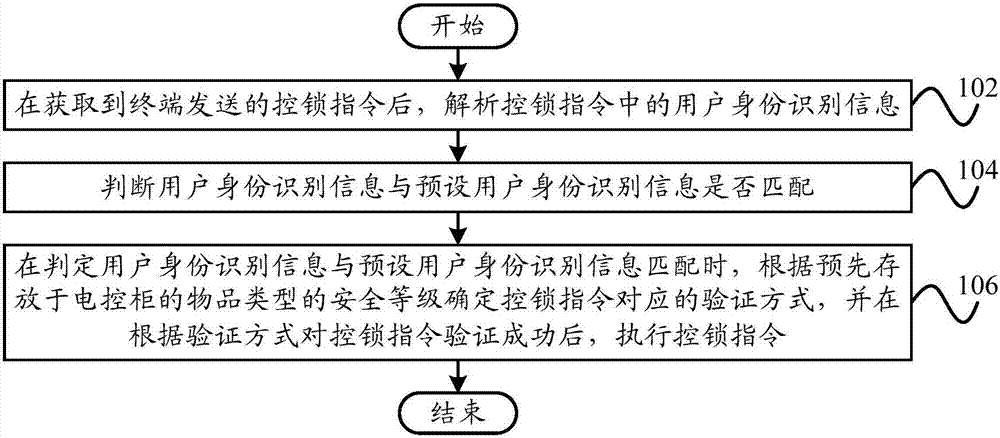
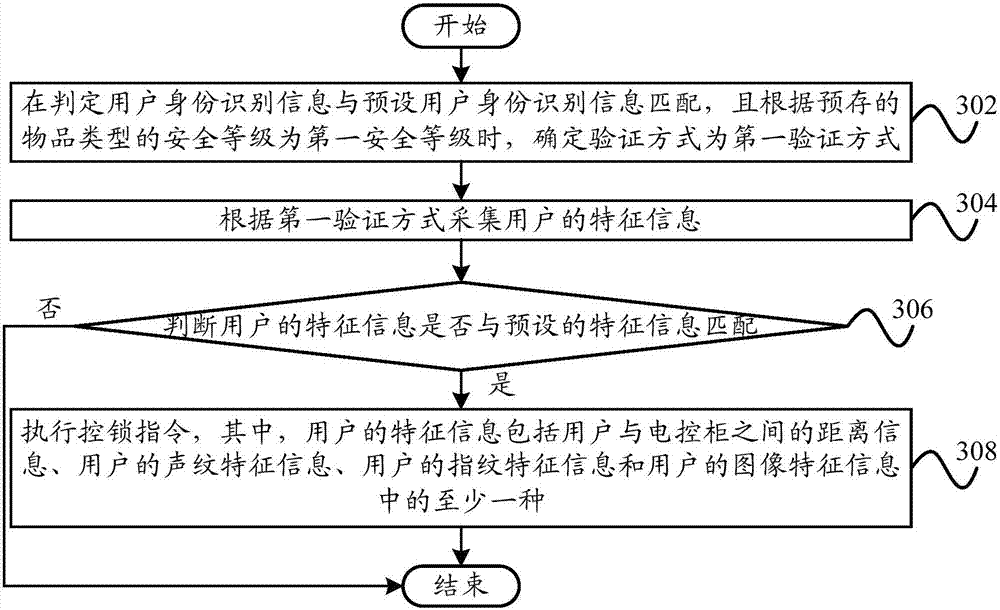
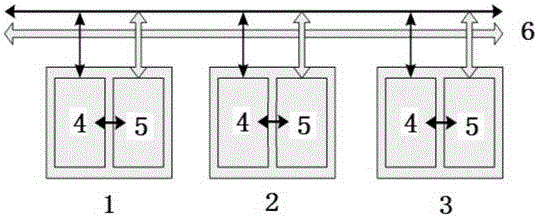
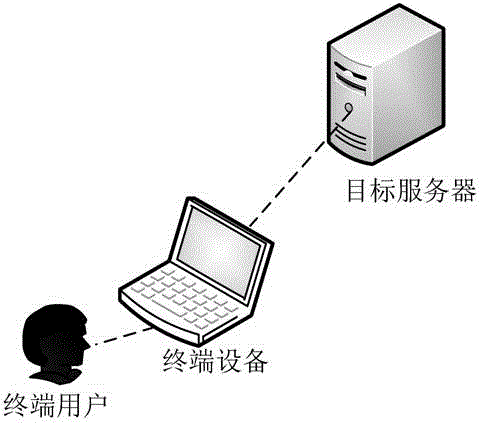
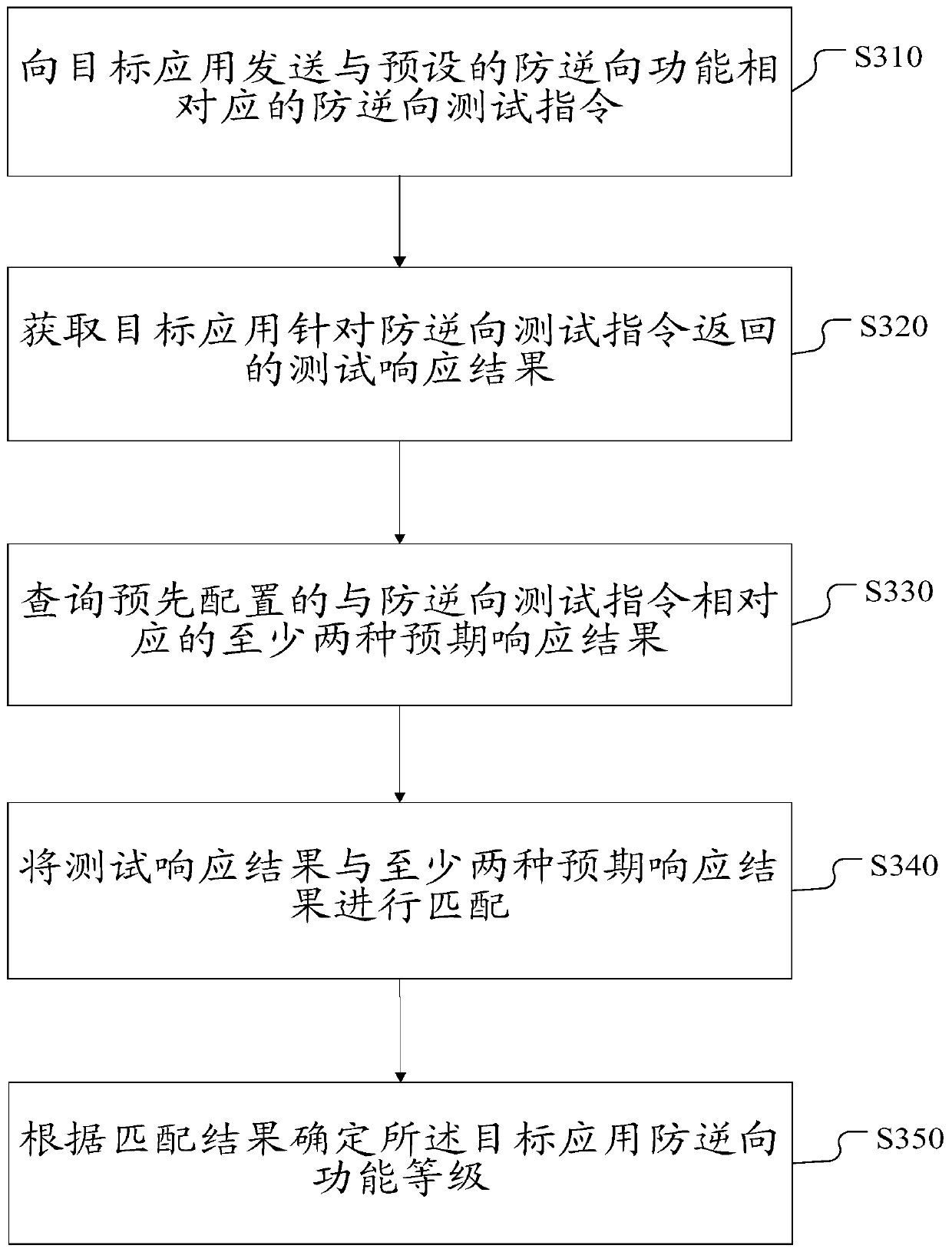
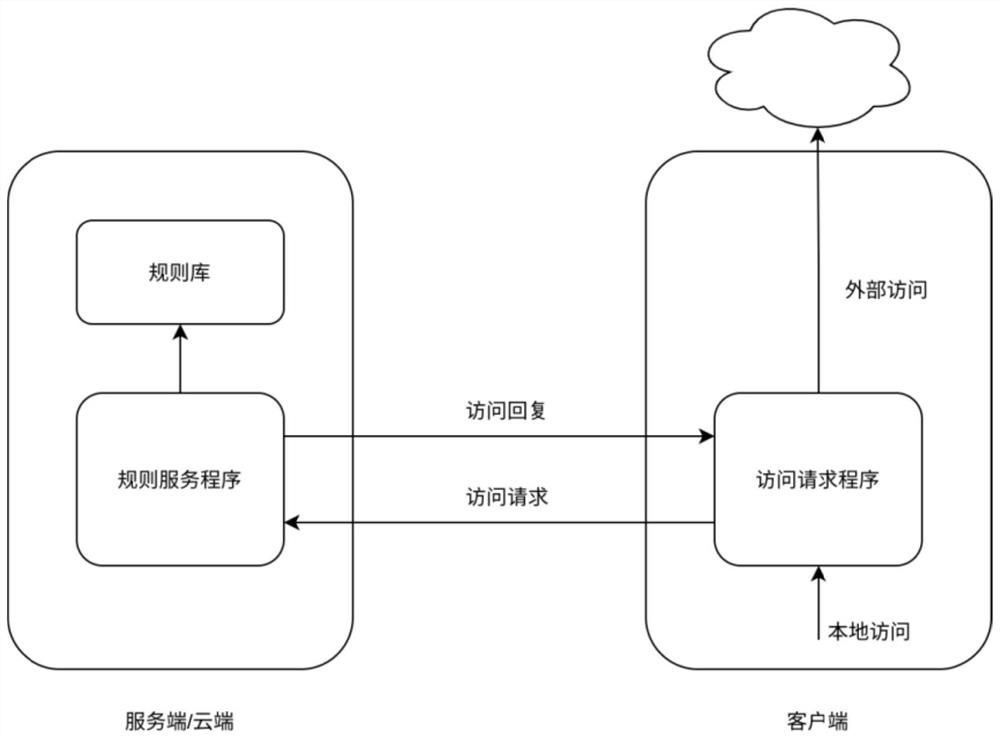
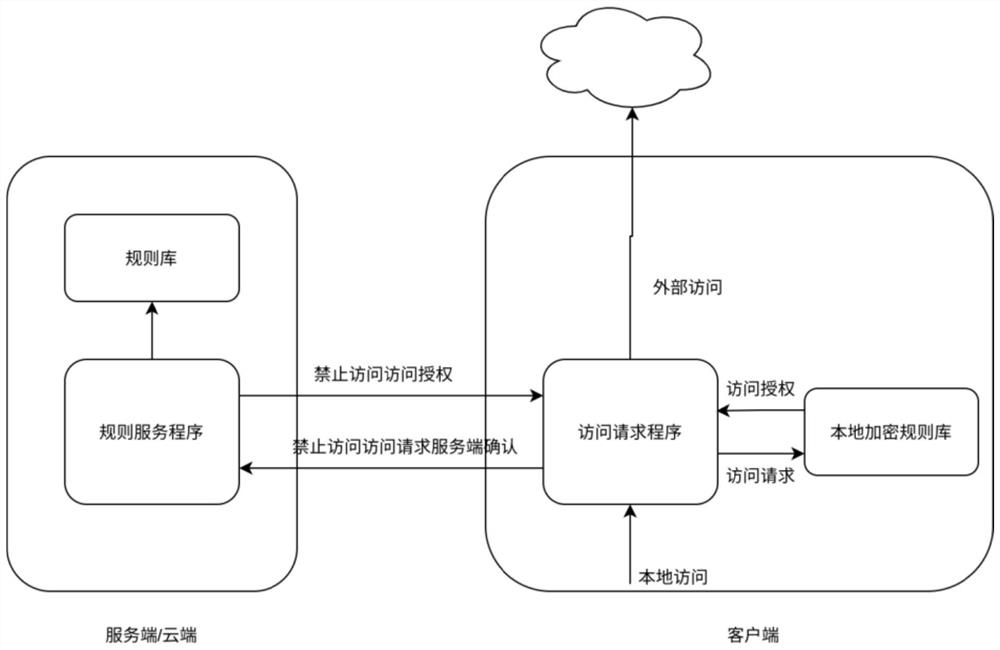
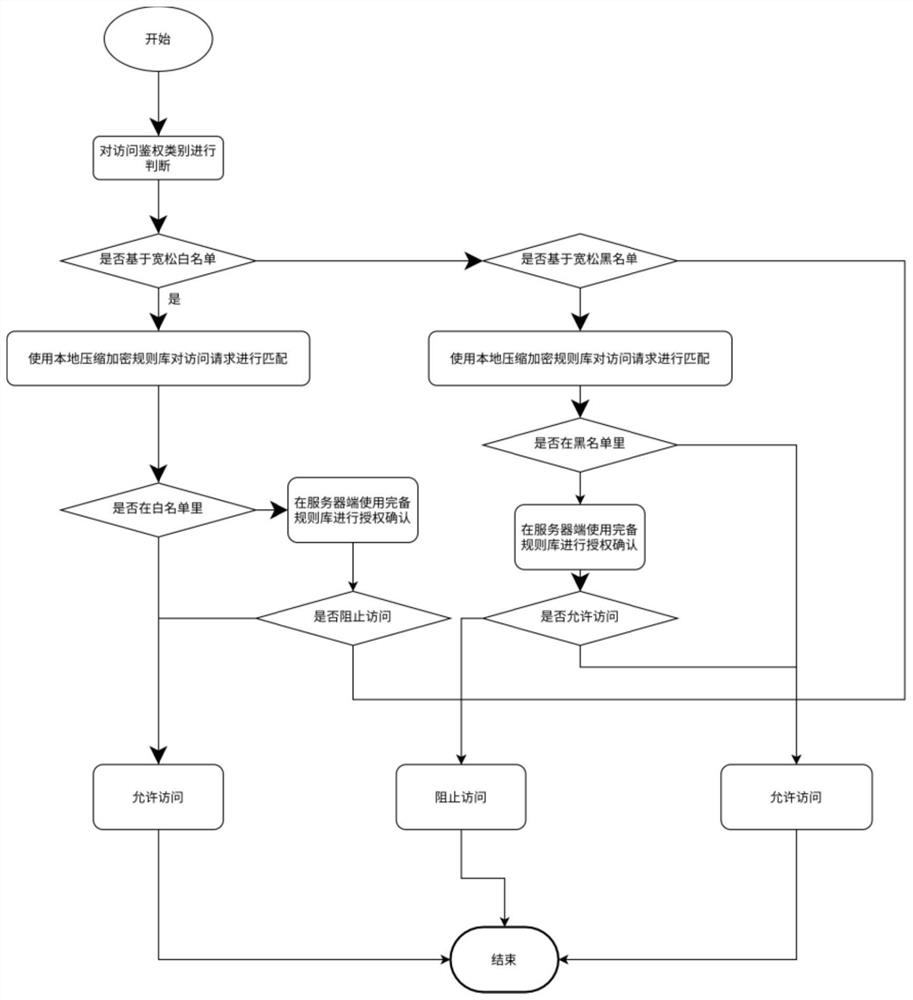
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
7 results about "Security level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, security level is a measure of the strength that a cryptographic primitive — such as a cipher or hash function — achieves. Security level is usually expressed in "bits", where n-bit security means that the attacker would have to perform 2 operations to break it, but other methods have been proposed that more closely model the costs for an attacker. This allows for convenient comparison between algorithms and is useful when combining multiple primitives in a hybrid cryptosystem, so there is no clear weakest link. For example, AES-128 (key size 128 bits) is designed to offer a 128-bit security level, which is considered roughly equivalent to 3072-bit RSA.
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
Closed loop type network security supervision method and system for security threat event
ActiveCN109672663AGuaranteed closed-loop processingGuaranteed correct repairTransmissionClosed loopNetwork Access Control
The invention relates to a closed loop type network security supervision method and system for a security threat event. When a security detection module finds the security threat event and needs to notify, a corresponding state tag code is set and recording is carried out; alarm information is generated and sent to an alarm contact; the alarm contact disposes and submits the event state tag code and modifies the event state tag code into a to-be-audited state; a network security supervision mechanism audits to confirm whether the event state tag code is effectively disposed; if no, the networksecurity supervision mechanism continuously notifies to rectify; and events disposed by adopting network access control are directionally tracked, and other effective disposes are completed accordingto flow. According to the invention, the particularity of network security is combined; a closed loop of finding, notification, dispose and tracking management is constructed for the security threatevent; the security threat event is continuously tracked so as to ensure closed-loop dispose and correct repair of the event; process data can be quantized and can be examined; a current situation anda dispose condition of the security threat event of a subordinate supervision mechanism are effectively quantized; network security supervision means are increased; and the network security supervision efficiency and the jurisdiction security level are continuously promoted.
Owner:HANGZHOU DBAPPSECURITY CO LTD
Lock control method and lock control system
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Security-level DCS high-speed redundant bus communication method
InactiveCN106850369AImprove reliabilityEliminate common cause failuresBus networksStructure of Management InformationComputer module
Owner:CHINA NUCLEAR CONTROL SYST ENG
Data transmission method and terminal equipment
Owner:BEIJING QIHOO TECH CO LTD
Security detection method, device and system based on iOS application
InactiveCN110147672ADecompilation/disassemblyPlatform integrity maintainanceData securitySecurity level
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Method for quickly authorizing access at weak client
PendingCN114003935AReduce loadReduce operating costsDigital data protectionEngineeringSecurity level
Owner:浙江连湖科技有限责任公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap