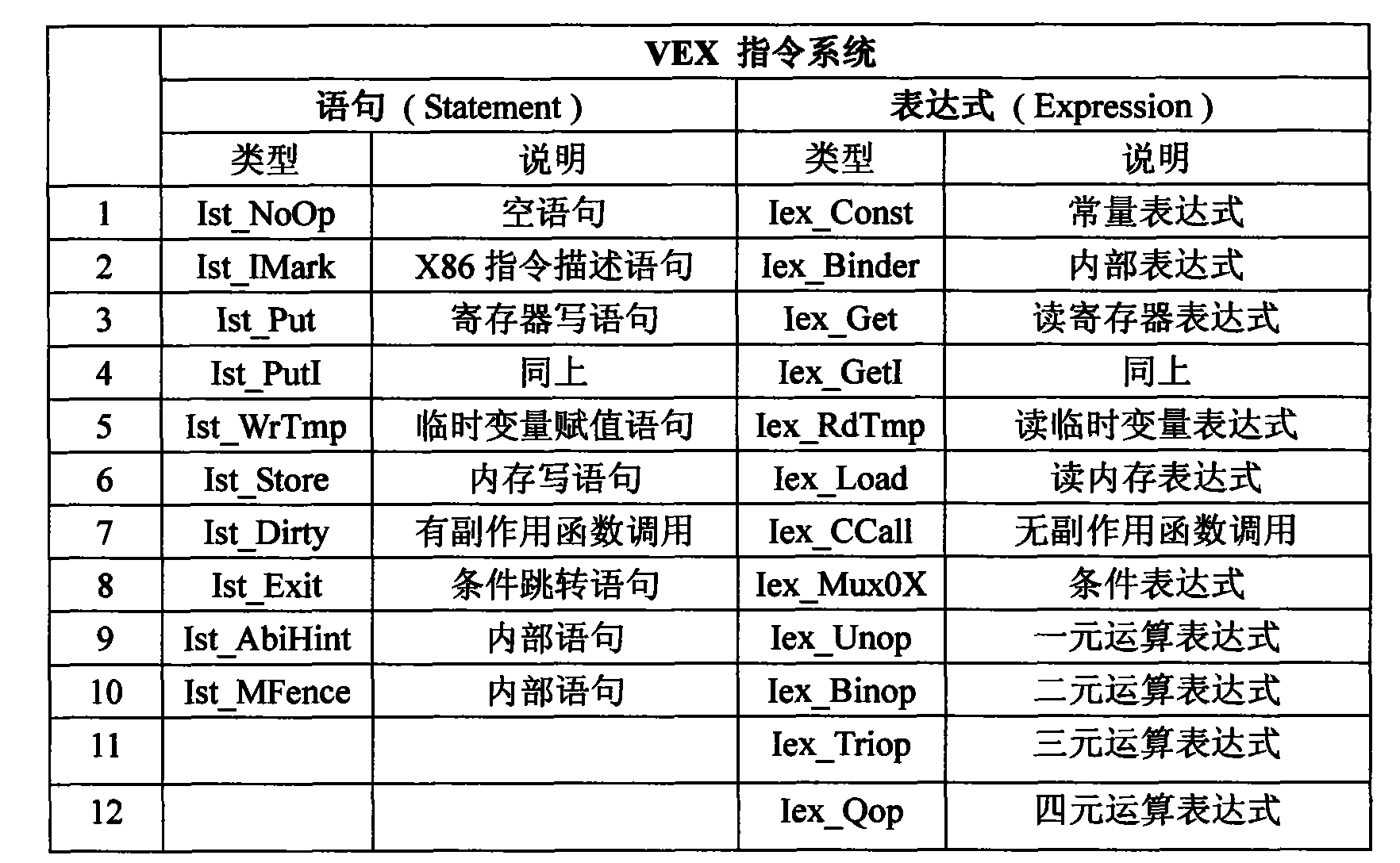
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
63results about "Platform integrity maintainance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
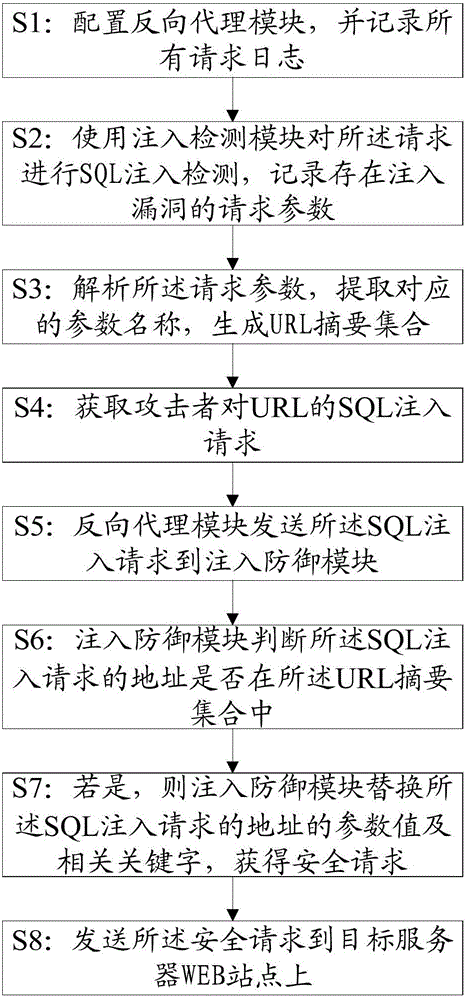
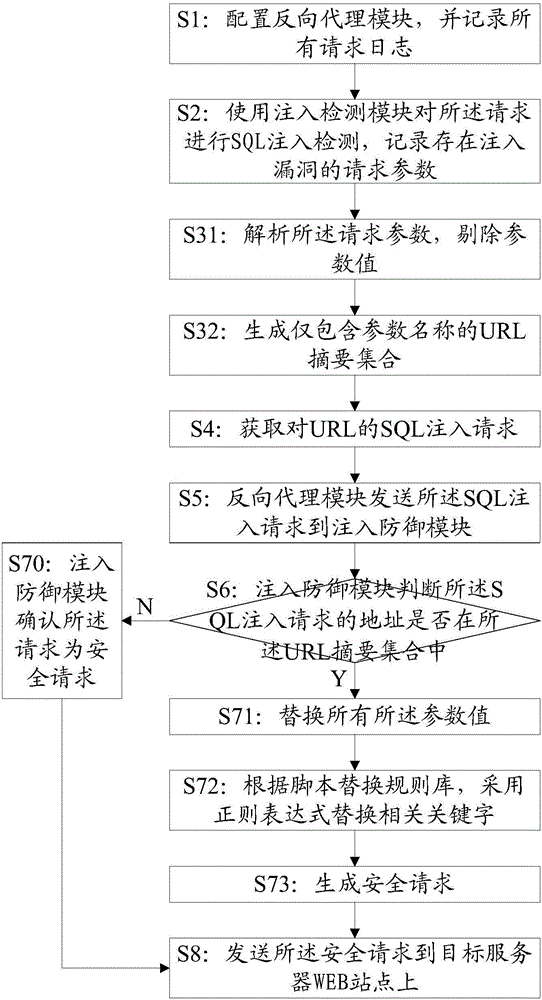
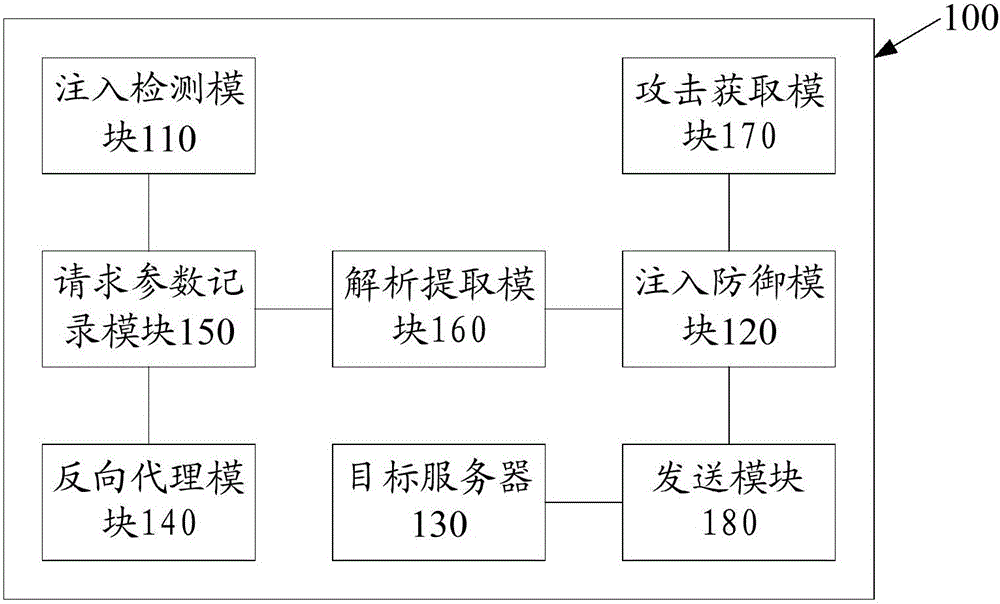
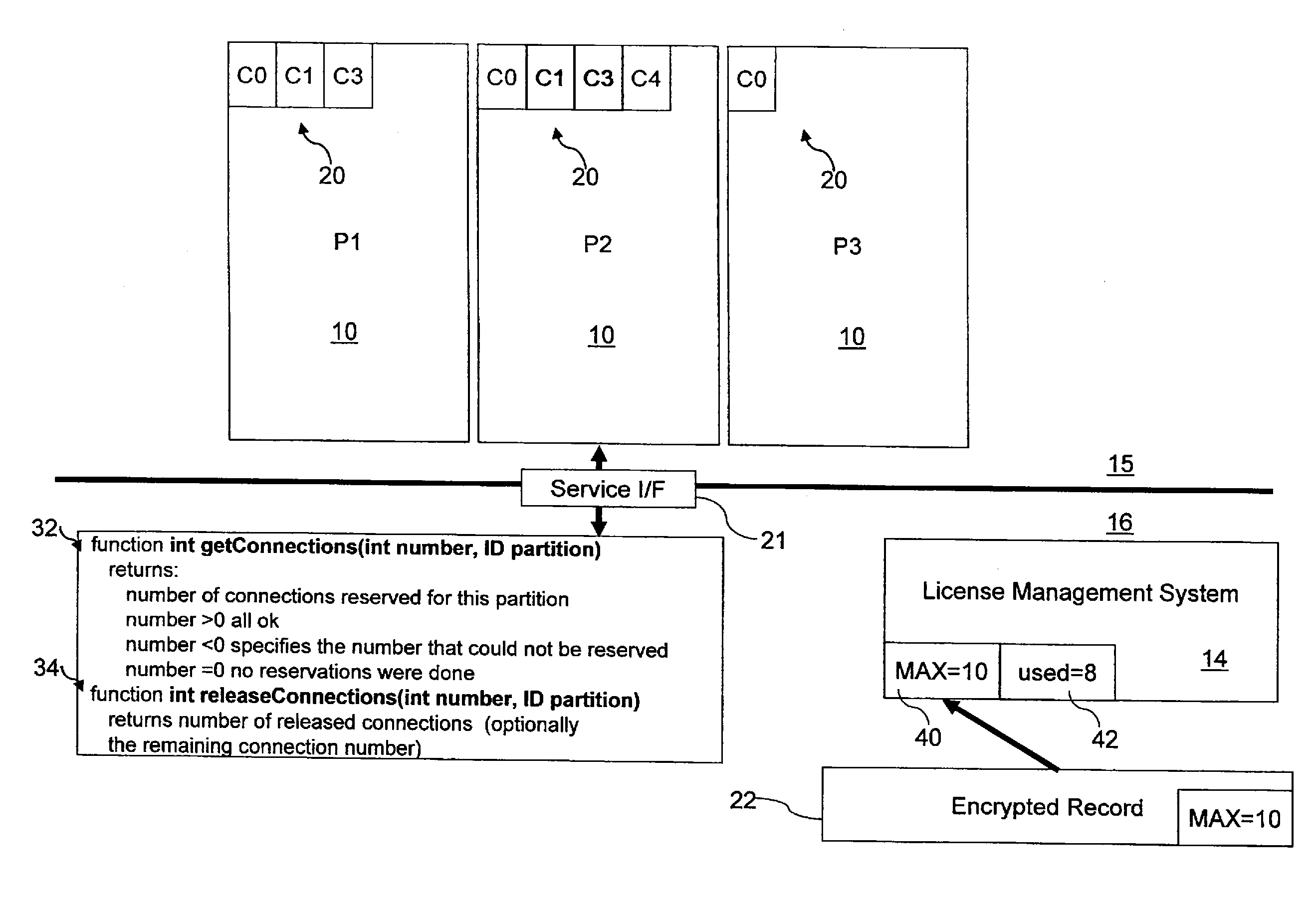
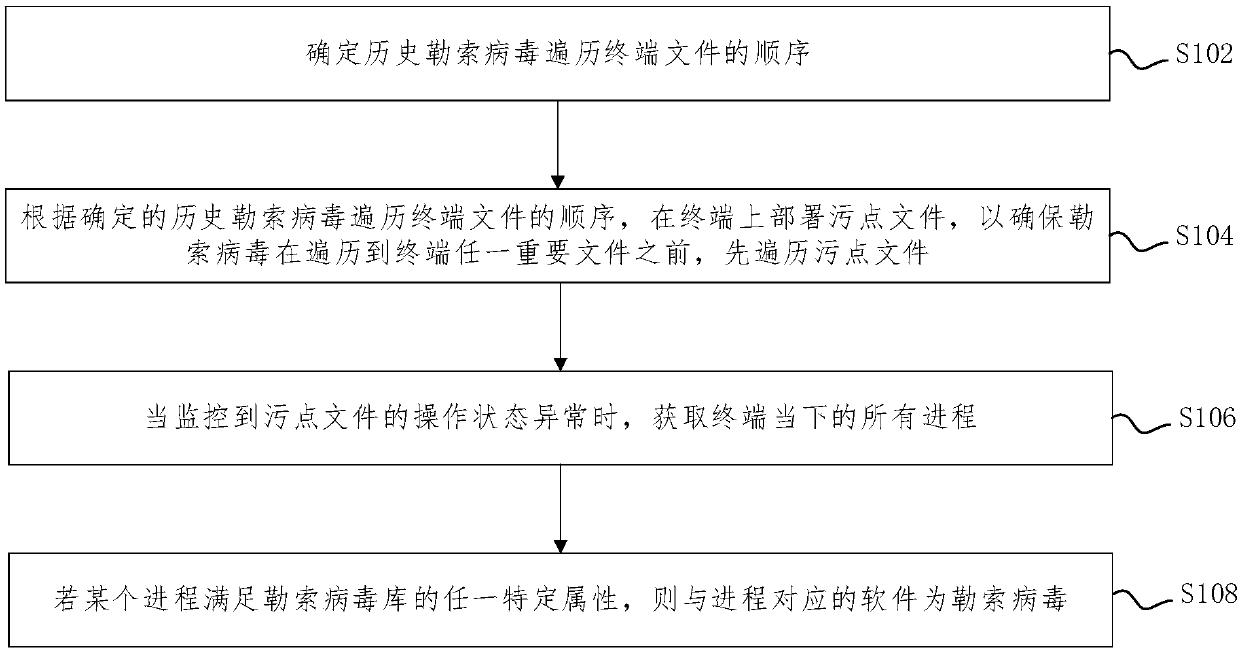
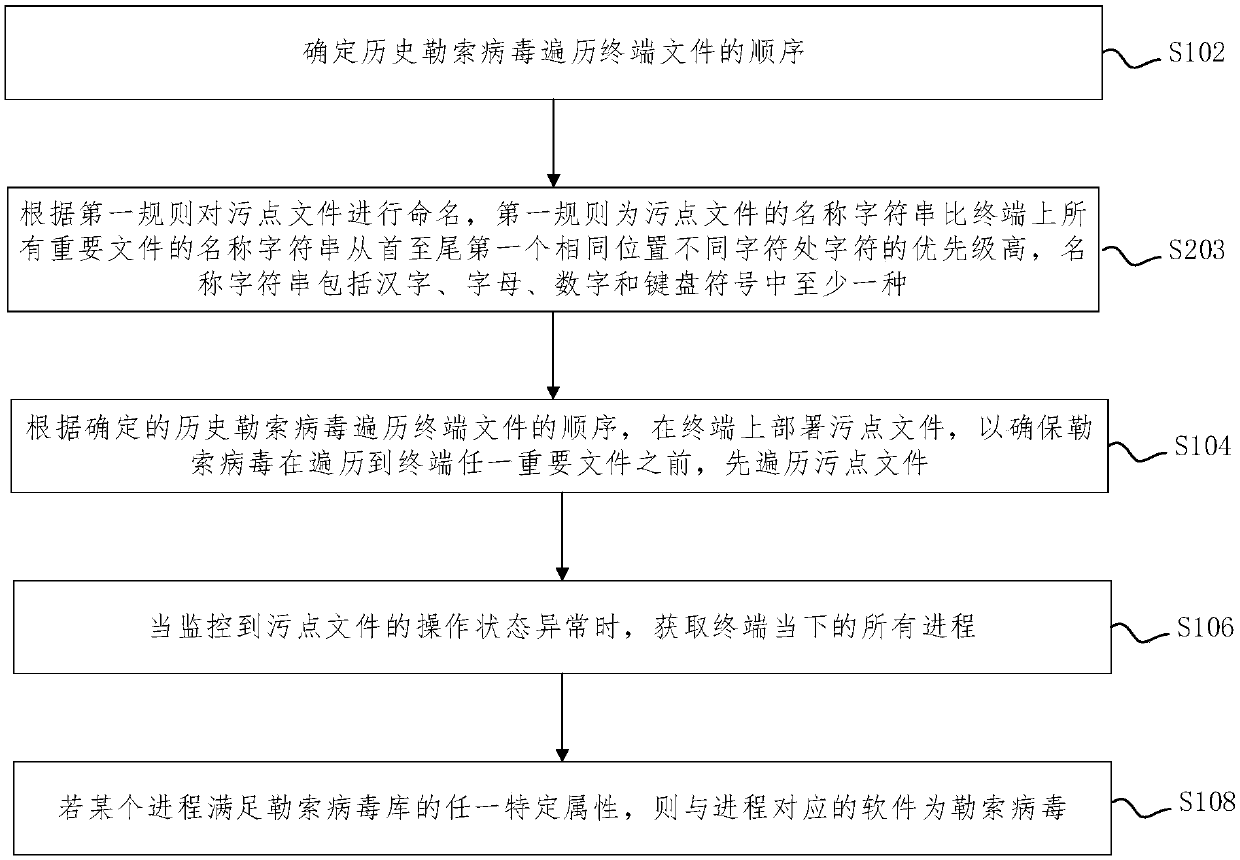
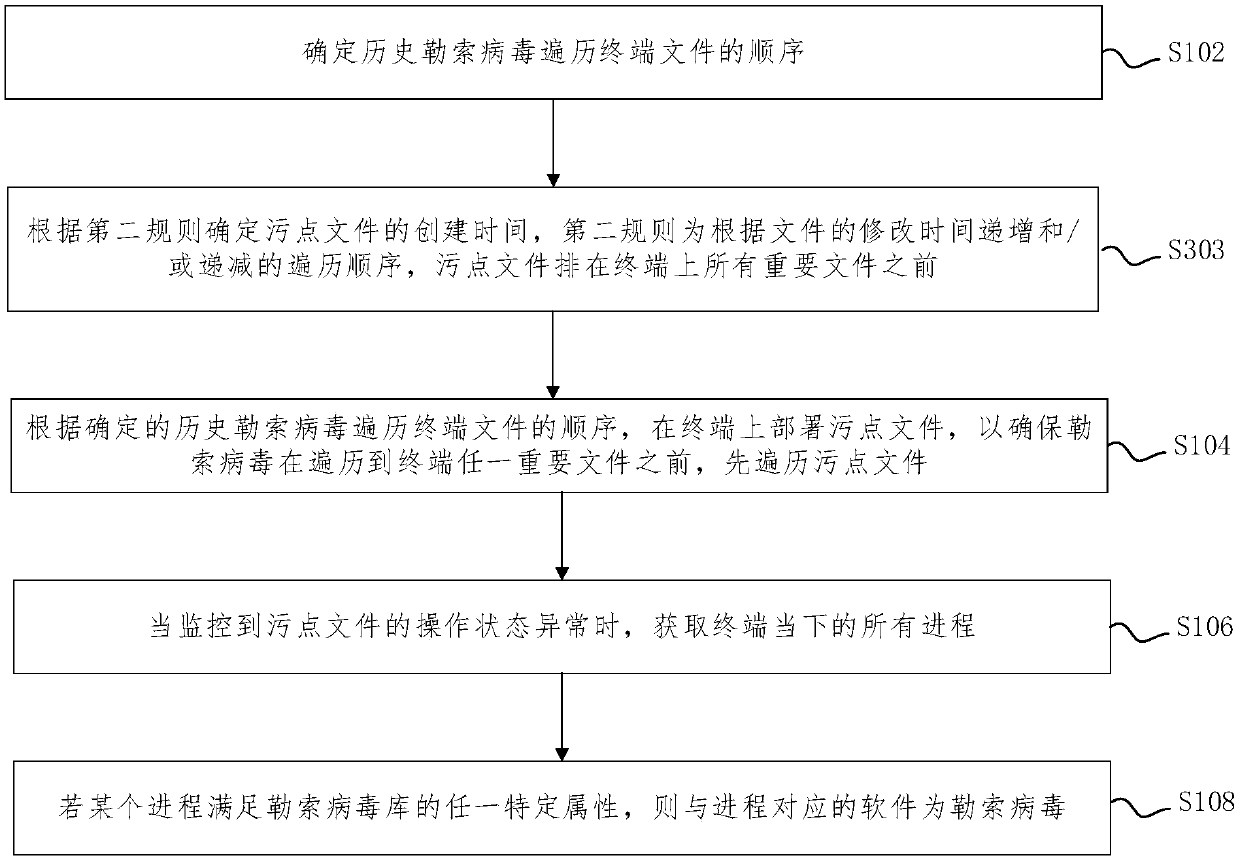
Application program control method based on two-time signature verification technology
ActiveCN103886260AEnsure safetyProgram loading/initiatingPlatform integrity maintainanceThird partyApplication software
An application program control method based on a two-time signature verification technology is achieved by performing two times of signing and two times of signature verification on application programs on an android terminal. Security detection is performed on the application programs through a reliable third-party security detection mechanism, the application programs passing the detection will be signed by the third-party security detection mechanism, and then the signed applications are returned to developers. When the application programs are installed on the intelligent android terminal, security detection is performed on the application programs first to see whether the application programs are signed by the third-party security detection mechanism or not, and signatures are verified; if signatures of the third-party detection mechanism do not exist or the signatures cannot pass verification, installation of the application programs is refused. Through the technical scheme, the application program control method based on the two-time signature verification technology has the advantages that signature information is fixed through introduction of the third-party detection signatures and a security control module of the android terminal so that secure application programs can be downloaded and installed in an android system through multiple channels, and while security of the android terminal is guaranteed, a flexible and efficient application program verification scheme is provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
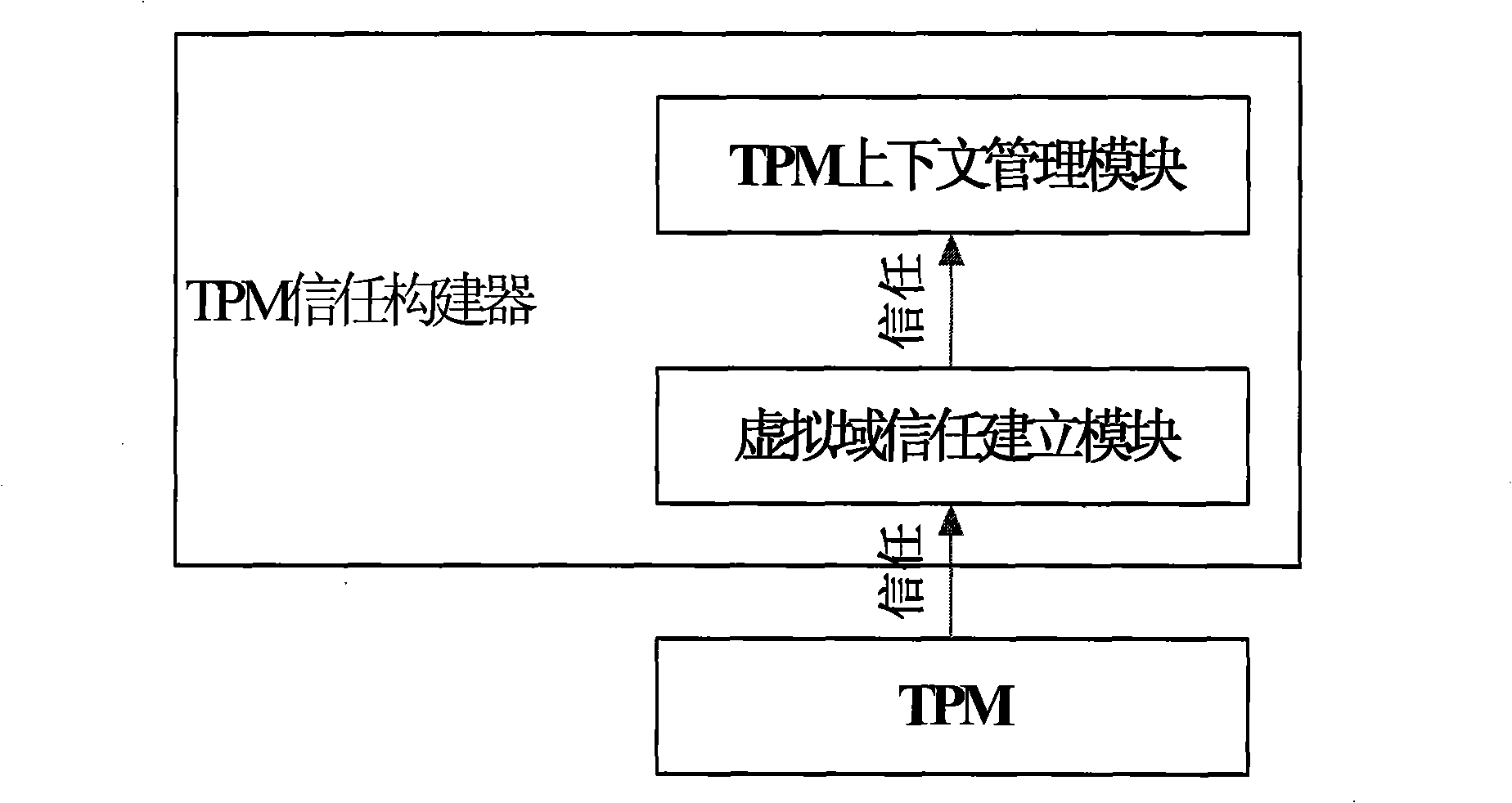
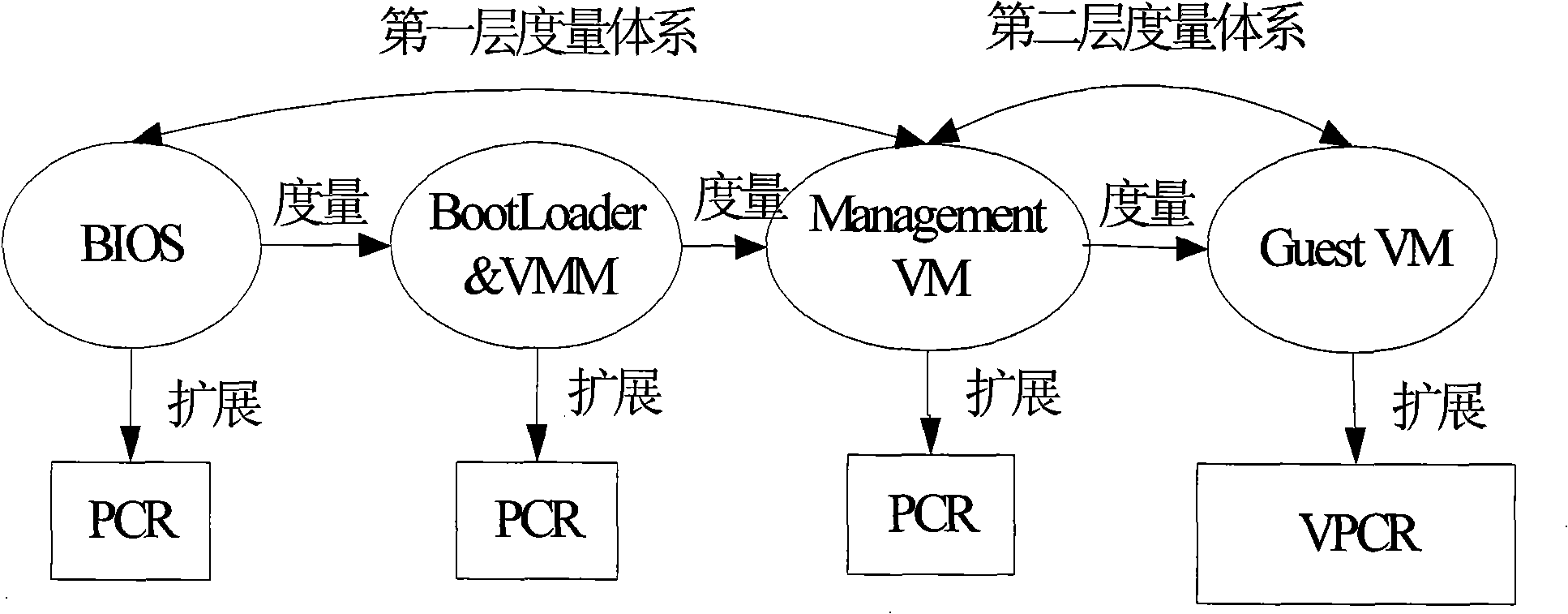
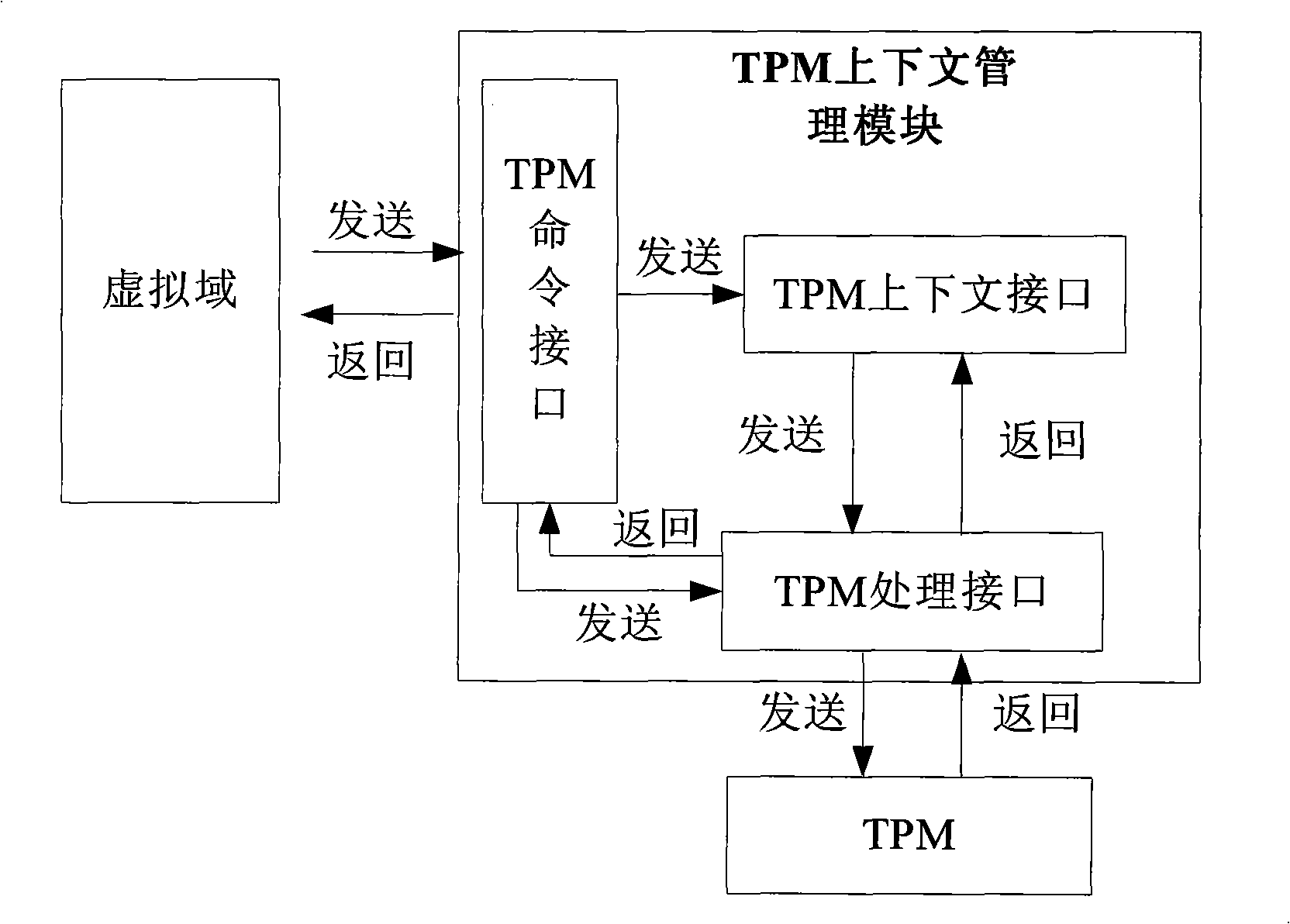
Method for constructing virtual environment trust
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
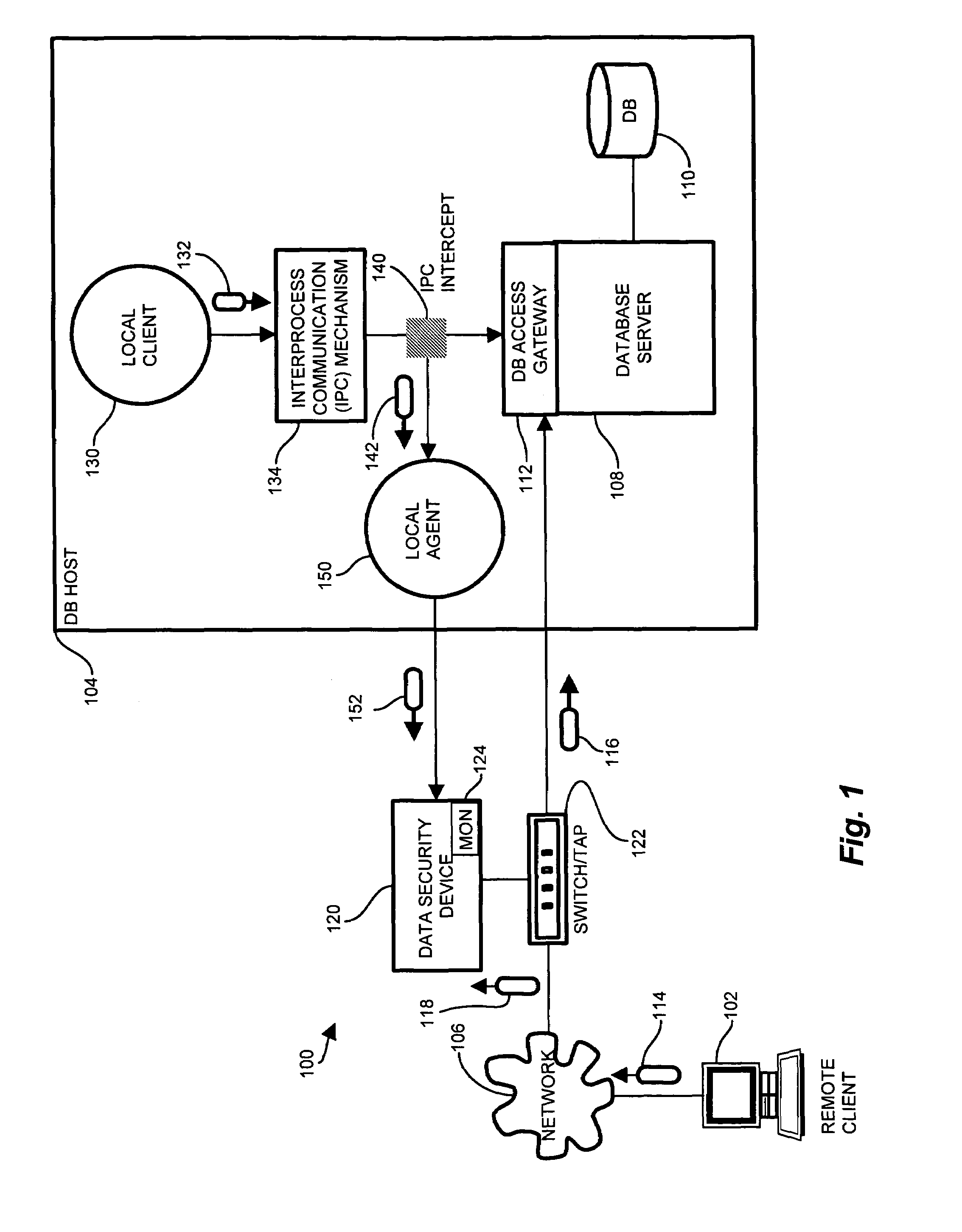
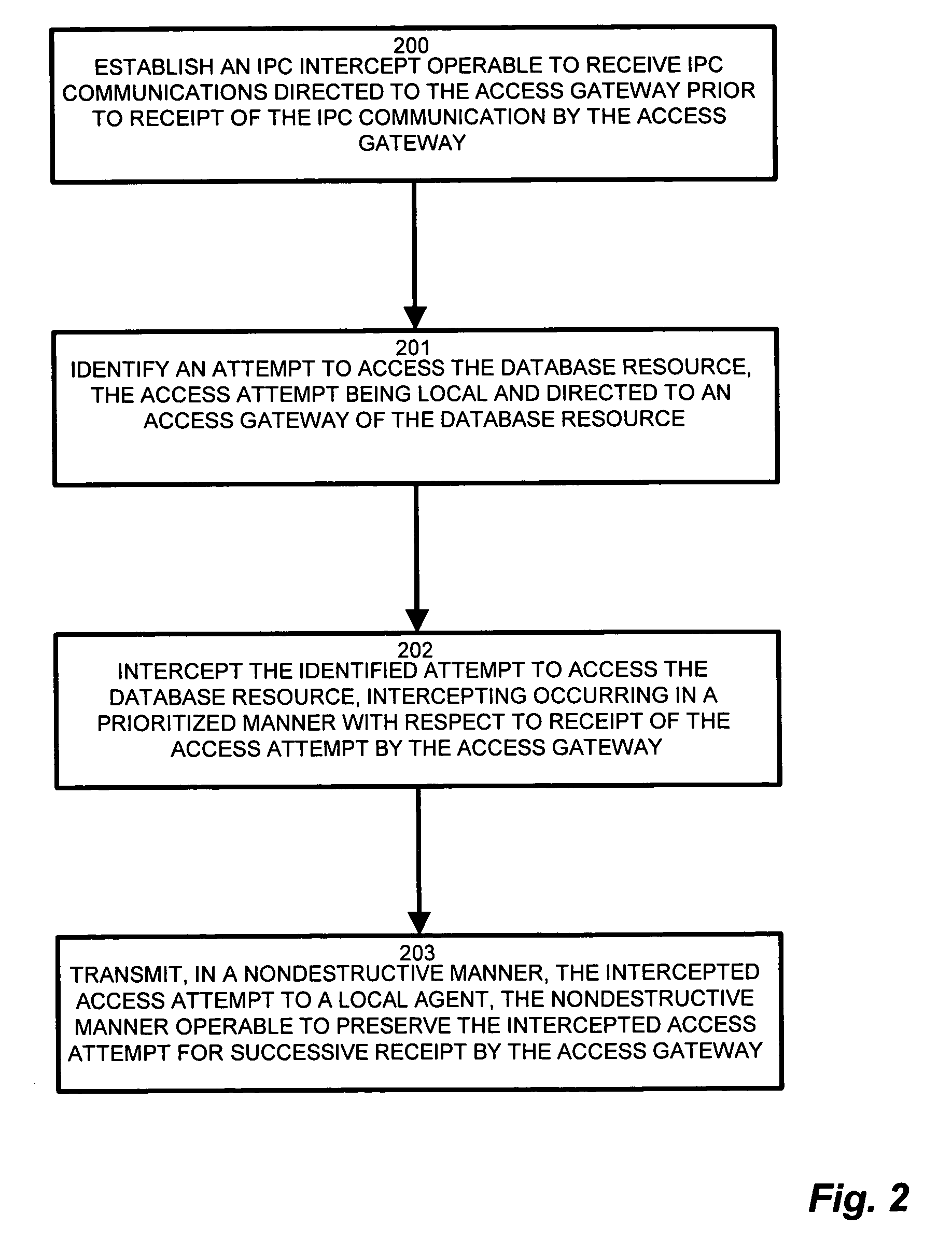
System and methods for tracking local database access
InactiveUS7426512B1Reduce resource overheadReduce overheadDigital data information retrievalData processing applicationsAnalysis dataData access
Owner:IBM CORP
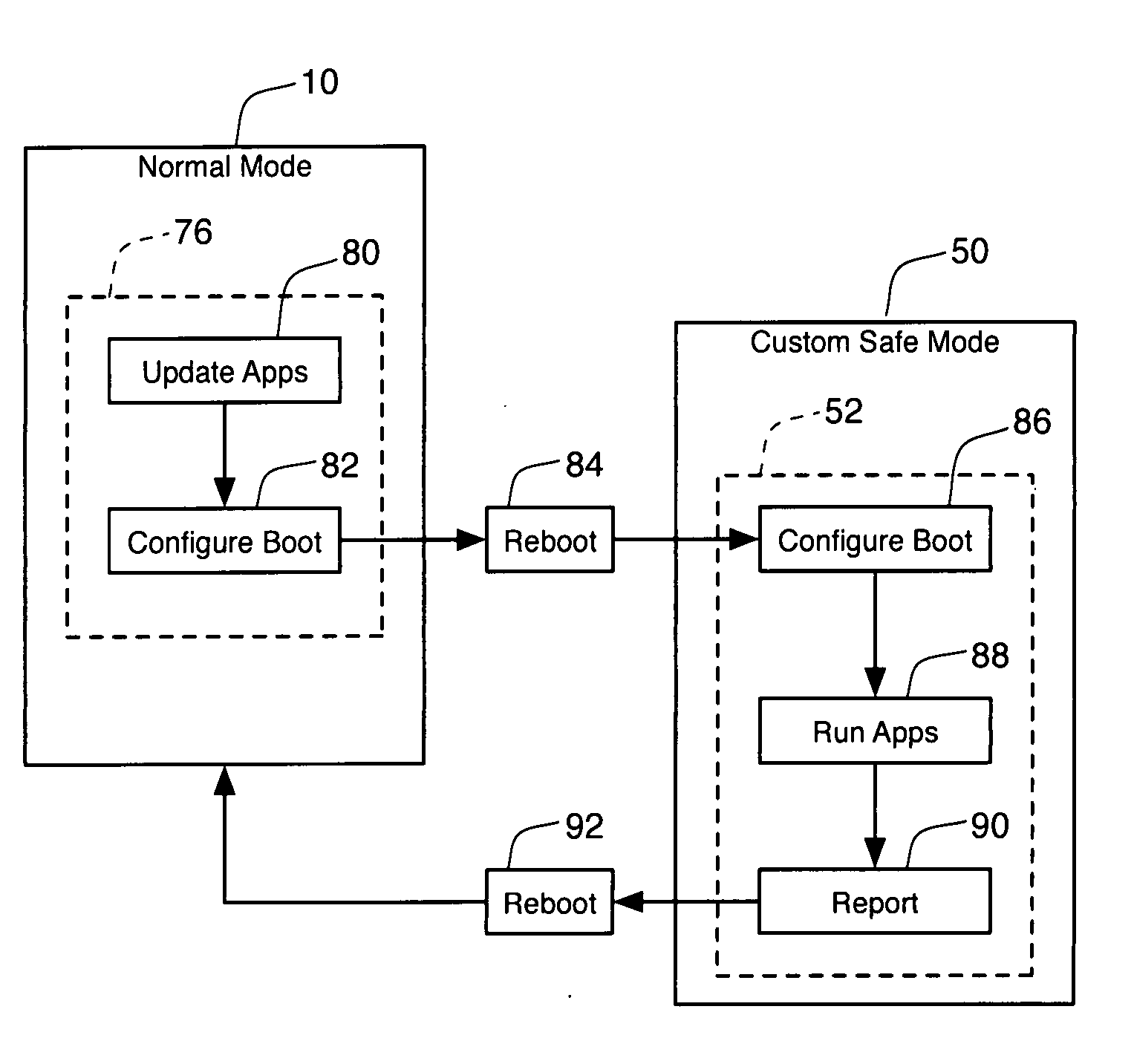
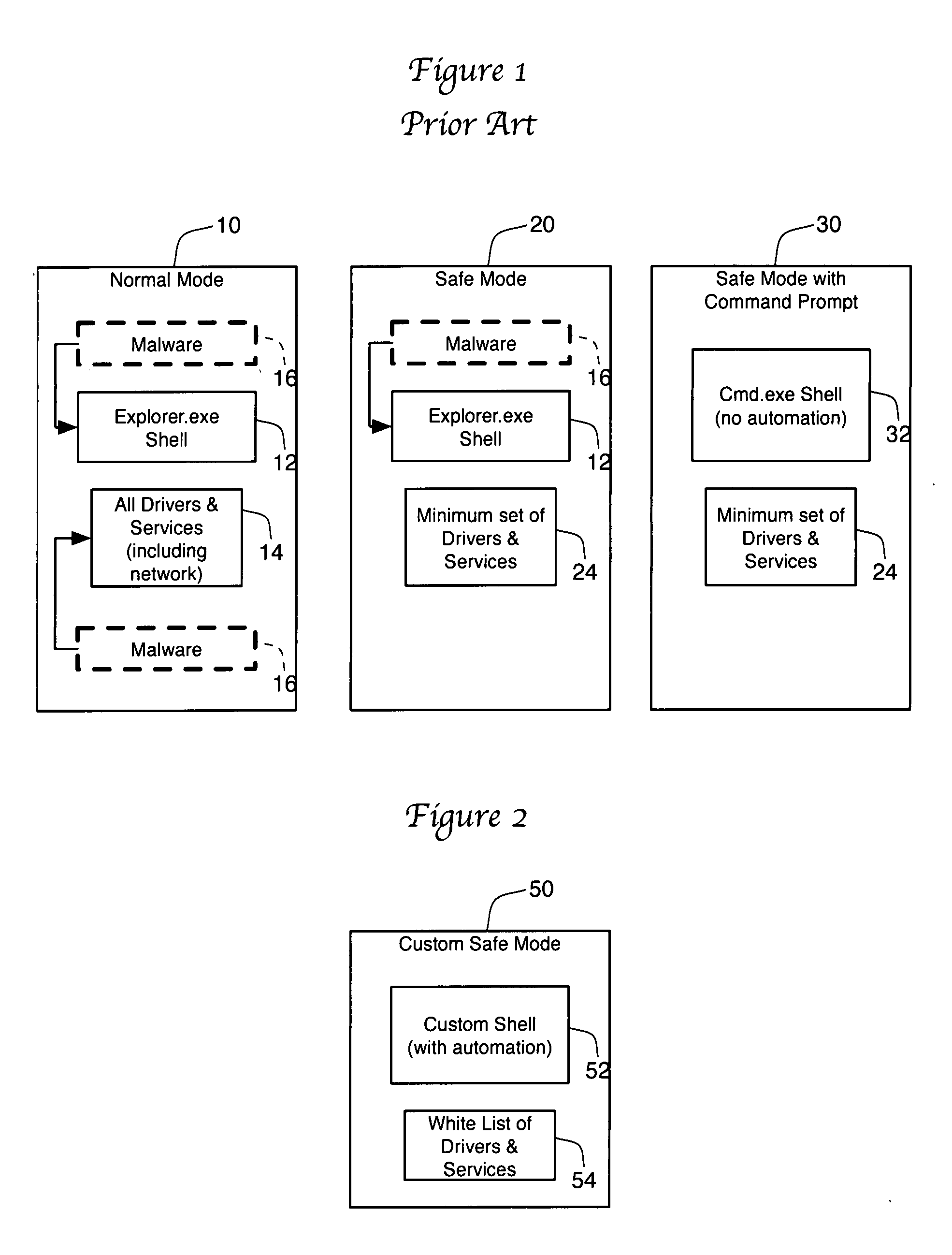
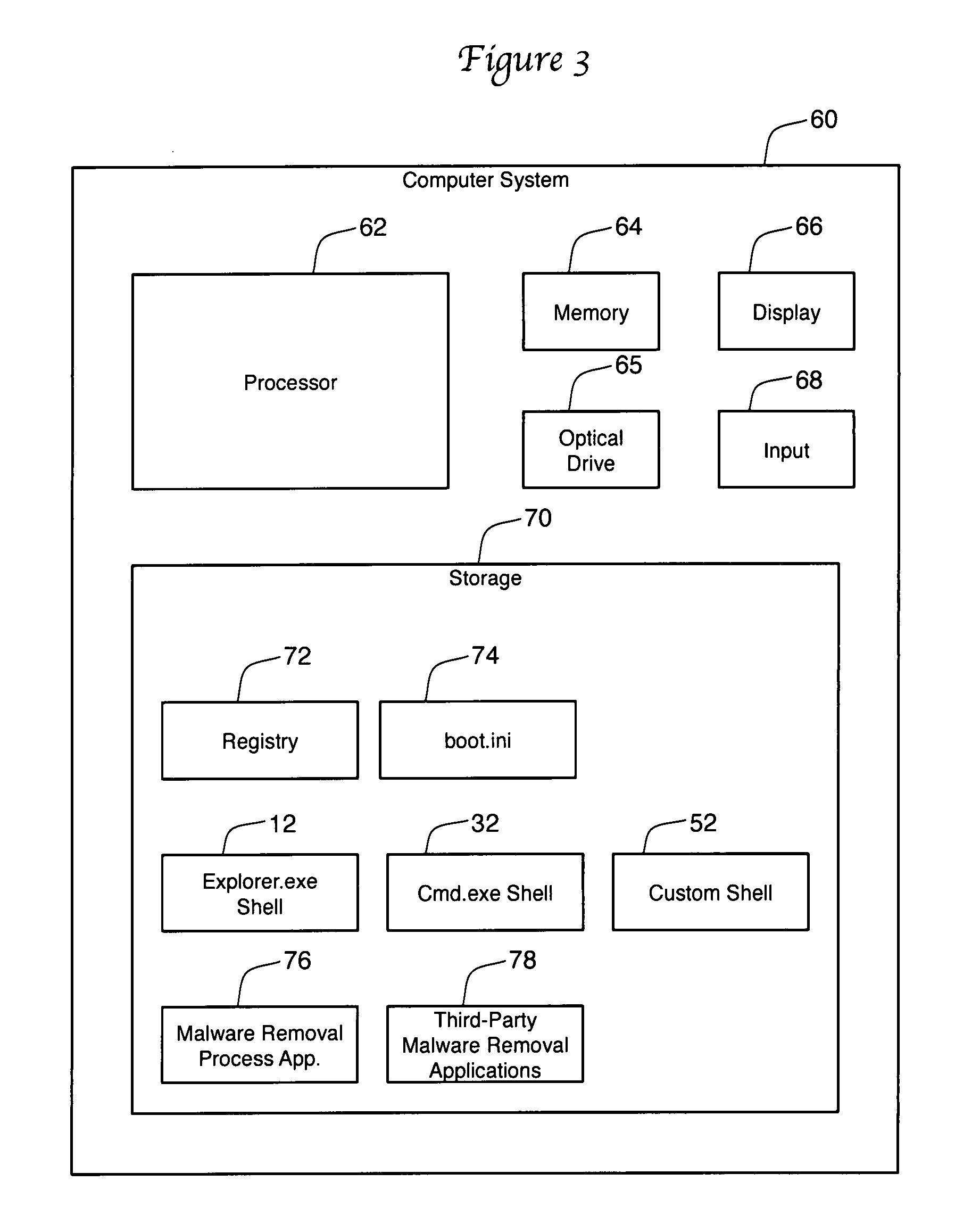
Malware automated removal system and method
ActiveUS20090013409A1Automate operationImprove software performanceMemory loss protectionError detection/correctionComputerized systemMalware
Owner:BBY SOLUTIONS
Use of policy levels to enforce enterprise control
InactiveUS20060225123A1Digital data processing detailsUnauthorized memory use protectionDistributed computingSoftware
Owner:TREND MICRO INC
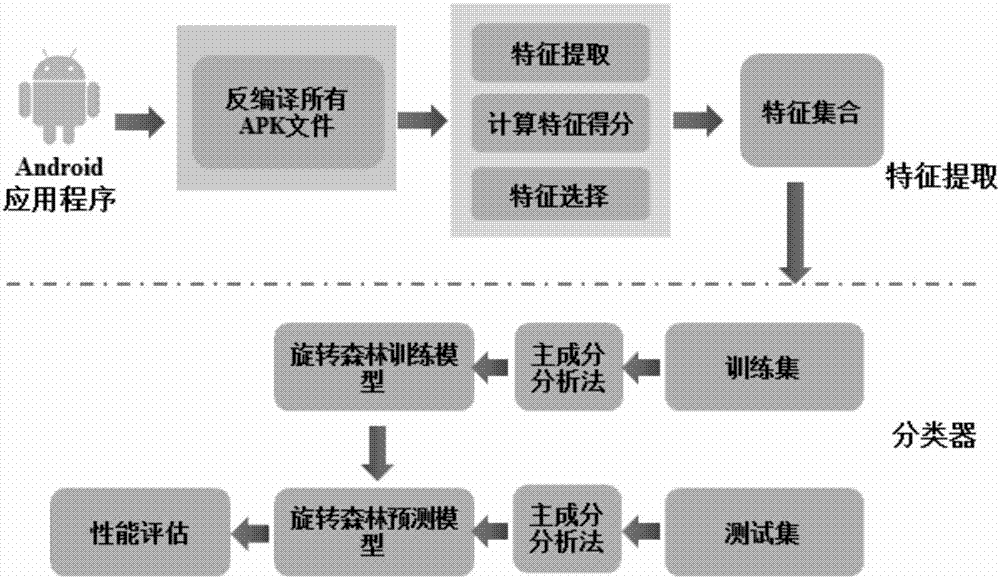
Efficient Android malware detection model DroidDet based on rotating forest
InactiveCN106919841AEfficient detectionImprove scalabilityPlatform integrity maintainanceSupport vector machine svm classifierApplication software
Owner:XIJING UNIV
Abnormality detection method and device based on log graph modeling
ActiveCN108920947AAvoid attackEnsure safetyCharacter and pattern recognitionPlatform integrity maintainanceNODALFeature vector
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
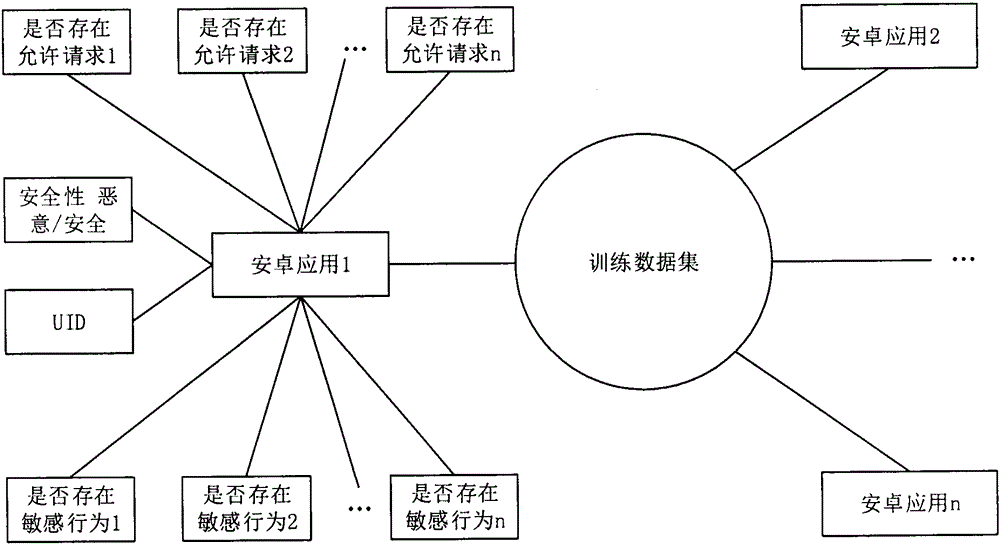
Android application safety analysis method based on sensitive behavior identification
InactiveCN105335655AImprove accuracyImprove detection accuracyPlatform integrity maintainanceTraining data setsBehavior recognition
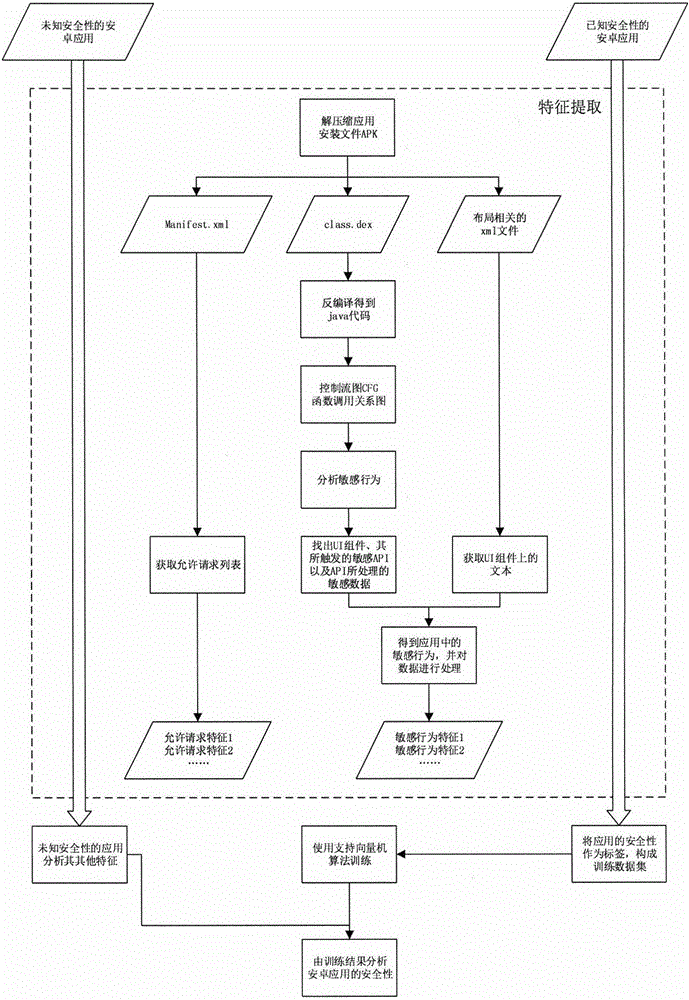
The invention provides an Android application safety analysis method based on sensitive behavior identification. The Android application safety analysis method comprises the following steps: 1) obtaining and analyzing a source code; 2) obtaining sensitive behaviors; 3) extracting a UI (User Interface) text; 4) processing sensitive behavior data; 5) extracting feature values; 6) forming a training data set; and 7) analyzing safety. A relationship between the UI text and a sensitive API (Application Program Interface) is taken as the characteristics of machine learning, and accuracy for detecting the malicious applications of an Android platform is effectively improved.
Owner:NANJING UNIV
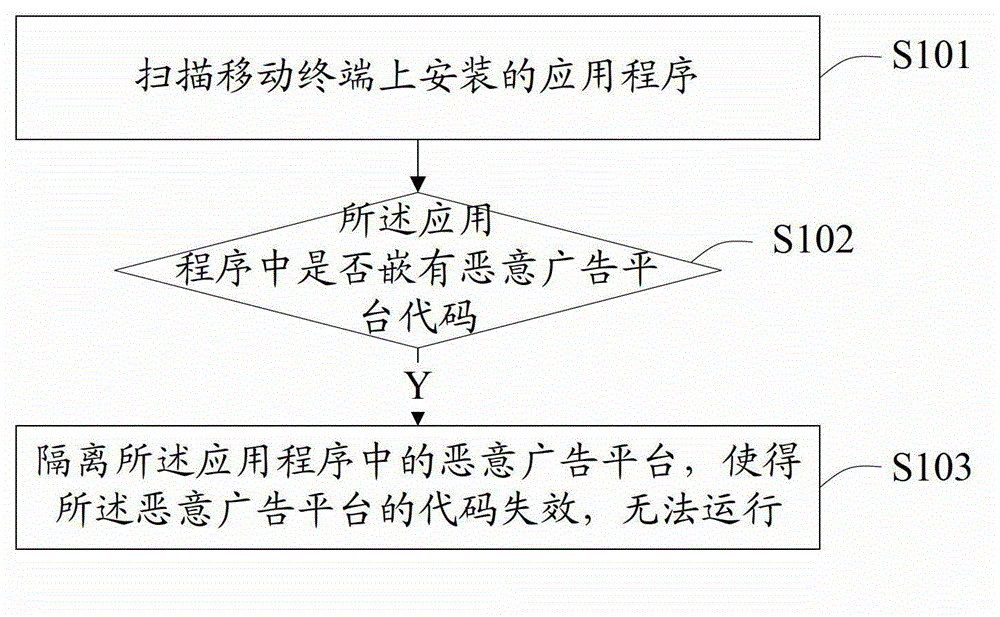
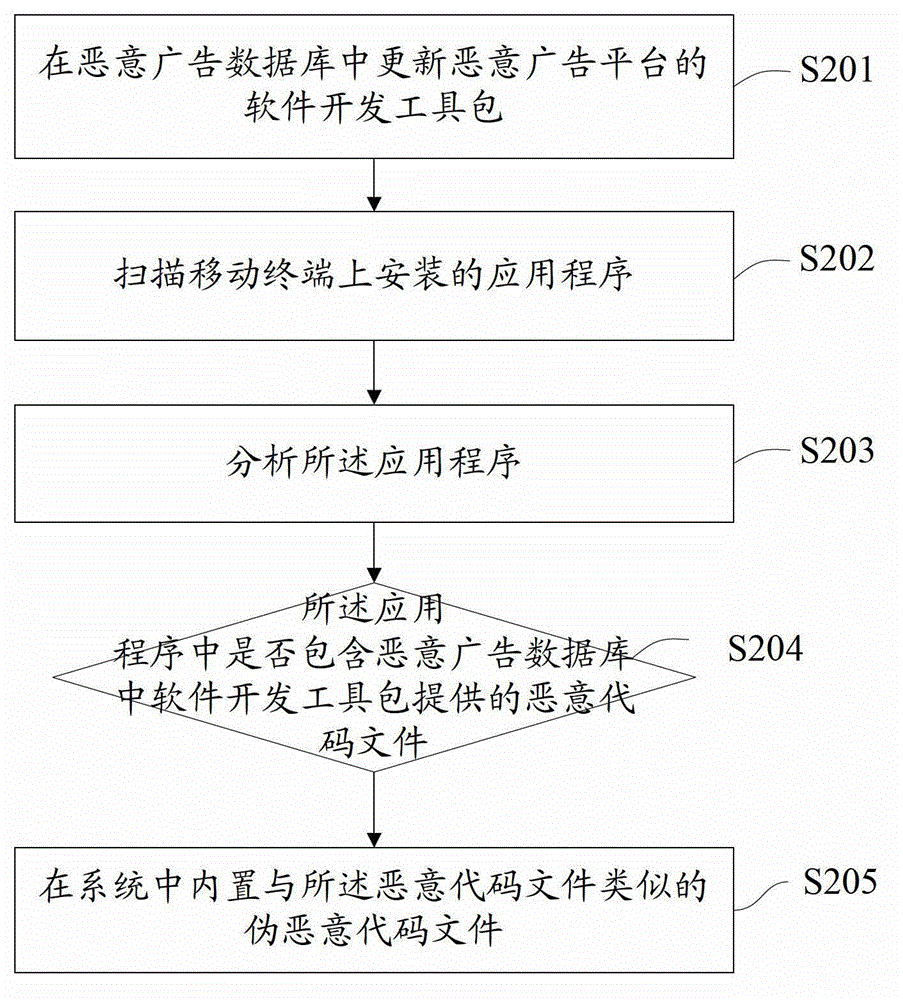
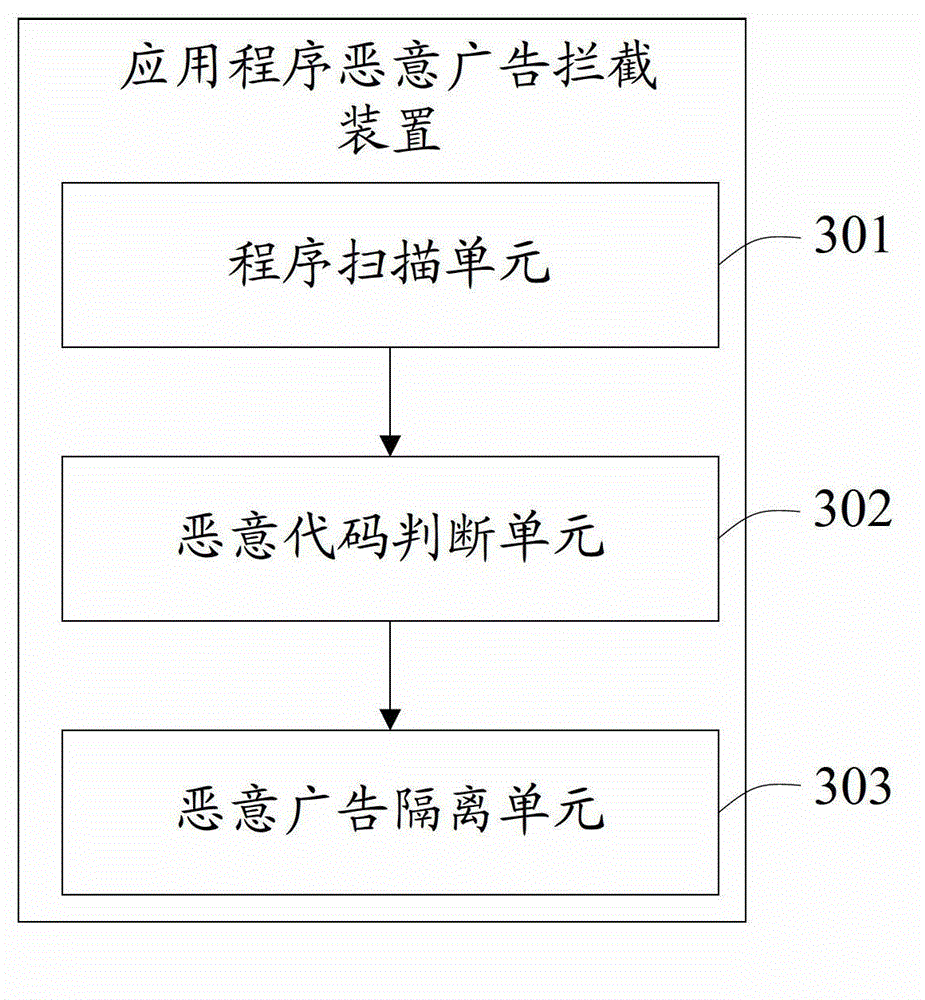
Method and device for intercepting malicious advertisements of application program
ActiveCN103065090AUse will not affectTroubleshoot background issuesPlatform integrity maintainanceComputer terminalApplication software
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Establishing method and system of trust chain
InactiveCN107451479AImprove securityImprove security and credibilityPlatform integrity maintainanceElectricityComputer module
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
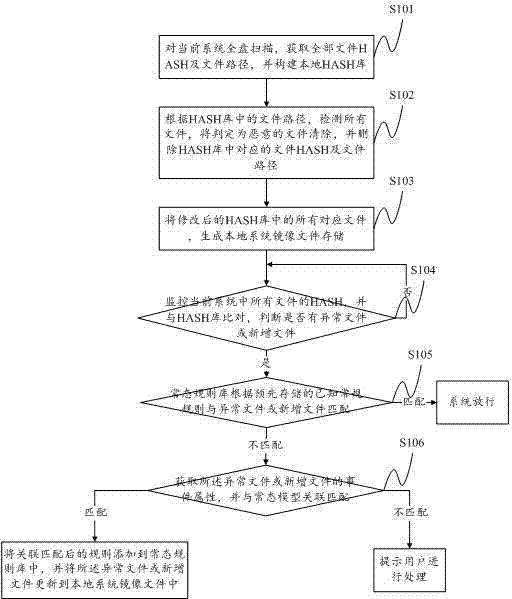
File tamper detecting and repairing method and system
ActiveCN103902855APlatform integrity maintainanceProgram/content distribution protectionOperating systemNormal state
Owner:HARBIN ANTIY TECH
Malicious software API call sequence detection method based on graph convolution
ActiveCN111259388AImprove bindingFlexible organizational structurePlatform integrity maintainanceNeural architecturesCall graphAlgorithm
Owner:SUN YAT SEN UNIV
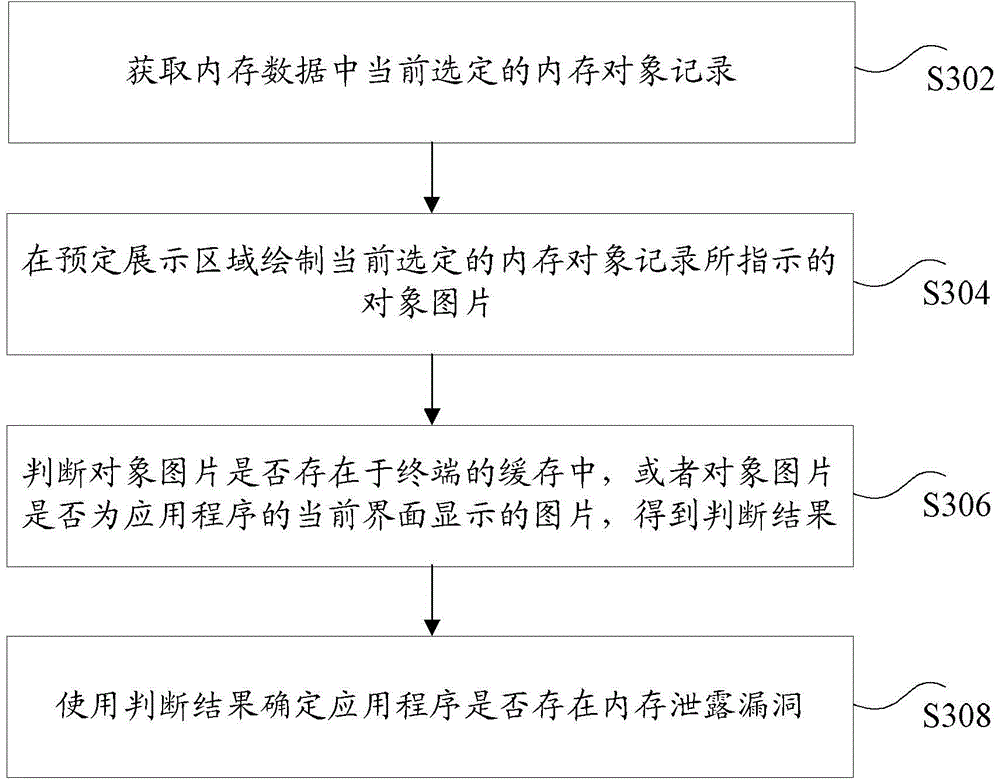
Detection method and apparatus for memory leak bug
ActiveCN105373471AAccurate detectionSolve the low detection accuracySoftware testing/debuggingPlatform integrity maintainanceParallel computingMemory object
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for preventing structured query language (SQL) implantation
Owner:FUJIAN TQ DIGITAL
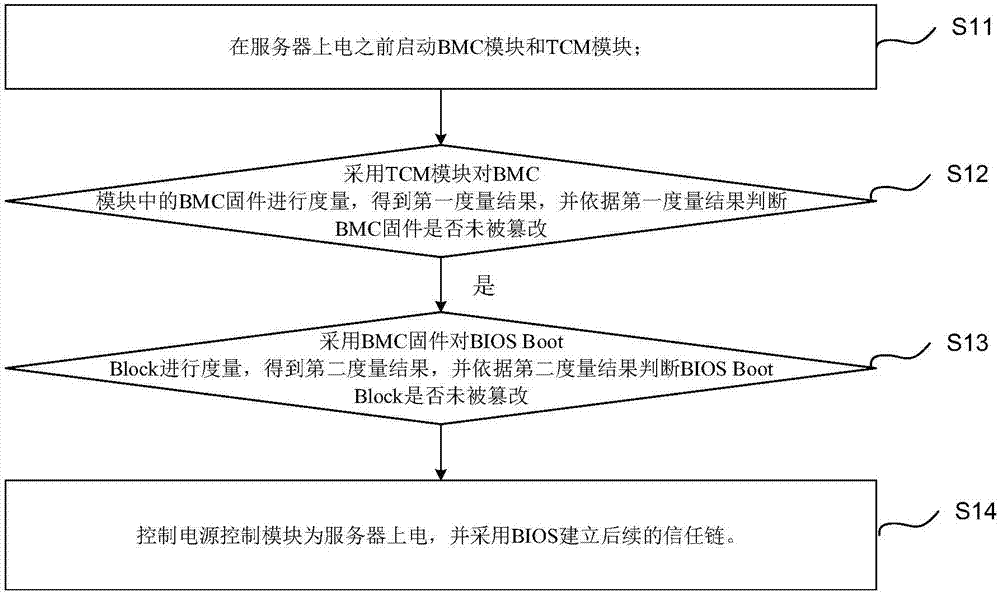
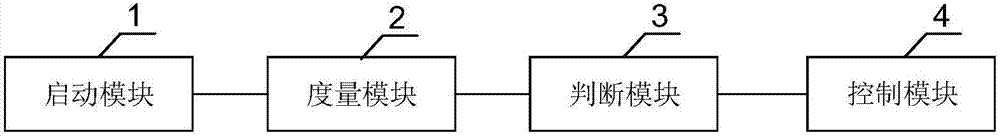
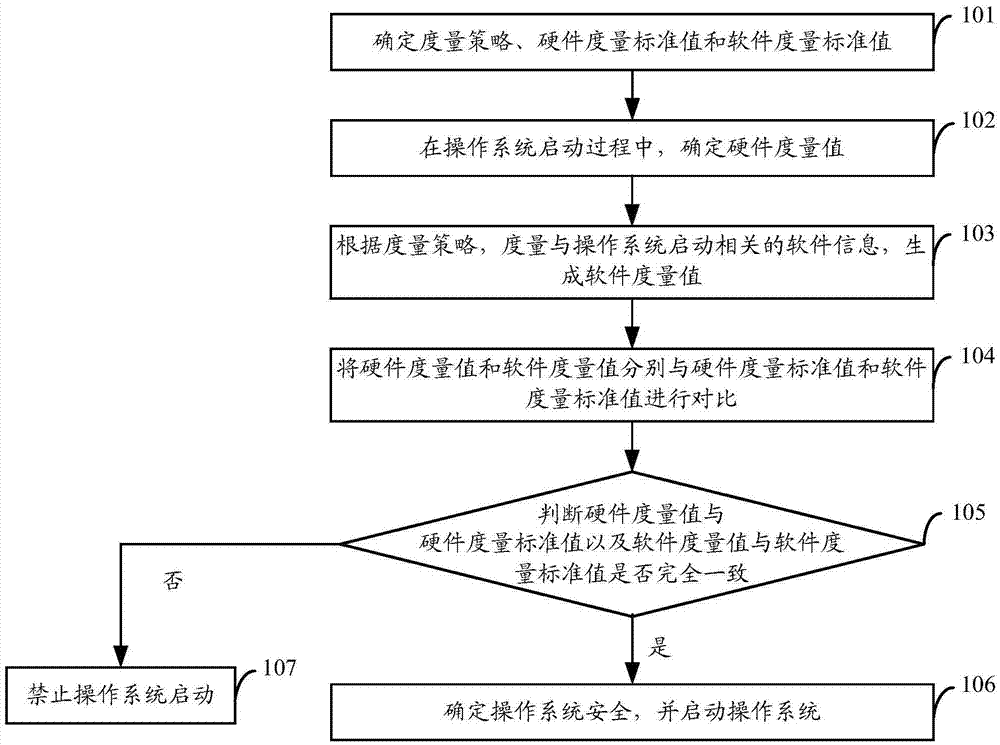
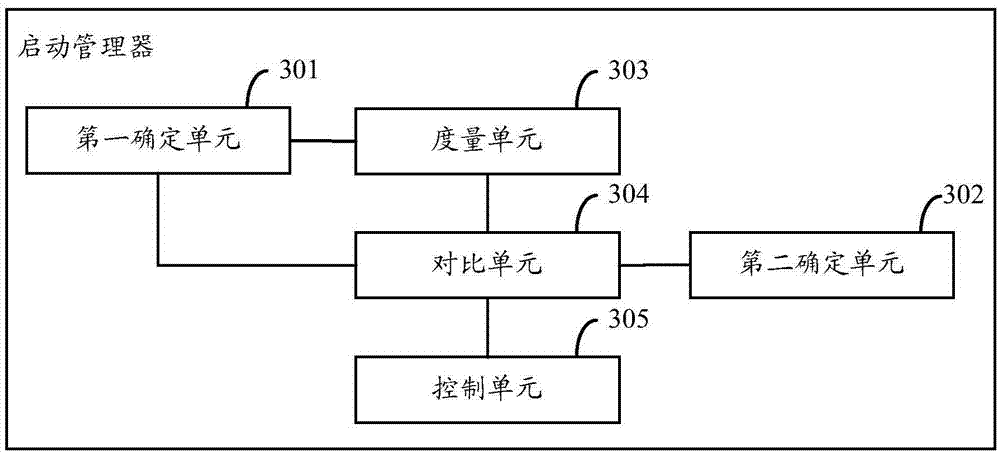
Operating system secure startup method, startup manager and operating system secure startup system
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
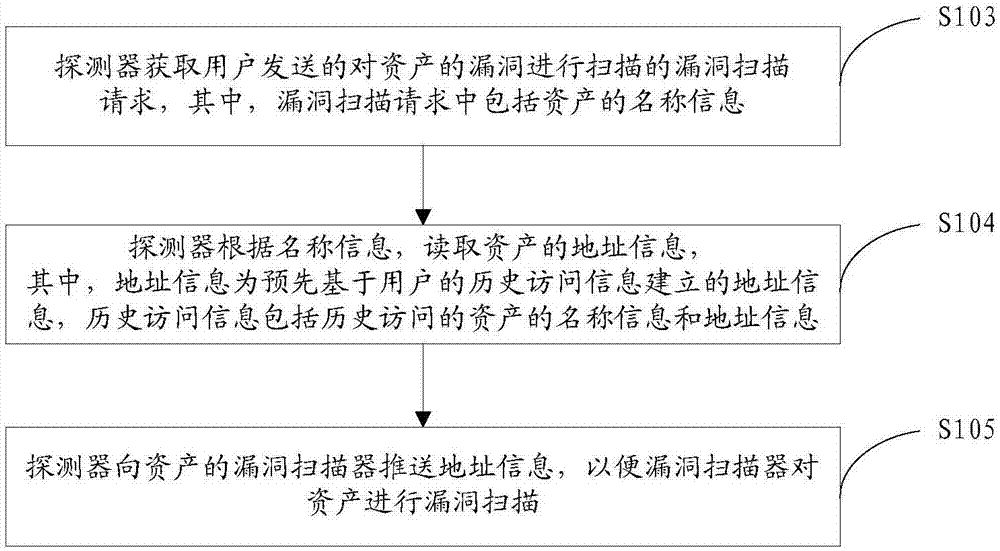
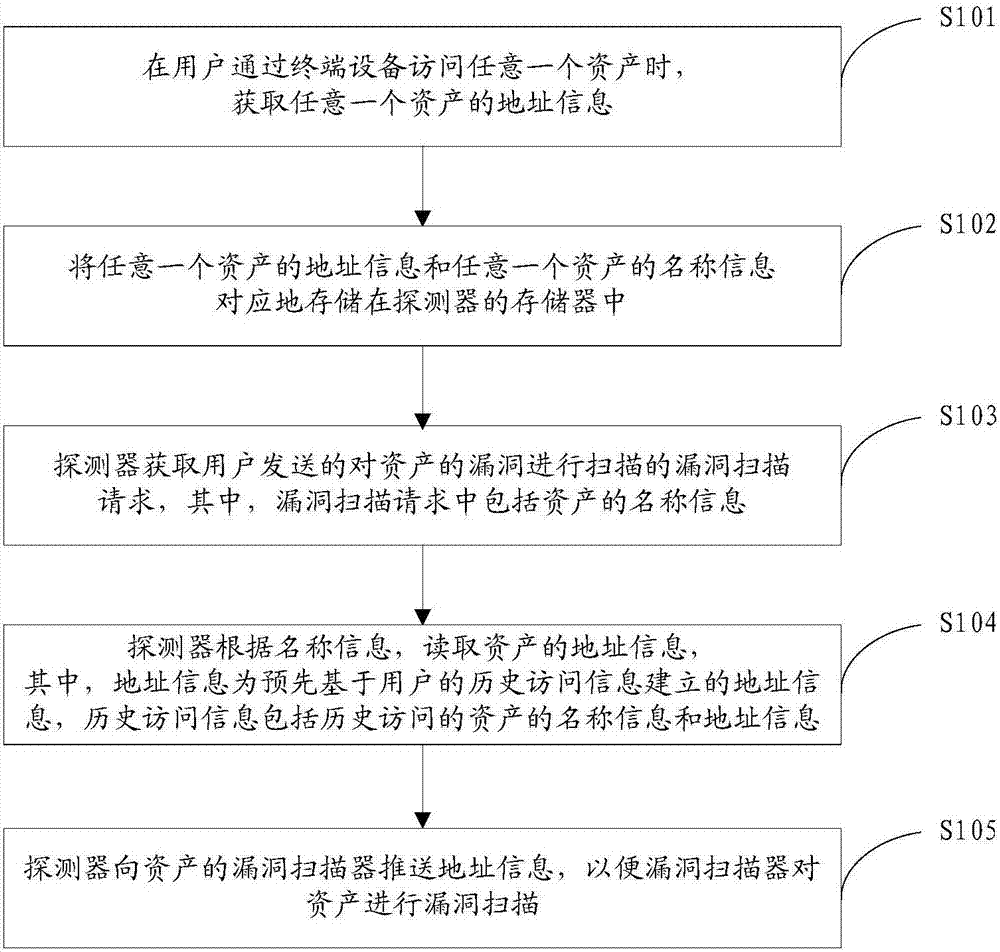
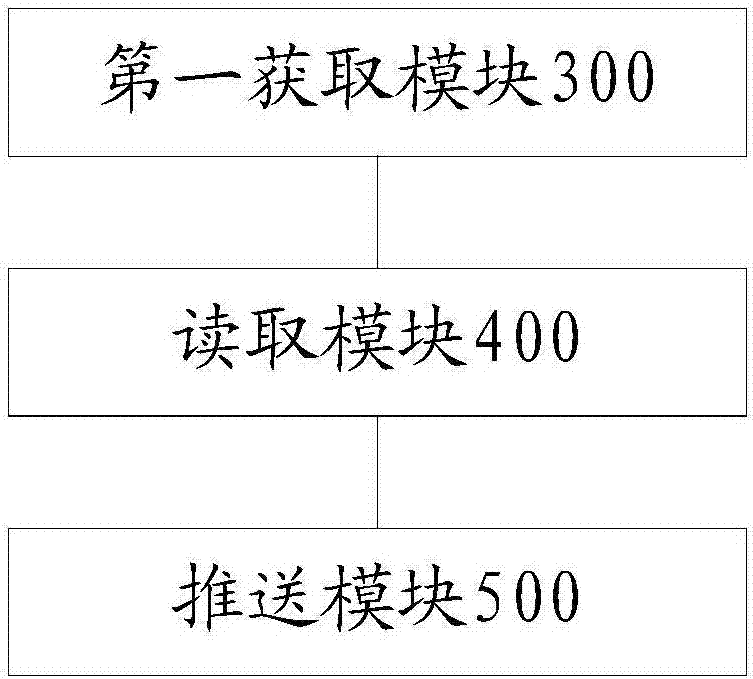
Vulnerability scanning method and vulnerability scanning device
InactiveCN107392031AAlleviate technical problems with high labor costsPlatform integrity maintainanceTransmissionTerminal equipmentOperating system
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Managing a virtual computer resource
InactiveUS20140089922A1Efficient and securePlatform integrity maintainanceSoftware simulation/interpretation/emulationComputer resourcesVirtual computing
Owner:IBM CORP
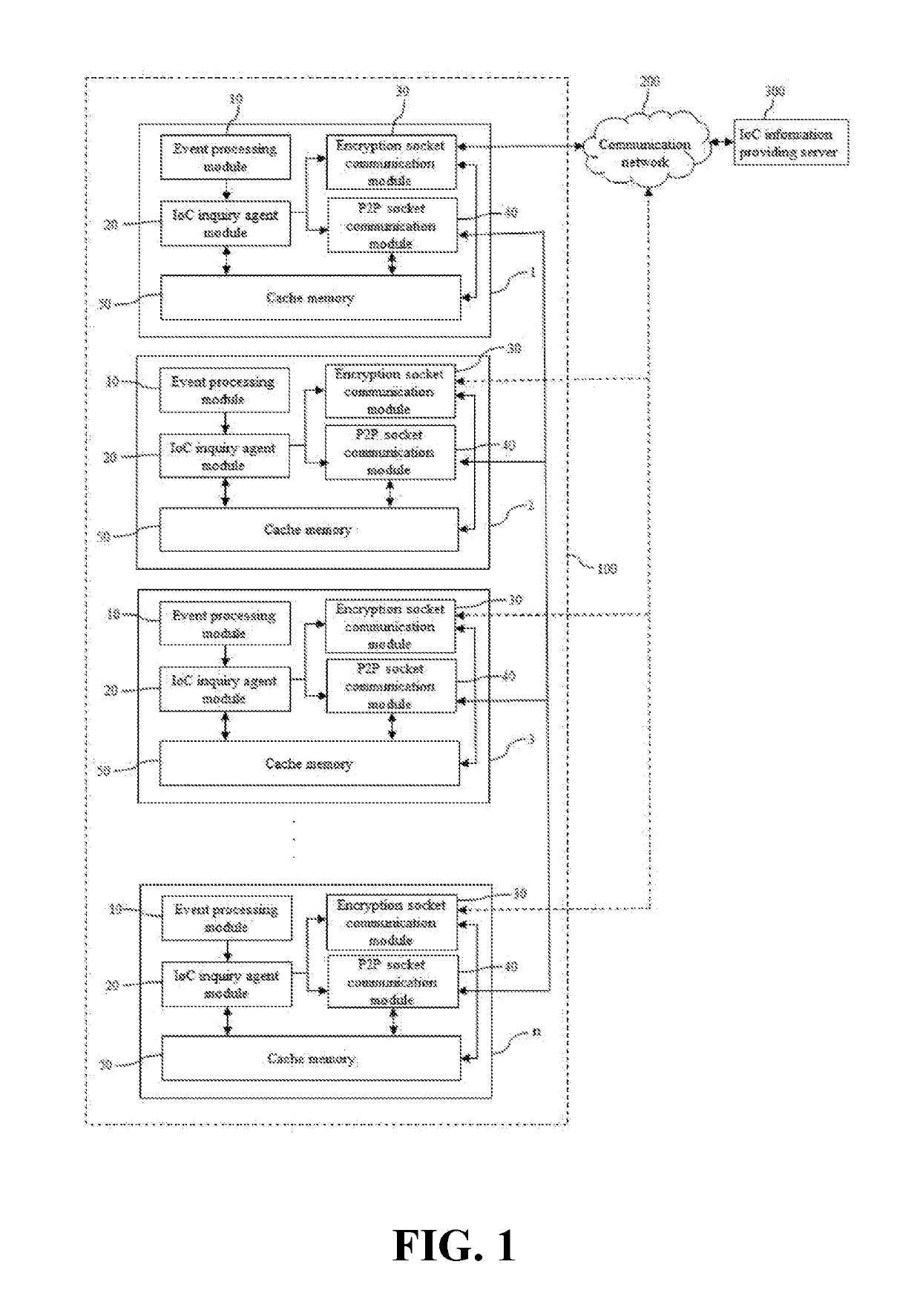
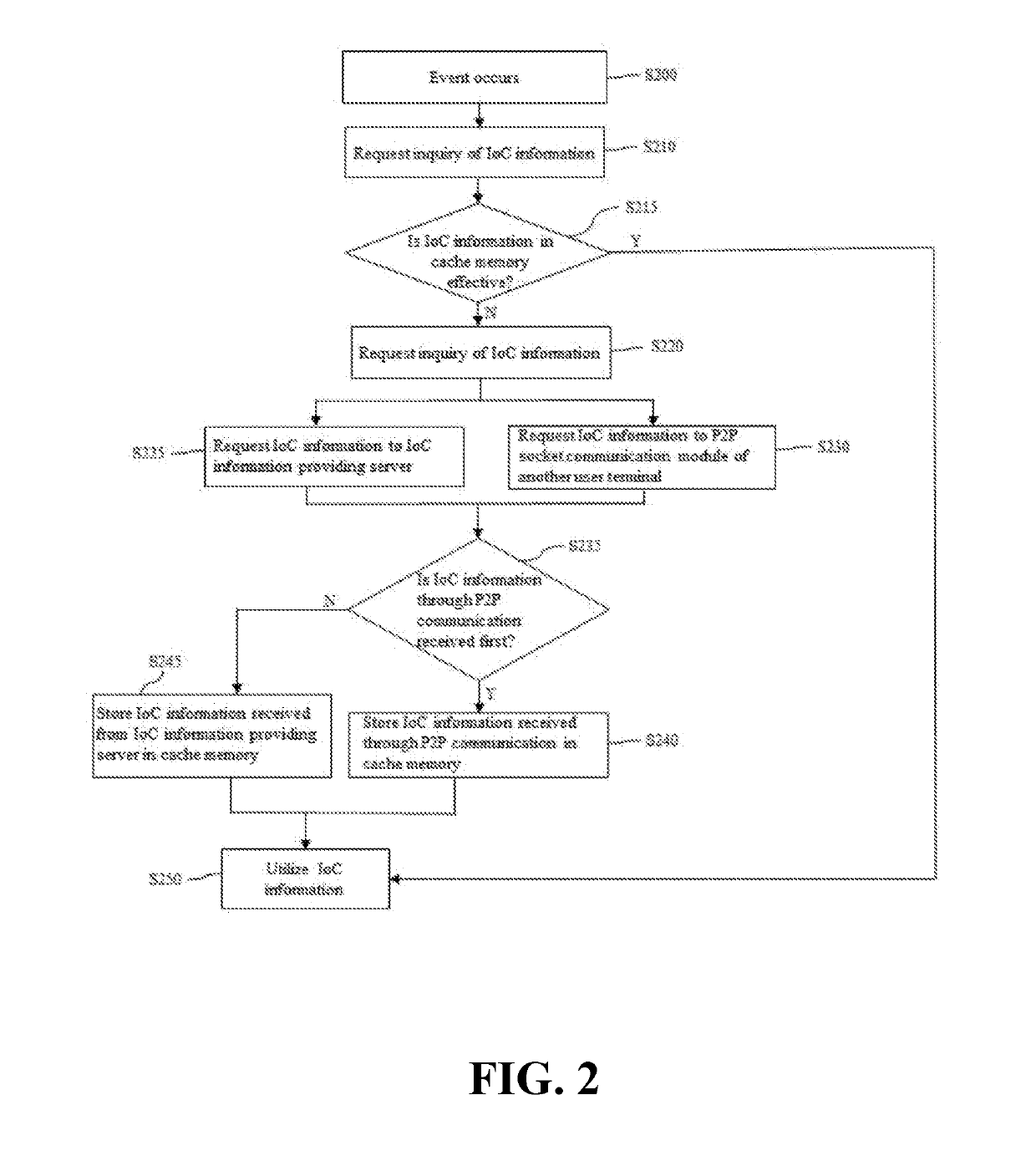
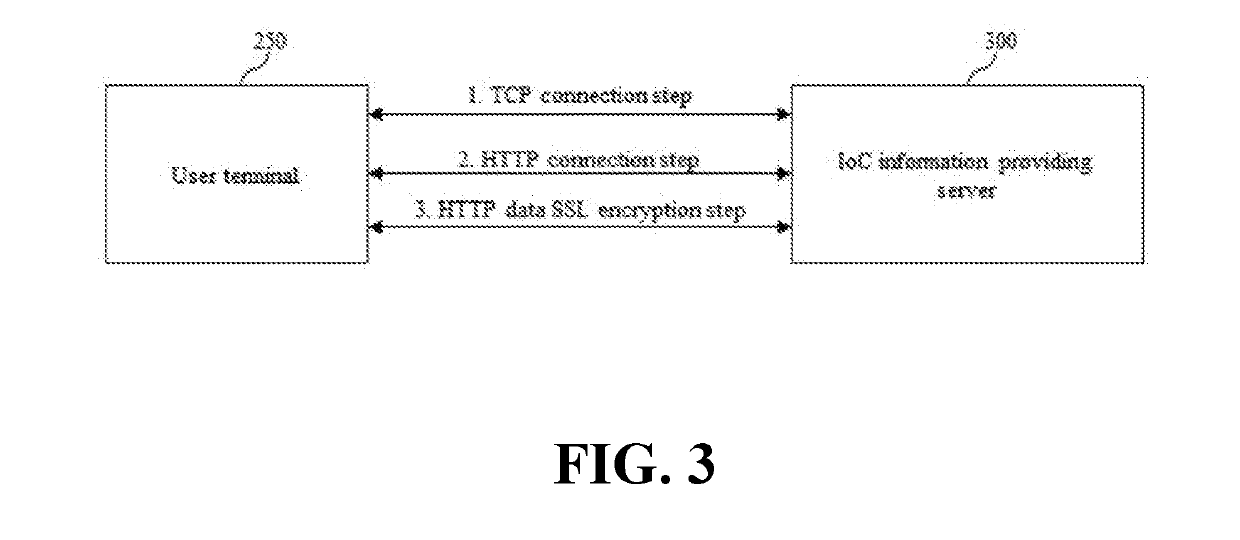
System and method for inquiring ioc information by p2p protocol
ActiveUS20190182270A1Platform integrity maintainanceTransmissionProtocol for Carrying Authentication for Network AccessEncryption
Owner:SANDS LAB INC
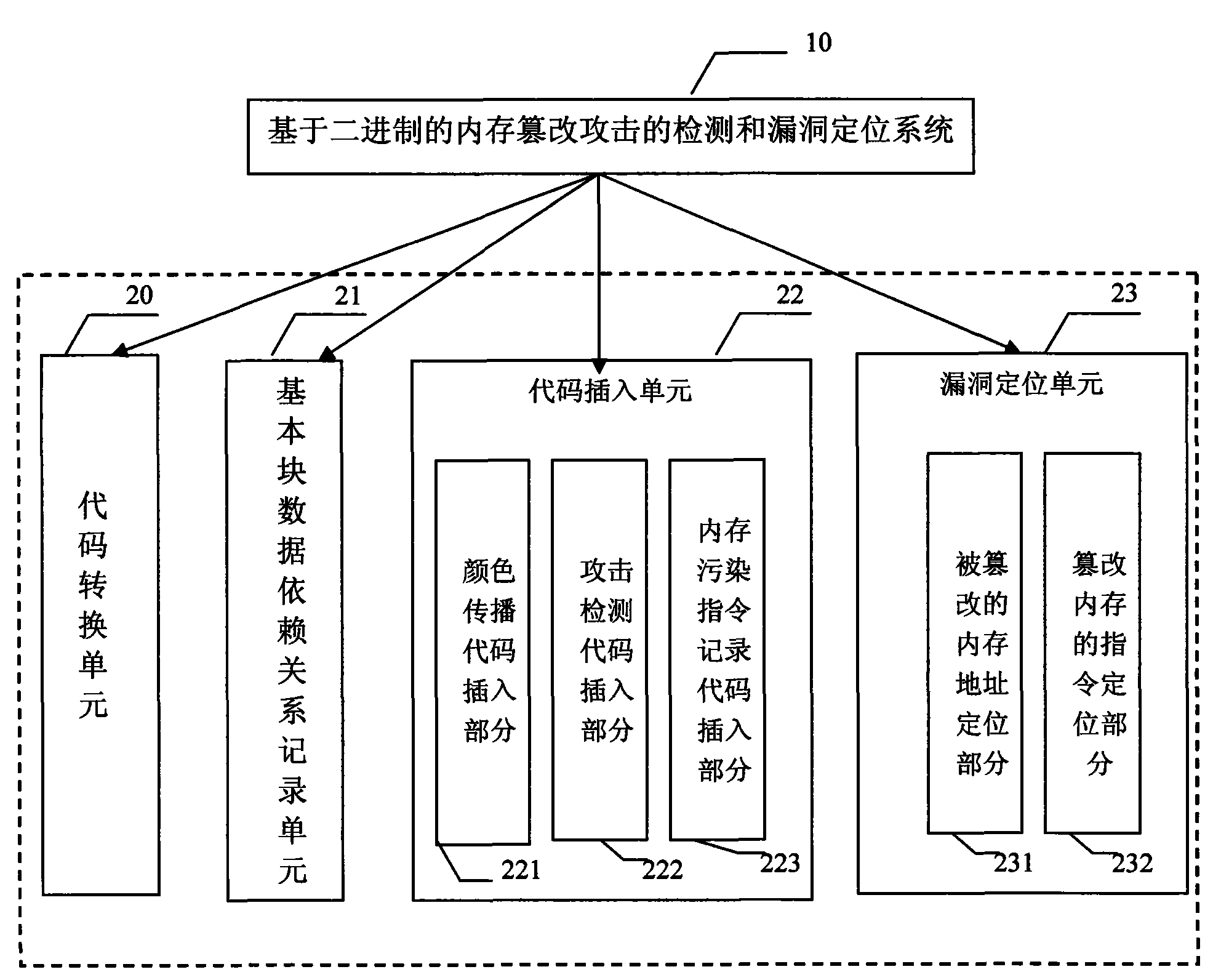
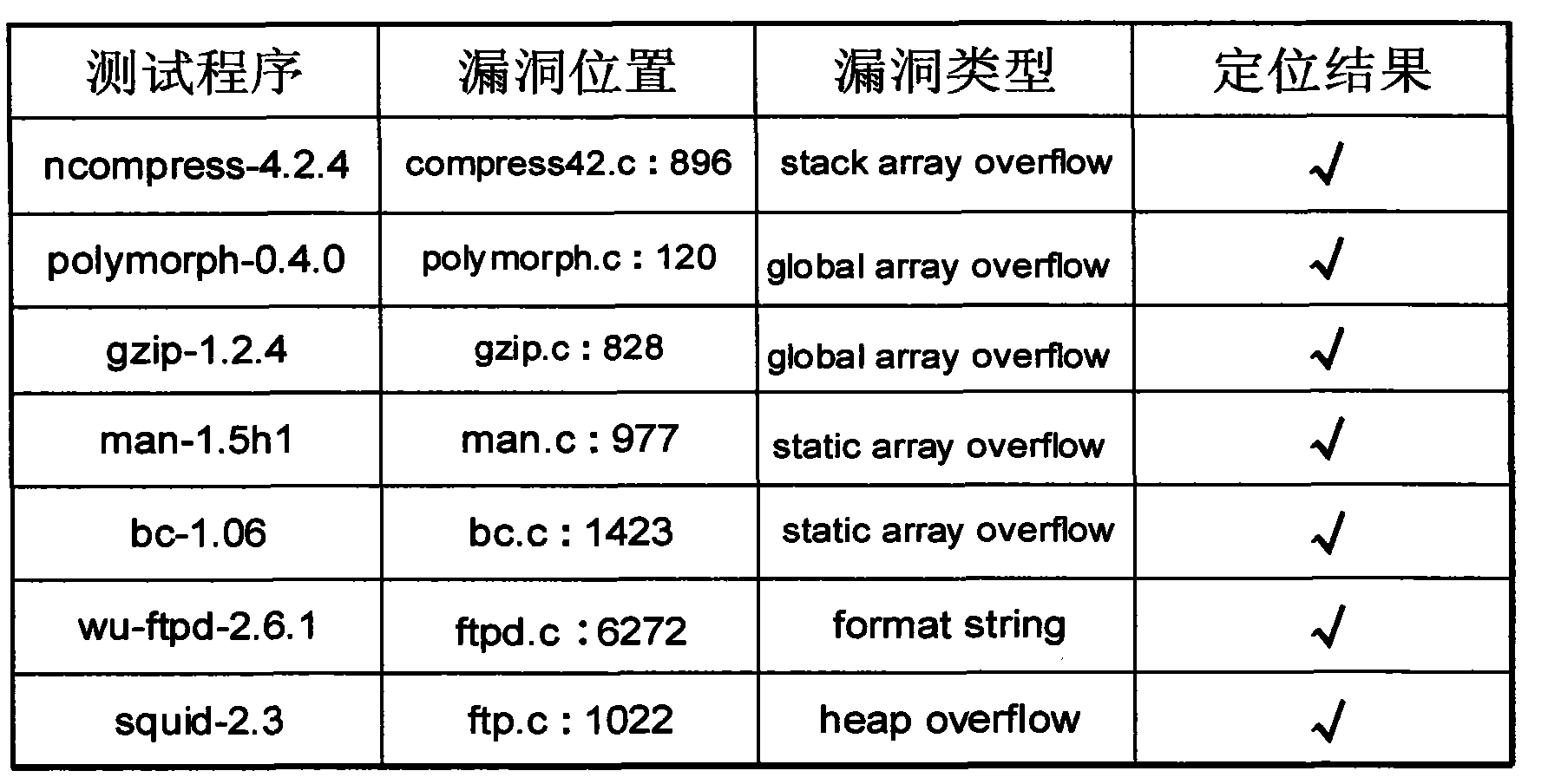
Binary-based system for detecting memory modifying attack and positioning bug
InactiveCN101615238AIncreased attack detection rangeAutomatically pinpoint program vulnerabilitiesPlatform integrity maintainanceMemory addressCode conversion
Owner:NANJING UNIV
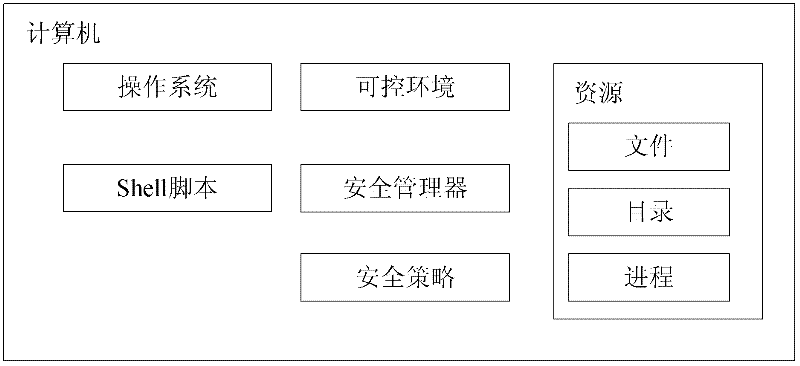
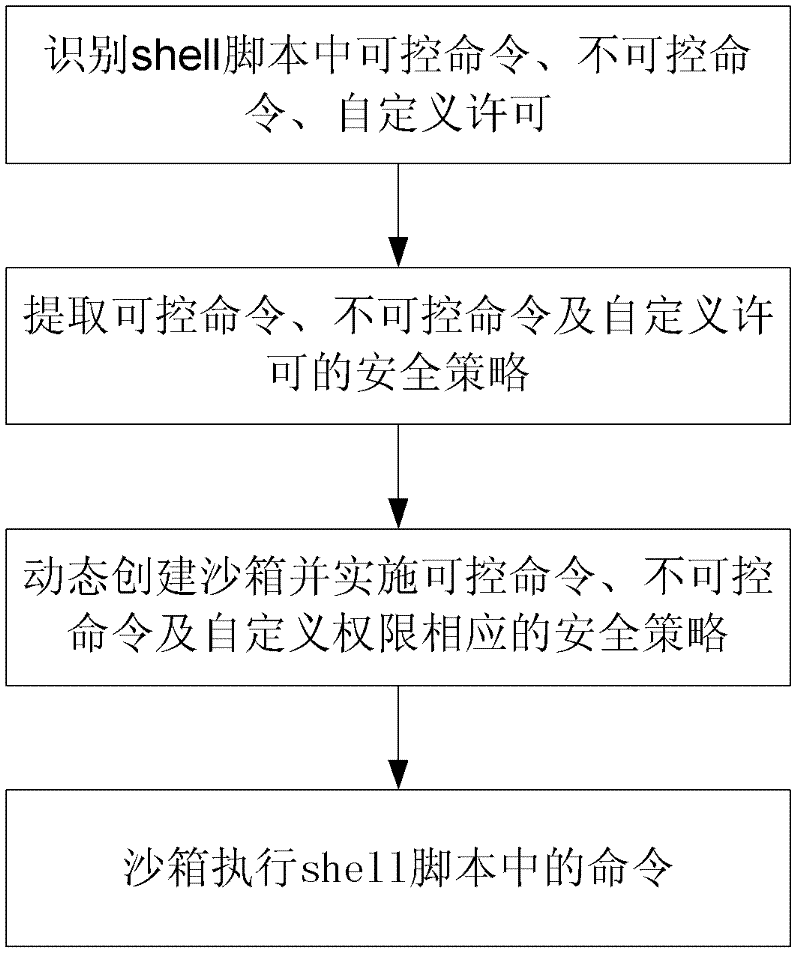
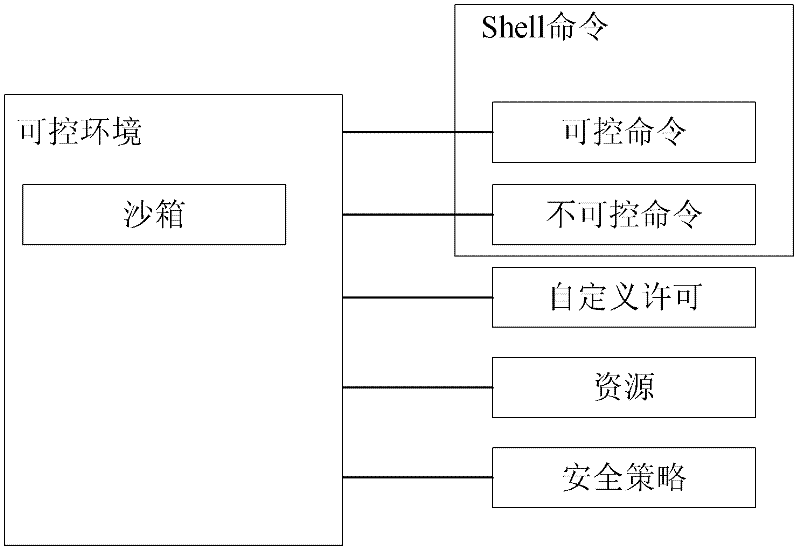
Method and system for safe operation of shell script based on sandbox technology
Owner:ZHEJIANG UNIV CITY COLLEGE
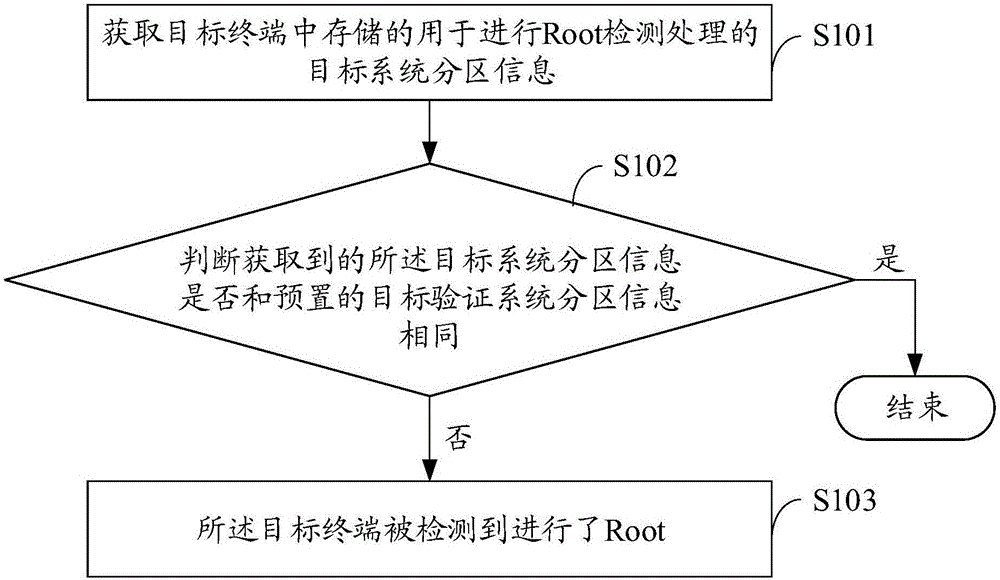
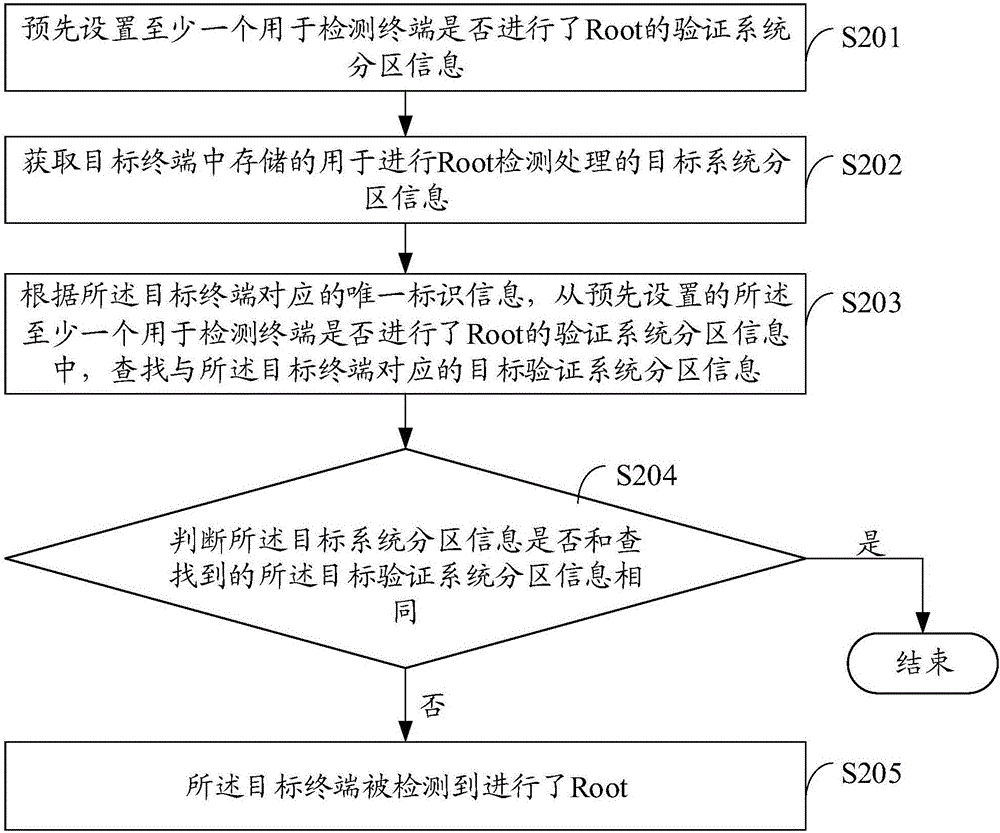
Root detection processing method and device, and terminal
InactiveCN105912937AImprove practicalityEasy to detectPlatform integrity maintainanceComputer hardwareEngineering
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
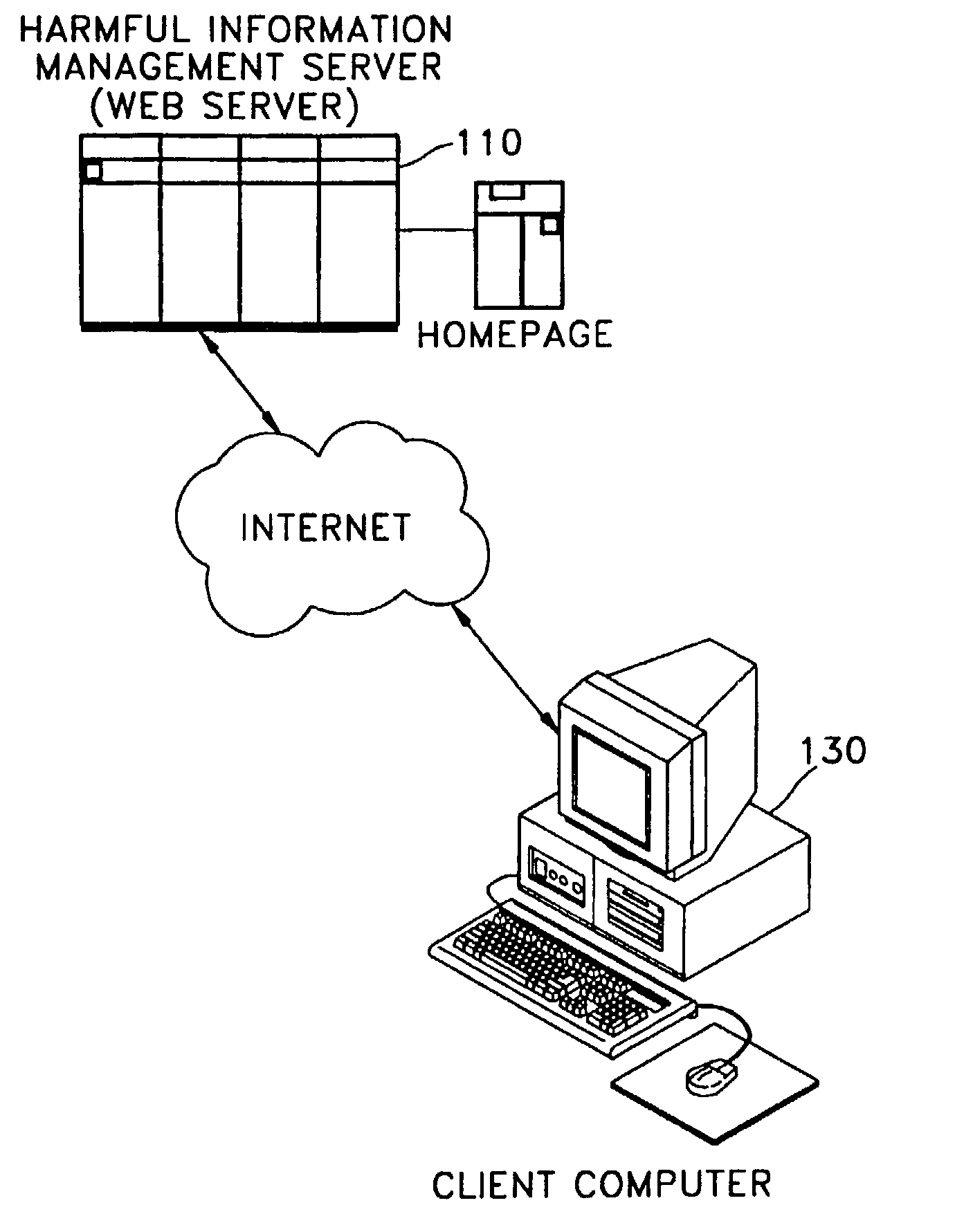
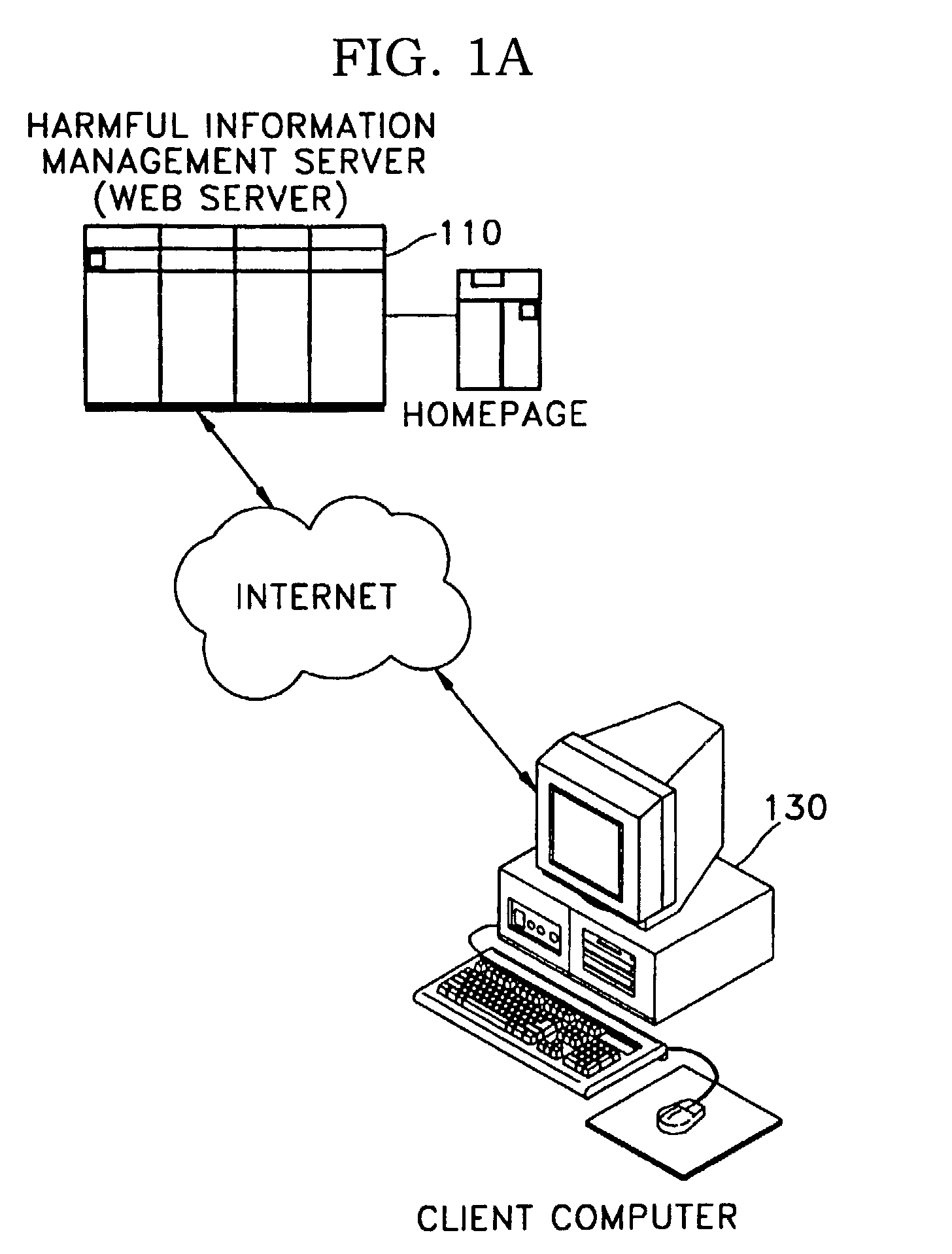
System and method for blocking harmful information online, and computer readable medium therefor
Owner:INCA INTERNET
Method for controlling single board to be safely started and method and device for upgrading software package
ActiveCN105117651AStartup does not affectImprove securityVersion controlPlatform integrity maintainanceElectricitySingle plate
The invention discloses a method for controlling a single board to be safely started. The method comprises the steps that after the single board is powered on, the resigned name of a software package to be loaded to the single board is acquired, the resigned name of the software package is obtained by using a single plate private key of the single board for resigning the software package, and is made after the original signature of the software package passes verification through a software package public key of the software package, and the original signature is obtained by signing the software package through a software package private key of the software package; the resigned name of the software package is verified through a single board public key paired with the single board private key; after the resigned name passes verification, the single board is started. According to the method for controlling the single board to be safely started, it can be guaranteed that the single board can still be safely started when the private key of the software package is leaked.
Owner:SHANGHAI HUAWEI TECH CO LTD
Mobile operation and maintenance management platform safe operation and big data application system under cloud environment
InactiveCN109284839APlatform integrity maintainanceData switching networksModularityTechnical support
Owner:金税信息技术服务股份有限公司
Apparatus and method for blocking ransome ware using access control to the contents file
The present application relates to the apparatus for blocking Ransome ware using access control to the contents file, it includes an access permission program checking unit for checking whether a program of a process detected as being started in an user's computer is a reliable program, checking whether a parent process of the program is a reliable program, and determining whether the program is the program that is allowed to access the contents file; a whitelist registration unit for registering information of the contents file to be protected; and a contents file access control unit for allowing the process to access the contents file registered in the whitelist registration unit when the program of the process is the program that is allowed to access the contents file determined by the access permission program checking unit, and blocking the process from accessing the contents file registered in the whitelist registration unit when the program of the process is not the program that is allowed to access the contents file determined by the access permission program checking unit.
Owner:WITHNETWORKS CO LTD
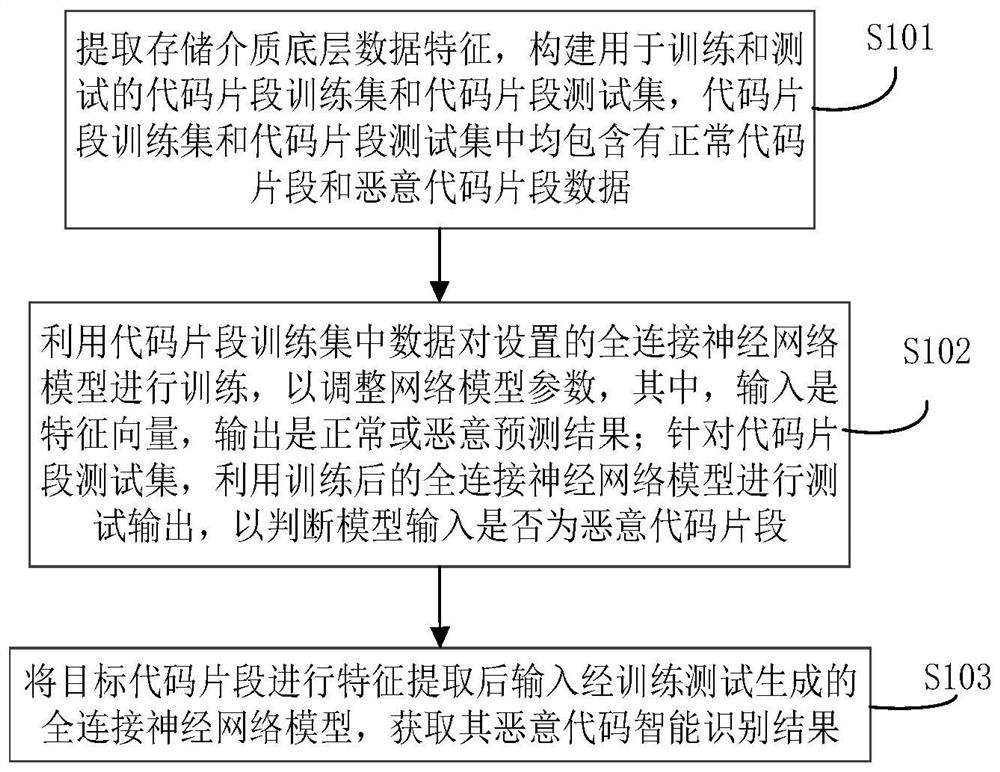
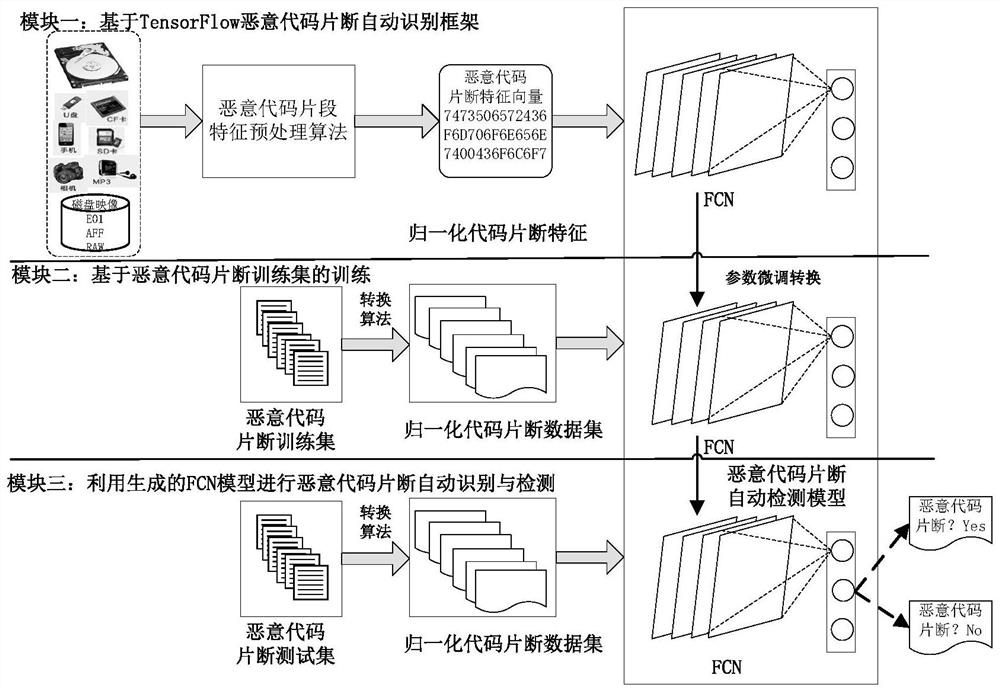
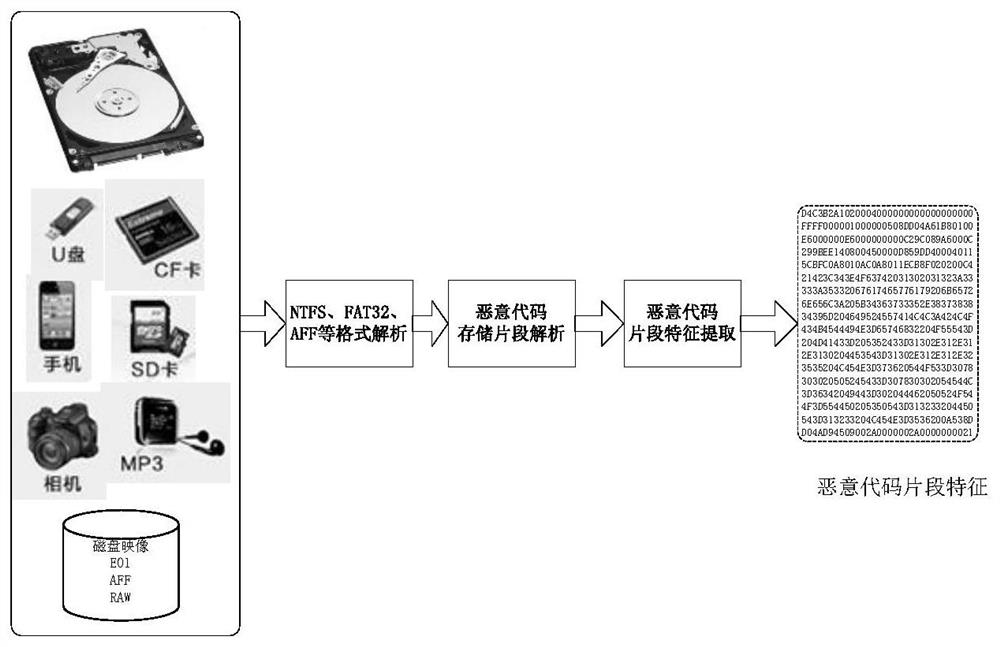
Intelligent malicious code fragment evidence obtaining method and system
ActiveCN111881447ACharacter and pattern recognitionPlatform integrity maintainanceFeature vectorFeature extraction
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
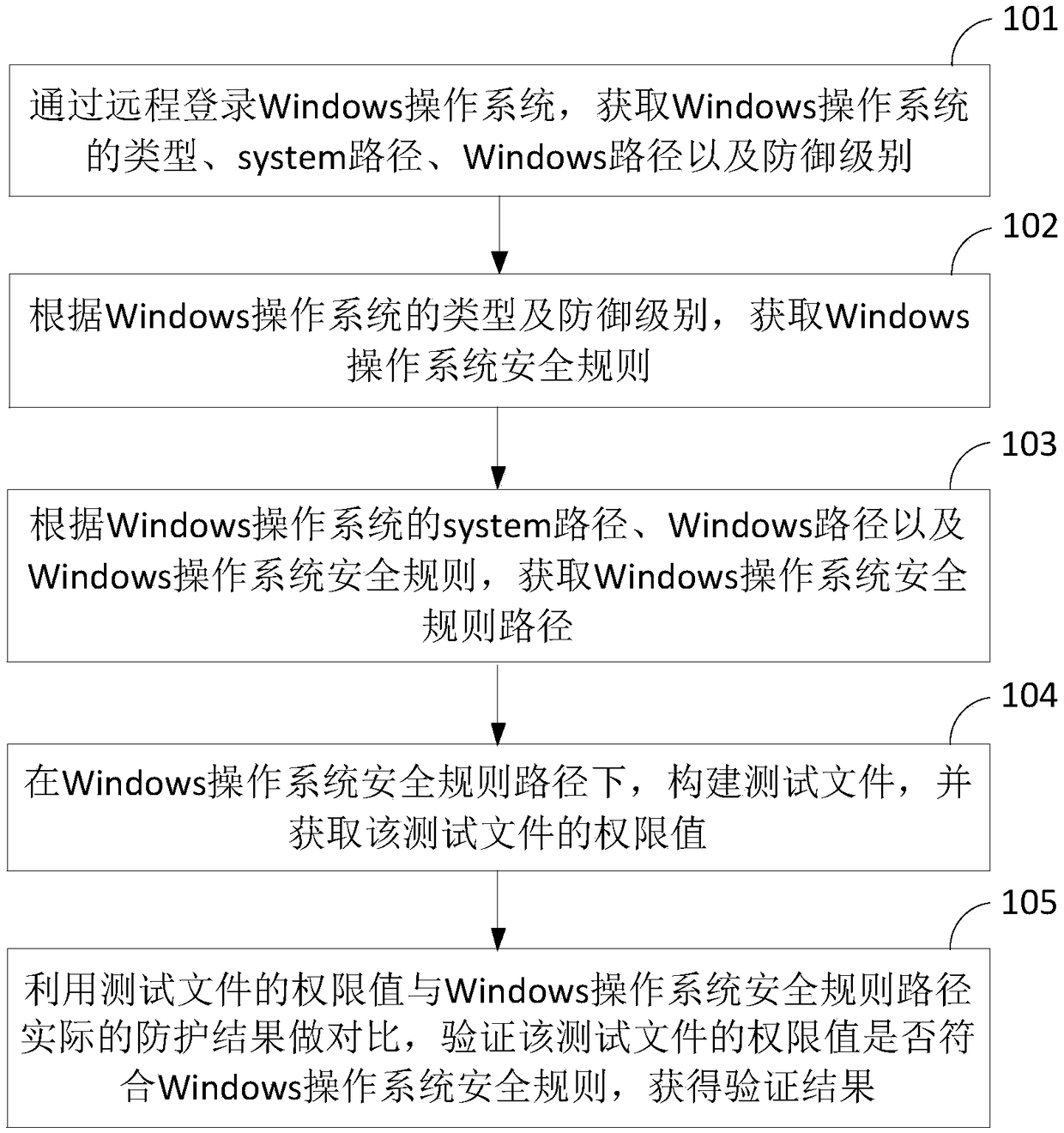
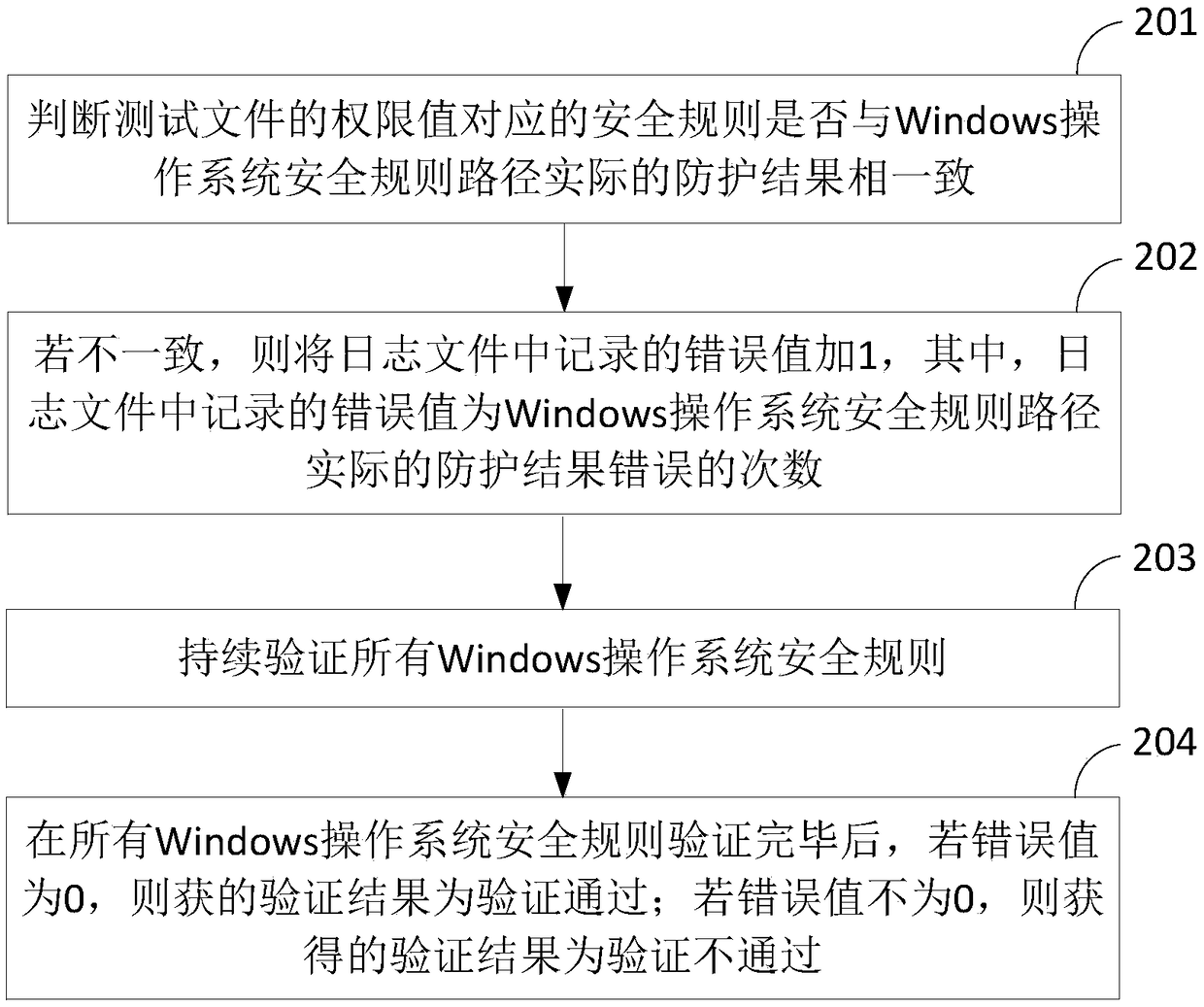
An automatic verification method and apparatus for remote Windows operating system security rules
ActiveCN109284612AImplement automatic verificationEnsure safetyPlatform integrity maintainanceOperational systemValidation methods
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Ransomware detection method and device
InactiveCN110941822ARealize detectionDoes not affect operating speedPlatform integrity maintainanceComputer hardwareRansomware
Owner:WUHAN ANTIY MOBILE SECURITY
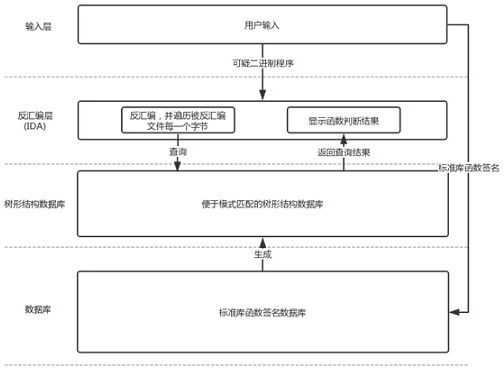
Link library function name identification method and device for computer binary program
Owner:NAT UNIV OF DEFENSE TECH
MPK technology-based inter-microkernel-module communication method and system, and medium
PendingCN111949596AReduce IPC performance overheadEnsure safetyDigital computer detailsPlatform integrity maintainanceComputer architectureEngineering
Owner:SHANGHAI JIAO TONG UNIV
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap