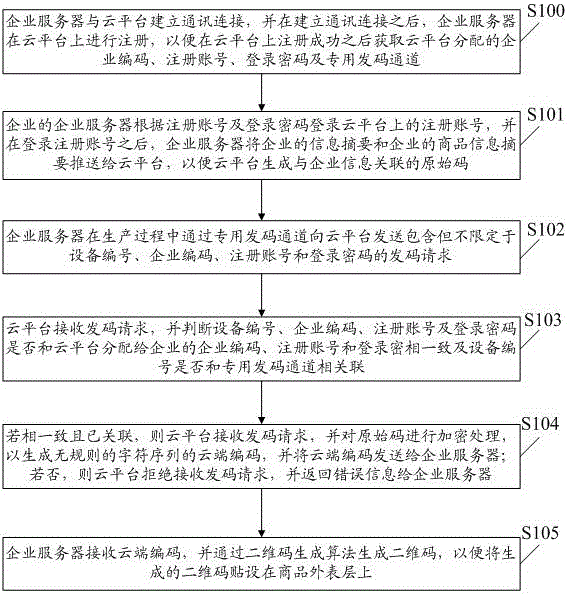
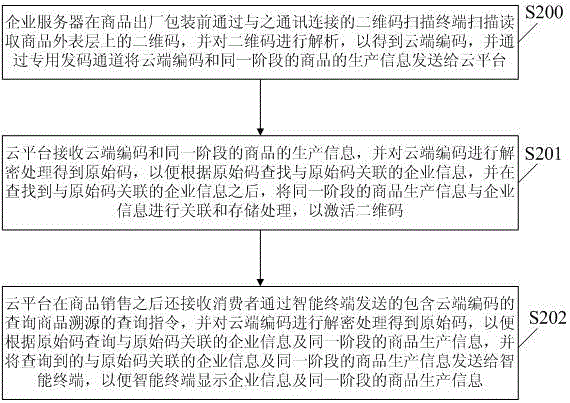
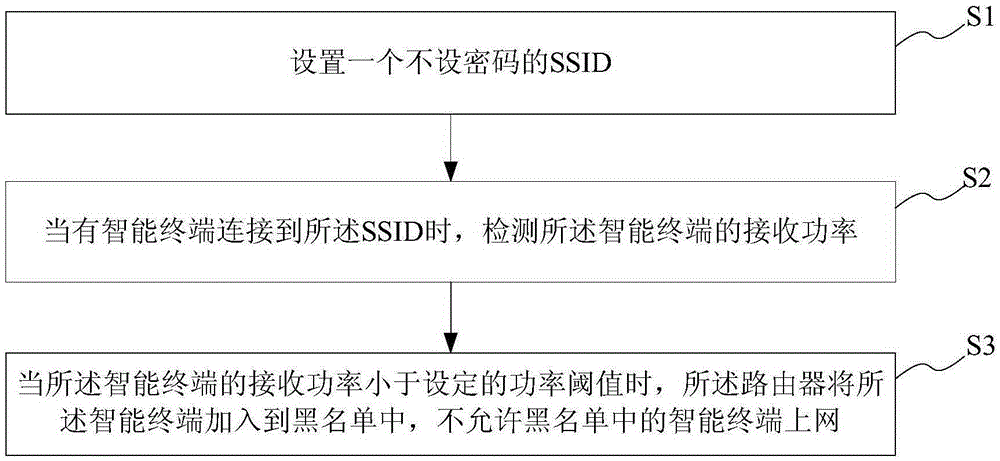
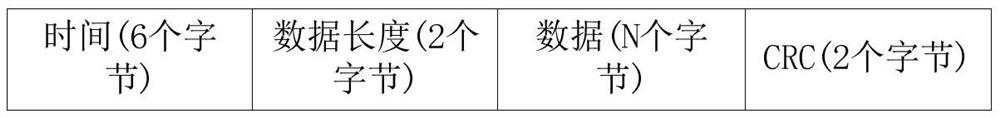
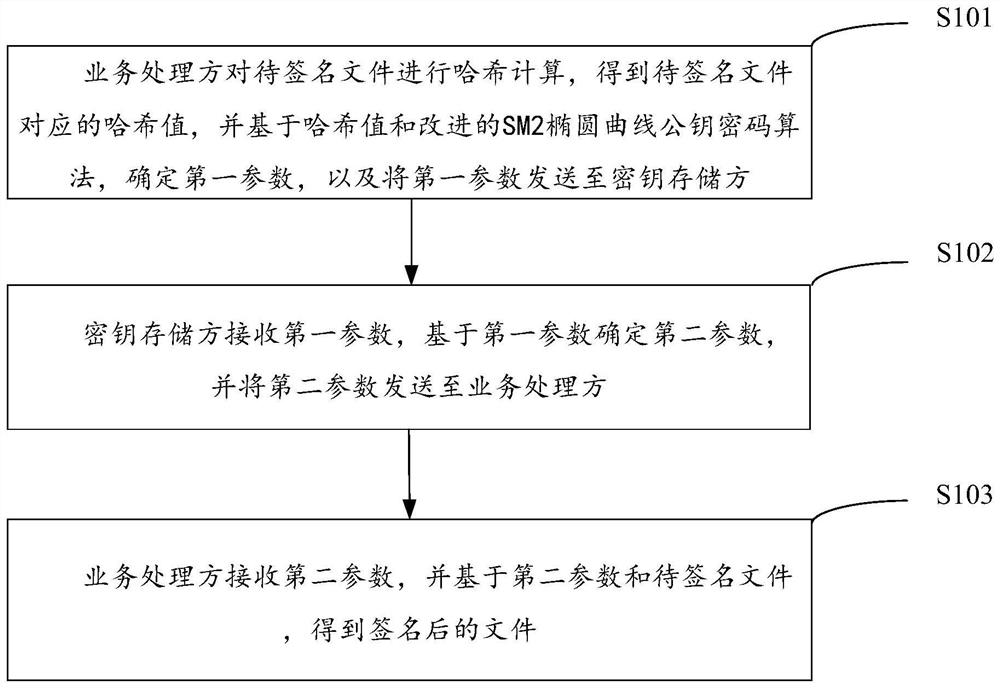
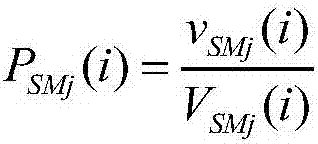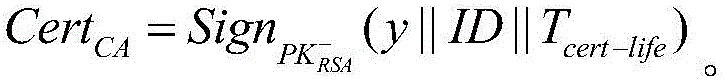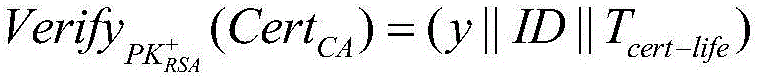Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32 results about "Cipher" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography.
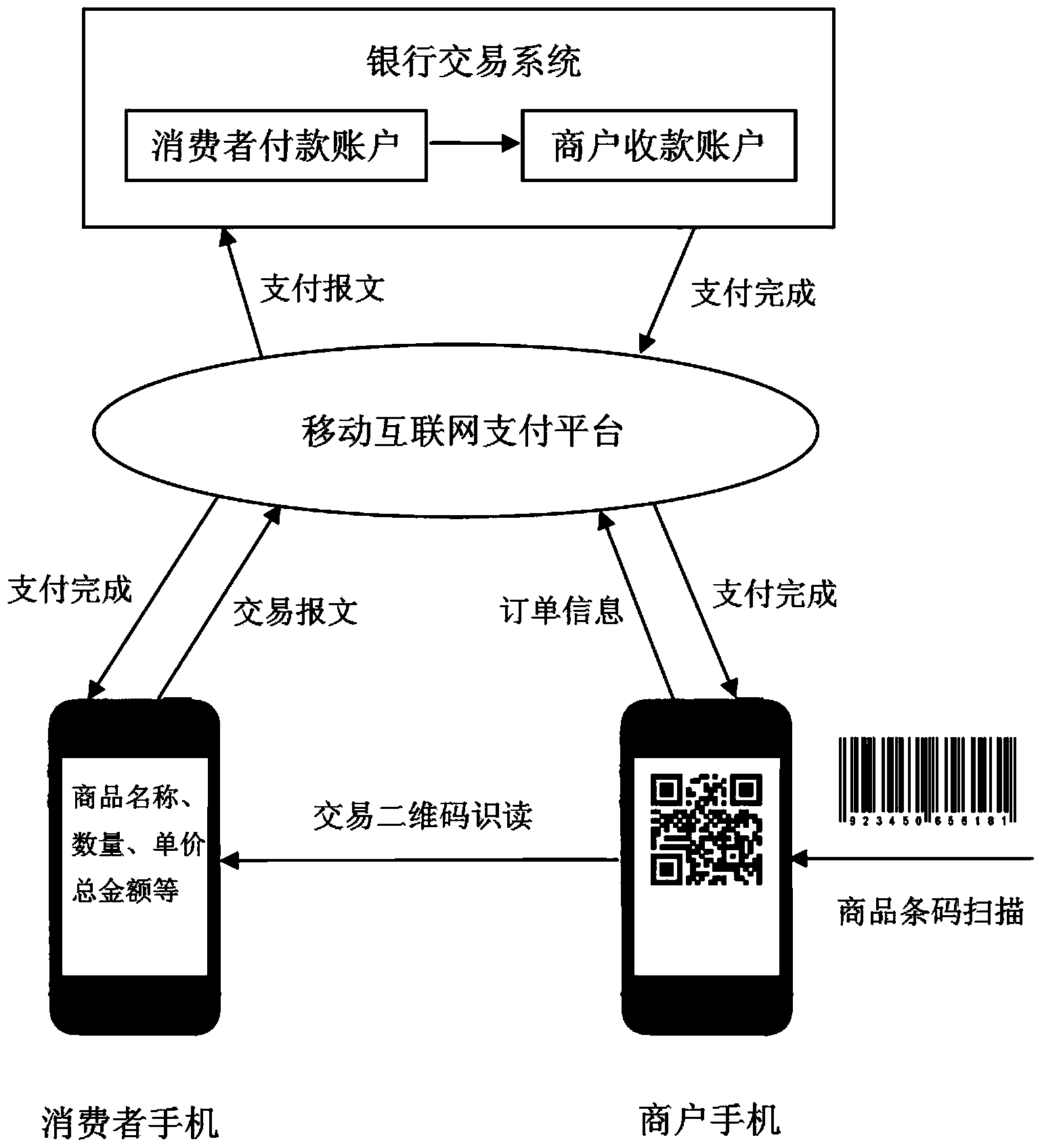
Mobile payment method for field shopping
InactiveCN103854173ASolve the problem of being easily stolenEliminate human input errorsProtocol authorisationThe InternetComputer science
Owner:UNISPLENDOUR CO LTD +2
Authentication system for mobile terminal having electronic money function
InactiveUS20060160525A1Reduce usageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPasswordComputer terminal
Owner:FUJIFILM CORP
CDMA port-to-port encryption communication system and key distribution method thereof
InactiveCN101635924AImprove securityReduce security risksSecurity arrangementCommunications securityCommunications system
The invention discloses a CDMA port-to-port encryption communication system and a key distribution method thereof, the CDMA port-to-port encryption communication system comprises a CDMA network and a terminal mobile telephone thereof, a public switched telephone network and a terminal fixed-line telephone thereof, a short message service center as well as the following three cipher processing units including a cipher chip of a mobile telephone terminal, a key distribution management center (KDMC) and a Firmware cipher module of a gateway mobile switching center. The key distribution management center is used for key distribution management of the communication system. The key distribution is realized by a layered distribution method, i.e. a first layer is an equipment key which is distributed in the process of initialization; a second layer is a key-encryption key and a short message service key which are distributed in startup of an enciphered mobile telephone; and a third layer is a session key which is distributed every time a session is launched between the enciphered mobile telephones. At the same time, by adopting a bidirectional certification technology for key distribution and combination of a key update and remote destroying method, the safety risk in key exposure is reduced, and the communication safety is improved.
Owner:CETC CYBERSPACE SECURITY TECH CO LTD
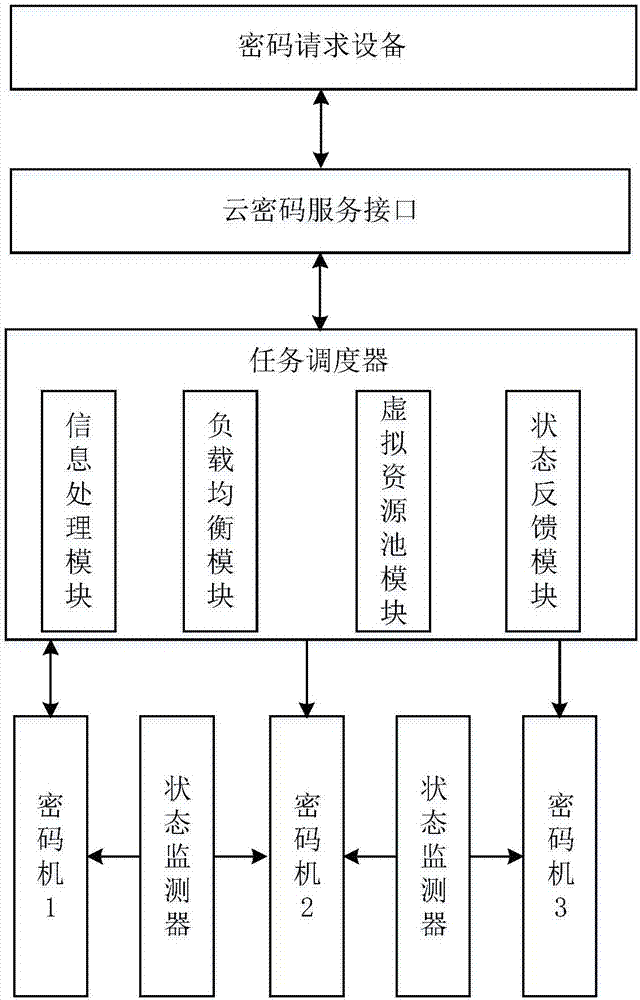
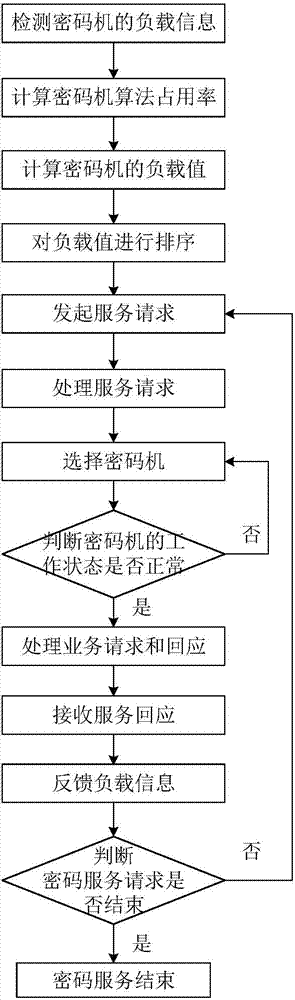
System and method for providing cryptographic service through virtual cryptographic equipment cluster
ActiveCN107040589ARealize dynamic managementOvercome underutilizationResource allocationDigital data protectionOccupancy rateVirtualization
Owner:XIDIAN UNIV
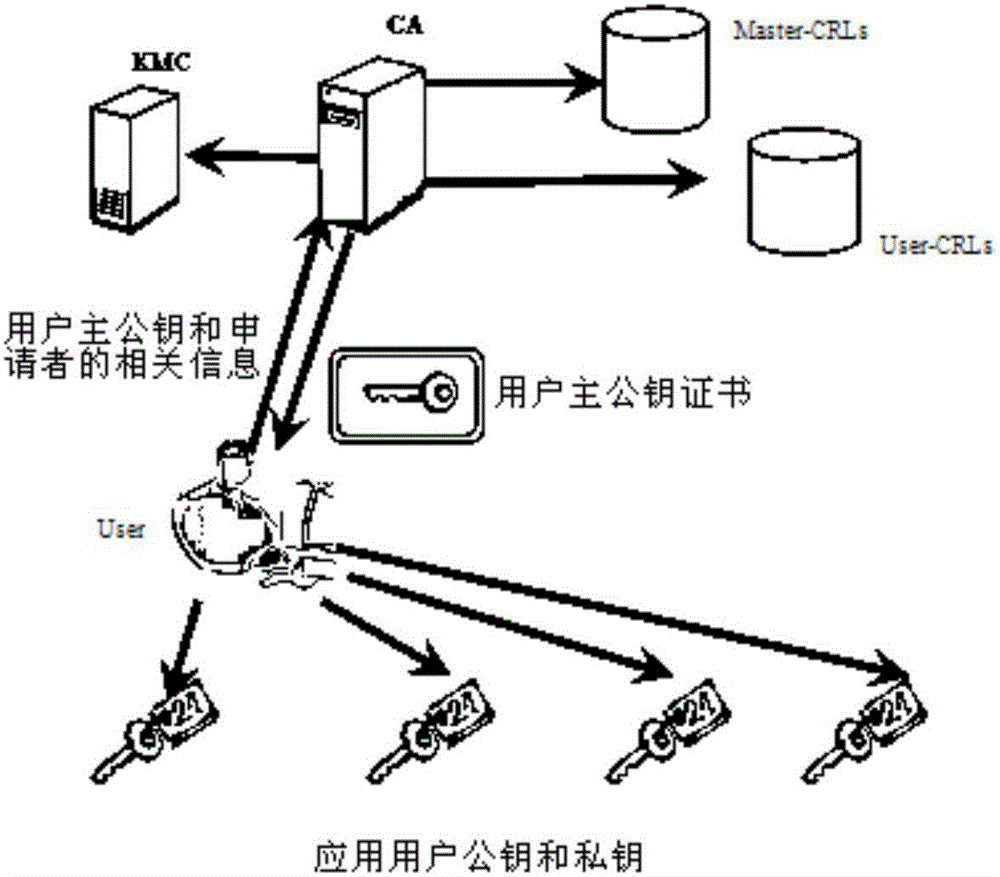
Reusable public key certificate scheme based on public key infrastructure
InactiveCN106059747AImprove management efficiencyReduce in quantityKey distribution for secure communicationUser identity/authority verificationRelevant informationPassword
Owner:成都蓝海贝信息技术有限公司
Verification method combining static password and dynamic password and terminal equipment
InactiveCN105871546AEasy to rememberDon't worry about stealingKey distribution for secure communicationMultiple keys/algorithms usageValidation methodsPassword
Owner:张雪莱
Non-key gate control system
InactiveCN101343961AExtended service lifeImprove securityElectric permutation locksMicrocontrollerSystem controller
The invention relates to a keyless gate controlling system. The keyless gate controlling system comprises a keyless system controller utilizing the cipher mode of mutual identification verification, a carrying card, and a receiving and transmitting antenna, the keyless system controller positioned at a car body end comprises a low frequency transmitting circuit connected with a singlechip and a high frequency receiving circuit; the carrying card adopts an identification verification card which comprises a low frequency receiving circuit connected with a microprocessor and a high frequency transmitting circuit; by adopting the keyless gate controlling system, the problem that the great inconvenience brought to users due to the car door opening mode through directly using a key or a remote controller is solved.
Owner:SHANGHAI SICAR VEHICLE TECH DEV
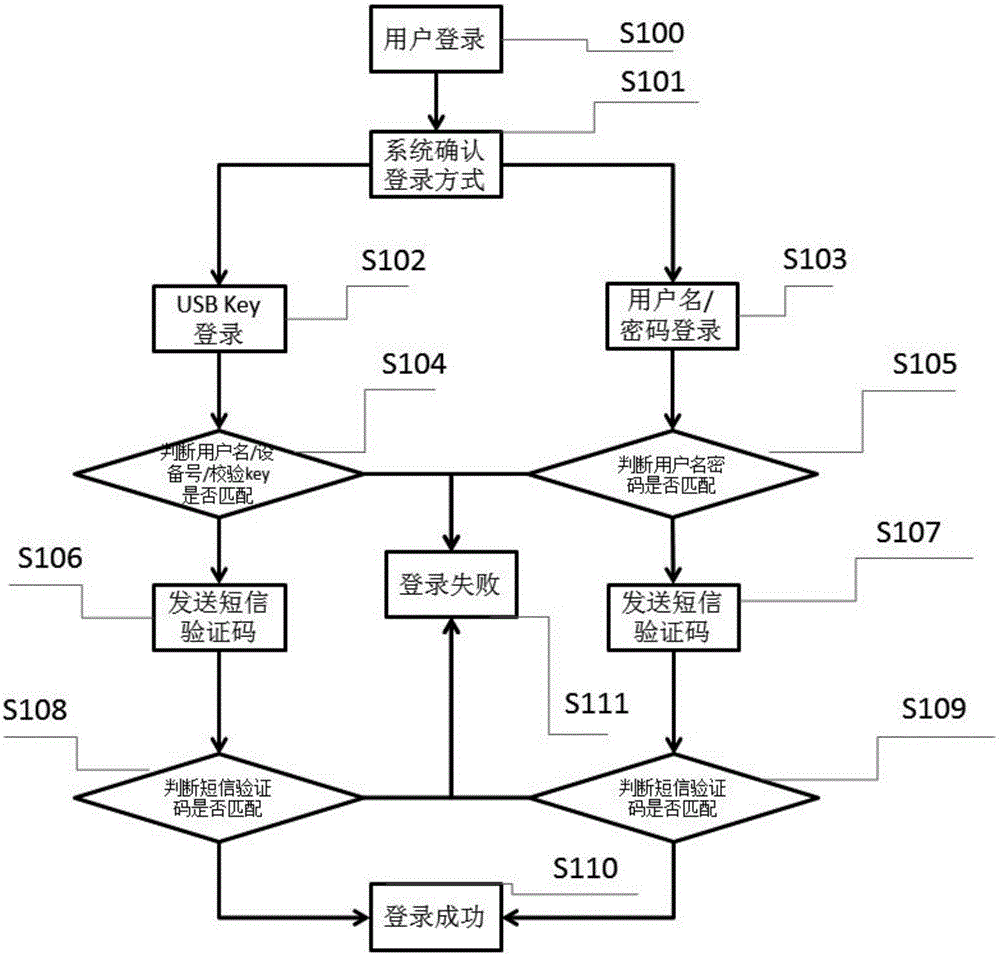
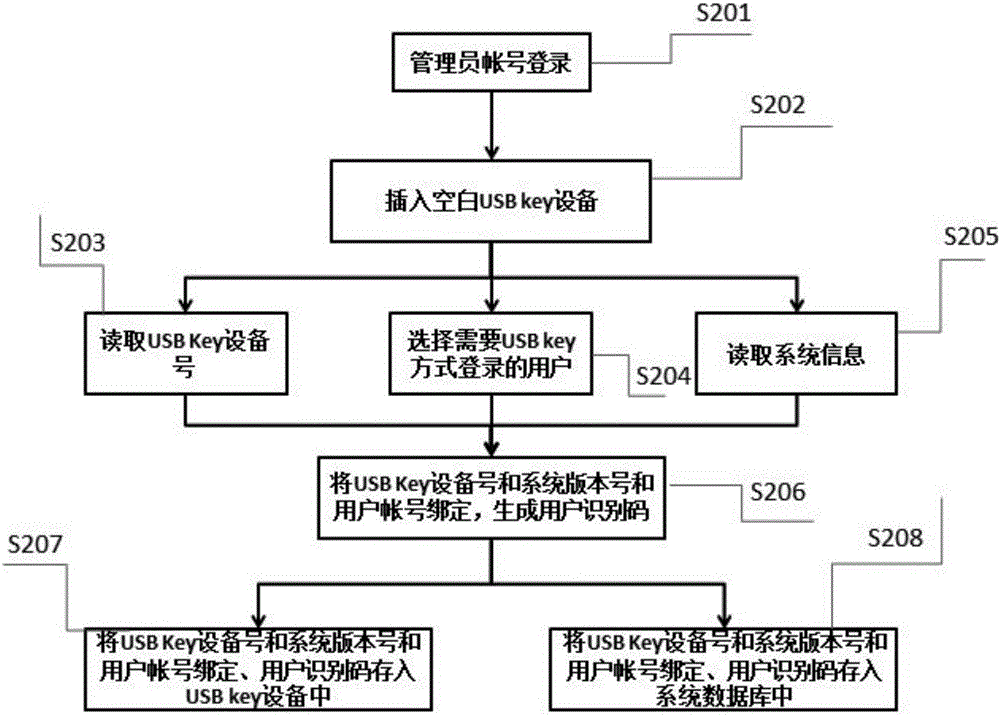
User logging-in method under system control
Owner:安徽天达网络科技有限公司
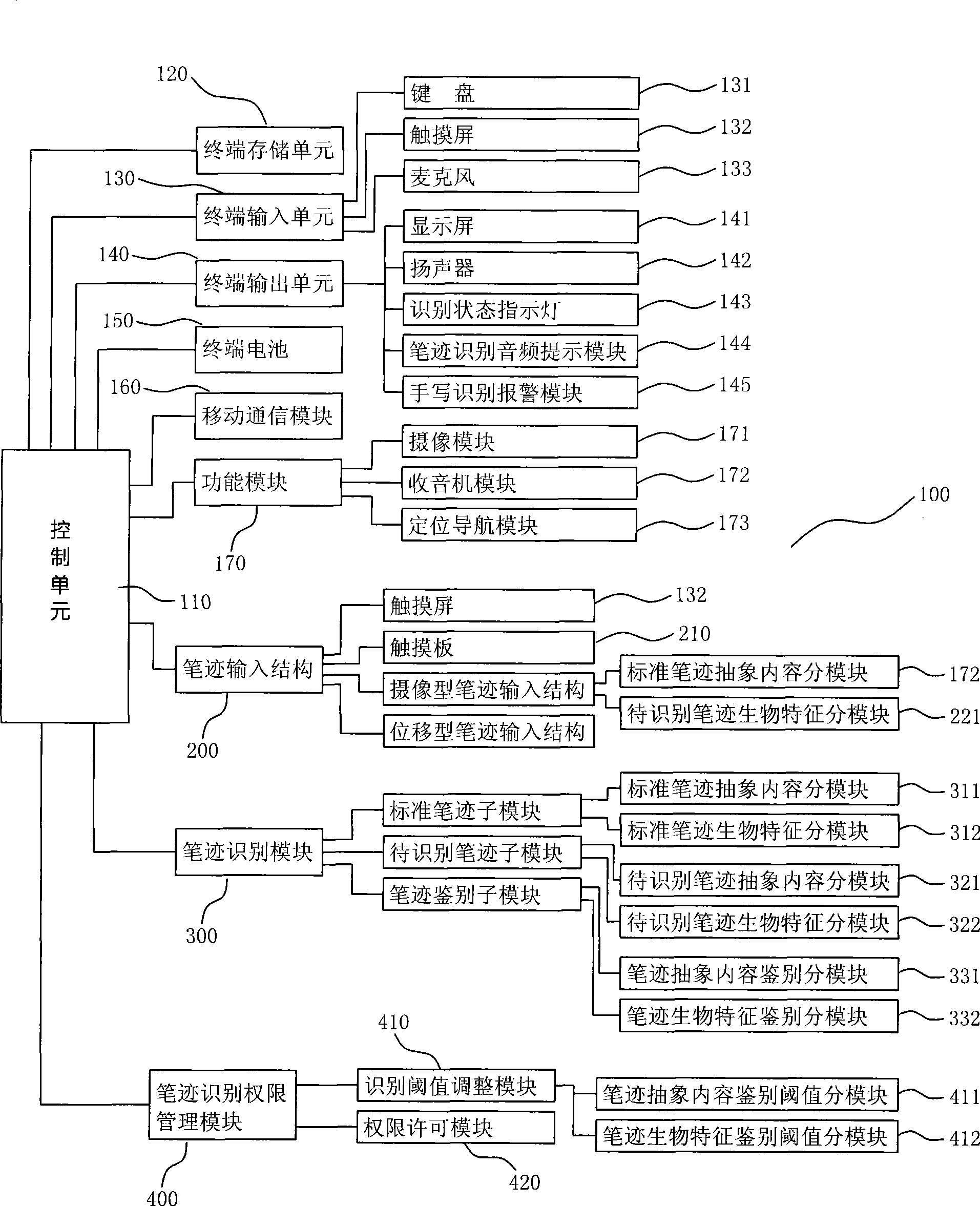
Hand-hold terminal with handwriting recognition identity affirmation function and its implementing method
InactiveCN101482904AValid identificationGuaranteed privacyCharacter and pattern recognitionComputer security arrangementsUser needsHandwriting
Owner:SHANGHAI LINGRUI INFORMATION TECH
File encryption operation method and file encryption operation system
ActiveCN102819702AImprove efficiencyImprove securityComputer security arrangementsSecuring communicationComputer hardwarePassword
The invention discloses a file encryption operation method and a file encryption operation system. The method comprises the steps of: receiving a file operation instruction; transferring an encrypted target file according to the file operation instruction; carrying out memory decryption on the encrypted target file according to key information corresponding to the encrypted target file, and operating the encrypted target file after memory decryption. According to the scheme disclosed by the invention, the password of the encrypted target file does not need to be manually input; opening and operating of the file can be achieved by decrypting the file without a manual operation, and the operating efficiency of the key information is improved. On the other hand, the encrypted target file is decrypted by the key information in the memory; the decrypted file is stored in the memory, and a permanent file is not generated, therefore, the password is not stolen by the others, and the operating security of the encrypted file is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
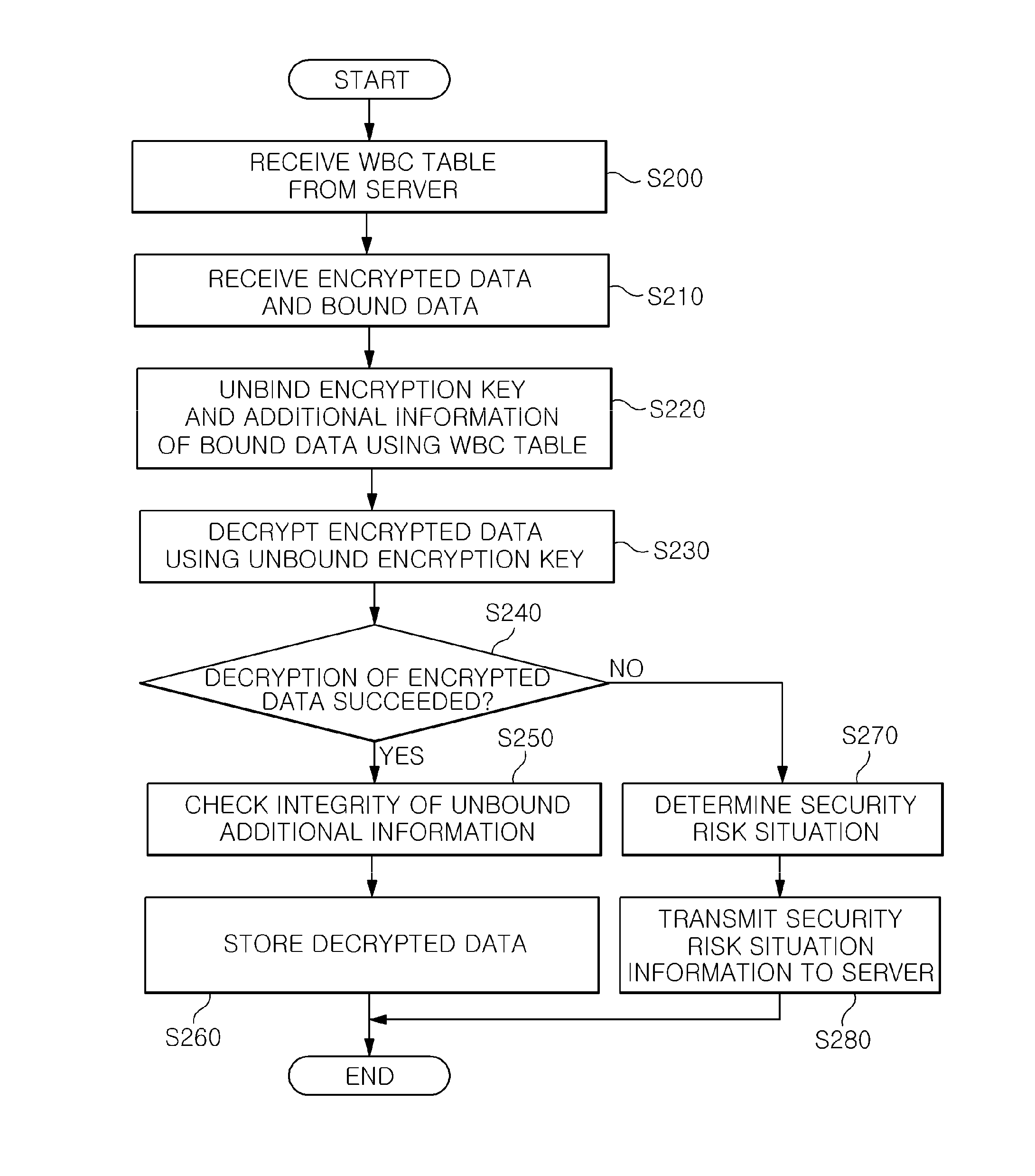
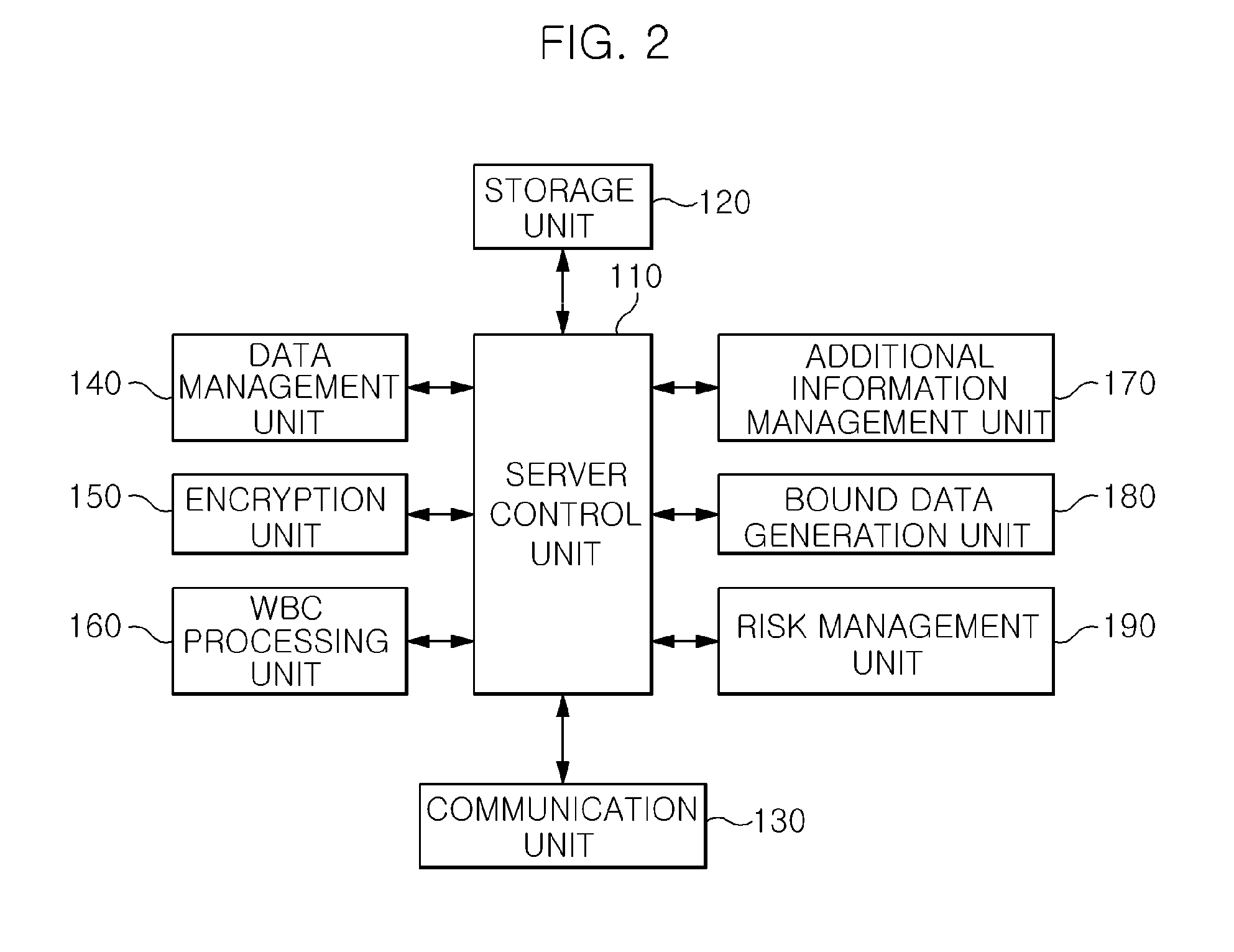
Content protection apparatus and method using binding of additional information to encryption key
InactiveUS20120099726A1Deciphering becomes impossibleKey distribution for secure communicationRandom number generatorsManagement unitProcessing element
Owner:ELECTRONICS & TELECOMM RES INST
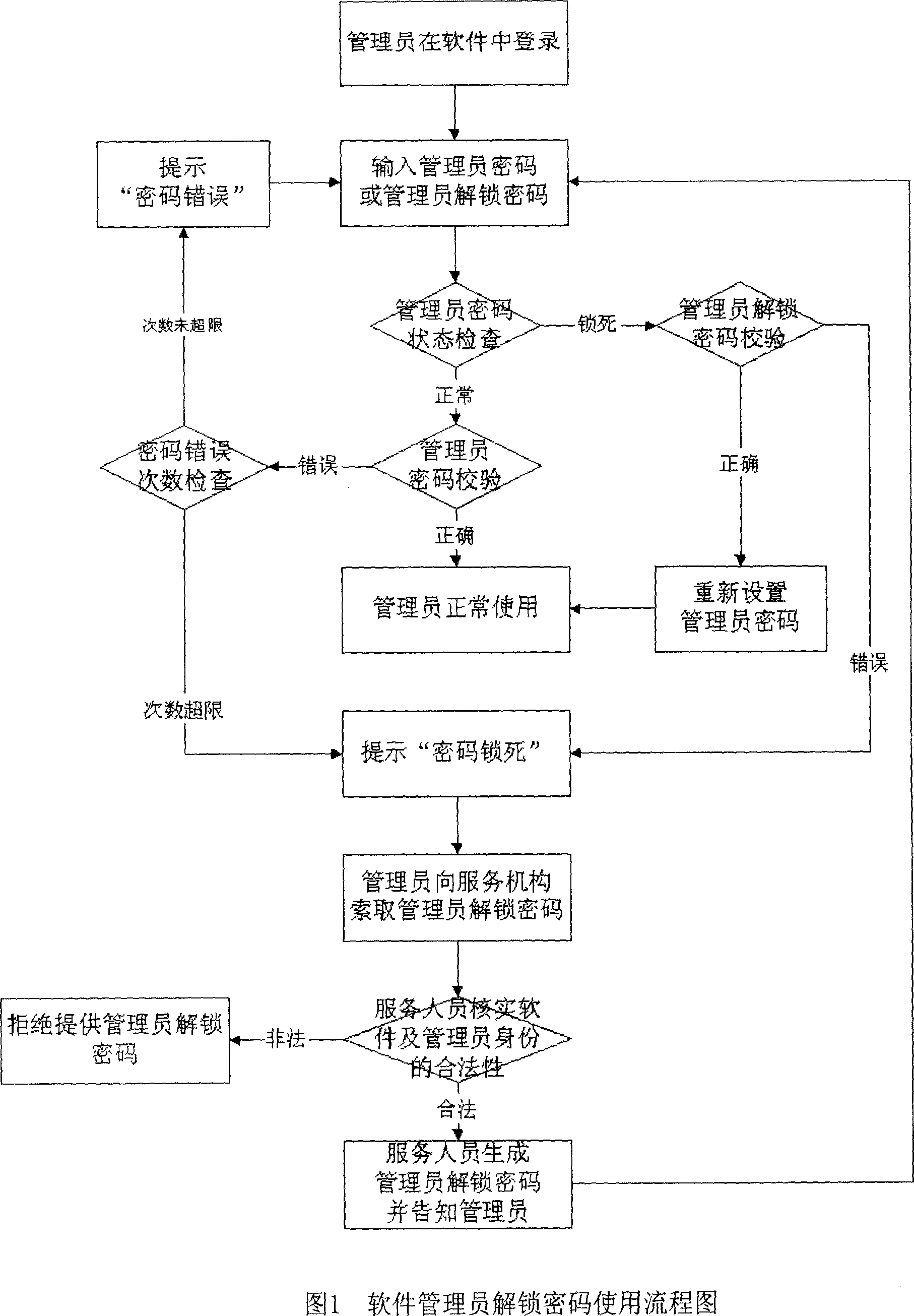
Method for administrator to unlock password
InactiveCN1967556AAvoid the disadvantages of easy leakageReduce lossesDigital data authenticationPasswordSoftware engineering
Owner:BEIJING ZHONGXINGTONG ELECTRONICS TECH
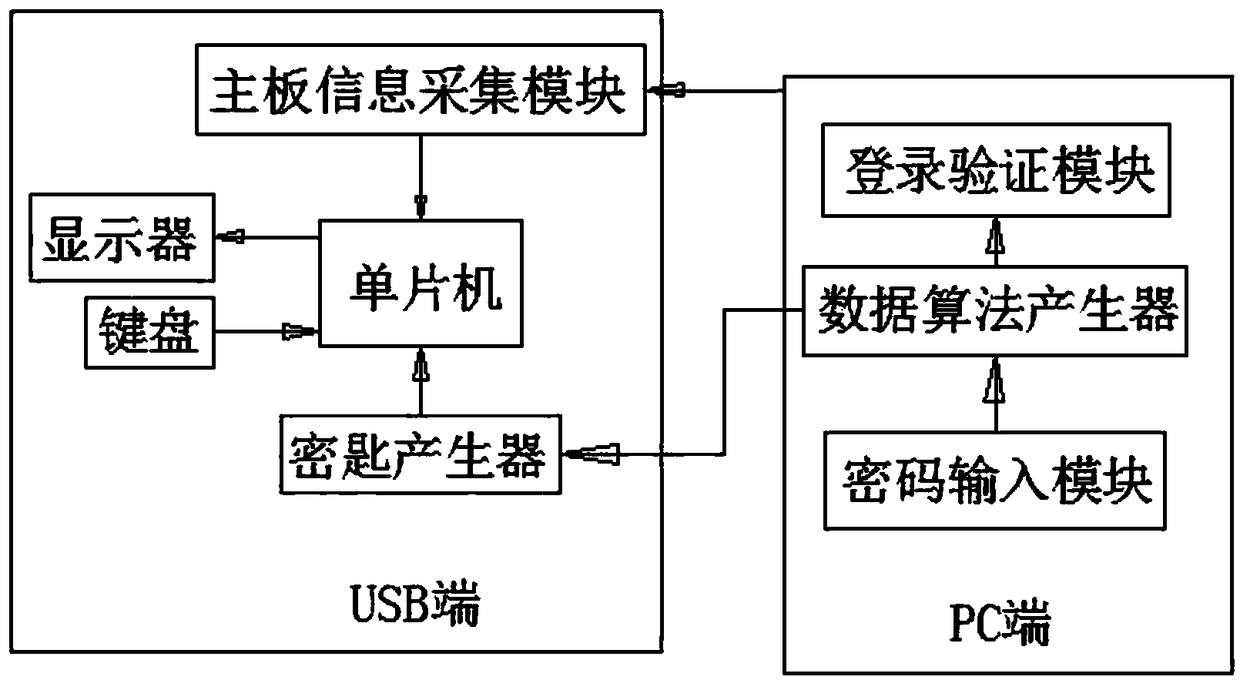
Dynamic displaying cipher keboard
InactiveCN101021756AProtection of rights and interestsPrevent password theftInternal/peripheral component protectionInput/output processes for data processingDriver circuitProcess dynamics
Owner:郭文 +1
Two-dimensional code transmitting and activation method and system
ActiveCN105761090AImprove protectionSecure coding dynamic managementCommerceActivation methodComputer hardware
Owner:深圳中检网络传媒有限公司
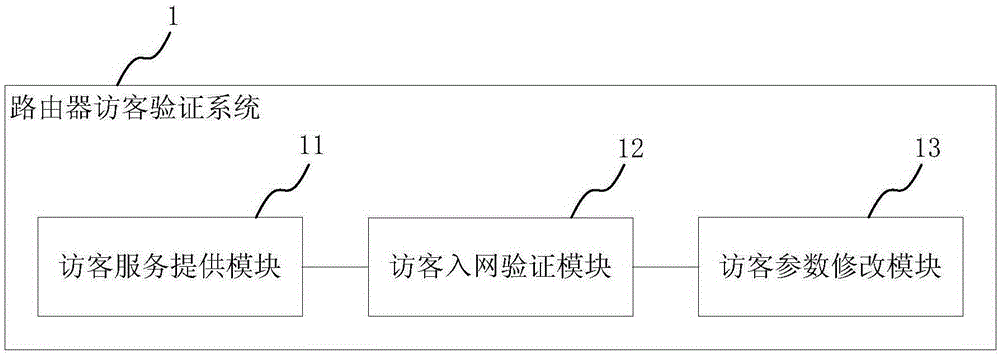
Router visitor verification method and system and router
InactiveCN105245539AEnsure safetyTransmission monitoringSecurity arrangementValidation methodsPassword
Owner:PHICOMM (SHANGHAI) CO LTD
Method for registering prompt communication user account number by utilizing E-mail addresses
Owner:王强
Cipher equipment virtualization method in cloud environment
InactiveCN106357700ATroubleshoot virtualization issuesAccess controlTransmissionVirtualizationComputer hardware
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Shared express bag
Owner:上海钊易数码科技有限公司
Lock It!
InactiveUS20160051084A1Easy to operateMaintaining food moistureCooking-vessel materialsClosuresPlastic materialsFood storage
A food storage container comprising a bottom container for storing food, an easy to lift ventilation cover and a locking lid for securing the contents of the food storage container. The locking lid is provided at the top portion thereof with a combination lock. The combination lock having a plurality of wheels and notches being aligned with numbers on a rotatable dial. The combination lock is provided with lock bolts and engageable locking cases on both sides preventing the food storage container from opening. The food storage container is preferably formed from dishwasher-safe and microwave-safe materials. The combination lock of the present invention can be formed from a metal, glass or plastic material.
Owner:MARTINEZ SHAINA
Protection device used for bank hardware code
InactiveCN104301118ASolve technical problems of potential safety hazardsPrevent leakageMultiple keys/algorithms usageUser identity/authority verificationCipher
The invention discloses a protection device used for a bank hardware code. The protection device comprises three layers of code protection modules, the code protection module on the first layer is used for setting a mark secrete key, the code protection module on the second layer is used for encrypting or decrypting a work secrete key, the code protection module on the third layer is used for setting a data secrete key, and the mark secrete key is used for encrypting the code protection module on the second layer, generating a signature and verifying the signature. The code protection module on the third layer is a secrete key used for encrypting data in the work secrete key and used for encrypting sensitive data, wherein encryption operations of the sensitive data include the steps that the sensitive data undergo desensitization processing, whether the desensitized data meet predefined desensitization requirements is judged, and the hardware code is stored when the desensitized data meet the predefined desensitization requirements. The protection device has the advantages that sensitive information in banks is prevented from being let out and safety is guaranteed.
Owner:CHENGDU SHUANGAOYANG TECH
Method of generating and verifying pure software dynamic password
InactiveCN106254068AImprove securityPrevent peepingKey distribution for secure communicationComputer hardwareSoftware system
Owner:张晓辉 +1
Intelligent door lock system capable of automatically judging abnormal state of door lock
ActiveCN112150672AAchieve protectionEasy to implementIndividual entry/exit registersComputer hardwareAttack
Owner:NANJING LES CYBERSECURITY & INFORMATION TECH RES INST CO LTD
Key management method and system supporting multiple key systems
ActiveCN112054901AEnsure safetyPrevent theftKey distribution for secure communicationPasswordEngineering
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Mobile phone hotspot controlled keyhole-free safety box
InactiveCN110056285AStop theftNon-mechanical controlsIndividual entry/exit registersElectromagnetic lockPassword
Owner:路越
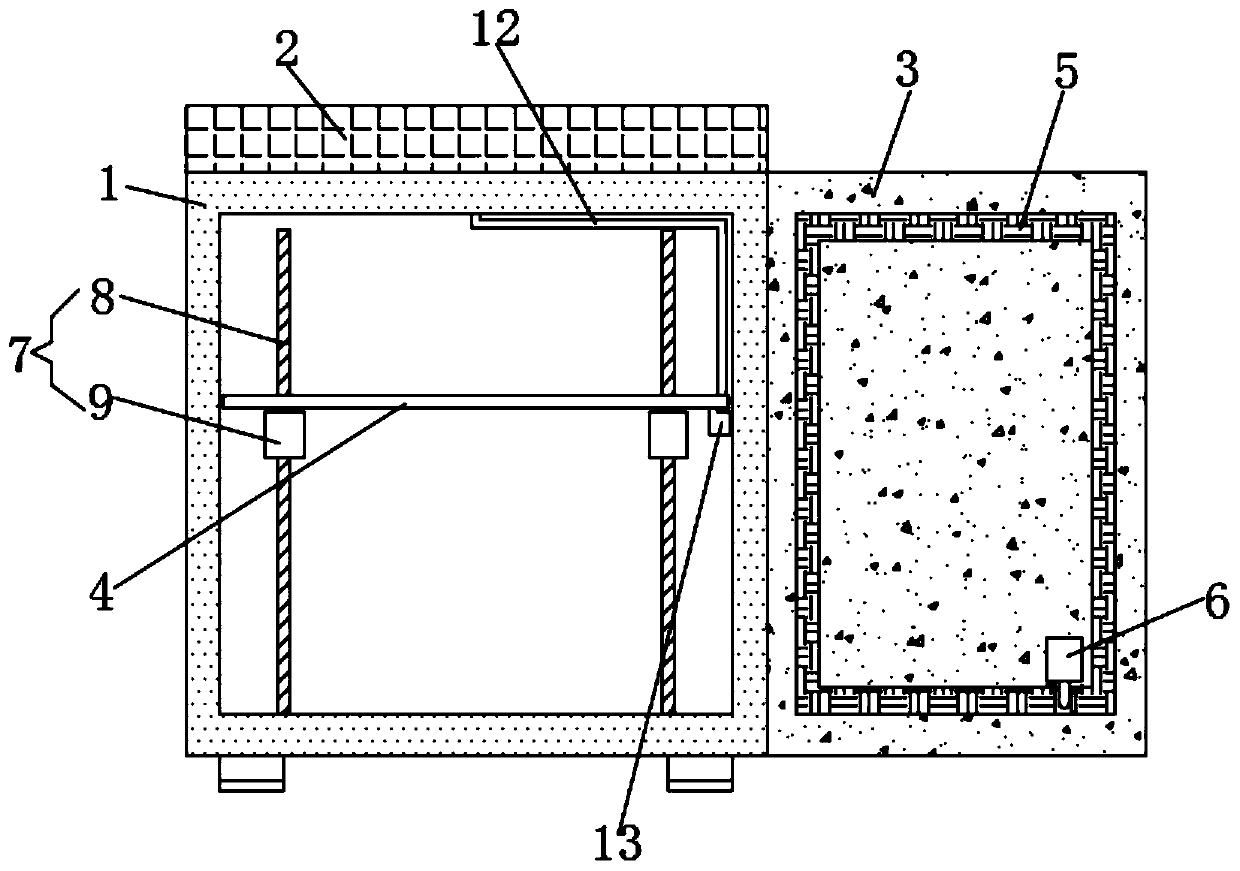
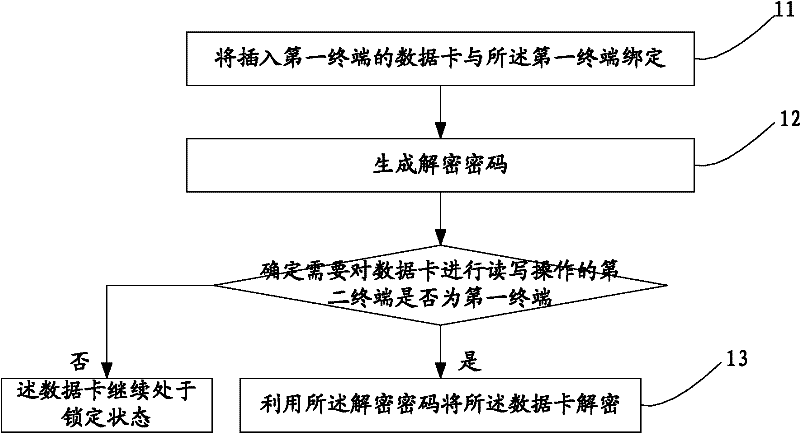
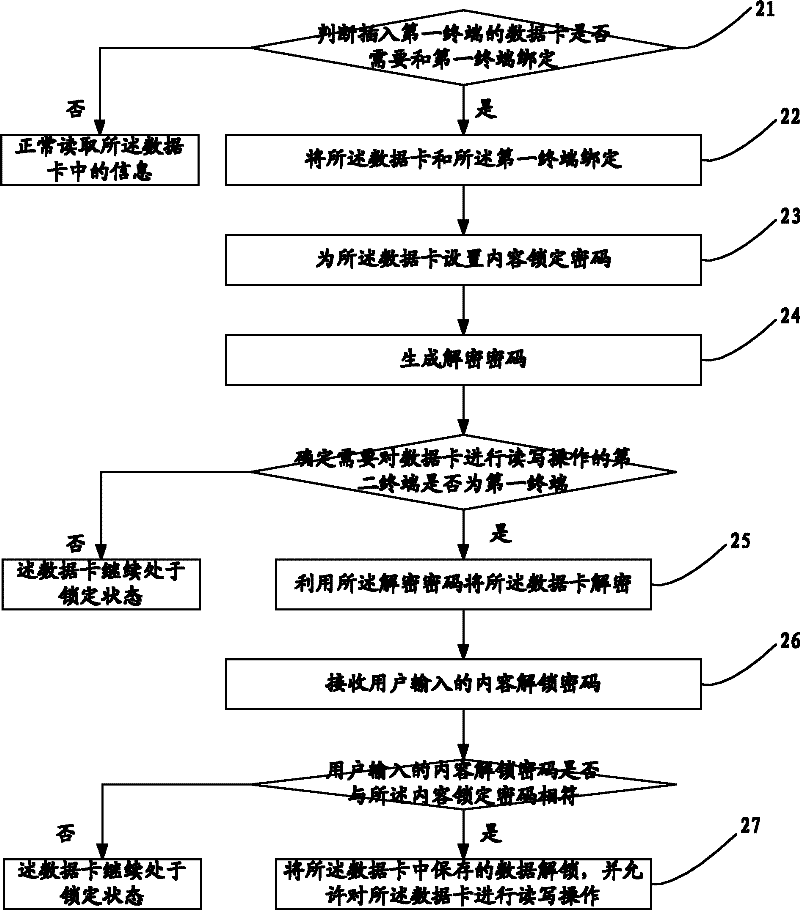
A method and device for improving data card security
InactiveCN102270183AImprove securityUnauthorized memory use protectionRecord carriers used with machinesPasswordCipher
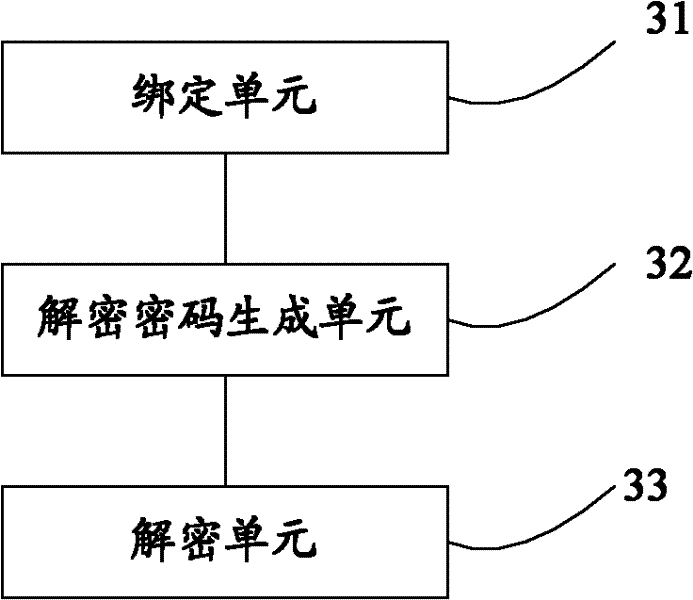
The embodiment of the invention discloses a method and a device for improving the security of a data card, which relate to the field of information security and are invented for improving the security of information in the data card. The method includes: binding the data card inserted into the first terminal with the first terminal; generating a decryption password; when the data card needs to be read and written, determining that the data card needs to be read and written Whether the second terminal is the first terminal, and if so, use the decryption password to decrypt the data card. The embodiments of the present invention are mainly used in various data cards.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Electronic retrieval file box
InactiveCN107718928ASolve the problem that cannot be used at the same timePlay a double layer of protectionFiling appliancesInternal memoryPassword
Owner:陈红燕
Unlicensed vehicle recognition system
InactiveCN106327853ANon-electrical signal transmission systemsRoad vehicles traffic controlIn vehicleRemote control command
The invention relates to an unlicensed vehicle recognition system. An inspector holding a remote controller (103) presses different buttons to send different remote control instructions which are transmitted to a vehicular controller (102) in a wireless or infrared manner; the vehicular controller (102) controls a plurality of top lights (101) in different colors to flicker according to different color sequences or controls the top lights (101) in different colors to be lighten according to different combinations; the vehicular controller (102) controls a speaker (104) to give out different voices or melodies; if no display or sound is detected, the lights in different colors are not right in display sequence or display combination, or the sound or the melodies are not right, an inspected vehicle is possibly an unlicensed vehicle. The inspector holding the remote controller (103) presses different buttons, the vehicular controller (102) receives the remote control instructions and replies a string of code data through wireless or infrared signals, and various existing encryption algorithms can be adopted for encryption; if no code data is replied or the replied code data are not right, the inspected vehicle is possibly an unlicensed vehicle.
Owner:HANGZHOU HOPECHART
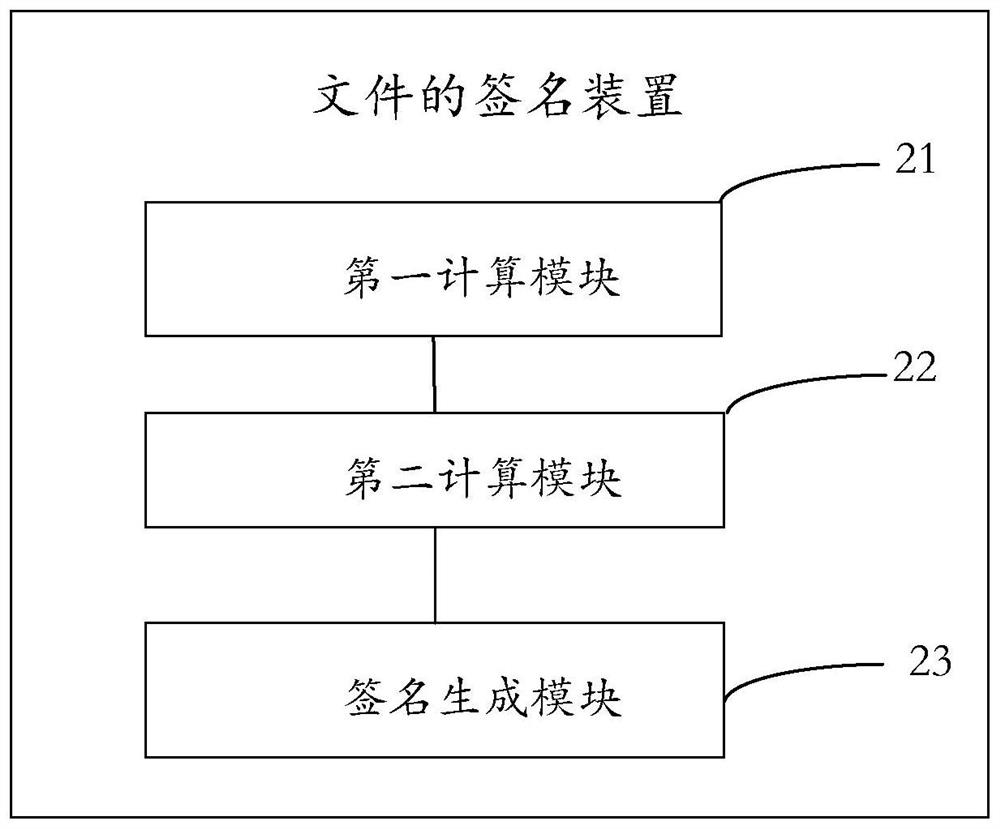
File signature method and device, terminal and storage medium
PendingCN114329542AReduce computing pressureAchieve the effect of blind signingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkSignature file
Owner:上海市数字证书认证中心有限公司
Method for defensing zero power consumption attack on code device
ActiveCN103001762AGood resistance to zero power consumption attack performanceReasonable speedEncryption apparatus with shift registers/memoriesMultiplexingCoprocessor
The invention discloses a method for defensing zero power consumption attack on a code device. The method is characterized in that inverse operation on a GF (28) finite field in a byte replacing module is replaced with GF (28) field additivity shielding inverse operation. The specific process is that inverse operation is first conducted on the GF (28) finite field, then the GF (28) field additivity shielding inverse operation is conducted, and a simpler GF (256) field additivity shielding inverse algorithm is provided by adopting a key module multiplexing method on the base that the traditional improved advanced encryption standard is analyzed. The method has the advantages of maintaining good zero power consumption attack resistance, being reasonable in area expense and circuit speed and capable of being widely applied to coprocessors and fields with high requirements for area, speed and security.
Owner:NINGBO UNIV
An encryption system for accounting software
PendingCN109214147AEnsure safetyUniqueness guaranteedDigital data protectionProgram/content distribution protectionMicrocontrollerMultiple encryption
Owner:INNER MONGOLIA NORMAL UNIVERSITY +1
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap