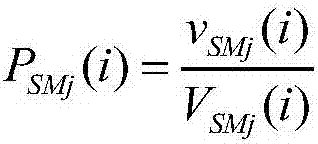Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
129results about "Digital data protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
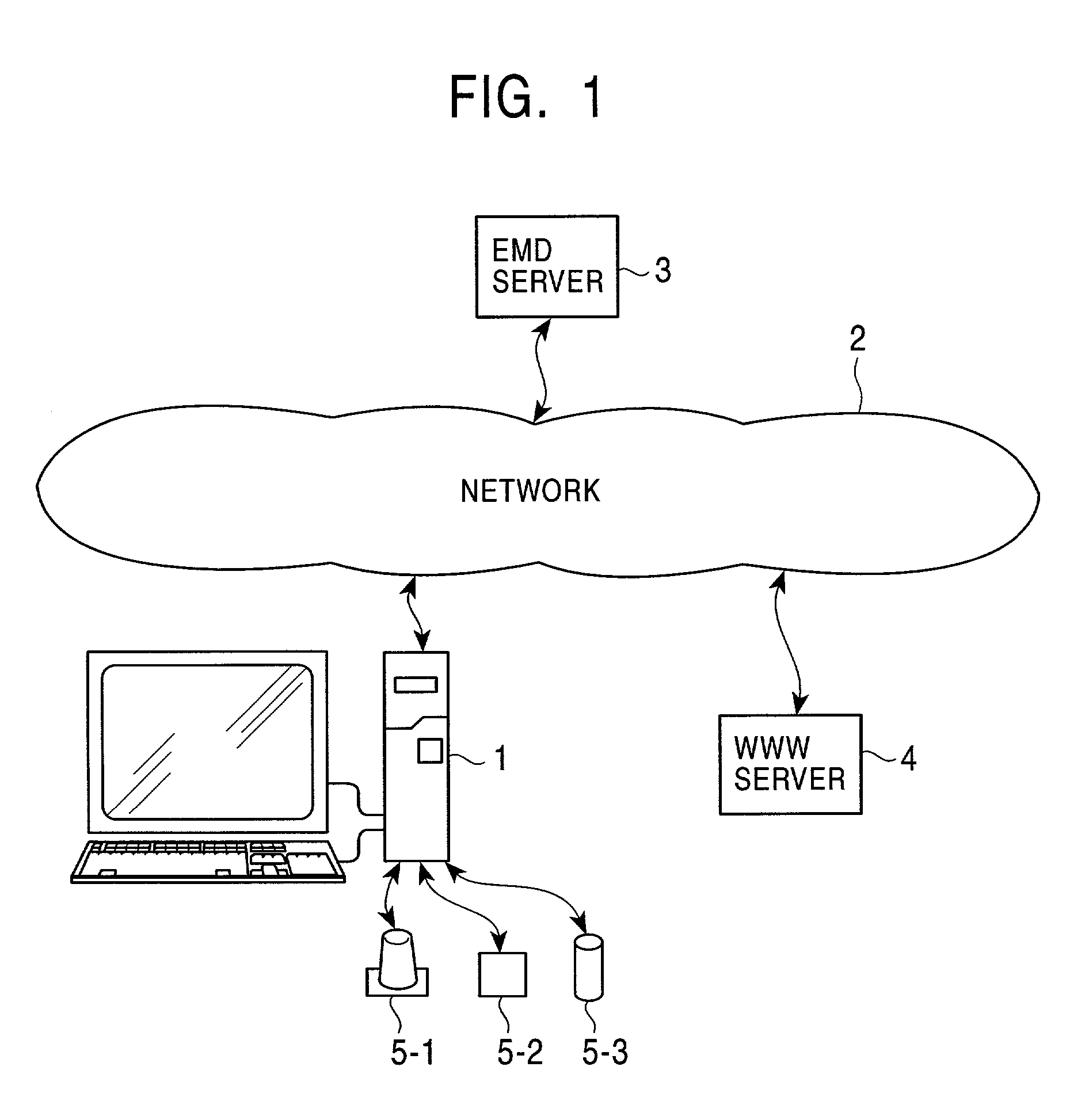
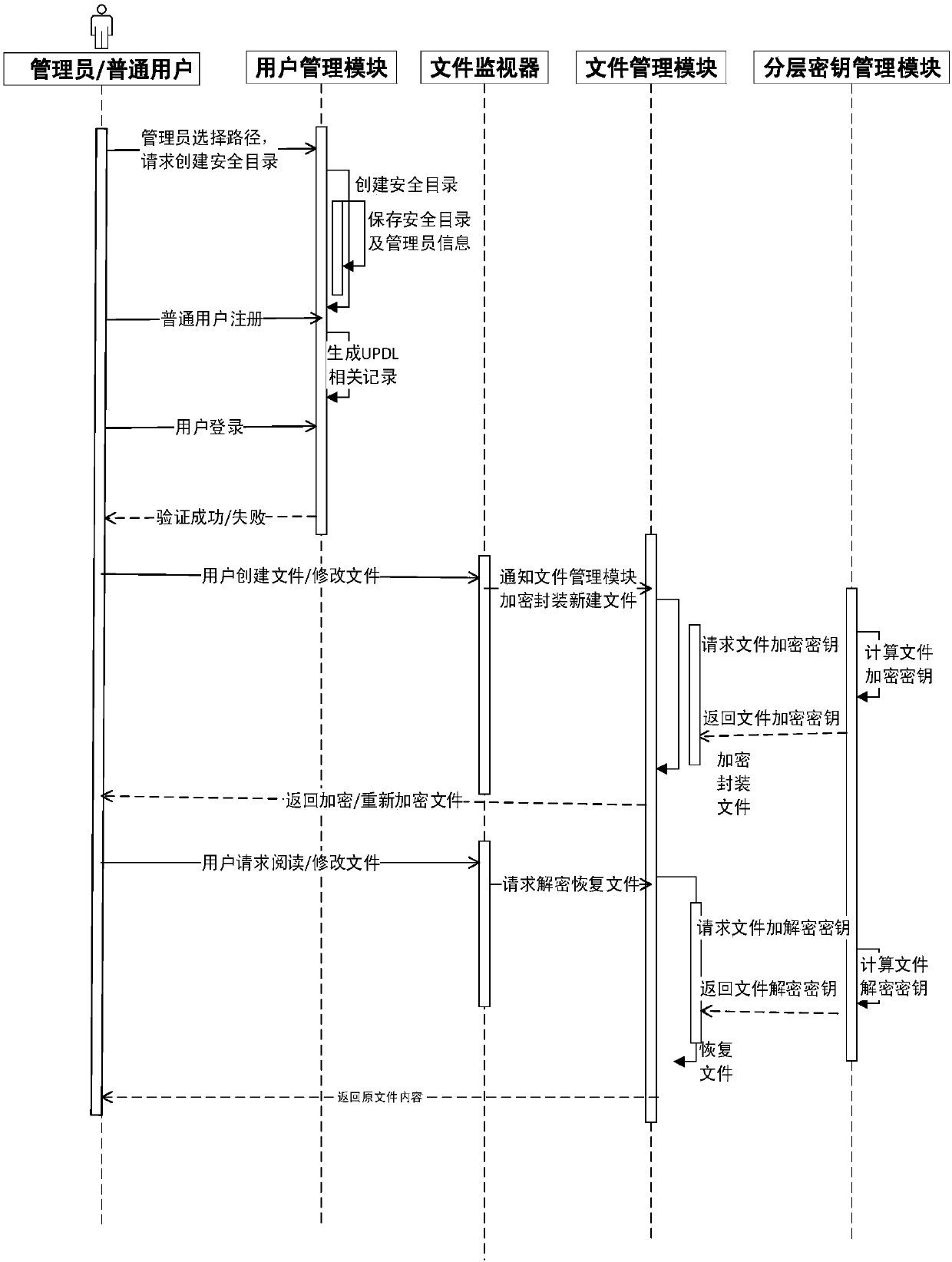
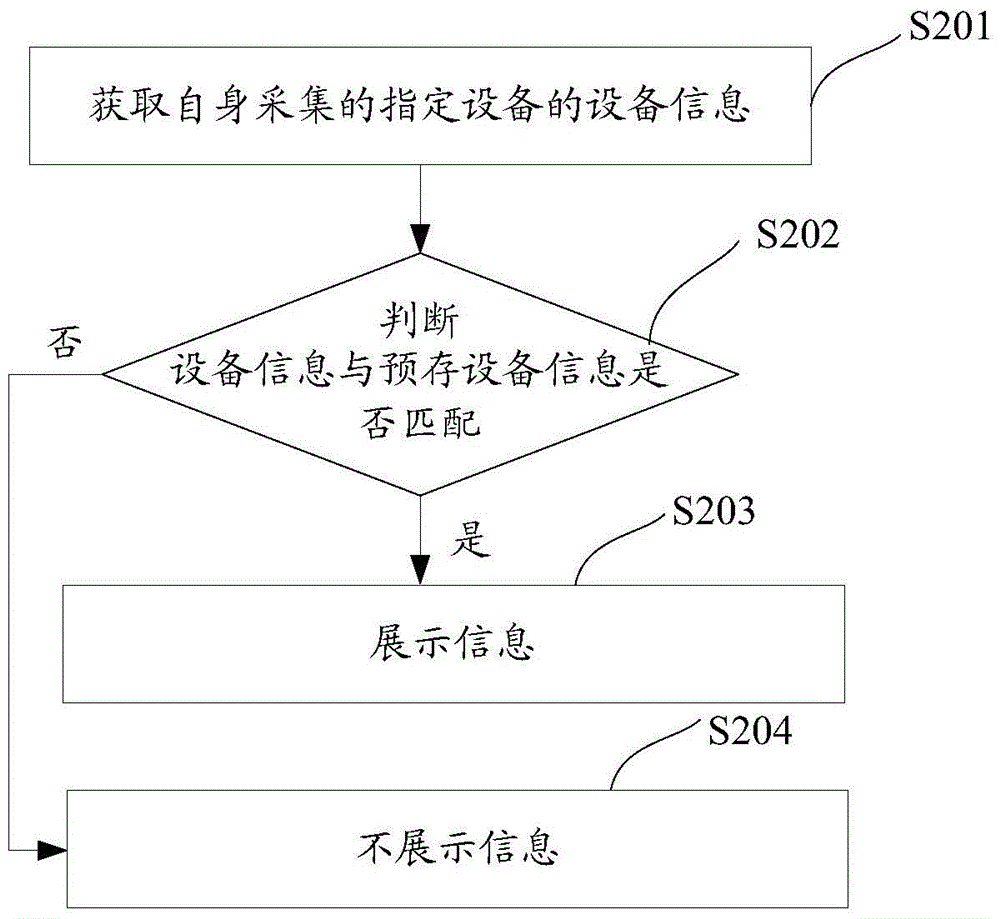
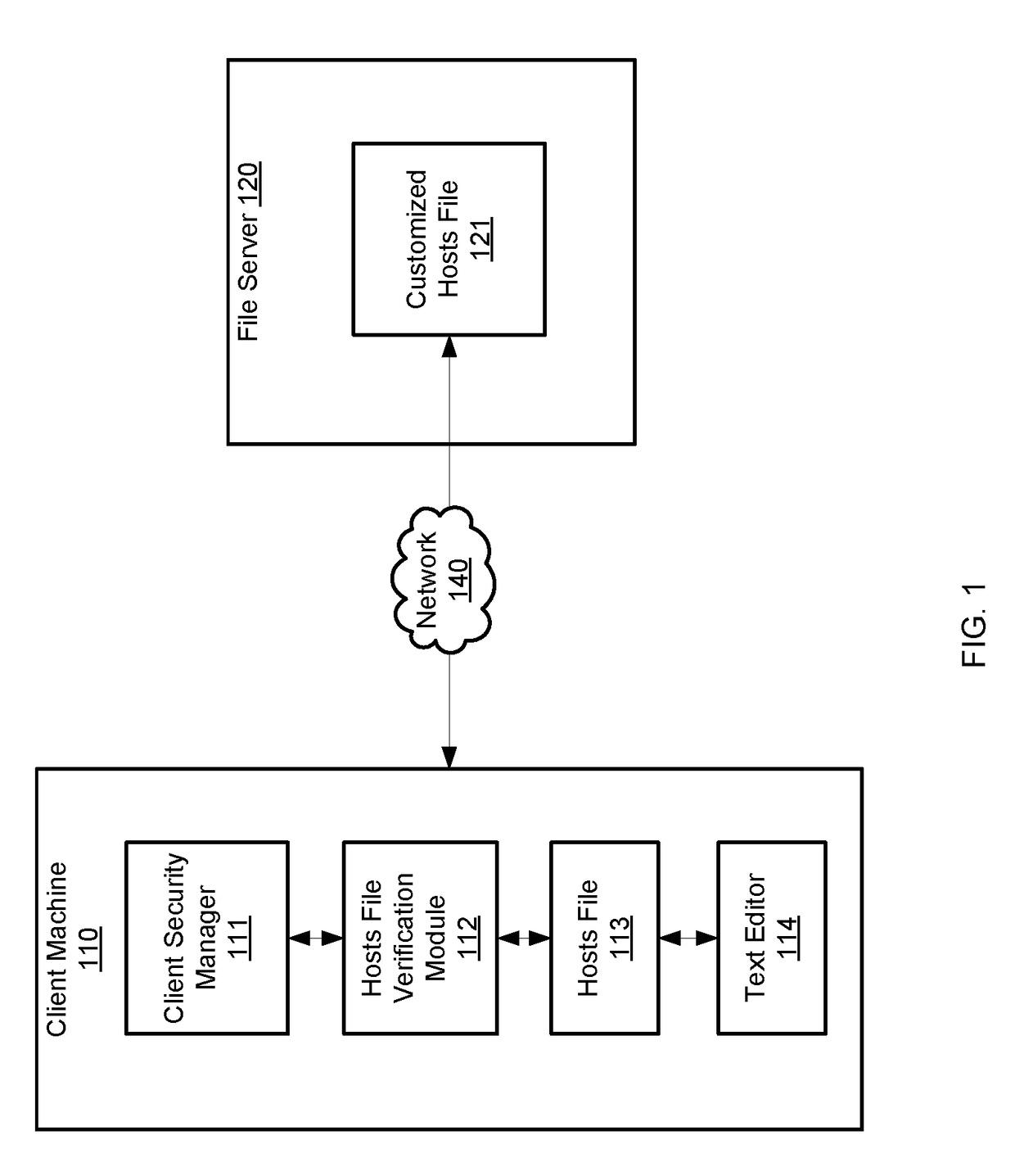
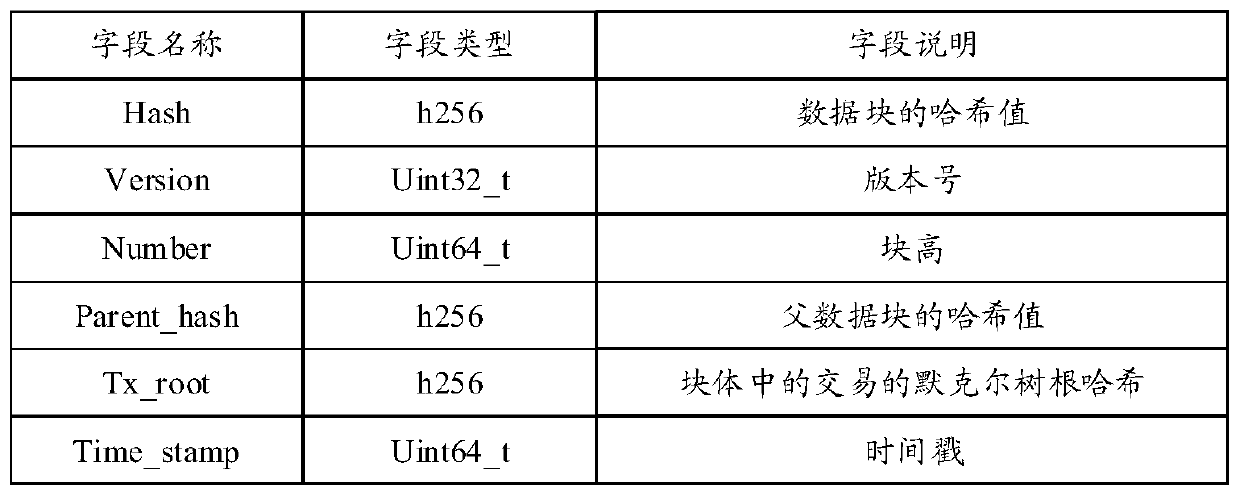
Method and apparatus for data retention in a storage system
ActiveUS20050125411A1Digital data information retrievalMemory loss protectionRetention periodSoftware engineering
A system and method are provided for retention of data on a storage system. An application program provides the storage system with data to be stored on the storage system. The application program also provides the storage system with a retention period that indicates a period of time for which the data may not be deleted. When the storage system receives a request to delete the data, it first evaluates the retention period associated with that data to determine if the retention period has expired. If the retention period has not expired, the storage system denies the request to delete the data.
Owner:EMC IP HLDG CO LLC
Screen projection method, system and related device
InactiveCN110221798ADigital data protectionCathode-ray tube indicatorsUser needsLarge screen display
Owner:HUAWEI TECH CO LTD
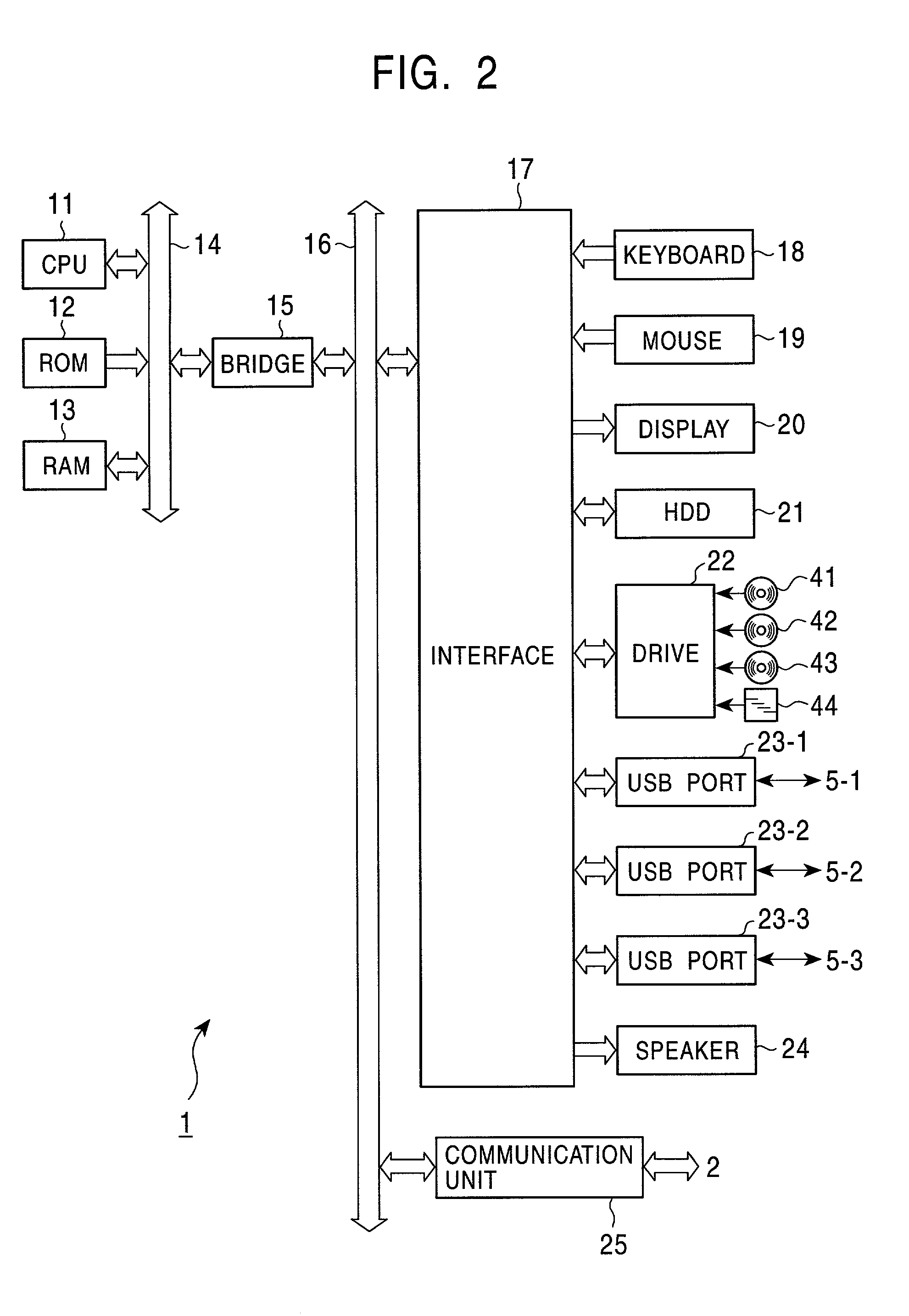
Information processing apparatus and method, and program storing medium
InactiveUS7478437B2Disc-shaped record carriersDigital data processing detailsInformation processingComputer science
Owner:SONY CORP
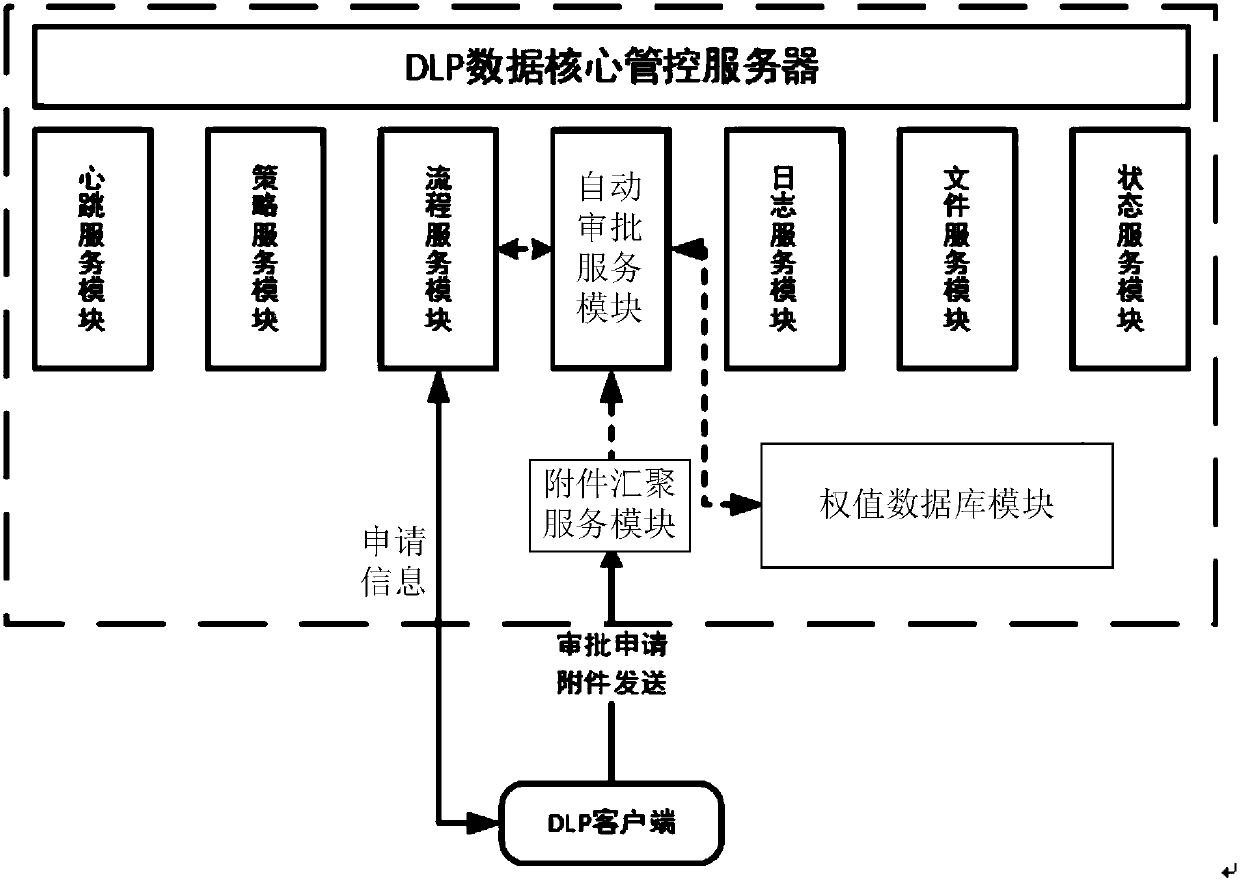
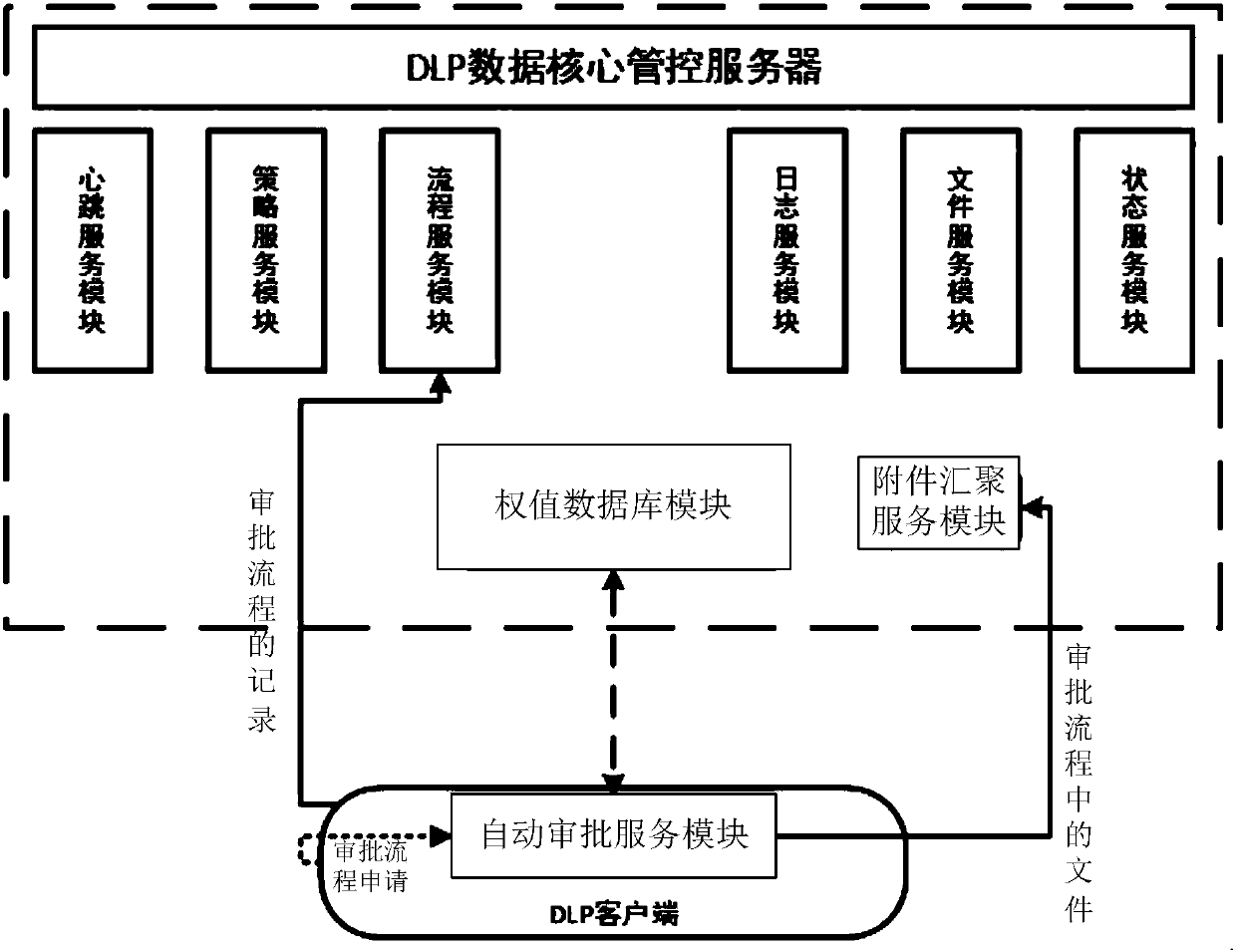
Task approval method and system of data leakage prevention system
InactiveCN107633380ARealize fully automatic approvalPrevent leakageDigital data protectionOffice automationDocumentationComputer science
Owner:北京明朝万达科技股份有限公司
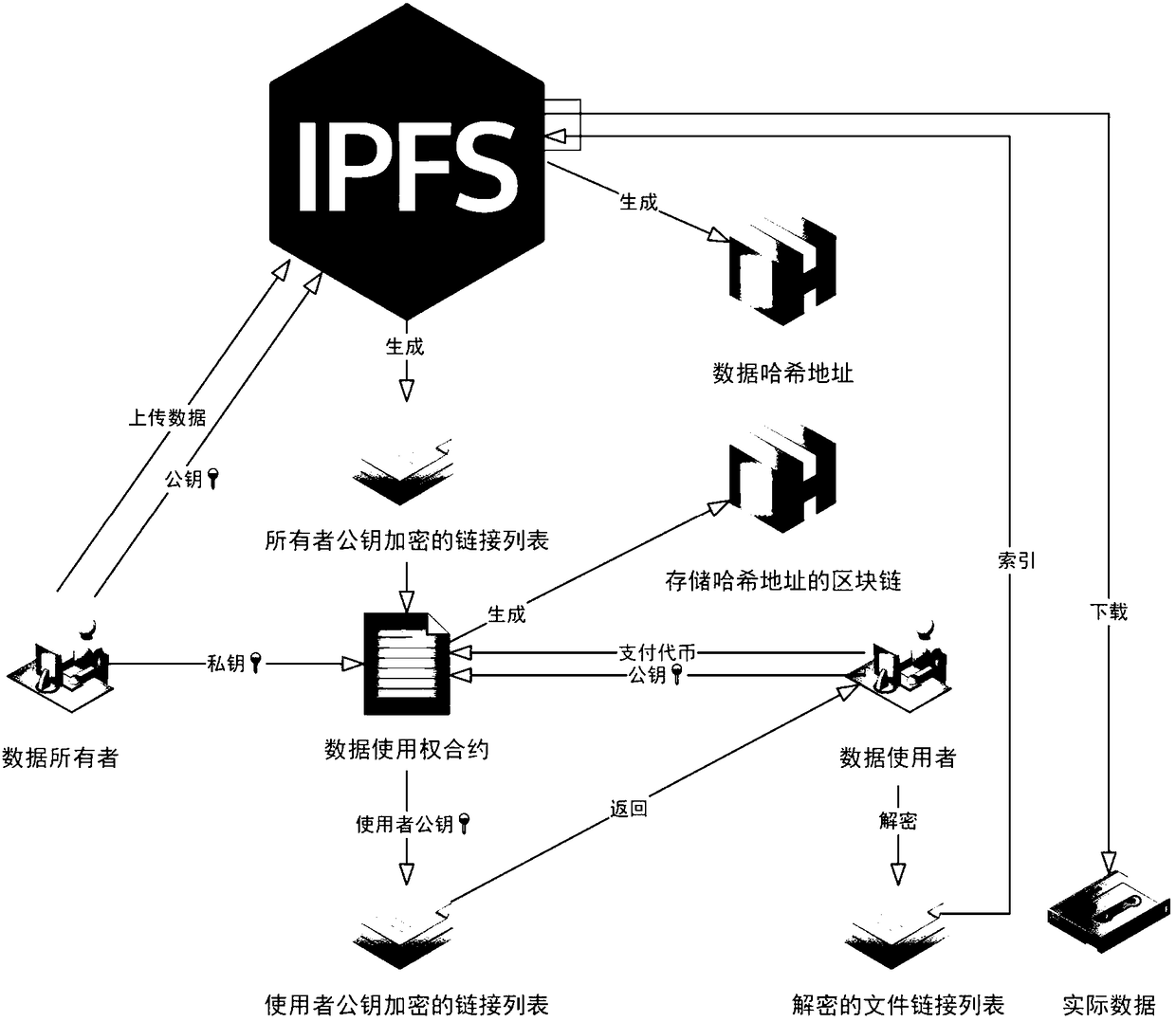
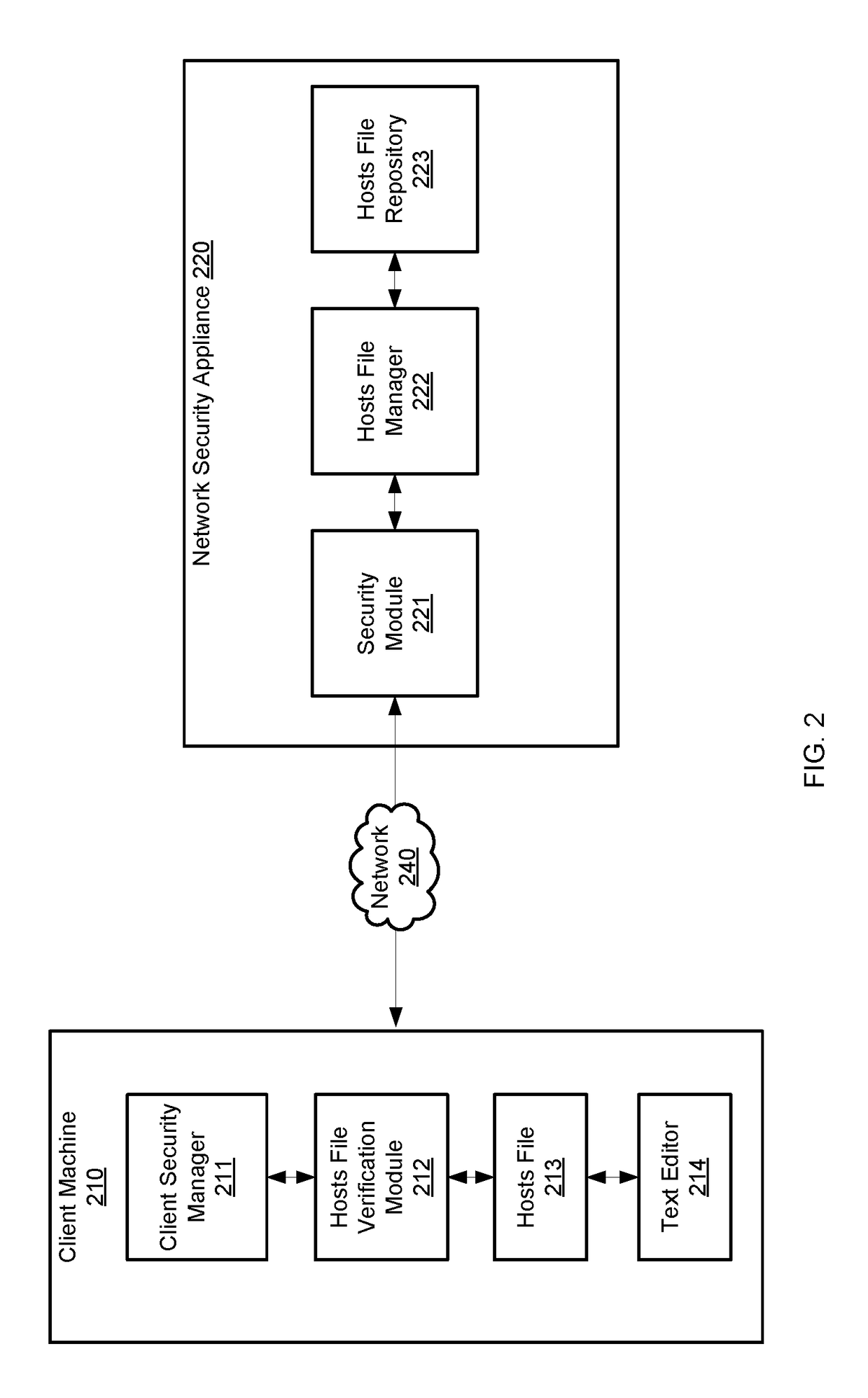
Method and equipment for medical image data decentralized management based on block chain
Owner:上海全景医学影像诊断中心有限公司
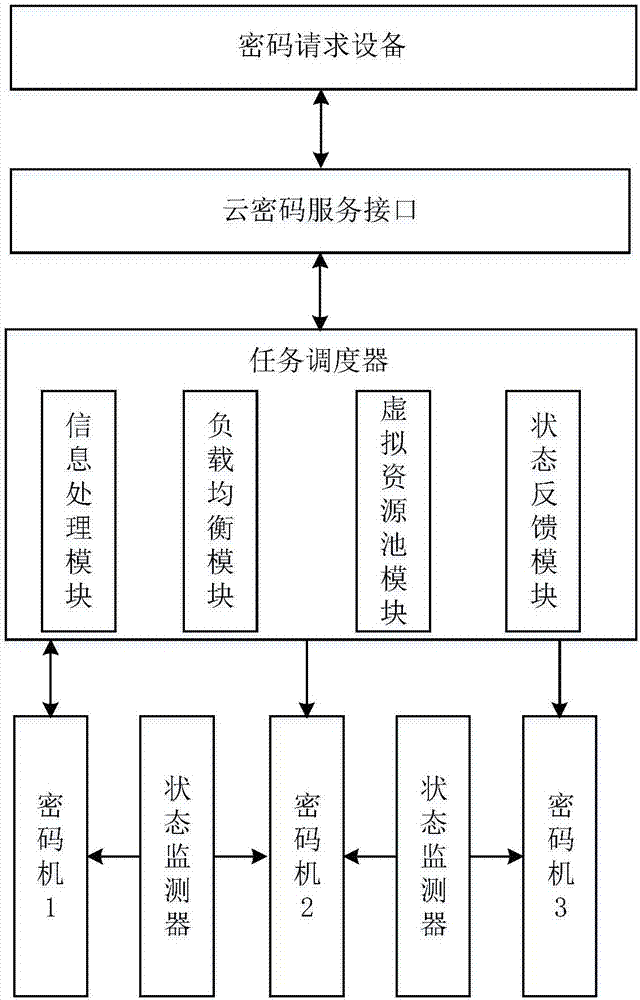
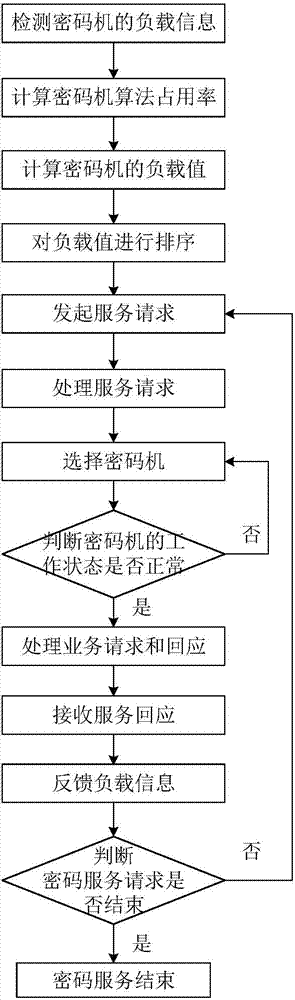
System and method for providing cryptographic service through virtual cryptographic equipment cluster
ActiveCN107040589ARealize dynamic managementOvercome underutilizationResource allocationDigital data protectionOccupancy rateVirtualization
Owner:XIDIAN UNIV
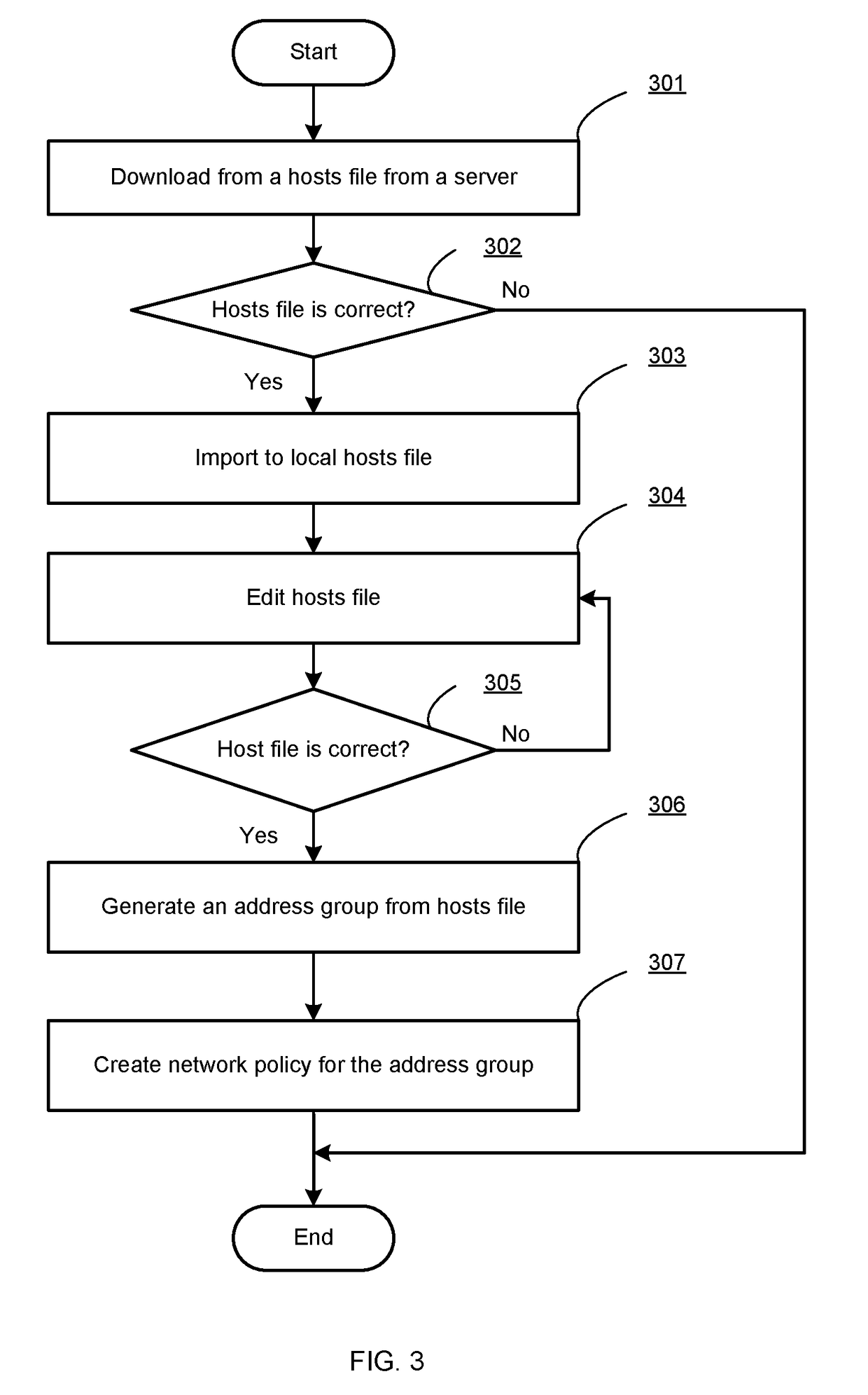
(k,n) threshold based user-friendly visual secret sharing method
ActiveCN105404817AImprove the range of image applicationsIncrease contrastDigital data protectionGray levelHistogram equalization
The invention discloses a (k,n) threshold based user-friendly visual secret sharing method and mainly solves the problems of low security and contrast in the prior art. The method is implemented by the steps of 1, performing (k,n) random grid processing on a binary secret image S to obtain n basic shared images of random grids; 2, performing block segmentation on an input gray cover image by using histogram equalization to obtain a gray level equivalent to the gray level of each small image block; 3, performing halftone processing on the cover image subjected to the block segmentation, and according to a generated dithering matrix, obtaining a shared cover image after the halftone processing; and 4, performing block segmentation on the generated basic shared images and cover image, performing combination according to a stacking ratio of a constant value delta, and performing block segmentation and combination to generate a meaningful final shared image. According to the method, the attack of attackers can be prevented, the meaningful final shared image can be generated, and the application range of visual secret sharing can be extended.
Owner:XIDIAN UNIV
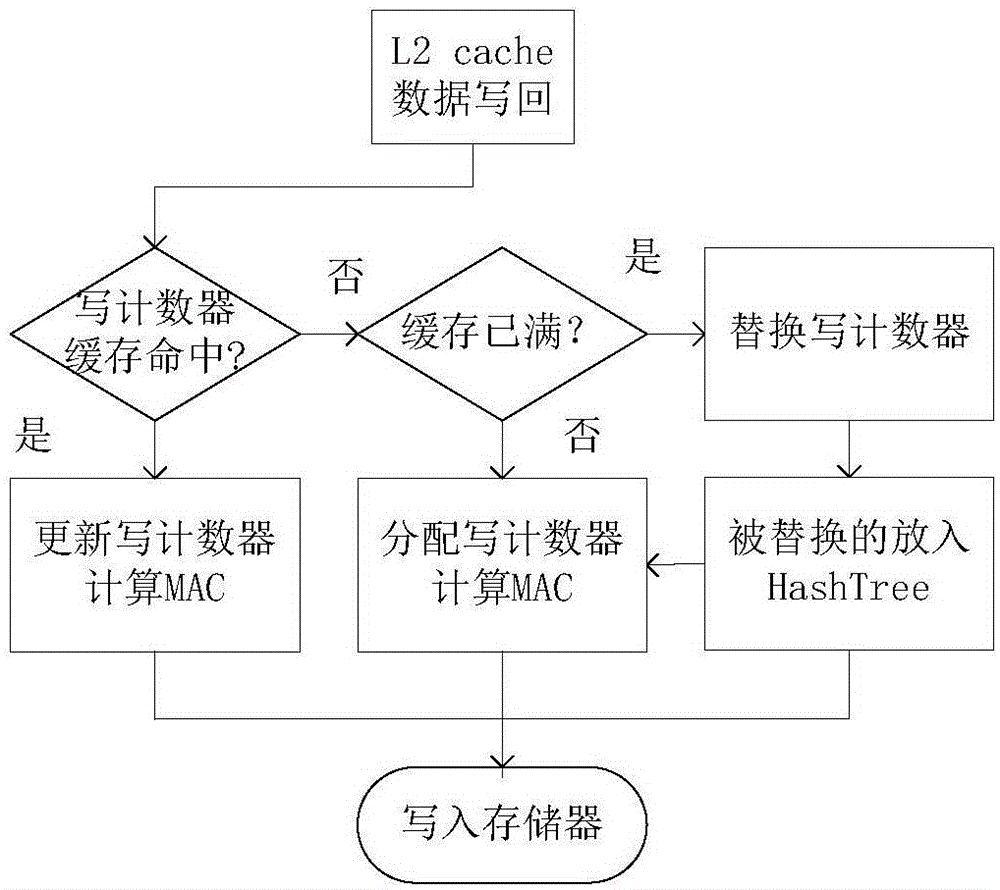
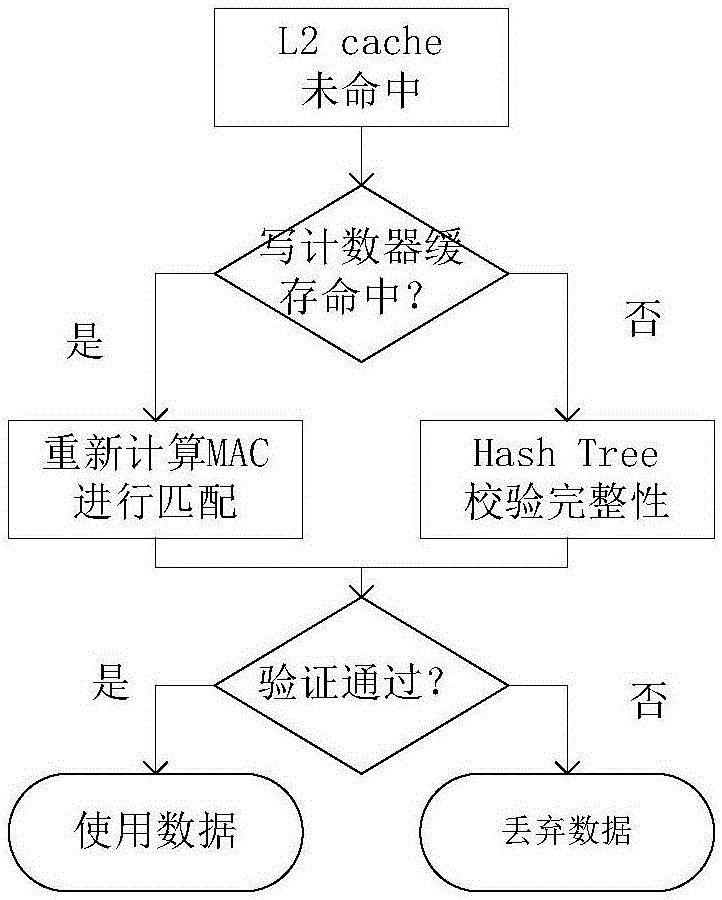
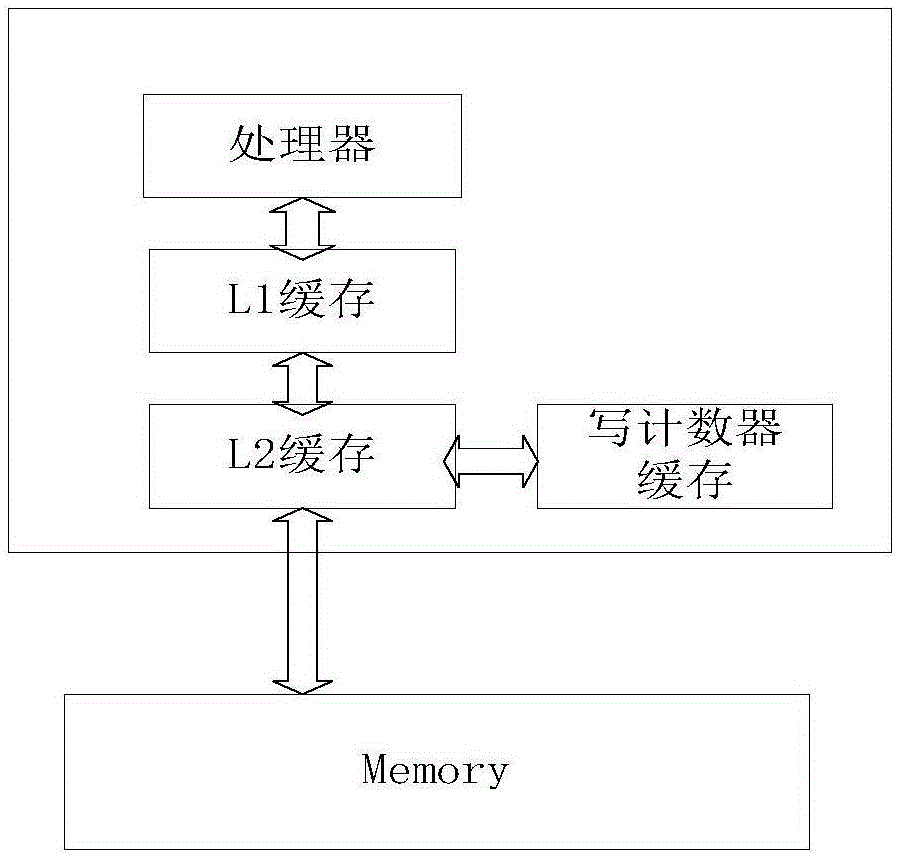
Memory integrity protection method based on write counter
Owner:HARBIN ENG UNIV
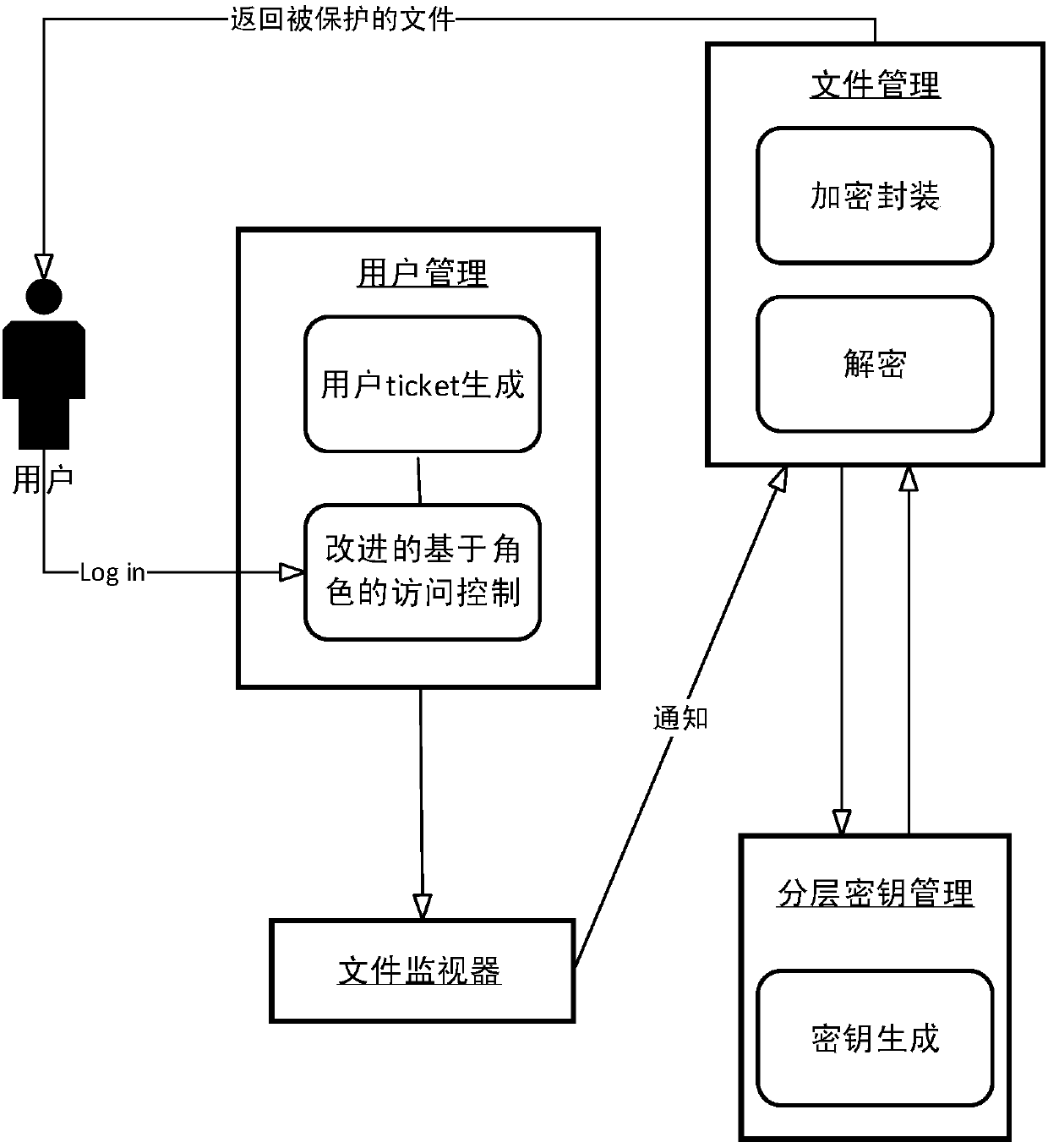
File protection method and system
Owner:PEKING UNIV
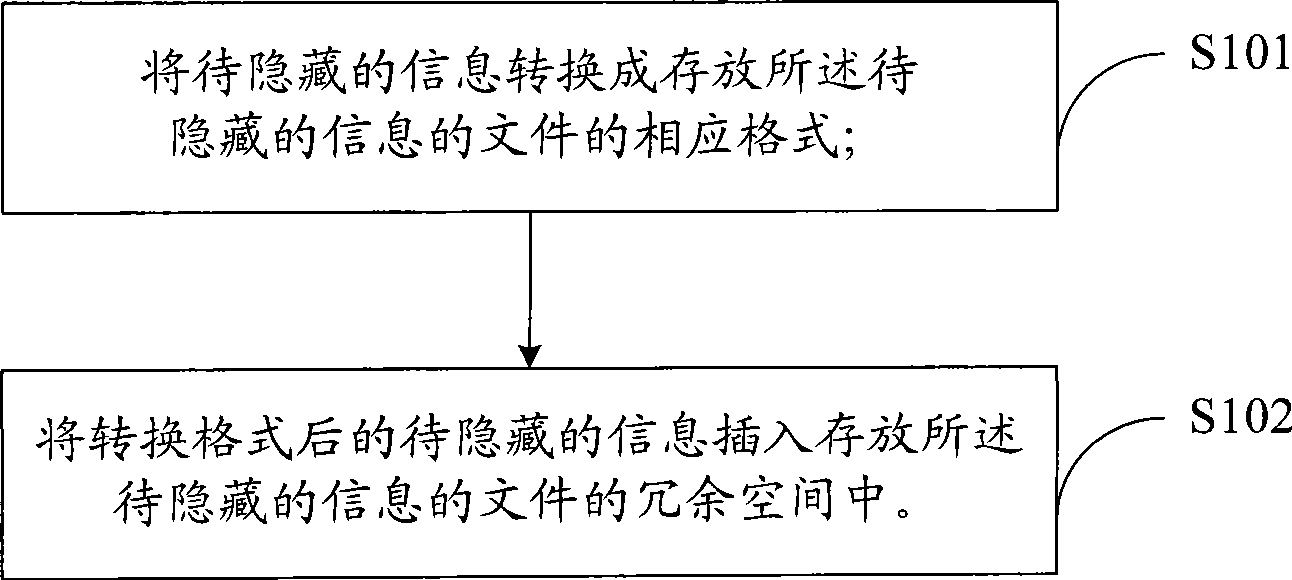
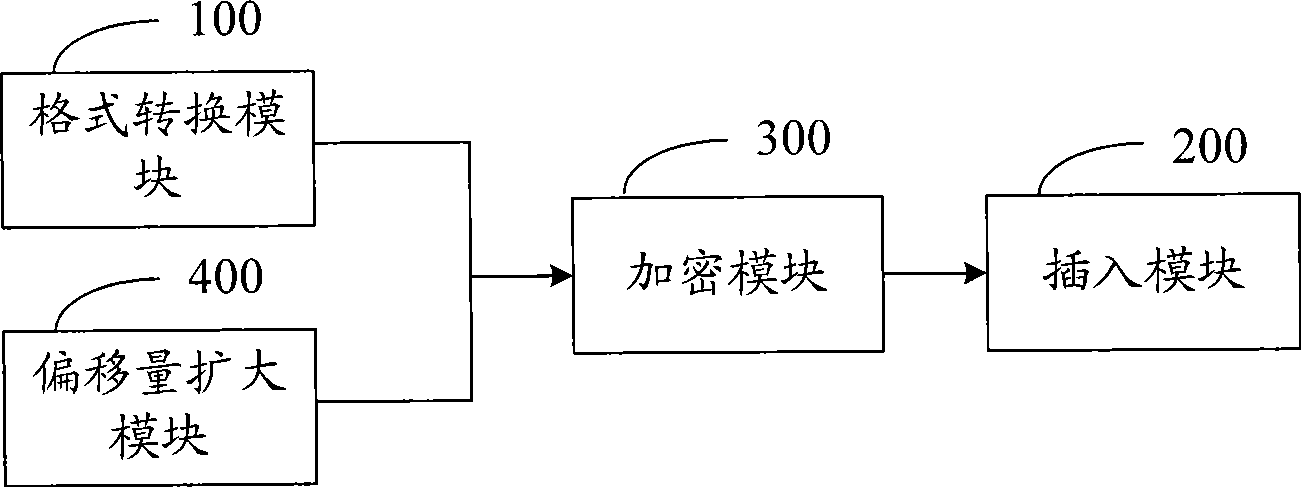
Information hiding method, system and electronic equipment
InactiveCN101499116ADigital data protectionSpecial data processing applicationsData contentInformation hiding
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
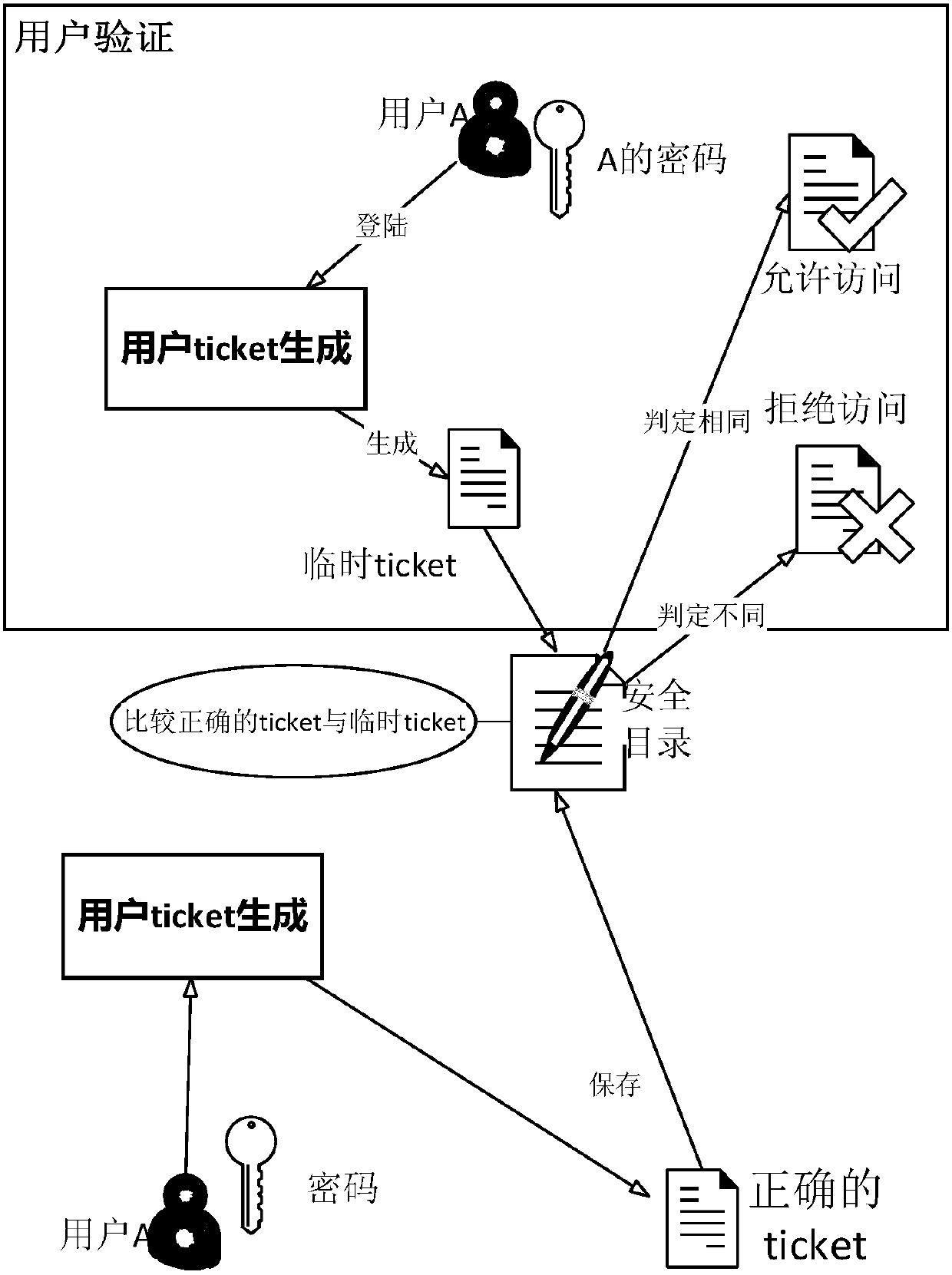
Reading method and device for verification information
ActiveCN105207775APrevent stealing authentication informationEnsure information securityUser identity/authority verificationDigital data protectionStatus changedComputer terminal
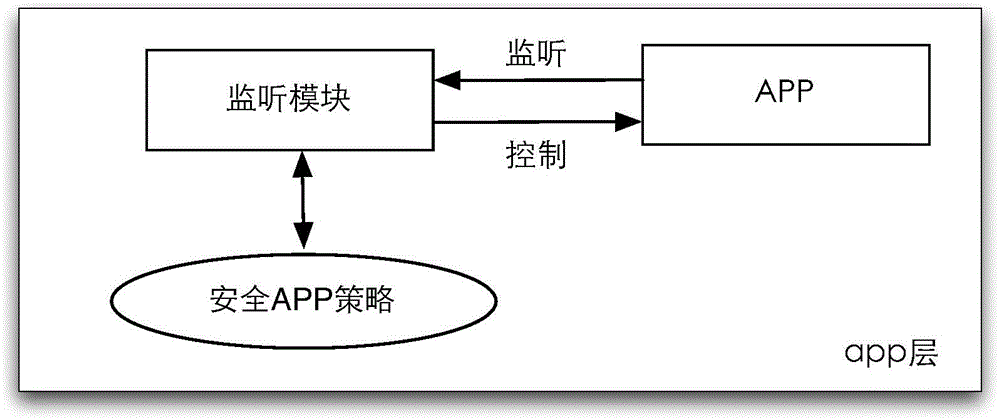
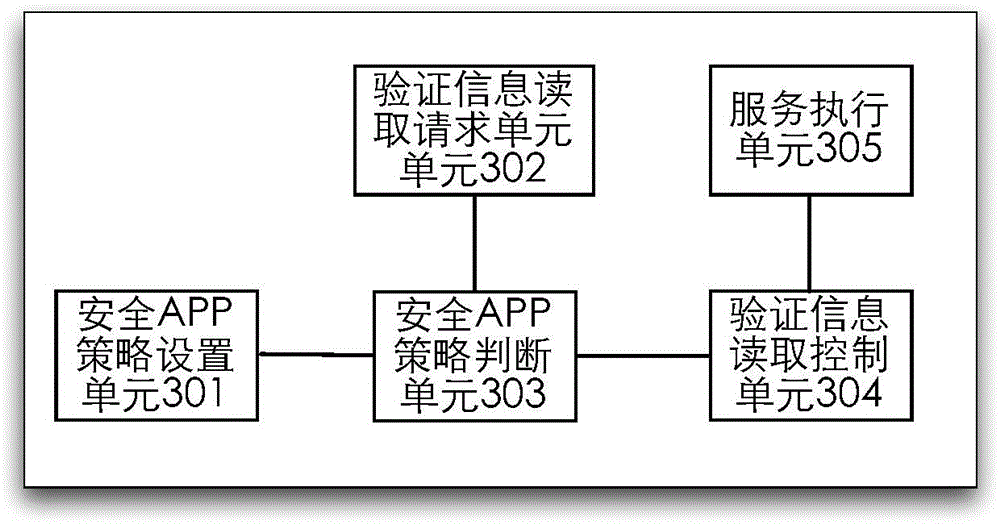
The invention discloses a reading method and device for verification information. The method comprises the steps that a safety APP strategy is set on a terminal for reading the verification information, wherein the verification information is a message used for verifying the identity or authority of a terminal or a user in a specific service execution process; after the terminal receives the verification information from a network device, application programs request to obtain the verification information; whether the application programs accord with the safety APP strategy is judged, and according to the judgment result, only the application programs according with the safety APP strategy are allowed to read the verification information; and the verification information is utilized to verify the identity or authority of the terminal or the user in the specific service execution process. According to the invention, the safety APP strategy is set in advance, only the APPs according with the safety APP strategy are allowed to access the verification information, and malicious application programs such as Trojan cannot read the verification information under the condition that the malicious application programs do not accord with the safety APP strategy, so that the invalid application programs are effectively prevented from stealing the accord with the verification information, and the information safety is ensured.
Owner:BEIJING QIHOO TECH CO LTD
Method and system used for refining database authority
InactiveCN108304732AImprove securityFine-grained control permissionsDigital data protectionData sourceDatabase
The invention provides a method and a system used for refining database authority. The method includes: establishing a data source table according to configuration information of a database of which the authority needs to be refined; acquiring database name information and table information and field information in the database from the configuration information to establish a resource table; creating accessing users, and storing accessing-user information to establish a user table; and establishing relationships of the accessing users and resources in the resource table according to the accessing users and the resources in the resource table, and carrying out storing to establish a user resource relationship table. According to the method, finer control authority can be realized for the database, and security of the database is improved.
Owner:PETRO-CYBERWORKS INFORMATION TECH CO LTD
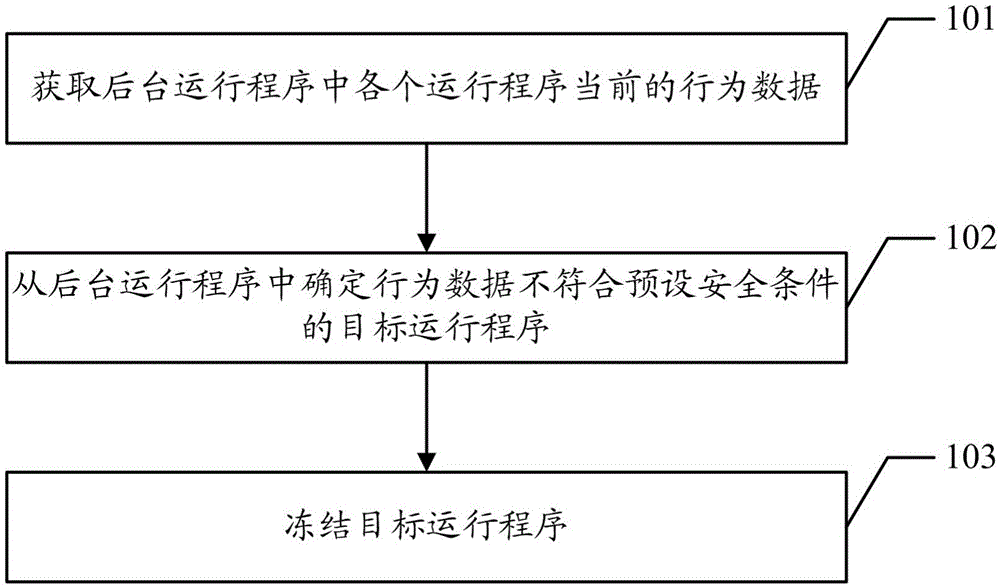
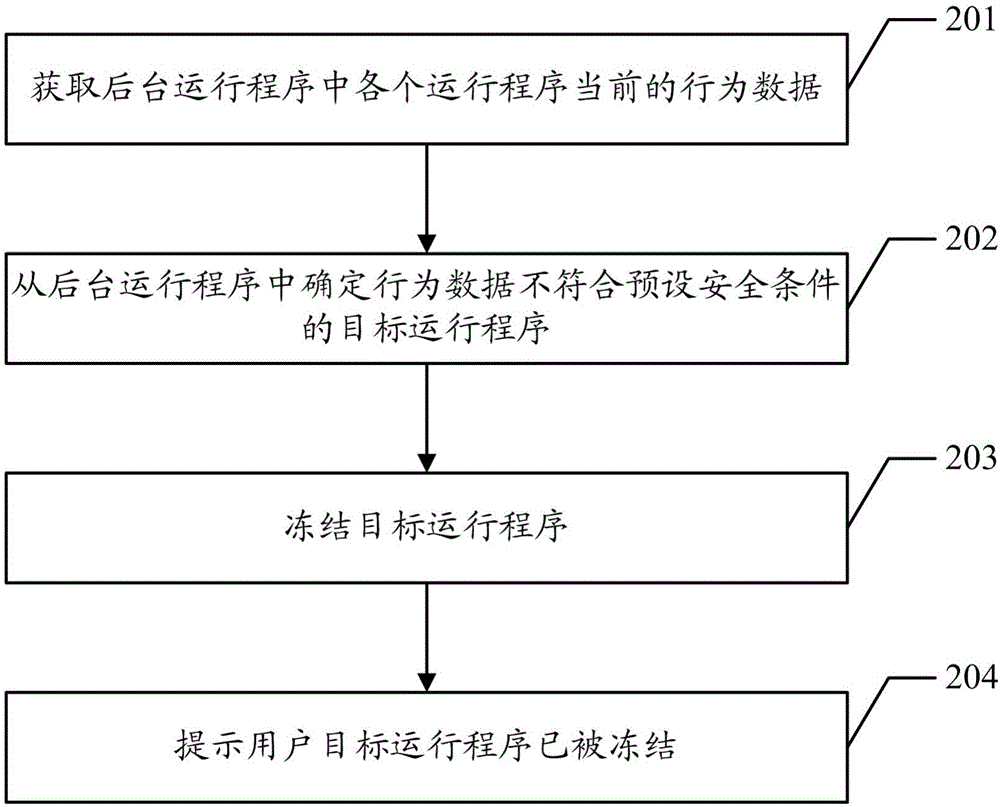
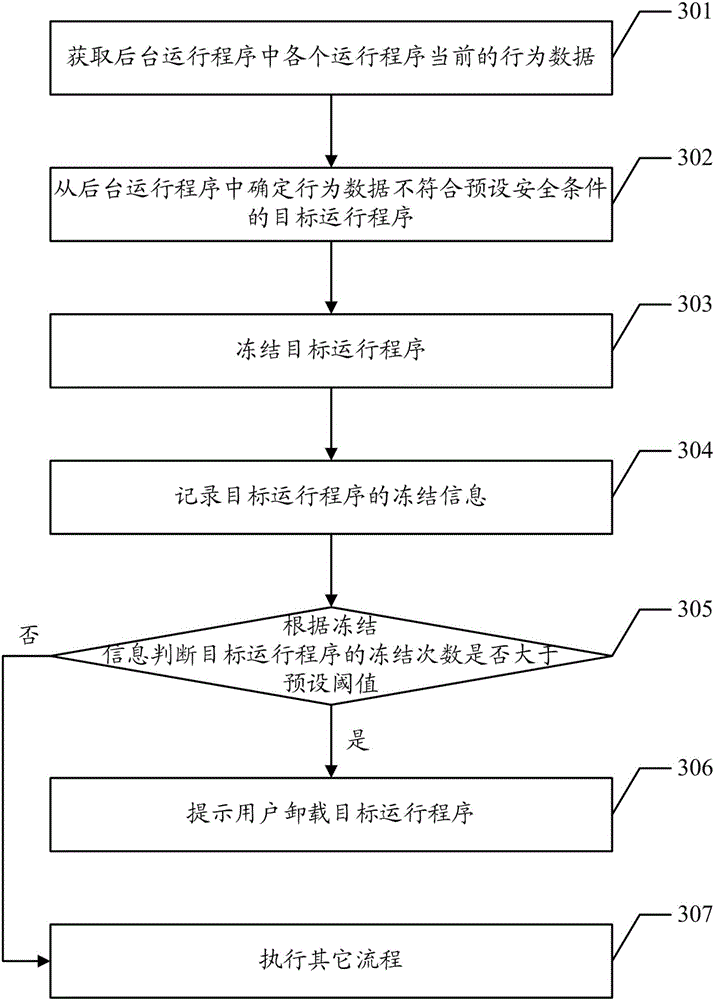
Freezing method of application program and terminal
InactiveCN106325993APrevent leakageImprove securityProgram initiation/switchingDigital data protectionSecurity specificationComputer terminal
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Data processing method and device, storage medium and processor
ActiveCN109886040ASafe and accurate accessAddresses vulnerabilities that make it difficult to securely and accurately access filesDigital data protectionComputer hardwareNetwork packet
Owner:武汉融氢科技有限公司
Securing Electronic Data by Automatically Destroying Misdirected Transmissions
PendingUS20200117800A1Digital data protectionDigital data authenticationData miningSoftware engineering
Owner:BOTTOMLINE TECH
System and method for transferring medical data
PendingCN112768022AIncreased protectionGuaranteed Voluntary LicensingMedical data miningMedical automated diagnosisData streamData management
The invention discloses a system and a method for transferring medical data, and belongs to the technical field of medical data management. The system is provided and comprises a data acquisition module, a data processing module, an auditing module, a verification module and a security module, and all the modules are electrically connected in sequence. The method for transferring medical data is provided and comprises the following steps that S1, a medical institution calls related medical data according to the content of an application form; S2, the related medical data in the step S1 are classified and standardization and desensitization processing are performed; S3, the data in the step S2 are audited to ensure that the data are consistent with the content of the application form; S4, the patient and the medical institution authorize related medical data; and S5, security protection is performed on the internal and network security of the medical institution to ensure data transmission security. According to the method and the system, privacy, security and standardization of medical data transferring are ensured, and the value of the medical data is improved.
Owner:HANGZHOU ZHUOJIAN INFORMATION TECH CO LTD
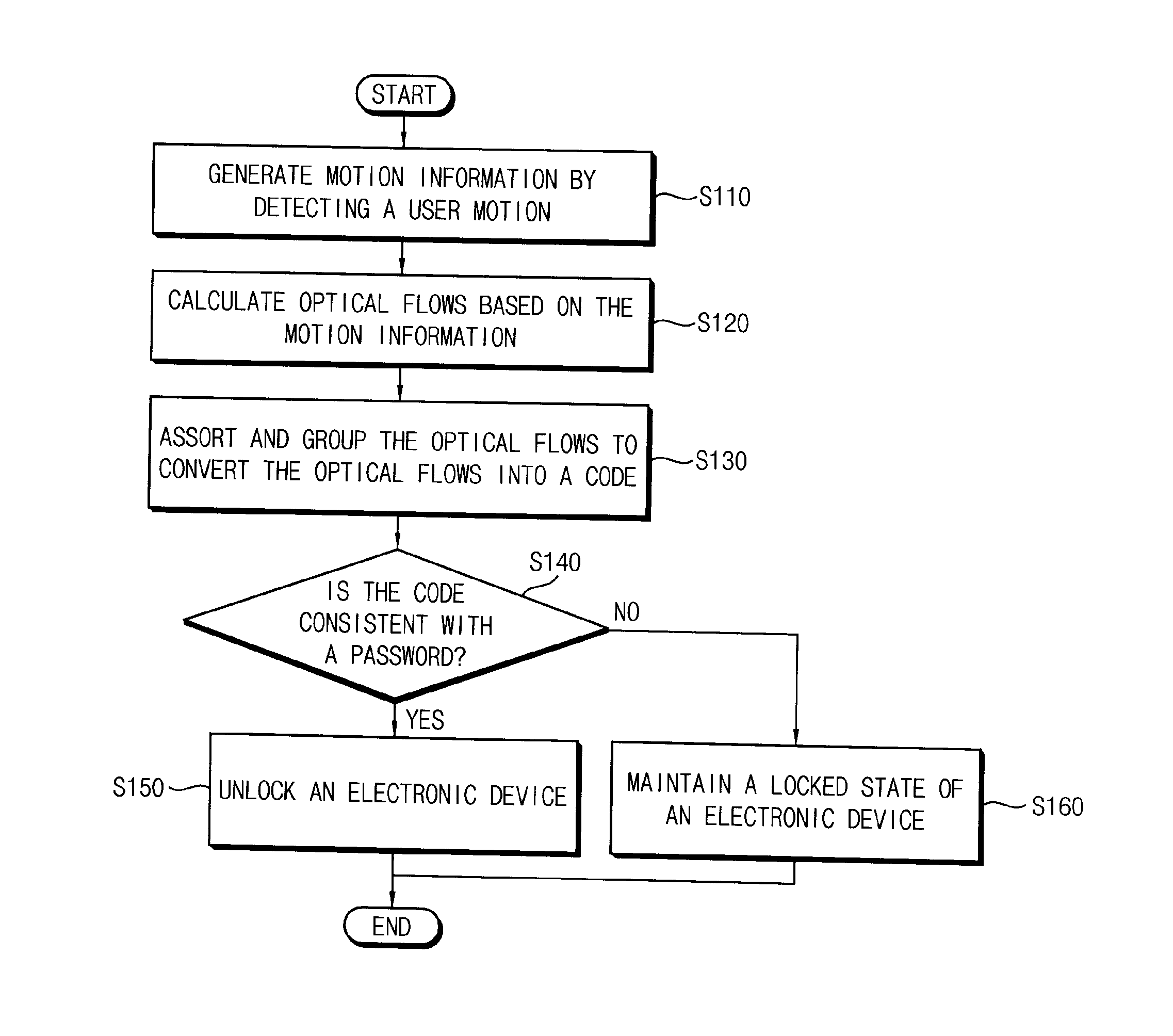
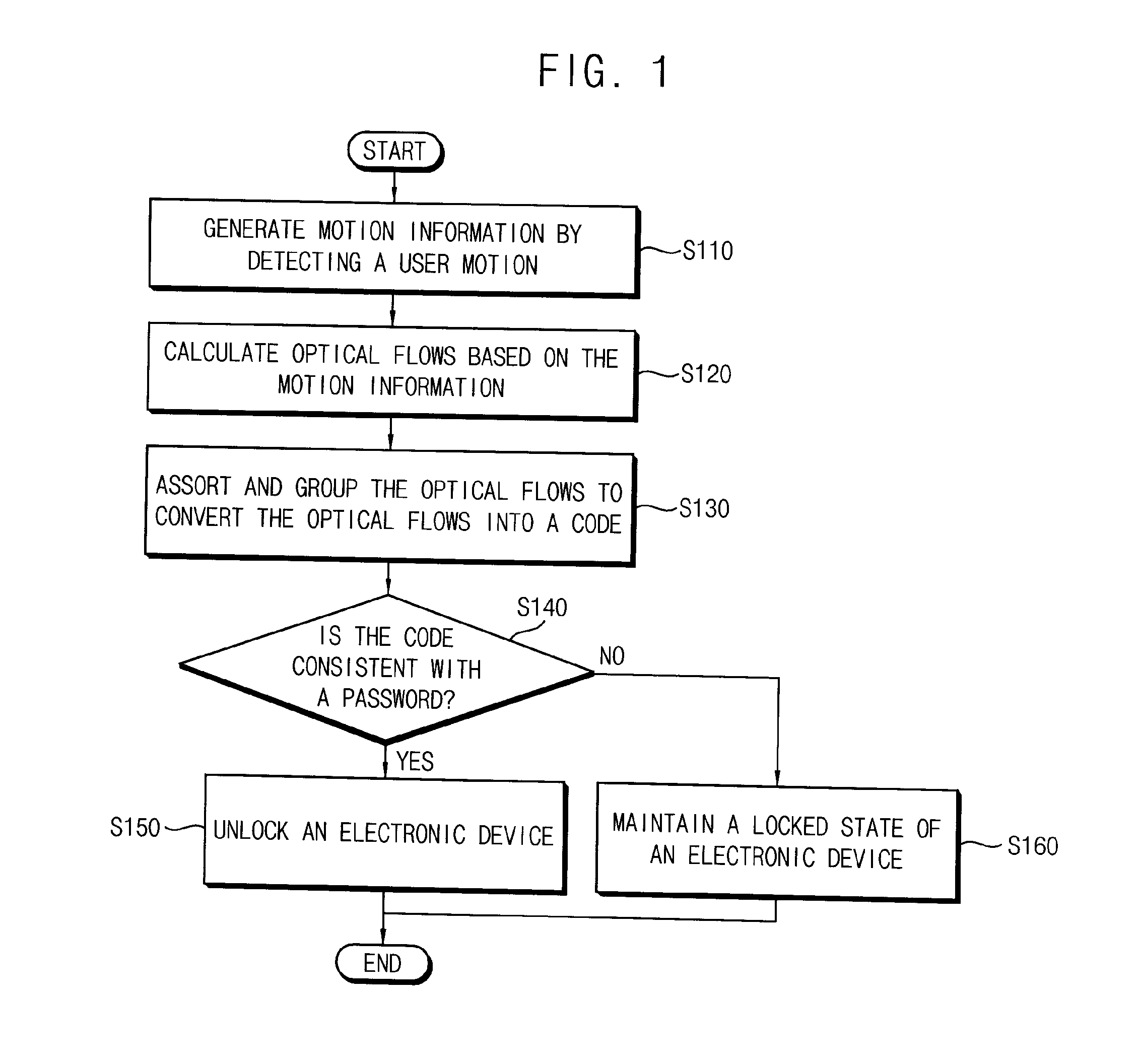
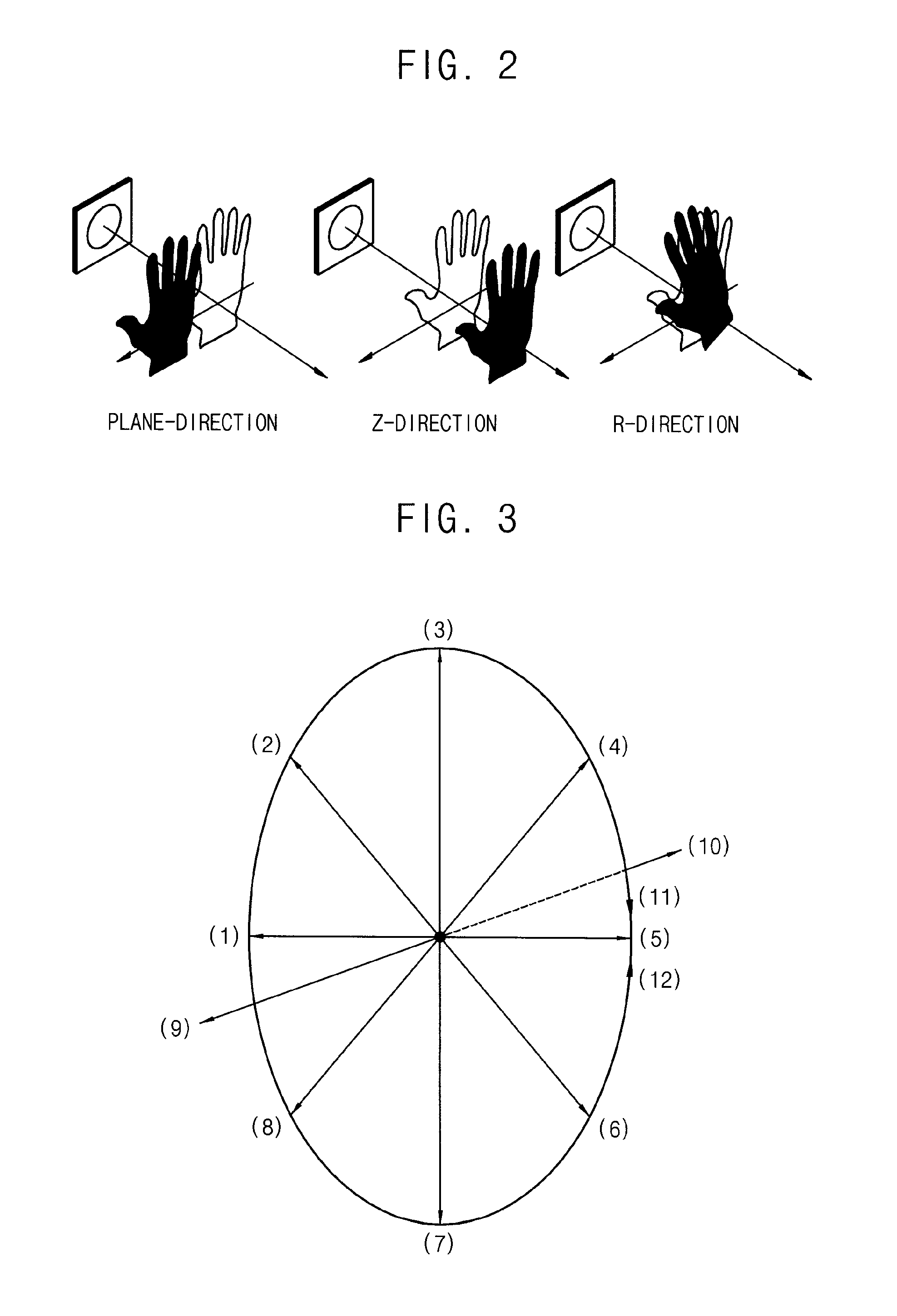
Method of unlocking an electronic device based on motion recognitions, motion recognition unlocking system, and electronic device including the same
InactiveUS20150248551A1Digital data processing detailsAnalogue secracy/subscription systemsPasswordSimulation
Owner:SAMSUNG ELECTRONICS CO LTD
Information display method and device
ActiveCN105653963ADigital data protectionInternal/peripheral component protectionReal-time computingUser information
Owner:ADVANCED NEW TECH CO LTD
Apparatus and method for blocking ransome ware using access control to the contents file
The present application relates to the apparatus for blocking Ransome ware using access control to the contents file, it includes an access permission program checking unit for checking whether a program of a process detected as being started in an user's computer is a reliable program, checking whether a parent process of the program is a reliable program, and determining whether the program is the program that is allowed to access the contents file; a whitelist registration unit for registering information of the contents file to be protected; and a contents file access control unit for allowing the process to access the contents file registered in the whitelist registration unit when the program of the process is the program that is allowed to access the contents file determined by the access permission program checking unit, and blocking the process from accessing the contents file registered in the whitelist registration unit when the program of the process is not the program that is allowed to access the contents file determined by the access permission program checking unit.
Owner:WITHNETWORKS CO LTD
Tax system consensus method based on alliance chain
PendingCN109859024AReduce false invoicesReduce economic and administrative costsFinanceDigital data protectionIndependent dataChain network
A tax system consensus method based on an alliance chain comprises the steps that an alliance chain network is established by a tax supervision institution, a tax registration institution serves as anaccounting node in the alliance chain network, other participation institutions are connected to the accounting nodes in the alliance chain network, and each participation institution and the tax supervision and registration institution are provided with independent databases; a digital protocol and a transaction contract are uniformly formulated by a tax administration mechanism in the alliancechain network; each participation institution realizes digital registration through an alliance chain; and if any participation mechanism in the alliance chain calls the transaction contract, all operation records of the transaction contract are generated into a file, the file and the transaction contract is encrypted by adopting a hash algorithm, the file and the transaction contract are sent tothe accounting node, and the file is stored by a database of each accounting node. According to the tax system consensus method provided by the technical scheme, the economic cost and administrative management cost of the tax department are reduced, the enterprise operation cost is reduced, and information sharing between the enterprise and the tax system is realized.
Owner:陕西优米数据技术股份有限公司
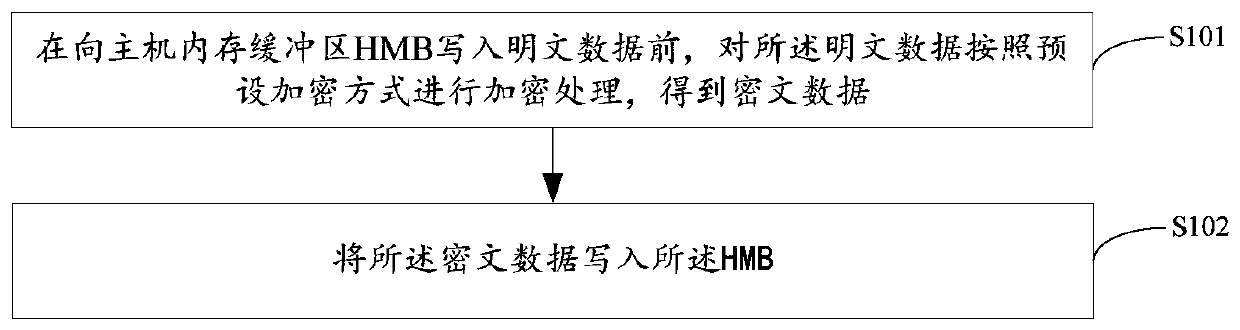
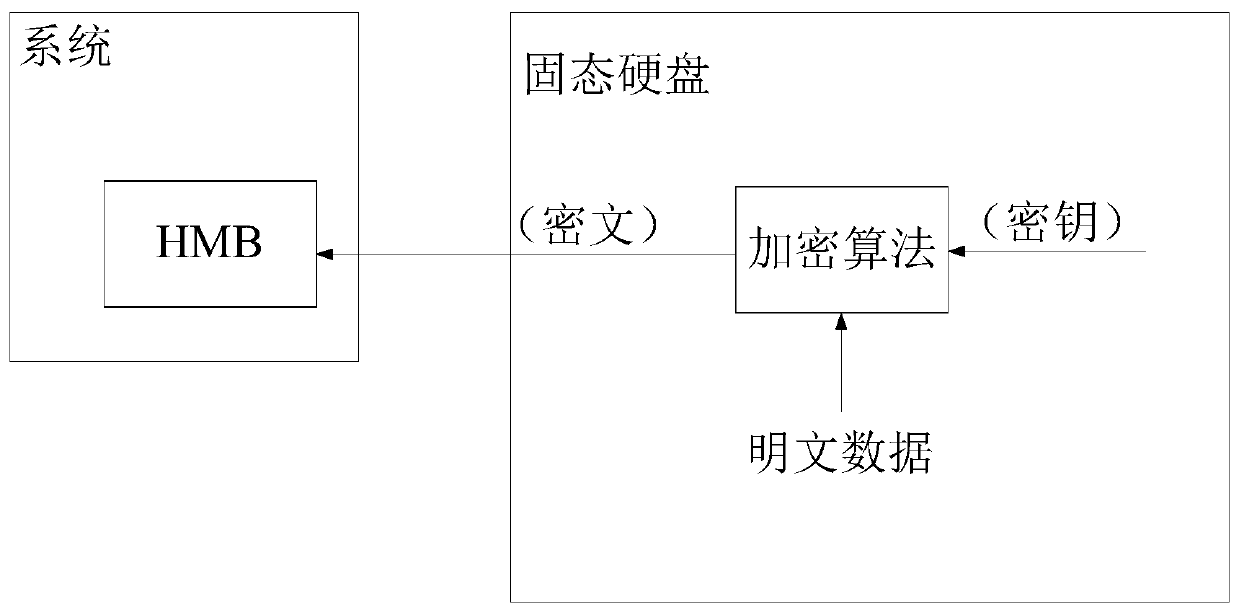
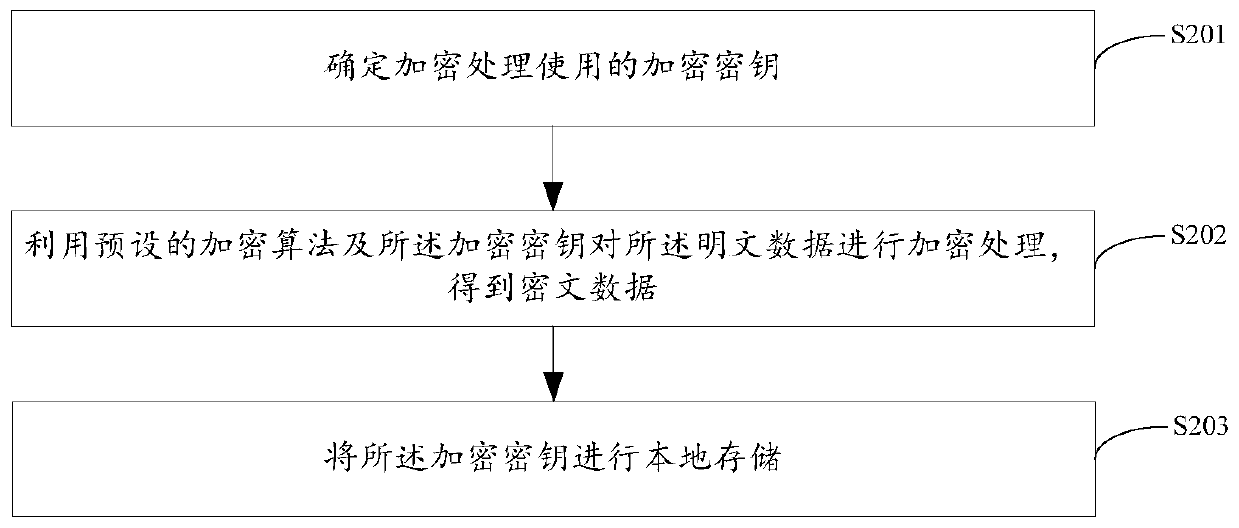
Data protection method and device, solid state disk and storage medium
PendingCN110472445AEnsure safetyDigital data protectionInternal/peripheral component protectionPlaintextCiphertext
Owner:SHENZHEN TIGO SEMICON
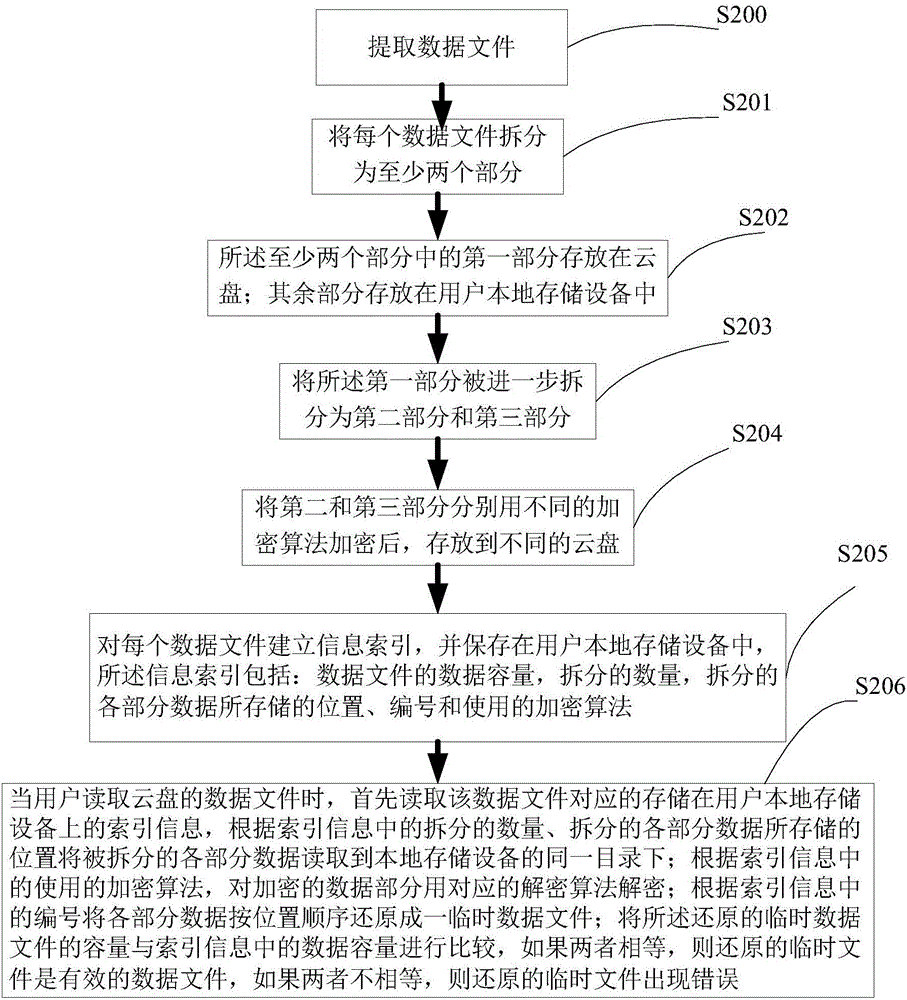
Cloud disk-based historical data file security protection method and system
InactiveCN106127066AImprove securityCutting costsDigital data protectionDocumentation procedureData file
Owner:青岛恒金源电子科技有限公司
Decentralized computing systems and methods for performing actions using stored private data
InactiveUS20220014367A1Key distribution for secure communicationPublic key for secure communicationEngineeringOne-time password
A distributed computing system is used to form a login network to perform an action for a user, using private data. The login network executes the verification using blockchain computing architecture, which is decentralized. The private data is stored on the blockchain in an obfuscated form. In order to compute the private data from the obfuscated form, multiple distributed private key shares are required to generate multiple decryption shares, which are combined to compute a One Time Pad (OTP). In turn, the OTP is used to obtain the private data from the obfuscated form.
Owner:LOGIN ID INC
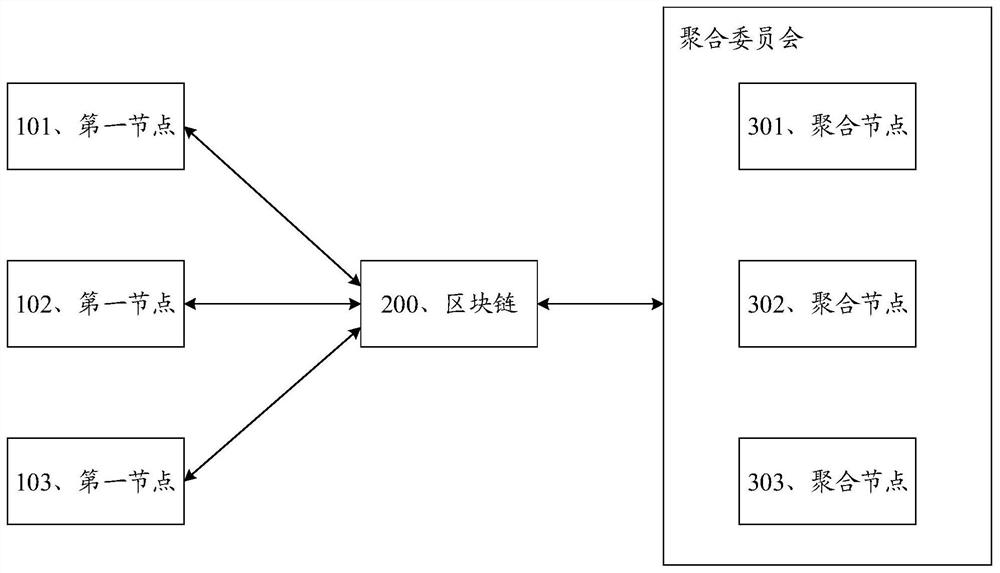
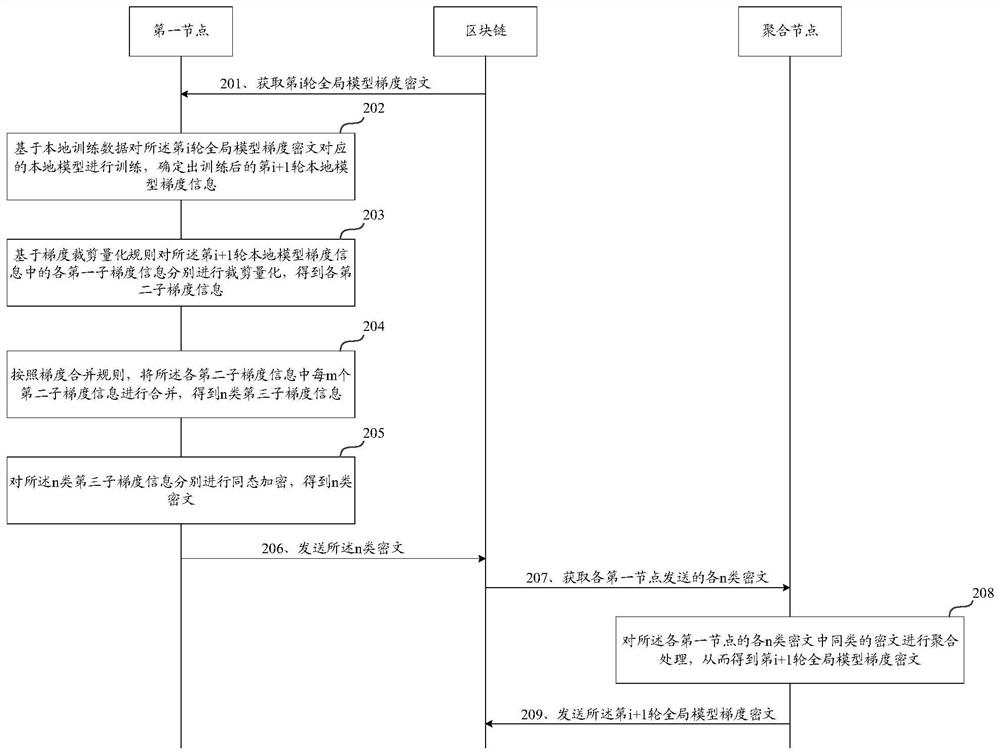
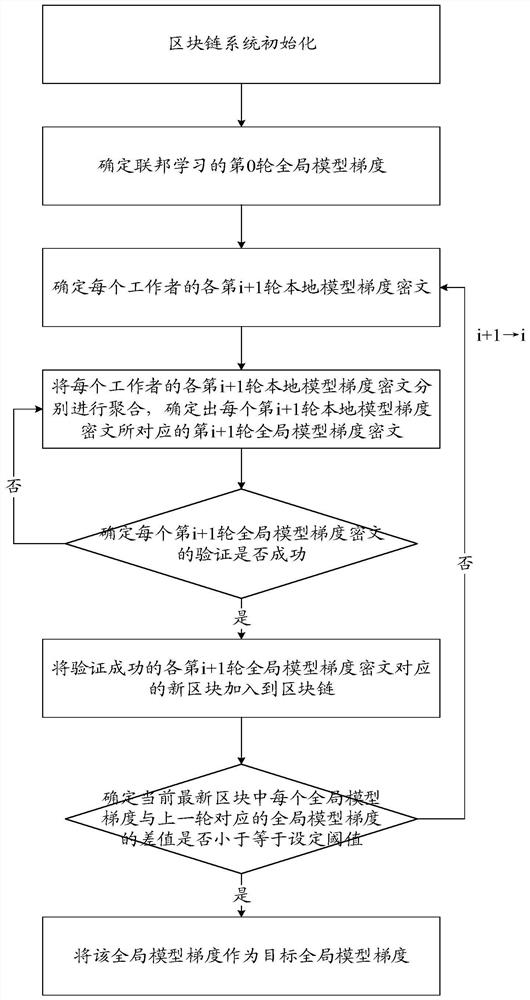
Federal learning method and device based on blockchain
Owner:WEBANK (CHINA) +1
Terminal and file management method
InactiveCN103366124APrevent arbitrary readEnsure safetyDigital data protectionFile storageFile management
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Information processing method and device
ActiveCN104424405AReduce complexityImprove convenienceDigital data protectionDigital data authenticationComputer hardwareInformation processing
Owner:LENOVO (BEIJING) CO LTD
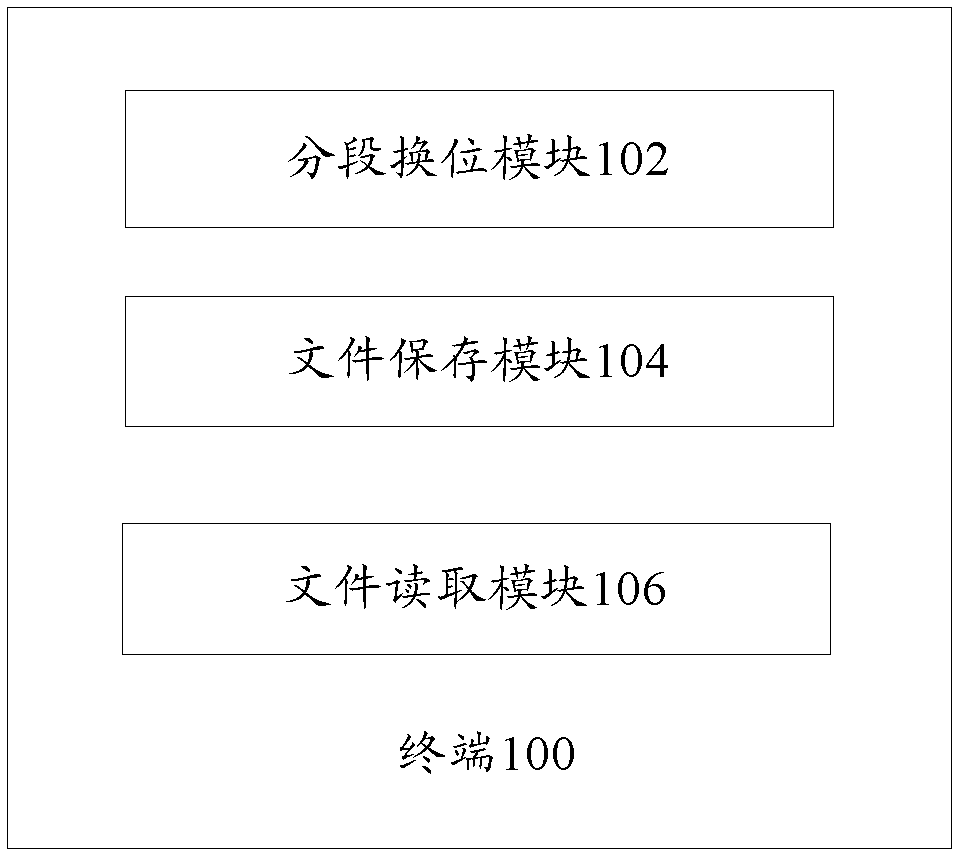
Method and Apparatus for Splitting and Encrypting Files in Computer Device
InactiveUS20140143540A1Effective encryptionDigital data protectionMemory systemsComputer engineeringMoving window
Owner:CLOUDIOH
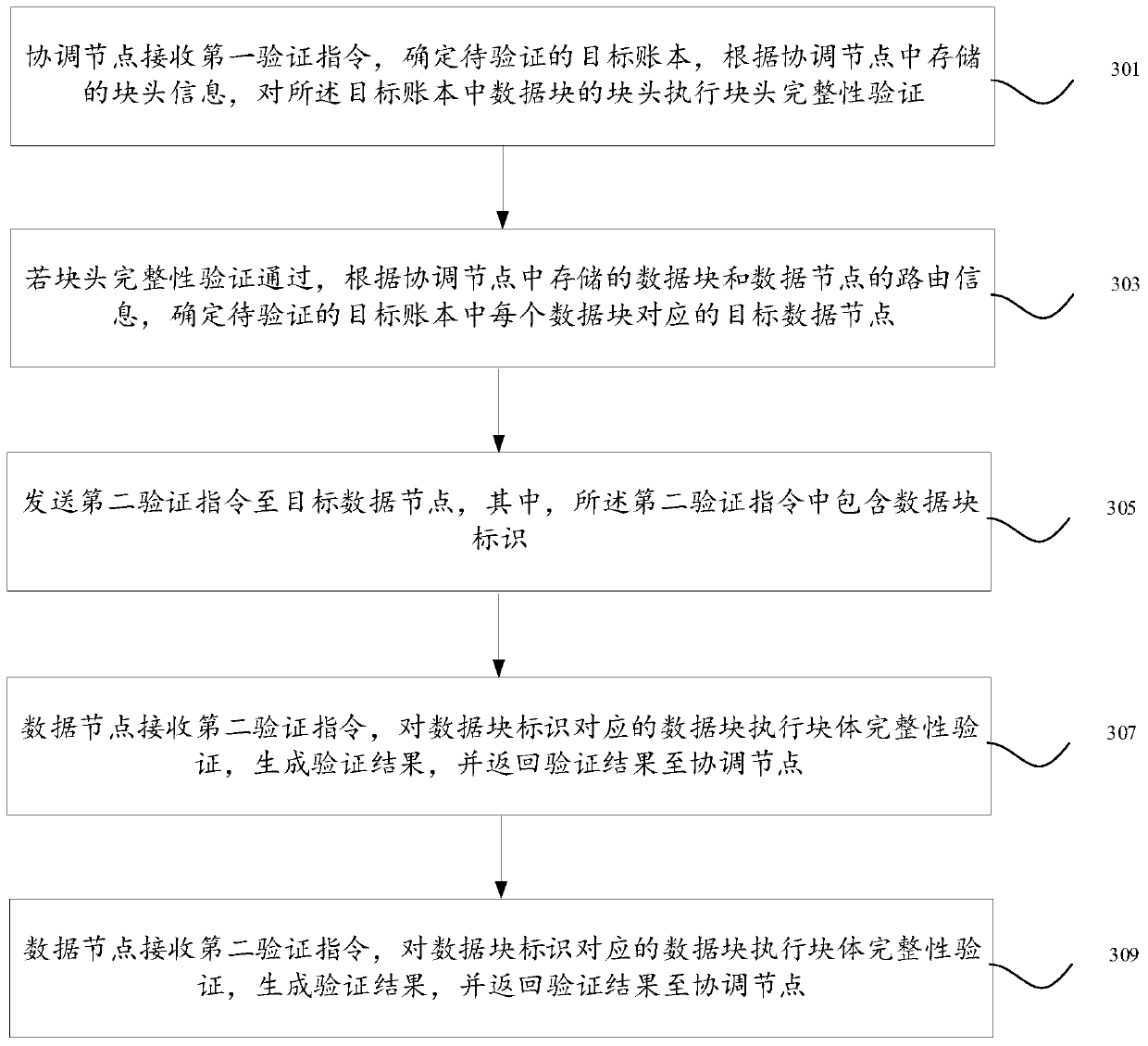
Data verification method, system and device, and equipment
ActiveCN110147685AImprove verification efficiencyExamples cannot be limitedDigital data protectionSource Data VerificationChain type
Owner:ADVANCED NEW TECH CO LTD
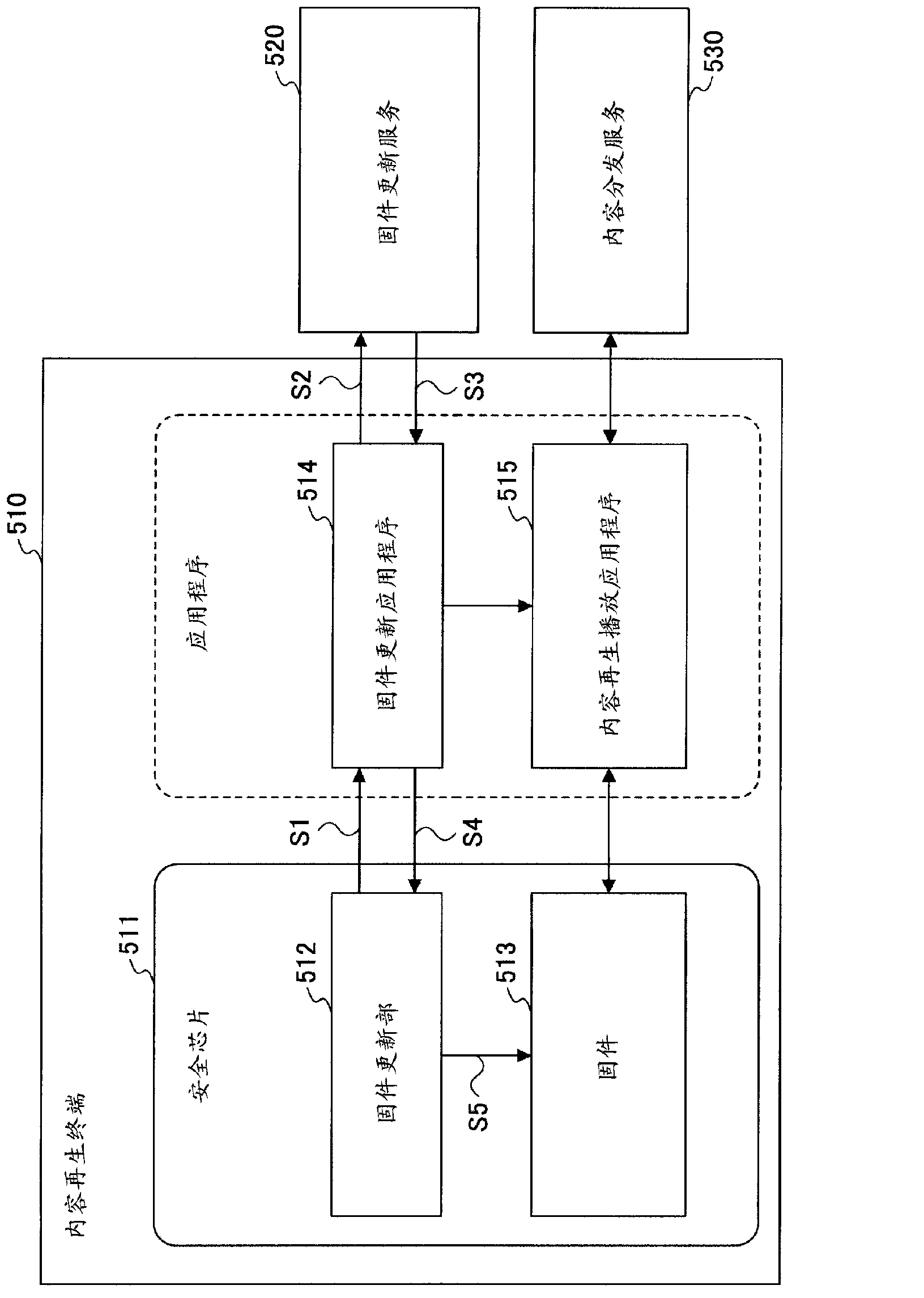
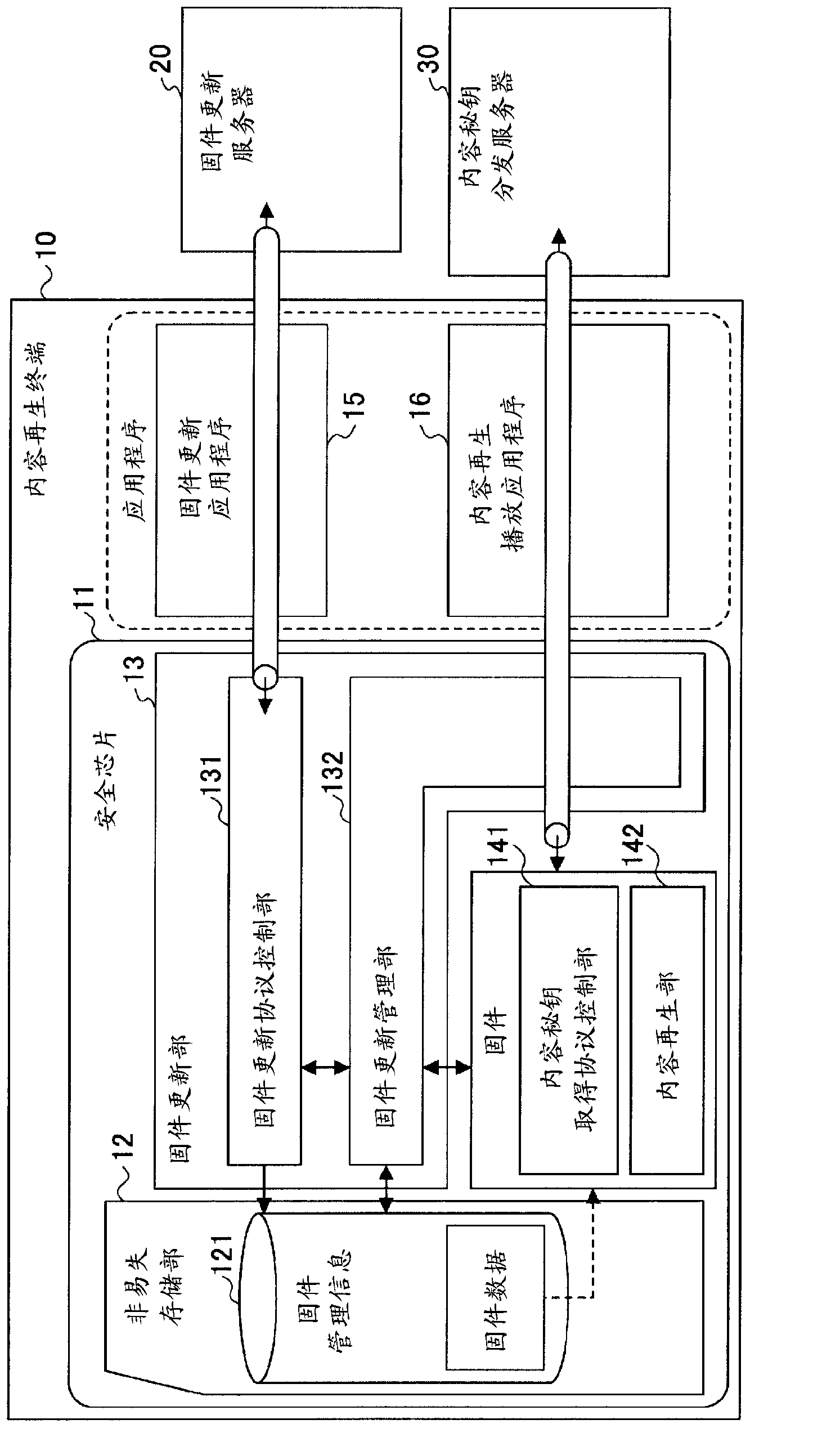
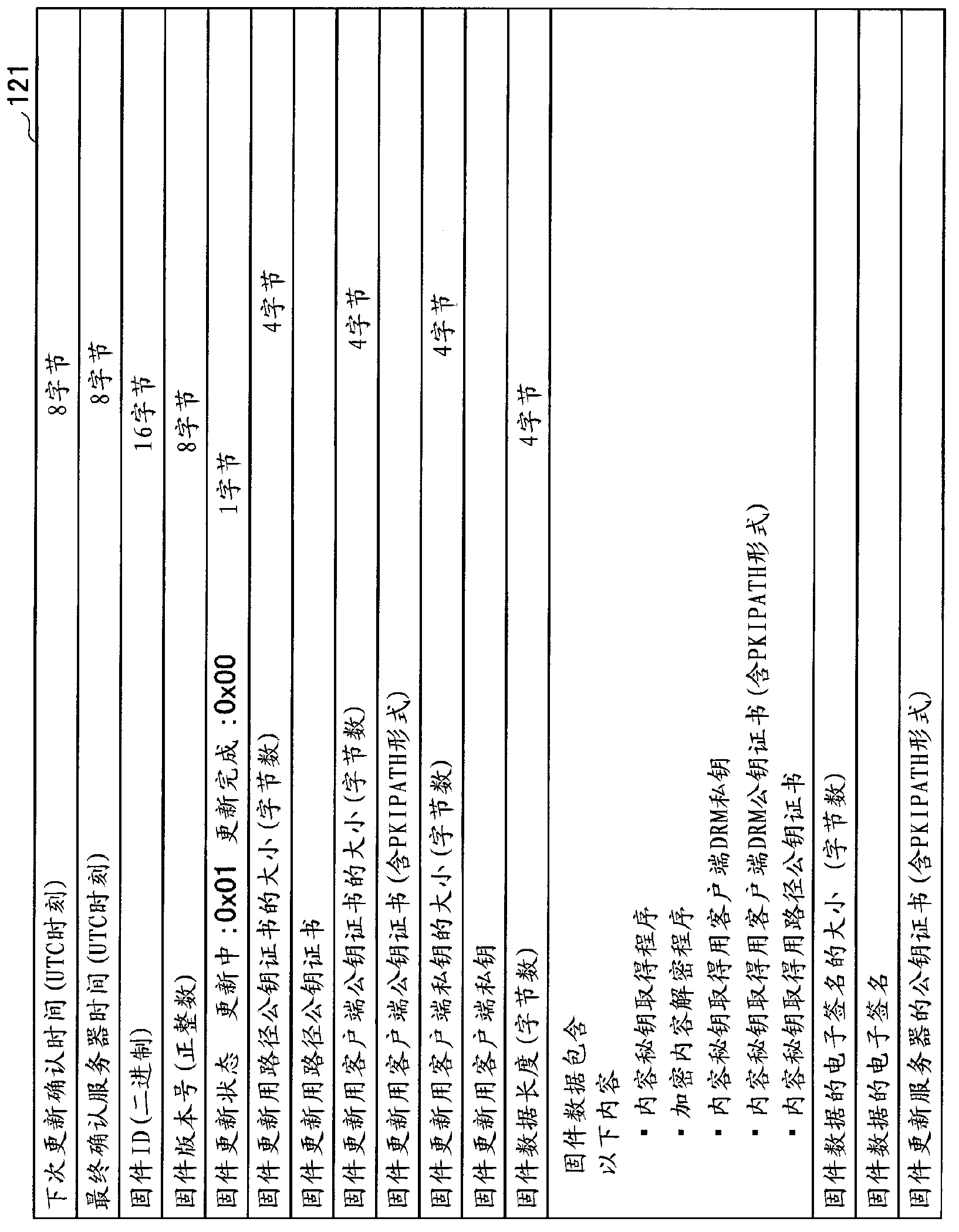
Content data playback device, update management method, and update management program
ActiveCN103154964ADigital data protectionProgram/content distribution protectionTime informationManagement unit
Owner:FUJITSU LTD
Popular searches
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap