Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
351results about "Digital data processing details" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
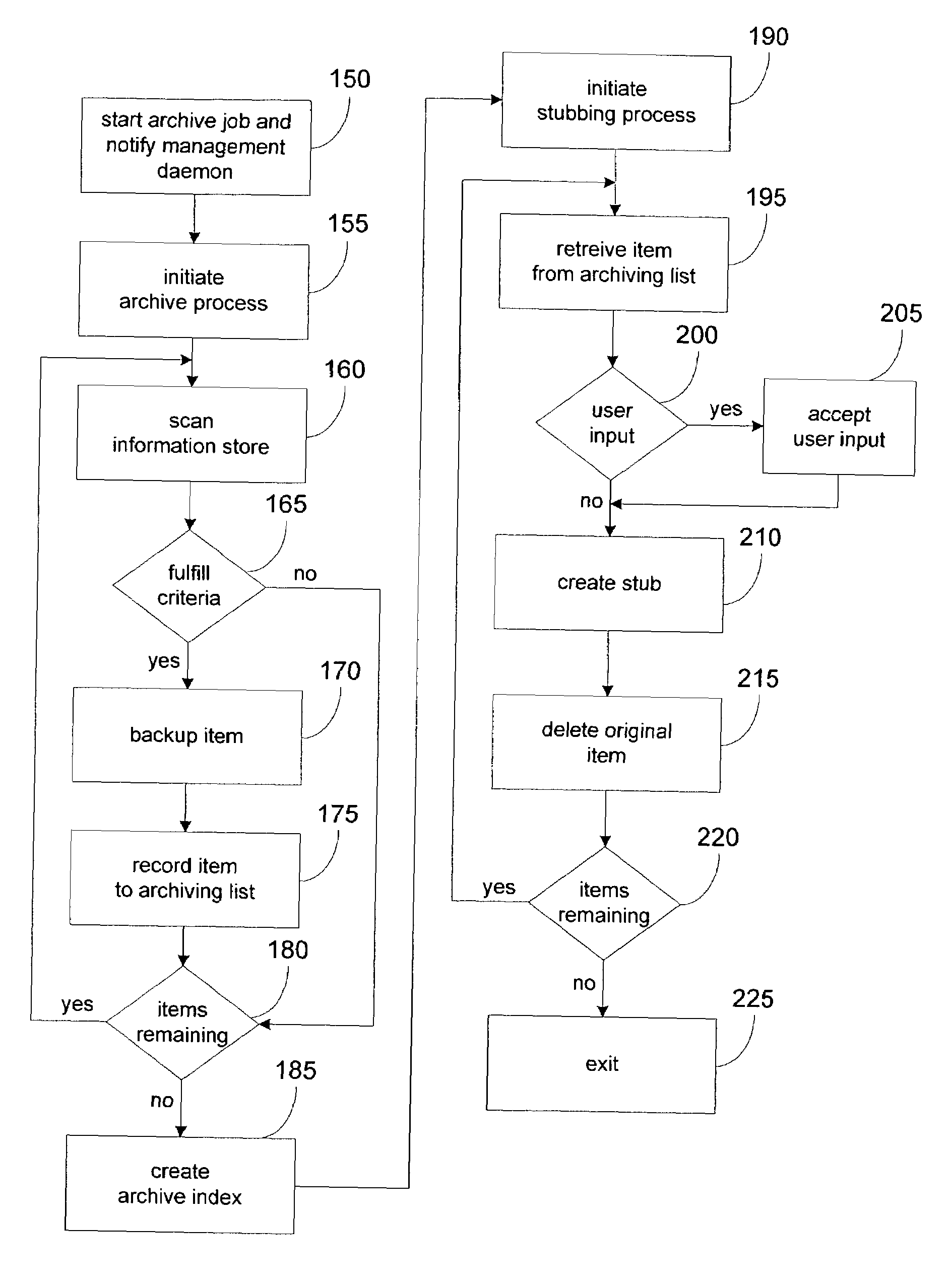
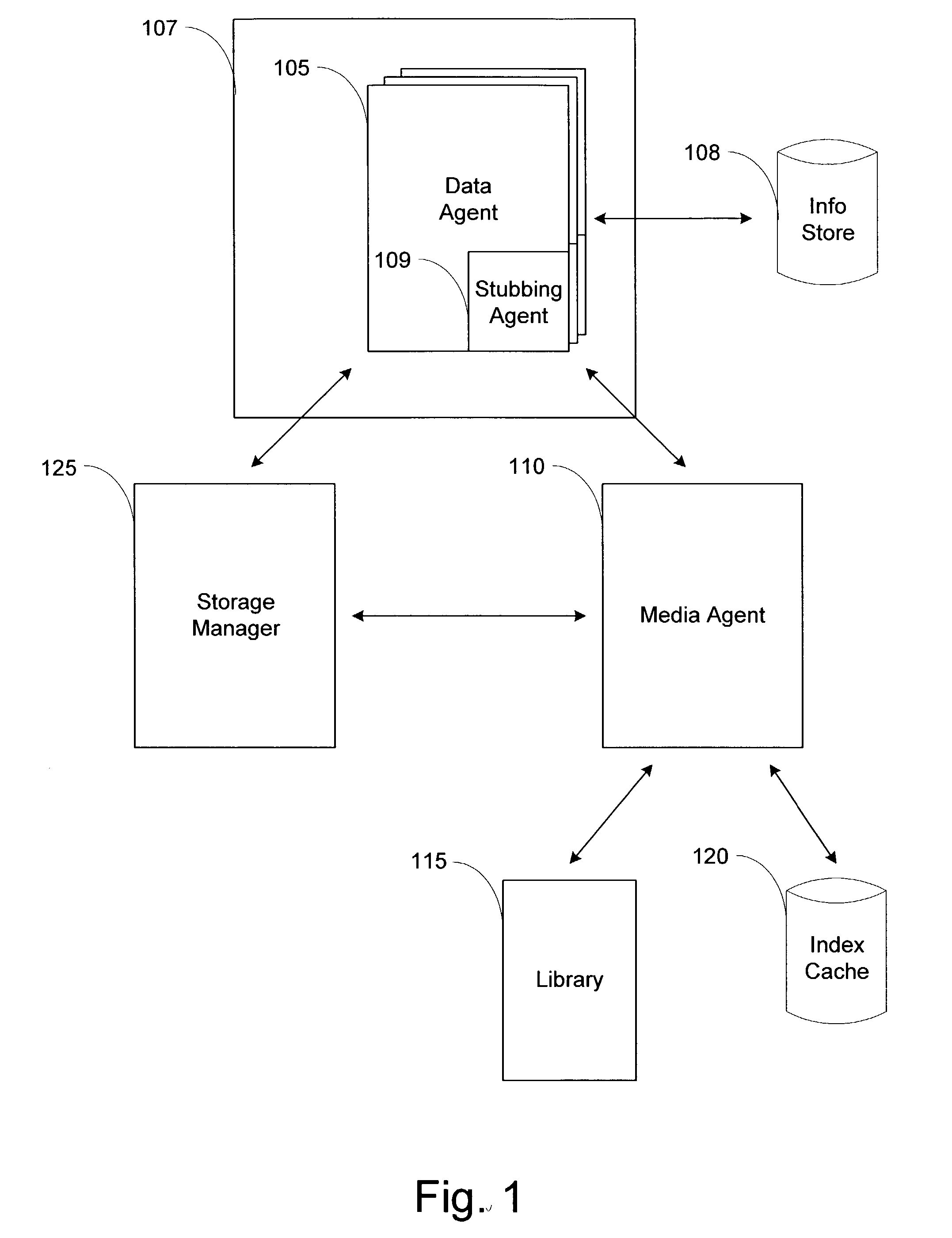
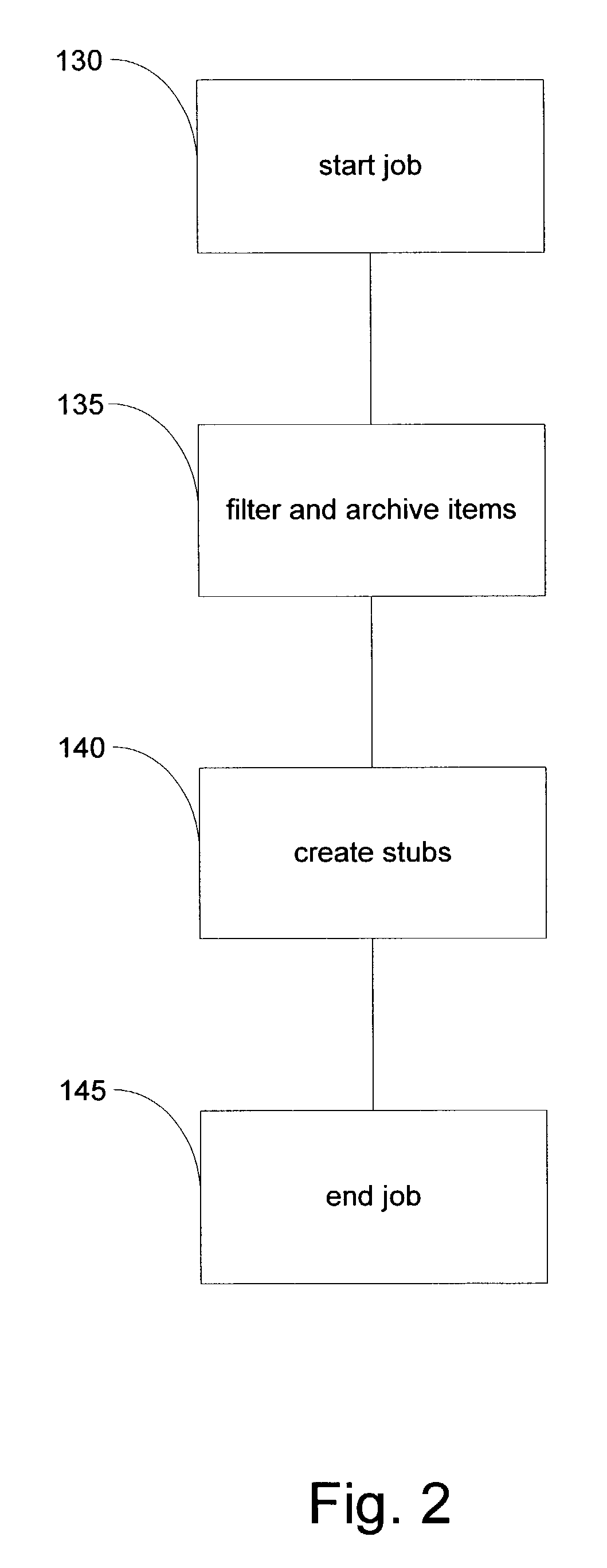
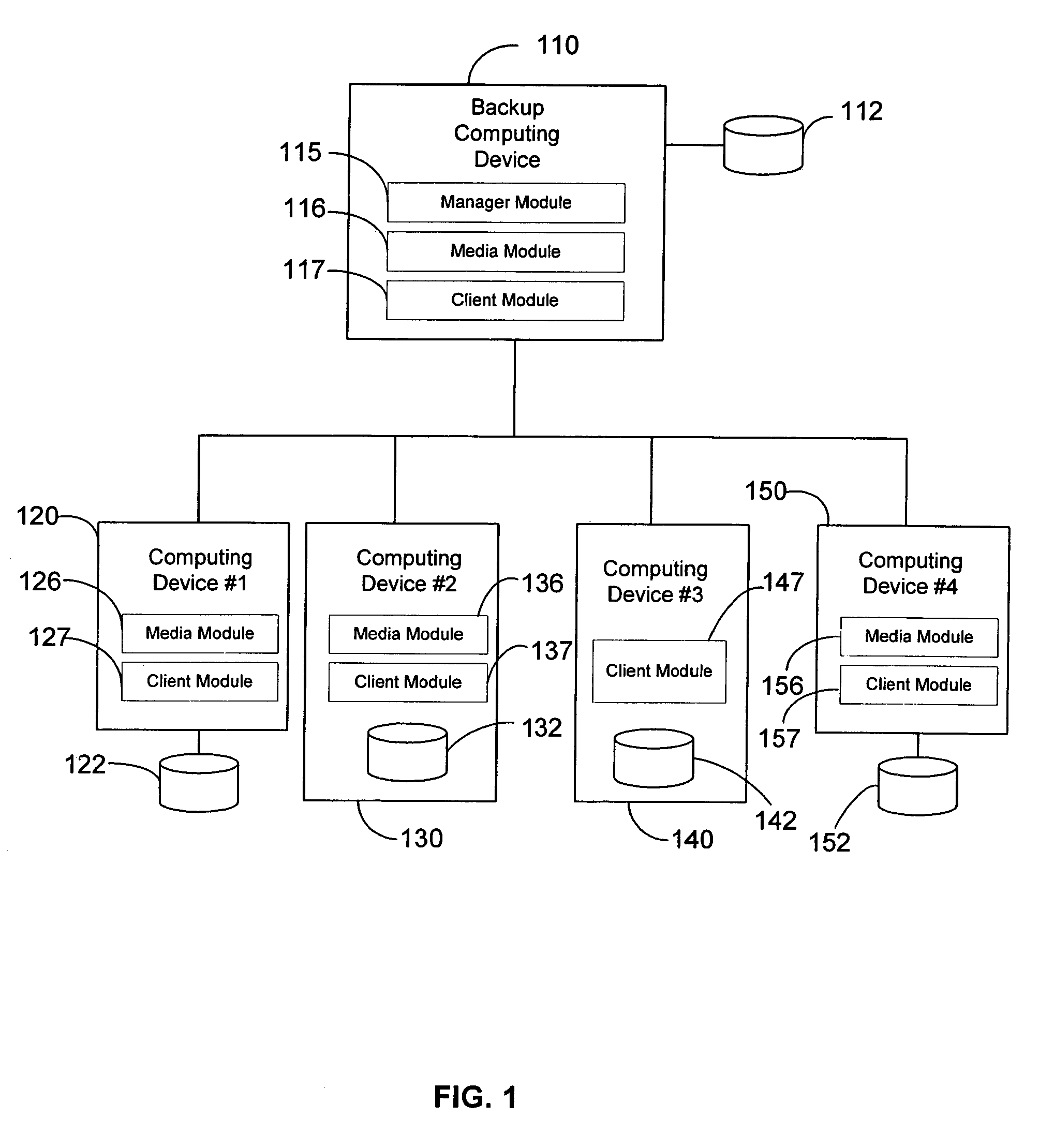
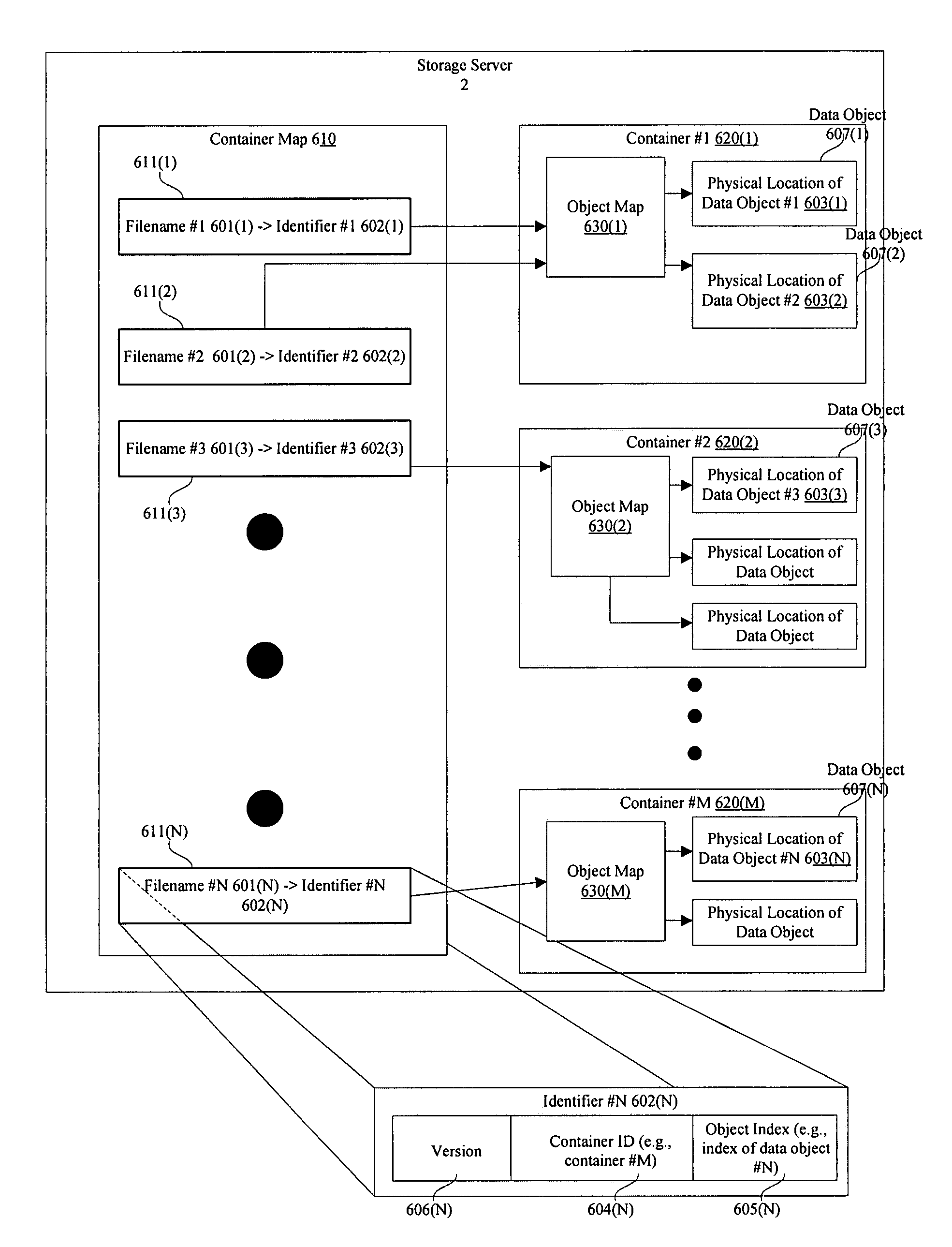
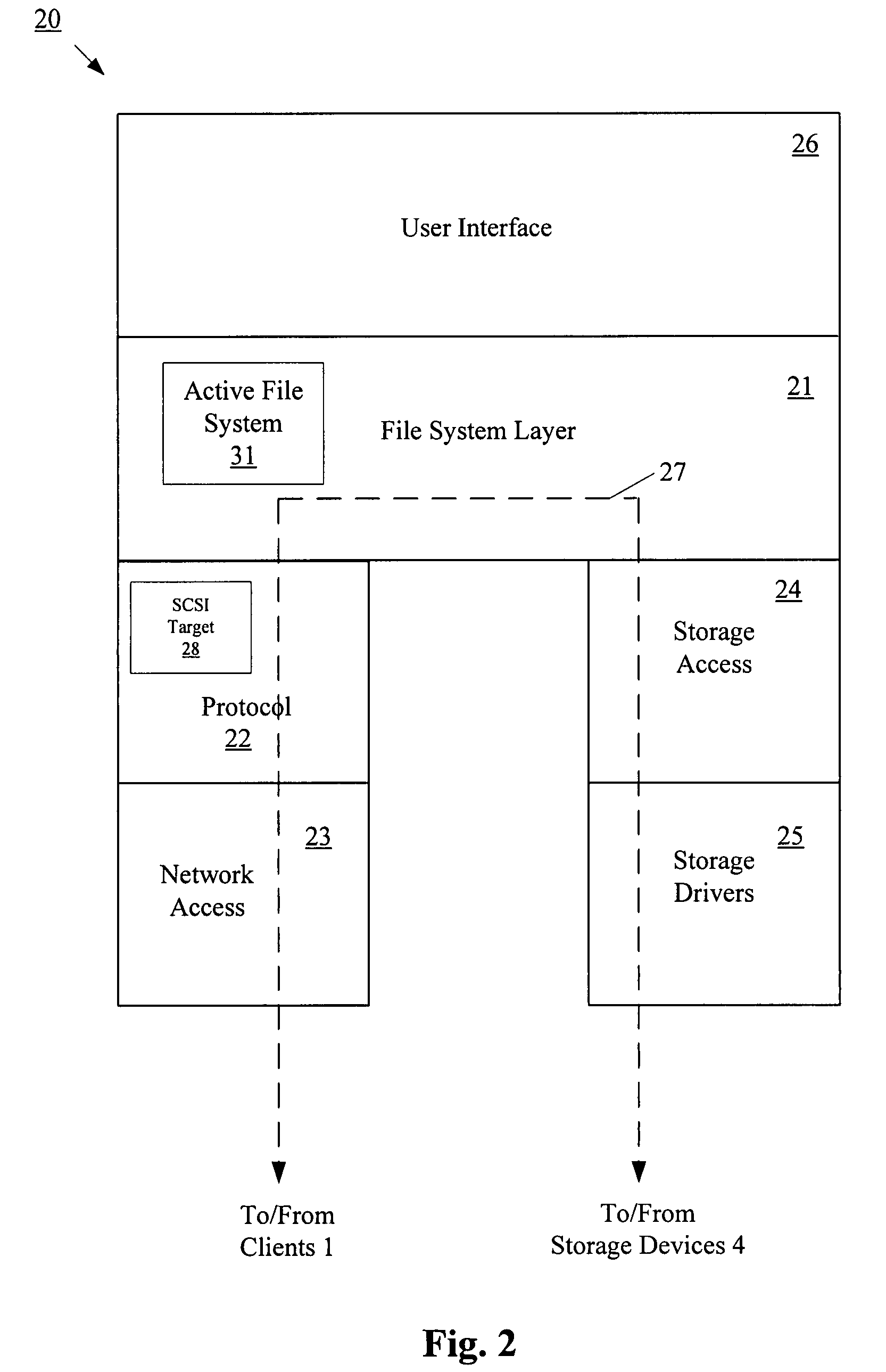
System and method for archiving objects in an information store
InactiveUS7107298B2Error detection/correctionDigital data processing detailsData typeInformation storage
Owner:COMMVAULT SYST INC
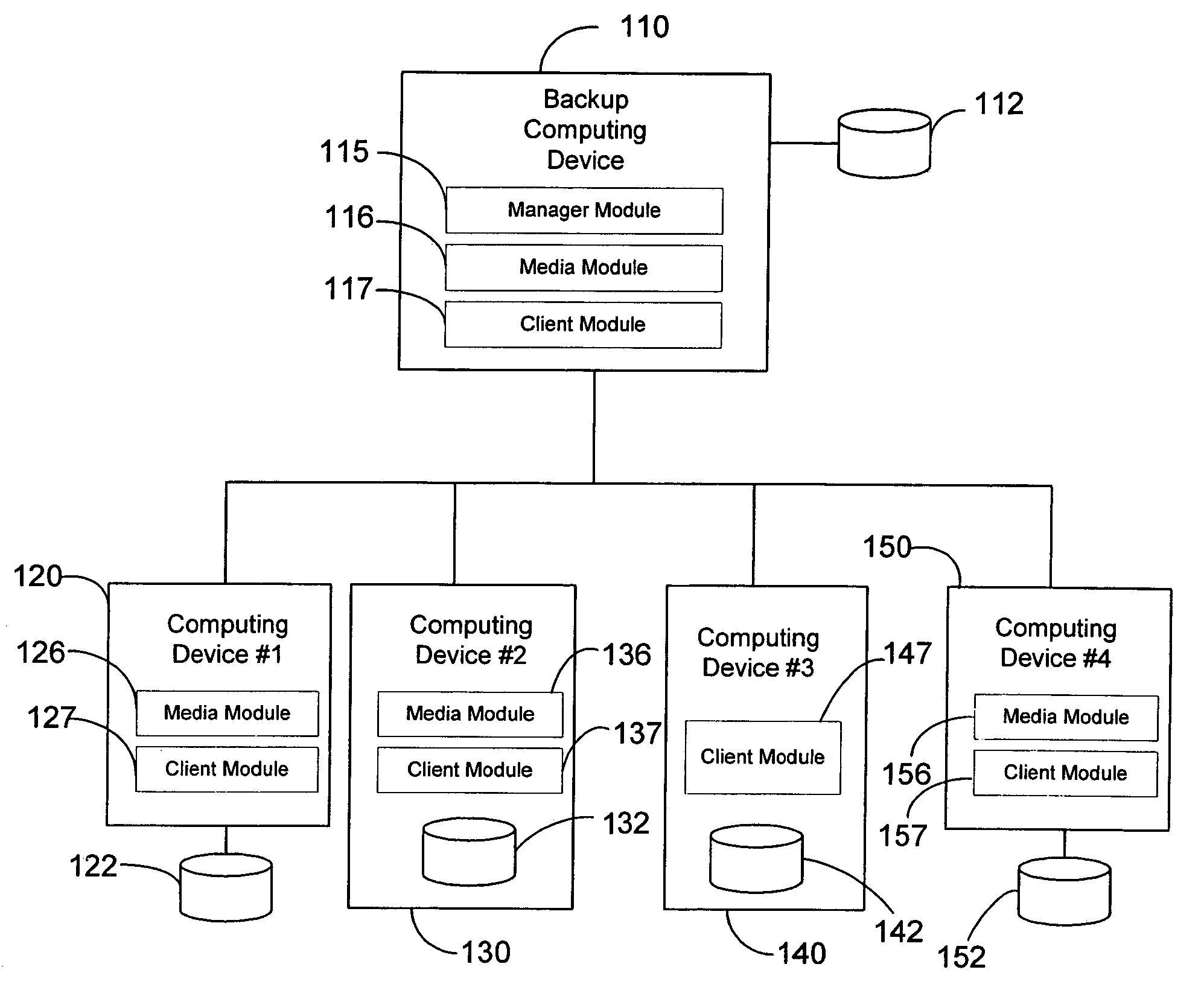
Modular backup and retrieval system
InactiveUS7389311B1Data processing applicationsDigital data processing detailsSystems managementModularity
Owner:COMMVAULT SYST INC
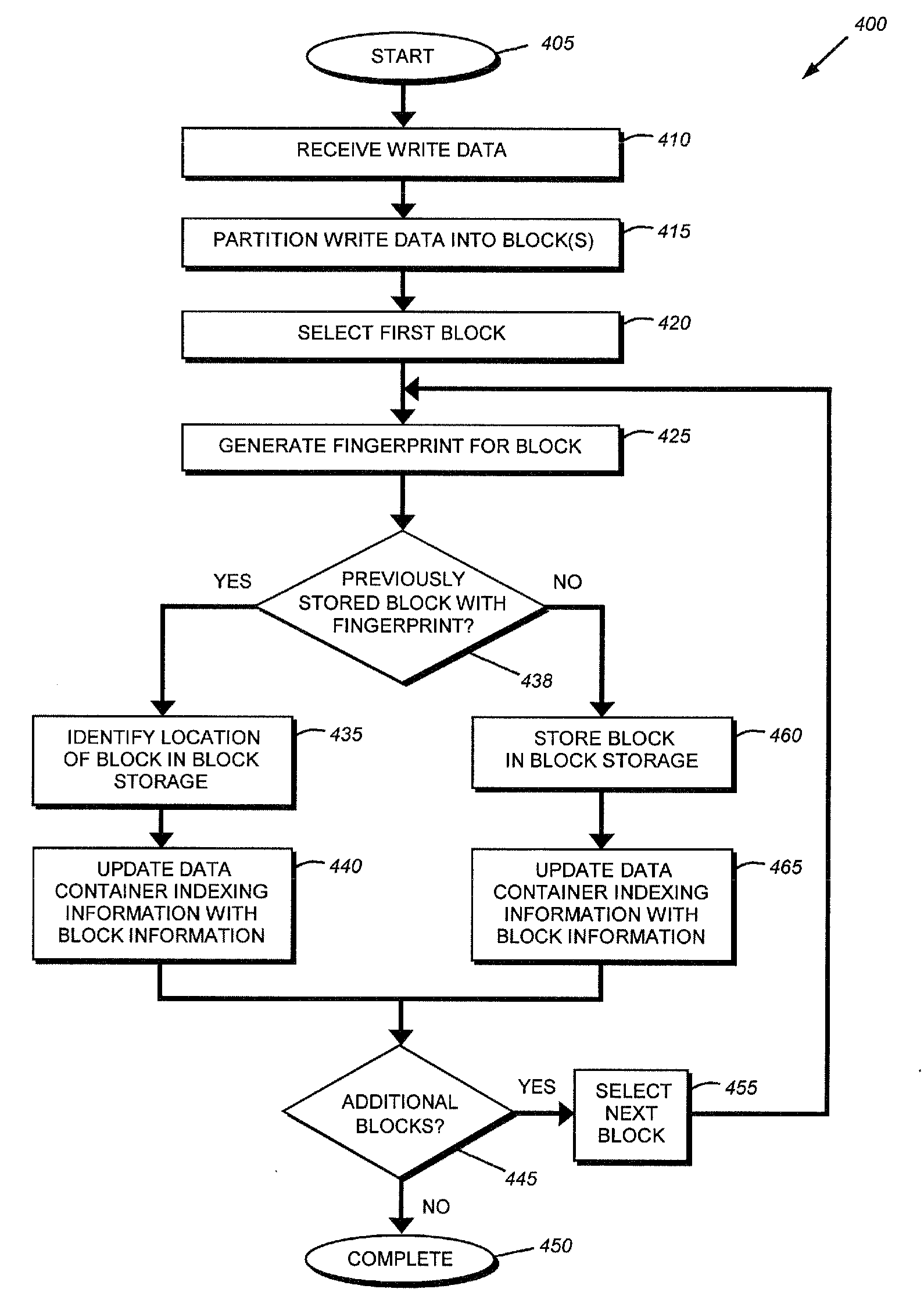
System and method for on-the-fly elimination of redundant data
ActiveUS20080294696A1Digital data information retrievalDigital data processing detailsOperational systemFile system
Owner:NETWORK APPLIANCE INC
System and method for managing and presenting entity information
InactiveUS20060101005A1Easy to displayShorten the timeDigital data processing detailsMaps/plans/chartsTime rangeRunning time
Owner:YANG WENDY W +1
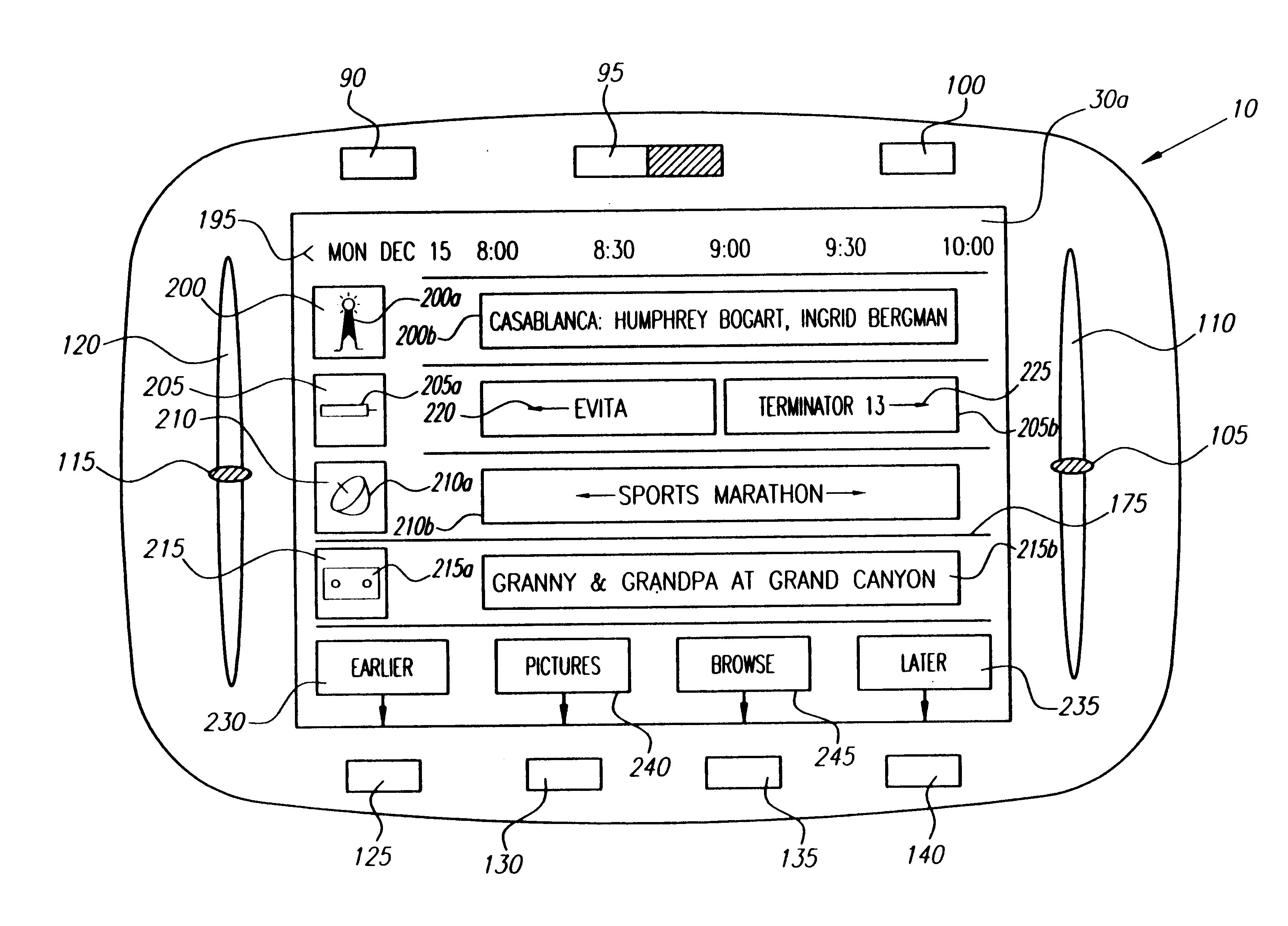
Portable internet-enabled controller and information browser for consumer devices
InactiveUS6882299B1The process is simple and easy to understandTelevision system detailsElectric signal transmission systemsGraphicsRemote control
Owner:RES INVESTMENT NETWORK
System for controlling exterior vehicle lights
InactiveUS6928180B2Control be disableAvoid componentsVehicle headlampsDigital data processing detailsAutomatic controlImage sensor
A system and method of automatically controlling exterior vehicle lights includes an image sensor and a controller to generate control signals. The control signals are derived based on information obtained from the image sensor as well as other detected parameters pertaining to the detected light source(s), the vehicle having the inventive control system, and the ambient environment. The control circuit may simply turn certain exterior lights on or off, or change the brightness, aim, focus, etc. to produce various beam patterns that maximize the illuminated area in front of the vehicle without causing excessive glare in the eyes of other drivers.
Owner:GENTEX CORP
Methods for combating malicious software
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
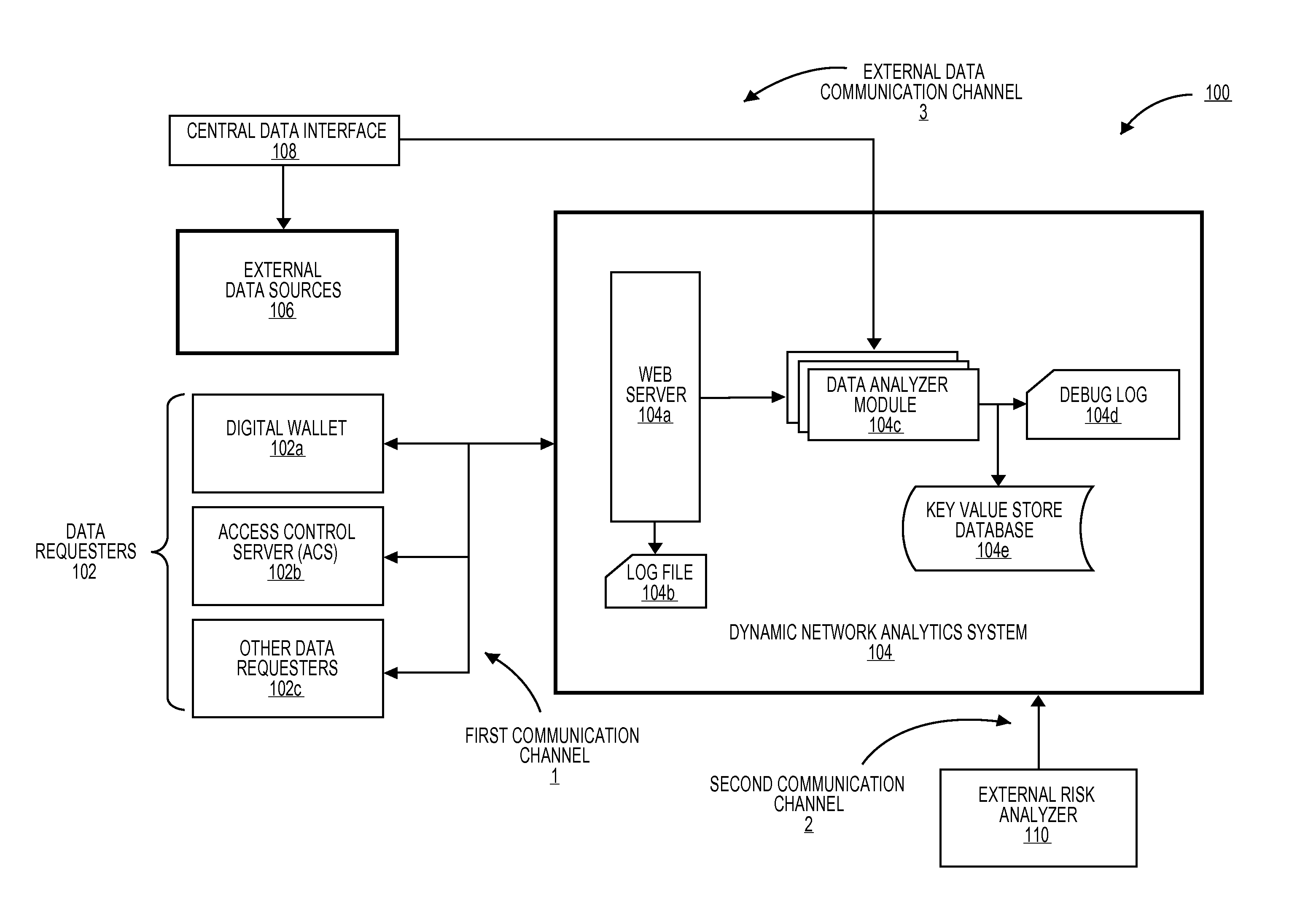
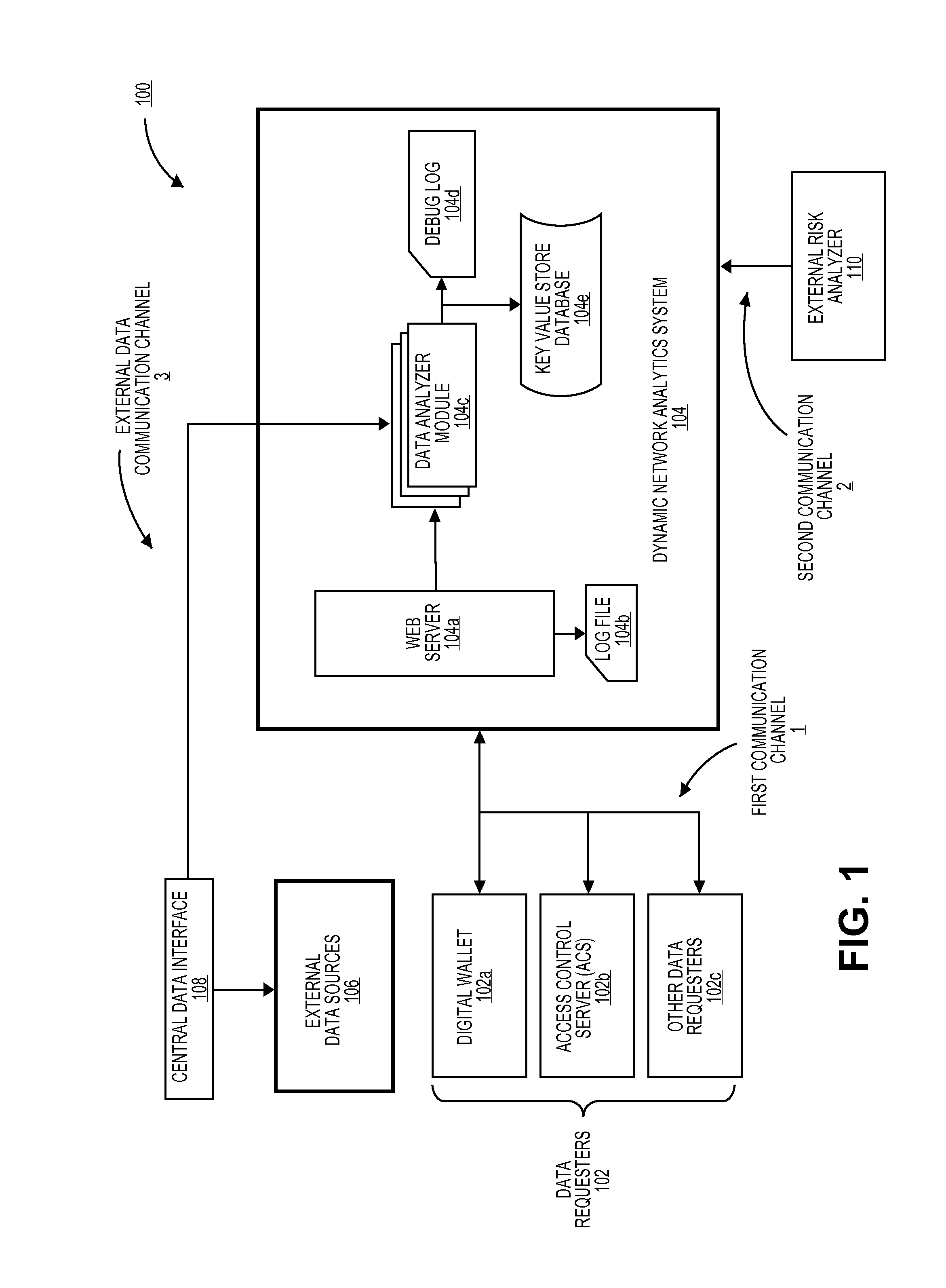
Dynamic network analytics system
ActiveUS20130144888A1Digital data information retrievalDigital data processing detailsNetwork analyticsExternal data
Owner:VISA INT SERVICE ASSOC
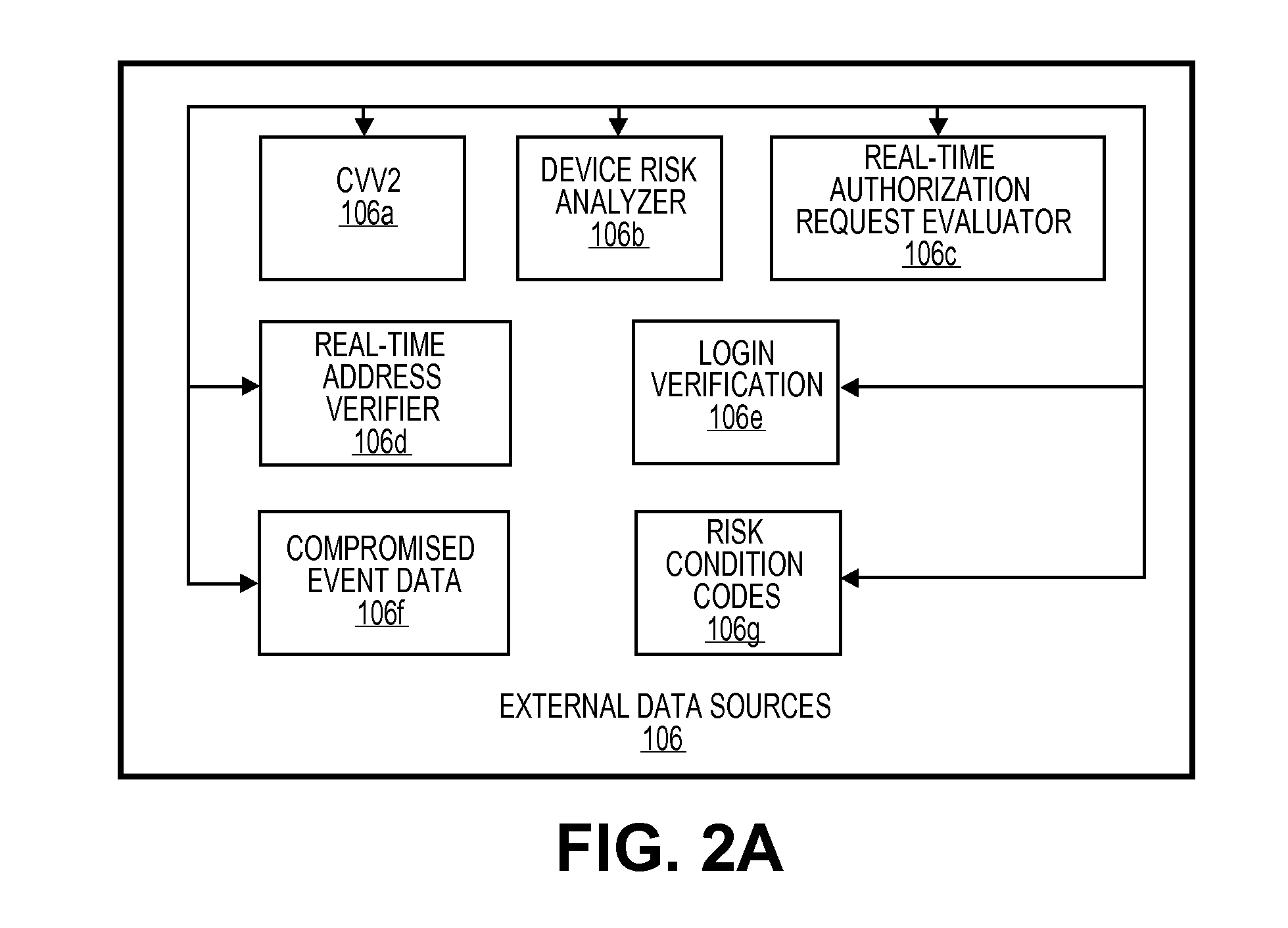
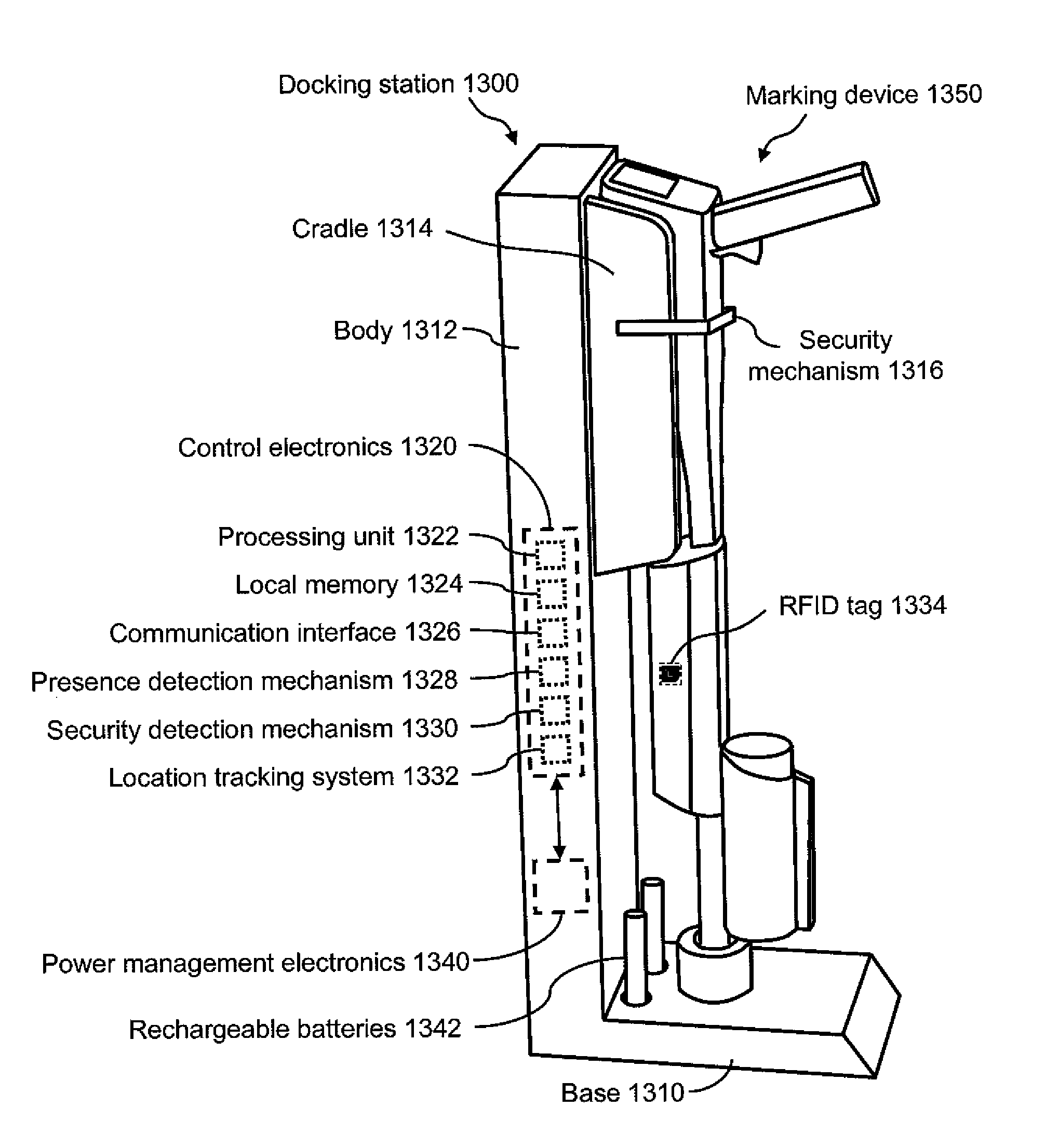
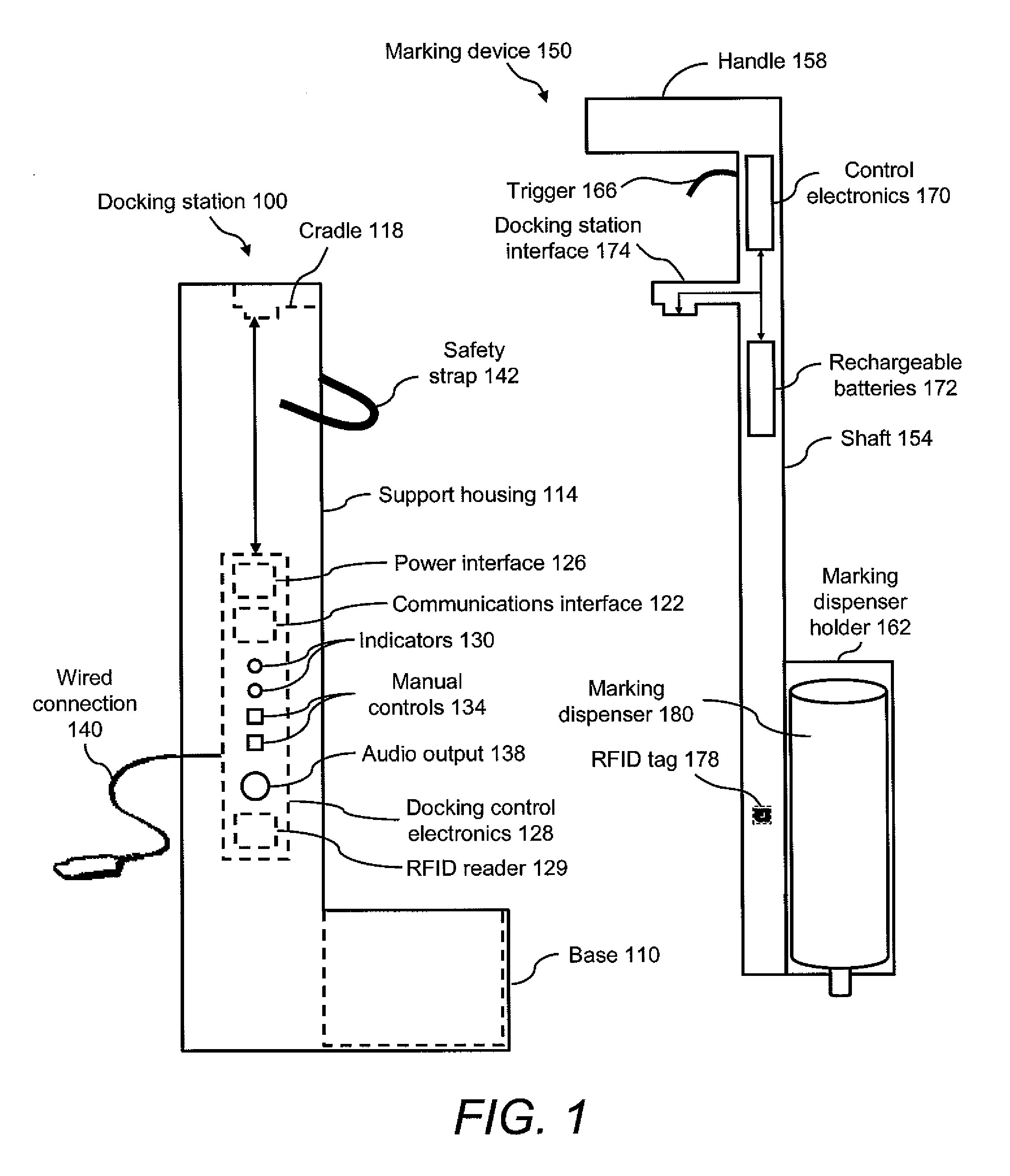
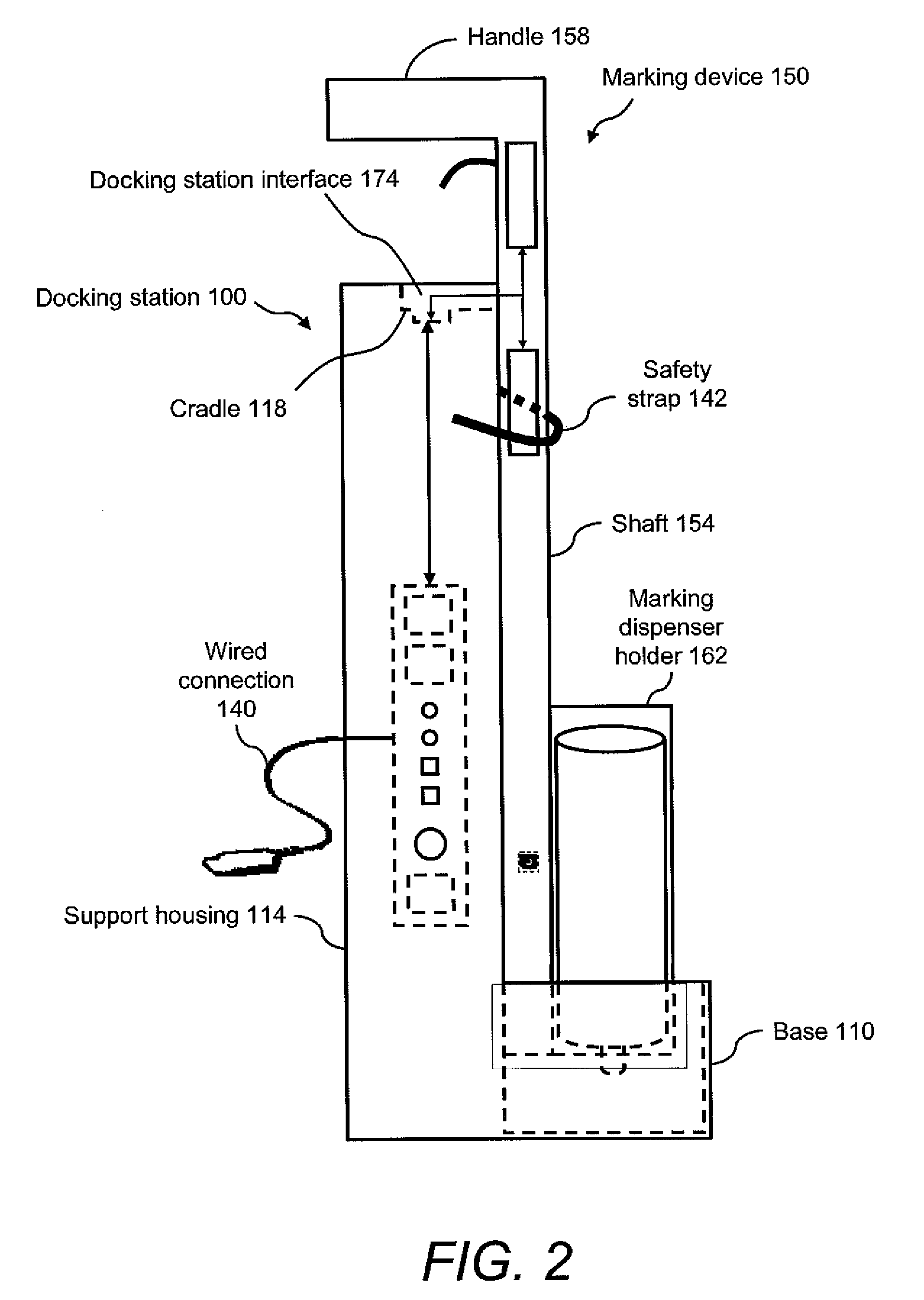
Marking device docking stations having security features and methods of using same
Owner:CERTUSVIEW TECH LLC
Method and System for Managing Metadata
InactiveUS20080201299A1Digital data processing detailsMetadata multimedia retrievalContext basedApplication software
Owner:NOKIA CORP
Multiple entity control of access restrictions for media playback
InactiveUS20050086683A1Digital data processing detailsAnalogue secracy/subscription systemsThird partyWorld Wide Web
Owner:INTEL CORP
Method and Apparatus for Fingerprint Image Reconstruction
Owner:SYNAPTICS INC
Method and Apparatus for Optimizing Queries over Vertically Stored Database
InactiveUS20090132474A1Good effectDigital data information retrievalDigital data processing detailsData miningComputer science
Owner:IBM CORP
Automated application discovery and analysis system and method
ActiveUS20060123022A1Digital data processing detailsObject oriented databasesSystems designMonitoring system
Owner:GLOBAL SAAS SOLUTIONS PTE LTD
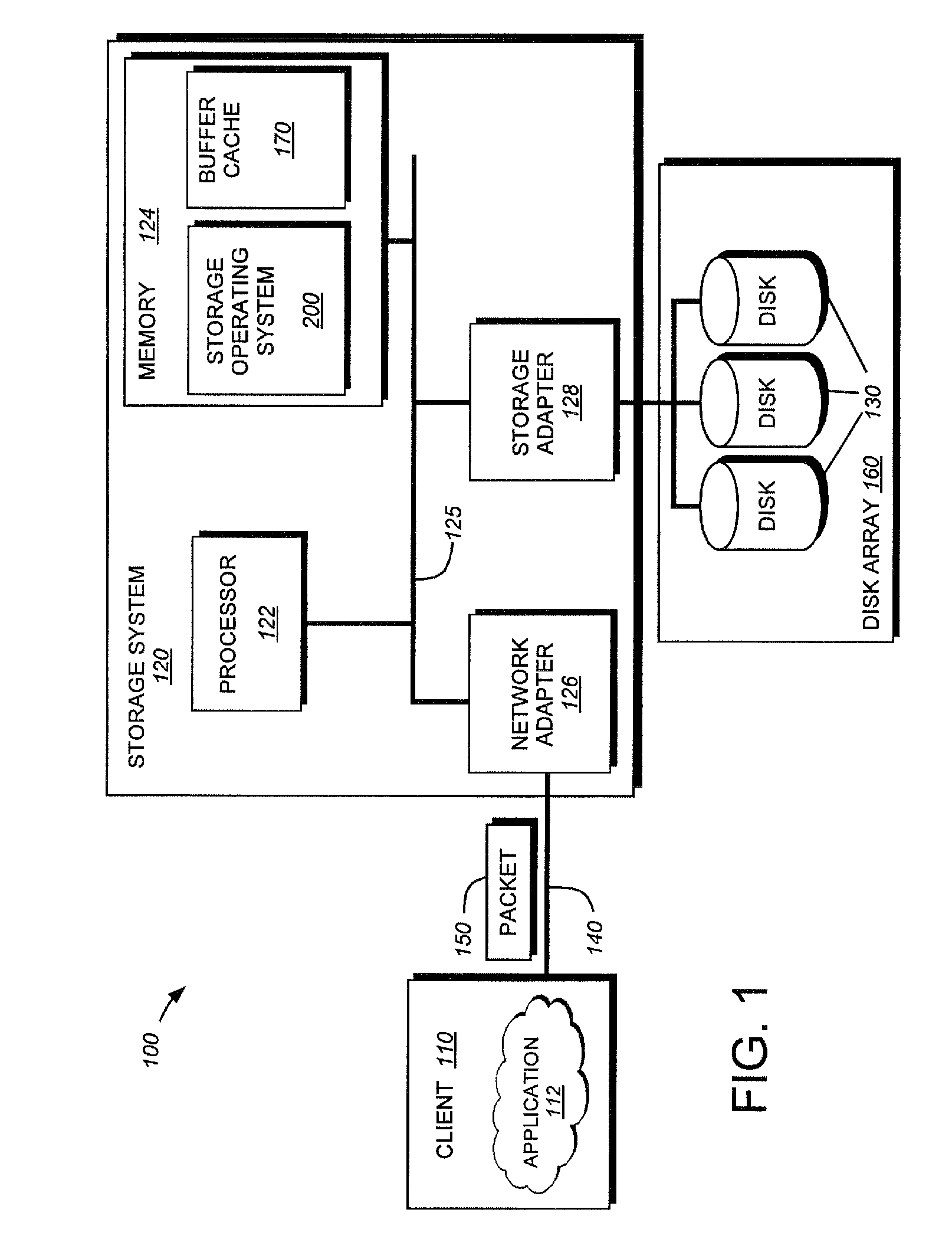
Method and apparatus for data retention in a storage system
ActiveUS20050125411A1Digital data information retrievalMemory loss protectionRetention periodSoftware engineering
A system and method are provided for retention of data on a storage system. An application program provides the storage system with data to be stored on the storage system. The application program also provides the storage system with a retention period that indicates a period of time for which the data may not be deleted. When the storage system receives a request to delete the data, it first evaluates the retention period associated with that data to determine if the retention period has expired. If the retention period has not expired, the storage system denies the request to delete the data.
Owner:EMC IP HLDG CO LLC
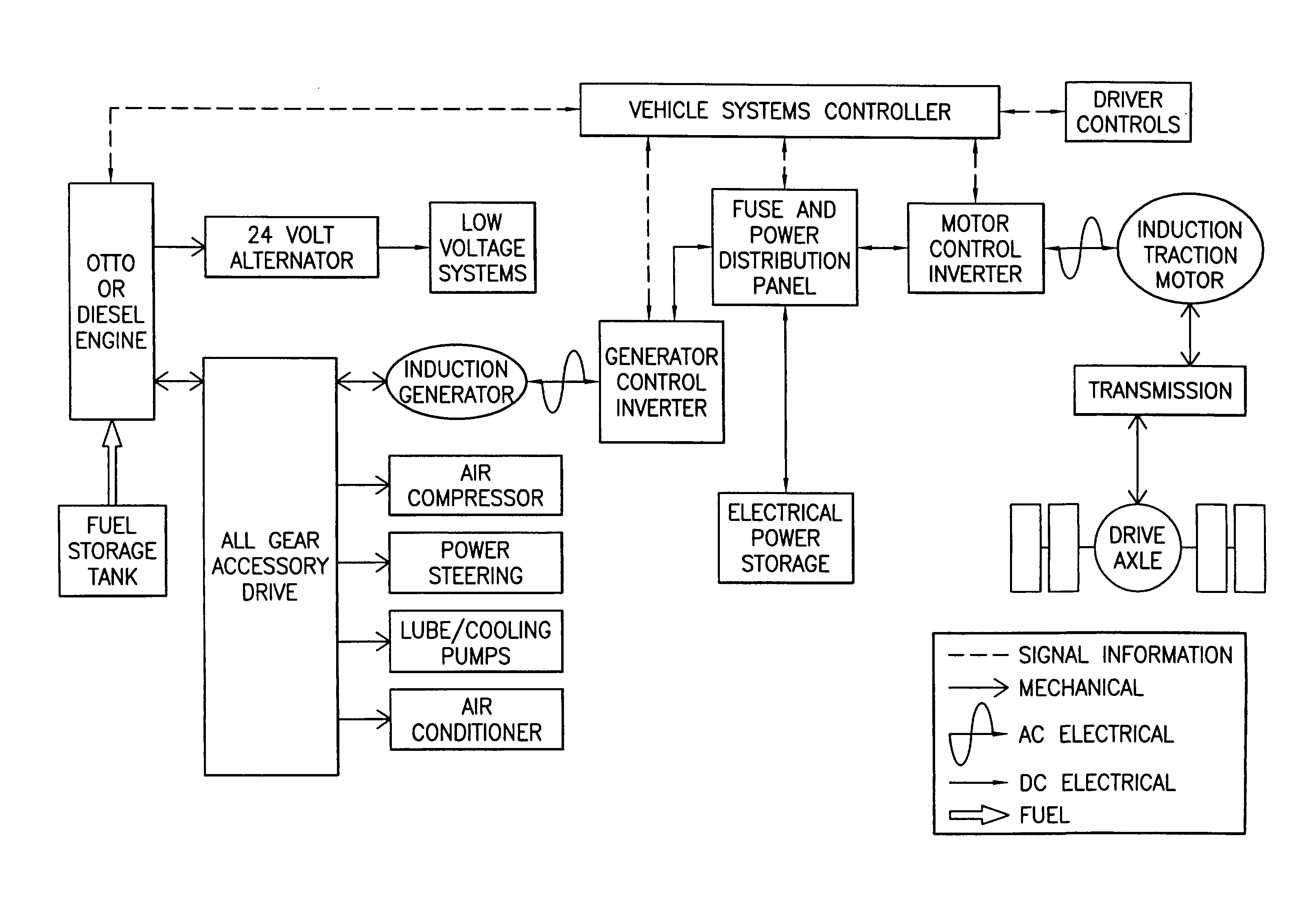
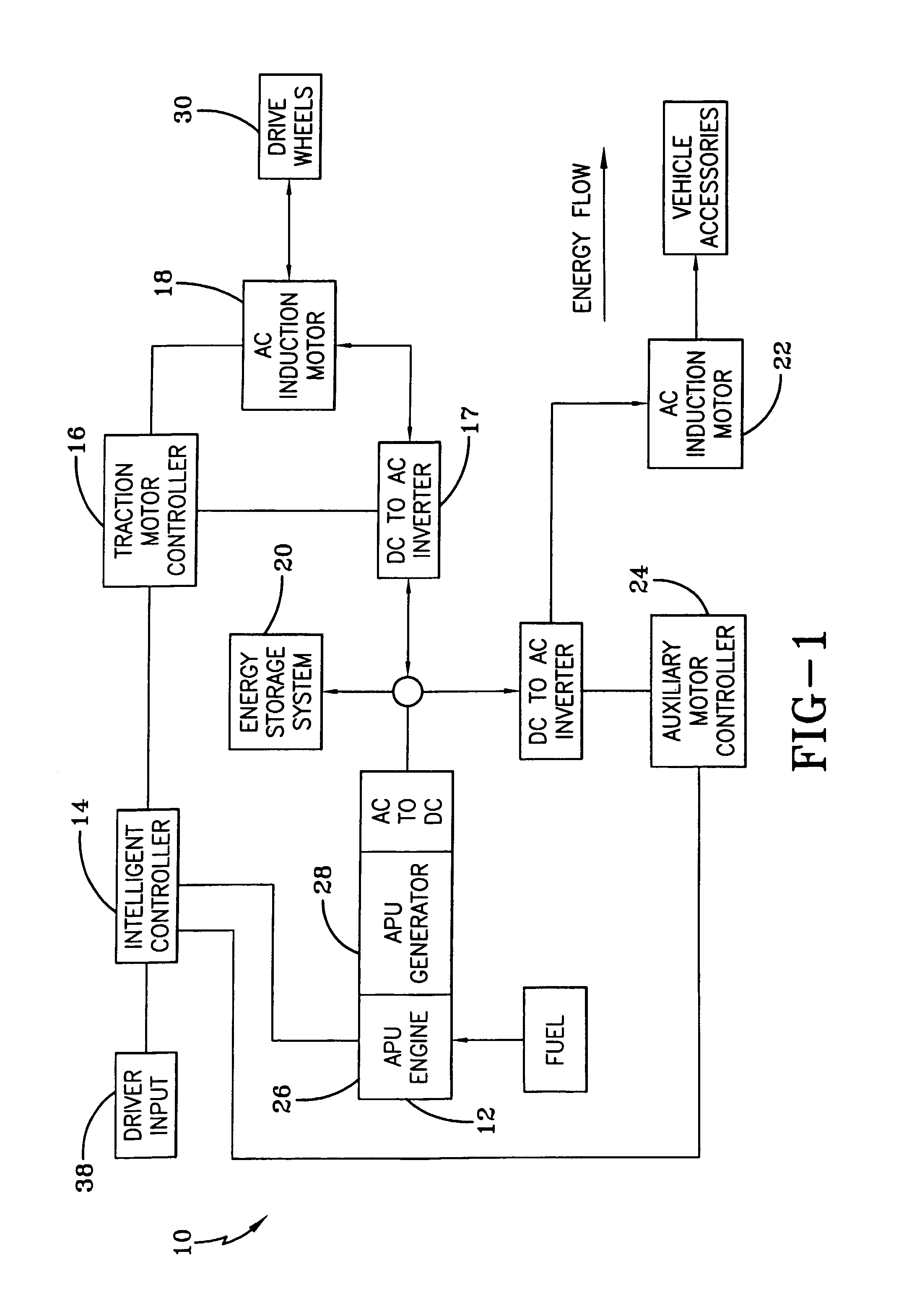
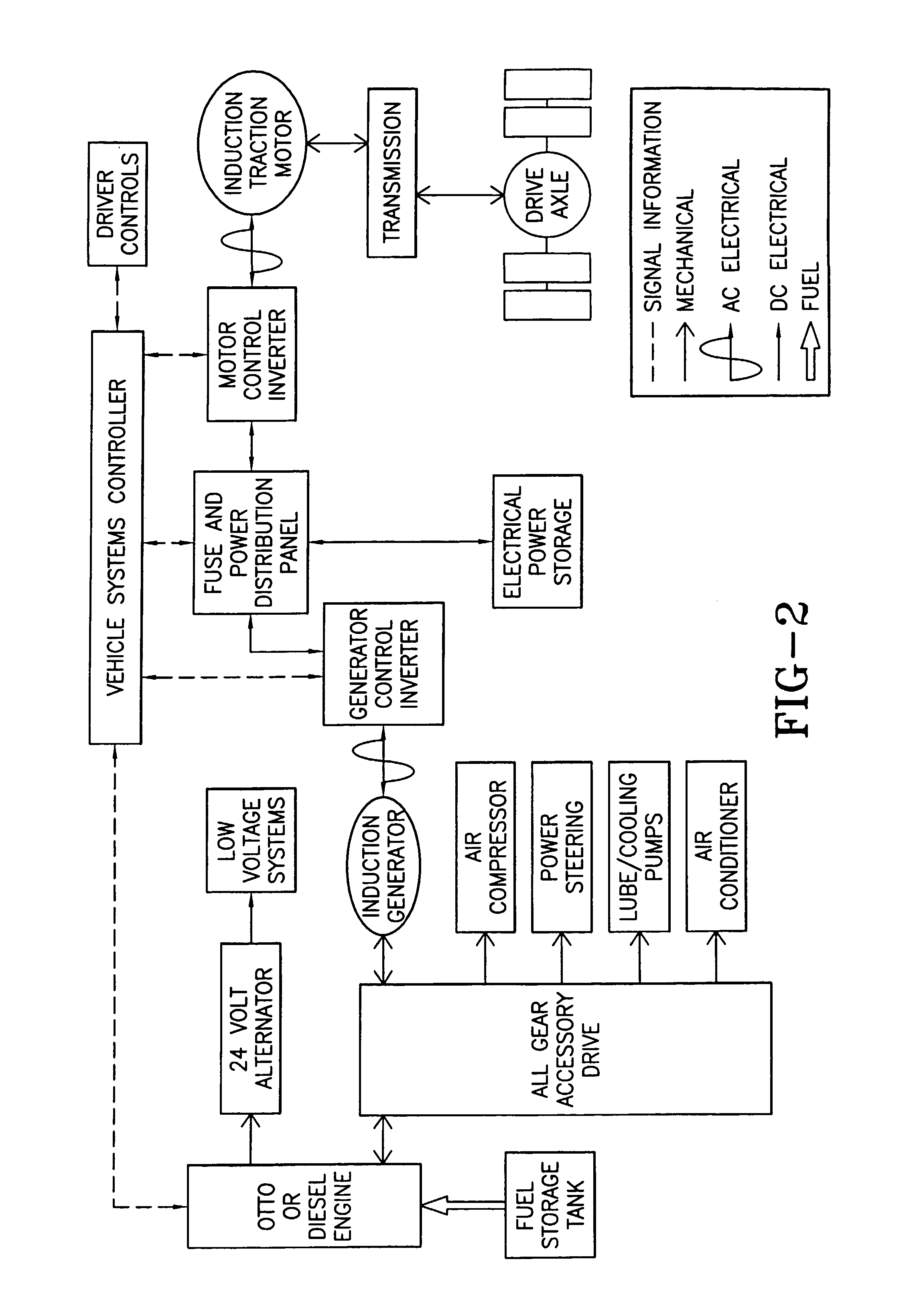
Hybrid electric vehicle
InactiveUS7252165B1Poor vehicle performanceImprove variationDigital data processing detailsVehicle sub-unit featuresLow voltageAuxiliary power unit
Owner:BOWLING GREEN STATE UNIV
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
Data containerization for reducing unused space in a file system
Owner:NETWORK APPLIANCE INC
Smart cover peek
InactiveUS20130328917A1Digital data processing detailsCathode-ray tube indicatorsSensor arrayDisplay device
A tablet device includes a display configured to present visual content, a sensor array configured to detect a status of a foldable flap in relation to the display, and a processor configured to operate the tablet device in accordance with the determined status of the foldable flap in relation to the display. In one embodiment, the processor receives a setting value and uses the setting value to execute an application in accordance with the determined relationship of the flap and the display.
Owner:APPLE INC
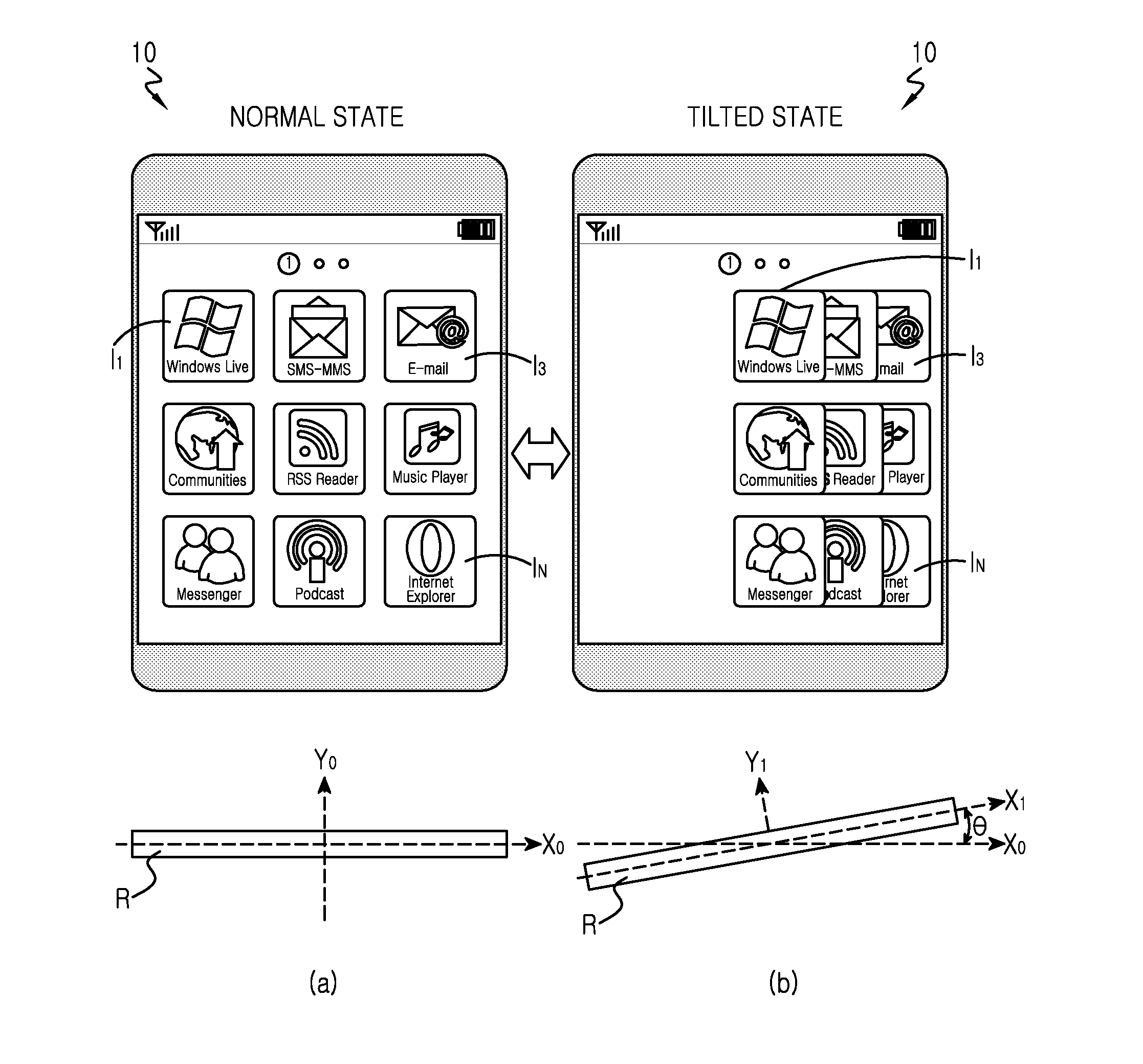
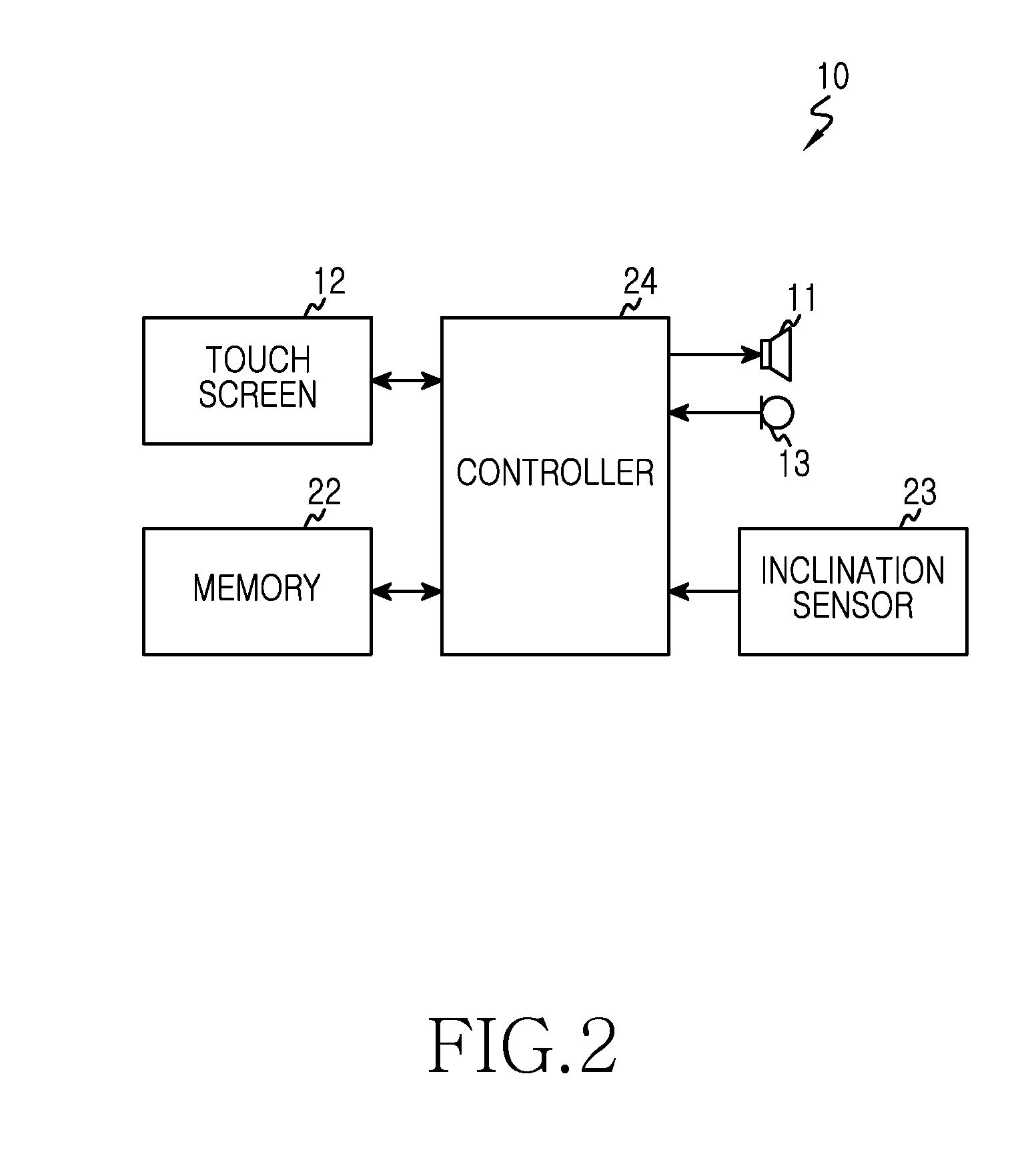
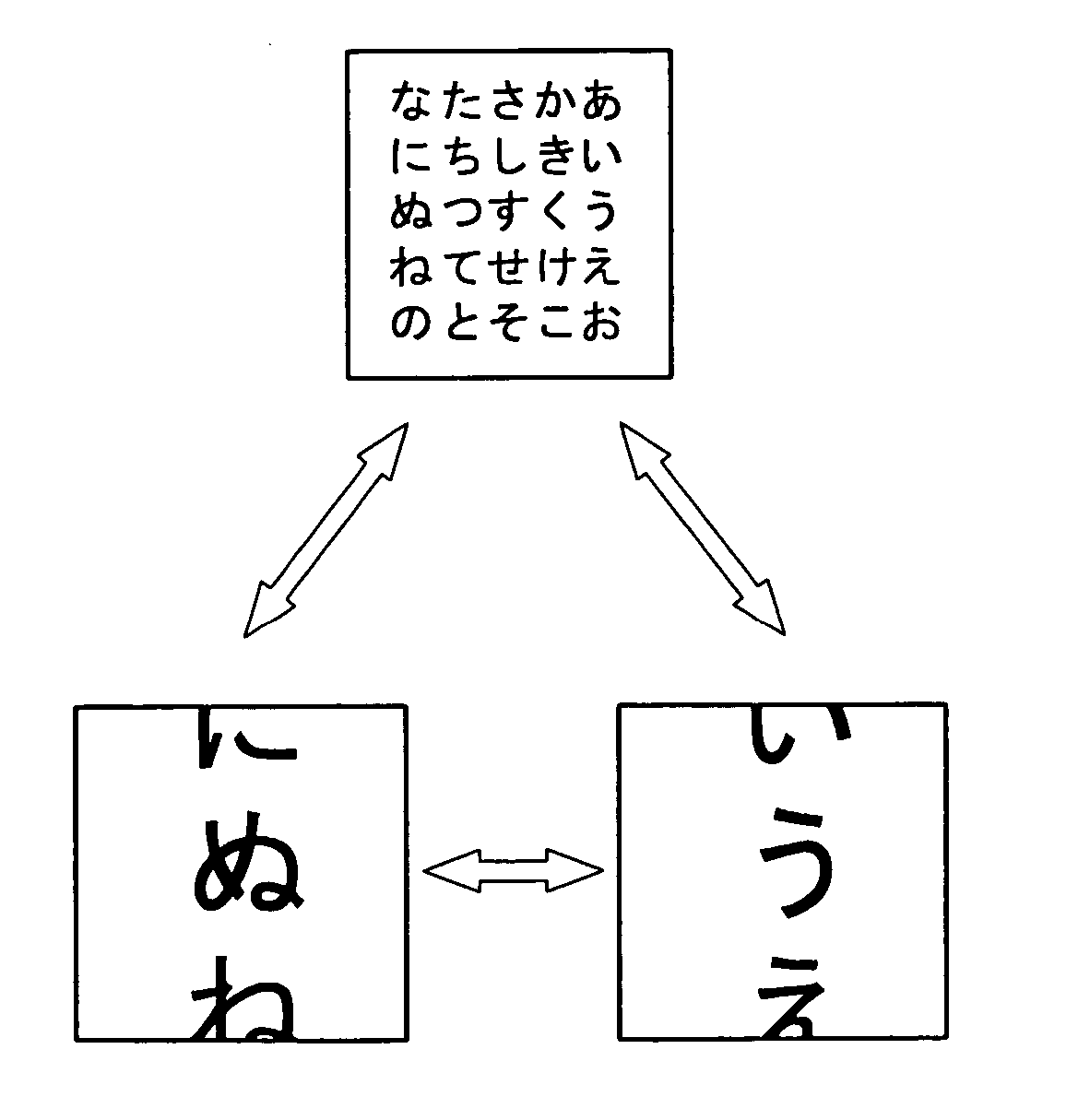
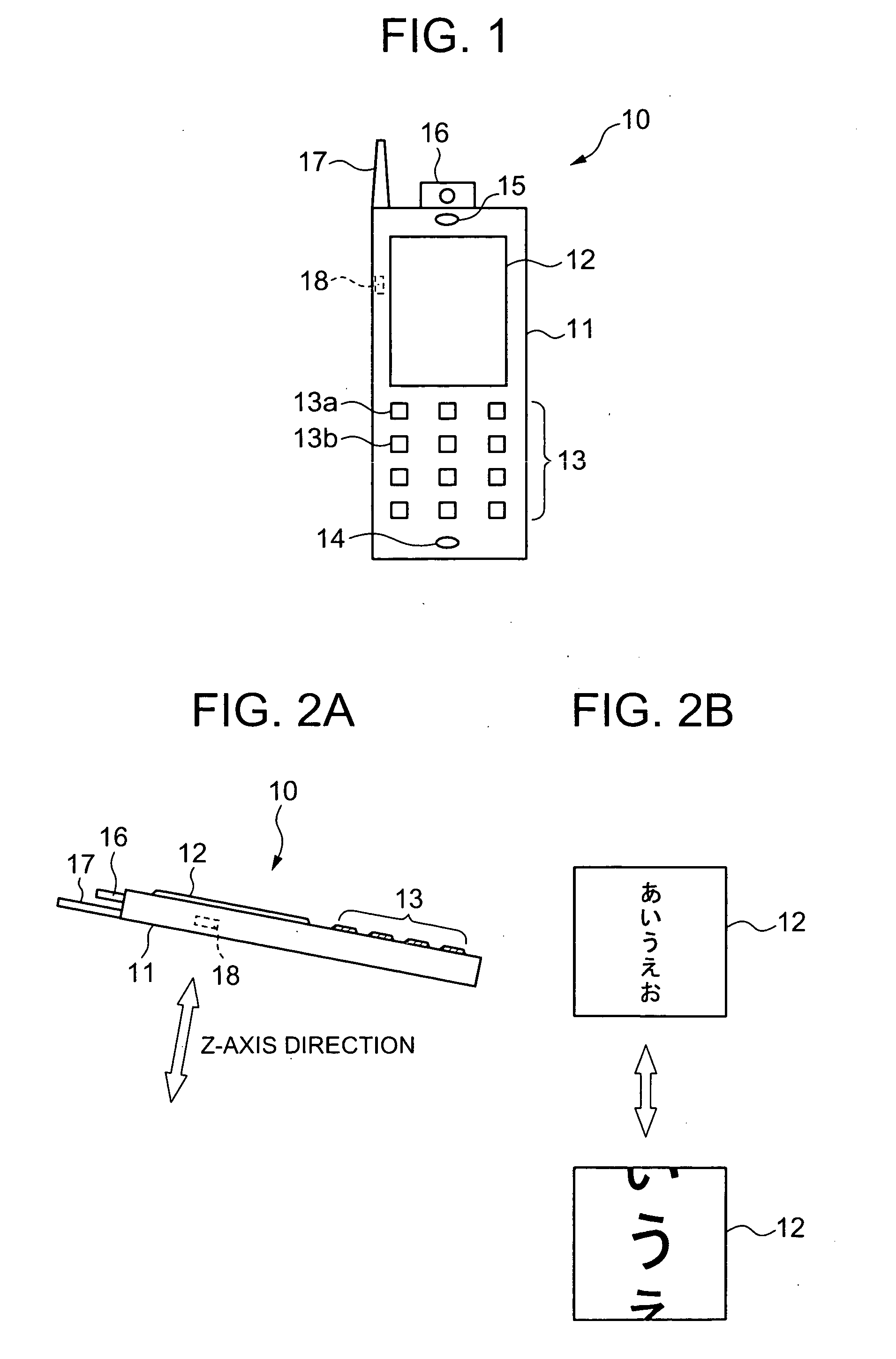
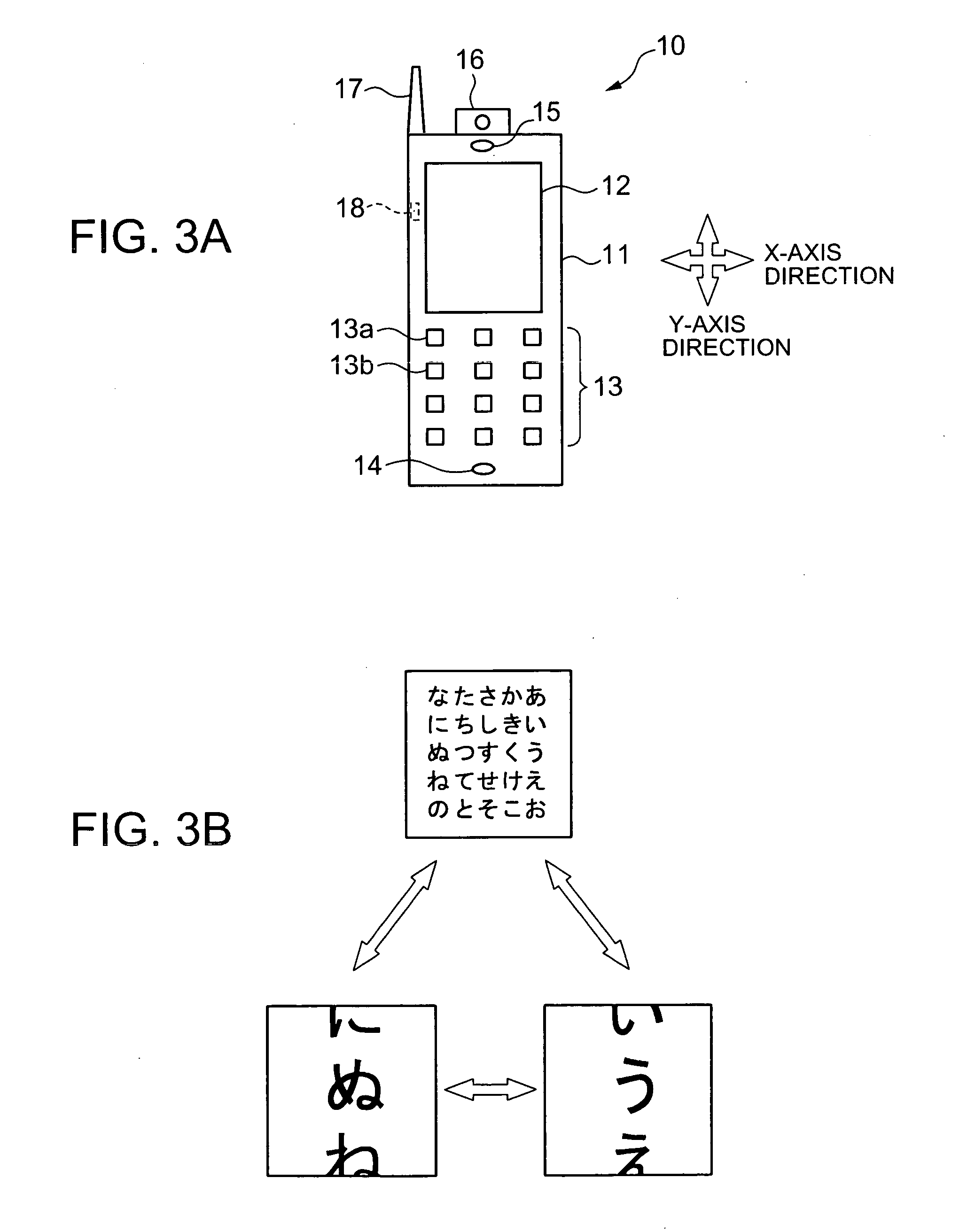
Method arranging user interface objects in touch screen portable terminal and apparatus thereof
ActiveUS20130111384A1Easily touch-selectableDigital data processing detailsInput/output processes for data processingTouchscreenUser interface
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for reducing network latency in data communication
InactiveUS7370120B2Data processing applicationsDigital data processing detailsContent distributionData compression
Owner:PROPEL SOFTWARE
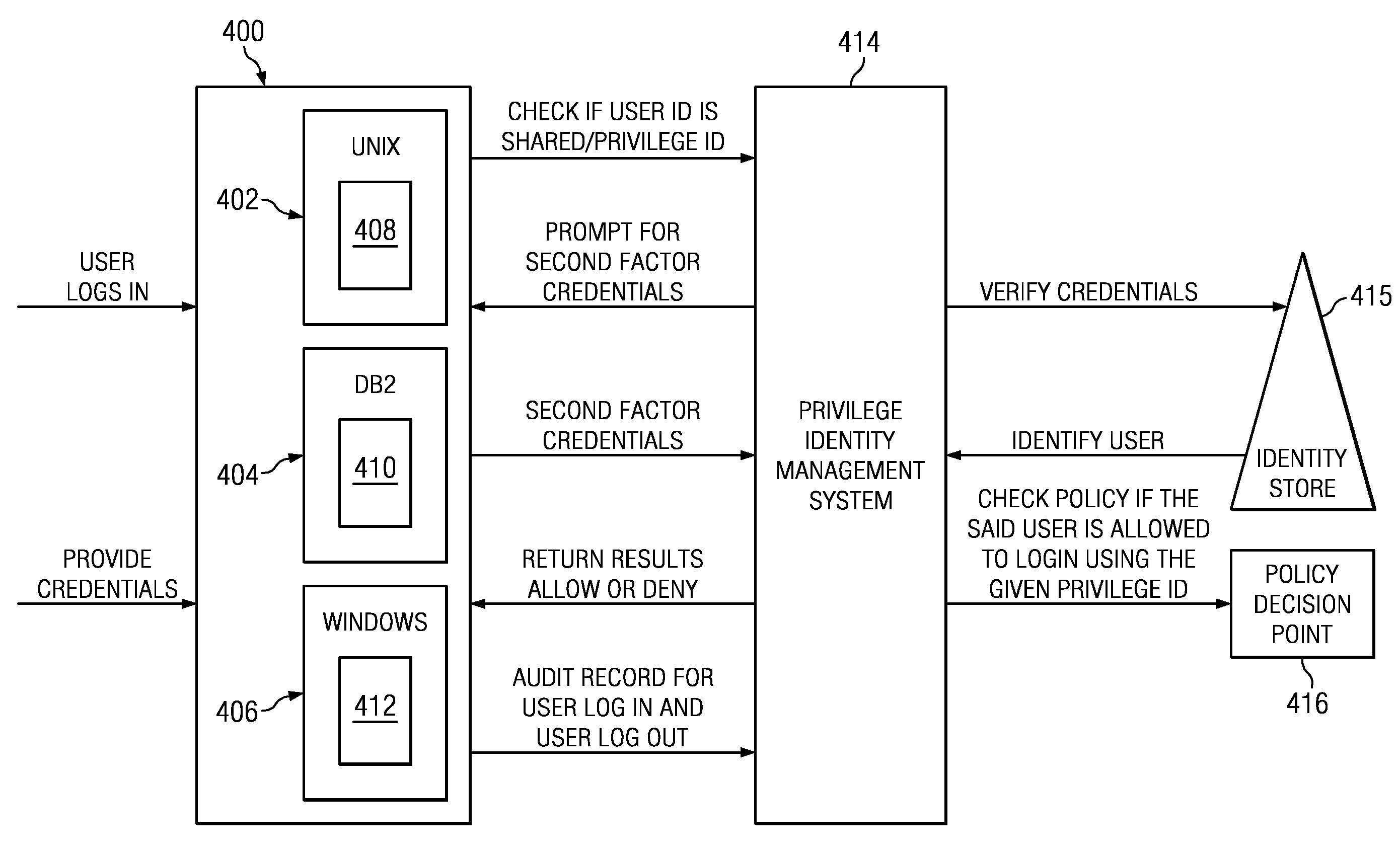
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
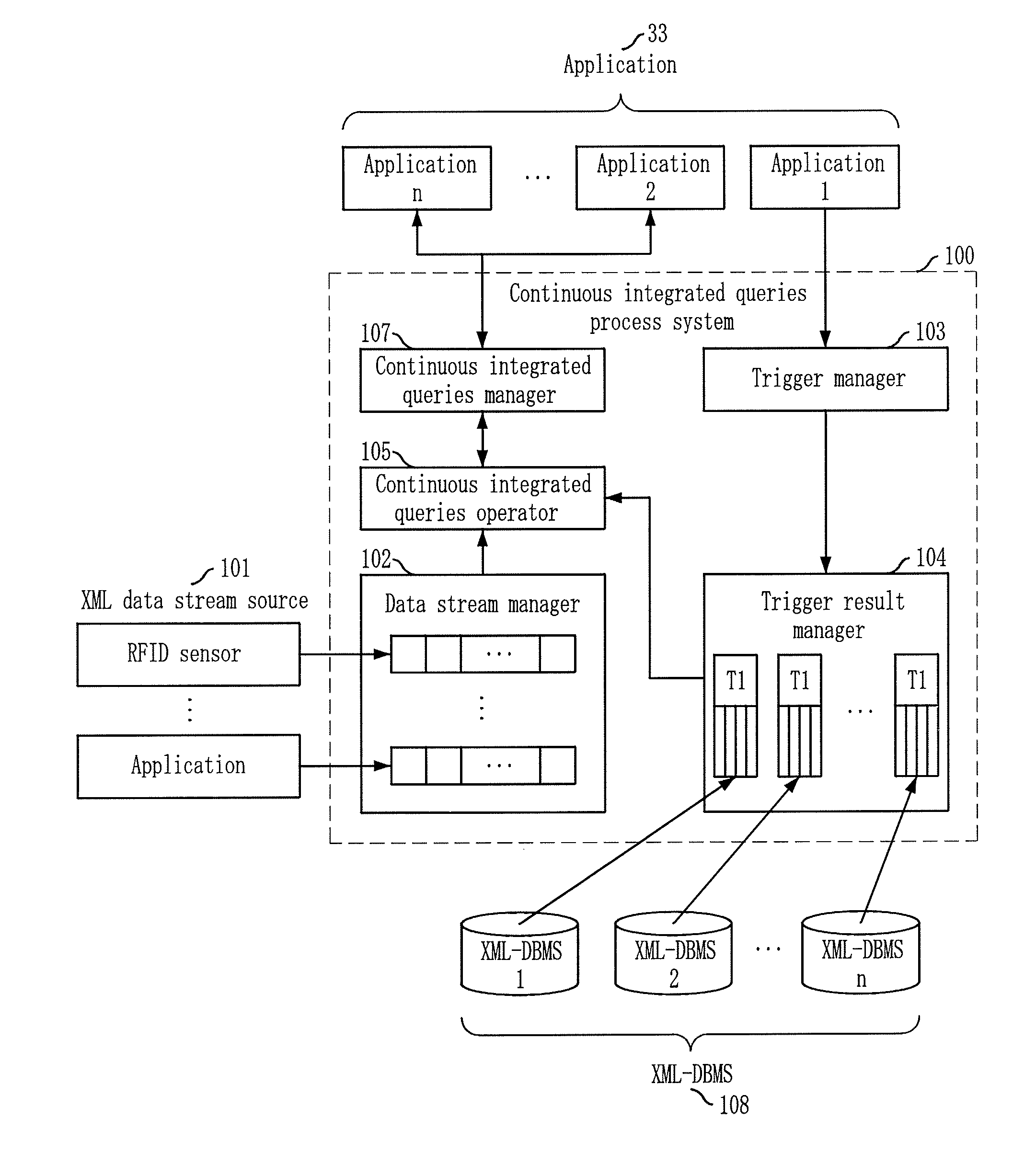
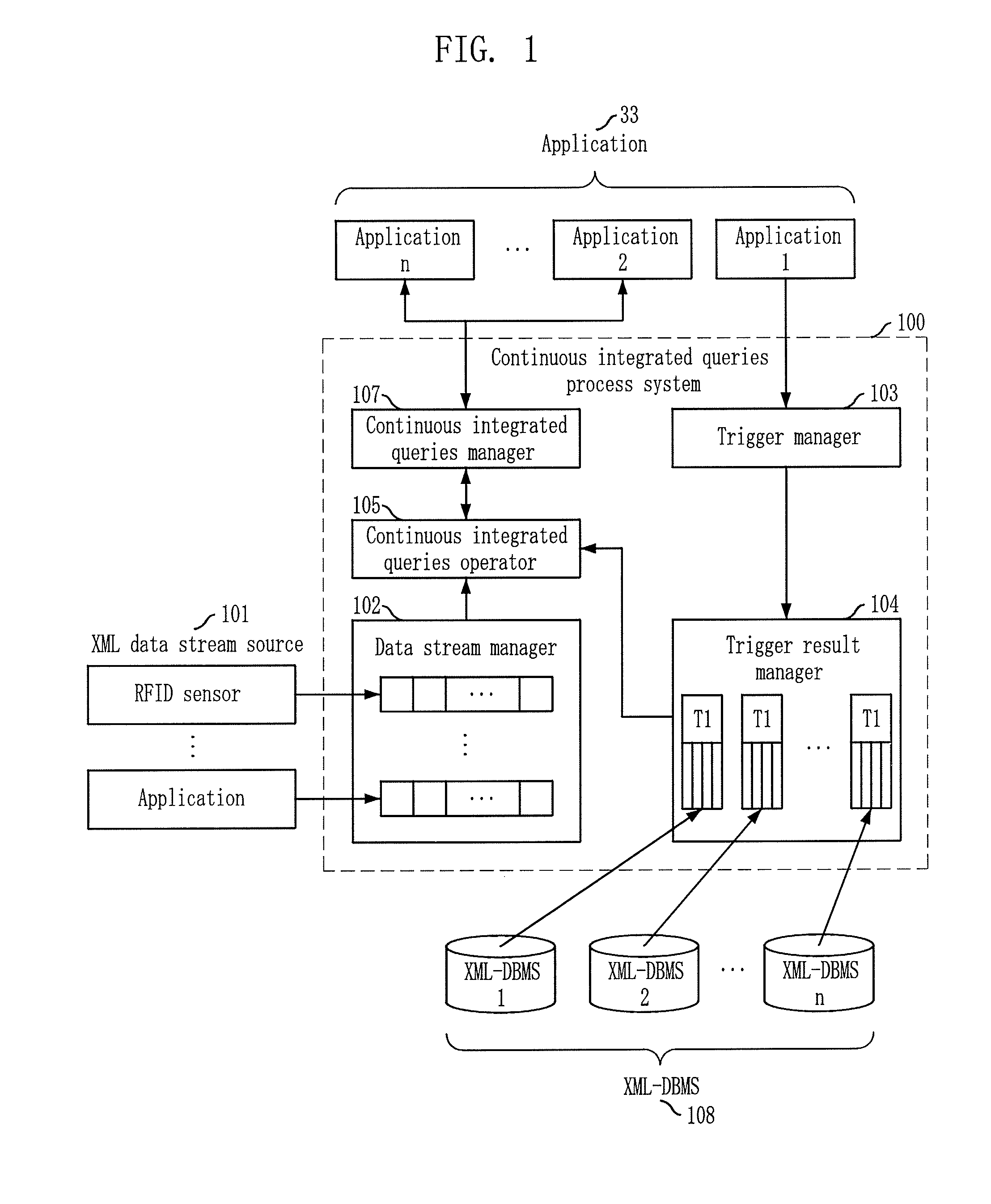
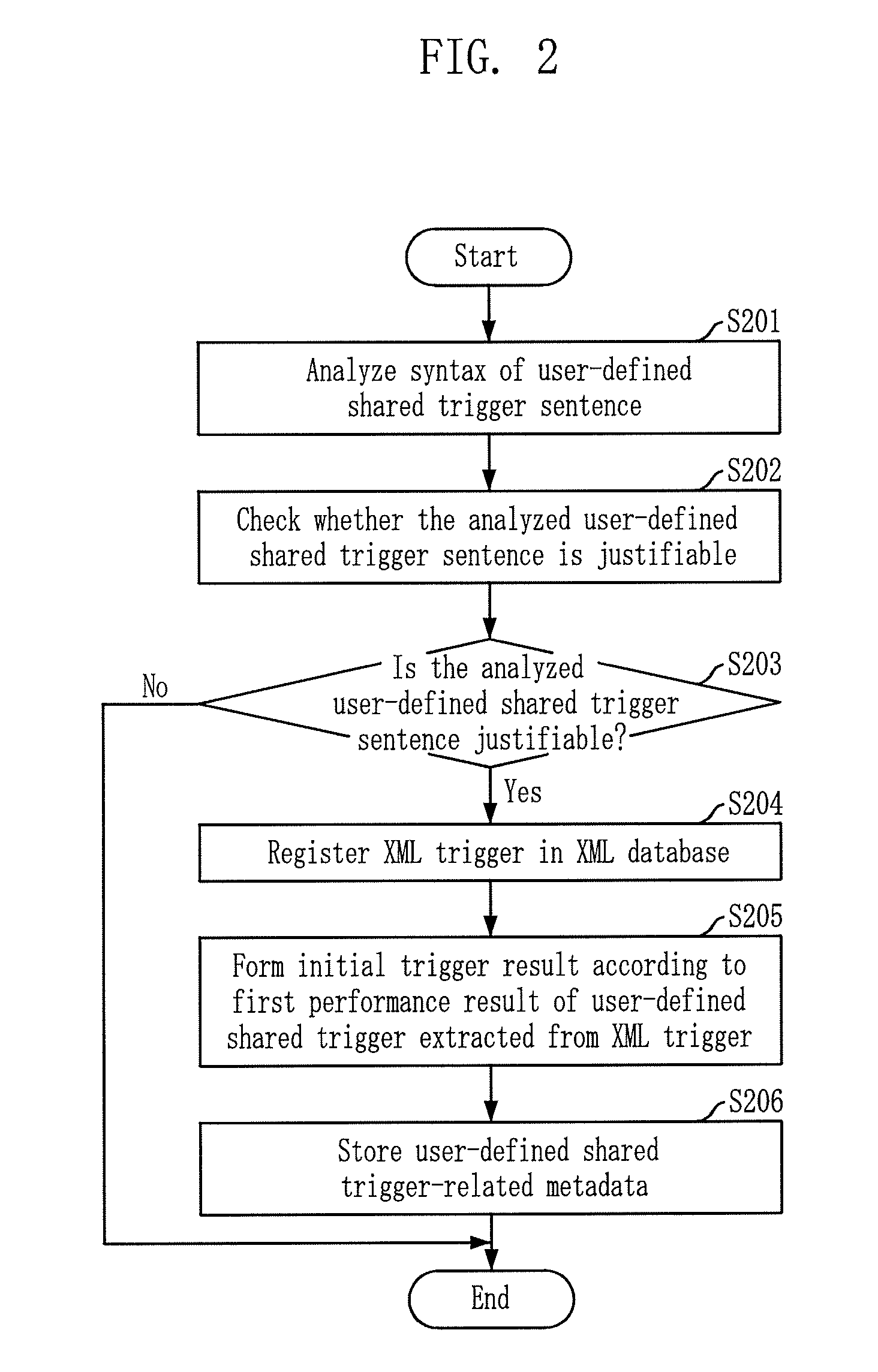
System and method for processing continuous integrated queries on both data stream and stored data using user-defined share trigger
InactiveUS20080046401A1Improve performanceDigital data information retrievalDigital data processing detailsExternal applicationData stream
Owner:ELECTRONICS & TELECOMM RES INST
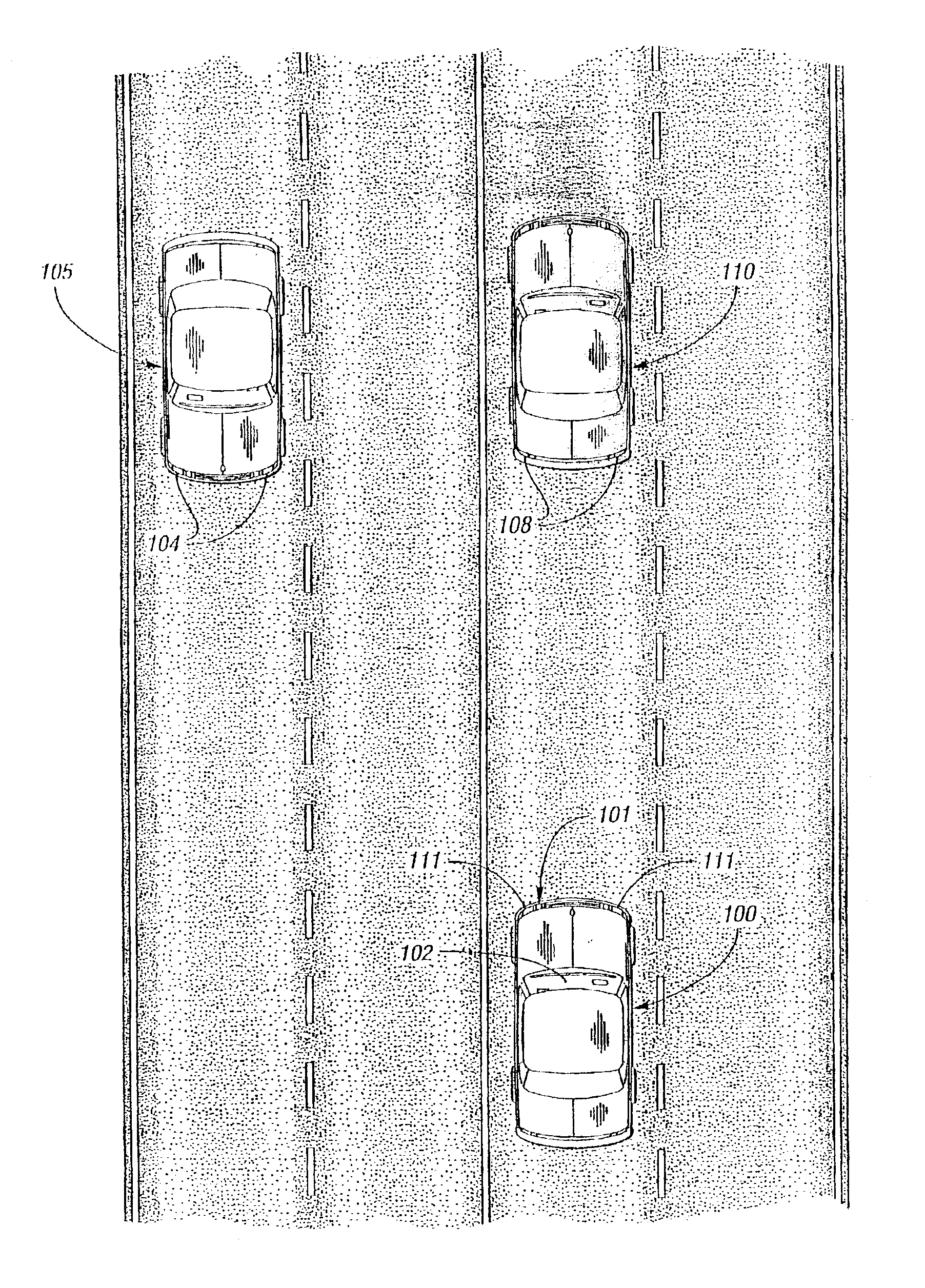
Jackknife Condition for Backing up of a Vehicle Attached to a Long Wheelbase Dual Axle Trailers
A jackknife warning condition controller and control method notifies a driver of a potential jackknife situation while backing up a vehicle with an attached trailer. The vehicle has a front axle with steerable front wheels controlled by the driver and a rear axle with non-steerable rear wheels. The trailer has a front axle with non-steerable front wheels and a rear axle with steerable rear wheels controlled by a trailer steering controller. The jackknife controller receives an operator-controlled vehicle steering angle and a measured hitch angle. The jackknife warning condition controller determines a directional jackknife warning condition and compares the measured hitch angle with the determined directional jackknife warning condition. If the measured hitch angle satisfies the directional jackknife warning condition then a notification is sent to the driver.
Owner:HONDA MOTOR CO LTD
Internal combustion engine control for improved fuel efficiency
ActiveUS20100006065A1Undesirable vibration reductionImprove efficiencyAnalogue computers for vehiclesElectrical controlWork cycleFuel efficiency
A variety of methods and arrangements for improving the fuel efficiency of internal combustion engines are described. Generally, an engine is controlled to operate in a skip fire variable displacement mode. Feedback control is used to dynamically determine the working cycles to be skipped to provide a desired engine output. In some embodiments a substantially optimized amount of air and fuel is delivered to the working chambers during active working cycles so that the fired working chambers can operate at efficiencies close to their optimal efficiency. In some embodiments, the appropriate firing pattern is determined at least in part using predictive adaptive control. By way of example, sigma delta controllers work well for this purpose. In some implementations, the feedback includes feedback indicative of at least one of actual and requested working cycle firings. In some embodiments, the appropriate firings are determined on a firing opportunity by firing opportunity basis. Additionally, in some embodiments, an indicia of the current rotational speed of the engine is used as a clock input for a controller used to selectively cause the skipped working cycles to be skipped.
Owner:TULA TECH INC
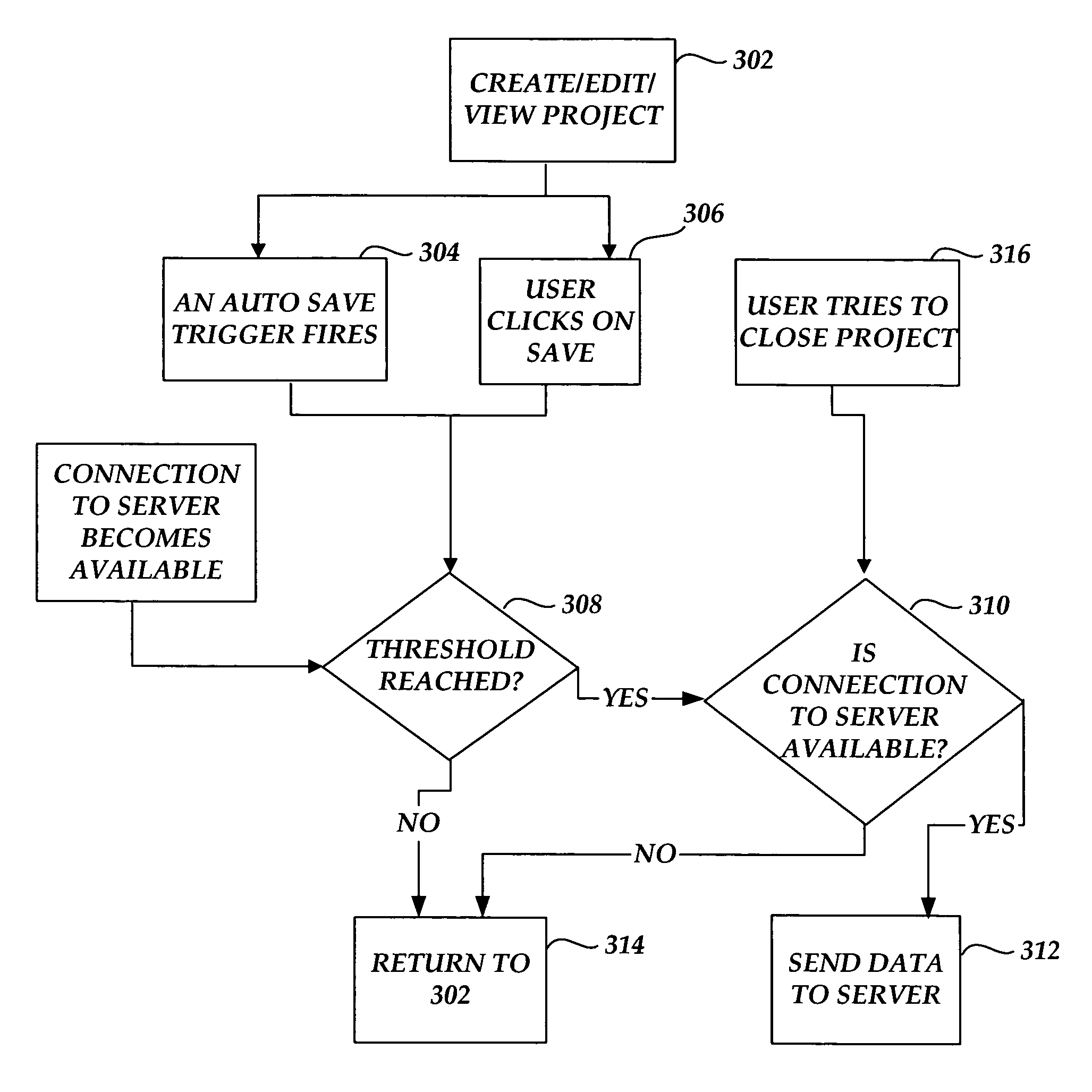
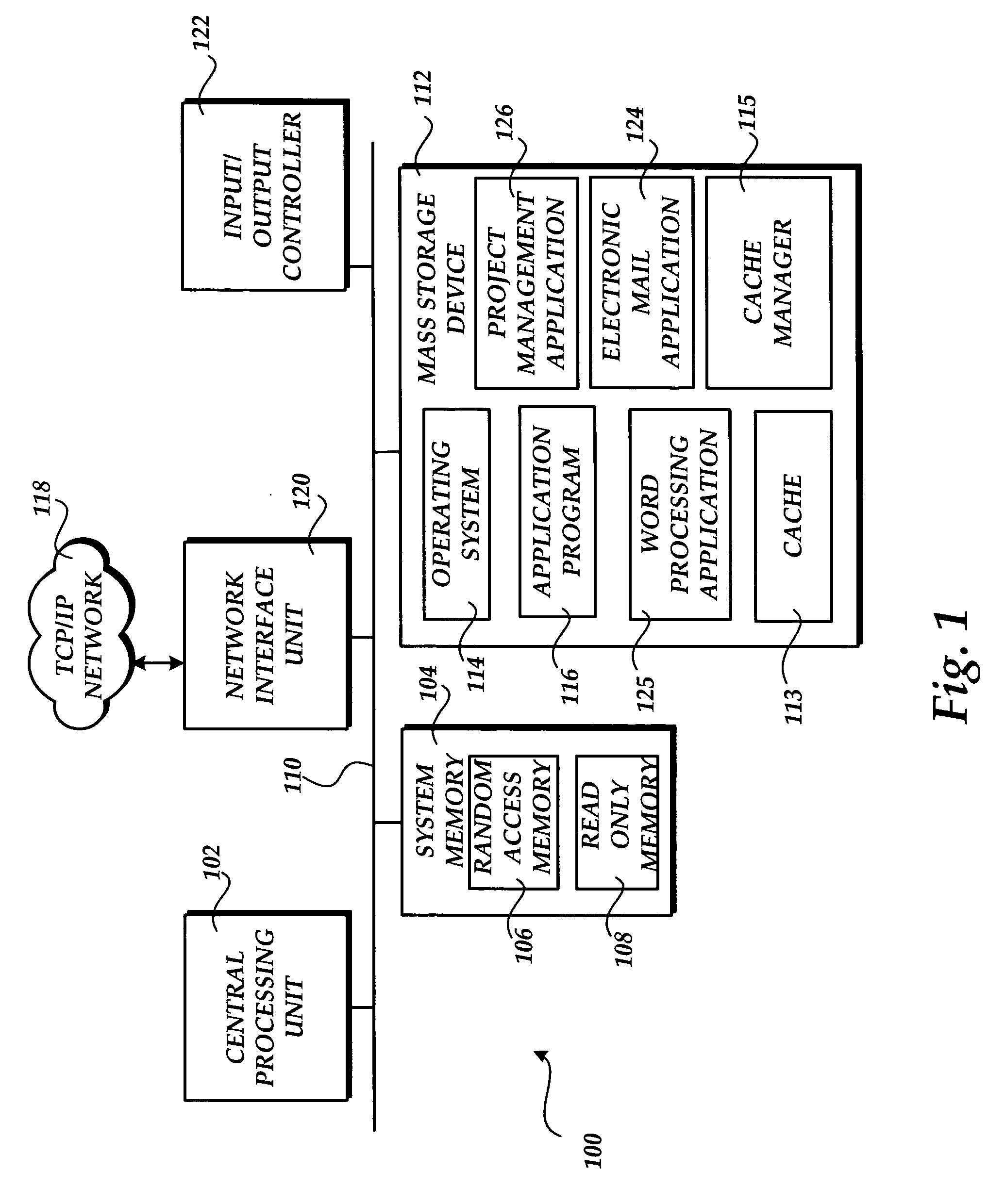
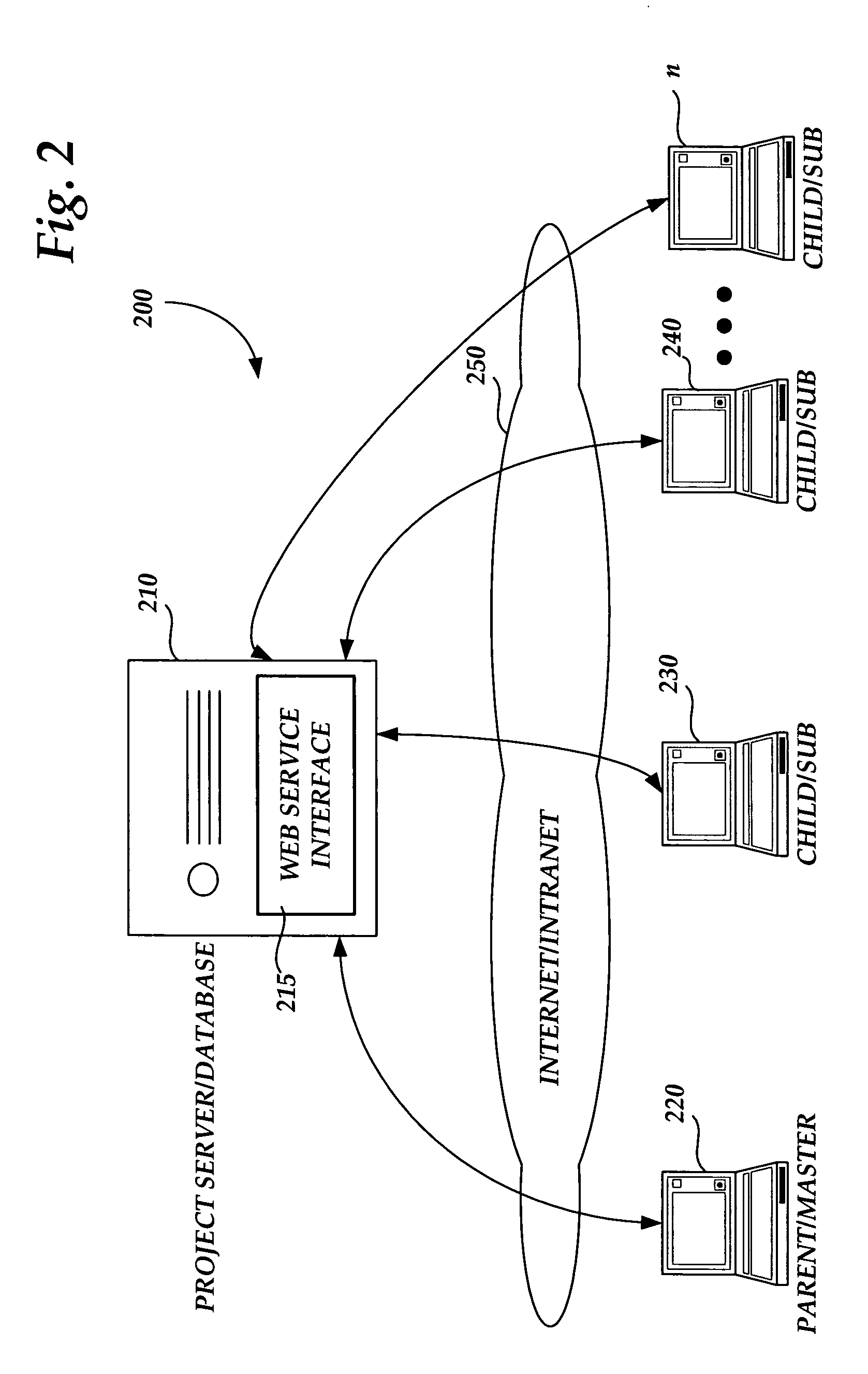
Methods and systems for caching and synchronizing project data
Methods and systems are provided for intelligently managing project data in a project management application. According to various aspects of the invention, project management data may be loaded and saved to a local cache of a client computer, such as a hard disk cache. The invention also provides a mechanism for reducing the size of data downloaded from and sent to a project server during load and save times.
Owner:MICROSOFT TECH LICENSING LLC
Electronic appliance having magnifying-glass display function, display controlling method, and display control program
ActiveUS20050001815A1Digital data processing detailsCathode-ray tube indicatorsComputer graphics (images)Magnifying glass
Owner:CASIO COMPUTER CO LTD
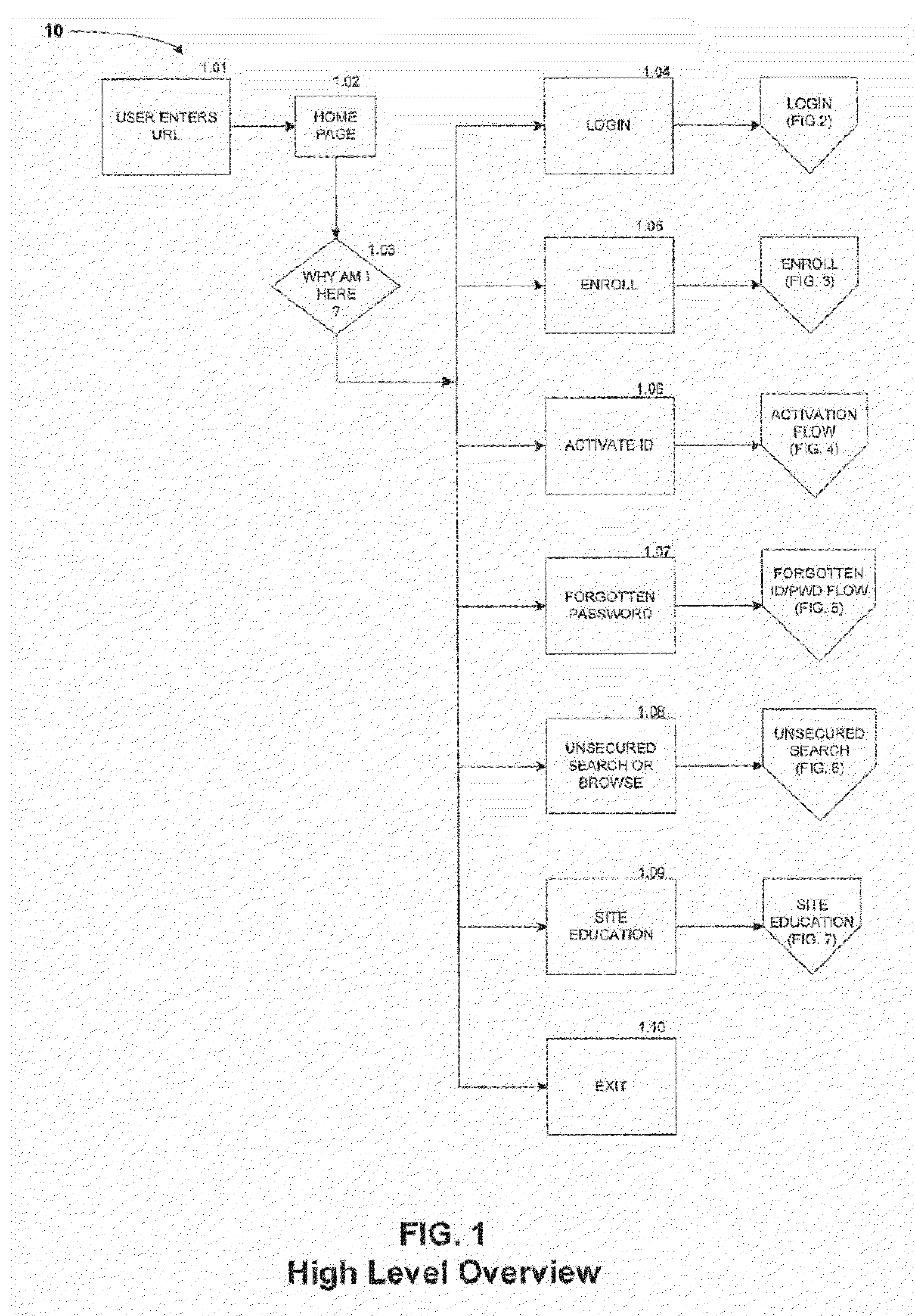
Online System for Communications Between Service Providers and Consumers
InactiveUS20100125803A1Input/output for user-computer interactionDigital data processing detailsElectronic marketsService provider
Owner:HUNT4SERVICES
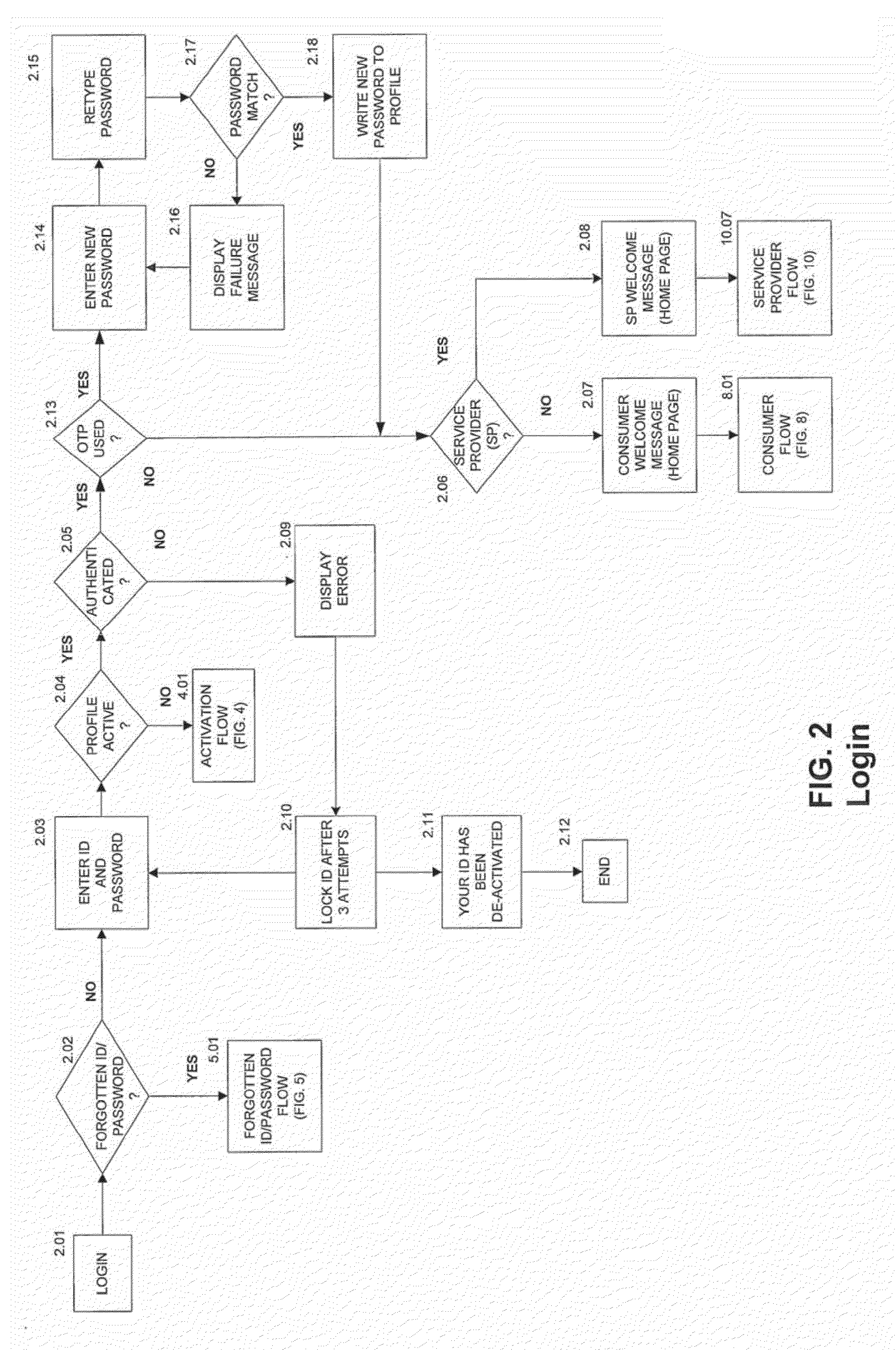
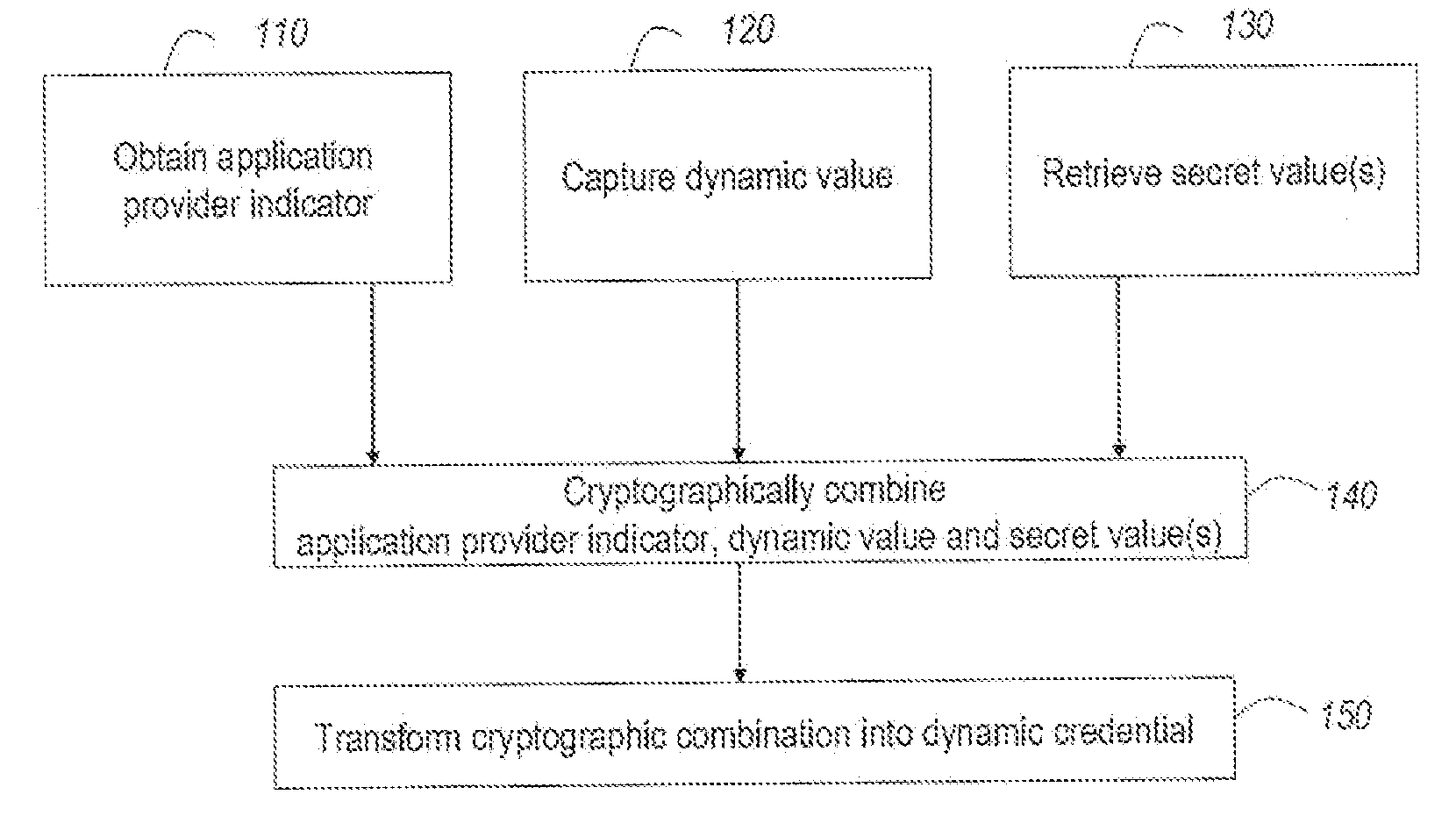
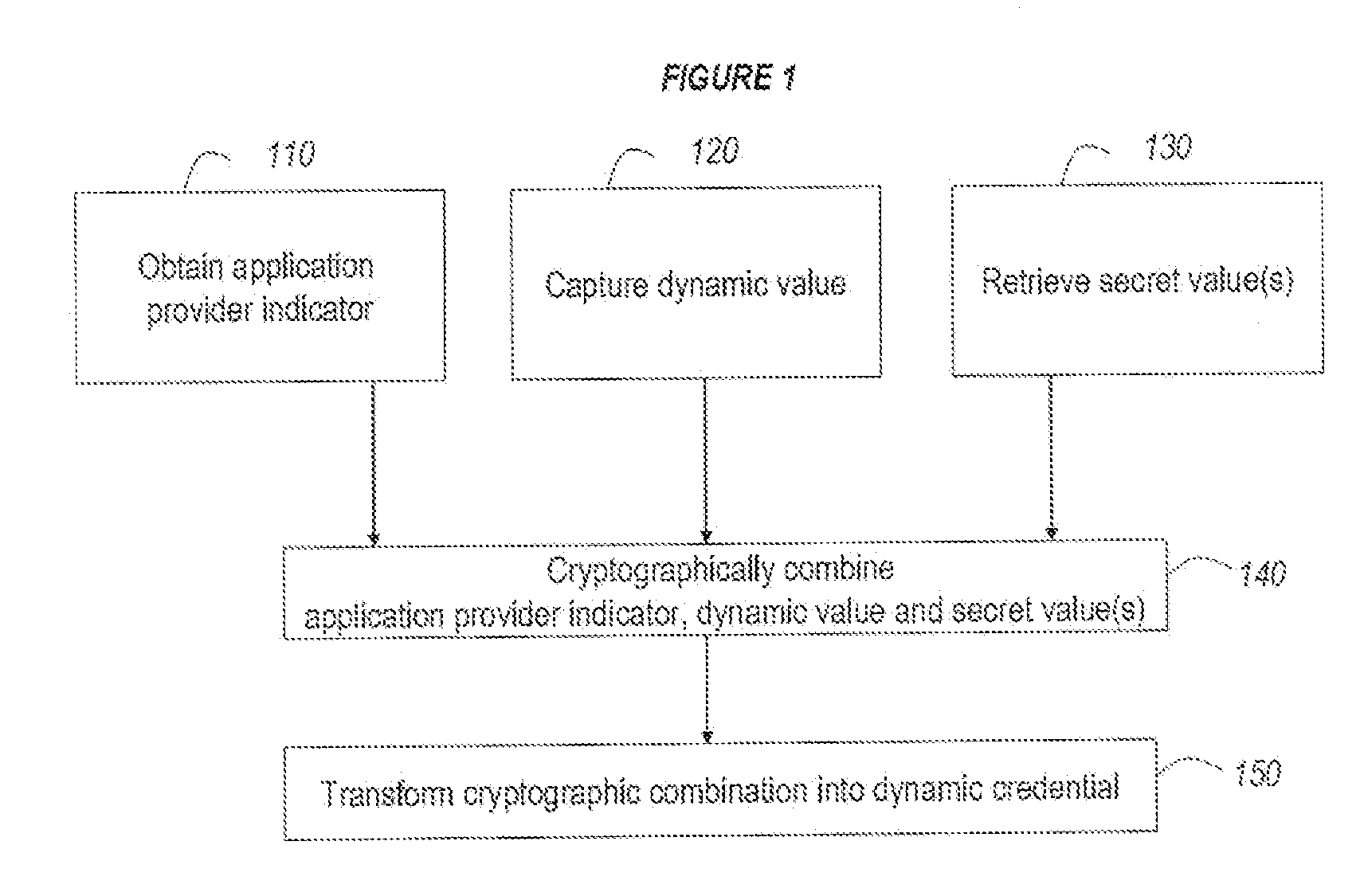
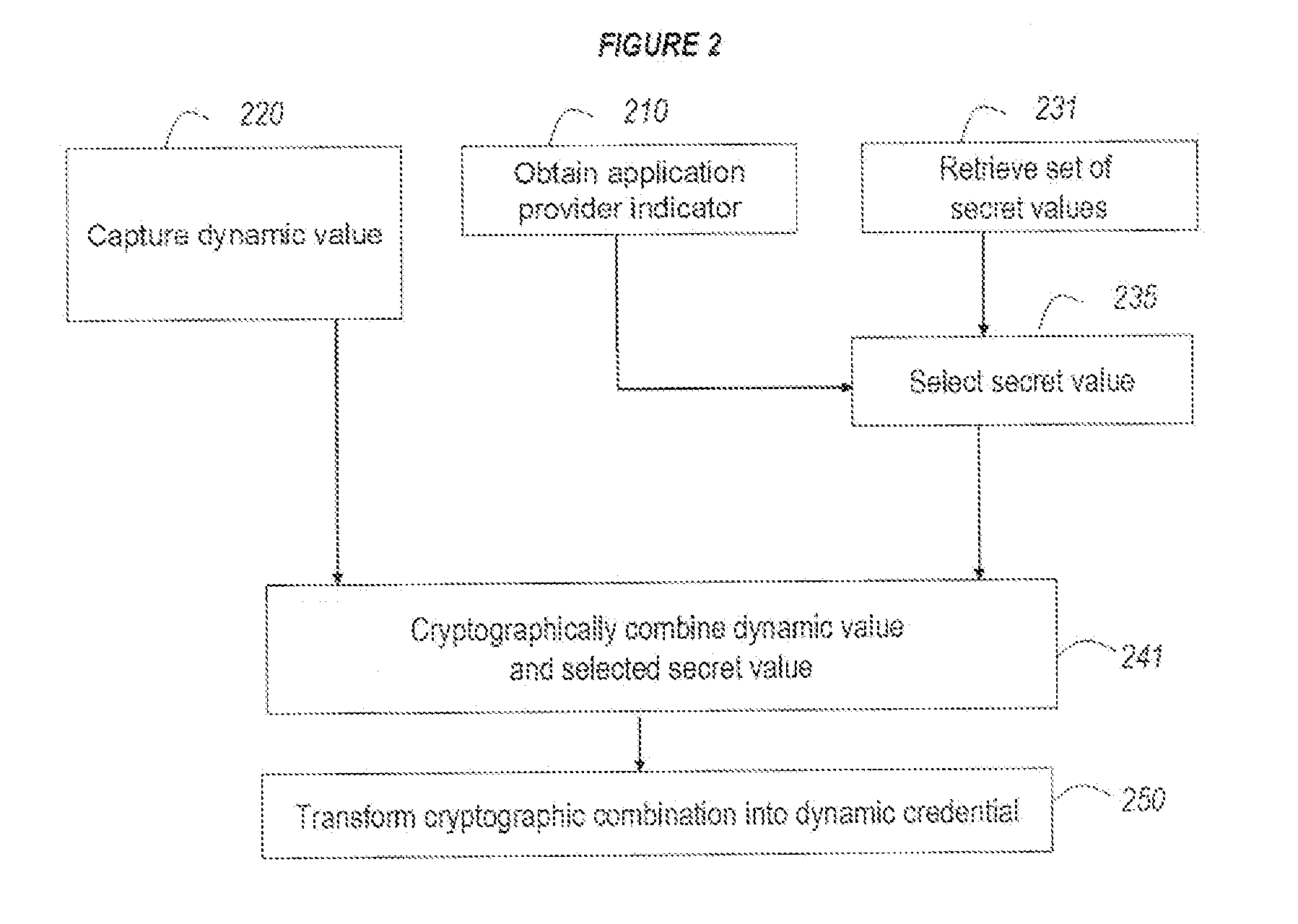
Strong authentication token usable with a plurality of independent application providers
ActiveUS20110099384A1Low costCost can be dividedMultiple keys/algorithms usageDigital data processing detailsPersonalizationUnique identifier
Owner:ONESPAN NORTH AMERICA INC
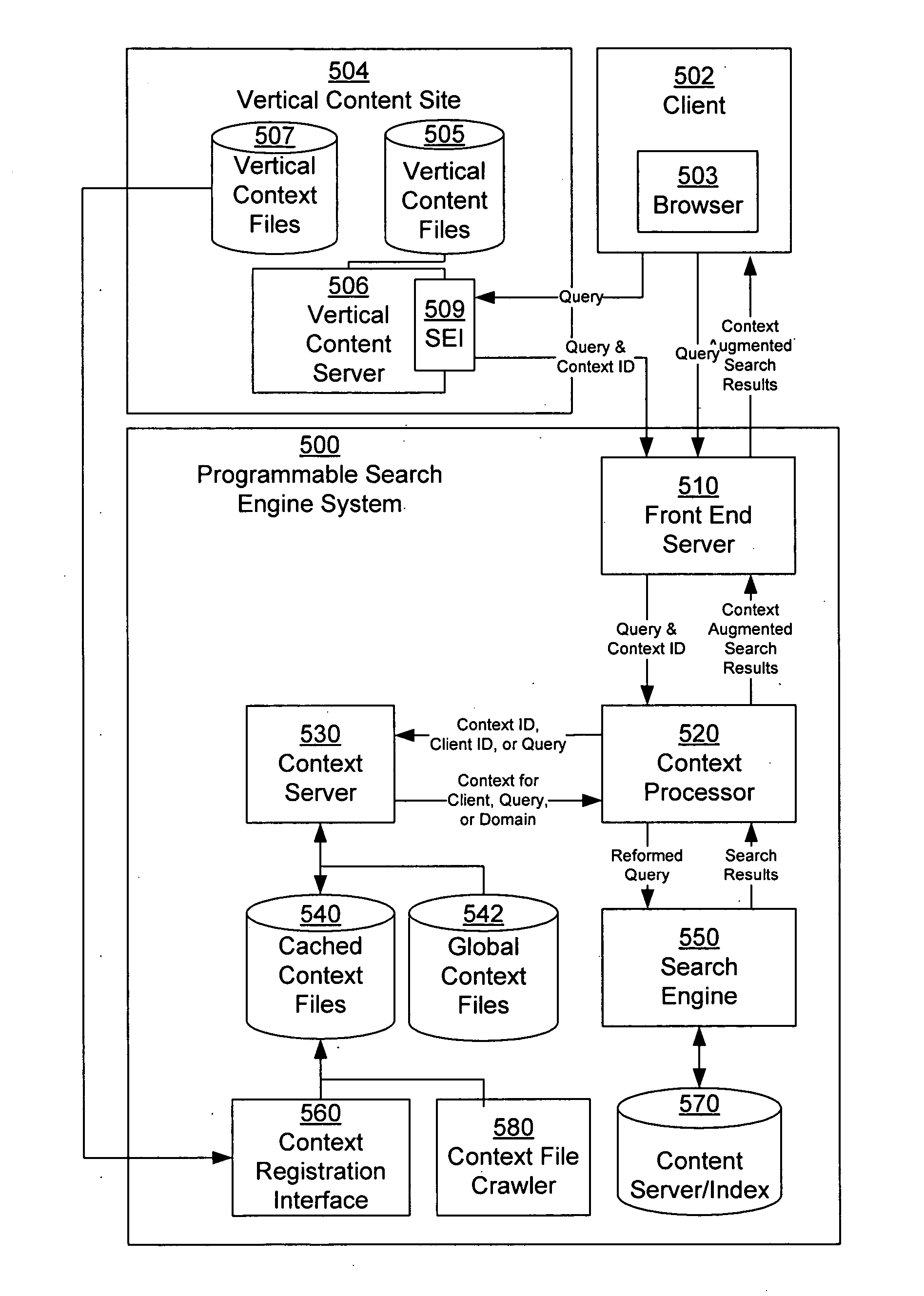
Detecting spam related and biased contexts for programmable search engines
ActiveUS20070038600A1Quality improvementWeb data indexingDigital data processing detailsClient-sideTime processing
Owner:GOOGLE LLC
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap