Method for restoring encrypted information in encryption card
A technology for encrypting information and implementing methods, applied in the field of encrypted cards, can solve the problems of inability to decrypt sensitive data, administrators unable to log in to start the encrypted card, unable to use data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] specific implementation plan
[0014] The method of the present invention will be described below in conjunction with the accompanying drawings and specific embodiments.
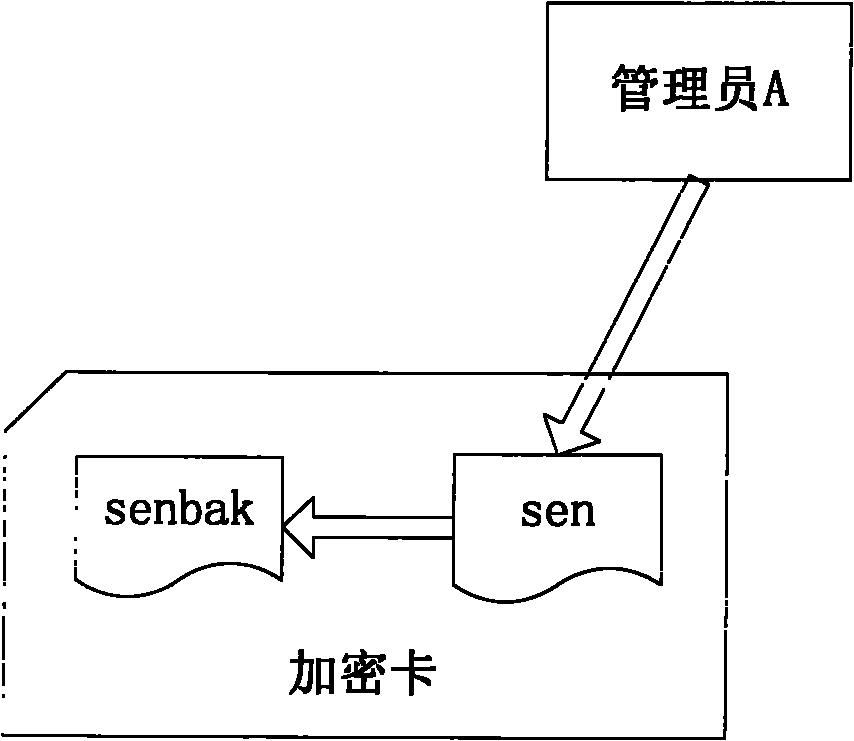
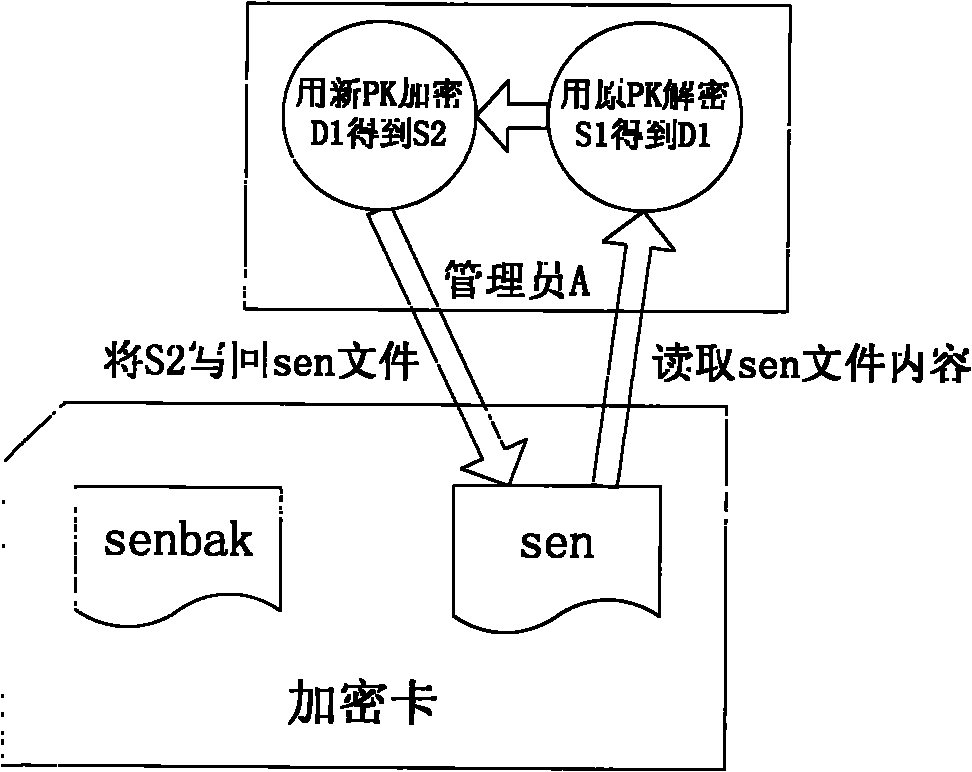
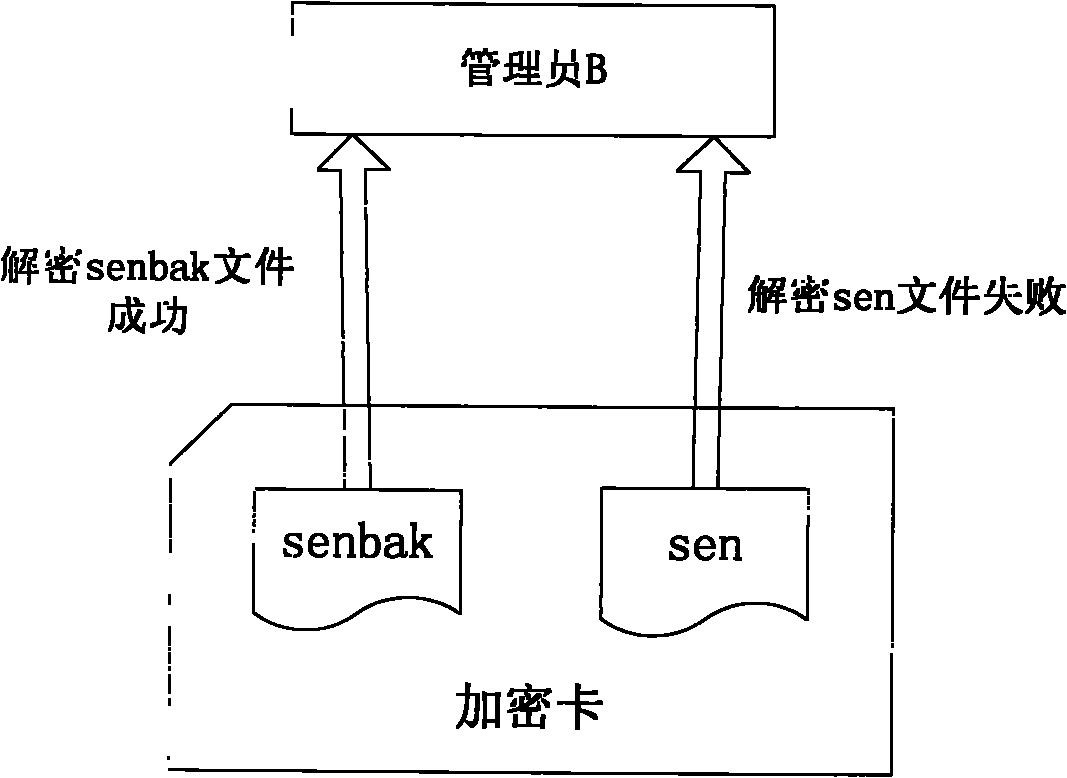
[0015] Such as figure 1 As shown, if administrator A wants to update the protection key, he must first create a backup file senbak of the sensitive ciphertext information sen in the card; secondly, if figure 2 As shown, the administrator A reads the content of the sen file into the memory, we use S1 to identify it, decrypt S1 with the original protection key PK1, and obtain the plaintext data D1, and then administrator A saves the newly generated protection key PK2 in the IC card or In the USB Key, encrypt D1 with PK2 to get a new ciphertext S2, administrator A writes S2 into the file sen, overwrites the original content of sen, and identifies himself in the file attribute to update the file, so far administrator A has completed The update work of the protection key. Administrator B needs to use the
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap