Detection method and apparatus for memory leak bug
A memory leak and detection method technology, applied in software testing/debugging, platform integrity maintenance, etc., can solve the problem of low detection accuracy, and achieve the effect of accurately detecting memory leak vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] According to an embodiment of the present invention, an embodiment of a detection method for a memory leak vulnerability is provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be implemented in a computer system such as a set of computer-executable instructions and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
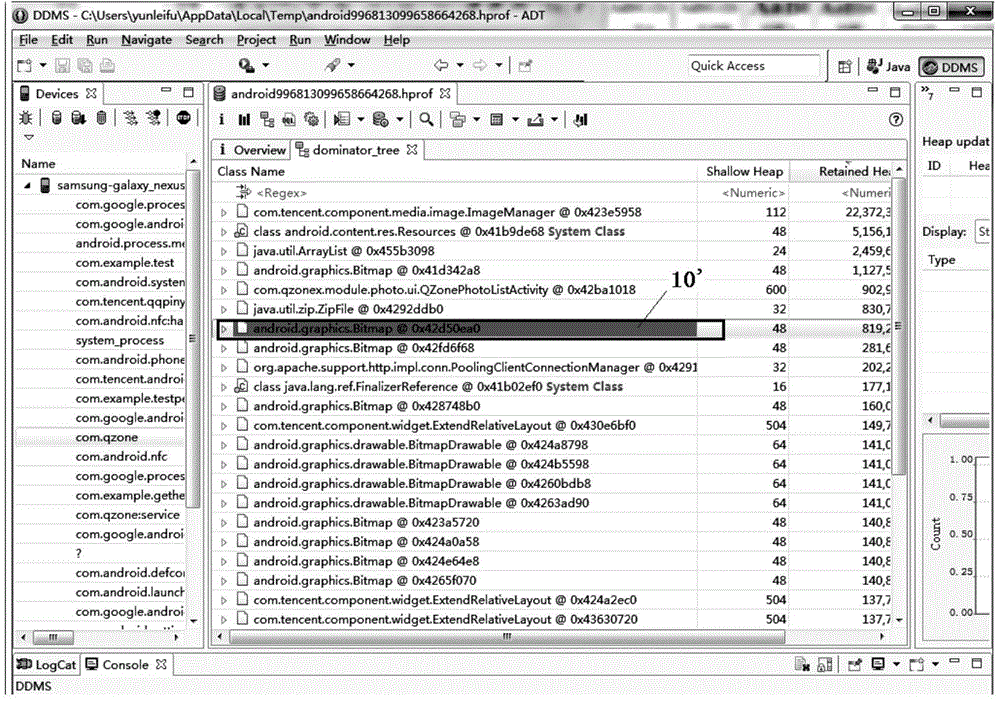
[0025] Optionally, in this embodiment, the above picture transmission method can be applied to figure 2 In the hardware environment formed by the first terminal 101 shown. Such as figure 2 As shown, the first terminal may be connected to the second terminal 102 through a network or a data line, and upload or download data to the second terminal 102 .
[0026] The above-mentioned network includes but not limited to: wide area network, metropolitan area network or local area network. In th
Embodiment 2
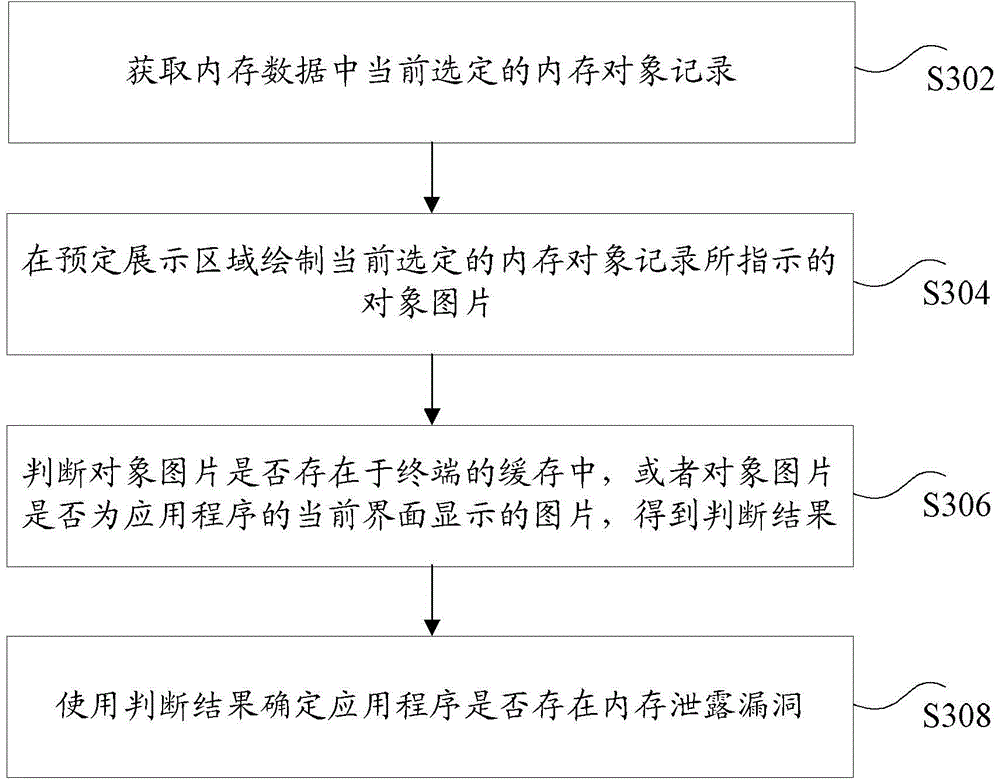
[0090] According to an embodiment of the present invention, there is also provided a detection device for implementing the above-mentioned memory leak vulnerability, such as Figure 8 As shown, the device may include: an acquisition module 50 , a drawing module 70 , a first judgment module 90 and a first determination module 80 .
[0091] Among them, the obtaining module is used to obtain the currently selected memory object record in the memory data, wherein the memory data is the data generated when the application program on the terminal is used in the memory record of the terminal, and the memory data includes one or more memory object records The drawing module is used to draw the object picture indicated by the currently selected memory object record in the predetermined display area; the first judging module is used to judge whether the object picture exists in the cache of the terminal, or whether the object picture is an application program The picture displayed on the c
Embodiment 3
[0121] The embodiment of the present invention also provides a terminal or a server. Optionally, in this embodiment, the terminal above can execute the method for detecting a memory leak vulnerability, and the device for detecting a memory leak vulnerability in the above embodiment can be set on the terminal or the server.
[0122] Figure 9 is a structural block diagram of a terminal according to an embodiment of the present invention. Such as Figure 9 As shown, the terminal 200 may include: one or more (only one is shown in the figure) processor 201, memory 203, and transmission device 205, such as Figure 9 As shown, the terminal may also include an input and output device 207 and an antenna 209 .
[0123] Among them, the memory 203 can be used to store software programs and modules, such as program instructions / modules corresponding to the method and device for detecting memory leaks in the embodiments of the present invention, and the processor 201 runs the software pr
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap