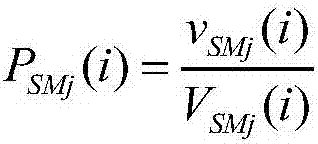System and method for providing cryptographic service through virtual cryptographic equipment cluster
A technology for cryptographic services and cryptographic devices, which is applied in the field of providing cryptographic services through virtualized cryptographic device clusters, can solve problems such as the inability to detect the busyness of the host machine in real time, the low utilization rate of cryptographic device resources, and the low work efficiency of the host machine. Overcome the inability to detect the busyness of the host in real time, protect security, and overcome inefficiencies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The invention will be further described below in conjunction with the accompanying drawings.
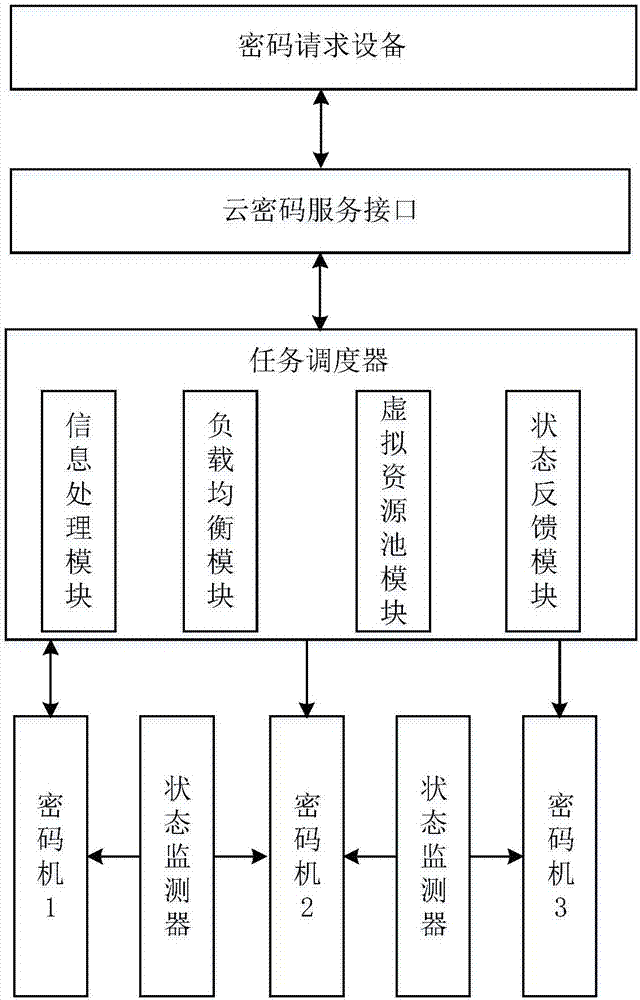
[0052] Refer to attached figure 1 , the system of the present invention is composed of a cloud cryptographic service interface, a task scheduler, a plurality of cryptographic machines and a state detector. in:
[0053] The cloud cryptography service interface is used to generate a service request message and send it to the task scheduler.
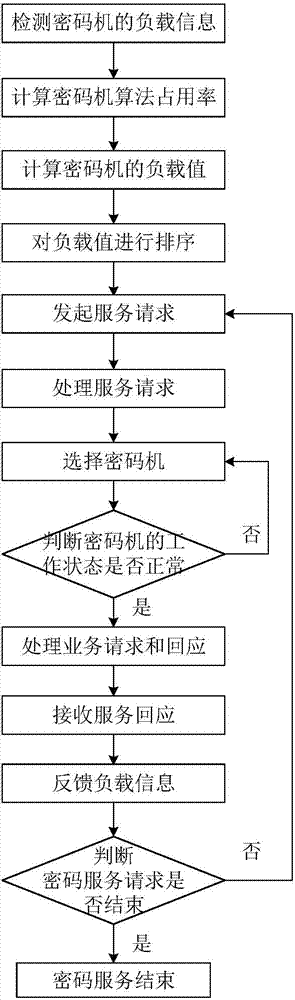
[0054] The task scheduler includes a load balancing module, an information processing module, a virtual resource pool module, and a state feedback module, wherein the load balancing module is used to calculate the occupancy rate of the commercial secret algorithm of each encryption machine, and calculate the utilization rate of each encryption machine According to the quick sort method, the load value of each cipher machine and its corresponding cipher machine serial number are arranged into a group of increasing sequences according to the a
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap