Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
19 results about "Network security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: it secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password.
Method and apparatus for providing network security using security labeling
ActiveUS20050097357A1Reduces potential leakageImprove network securityDigital data processing detailsMultiple digital computer combinationsNetwork security policySecurity level
A method and apparatus for providing network security using security labeling is disclosed. The method includes comparing first security level information and second security level information, and indicating processing to be performed on the packet based on the comparing. The first security level information is stored in a security label of a packet received at a network node, while the second security level information is stored at the network node.
Owner:CISCO TECH INC
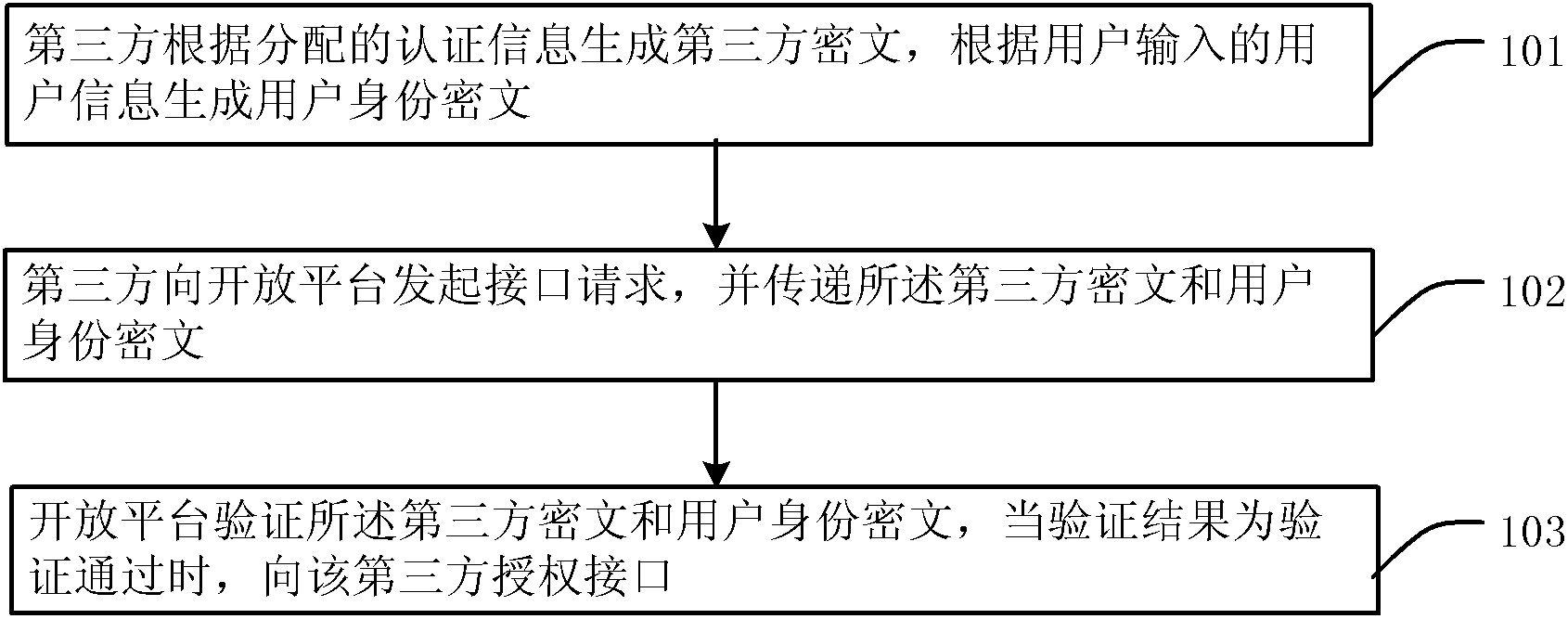
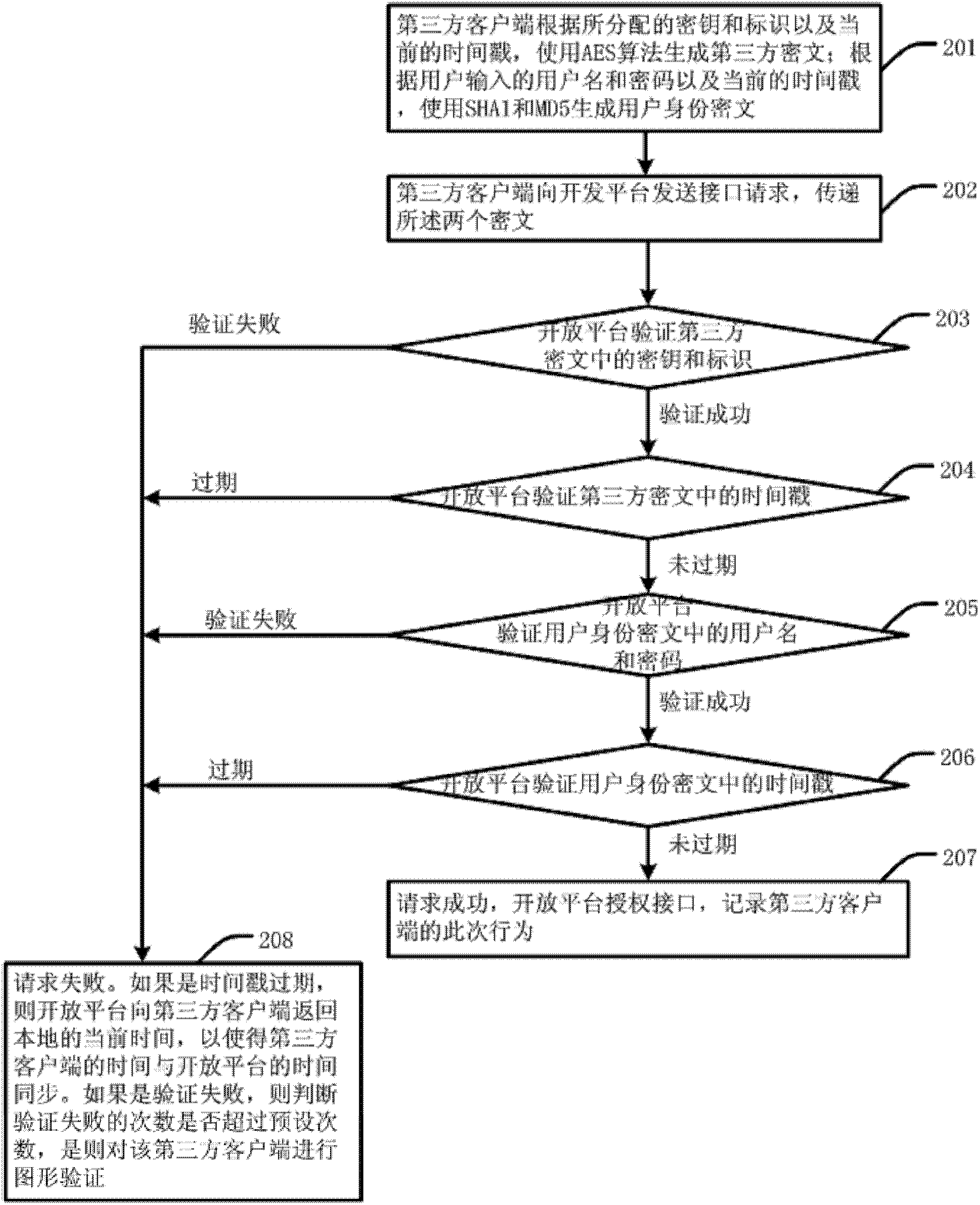
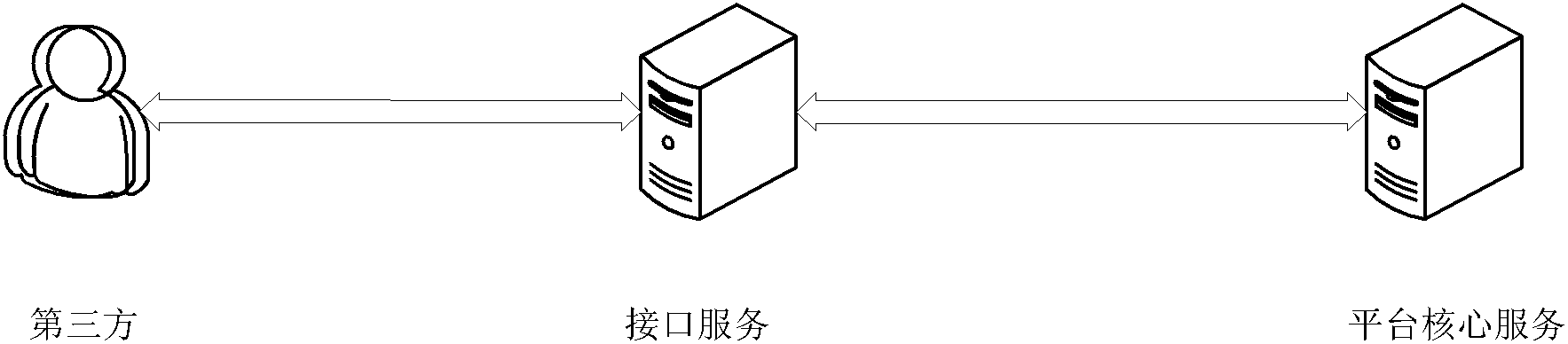
Method and system for third party application interface authorization
Owner:BEIJING FEINNO COMM TECH
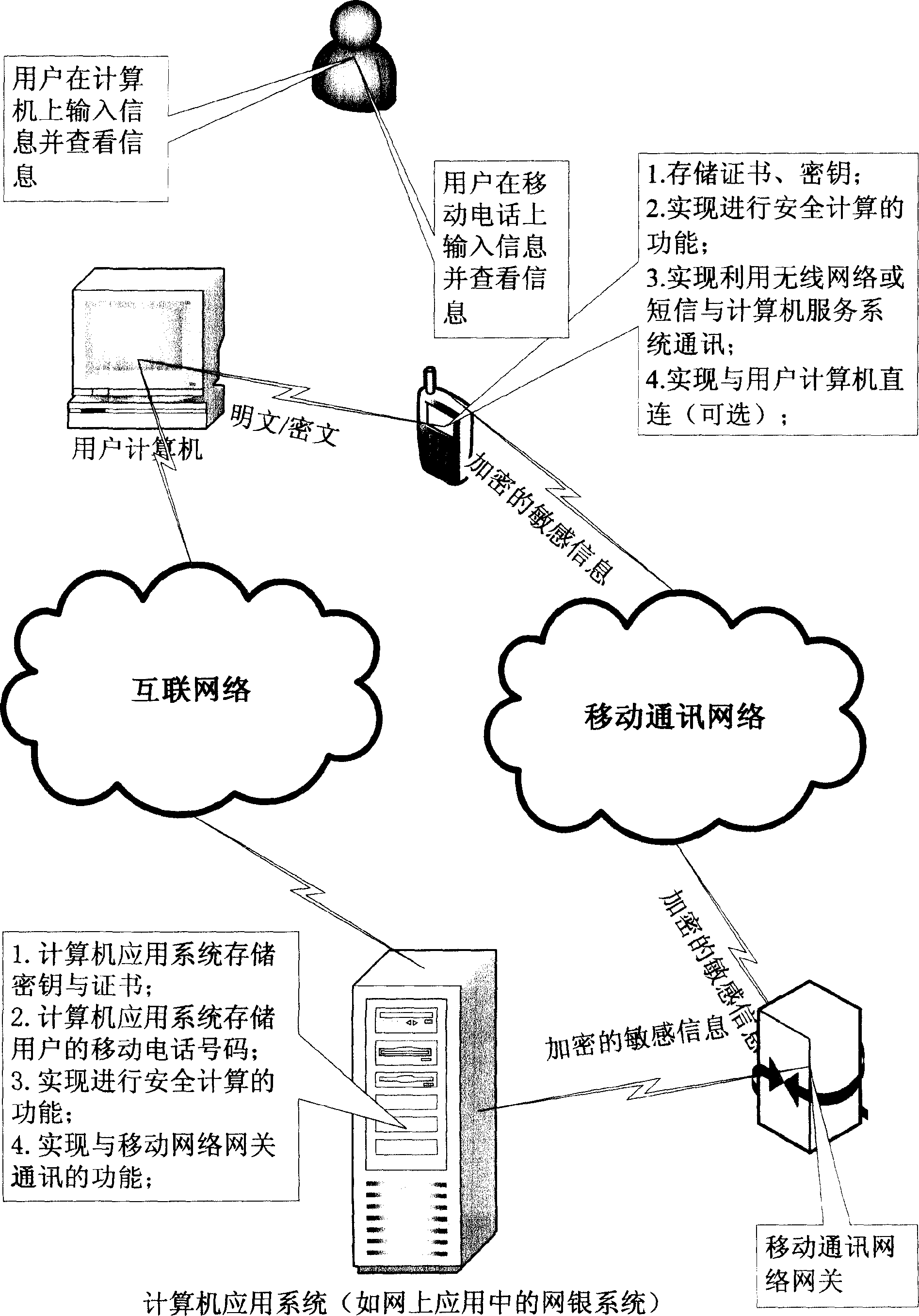
Technology for improving security of accessing computer application system by mobile phone
InactiveCN1838141APrevent leakageGuaranteed isolationDigital data authenticationPasswordPersonal computer
Owner:刘亚威
Communication method, device and system
ActiveCN109600339AAvoid the problem of large delayNetwork traffic/resource managementTransmissionQuality of serviceSession management
The invention relates to the technical field of wireless communication, in particular to a communication method, a communication system and communication equipment, which are used for realizing safetyprotection based on quality of service (QoS) flow so as to meet the safety requirements of different services and improve the flexibility of network safety. The method comprises the following steps that session management equipment receives a request, wherein the request is used for requesting session establishment or session modification; the session management equipment obtains a target security policy of the QoS flow according to the request; and the session management equipment sends indication information to a mobility management device, wherein the indication information is used for indicating a target security policy of the QoS flow.
Owner:HUAWEI TECH CO LTD
System and method for transferring medical data
PendingCN112768022AIncreased protectionGuaranteed Voluntary LicensingMedical data miningMedical automated diagnosisData streamData management
The invention discloses a system and a method for transferring medical data, and belongs to the technical field of medical data management. The system is provided and comprises a data acquisition module, a data processing module, an auditing module, a verification module and a security module, and all the modules are electrically connected in sequence. The method for transferring medical data is provided and comprises the following steps that S1, a medical institution calls related medical data according to the content of an application form; S2, the related medical data in the step S1 are classified and standardization and desensitization processing are performed; S3, the data in the step S2 are audited to ensure that the data are consistent with the content of the application form; S4, the patient and the medical institution authorize related medical data; and S5, security protection is performed on the internal and network security of the medical institution to ensure data transmission security. According to the method and the system, privacy, security and standardization of medical data transferring are ensured, and the value of the medical data is improved.
Owner:HANGZHOU ZHUOJIAN INFORMATION TECH CO LTD
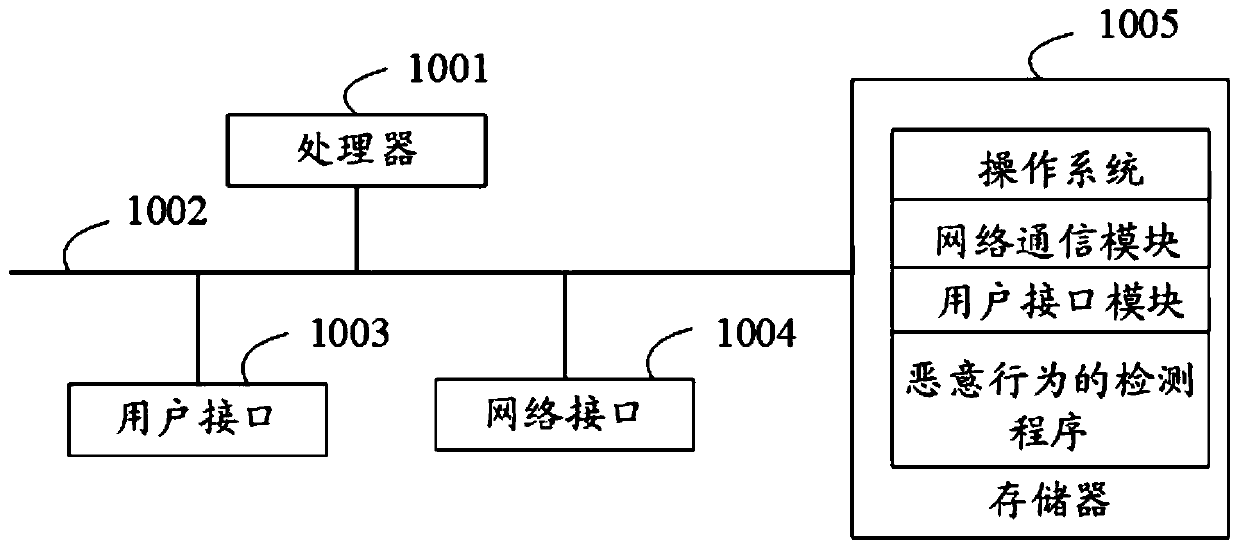
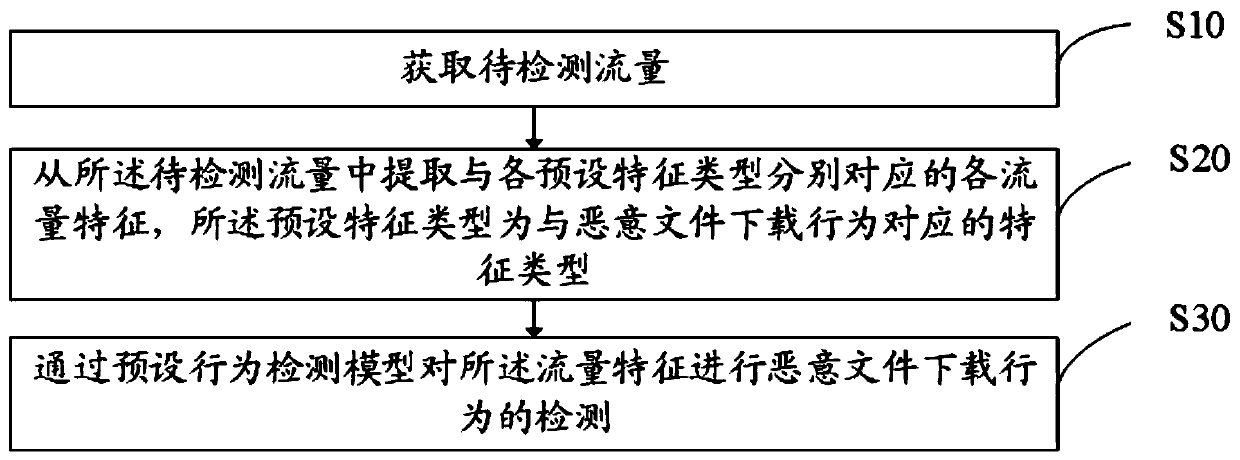
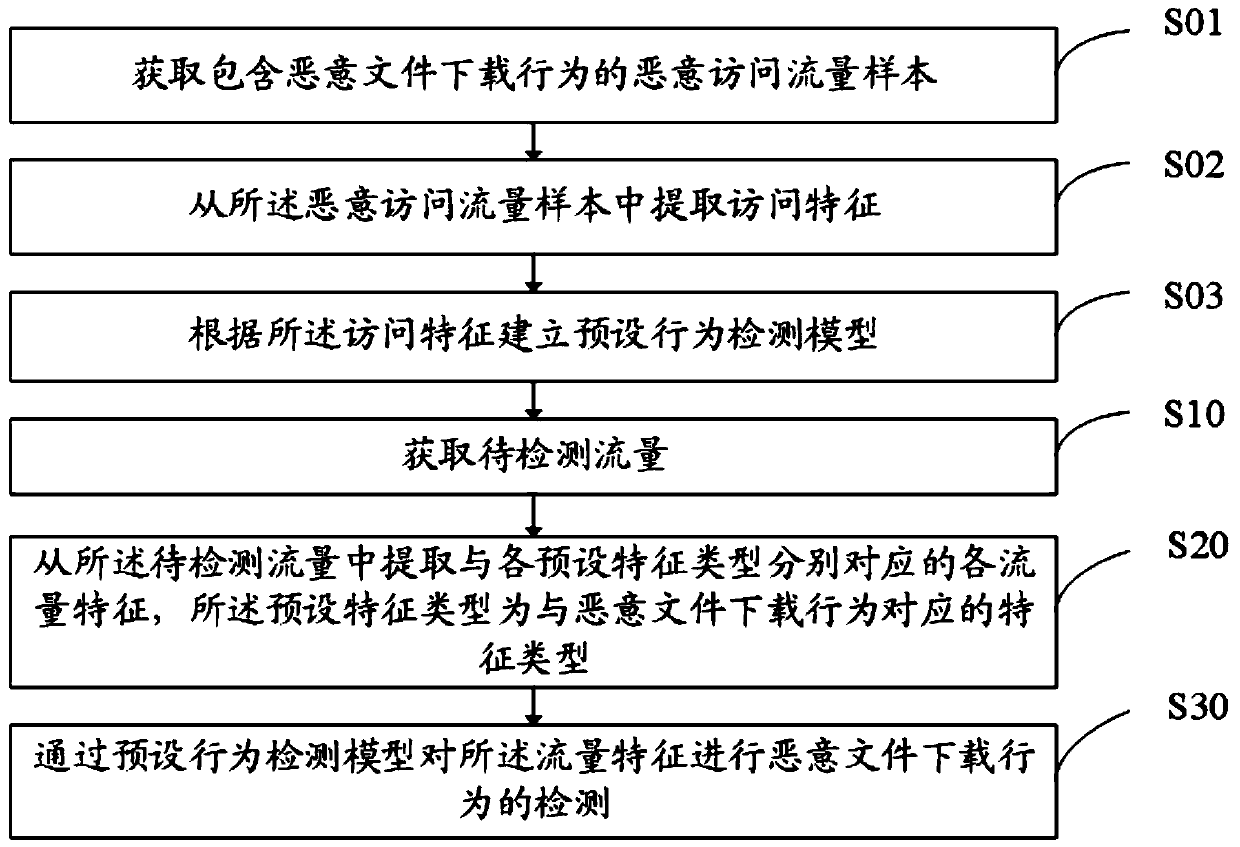
Malicious behavior detection method, user equipment, storage medium and device
Owner:SANGFOR TECH INC
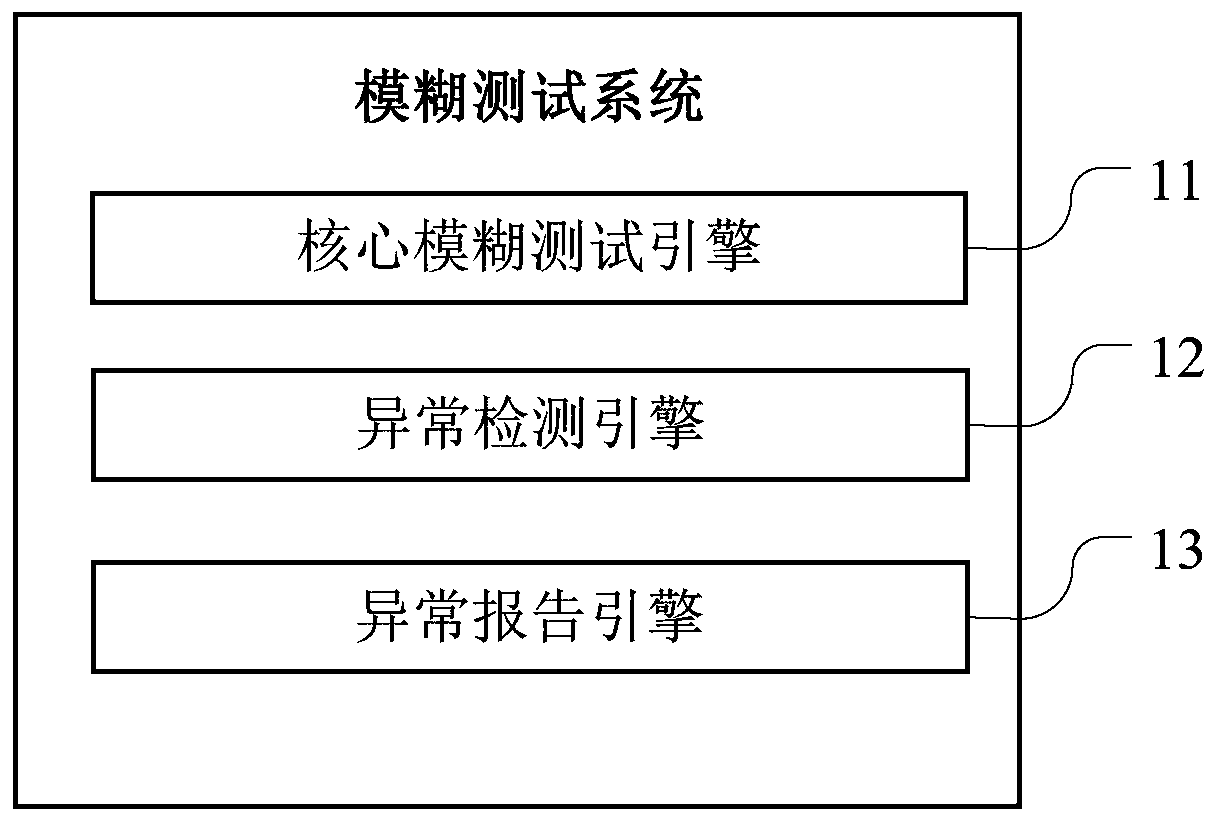
Fuzzy test system and terminal equipment
Owner:SECZONE TECH CO LTD +1
Picture sharing method and system
ActiveCN109525559AEnsure safetyEnsure the efficiency of screen transmissionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareNetwork code
The invention discloses a picture sharing method and system. The picture sharing method comprises the following steps: a master device performs handshake with a slave device when receiving a picture sharing request initiated by the slave device; when the master device performs handshake with the slave device successfully, the master device performs network coding on a picture signal to be shared,outputs a TS bare stream signal to the slave device, and plays the picture to be shared; and the slave device receives and decodes the TS bare stream signal, and synchronously displays the current picture to be shared. Thus, the picture information of the master device can be displayed synchronously on other slave devices without delay and jamming; and a private protocol is used in network transmission, therefore, network security and picture transfer efficiency are ensured.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Real-time mobile game long link processing method and device
ActiveCN109286665AOrderly interactionComplete interactionData switching networksComputer terminalNetwork security
The embodiment of the invention provides a real-time mobile game long link processing method and device. The method comprises the steps of receiving a current game service request sent by a mobile terminal; obtaining the corresponding current service ID according to the current game service request; matching the current service ID with service ID in a service response queue; when the current service ID is not in the service response queue and there is no spacing service ID between the current service ID and the last service ID in the service response queue, matching the current service ID withservice ID in a delayed request list; when there is no spacing service ID between the current service ID and the last service ID in the delayed request list, generating service response signals to the mobile terminal in sequence according to the service ID in the delayed request list, and storing the service ID in the delayed request list into the service response queue. The real-time mobile gamelong link processing method realizes ordered and complete interaction of data, establishes reliable long link communication and guarantees the network security.
Owner:DPSTORM
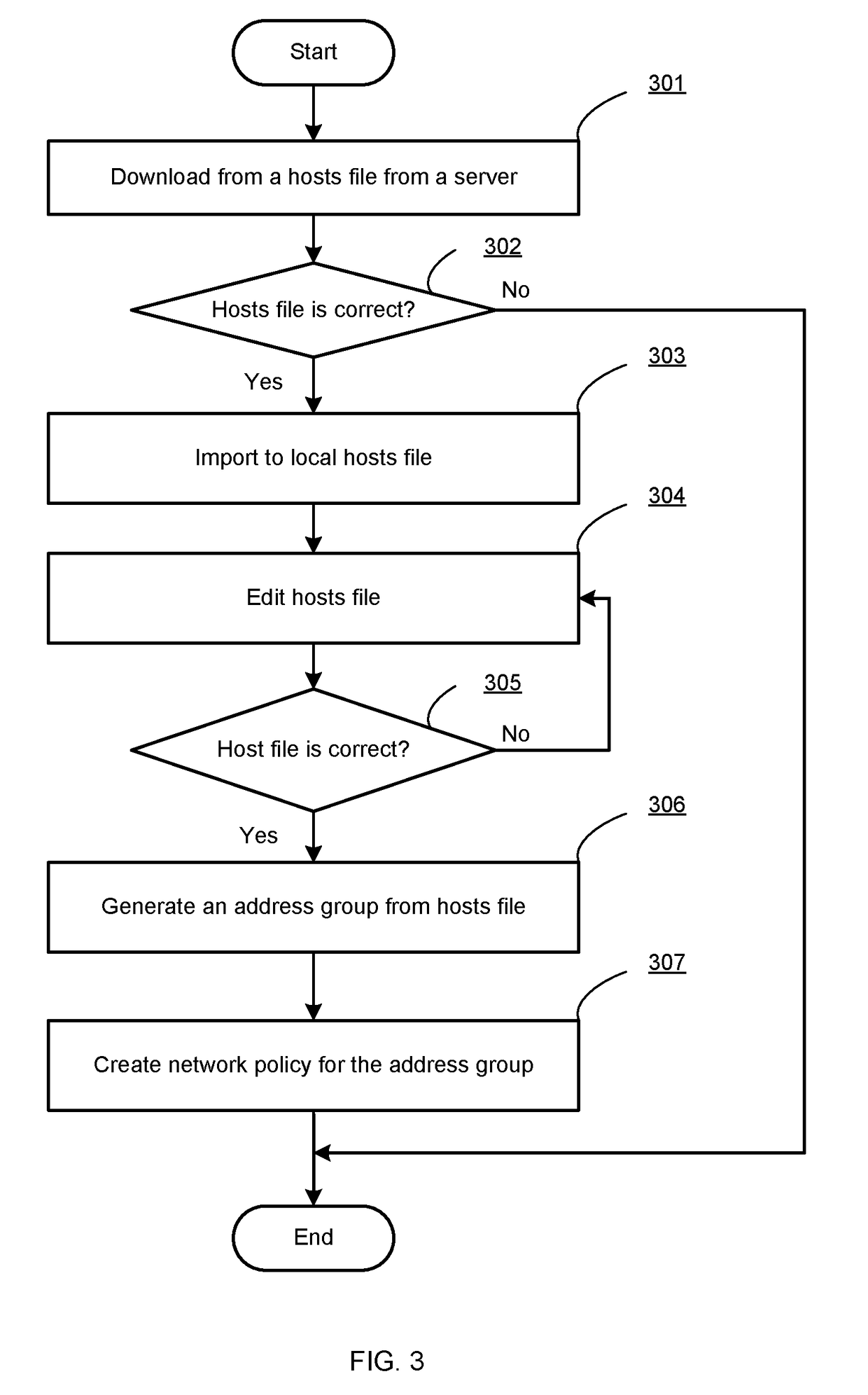
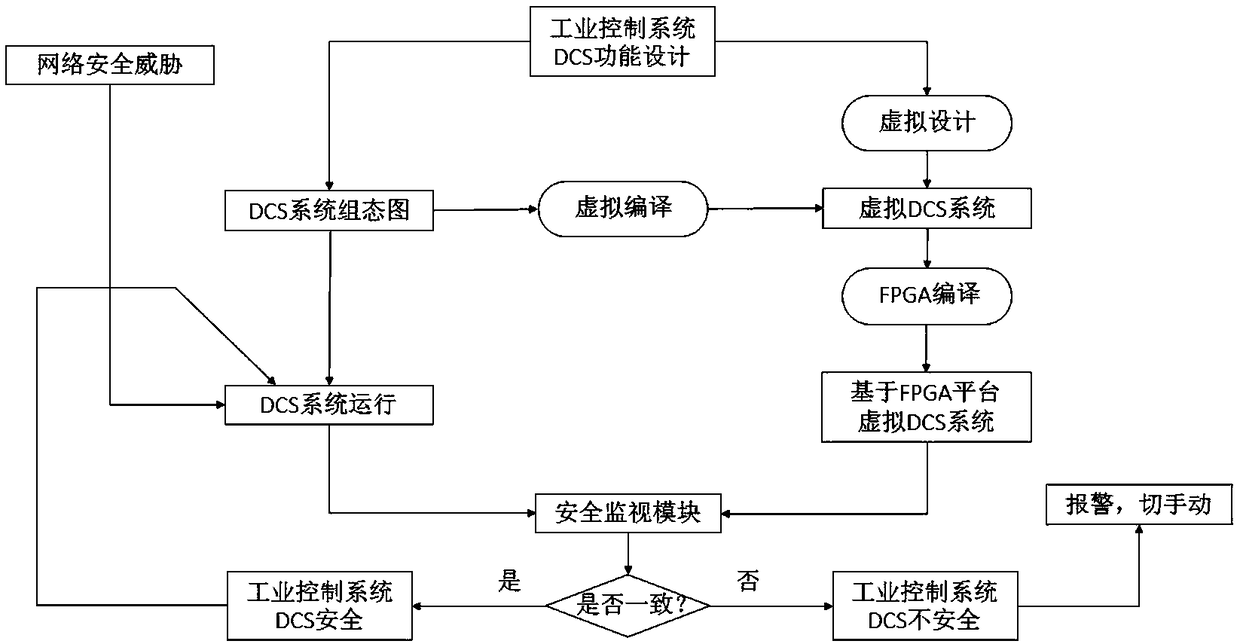
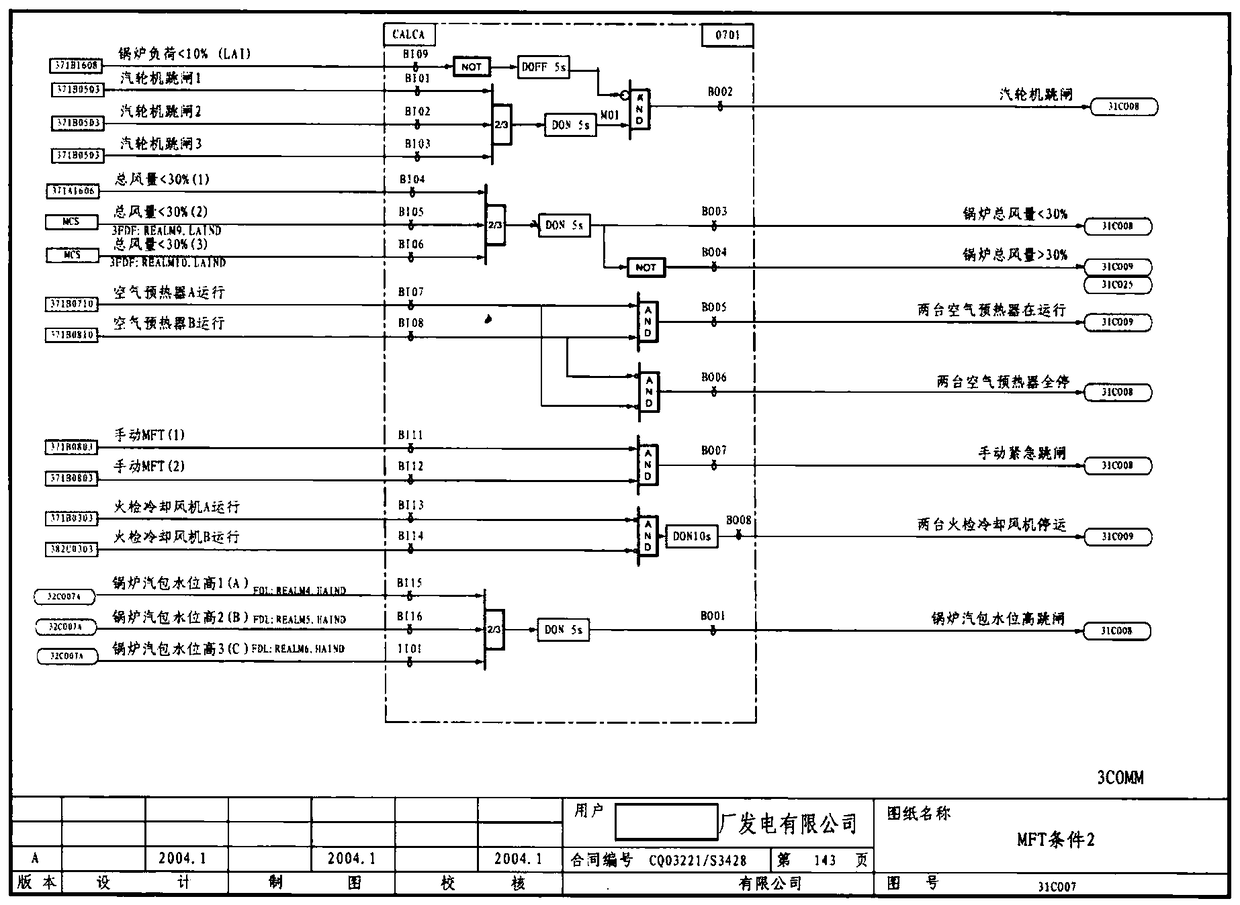
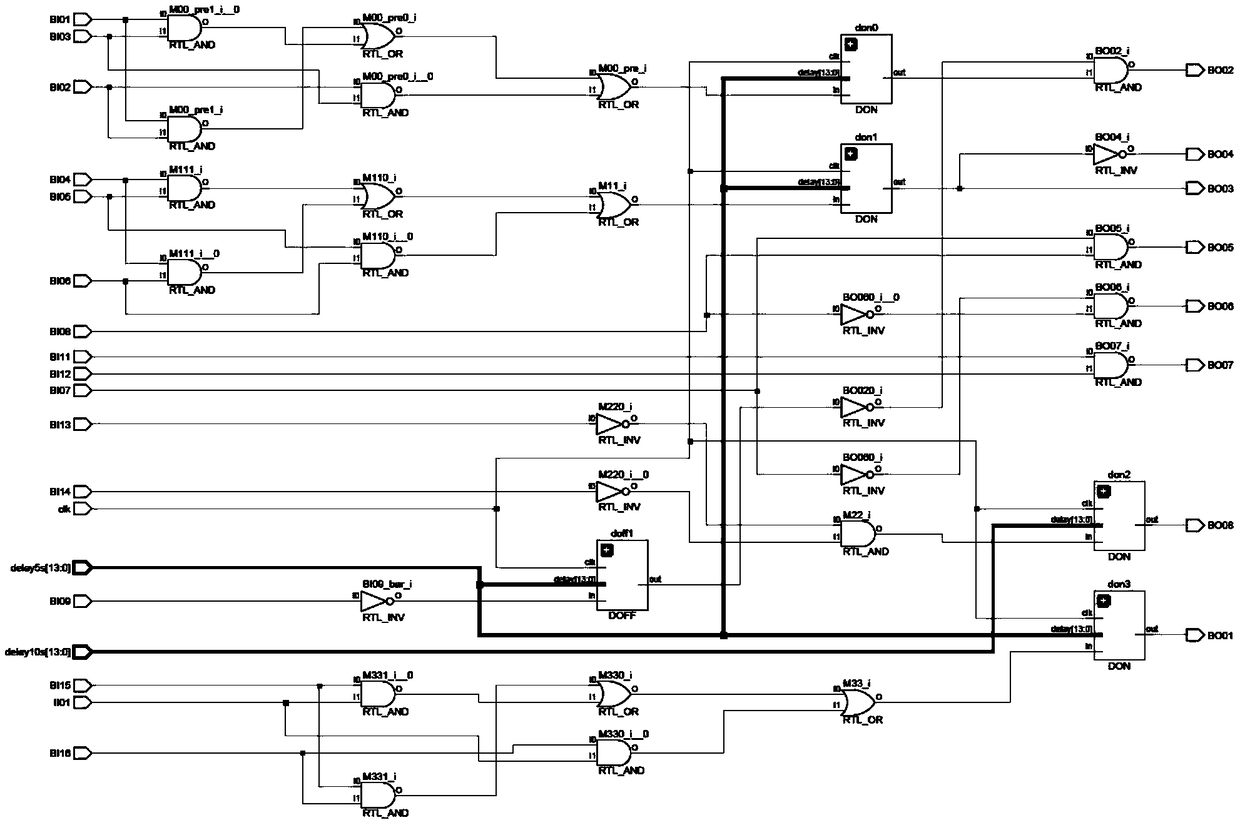
Industrial control system information security implementation method based on FPGA virtual DCS
ActiveCN109407638ARealize functionNetwork Security Monitoring and AssuranceTotal factory controlProgramme total factory controlChipsetFpga chip
Owner:核新云科技(南京)有限公司
Industrial control safety auditing system and method based on artificial intelligence
ActiveCN112437041AImprove securityMeet industry compliance audit requirementsTransmissionTotal factory controlInformation transmissionAttack
Owner:北京珞安科技有限责任公司
Remote access control list generation and data packet processing method for CM
ActiveCN105812352AEnsure safetyImprove processing efficiencyTransmissionComputer hardwareInterface layer
The invention relates to the technical field of communications and networks, and provides a remote access control list generation and data packet processing method for a CM, for configuring a CM at an interface layer. The method comprises the following steps: writing an ACL command and adding the ACL command into a TLV43 field of a CM configuration file; the CM downloading the CM configuration file from a TFTP server and analyzing the CM configuration file, and then storing the ACL command obtained through analysis in a queue buffer zone; and when a CM interface receives or sends a data packet, obtaining the ACL command in the queue buffer zone, matching the ACL command with header information of the data packet, and according to a matching result, processing the data packet. According to the technical scheme provided by the invention, the network security can be ensured, the processing efficiency of CM equipment for the data packet is improved, the network performance is improved, far-end flexible configuration of the CM equipment can also be realized, and the onsite maintenance cost of the CM equipment is decreased.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Railway network security risk visual analysis method and device
PendingCN114329583AAvoid risk of leakageRealize refined managementDigital data protectionPlatform integrity maintainanceInformatizationNetwork architecture
The invention provides a railway network security risk visual analysis method and device, and belongs to the technical field of railway network security. The prototype system of the railway informatization asset surveying and mapping platform adopts a service-oriented system architecture design under the constraint of a technology and industry standard specification system and the constraint of an information security system mechanism, and the overall architecture comprises an infrastructure layer, a data layer, a system support layer, an application layer and a presentation layer. The expansibility of the system is considered, and an extended network system structure of a data and service application system is realized. The railway network security risk visual analysis method comprises the following steps: positioning a railway network security risk visual analysis device; and acquiring and analyzing railway network security risk data by using the equipment main body, and classifying the railway network security risk data into primary risk data, intermediate risk data and advanced risk data. According to the method, the personnel with the corresponding level of authority can obtain the corresponding analysis information.
Owner:INST OF GEOGRAPHICAL SCI & NATURAL RESOURCE RES CAS +3
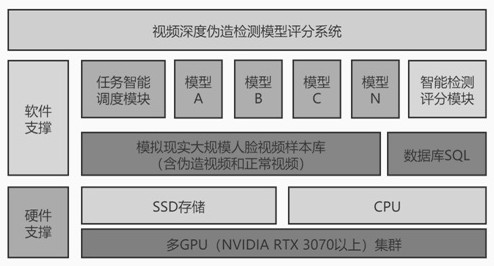
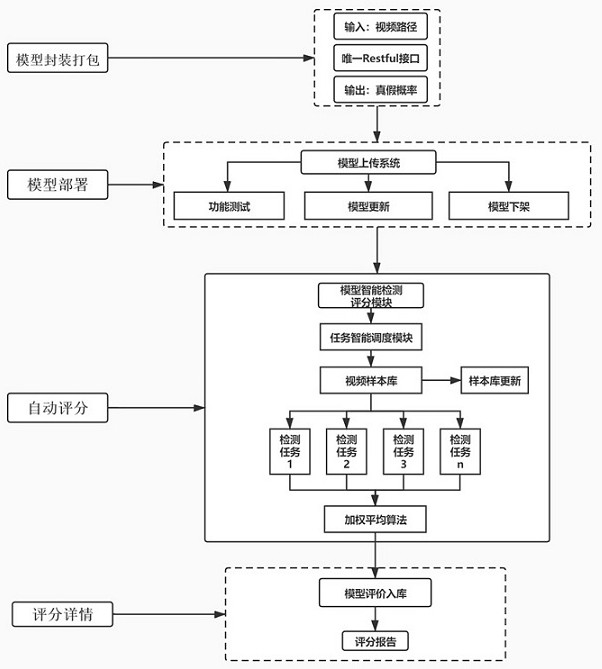
Model evaluation method based on deep counterfeit video detection and system
PendingCN113326400ABuilding and Strengthening Security Lines of DefenseImplement the buildDigital data information retrievalCharacter and pattern recognitionAlgorithmEngineering
Owner:HEFEI HIGH DIMENSIONAL DATA TECH CO LTD
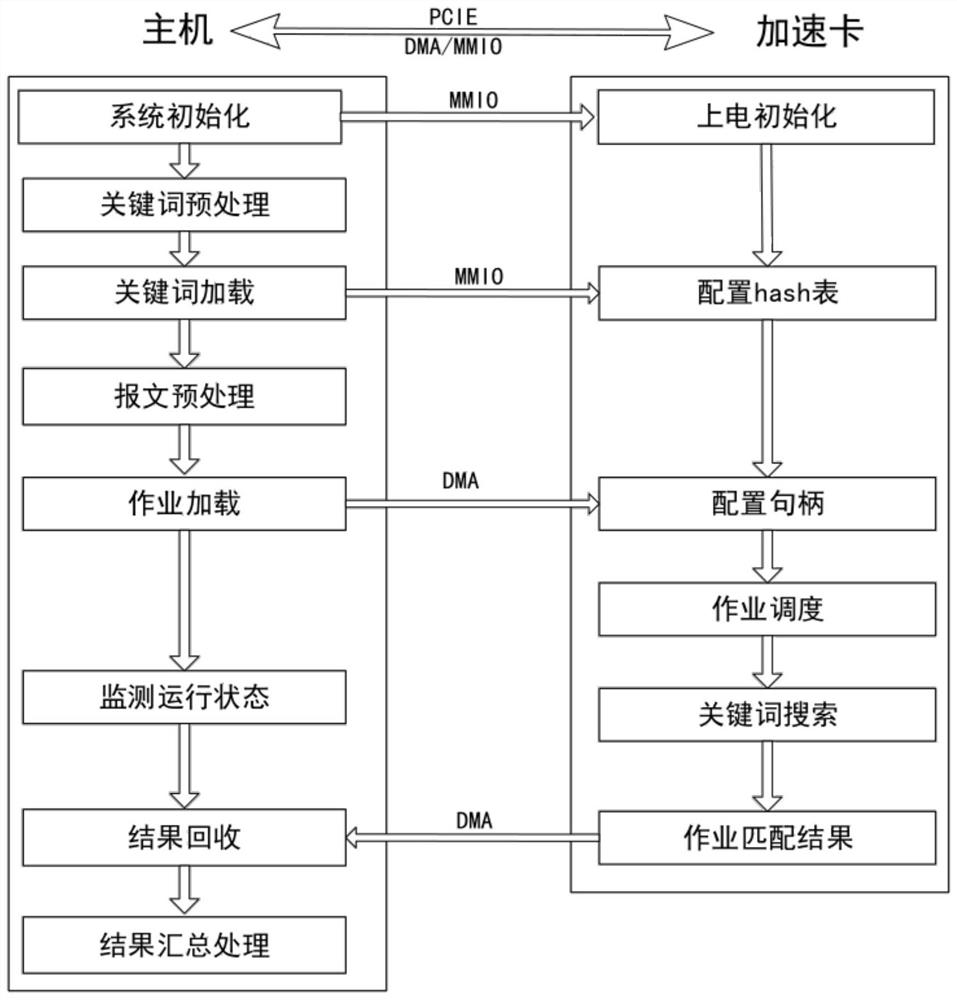
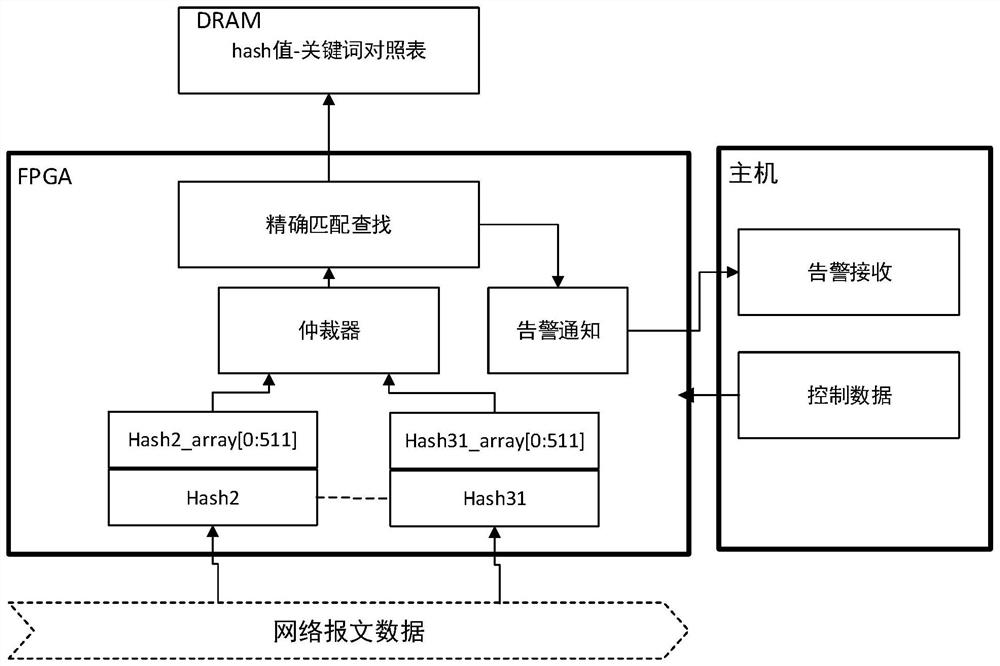
Efficient keyword filtering method for FPGA (Field Programmable Gate Array)
PendingCN114297368AFast searchReduce false alarm rateDigital data information retrievalSpecial data processing applicationsComputer architectureEngineering
Owner:无锡宏创盛安科技有限公司
Wifi processing method and display equipment
ActiveCN112040535AReduce the risk of not being able to connect properlyImprove experienceAssess restrictionPlatform integrity maintainanceWifi networkEngineering
Owner:QINGDAO HISENSE MEDIA NETWORKS CO LTD
Method and apparatus for network secure storage
ActiveUS20180032752A1Input/output to record carriersDigital data protectionService useNetwork security
This application discloses a method for network secure storage. The method includes: receiving a client request to create a window; creating a window in response to the client request; allocating a storage area for the window; allocating a rendering process to the window; and providing, to the rendering process, a storage service using the storage area.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A computer network security monitoring device
InactiveCN109167803AImprove securityProtection securityData switching detailsSingle chipSafety monitoring
Owner:君泰新能源汽车(大连)有限公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap