Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52 results about "Authorization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
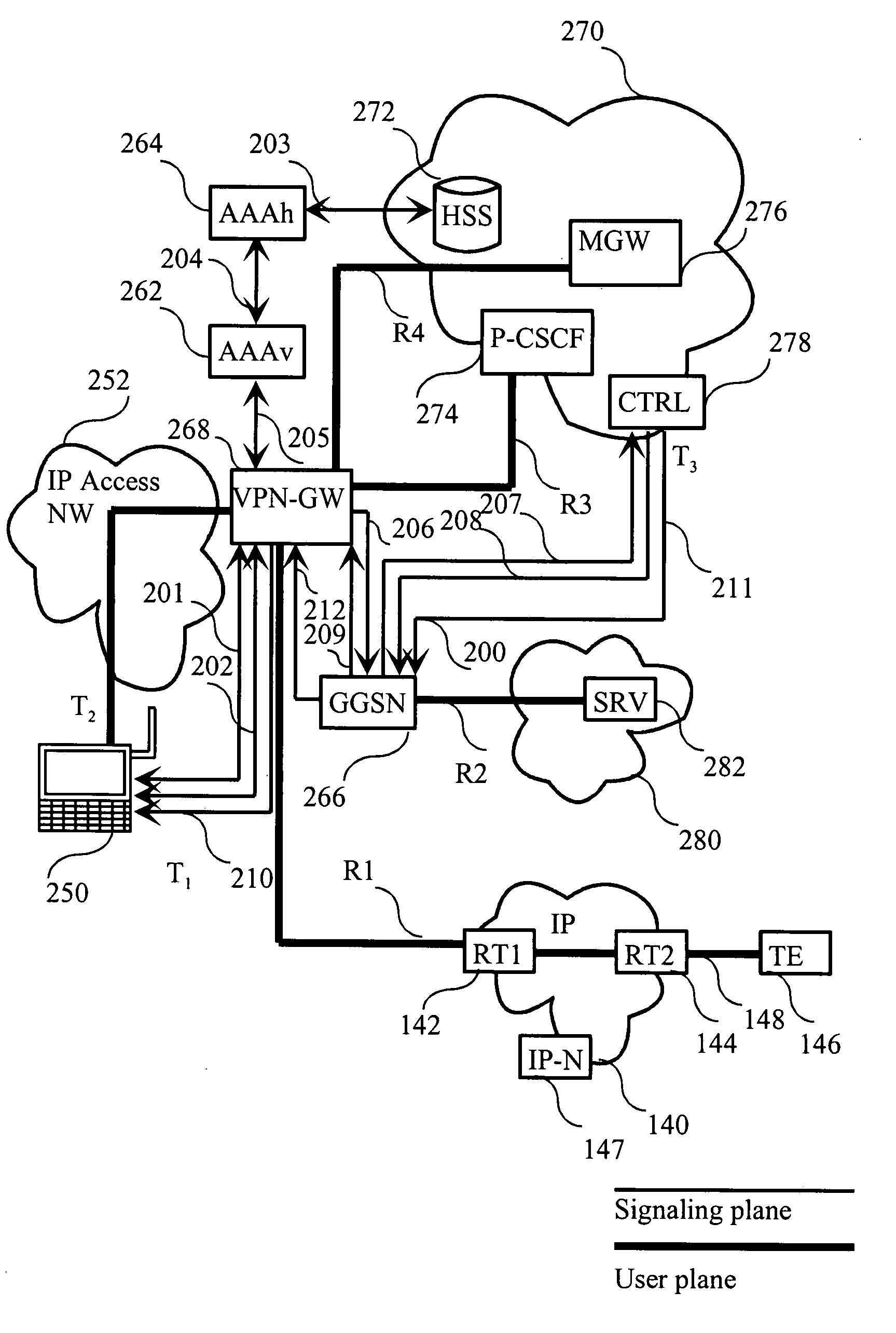
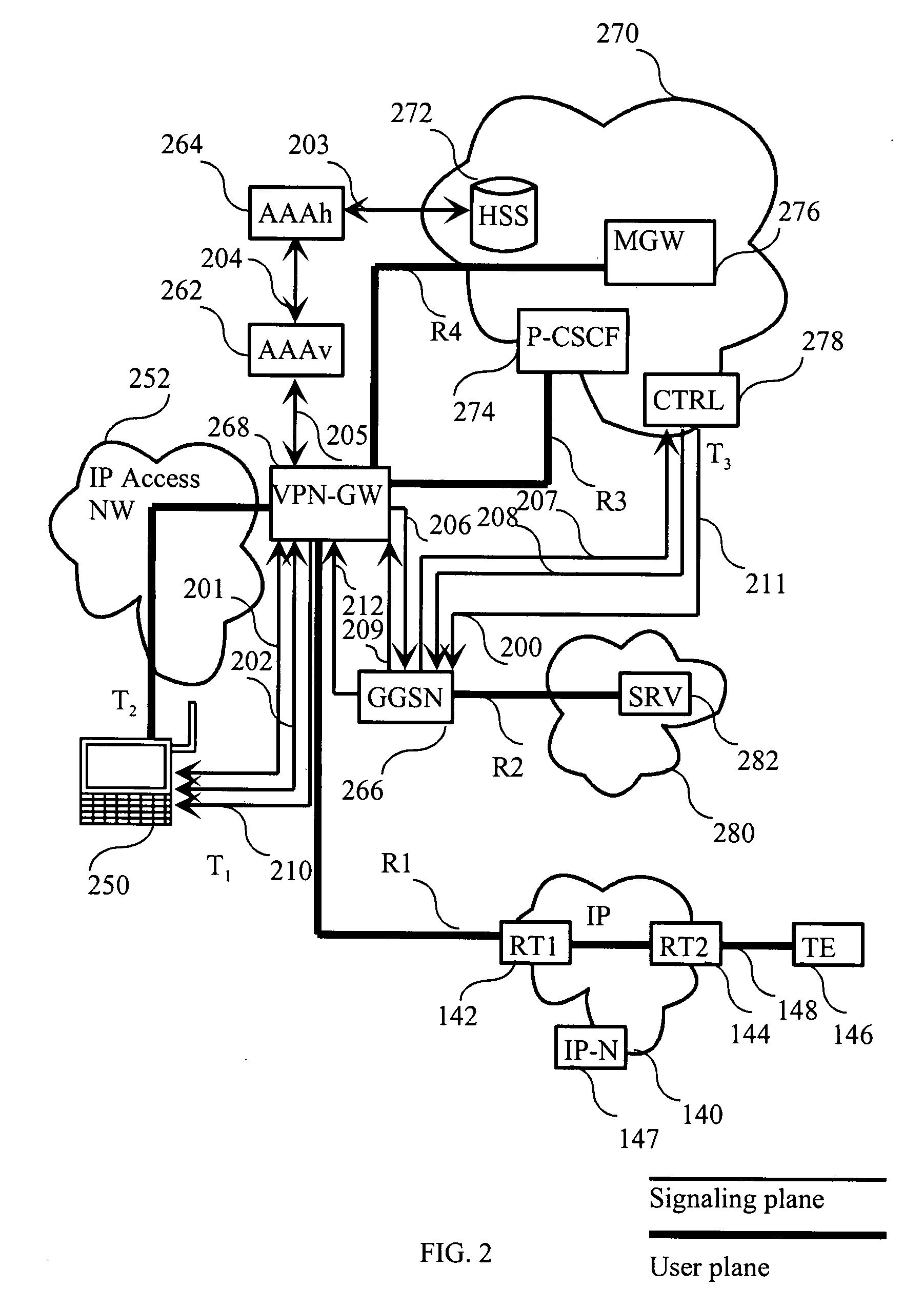
Authorization is the function of specifying access rights/privileges to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define an access policy. For example, human resources staff are normally authorized to access employee records and this policy is usually formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from (authenticated) consumers shall be approved (granted) or disapproved (rejected). Resources include individual files or an item's data, computer programs, computer devices and functionality provided by computer applications. Examples of consumers are computer users, computer Software and other Hardware on the computer.
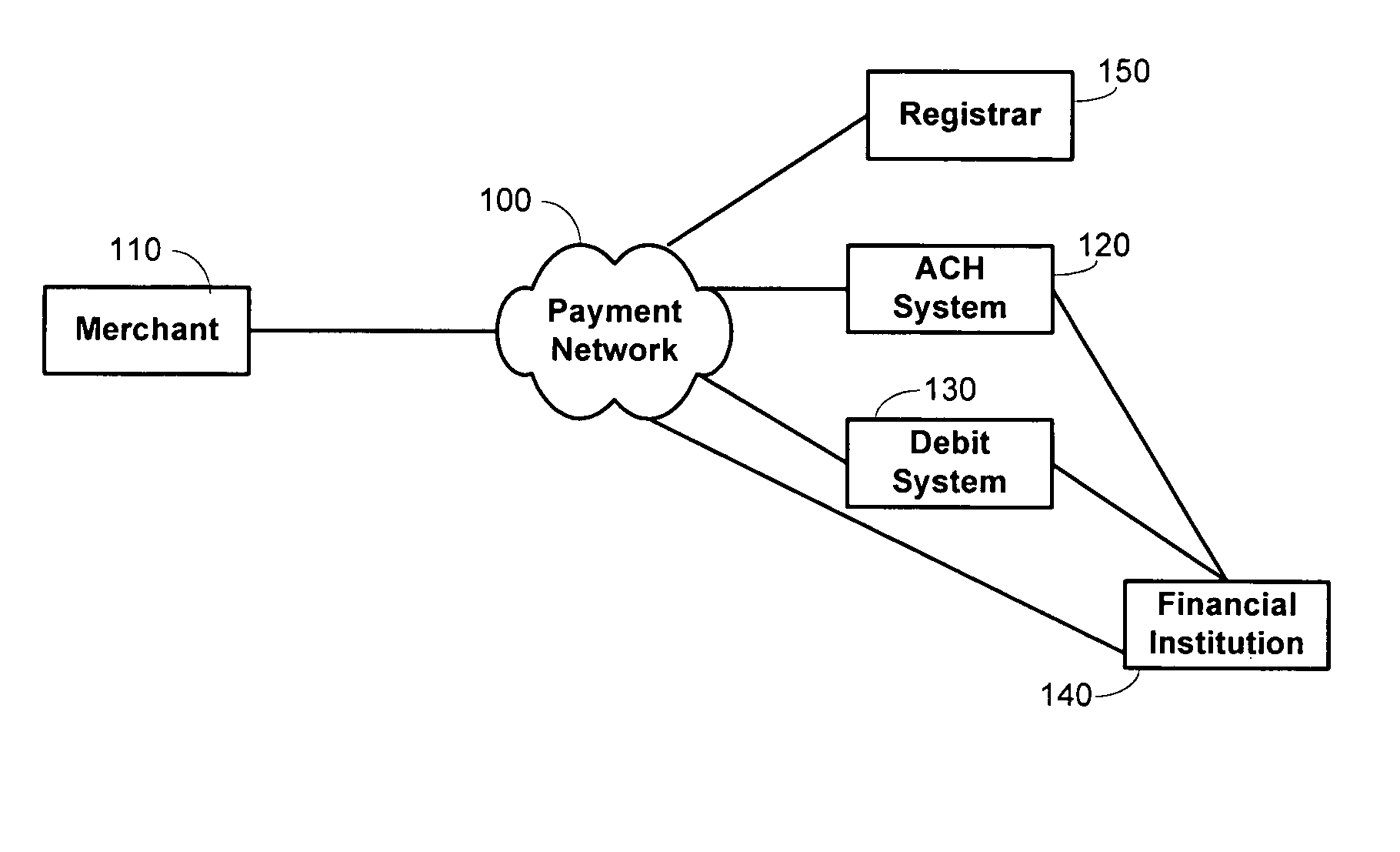
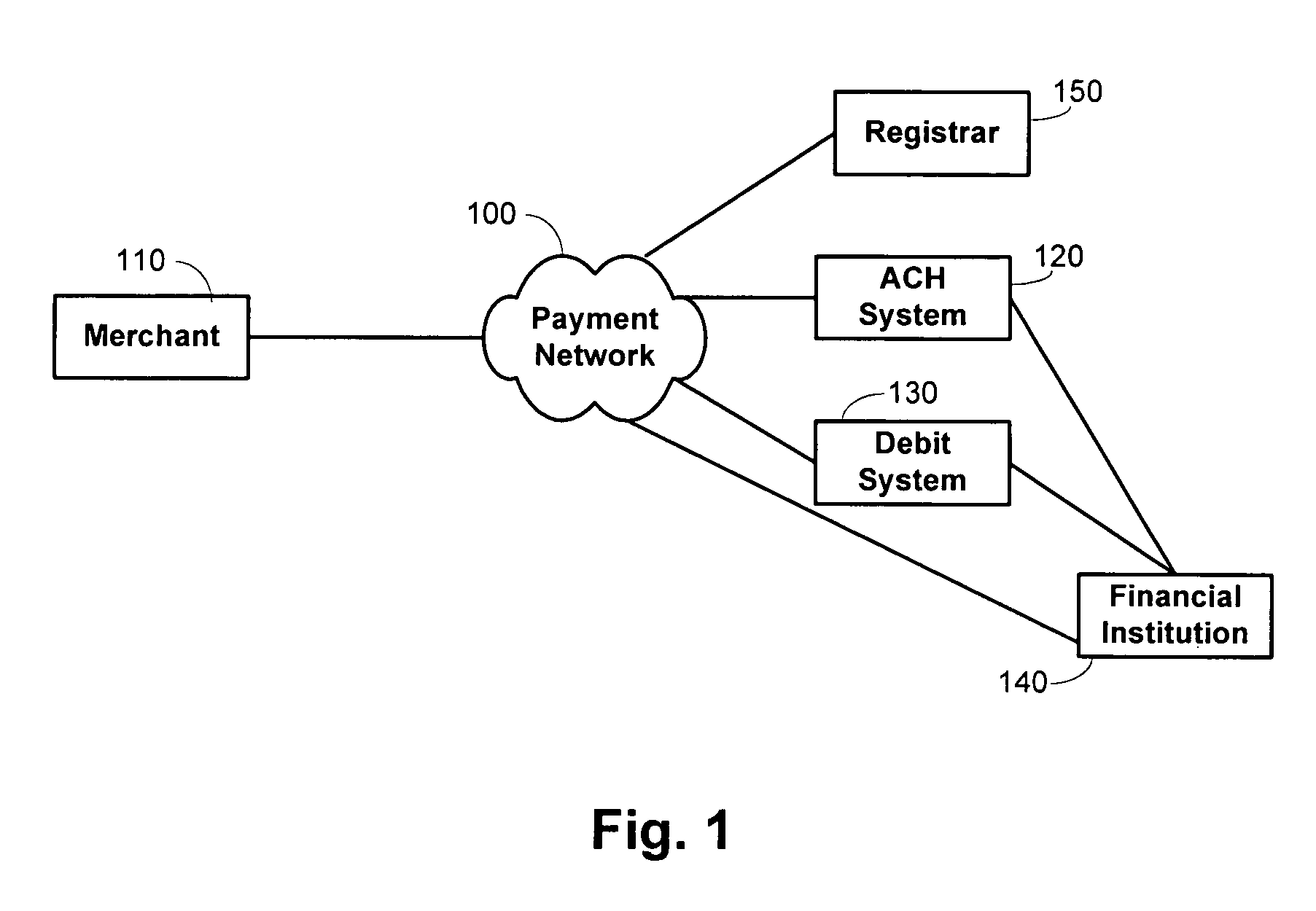
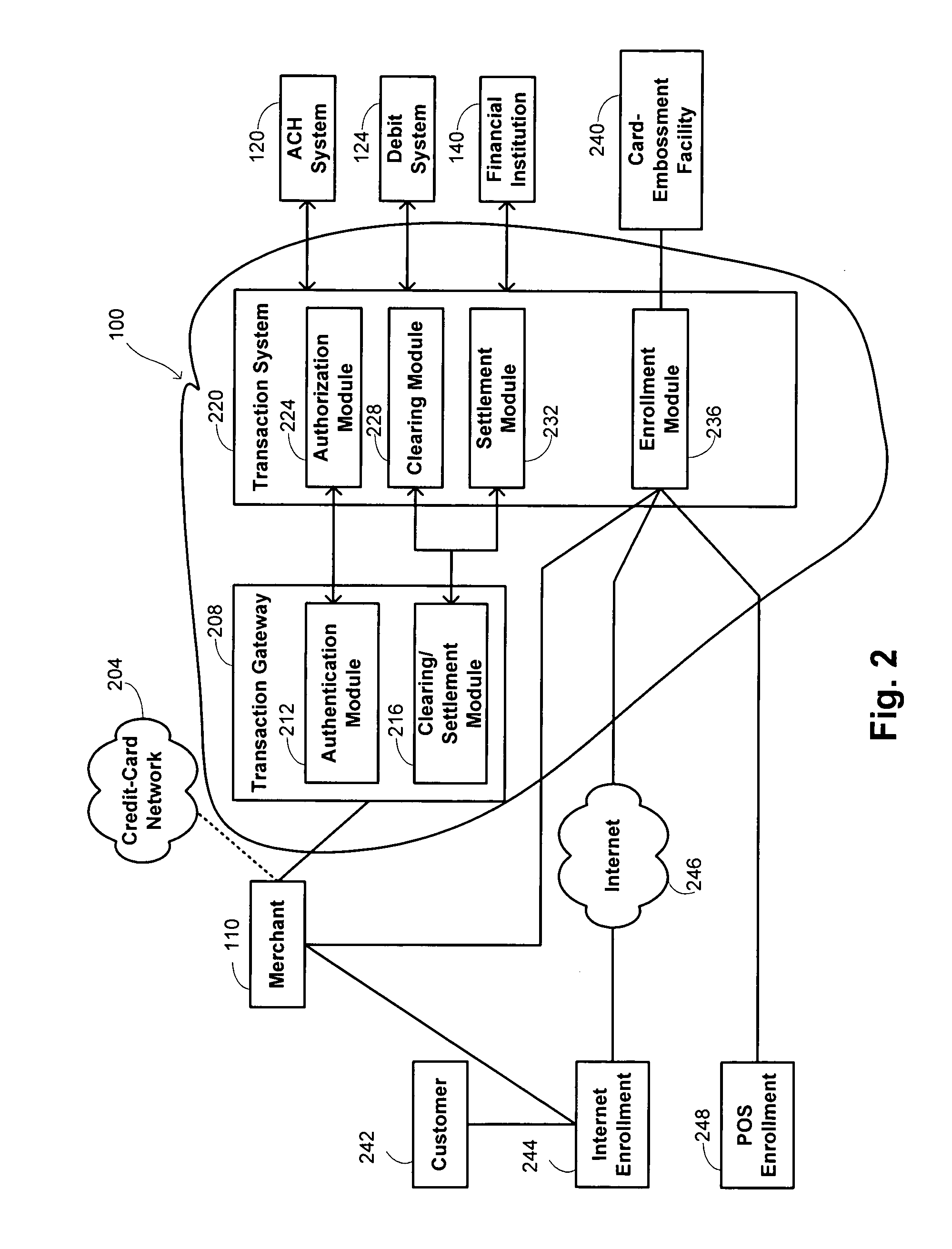
Methods and systems for private label transaction processing
Owner:FIRST DATA
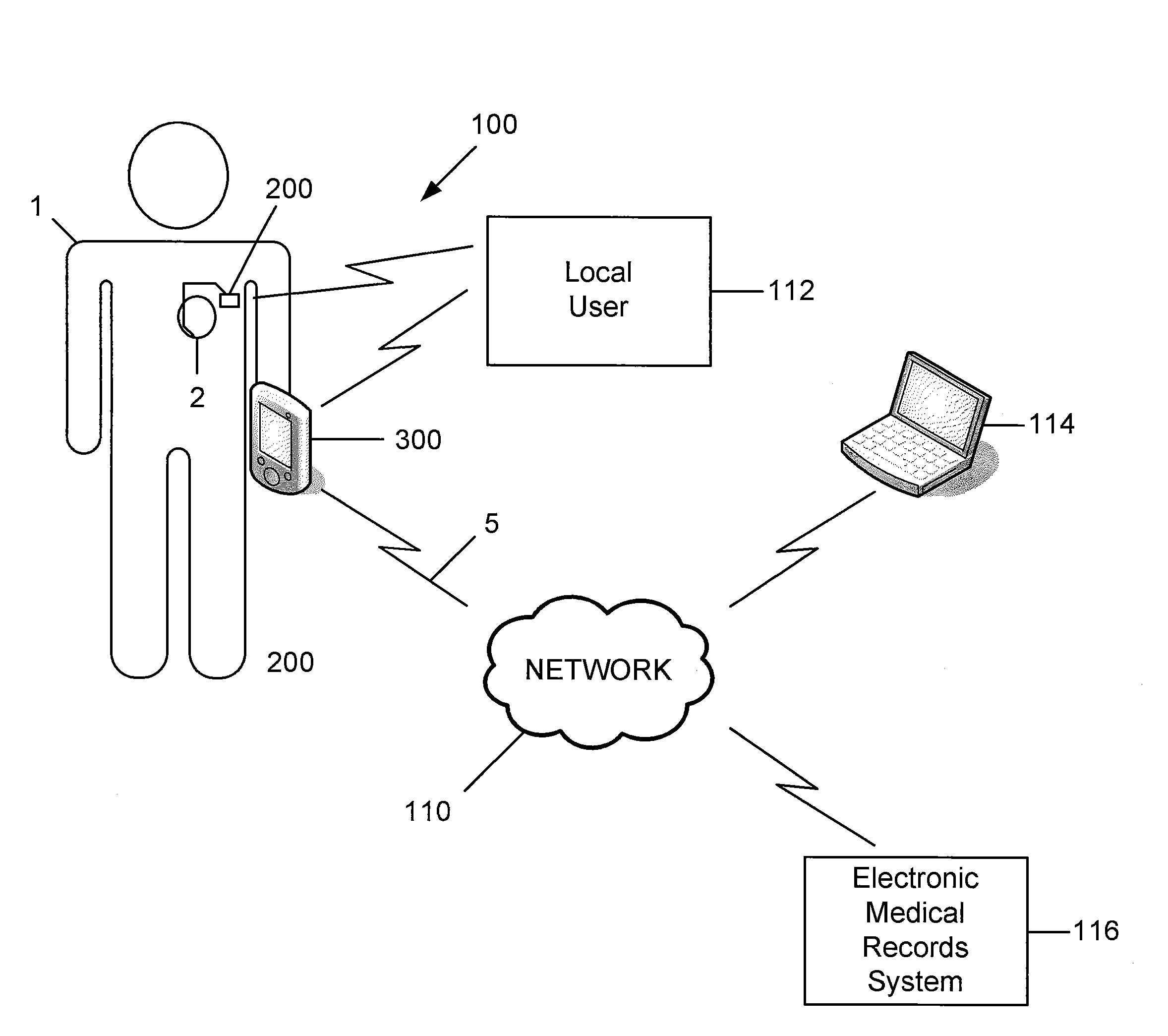
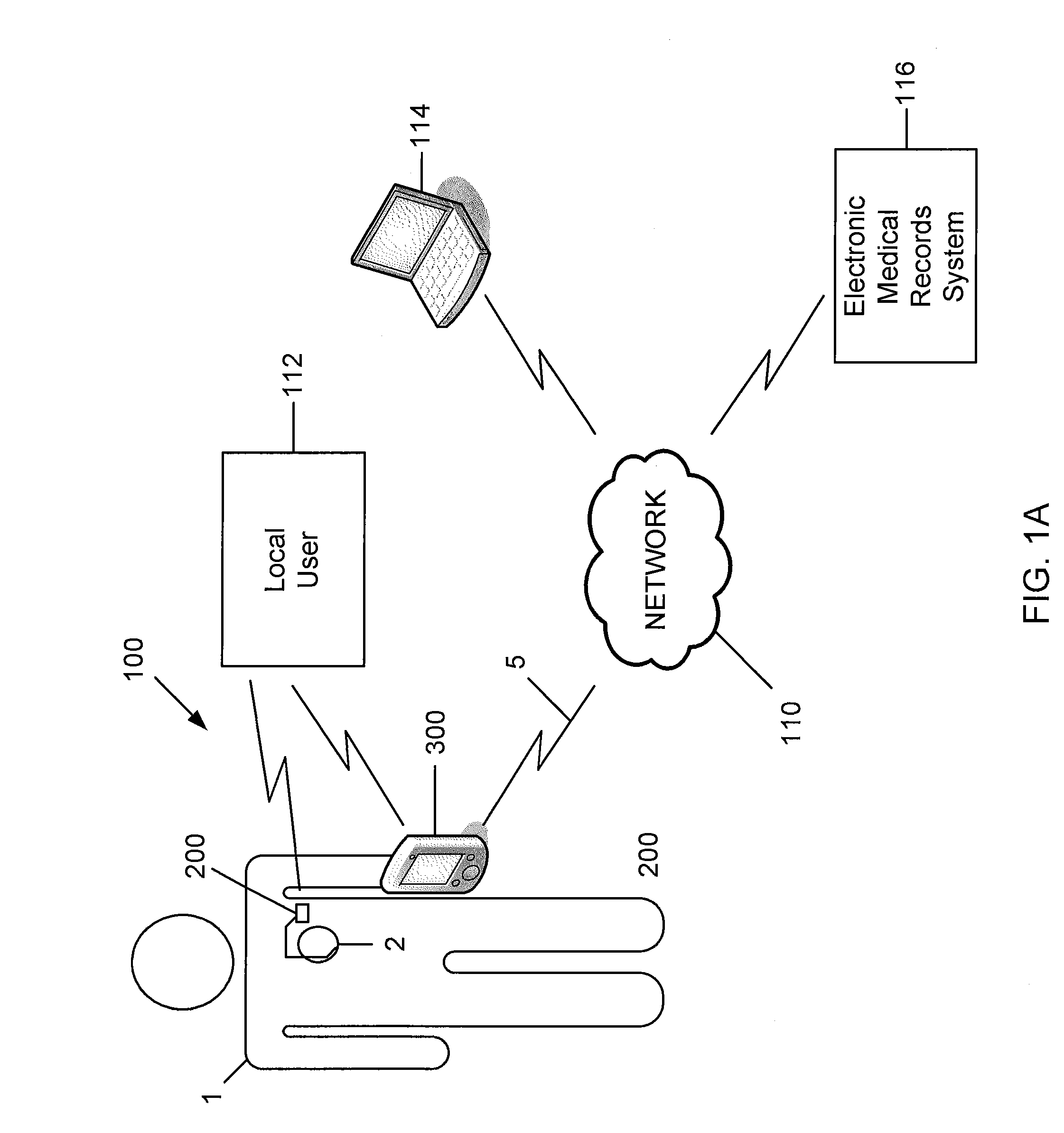
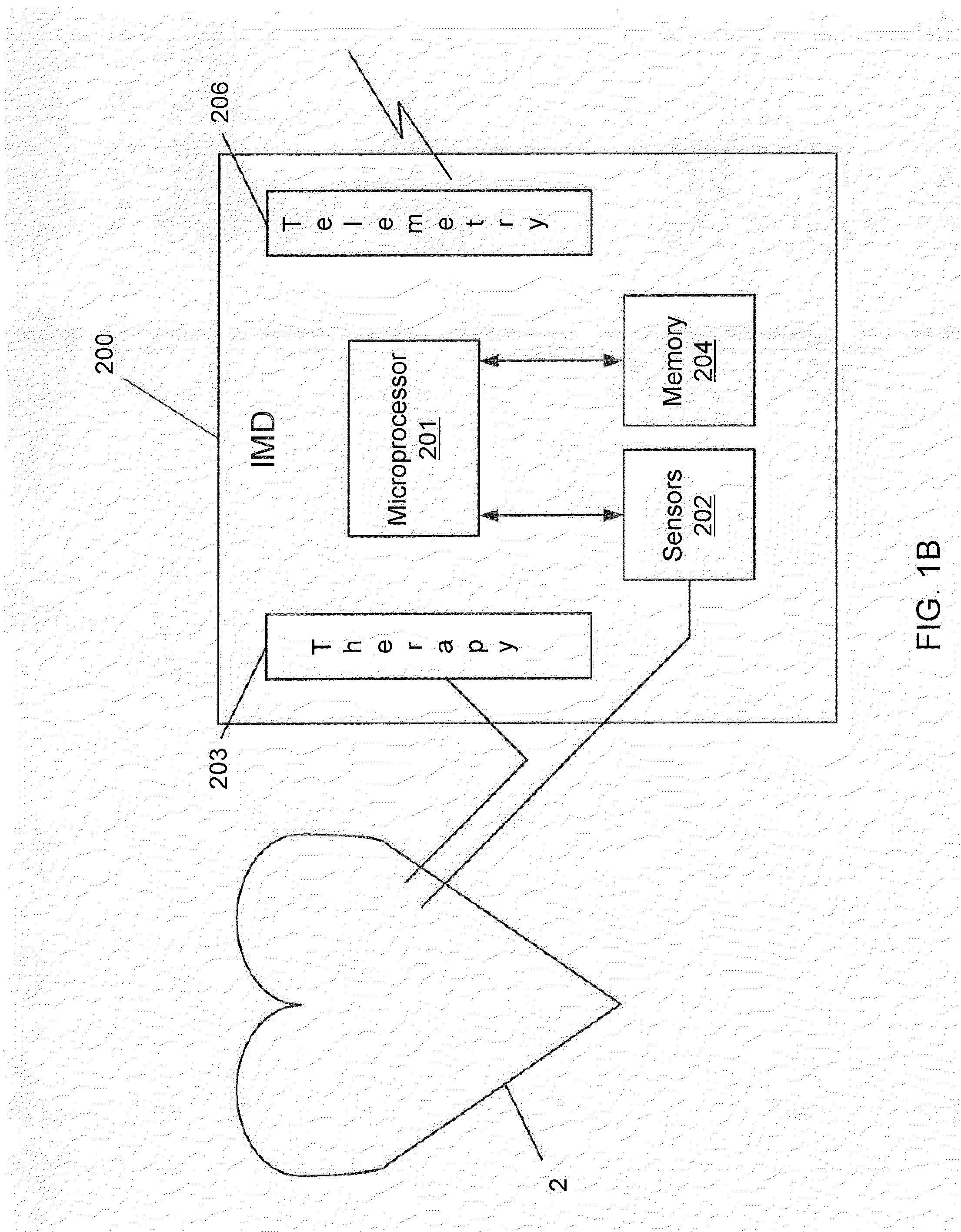
Enhanced Patient Programming Security for Remote Programming via Paired Communication / IMD Access via Custom Hardware
Owner:PACESETTER INC
System and method for conducting secure commercial order transactions
The inventive system and method enable secure remote commercial order transactions between customers and merchants. The inventive system and method ensure that customer entire confidential financial data (CFD) is never transmitted to the merchant by keeping that CFD proprietary to the customer's exiting financial service provider (FSP) with which the customer has established a financial account, and from which the merchant is authorized to receive payments. When an order is placed, the customer provides to the merchant a partial CFD (PCFD) sufficient, along with additional data, to identify the FSP to the merchant, and to identify the customer to the FSP. The merchant then provides the PCFD, along with at least partial order data, to the FSP, and order confirmation data (OCD) to the customer. Various embodiments of a novel order verification process are also provided that enable authorization, by the customer, of the order through contact between the customer and the FSP. In this manner, the complete CFD is kept absolutely secure as it never leaves the possession of the customer and the FSP. Optionally, the FSP is given the opportunity to offer additional services and / or products to the customer during order authentication, that are related or unrelated to the order. Advantageously, the inventive system and method function equally well for interactive electronic (e.g., online) orders, telephone orders, mobile commerce orders, facsimile orders, mail-order orders, and even in-person orders.
Owner:BYZ TEK
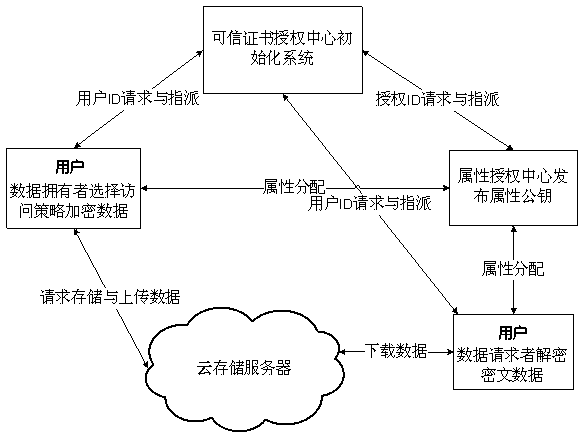
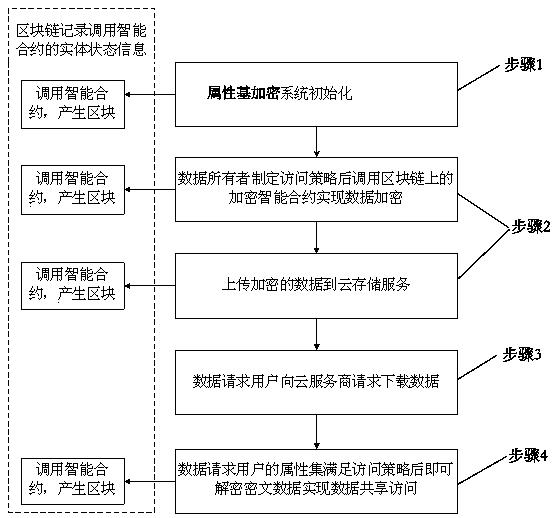
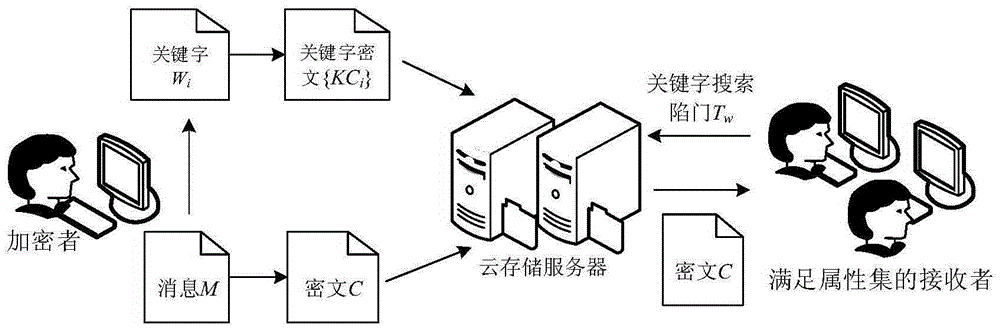
A cloud data security sharing method based on a block chain
Owner:CHONGQING UNIV
Method for the routing and control of packet data traffic in a communication system
InactiveUS20080198861A1Improve scalabilityEqually distributedDigital data processing detailsUser identity/authority verificationCommunications systemNetwork packet
Owner:CORE WIRELESS LICENSING R L
Data anti-leakage protection method for cloud storage environment
Owner:WUHAN UNIV OF TECH
Heterogeneous and integrated hybrid cloud resource management platform
InactiveCN109347676ARealize managementRealize unified managementData switching networksResource poolFull life cycle
The invention discloses a heterogeneous and integrated hybrid cloud resource management platform, comprising a cloud management platform which is a window for a user to interact with an infrastructureas a service (IAAS) layer platform and is connected with an infrastructure as a service layer; and the infrastructure as a service layer which is used for docking with the IAAS layer platform, shielding difference among various different suppliers on the IAAS layer platform and providing a uniform resource adaptive abstract interface for the cloud management platform. The cloud management platform comprises a resource management module which is a cloud management platform body, is connected with the infrastructure as a service layer and provides uniform management of resource pools for a resource manager; and a uniform user management module which provides functions such as tenant management, department management, user management, user group management and role authority authorization management, and supports a single sign on function. According to the heterogeneous and integrated hybrid cloud resource management platform, full life cycle tracking management is carried out, a customer can manage heterogeneous and integrated hybrid cloud resources based on the platform, and business application cloudization migration, reliability and IT operation efficiency are clearly improved.
Owner:HANGZHOU YUNJI TECH CO LTD
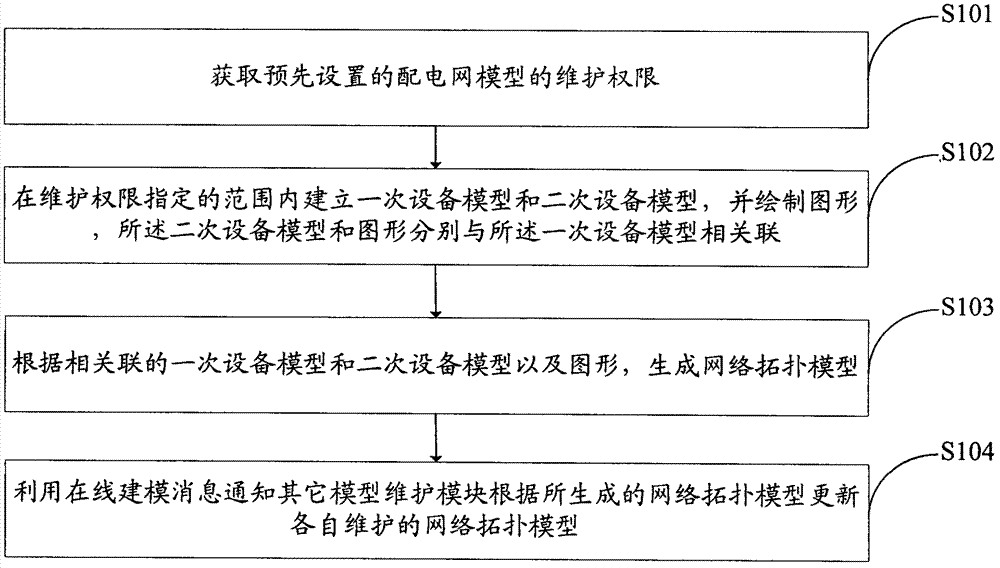
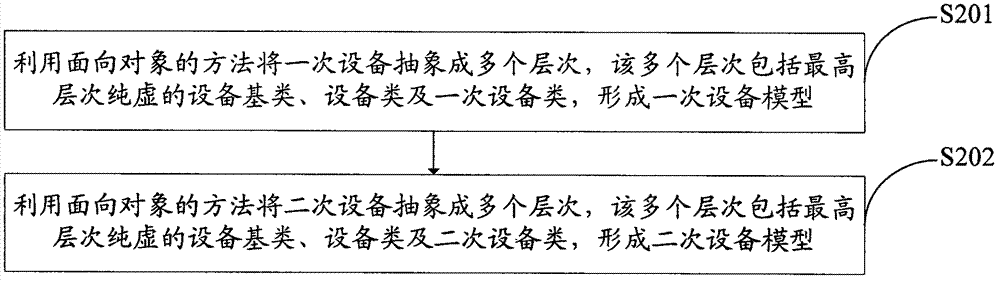
Method and system for establishing distribution network model
ActiveCN102957205AGuaranteed correctnessEasy maintenanceCircuit arrangementsSpecial data processing applicationsGraphicsPower grid
Owner:云谷技术(珠海)有限公司
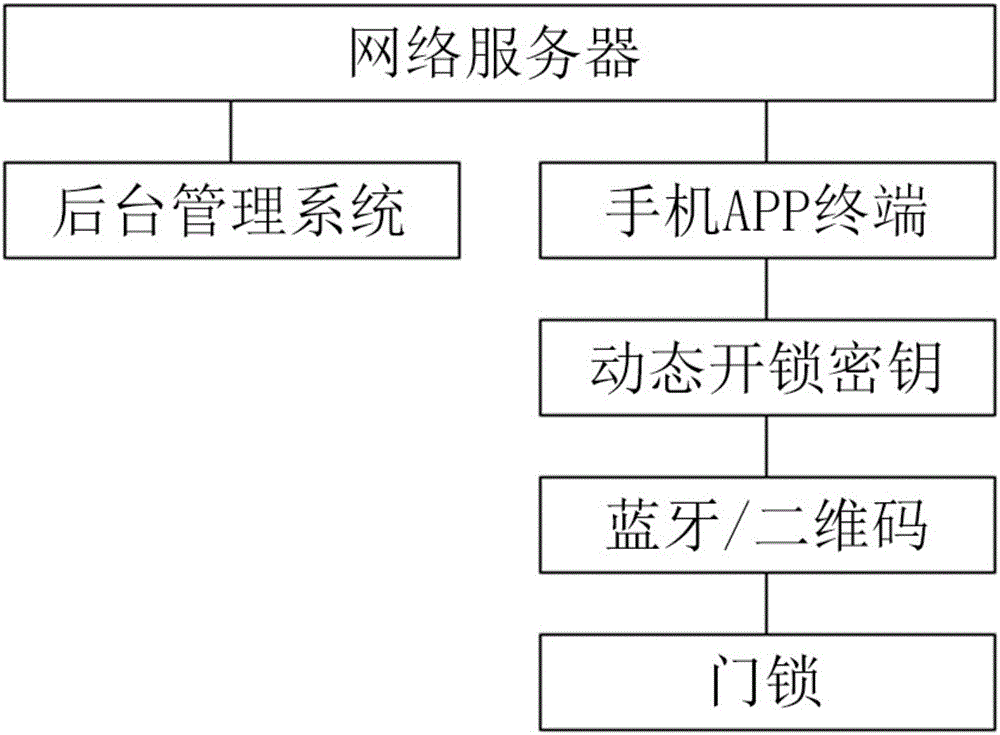
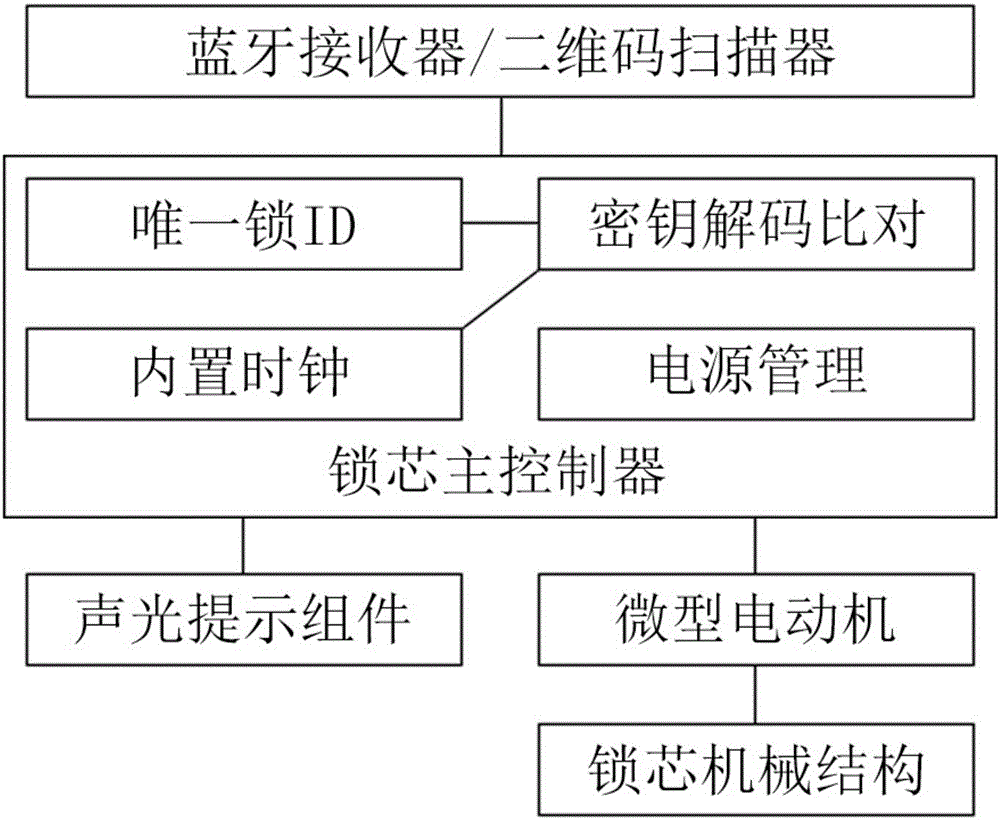
House-renting management system capable of opening locks based on Bluetooth or two-dimensional codes and method thereof
InactiveCN106530454ALow costProtection of rights and interestsData processing applicationsIndividual entry/exit registersStructure of Management InformationDimensional modeling
Owner:俞毅
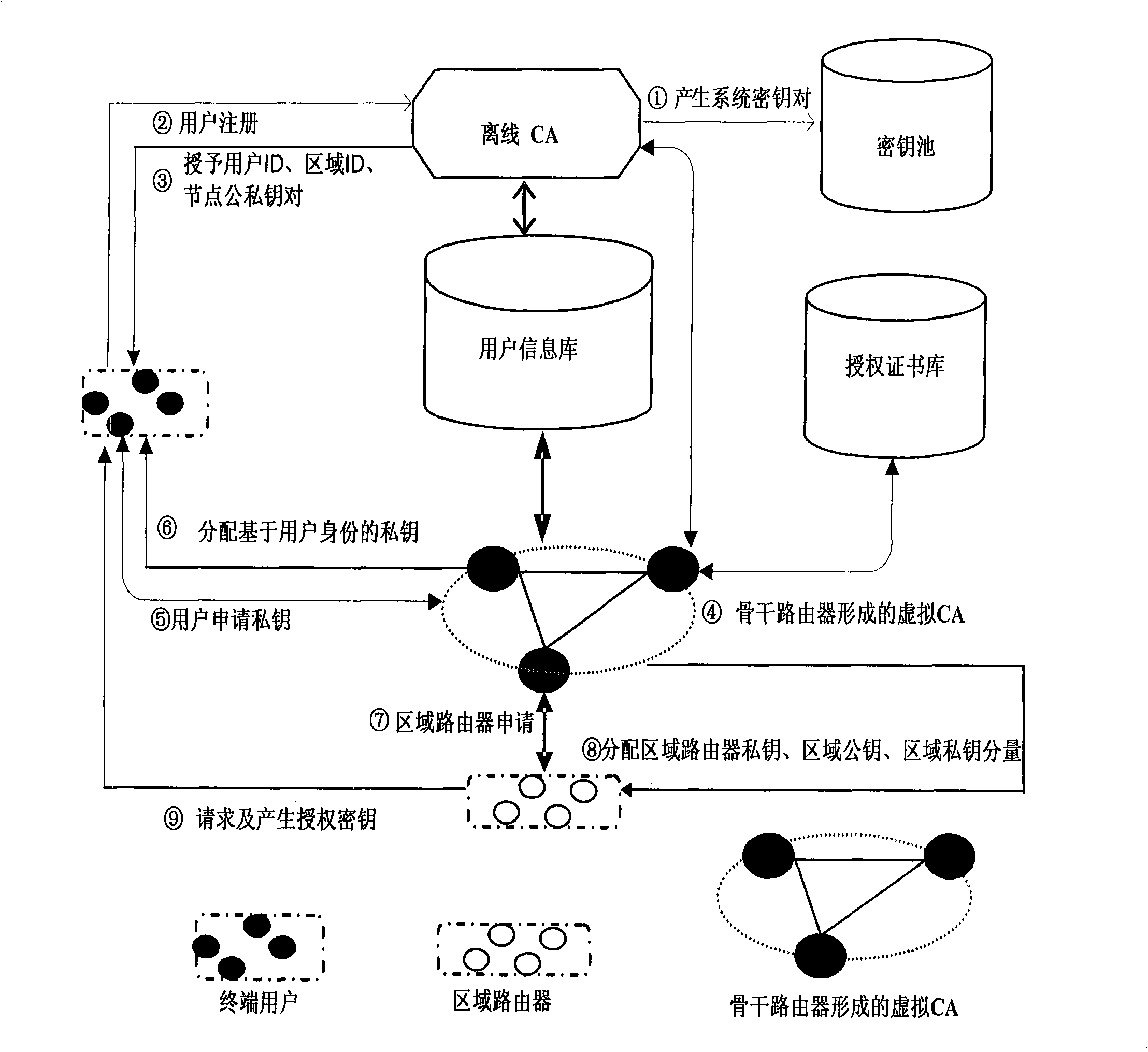
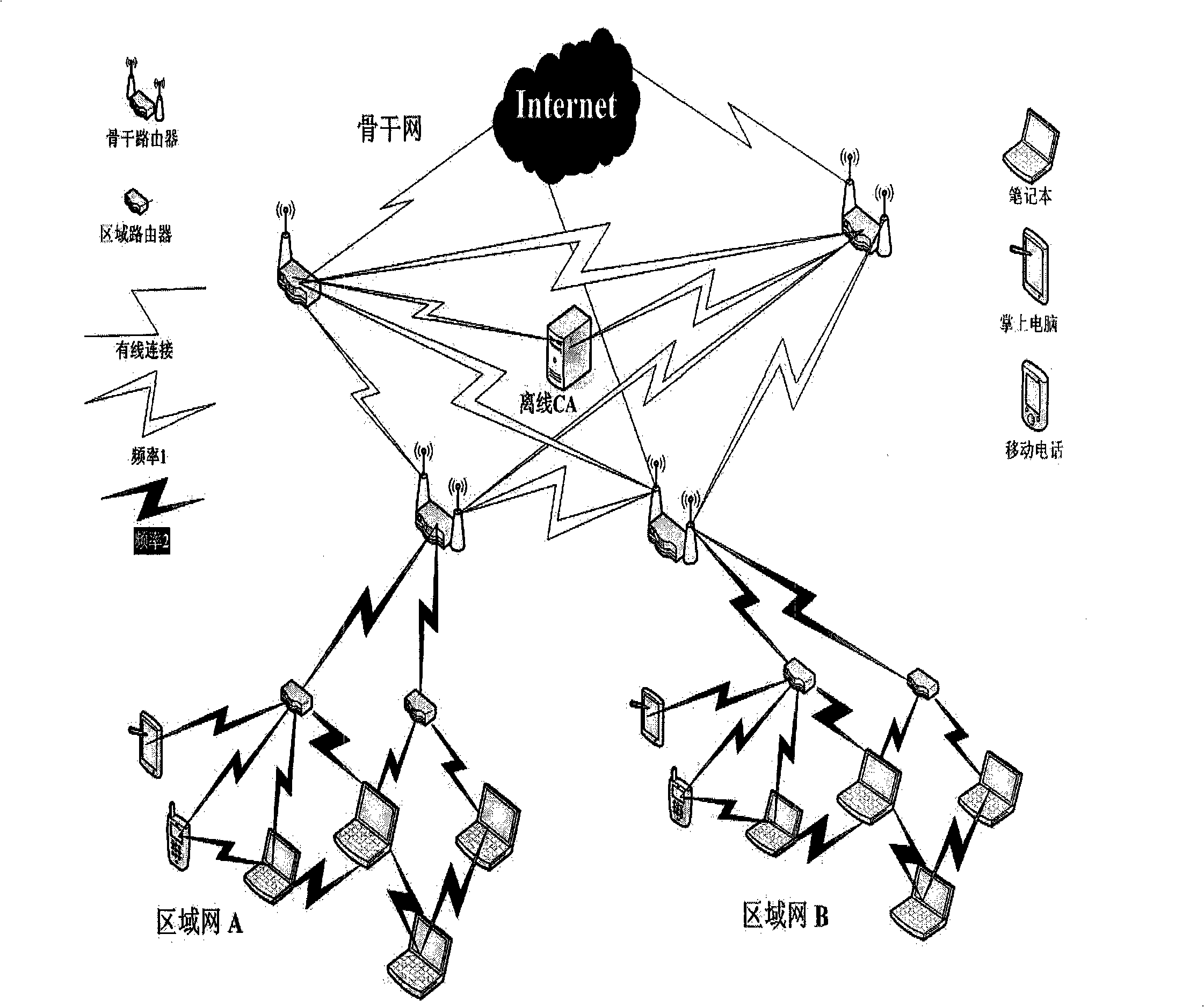
Access authentication method of wireless mesh network
InactiveCN101494862AUser identity/authority verificationNetwork topologiesAuthorizationManagement system
Owner:BEIJING UNIV OF TECH
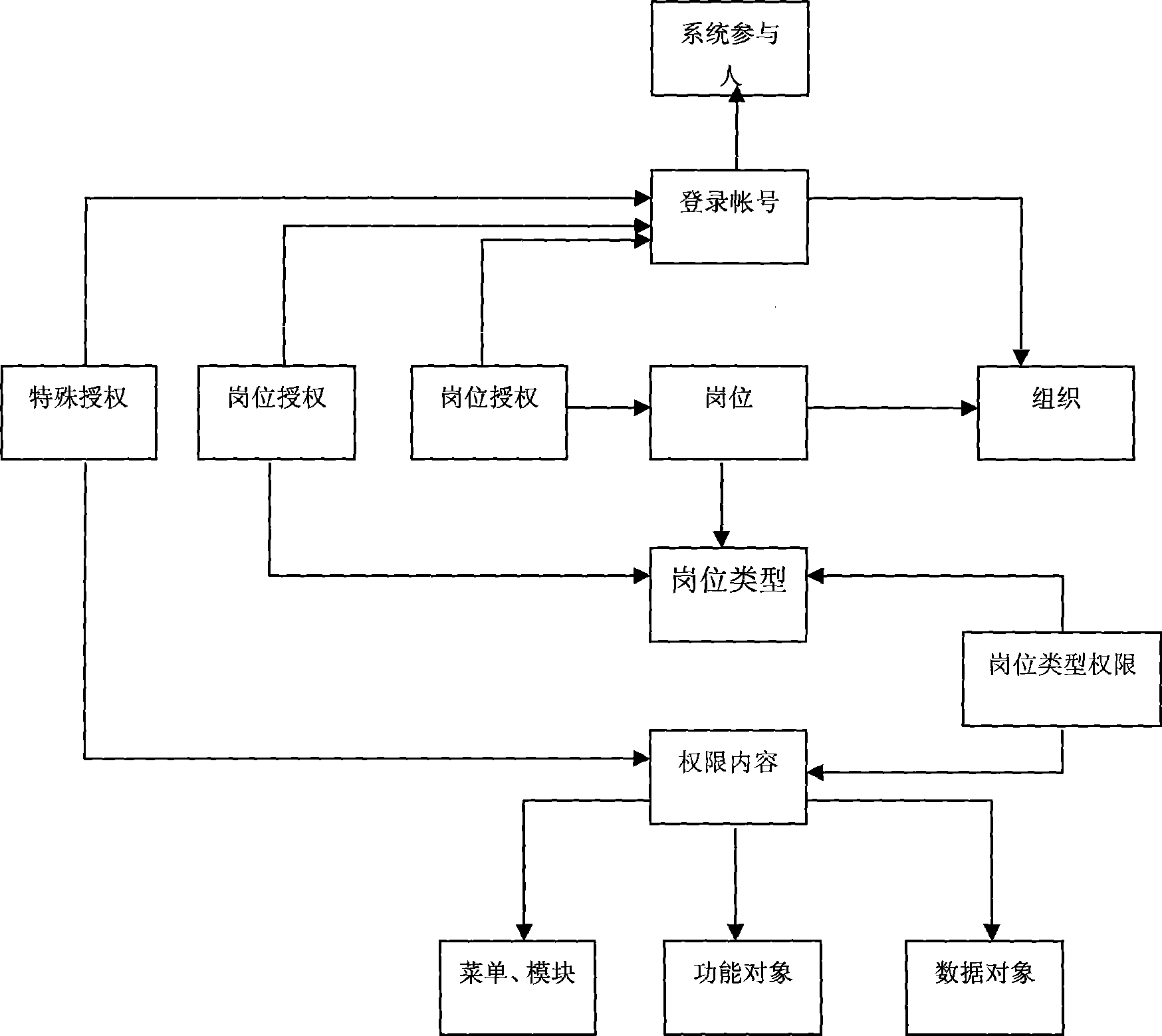
Human authority control method engaged with system
Owner:上海全成通信技术有限公司
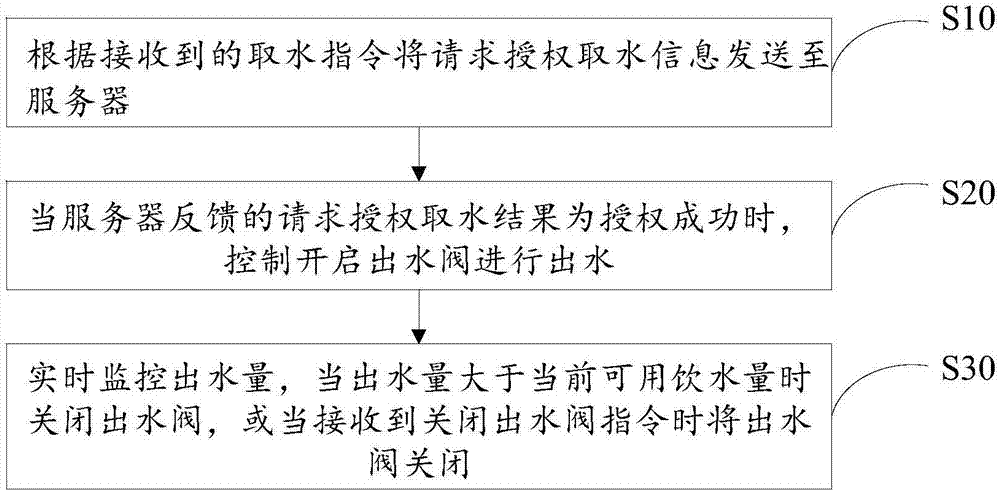
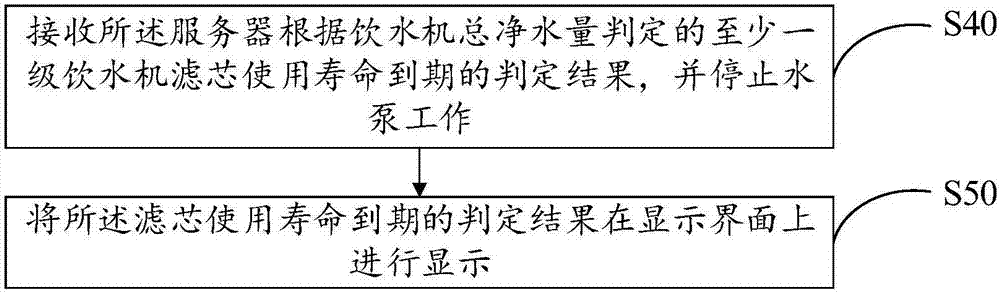
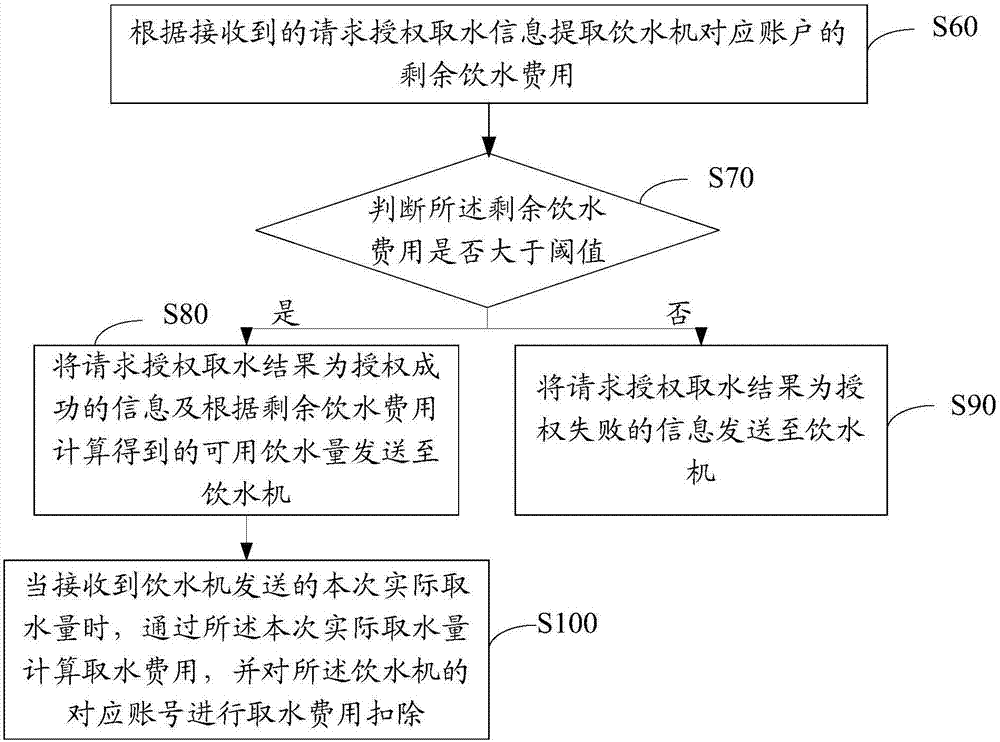
Internet based water dispenser management method and device
InactiveCN107103694APre-payment schemesApparatus for dispensing fluids/granular materialsAuthorizationWater use
Owner:深圳市优点智联科技有限公司
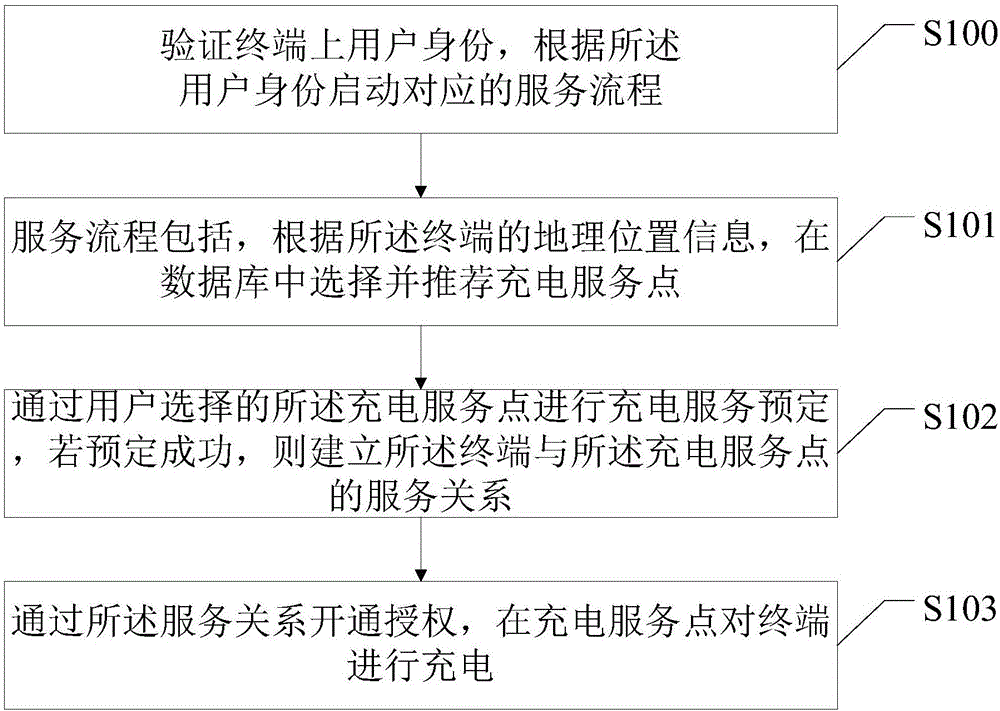
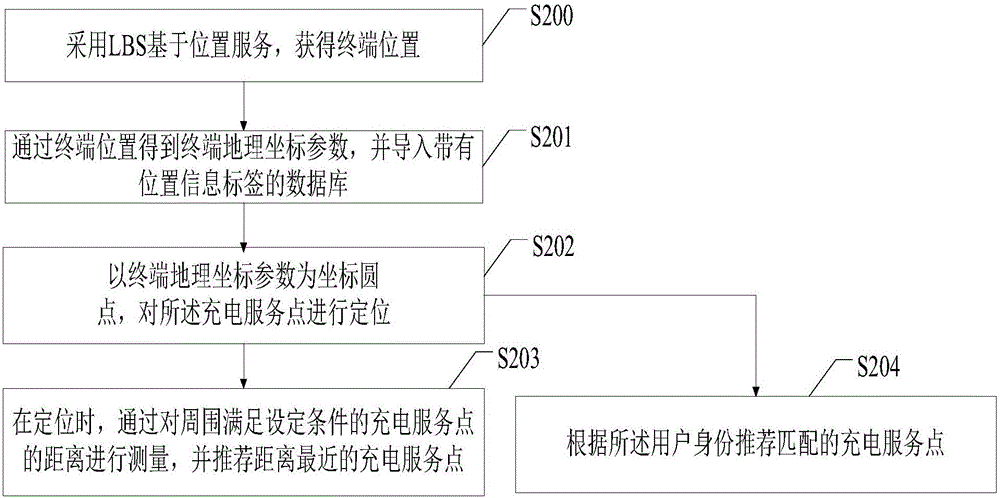
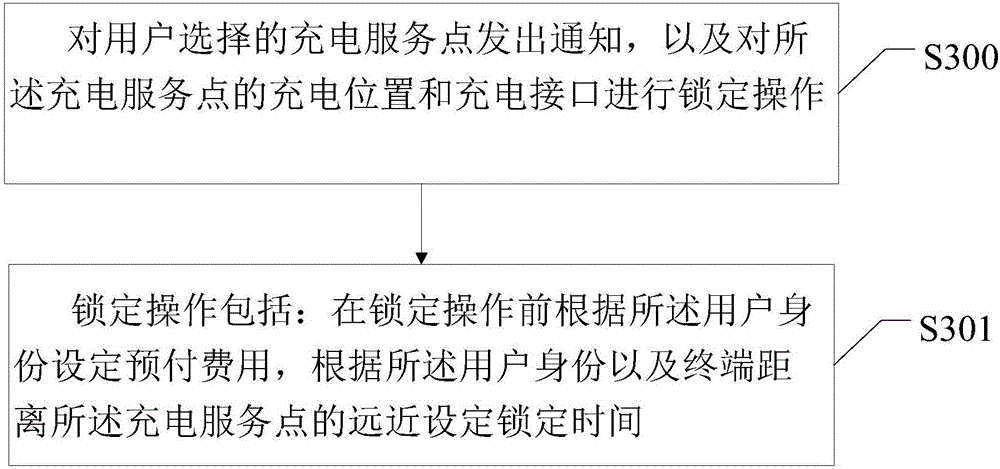
Charging service intelligent implementation method and device on basis of terminal
InactiveCN106297030ASolve the problem that the charging service point cannot be foundIncrease usageApparatus for hiring articlesLocation information based serviceGeolocationComputer terminal
Owner:深圳市恒义聚贸易有限公司
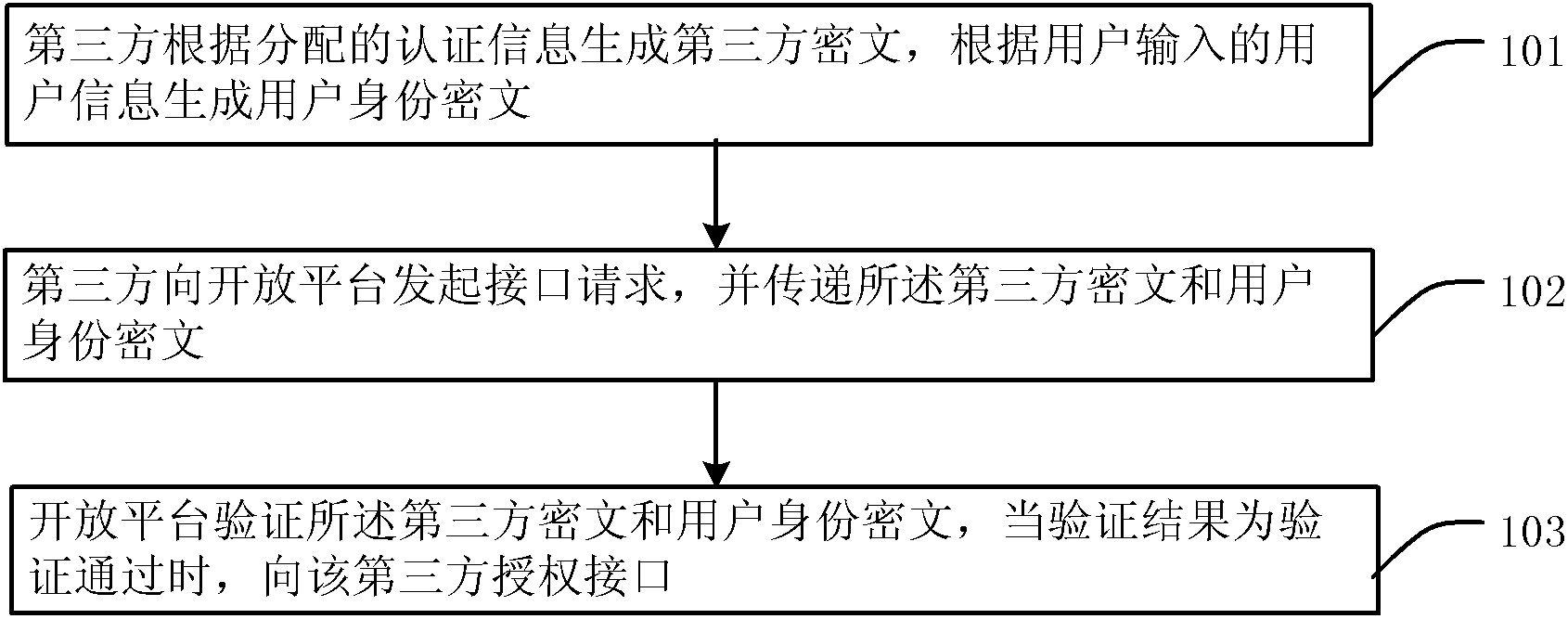
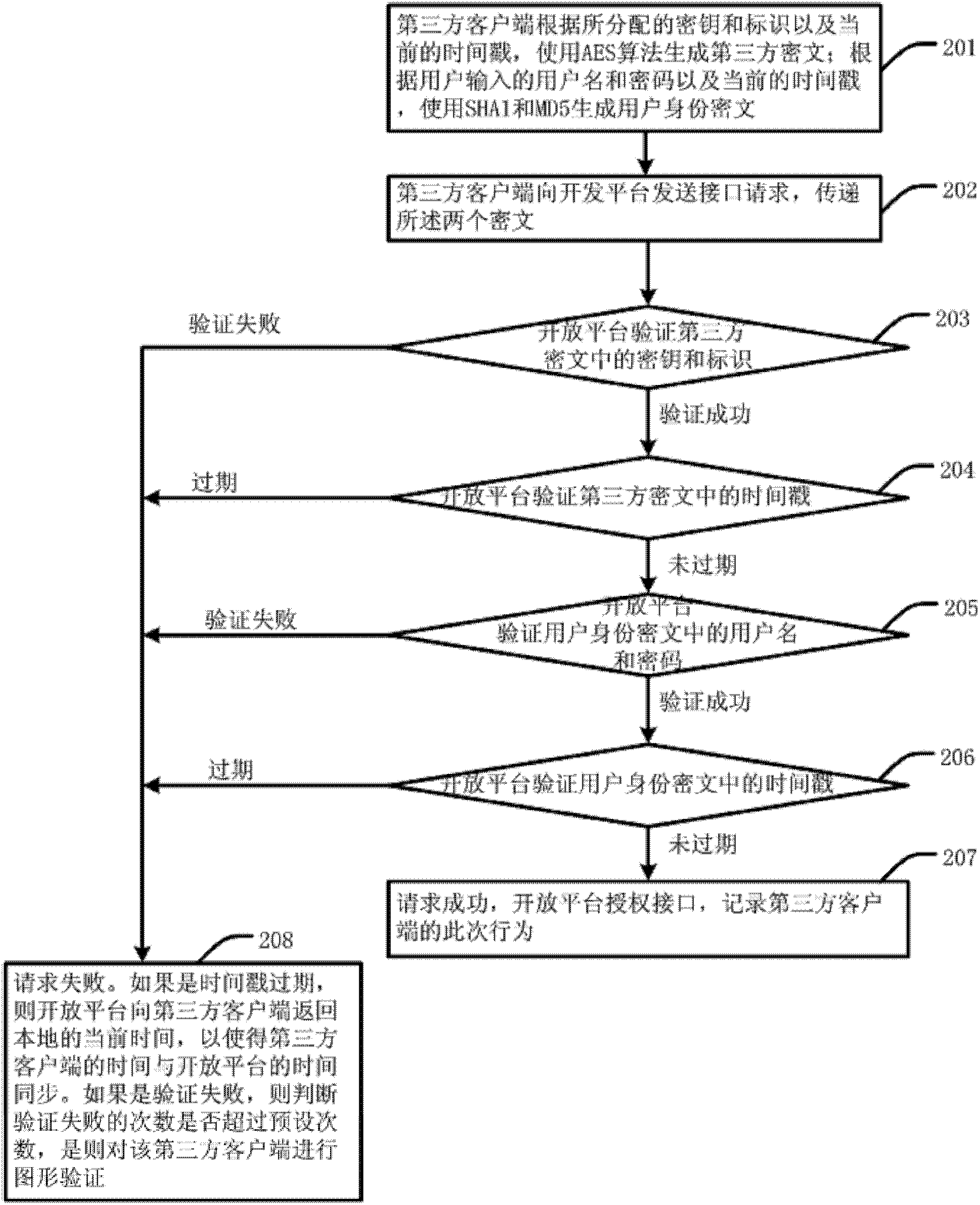
Method and system for third party application interface authorization
Owner:BEIJING FEINNO COMM TECH
Method and device for searching cells in sensing system
InactiveCN103546940AOptimal Selection MechanismChoose accuratelyAssess restrictionNetwork topologiesResidenceCell selection
Owner:CHINA ACAD OF TELECOMM TECH
Determination of access checks in a mixed role based access control and discretionary access control environment
InactiveUS20080271139A1Digital data processing detailsUser identity/authority verificationDiscretionary access controlAuthorization
Owner:IBM CORP
Method and system for providing assistance to vehicles with damaged wheel components
ActiveUS7457614B2Short timeCheap serviceSpecial service for subscribersRadio/inductive link selection arrangementsAuthorizationDirect shipment
Owner:PIRELLI TYRE SPA
Digital identity authentication method and system based on secure two-dimensional code
Owner:新大陆(福建)公共服务有限公司
Data processing method and device, storage medium and processor
ActiveCN109886040ASafe and accurate accessAddresses vulnerabilities that make it difficult to securely and accurately access filesDigital data protectionComputer hardwareNetwork packet
Owner:武汉融氢科技有限公司
Method for accessing and exiting frequency spectrum of hybrid cognitive network
InactiveCN102202317ATaking into account efficiencyConsider complexityNetwork planningMulti bandCognitive user
Owner:SUZHOU UNIV
Circusee synchronization method and system realized on webpage as well as client
InactiveCN102387202AImprove experienceImprove interactivityTransmissionSpecial data processing applicationsWeb pageAuthorization
Owner:SUZHOU CODYY NETWORK SCI & TECH
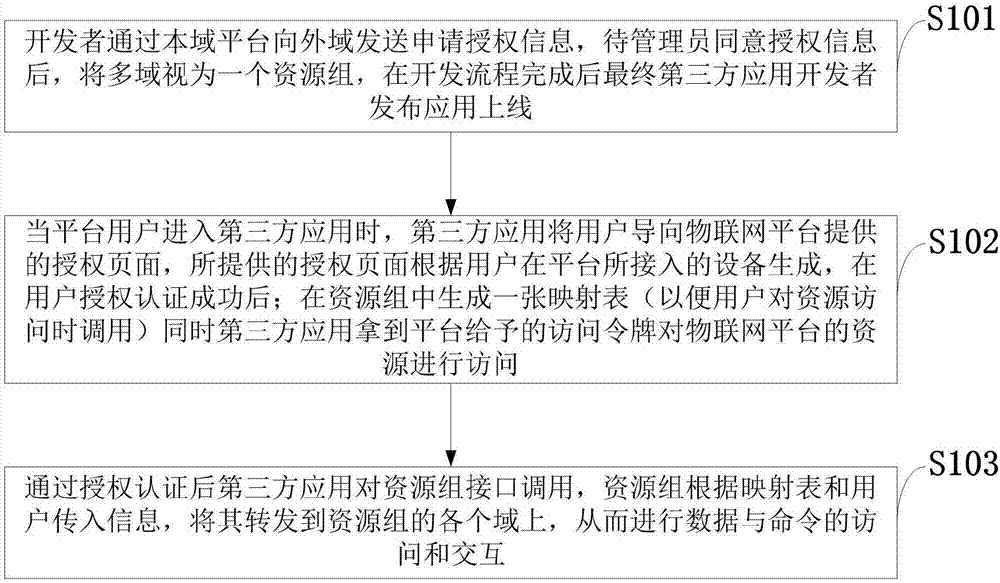
Third-party application authorization and authentication method based on multi-domain collaborative architecture
ActiveCN107018128ASafe and reliable authorized accessTroubleshoot authentication issuesTransmissionThird partySoftware engineering
Owner:陕西沃傲信息科技有限公司
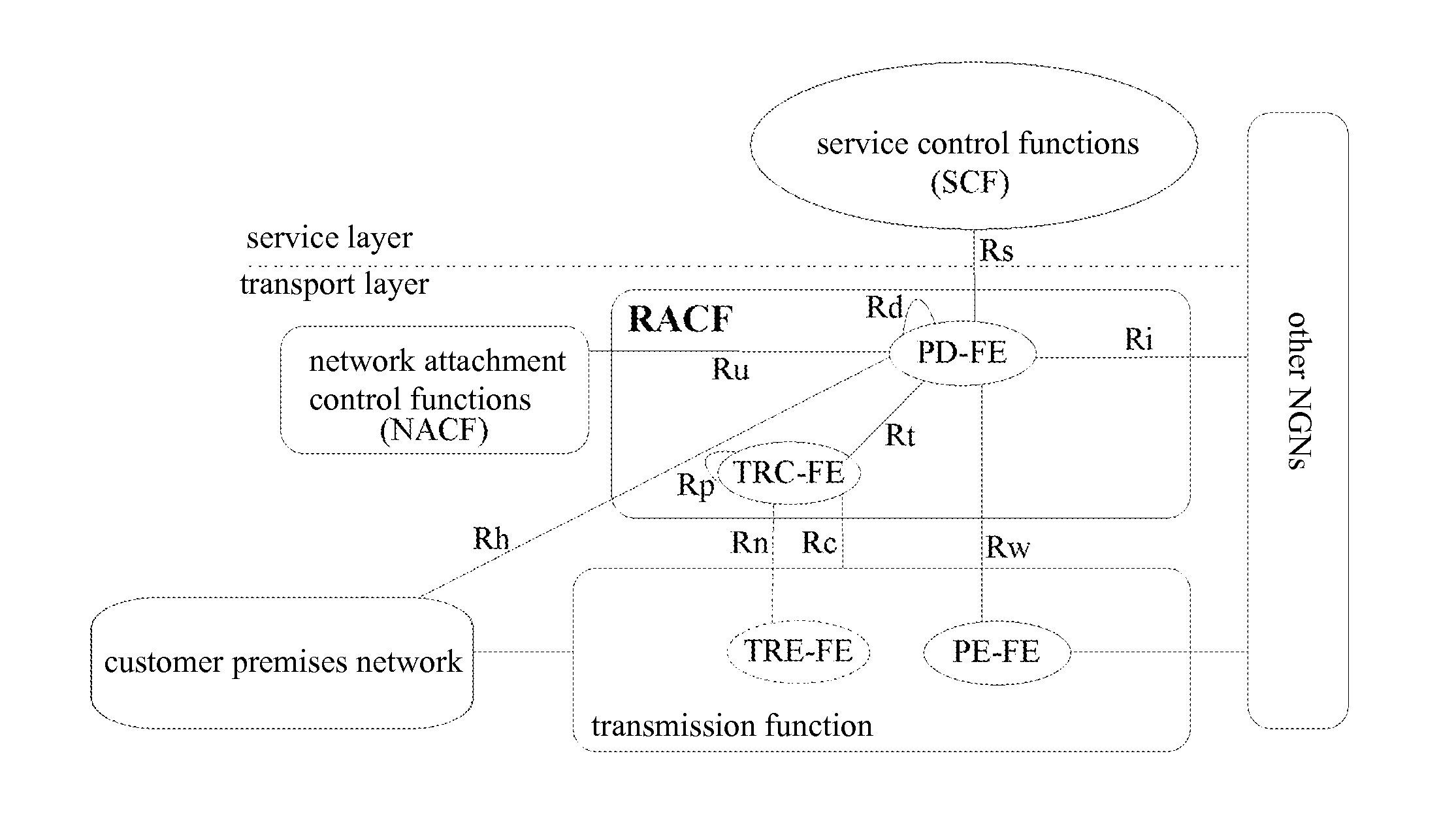
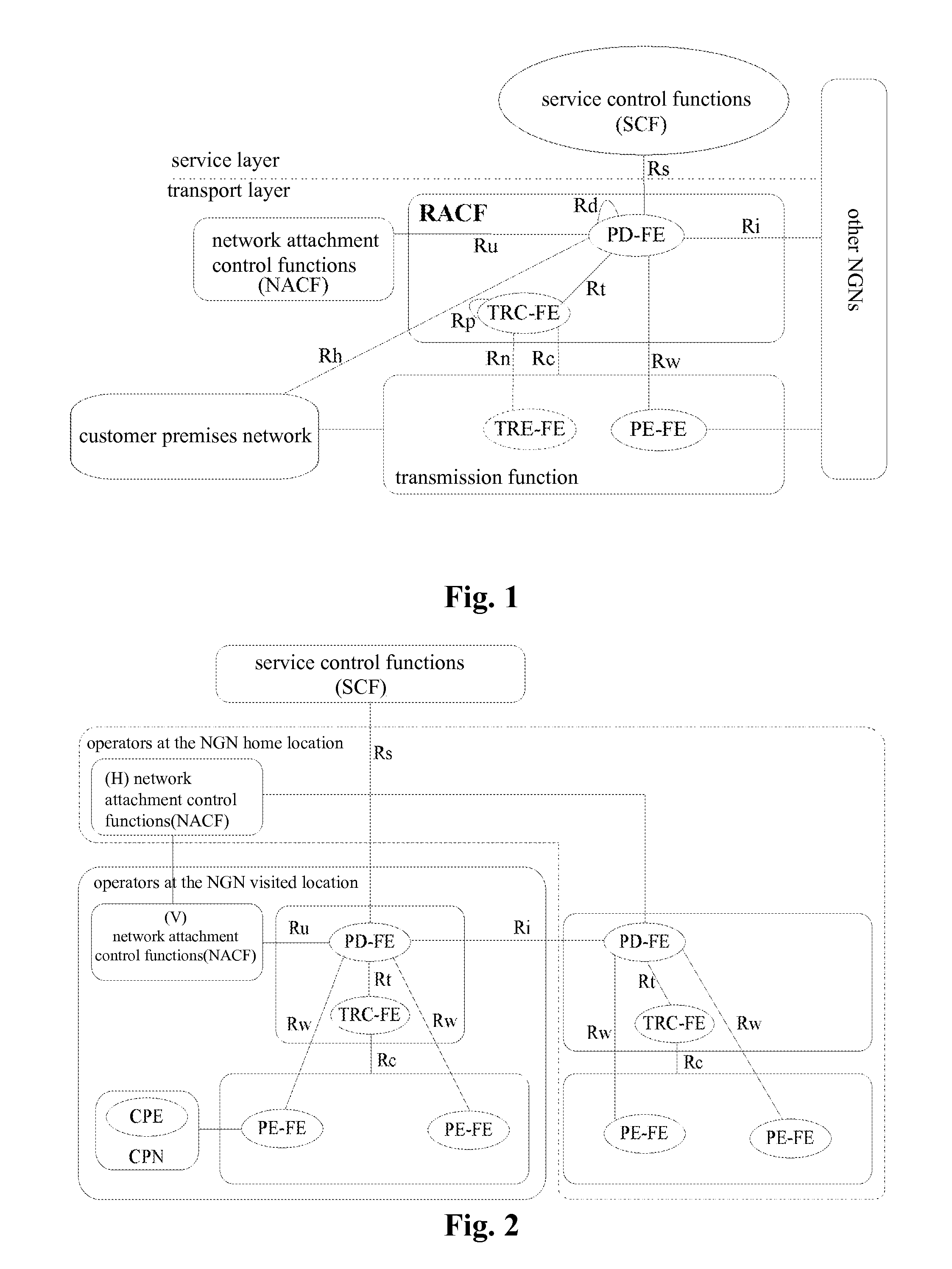
Method for Resource and Admission Control
InactiveUS20110235507A1Solve the real problemNetwork traffic/resource managementError preventionPolicy decisionAuthorization
Owner:ZTE CORP
Method and device for identifying visited and home authentication servers
Owner:ORANGE SA (FR)
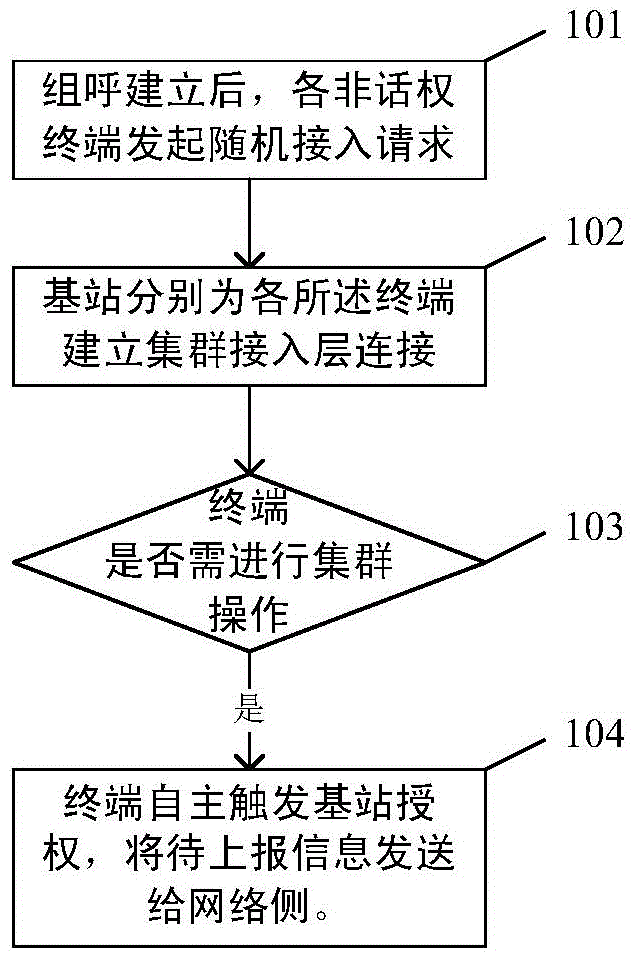
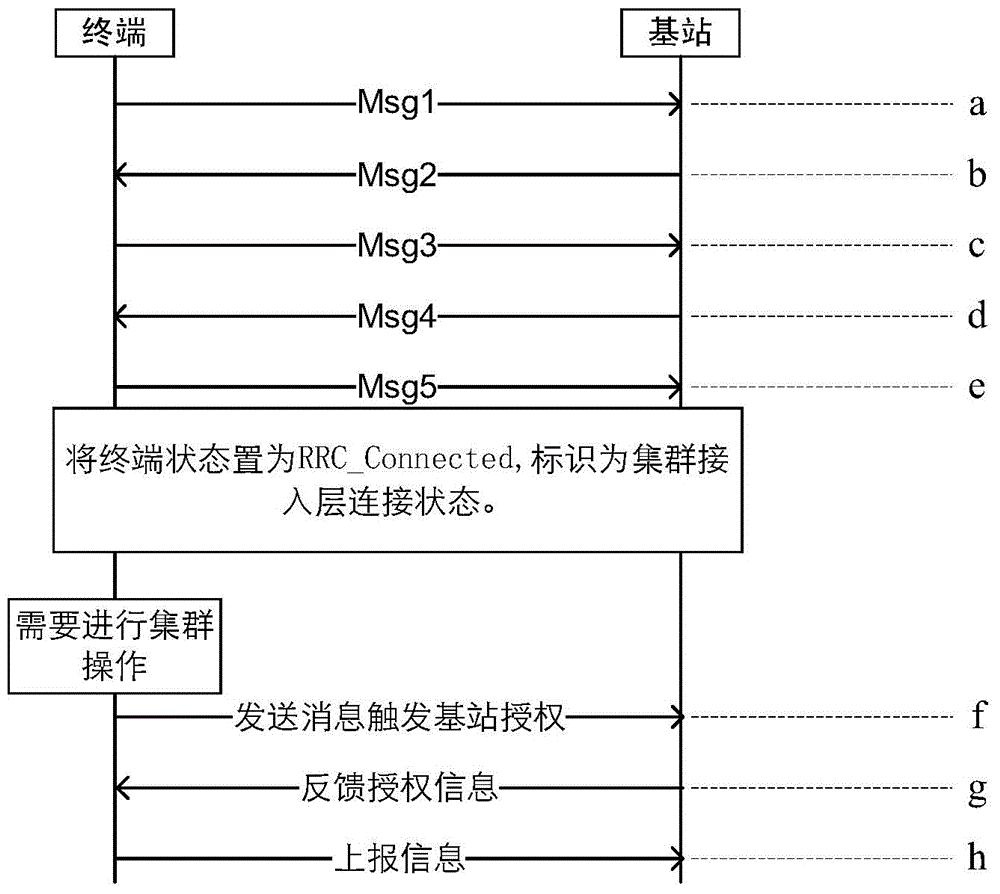
Method, device and system for reporting terminal information in cluster system
Owner:BEIJING XINWEI TELECOM TECH
System and method for device authorization and remediation
ActiveUS20150281190A1Digital data processing detailsUser identity/authority verificationDiagnostic dataRestoration device
A method is provided for authorizing a device for consuming content. In method includes the steps of generating an authorization request, the authorization request for authorization data including device diagnostic data (instructions) an device remedial data (instructions), transmitting the authorization request from the device to an authorizing service, and authorizing or remediating the device according to an authorization response to the authorization request received from an authorization server.
Owner:ARRIS ENTERPRISES LLC
Key information processing method and device and system thereof
ActiveCN101662361ASecuring communicationCoded identity card or credit card actuationInformation processingComputer module
The invention discloses a key information processing method and a device and a system thereof, which are applied in a smart card system and used for avoiding the problem that the charging mode in the prior art is possible to cause illegal self-charging on user cards by a business process terminal. The method comprises the steps of obtaining a first random number by a business process device; providing the obtained first random number for a background processing system; receiving key information which is fed back by the background processing system and generated by encryption algorithm on the first random number by using first encryption rules; and providing the key information which is used for authentication and authorization of a secure access module for the secure access module.
Owner:BEIJING MUNICIPAL ADMINISTRATION & COMM CARD CO LTD
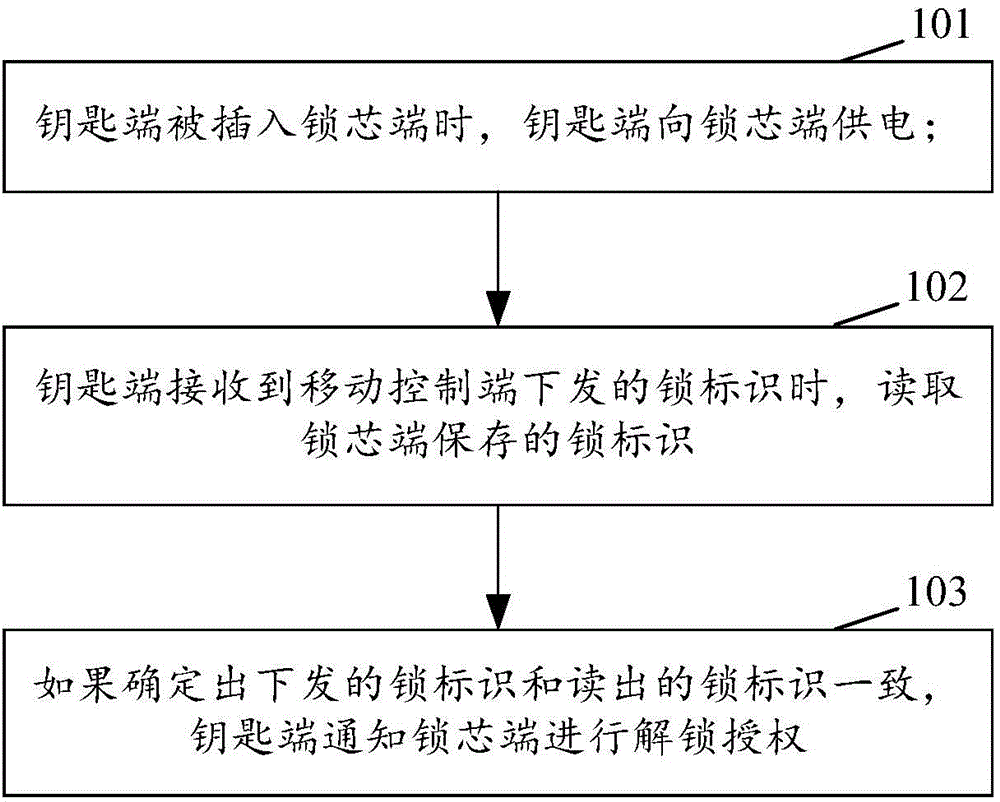
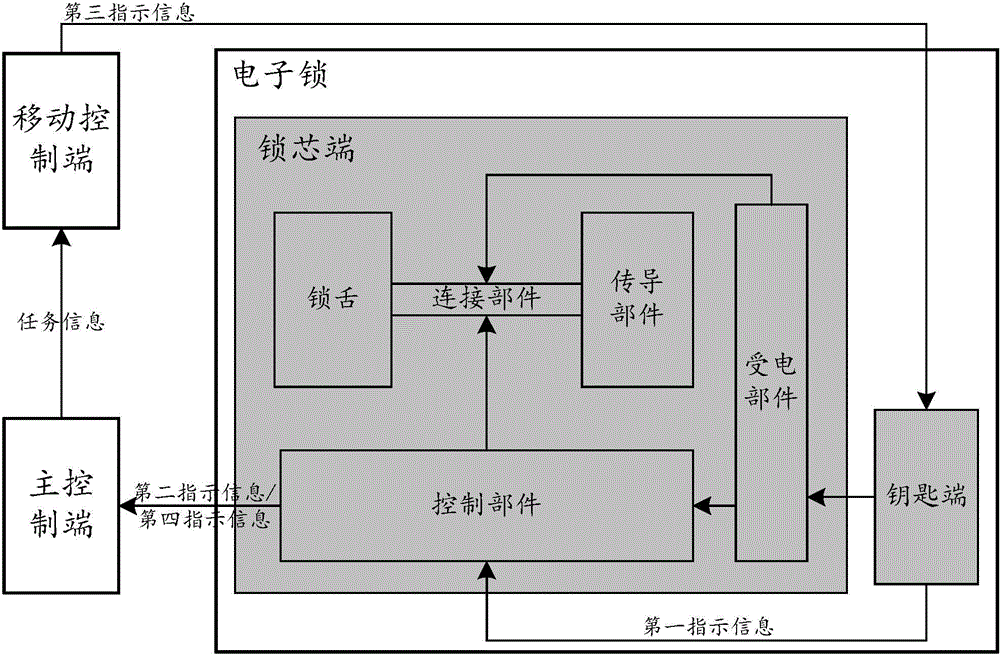
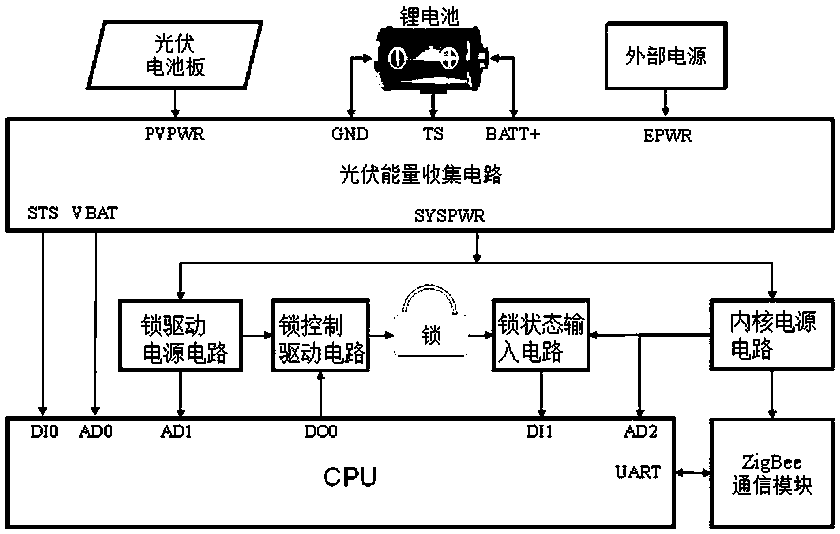
Method for controlling electronic lock, electronic lock, key terminal and lock cylinder terminal
InactiveCN105989648ANo maintenanceReduce operation and maintenance complexityNon-mechanical controlsIndividual entry/exit registersAuthorizationManagement system
The invention discloses a method for controlling an electronic lock, the electronic lock, a key terminal and a lock cylinder terminal. The method comprises the following steps that when the key terminal is inserted into the lock cylinder terminal, the key terminal supplies power to the lock cylinder terminal; when the key terminal receives a lock mark transmitted by a mobile control terminal, the key terminal reads a lock mark stored by the lock cylinder terminal; and if it is determined that the transmitted lock mark is identical to the read lock mark, the key terminal informs the lock cylinder terminal of unlocking and authorization. According to the invention, an internal power supply in a case is prevented from supplying power to the electronic lock, so considerable regular maintenance of the internal power supply in the case is avoided, and complexity in operation and maintenance of a lock management system is reduced; and thus, operation and maintenance cost for a communication network is decreased.
Owner:ZTE CORP +1
Intelligent lock system and control method thereof
Owner:NANJING FORESTRY UNIV
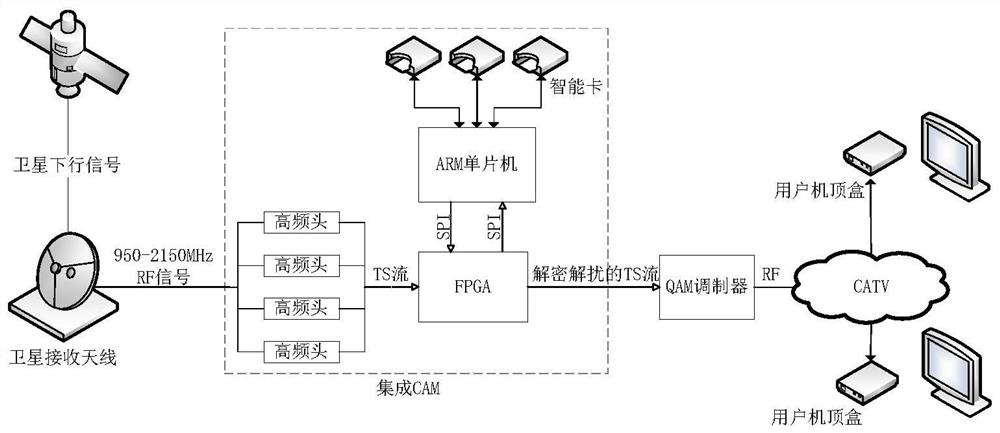
System and method for processing multi-transponder program by integrating conditional access module
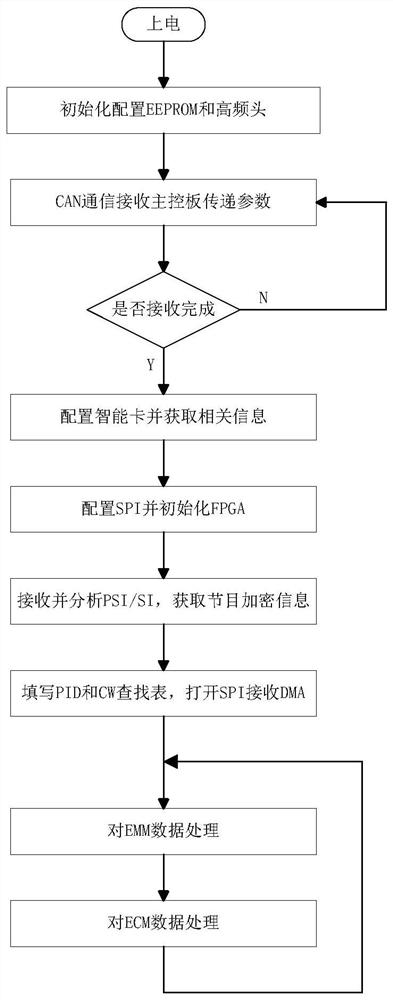
ActiveCN113727159AIncrease in sizeIncrease costSelective content distributionComputer architectureConditional access
Owner:XI AN JIAOTONG UNIV
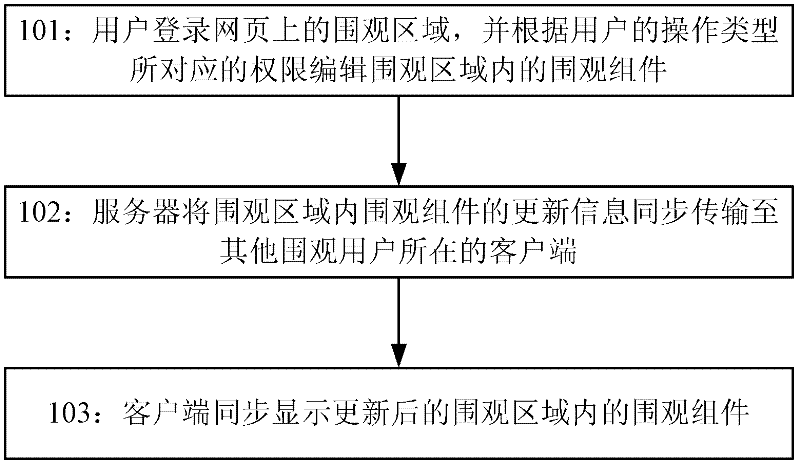
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap