Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product or document is not counterfeit.
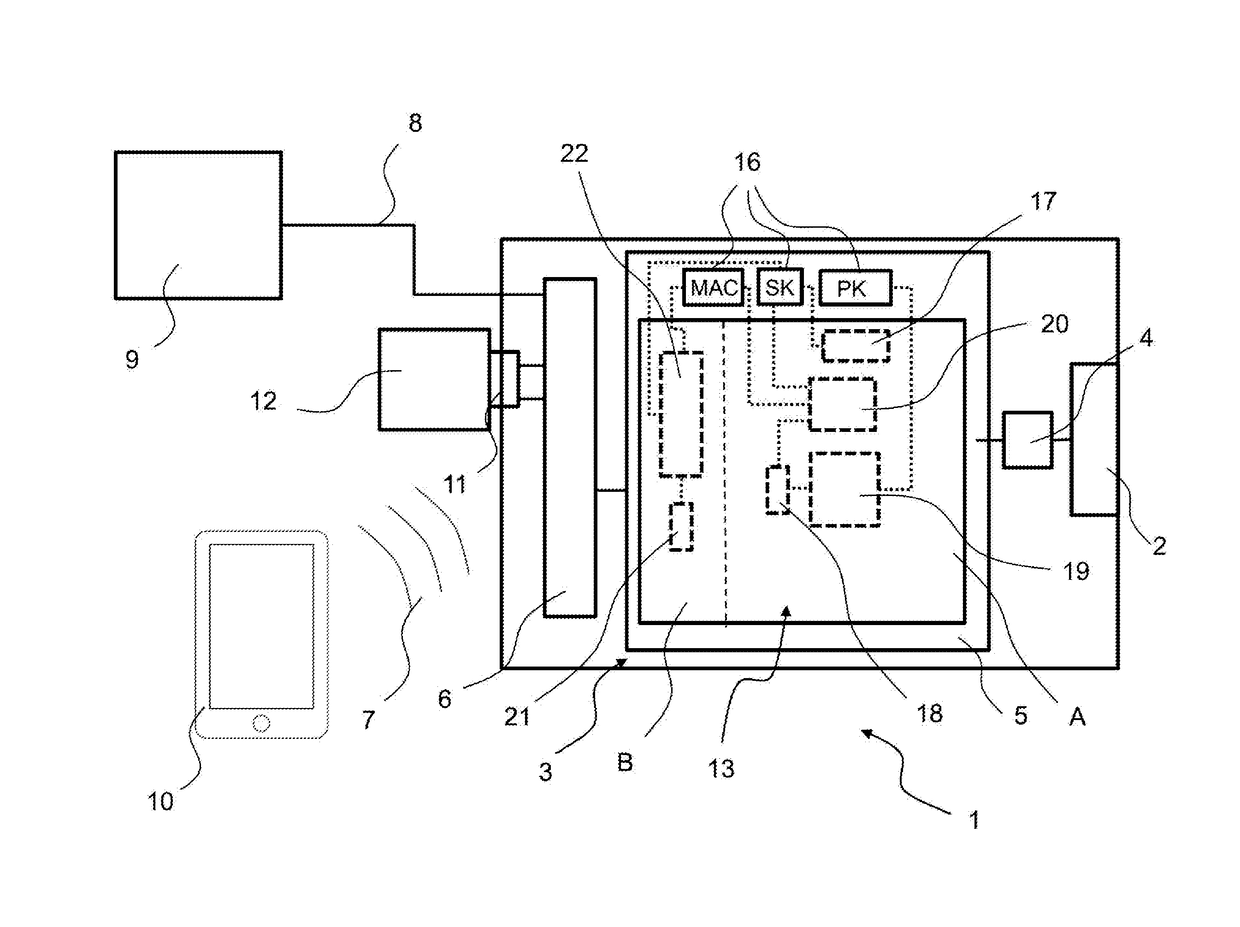
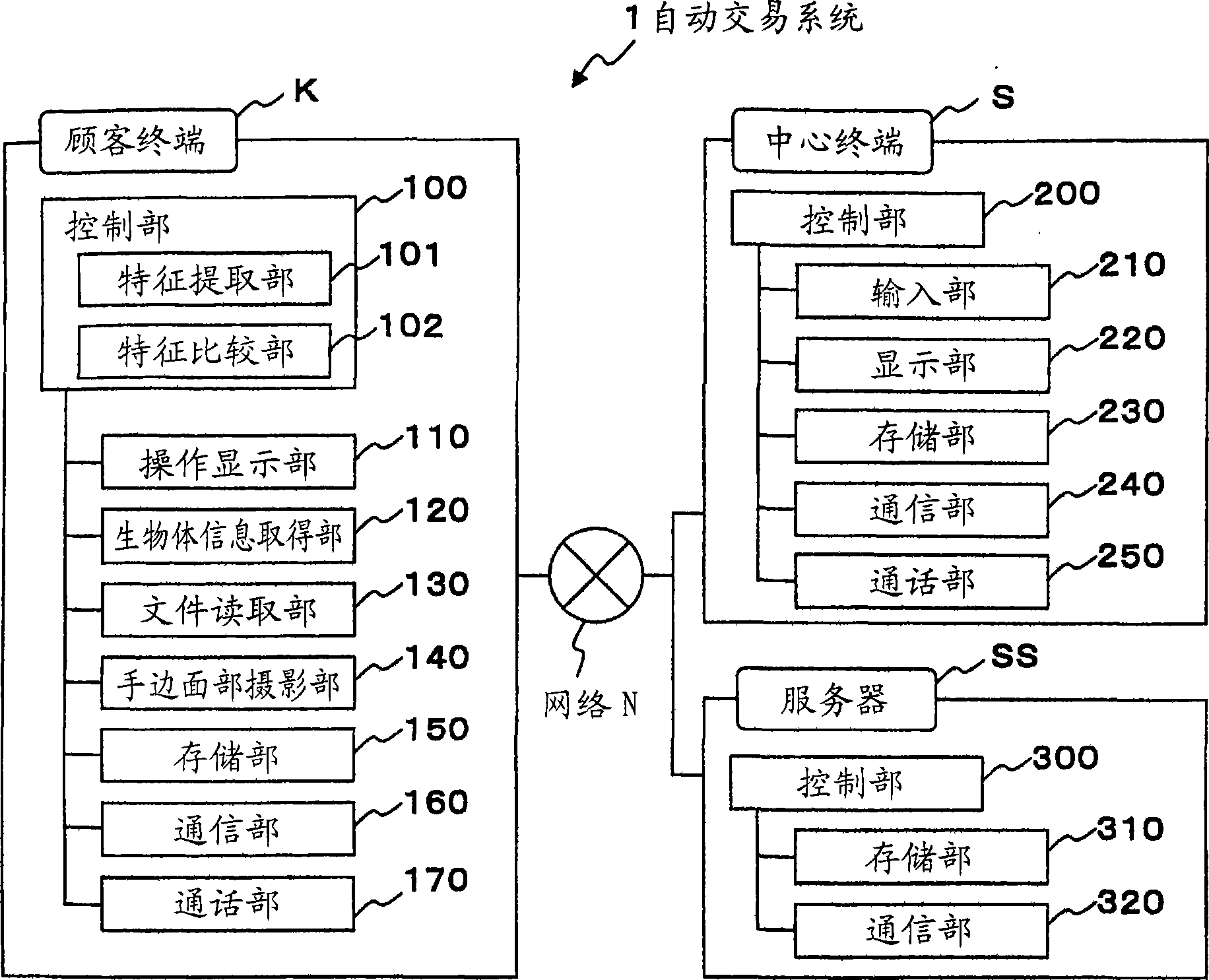
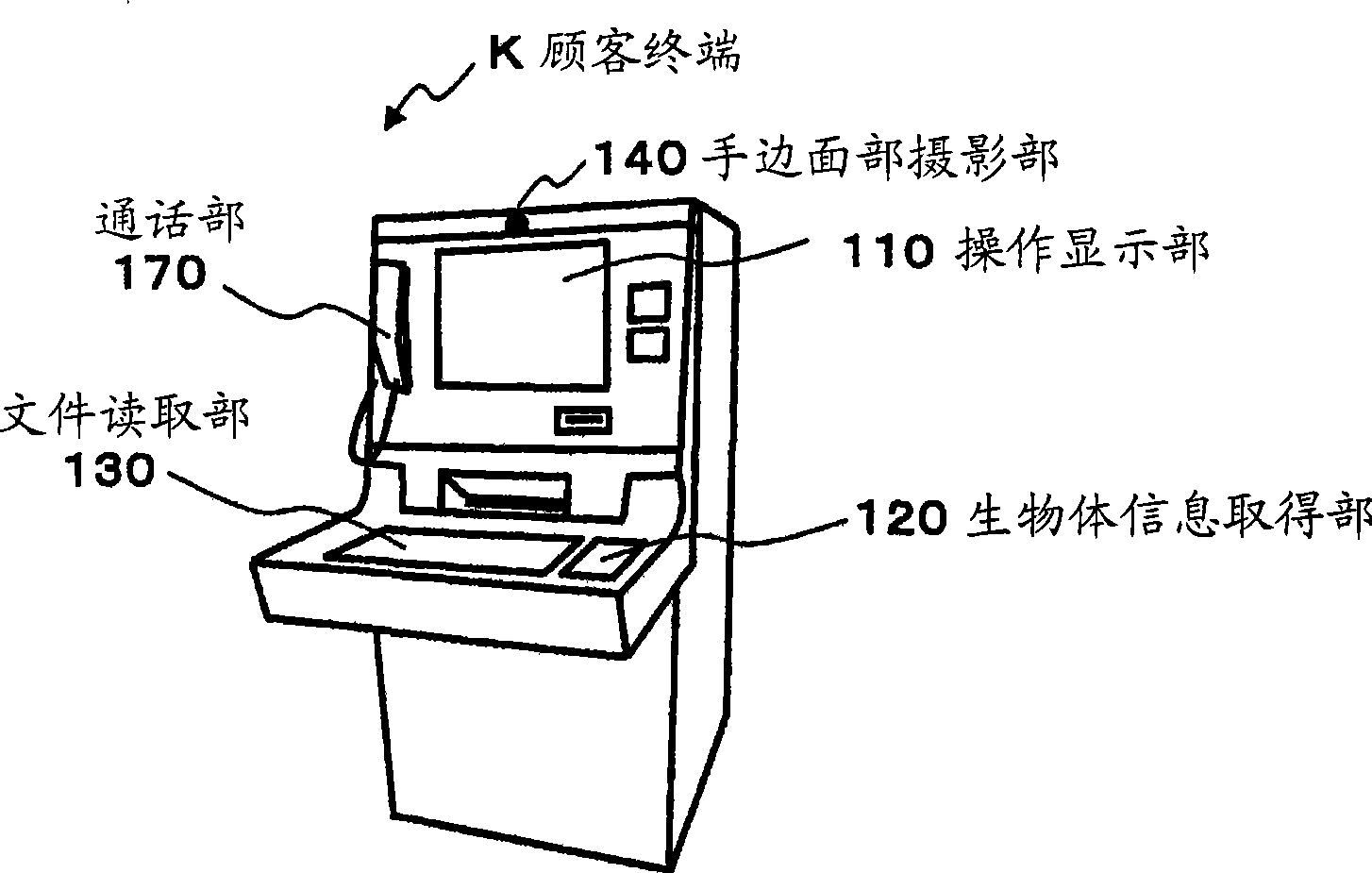
Room key based in-room player tracking
A disclosed authentication instrument is used to authorize various services at a hotel-casino complex, such as but not limited to in-room gaming, in-room sports wagering, room access, safe access, mini-bar access, Electronic Fund Transfers (EFT), player tracking services and in-room entertainment services (e.g., video games and movie channels). A smart card, an electronic token and a magnetic striped card are examples of hardware that may be used as authentication instruments. For in-room gaming, the authentication instrument may be used to authorize, in a secure and legal manner, in-room game play sessions on an entertainment terminal connected to a remote gaming machine.
Owner:IGT
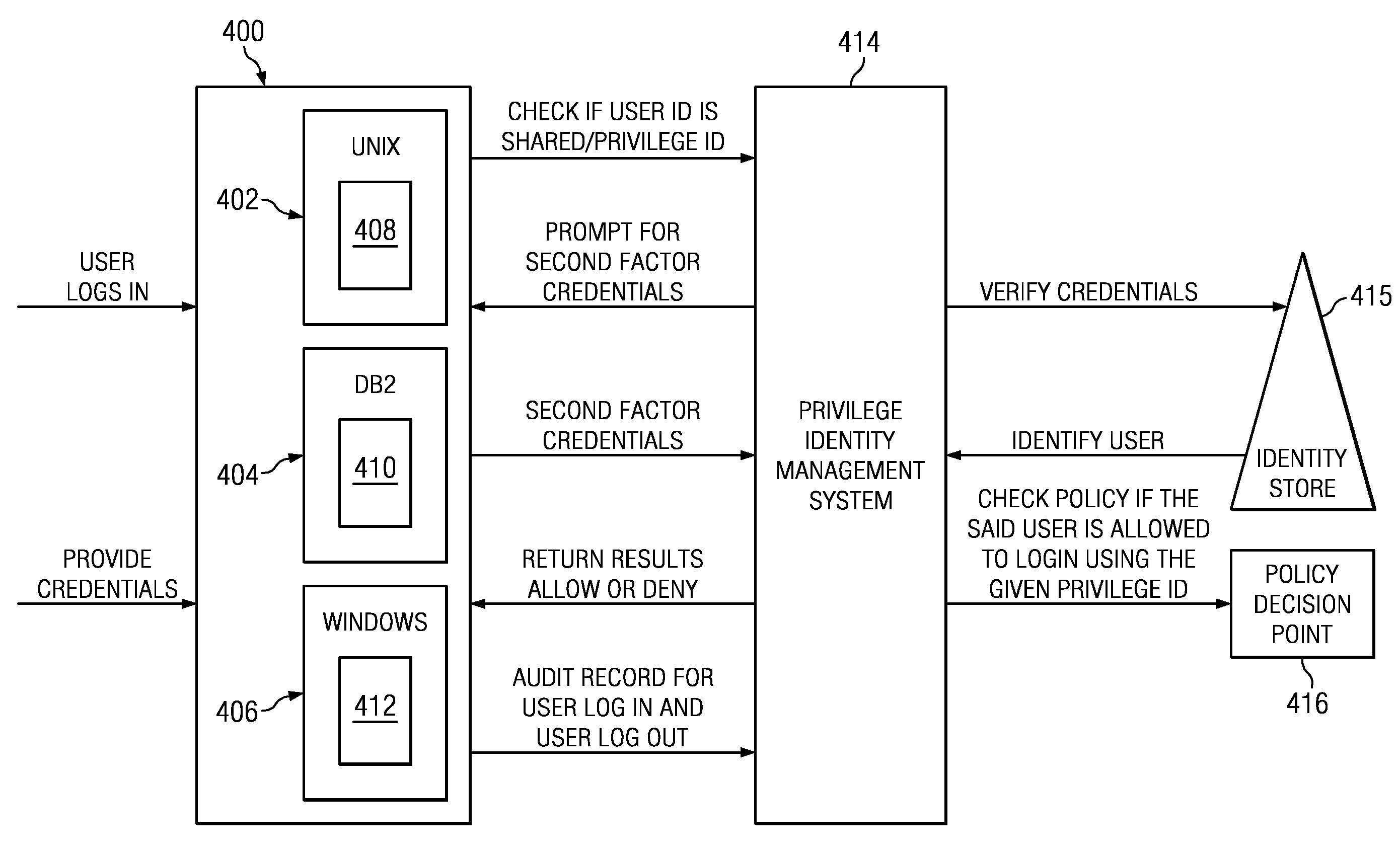
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
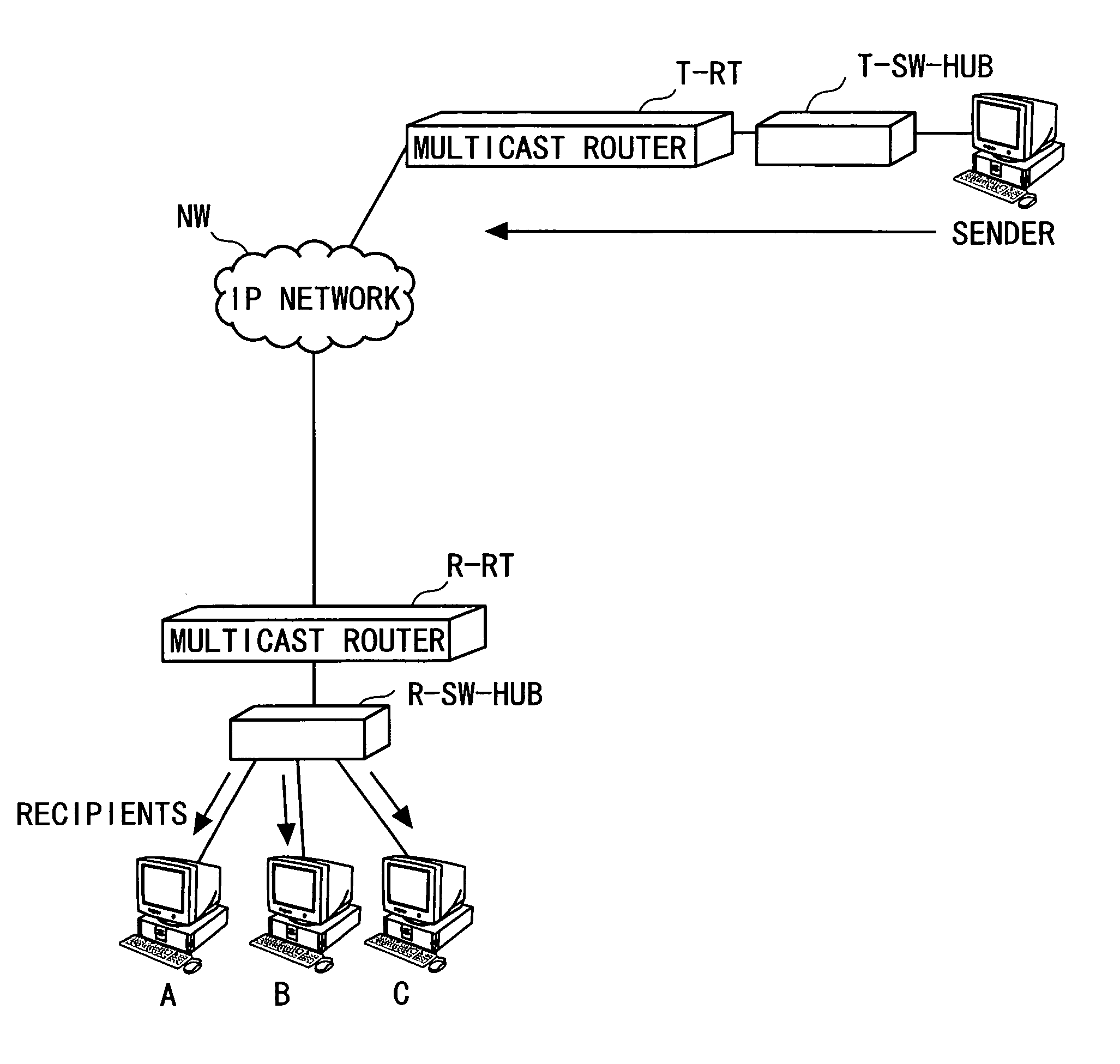
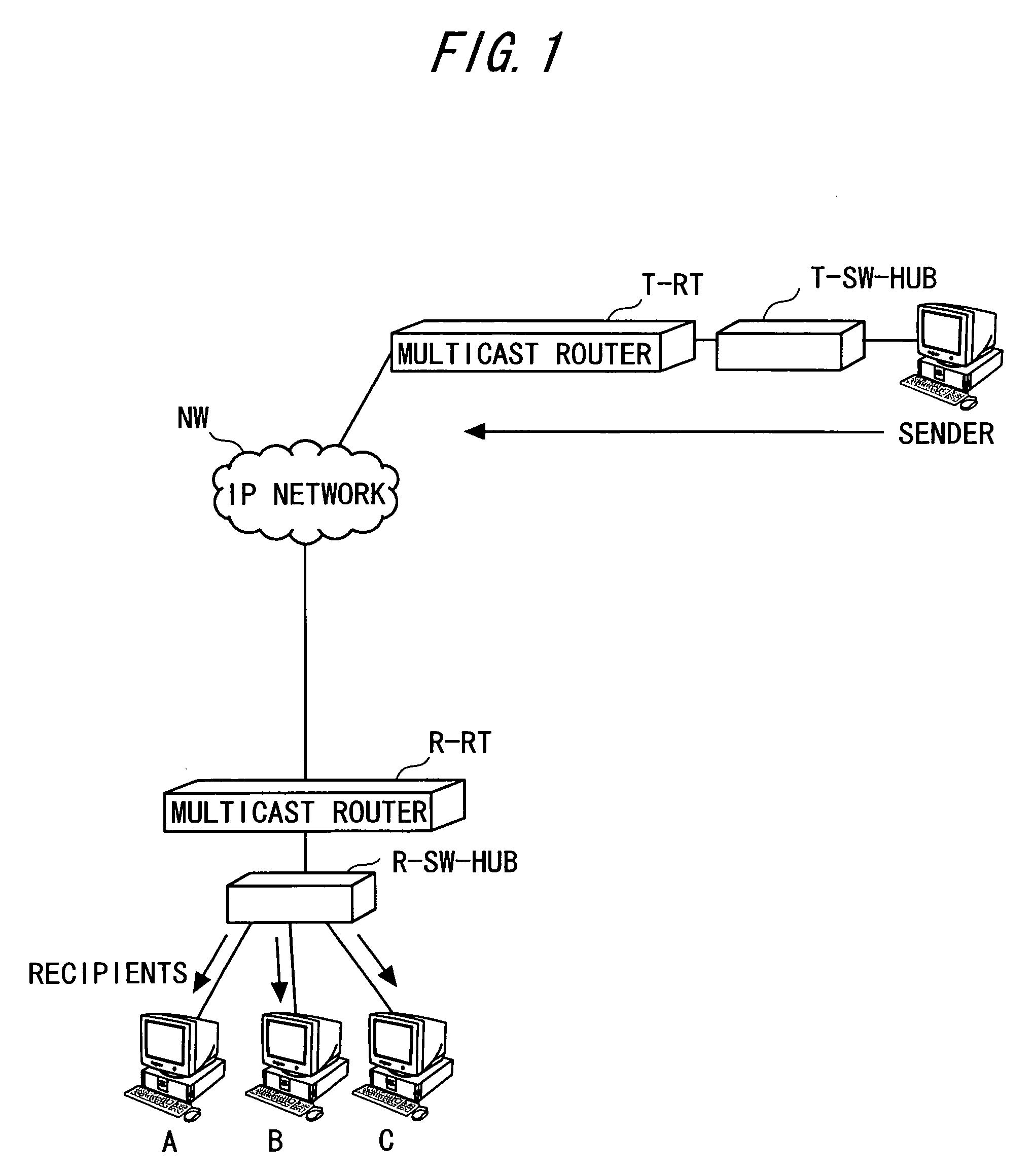
IP multicast communication system
InactiveUS20050111474A1Preventing and disturbing receptionSpecial service provision for substationTime-division multiplexCommunications systemIP multicast
Owner:FUJITSU LTD
System and method for conducting secure commercial order transactions
The inventive system and method enable secure remote commercial order transactions between customers and merchants. The inventive system and method ensure that customer entire confidential financial data (CFD) is never transmitted to the merchant by keeping that CFD proprietary to the customer's exiting financial service provider (FSP) with which the customer has established a financial account, and from which the merchant is authorized to receive payments. When an order is placed, the customer provides to the merchant a partial CFD (PCFD) sufficient, along with additional data, to identify the FSP to the merchant, and to identify the customer to the FSP. The merchant then provides the PCFD, along with at least partial order data, to the FSP, and order confirmation data (OCD) to the customer. Various embodiments of a novel order verification process are also provided that enable authorization, by the customer, of the order through contact between the customer and the FSP. In this manner, the complete CFD is kept absolutely secure as it never leaves the possession of the customer and the FSP. Optionally, the FSP is given the opportunity to offer additional services and / or products to the customer during order authentication, that are related or unrelated to the order. Advantageously, the inventive system and method function equally well for interactive electronic (e.g., online) orders, telephone orders, mobile commerce orders, facsimile orders, mail-order orders, and even in-person orders.
Owner:BYZ TEK
Apparatus and Method for Variable Authentication Requirements
ActiveUS20120239950A1Volume/mass flow measurementUser identity/authority verificationState dependentAuthentication
Owner:LENOVO PC INT
Controller regional network bus safety communication method, device and system
ActiveCN108965218AImprove securityReduce transmission overheadUser identity/authority verificationBus networksSecure communicationArea network
The present invention provides a controller regional network bus safety communication method, device and system which can effectively withstand attackers' eavesdropping, injection and attack replay. Agateway ECU (Electronic Control Unit) generates a random number and sends the random number to at least one CAN (Controller Area Network) bus ECU. A first CAN bus ECU obtains the random number sent by the gateway ECU and generates a first information authentication code based on secret keys of a first CAN identifier, the random number sent by the gateway ECU, a counting value of the first CAN identifier and data of a first CAN message. The first CAN bus ECU performs encryption operation based on the secret keys of the first CAN identifier and a second CAN message to obtain a first encryptionoperation result and perform equal length encryption operation for the first encryption operation result, the first information authentication code, the counting value of the first CAN identifier andthe data of the first CAN message so as to obtain the first CAN message with encryption authentication and send the first CAN message with encryption authentication.
Owner:HUAWEI TECH CO LTD
Method for updating a firmware component and device of measurement and control technology
ActiveUS20170293484A1The encryption method is simpleLess resourcesProgramme controlMemory architecture accessing/allocationEncryptionAuthentication
Owner:ENDRESSHAUSER CONDUCTA GMBHCO
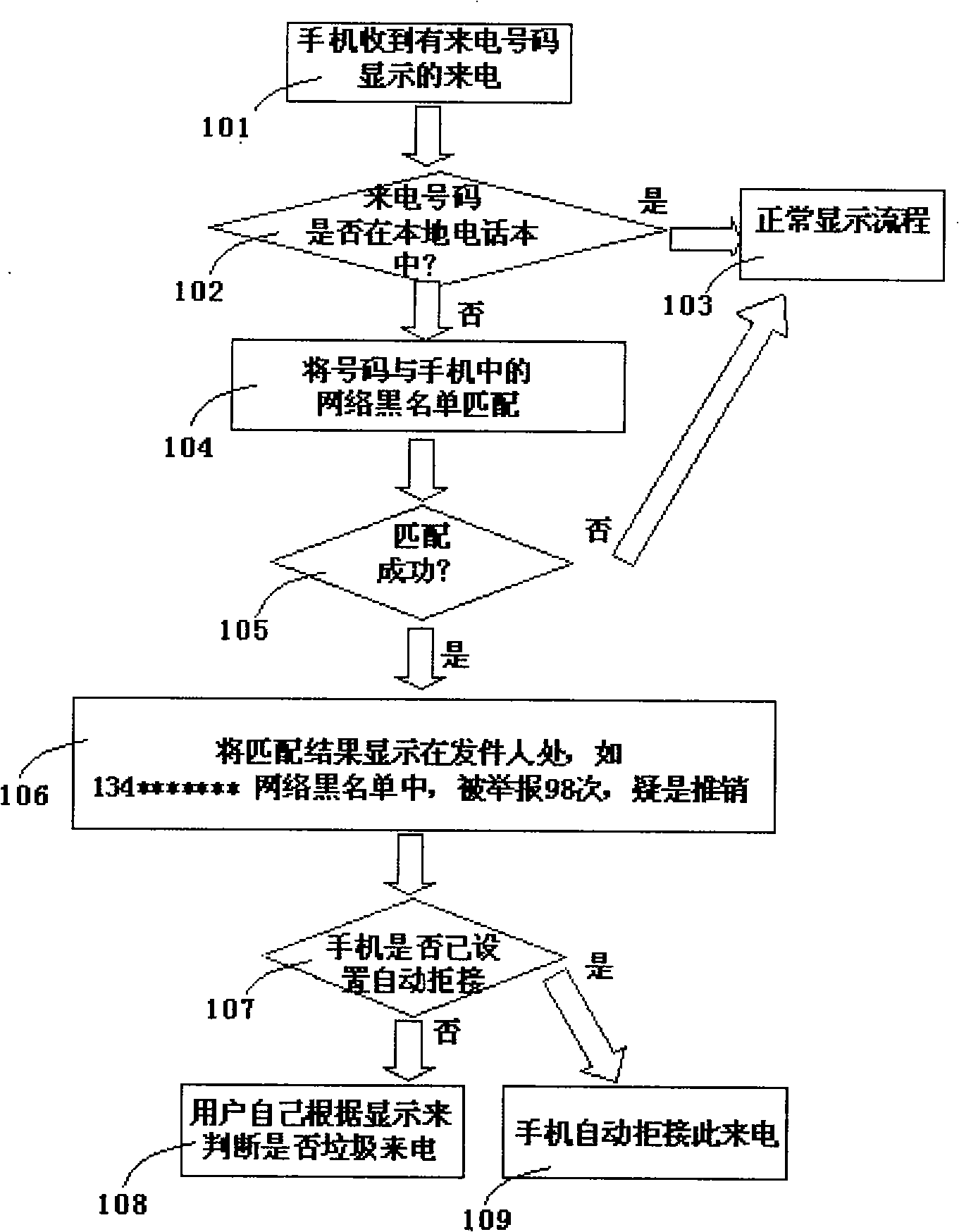
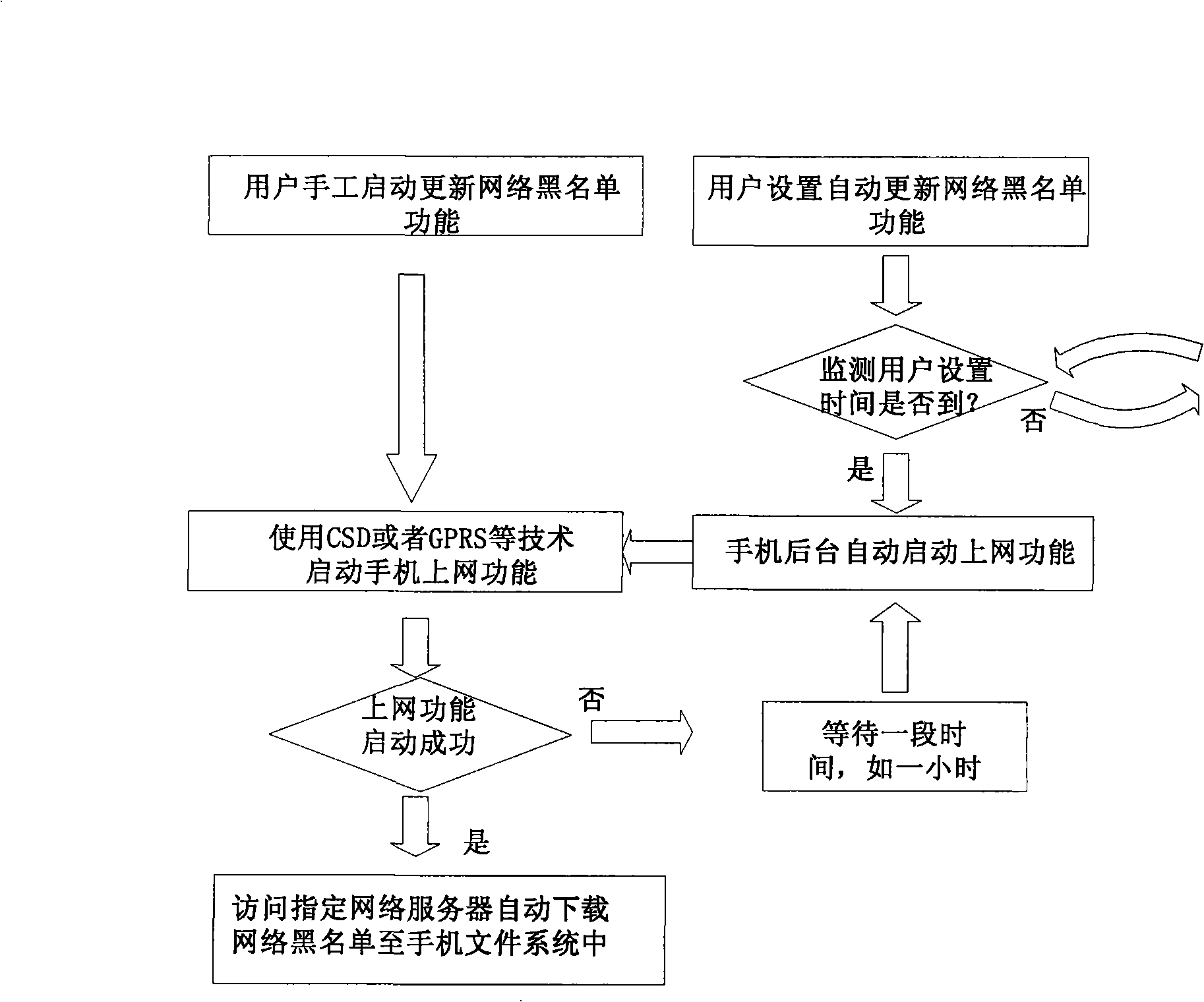
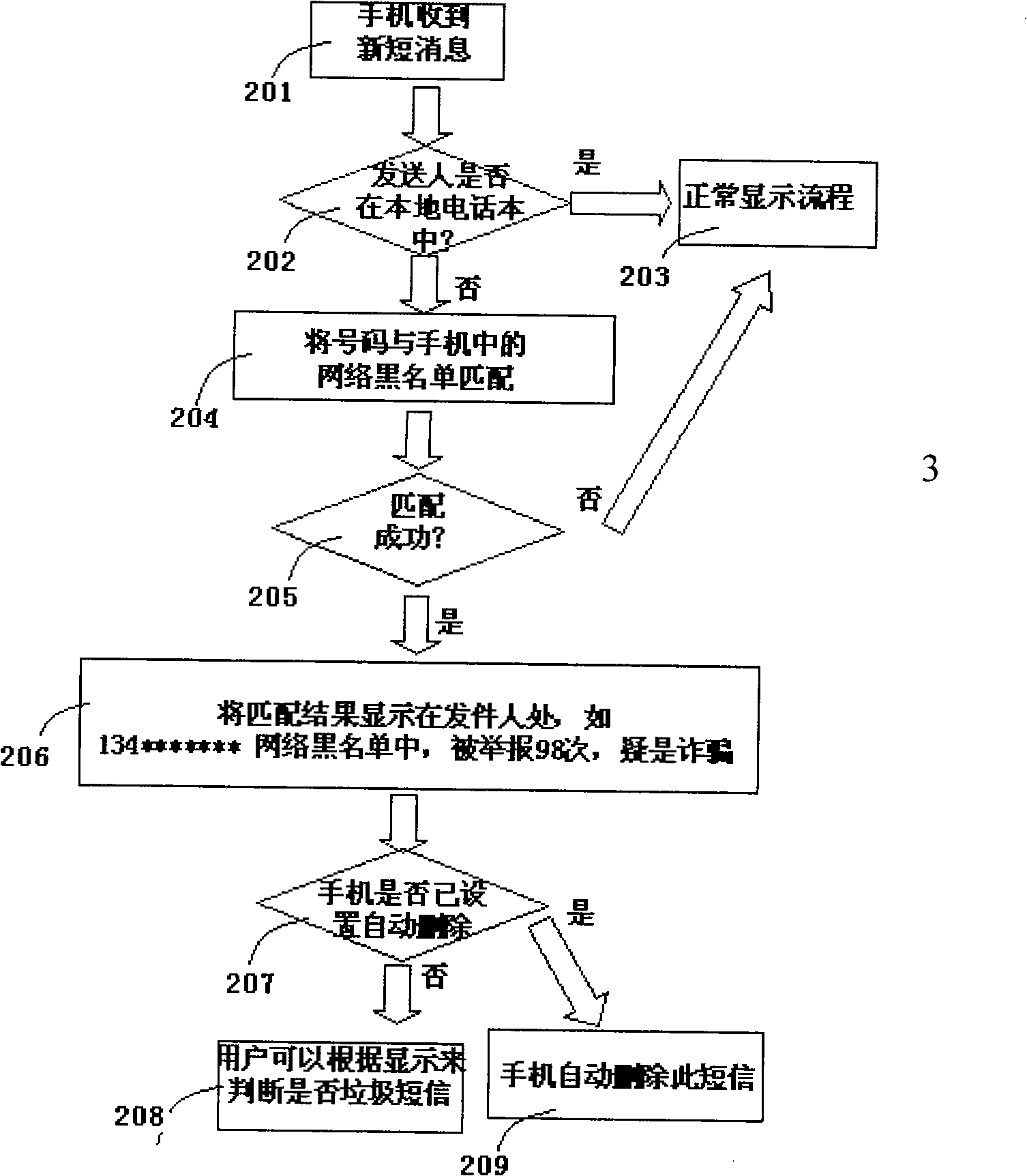
Method and communication terminal capable of automatically matching incoming call number or note number
ActiveCN101304552AAutomatic authenticationWith interceptionRadio/inductive link selection arrangementsBlack listAuthentication
Owner:JRD COMM (SHENZHEN) LTD
Shop apparatus, purchaser apparatus, purchaser identity proving apparatus, and purchaser identity verifying apparatus
ActiveUS20080177636A1Eliminate unlinkabilityEliminate inconvenienceComputer security arrangementsBuying/selling/leasing transactionsZero-knowledge proofAuthentication
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
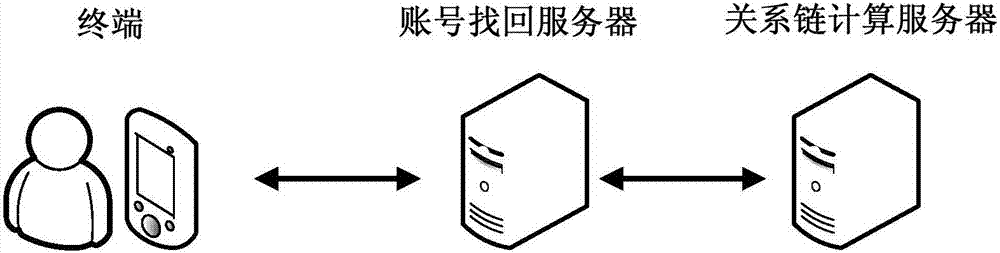
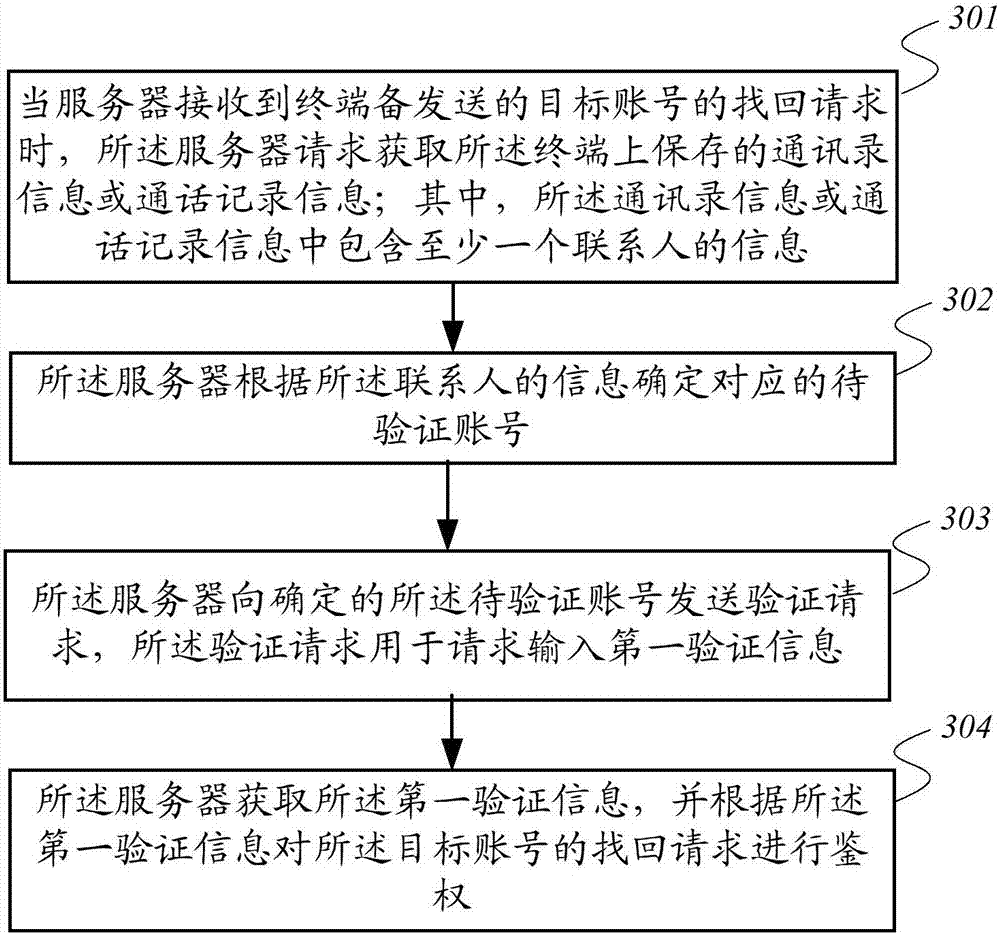
Account authentication method and server
Owner:TENCENT TECH (SHENZHEN) CO LTD
TDD Uplink and Downlink Configuration Updating Method and Apparatus and TDD Re-Configuration Information Notification Method and Apparatus
InactiveUS20150208382A1Avoid delayAvoid resourcesTime-division multiplexRadio transmissionComputer hardwareEncryption
A method for encrypting a terminal with a subscriber identity card includes: a terminal storing the unique identity number of a subscriber identity card; the terminal detecting an operation of a user and authenticating a current user according to authentication conditions set by the user. Authenticating the current subscriber refers to that the terminal reads the unique identity number of the current subscriber identity card, and compares the read unique identity number of current subscriber identity card with the stored unique identity number of subscriber identity card; if they are the same, the terminal is controlled to enter a normal working state; and if they are different, the terminal locks by itself or disables the access of current user. The present document encrypts a mobile terminal with a subscriber identity card, so as to make the encryption technique of the terminal more secure and reliable, and improve the user experience.
Owner:ZTE CORP
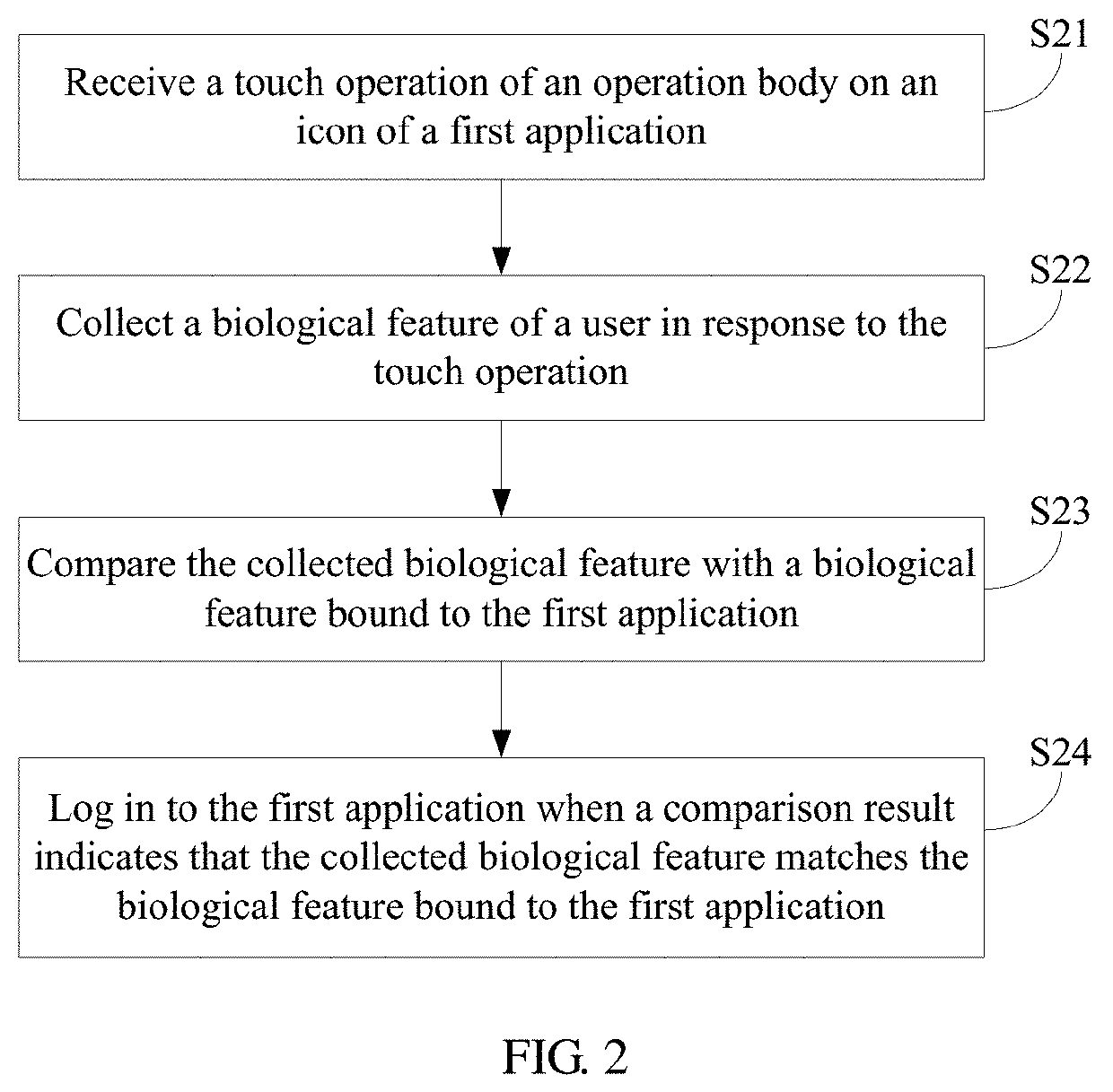
Authentication Method and Electronic Device
ActiveUS20190354661A1Complicated operationInternal/peripheral component protectionDigital data authenticationHuman–computer interactionAuthentication
Owner:HUAWEI TECH CO LTD
Authentication control method for application client, server and terminals
Owner:珠海市魅族通讯设备有限公司
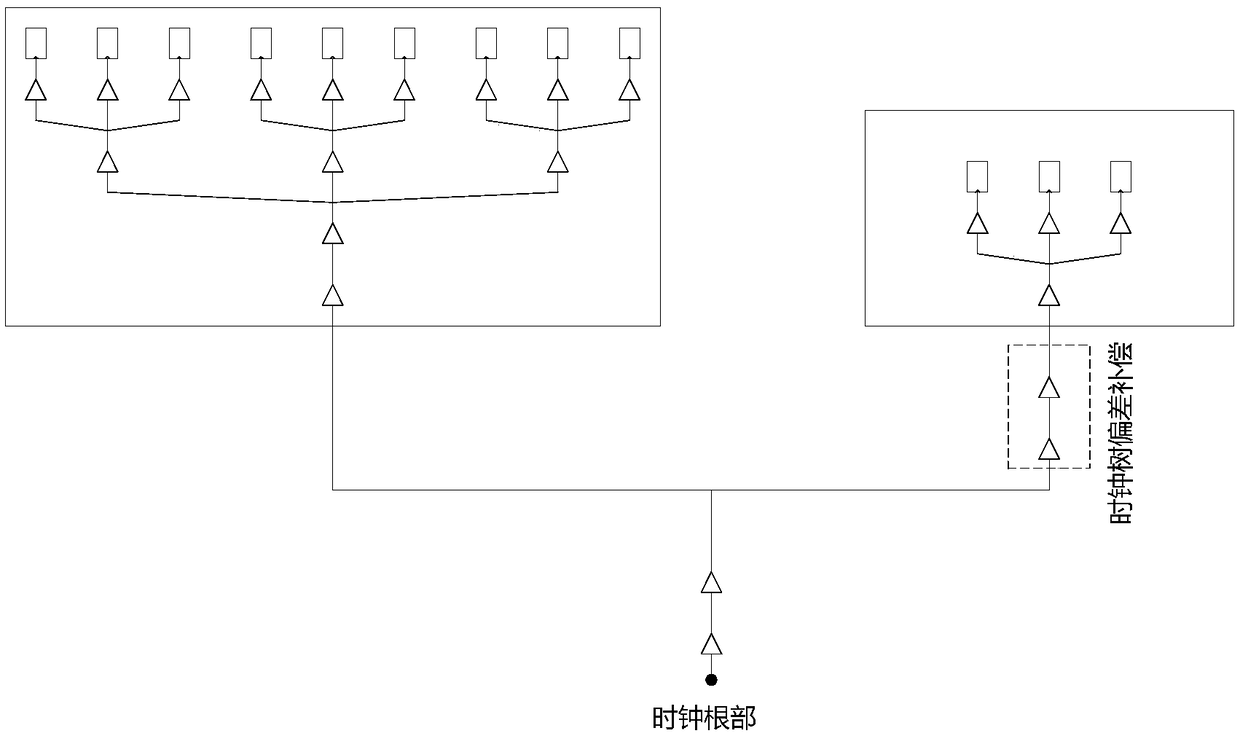
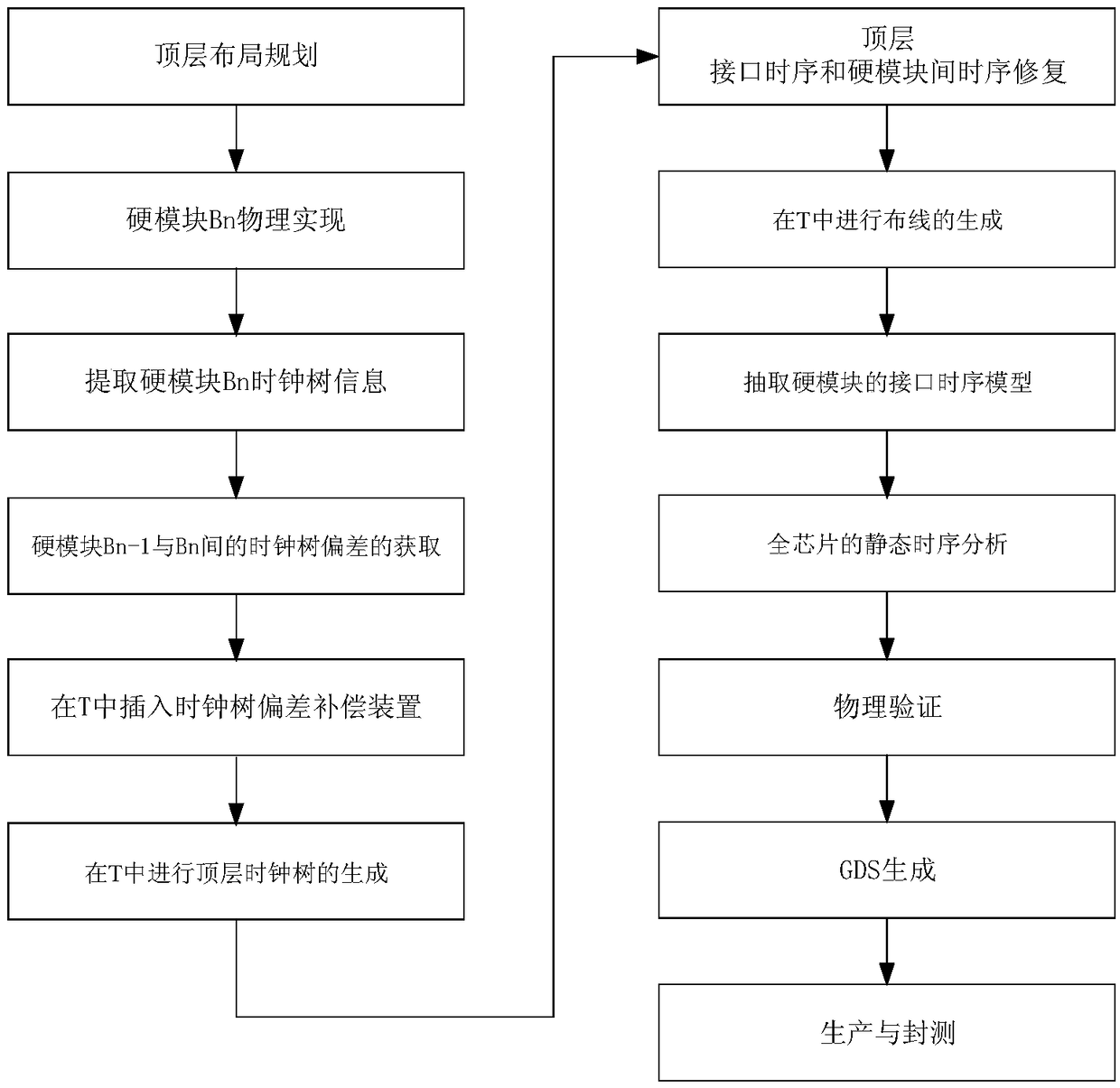
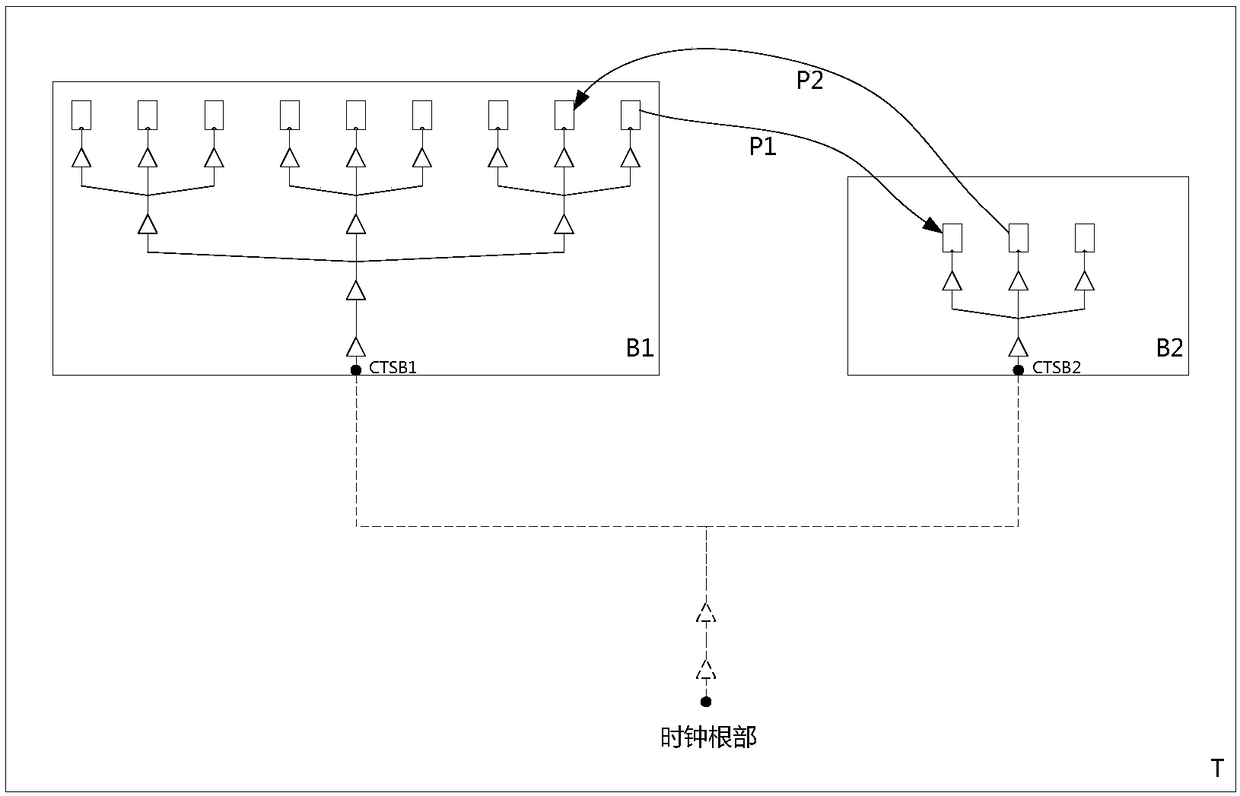
Clock-tree layout flow method and clock-tree deviation compensation device in integrate circuit
ActiveCN109376467AReduce hierarchyReduce difficultySpecial data processing applicationsStatic timing analysisPhysical verification
Owner:WUHAN INSTITUTE OF TECHNOLOGY
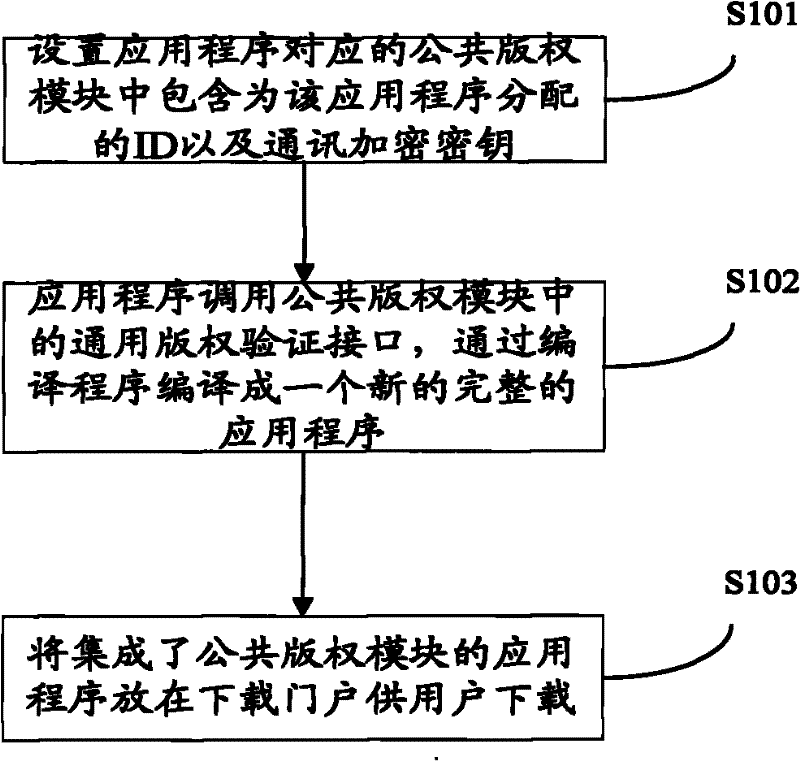
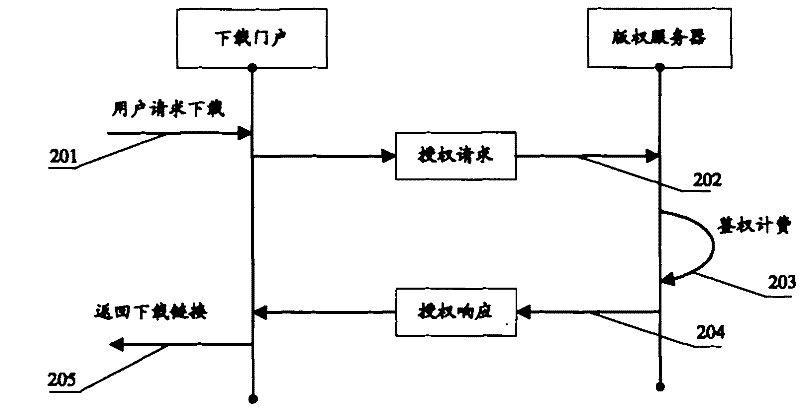
Application program copyright protection method and digital copyright protection system
ActiveCN102194077ASelf-protectiveImprove your own securityUser identity/authority verificationProgram/content distribution protectionDependabilityProtection system
Owner:ZTE CORP
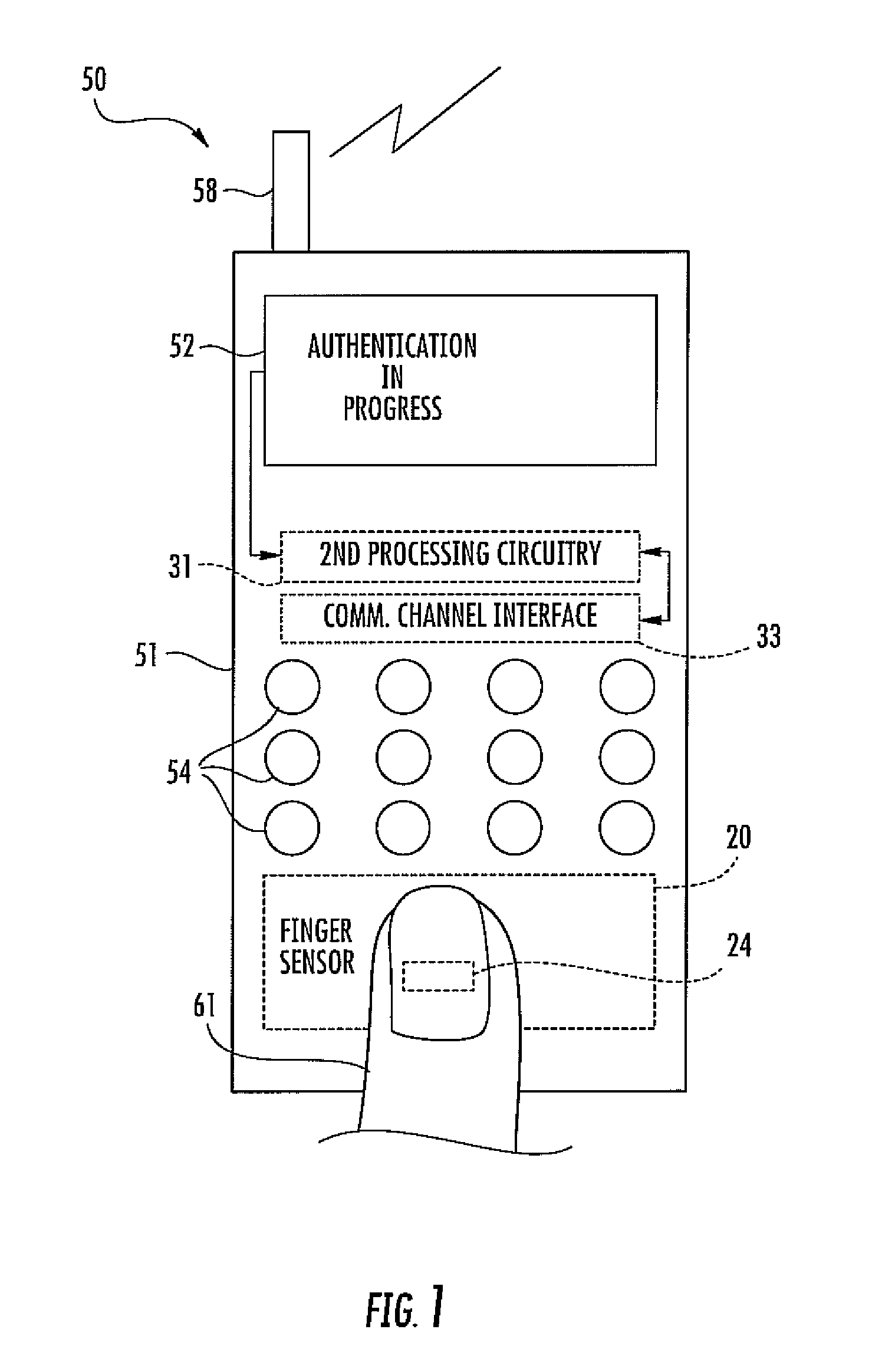
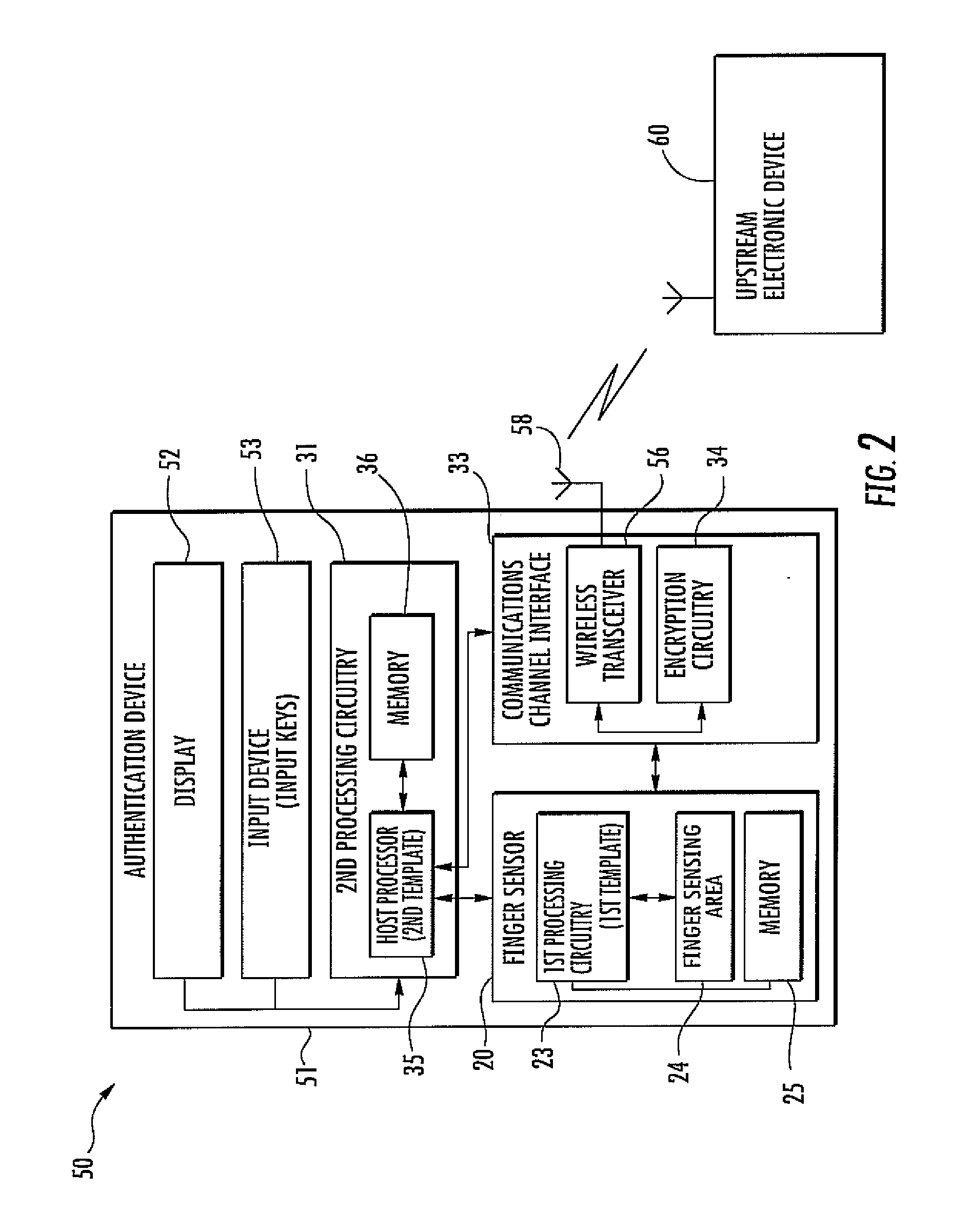
Authentication device including template validation and related methods
ActiveUS20130121542A1Less processing intensiveDigital data authenticationMatching and classificationTemplate basedComputer science
Owner:APPLE INC
Automatic traction apparatus and automatic traction system
InactiveCN101499197APrevent wrongdoingComplete banking machinesImage analysisTraction systemFeature extraction
Owner:OKI ELECTRIC IND CO LTD
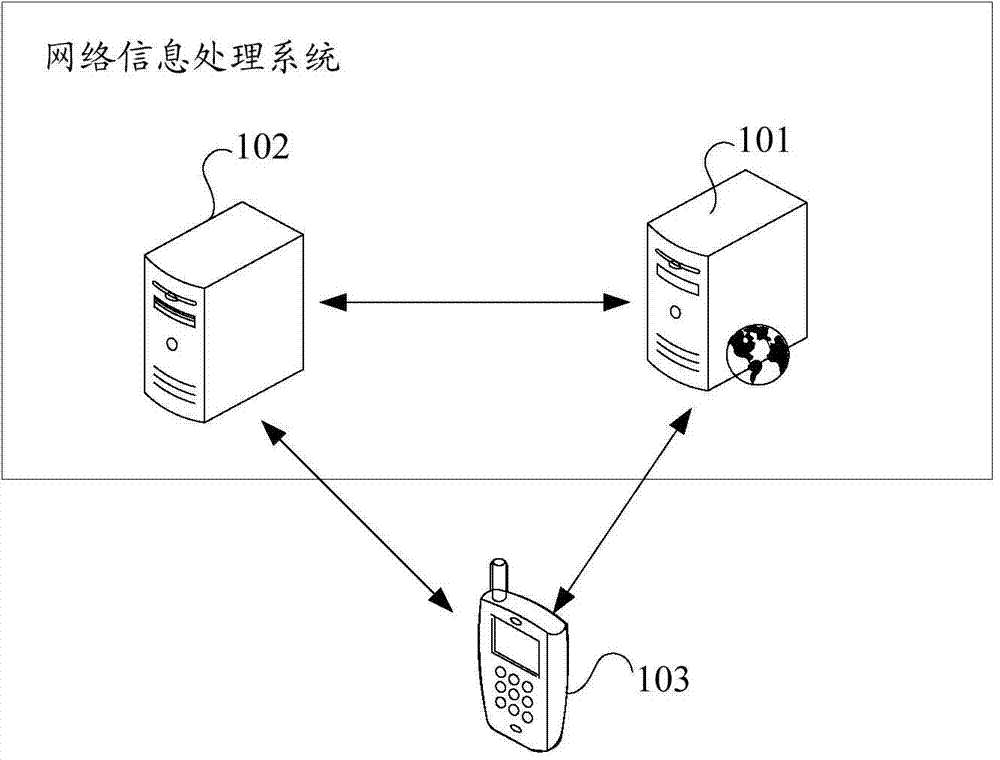
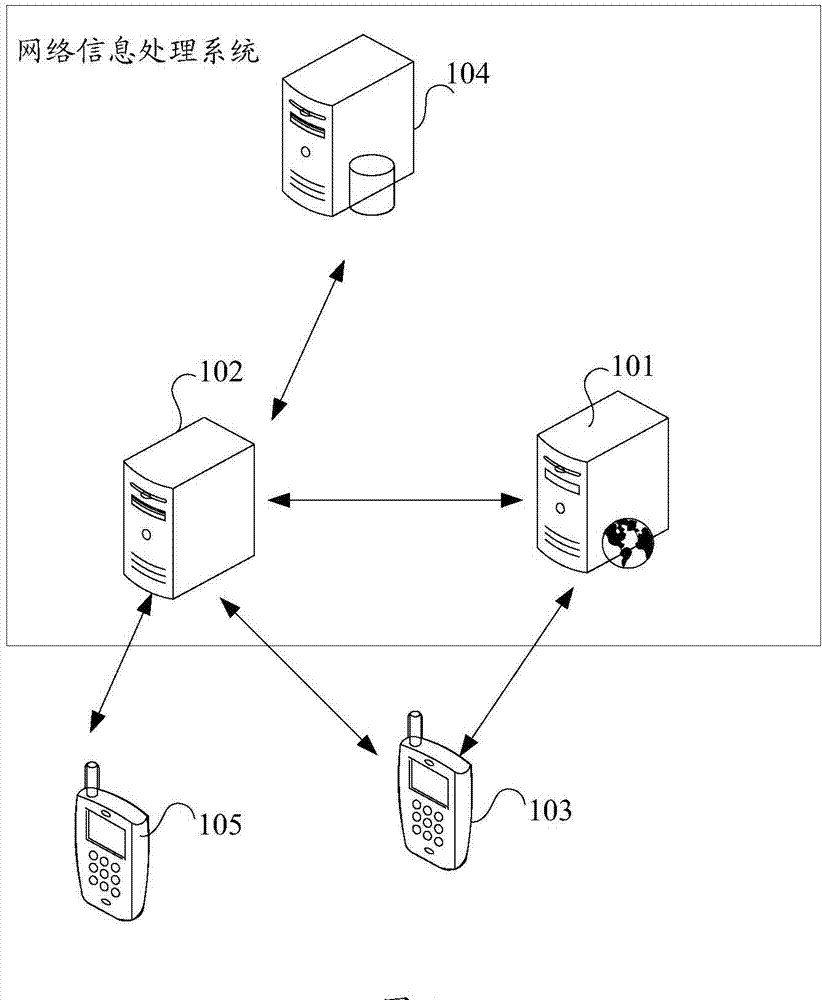
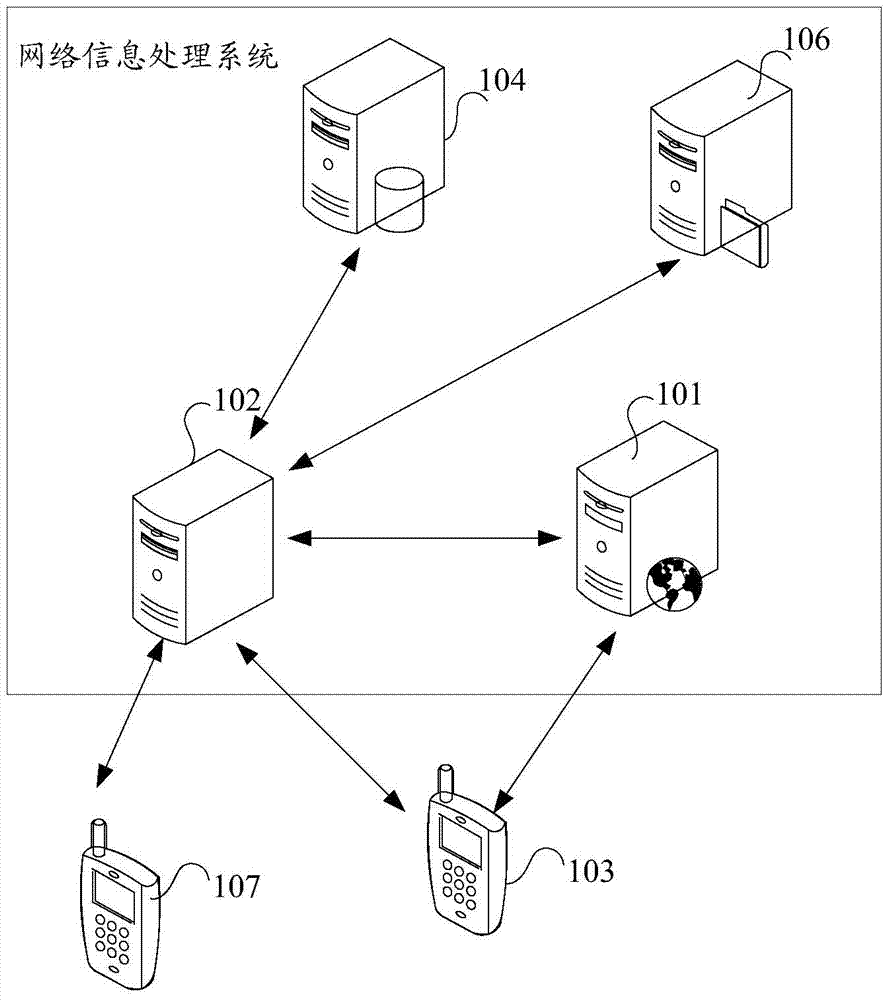
Network information processing system and method
InactiveCN103944923AEfficient acquisitionSave resourcesData switching networksInformation processingDistributed computing
Owner:沈文策
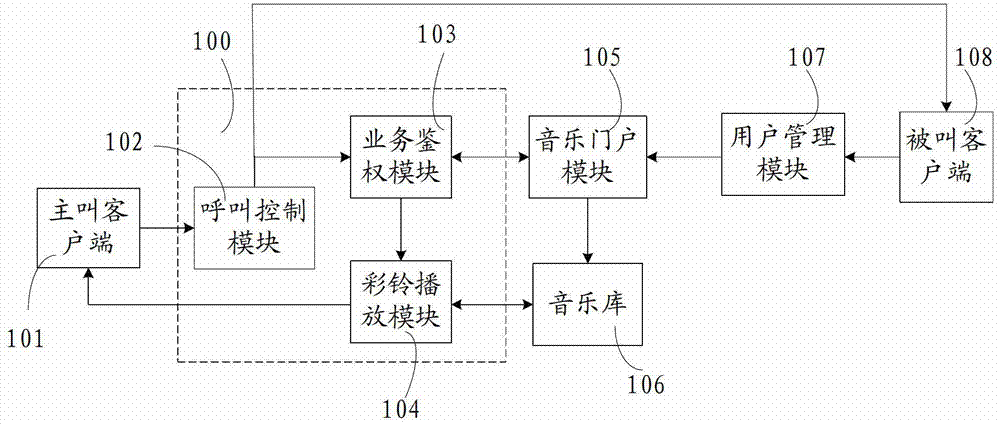
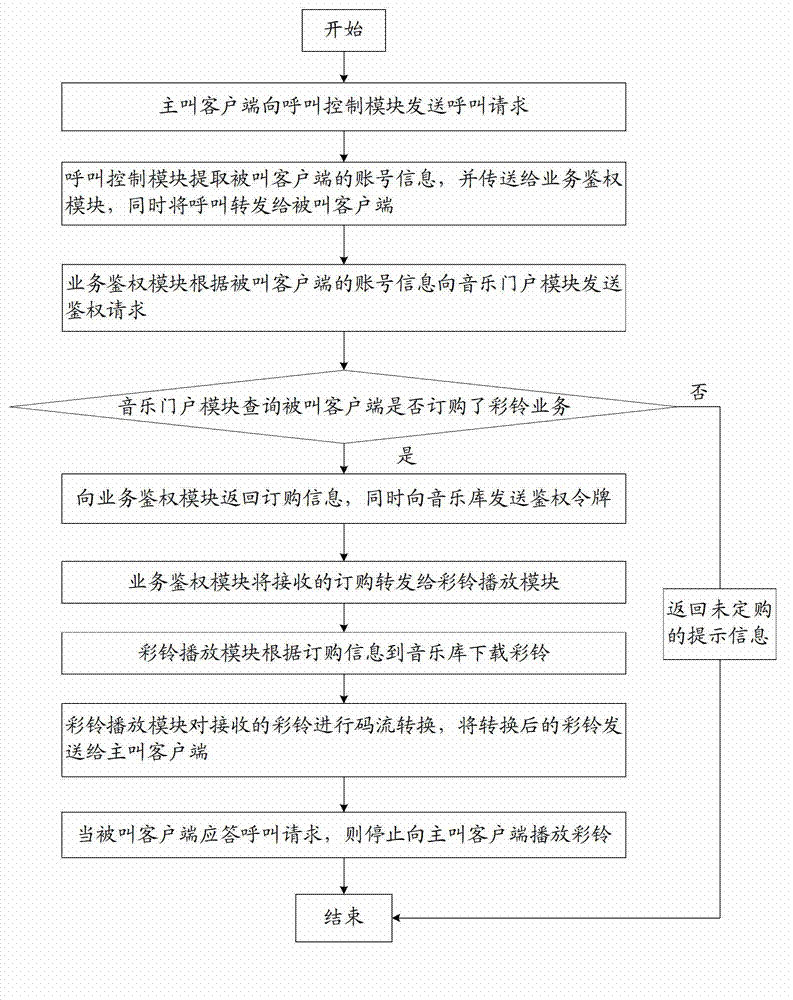
Polyphonic ringtone business system and implementation method based on converged communication
ActiveCN103037113ALow costProtection of rights and interestsSpecial service for subscribersWireless commuication servicesPersonalizationPassword
Owner:北京思特奇信息技术股份有限公司
Method for improving on-line speed of user and access equipment for broadband to get access to server remotely
InactiveCN104767765AImprove online speedShorten the timeUser identity/authority verificationIp addressBroadband
The invention discloses a method for improving on-line speed of a user and access equipment for broadband to get access to a server remotely. The method comprises the steps that BRAS access equipment applies an IP address from a DHCP server by simulating a pseudo-user in advance, and an IP address pool is formed; a dynamic host configuration protocol (DHCP) discovery message for requesting being online carrying an MAC address of a real user from the real user is received; identity authentication is conducted to the real user; if the real user passes through the identity authentication, then an unallocated IP address is selected from the IP address pool to the real user, the selected IP address is set to be in an allocated state, the corresponding relation between the MAC address of the real user and the IP address allocated to the real user is recorded, the IP address allocated to the real user is packaged in a DHCP-ACK message for being transmitted to the real user, and the real user is made to be on-line.
Owner:NEW H3C TECH CO LTD
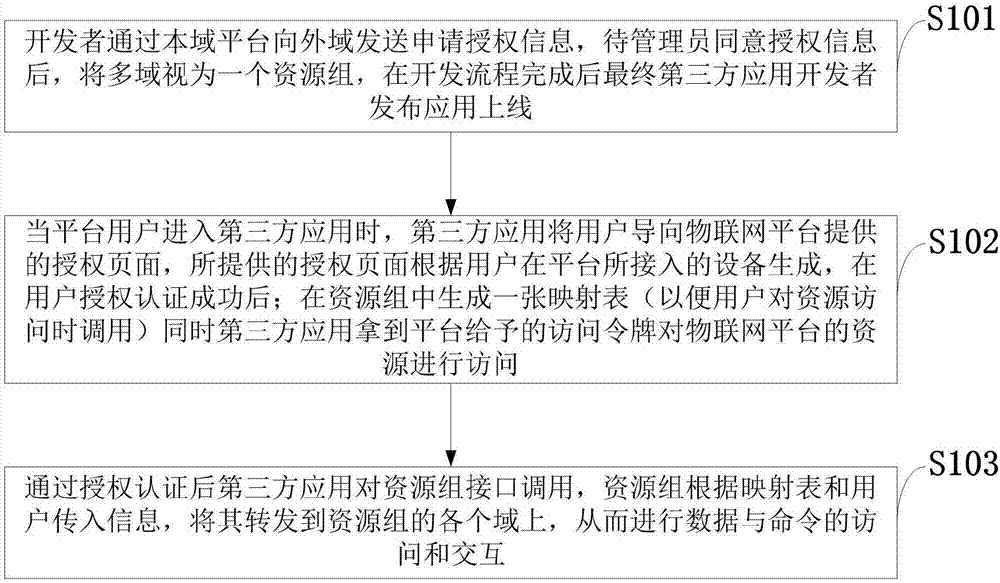
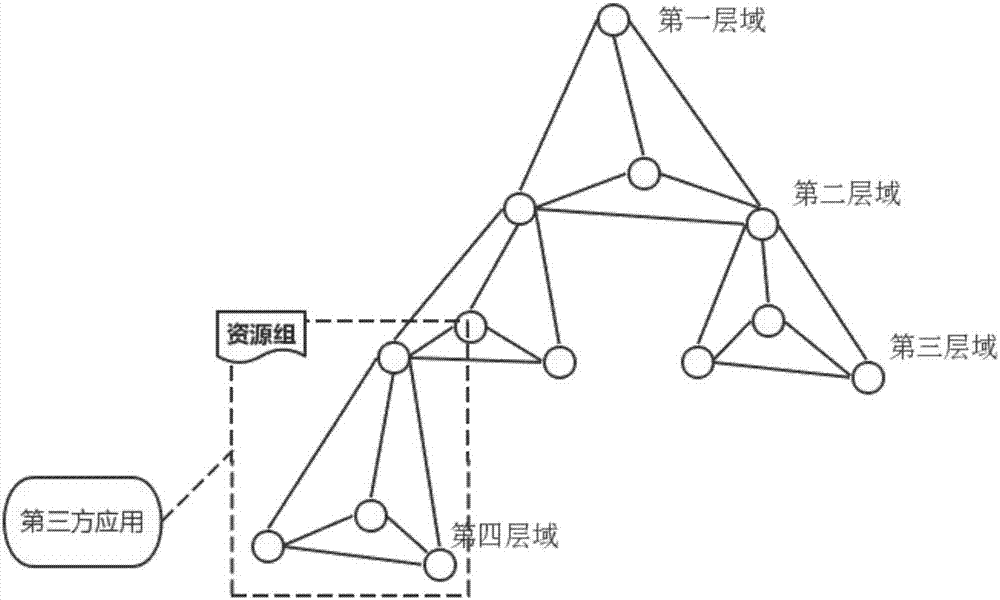
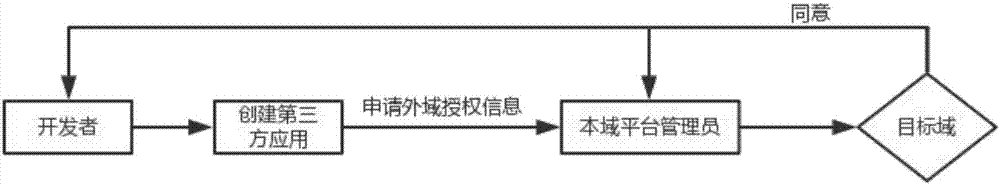
Third-party application authorization and authentication method based on multi-domain collaborative architecture
ActiveCN107018128ASafe and reliable authorized accessTroubleshoot authentication issuesTransmissionThird partySoftware engineering
Owner:陕西沃傲信息科技有限公司
Community-based visitor management method, community server and storage medium
InactiveCN110491007AImprove convenienceImprove securityIndividual entry/exit registersCommunity basedAuthentication
The invention discloses a community-based visitor management method, a community server, and a storage medium. The community-based visitor management method includes a step of receiving visitor information sent by a gate machine, a step of determining whether a visitor is an invited visitor or not based on the visitor information, a step of sending an authentication instruction to the gate machineif not such that the gate machine obtains a visitor request of the visitor according to the authentication instruction, wherein the visitor request comprises information of a visited owner, and a step of sending the visitor request according to the information of the visited owner. In the above manner, the invention can effectively improve the convenience and security of allowing the visitor to enter a community.
Owner:EVERGRANDE SMART TECH CO LTD
Digital money mining system and method based on biometric ID authentication
InactiveCN109034799AAuthentication is reliableDigital data authenticationProtocol authorisationDigital currencyIdentity recognition
Owner:晓看科技(上海)有限公司
Physical no-cloning technology based RFID card type intelligent door lock
InactiveCN108921995AImprove protectionImprove securityUser identity/authority verificationInternal/peripheral component protectionPasswordThe Internet
The invention discloses a physical no-cloning technology based RFID card type intelligent door lock. The physical no-cloning technology based RFID card type intelligent door lock comprises RFID cards,a door lock and a database, wherein the database is arranged on a background server; while ID which corresponds to the RFID cards is received, data is compared with data in the database through an internet; the database is used for storing ID which corresponds to each RFID card; a door lock inner chip comprises a PUF circuit; the RFID chip comprises an RFID module which is used for generating motivation; after receiving the motivation, the PUF circuit generates a corresponding secret key; and the database provides a matching source and is compared with the secret key generated by the PUF circuit, so that authentication is realized, and therefore, unlocking is performed based on a door lock password authentication mode. The PUF circuit can resist probe attack and physical attack, and is not stored with the secret key information, so that other people cannot read a chip secret key through a probe and the like to steal inner information, and therefore, safety of the door lock is greatlyimproved.
Owner:HOHAI UNIV CHANGZHOU
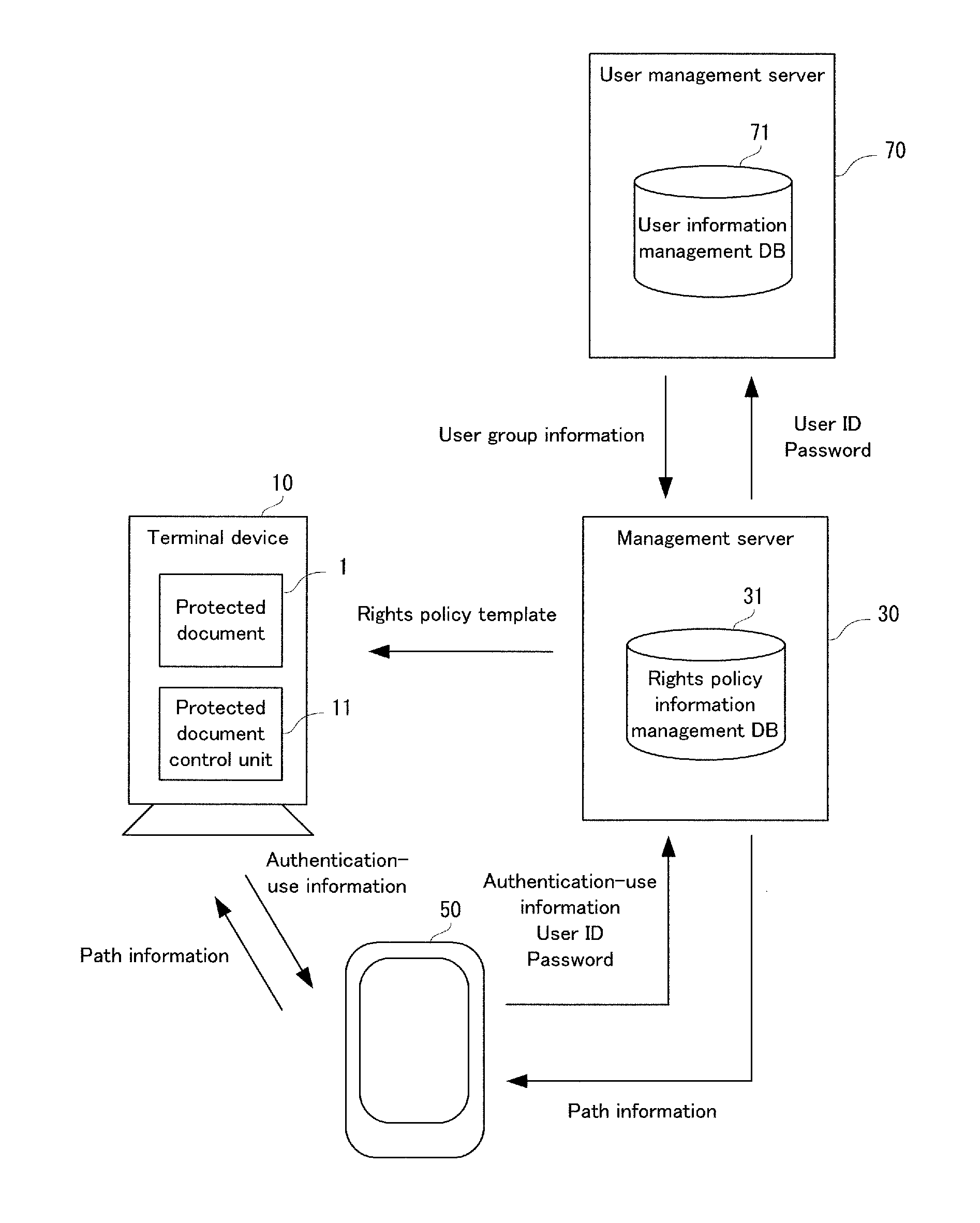
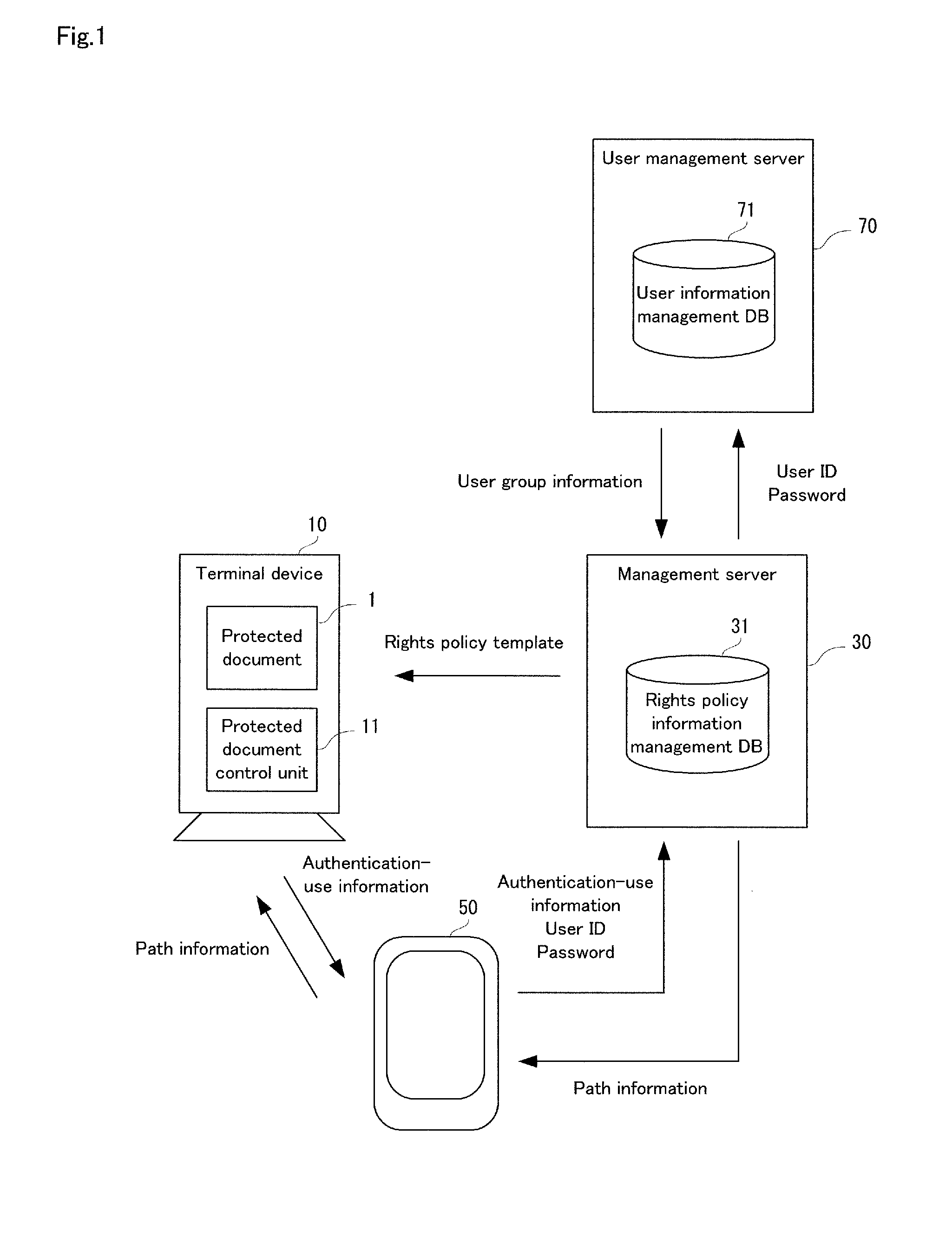
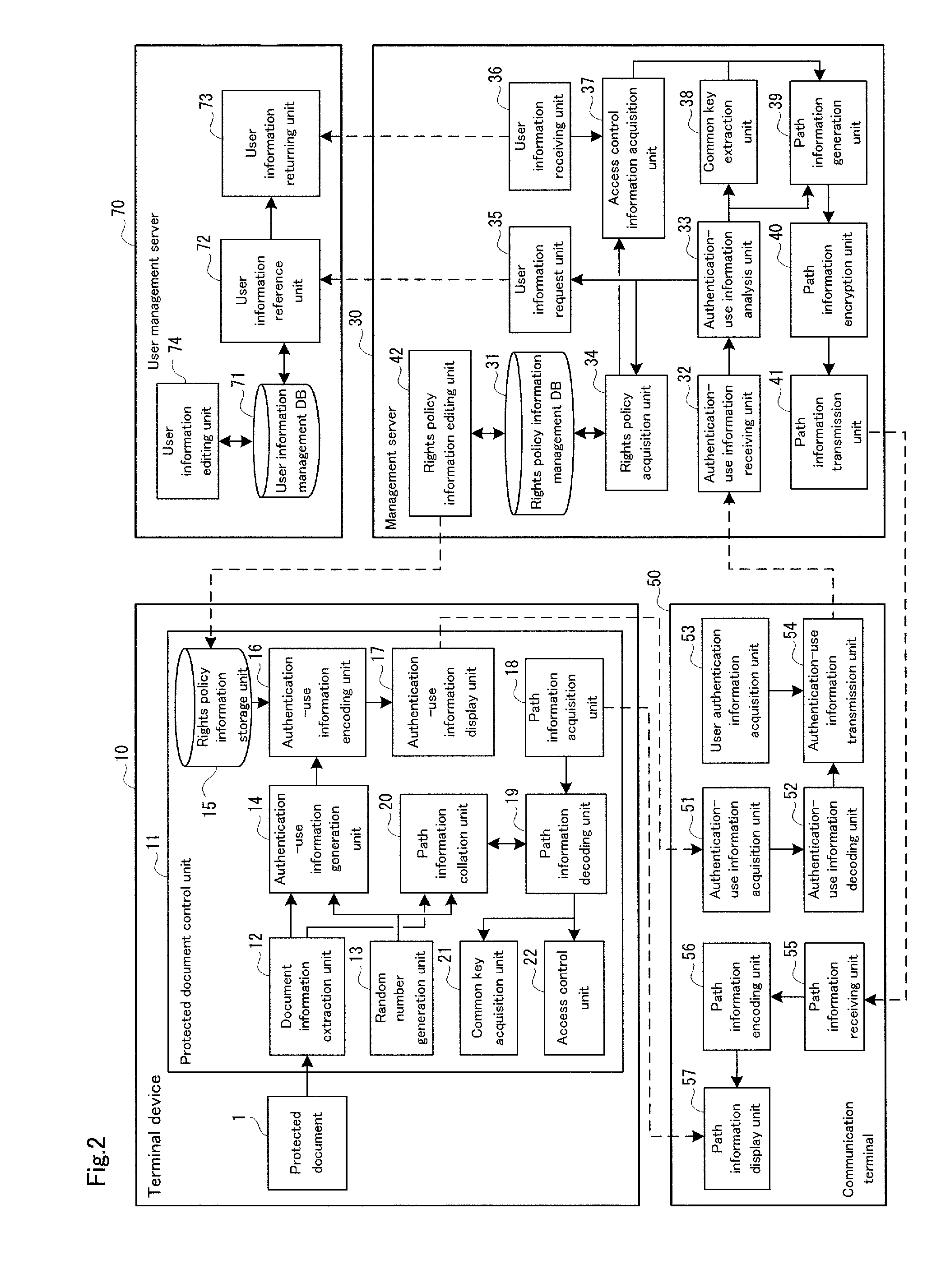
Document authority management system, terminal device, document authority management method, and computer-readable recording medium
InactiveUS20140245375A1Avoid disclosure of confidential informationTransmissionSecurity arrangementTerminal equipmentDocumentation
Owner:NEC CORP
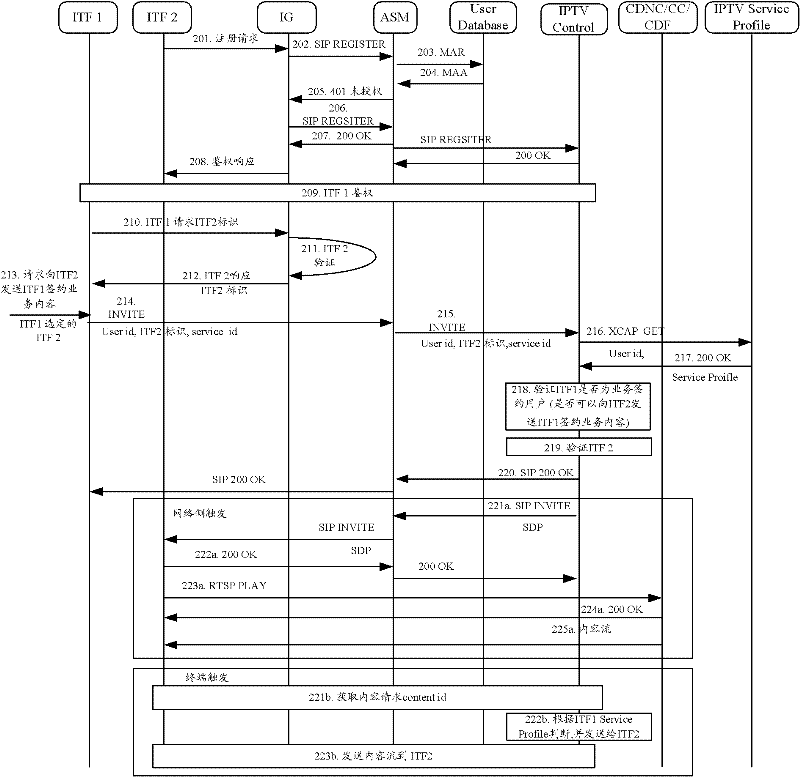
Business watching method and system for Internet protocol television
ActiveCN102685606ATransmissionSelective content distributionComputer terminalProtocol for Carrying Authentication for Network Access
Owner:HUAWEI DEVICE CO LTD
Methods and apparatus for a wireless terminal with third party advertising: dual authentication method
InactiveUS20060282384A1Improve receptivityIncrease exposureDigital data authenticationMarketingThird partyComputer hardware
Owner:MOCHIS INVESTMENT
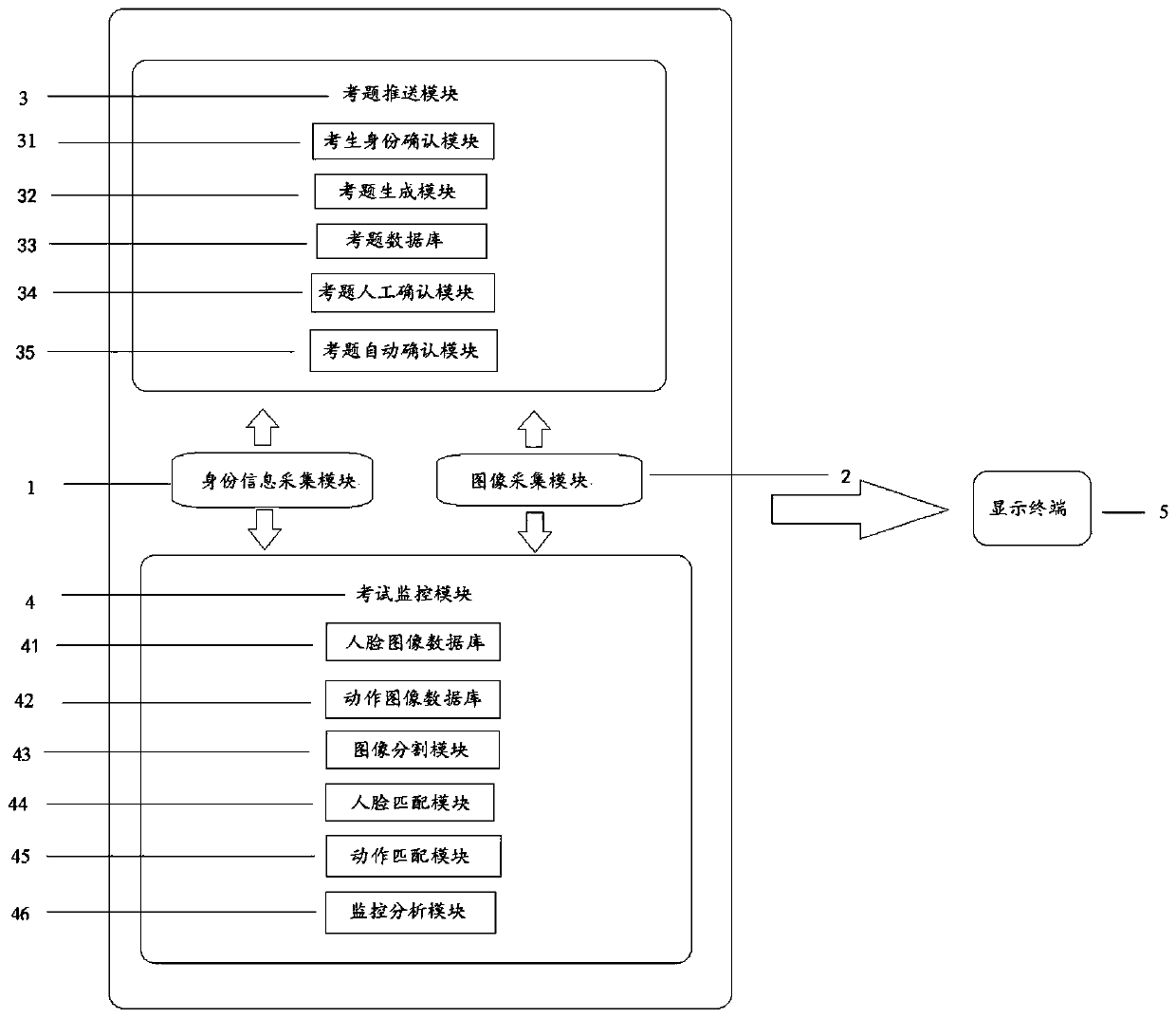
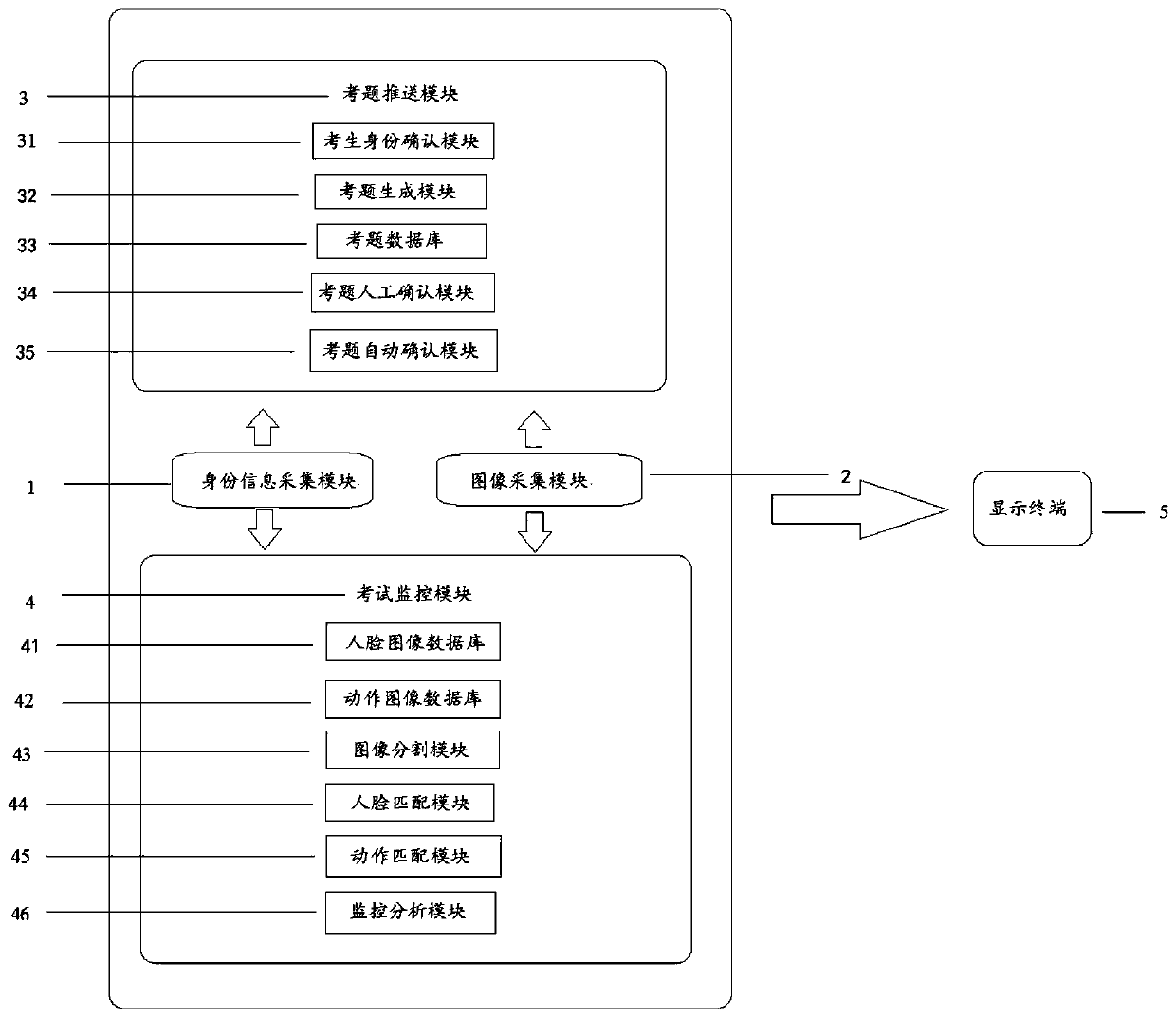
Examination system and processing method thereof
ActiveCN109711263AExam Situation MonitoringPrevent substitute examsData processing applicationsCharacter and pattern recognitionComputer scienceInformation acquisition
Owner:BEIJING GZT NETWORK TECH
Electronic payment method, device and terminal
InactiveCN106570691AReduce the risk of lossAvoid unreadableTransmissionProtocol authorisationUser inputBackup validation
The embodiment of the invention discloses an electronic payment method comprising the following steps: receiving a user inputted payment confirm order; responding to the payment confirm order, sending verify essential factor request information to N storage nodes, wherein the verify essential factor request information is used for requesting a server to issue verify essential factors forming an identity verify template, and N is an integer >=2; receiving M verify essential factors of K storage nodes from N storage nodes, wherein K and M are respectively integer >=1, and K is <N; combining M verify essential factors so as to form the identity verify template; using the identity verify template to verify user inputted to-be-verified information; if verification fails, using a backup identity verify flow to verify the to-be-verified information; if the backup identity verify flow successes, sending an online payment order to the server, wherein the online payment order is used for indicating the server to carry out online payment. The embodiment also discloses an electronic payment device and a terminal.
Owner:NUBIA TECH CO LTD
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap