Method for quickly authorizing access at weak client
A technology of authorized access and client, which is applied in the direction of instruments, electronic digital data processing, digital data protection, etc., can solve the problems of poor client user experience and increased cost, and achieve the goal of improving experience, reducing load, and reducing authorization time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention is further described below in conjunction with specific examples. It should be understood that these examples are only used to illustrate the present invention and are not intended to limit the scope of the present invention. In addition, it should be understood that after reading the teachings of the present invention, those skilled in the art can make various changes or modifications to the present invention, and these equivalent forms also fall within the scope defined by the appended claims of the present application.
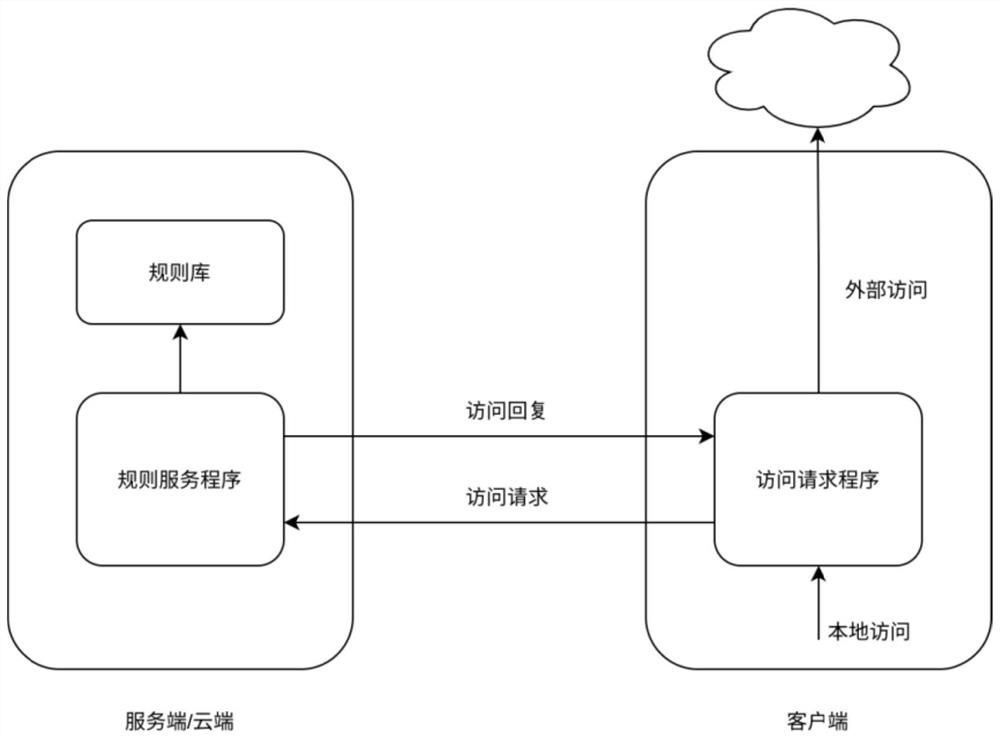
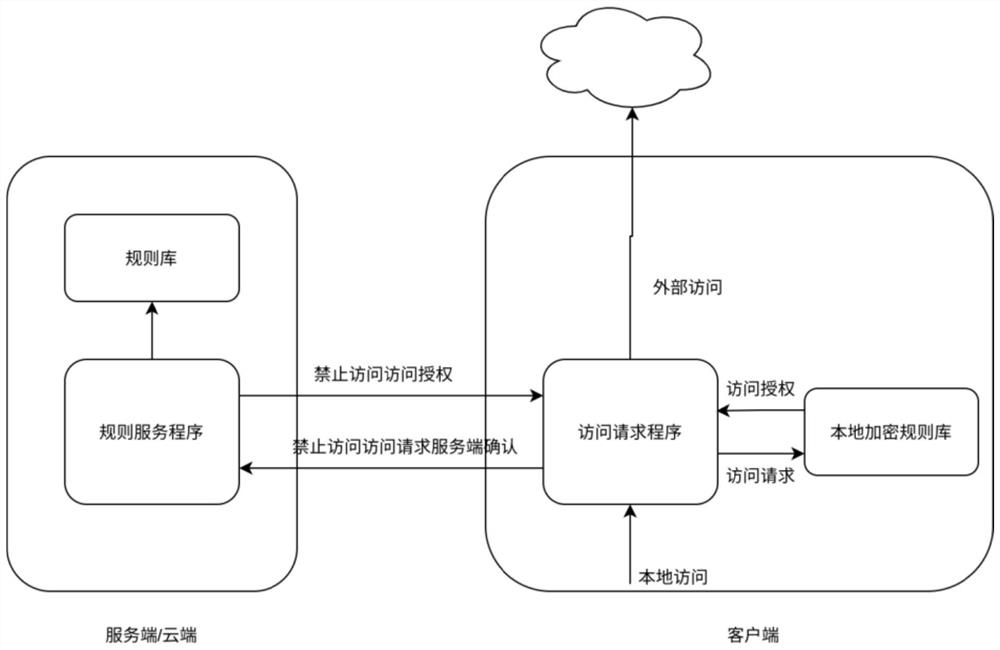
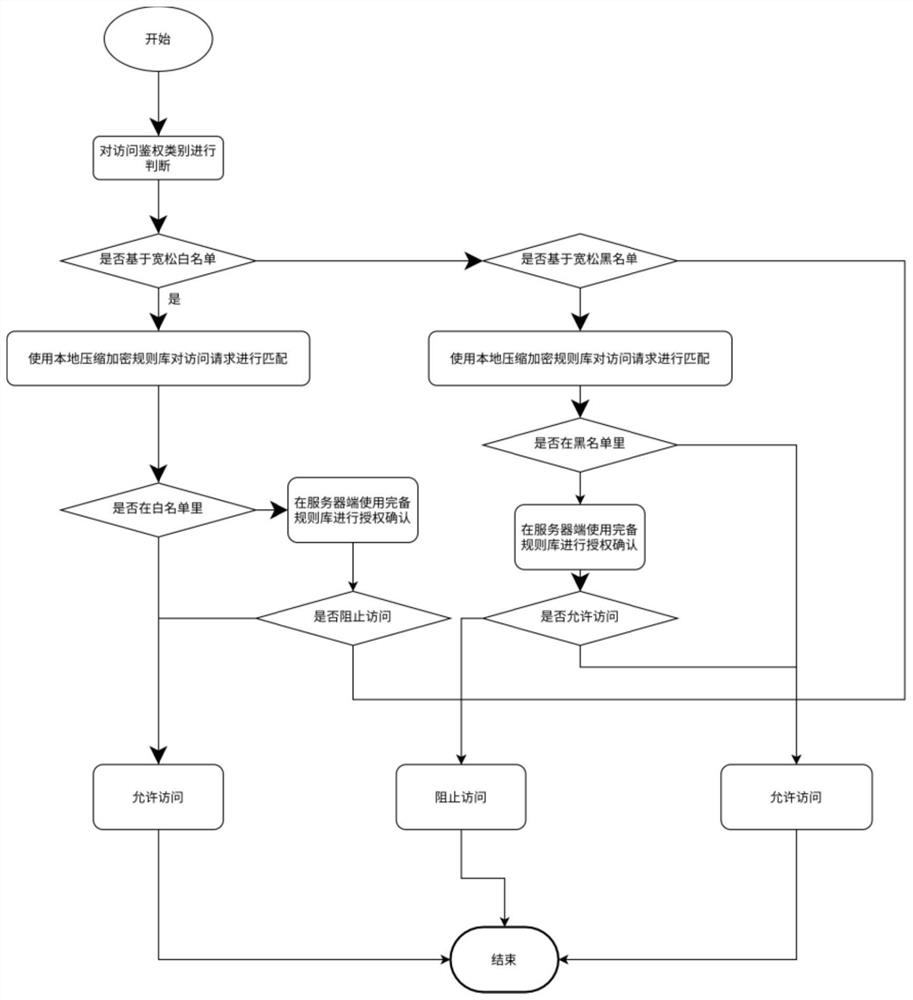
[0024] Such as figure 2 As shown, the method proposed by the present invention adds localized processing on the client side, and reduces the pressure on the server side by increasing the local encryption rule base. After adding the local encryption rule base, according to different security levels:
[0025] In the case of low security level (loose mode), the access request can be processed locally on the client, and the part tha
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap