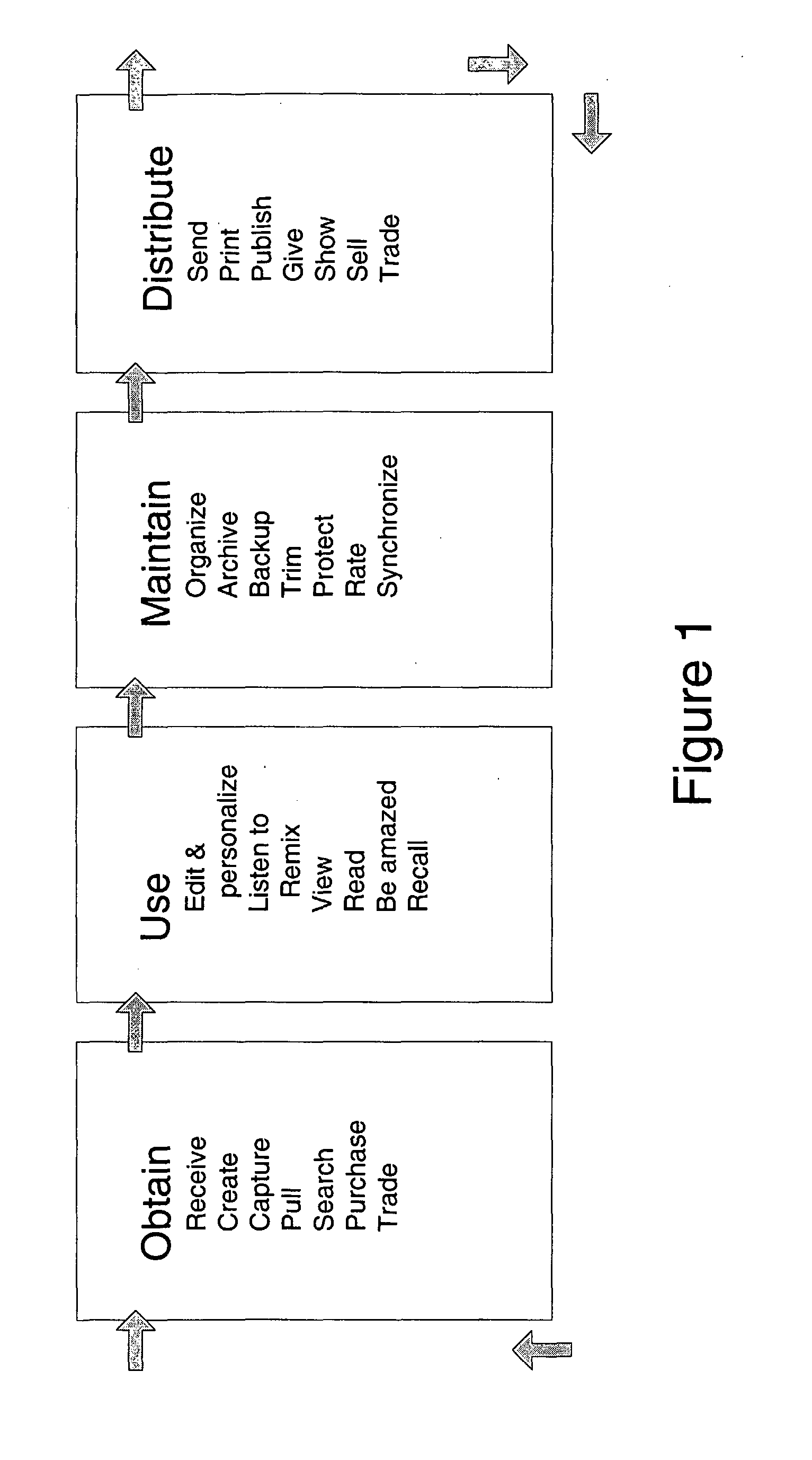
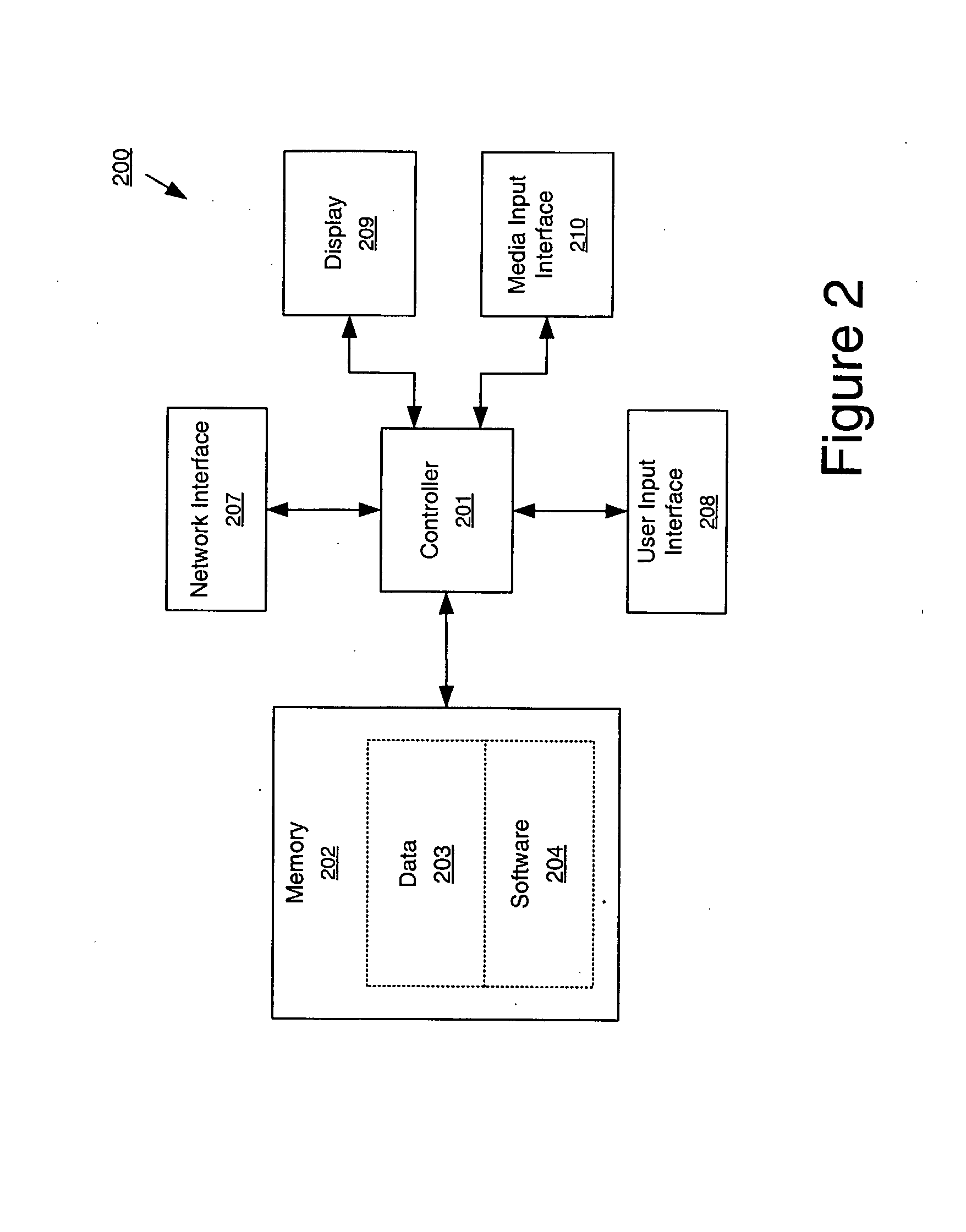
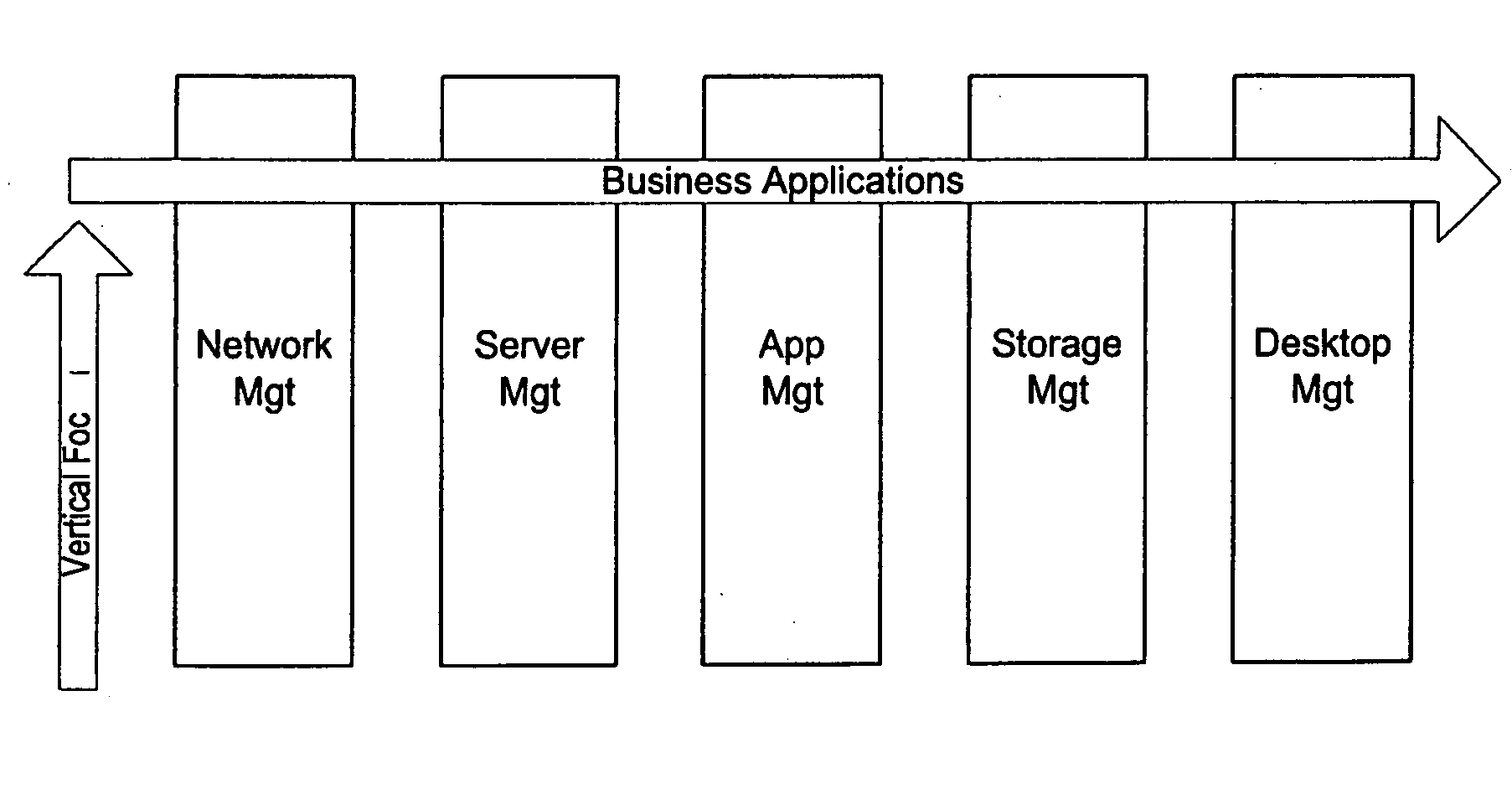
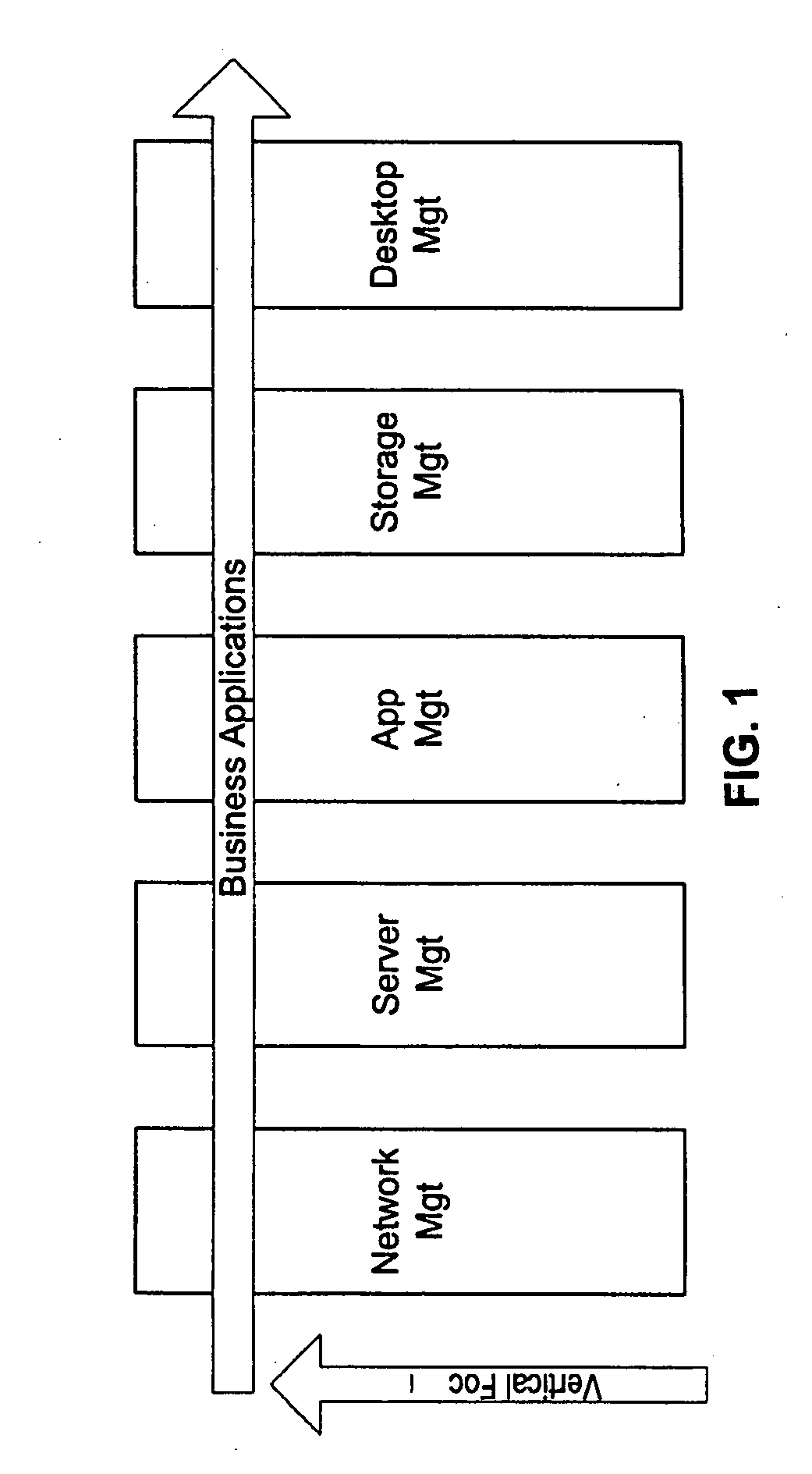
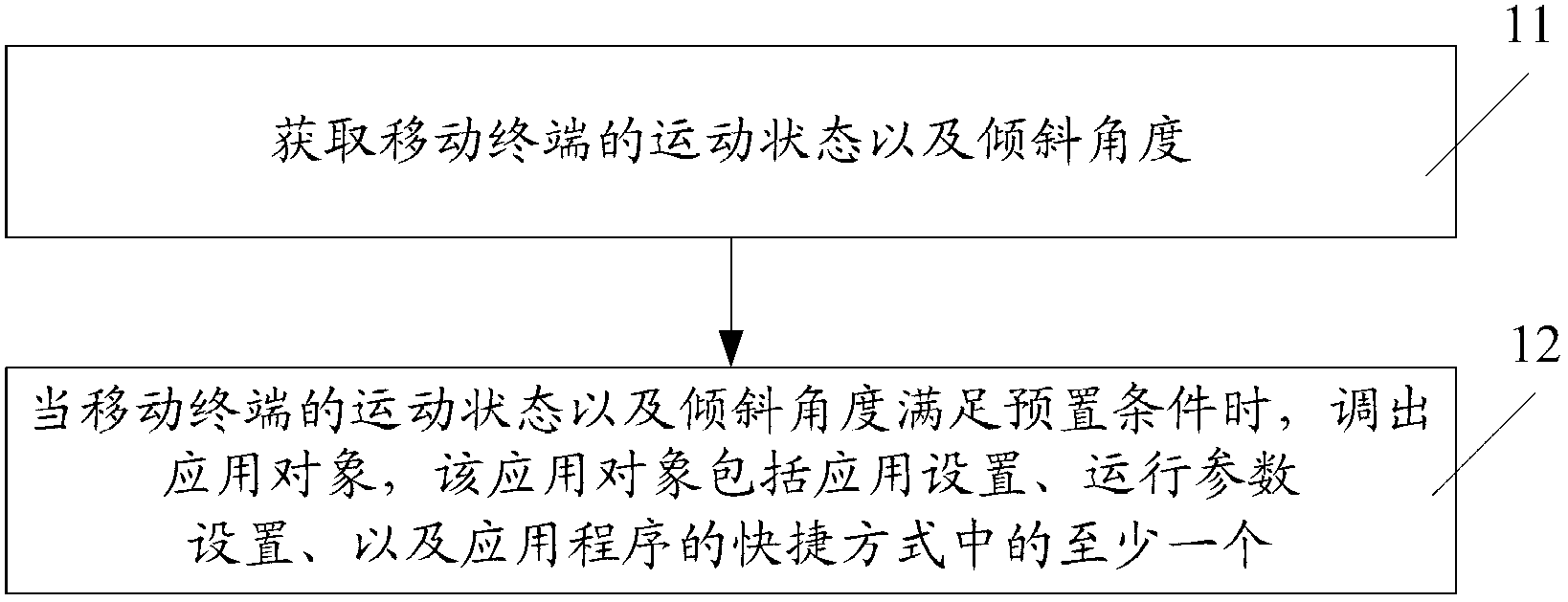
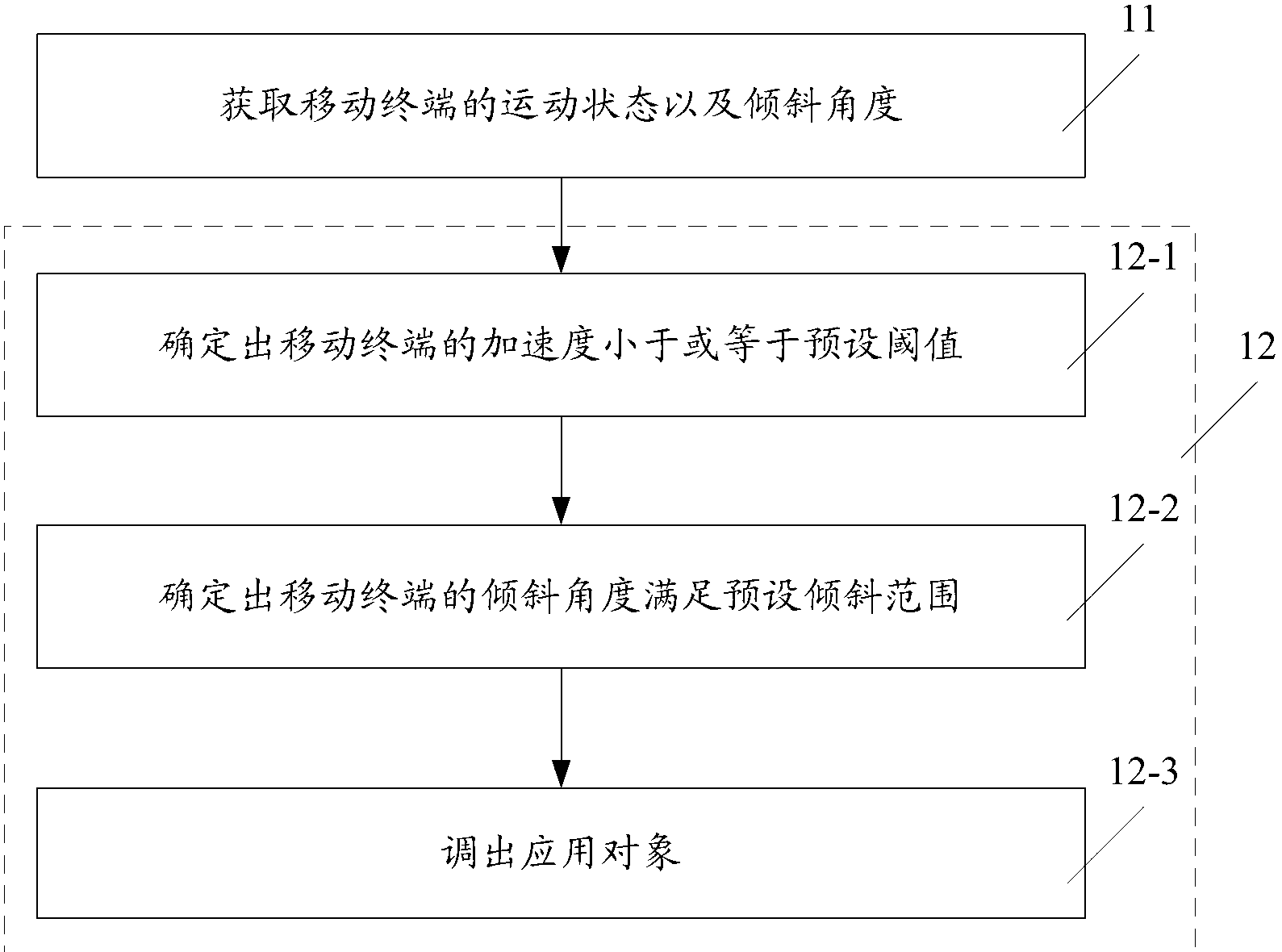
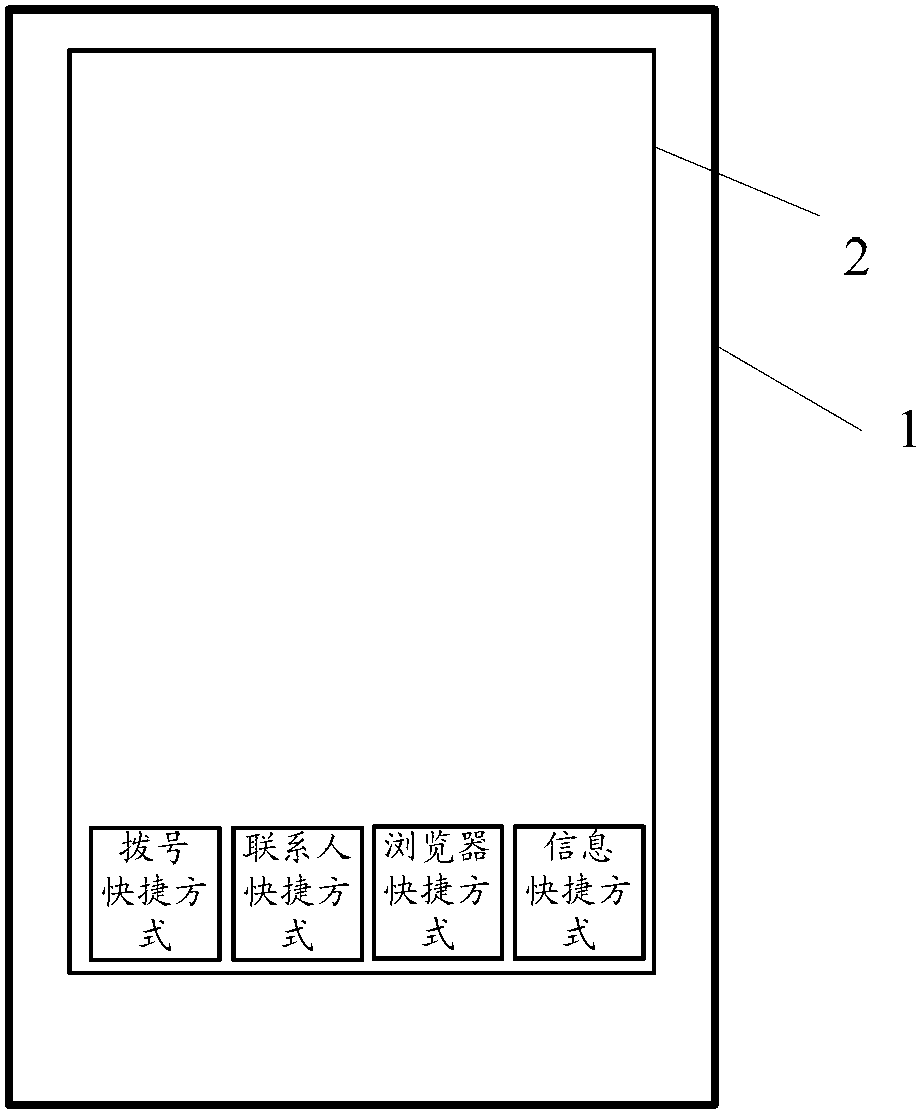
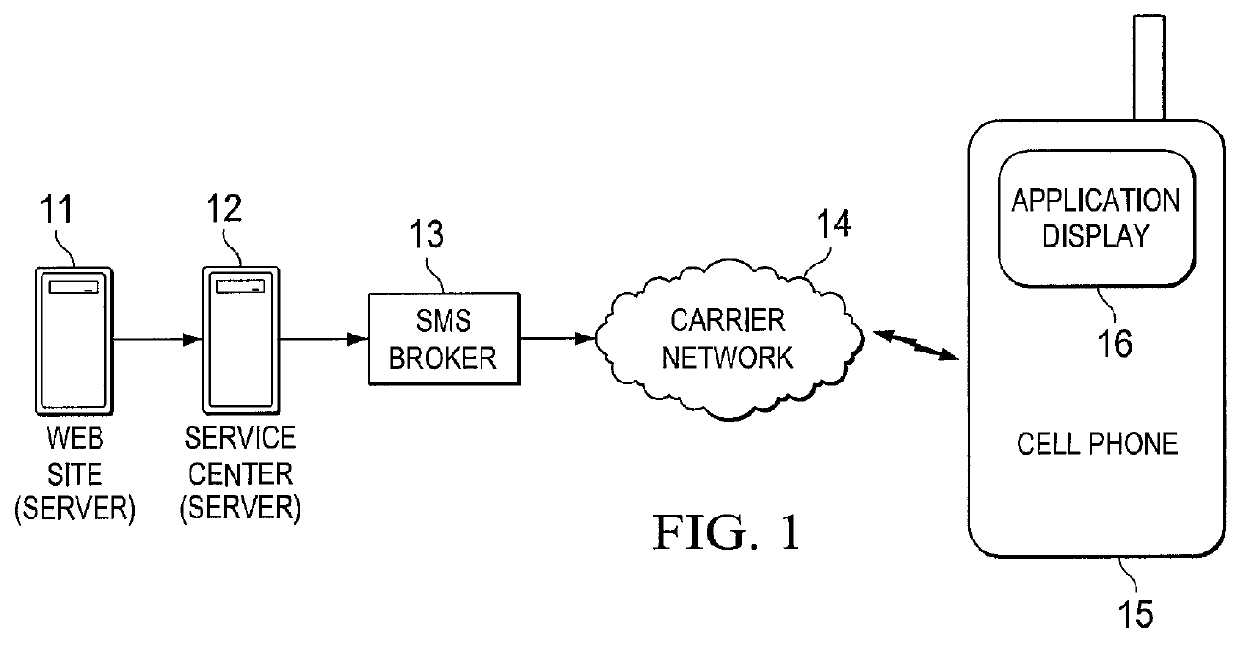
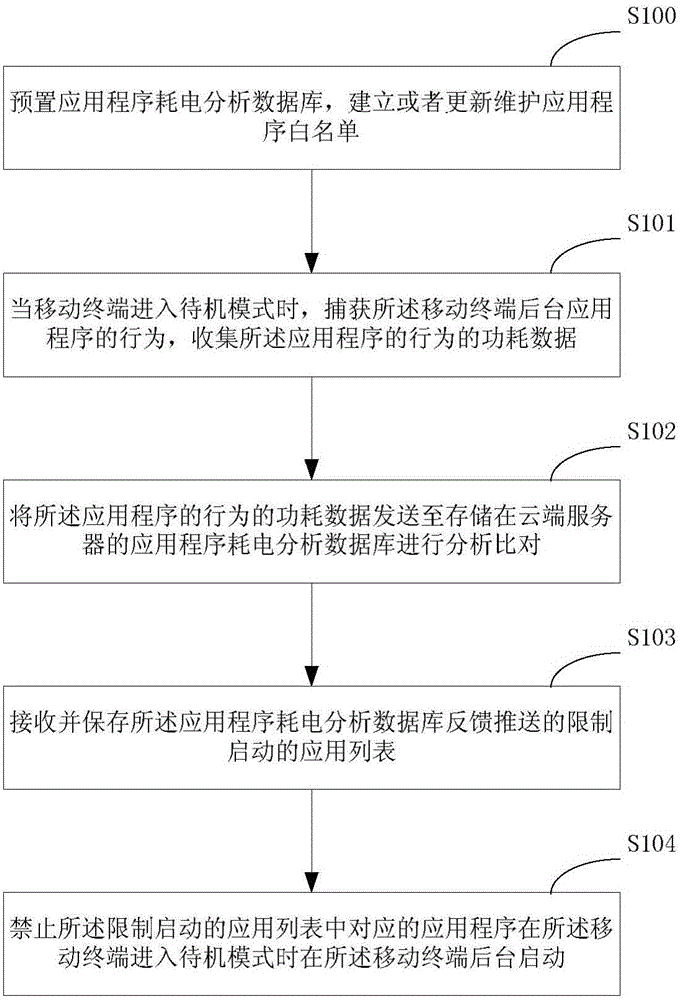
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
119 results about "Application software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Application software (app for short) is software designed to perform a group of coordinated functions, tasks, or activities for the benefit of the user. Examples of an application include a word processor, a spreadsheet, an accounting application, a web browser, an email client, a media player, a file viewer, an aeronautical flight simulator, a console game or a photo editor. The collective noun application software refers to all applications collectively. This contrasts with system software, which is mainly involved with running the computer.
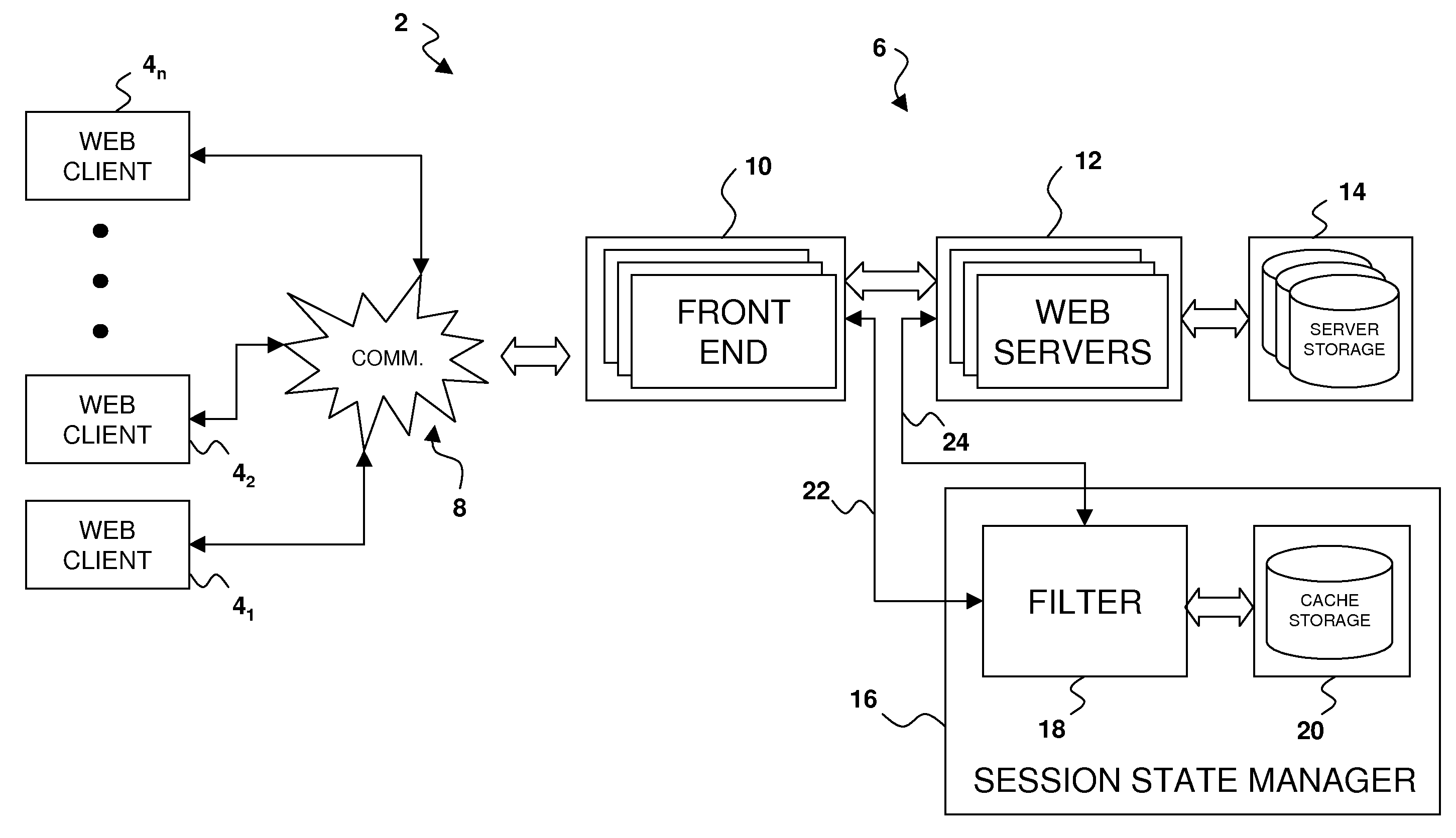
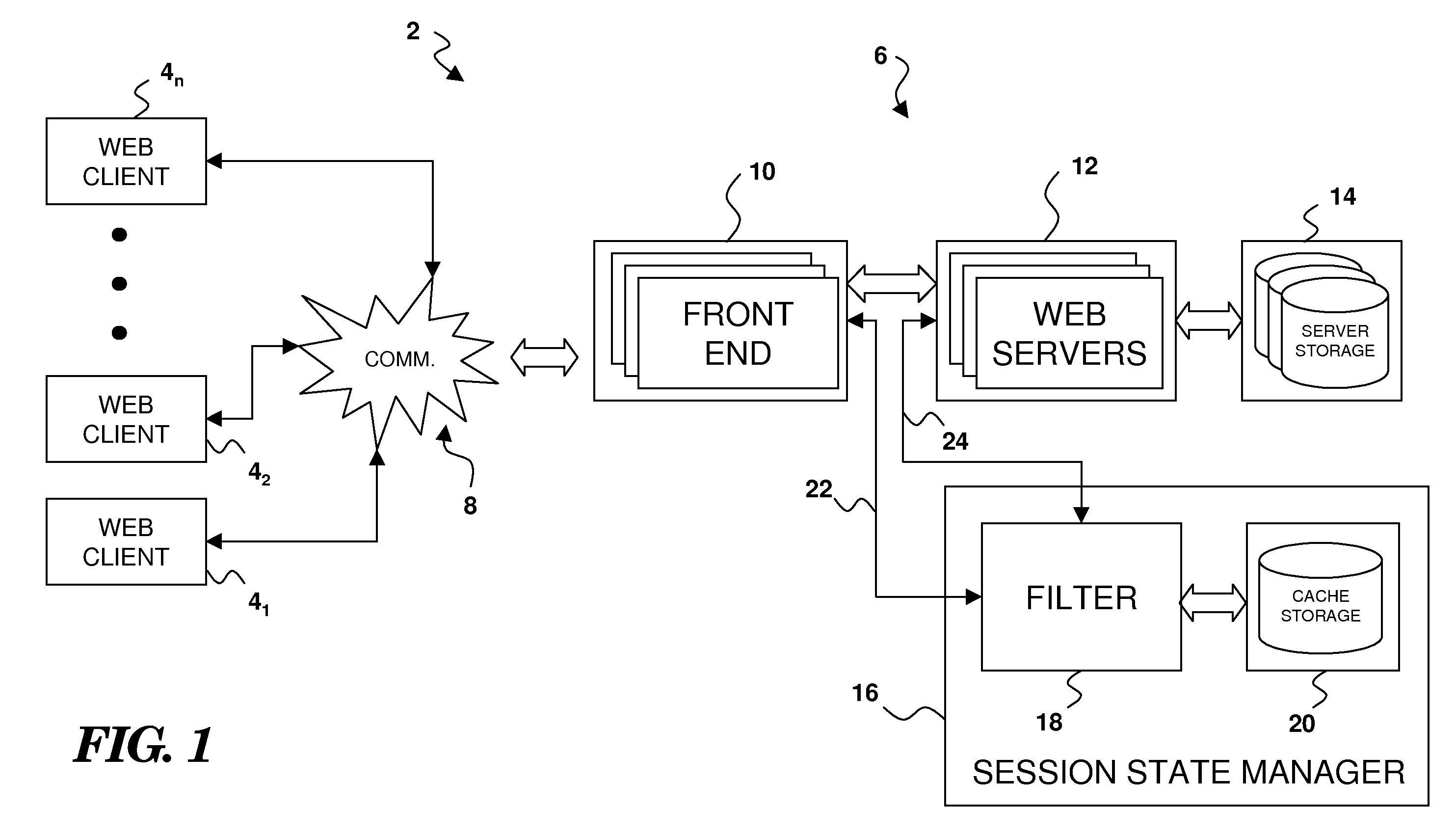
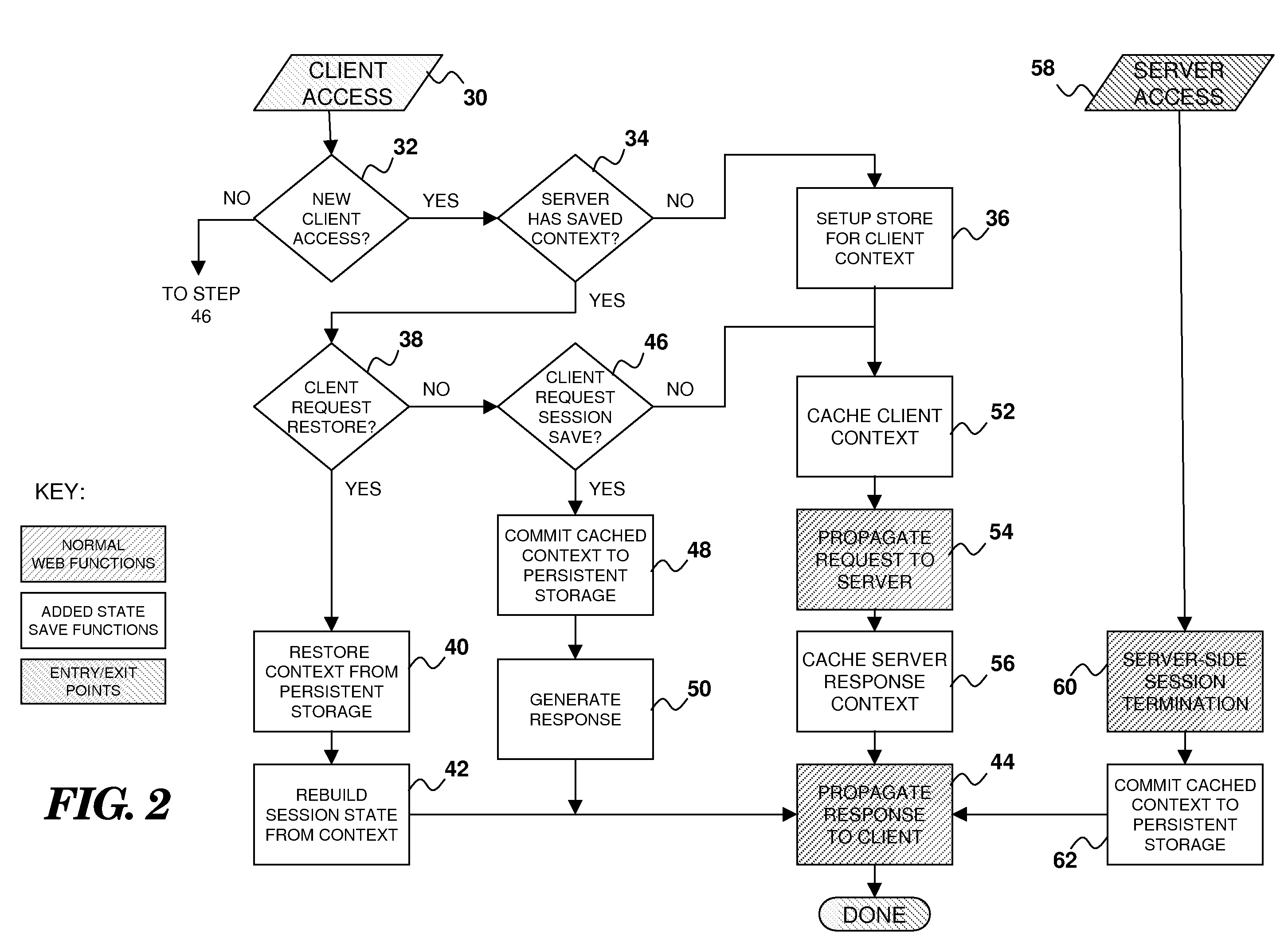
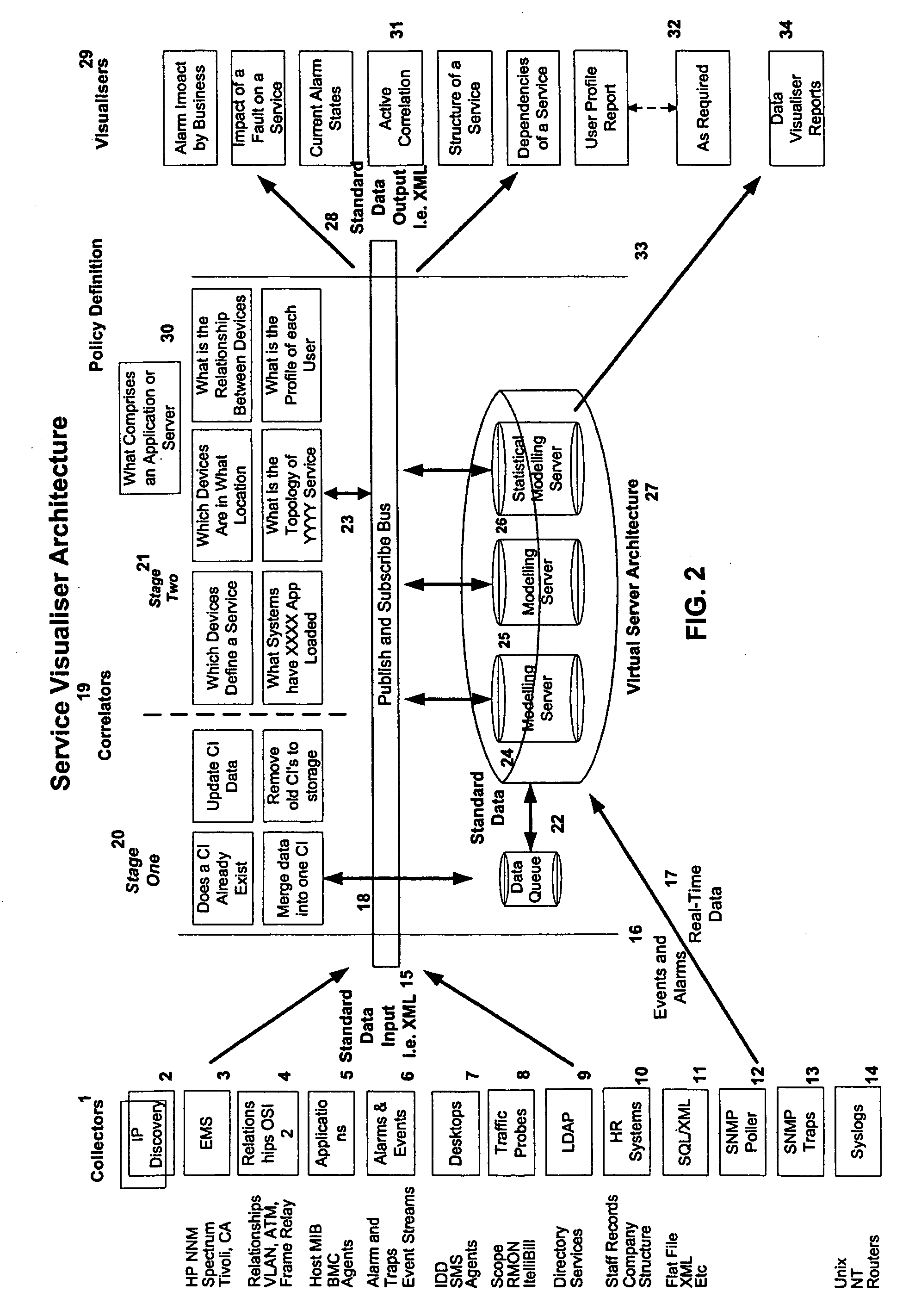
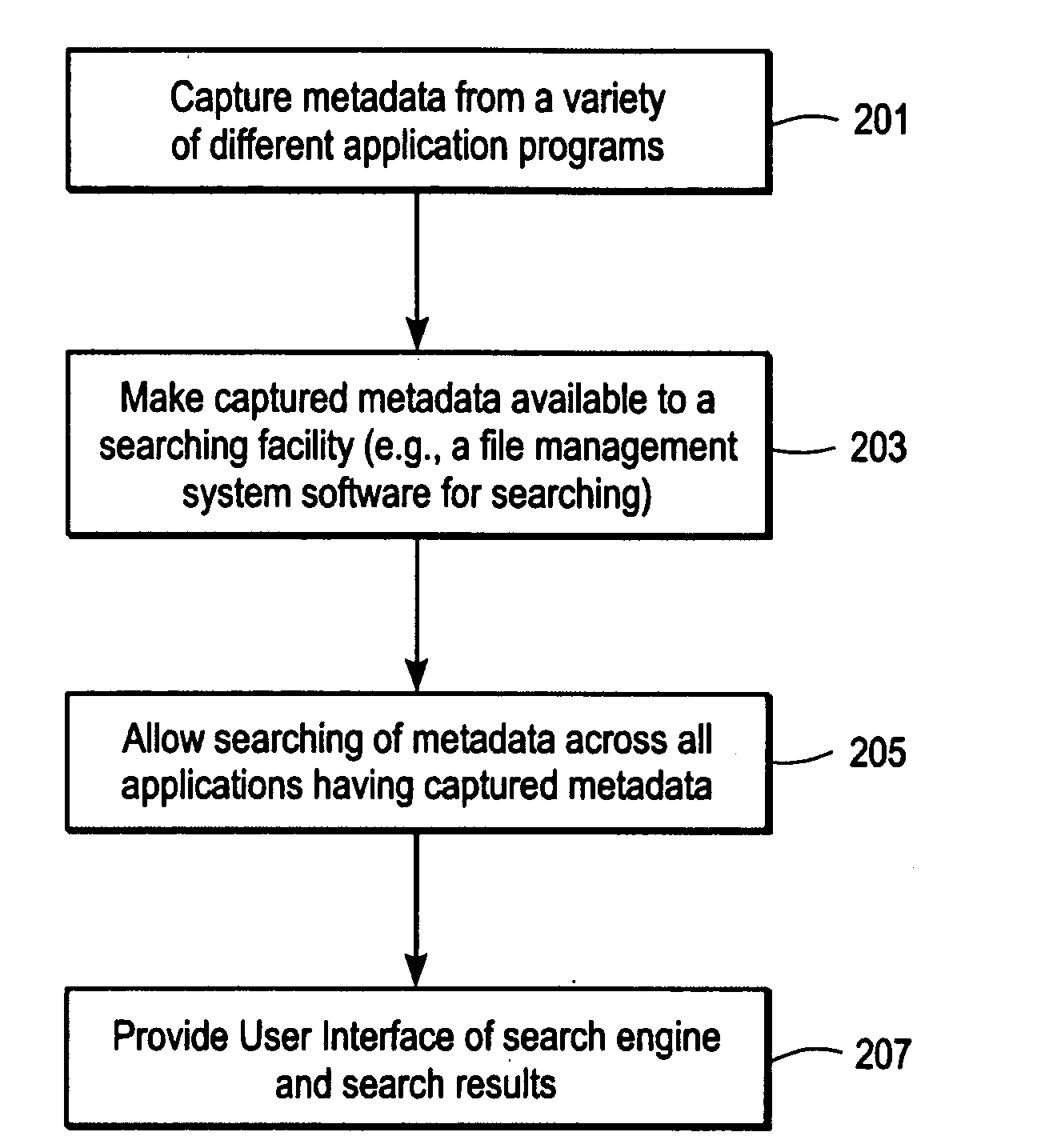
Managing Session State For Web Applications
Owner:IBM CORP
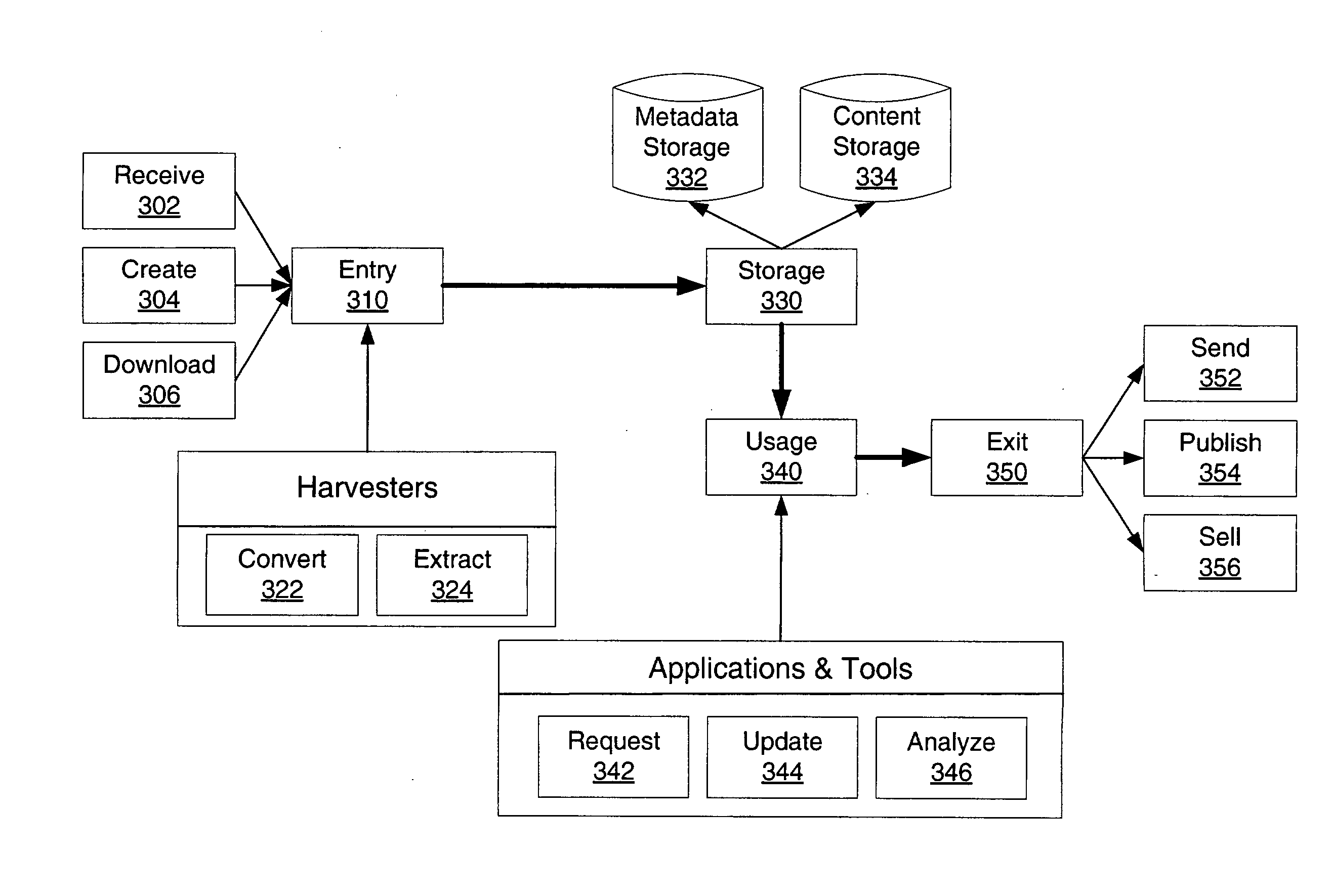
Method and System for Managing Metadata
InactiveUS20080201299A1Digital data processing detailsMetadata multimedia retrievalContext basedApplication software
Owner:NOKIA CORP
Automated application discovery and analysis system and method
ActiveUS20060123022A1Digital data processing detailsObject oriented databasesSystems designMonitoring system
Owner:GLOBAL SAAS SOLUTIONS PTE LTD
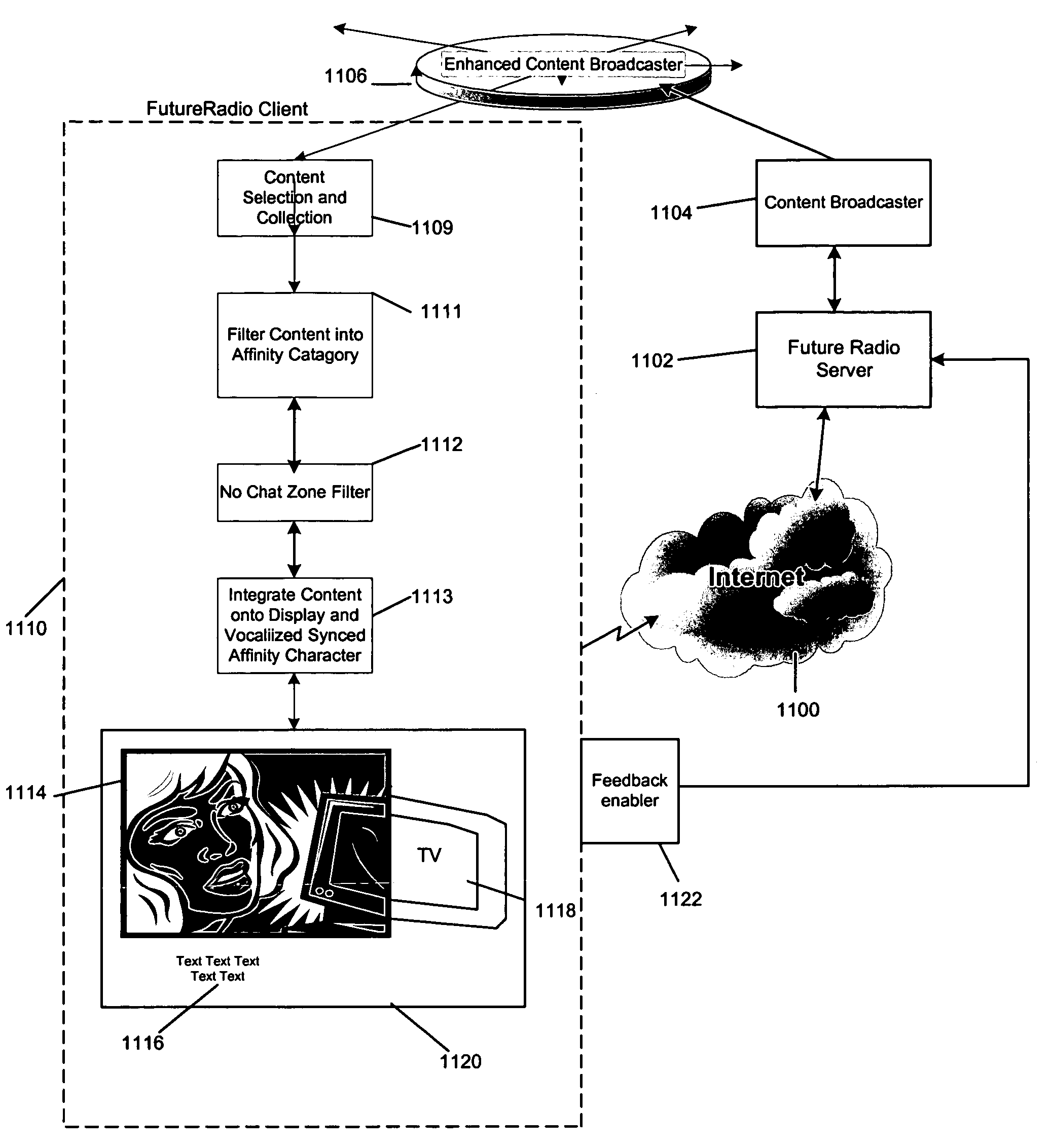
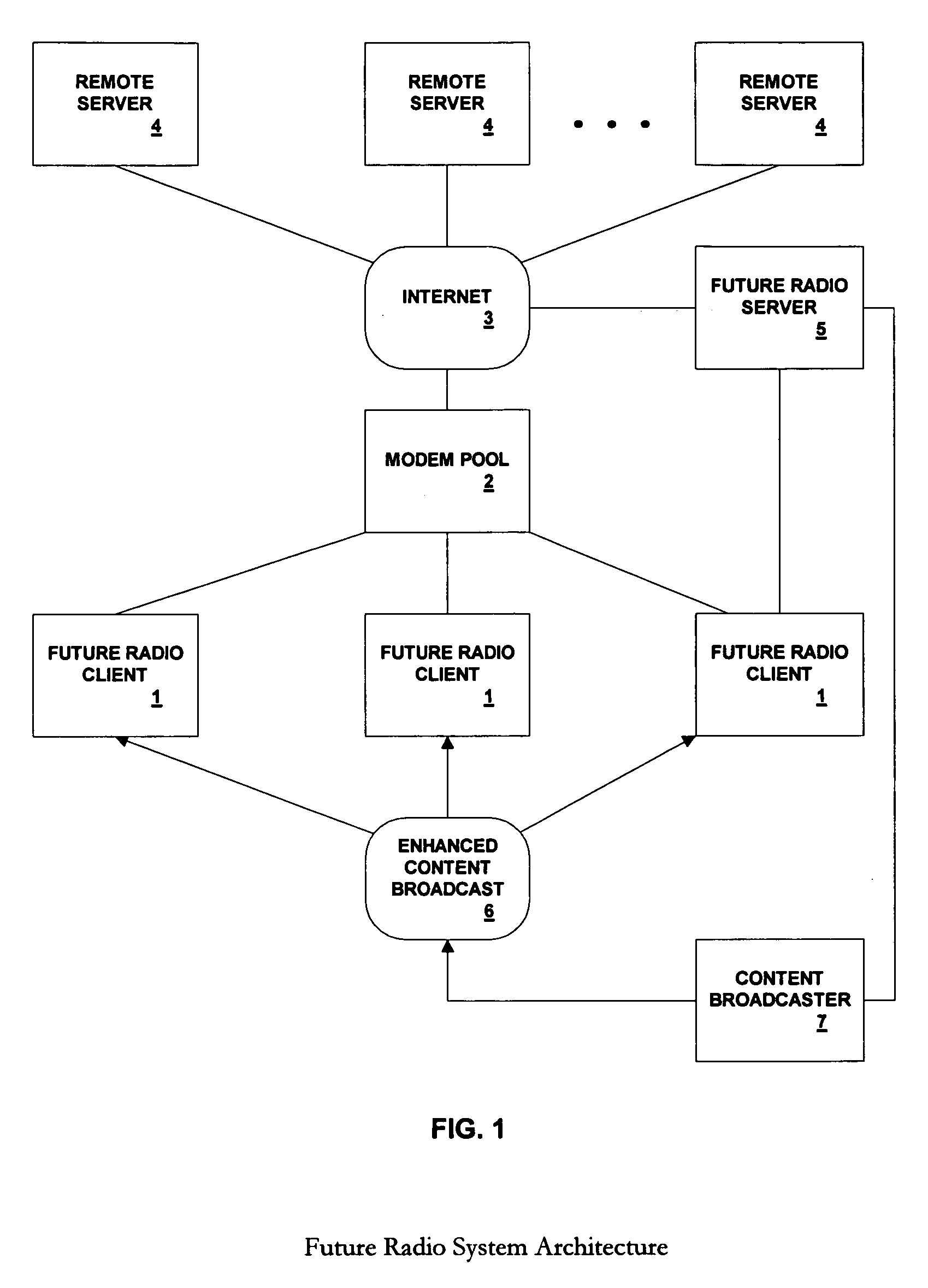
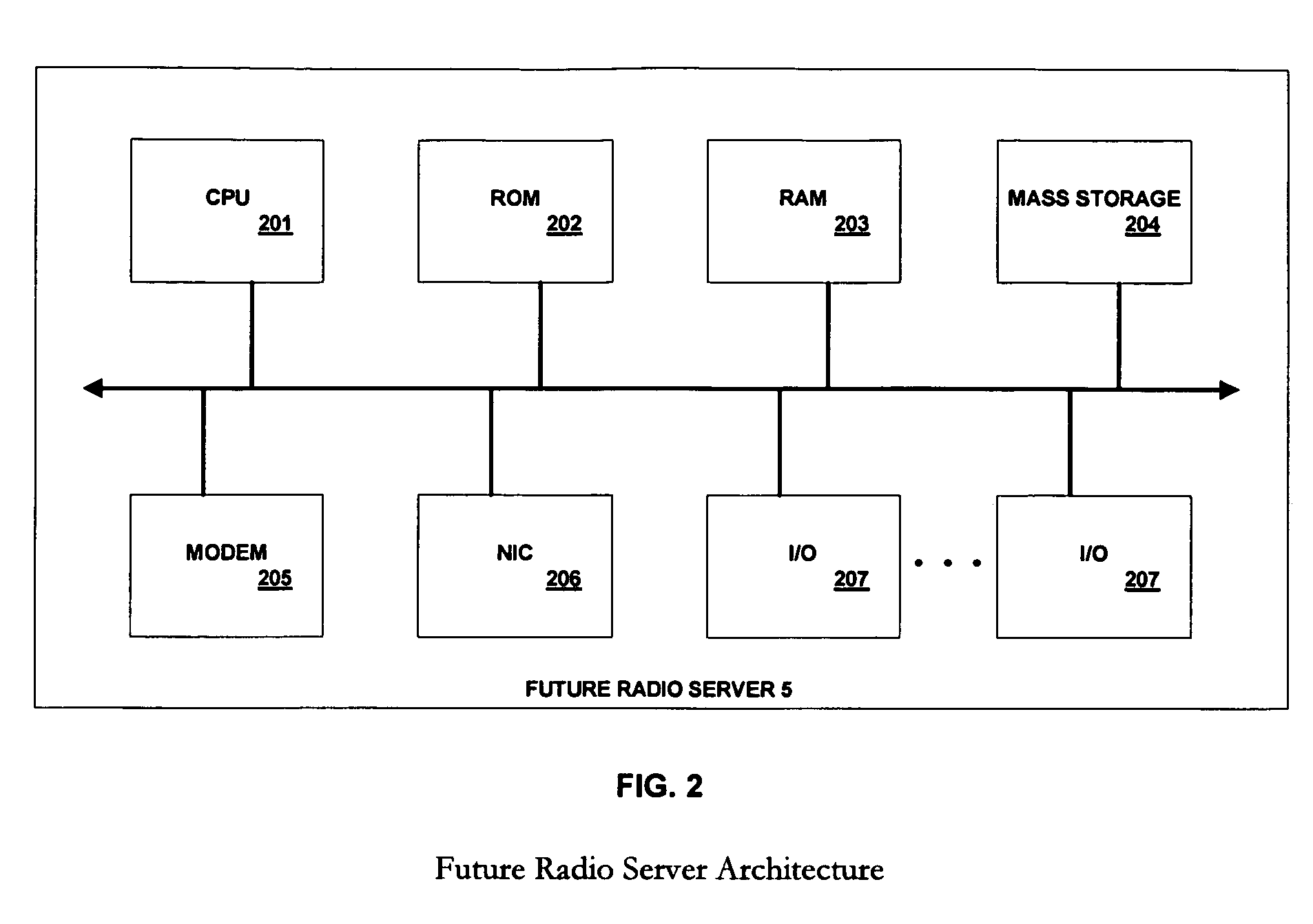
Interactive multi media user interface using affinity based categorization
InactiveUS7284202B1High communication latencyTelevision system detailsDigital data information retrievalThe InternetE-commerce
Owner:MICROSOFT TECH LICENSING LLC
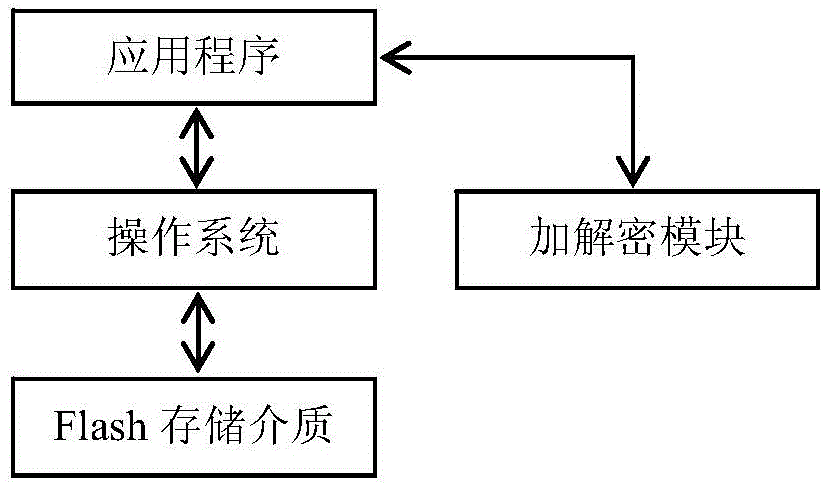
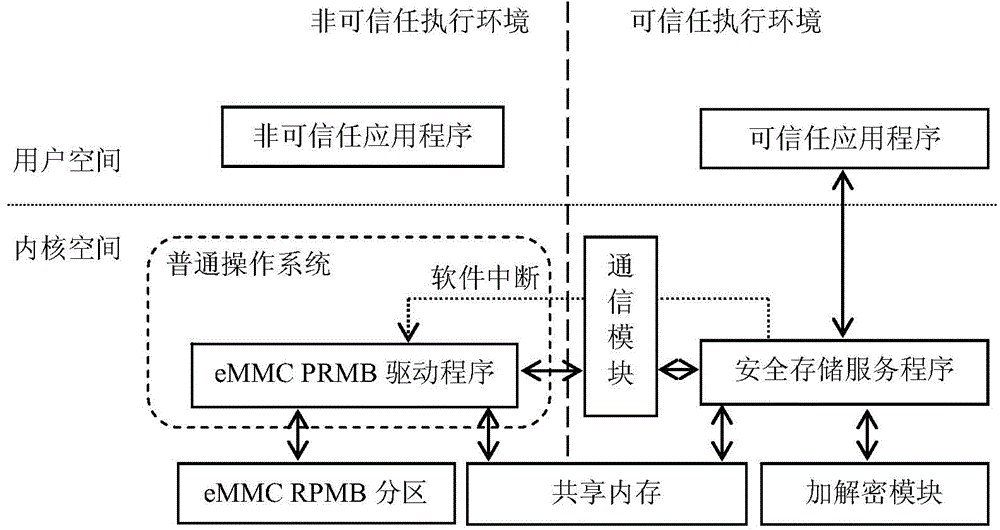
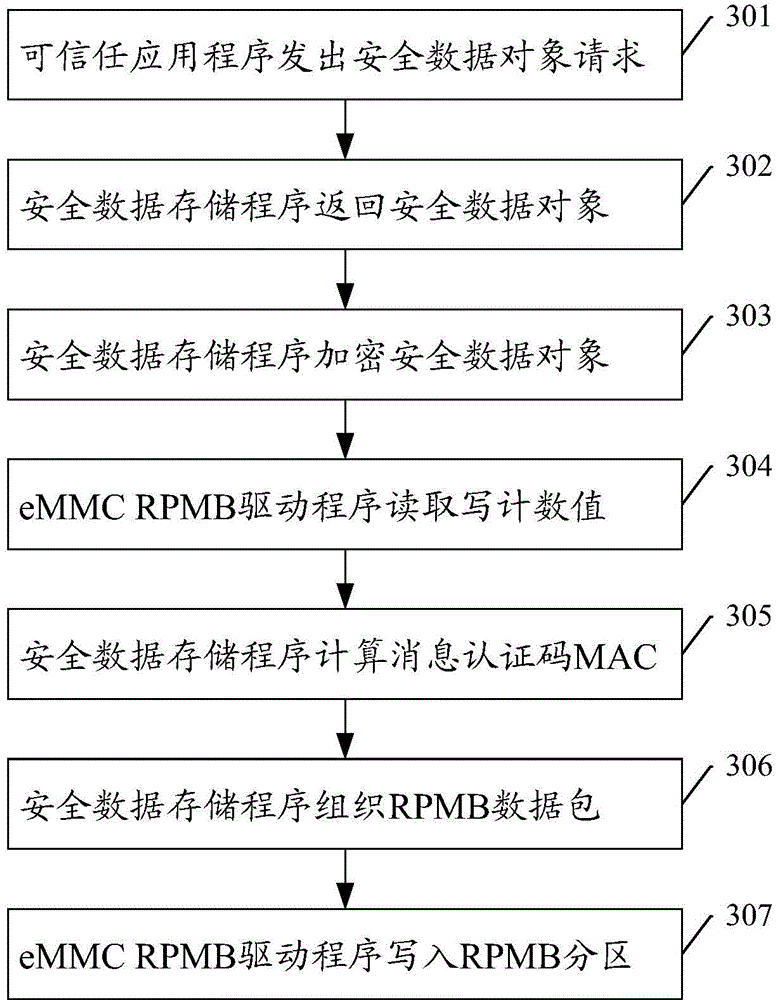
Security data storage method and system
ActiveCN104392188AEnsure safetyAvoid readingDigitally marking record carriersInternal/peripheral component protectionApplication softwareData store
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
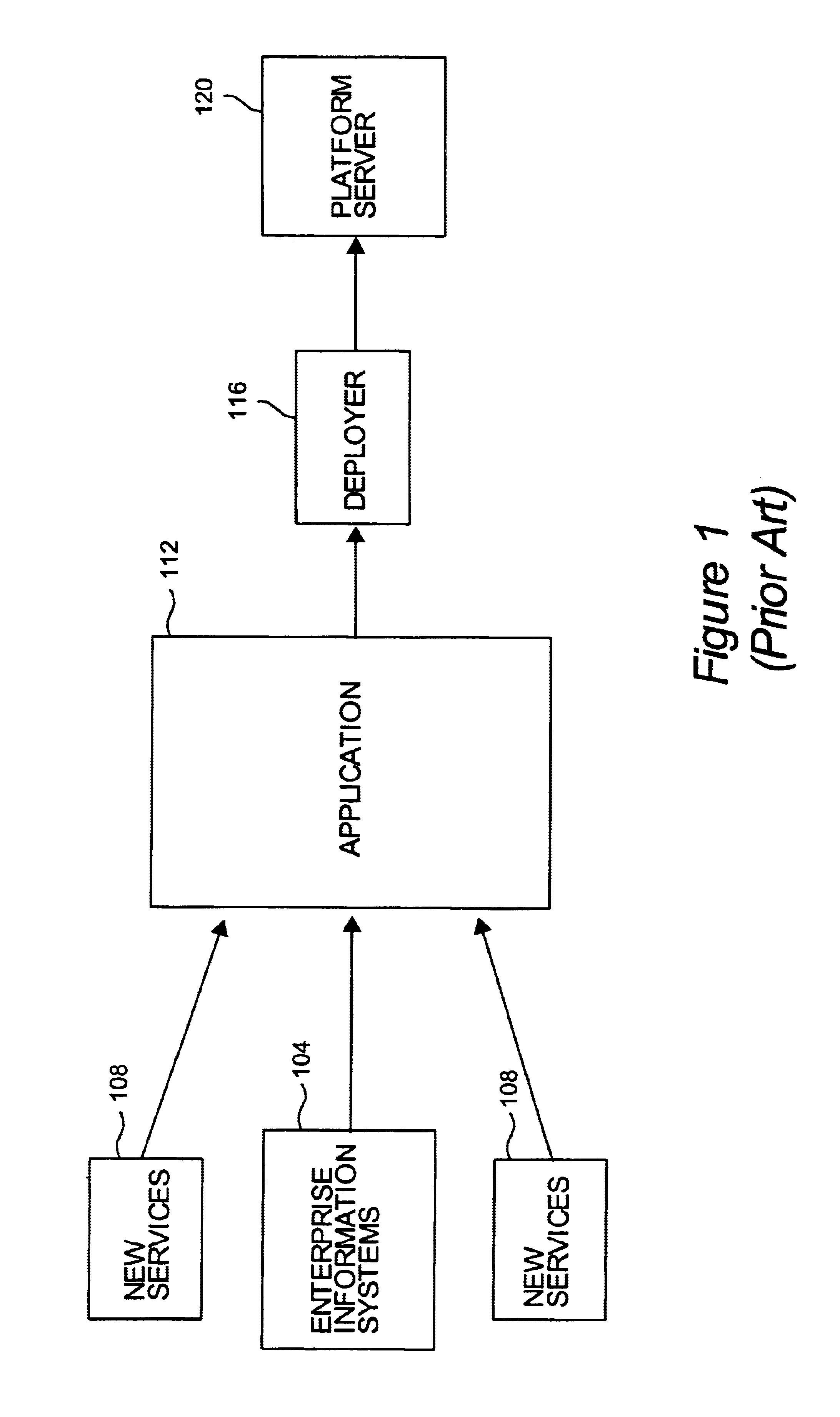
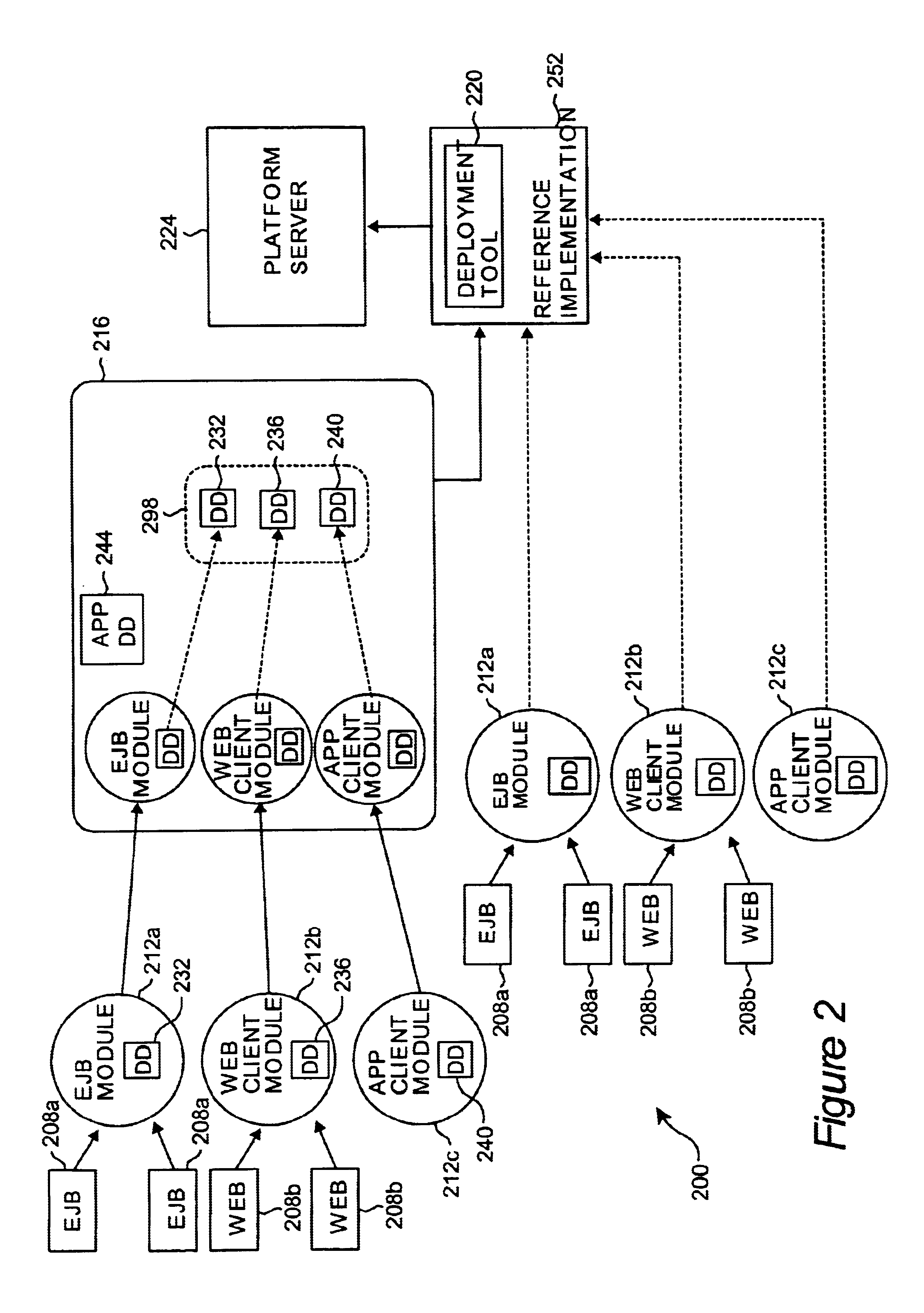
Method and apparatus for implementing deployment descriptors in an enterprise environment
Methods and apparatus for implementing deployment descriptors which are used to deploy modules in an enterprise environment are disclosed. According to one aspect of the present invention, a method for deploying an application using a deployment tool for use on a platform server includes creating the application, creating an application deployment descriptor for the application, packaging the application in an archive, and deploying the application packaged in the archive. Creating the application includes obtaining an application component which has an associated application component deployment descriptor that has information relating to the deployment of the application component. The application deployment descriptor for the application includes information arranged to identify the application component, and packaging the application in an archive includes packaging the application component, the application component deployment descriptor, and the application deployment descriptor. The application packaged in the archive is deployed using the application component deployment descriptor.
Owner:ORACLE INT CORP
Support for application programs in a distributed environment
InactiveUS6138168AEasy to identifyProgram initiation/switchingInterprogram communicationModularityMessage type
Owner:IBM CORP
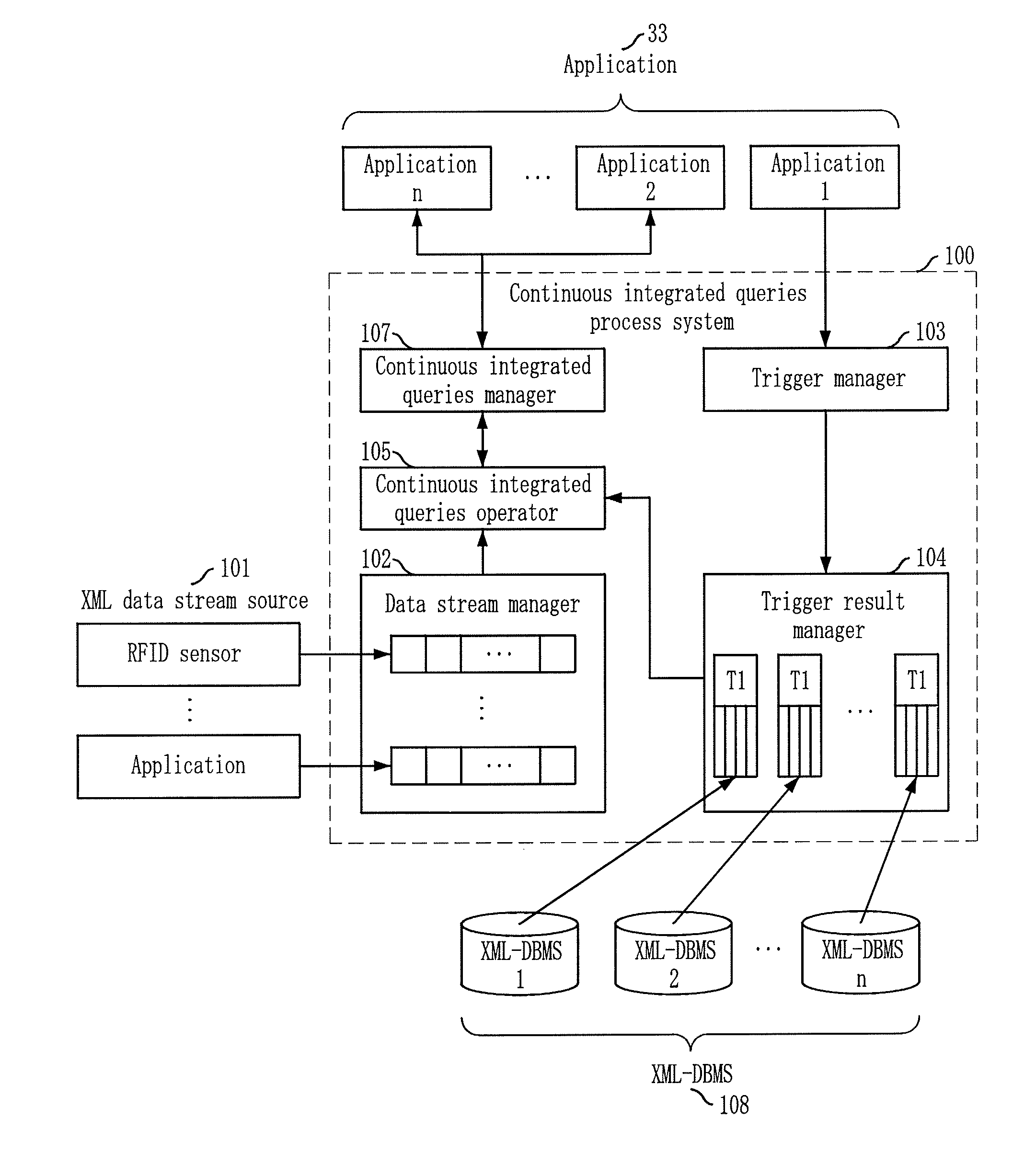
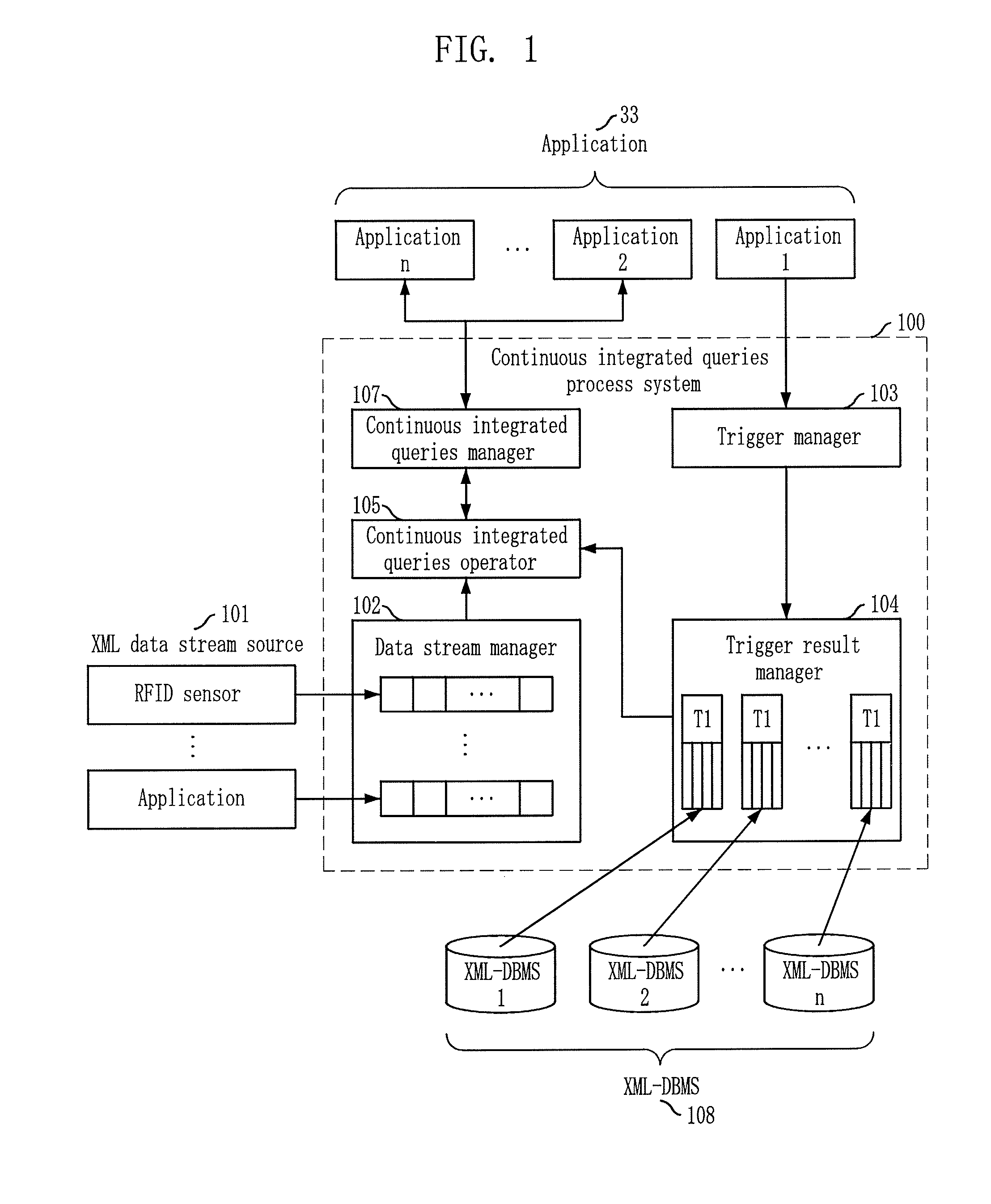
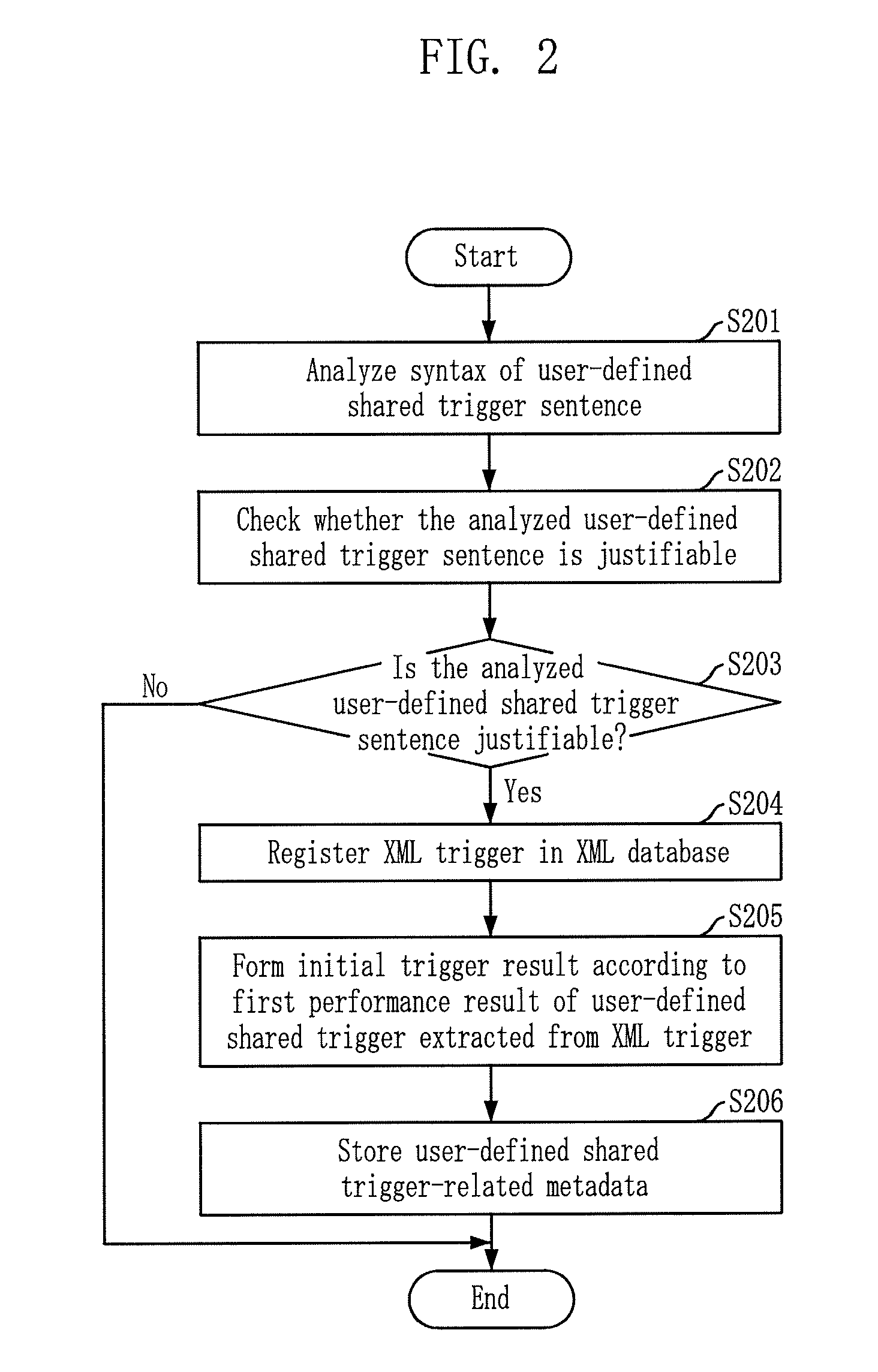
System and method for processing continuous integrated queries on both data stream and stored data using user-defined share trigger
InactiveUS20080046401A1Improve performanceDigital data information retrievalDigital data processing detailsExternal applicationData stream
Owner:ELECTRONICS & TELECOMM RES INST
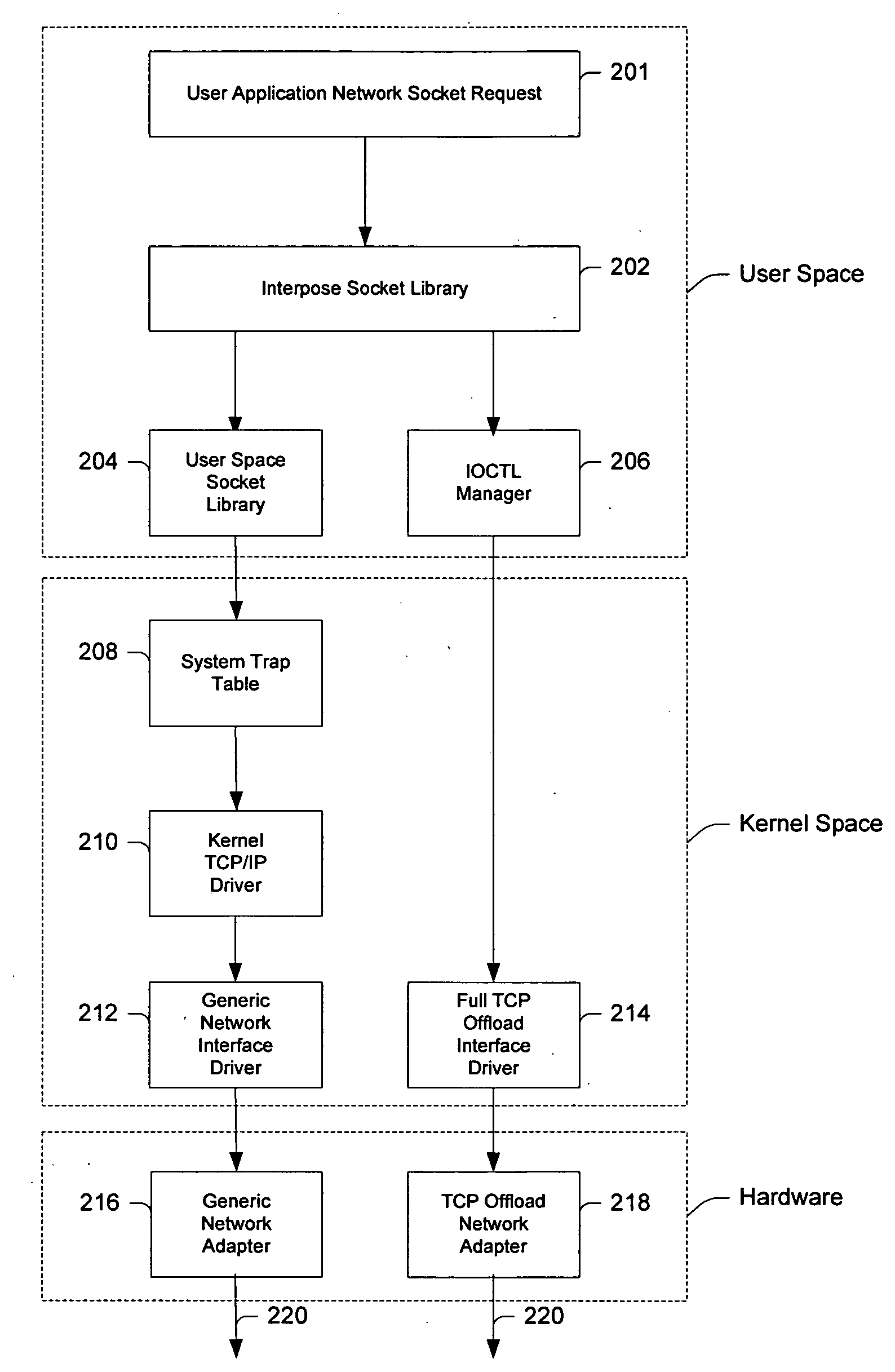
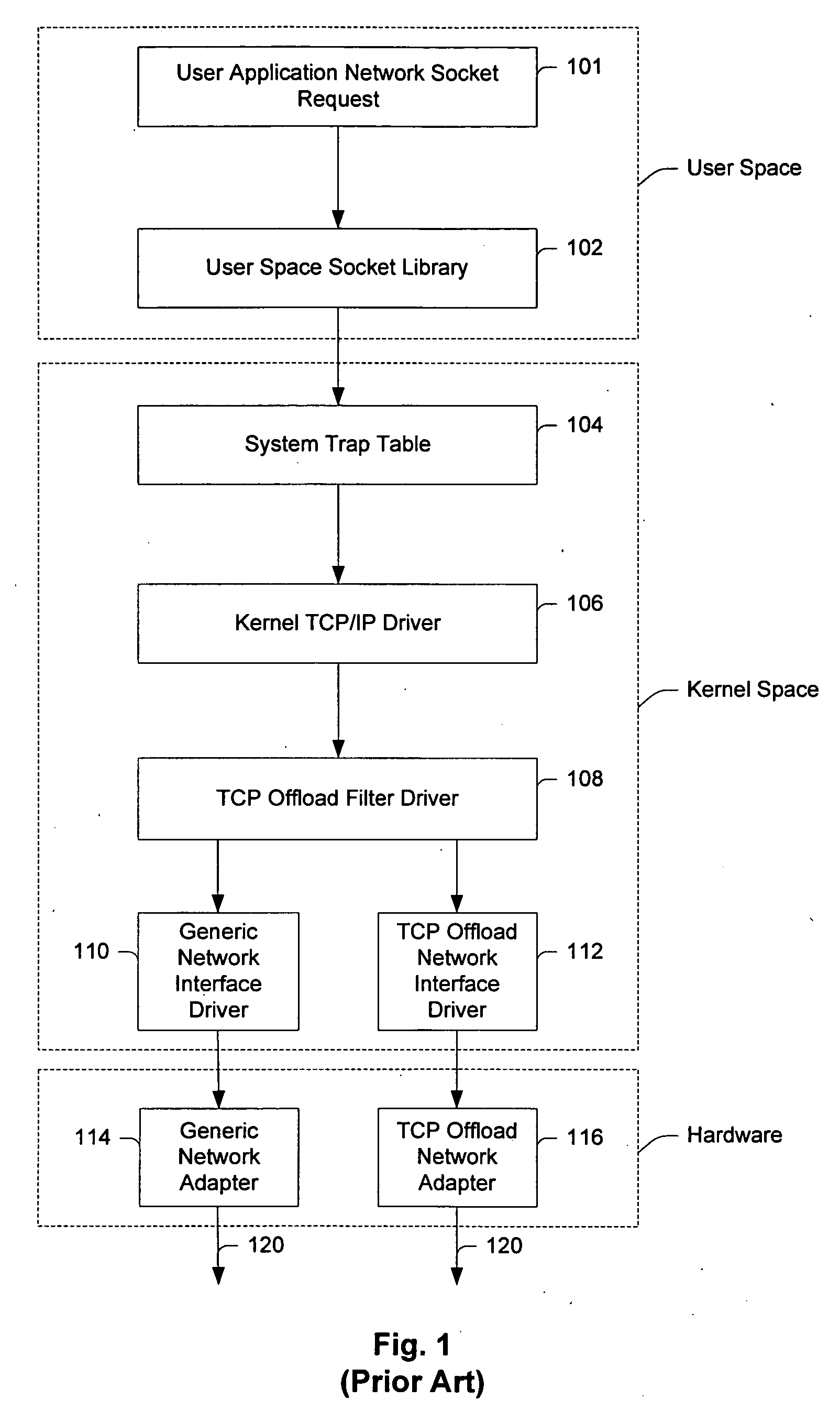
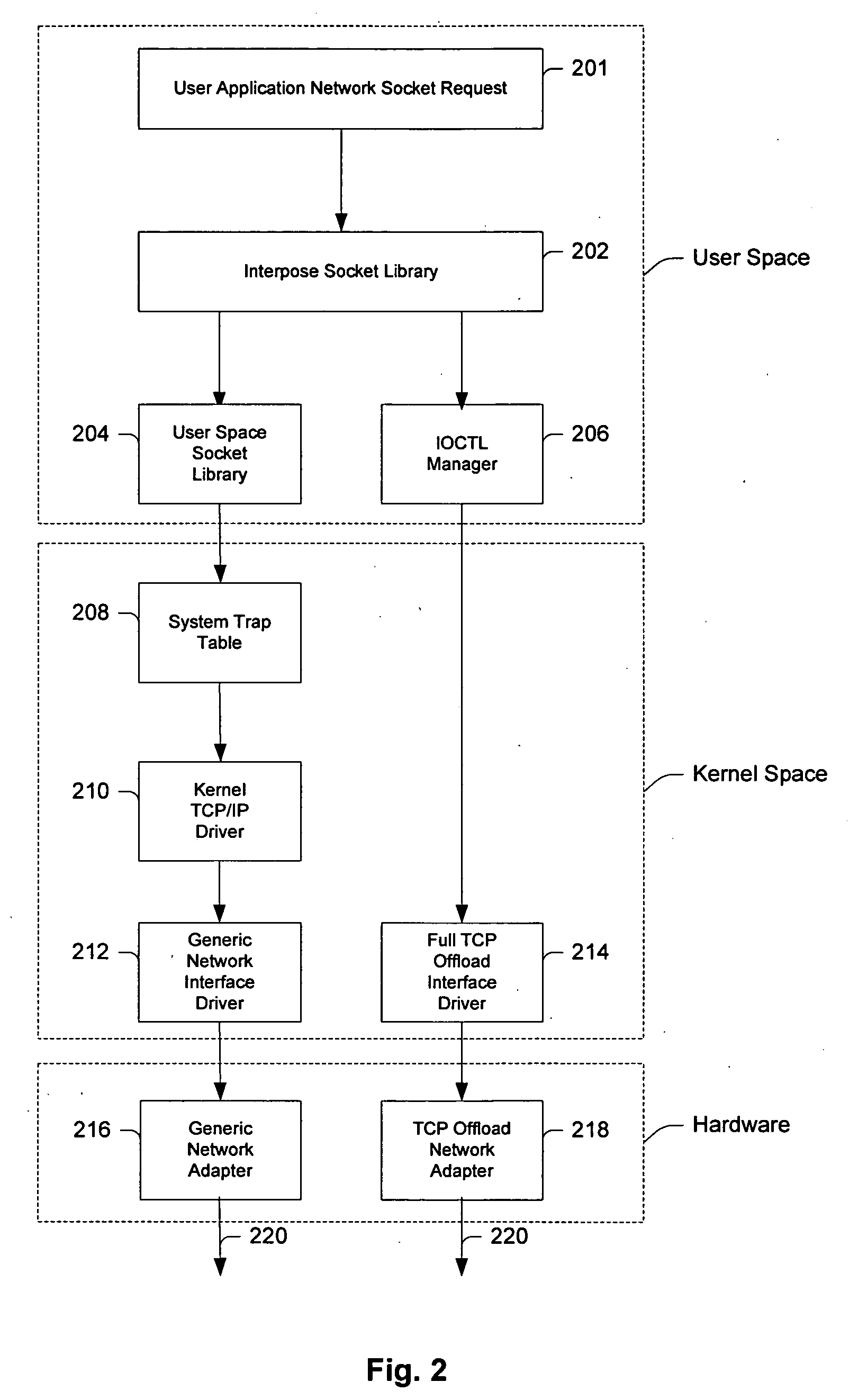
System and method for interfacing TCP offload engines using an interposed socket library
InactiveUS20050021680A1Improve system performanceReduce CPU utilizationMultiple digital computer combinationsProgram controlOperational systemNetwork socket
Owner:CENATA NETWORKS
System and method for switching between conversations in instant messaging applications
ActiveUS20100217808A1Digital computer detailsData switching networksApplication softwareInstant messaging
A system and method are provided for switching between conversations in instant messaging applications. The instant messaging application is configured for displaying a list of conversations upon detecting selection of the option within a menu or link within the conversation screen and permit navigation to another conversation. The conversations may be prioritized based first on whether the conversation has any unread messages and within the grouping of those conversations having unread messages, may be prioritized based on when the last activity occurred. In this way, the user has easiest access to conversations with the most recent activity with the ability to scroll down the list of conversations to continue an older conversation if desired.
Owner:MALIKIE INNOVATIONS LTD
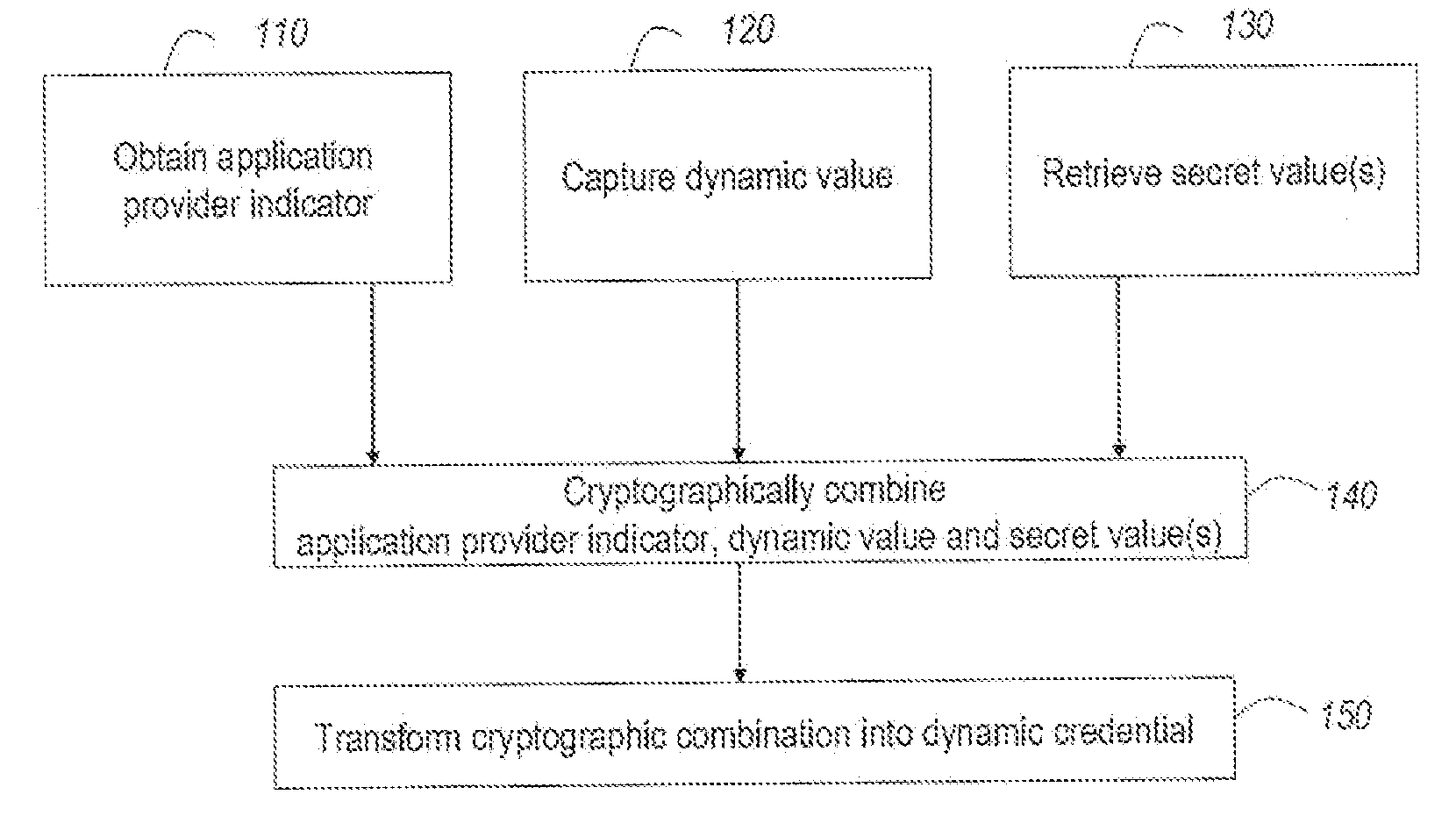
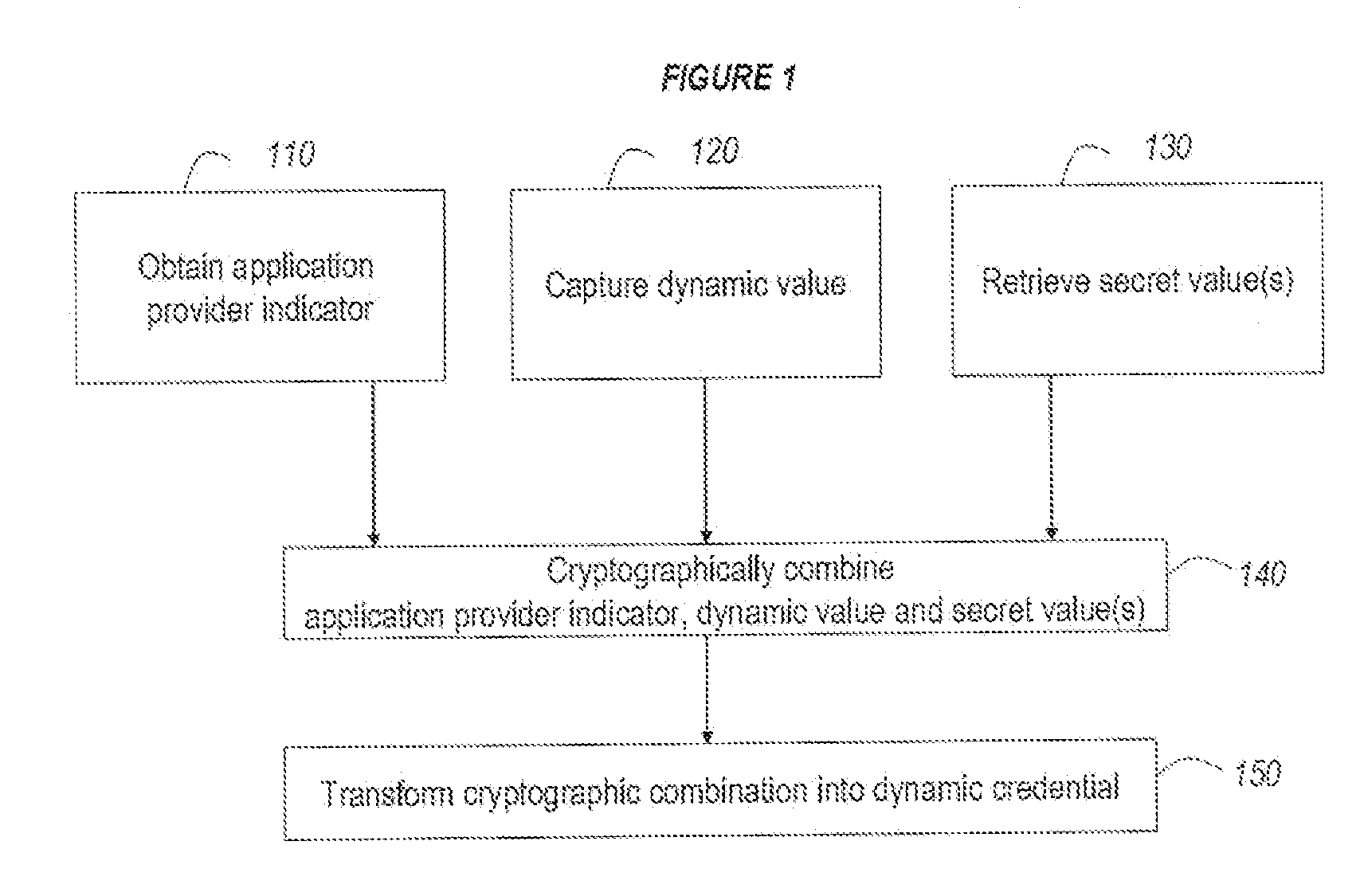
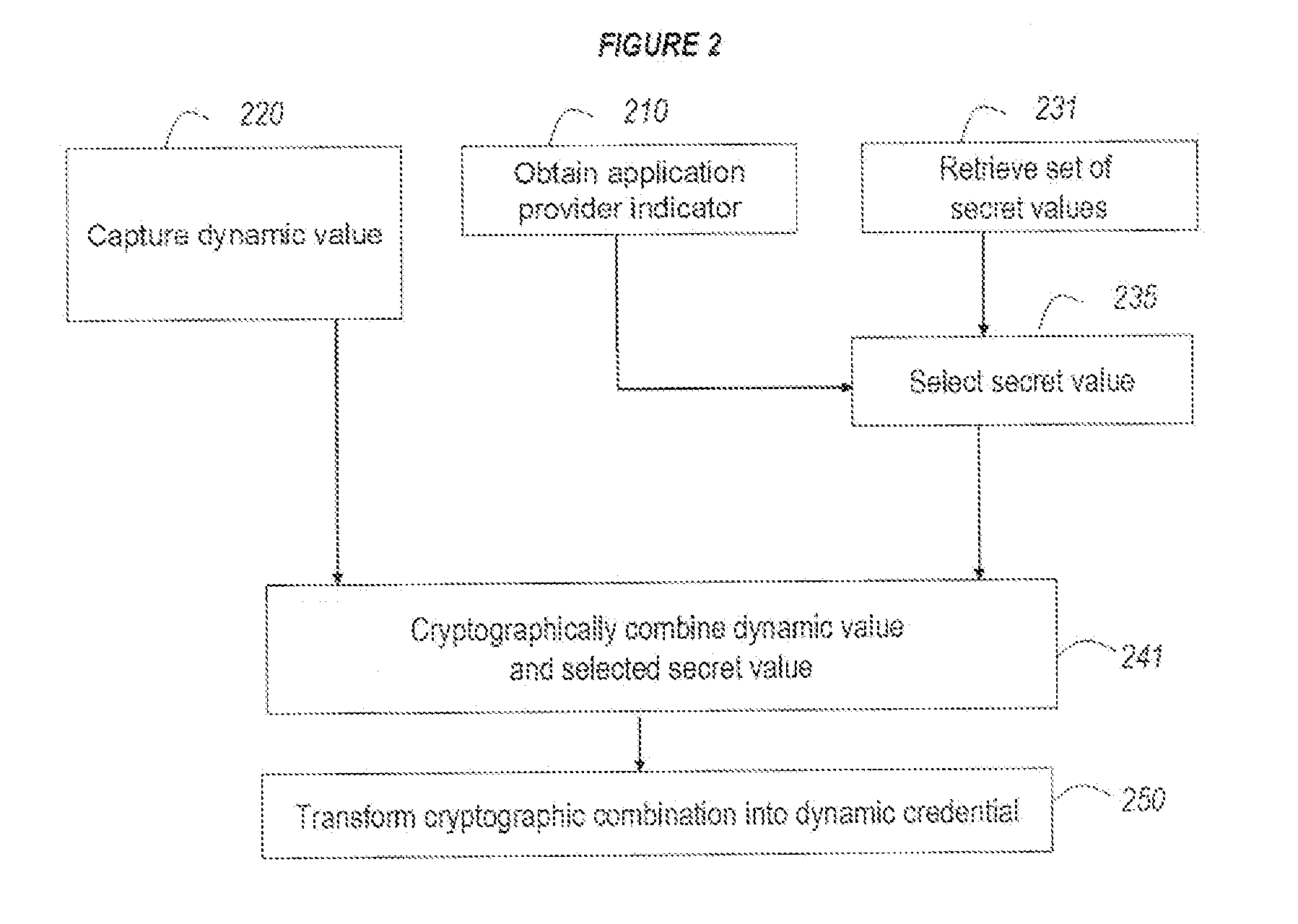
Strong authentication token usable with a plurality of independent application providers
ActiveUS20110099384A1Low costCost can be dividedMultiple keys/algorithms usageDigital data processing detailsPersonalizationUnique identifier
Owner:ONESPAN NORTH AMERICA INC
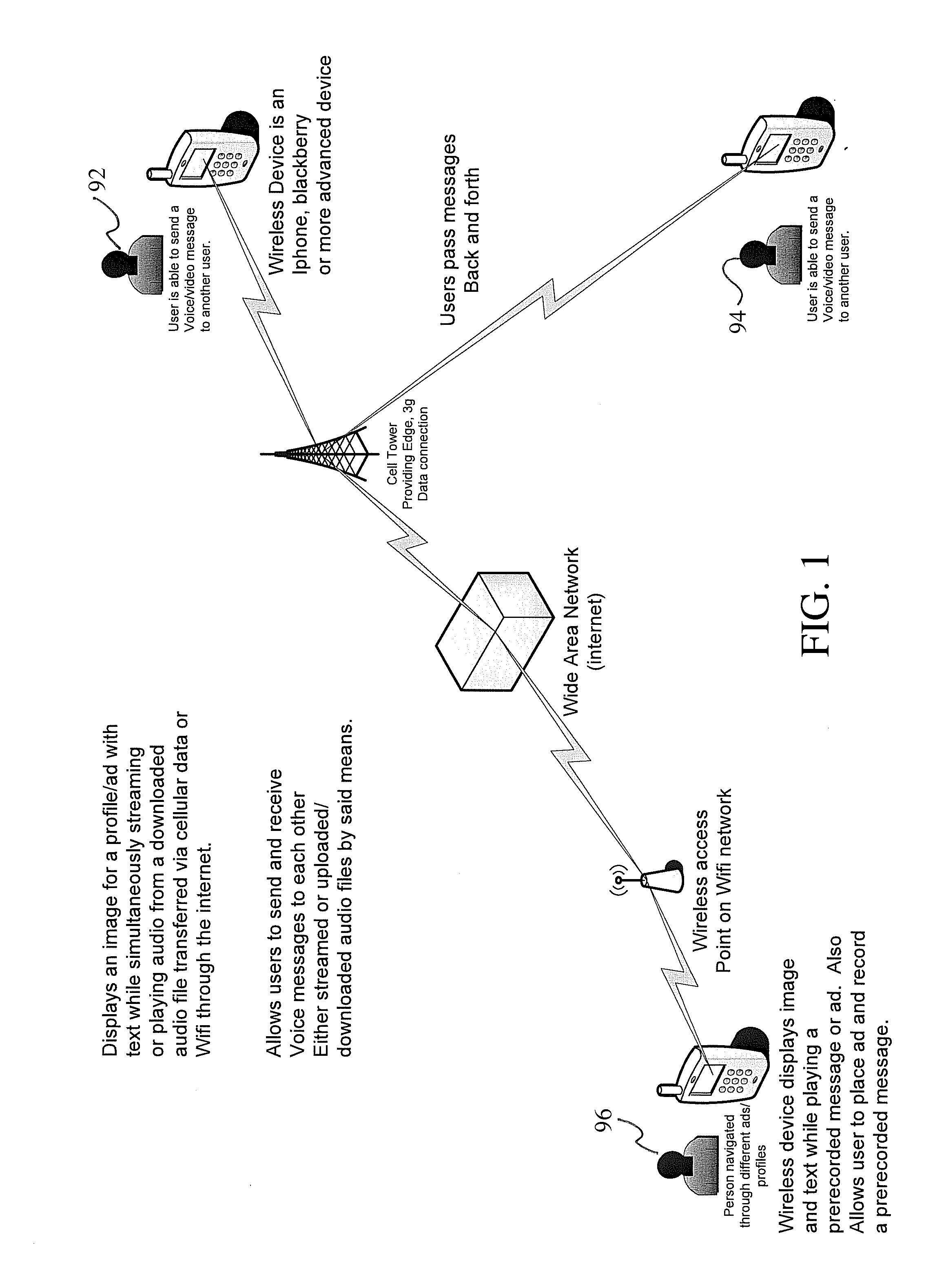
System and method of providing an interface to the internet
InactiveUS20030187739A1AdvertisementsSpecial data processing applicationsInternet privacyApplication software
Owner:POWERS ARTHUR C
Android-based platform application installation control method and system
InactiveCN102087605AComputer security arrangementsProgram loading/initiatingApplication softwareEncryption
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
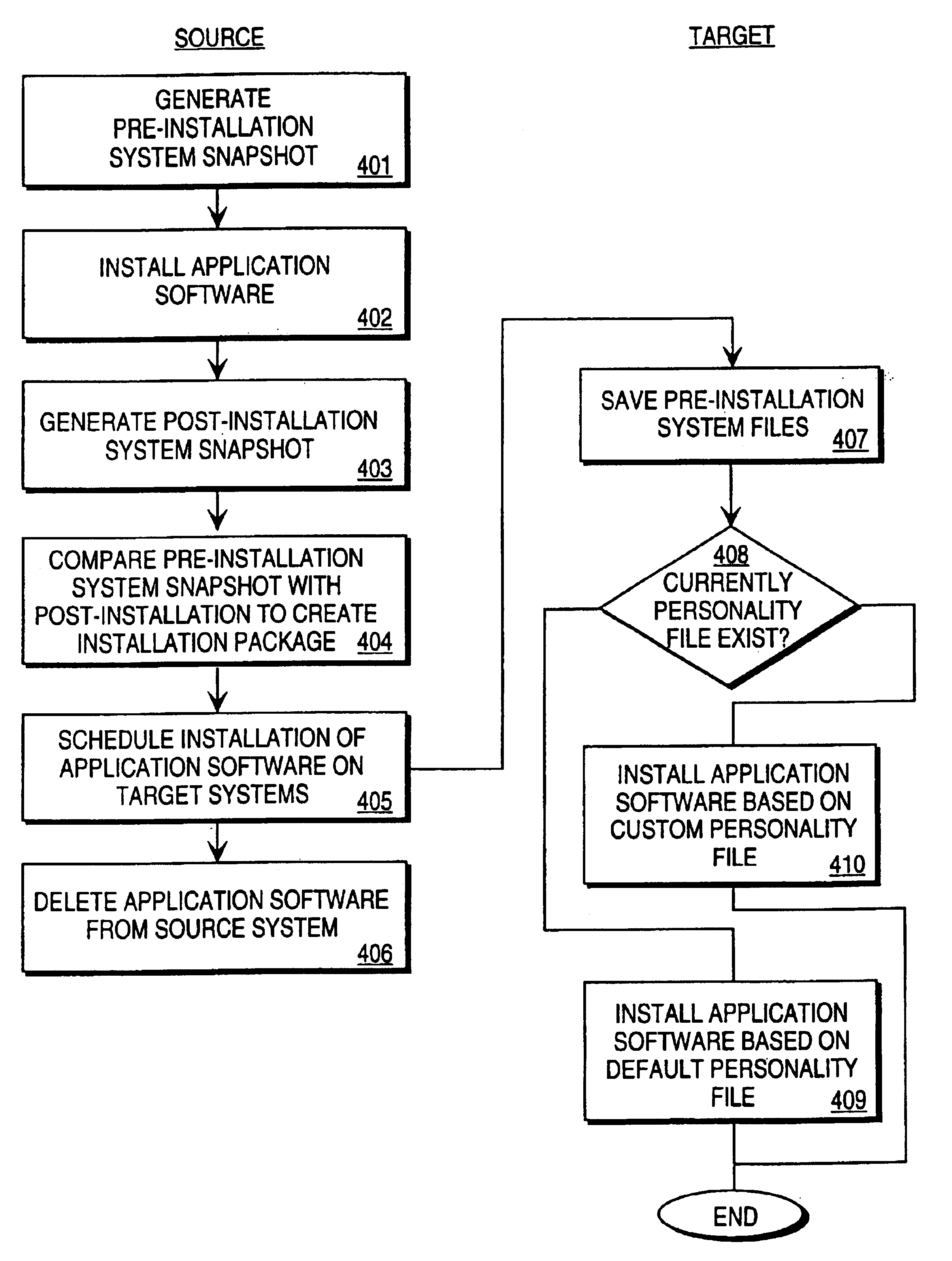
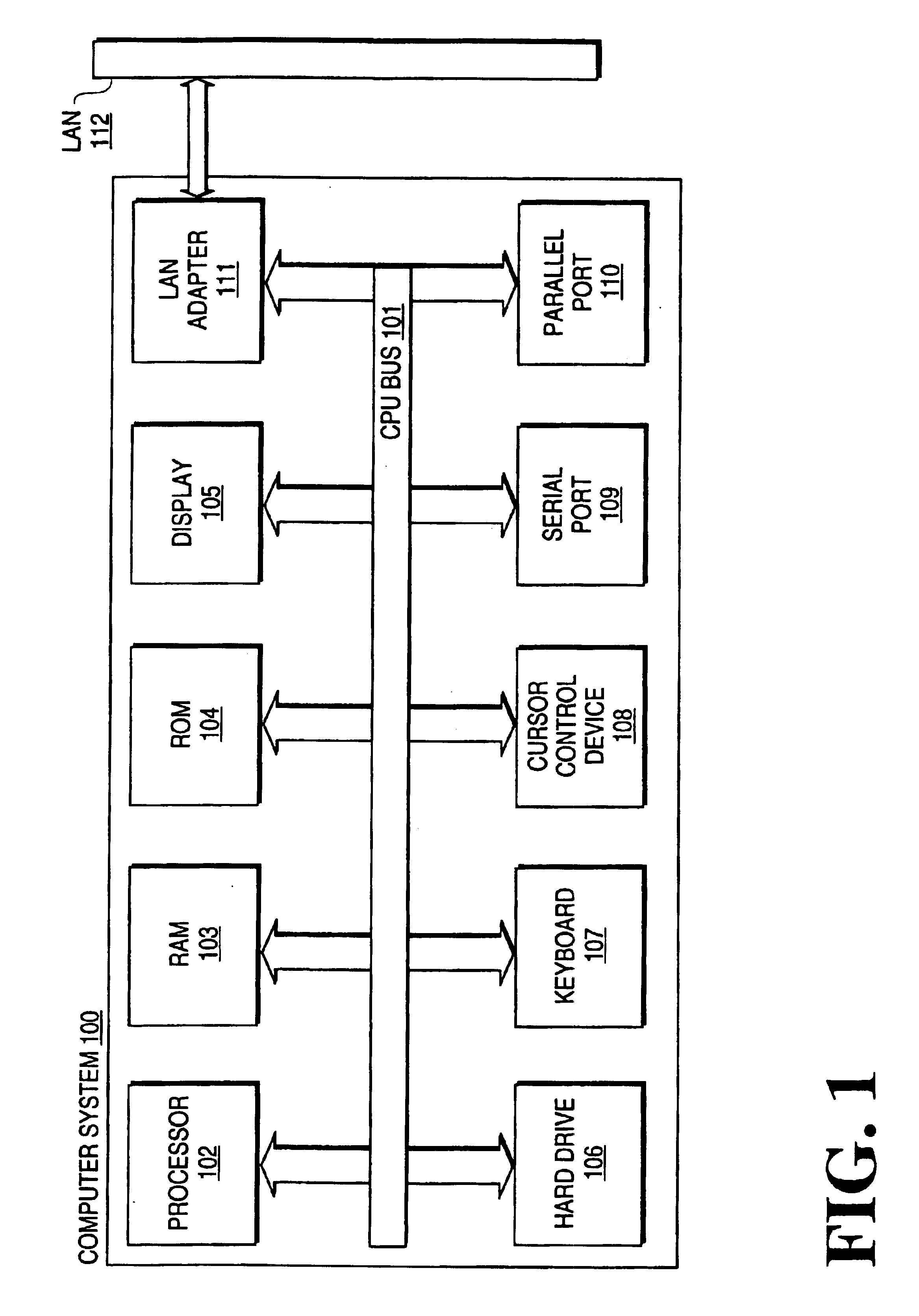
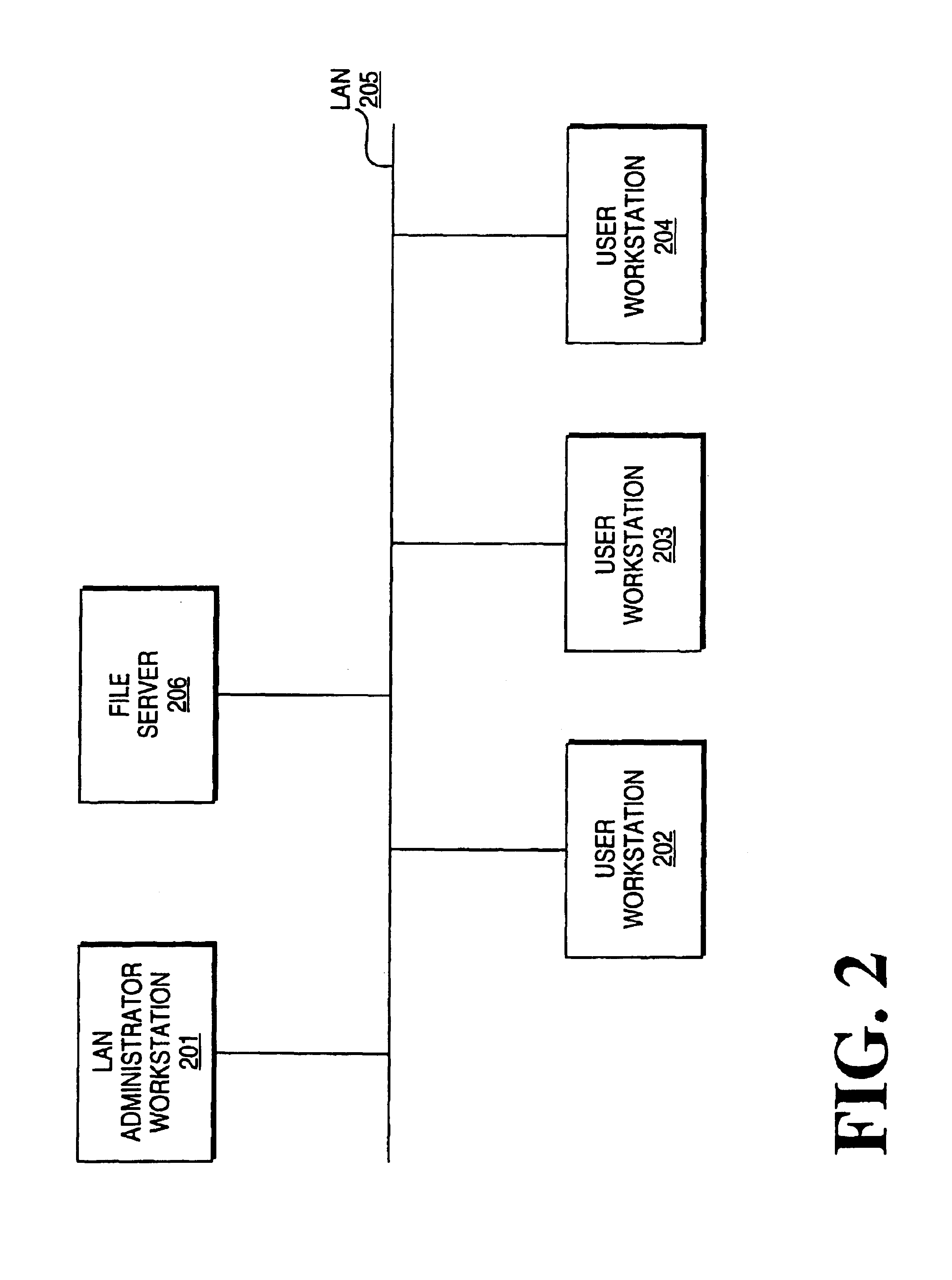
Installation of application software through a network from a source computer system on to a target computer system
InactiveUS6944858B2Digital computer detailsHardware monitoringApplication softwareLocal area network
A technique for the remote installation of application software from a source computer system to one or more target computer systems (workstation) coupled to a Local Area Network (LAN). The present invention allows a LAN Administrator to install application software on a user's workstation automatically at any time without user's intervention. The state of (i.e. a snapshot of) the LAN Administrator's system before and after the installation of the application software is captured and an installation package is built. Installation on the user workstations is then scheduled. For installation, the installation package is transmitted to the user workstation where an install program carries out commands in the installation package for installing the application software.
Owner:INTEL CORP
Mobile Device Messaging Application
Owner:QURESHI RICK
Application program control method based on two-time signature verification technology
ActiveCN103886260AEnsure safetyProgram loading/initiatingPlatform integrity maintainanceThird partyApplication software
An application program control method based on a two-time signature verification technology is achieved by performing two times of signing and two times of signature verification on application programs on an android terminal. Security detection is performed on the application programs through a reliable third-party security detection mechanism, the application programs passing the detection will be signed by the third-party security detection mechanism, and then the signed applications are returned to developers. When the application programs are installed on the intelligent android terminal, security detection is performed on the application programs first to see whether the application programs are signed by the third-party security detection mechanism or not, and signatures are verified; if signatures of the third-party detection mechanism do not exist or the signatures cannot pass verification, installation of the application programs is refused. Through the technical scheme, the application program control method based on the two-time signature verification technology has the advantages that signature information is fixed through introduction of the third-party detection signatures and a security control module of the android terminal so that secure application programs can be downloaded and installed in an android system through multiple channels, and while security of the android terminal is guaranteed, a flexible and efficient application program verification scheme is provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
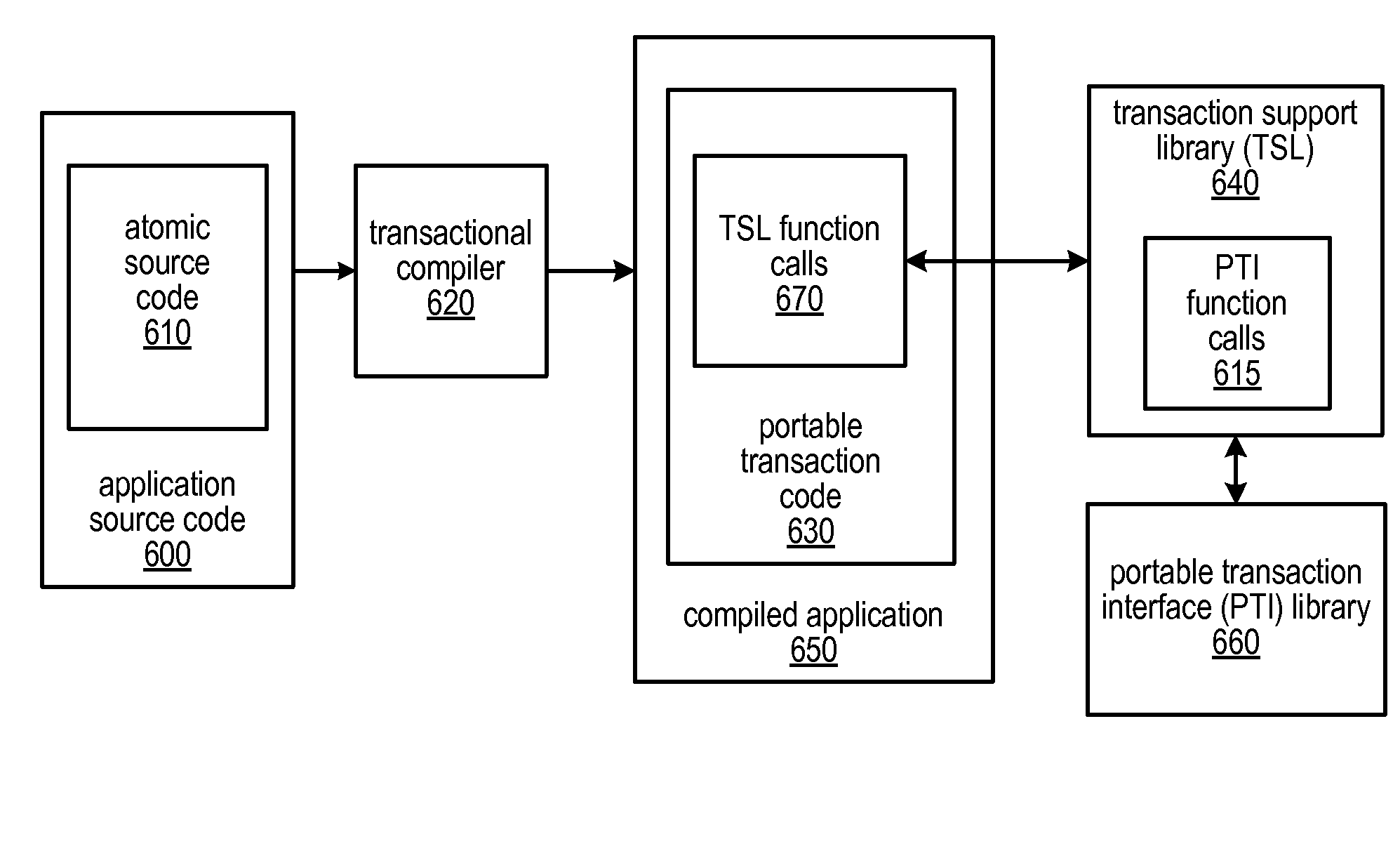
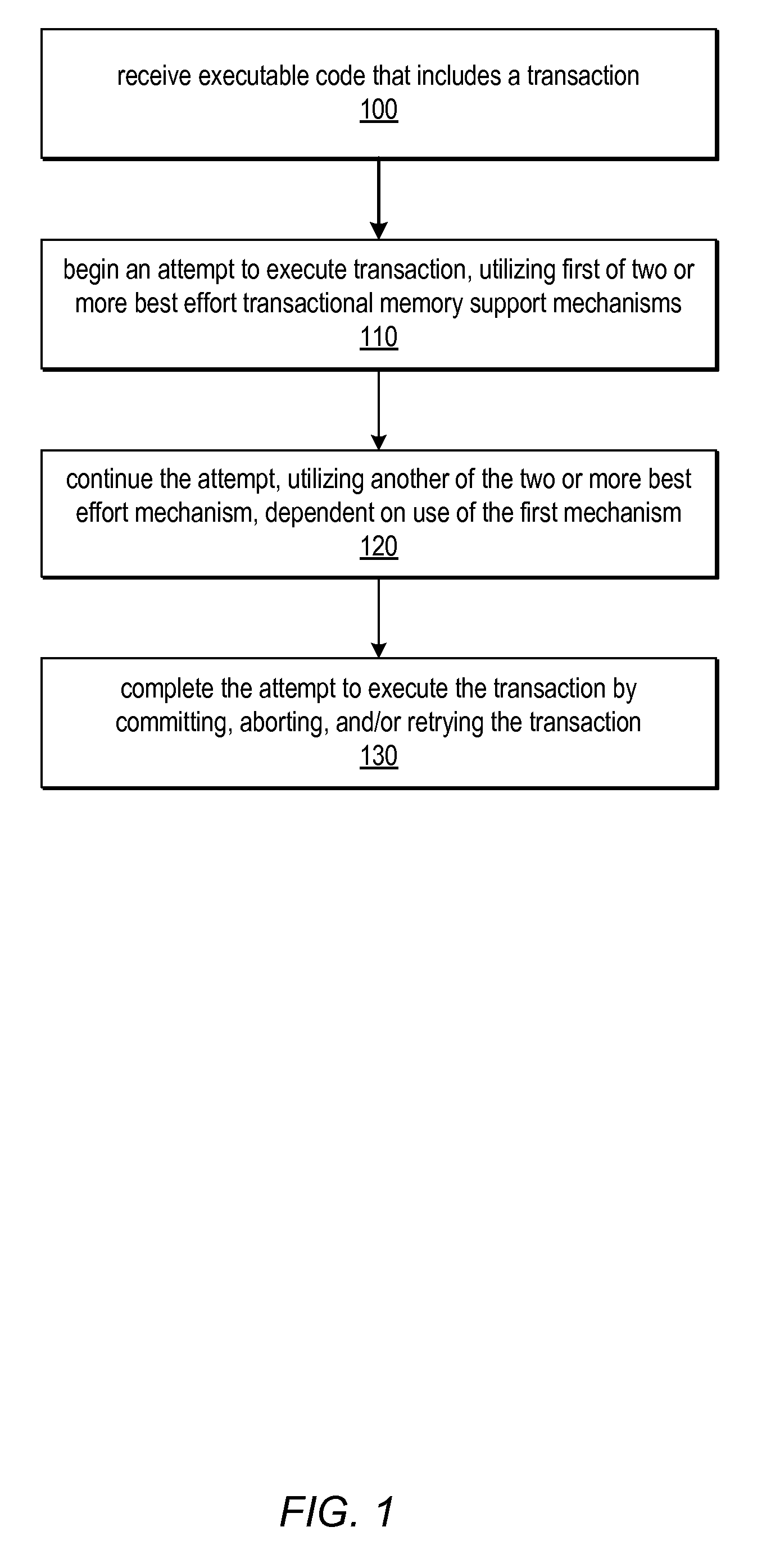
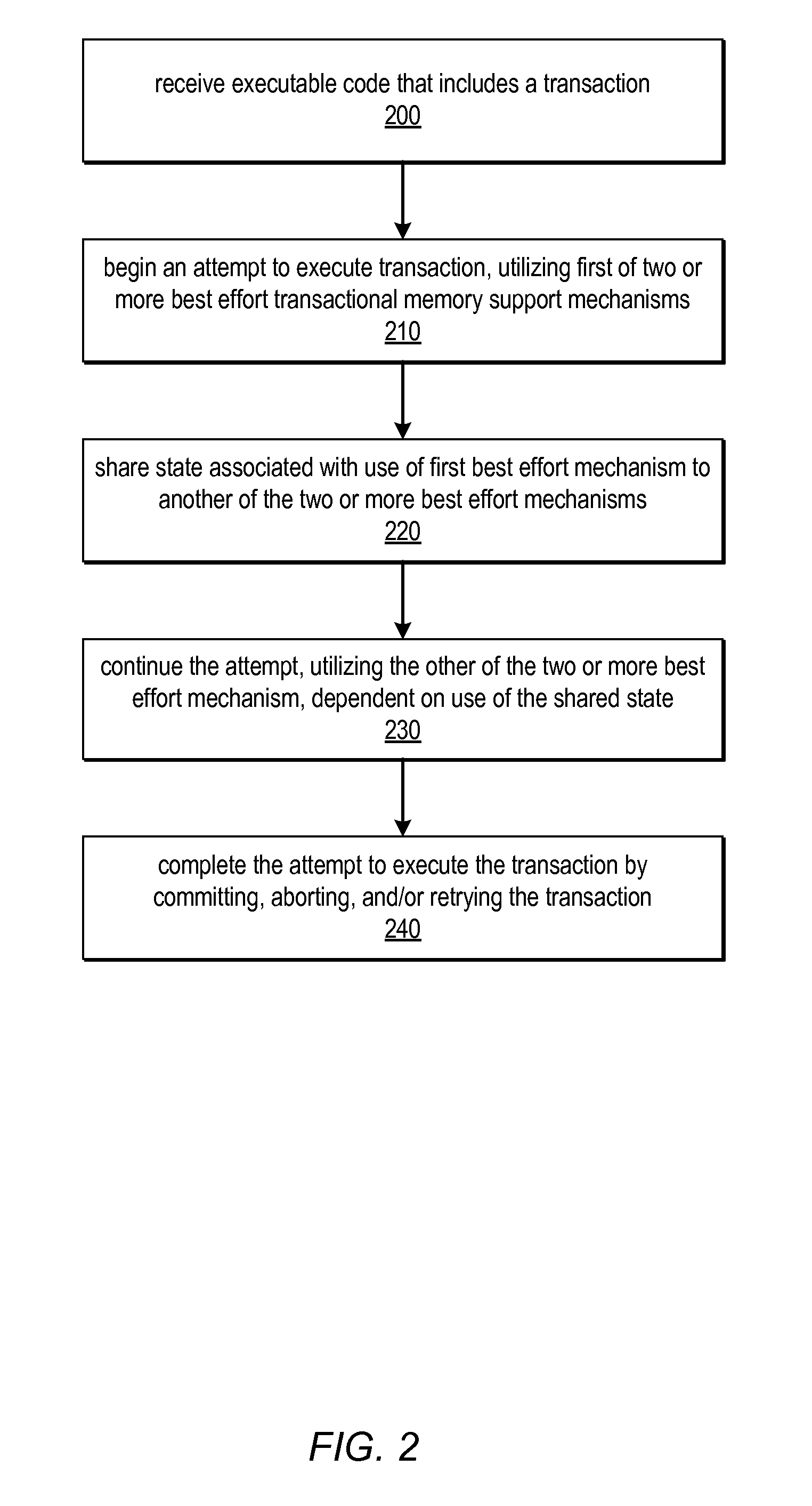
System and Method for Utilizing Available Best Effort Hardware Mechanisms for Supporting Transactional Memory
ActiveUS20090282386A1Reduce difficultyReduce overheadMemory systemsSpecific program execution arrangementsTransactional memoryApplication software
Systems and methods for managing divergence of best effort transactional support mechanisms in various transactional memory implementations using a portable transaction interface are described. This interface may be implemented by various combinations of best effort hardware features, including none at all. Because the features offered by this interface may be best effort, a default (e.g., software) implementation may always be possible without the need for special hardware support. Software may be written to the interface, and may be executable on a variety of platforms, taking advantage of best effort hardware features included on each one, while not depending on any particular mechanism. Multiple implementations of each operation defined by the interface may be included in one or more portable transaction interface libraries. Systems and / or application software may be written as platform-independent and / or portable, and may call functions of these libraries to implement the operations for a targeted execution environment.
Owner:ORACLE INT CORP
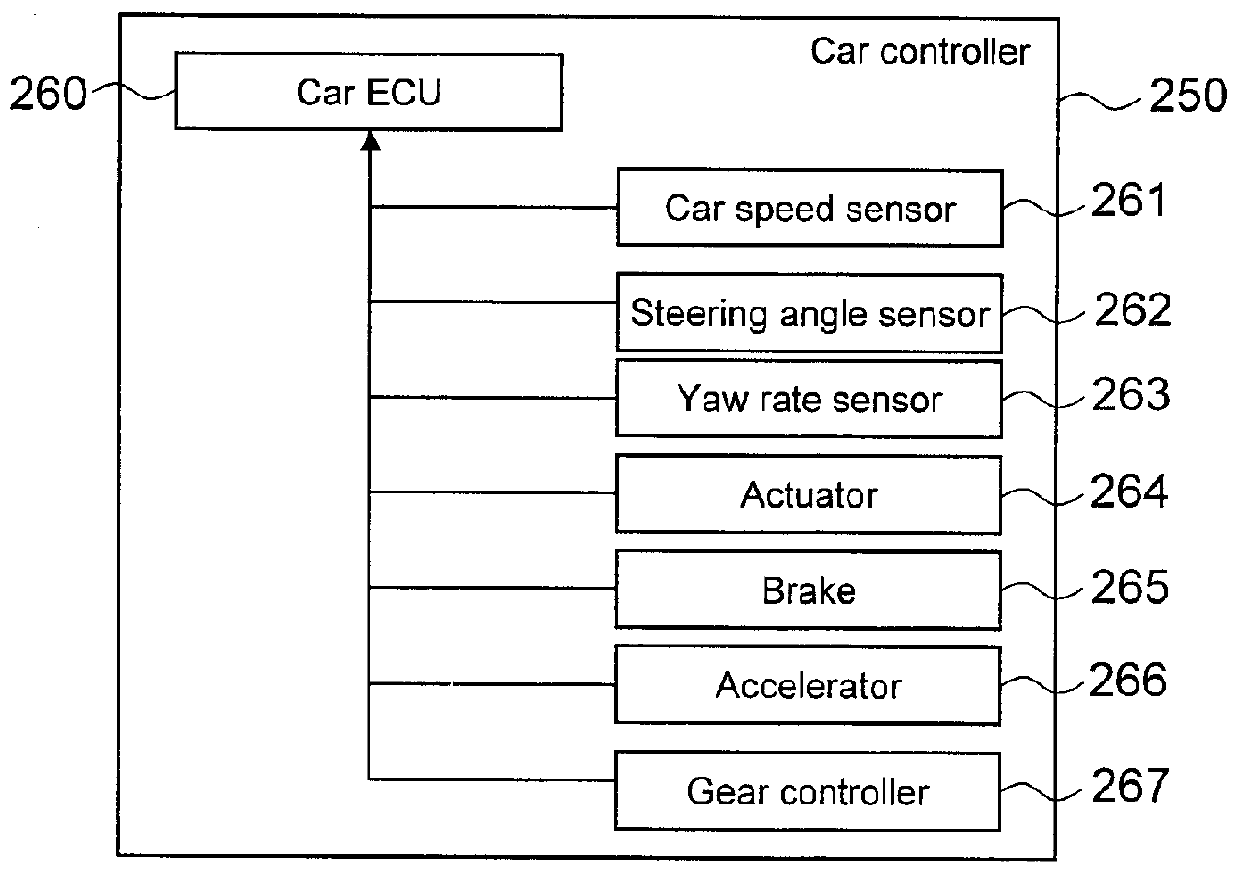
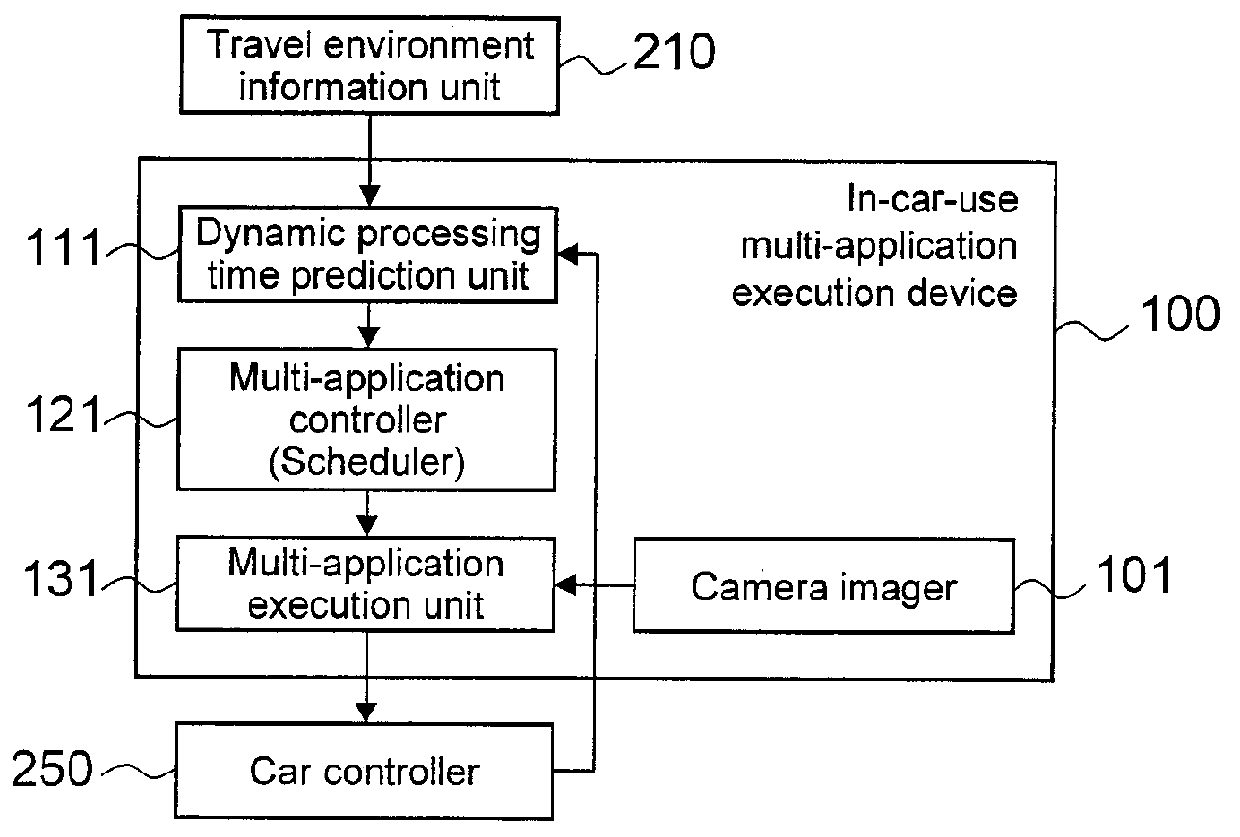
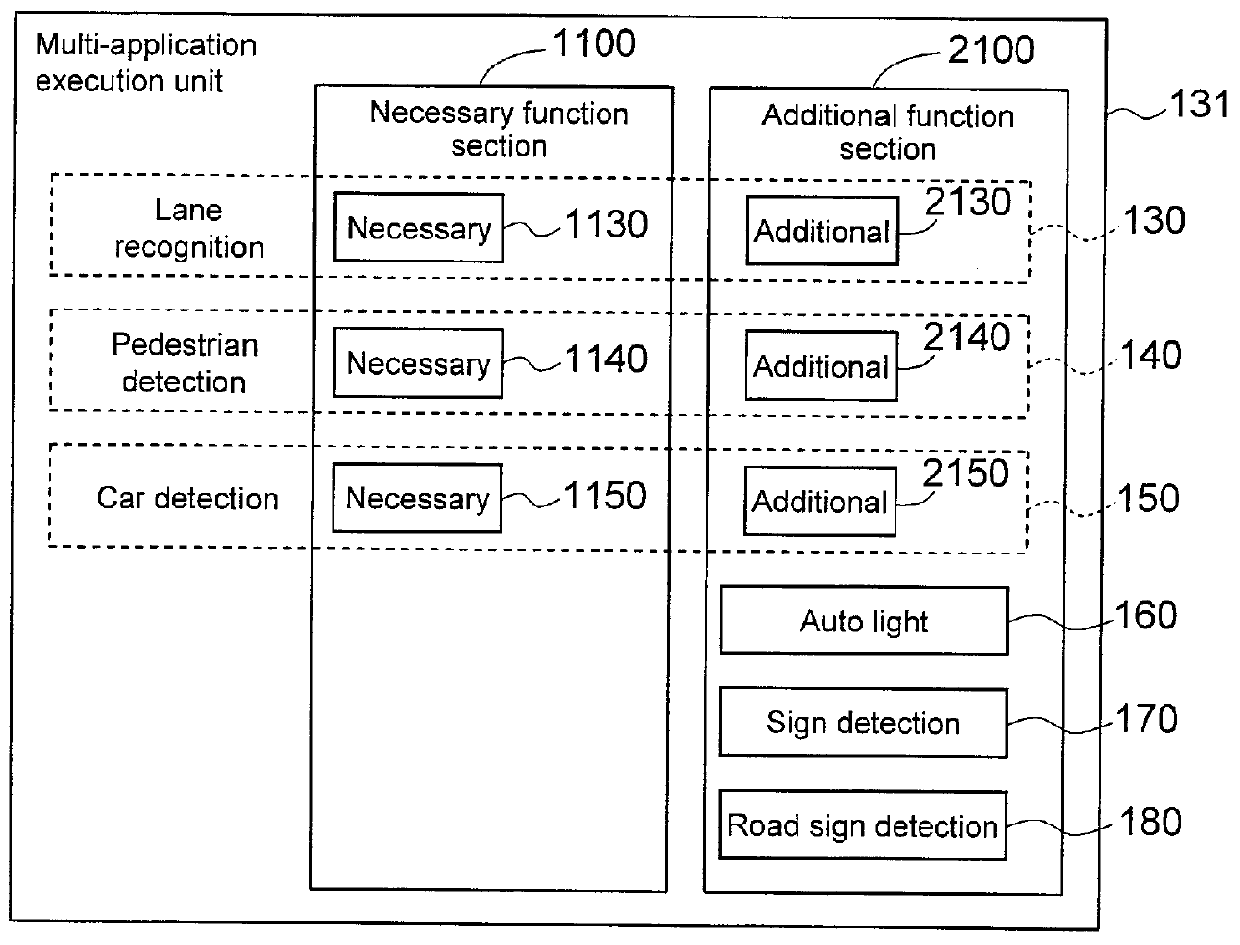
In-Car-Use Multi-Application Execution Device
ActiveUS20120216208A1Limited processing capabilitiesEnsure safetyProgram initiation/switchingRoad vehicles traffic controlApplication softwareOperating system
Owner:HITACHI ASTEMO LTD
Method for calling application object out and mobile terminal
InactiveCN102799361ADigital data processing detailsInput/output processes for data processingApplication softwareApplication object
Owner:HUAWEI DEVICE CO LTD
Systems and Methods for Remotely Controlling and Customizing Applications Resident on a Mobile Device
Owner:APPLE INC
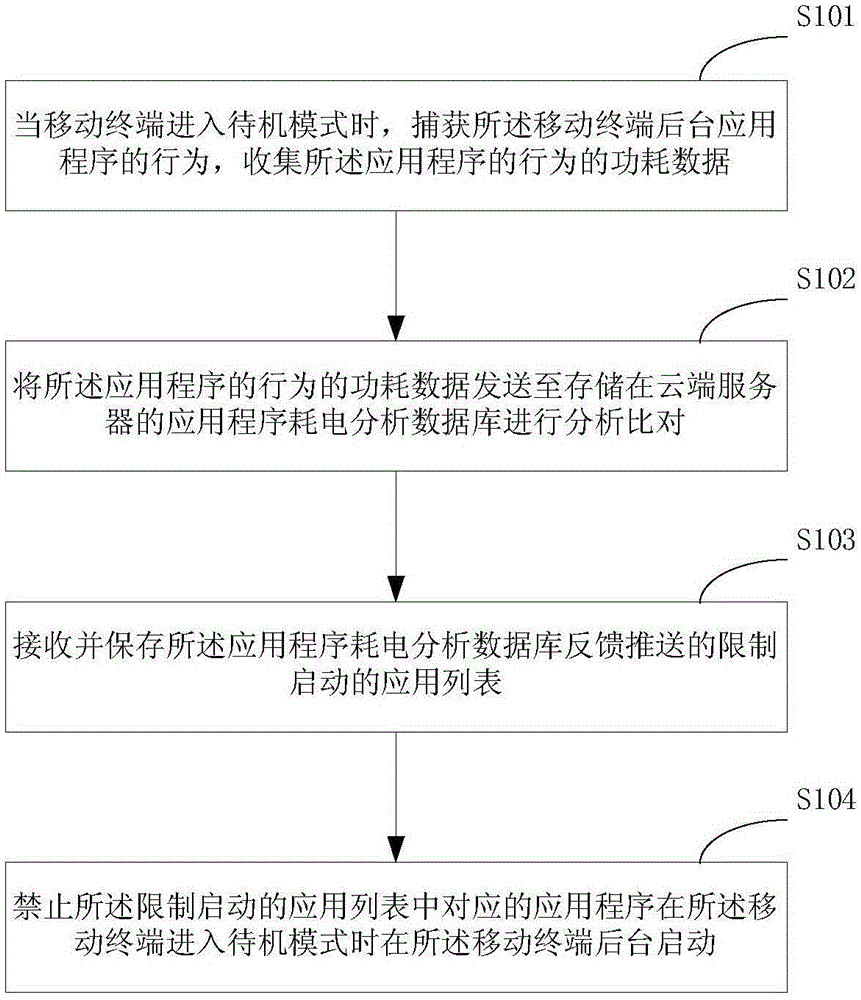
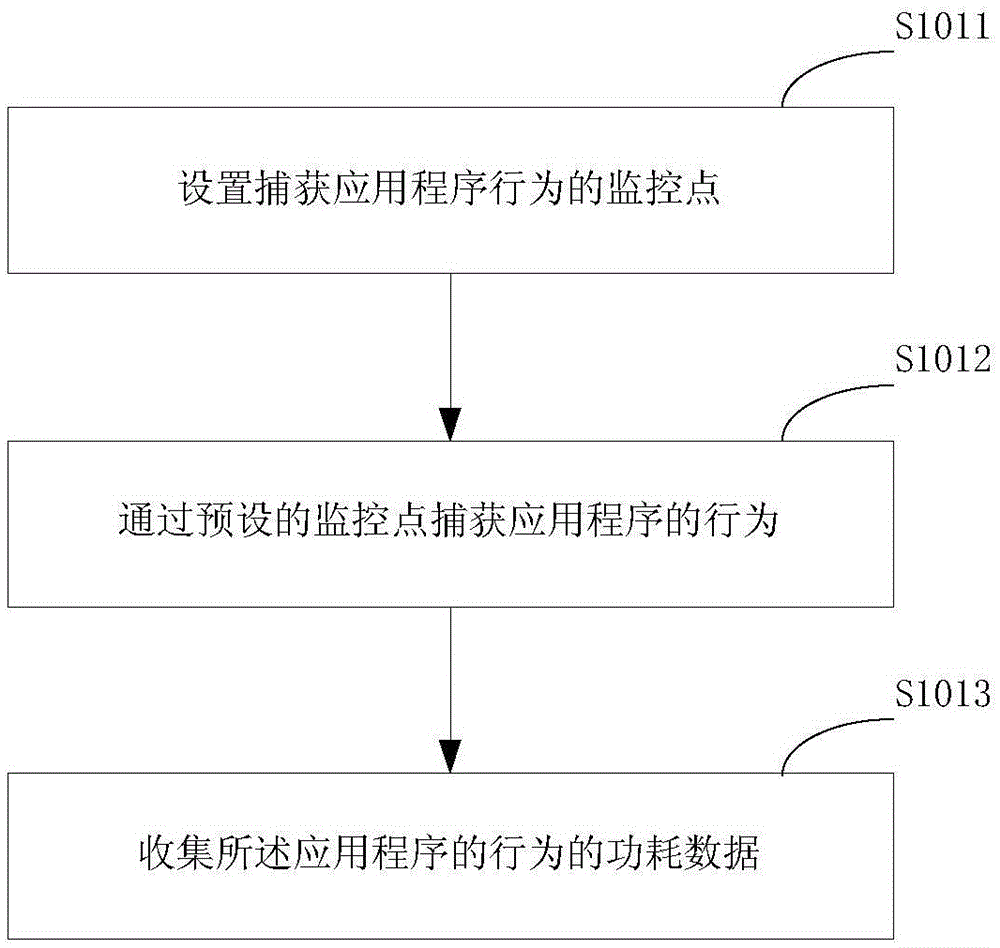
Method for reducing power consumption of device, mobile terminal and system
ActiveCN105159816AReduce power consumptionImprove battery lifeHardware monitoringCurrent supply arrangementsTerminal equipmentComputer terminal
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
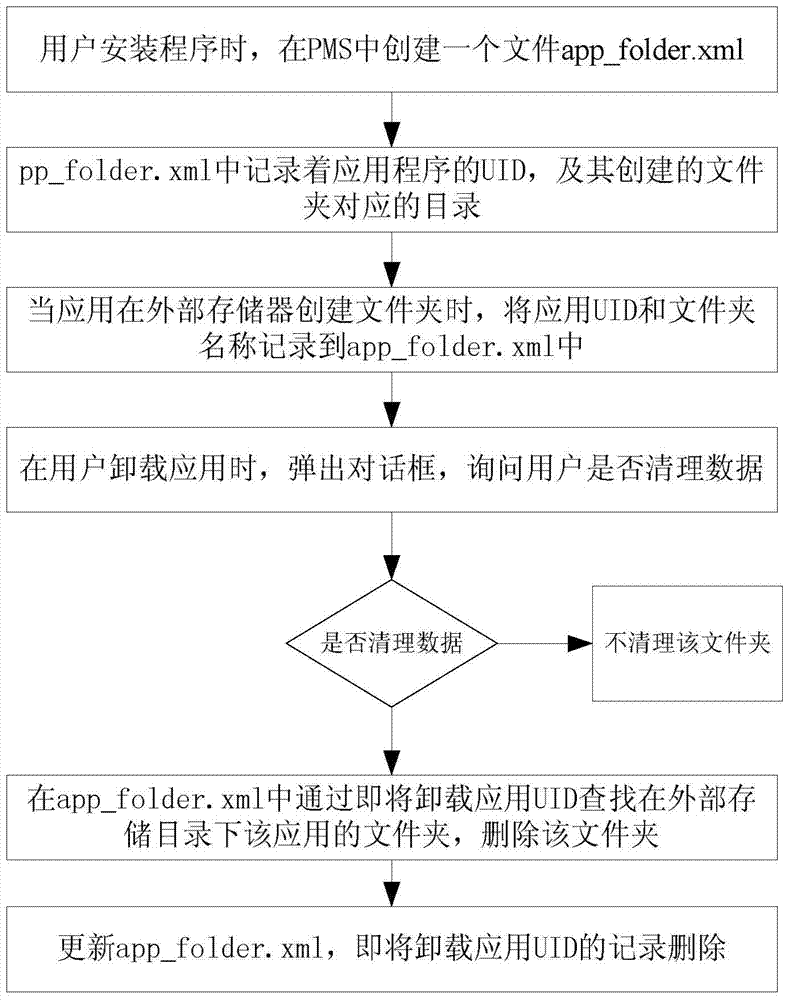
Method for uninstalling application and deleting garbage file in Android system
InactiveCN103577567AClean up in timeRapid positioningSpecific program execution arrangementsSpecial data processing applicationsExternal storagePackage management
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
System having generalized client-server computing
InactiveUS7320027B1Good communication privacyReduce traffic problemsMultiple digital computer combinationsTransmissionApplication softwareClient-side
Owner:AMERICAN TELEPHONE & TELEGRAPH CO +1
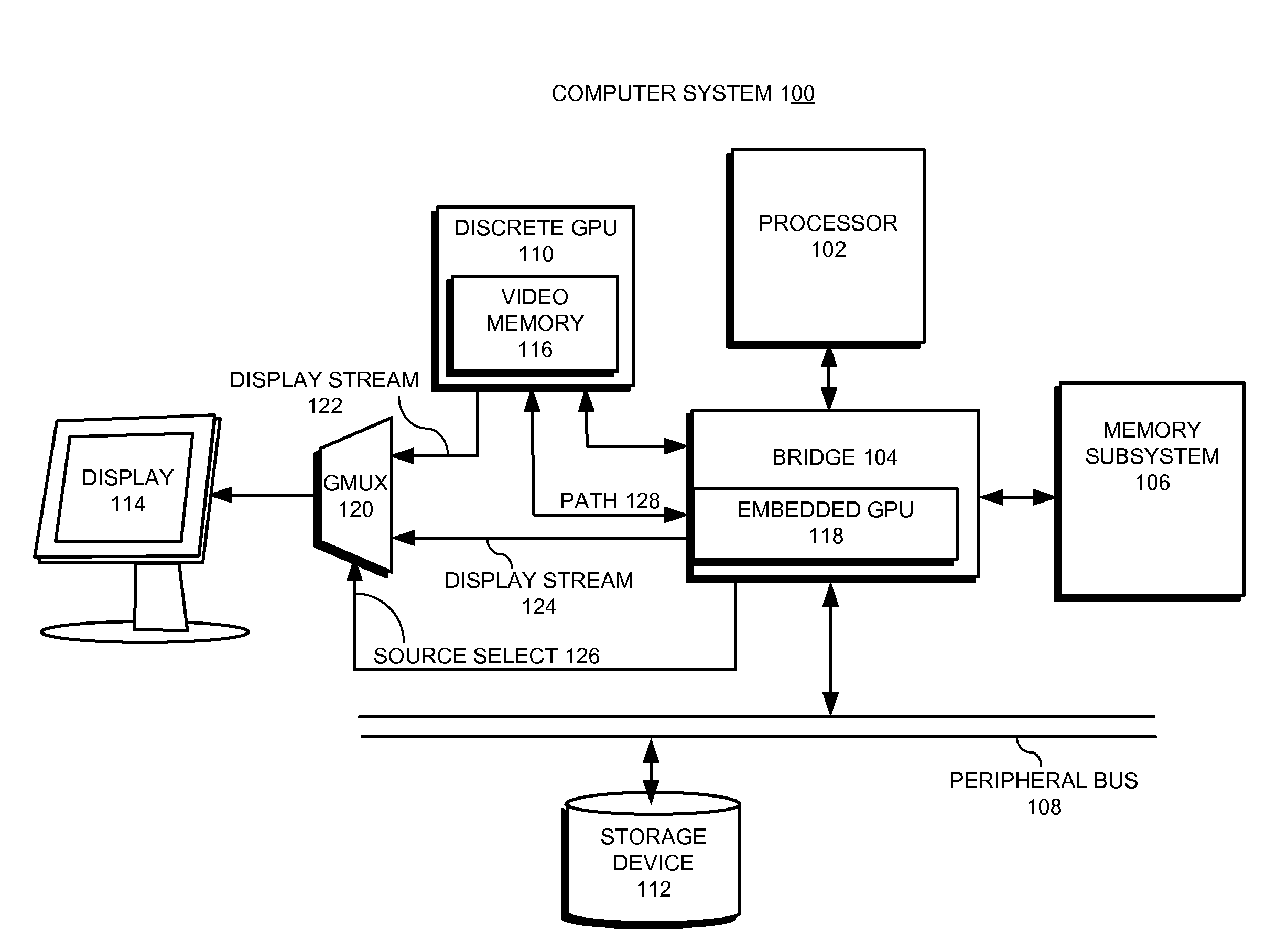
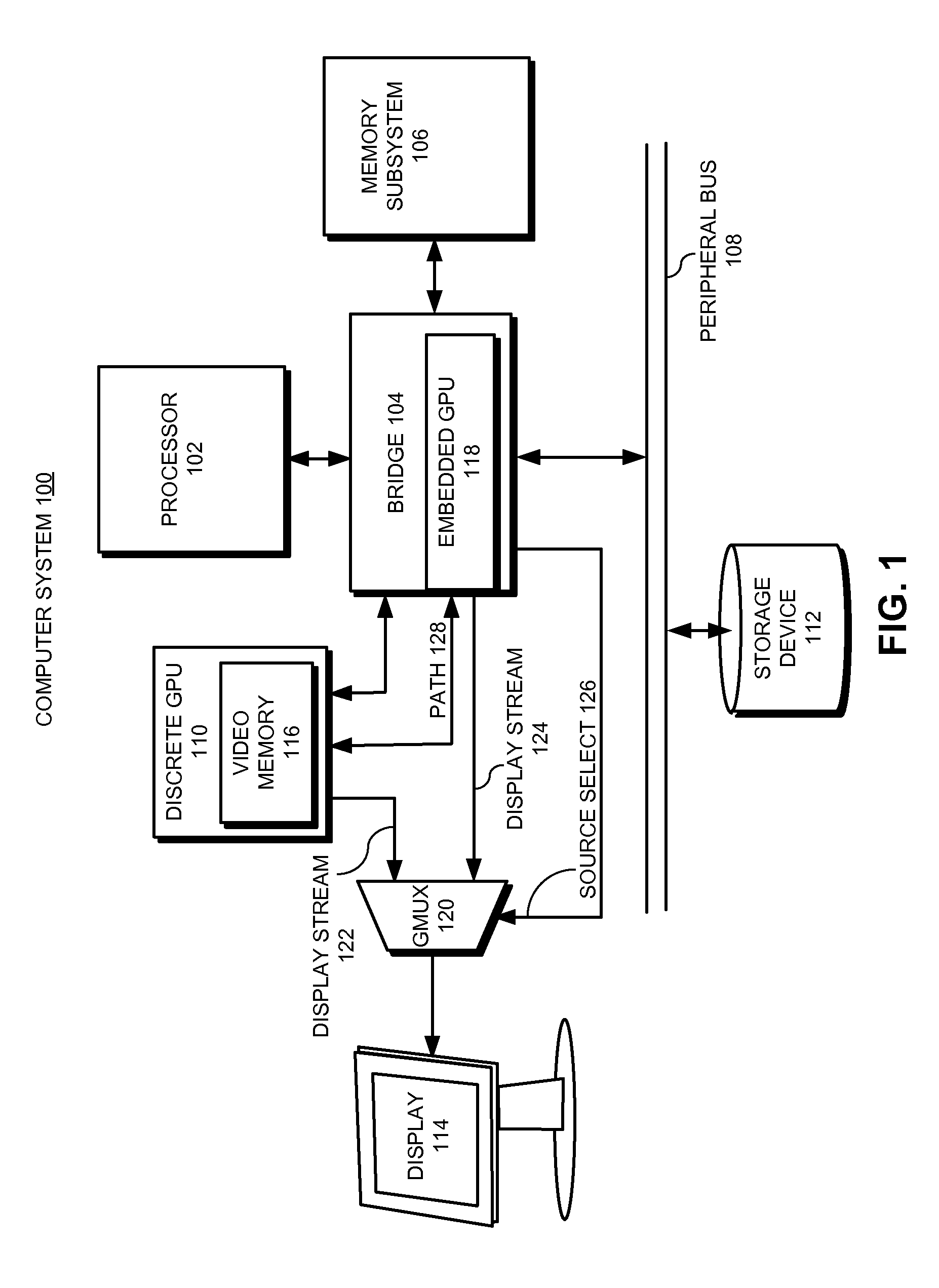
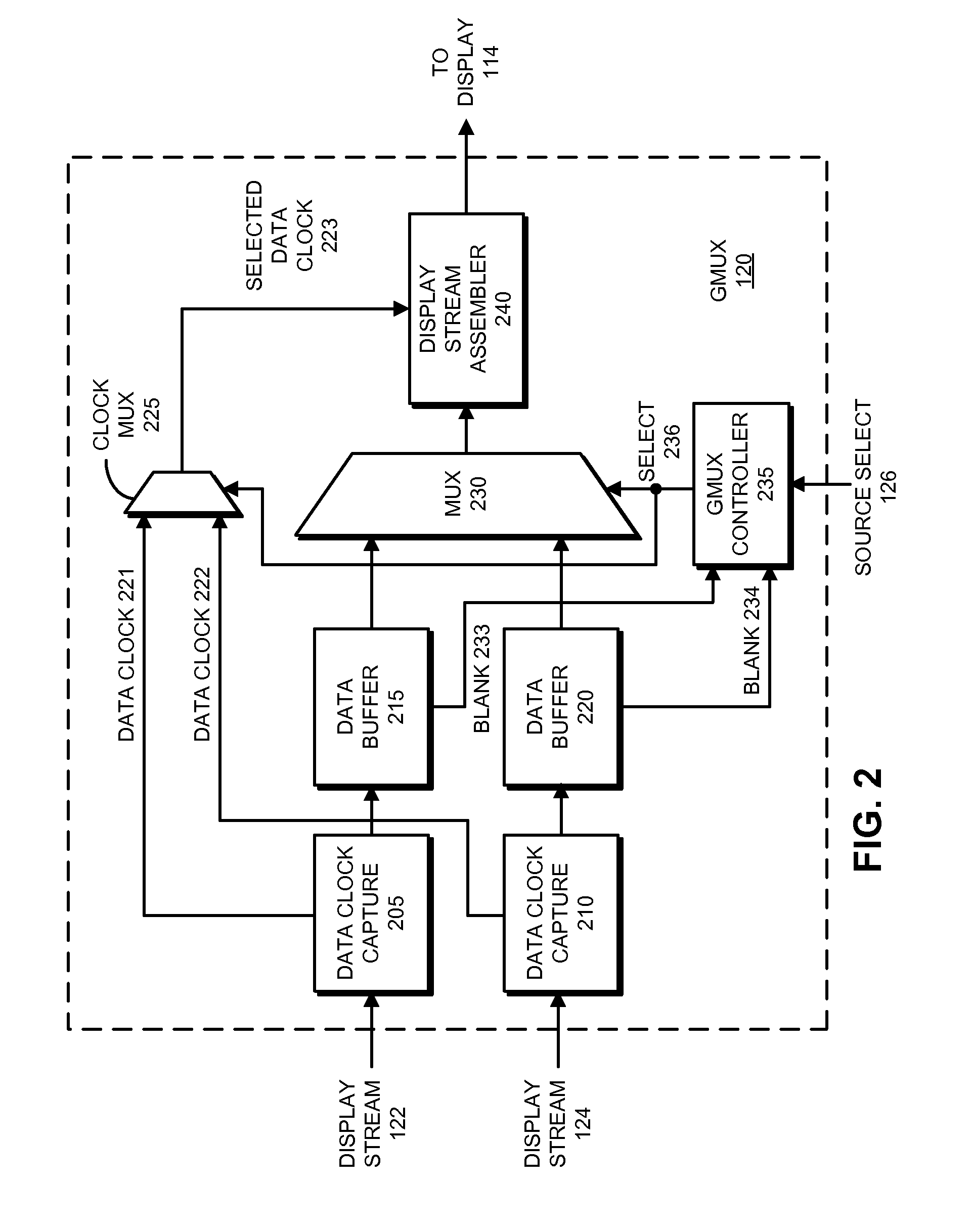
Facilitating atomic switching of graphics-processing units
InactiveUS20120092351A1Configure on switchCathode-ray tube indicatorsProgram controlGPU switchingComputational science
Owner:APPLE INC
Spontaneous Player Preferences
ActiveUS20110250960A1Cathode-ray tube indicatorsMultiple digital computer combinationsData transmissionApplication software
Owner:ARISTOCRAT TECH INC ATI
Memory test method, tested terminal, test client and system
ActiveCN106557424AImprove performanceImprove optimization efficiencySoftware testing/debuggingClient-sideApplication software
Owner:TENCENT TECH (SHENZHEN) CO LTD
Distributed processing system, method of the same
InactiveUS7031944B2Increase valueResource allocationMultiple digital computer combinationsApplication serverComputer terminal
Owner:NEC CORP
Browsing or searching user interfaces and other aspects
ActiveUS20090307306A1Multiple digital computer combinationsFile metadata searchingClient-sideApplication software
Owner:APPLE INC
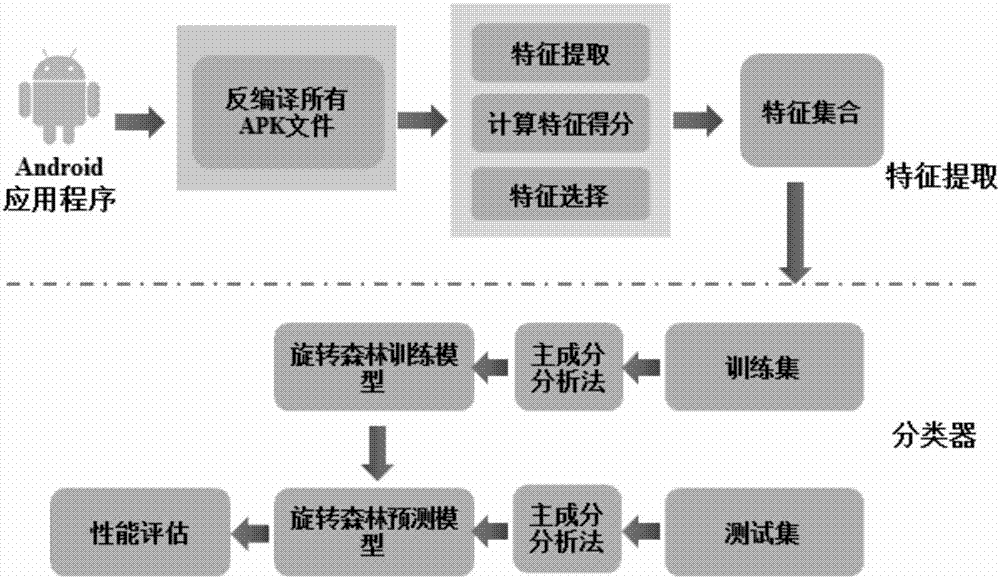
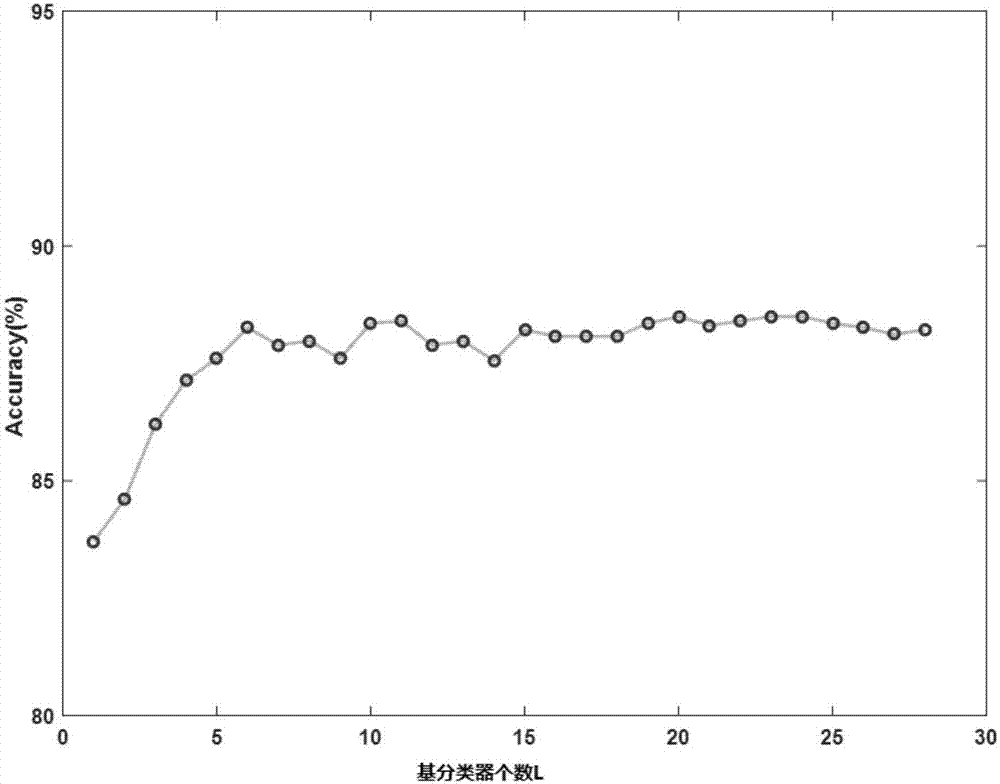
Efficient Android malware detection model DroidDet based on rotating forest
InactiveCN106919841AEfficient detectionImprove scalabilityPlatform integrity maintainanceSupport vector machine svm classifierApplication software
Owner:XIJING UNIV
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap