Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4 results about "Session key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A session key is a single-use symmetric key used for encrypting all messages in one communication session. A closely related term is content encryption key (CEK), traffic encryption key (TEK), or multicast key which refers to any key used to encrypt messages, as opposed to other uses, like encrypting other keys (key encryption key (KEK) or key wrapping key).
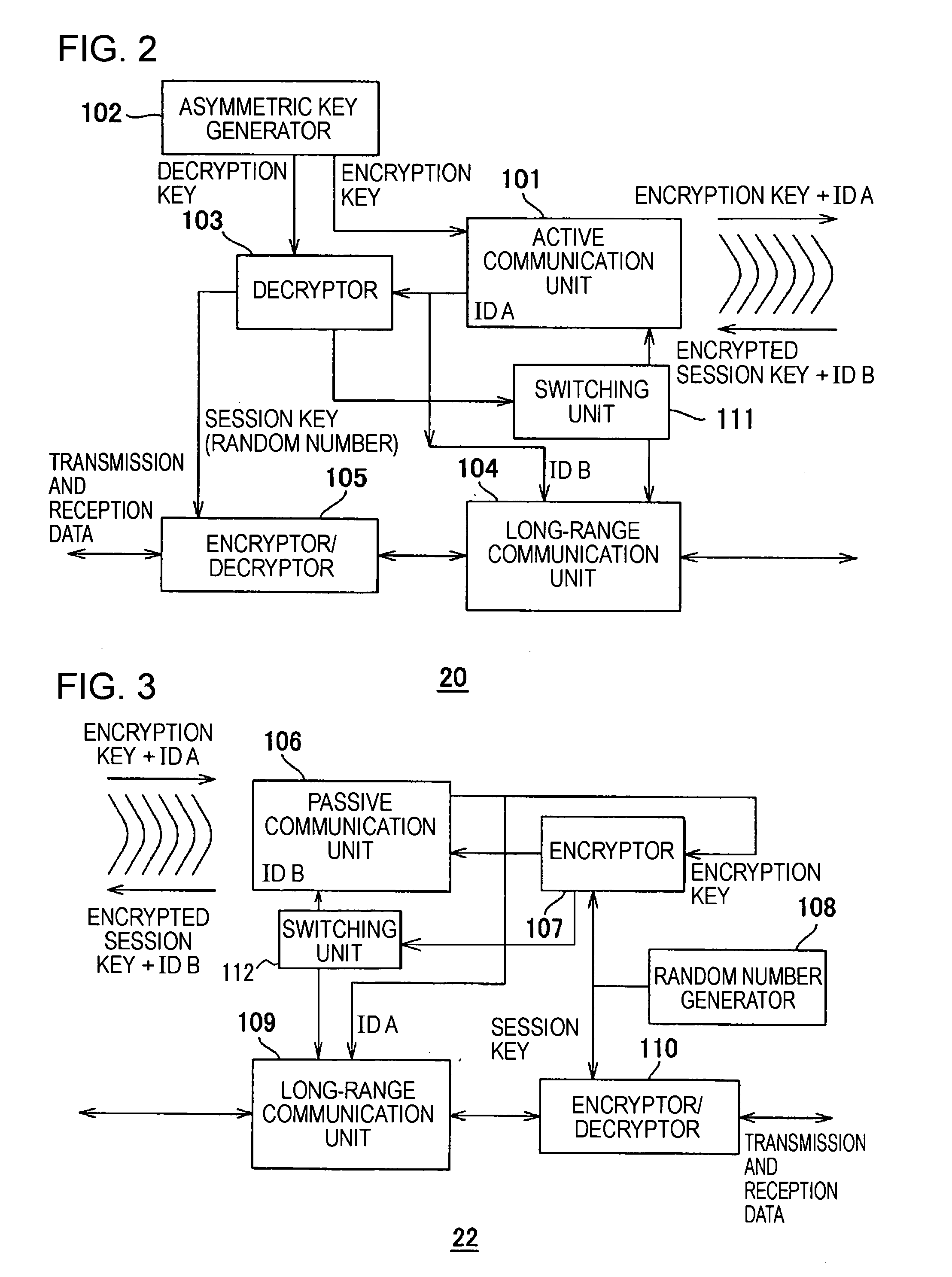
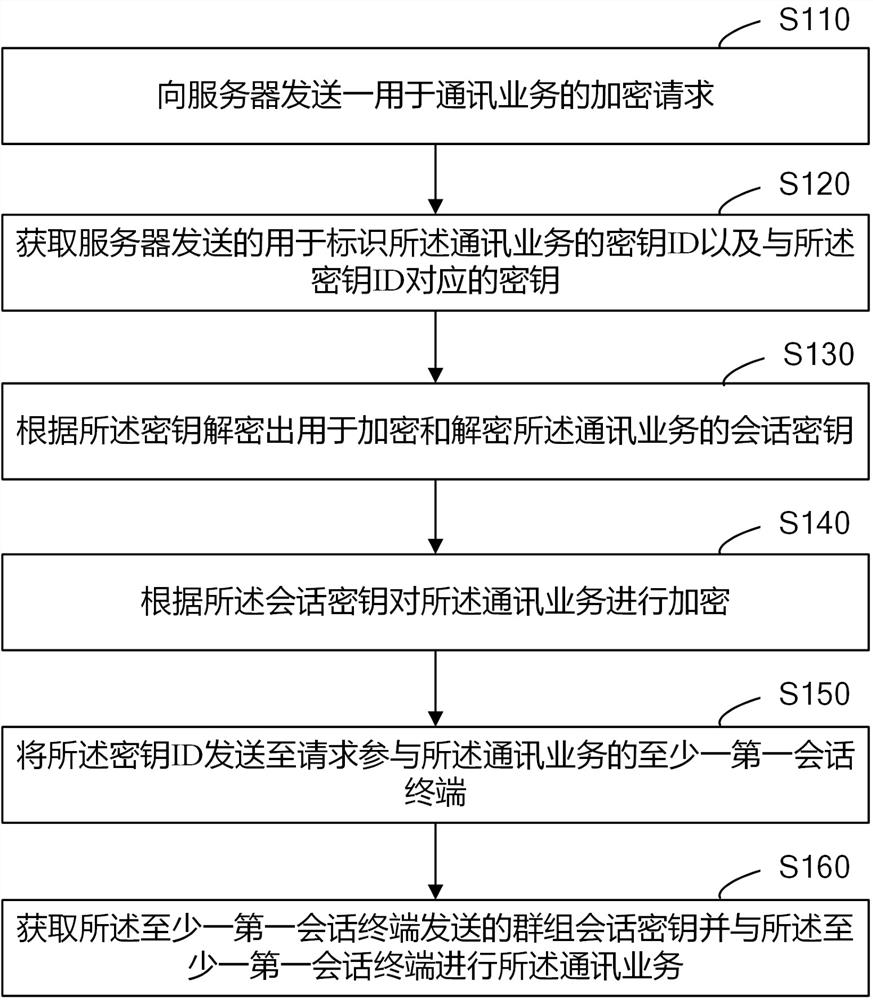
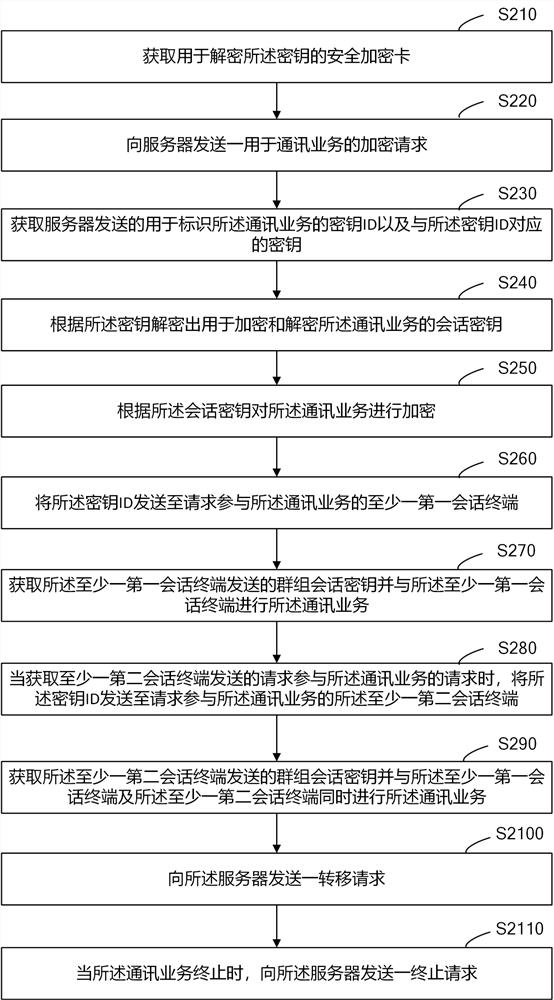
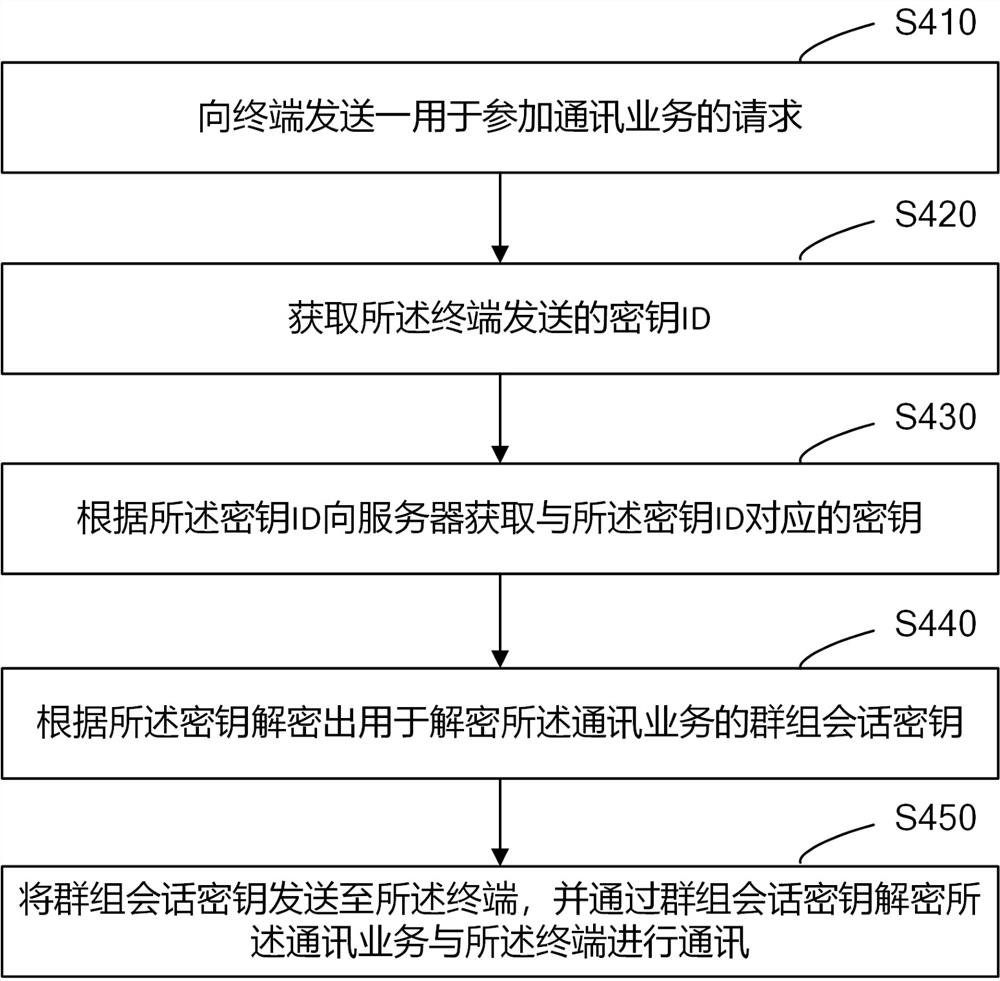
Communication System And Communication Device
InactiveUS20080020707A1Easy to identifyReduce riskKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCommunications system
Owner:SONY CORP
CDMA port-to-port encryption communication system and key distribution method thereof
InactiveCN101635924AImprove securityReduce security risksSecurity arrangementCommunications securityCommunications system
The invention discloses a CDMA port-to-port encryption communication system and a key distribution method thereof, the CDMA port-to-port encryption communication system comprises a CDMA network and a terminal mobile telephone thereof, a public switched telephone network and a terminal fixed-line telephone thereof, a short message service center as well as the following three cipher processing units including a cipher chip of a mobile telephone terminal, a key distribution management center (KDMC) and a Firmware cipher module of a gateway mobile switching center. The key distribution management center is used for key distribution management of the communication system. The key distribution is realized by a layered distribution method, i.e. a first layer is an equipment key which is distributed in the process of initialization; a second layer is a key-encryption key and a short message service key which are distributed in startup of an enciphered mobile telephone; and a third layer is a session key which is distributed every time a session is launched between the enciphered mobile telephones. At the same time, by adopting a bidirectional certification technology for key distribution and combination of a key update and remote destroying method, the safety risk in key exposure is reduced, and the communication safety is improved.
Owner:CETC CYBERSPACE SECURITY TECH CO LTD
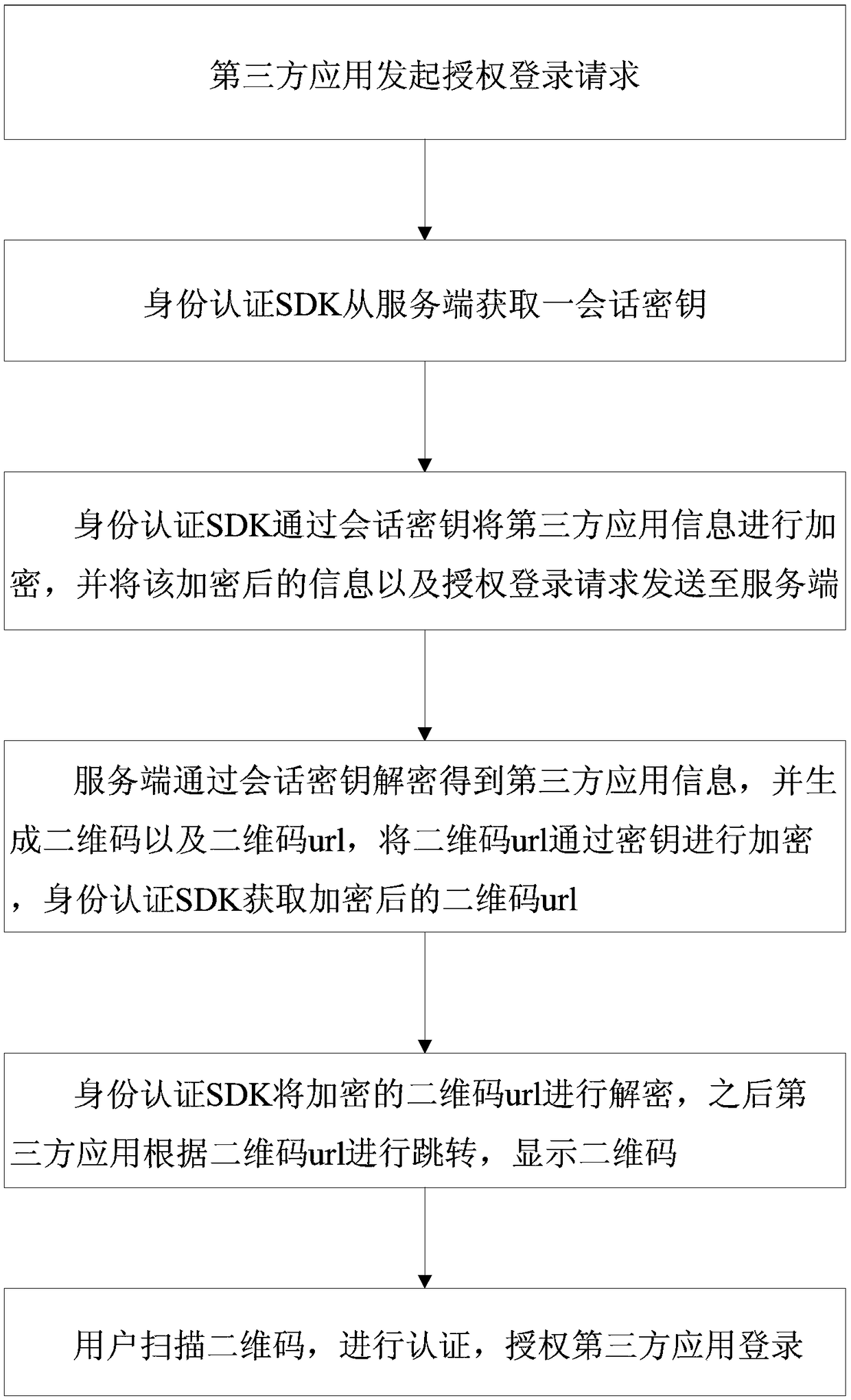
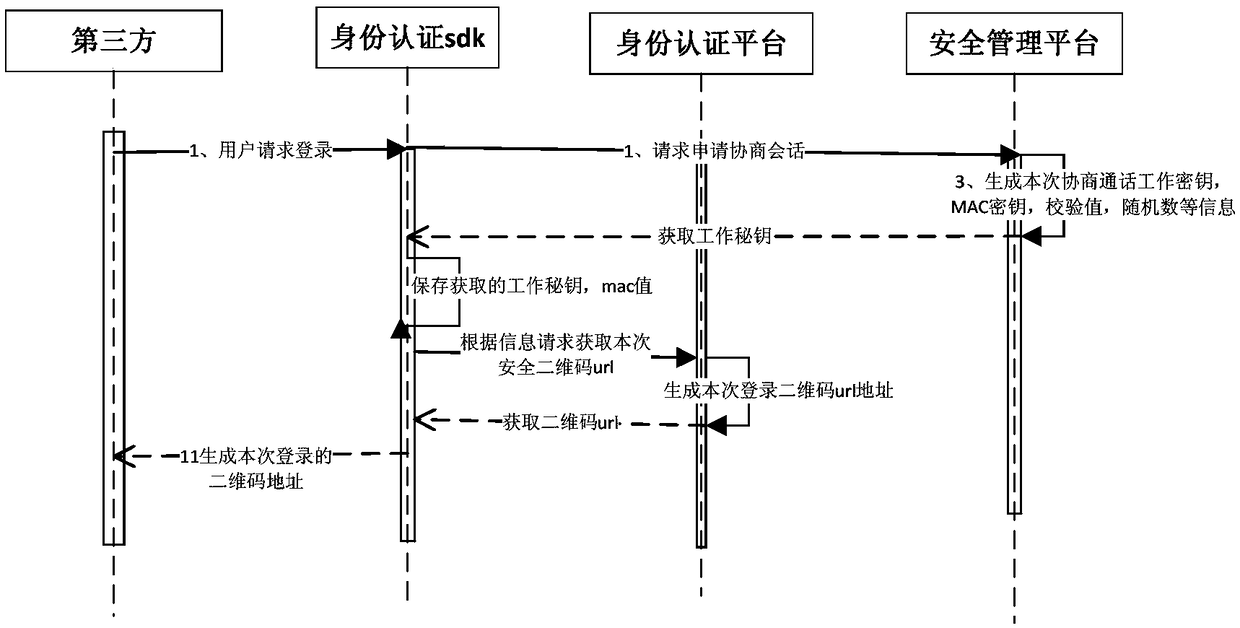
Digital identity authentication method and system based on secure two-dimensional code
Owner:新大陆(福建)公共服务有限公司
Information encryption, decryption and control method and device and electronic equipment
InactiveCN112260832AImplement the encryption functionImplement the decryption functionKey distribution for secure communicationTelevision conference systemsStationInternet privacy
Owner:南京易科腾信息技术有限公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap