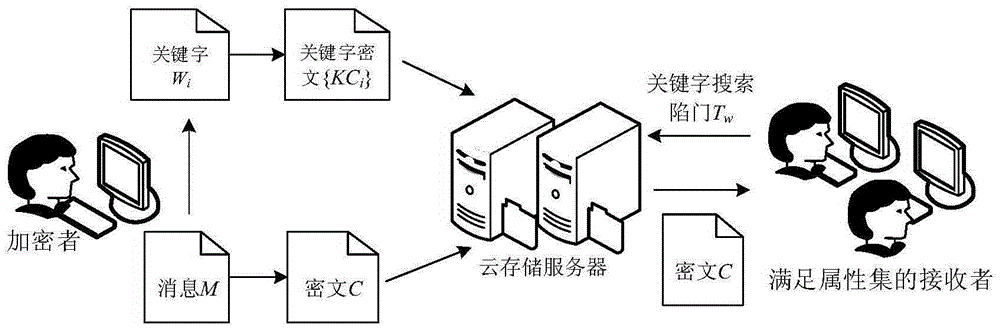
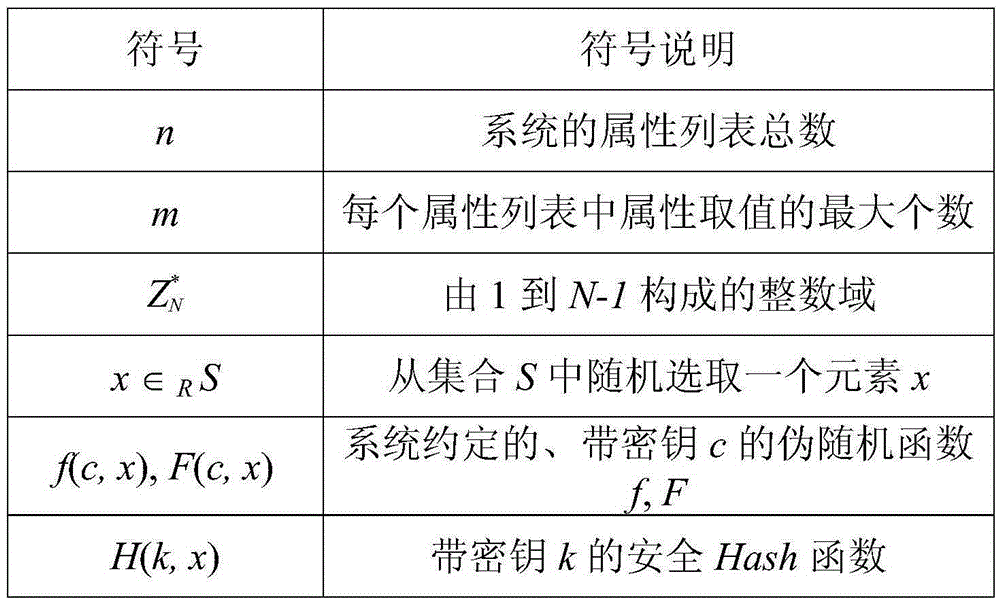
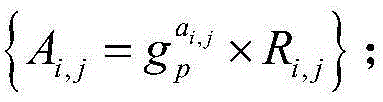Data anti-leakage protection method for cloud storage environment
A cloud storage and anti-leakage technology, applied in the field of information security, can solve problems such as unsatisfactory data leakage protection, retention, complex calculation process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] The present invention will be further described in detail below in conjunction with examples, but these examples should not be construed as limiting the present invention.
[0067] In step 2), select the security parameter λ shown below and the group generator g to be paired p , g r , Y and the parameters a, a′, g in the master key 2 , used to generate the public key PK L and master key MK:
[0068] λ=2 160
[0069] g p =[7809132837767772651573398790375403753462635003623019020044719272892058114280169545363627979672267814658276323812421368981173841647068218684446465465855241,7406643807957608305790166986115601778083675130710226906362591601230255575641360818656017098156052158125464120405691949210352493932149295057446052059530714]
[0070] g r =[4927806246087013323176344129922077121049761463643223330379875014379649792357196308368218031913996561191471542282649512239400384858148590491435071205008076,3959556302535778130756496571193265082800275622456294723604146789658349454
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap