud environment for tagged metadata about new resources and configures a producer-side service to a private link. Subsequently, the system exposes metadata information about the private link. The system monitors for tagged metadata about private links and configures the consumer-side private link endpoint to the private link. The producer and the consumer communicate using the configured private link.
Owner:SALESFORCE COM INC
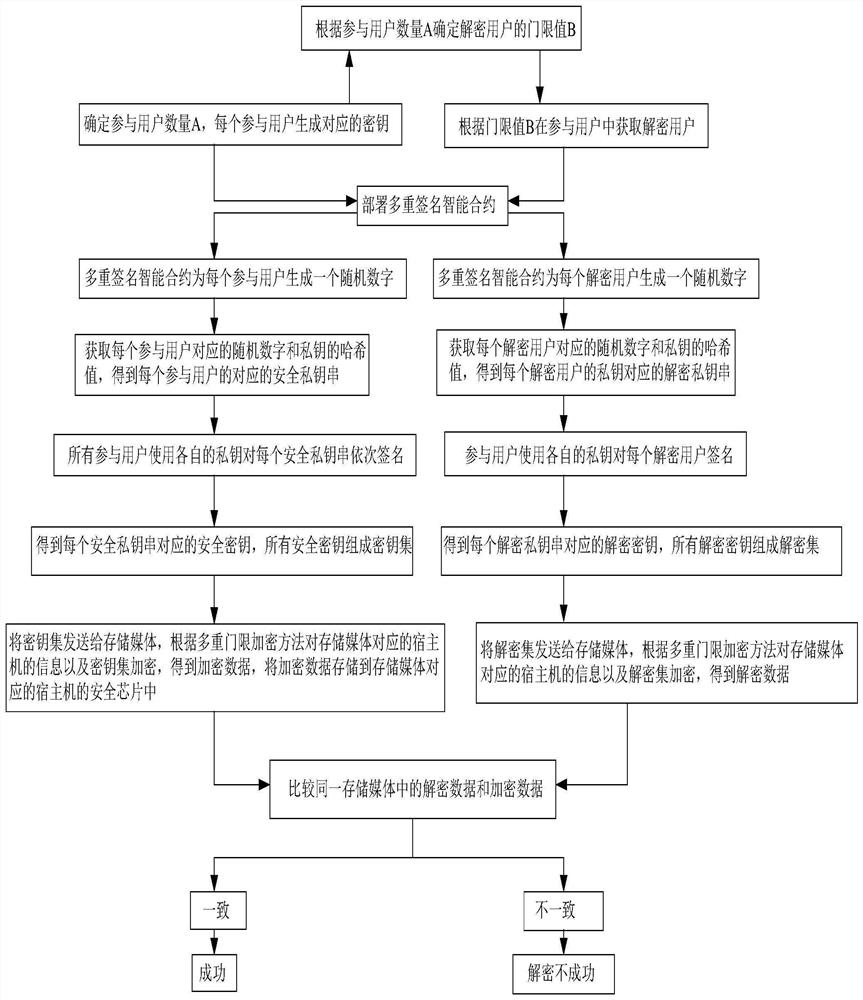
Method, system and device for enhancing security of storage media and medium
ActiveCN113111396AFix security issuesSolve too manyDigital data protectionInternal/peripheral component protectionInternet privacyEngineering
Owner:湖北央中巨石信息技术有限公司
Method and system for solving potential safety hazards of rights and interests of DPOS consensus nodes
Owner:上海简苏网络科技有限公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap