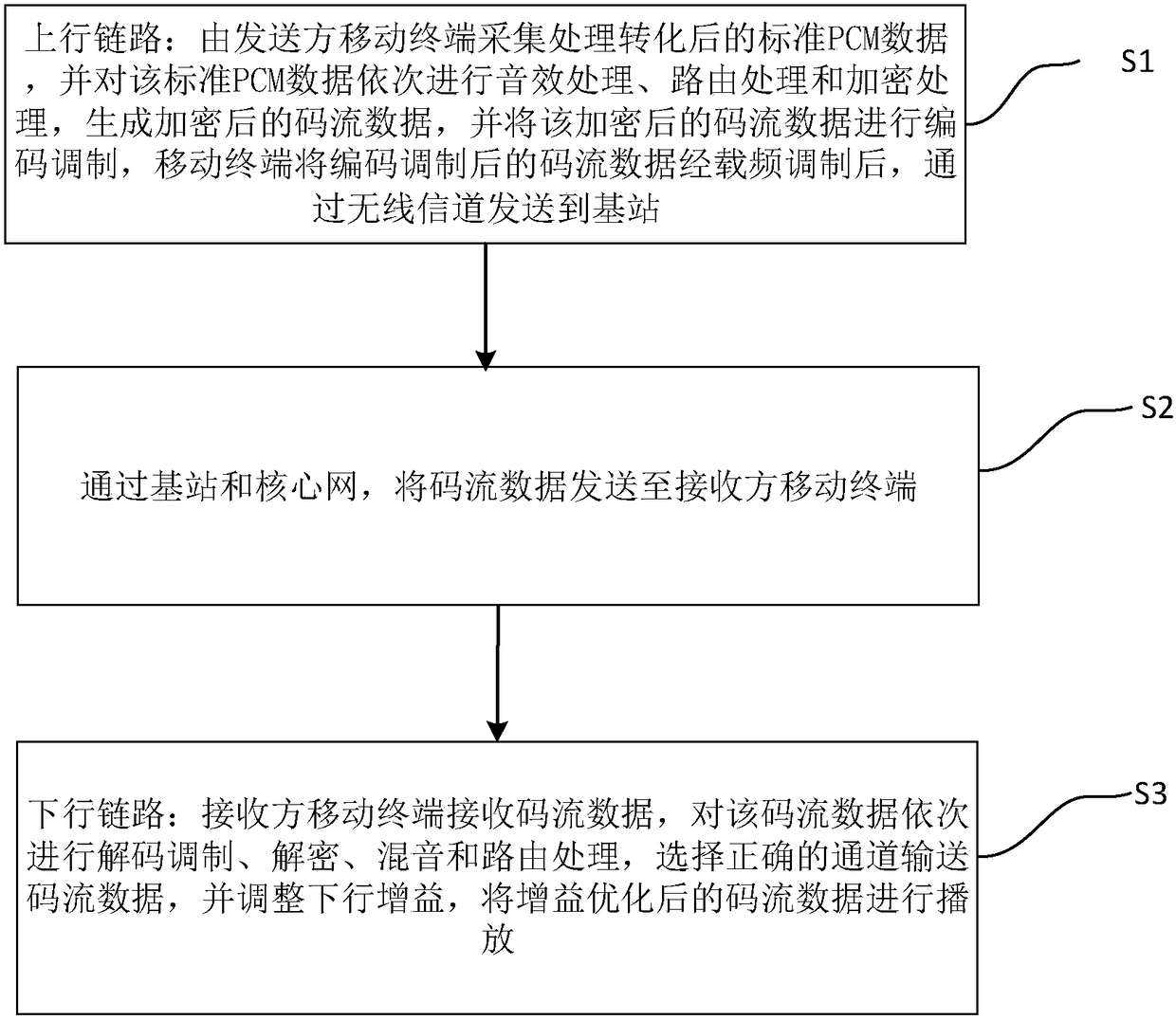
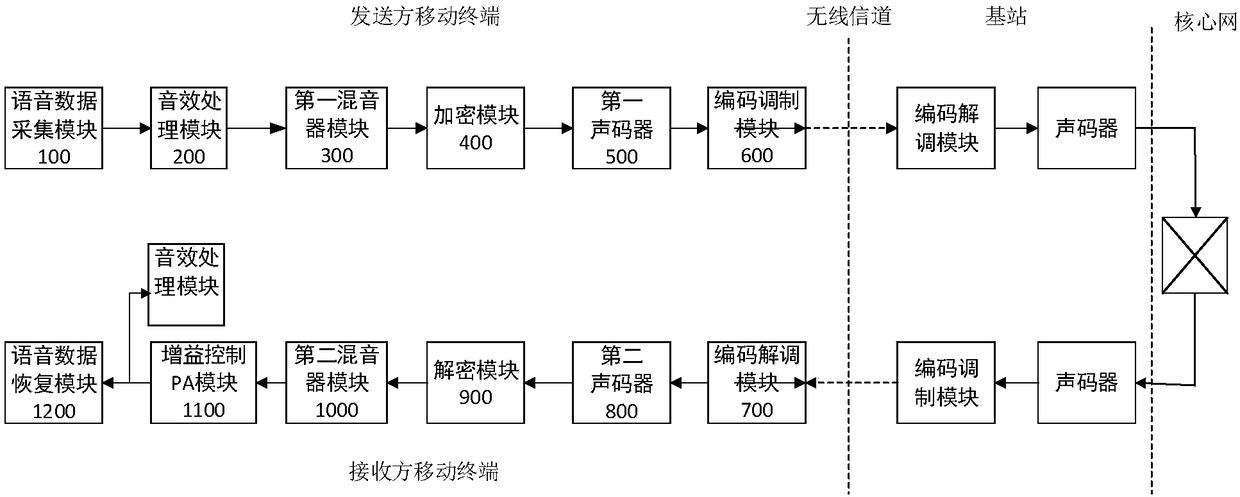
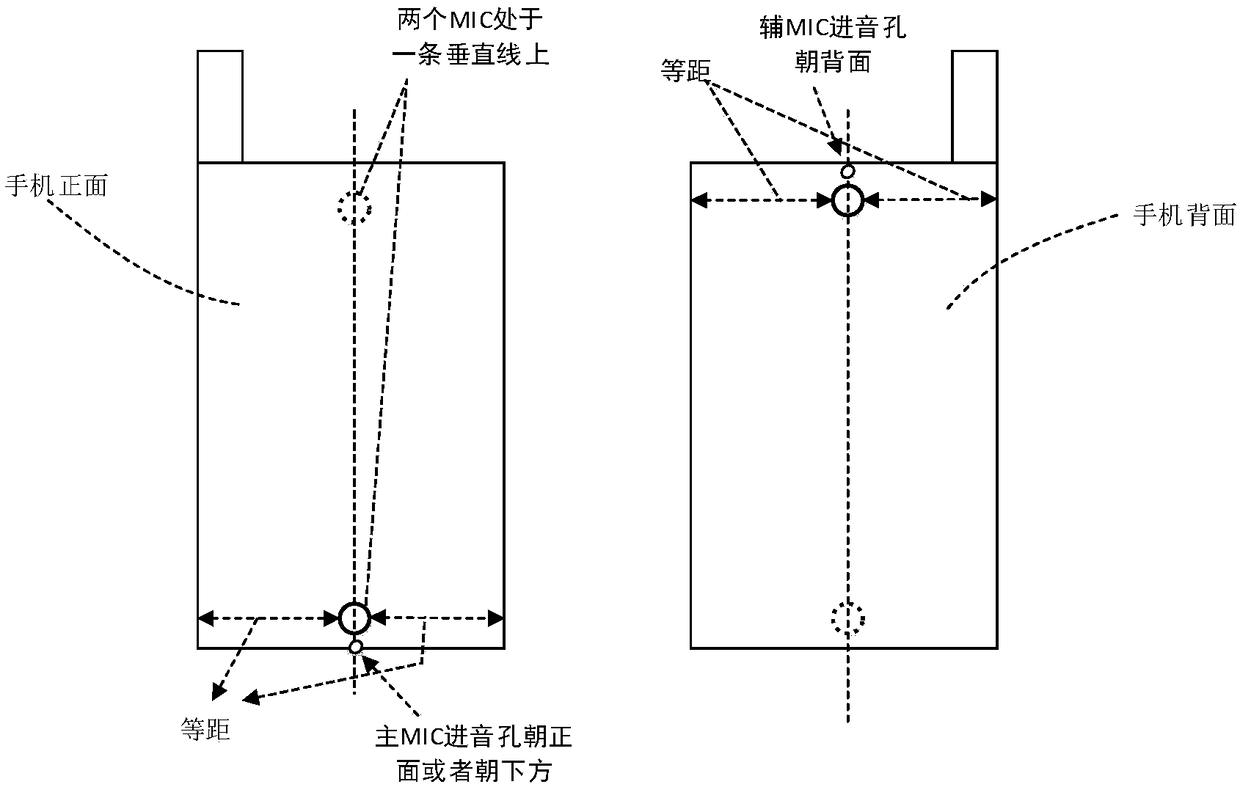
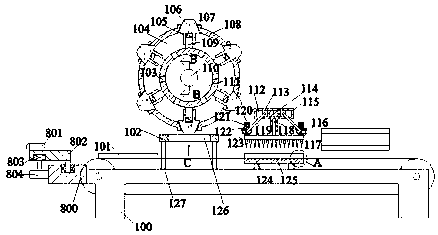
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "Encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, encryption is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. Encryption does not itself prevent interference, but denies the intelligible content to a would-be interceptor. In an encryption scheme, the intended information or message, referred to as plaintext, is encrypted using an encryption algorithm – a cipher – generating ciphertext that can be read only if decrypted. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is in principle possible to decrypt the message without possessing the key, but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users.
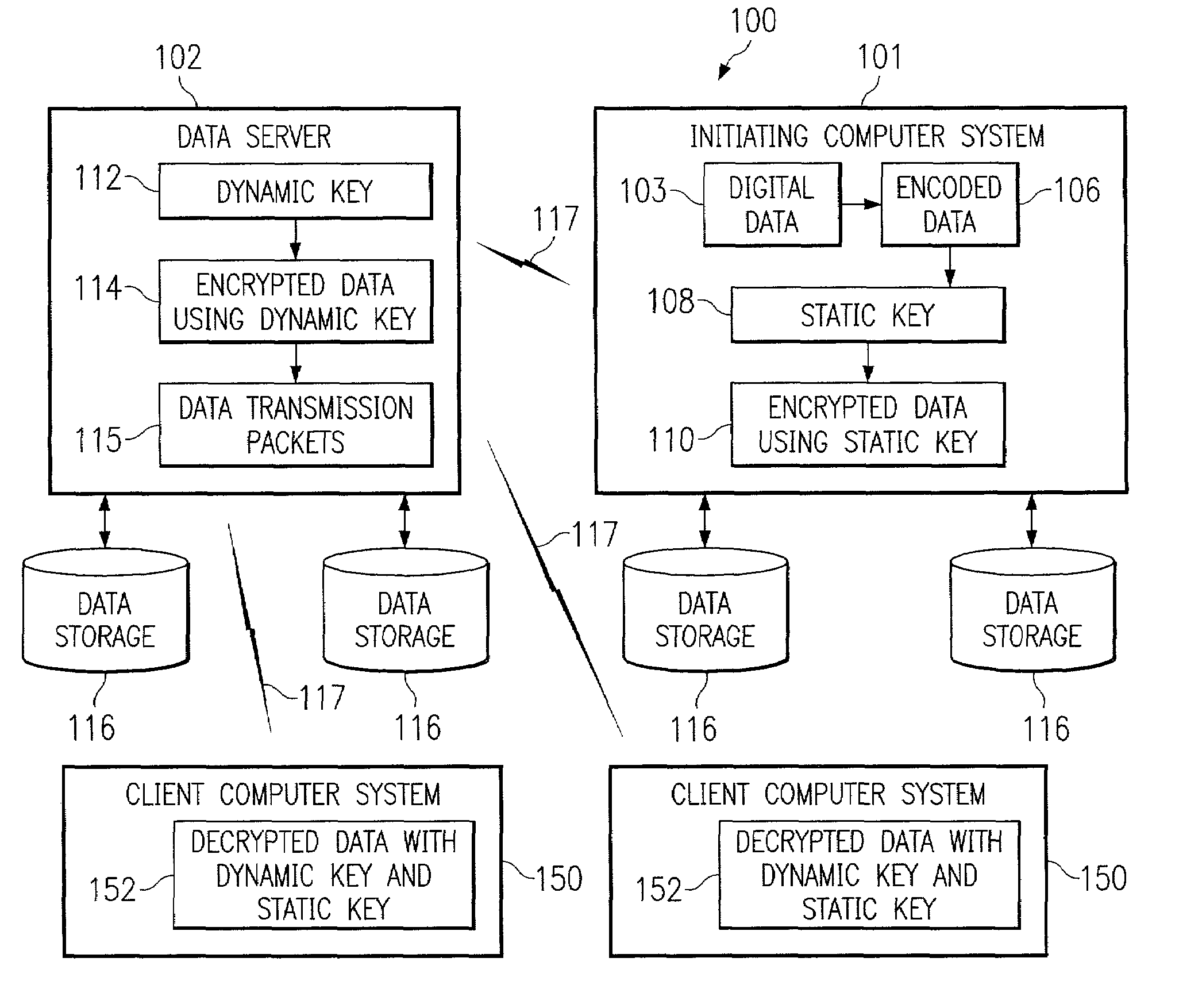
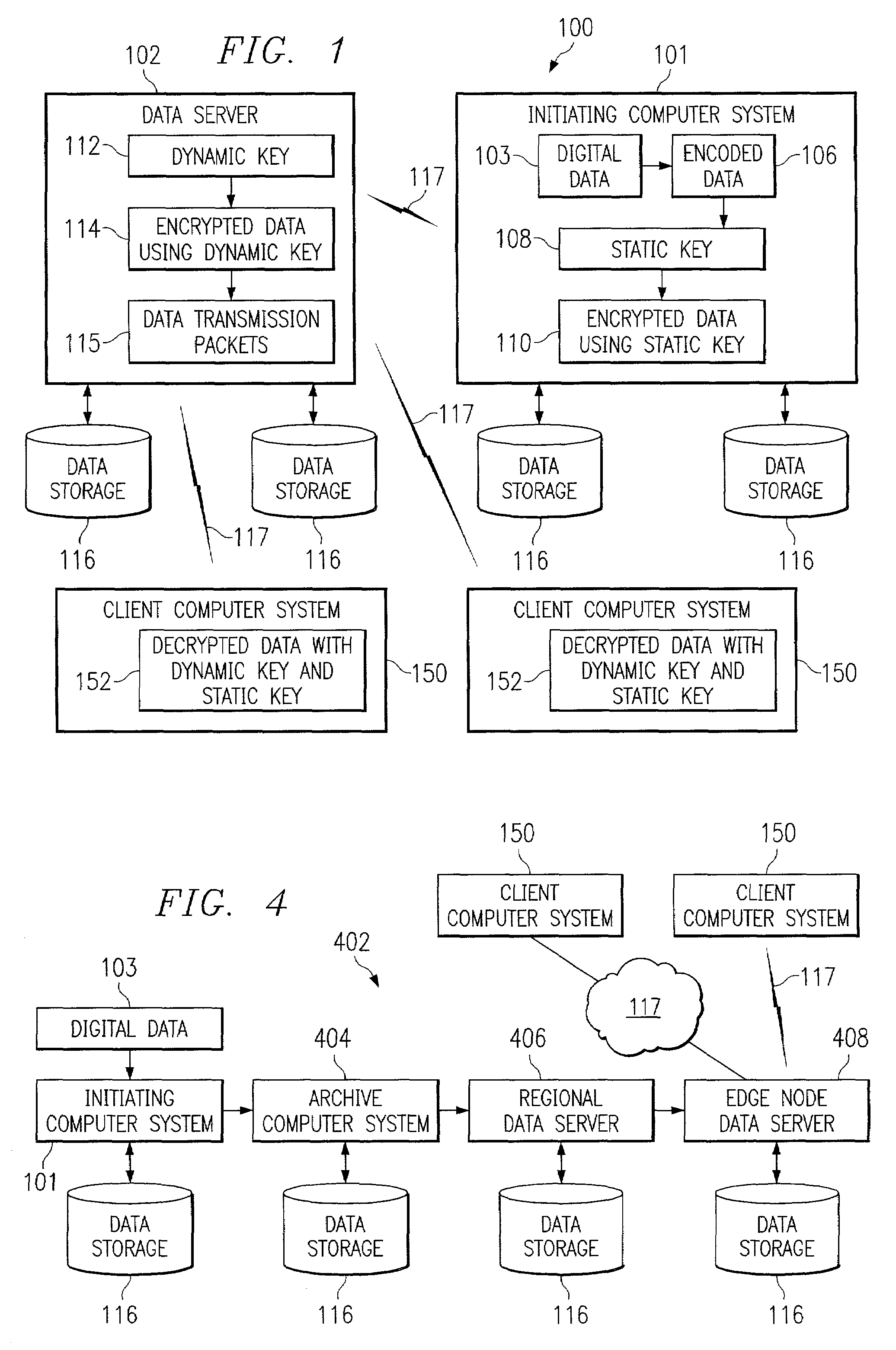
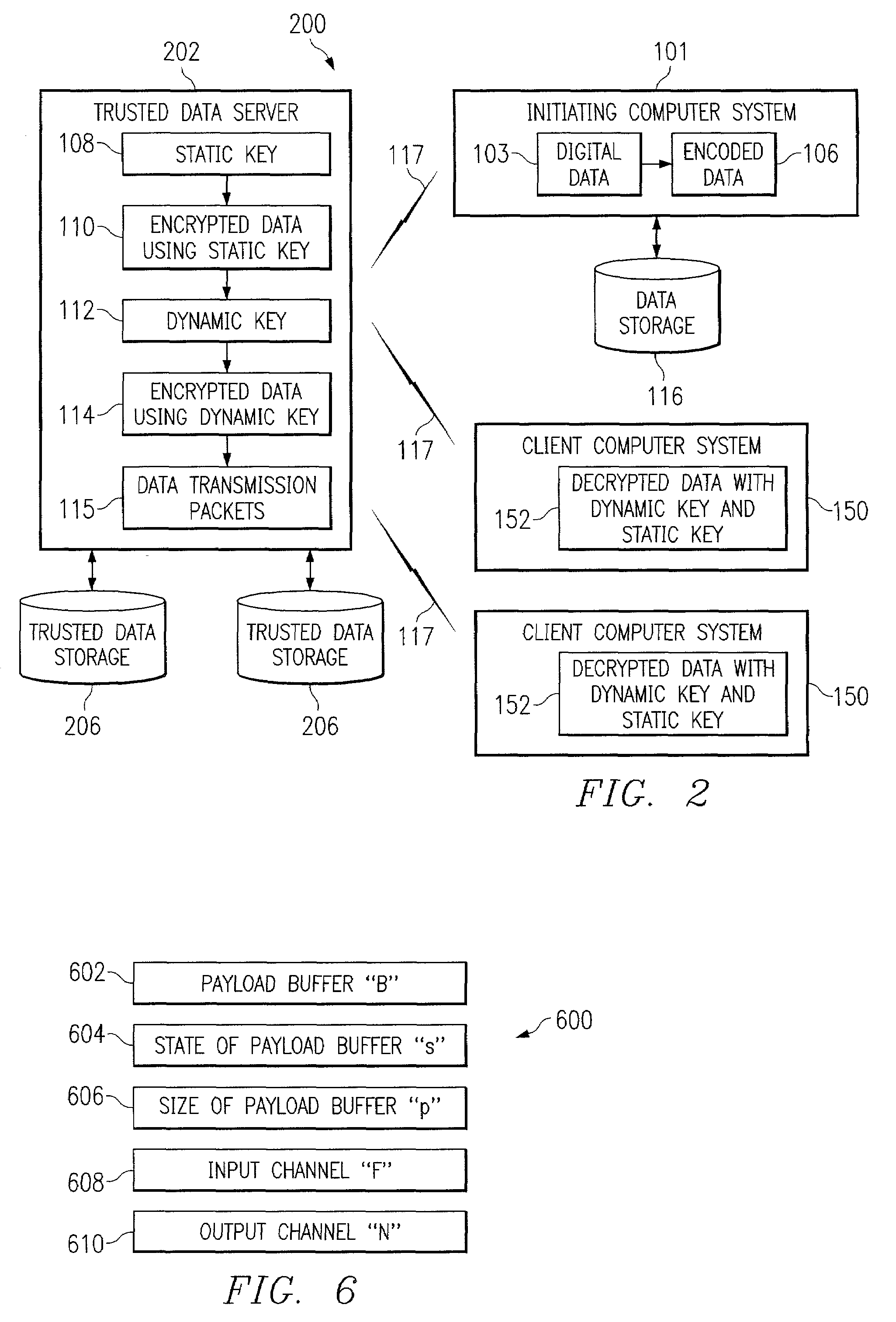
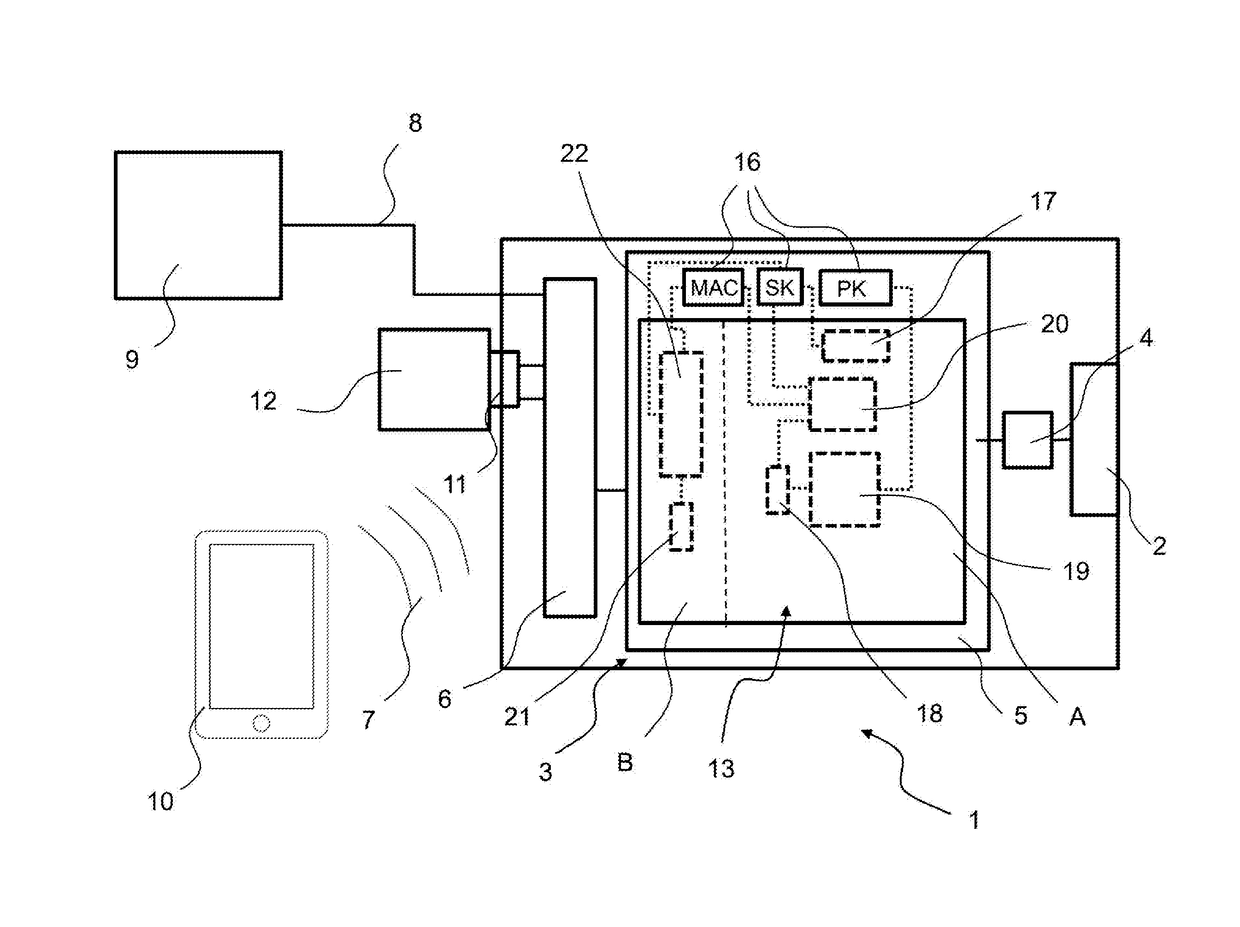
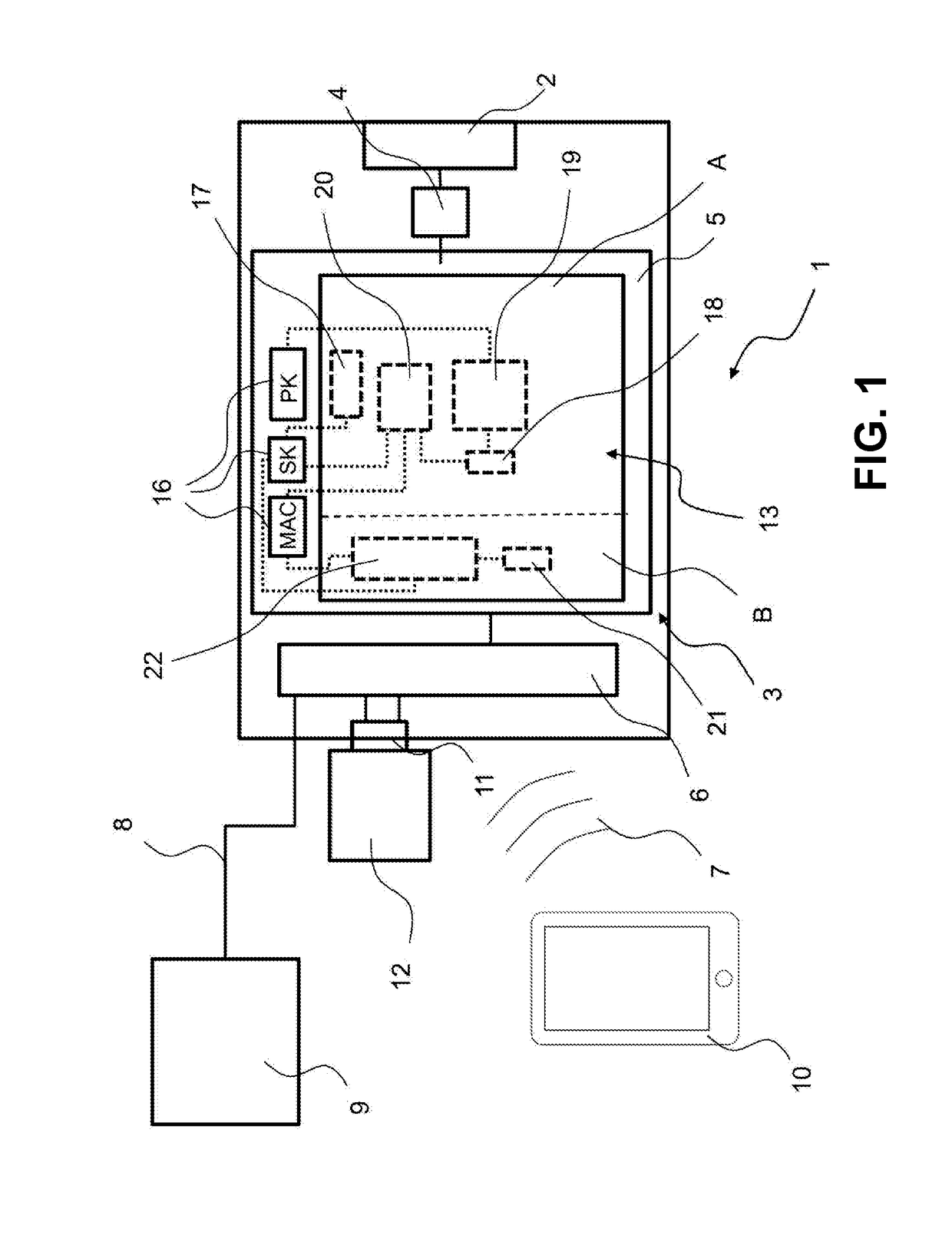
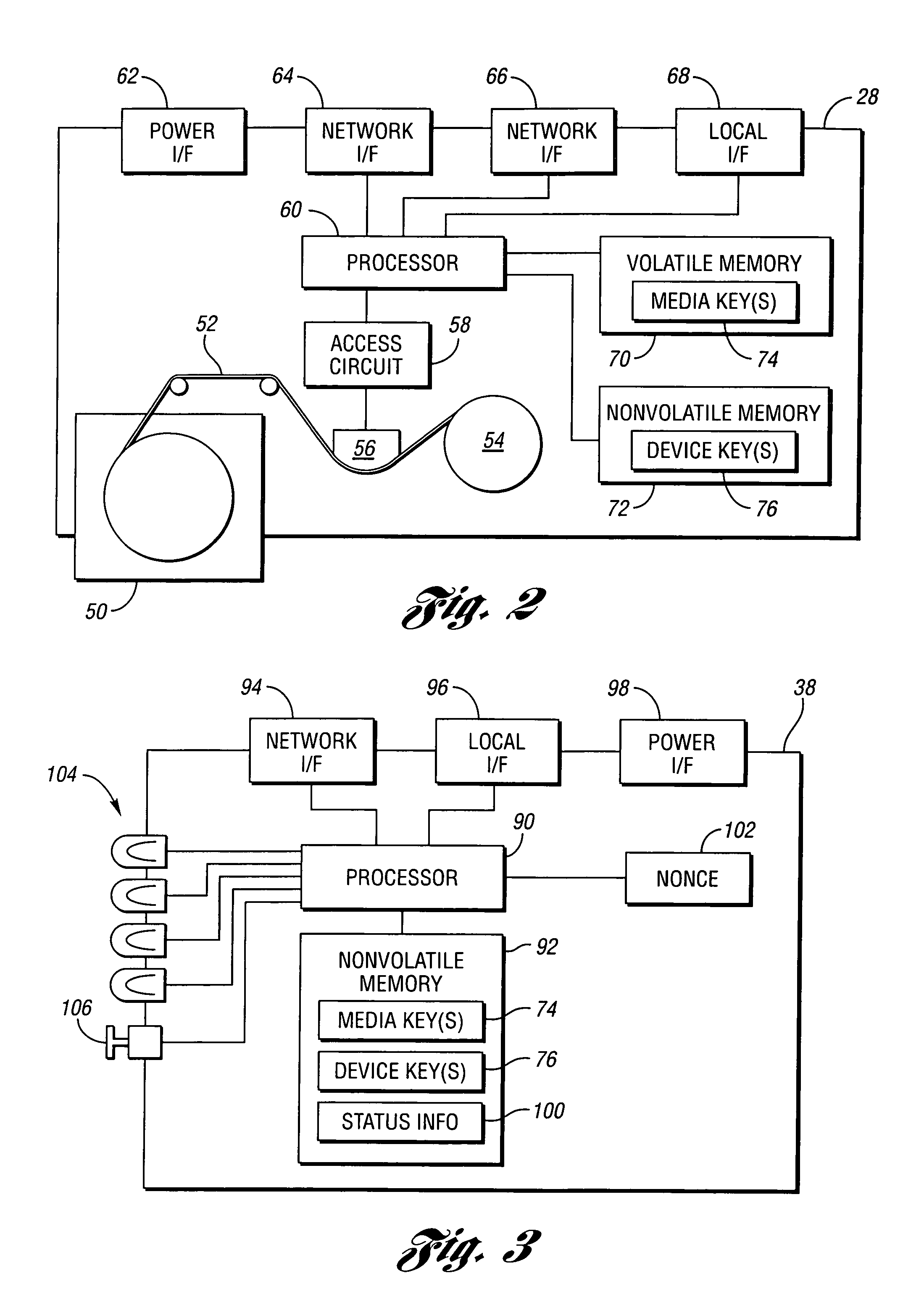
Systems, methods, and computer program products for accelerated dynamic protection of data
InactiveUS7280658B2Sufficient protectionKey distribution for secure communicationSecret communicationComputer resourcesEnd to end security
Owner:SNAP INC
Efficient, Secure, Cloud-Based Identity Services
InactiveUS20110246765A1Improve securityUser identity/authority verificationWeb serviceSecurity Measure
An Identity Ecosystem Cloud (IEC) provides global, scalable, cloud-based, cryptographic identity services as an identity assurance mechanism for other services, such as data storage, web services, and electronic commerce engines. The IEC complements these other services by providing enhanced identity protection and authentication. An IEC performs identity services using surrogate digital certificates having encryption keys that are never exposed to the public. An individual requesting other services must meet an identity challenge before access to these other services is granted. Service requests to the IEC, and responses from the IEC, are securely encrypted. An IEC integrates smoothly into existing services by layering on top of, or being used in conjunction with, existing security measures. Identity transactions may be logged in a manner that complies with strict medical and financial privacy laws.
Owner:SURIDX
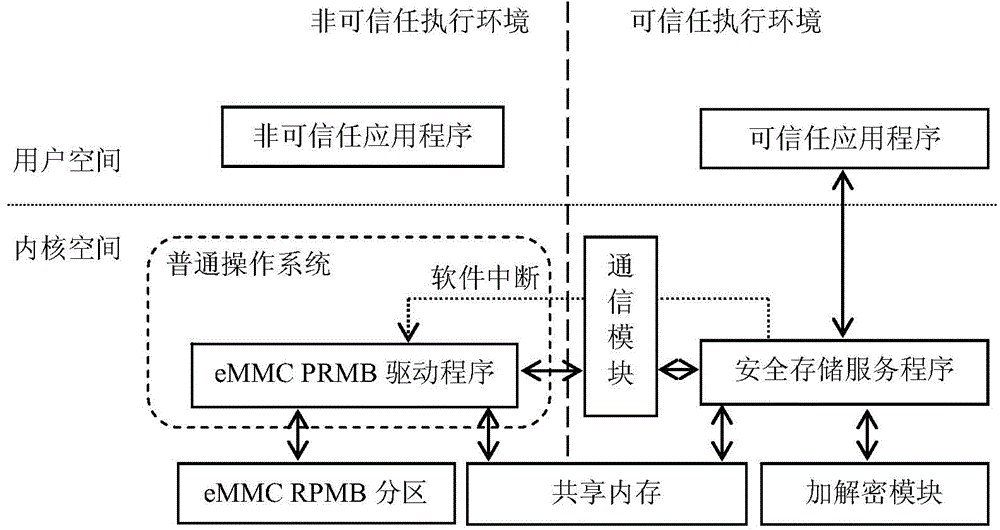
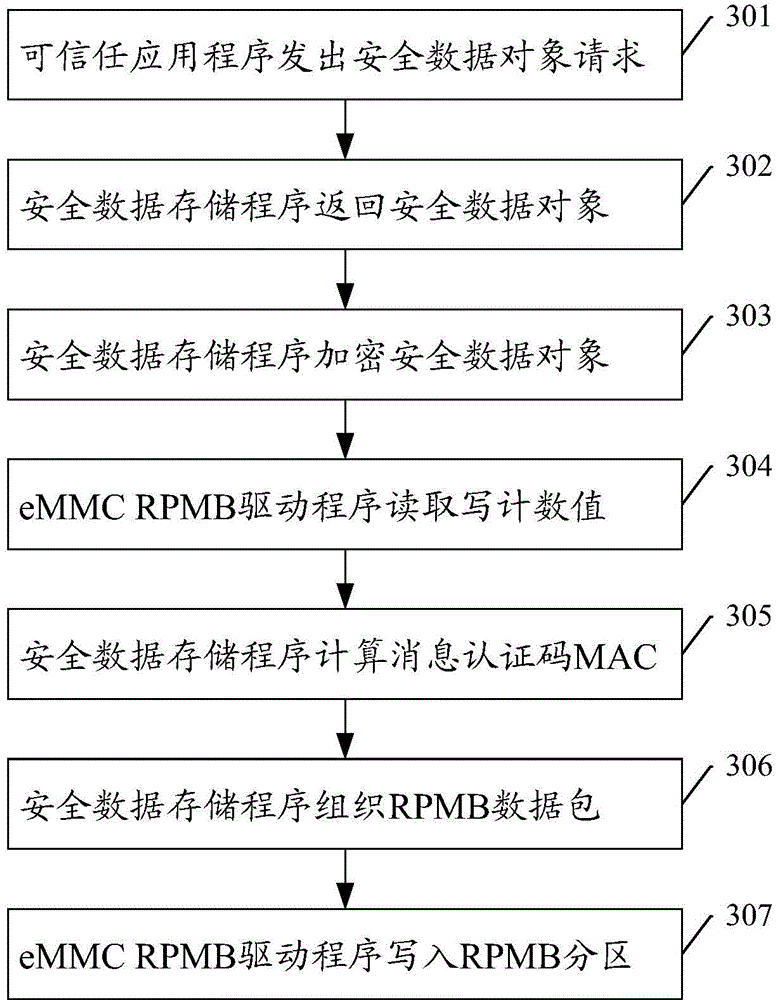
Security data storage method and system
ActiveCN104392188AEnsure safetyAvoid readingDigitally marking record carriersInternal/peripheral component protectionApplication softwareData store
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
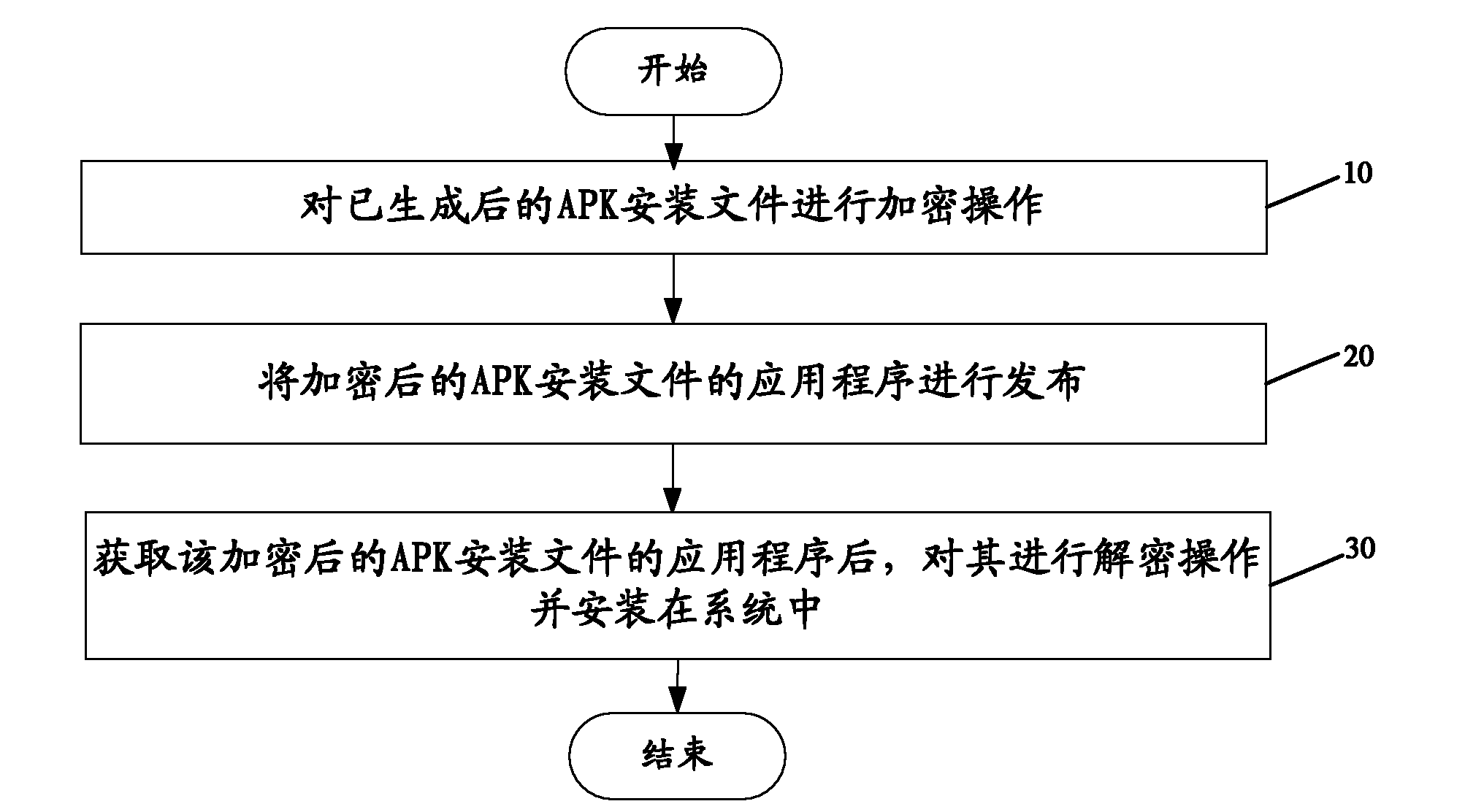
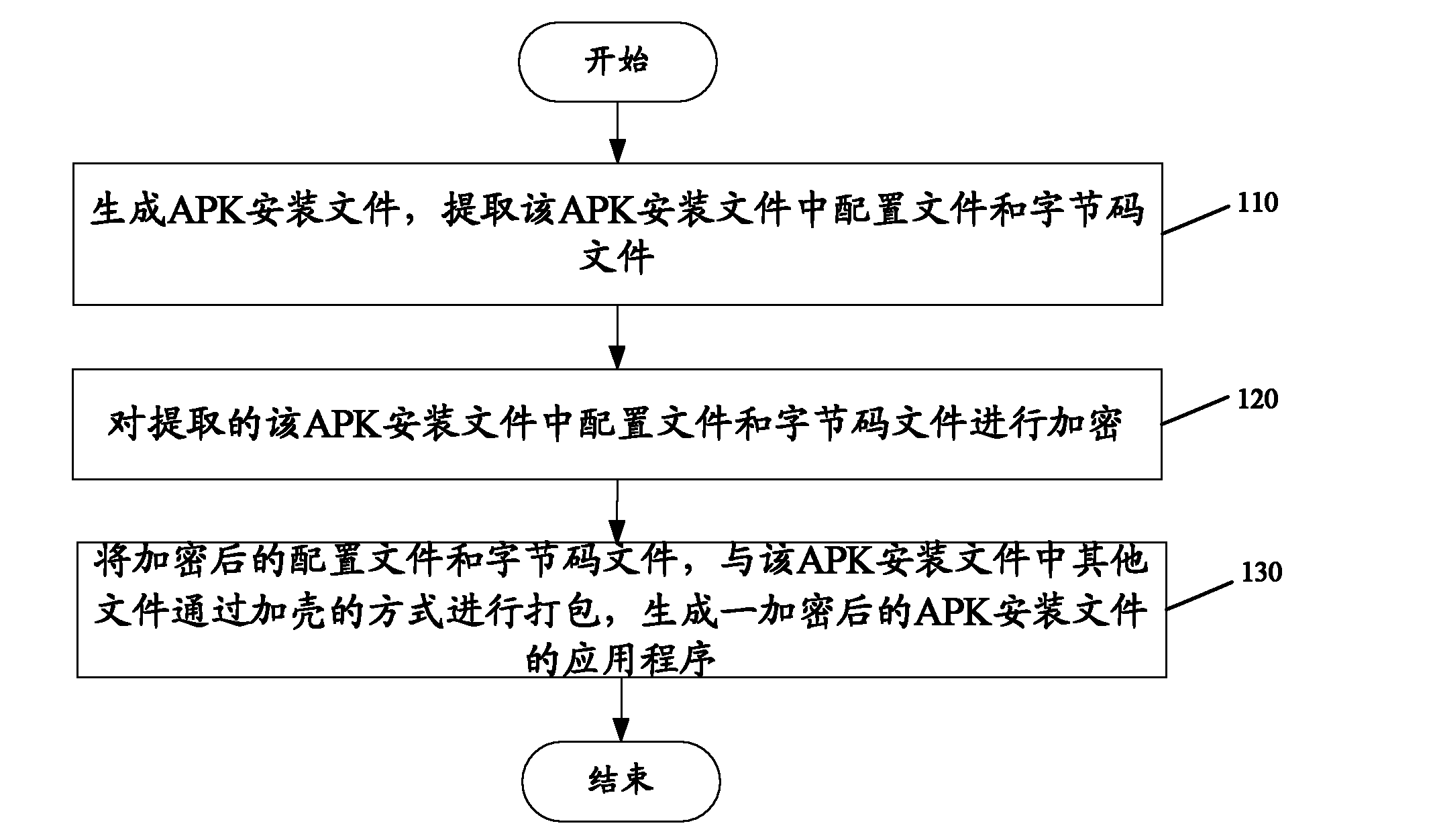
Android-based platform application installation control method and system
InactiveCN102087605AComputer security arrangementsProgram loading/initiatingApplication softwareEncryption
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
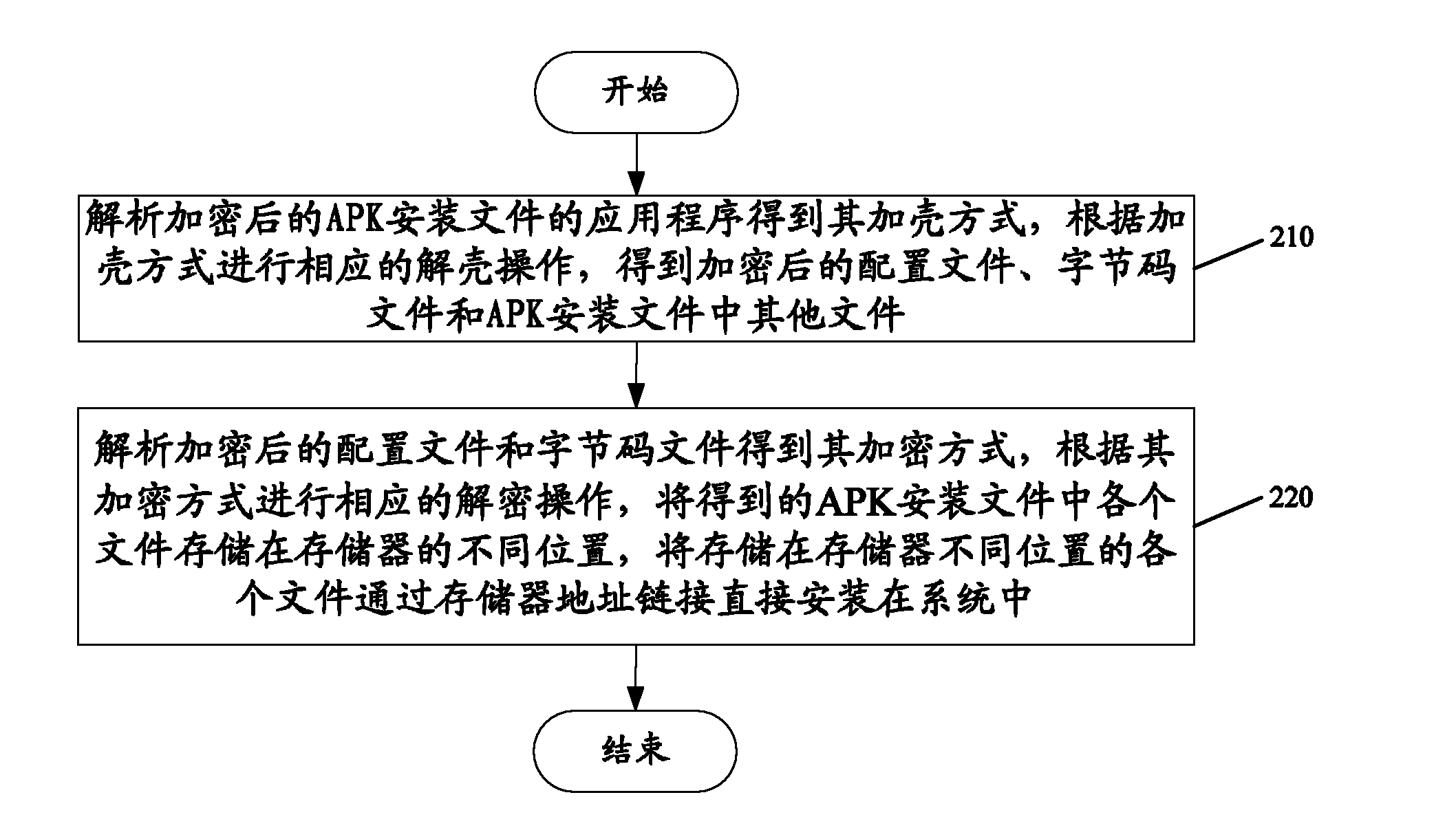
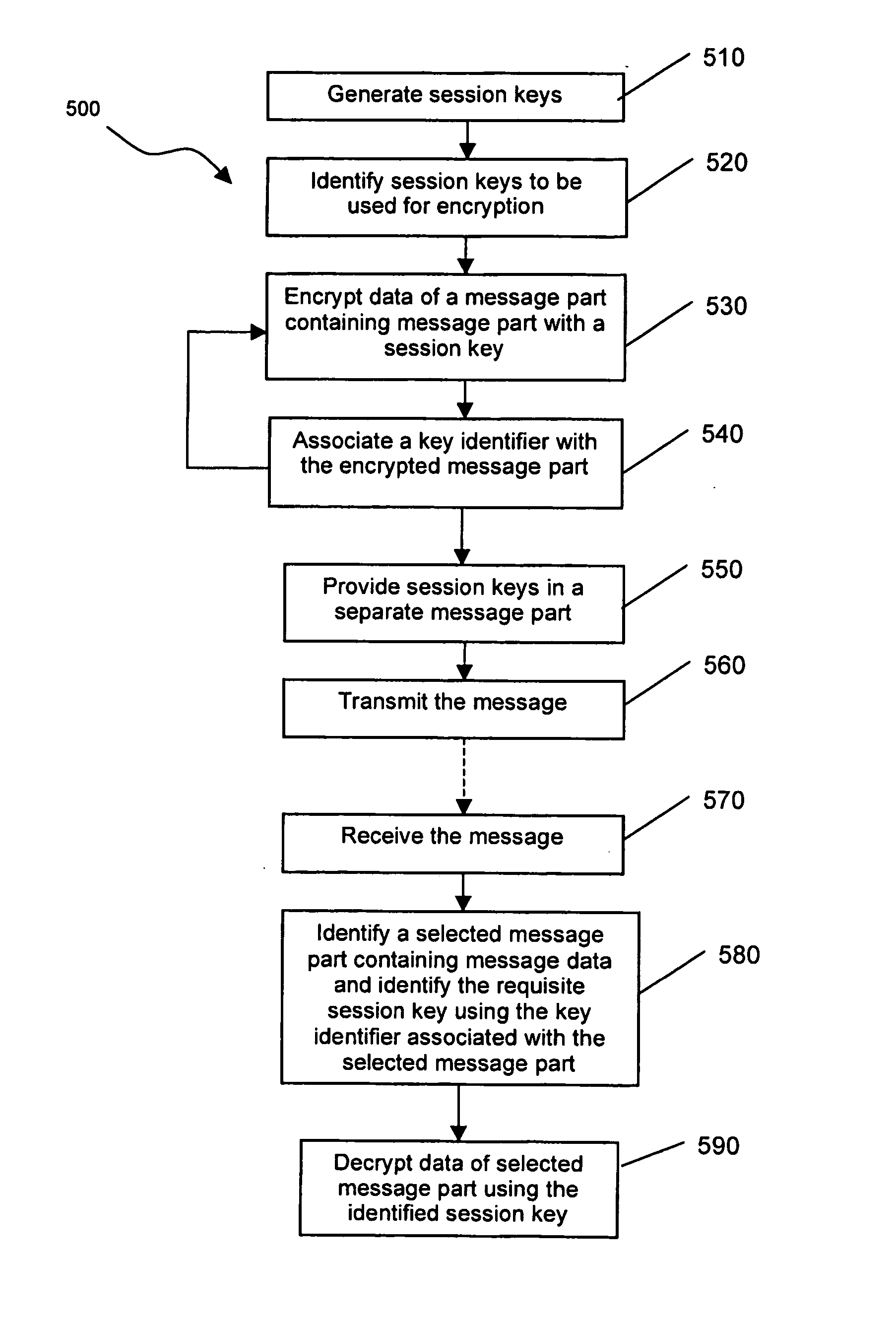
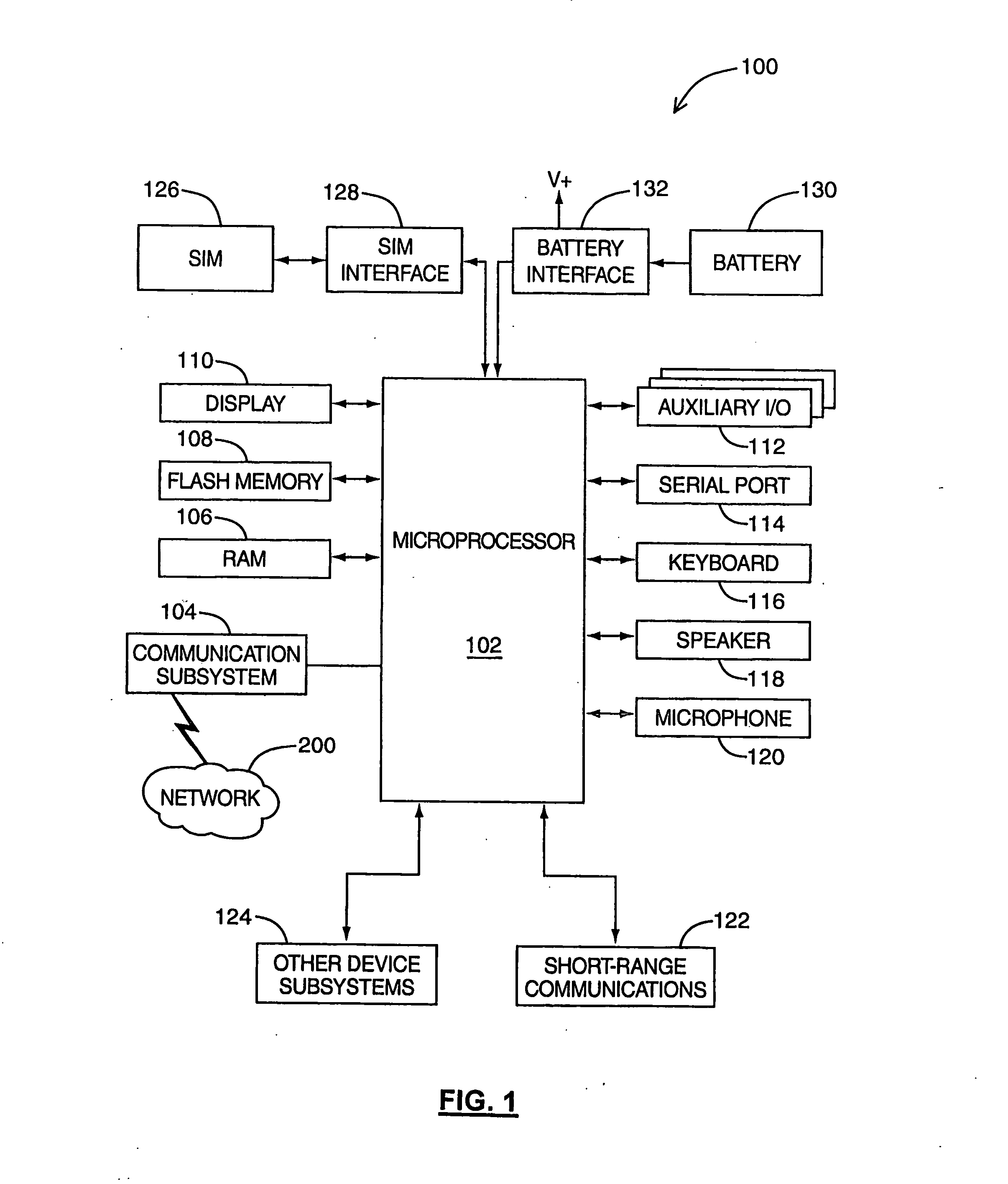
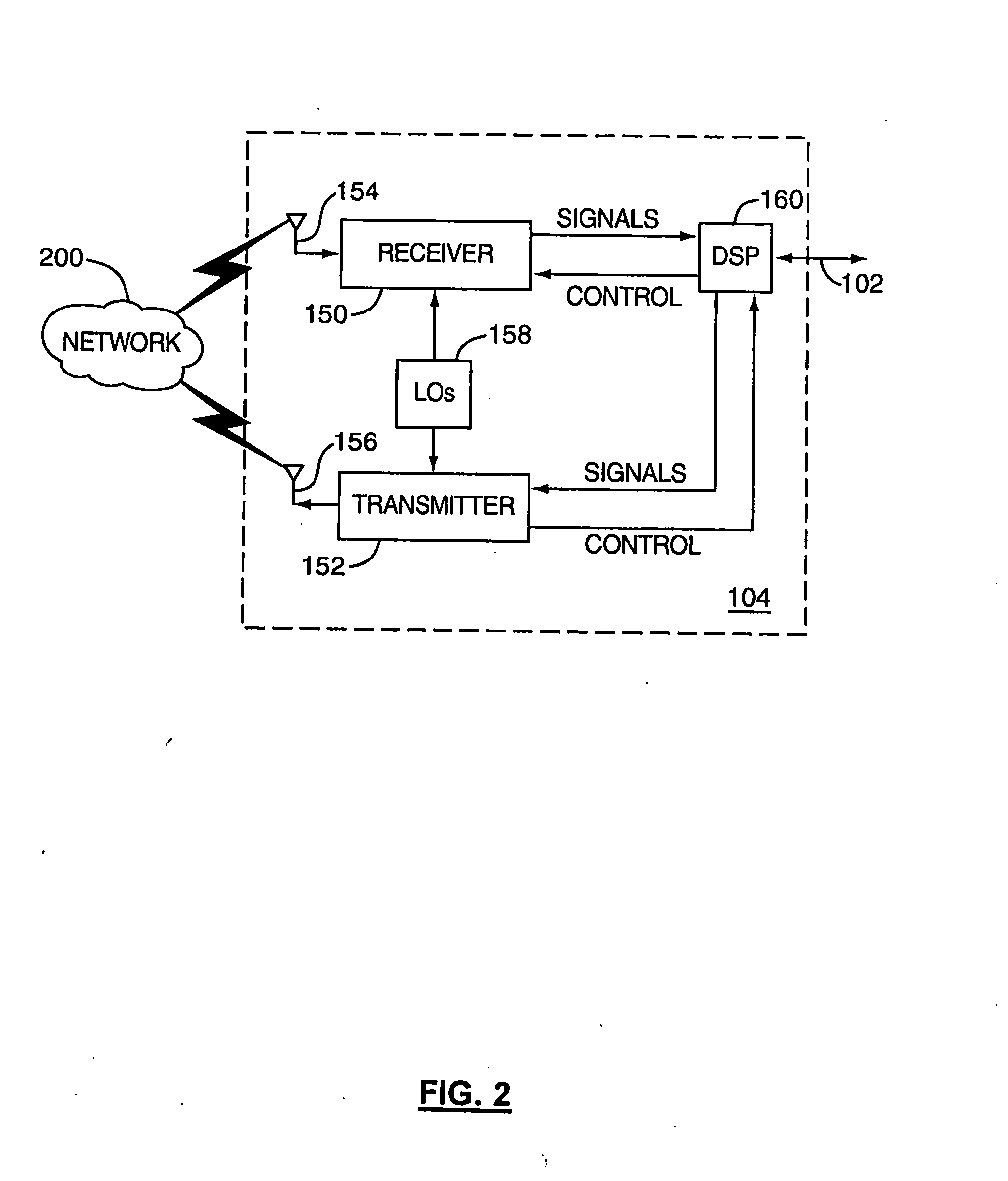
System and method for processing messages with encryptable message parts
Owner:BLACKBERRY LTD
Digital certificate safety lock device and digital certificate authentication system and method
InactiveCN102255730AImprove general performanceImprove applicabilityUser identity/authority verificationMicrocontrollerTablet computer
The invention relates to a digital certificate safety lock device and a digital certificate authentication system and method. The digital certificate safety lock device comprises a universal encryption and digital signature microcontroller, an audio plug and a first modulation and demodulation module, wherein the universal encryption and digital signature microcontroller is provided with an encryption and digital signature module and a storage for storing a digital certificate, a key of the digital certificate and encryption and decryption algorithms; and the first modulation and demodulation module is used for modulating data information from the encryption and digital signature module for transmitting through an MIC (Microphone) pole of the audio plug, demodulating a signal received from a first sound channel pole of the audio plug and transmitting the demodulated signal to the encryption and digital signature module. The digital certificate safety lock device is provided with a universal audio interface plug which has high university and adaptability and can support communication terminals such as mobile phones, tablet computers, PDAs (Personal Digital Assistants) or PCs (Personal Computers) and the like, with audio interfaces. Due to the functions of independent hardware signature, digital certificate encryption and the like, the security of application logon and transactions of Internet banks or enterprises can be ensured to the maximum extent.
Owner:吴沙林 +1
Method for updating a firmware component and device of measurement and control technology
ActiveUS20170293484A1The encryption method is simpleLess resourcesProgramme controlMemory architecture accessing/allocationEncryptionAuthentication
Owner:ENDRESSHAUSER CONDUCTA GMBHCO
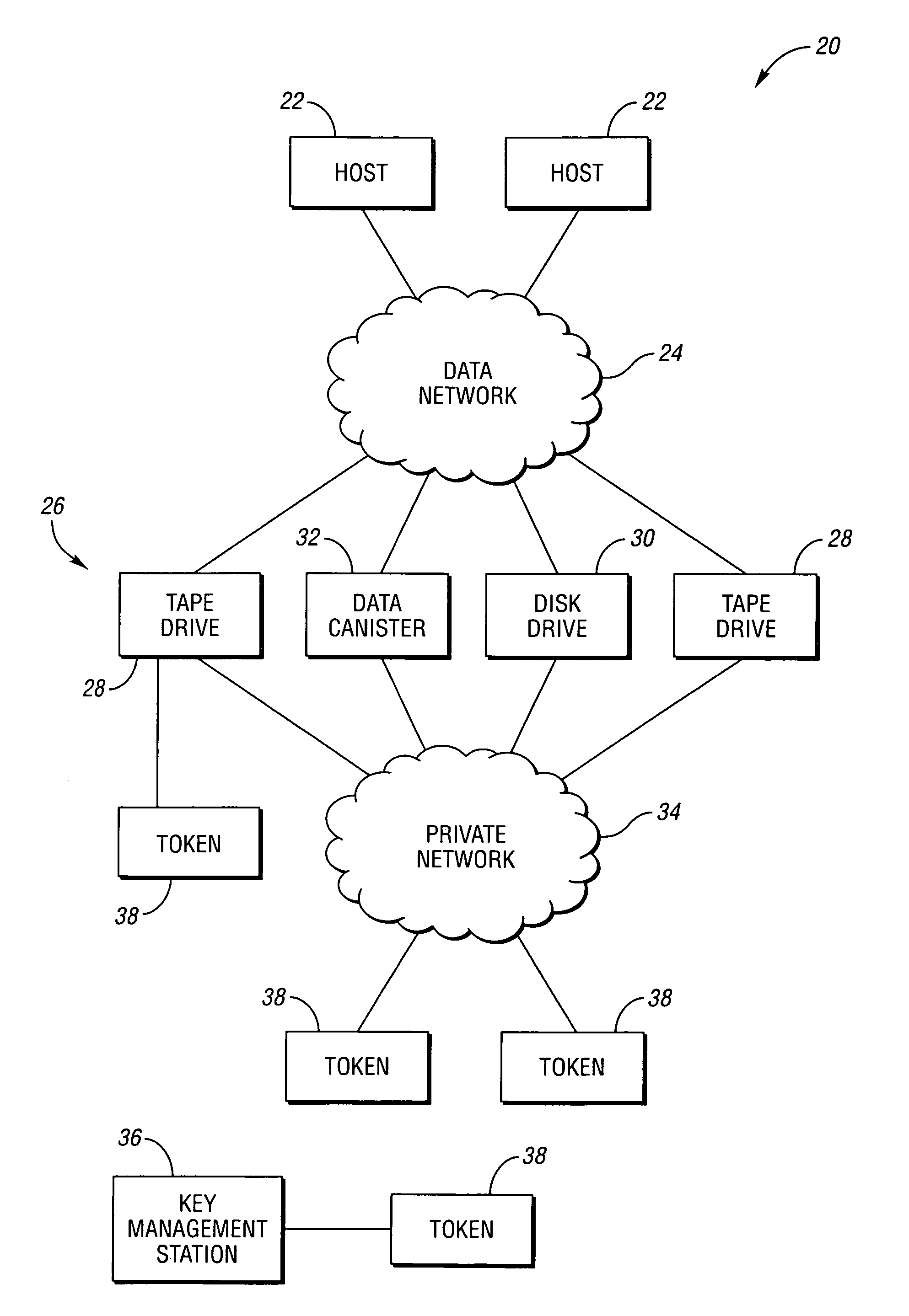
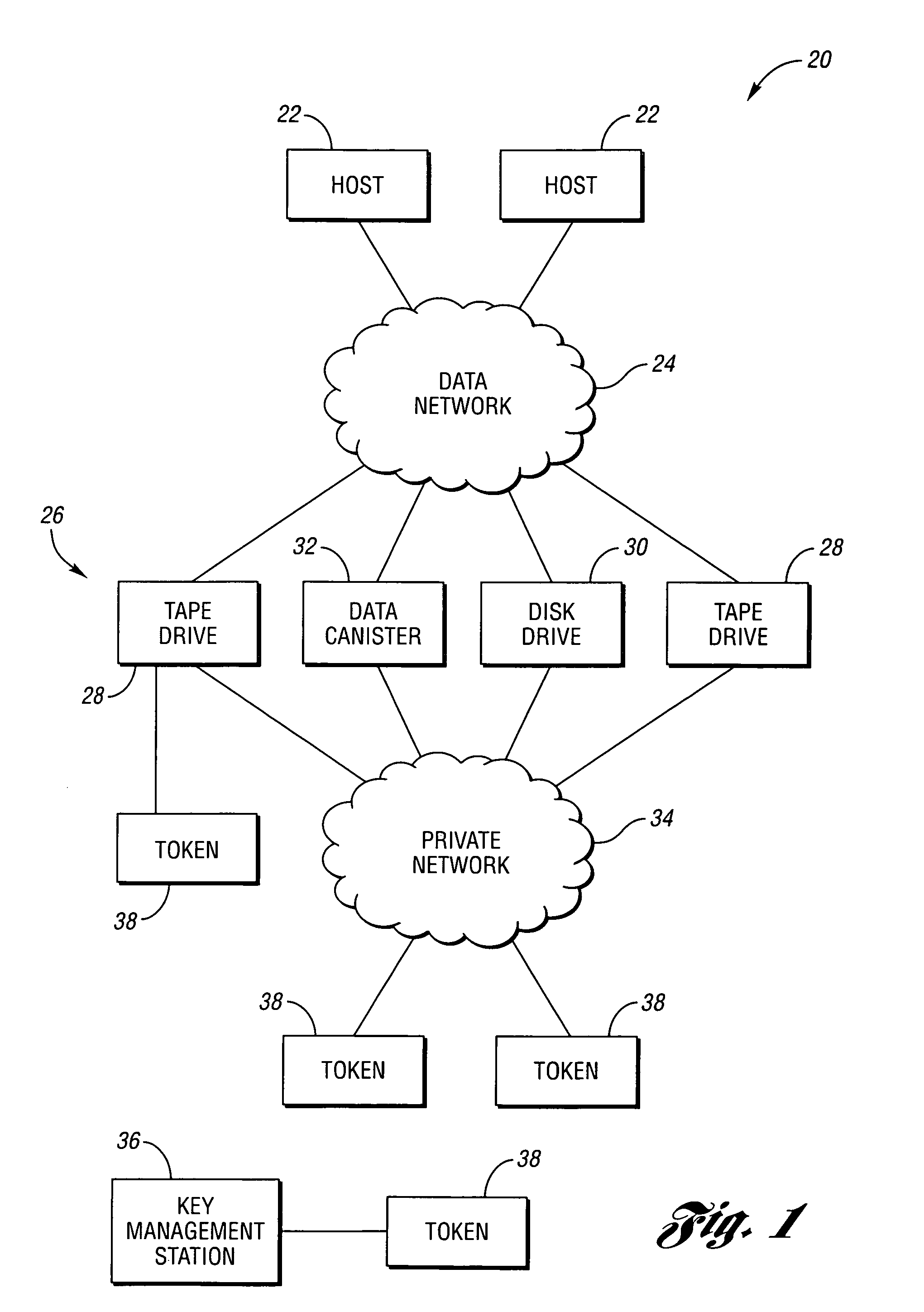
Token-based encryption key secure conveyance
ActiveUS7971062B1Key distribution for secure communicationDigital data processing detailsEncryptionControl logic
Owner:ORACLE INT CORP
Network communication encrypting method and system
Owner:BEIJING FEINNO COMM TECH
Removable storage device data protection
ActiveUS20130031376A1Unauthorized memory use protectionHardware monitoringFile systemRemovable media
Owner:LENOVO (SINGAPORE) PTE LTD
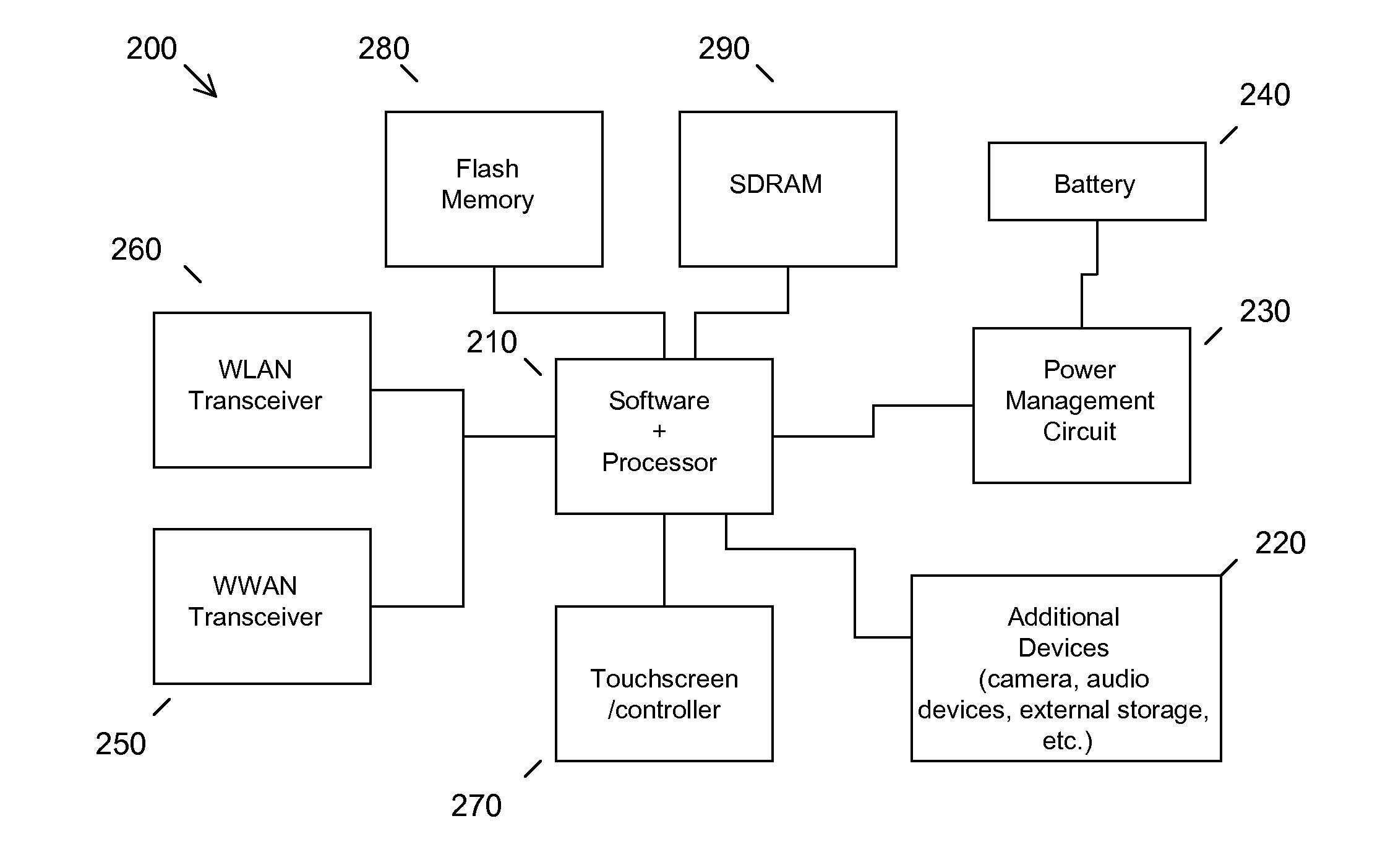
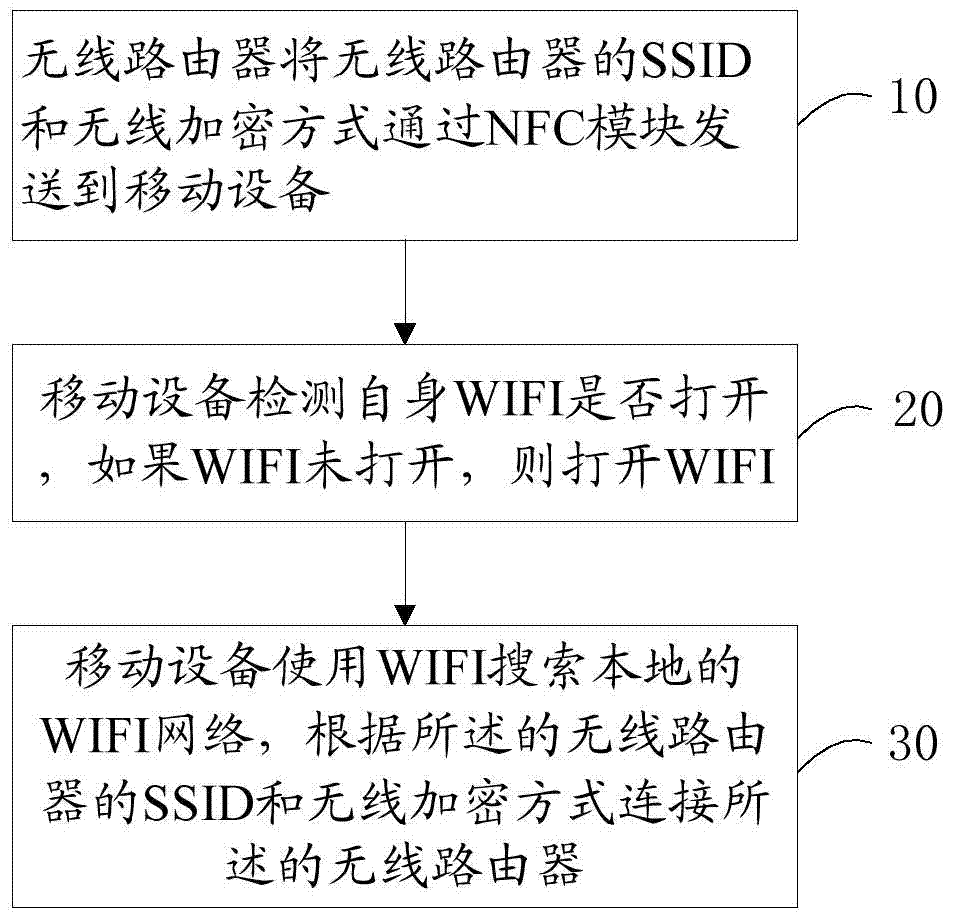
Method and system for wireless router authorized connection based on NFC technology
Owner:FUZHOU ROCKCHIP SEMICON
TDD Uplink and Downlink Configuration Updating Method and Apparatus and TDD Re-Configuration Information Notification Method and Apparatus
InactiveUS20150208382A1Avoid delayAvoid resourcesTime-division multiplexRadio transmissionComputer hardwareEncryption
A method for encrypting a terminal with a subscriber identity card includes: a terminal storing the unique identity number of a subscriber identity card; the terminal detecting an operation of a user and authenticating a current user according to authentication conditions set by the user. Authenticating the current subscriber refers to that the terminal reads the unique identity number of the current subscriber identity card, and compares the read unique identity number of current subscriber identity card with the stored unique identity number of subscriber identity card; if they are the same, the terminal is controlled to enter a normal working state; and if they are different, the terminal locks by itself or disables the access of current user. The present document encrypts a mobile terminal with a subscriber identity card, so as to make the encryption technique of the terminal more secure and reliable, and improve the user experience.
Owner:ZTE CORP
Method for realizing encryption communication
Owner:HUAWEI TECH CO LTD
Image encryption for print-and-scan channels using pixel position permutation
InactiveUS20100169649A1User identity/authority verificationPictoral communicationImaging dataEncryption
An image encryption method that includes receiving image data based on an image, wherein the image data comprises a plurality of pixel values, and permuting a plurality of, and preferably all of, the pixel values using at least a secret key to create permuted image data. Also, an image decryption method that includes scanning a printed image to create scanned image data. The printed image is generated from permuted image data that is generated by permuting a plurality of first pixel values of first image data using at least a secret key, obtaining a plurality of second pixel values from the scanned image data, and reverse-permuting a plurality of the second pixel values using at least the secret key to create reverse-permuted scanned image data.
Owner:PITNEY BOWES INC
Information processing method, device and equipment and readable storage medium
ActiveCN111178884AAvoid direct contactImplement usage managementFinancePayment protocolsInformation processingTransaction data
The invention belongs to the technical field of security mechanisms, and provides an information processing method, device and equipment and a readable storage medium, and the method comprises the steps of building the connection with a business system when a connection request of the business system is received, and maintaining the connection state with the business system; creating account information corresponding to the service system, returning the created account information to the service system, and the account information at least comprises an encryption private key; when transactioninformation sent by a service system is received, extracting an encrypted private key from account information carried by the transaction information, and decrypting the extracted encrypted private key to obtain a private key; and signing the transaction data carried by the transaction information by using the decrypted private key, and returning the signed transaction data to the business system,so that the business system performs transaction with an external system according to the signed transaction data. According to the invention, the security of the private key of the service system can be ensured, so that the security of private information and assets of the service system is ensured.
Owner:PINGAN YIQIANBAO E COMMERCE CO LTD
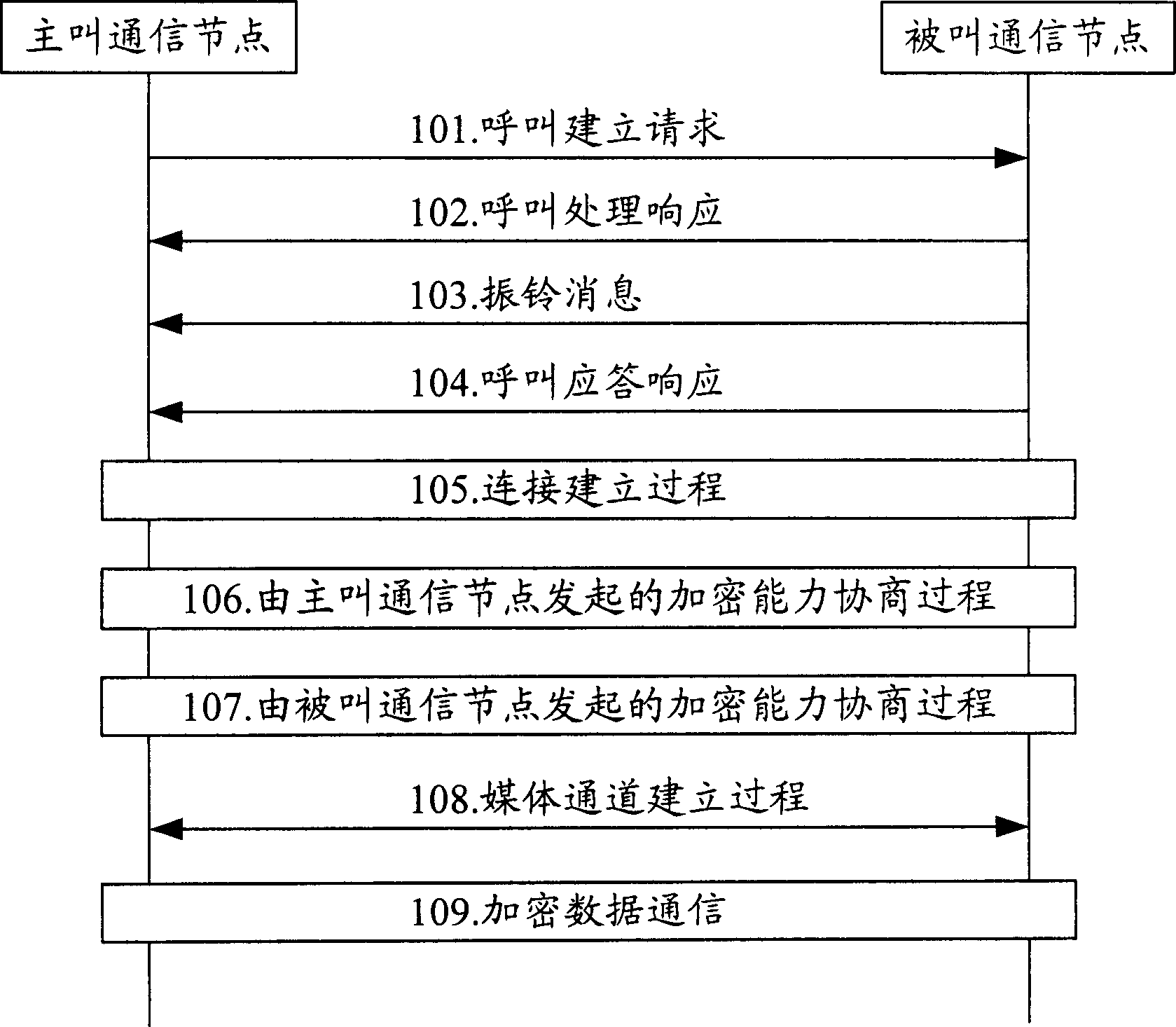
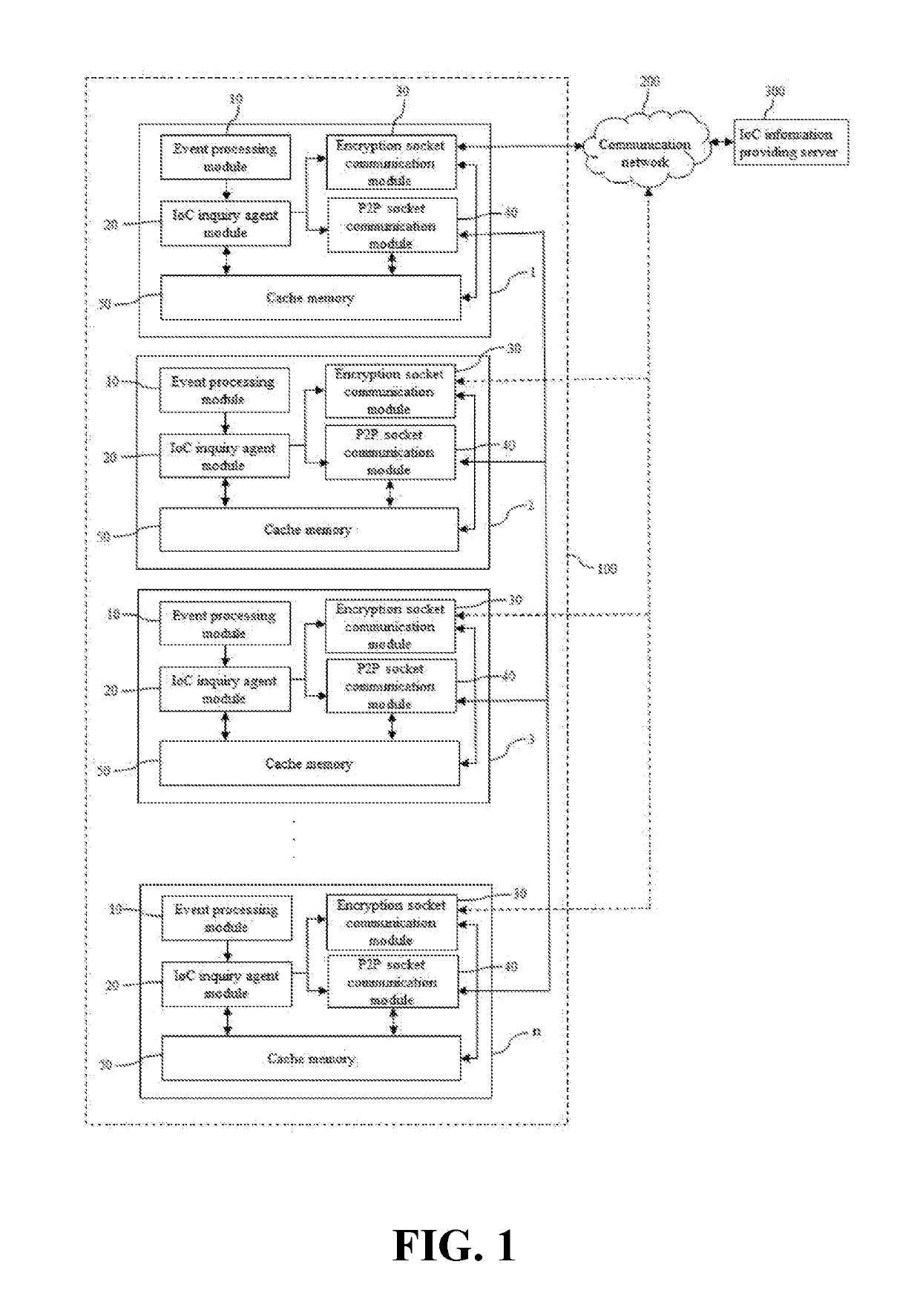
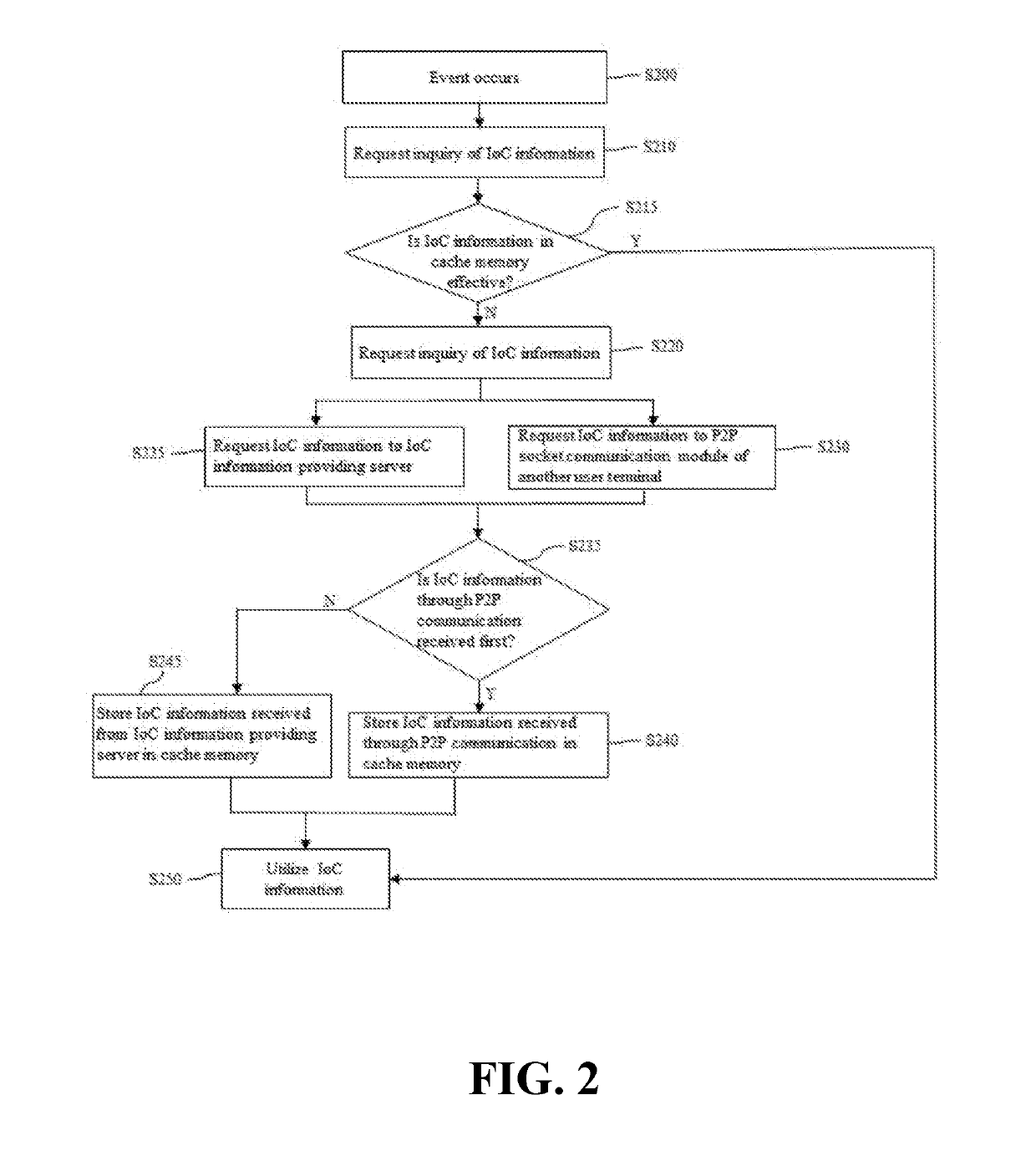
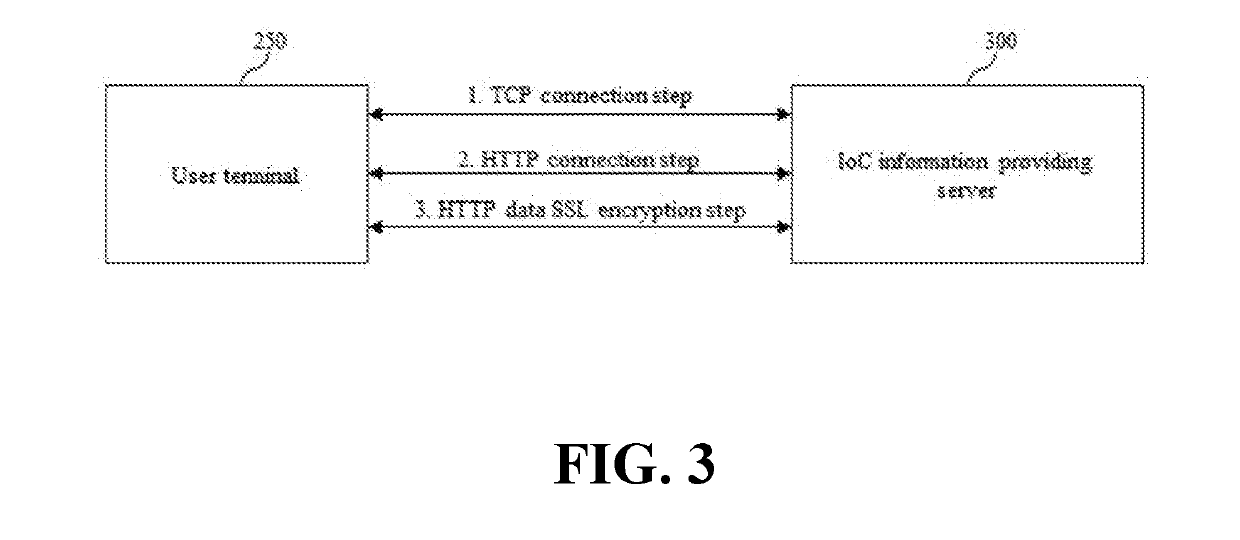
System and method for inquiring ioc information by p2p protocol
ActiveUS20190182270A1Platform integrity maintainanceTransmissionProtocol for Carrying Authentication for Network AccessEncryption
Owner:SANDS LAB INC
Network connection method, network connection device and terminal
ActiveCN106131834AImprove user security experienceImprove securitySecurity arrangementPasswordNetwork connection
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
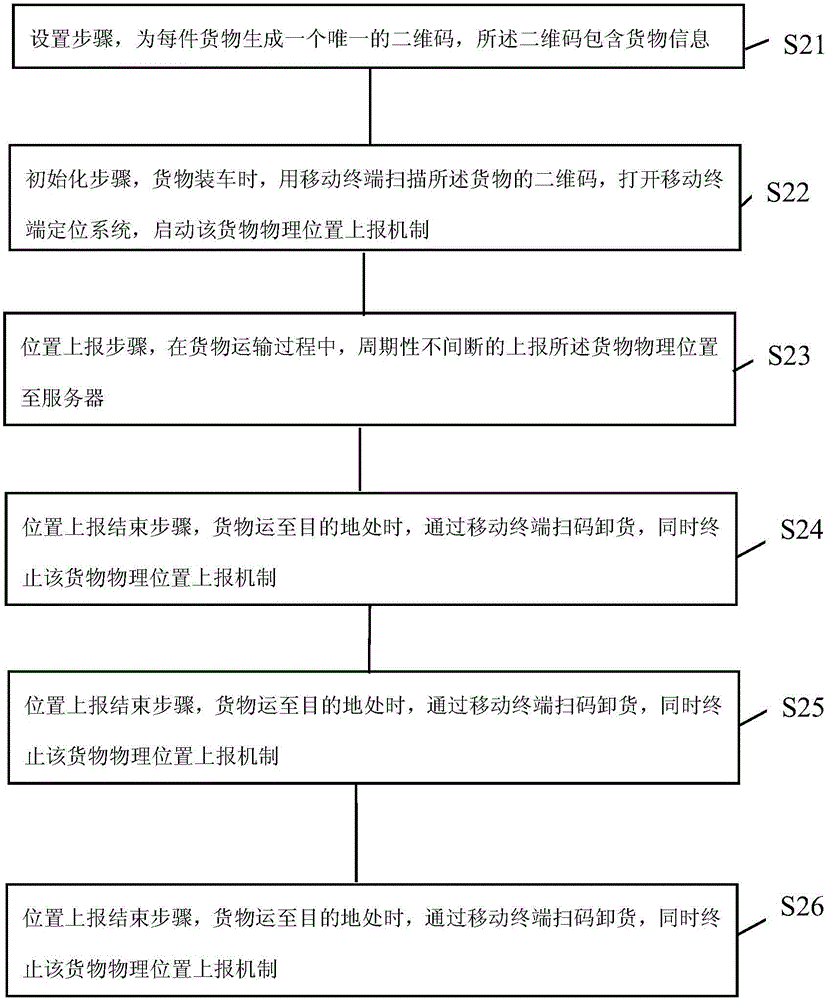
Goods positioning method
ActiveCN106779563ARun fastReduce memory usageCo-operative working arrangementsTransmissionMemory footprintComputer terminal
Owner:北京兴贸科技有限公司
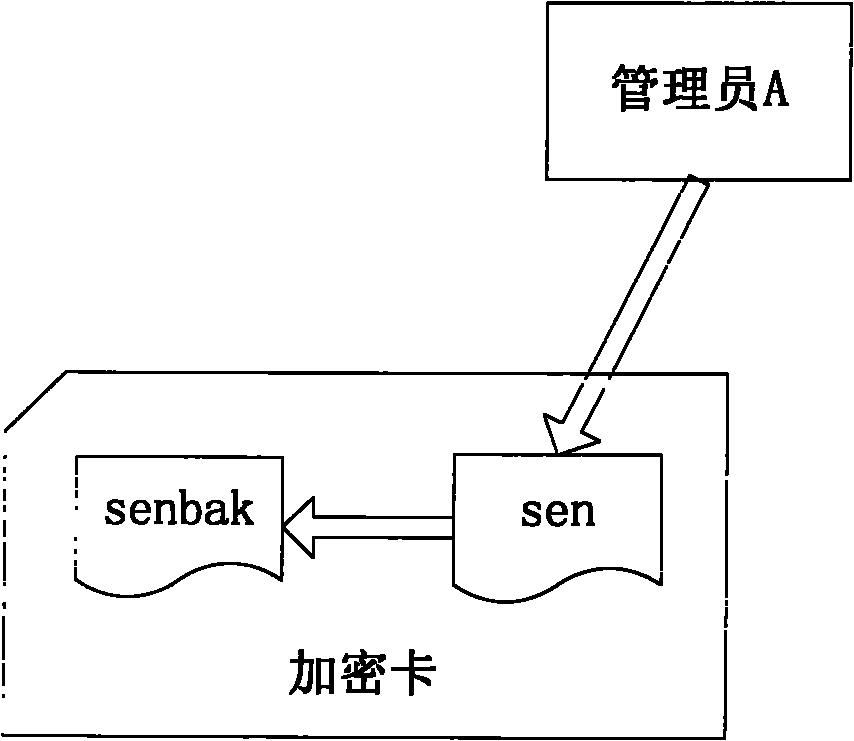
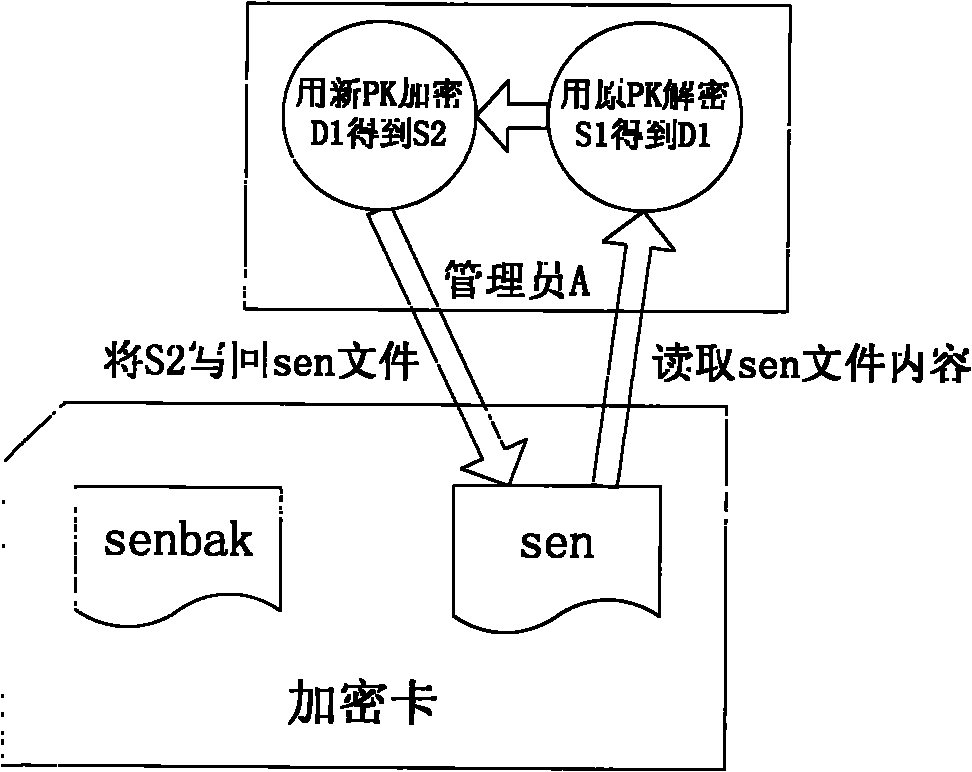
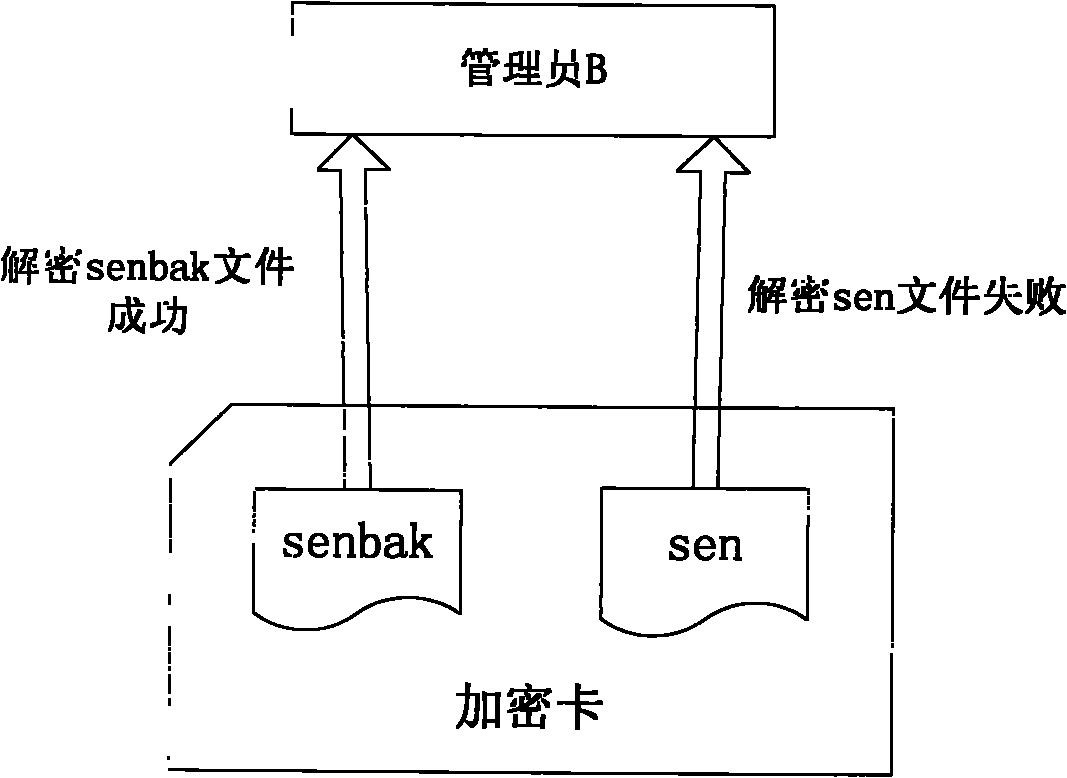
Method for restoring encrypted information in encryption card
ActiveCN102004873AGuaranteed to workInternal/peripheral component protectionRedundant operation error correctionComputer hardwareEncryption
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Simultaneous digital image and the image file's internal metadata printing system
A system that simultaneously prints digital image files' images and image files' internal metadata. The details for a digital image may be printed onto the front side and / or back side of a picture's printed hardcopy while simultaneously printing the digital image file's internal metadata or simultaneously displaying the digital image with its file's internal metadata on electronic media such as televisions, desktop, laptop and tablet computer screens, digital picture frames, cell phone, smart phone and telephone displays, public billboards, Internet web pages and x-ray photographs. The digital picture's details, being presented in the subject system as a file's internal metadata, include but are not limited to the picture's file name, the photographer's name, a copyright holder's name and a description of the picture, as well as the picture's technical details such as its image format, date, GPS location, focusing mode, metering mode, shutter speed, flash exposure compensation, resolution, ISO sensitivity, white balance, etc. A unique image identification code, password protection and encryption, can be assigned to each image and incorporated in the image file's internal metadata.
Owner:BERNARDO JOSEPH A
Data transmission method, device and system, storage medium and electronic device
PendingCN112738117AImprove securityRealize dynamic acquisitionTransmissionData accessData acquisition
Owner:QINGDAO HAIER TECH +1
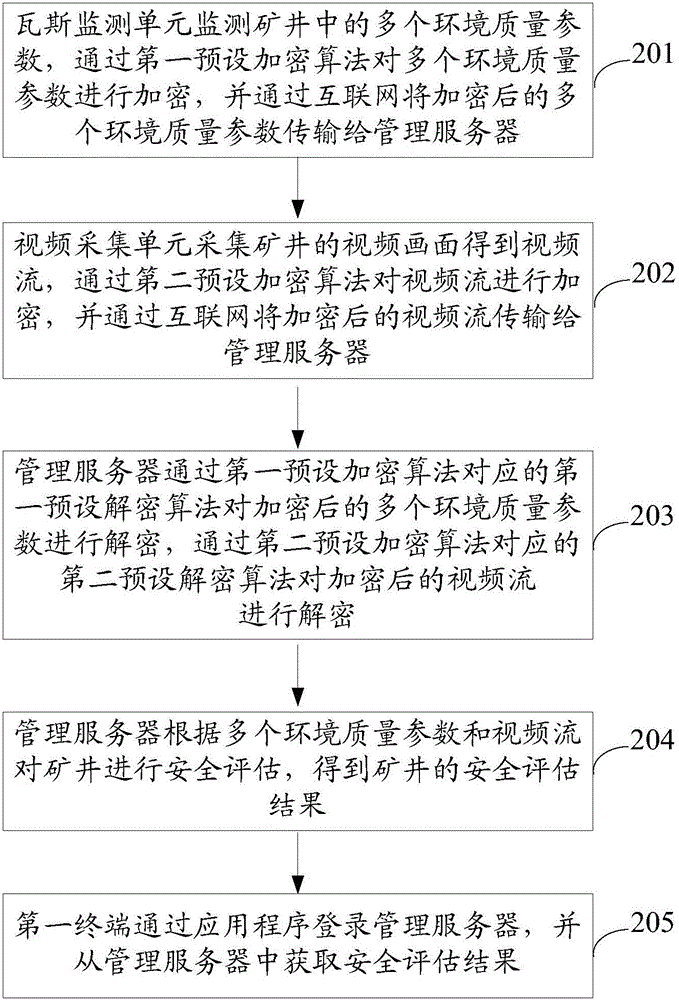
Coal mine management system and method
Owner:中融博瑞(北京)科技发展有限公司
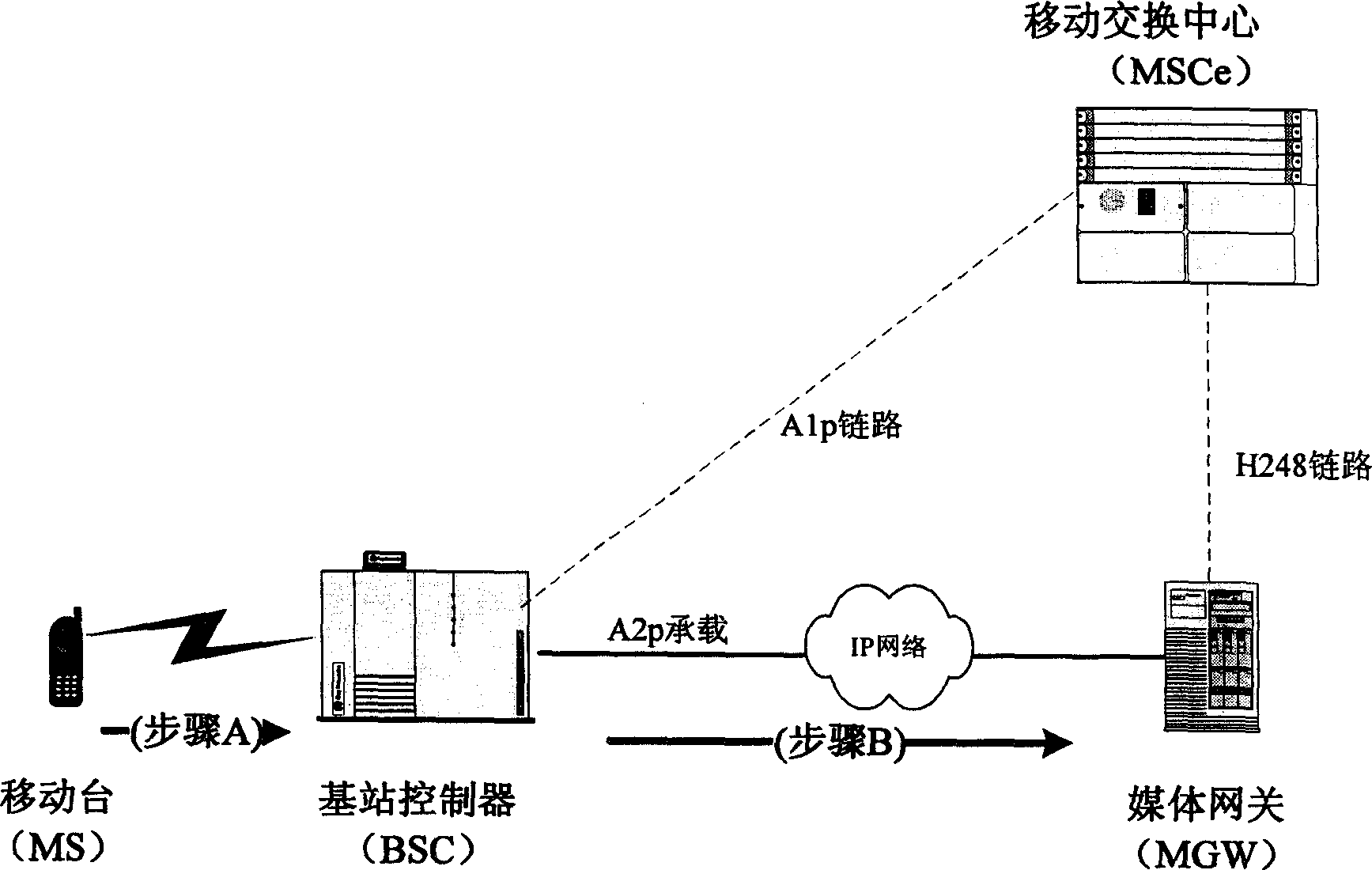
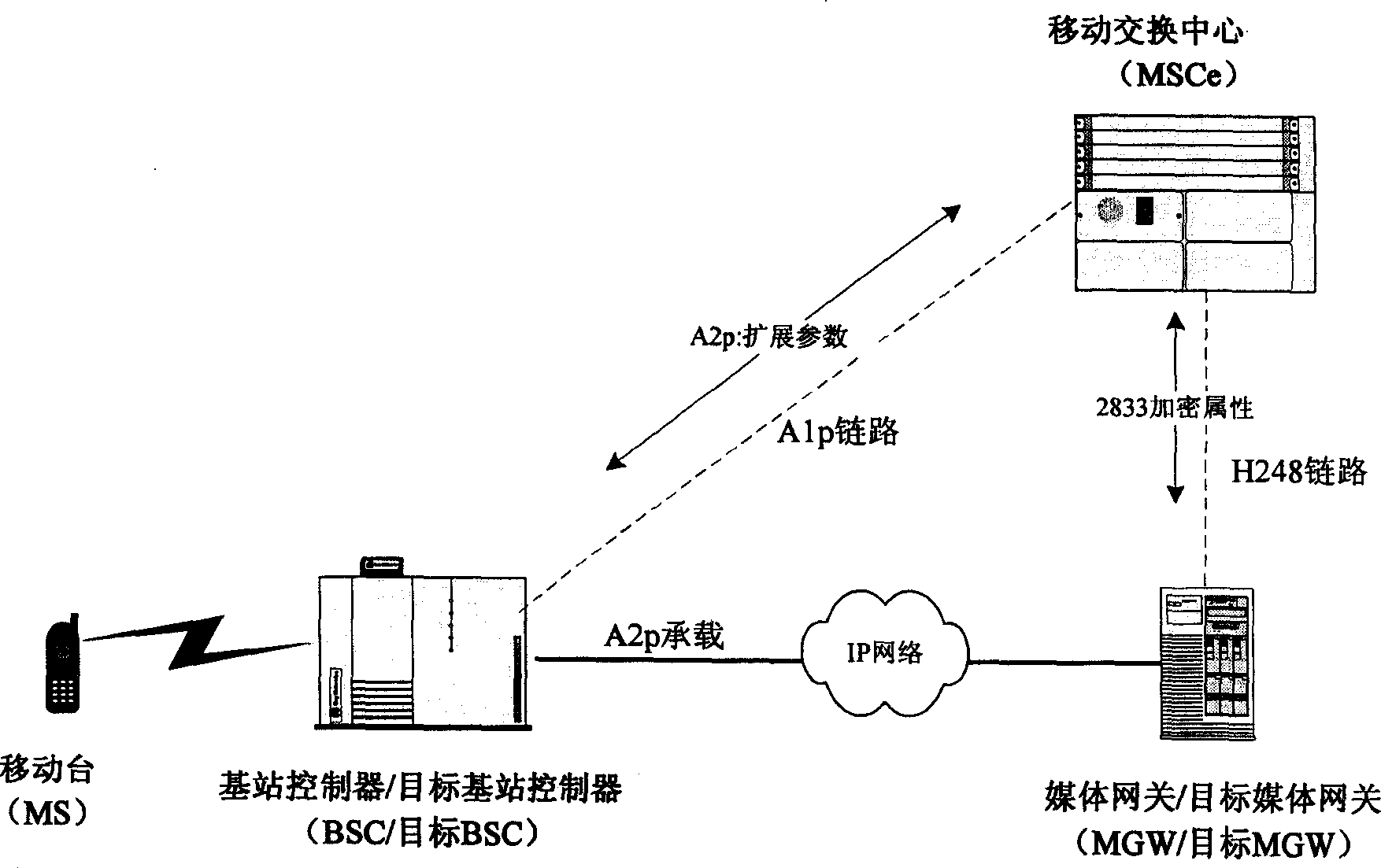
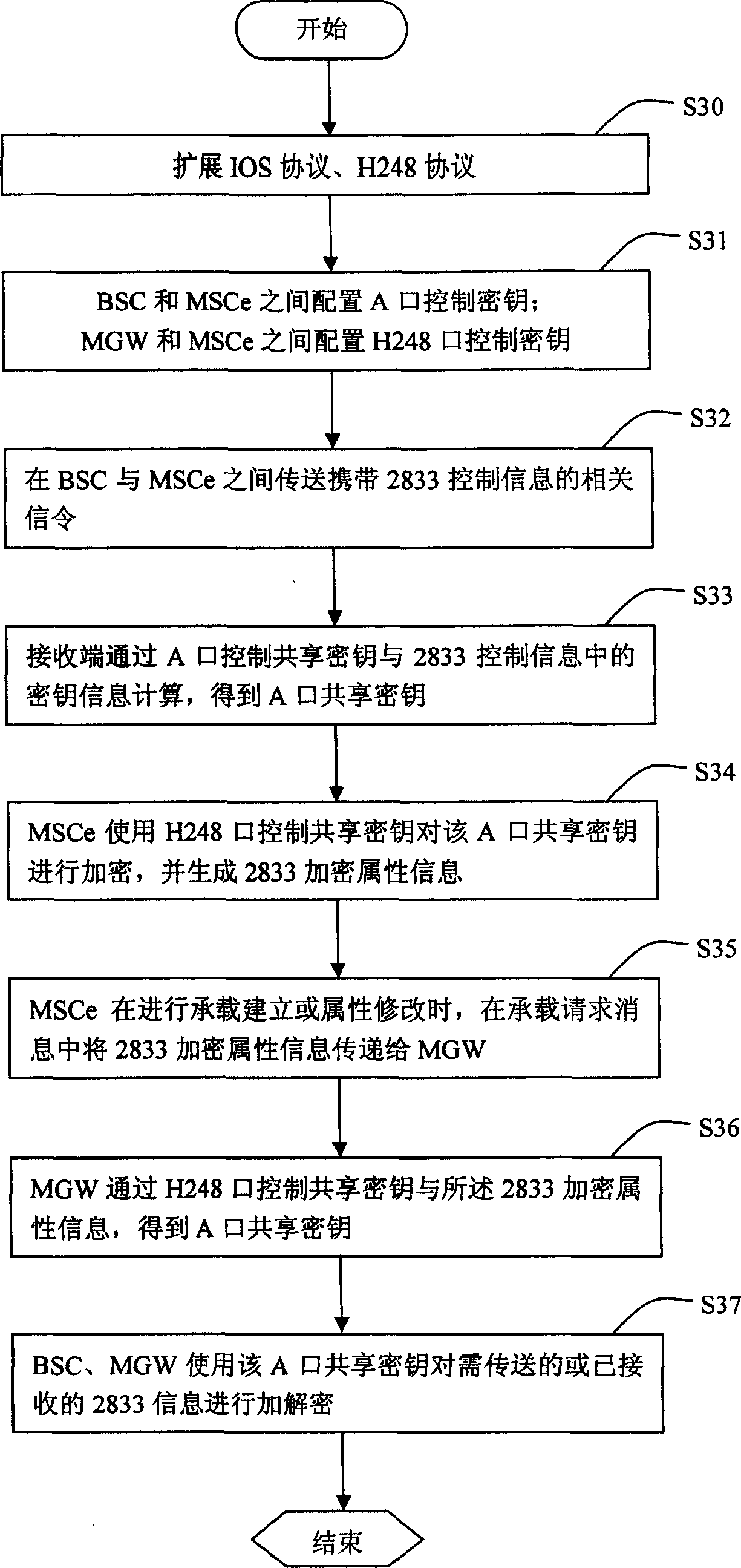
Method for carrying out encryption transfer on 2833 information in CDMA
InactiveCN1878399AProtect interestsImprove service satisfactionMultiple keys/algorithms usageRadio/inductive link selection arrangementsTelecommunicationsEncryption
Owner:HUAWEI TECH CO LTD
Secure customer communication method and system
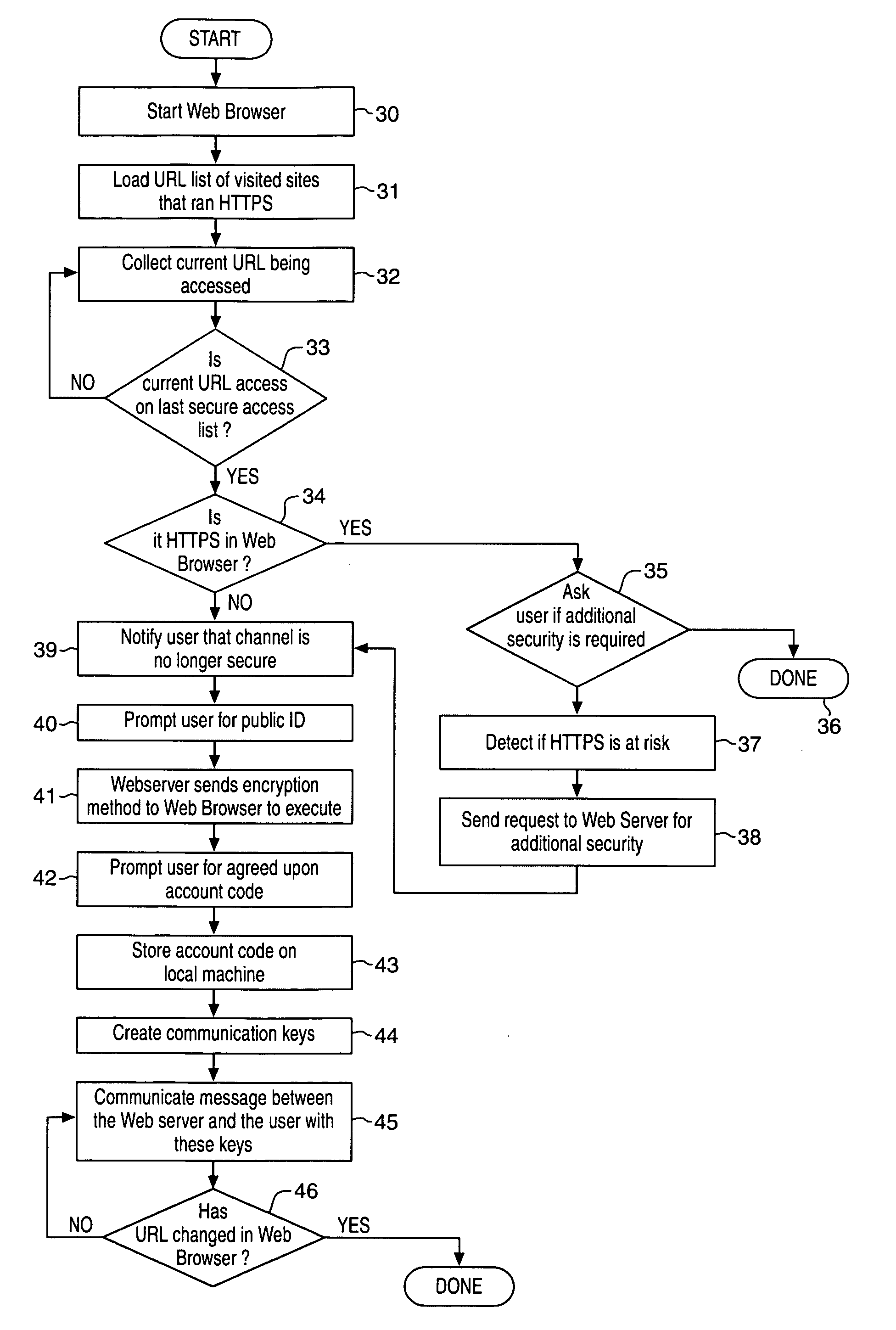
ActiveUS20050273443A1Public key for secure communicationUser identity/authority verificationComputer hardwareWeb browser
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT +1
Outdoor public place pre-ordering apparatus
InactiveCN101710406AConvenient lifeConvenient entertainmentReservationsSpecial data processing applicationsMicrocontrollerPublic place
Owner:DALIAN UNIV OF TECH
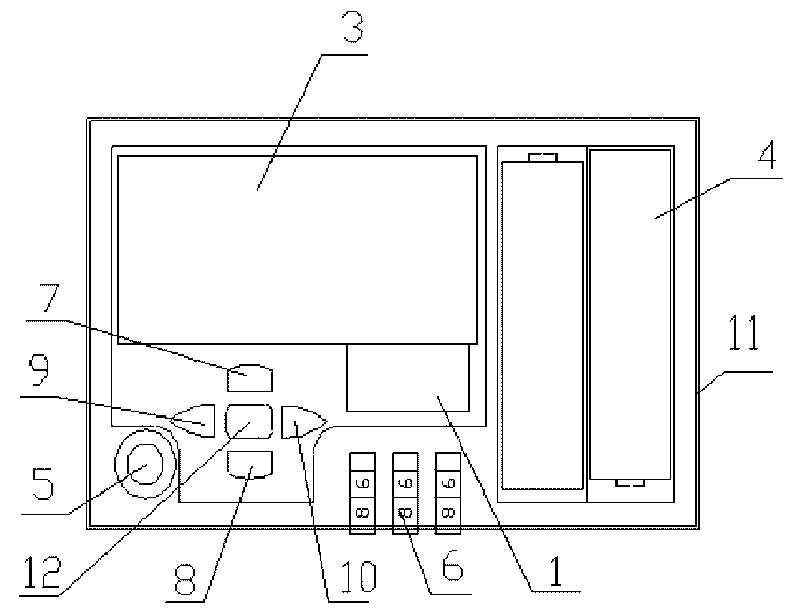
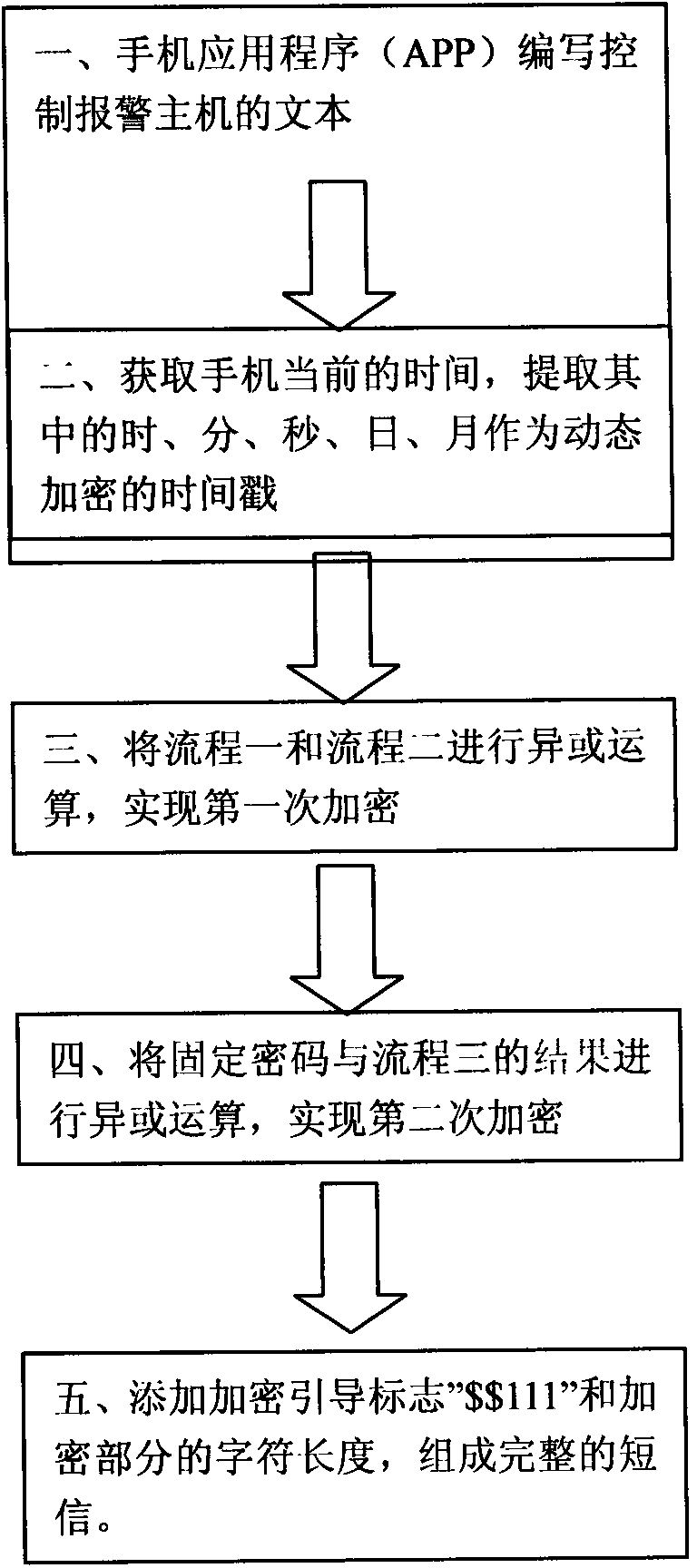
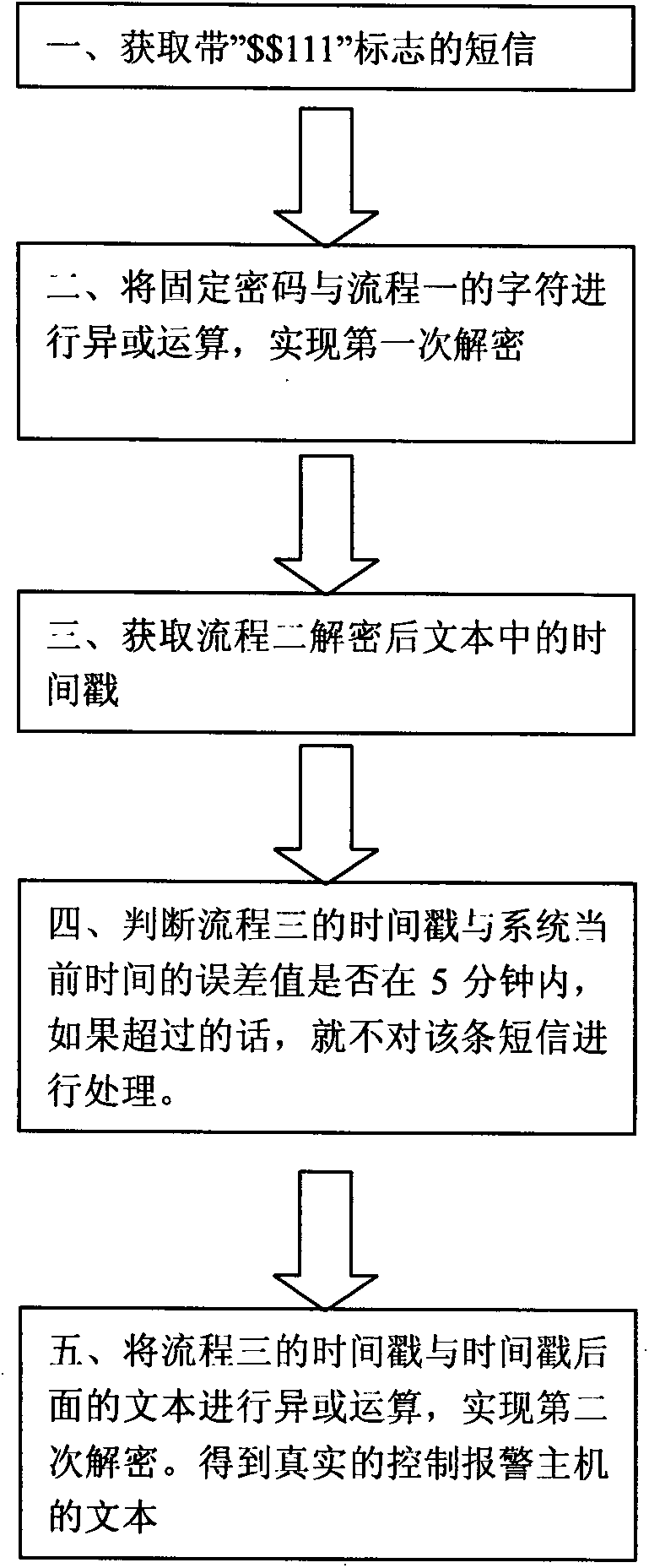
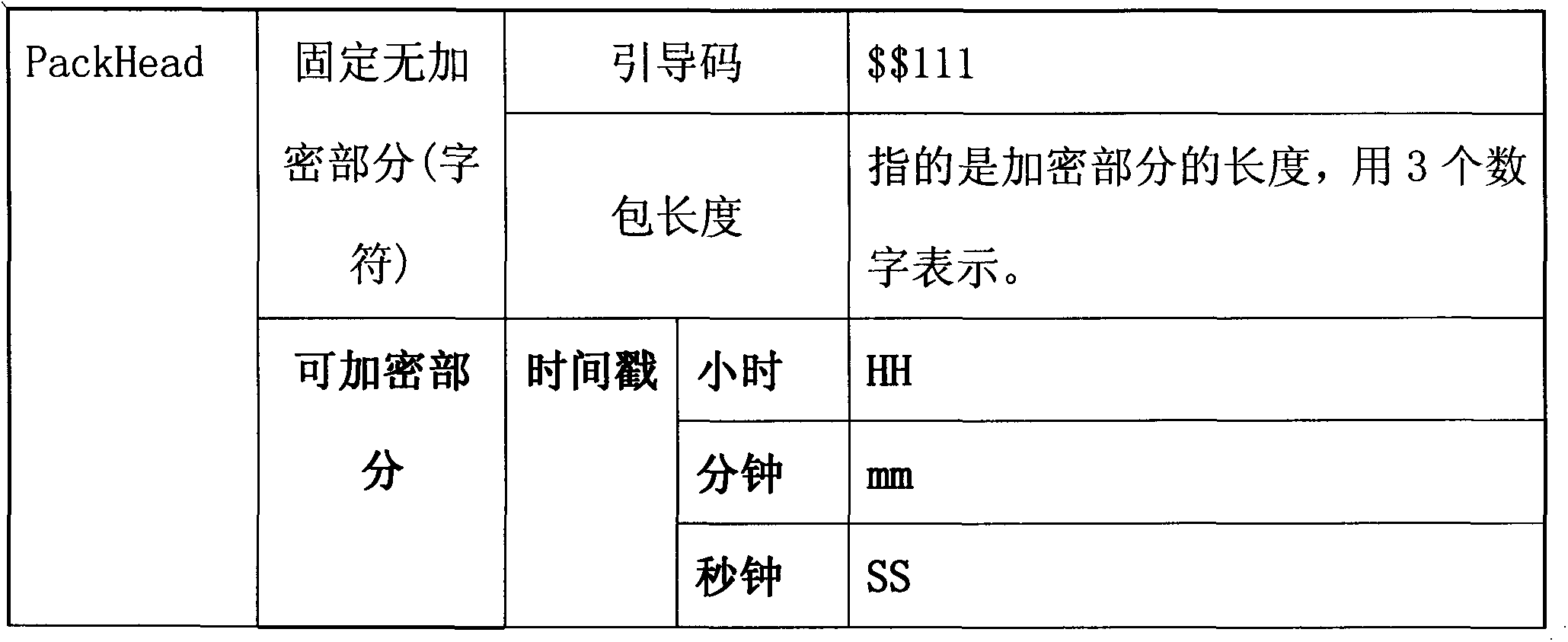
Method for achieving dynamic short message encryption between cell-phone application procedure and host
ActiveCN103546274APrevent illegal useSynchronising transmission/receiving encryption devicesMessaging/mailboxes/announcementsComputer hardwareTimestamp
Owner:深圳古诸华智能技术有限公司
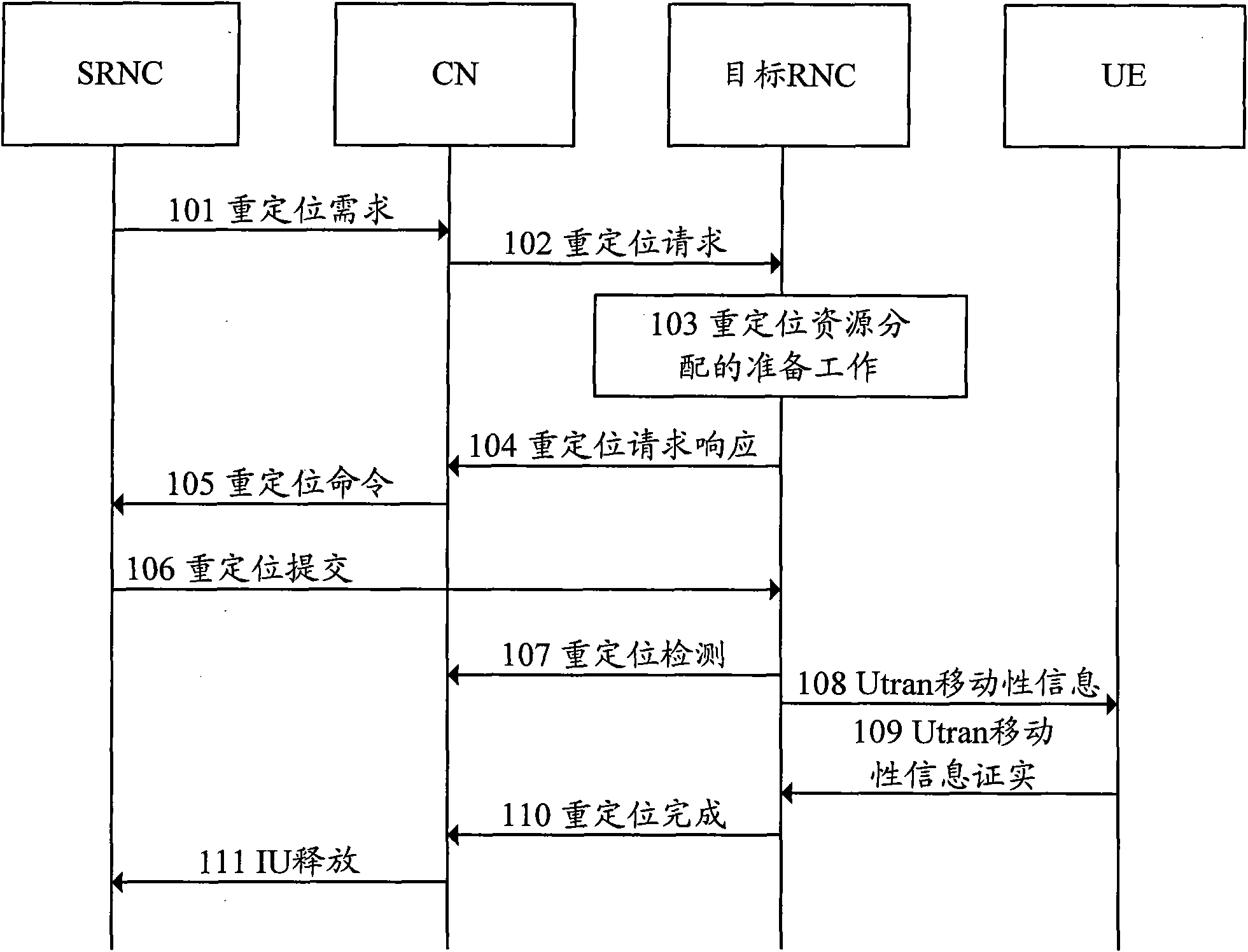
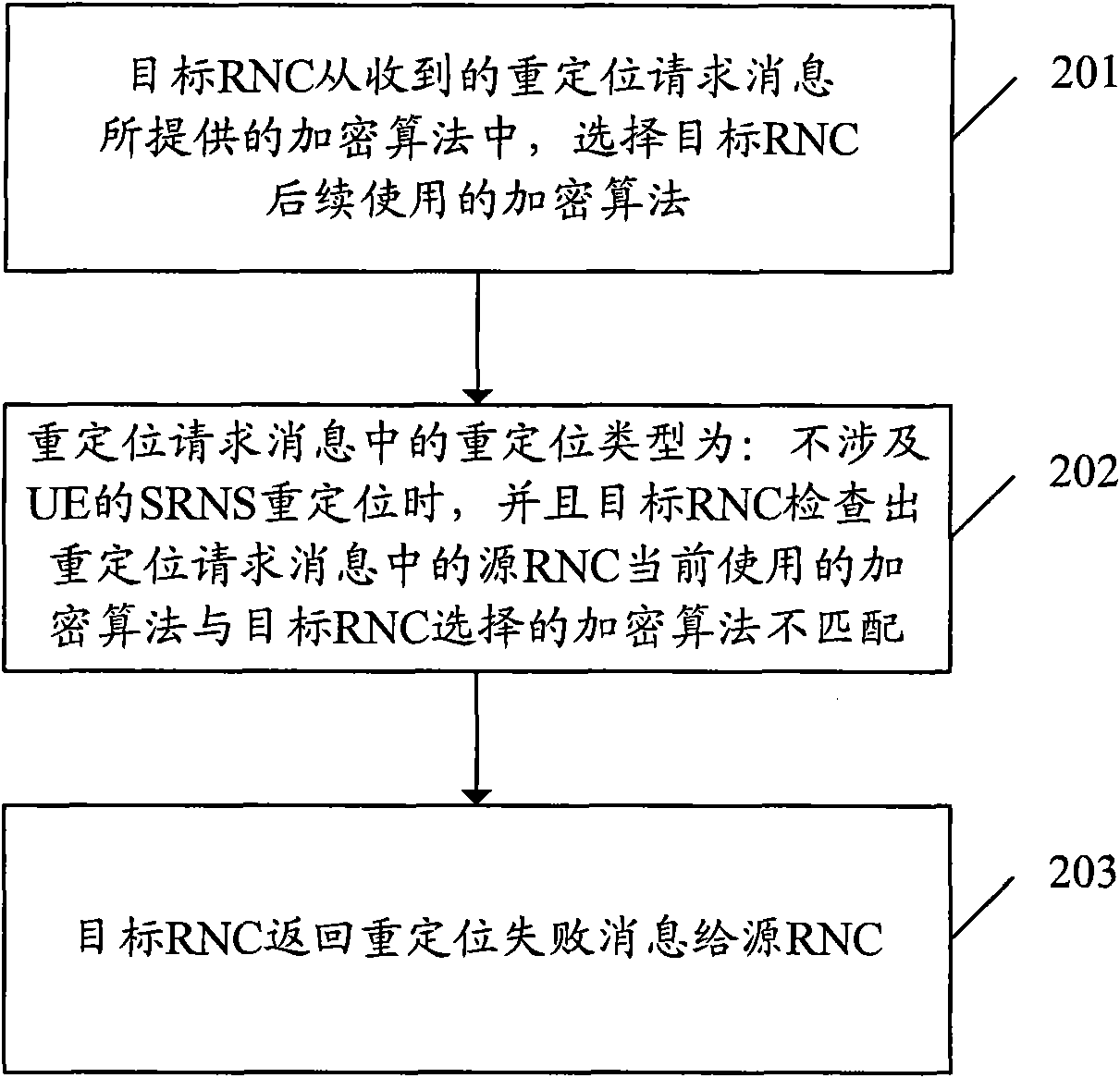
Repositioning processing method and system
InactiveCN102036233ARelocation is validGuarantee UE business behaviorError prevention/detection by using return channelConnection managementRadio networksProcess failure
Owner:ZTE CORP
Content copyright protection method based on original video data transformation encryption
Owner:UNITEND TECH +1
Cross-platform information source speech encryption method and cross-platform information source speech encryption device
ActiveCN108429851AImprove securityReduce complexitySubstation equipmentTransmissionModularitySpeech sound
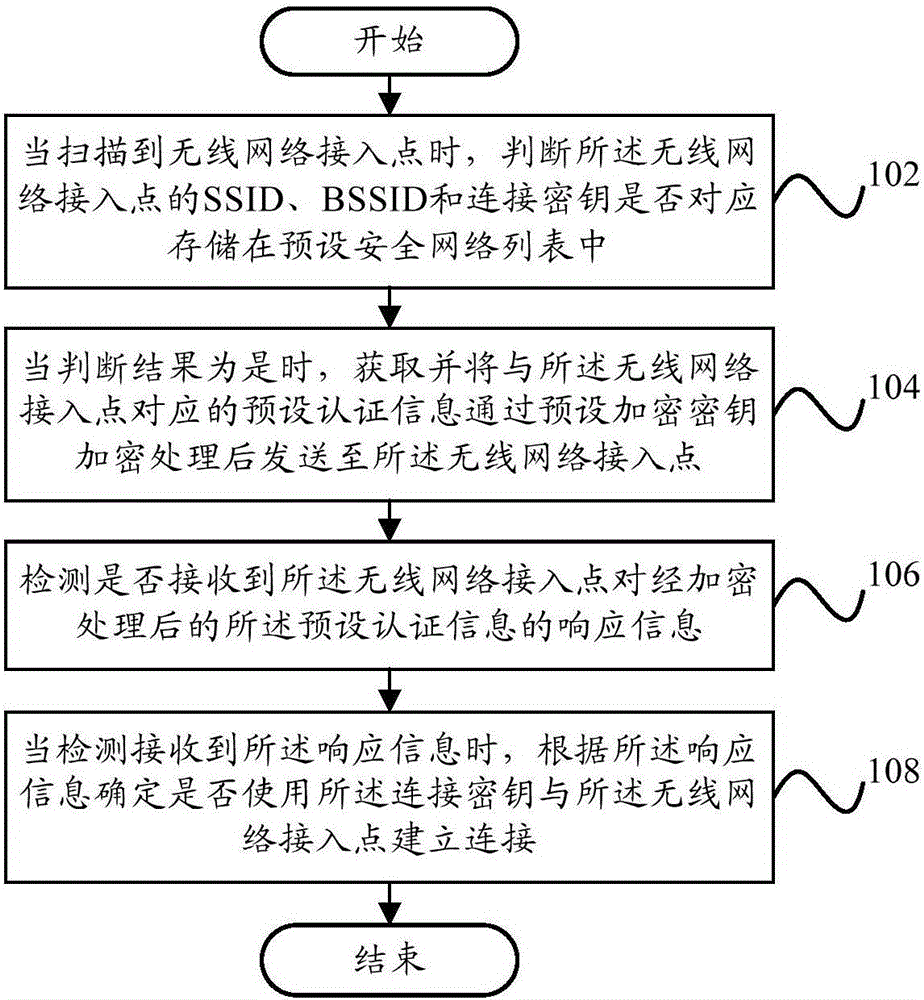
Owner:DATANG TERMINAL TECH
Method and apparatus for tobacco processing using blockchain encryption
InactiveCN109007951AImprove reliabilitySimple structureTobacco preparationTobacco treatmentMotor driveDrive motor
Owner:宁波鄞州台本荣机械设备有限公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap