Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
50results about "Internal/peripheral component protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
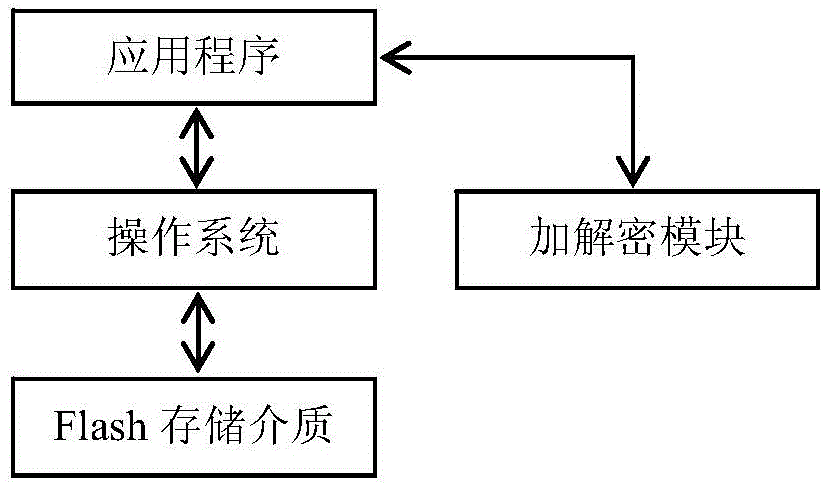
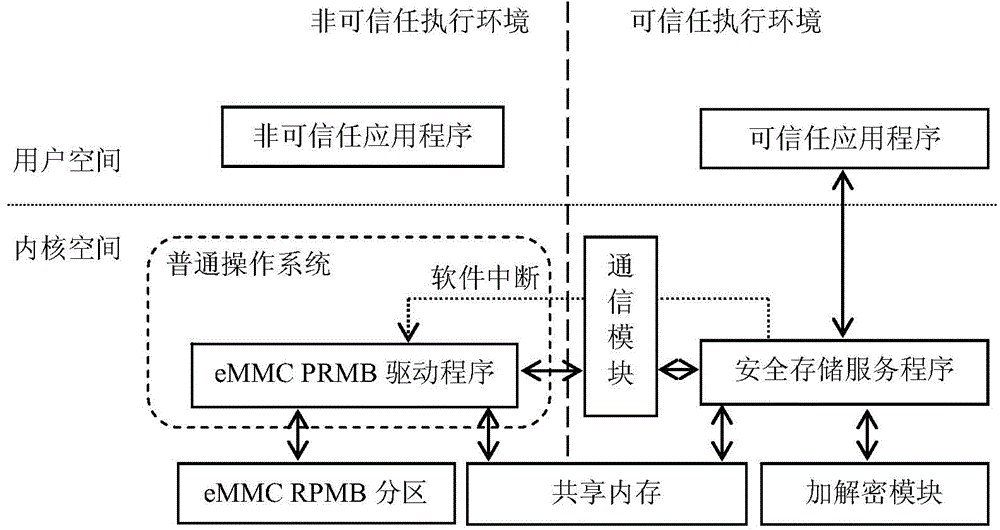
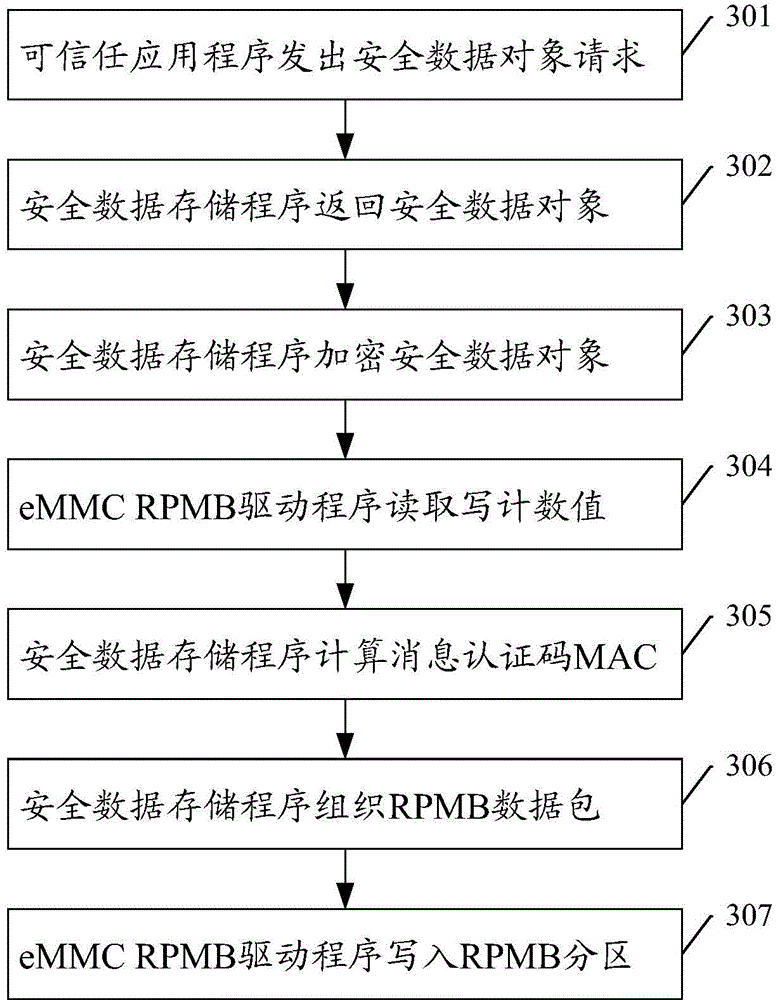
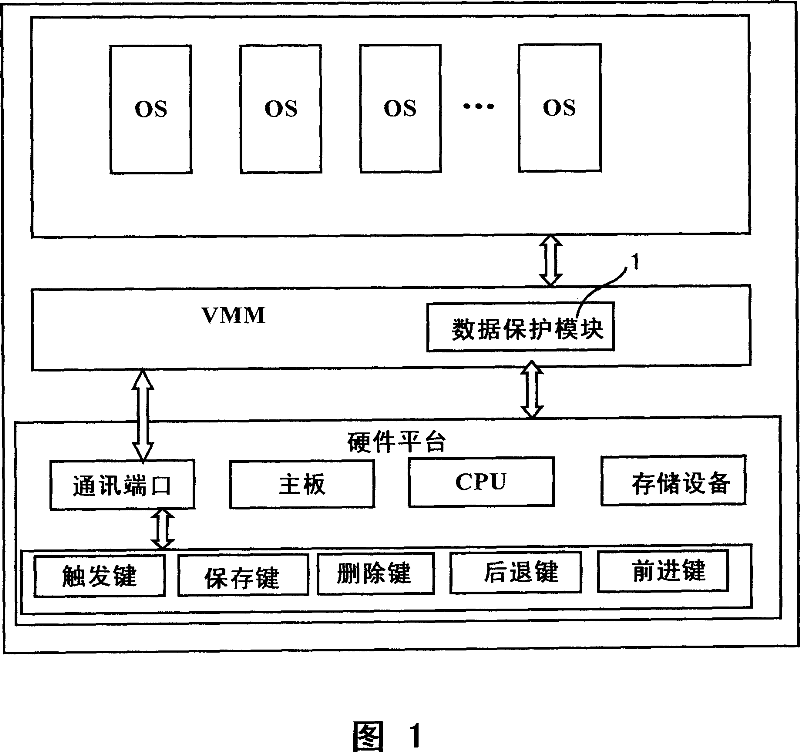
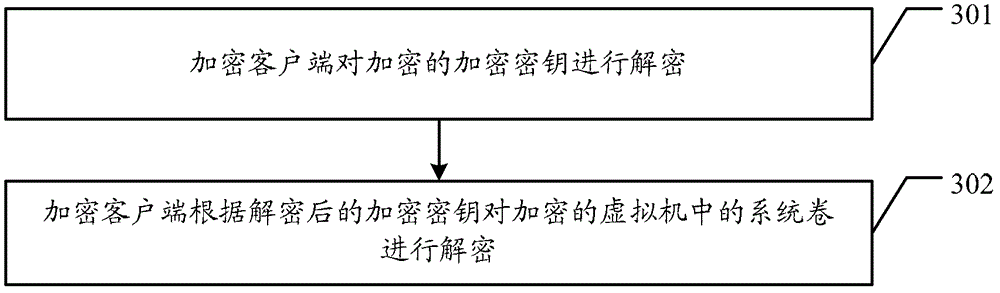
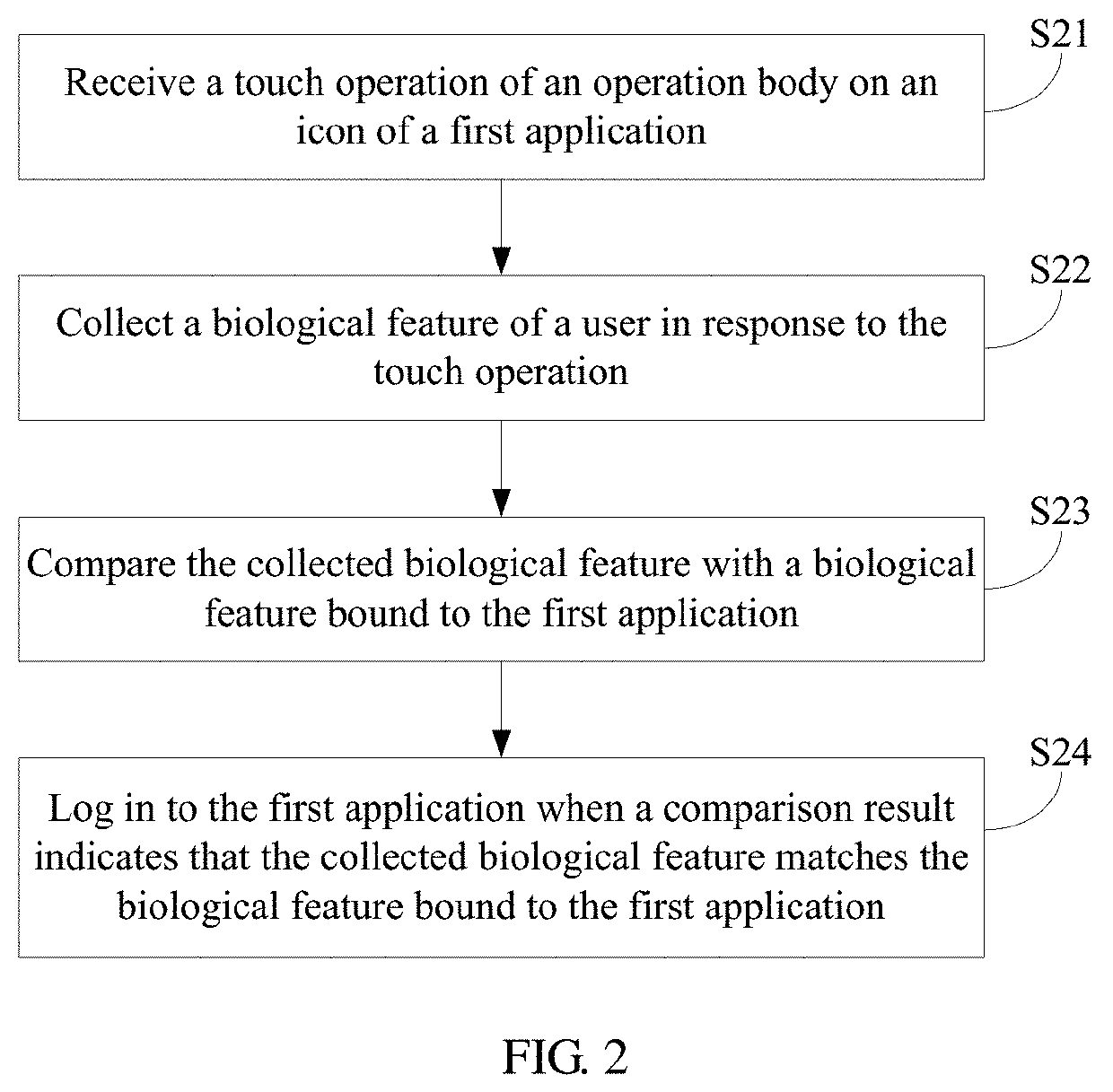
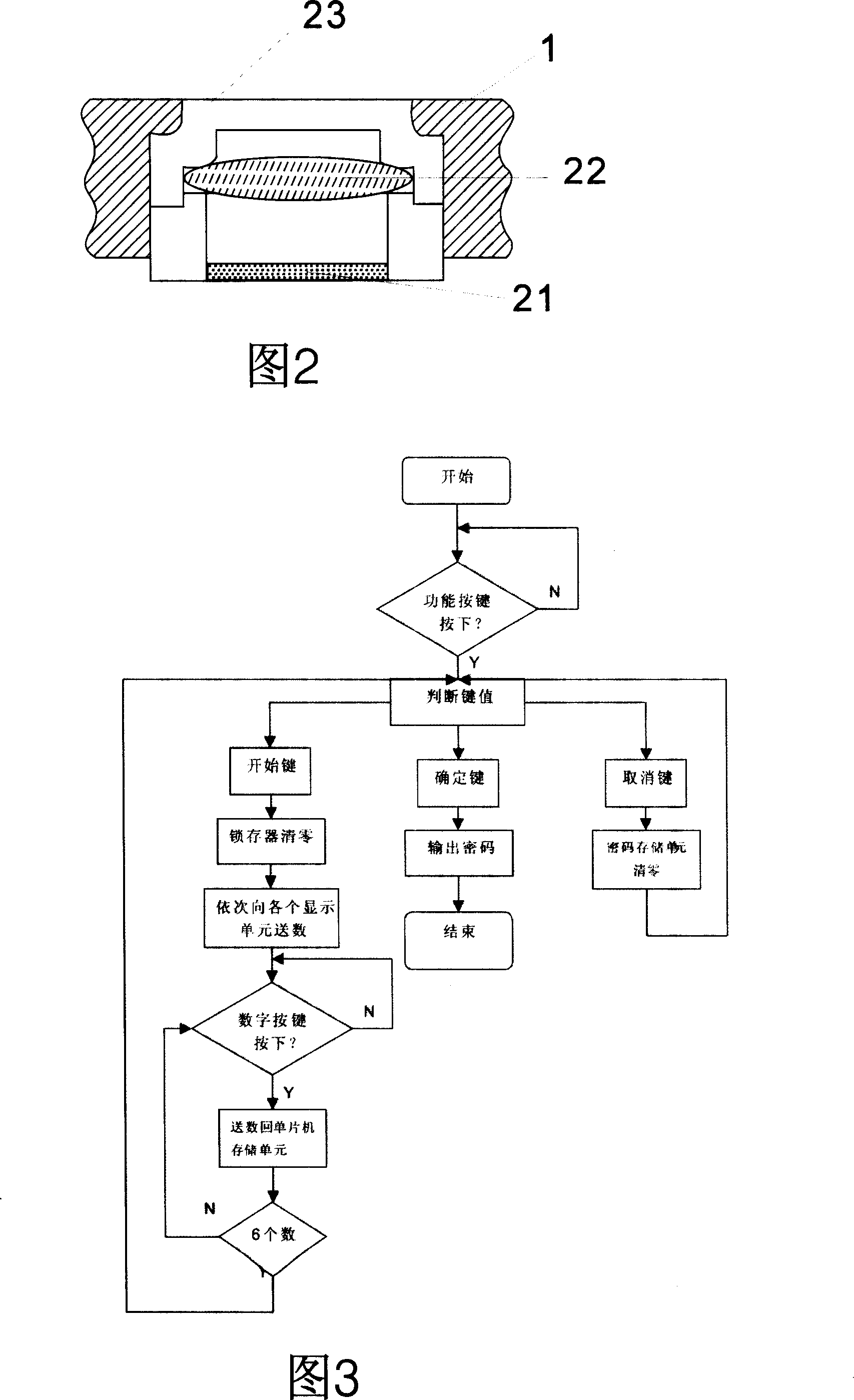
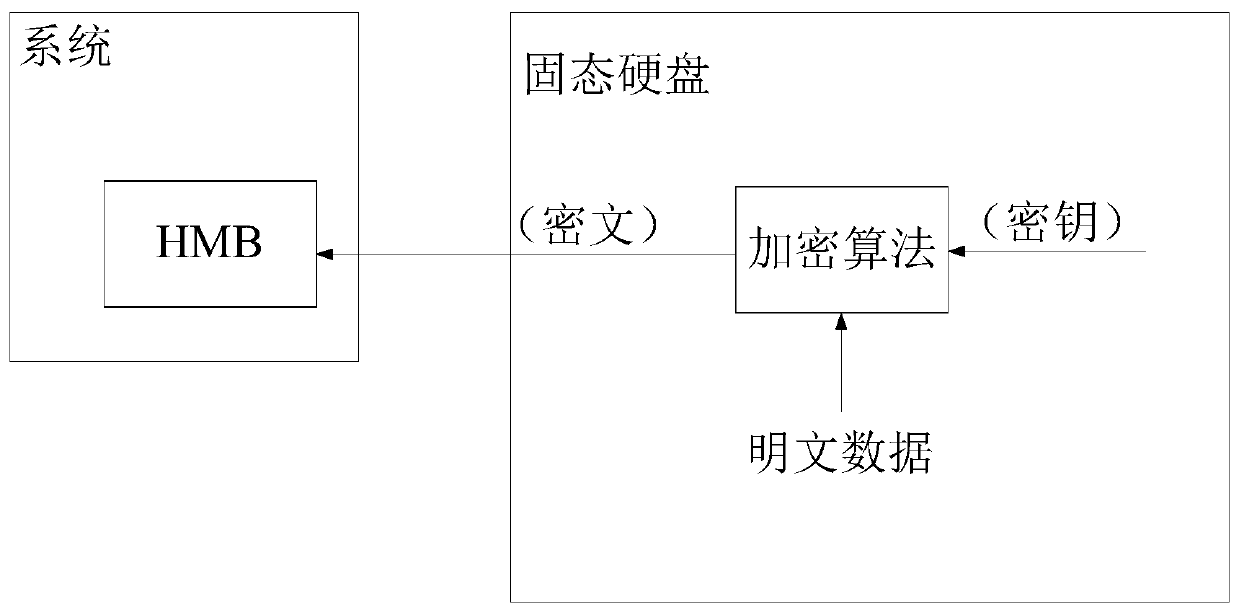
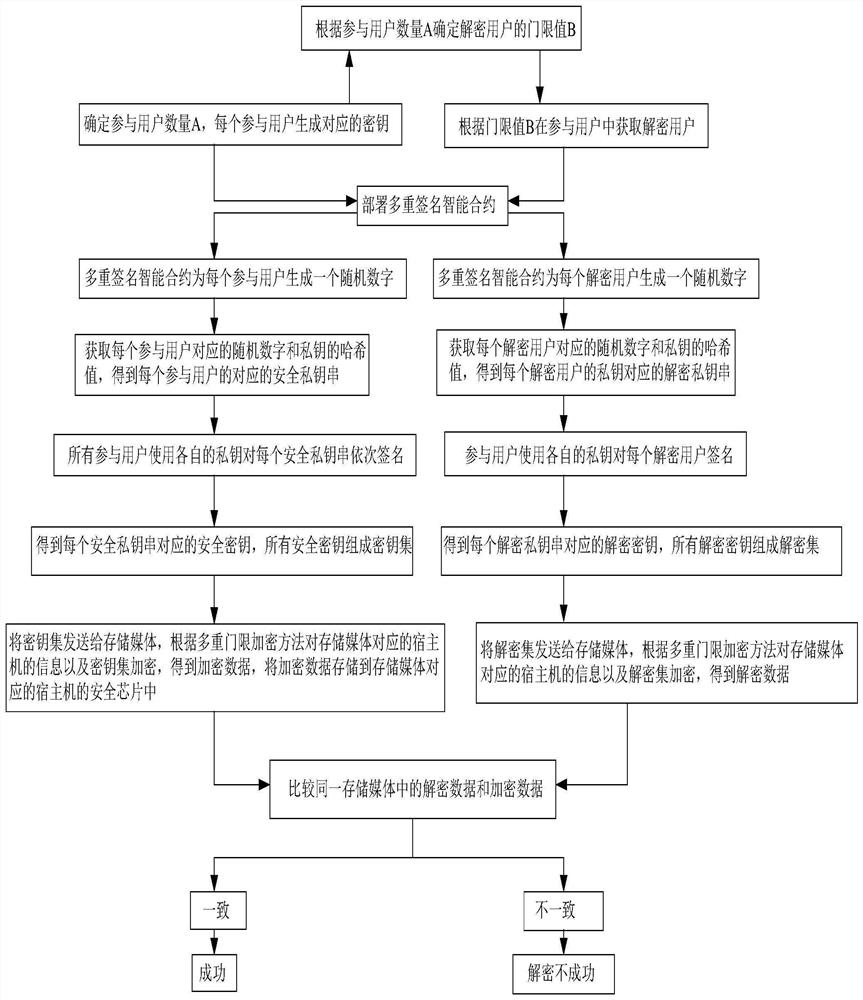
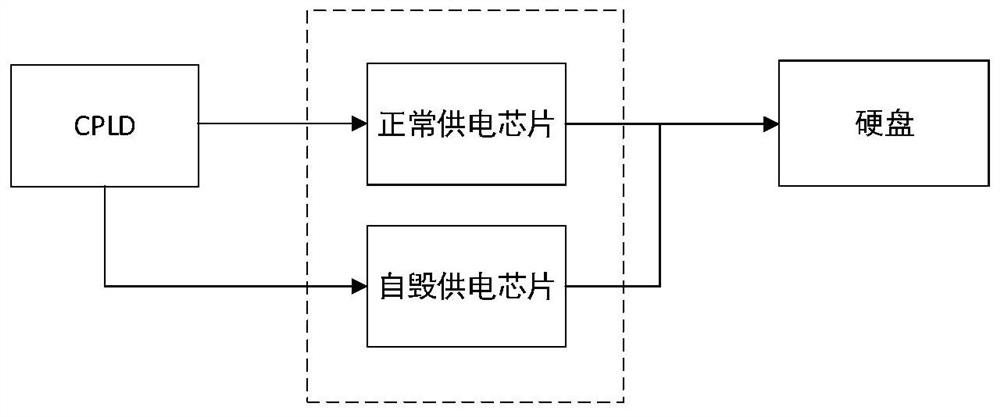
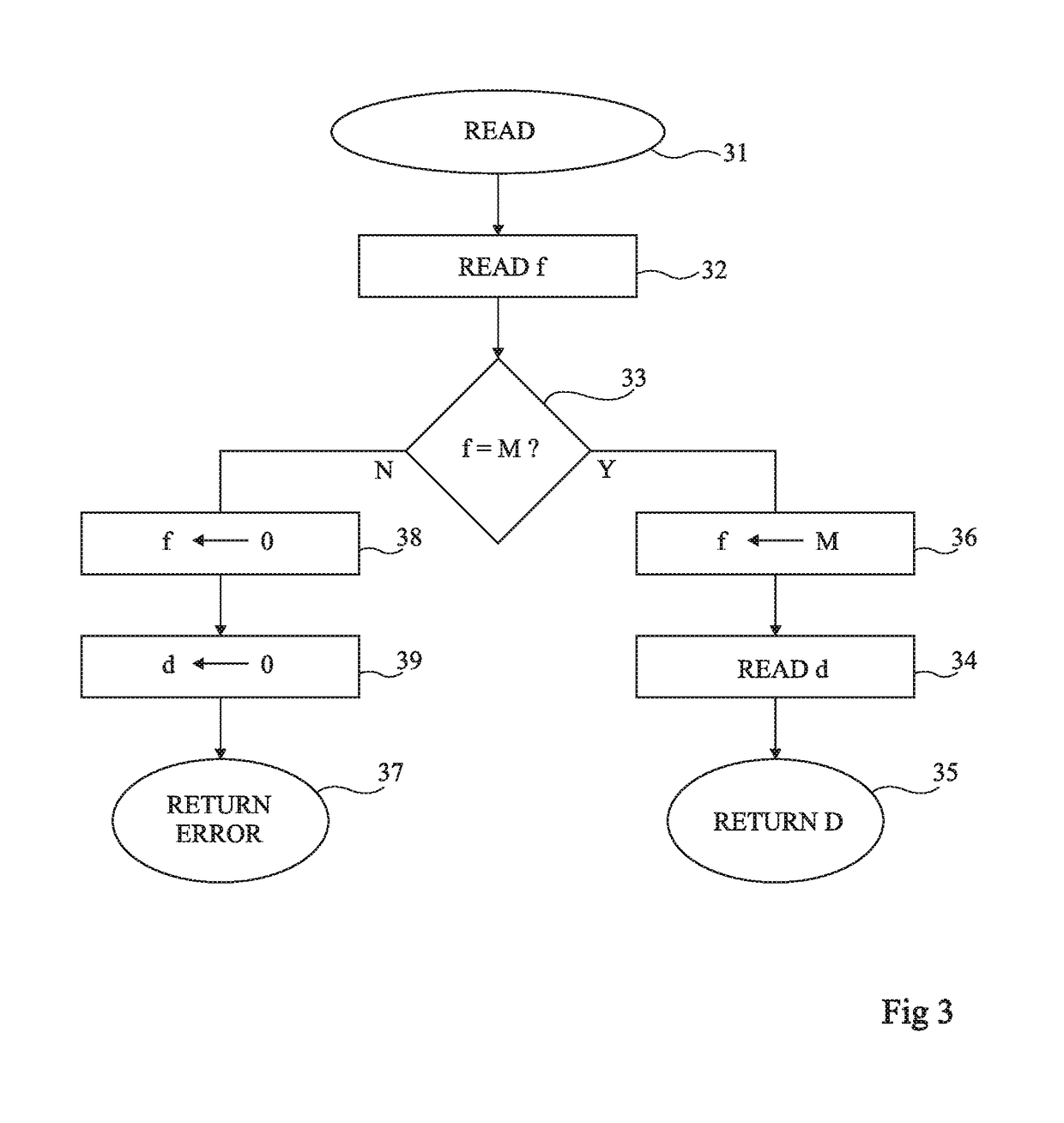
Security data storage method and system
ActiveCN104392188AEnsure safetyAvoid readingDigitally marking record carriersInternal/peripheral component protectionApplication softwareData store
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
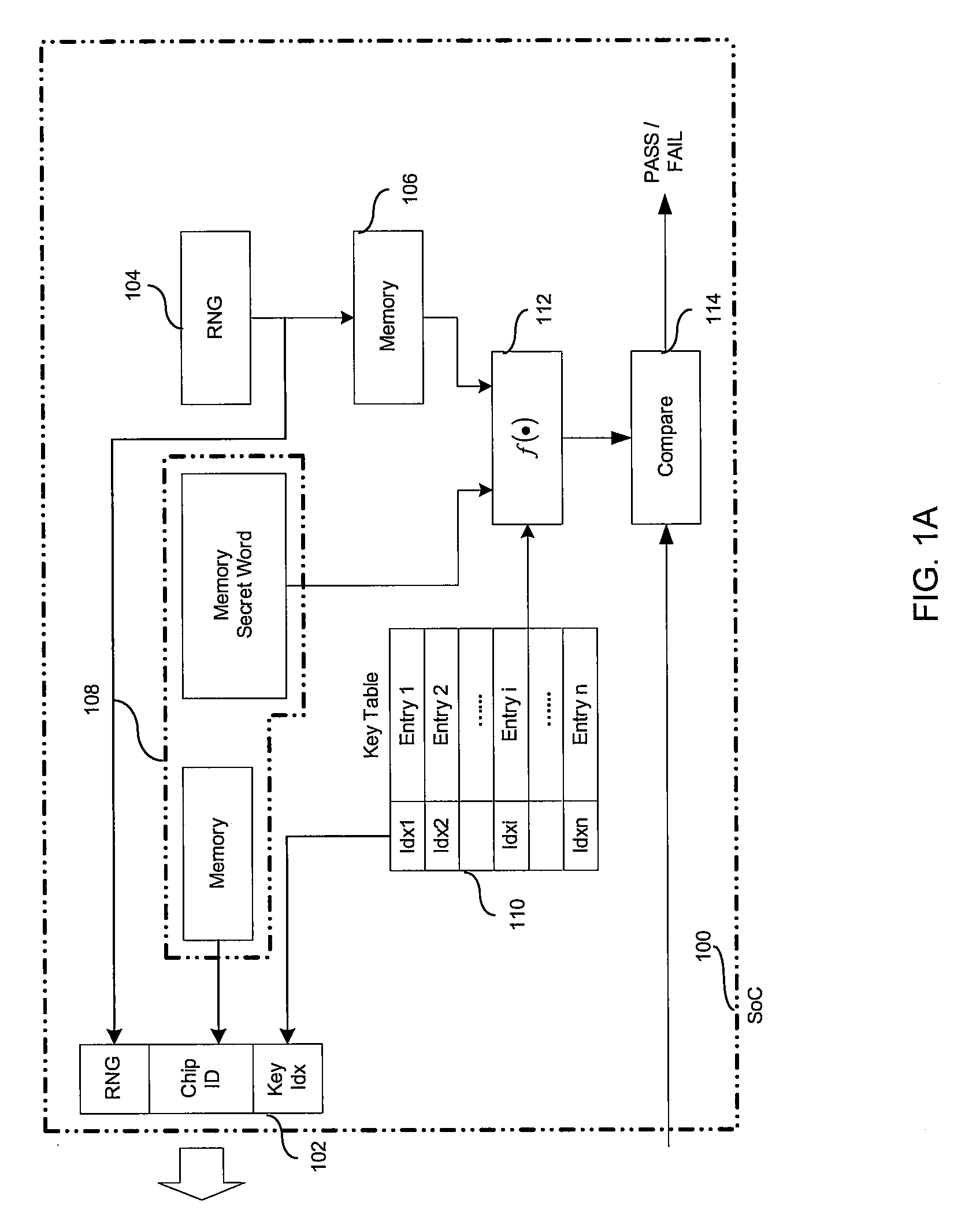
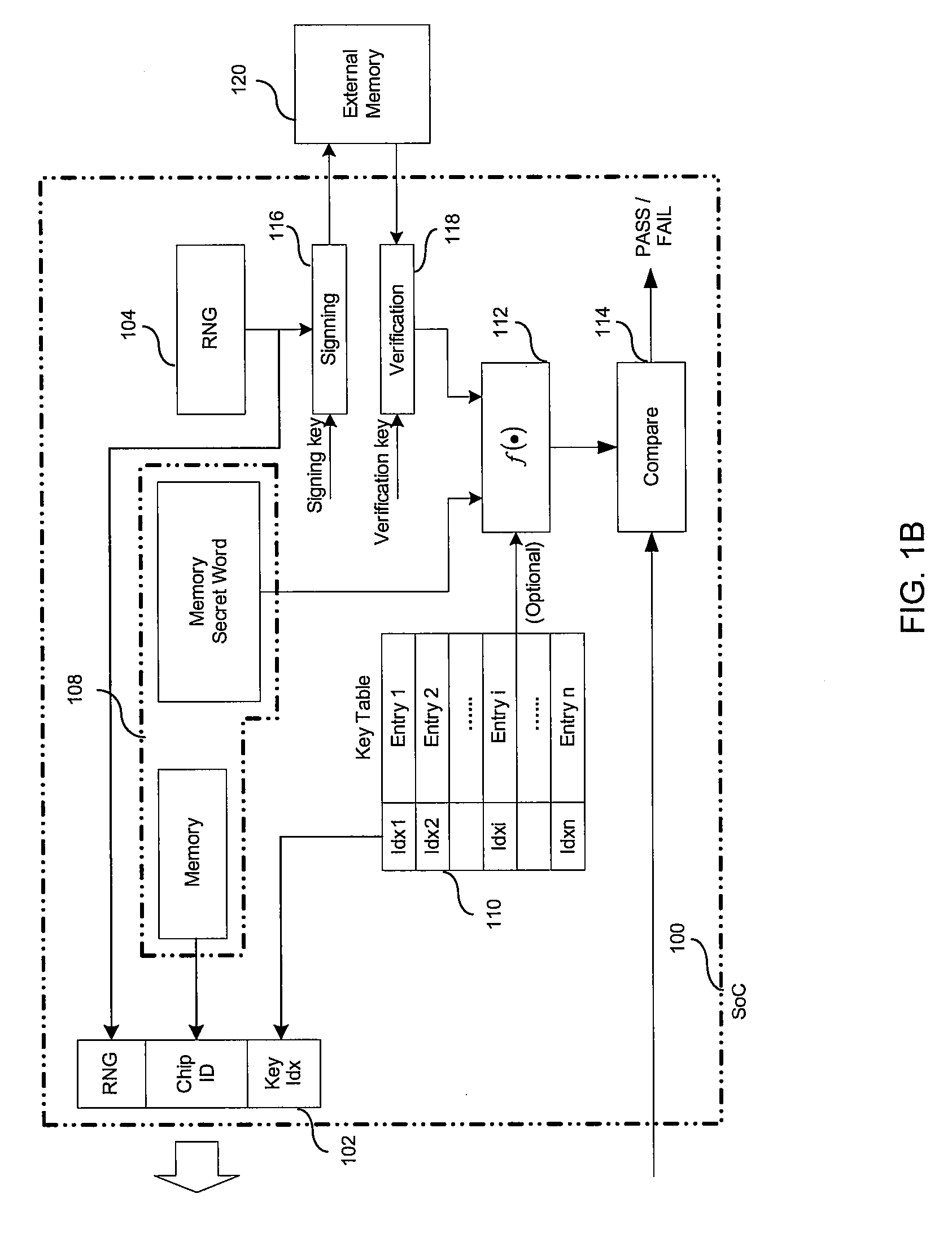
Method and apparatus of secure authentication for system on chip (SOC)
ActiveUS20080263362A1User identity/authority verificationInternal/peripheral component protectionSecurity functionComputer hardware
Owner:AVAGO TECH INT SALES PTE LTD
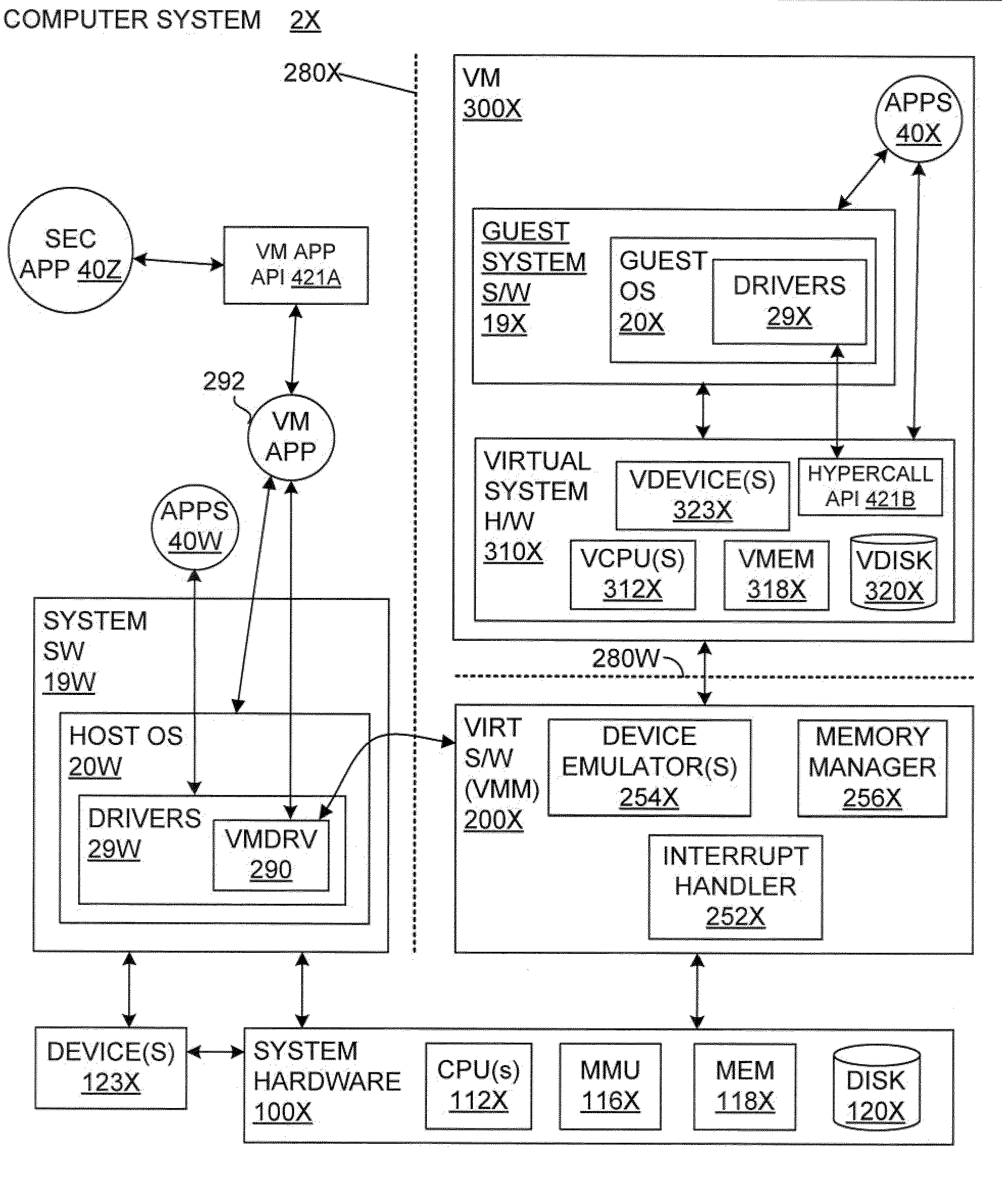
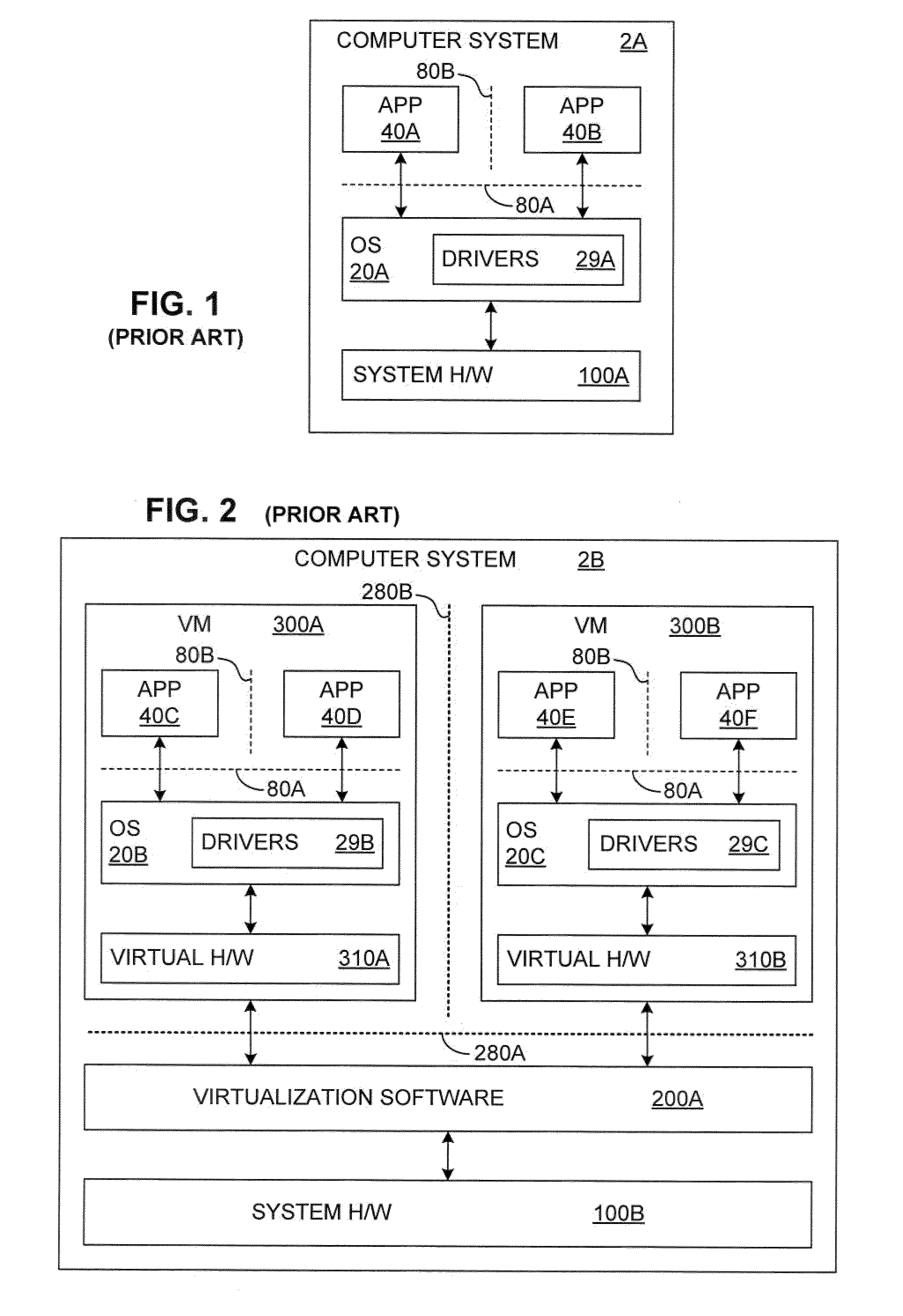
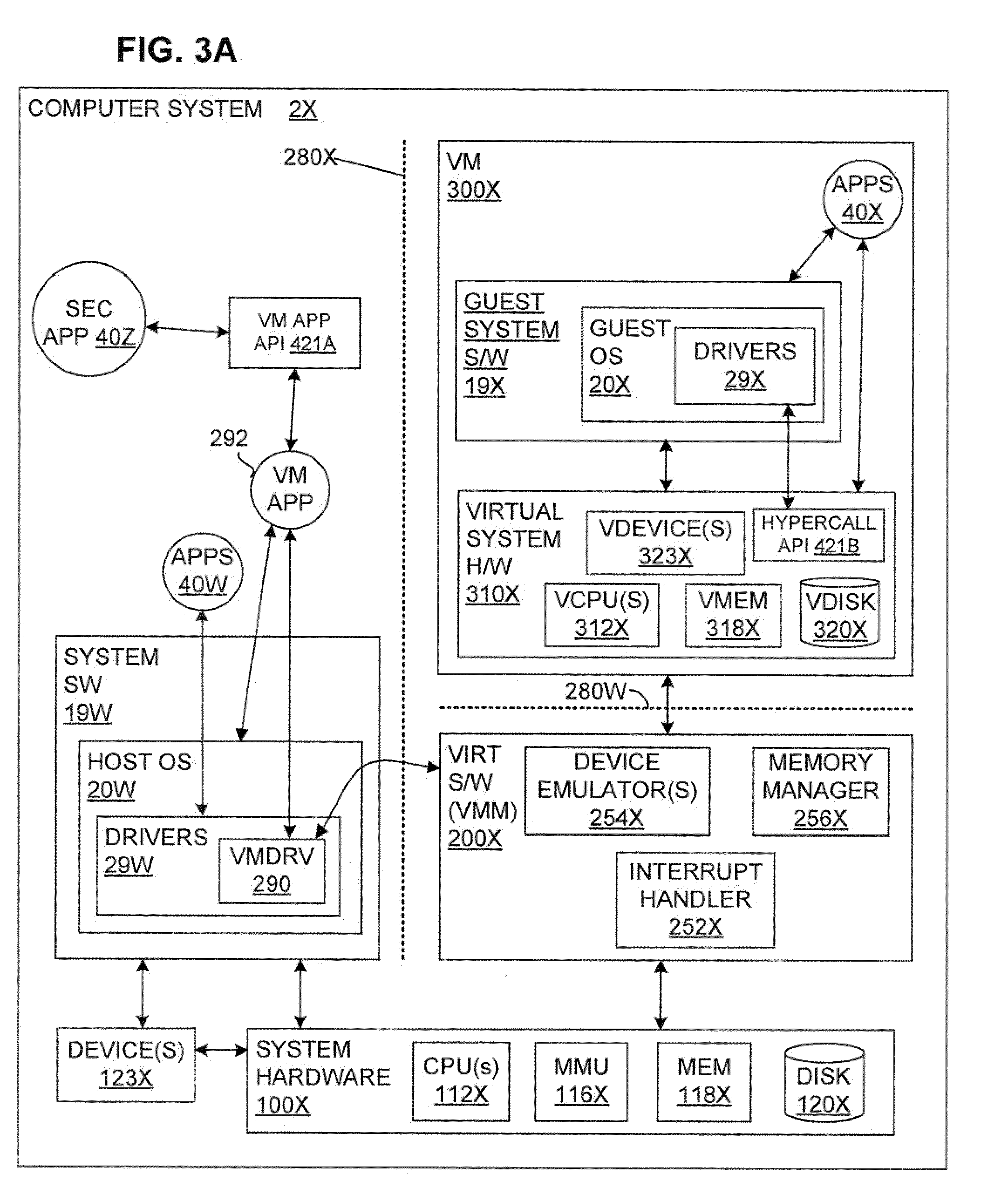
System and method to enhance memory protection for programs in a virtual machine environment
ActiveUS20110078361A1Memory adressing/allocation/relocationMultiprogramming arrangementsVirtualizationOperational system
Owner:VMWARE INC
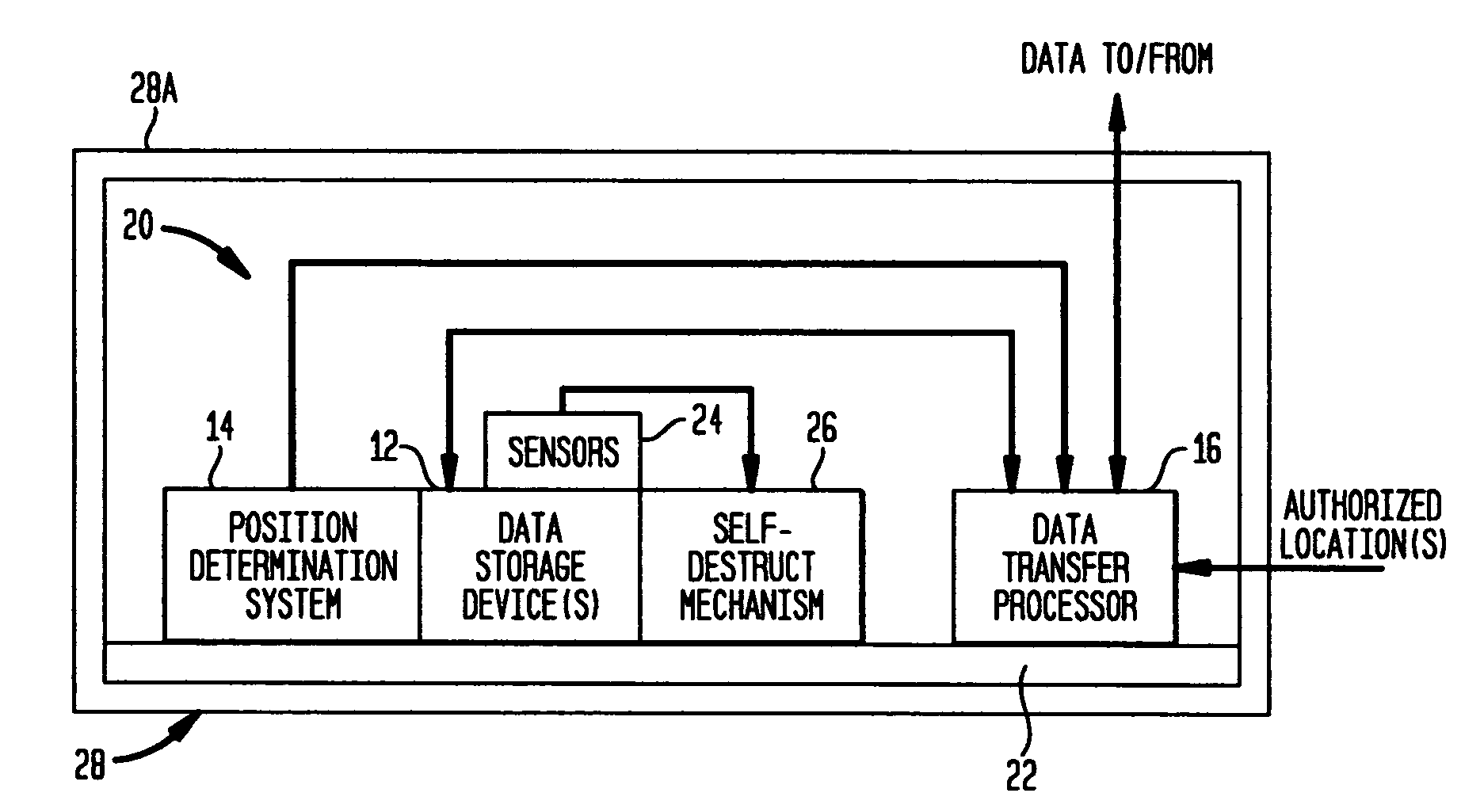
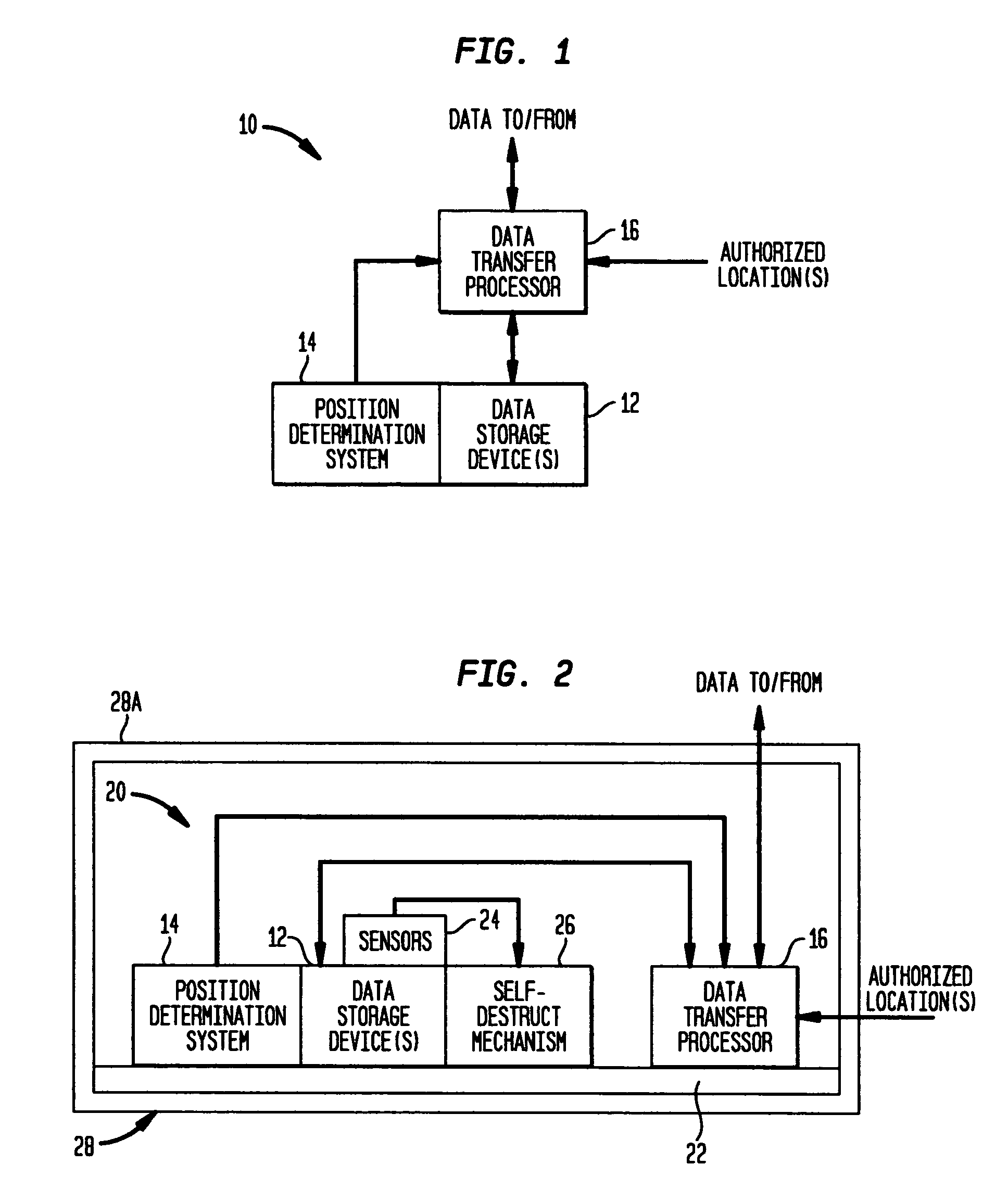
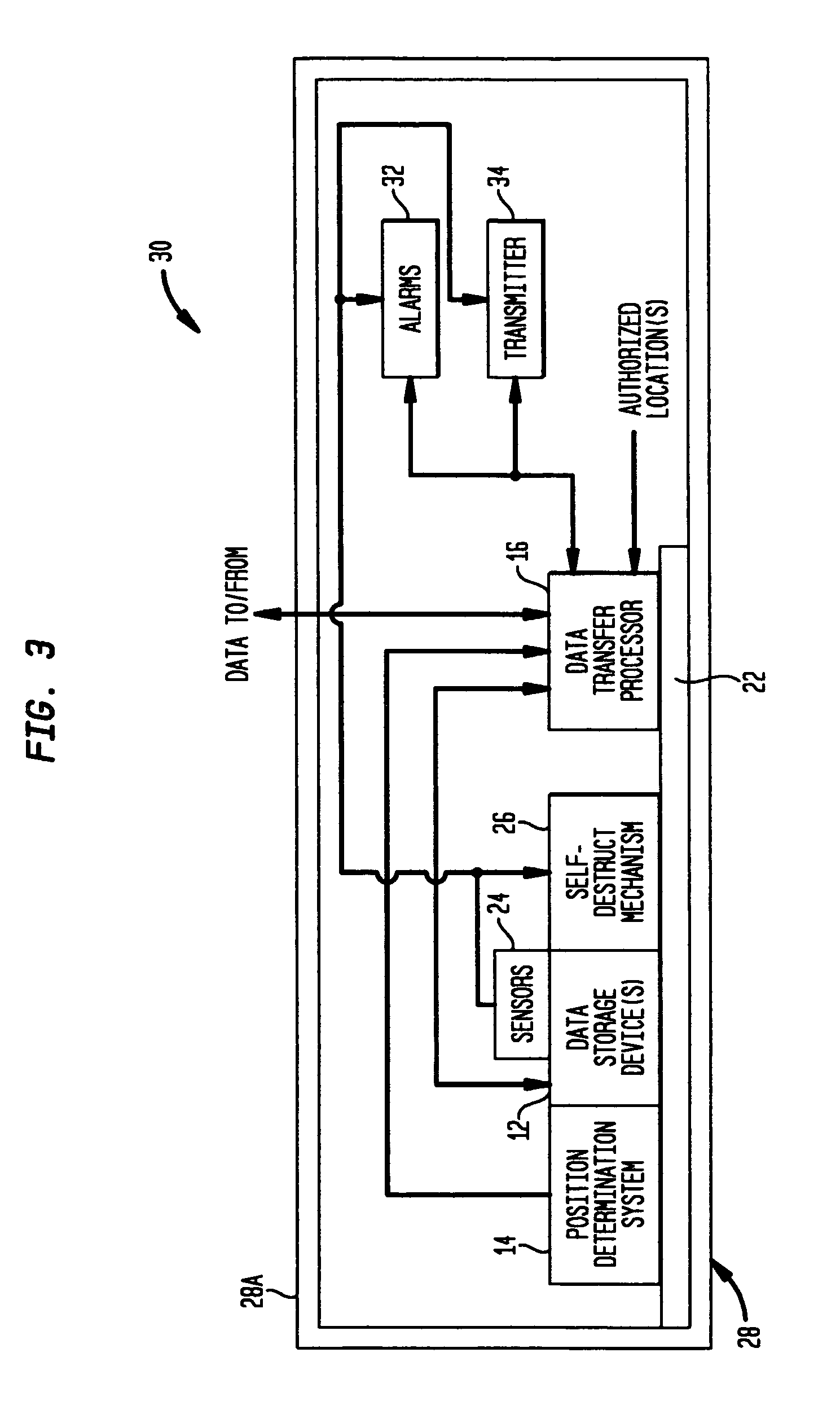
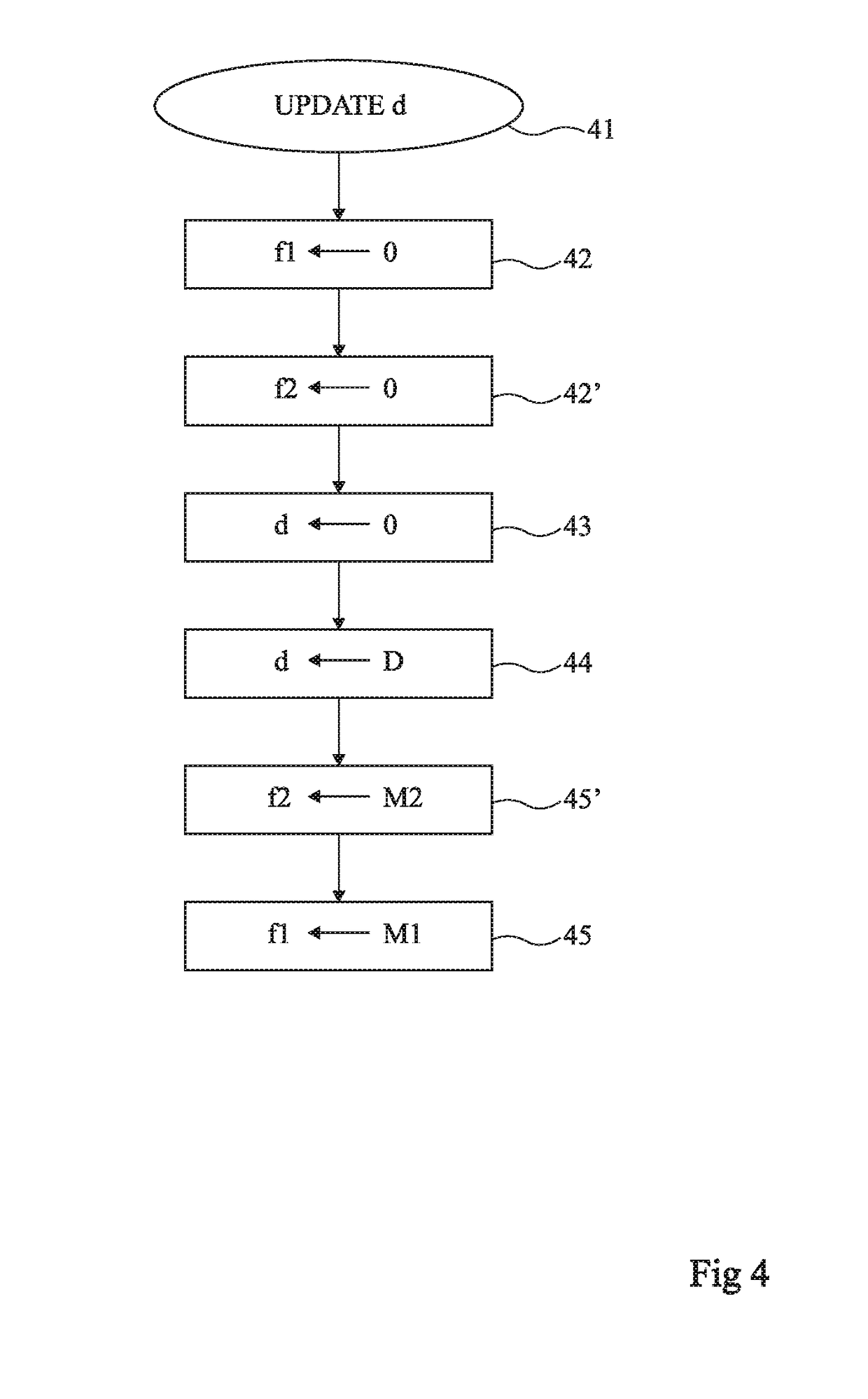
Portable information processing device having data evacuation function and method thereof
InactiveUS7024698B2Volume/mass flow measurementUnauthorized memory use protectionInformation processingLocation status
A processor means is connected with other individual means, and controls those individual means. Storage means stores data to be processed by the processor means and the resultant data after the process. An important data in the storage means is transmitted to other devices for evacuation by using a wireless communication means, when a situating condition of a portable information-processing device is judged abnormal (e.g., when being stolen) based on an output of a status detector means. The data in the storage means is deleted, when the transmission is completed or the transmission is interrupted. Protection of the data and the confidentiality are thus achieved even if the portable information-processing device is stolen, since the data can be evacuated, and the data is erased after completion of the data evacuation or if the data evacuation becomes not attainable.
Owner:PANASONIC CORP
System for securing the confidentiality of electronically stored data in the event of the physical theft thereof
InactiveUS7263190B1Secures confidentialityEasy data transferVolume/mass flow measurementUnauthorized memory use protectionConfidentialityData storing
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Digital data transparency protected safety read-write system and method
InactiveCN101042681AWon't worry about damageImprove usabilityUnauthorized memory use protectionInternal/peripheral component protectionDigital dataOperational system
Owner:LENOVO (BEIJING) CO LTD
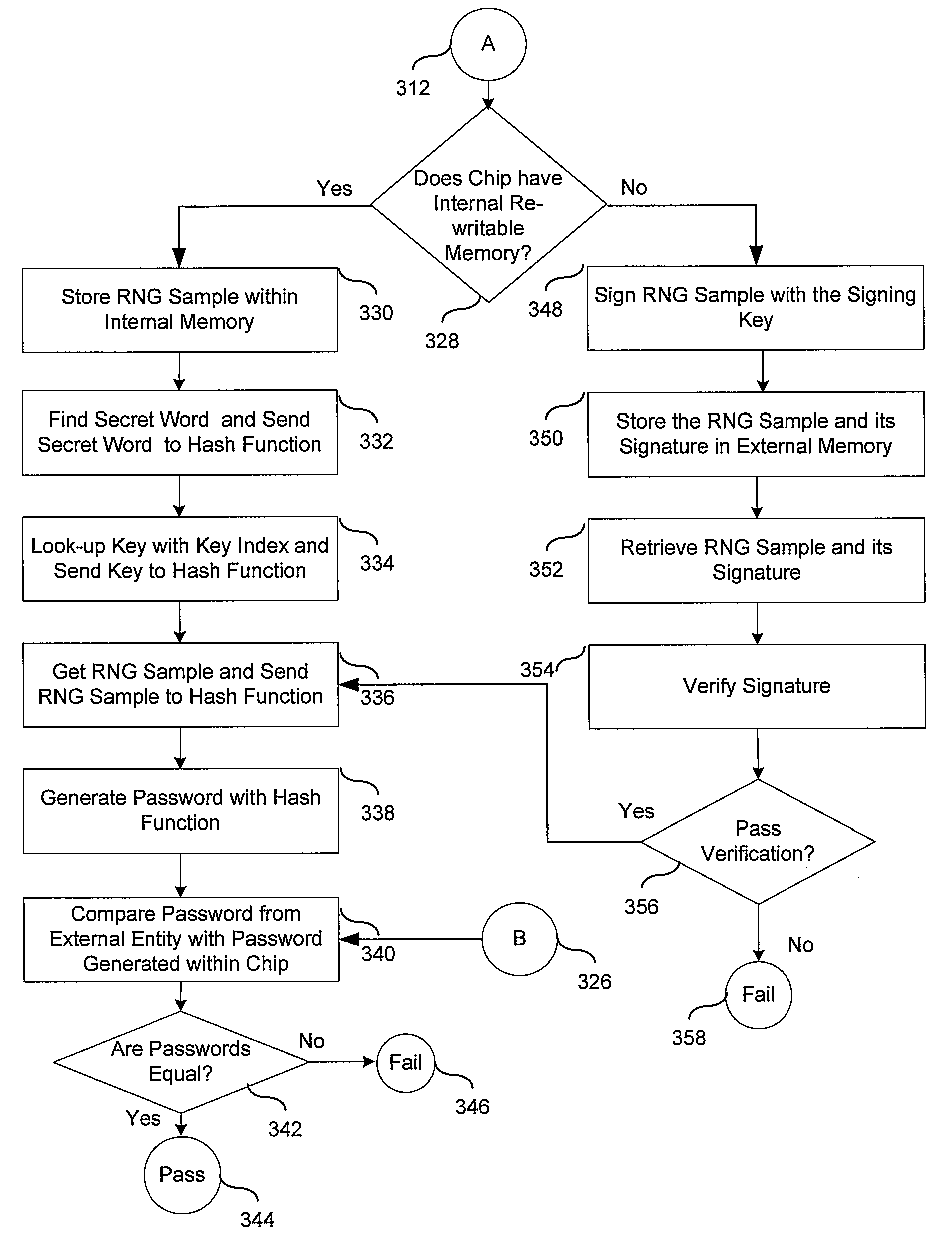
Physically unclonable function (PUF) circuits employing multiple puf memories to decouple a puf challenge input from a puf response output for enhanced security
InactiveUS20190342106A1User identity/authority verificationDigital storagePhysical unclonable functionChallenge response
Physically unclonable function (PUF) circuits employing multiple PUF memories to decouple a PUF challenge input from a PUF response output for enhanced security. The PUF circuit includes a PUF challenge memory and a PUF response memory. In response to a read operation, the PUF challenge memory uses a received PUF challenge input data word to address PUF challenge memory arrays therein to generate a plurality of intermediate PUF challenge output data words. The PUF response memory is configured to generate a second, final PUF response output data word in response to intermediate PUF challenge output data words. In this manner, it is more difficult to learn the challenge-response behavior of the PUF circuit, because the PUF challenge input data word does not directly address a memory array that stores memory states representing final logic values in the PUF response output data word.
Owner:QUALCOMM INC
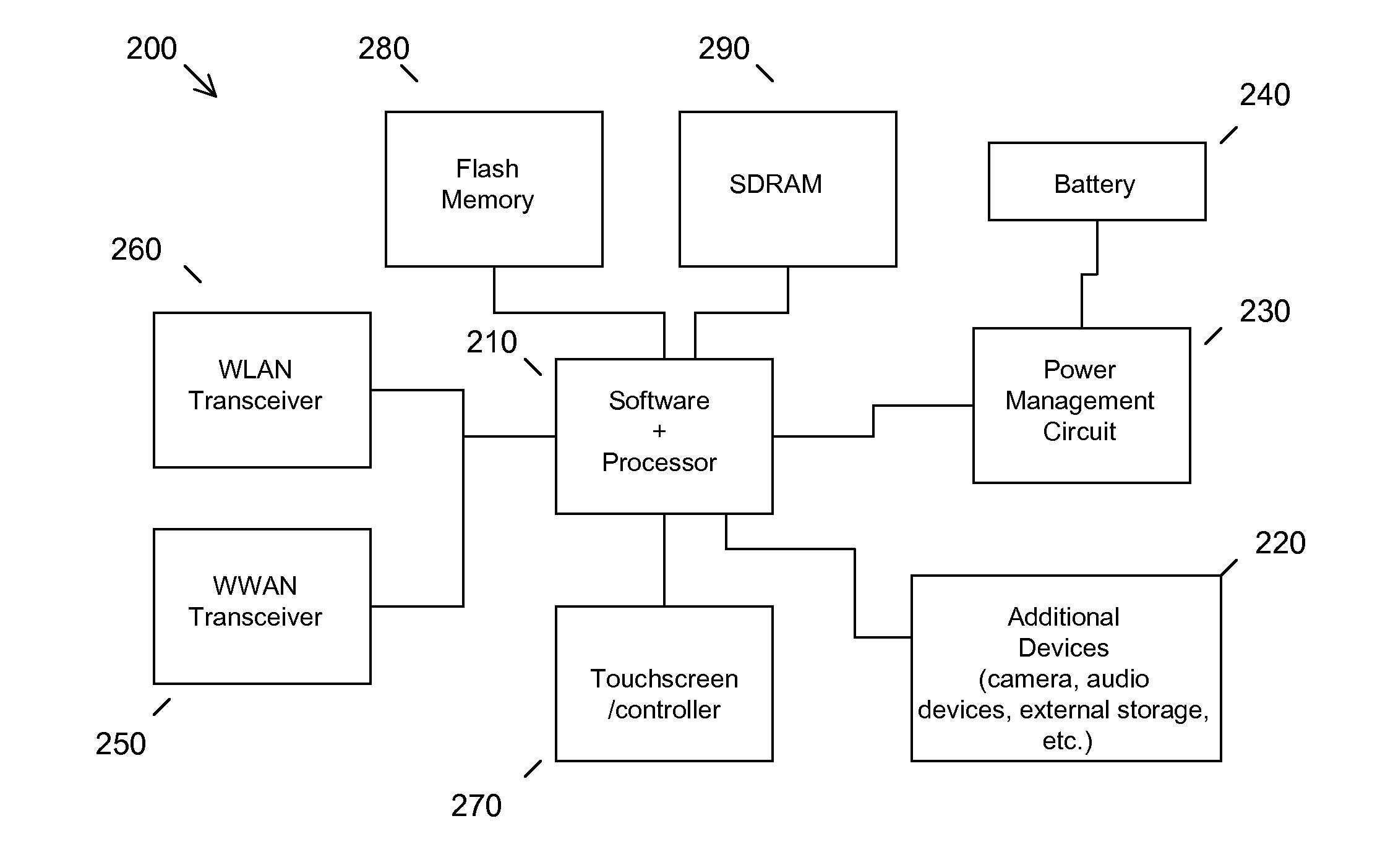
Removable storage device data protection
ActiveUS20130031376A1Unauthorized memory use protectionHardware monitoringFile systemRemovable media
Owner:LENOVO (SINGAPORE) PTE LTD
Encryption method, decryption method, and corresponding device and system
InactiveCN102726028APrevent leakageImprove securityInternal/peripheral component protectionSecuring communicationComputer hardwareClient-side
Owner:HUAWEI TECH CO LTD
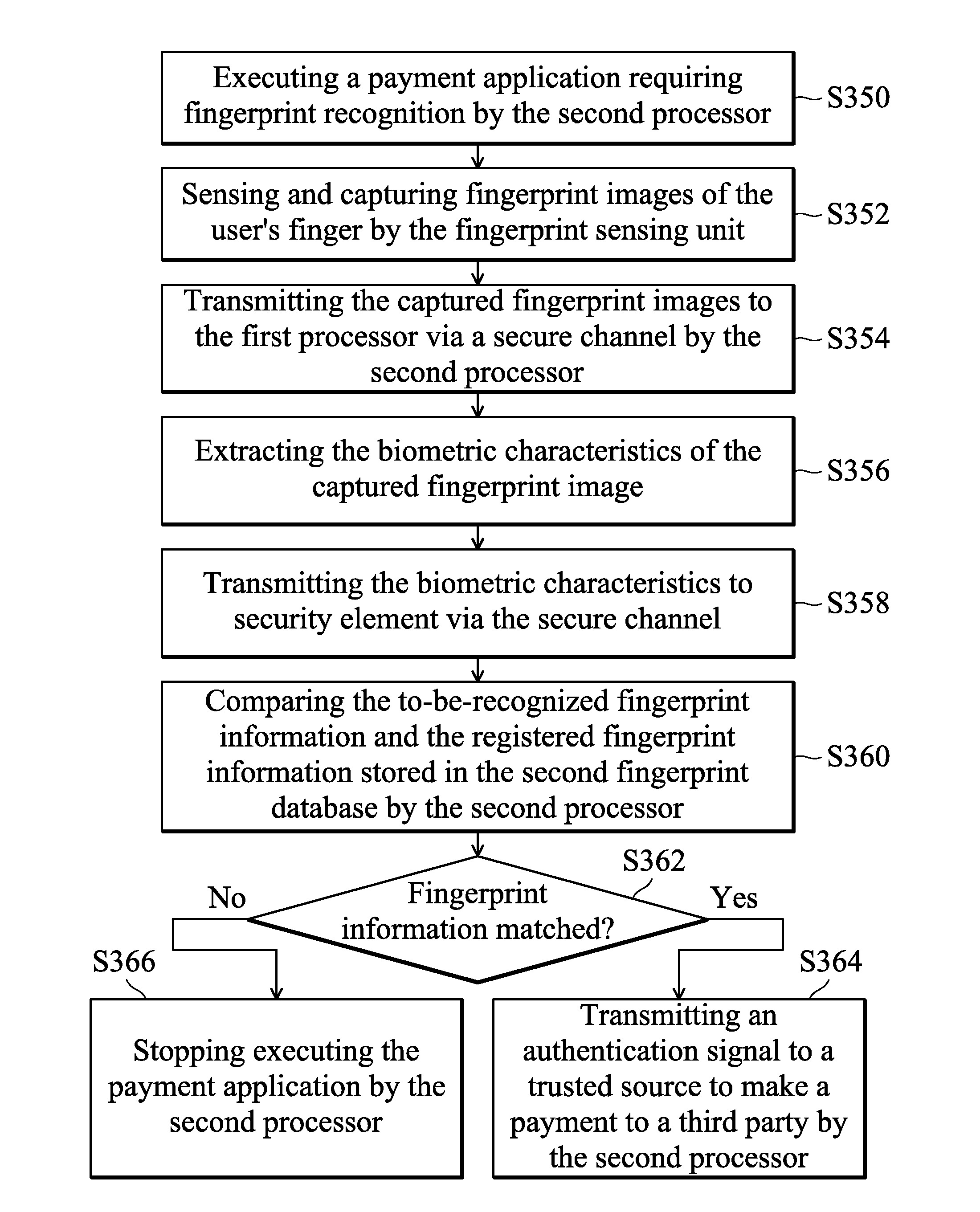
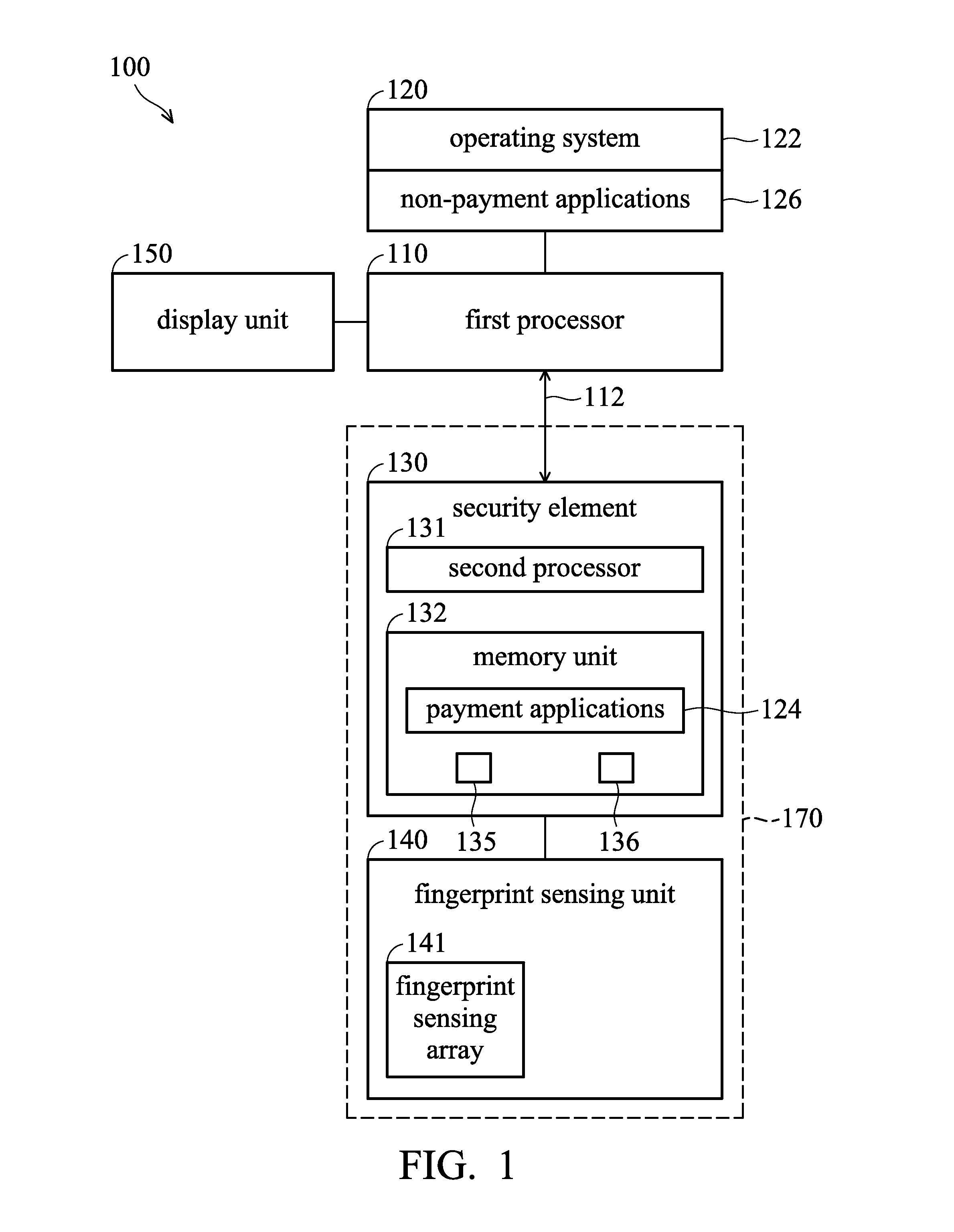
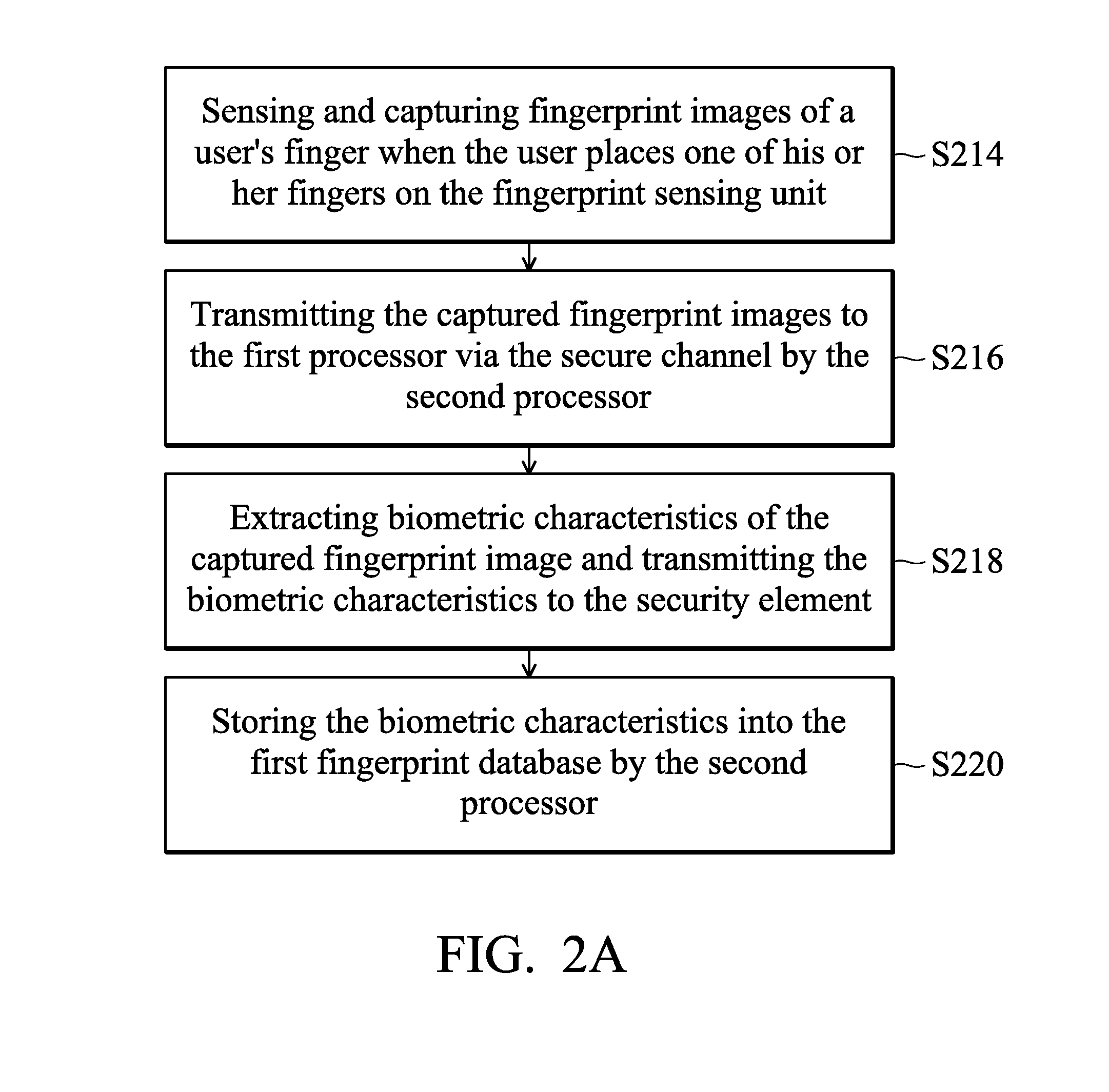
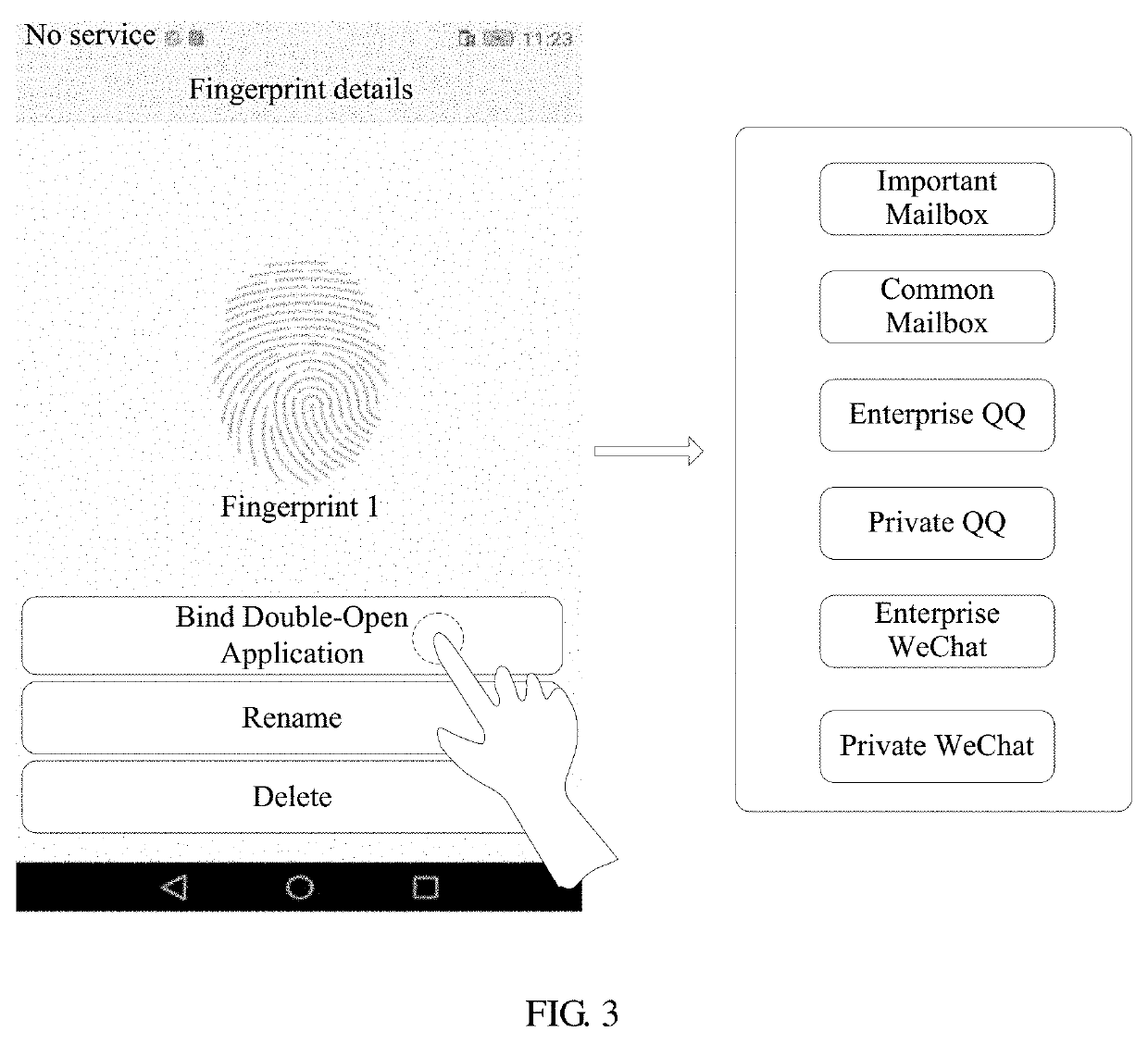
Fingerprint recognition control methods for payment and non-payment applications
ActiveUS20160048840A1Internal/peripheral component protectionDigital data authenticationPayment transactionComputer hardware
Owner:EGIS TECH
Authentication Method and Electronic Device
ActiveUS20190354661A1Complicated operationInternal/peripheral component protectionDigital data authenticationHuman–computer interactionAuthentication
Owner:HUAWEI TECH CO LTD
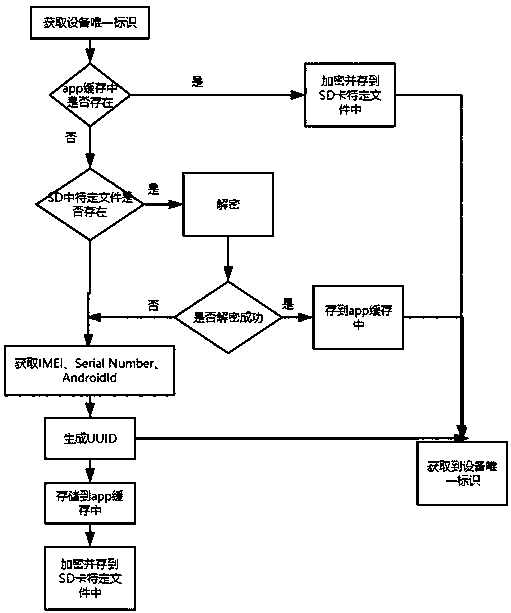
Method for acquiring unique identifier of Android equipment
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
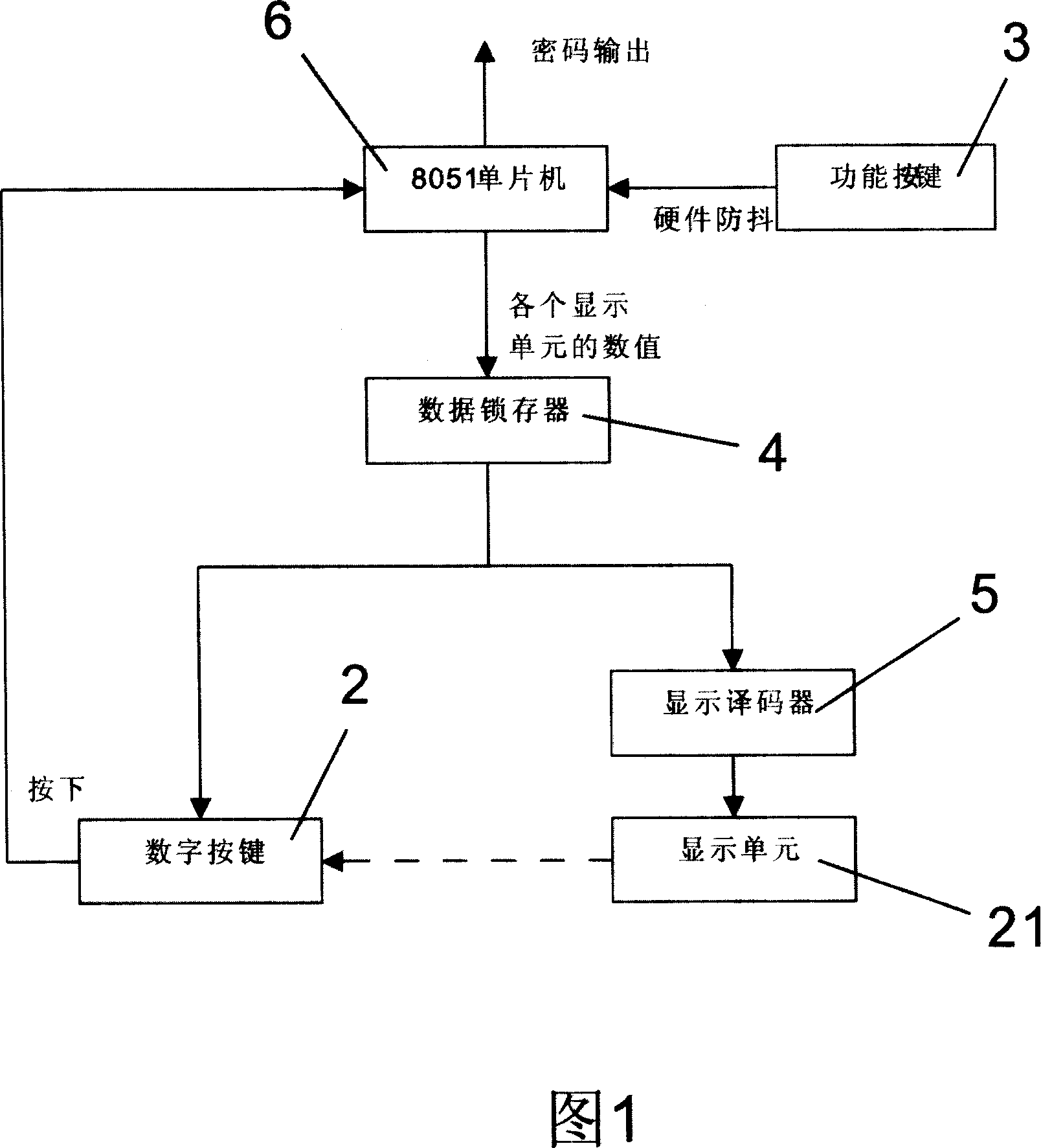
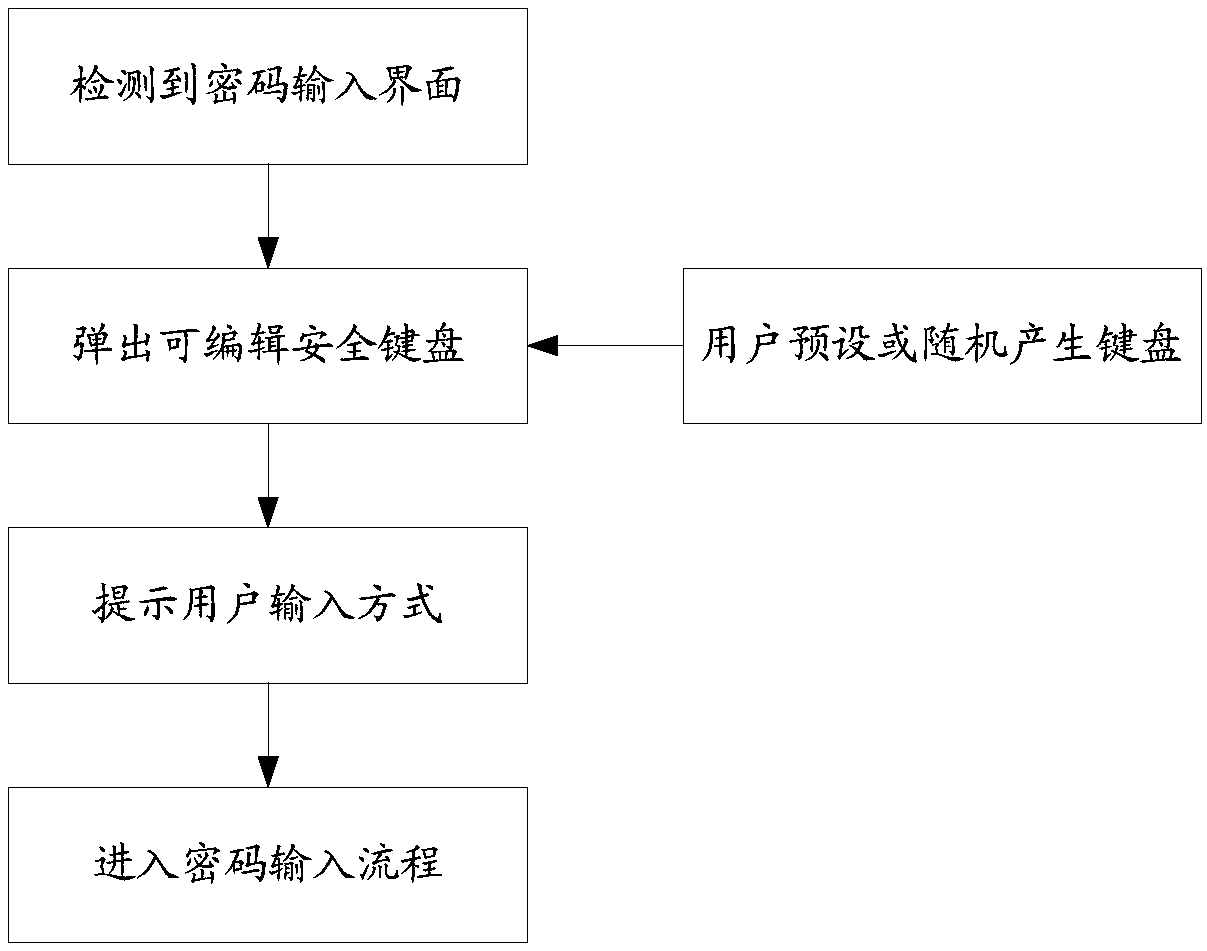
Dynamic displaying cipher keboard
InactiveCN101021756AProtection of rights and interestsPrevent password theftInternal/peripheral component protectionInput/output processes for data processingDriver circuitProcess dynamics
Owner:郭文 +1
Automated monitoring, detection, and reporting of unauthorized movement and/or theft of vehicles and cargo
A method and an enhanced electronic logging device (ELD) enable a load lock feature of a vehicle that assists with automated theft detection, reporting, and tracking of stolen vehicles / cargo. The processor of the ELD enables the ELD to register the operator MCD to receive notifications generated by a load lock module and present on a display of the ELD at least one selectable option for activating a load lock of the vehicle, the load lock identifying that the operator has parked the vehicle and has triggered the ELD to report any movement of the vehicle that occurs while the load lock is activated. The processor generates and transmits a notification of unauthorized movement or a potential theft of the vehicle in response to receiving an input from the movement detection device indicating that the vehicle is moving or being moved from a parked location while the load lock is activated.
Owner:OVERHAUL GRP INC
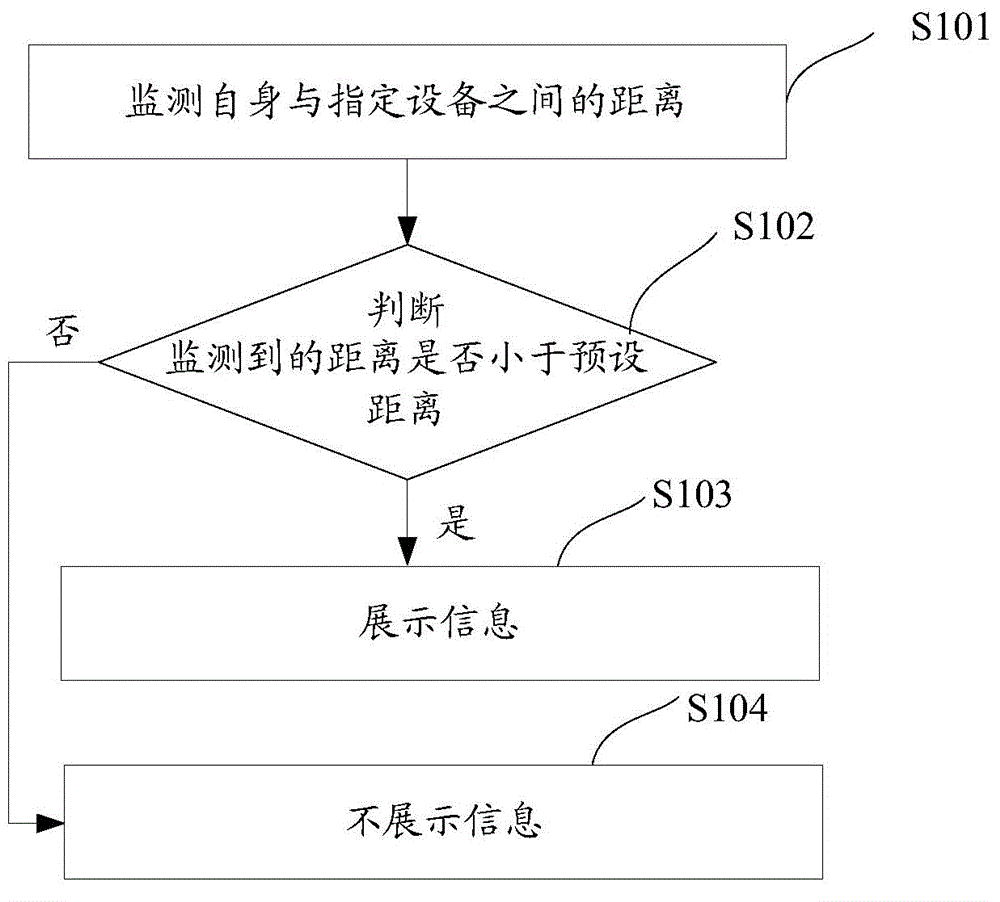
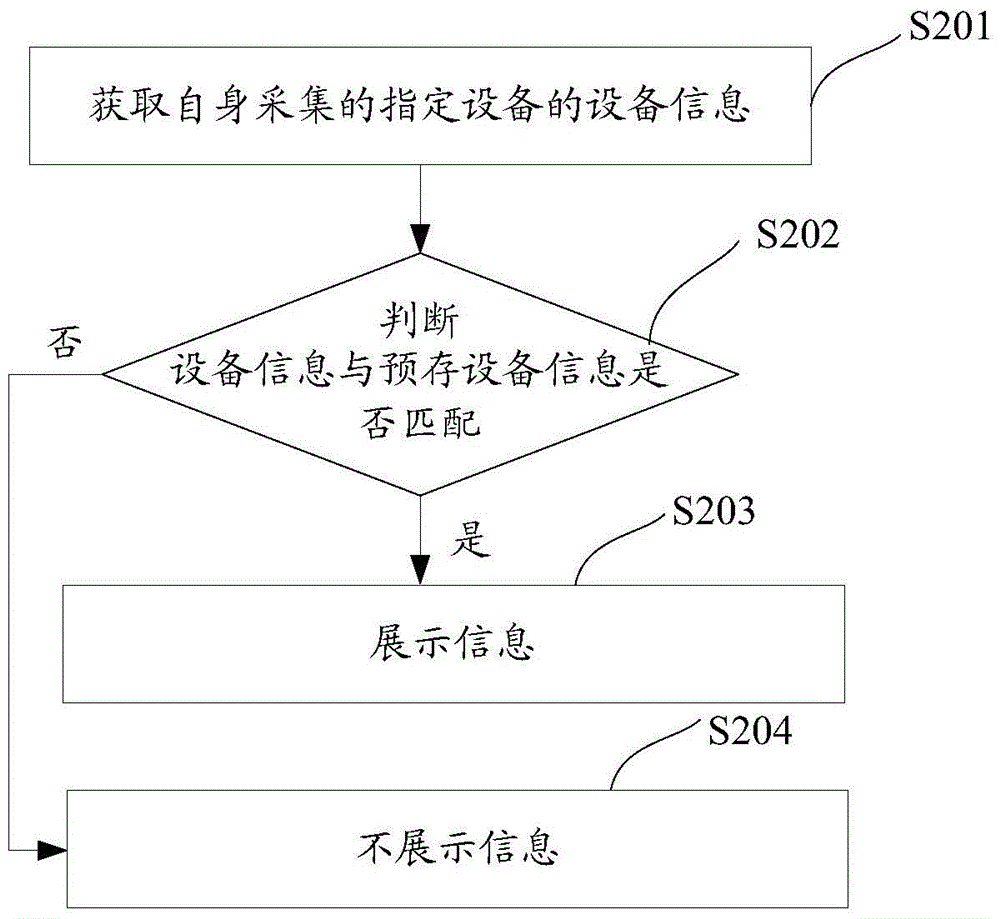
Information display method and device
ActiveCN105653963ADigital data protectionInternal/peripheral component protectionReal-time computingUser information
Owner:ADVANCED NEW TECH CO LTD
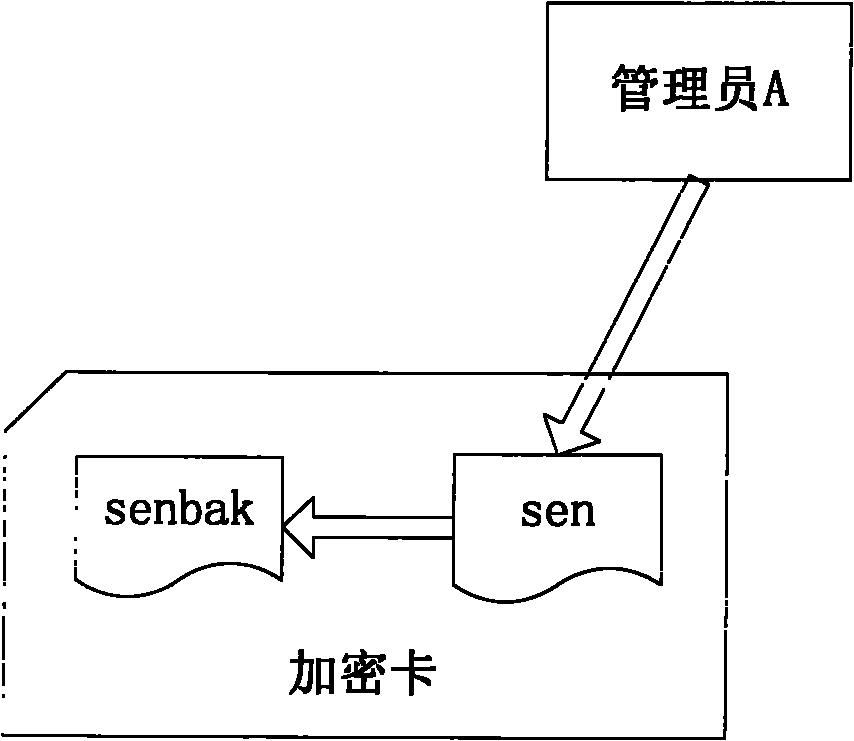
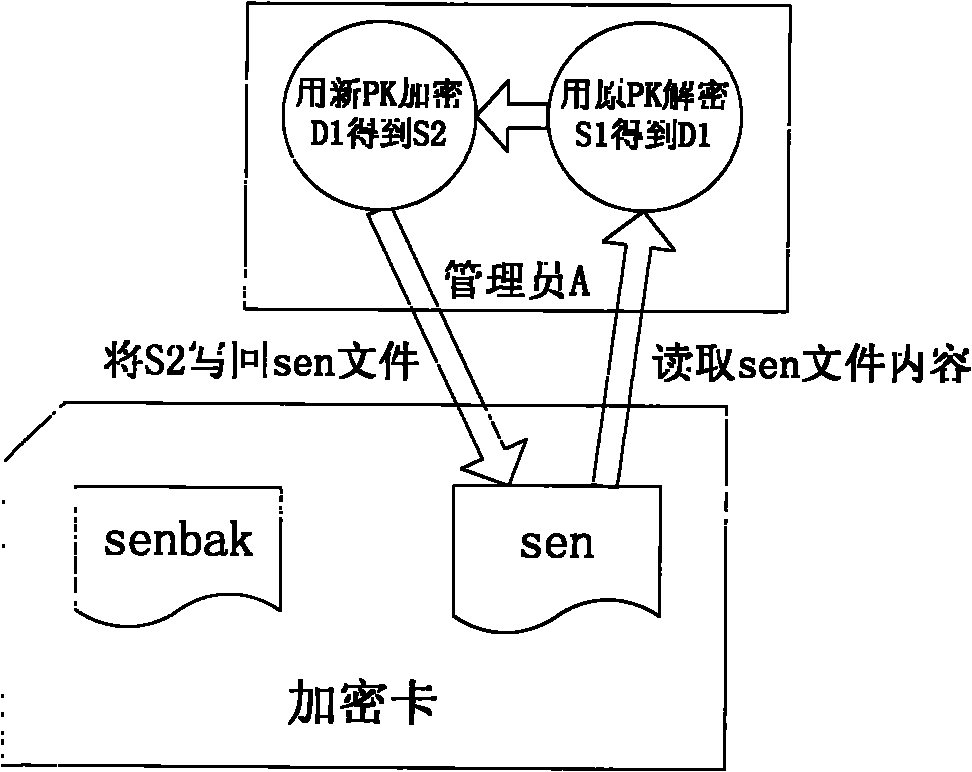
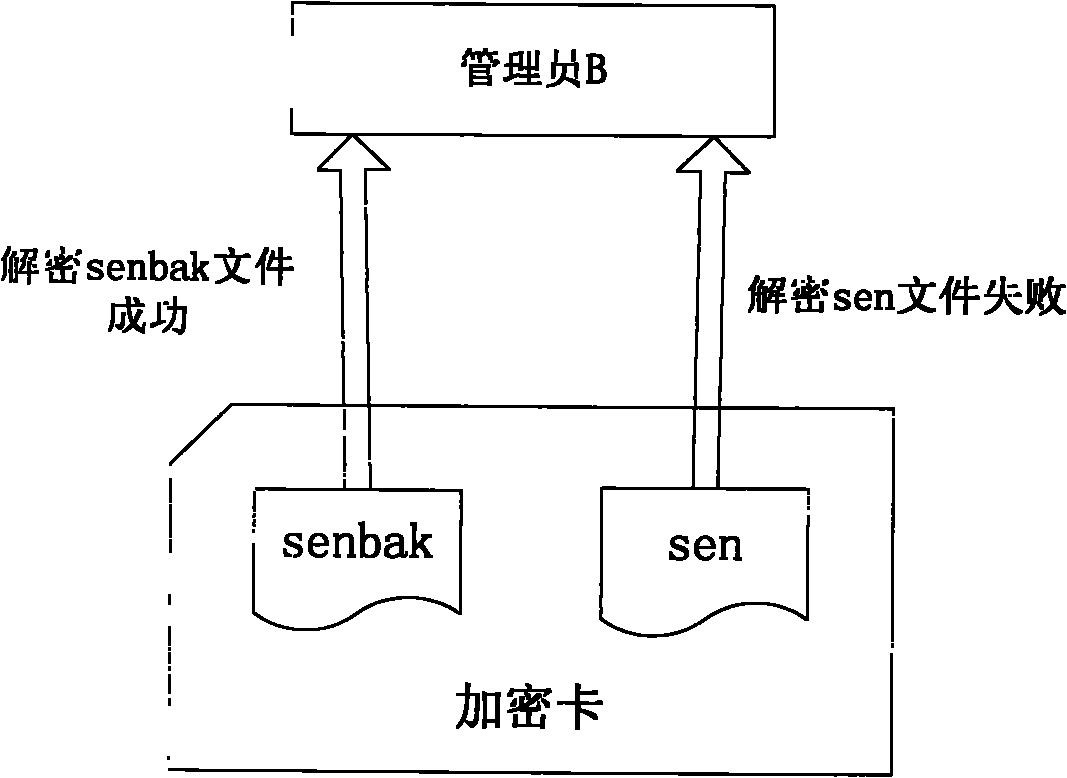
Method for restoring encrypted information in encryption card
ActiveCN102004873AGuaranteed to workInternal/peripheral component protectionRedundant operation error correctionComputer hardwareEncryption
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
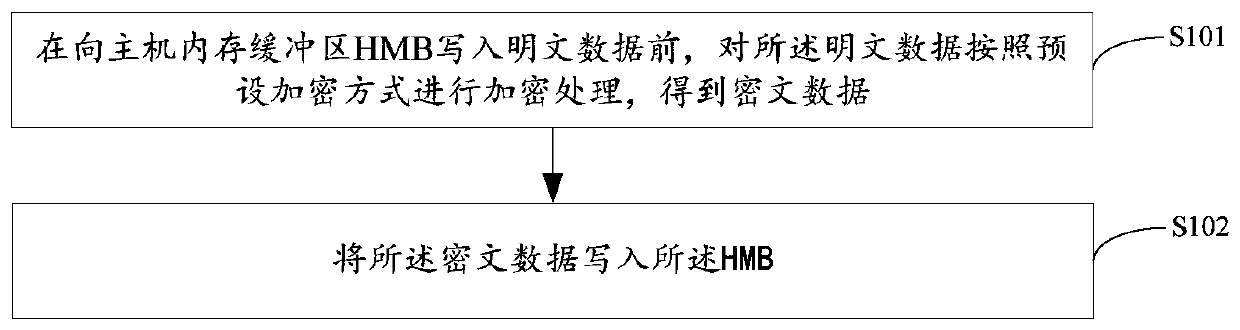
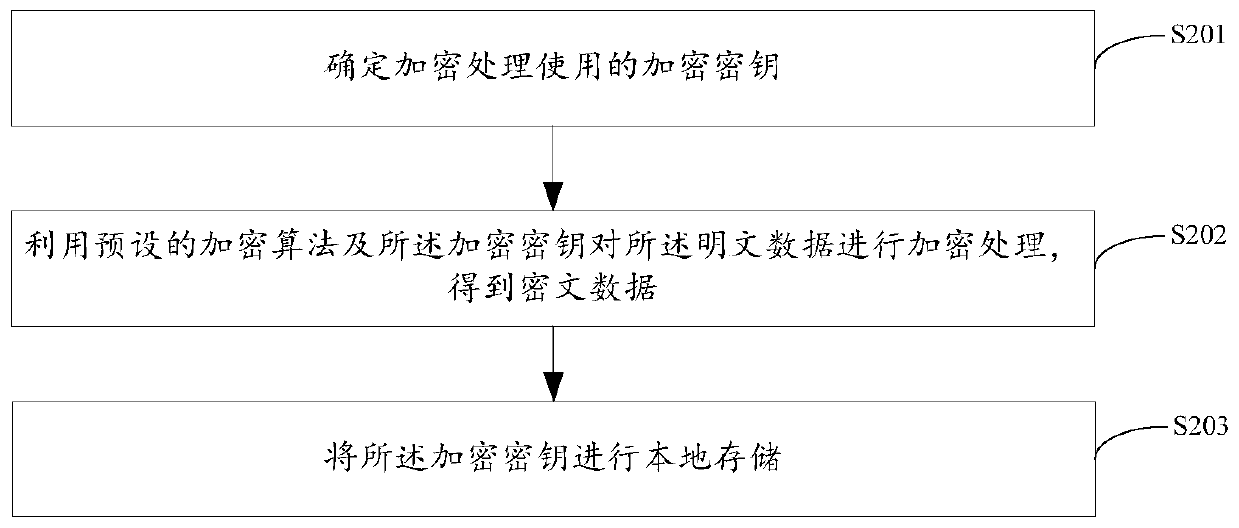
Data protection method and device, solid state disk and storage medium
PendingCN110472445AEnsure safetyDigital data protectionInternal/peripheral component protectionPlaintextCiphertext
Owner:SHENZHEN TIGO SEMICON
Display control method, terminal and computer readable storage medium
InactiveCN108322596AInternal/peripheral component protectionTelephone set constructionsComputer engineeringComputer terminal
Owner:NUBIA TECHNOLOGY CO LTD
Physical no-cloning technology based RFID card type intelligent door lock
InactiveCN108921995AImprove protectionImprove securityUser identity/authority verificationInternal/peripheral component protectionPasswordThe Internet
The invention discloses a physical no-cloning technology based RFID card type intelligent door lock. The physical no-cloning technology based RFID card type intelligent door lock comprises RFID cards,a door lock and a database, wherein the database is arranged on a background server; while ID which corresponds to the RFID cards is received, data is compared with data in the database through an internet; the database is used for storing ID which corresponds to each RFID card; a door lock inner chip comprises a PUF circuit; the RFID chip comprises an RFID module which is used for generating motivation; after receiving the motivation, the PUF circuit generates a corresponding secret key; and the database provides a matching source and is compared with the secret key generated by the PUF circuit, so that authentication is realized, and therefore, unlocking is performed based on a door lock password authentication mode. The PUF circuit can resist probe attack and physical attack, and is not stored with the secret key information, so that other people cannot read a chip secret key through a probe and the like to steal inner information, and therefore, safety of the door lock is greatlyimproved.
Owner:HOHAI UNIV CHANGZHOU
System and method for device authorization and remediation
ActiveUS20150281190A1Digital data processing detailsUser identity/authority verificationDiagnostic dataRestoration device
A method is provided for authorizing a device for consuming content. In method includes the steps of generating an authorization request, the authorization request for authorization data including device diagnostic data (instructions) an device remedial data (instructions), transmitting the authorization request from the device to an authorizing service, and authorizing or remediating the device according to an authorization response to the authorization request received from an authorization server.
Owner:ARRIS ENTERPRISES LLC
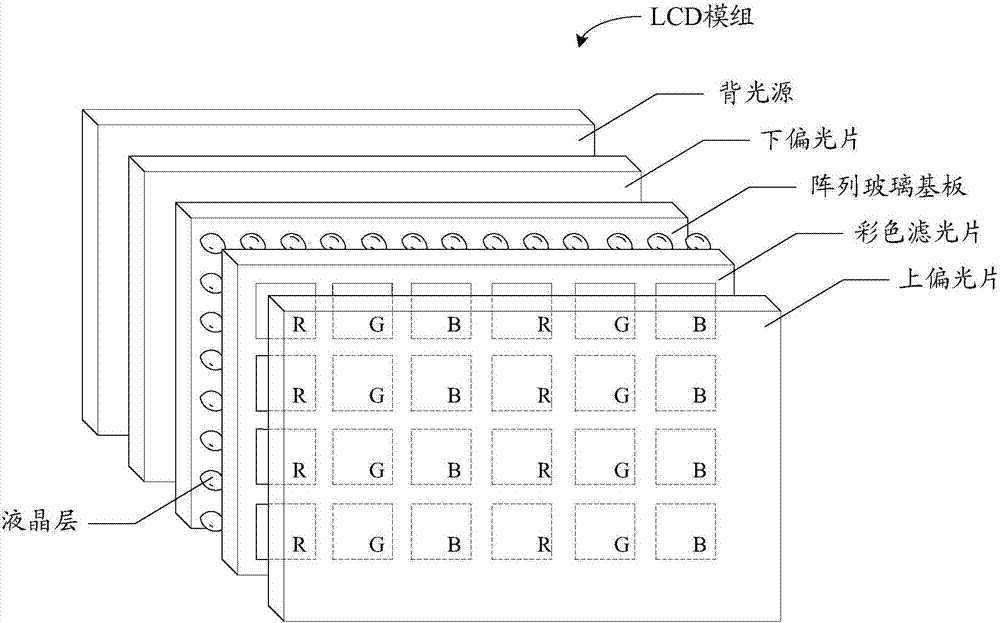
Image processing apparatus, image processing program and image processing method
InactiveUS20060152751A1Improve ease of useReduce manufacturing costDigital data protectionInternal/peripheral component protectionImaging processingComputer graphics (images)
Owner:KK TOSHIBA +1
Information display method and related product
InactiveCN110298207AInternal/peripheral component protectionDigital data authenticationFingerprintElectronic equipment
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method and apparatus for managing private data in multi-function products
ActiveUS20070043953A1Prevent unauthorized accessDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
Owner:HEWLETT PACKARD DEV CO LP
Computer information leakage prevention device and use method
Owner:河北盘古网络技术有限公司
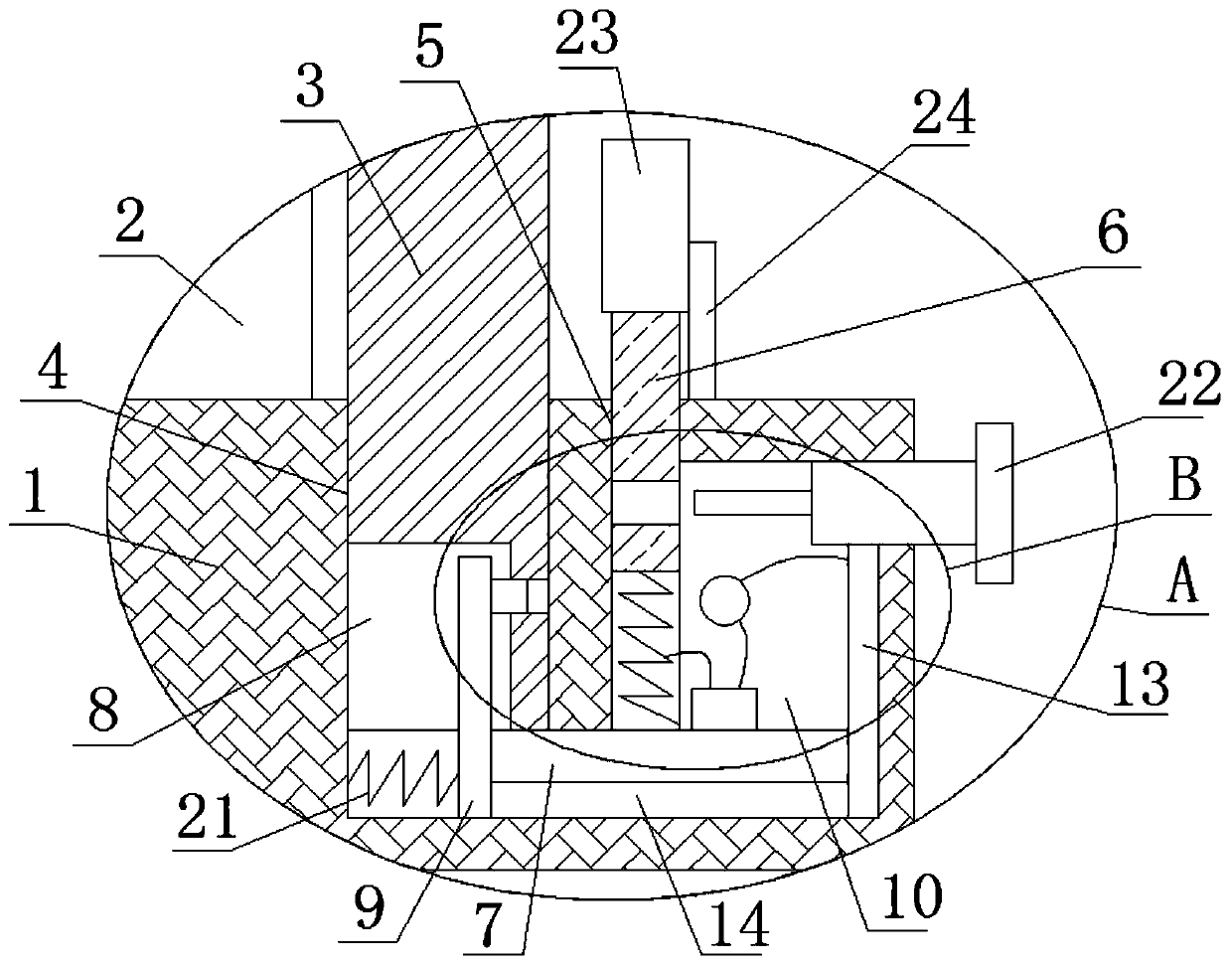
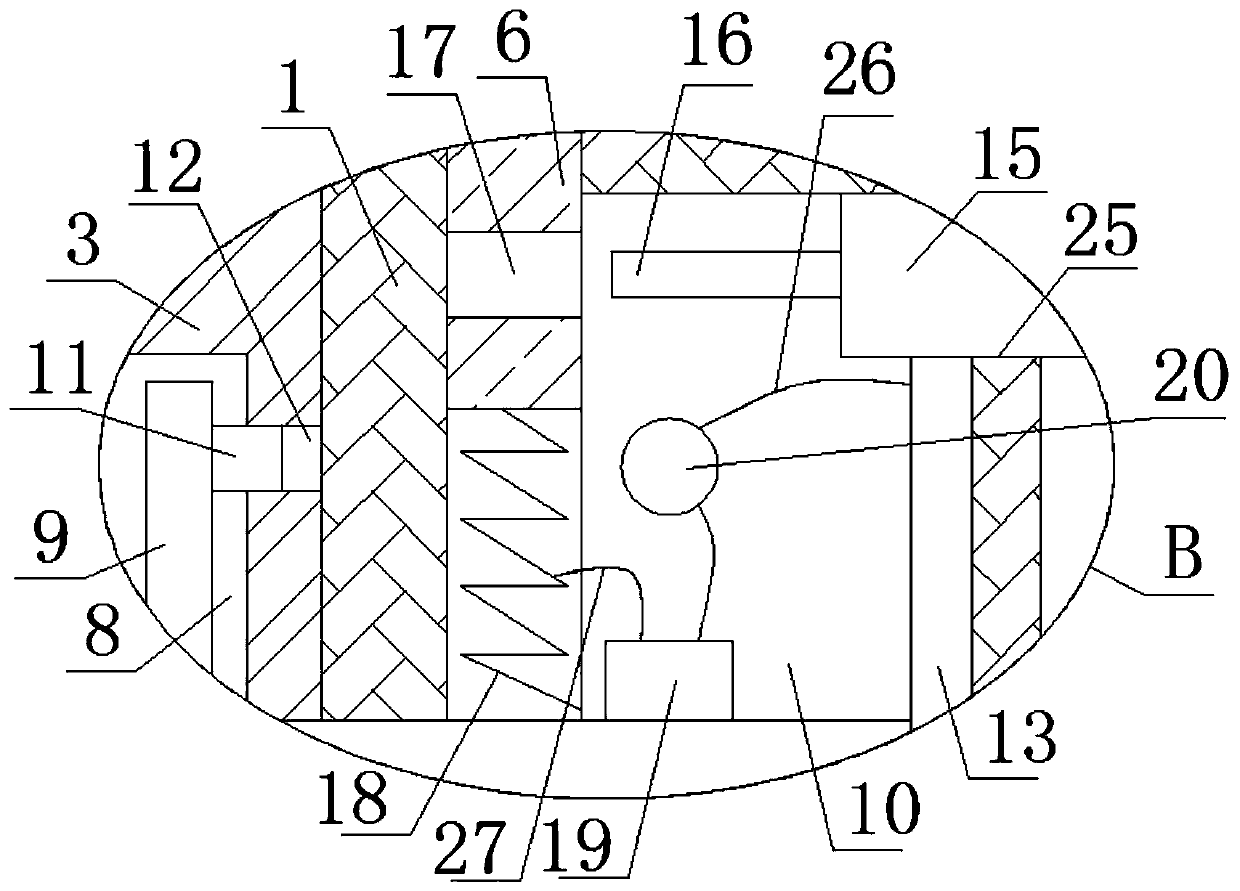
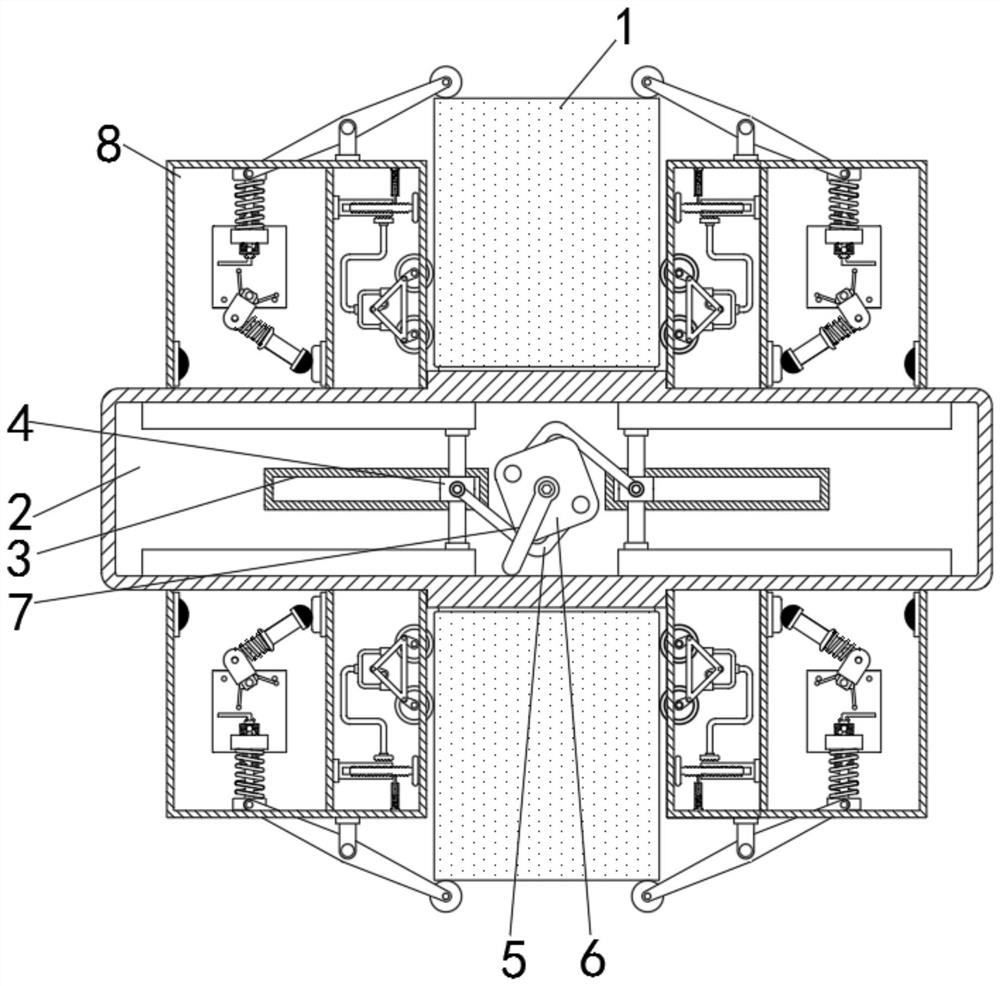
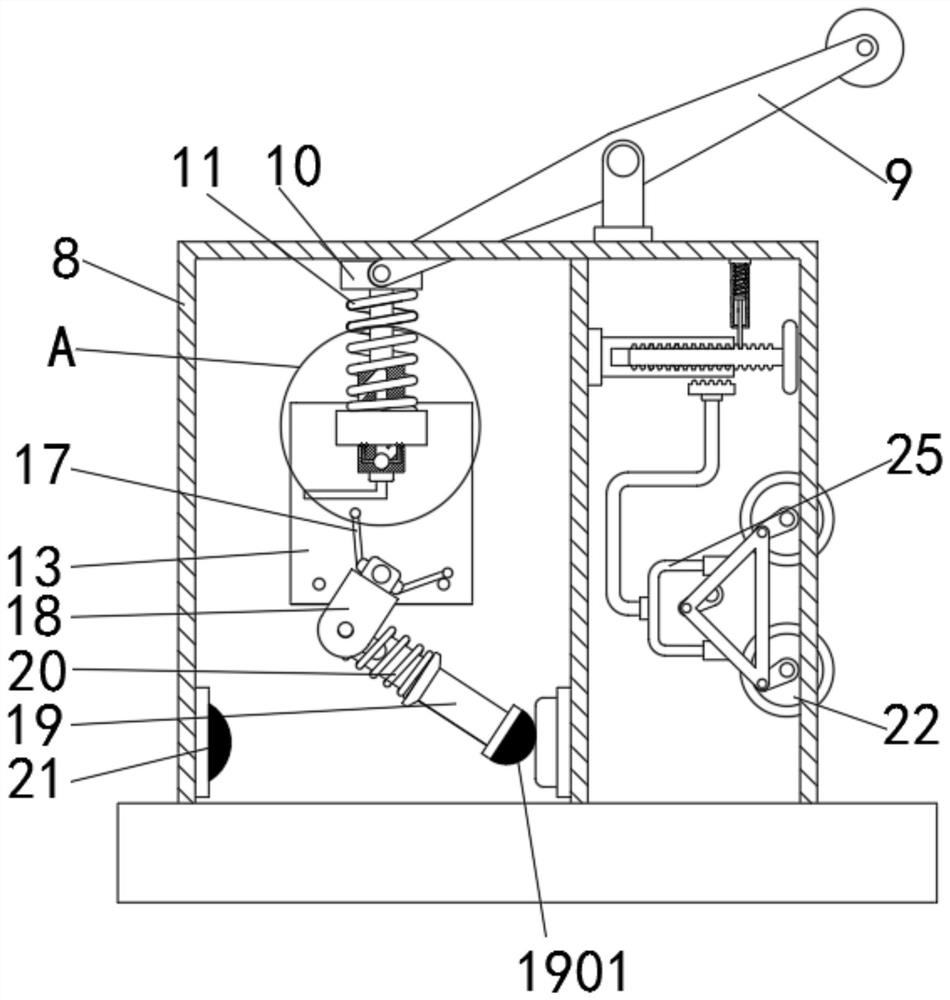
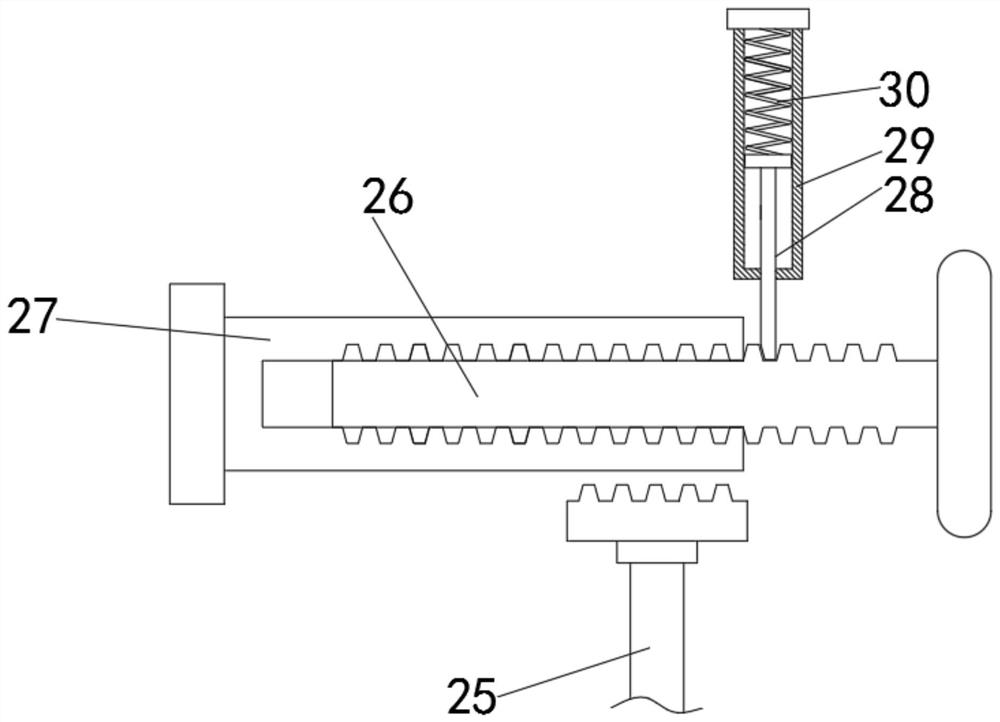
Intelligent anti-theft alarm computer hardware protection device with locking function
InactiveCN112434353AImprove securityWith lock functionInternal/peripheral component protectionEmbedded systemComputer hardware
The invention relates to the technical field of network information security, and discloses an intelligent anti-theft alarm computer hardware protection device with a locking function, which comprisesa hardware main body, a computer component is inserted into the inner side of the hardware main body, and a second connecting rod is arranged on the lower side of a first connecting rod; a first rotating block is rotatably connected to the lower side of the second connecting rod, a first moving rod is rotatably connected to the lower side of the first rotating block, a second spring is arranged on the outer side of the first moving rod, a first metal block is fixedly connected to the lower side of the first moving rod, and a second metal block is arranged on the left side of the first movingrod. According to the computer hardware protection device with the intelligent anti-theft alarm function and the locking function, through the action of a second spring and a key groove in a first moving rod, the first moving rod is driven to rotate, a first metal block makes contact with a second metal block, and therefore an external alarm device is connected; by means of the structure, the effects of intelligent anti-theft alarm and high safety are achieved.
Owner:朱诵伟
Method, system and device for enhancing security of storage media and medium
ActiveCN113111396AFix security issuesSolve too manyDigital data protectionInternal/peripheral component protectionInternet privacyEngineering
Owner:湖北央中巨石信息技术有限公司
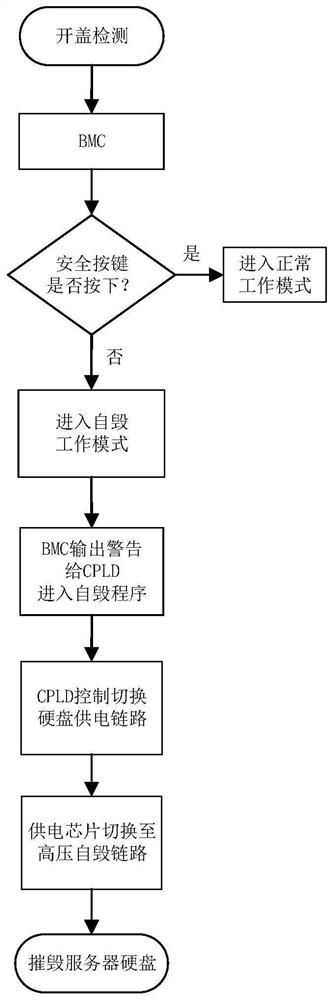
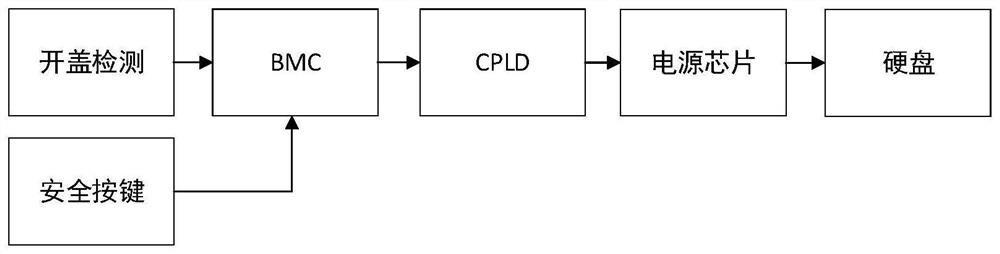
Server cover opening detection method and system
PendingCN113138901AImprove confidentialityIncreased data protectionHardware monitoringInternal/peripheral component protectionProgrammable logic deviceComplex programmable logic device
Owner:SHANDONG YINGXIN COMP TECH CO LTD
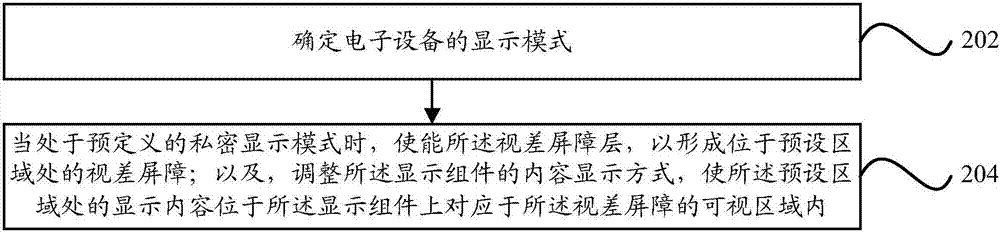
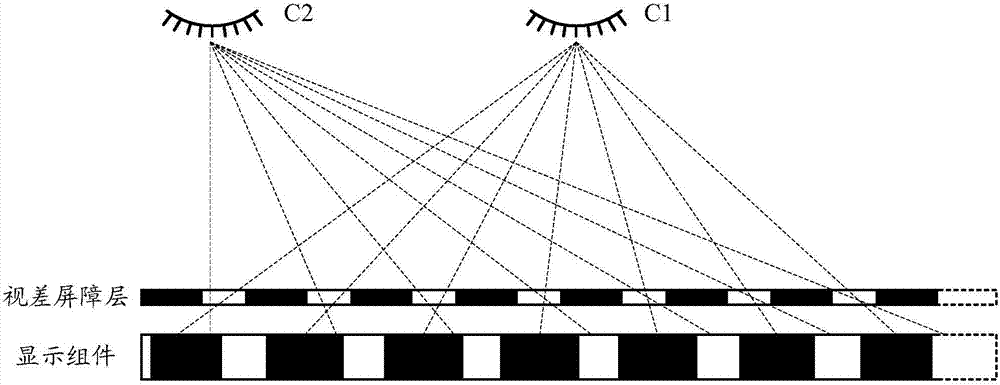
Display method and apparatus, and electronic device
PendingCN107229884AImprove privacyInternal/peripheral component protectionComputer graphics (images)Parallax barrier
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
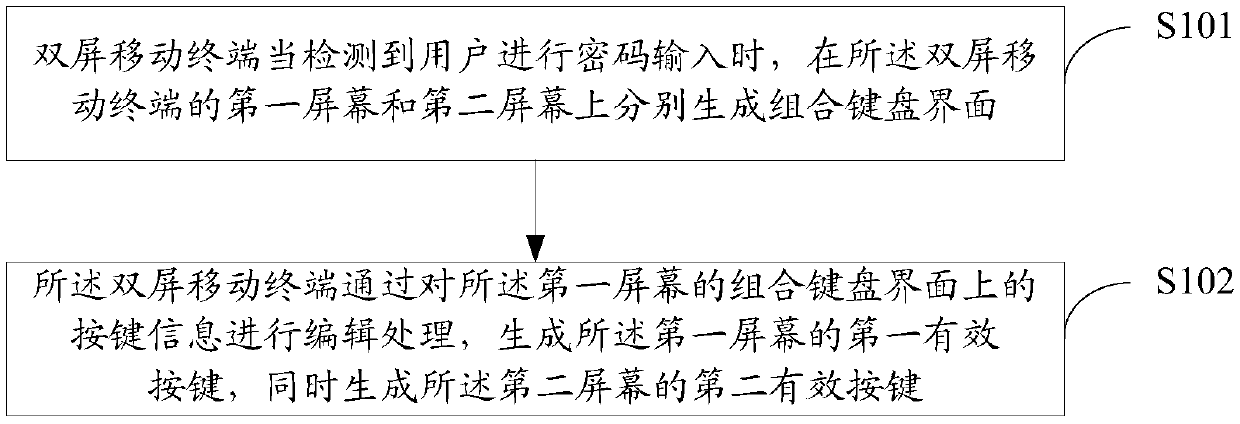
Method, device and equipment for generating password input keyboard, and storage medium
InactiveCN111062065ASolve the security problem of password inputIncreased sensitivityDevices with multiple keyboard unitsDevices with multiple display unitsComputer hardwareKey pressing
Owner:ZTE CORP
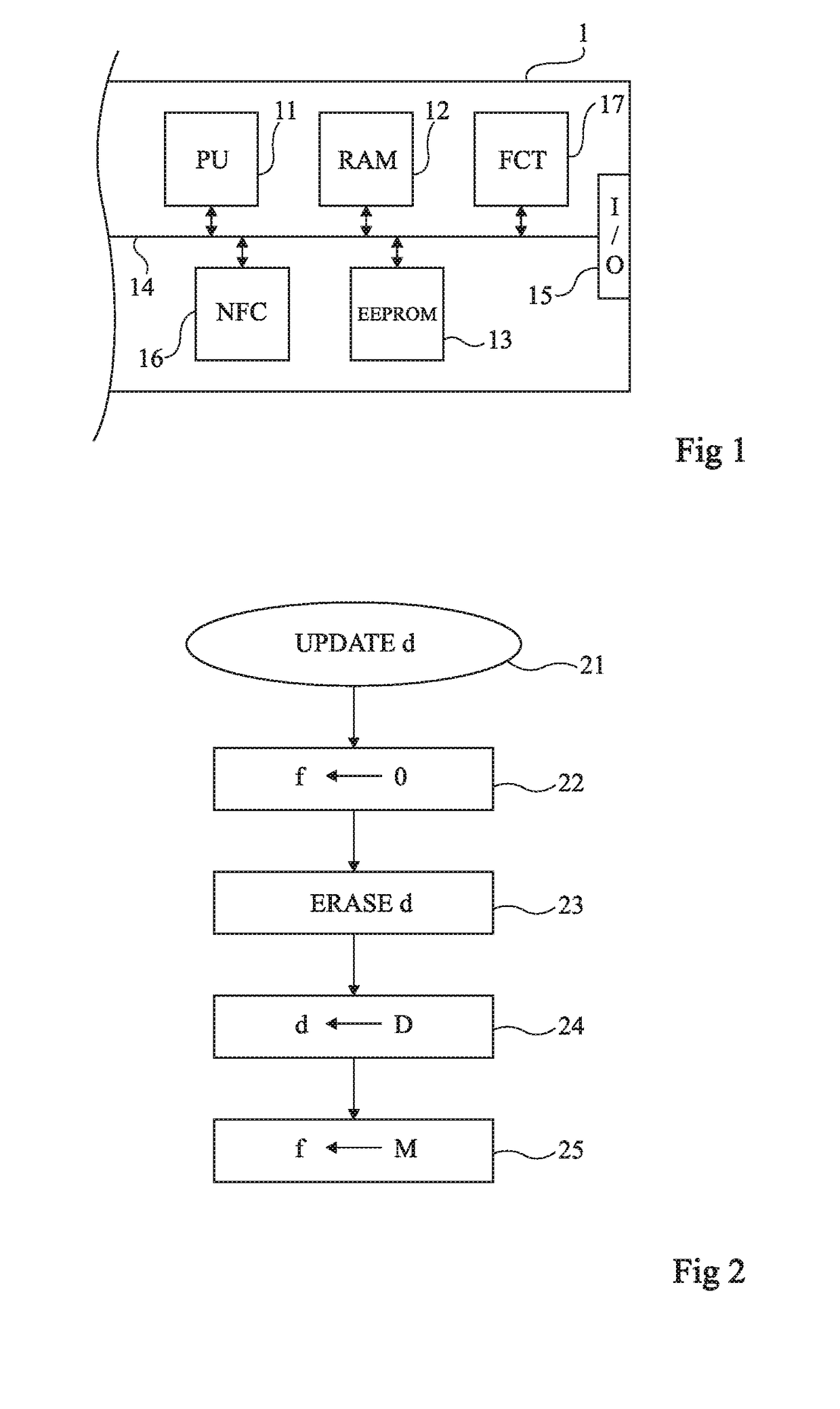
Atomicity management in an eeprom
Owner:PROTON WORLD INT
Popular searches
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap