Method, system and device for enhancing security of storage media and medium
A technology for storage media and security, applied in the field of data security, can solve problems such as data leakage, achieve the effect of enhancing security, solving security problems, and avoiding potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 2
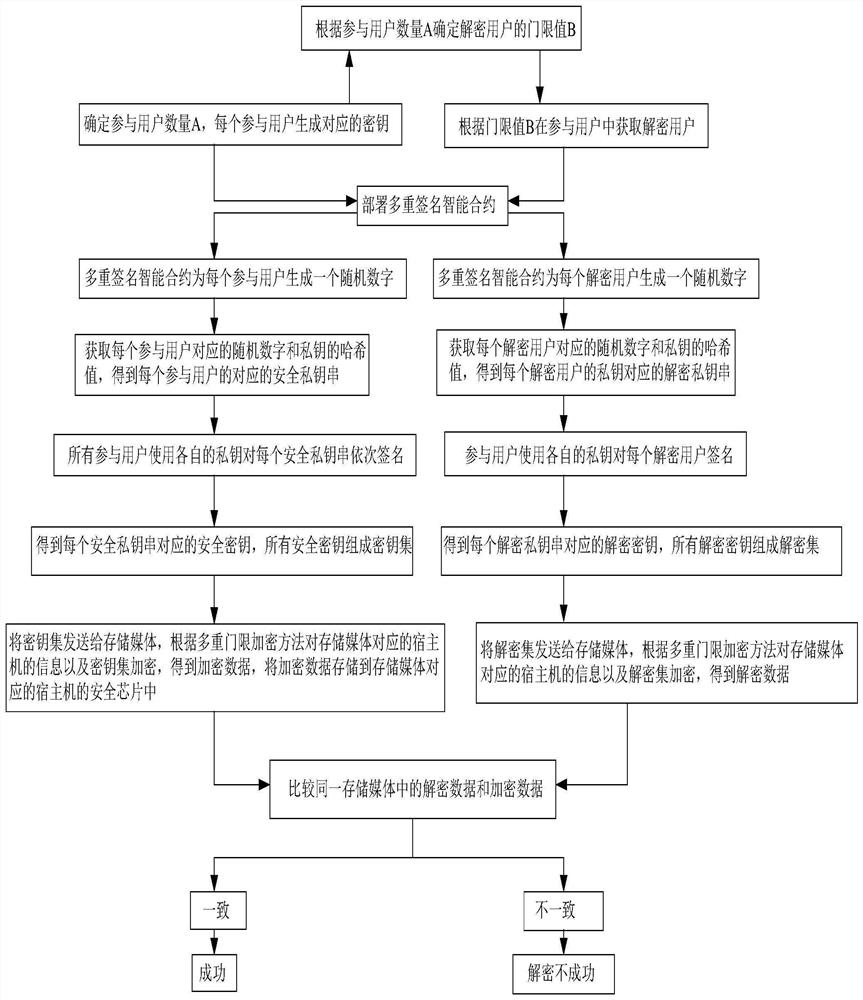
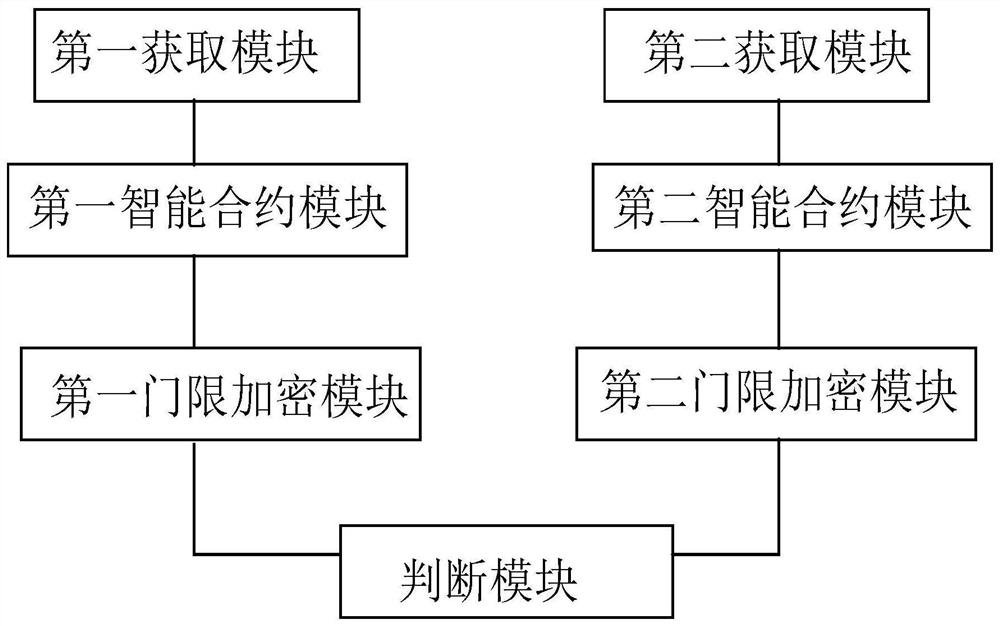
[0106] Please refer to figure 2 , figure 2 It is a schematic composition diagram of a system for enhancing the security of storage media. Embodiment 2 of the present invention provides a system for enhancing the security of storage media. The system includes:
[0107] The first smart contract module is used to obtain the secure private key string, sign the secure private key string according to the multi-signature smart contract to obtain a key set, and send the key set to the storage medium;
[0108] The second smart contract module is used to obtain the decrypted private key string, sign the decrypted private key string according to the multi-signature smart contract to get decryption, and send the decryption to the storage medium;
[0109] The first threshold encryption module is used to encrypt the key set received by the storage medium and the information of the host computer corresponding to the storage medium based on the multiple threshold encryption method to obtain e
Embodiment 3
[0119] Embodiment 3 of the present invention provides an electronic device, including a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the computer program, the Steps of a method of enhancing storage media security.
[0120] Wherein, the processor may be a central processing unit, or other general-purpose processors, digital signal processors, application-specific integrated circuits, off-the-shelf programmable gate arrays or other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components etc. A general-purpose processor may be a microprocessor, or the processor may be any conventional processor, or the like.
[0121] The memory can be used to store the computer program and / or module, and the processor implements various functions of the device for enhancing the security of the storage medium in the invention by running or executing the data stored in the memo
Embodiment 4
[0123] Embodiment 4 of the present invention provides a computer-readable storage medium, the computer-readable storage medium stores a computer program, and when the computer program is executed by a processor, the steps of the method for enhancing the security of the storage medium are implemented .
[0124] The computer storage medium in the embodiments of the present invention may use any combination of one or more computer-readable media. The computer readable medium may be a computer readable signal medium or a computer readable storage medium. A computer readable storage medium may be, but is not limited to, an electrical, magnetic, optical, electromagnetic, infrared, or semiconductor system, apparatus, or device, or any combination thereof. More specific examples (non-exhaustive list) of computer-readable storage media include: electrical connections with one or more conductors, portable computer disks, hard disks, random access memory (RAM), read-only memory (ReadOnlyMe
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap