Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
156results about "Memory systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
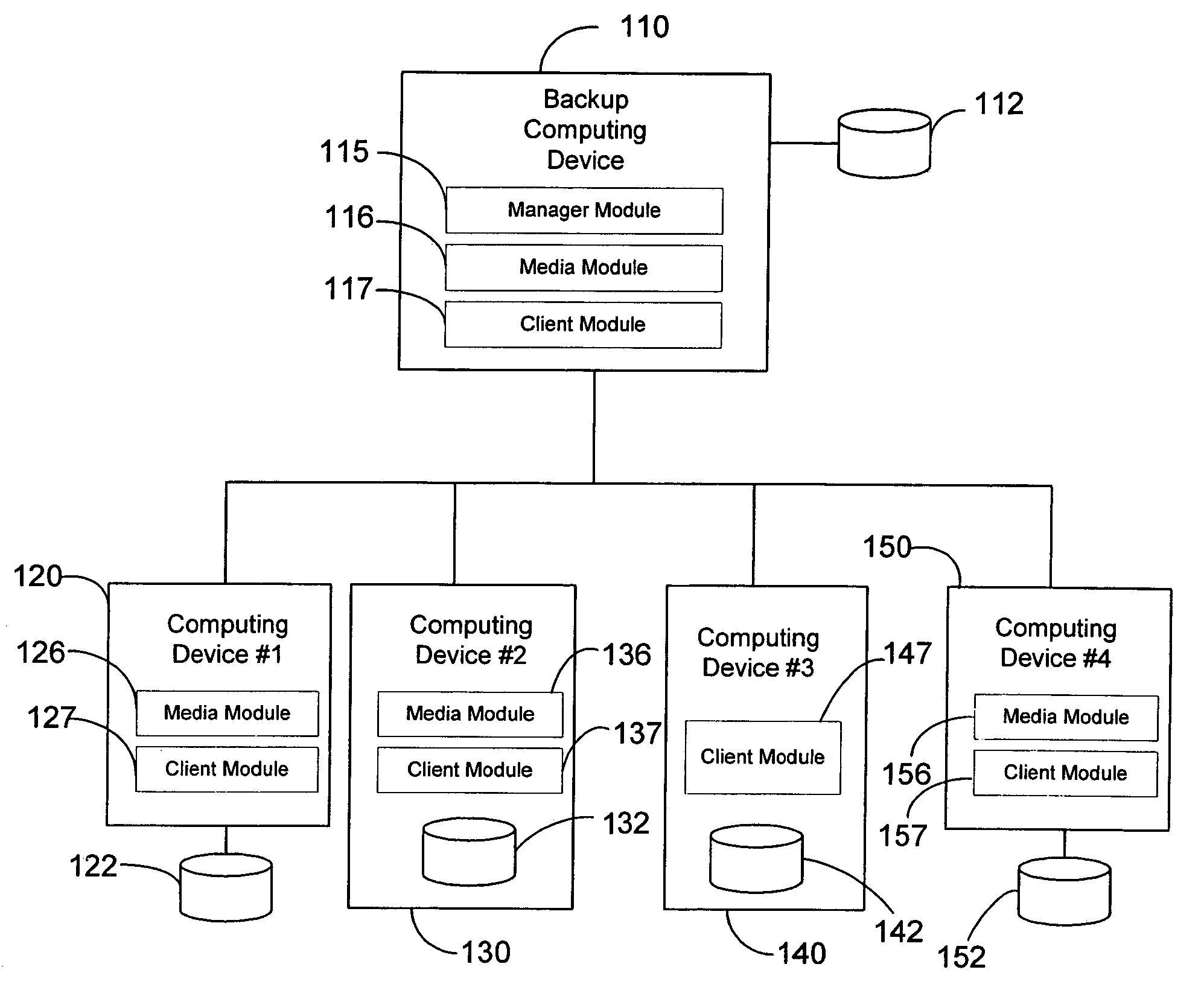
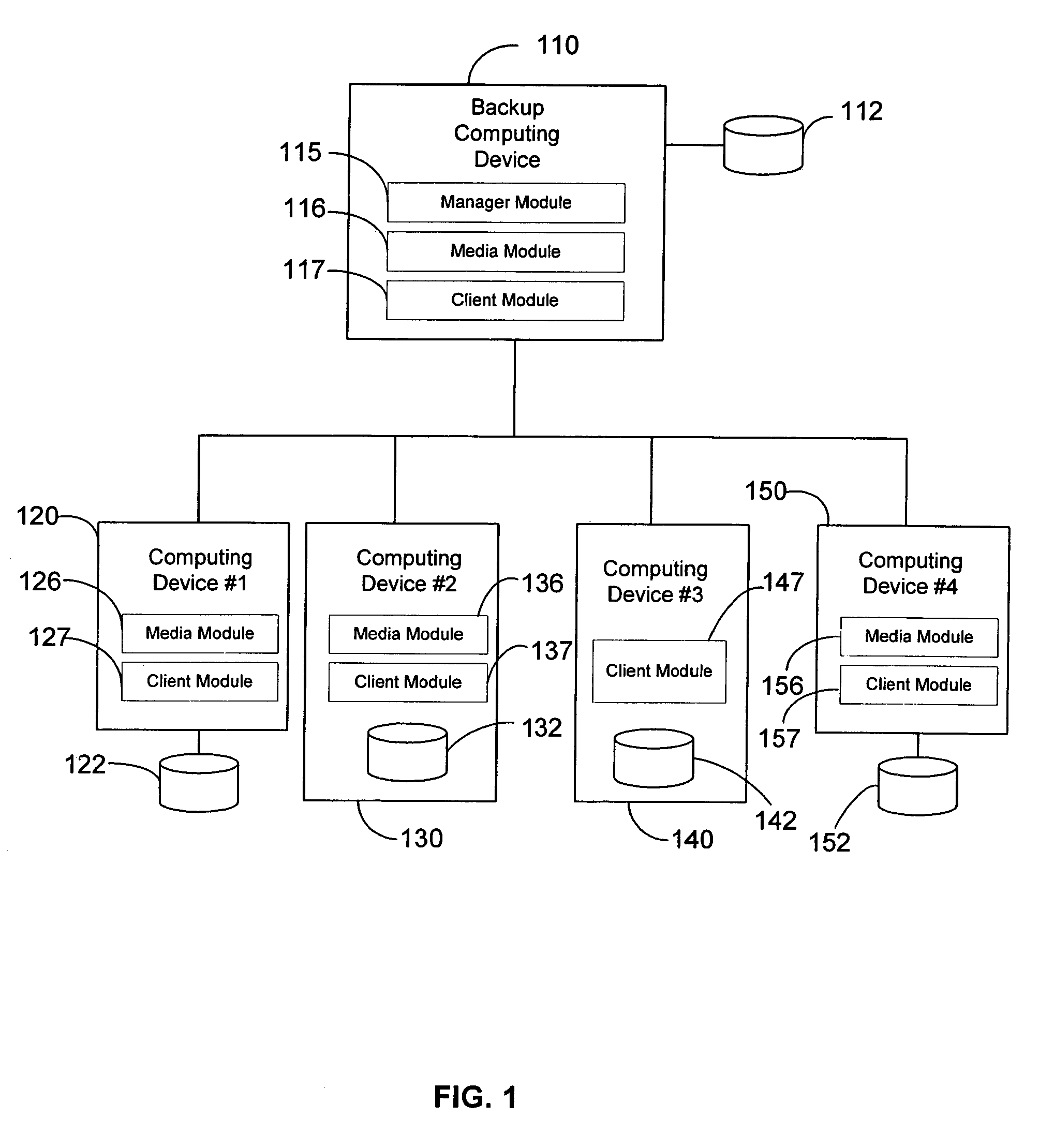
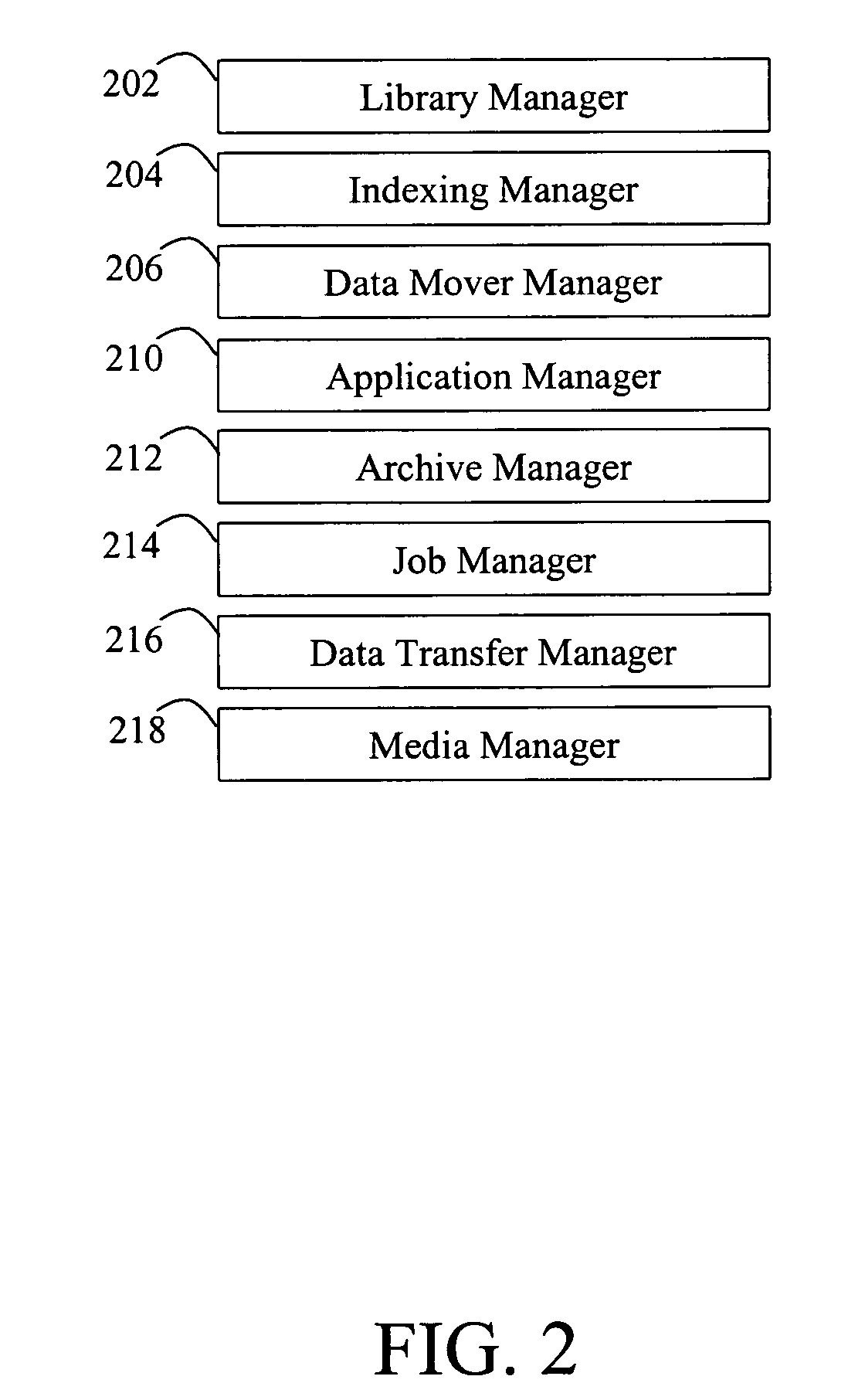
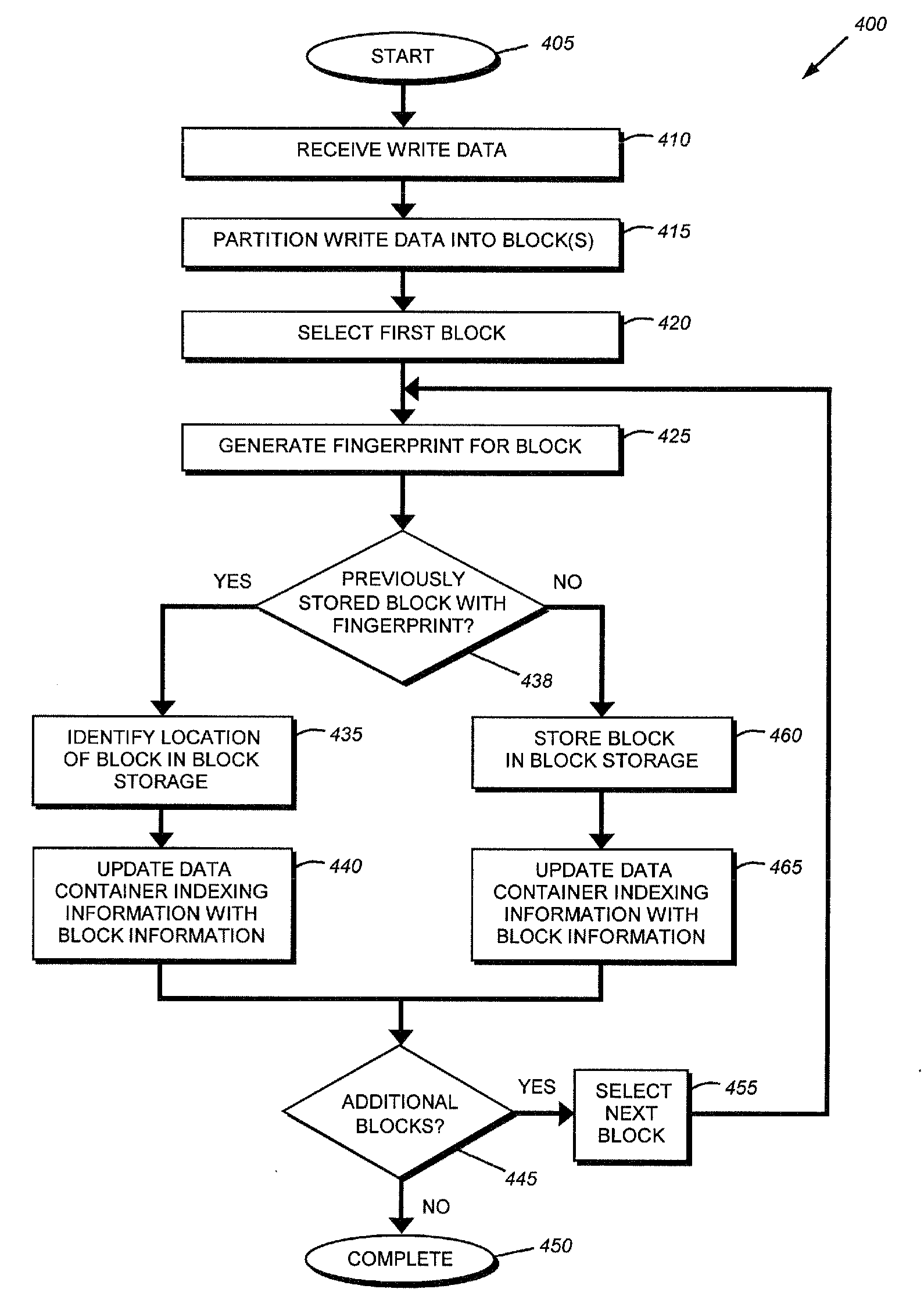
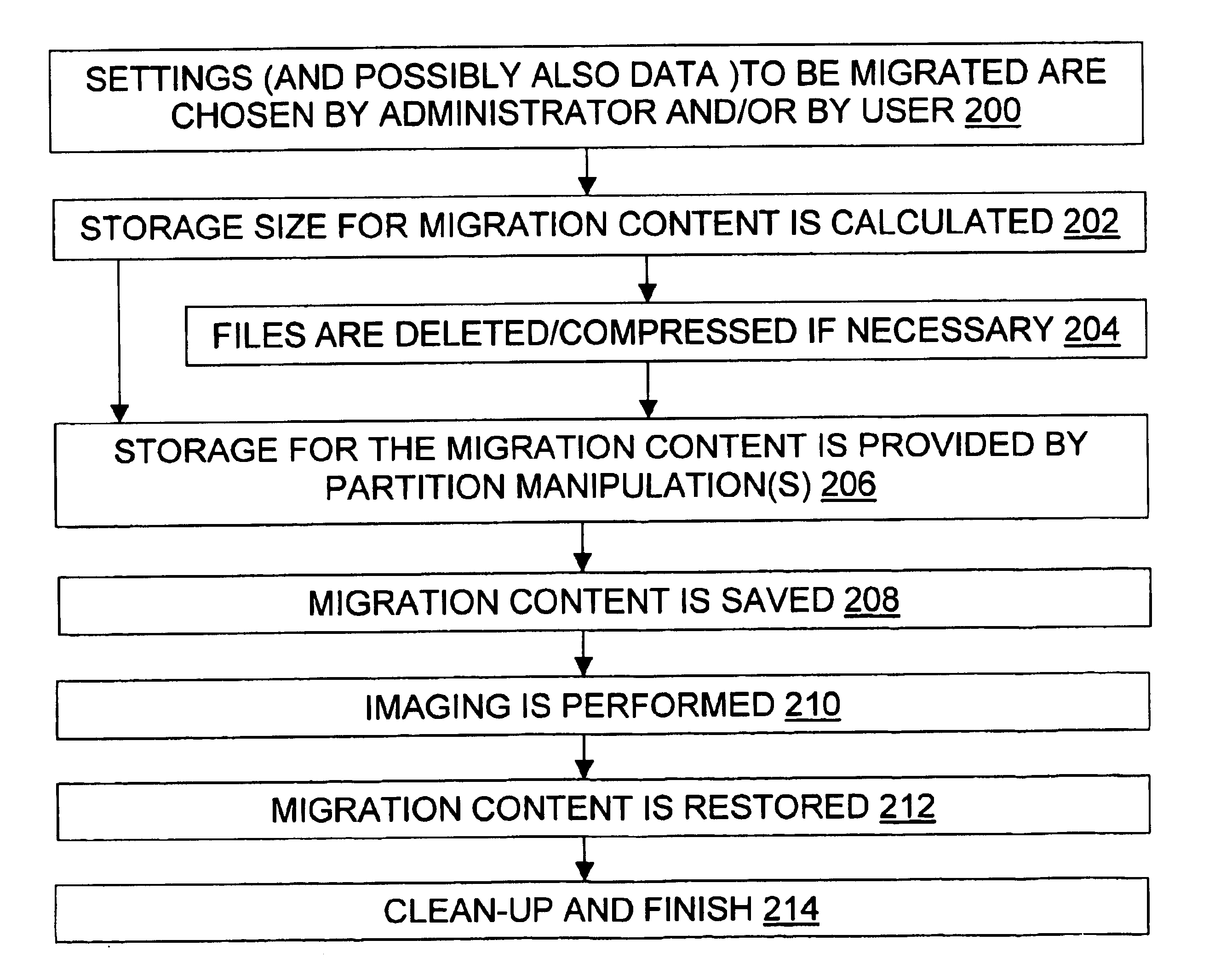
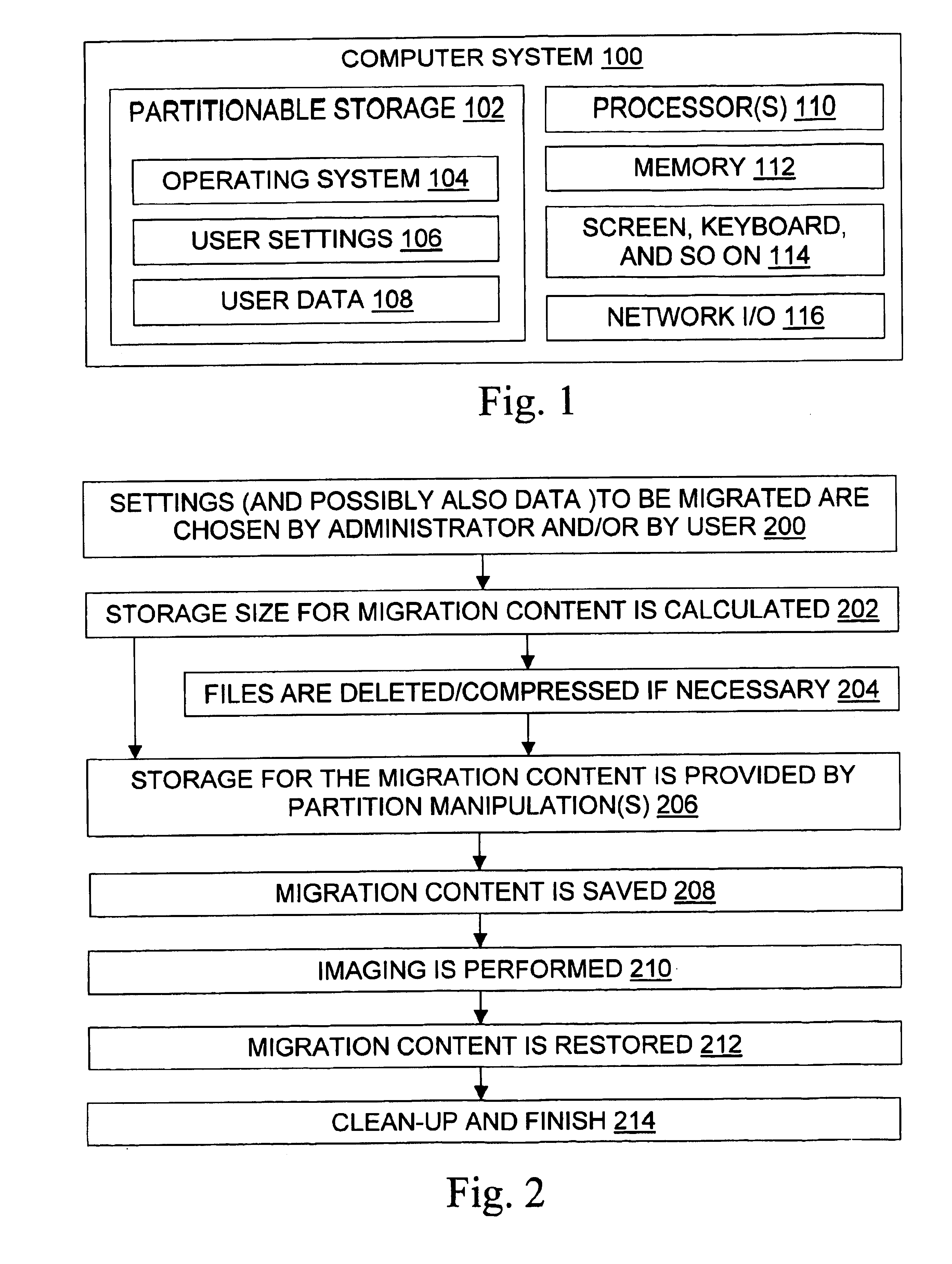
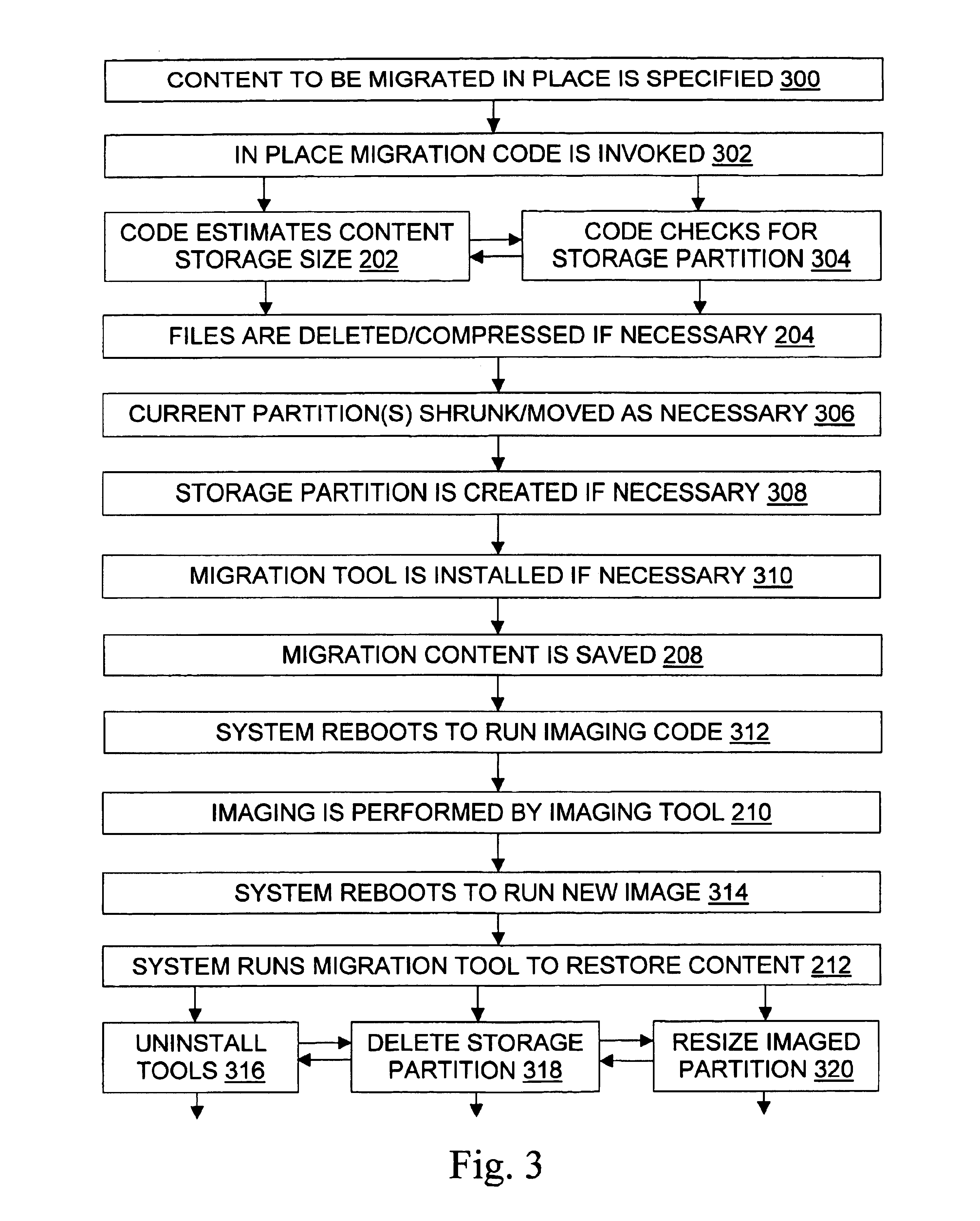
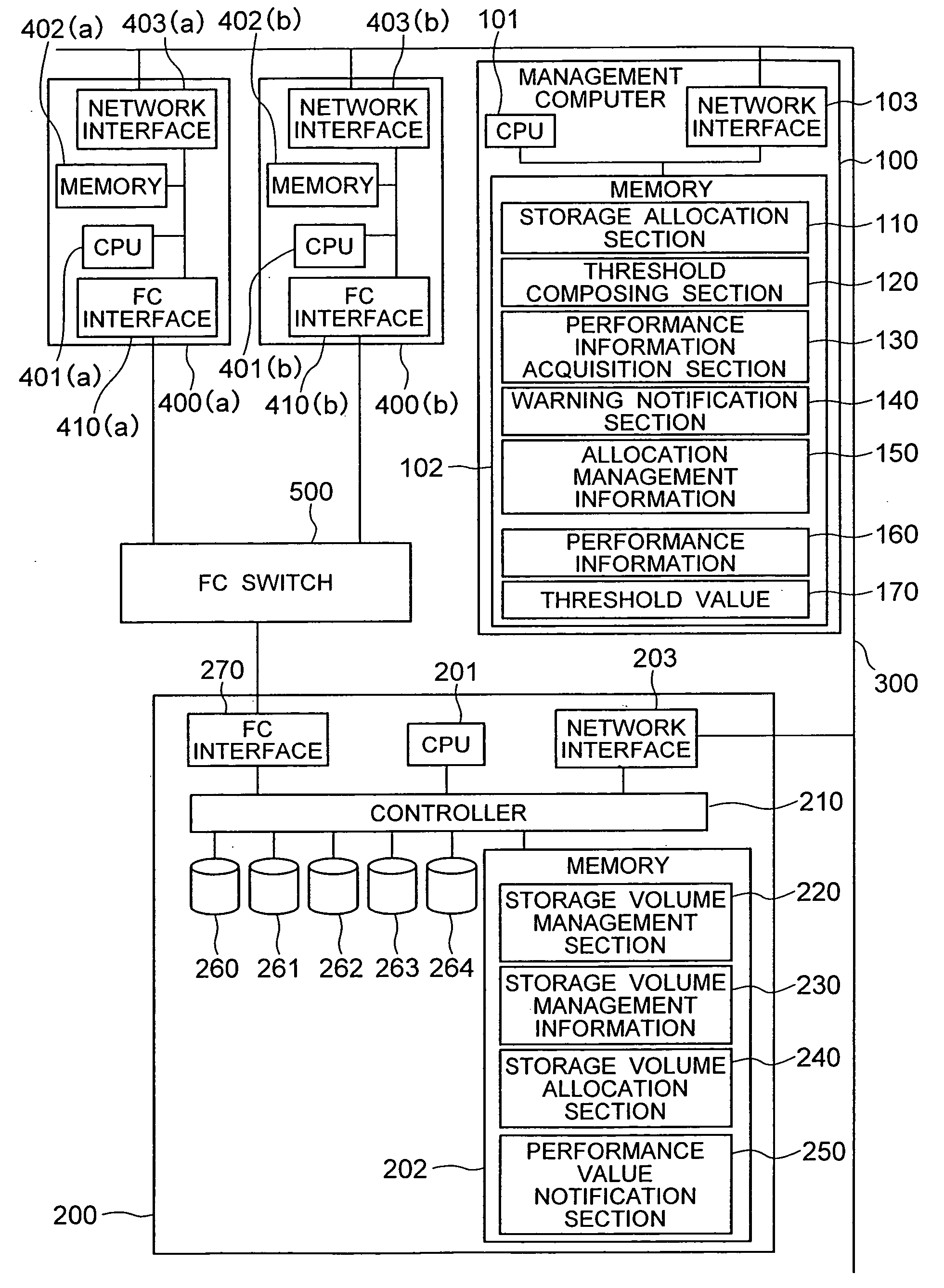
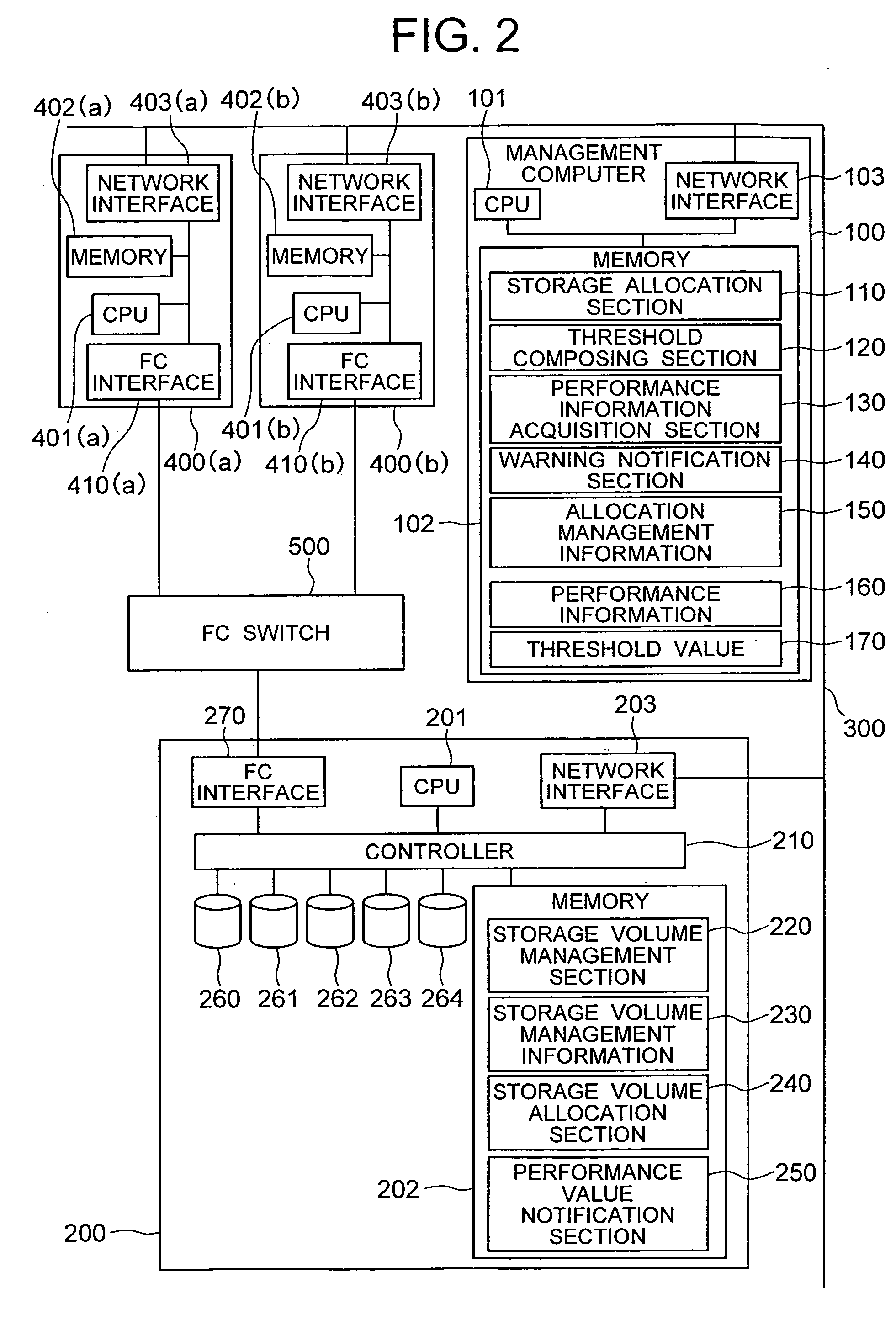
Modular backup and retrieval system
InactiveUS7389311B1Data processing applicationsDigital data processing detailsSystems managementModularity
Owner:COMMVAULT SYST INC
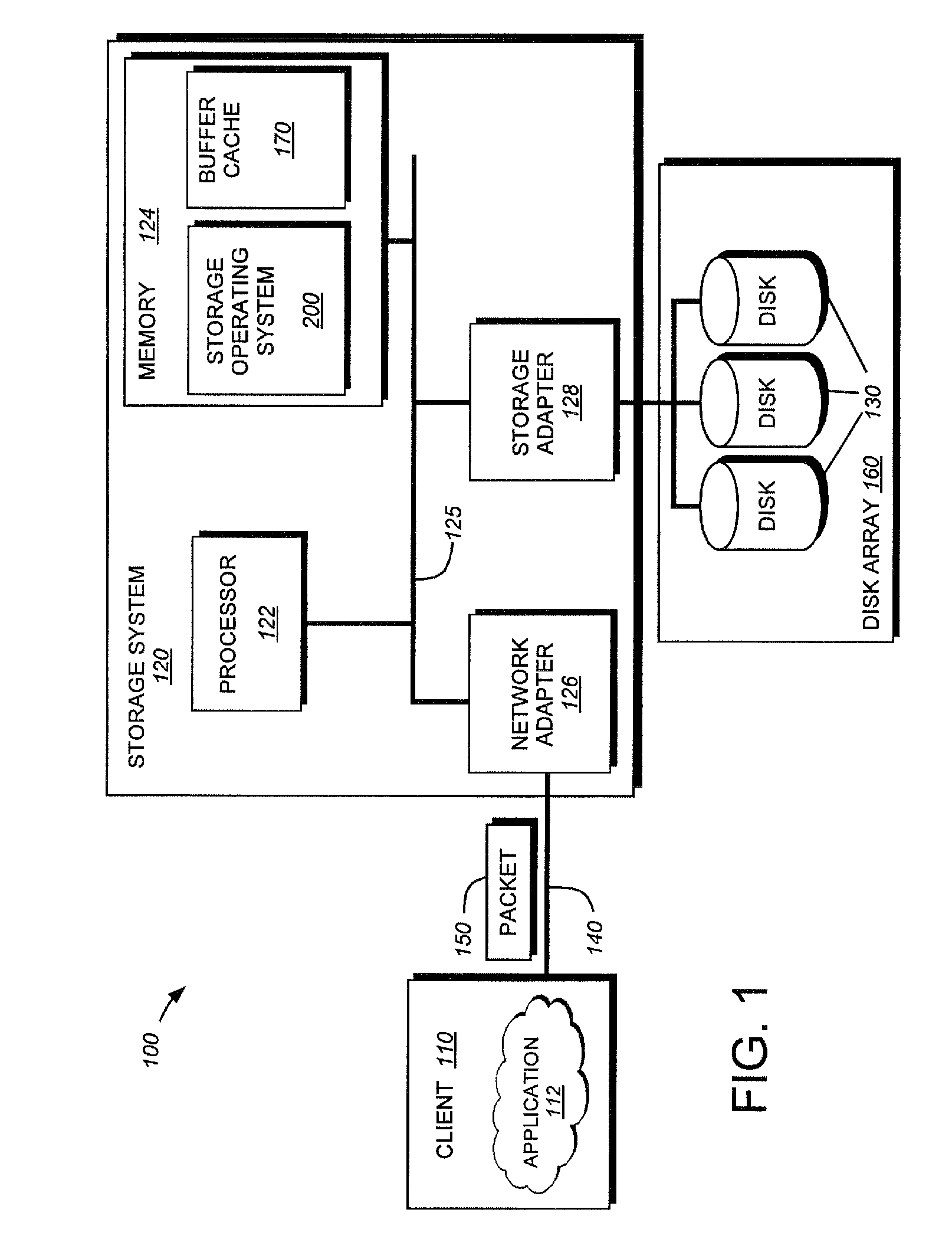
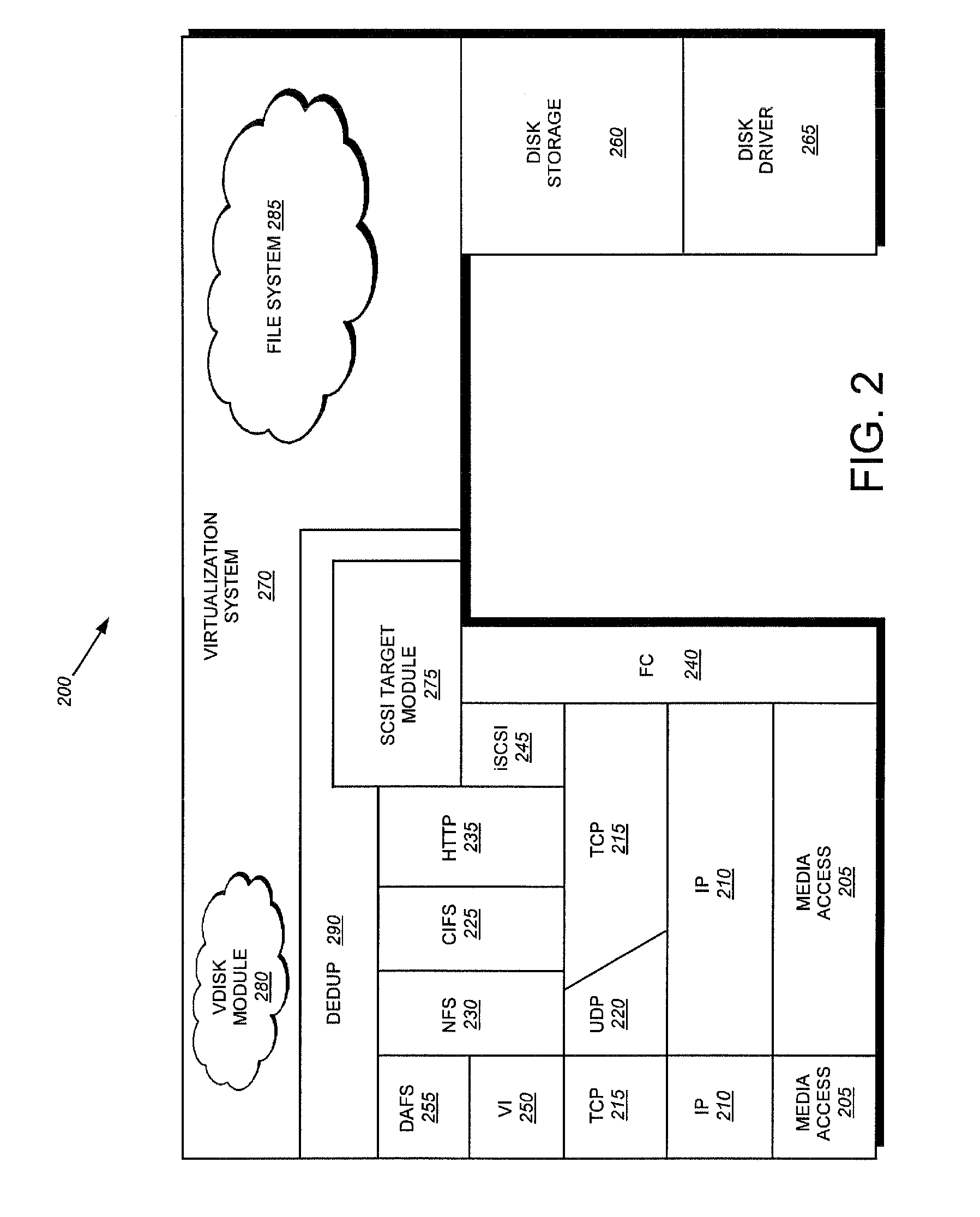
System and method for on-the-fly elimination of redundant data
ActiveUS20080294696A1Digital data information retrievalDigital data processing detailsOperational systemFile system
Owner:NETWORK APPLIANCE INC
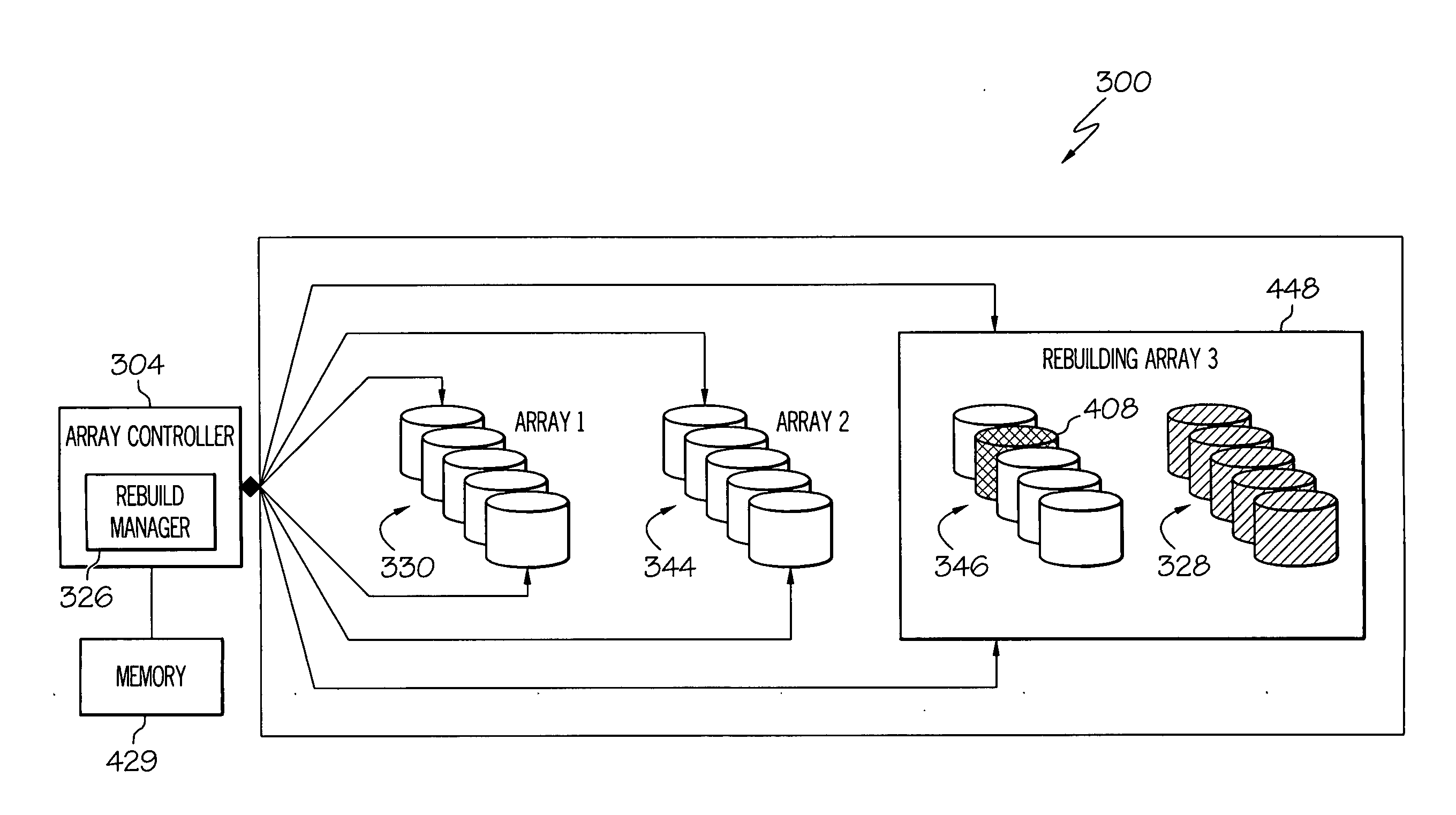
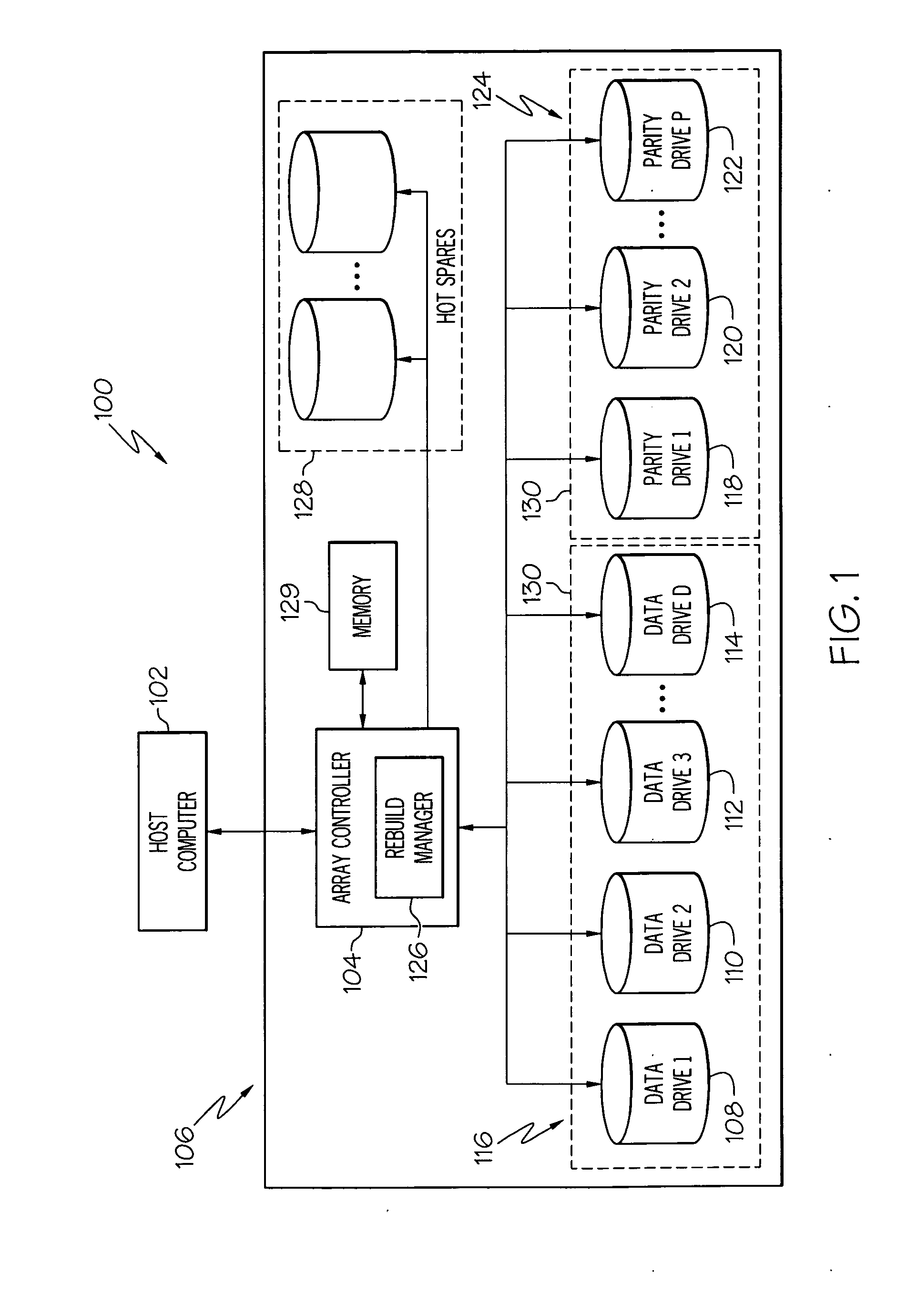
High performance disk array rebuild
InactiveUS20090228648A1Increasing rebuild timeError detection/correctionMemory systemsMagnetic disksDisk array
Owner:IBM CORP
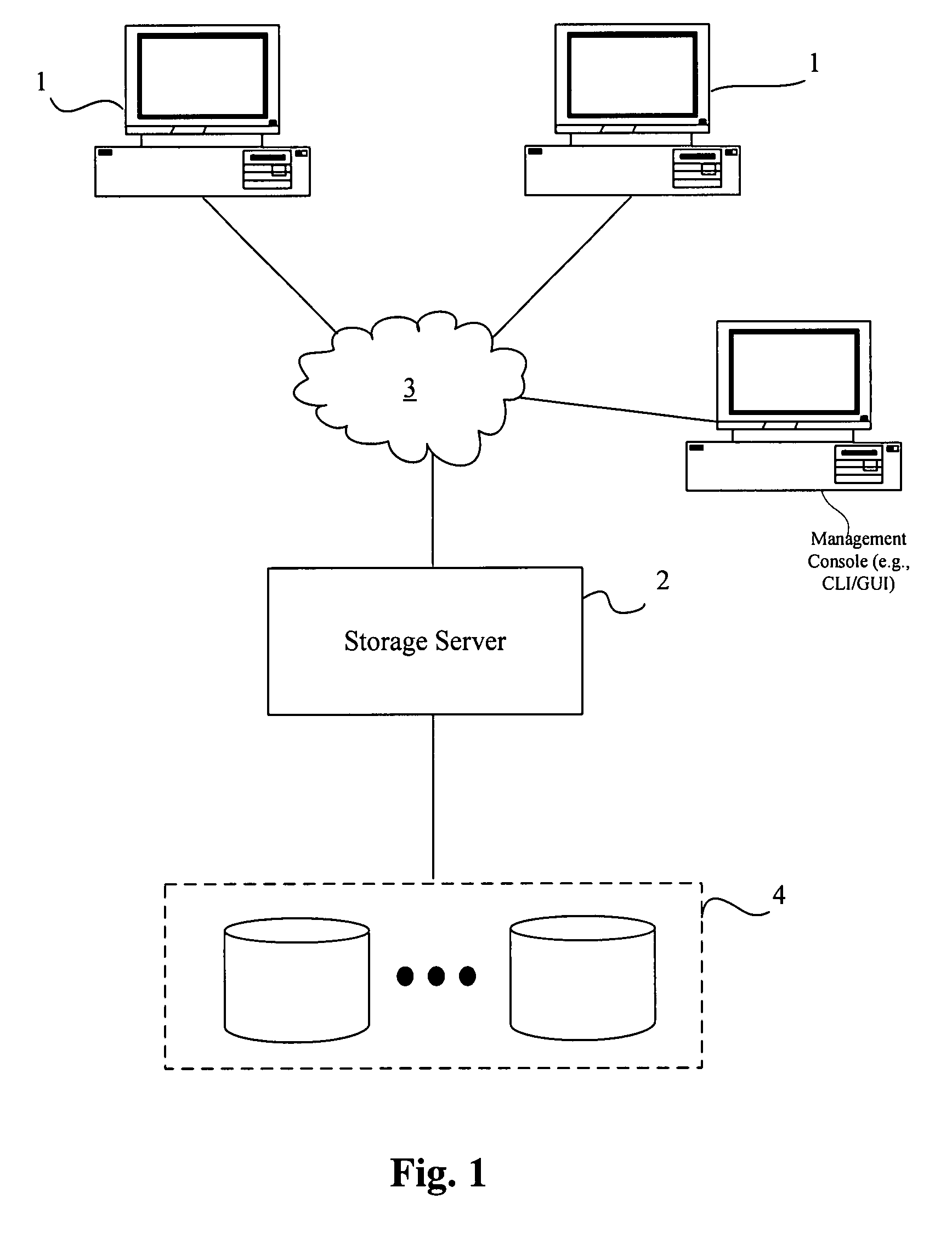
Dynamic identification and administration of networked clients
ActiveUS7568018B1Data resettingMultiple digital computer combinationsSubject matterDistributed computing
The present inventive subject matter relates to networked computing environments and more specifically to dynamic identification and administration of networked clients. Various embodiments of the present inventive subject matter include systems and methods for defining, on a server, a configuration of interest comprising one or more potential properties of a client, communicating the configurations of interest over a network to one or more clients, dynamically evaluating a client state relative to the configurations of interest, and communicating a representation of the client state in relation to the configuration of interest to the server. Further embodiments include automatically creating and displaying associations of clients based on configurations of interest. Yet further embodiments include clients requesting and receiving updates to the configurations of interest. Still further embodiments include actions associated with configurations of interest. Such actions, in various embodiments, include performing administrative actions on various networked clients.
Owner:NEW BOUNDARY TECH
Managing data storage for databases based on application awareness
Owner:EMC IP HLDG CO LLC
Automated application discovery and analysis system and method
ActiveUS20060123022A1Digital data processing detailsObject oriented databasesSystems designMonitoring system
Owner:GLOBAL SAAS SOLUTIONS PTE LTD
Application server system and computer product
InactiveUS20070226715A1Solve problemsSoftware simulation/interpretation/emulationMemory systemsApplication serverComputer science
Owner:FUJITSU LTD
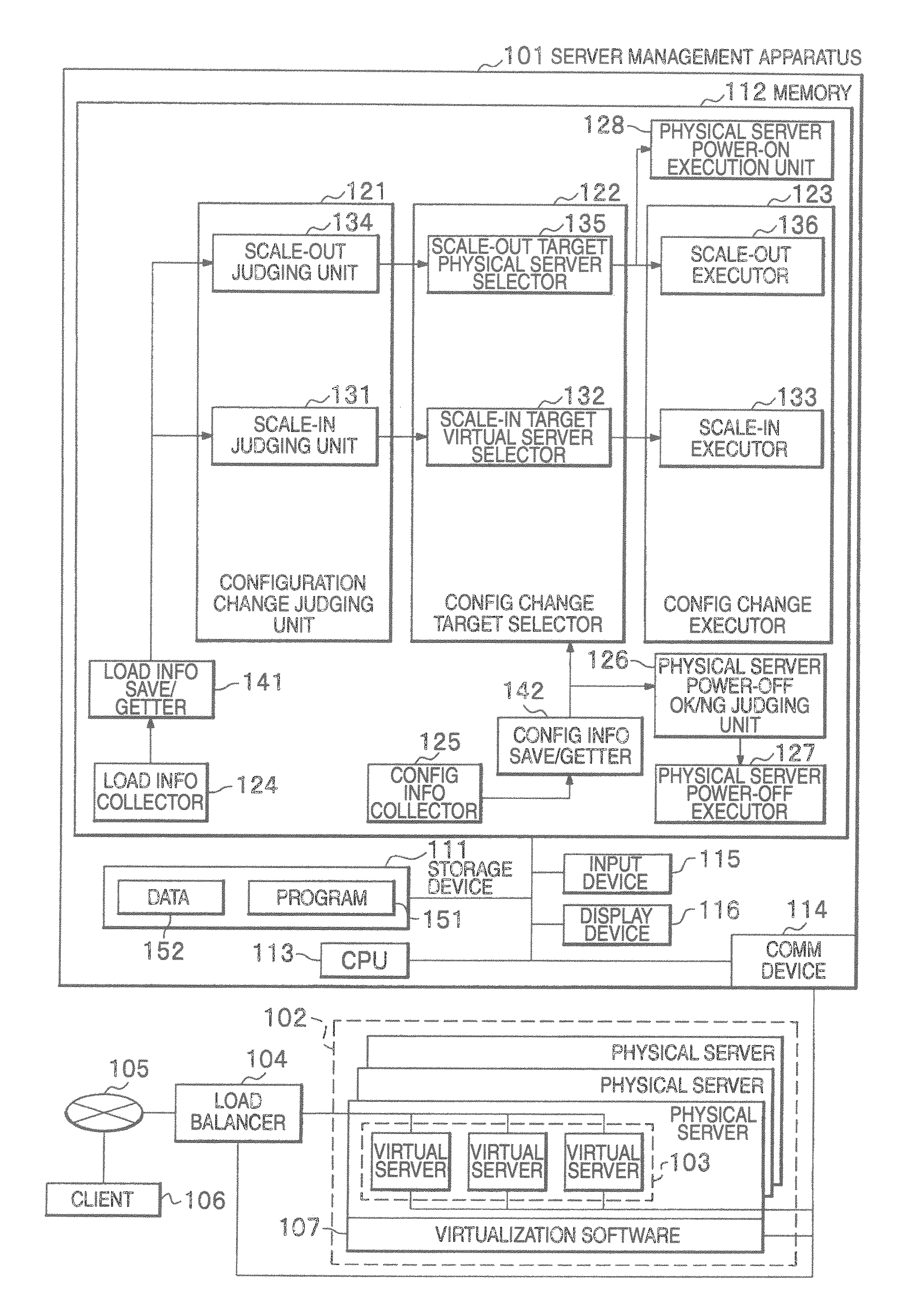
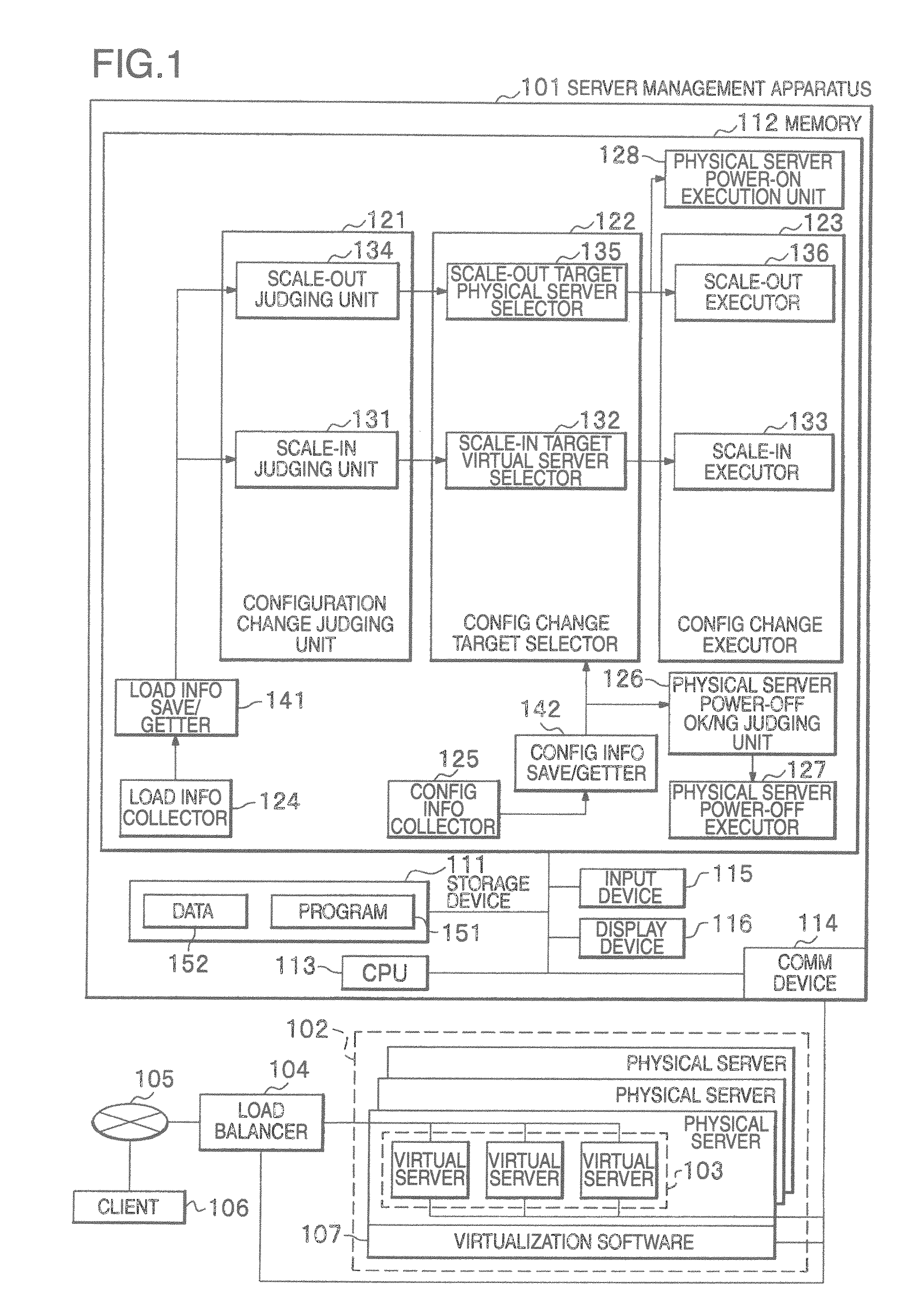
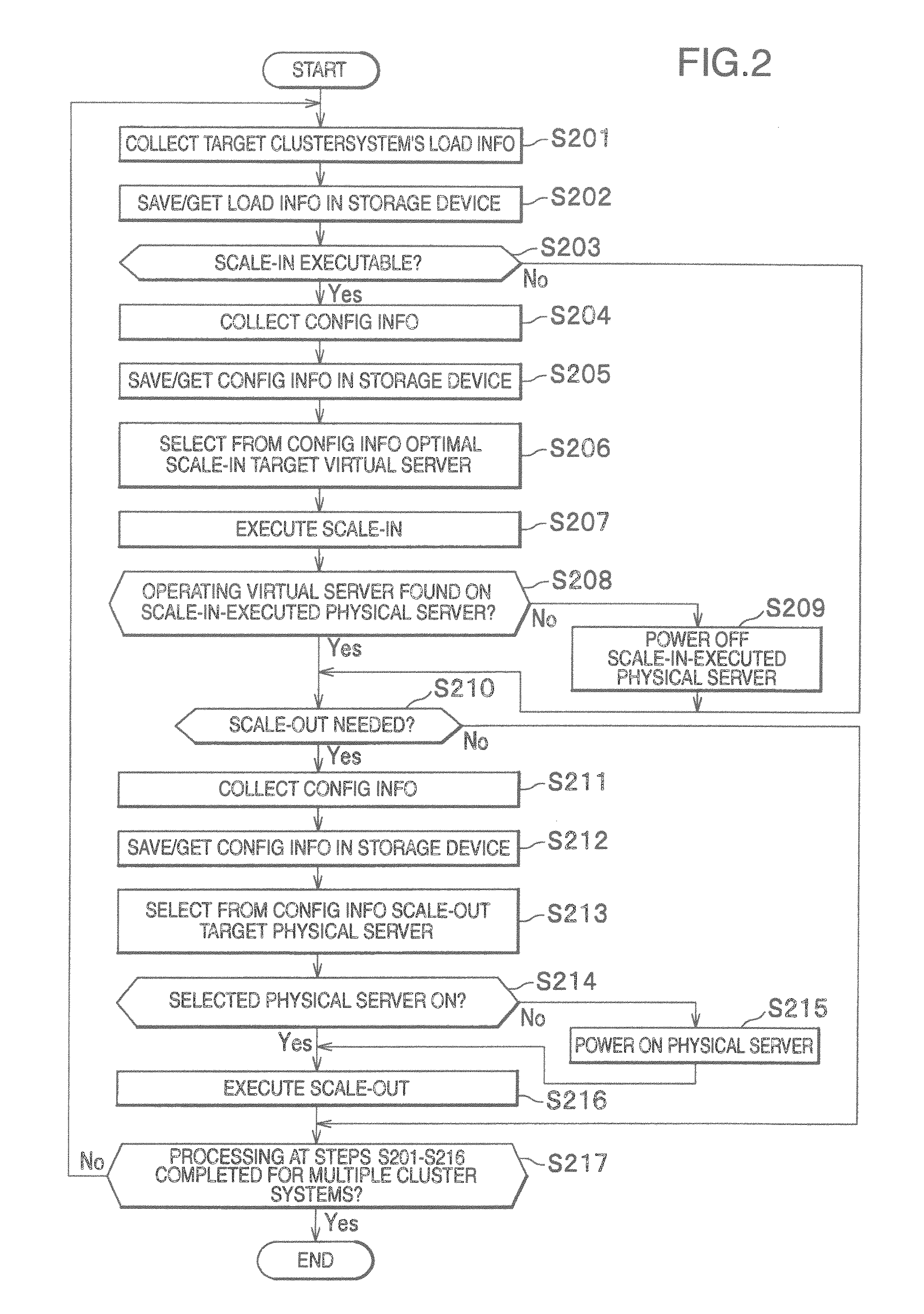
Server management apparatus and server management method
InactiveUS20110099403A1Increase volumeIncrease the number ofEnergy efficient ICTDigital computer detailsCluster systemsWorkload consolidation
Owner:HITACHI LTD
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
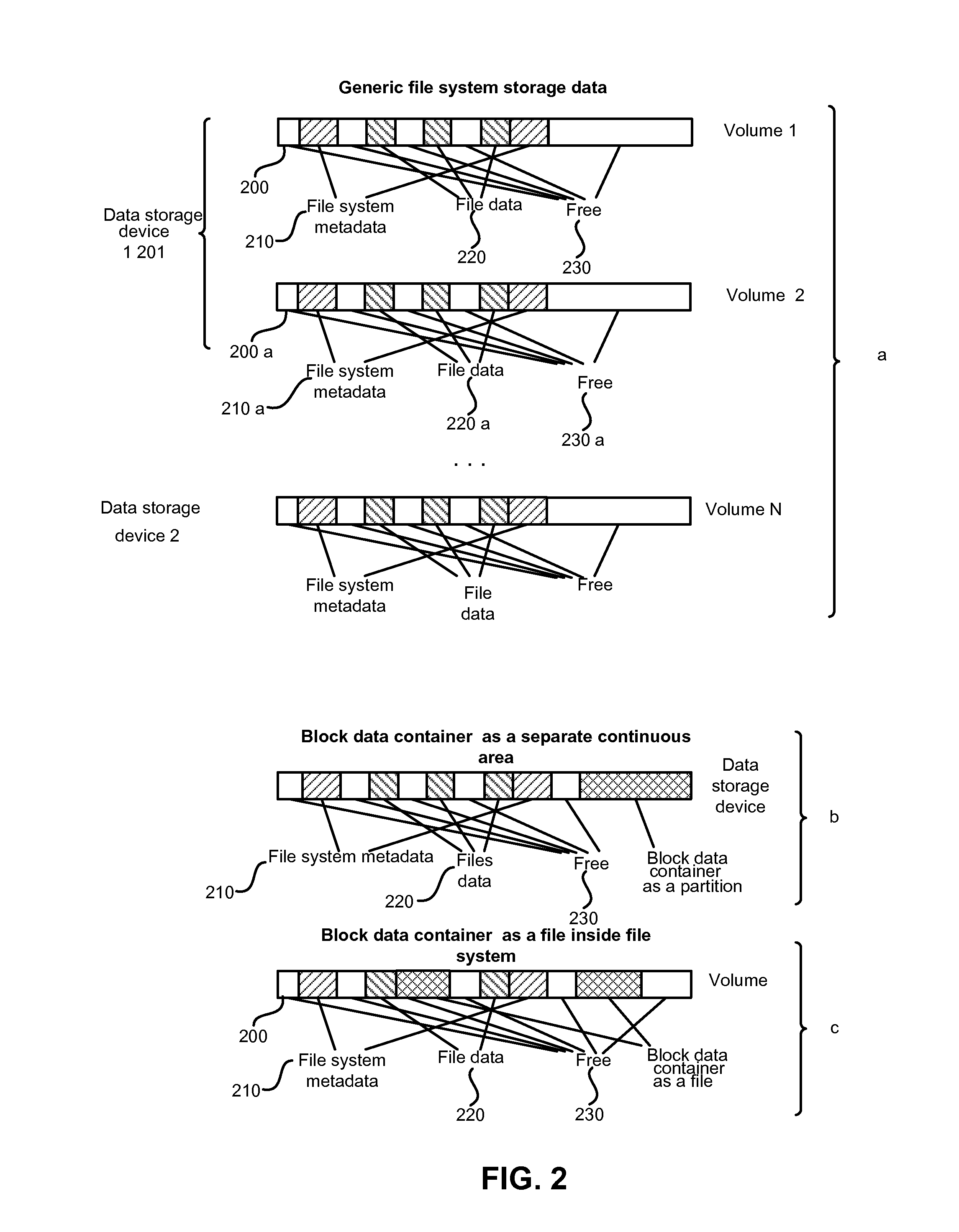
Data containerization for reducing unused space in a file system
Owner:NETWORK APPLIANCE INC
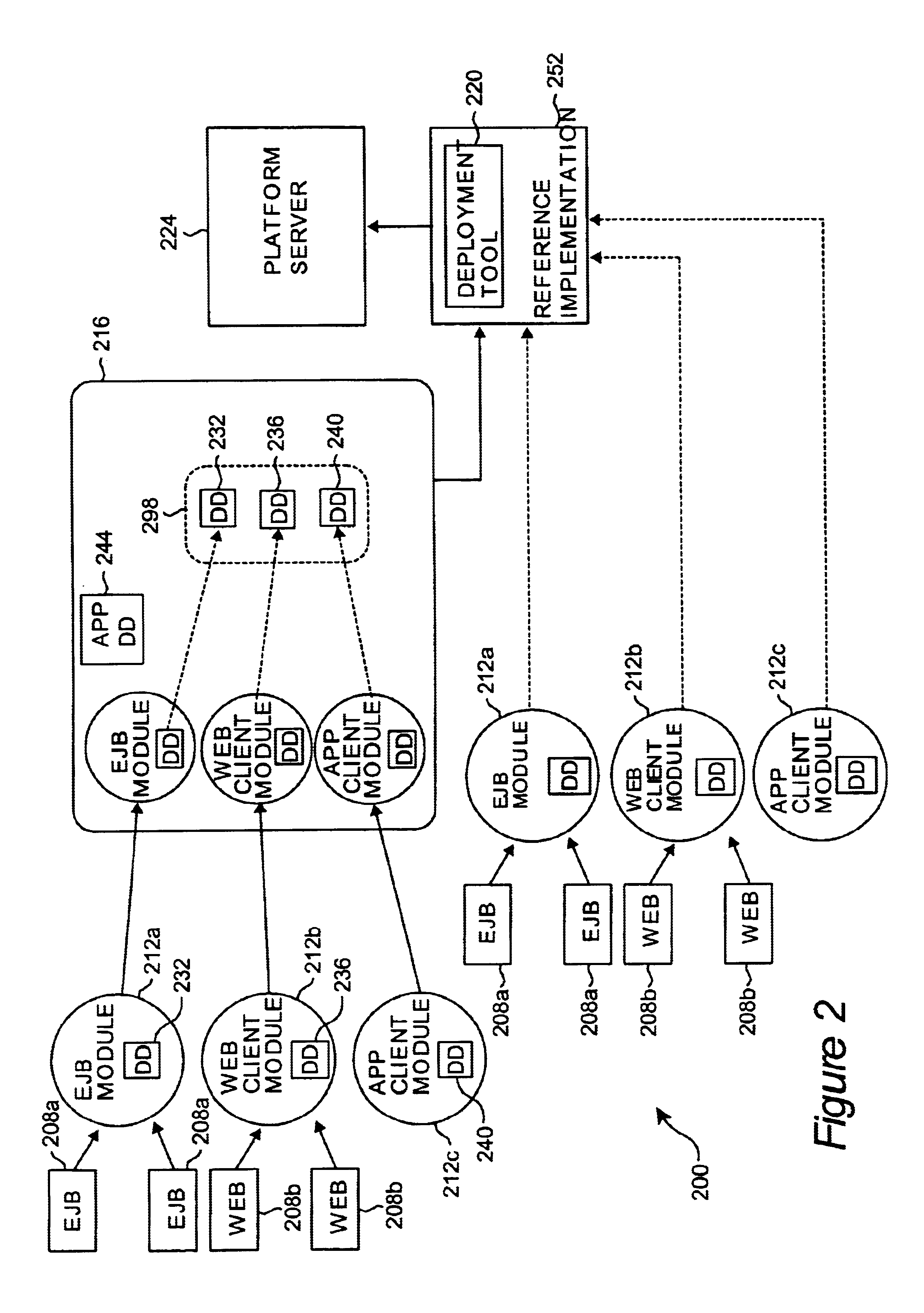
Method and apparatus for implementing deployment descriptors in an enterprise environment
Methods and apparatus for implementing deployment descriptors which are used to deploy modules in an enterprise environment are disclosed. According to one aspect of the present invention, a method for deploying an application using a deployment tool for use on a platform server includes creating the application, creating an application deployment descriptor for the application, packaging the application in an archive, and deploying the application packaged in the archive. Creating the application includes obtaining an application component which has an associated application component deployment descriptor that has information relating to the deployment of the application component. The application deployment descriptor for the application includes information arranged to identify the application component, and packaging the application in an archive includes packaging the application component, the application component deployment descriptor, and the application deployment descriptor. The application packaged in the archive is deployed using the application component deployment descriptor.
Owner:ORACLE INT CORP
Methods for upgrading, diagnosing, and maintaining replaceable non-volatile memory
In one embodiment of the invention, a replaceable memory apparatus is disclosed. The replaceable memory apparatus includes a first rectangular multilayer printed circuit board having a first side and a second side opposite the first side; a first male pluggable electrical connector mounted to the first side near a first edge; a first female pluggable electrical connector mounted to the second side; and first non-volatile memory mounted to the first side and the second side. The first female pluggable electrical connector is coupled to the first male pluggable electrical connector to feed through first signals. The first non-volatile memory is coupled to the first female pluggable electrical connector and the first male pluggable electrical connector to receive the first signals.
Owner:WESTERN DIGITAL TECH INC
Support for application programs in a distributed environment
InactiveUS6138168AEasy to identifyProgram initiation/switchingInterprogram communicationModularityMessage type
Owner:IBM CORP
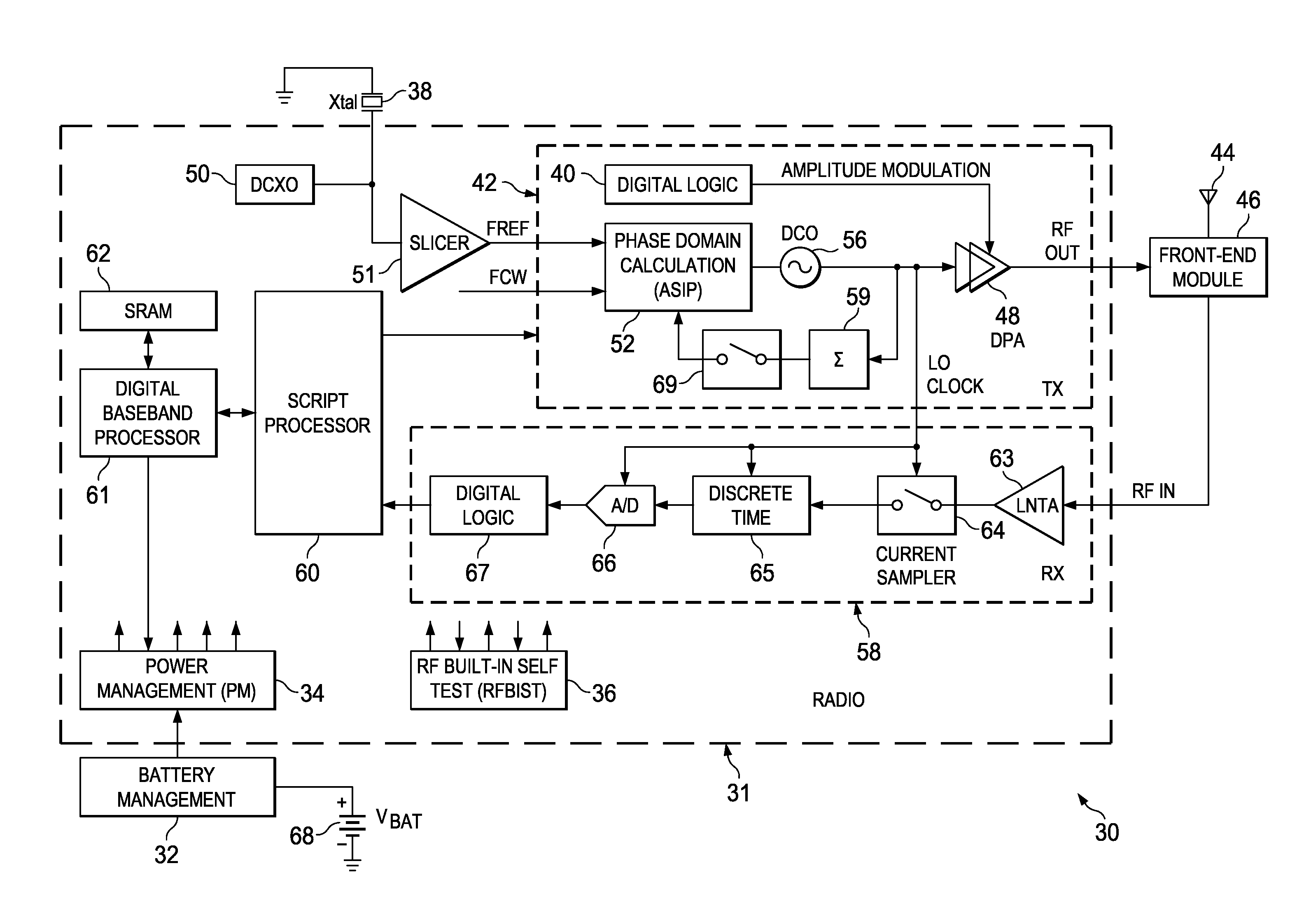
Computation parallelization in software reconfigurable all digital phase lock loop
ActiveUS20090070568A1Easy to reconfigureReduce per cycle current transientPulse automatic controlGeneral purpose stored program computerData stream processingTime-sharing
Owner:TEXAS INSTR INC
System and method for using multivolume snapshots for online data backup
ActiveUS8074035B1Increasing computer system availabilityError detection/correctionDigital data processing detailsFile systemData store
Owner:MIDCAP FINANCIAL TRUST
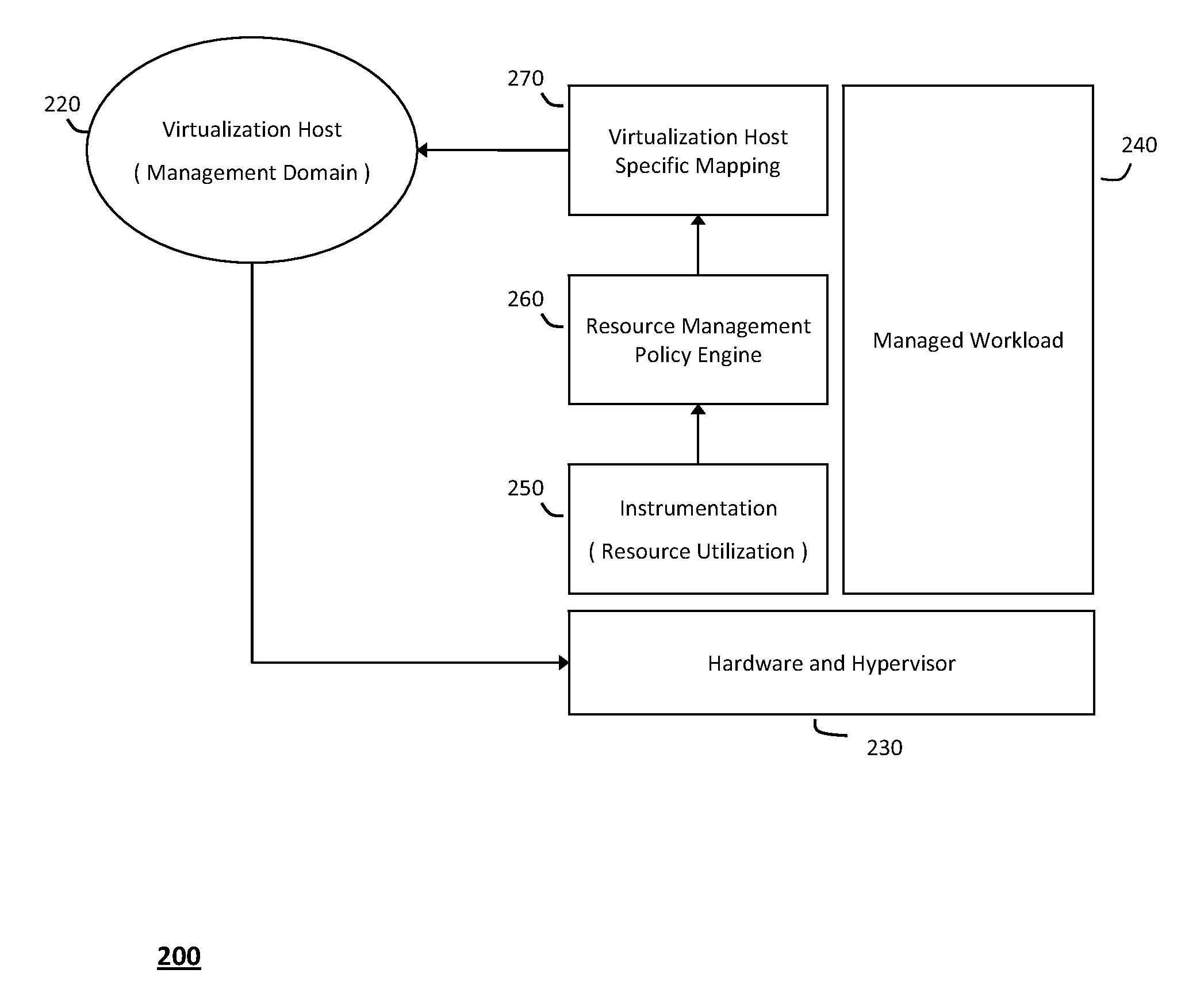
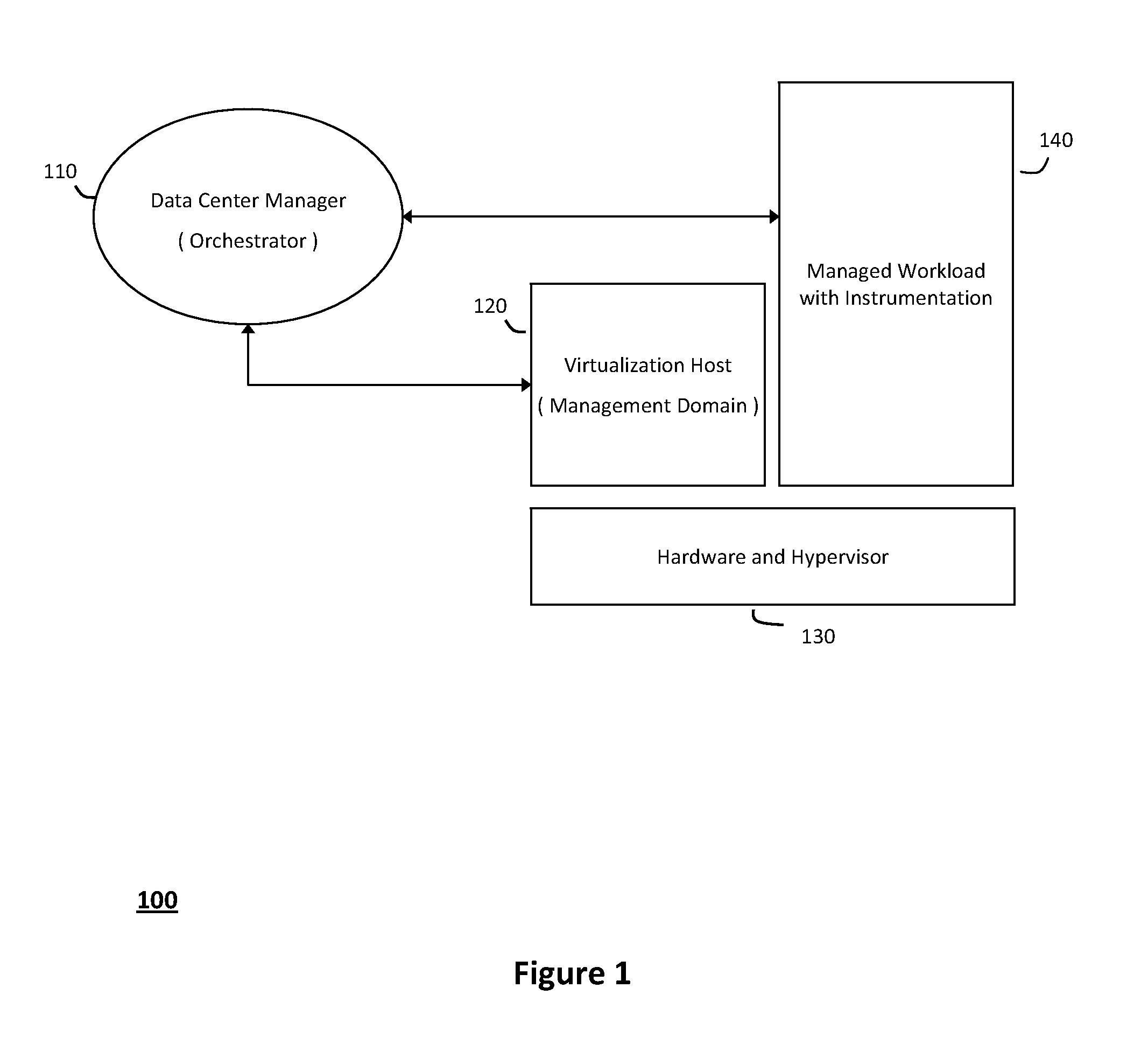
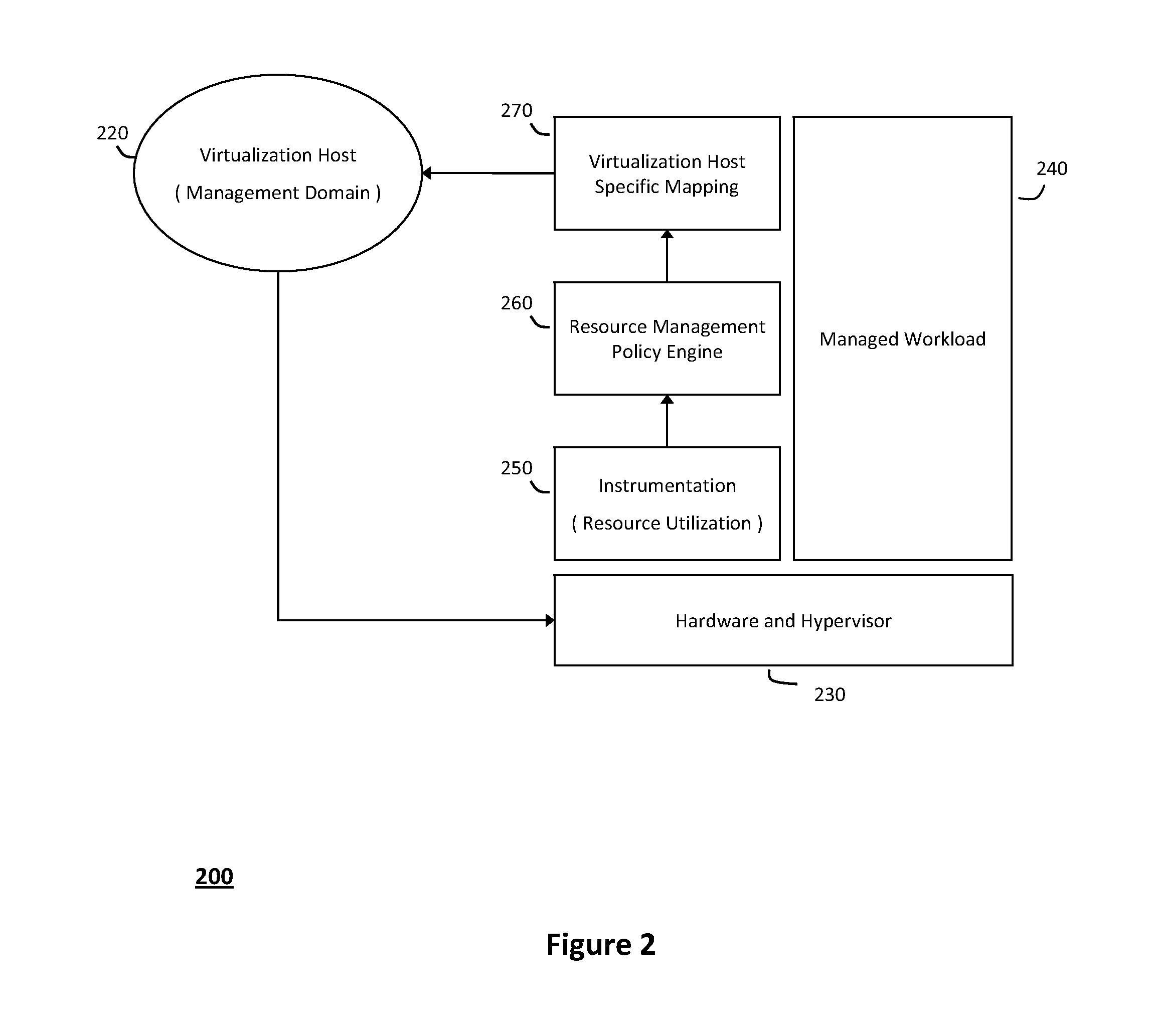
System and method for structuring self-provisioning workloads deployed in virtualized data centers
ActiveUS20120054763A1Improve portabilityResource allocationDigital computer detailsVirtualizationData center
Owner:SUSE LLC
System and method for migrating stateless virtual functions from one virtual plane to another
A system and method for migration of stateless virtual functions from one virtual plane to another are provided. When a migration of a source virtual function to a destination virtual function in another virtual plane is to be performed, a source single root PCI manager (SR-PCIM) is first interrupted by a multiple root PCI manager (MR-PCIM). Configuration information that defines the source virtual function is then redefined on the destination virtual function for this stateless migration. A function level reset may then be performed on the source virtual function. The destination SR-PCIM may be interrupted by the MR-PCIM with an interrupt for the destination virtual function. A function level reset may then be performed on the destination virtual function. The destination virtual function state may then be changed to an “active” state such that the migrated virtual function begins processing transactions.
Owner:INT BUSINESS MASCH CORP
Service licensing and maintenance for networks
InactiveUS20060036847A1Random number generatorsUser identity/authority verificationUnique identifierPhysical address
Owner:CISCO TECH INC
Test management system and method
InactiveUS20100146514A1Complex in executionResource allocationError detection/correctionExecution planTest management
Owner:IBM CORP
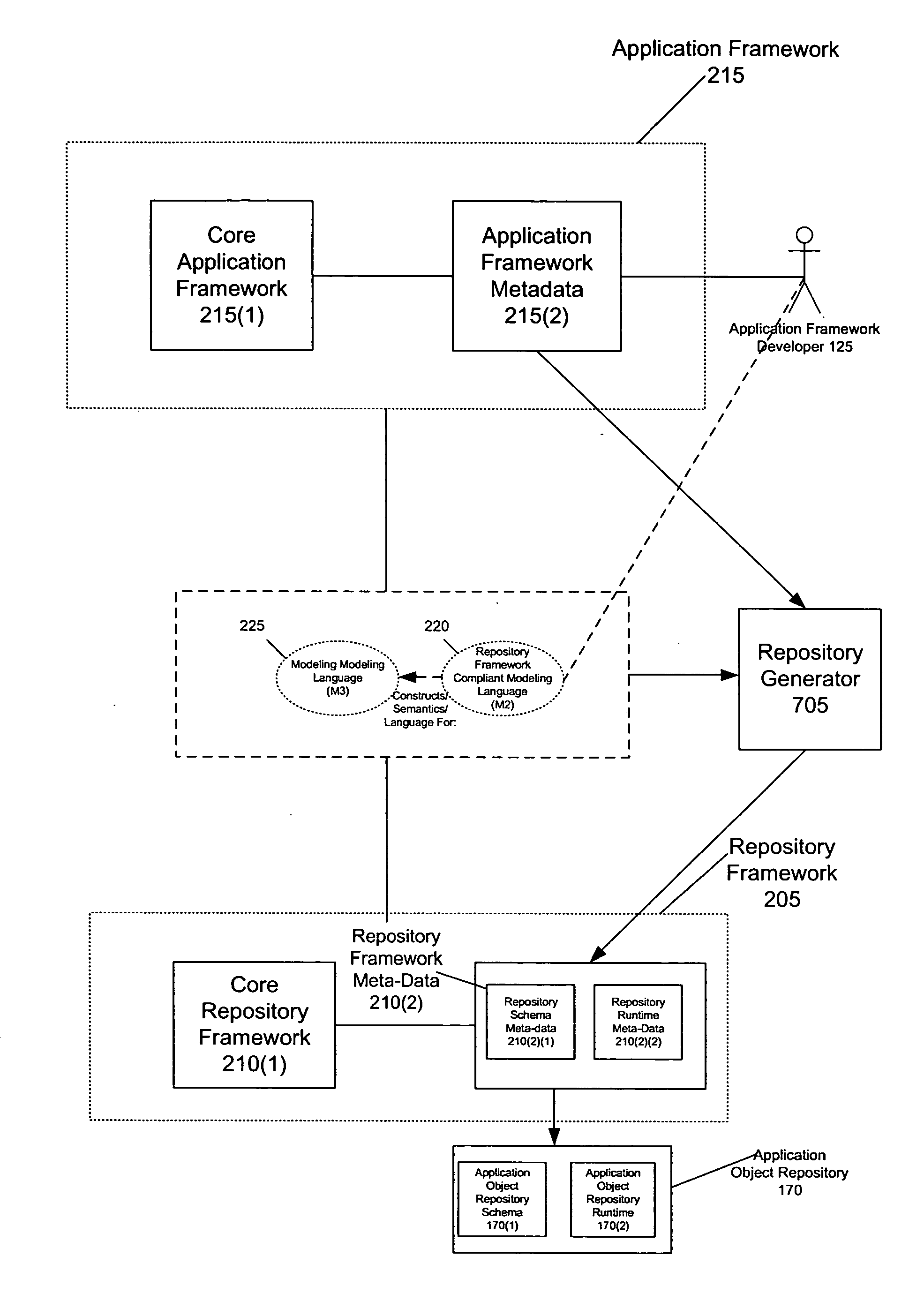
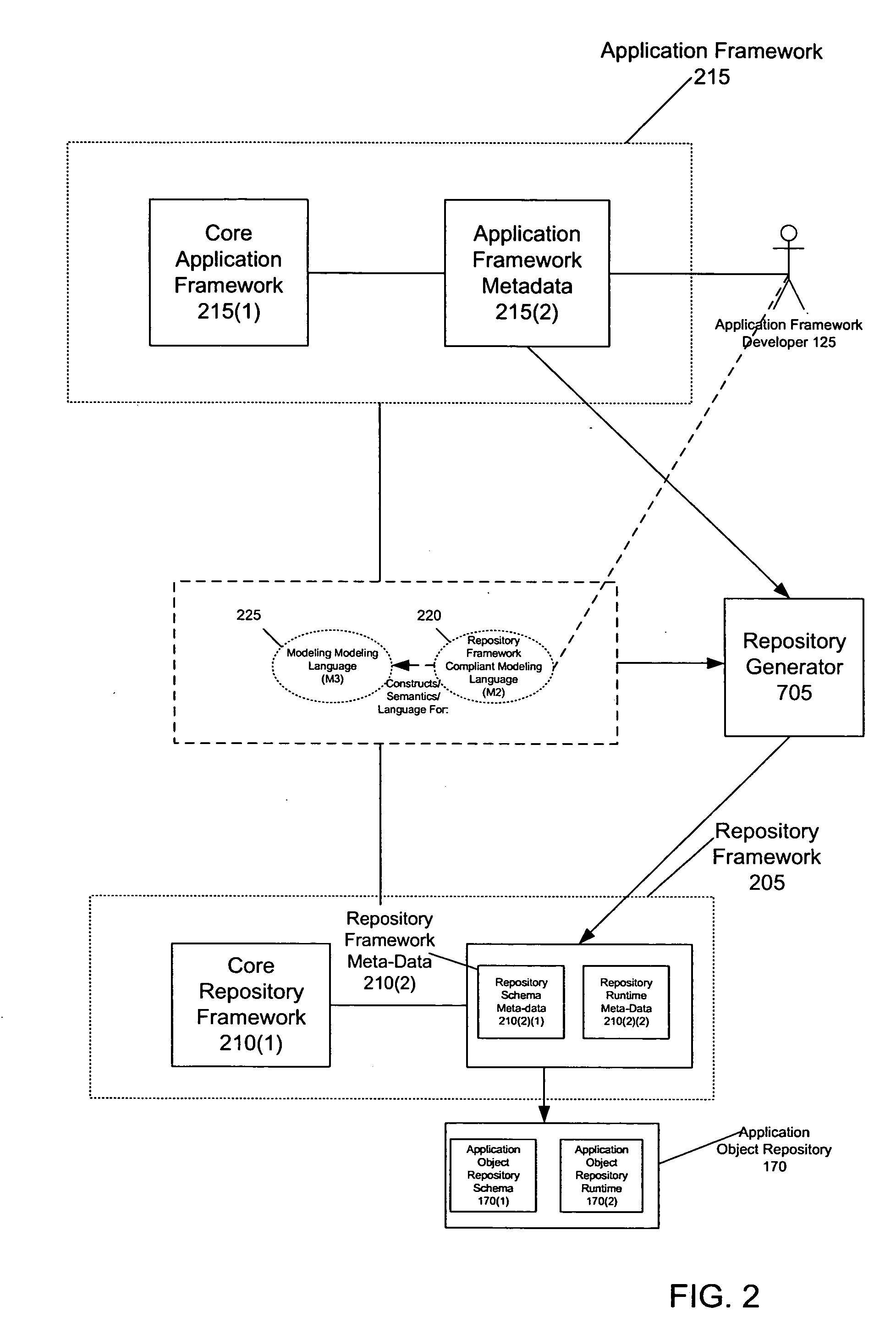
Method and system for generating an application object repository from application framework metadata
Owner:SAP AG
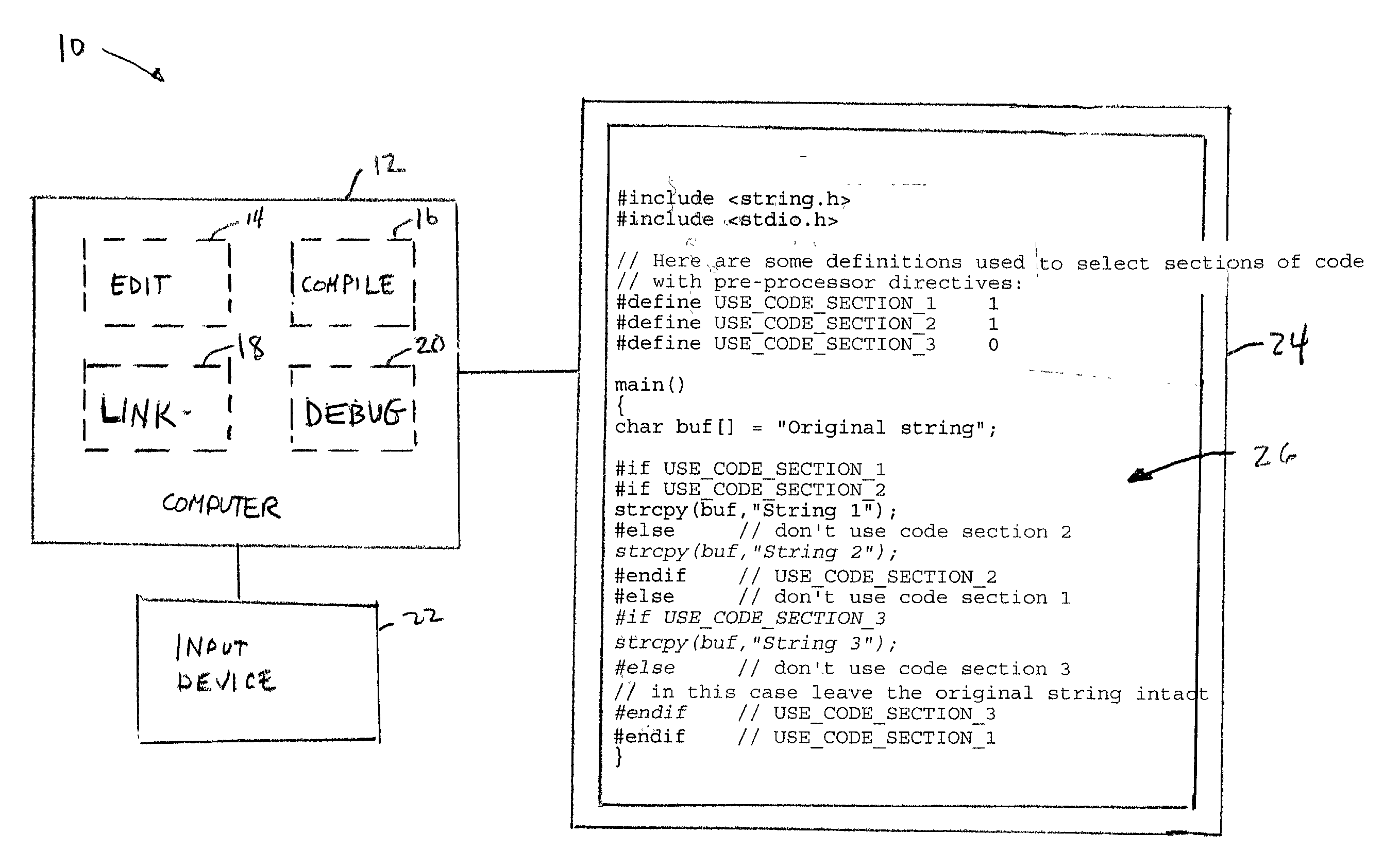
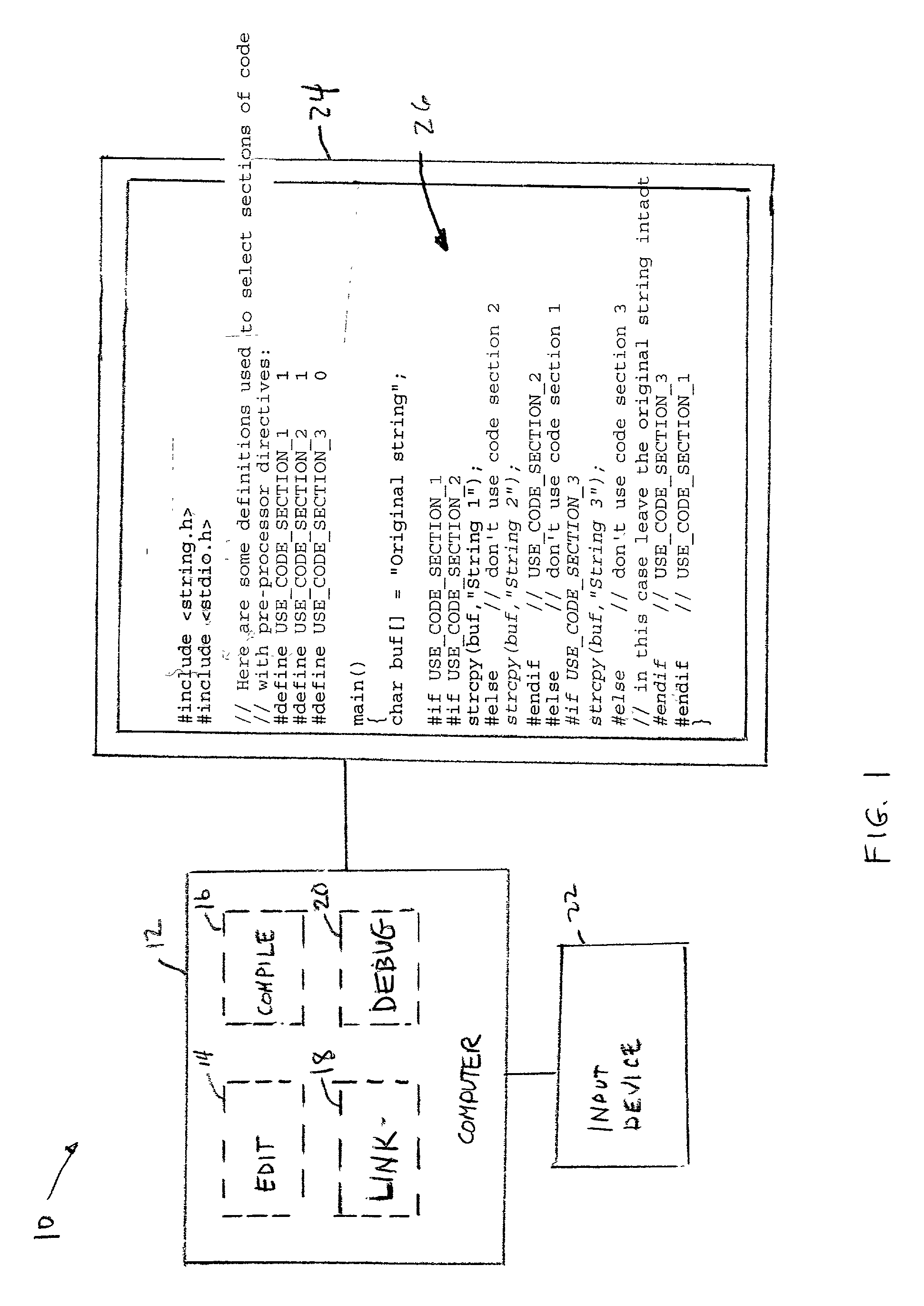
Design system and method having improved display of code
Owner:ACCESS SYSTEMS AMERICAS
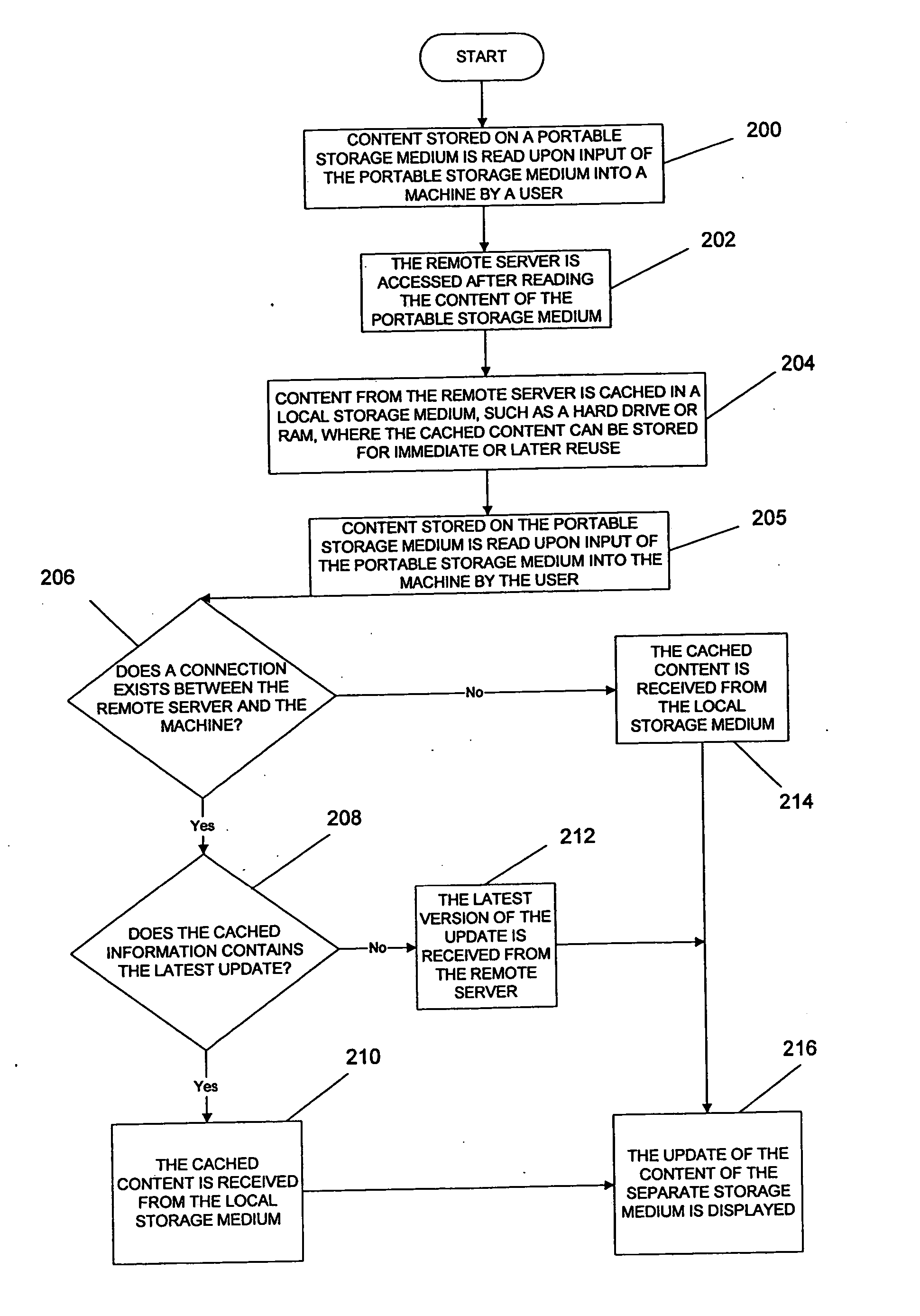
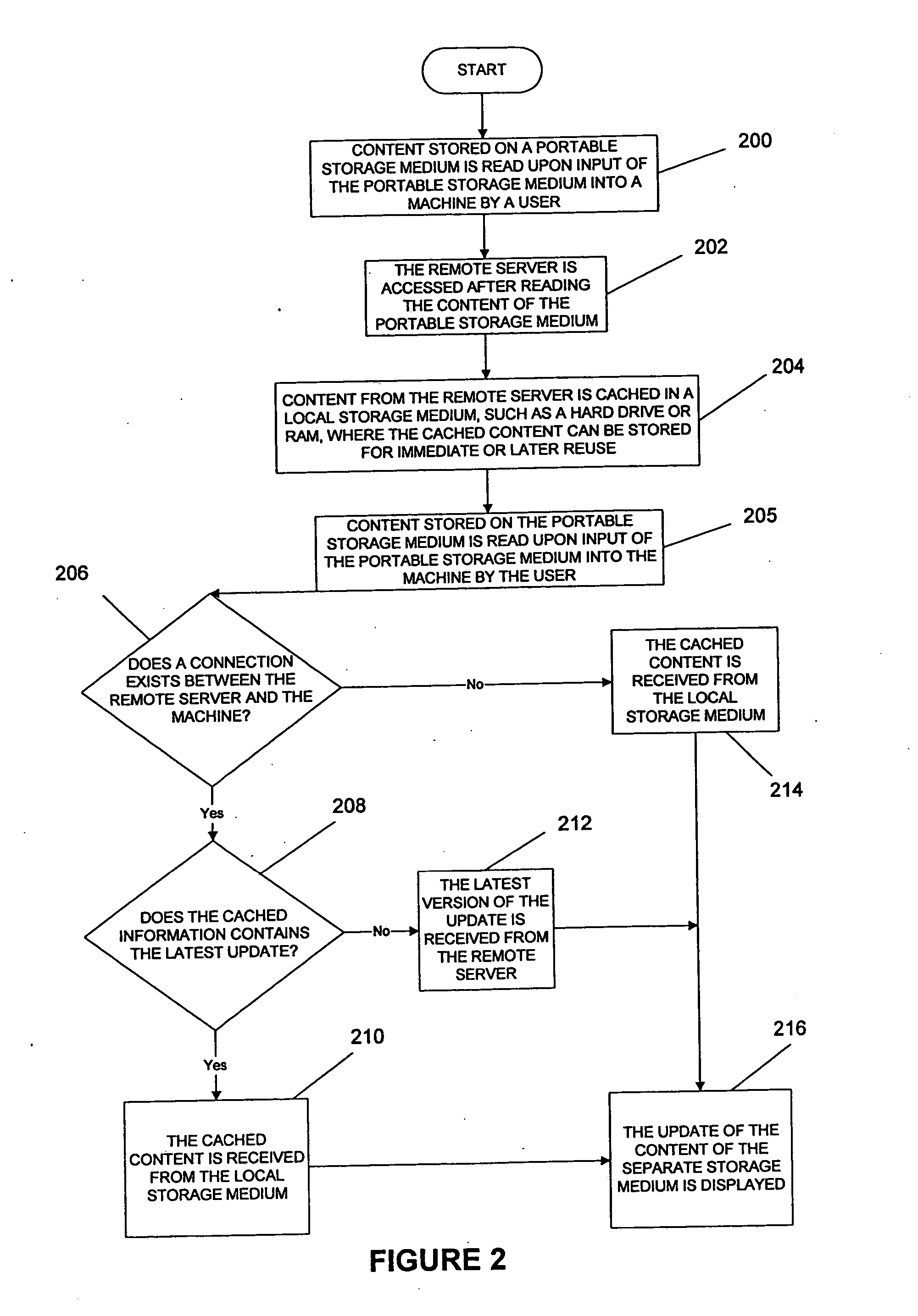
Controlling playback of content stored on a portable storage medium
InactiveUS20050044481A1Easy to cutExtended shelf lifeData processing applicationsElectronic editing digitised analogue information signalsComputer networkLocal machine
Owner:ROVI TECH CORP
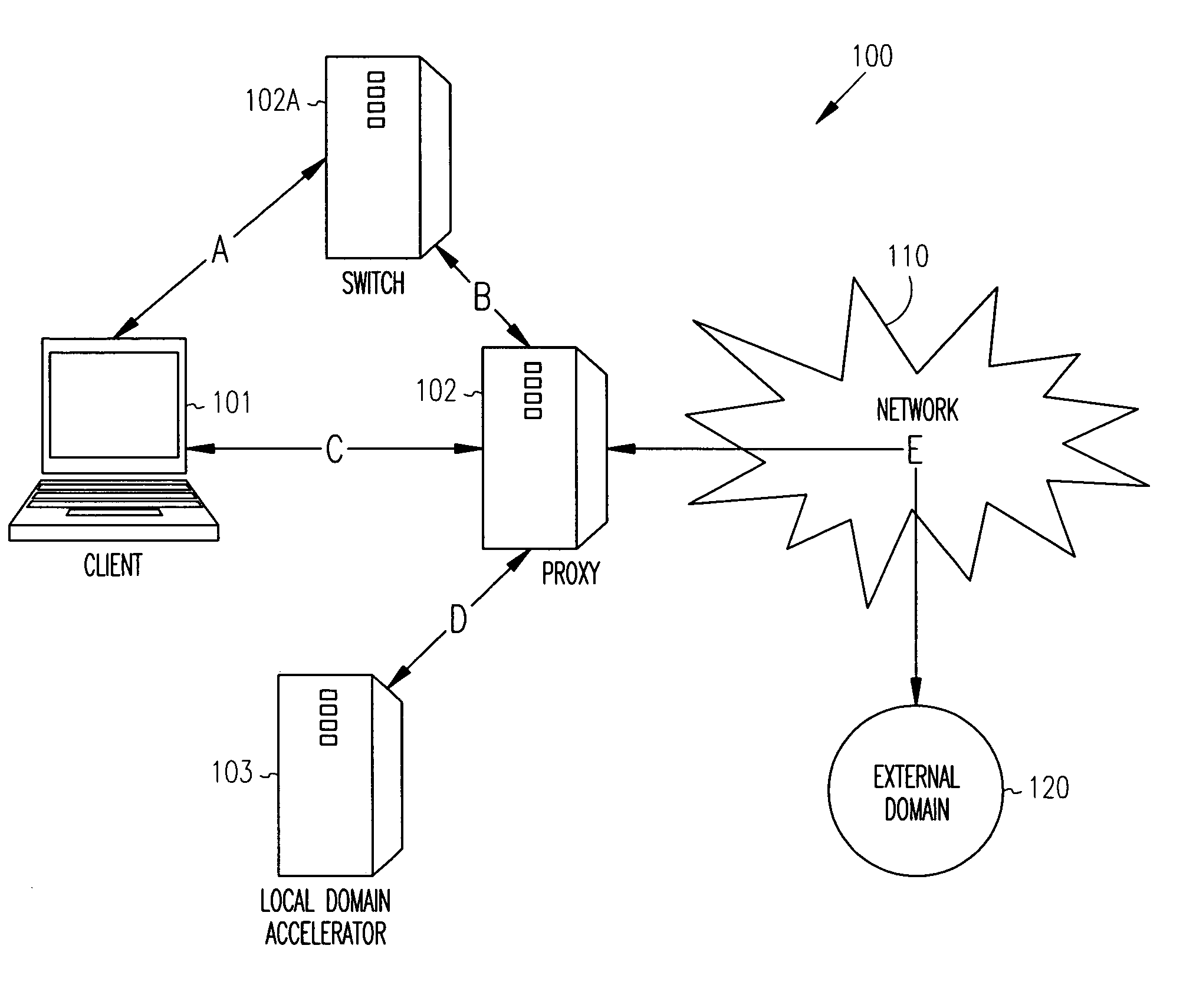
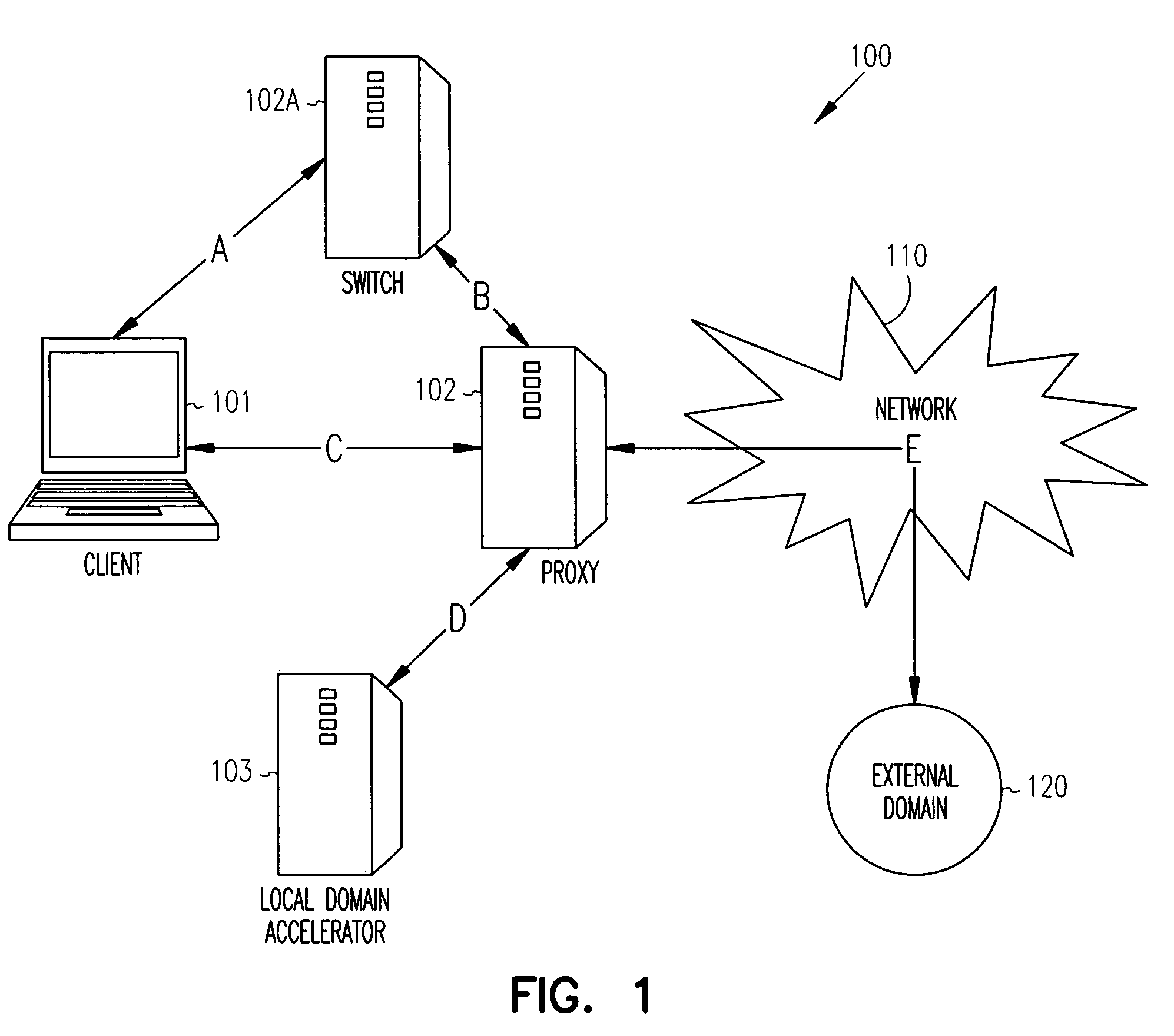
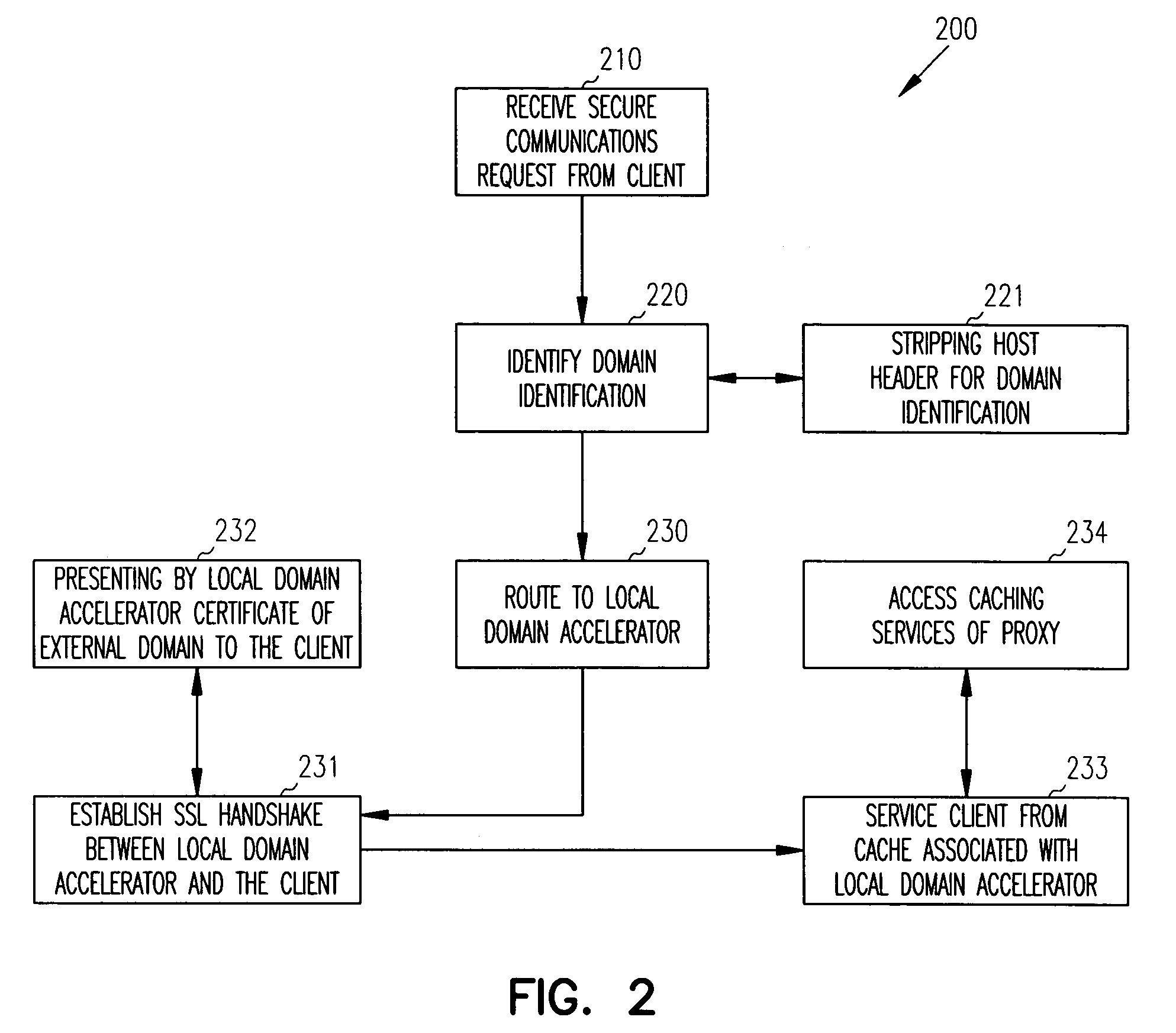
Techniques for securely accelerating external domains locally
InactiveUS7904951B1Multiple digital computer combinationsProgram controlSecure communicationInternet privacy
Owner:RPX CORP
Remote access communication architecture apparatus and method
ActiveUS7895334B1Connection managementMultiprogramming arrangementsCellular telephoneComputer science
Owner:SYNCHRONOSS TECH
Method for processing a document object model (DOM) tree using a tagbean
InactiveUS6981211B1Easy to replaceDigital computer detailsSemi-structured data mapping/conversionComponent Object ModelTheoretical computer science
Owner:IBM CORP
Systems and methods for generating and using trade areas
Methods and systems are provided for determining and using market areas associated with one or more branches of a business. Market areas are determined using a combination of deterministic and probabilistic techniques. Distances are calculated between customers and associated branches and a convex hull formed containing the closest 60%. A block and a tightened block is formed of dissemination areas contained within the convex hull. Where blocks are shared between branches, dissemination areas are weighted according to the portion of customers associated with each branch.
Owner:THE TORONTO DOMINION BANK
Computer system management program, system and method
InactiveUS20050138285A1Master quicklyInput/output to record carriersError detection/correctionSystems managementComputerized system
Owner:HITACHI LTD
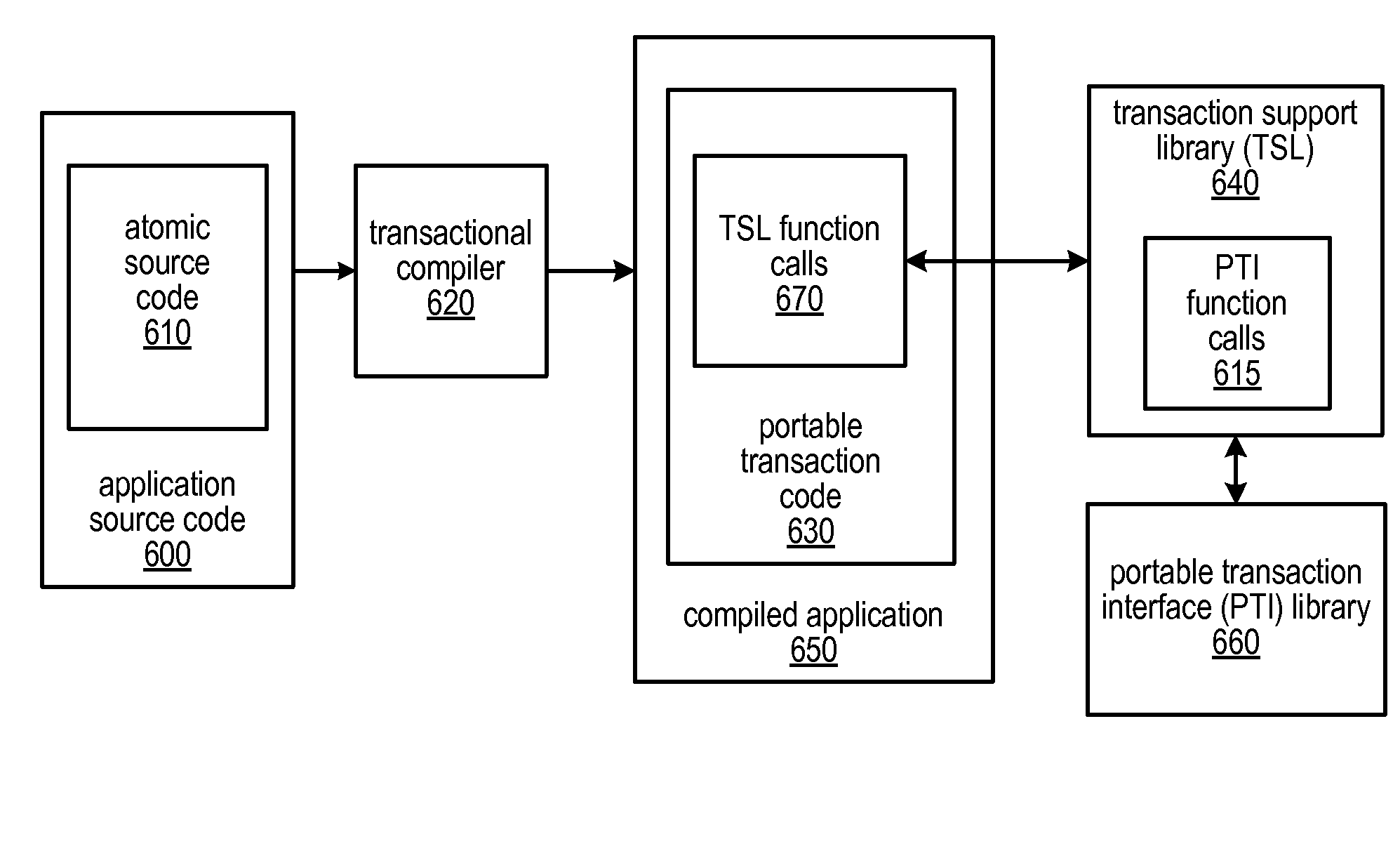
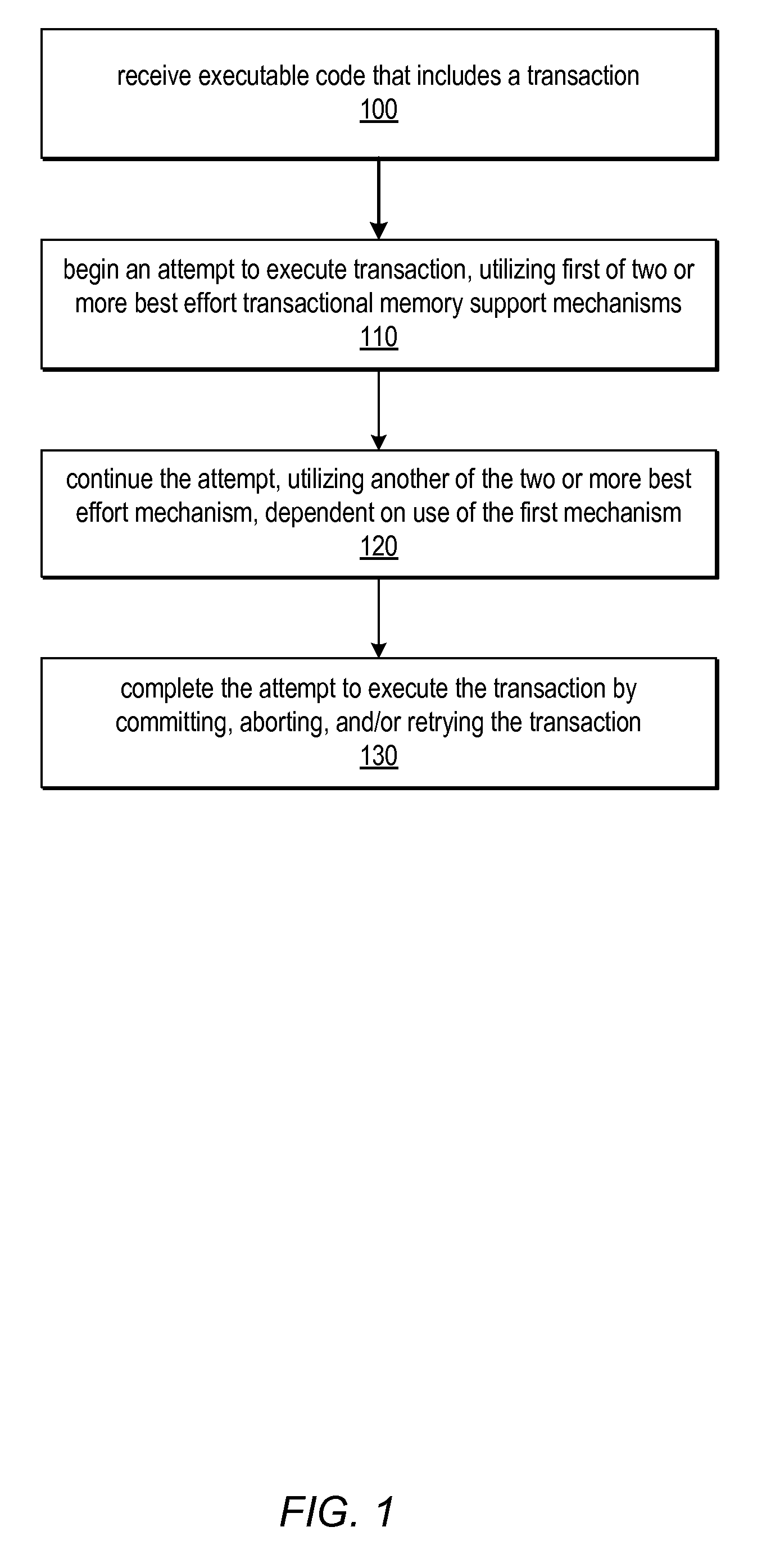
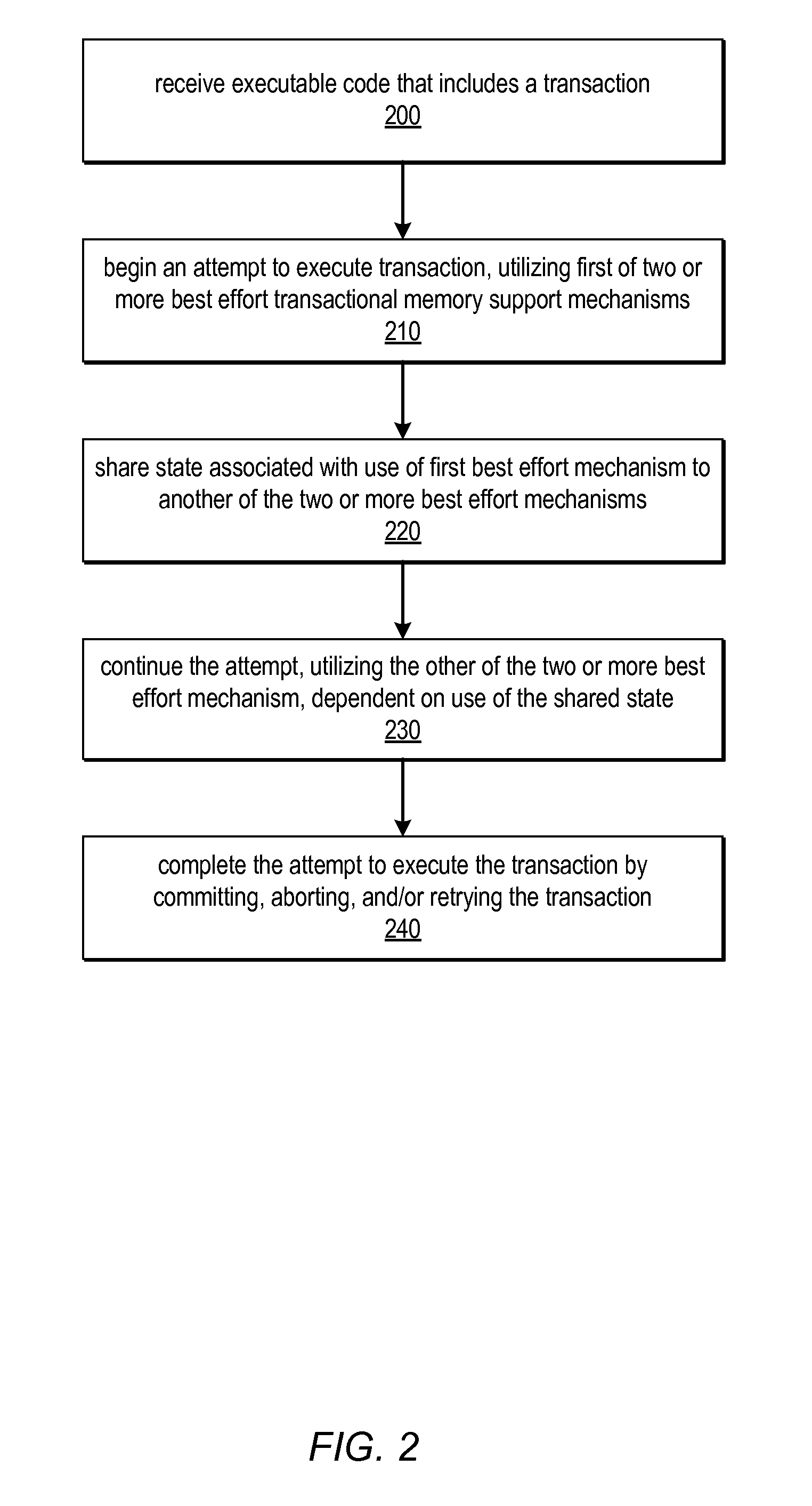
System and Method for Utilizing Available Best Effort Hardware Mechanisms for Supporting Transactional Memory
ActiveUS20090282386A1Reduce difficultyReduce overheadMemory systemsSpecific program execution arrangementsTransactional memoryApplication software
Systems and methods for managing divergence of best effort transactional support mechanisms in various transactional memory implementations using a portable transaction interface are described. This interface may be implemented by various combinations of best effort hardware features, including none at all. Because the features offered by this interface may be best effort, a default (e.g., software) implementation may always be possible without the need for special hardware support. Software may be written to the interface, and may be executable on a variety of platforms, taking advantage of best effort hardware features included on each one, while not depending on any particular mechanism. Multiple implementations of each operation defined by the interface may be included in one or more portable transaction interface libraries. Systems and / or application software may be written as platform-independent and / or portable, and may call functions of these libraries to implement the operations for a targeted execution environment.
Owner:ORACLE INT CORP
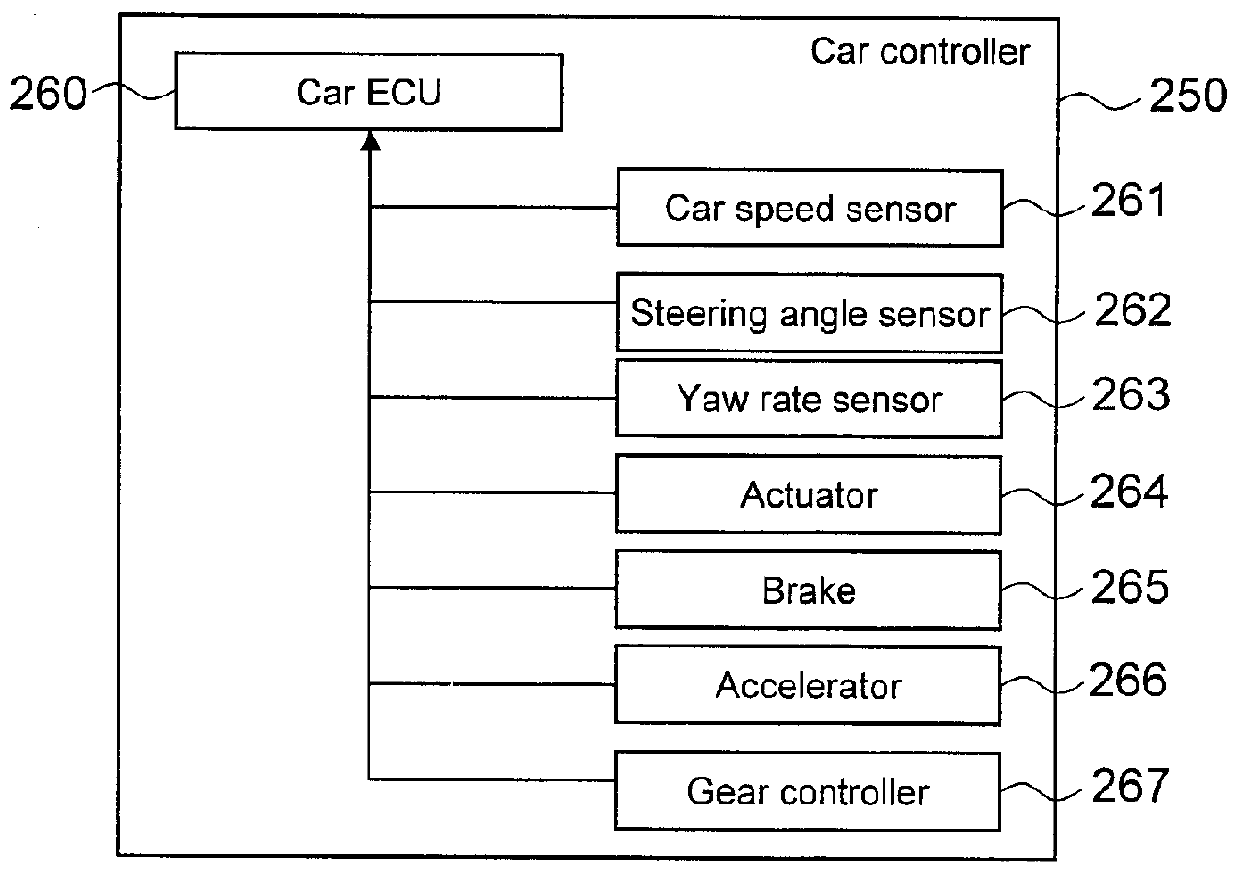
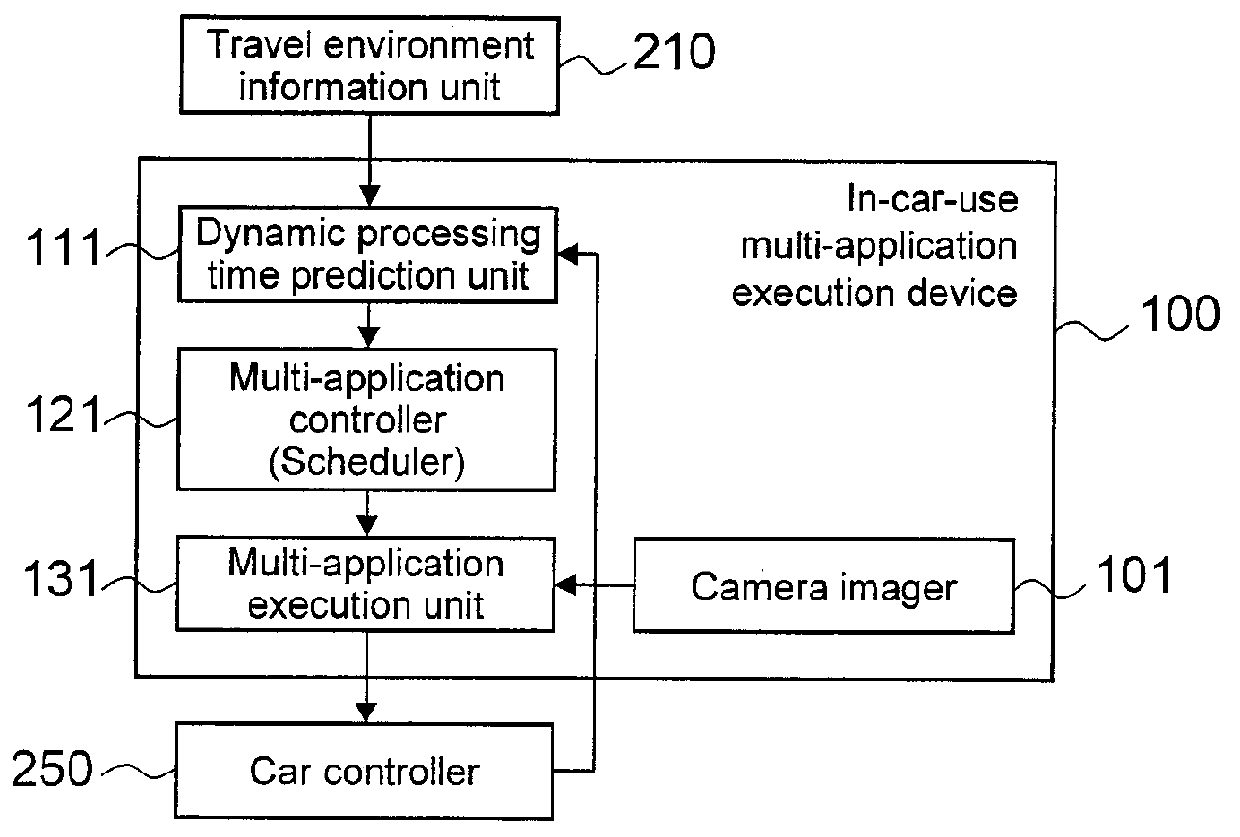
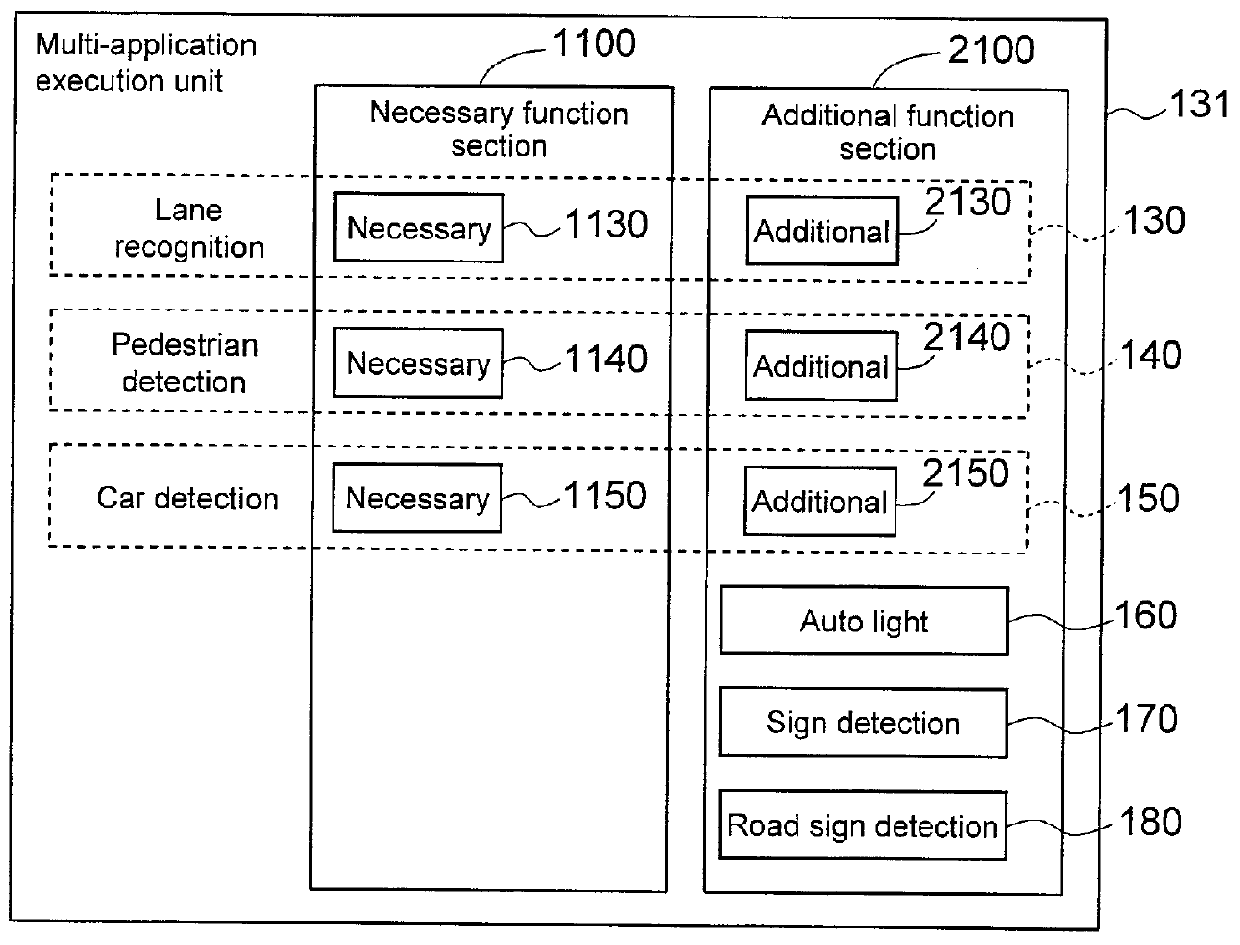
In-Car-Use Multi-Application Execution Device
ActiveUS20120216208A1Limited processing capabilitiesEnsure safetyProgram initiation/switchingRoad vehicles traffic controlApplication softwareOperating system
Owner:HITACHI ASTEMO LTD
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap