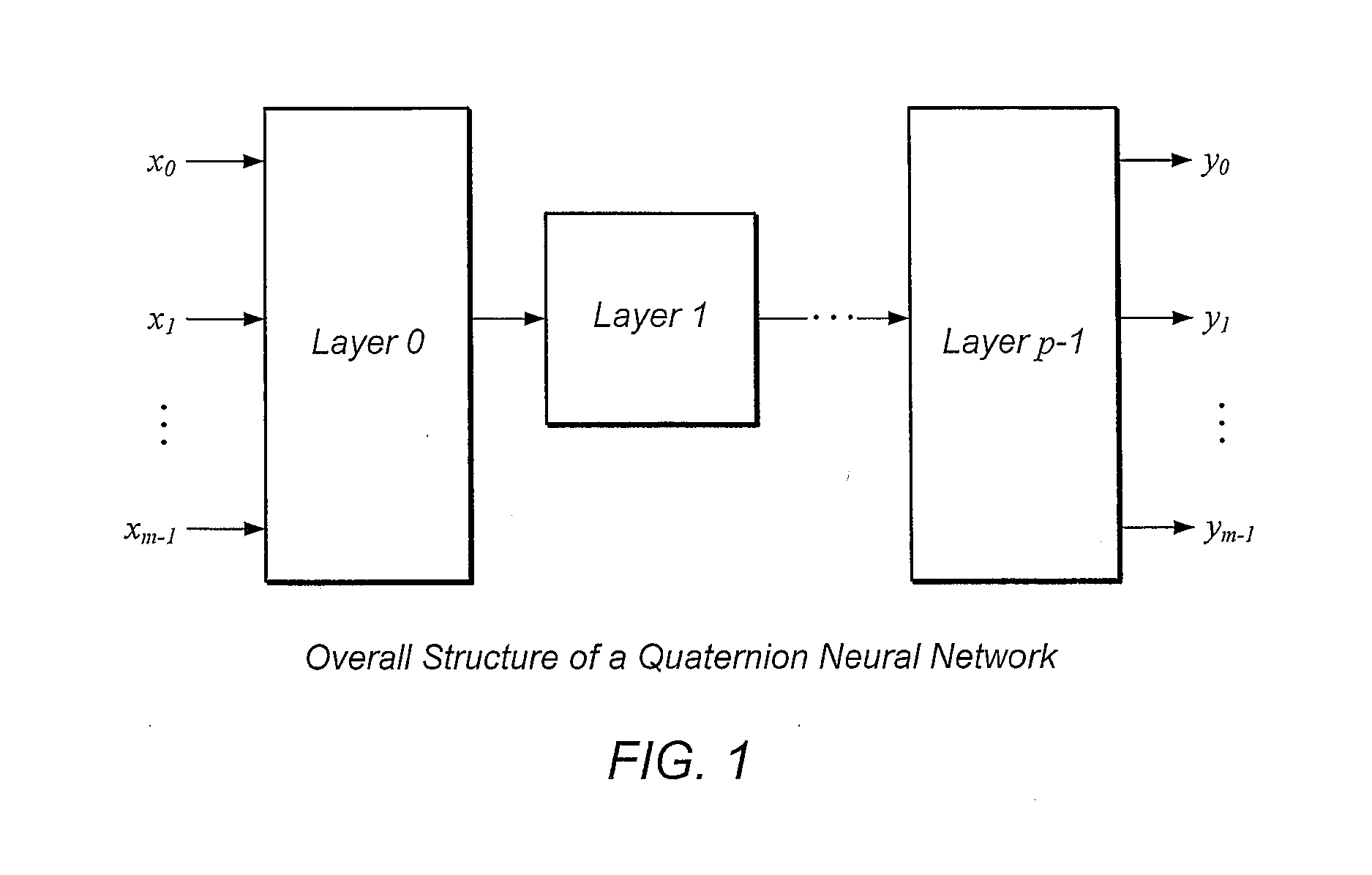
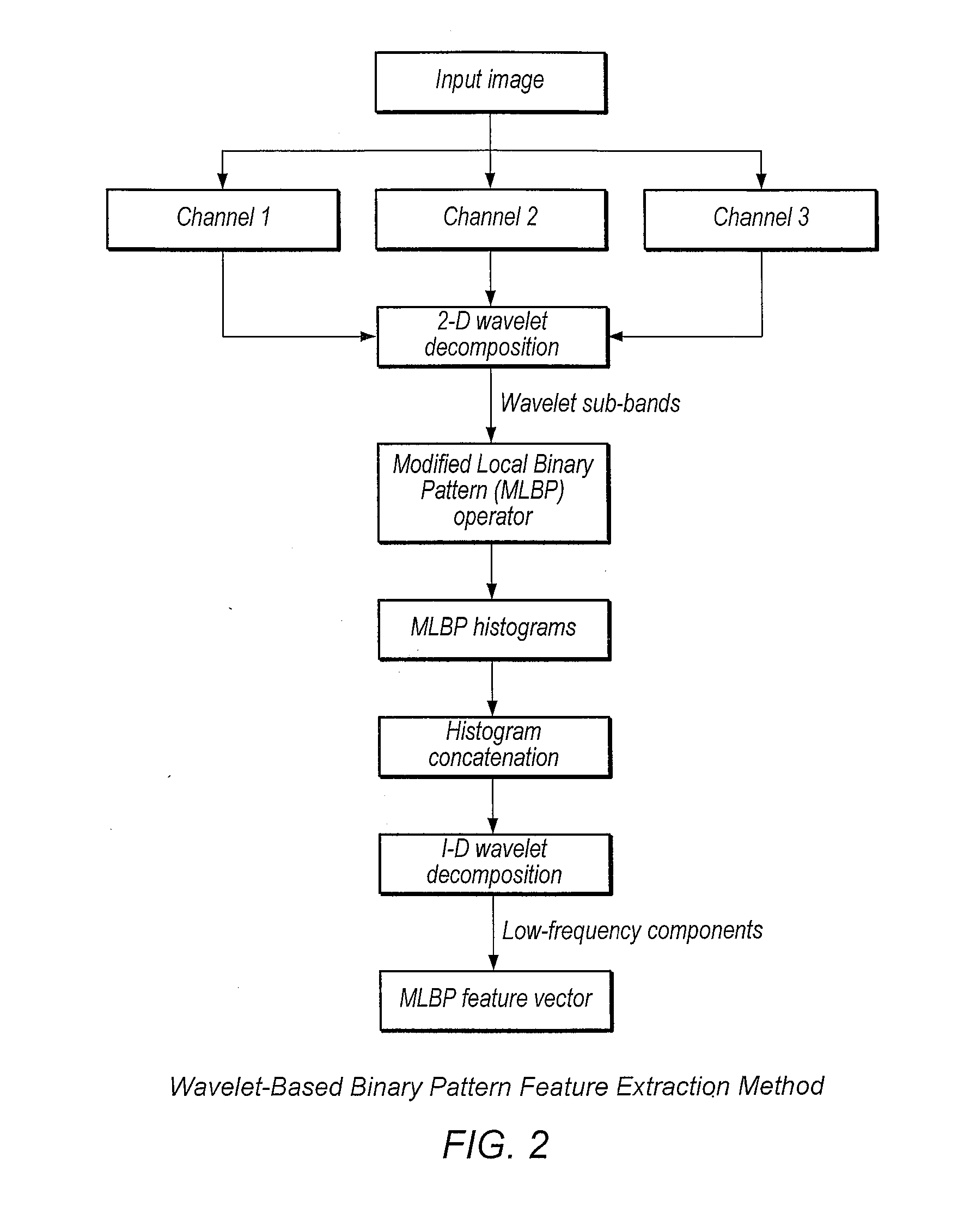
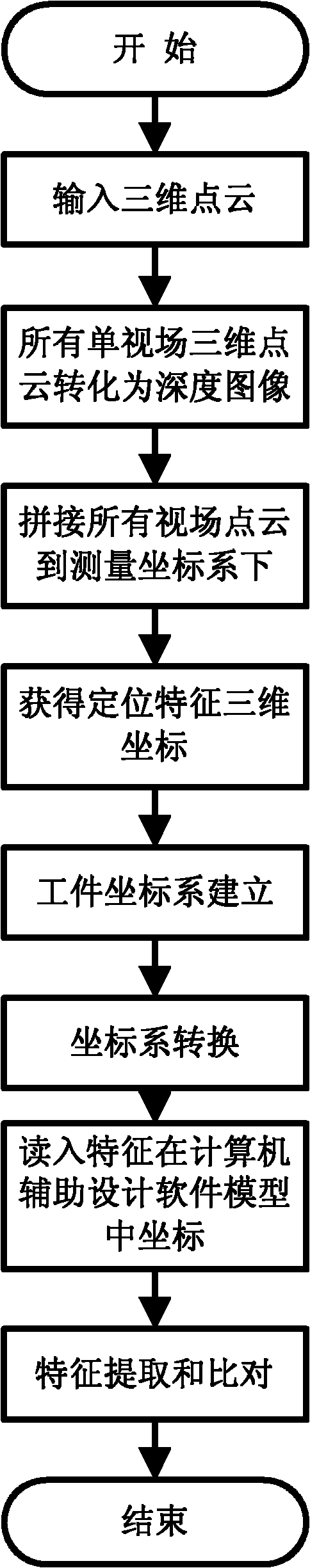
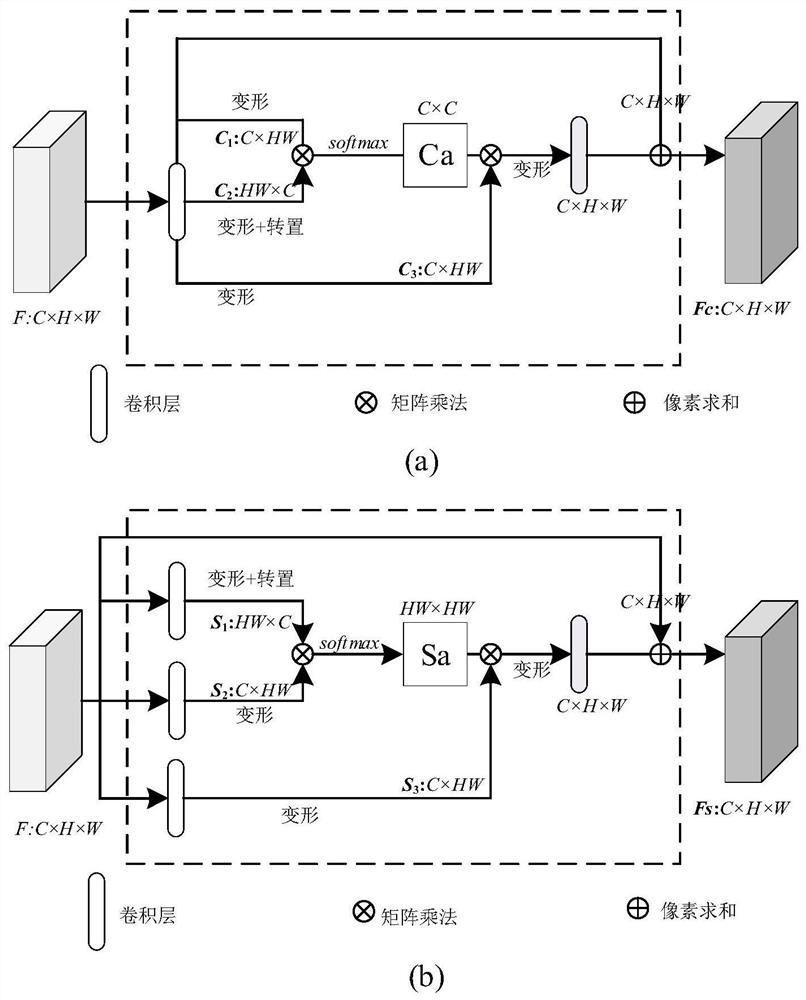
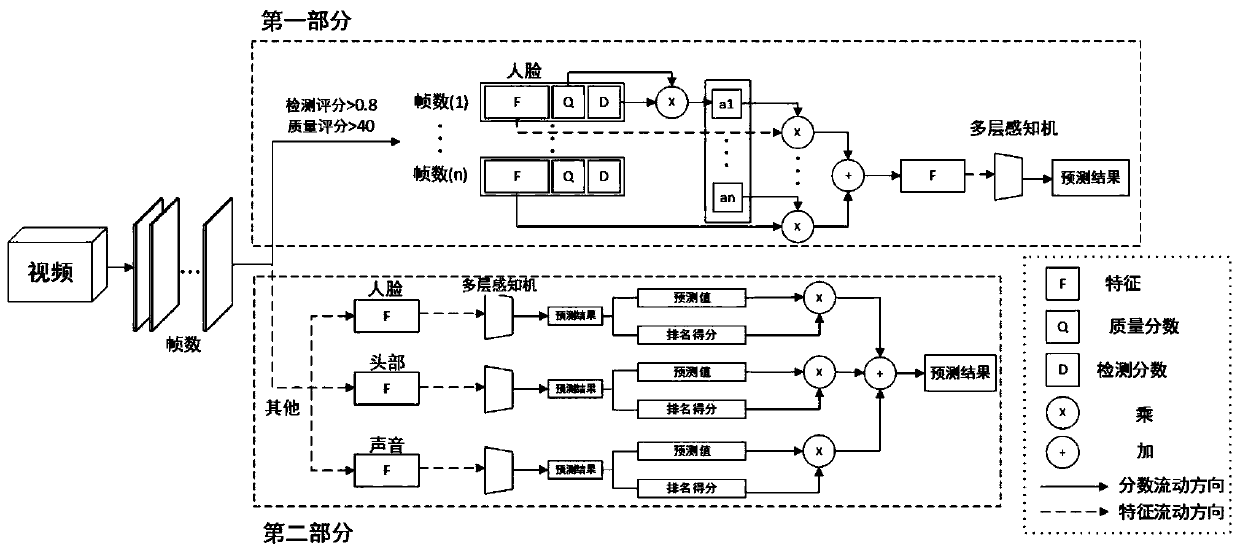
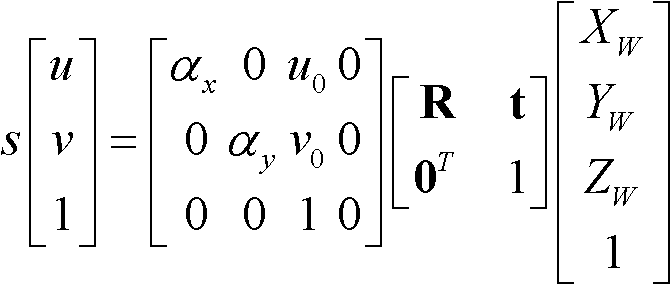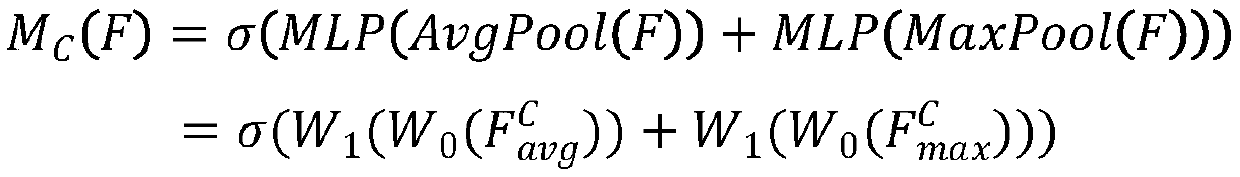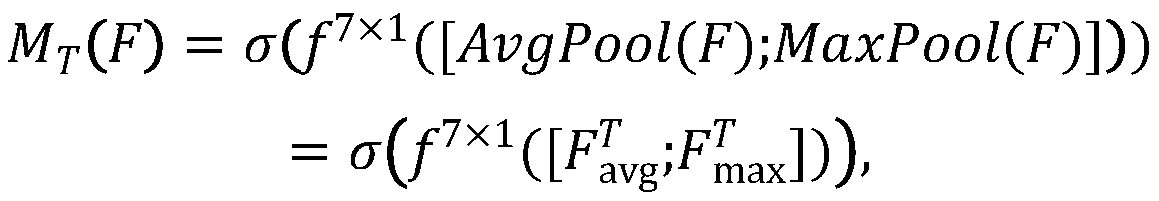Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
70 results about "Feature extraction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In machine learning, pattern recognition and in image processing, feature extraction starts from an initial set of measured data and builds derived values (features) intended to be informative and non-redundant, facilitating the subsequent learning and generalization steps, and in some cases leading to better human interpretations. Feature extraction is related to dimensionality reduction.
Systems and methods for quantitative analysis of histopathology images using multiclassifier ensemble schemes
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
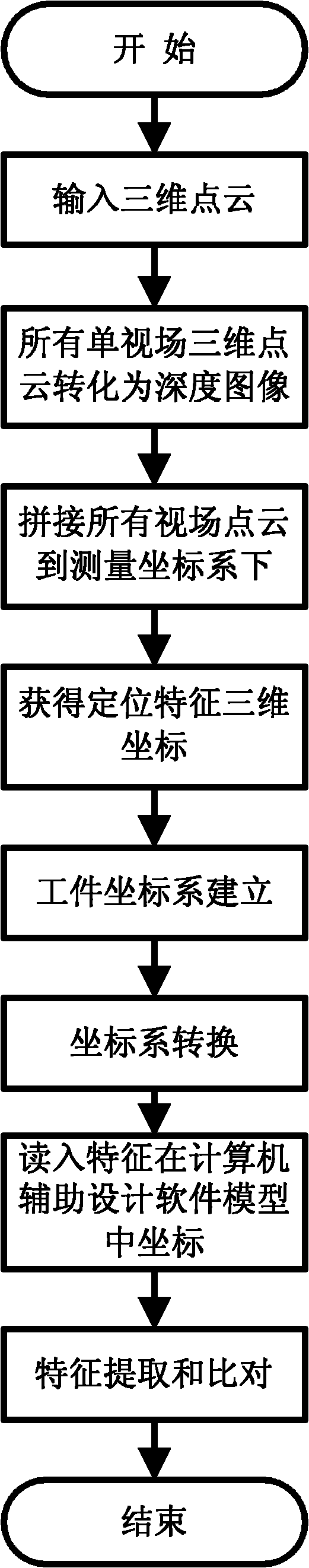
Full-automatic three-dimension characteristic extracting method
InactiveCN102135417AImplement automatic conversionAccurate targetImage analysisUsing optical meansPoint cloudFeature extraction
Owner:BEIHANG UNIV
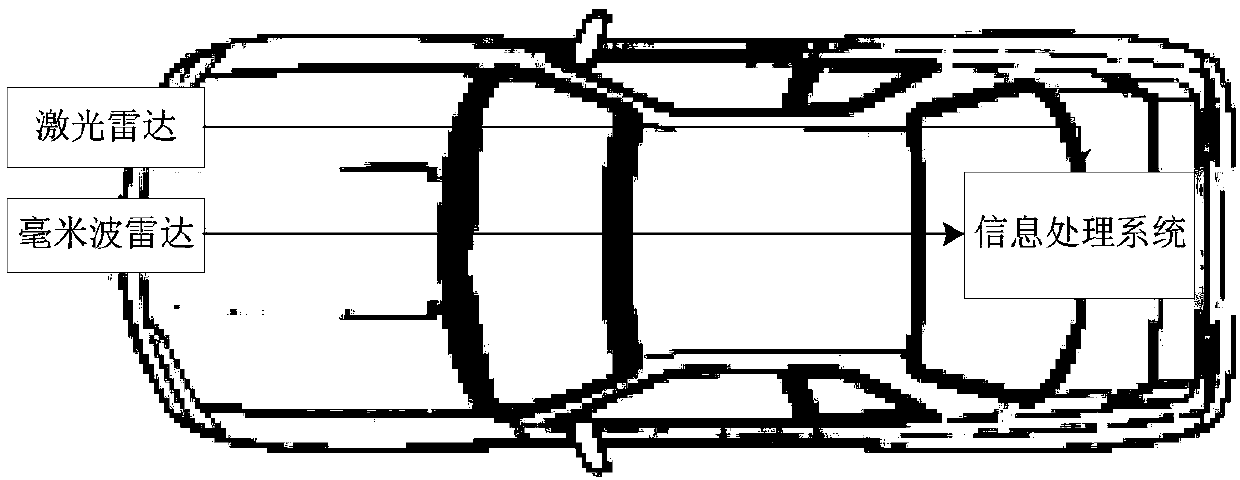
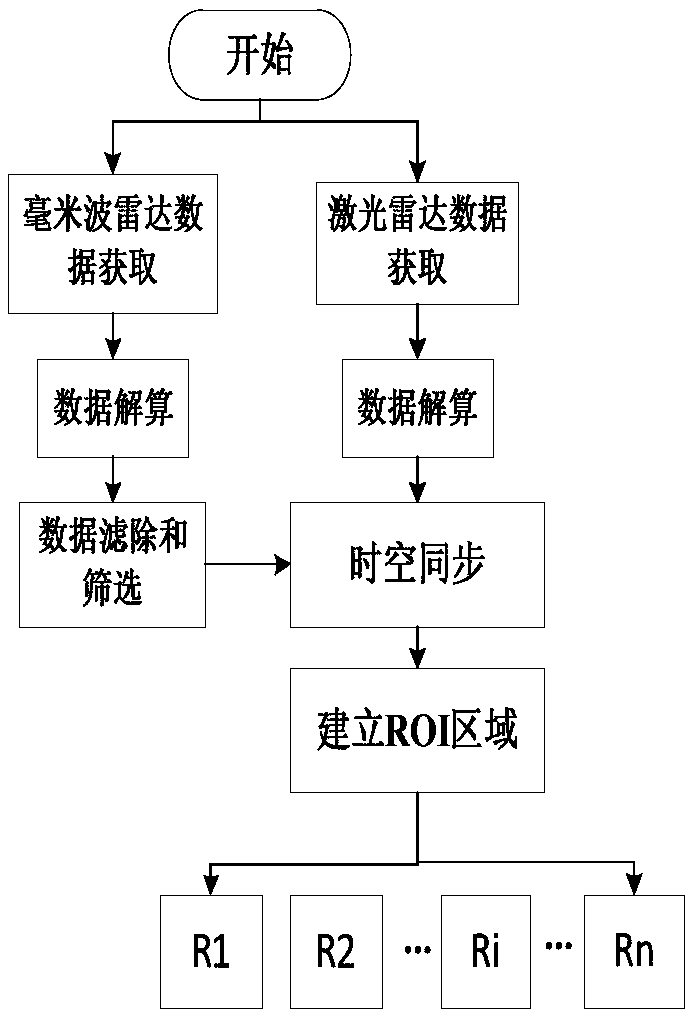
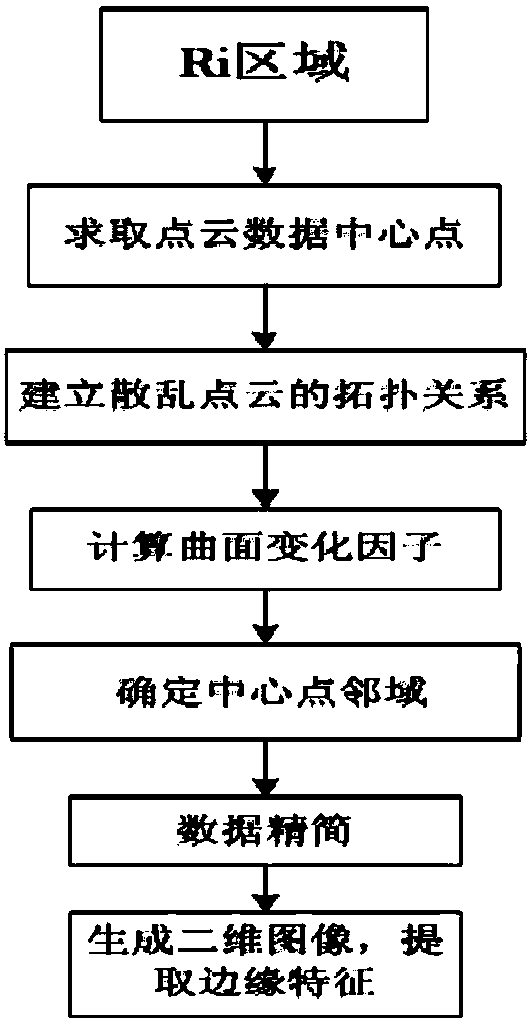
Obstacle feature extraction method based on millimeter wave radar and laser radar
InactiveCN108509972ASafe drivingThe perception result is accurateCharacter and pattern recognitionElectromagnetic wave reradiationFeature extractionPoint cloud
Owner:TIANJIN UNIV
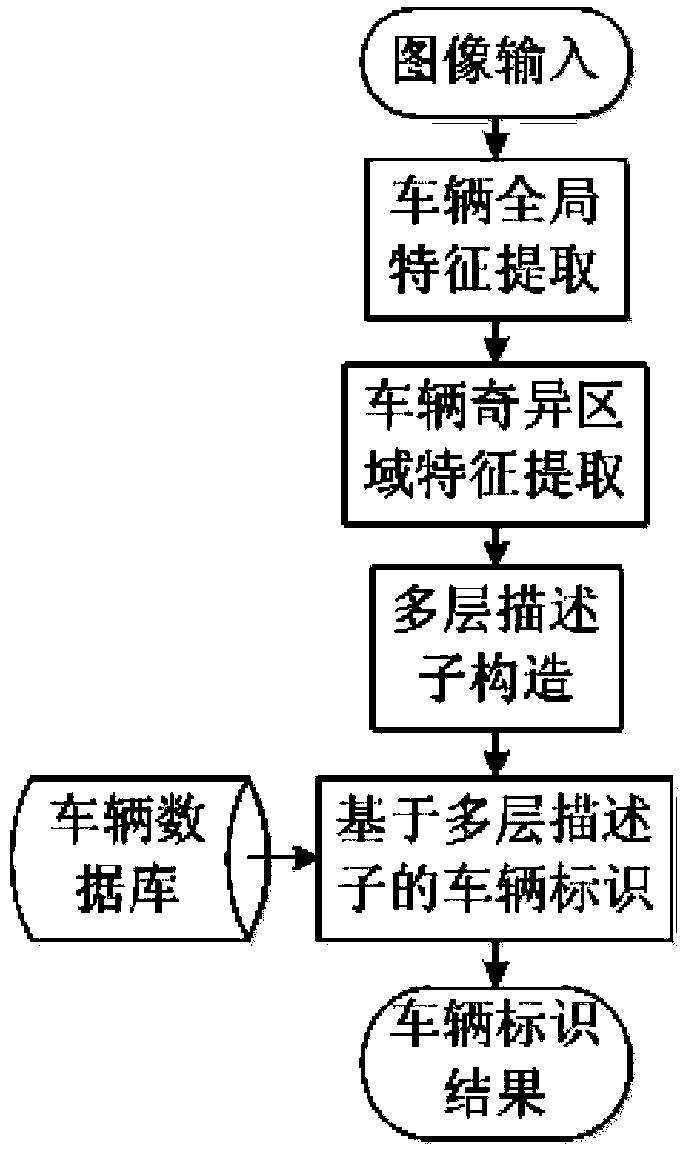
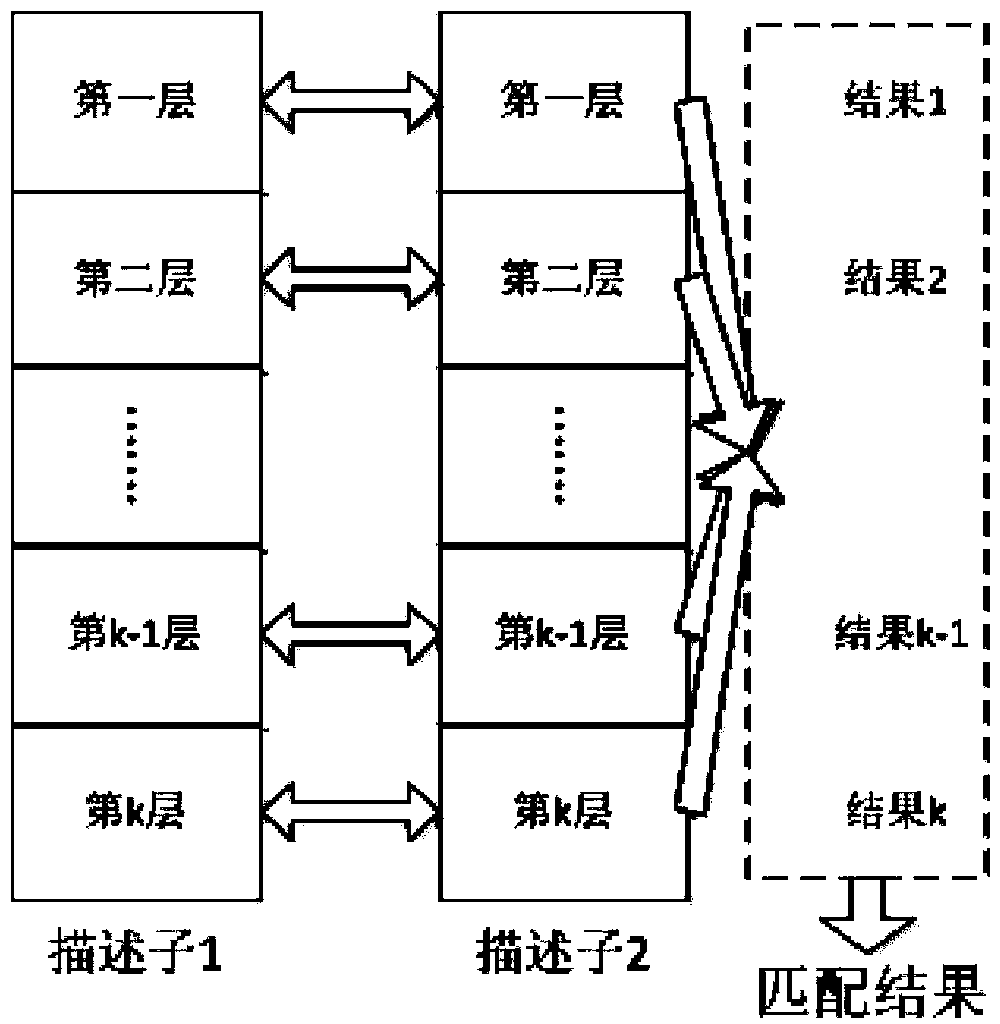
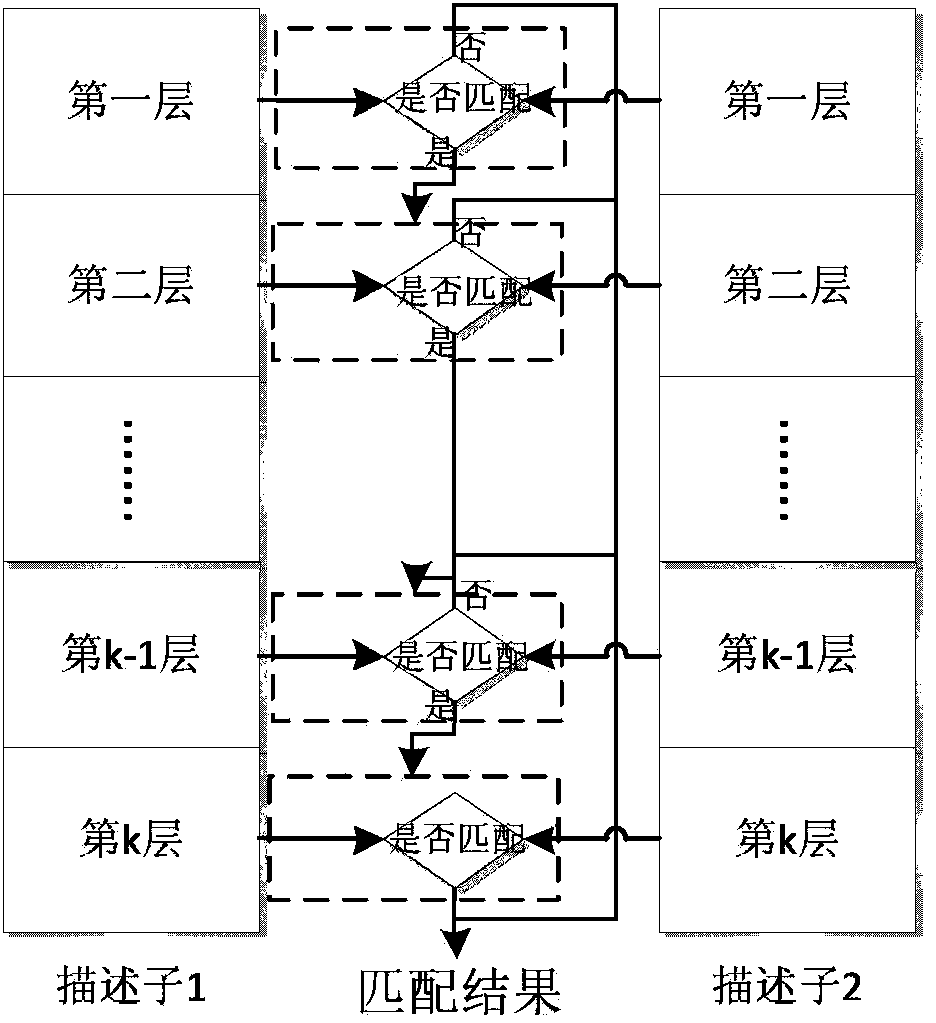
Vehicle identification method and system based on multilayer descriptors
ActiveCN103810505AImprove accuracyReduce complexityCharacter and pattern recognitionFeature extractionIn vehicle
Owner:PEKING UNIV
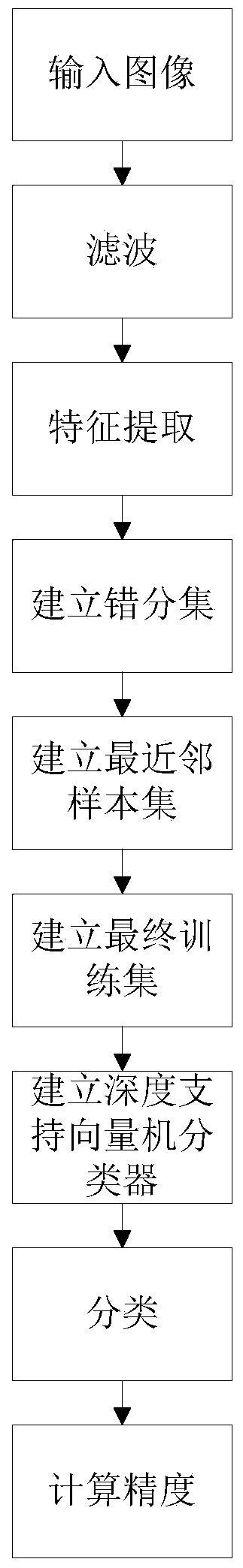
Polarized SAR image classification method based on K mean value and depth SVM
ActiveCN104239900AReduce the numberReduce sorting timeCharacter and pattern recognitionFeature extractionSynthetic aperture radar
Owner:XIDIAN UNIV
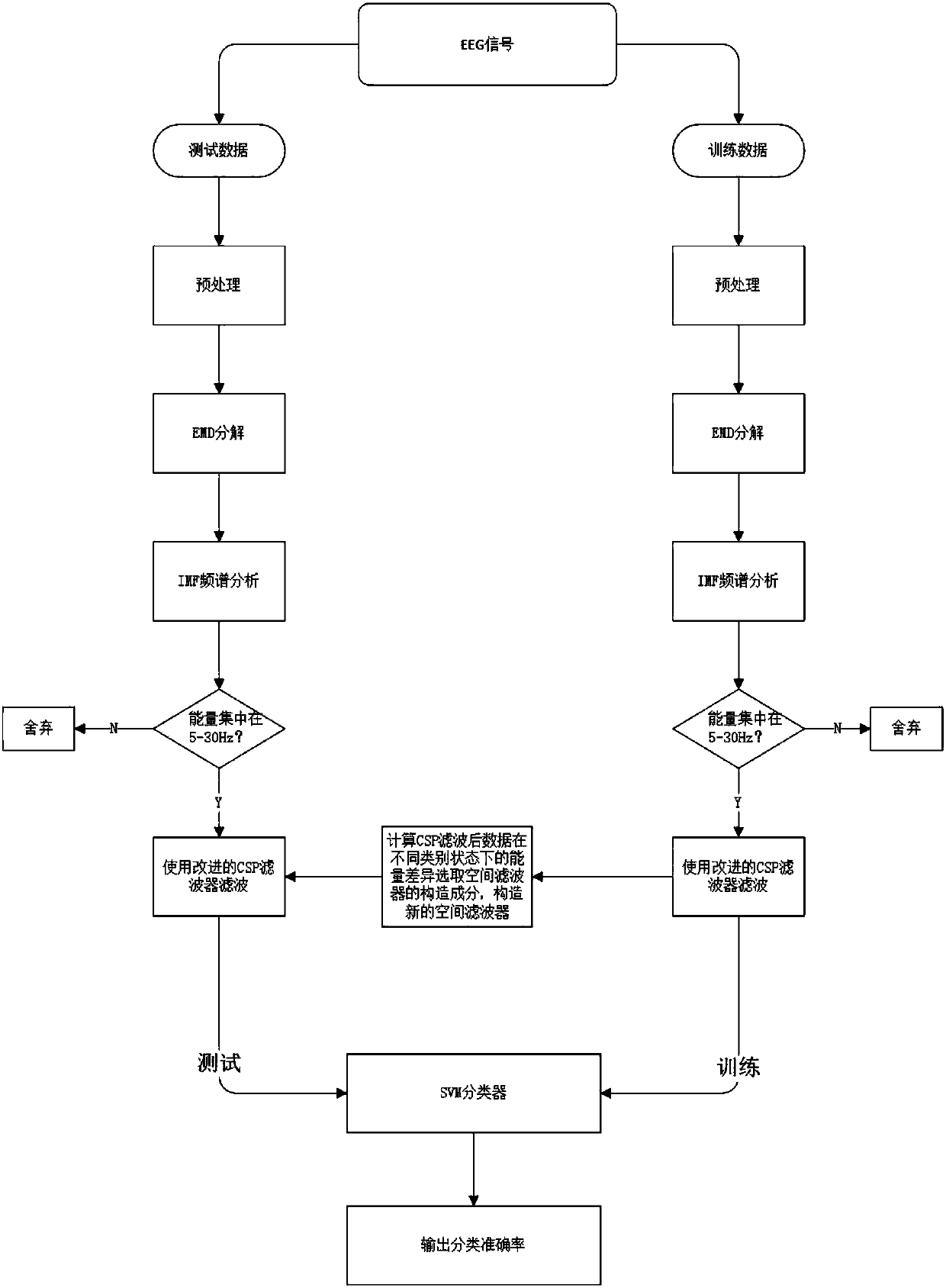
Electroencephalogram signal feature extraction method combining with public space mode algorithm and EMD
InactiveCN107239142ASolve the problem of lack of frequency domain informationSolve the problem of requiring a large number of input channelsInput/output for user-computer interactionCharacter and pattern recognitionFeature extractionDecomposition
Owner:NANJING UNIV OF POSTS & TELECOMM
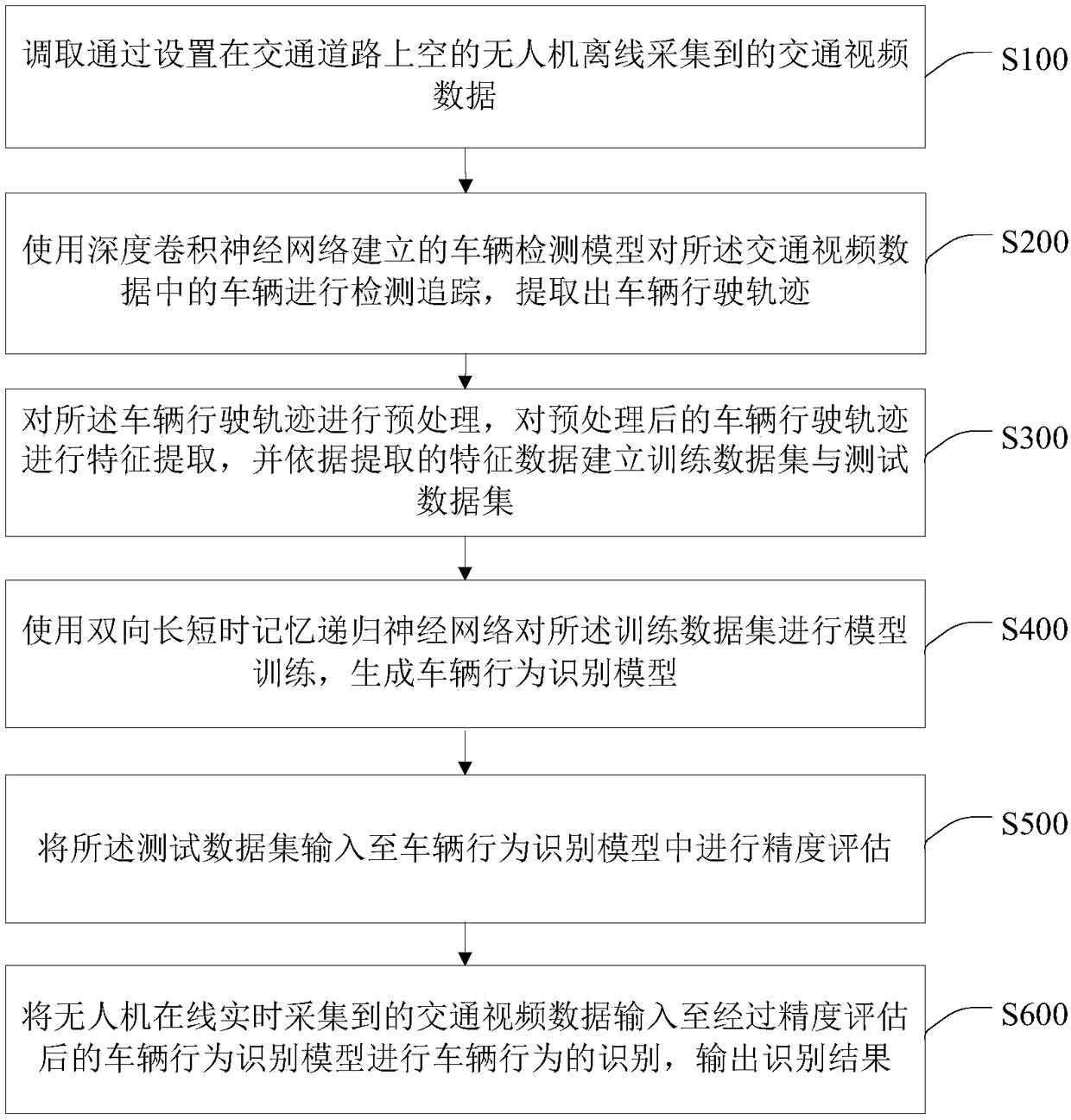
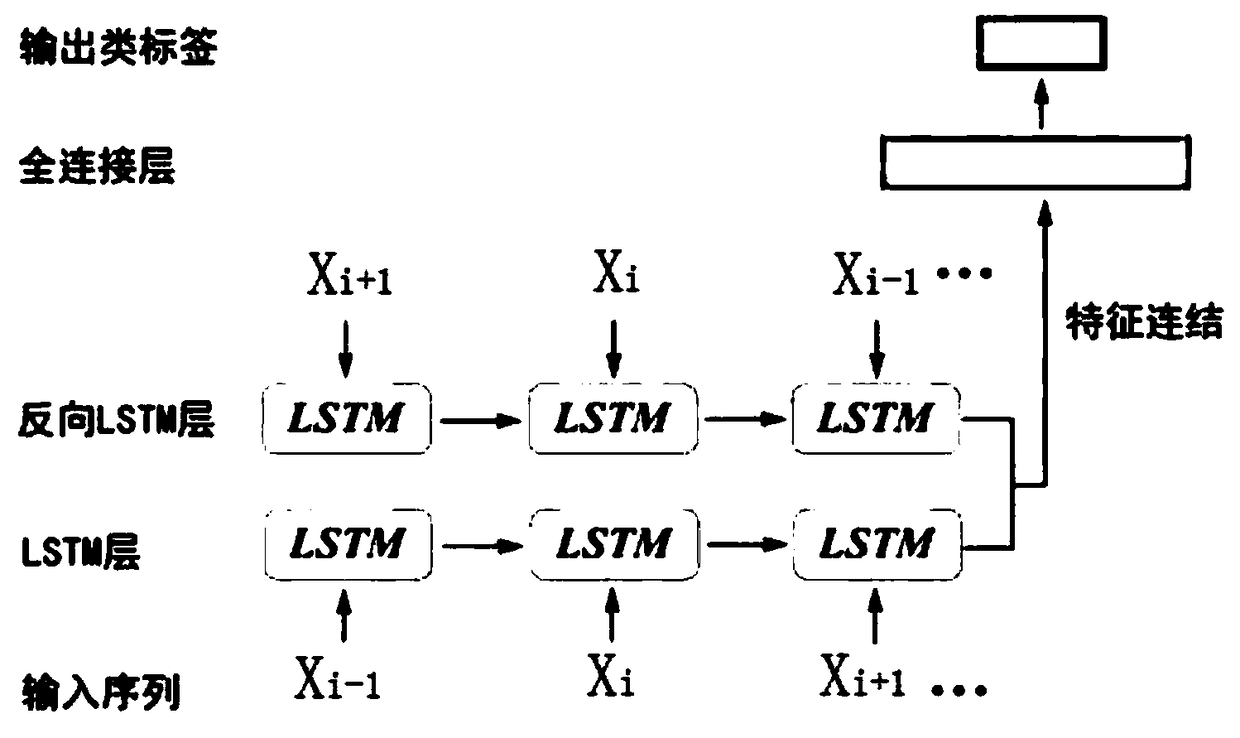
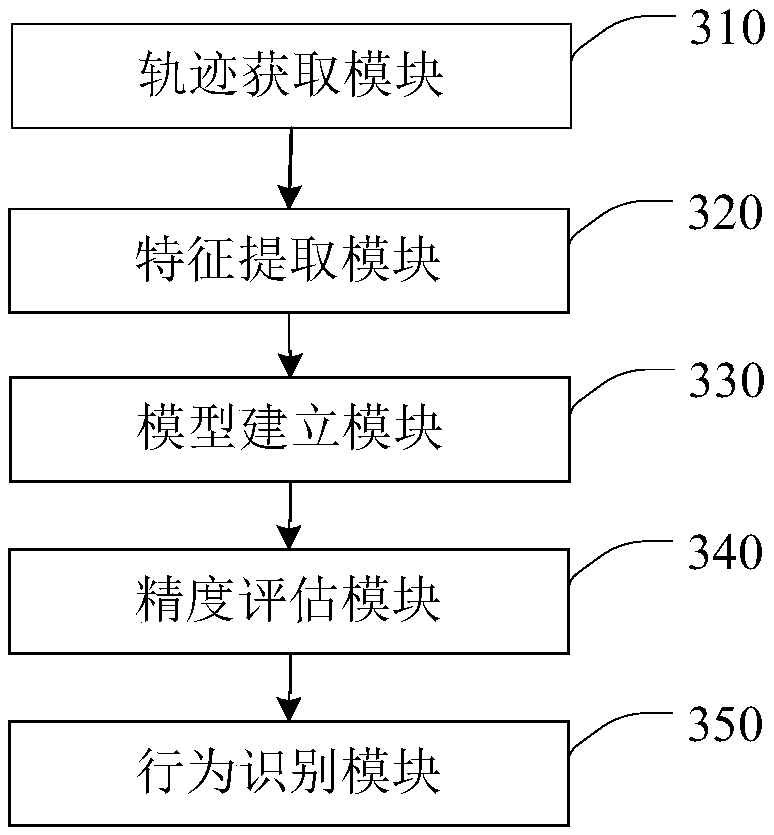
Bidirectional LSTM network-based vehicle behavior identification method and system
ActiveCN109285348AJudging driving behaviorImprove recognition accuracyDetection of traffic movementVehicle behaviorData set
Owner:SHENZHEN UNIV
Unmanned aerial vehicle target positioning method and system
InactiveCN106295613AAccurate targetingPrecise positioningStill image data retrievalScene recognitionFeature extractionGeolocation
The invention provides an unmanned aerial vehicle target positioning method and system. The method comprises the steps that an image feature database of a satellite remote sensing image is established; an unmanned aerial vehicle reconnaissance image is acquired and preprocessed; multi-scale image feature extracting is carried out on the preprocessed unmanned aerial vehicle reconnaissance image; an image retrieval similarity measurement model based on granular computing is established, and matching computing is carried out on the extracted image features and image features in the image feature database according to the image retrieval similarity measurement model to acquire a similarity measurement value; and the geographic position corresponding to the satellite remote sensing image with the similarity measurement value satisfying a preset threshold value is determined as the unmanned aerial vehicle target position. The method and system can accurately position an unmanned aerial vehicle target.
Owner:HARBIN UNIV OF SCI & TECH
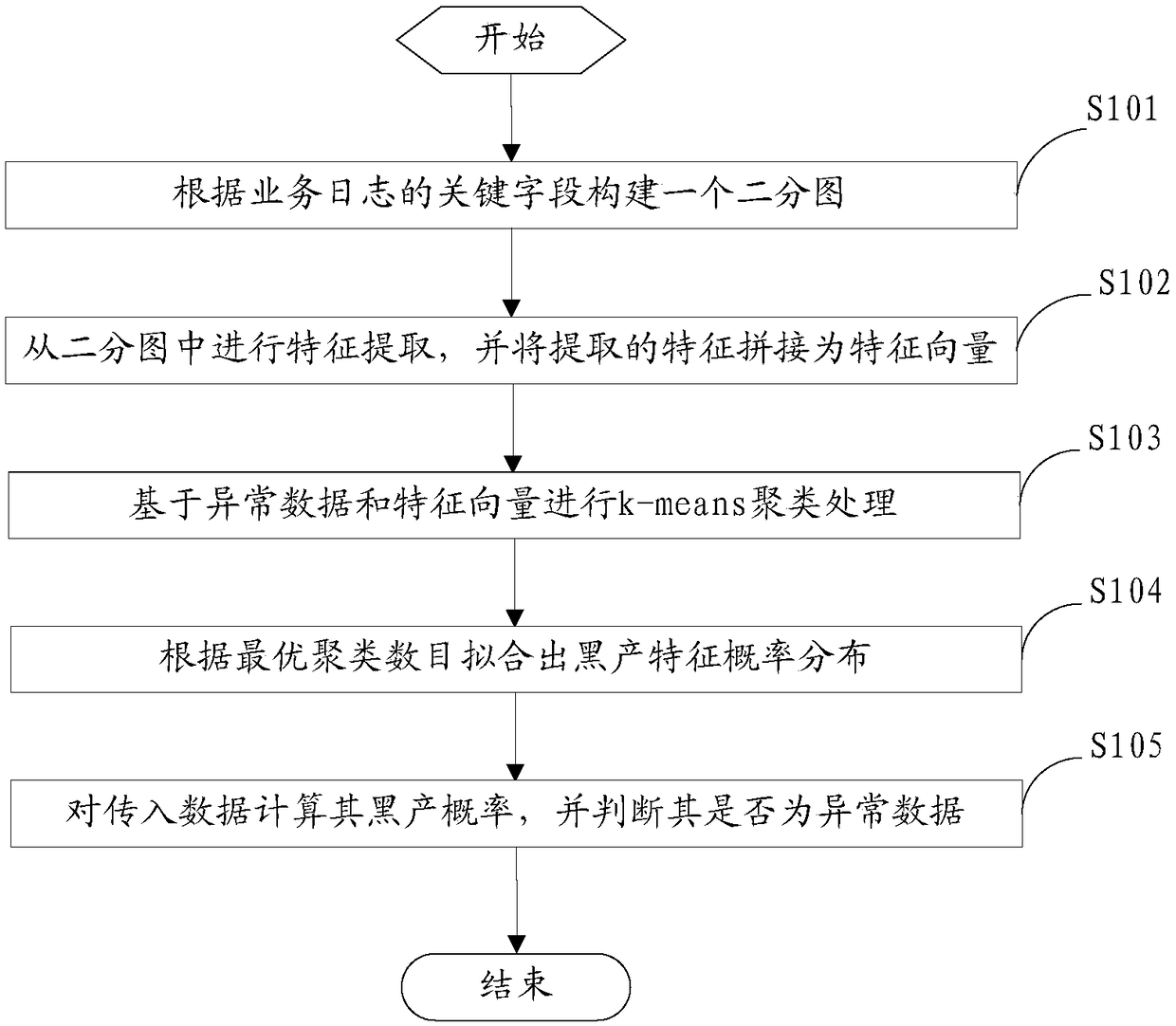
Abnormality detection method and device based on log graph modeling
ActiveCN108920947AAvoid attackEnsure safetyCharacter and pattern recognitionPlatform integrity maintainanceNODALFeature vector
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
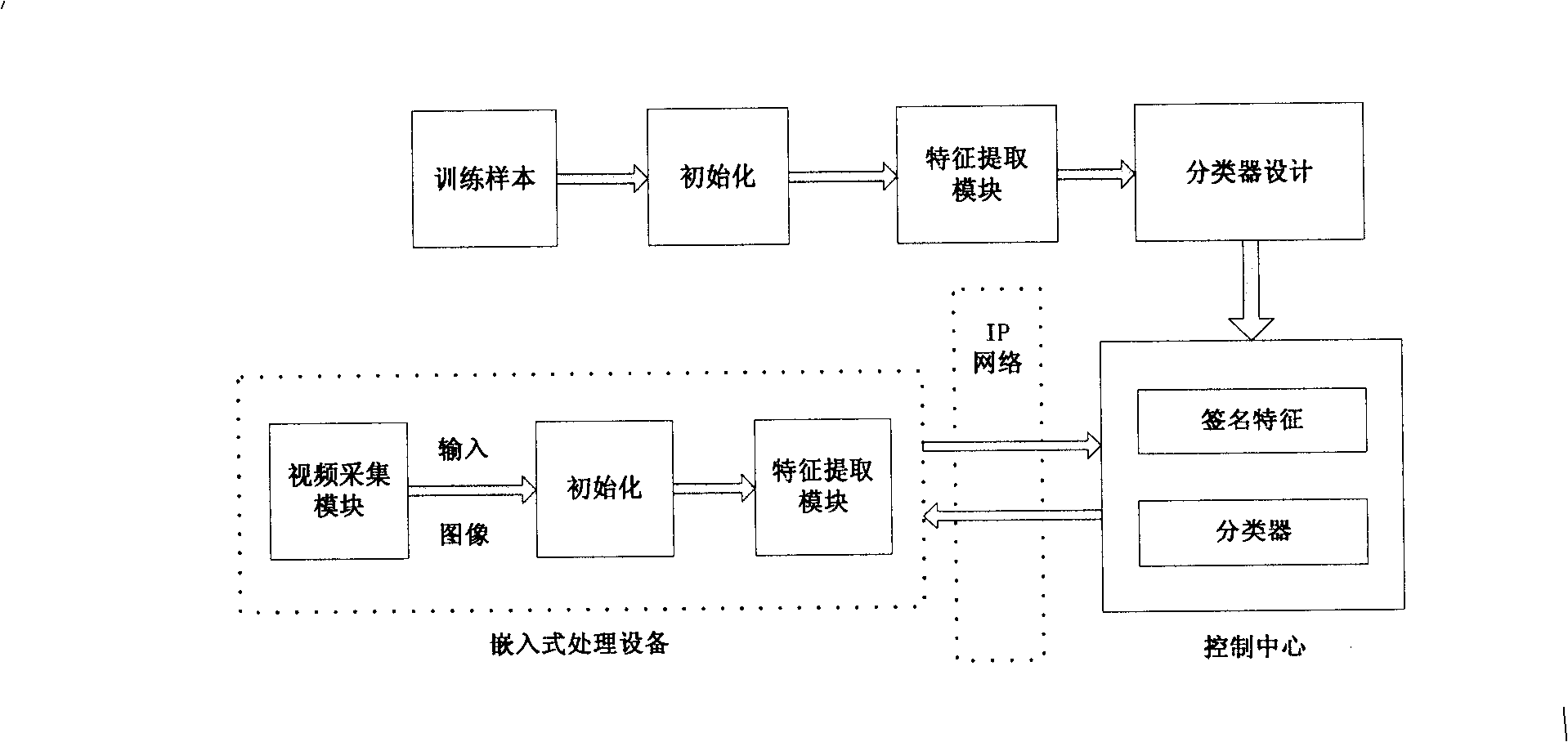
Device and method for identifying hand-written signature
InactiveCN101329735ALow costEasy to useCharacter and pattern recognitionHandwritingFeature extraction
Owner:VIMICRO CORP
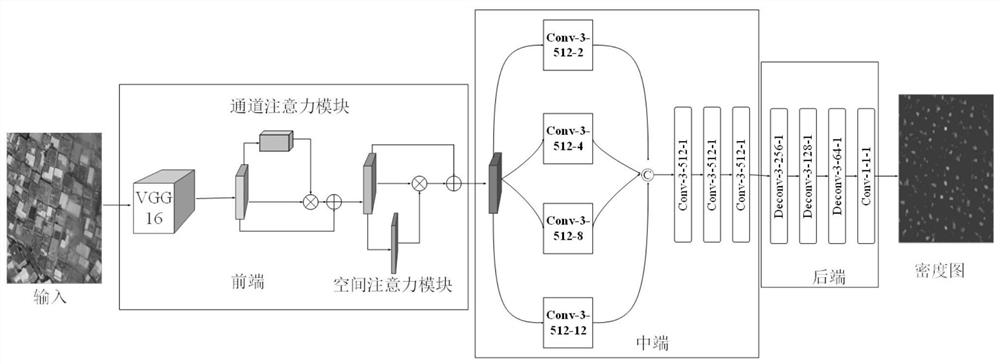
Method for counting targets in remote sensing image based on attention mechanism
ActiveCN112084868ASolve the problem of complex and confusing background interferenceSolving the problem of scale diversityImage enhancementImage analysisFeature extractionRemote sensing
Owner:BEIHANG UNIV
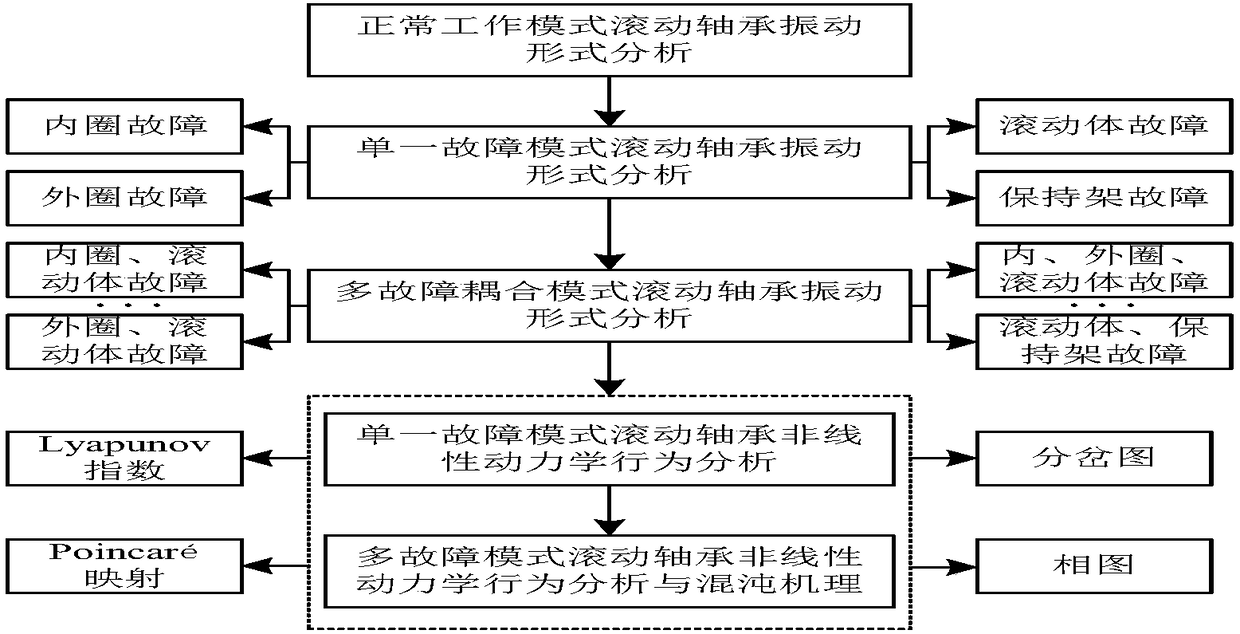
Rolling bearing multi-fault coupling mechanism and early fault feature extraction method
Owner:YANSHAN UNIV
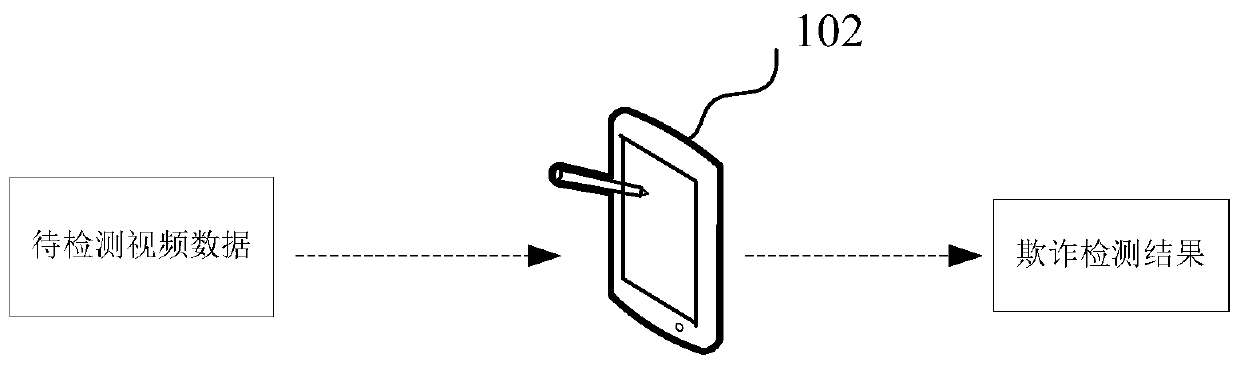
Video data fraud detection method and device, computer equipment and storage medium
PendingCN110781916AImprove accuracyIncrease diversitySpeech analysisAcquiring/recognising facial featuresFeature vectorData set
Owner:PING AN TECH (SHENZHEN) CO LTD
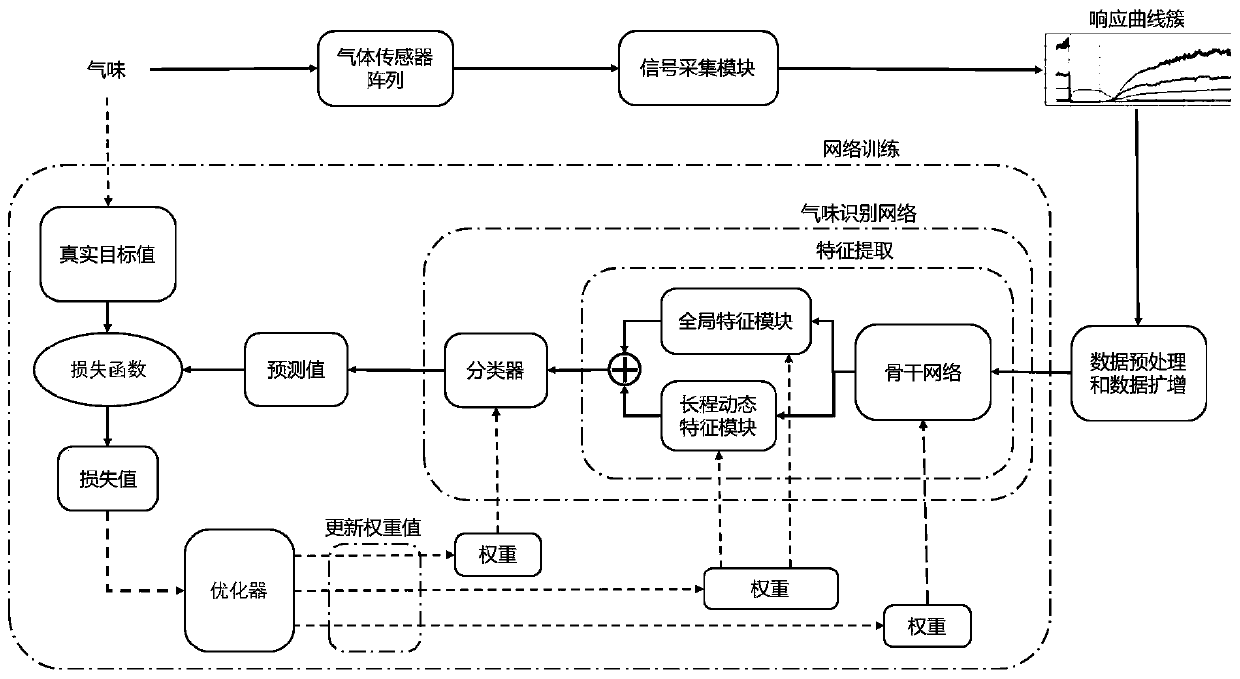
Odor identification method based on gas sensors and deep learning
ActiveCN111443165AImprove odor recognition performanceImprove computing efficiencyNeural learning methodsMaterial analysisNerve networkFeature extraction
Owner:HUAZHONG UNIV OF SCI & TECH
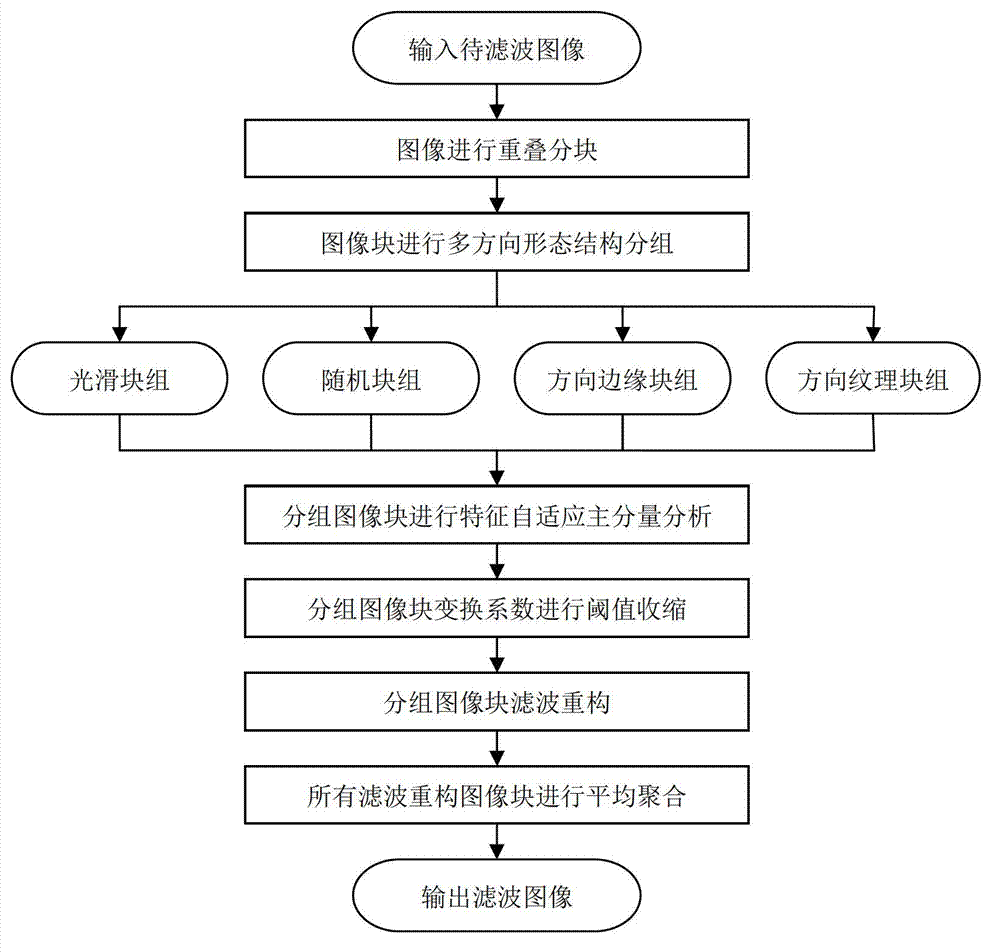
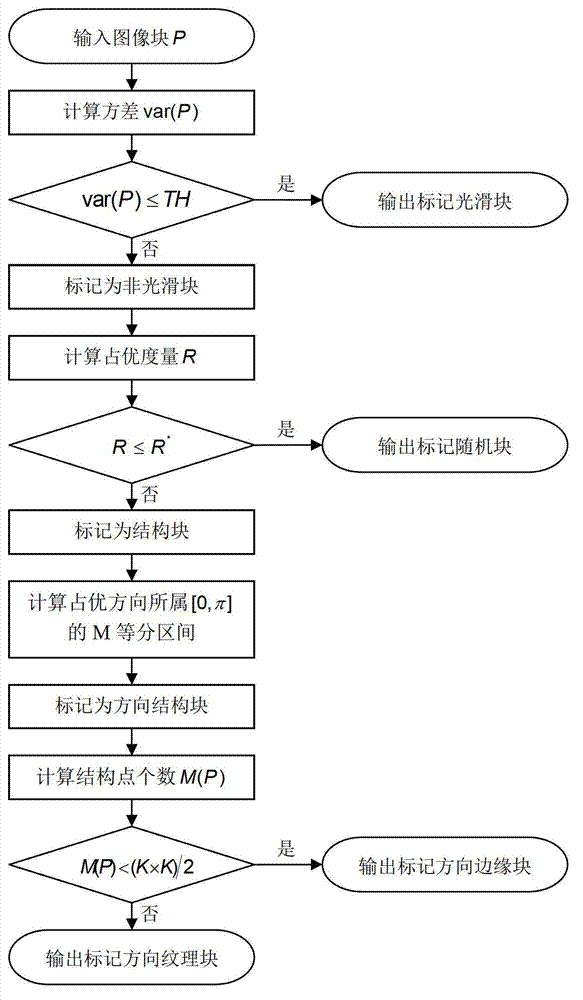
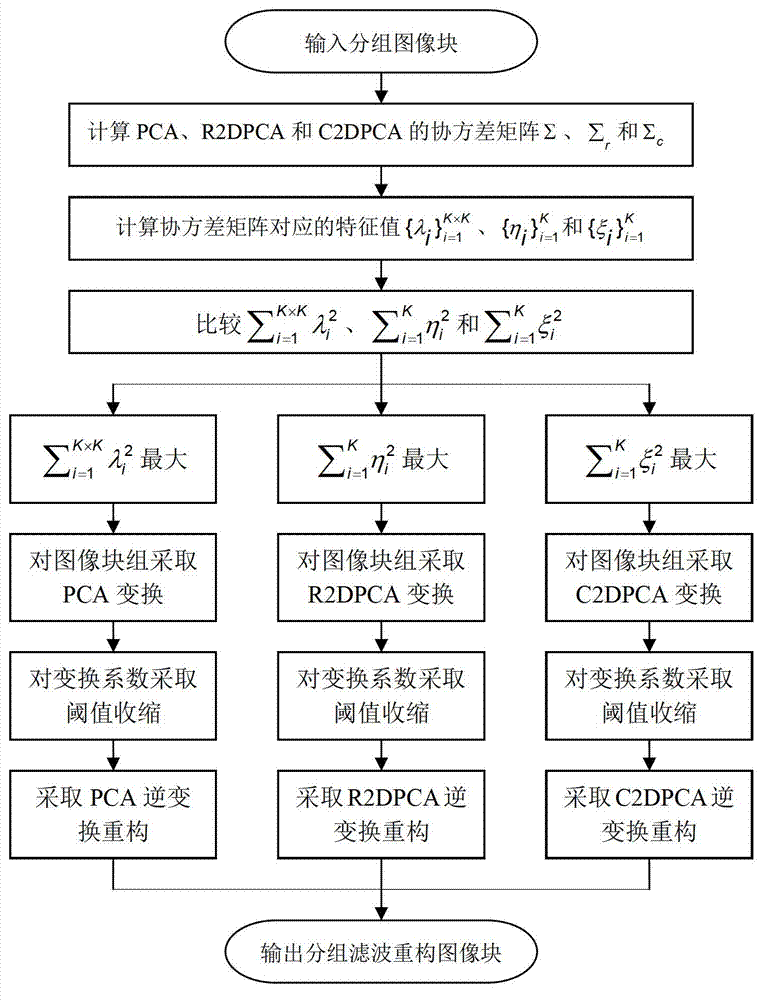
Principal component analysis collaborative filtering method for image multi-direction morphological structure grouping
ActiveCN103208097AKeep the main visual perception partKeep the visual partImage enhancementFeature extractionPrincipal component analysis
Owner:NANJING UNIV OF SCI & TECH
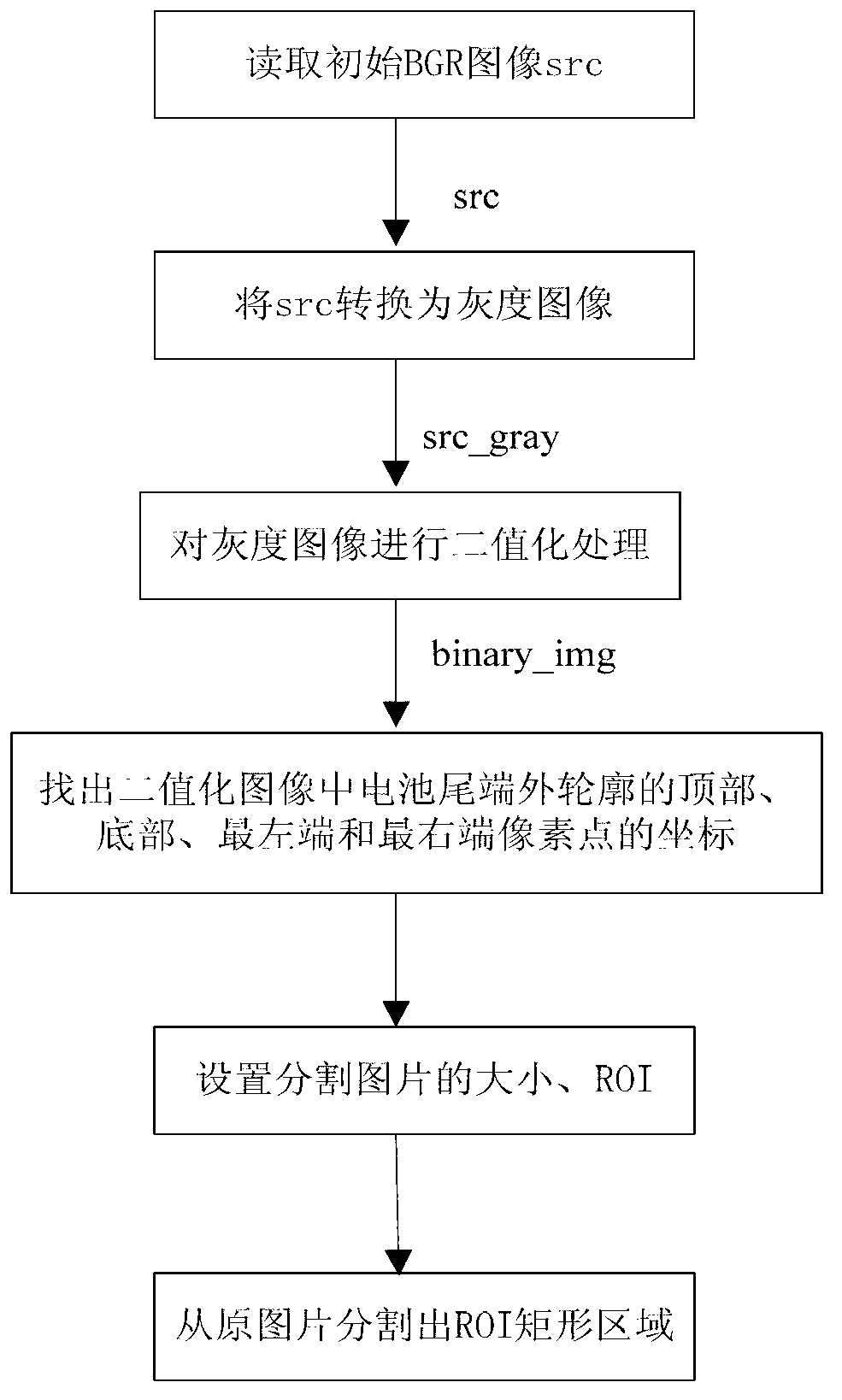
Image segmentation method for intelligent flaw detection of cell tail end
InactiveCN103345743AImprove detection efficiencyWon't hurtImage analysisFeature extractionMatch algorithms
Owner:NINGBO CHENGDIAN TAIKE ELECTRONICS INFORMATION TECH DEV
Super key distributed searching method
InactiveCN102243631AKeep Search DistributedImprove search accuracySpecial data processing applicationsFeature extractionQuery analysis
Owner:吴春尧
Automatic traction apparatus and automatic traction system
InactiveCN101499197APrevent wrongdoingComplete banking machinesImage analysisTraction systemFeature extraction
Owner:OKI ELECTRIC IND CO LTD
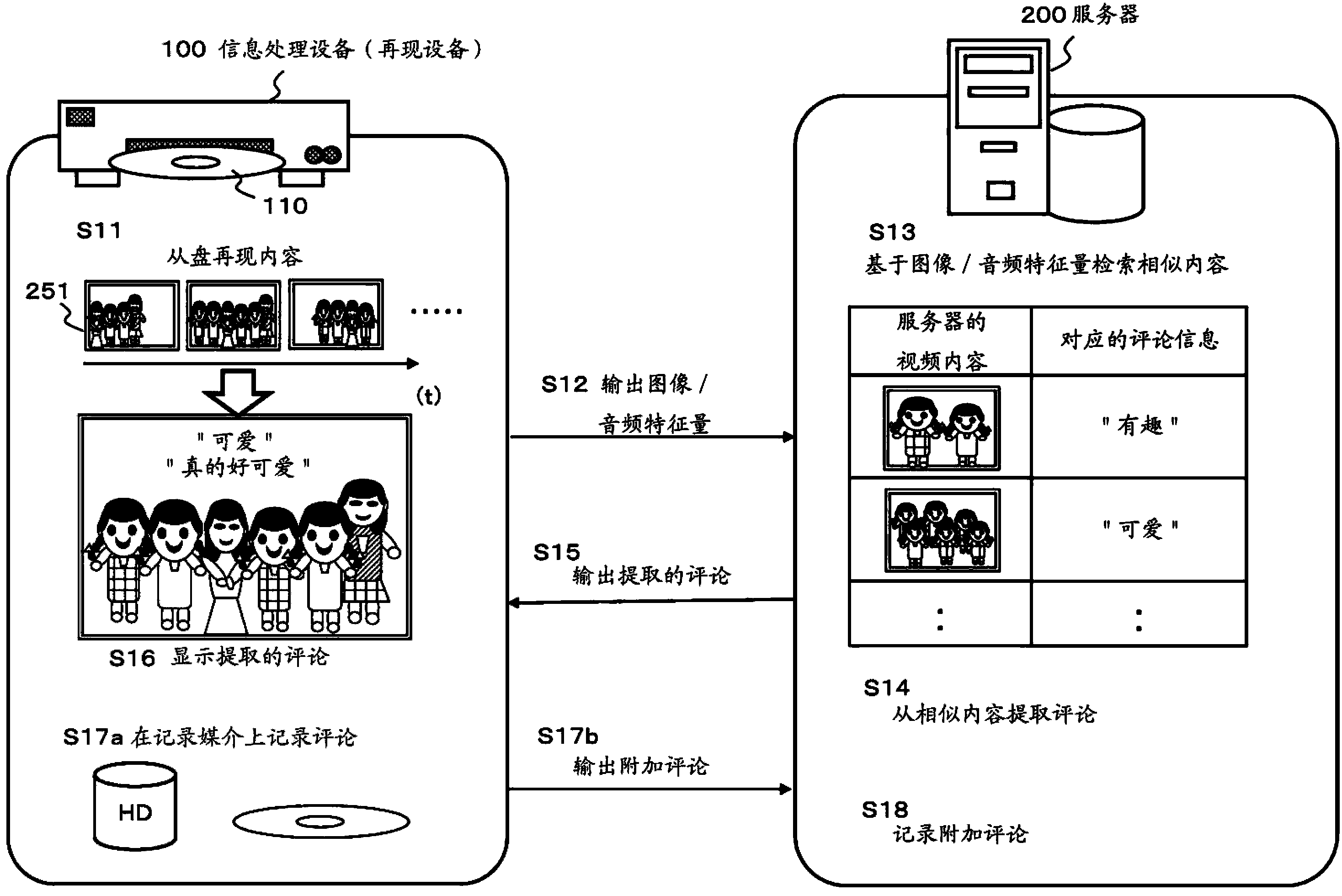
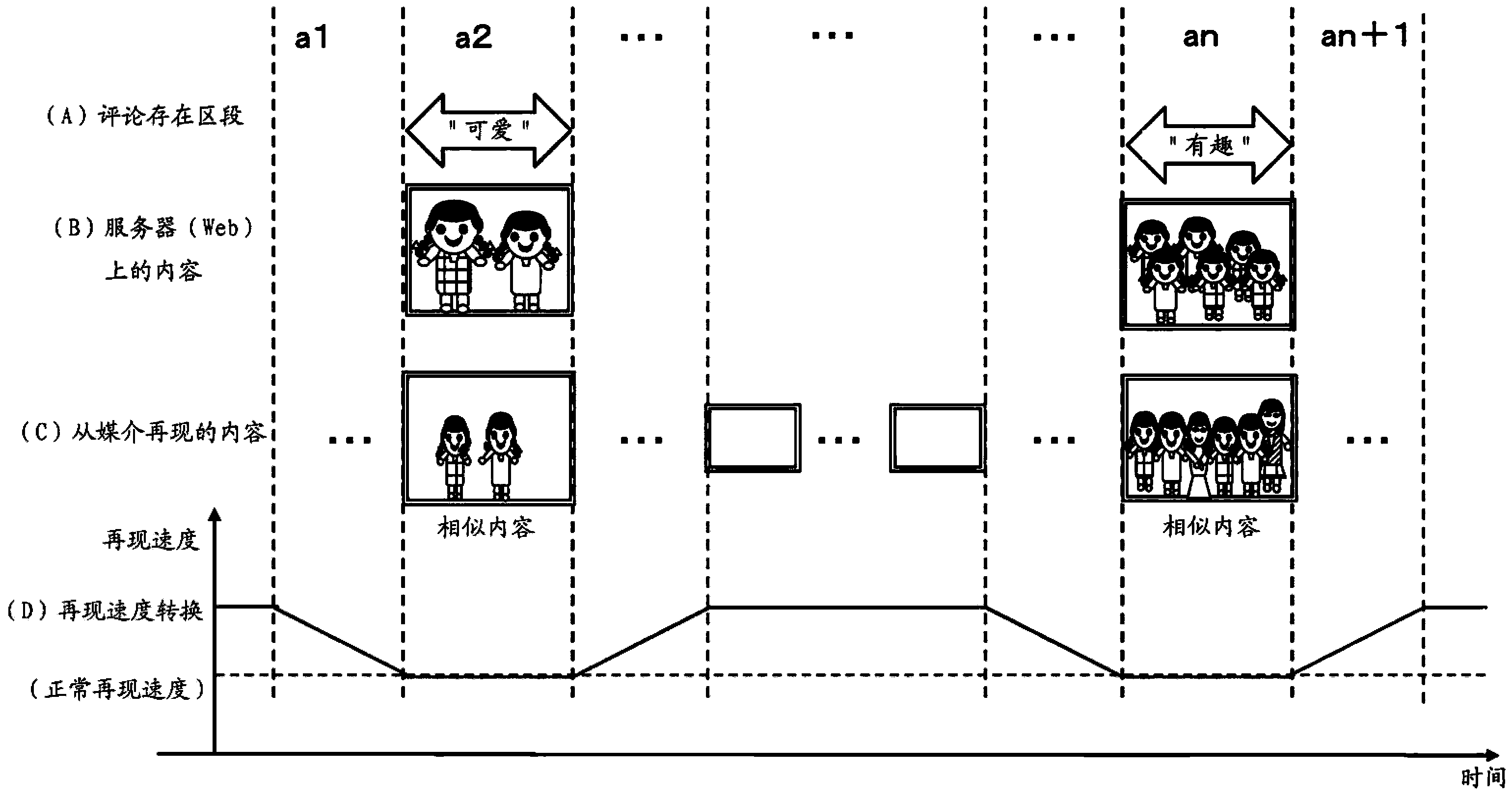
Information processing device, information processing method and program
InactiveCN103455539ATransmissionSelective content distributionFeature extractionInformation processing
Owner:SONY CORP
Session intention recognition method and device based on prompt learning and electronic equipment
PendingCN114330371AImprove accuracyCharacter and pattern recognitionNatural language data processingFeature extractionIntent recognition
The invention discloses a prompt learning-based session intention recognition method and device, electronic equipment and a computer readable medium. The method comprises the following steps: performing voice recognition and audio hidden feature extraction on session voice to obtain a session text and audio hidden features corresponding to the session voice; establishing a prompt according to the relevance between the session text and the audio hidden feature; and training a machine learning model by using the session text, the audio hidden feature, the prompt and the corresponding intention of the historical session voice, and processing the session text, the audio hidden feature and the prompt of the new session voice by using the machine learning model to identify the session intention of the new session voice. Due to the fact that prompt learning and self-supervised training based on the pre-training model are adopted, and the audio hidden features of the session voice are introduced into intention recognition, the intention recognition accuracy can be improved.
Owner:BEIHAI QIANG INFORMATION TECH CO LTD
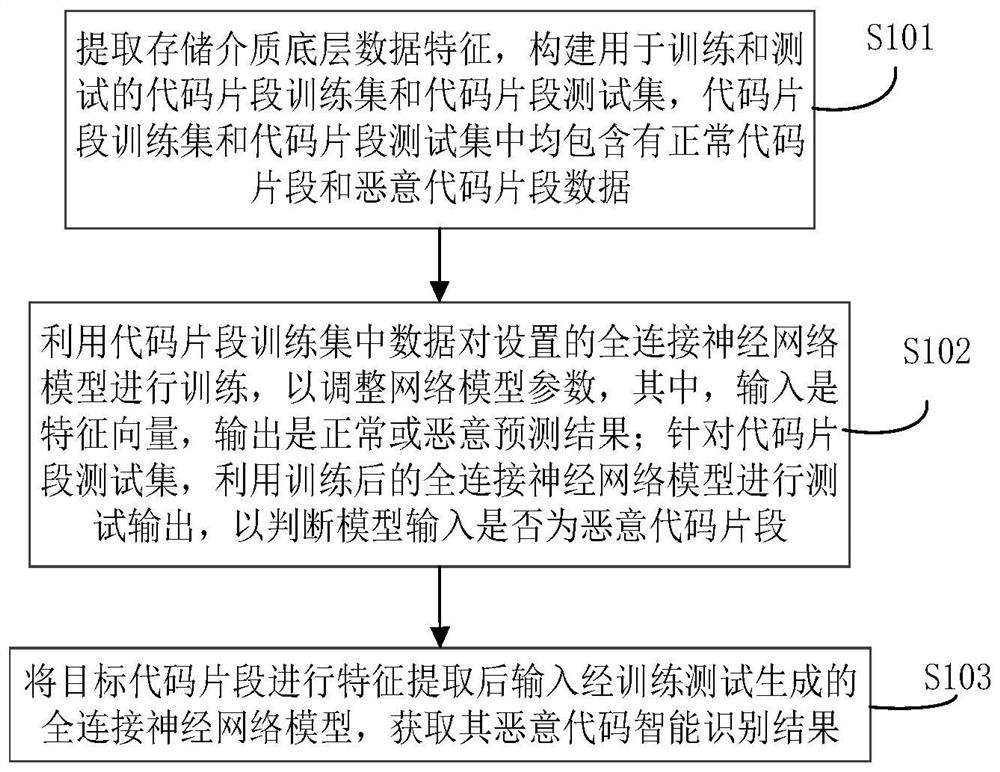
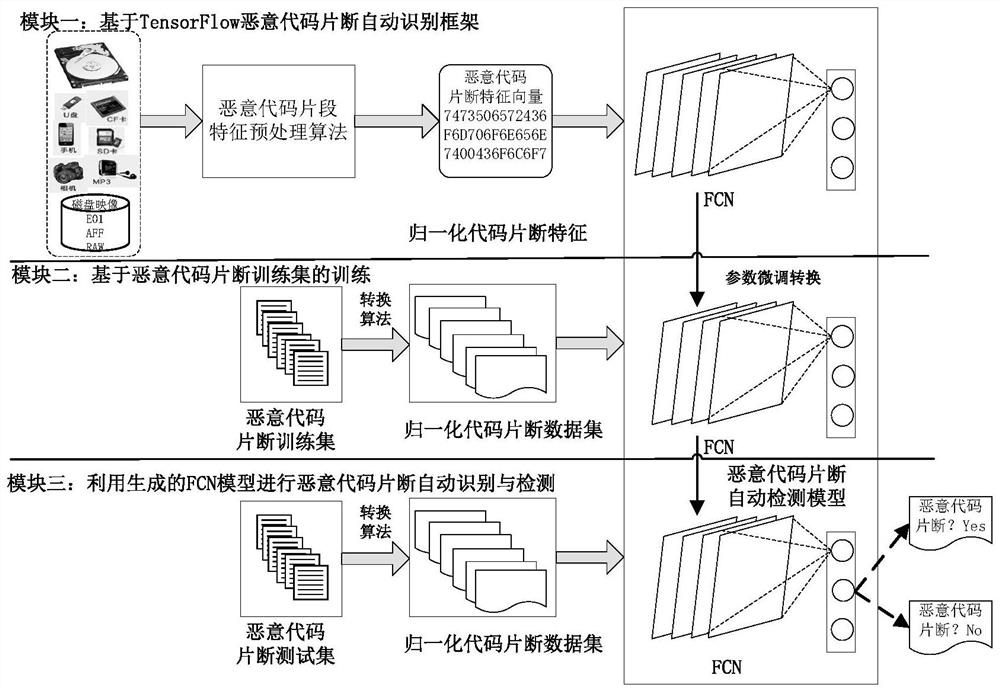
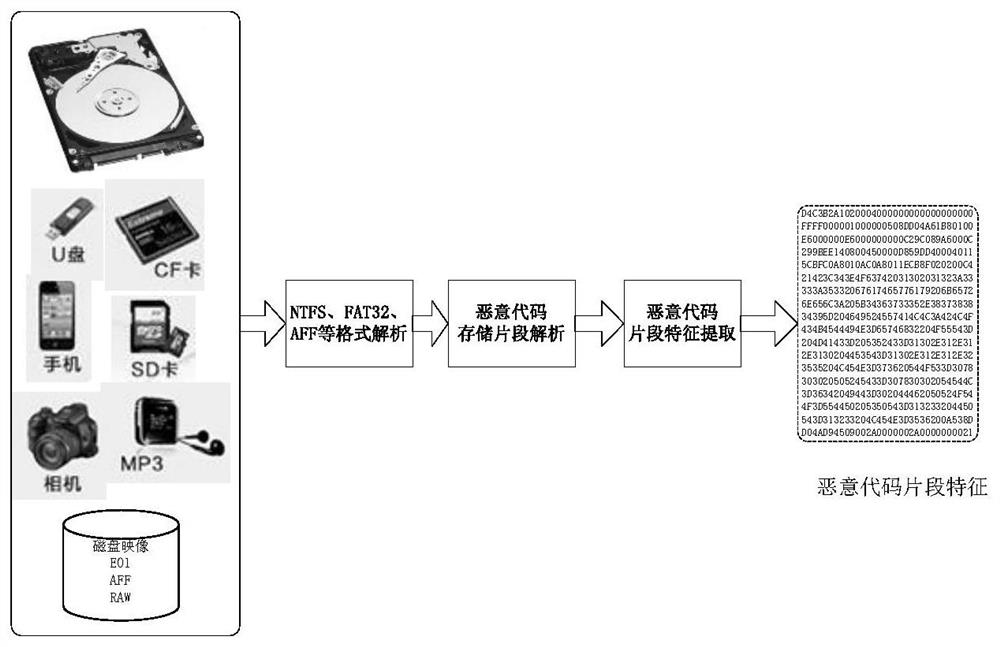
Intelligent malicious code fragment evidence obtaining method and system
ActiveCN111881447ACharacter and pattern recognitionPlatform integrity maintainanceFeature vectorFeature extraction
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
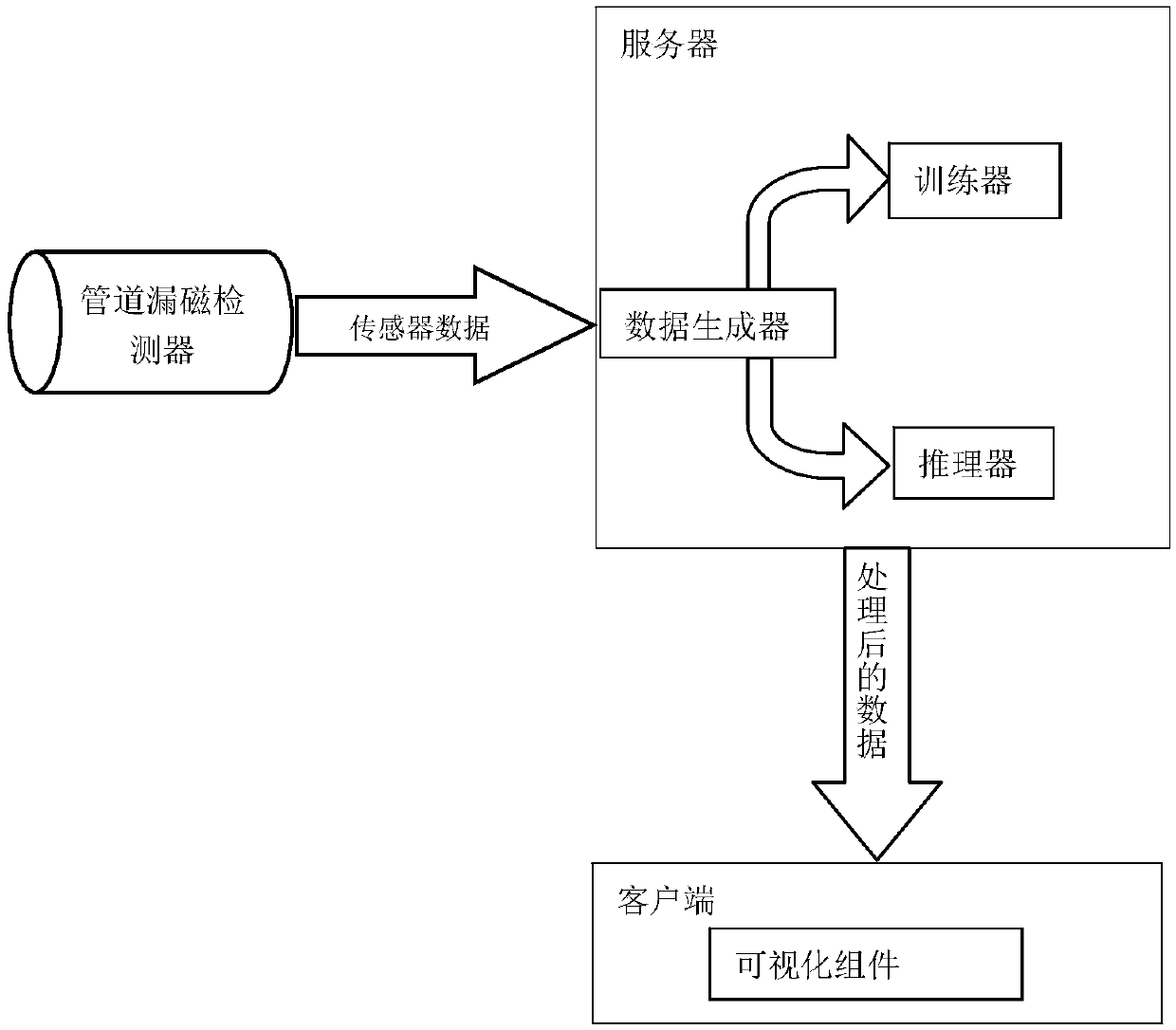
Pipeline magnetic flux leakage detecting data automatic analysis system
Owner:智云安科技(北京)有限公司
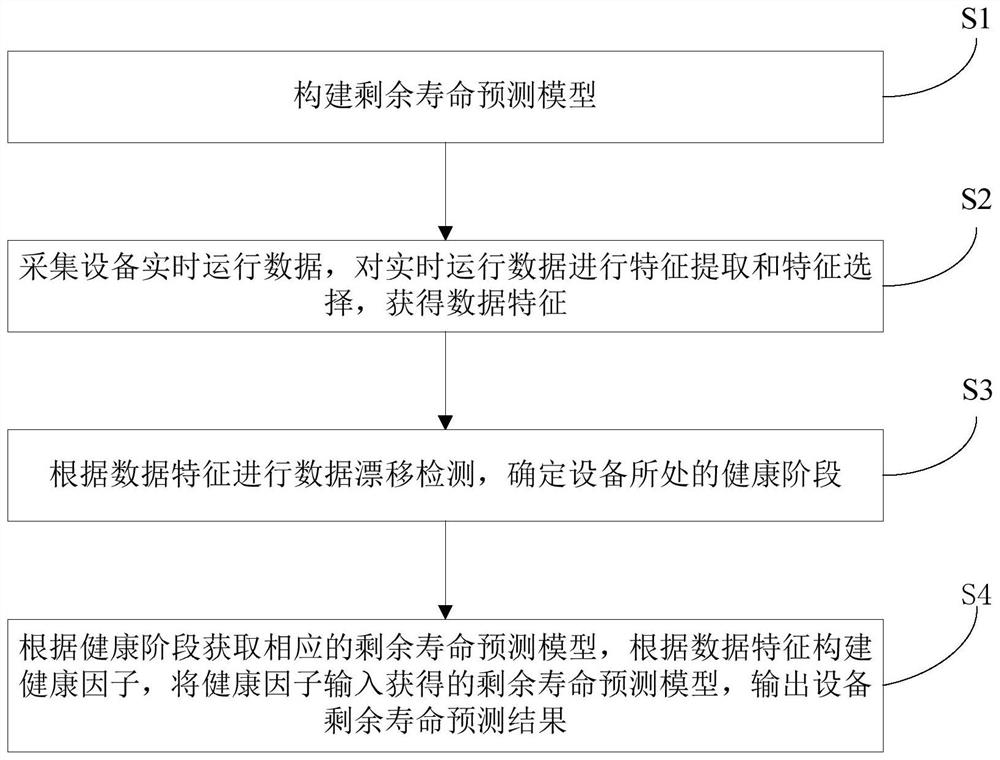
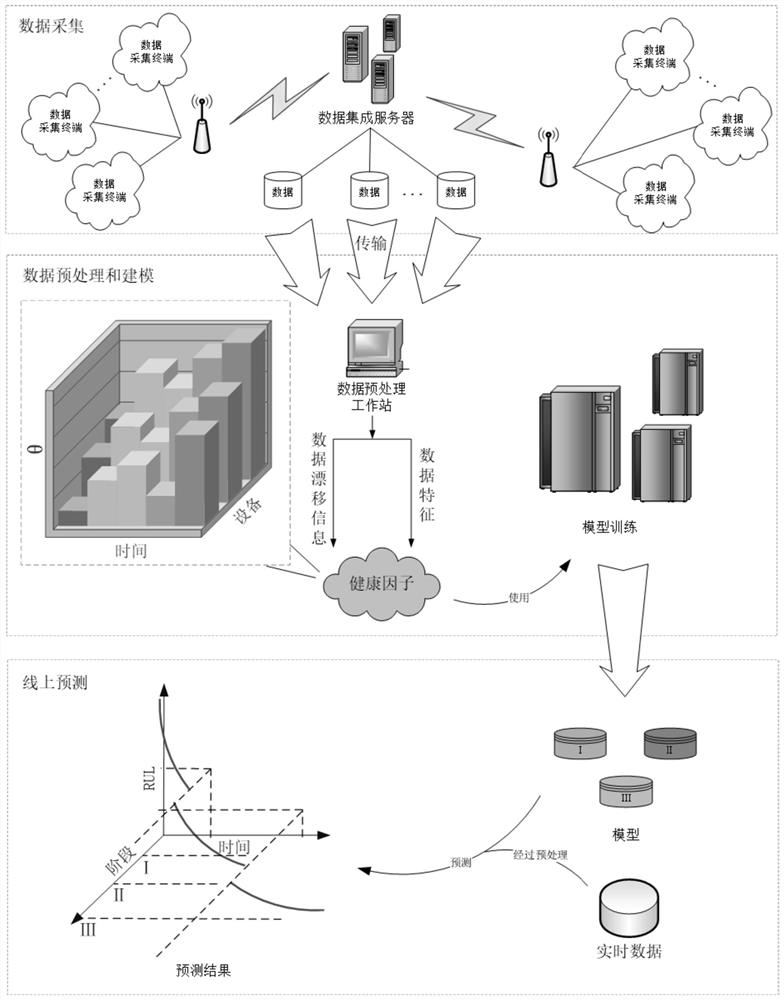
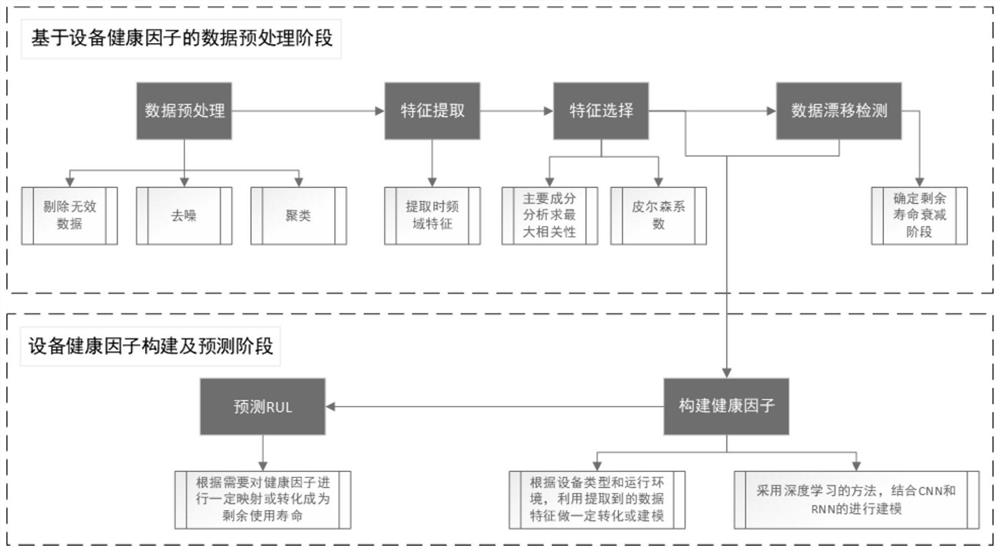
Equipment residual life prediction method and system based on industrial big data, and medium
ActiveCN113344295AOvercome dependenceOvercoming the pitfalls of machine alarmsForecastingCharacter and pattern recognitionFeature extractionAcquisition apparatus
Owner:SOUTH CHINA UNIV OF TECH
Product packaging defect detection and identification method based on machine vision
The invention discloses a product packaging defect detection and recognition method based on machine vision. The method comprises steps that firstly, a product packaging processing image without surface defects is extracted; a defect image template feature database is established; feature extraction, detection and identification of the packaging image of the to-be-detected product are carried out;and finally, the unqualified packaged products are blown into the collecting box, and the qualified packaged products are conveyed by the conveying belt to be output. The method is advantaged in thatproblems that in the prior art, the product packaging defect detection error rate is high, and production efficiency is low are solved.
Owner:SHAANXI UNIV OF SCI & TECH
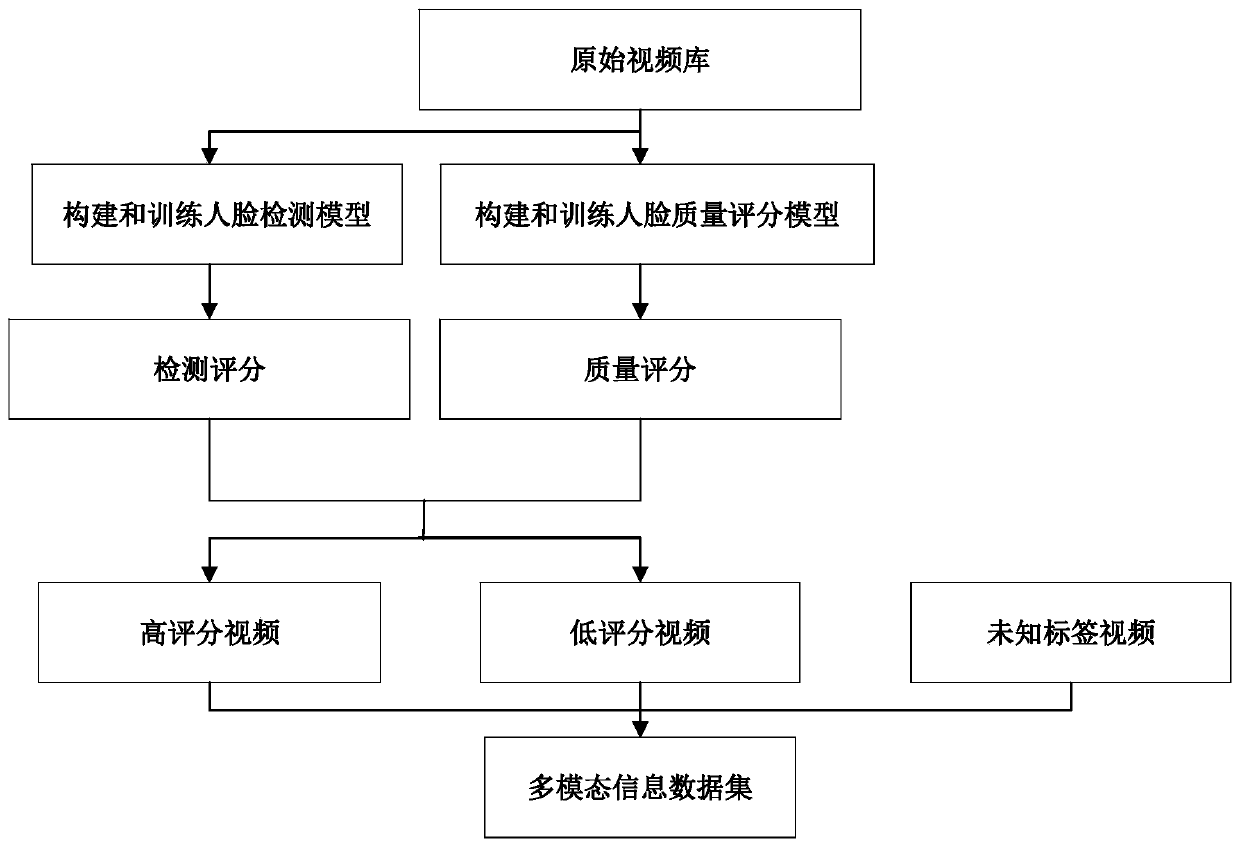
Identity recognition method based on multi-modal information
ActiveCN110674483ASolve the technical problem of screening out the multi-modal information data that meets the requirementsSolve the problem of not being able to identifyDigital data authenticationMultiple biometrics useFace detectionData set
Owner:GUANGDONG UNIV OF TECH
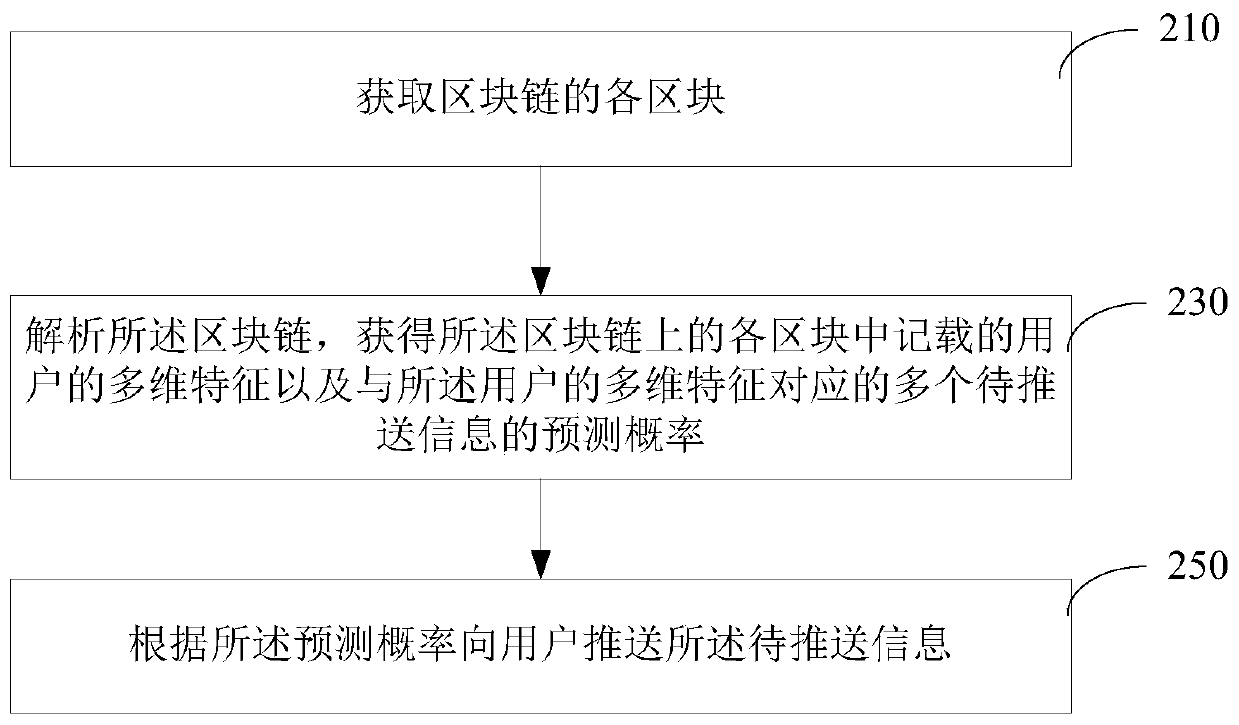
Information pushing method and device based on block chain, computer and storage medium
PendingCN110247974APush accurate and timelyRelieve pressureData switching networksSecuring communicationFeature extractionPrediction probability
Owner:DONGGUAN MENGDA INDAL INVESTMENT
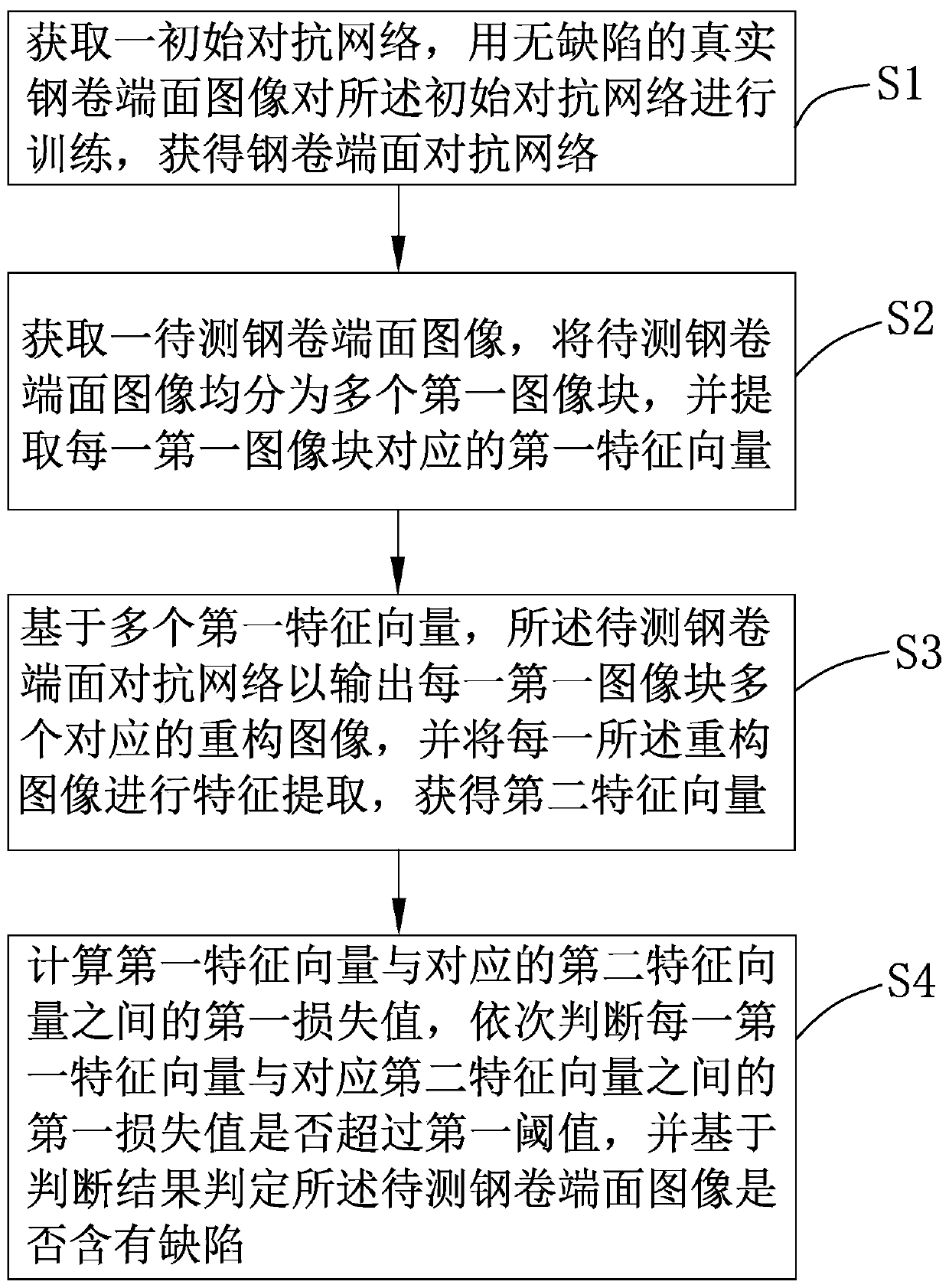
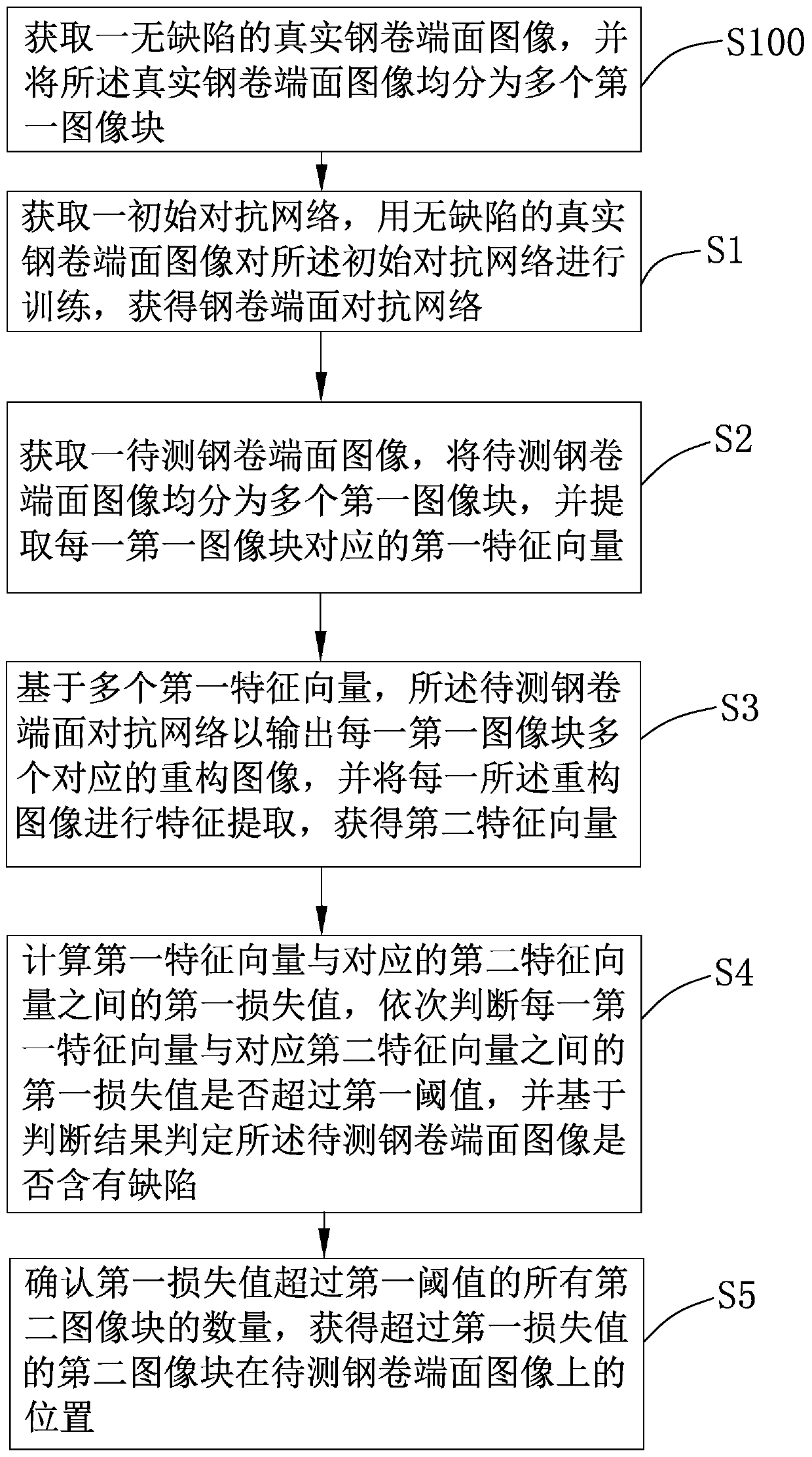
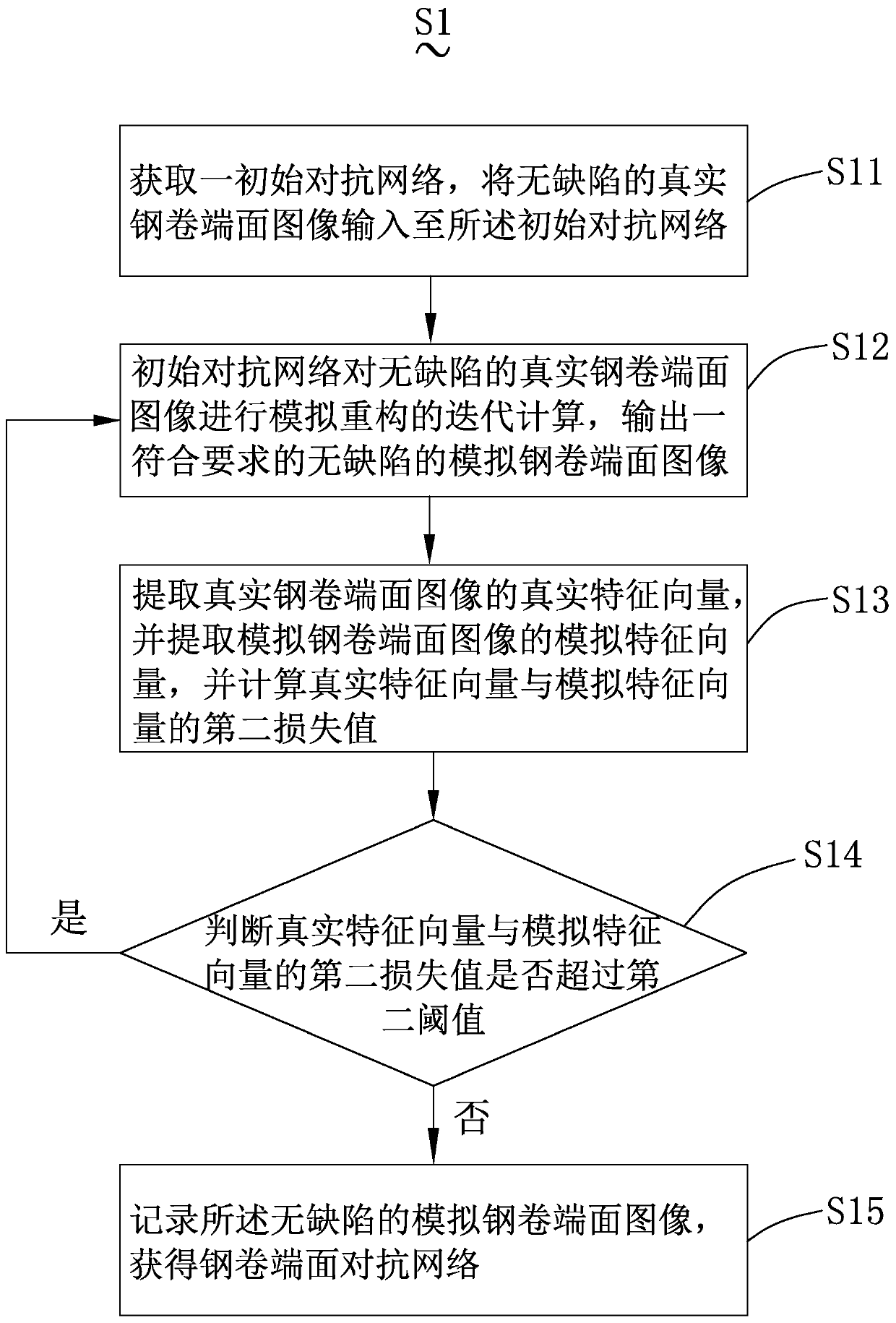
Steel coil end face defect distinguishing method and system and electronic device
PendingCN110349144AImprove recognition efficiencyReduce dependenceImage enhancementImage analysisFeature vectorFeature extraction
Owner:创新奇智(广州)科技有限公司
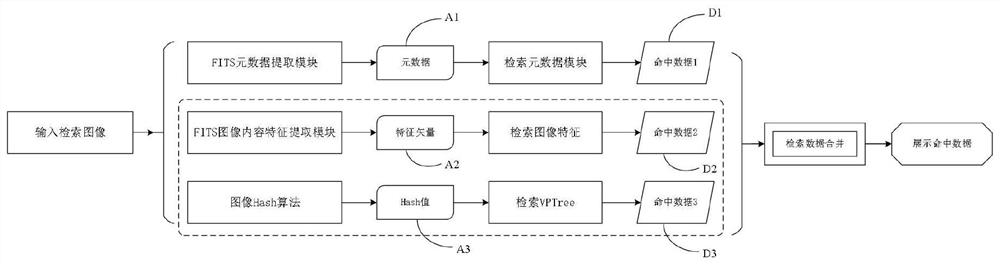
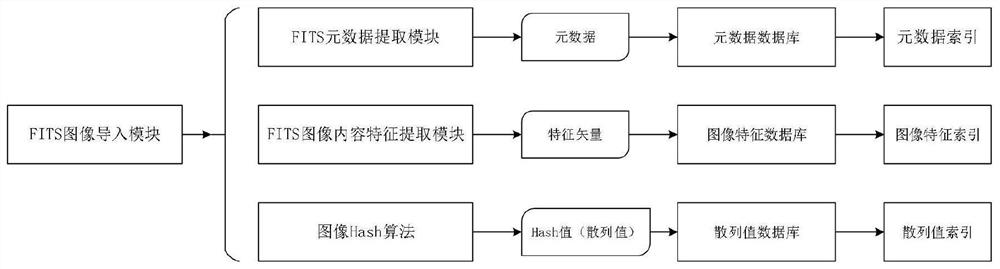
Astronomical mass observation data hybrid retrieval method based on image content and metadata
PendingCN112182276AHigh speedImprove retrieval accuracyStill image data indexingVectoral format still image dataData setData query
Owner:YUNNAN UNIVERSITY OF FINANCE AND ECONOMICS
Data recommendation method and device based on deep learning and terminal device
PendingCN110297973ARapid Initial ScreeningAccurate initial screeningDigital data information retrievalOffice automationFeature extractionTerminal equipment
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
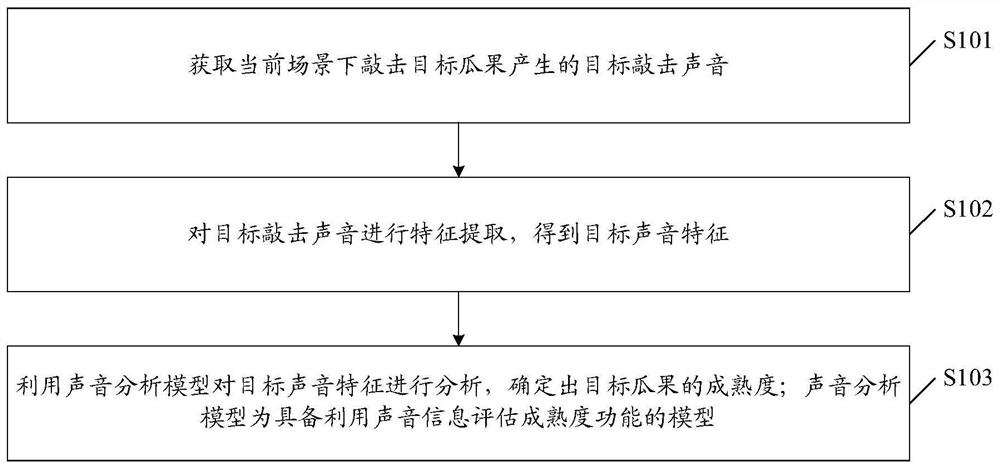
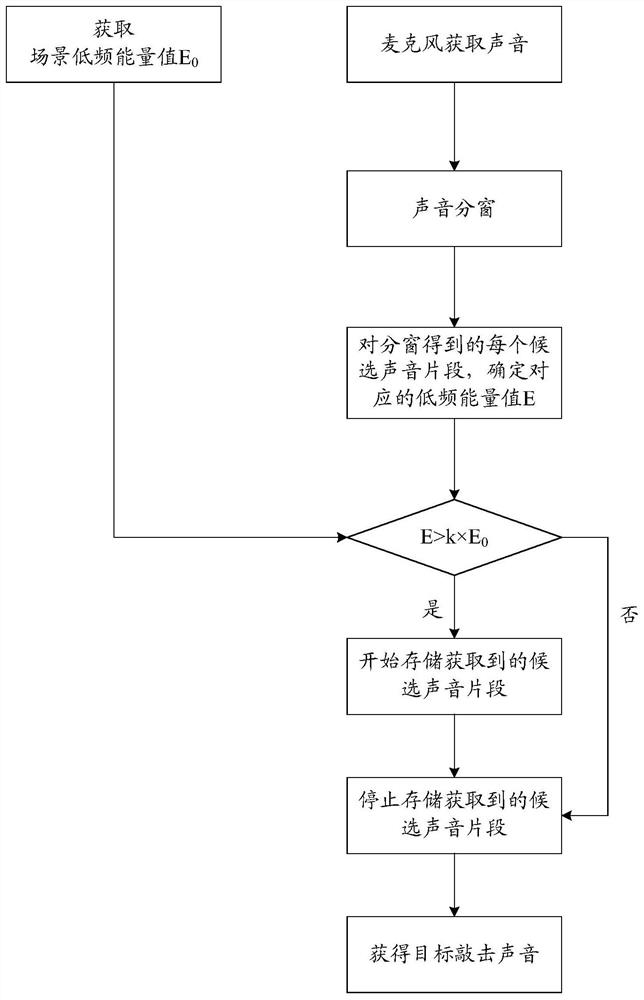
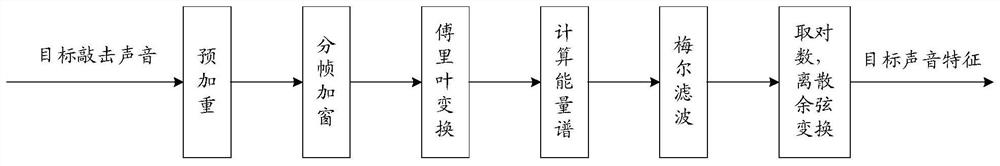
Maturity evaluation method and device and storage medium
ActiveCN111640451AMaturity determinationImprove accuracySpeech analysisFeature extractionSound analysis
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD +1
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap