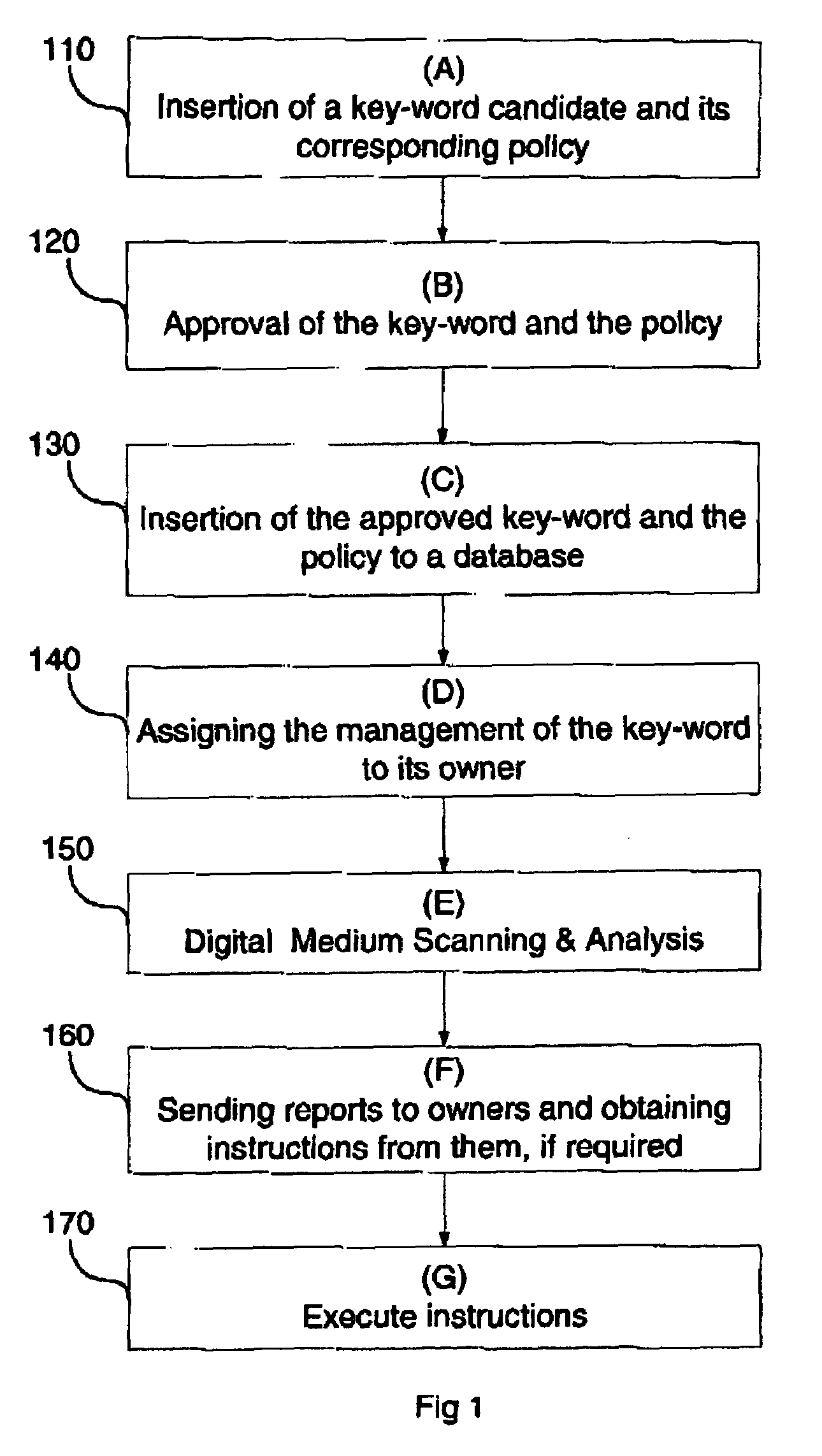
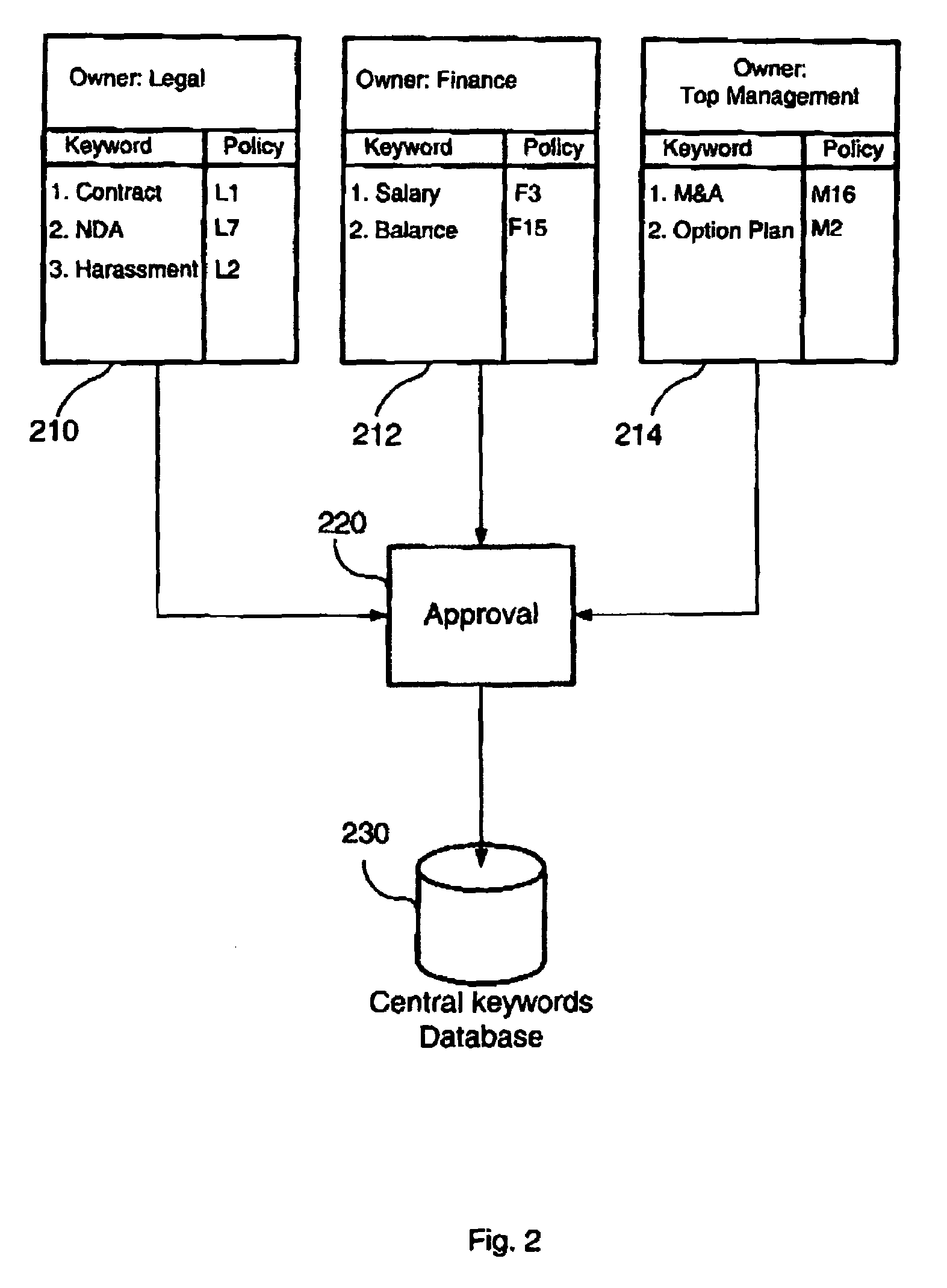
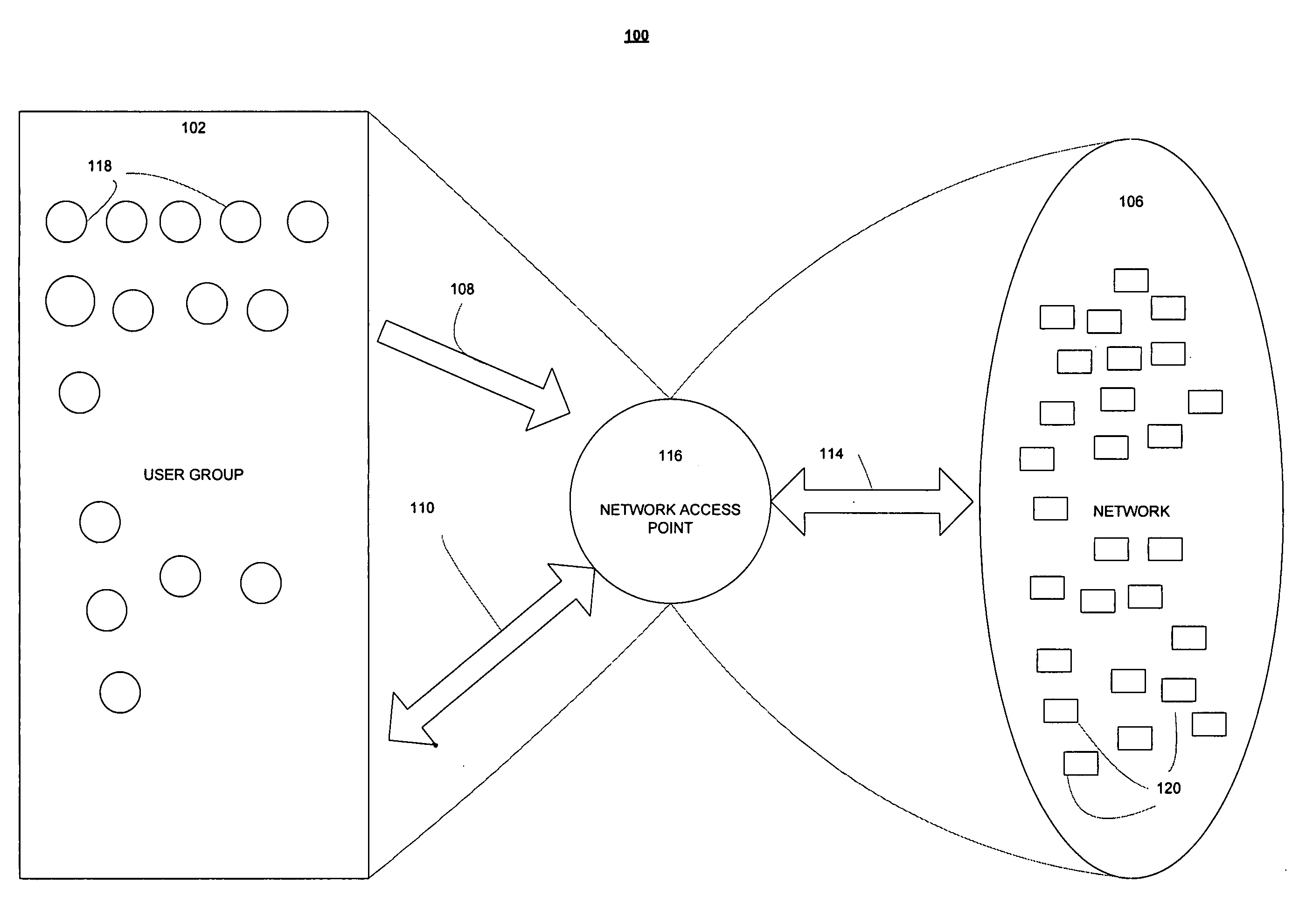
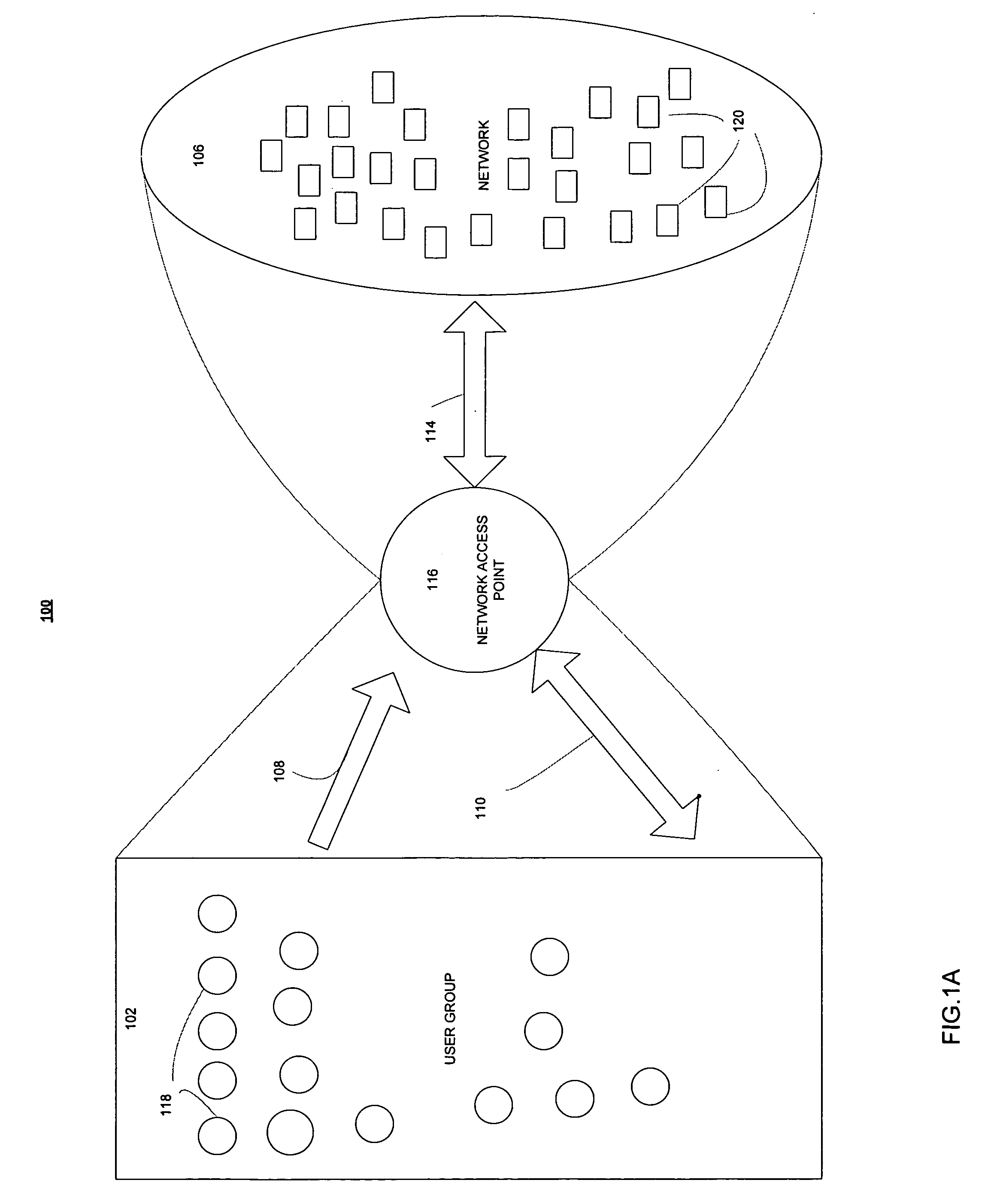
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
43results about "Analogue secracy/subscription systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
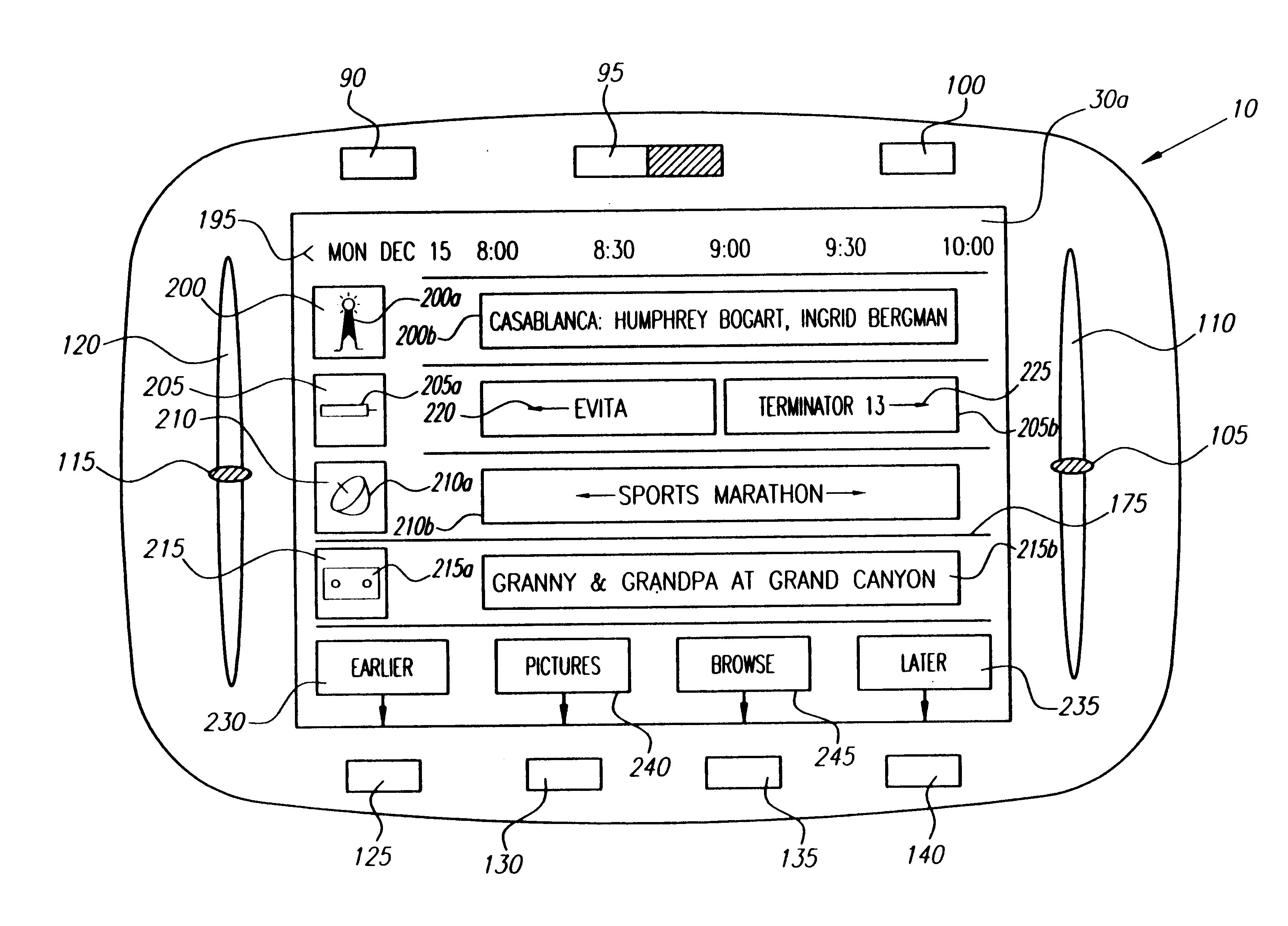
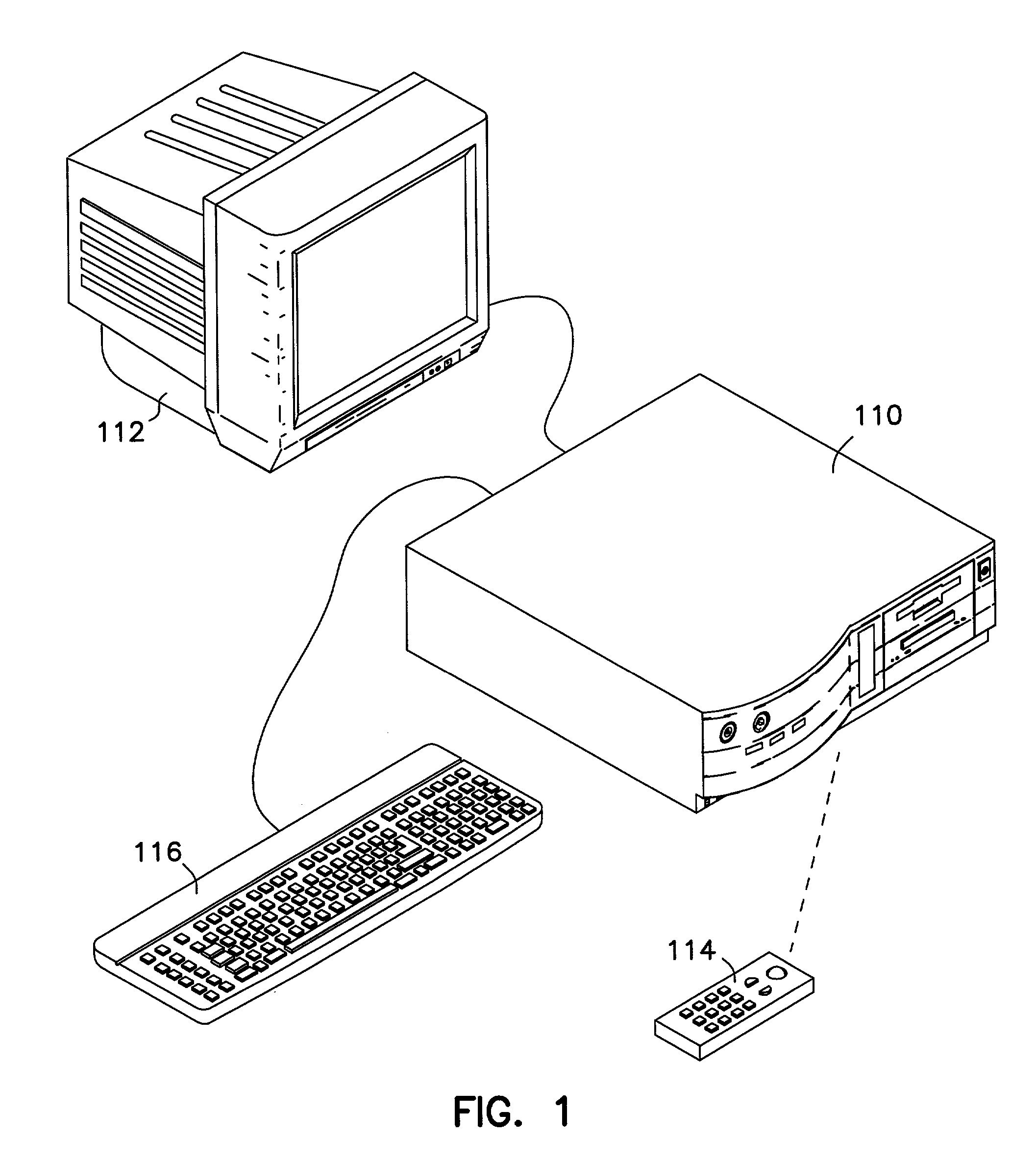
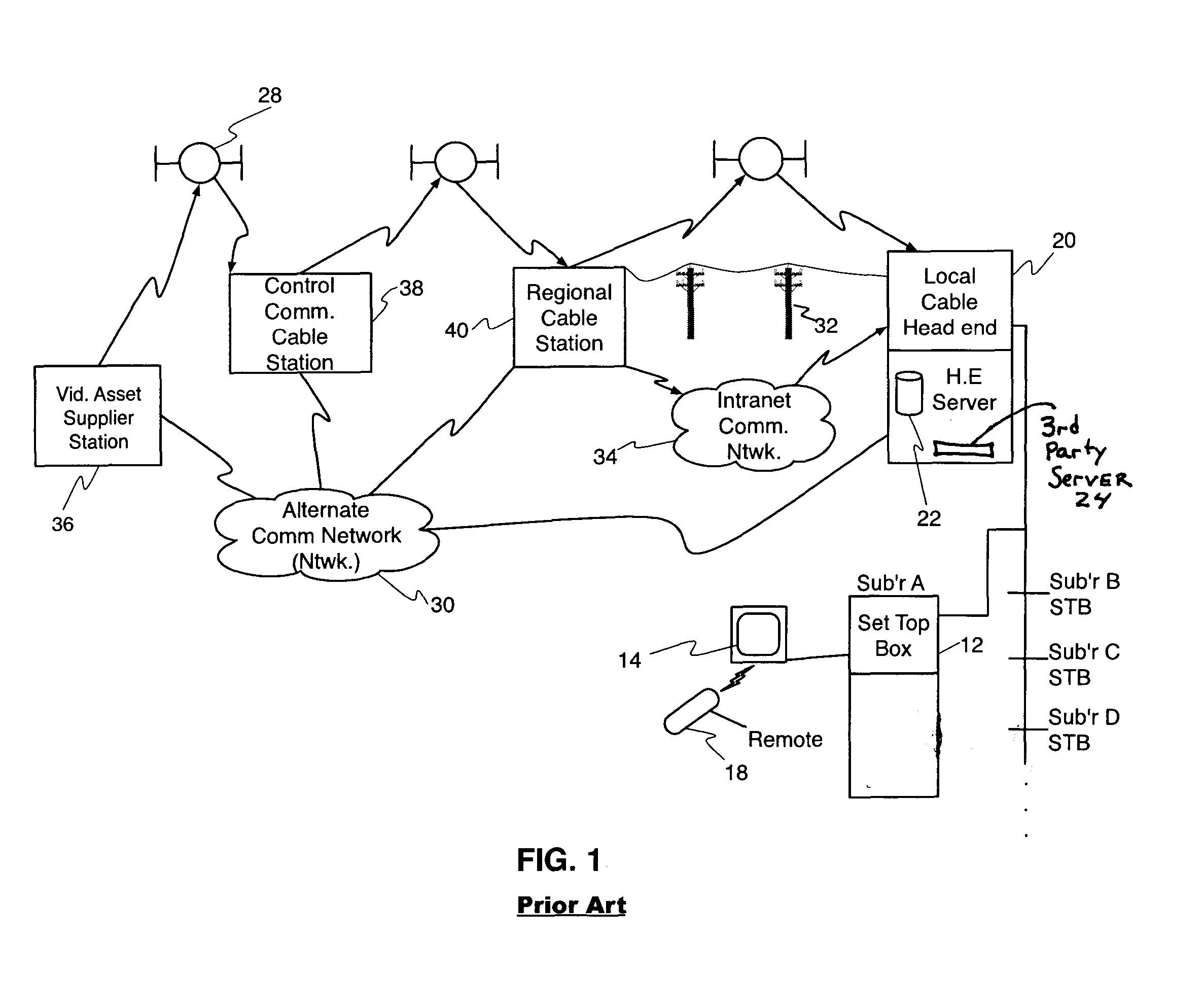
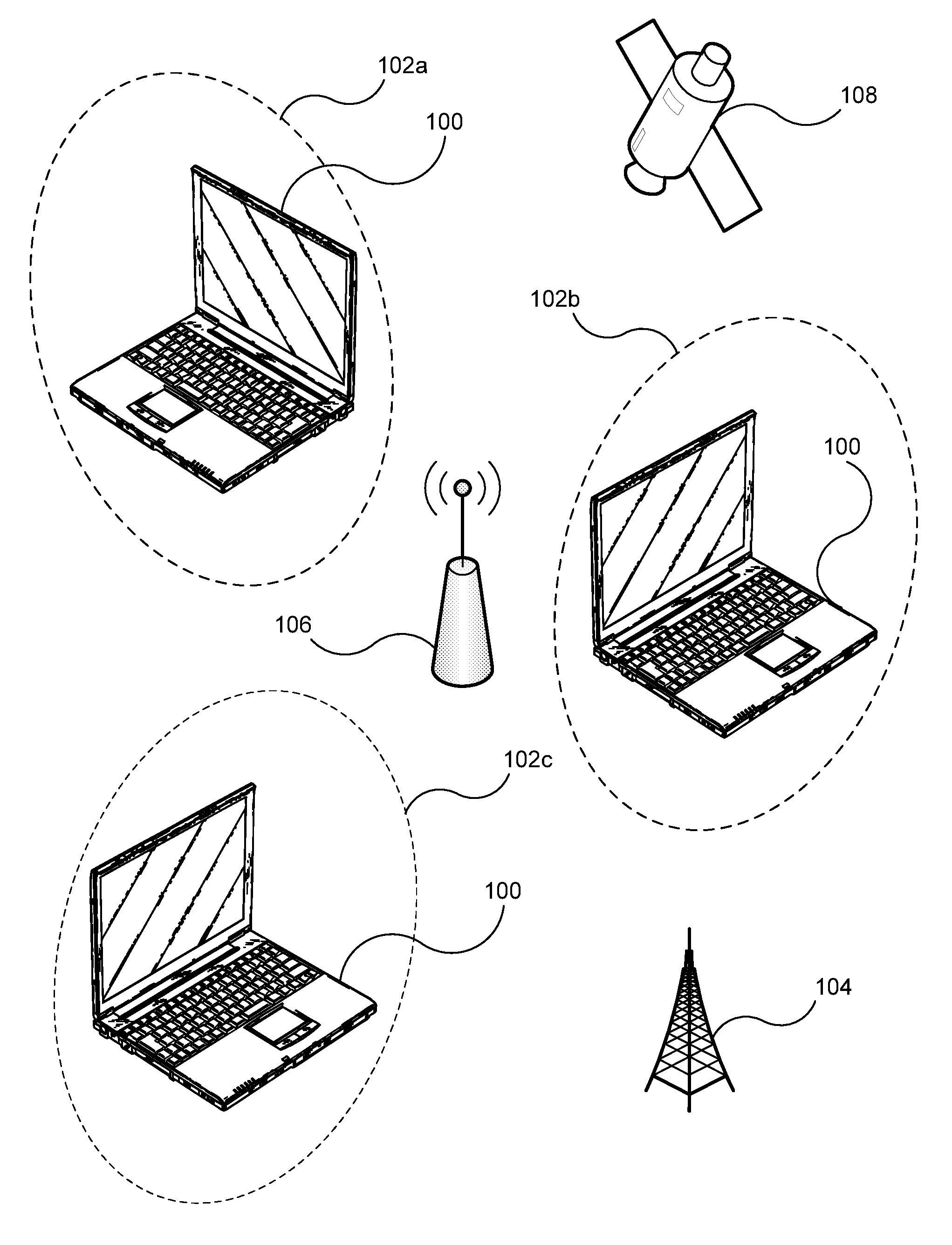
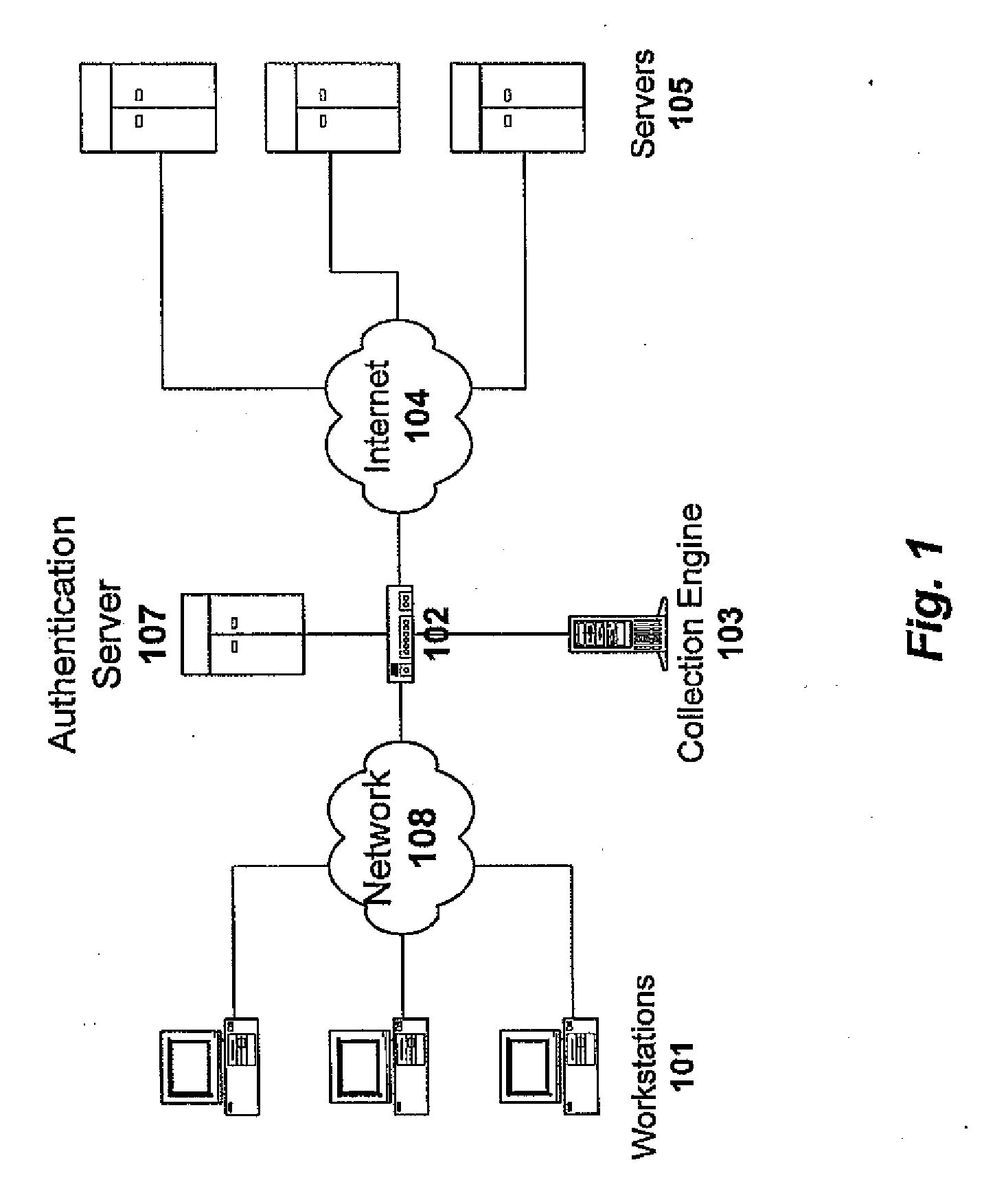
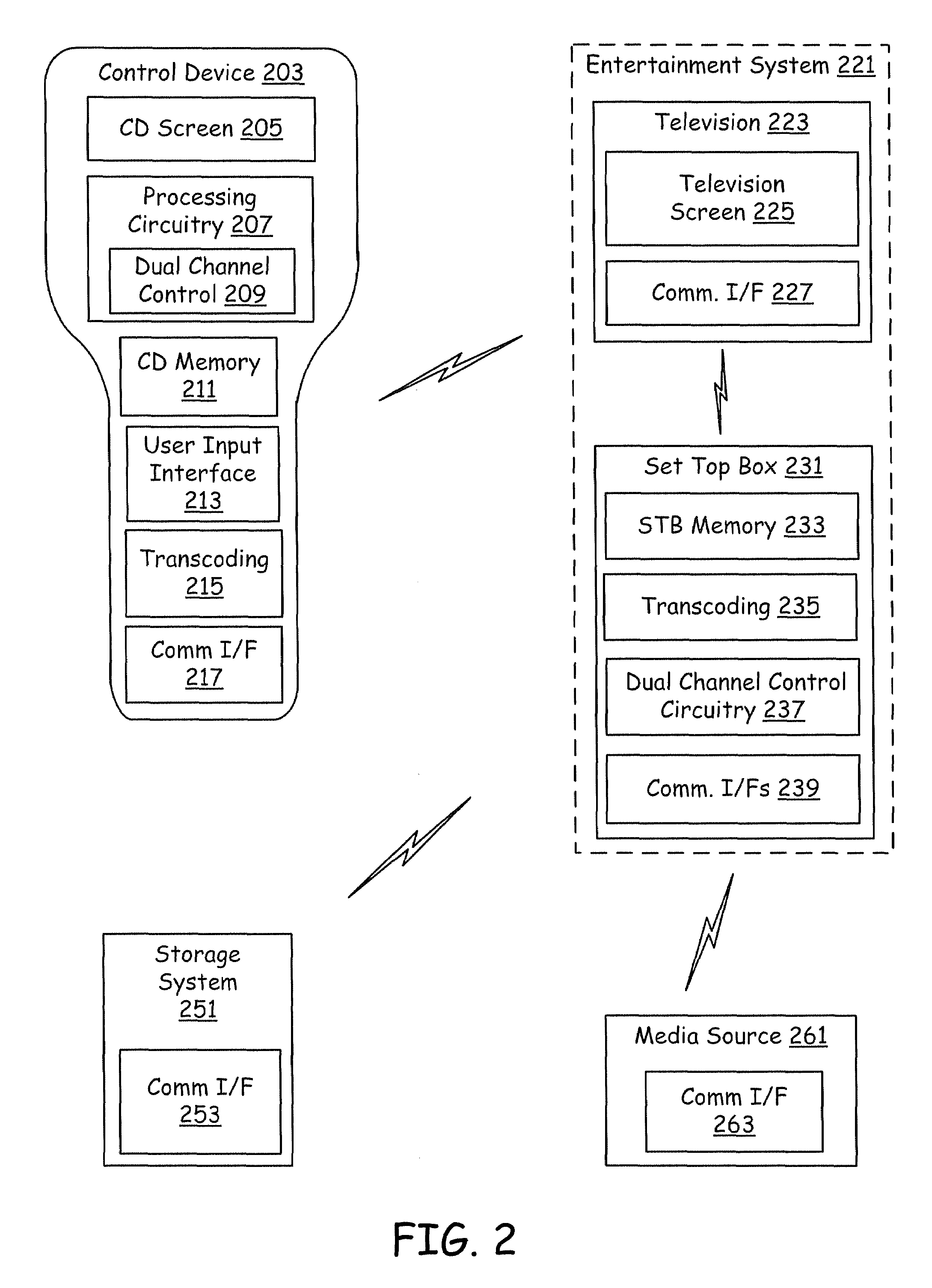
Portable internet-enabled controller and information browser for consumer devices
InactiveUS6882299B1The process is simple and easy to understandTelevision system detailsElectric signal transmission systemsGraphicsRemote control
Owner:RES INVESTMENT NETWORK
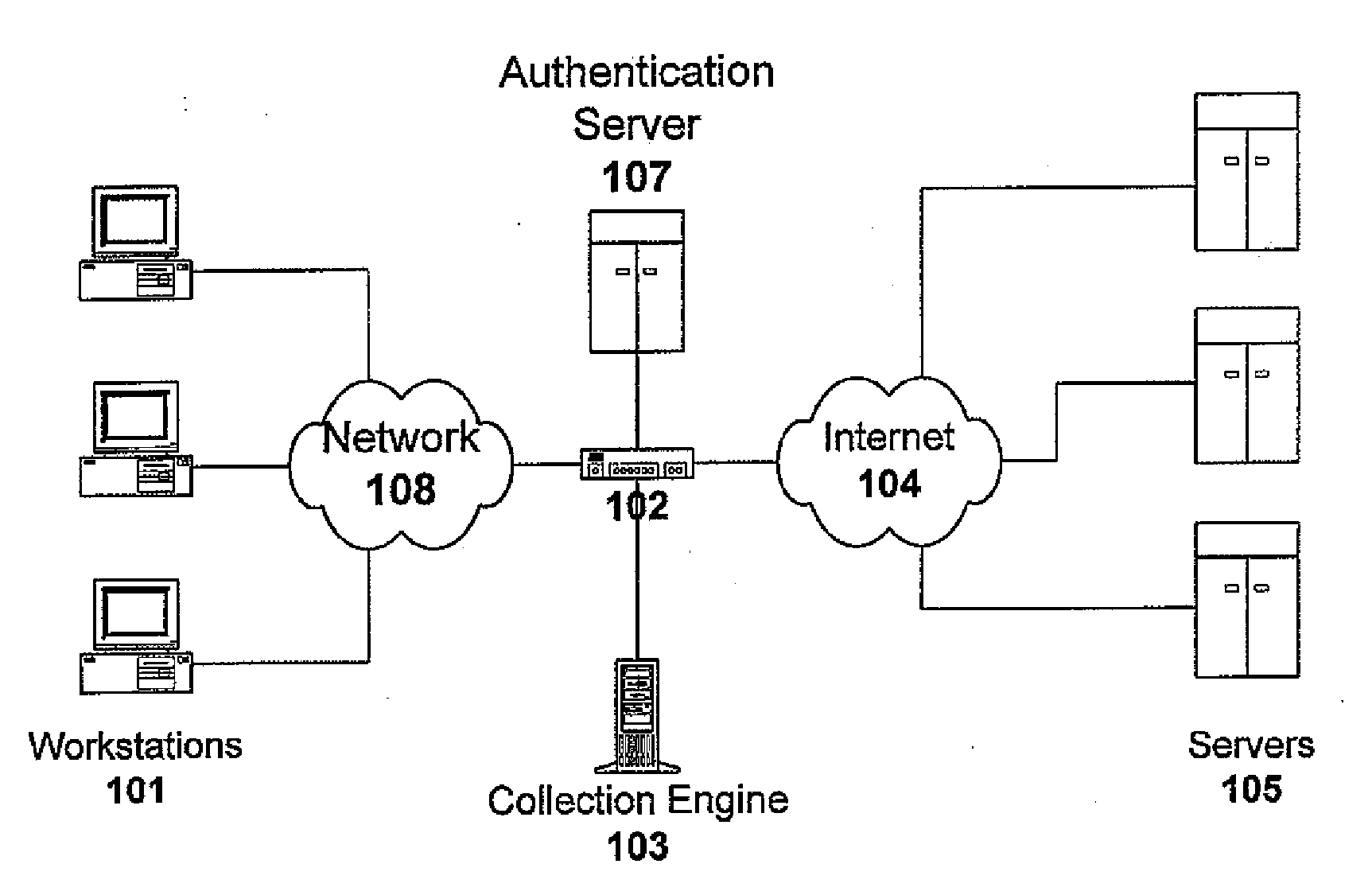
Methods for combating malicious software
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
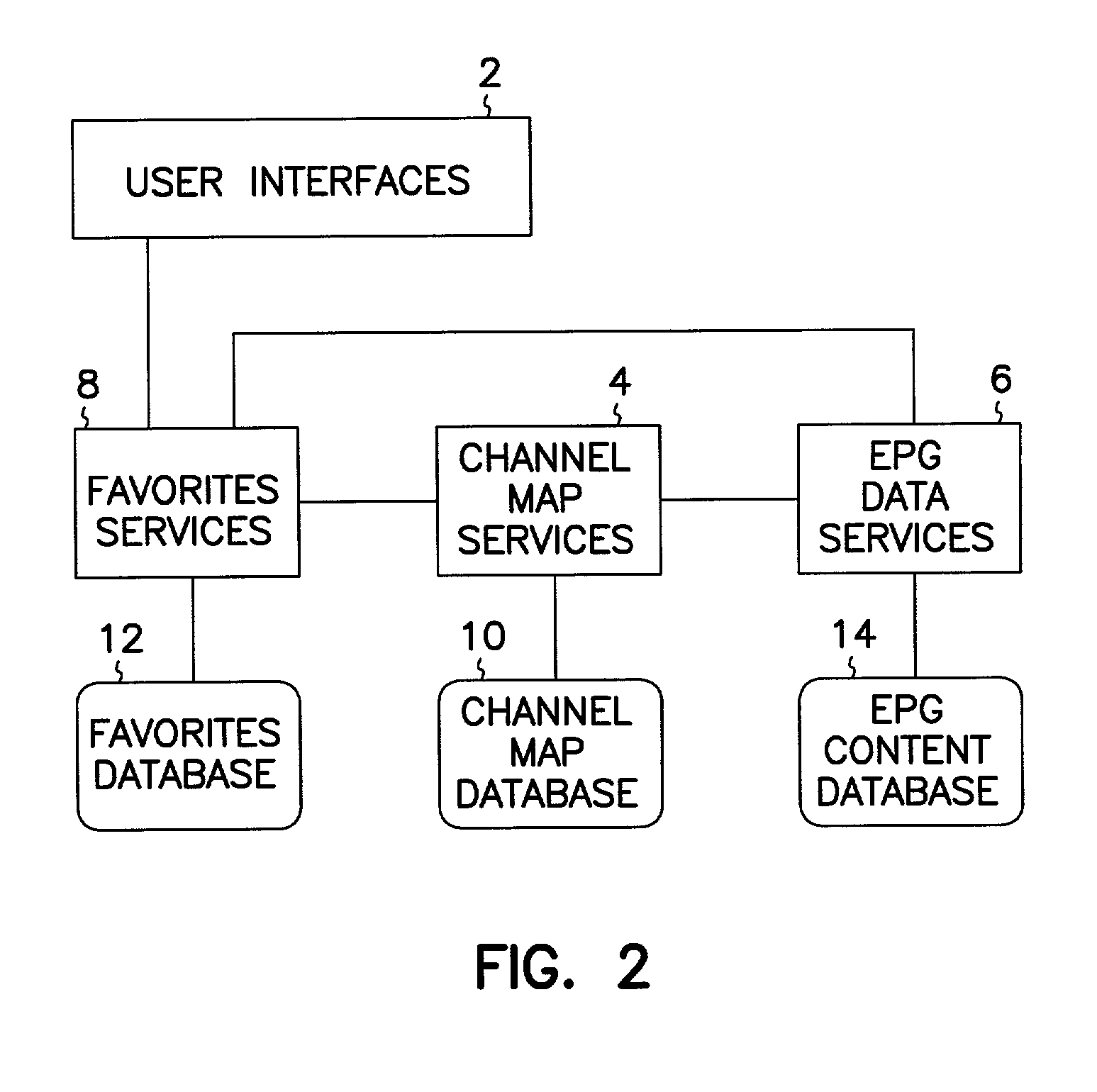
System for managing favorite channels
InactiveUS20030056216A1Television system detailsAnalogue secracy/subscription systemsComputerized systemPersonal computer
Owner:AMIGA DEV
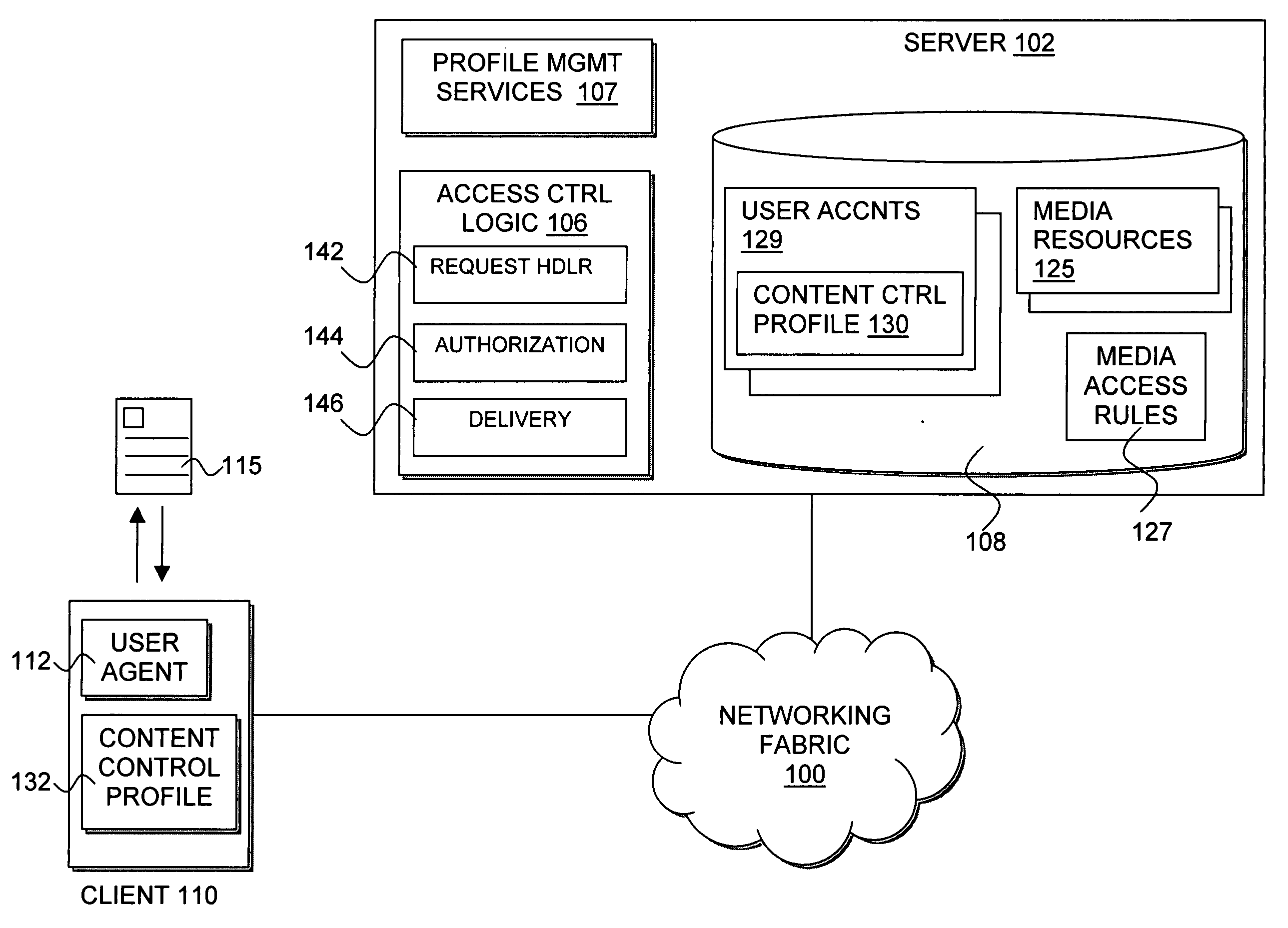
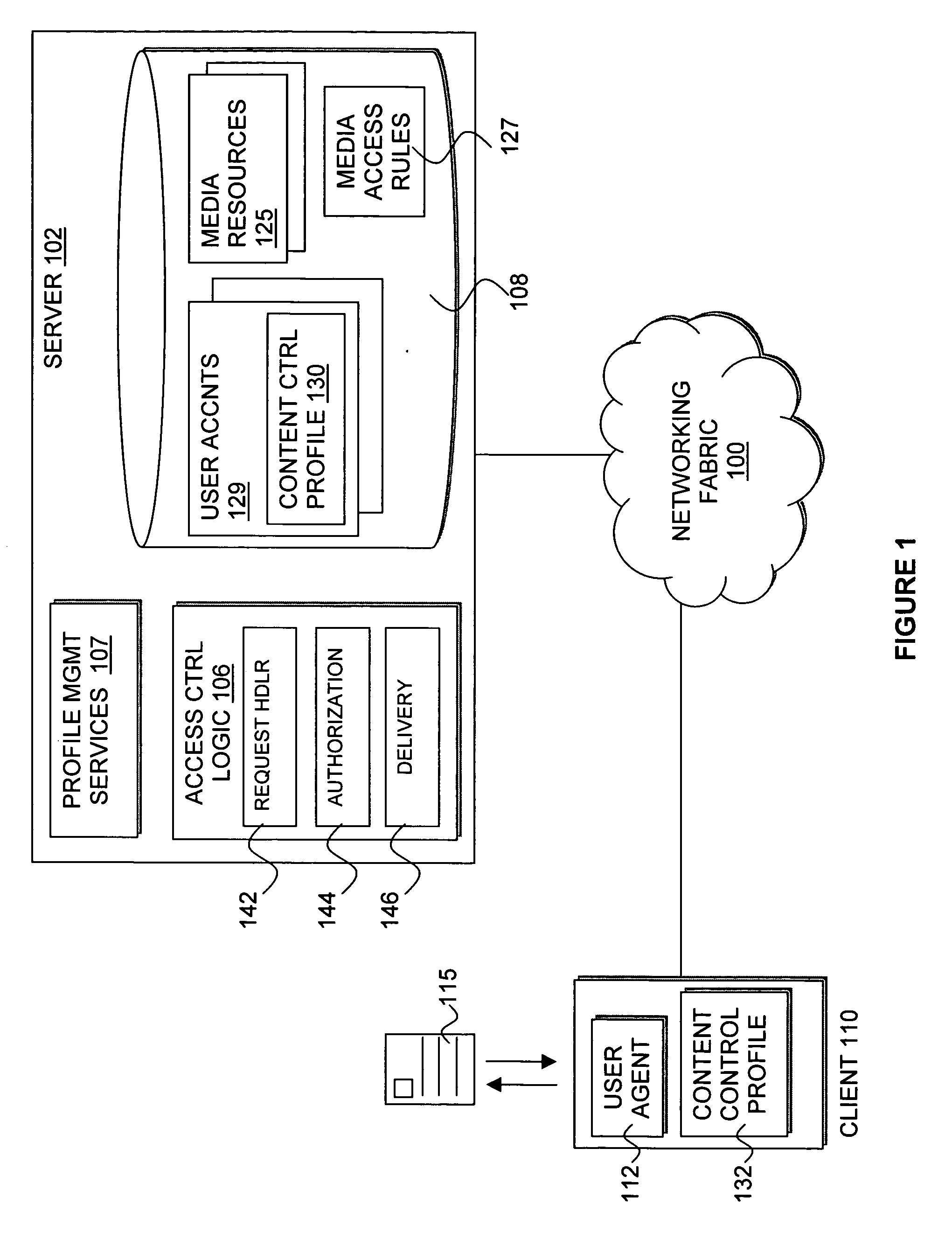
Multiple entity control of access restrictions for media playback
InactiveUS20050086683A1Digital data processing detailsAnalogue secracy/subscription systemsThird partyWorld Wide Web
Owner:INTEL CORP
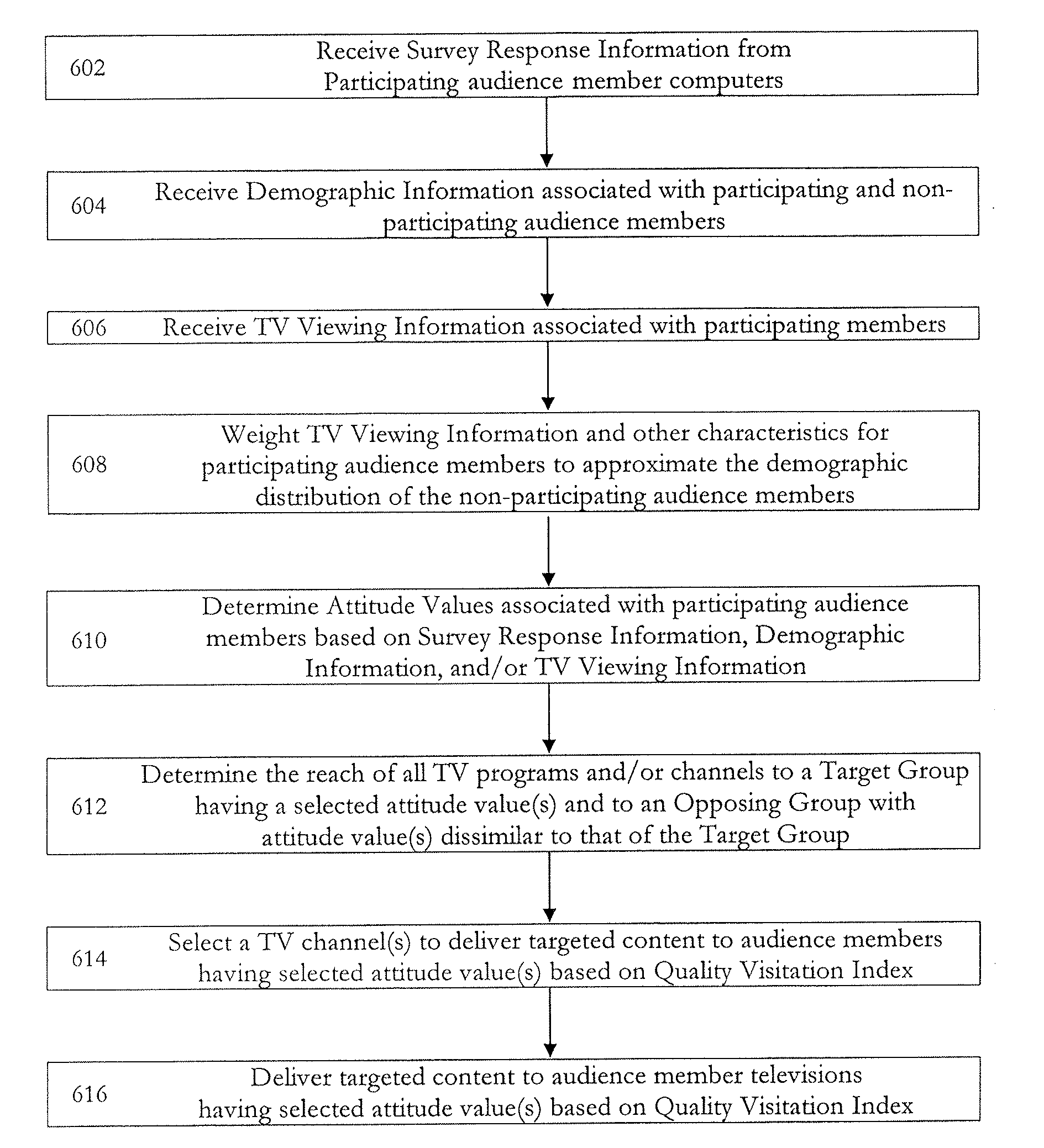
Method and apparatus for delivering targeted content to television viewers
InactiveUS20120192214A1AdvertisementsAnalogue secracy/subscription systemsCentral databaseLibrary science
Owner:RESONATE NETWORKS
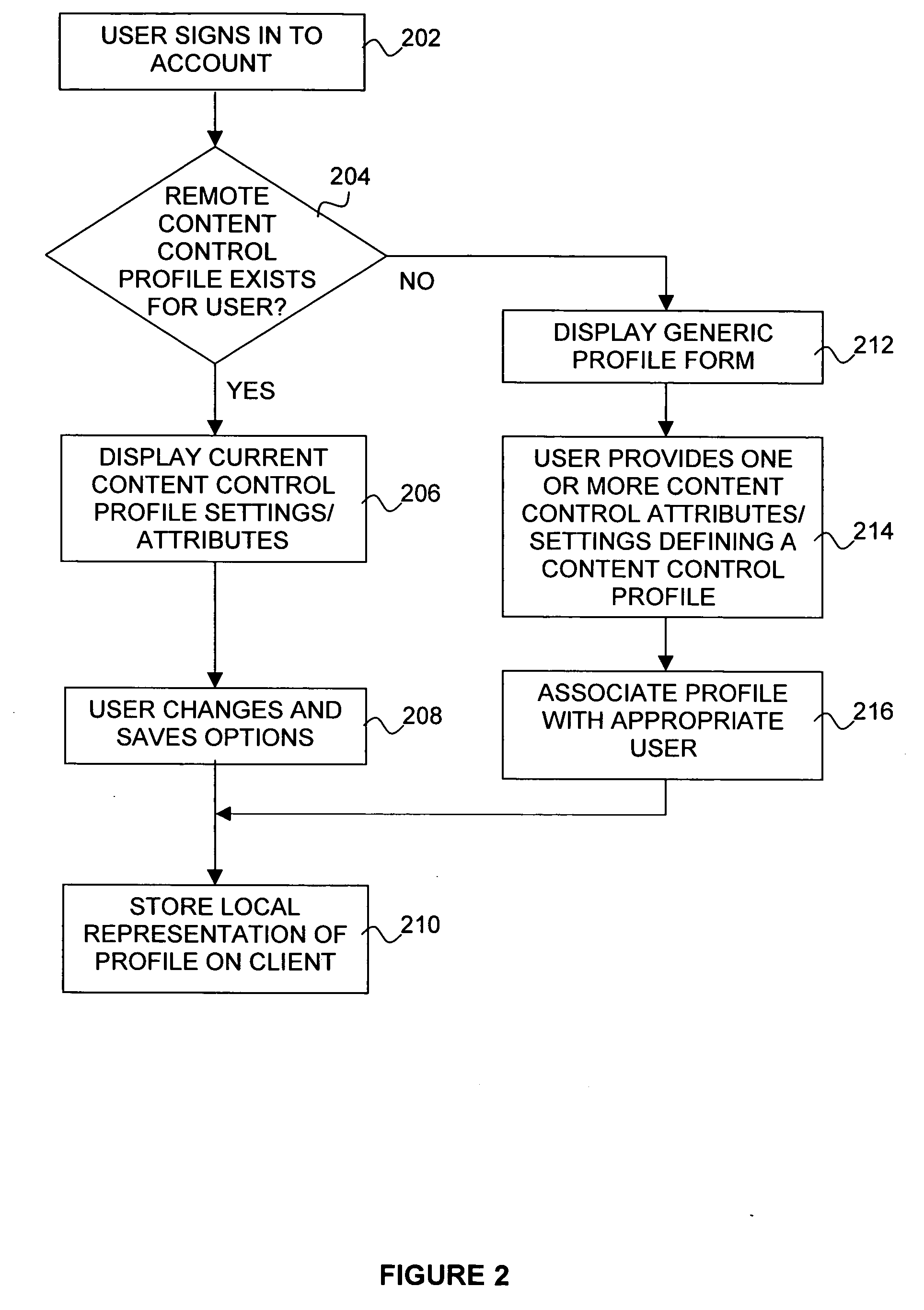
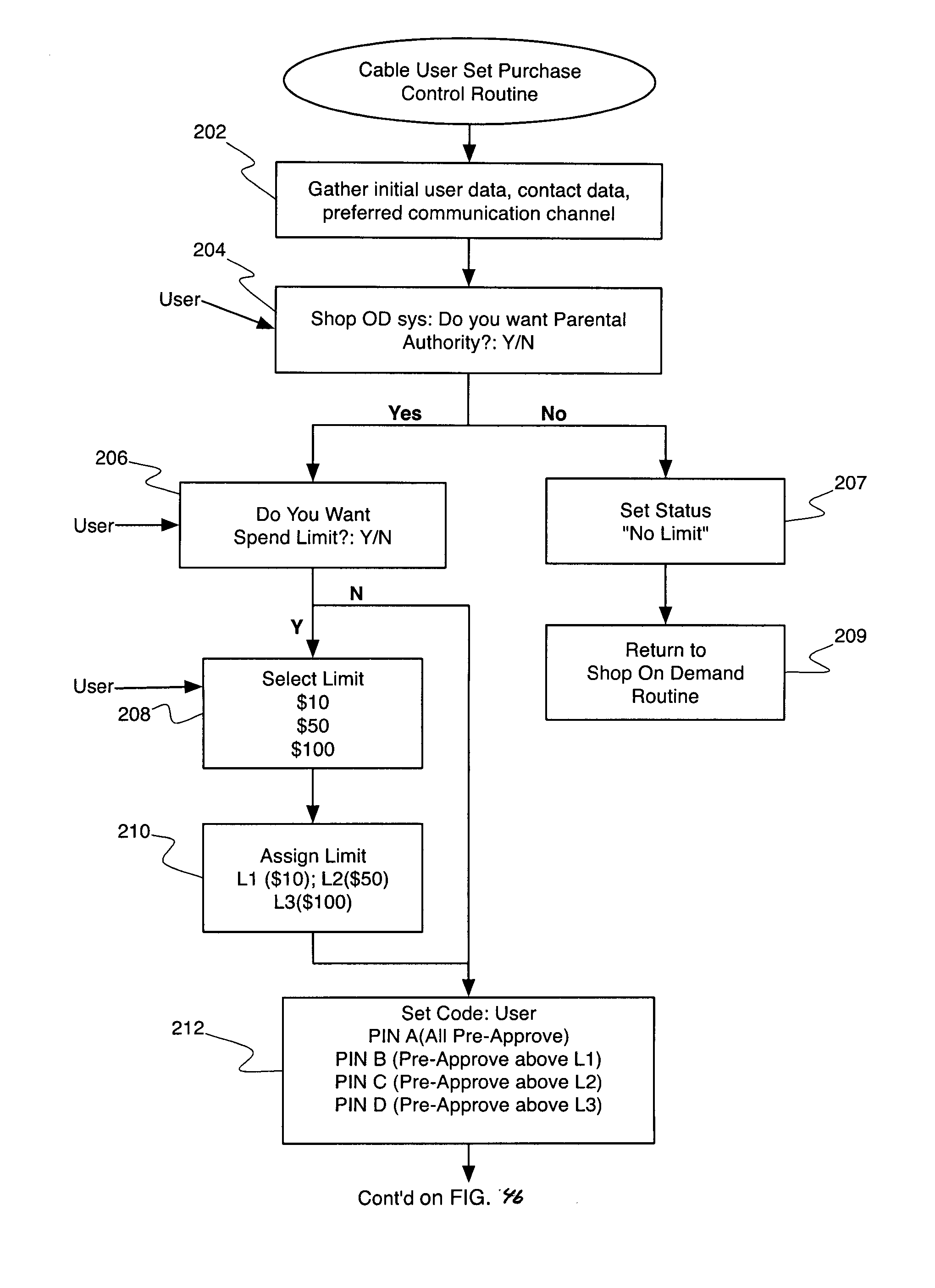
Transaction Process Controller with User History, Selectable Profile Controls, Confirmation and User Control Options for Shopping with Video On Demand Cable Systems
InactiveUS20070107017A1Television system detailsAnalogue secracy/subscription systemsThe InternetControl parameters
Owner:ON DEMAND SHOPPING
Media Content Programming Control Method and Apparatus
InactiveUS20110276993A1Analogue secracy/subscription systemsSelective content distributionTime scheduleInternet content
Owner:FERGUSON KENNETH H
Apparatus and Method for Variable Authentication Requirements
ActiveUS20120239950A1Volume/mass flow measurementUser identity/authority verificationState dependentAuthentication
Owner:LENOVO PC INT
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS20090182873A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyNetwork behavior
Owner:CONNEXITY AUDIENCE INC
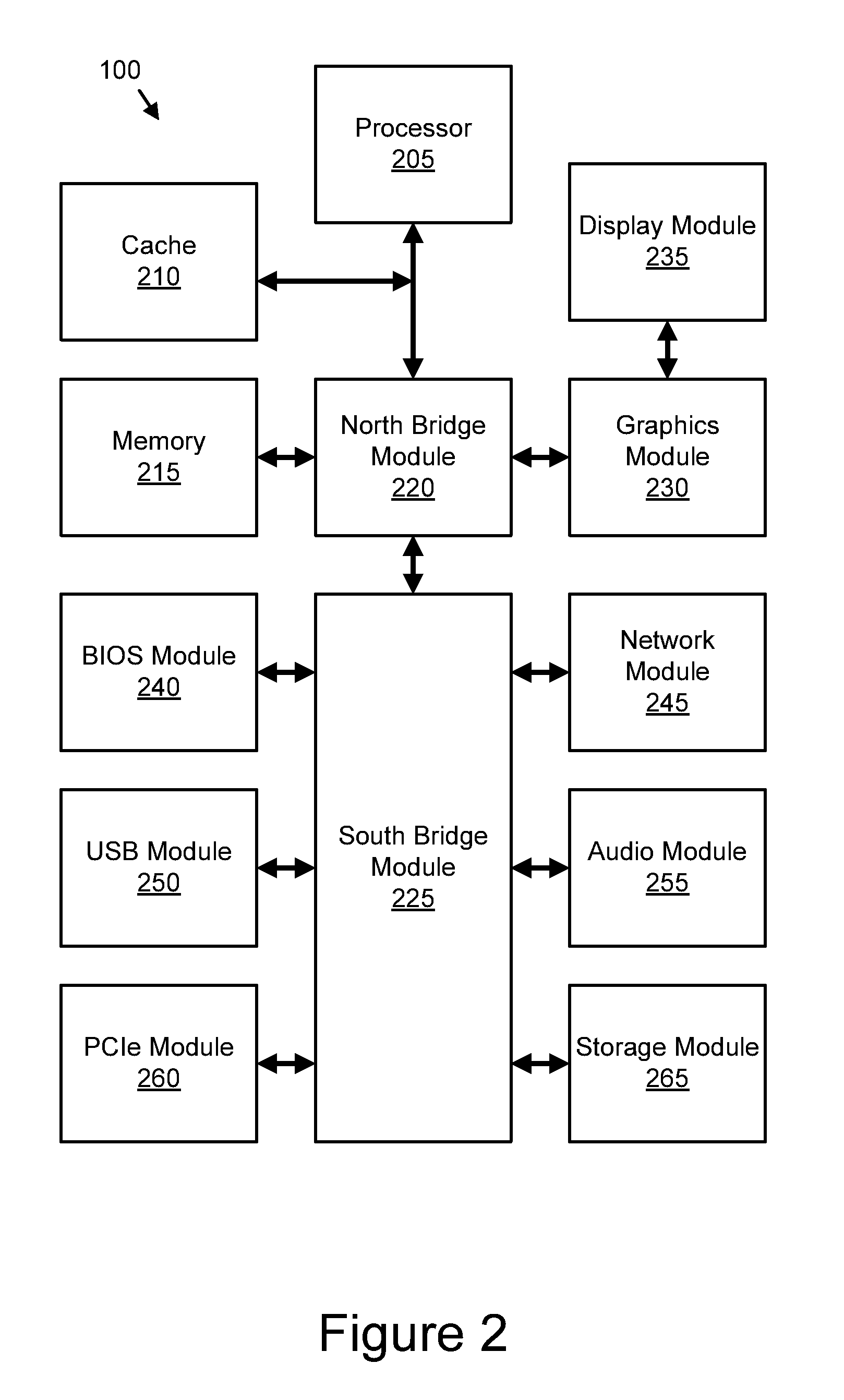
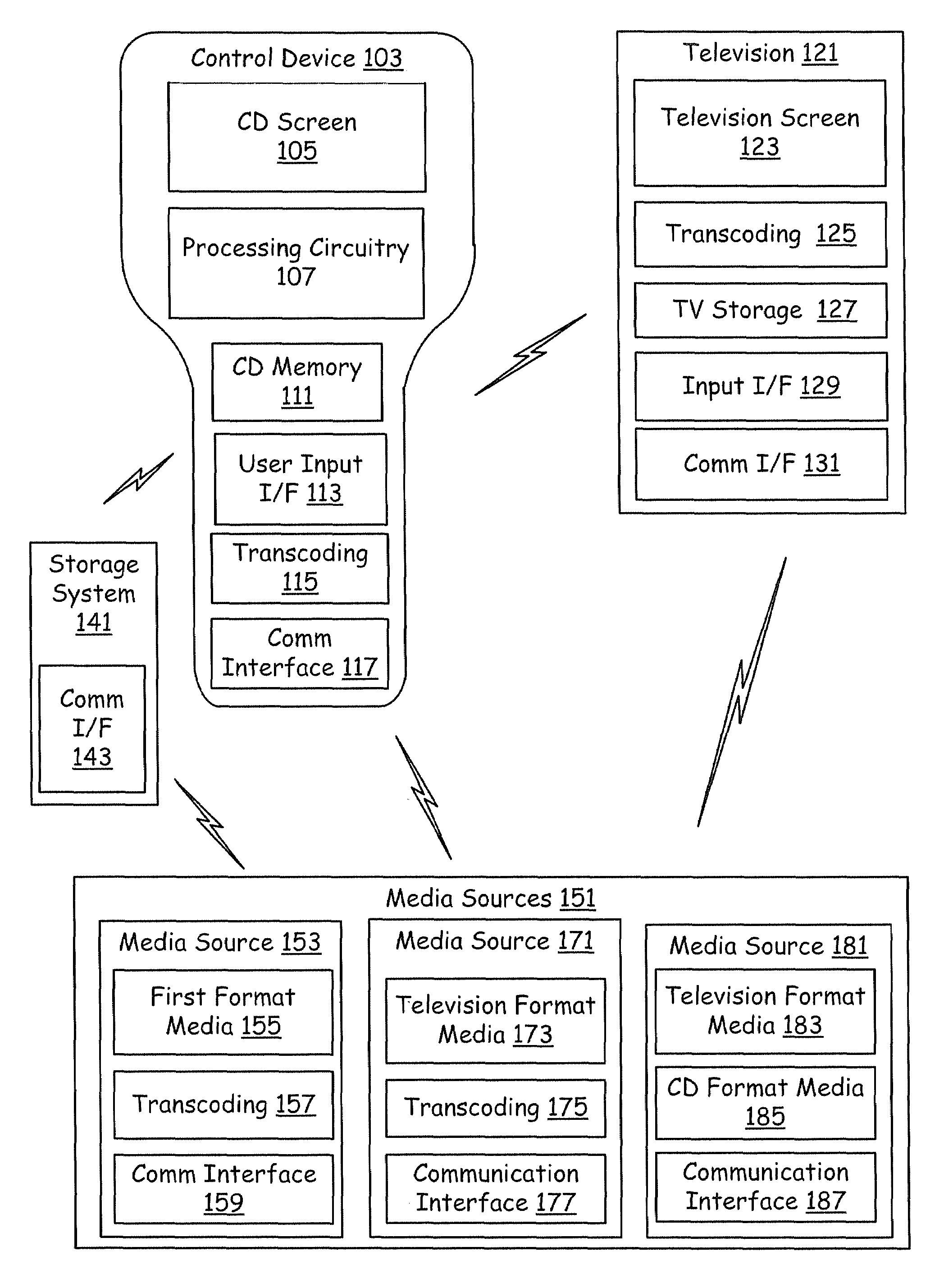
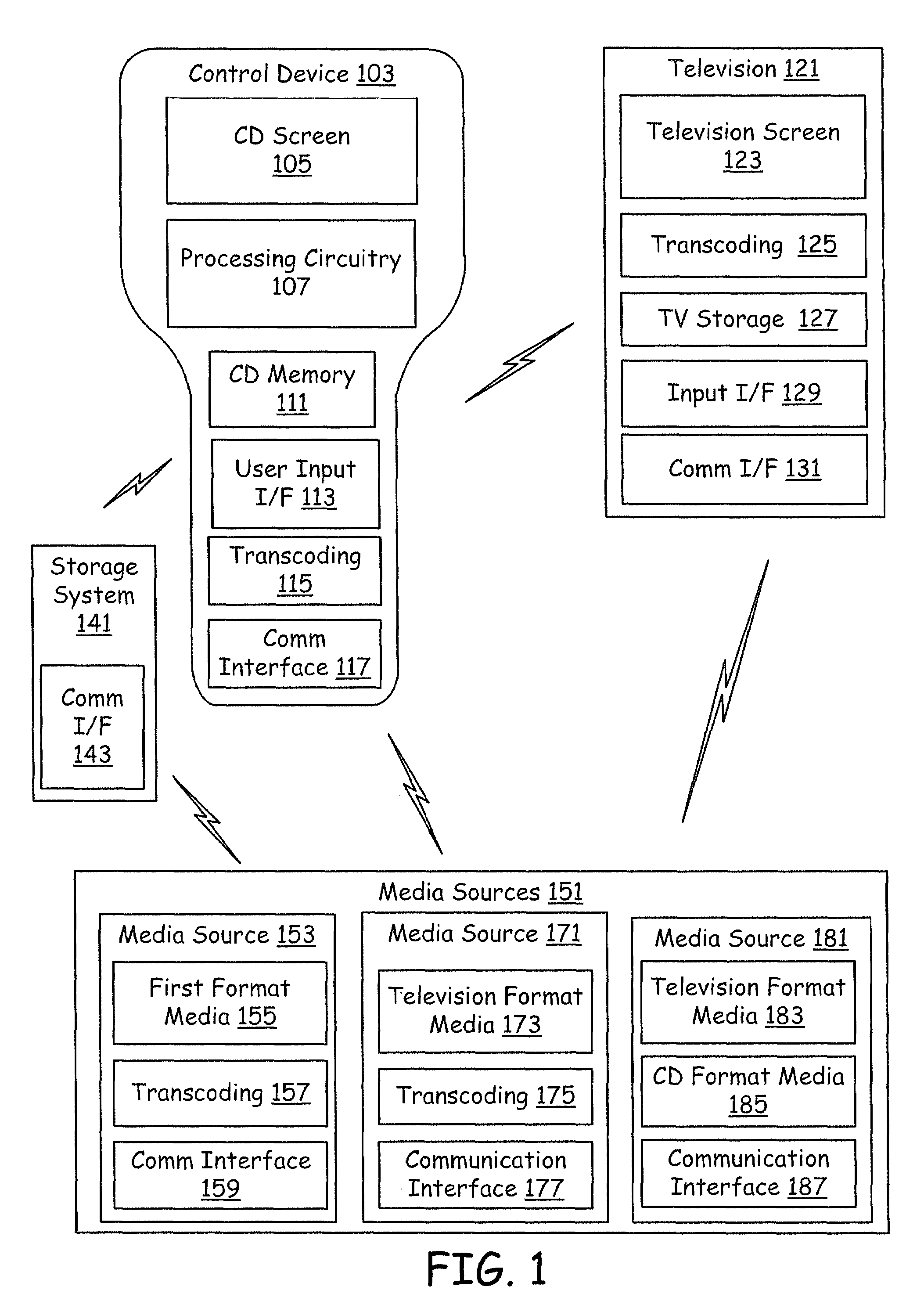
Centralized Device Virtualization Layer For Heterogeneous Processing Units
ActiveUS20100146620A1Operational speed enhancementResource allocationVirtualizationOperational system
A method for providing an operating system access to devices, including enumerating hardware devices and virtualized devices, where resources associated with a first hardware device are divided into guest physical resources creating a software virtualized device, and multiple instances of resources associated with a second hardware device are advertised thereby creating a hardware virtualized device. First and second permission lists are generated that specify which operating systems are permitted to access the software virtualized device and the hardware virtualized device, respectively. First and second sets of virtual address maps are generated, where each set maps an address space associated with either the software virtualized device or the hardware virtualized device into an address space associated with each operating system included in the corresponding permission list. The method further includes arbitrating access requests from each of the plurality of operating systems based on the permission lists and the virtual address maps.
Owner:NVIDIA CORP
Portable information processing device having data evacuation function and method thereof
InactiveUS7024698B2Volume/mass flow measurementUnauthorized memory use protectionInformation processingLocation status
A processor means is connected with other individual means, and controls those individual means. Storage means stores data to be processed by the processor means and the resultant data after the process. An important data in the storage means is transmitted to other devices for evacuation by using a wireless communication means, when a situating condition of a portable information-processing device is judged abnormal (e.g., when being stolen) based on an output of a status detector means. The data in the storage means is deleted, when the transmission is completed or the transmission is interrupted. Protection of the data and the confidentiality are thus achieved even if the portable information-processing device is stolen, since the data can be evacuated, and the data is erased after completion of the data evacuation or if the data evacuation becomes not attainable.
Owner:PANASONIC CORP
Parallel television based media recording
ActiveUS20070162941A1Television system detailsAnalogue secracy/subscription systemsComputer hardwareTelevision system
Owner:AVAGO TECH INT SALES PTE LTD
Information processing apparatus and method, and program storing medium
InactiveUS7478437B2Disc-shaped record carriersDigital data processing detailsInformation processingComputer science
Owner:SONY CORP
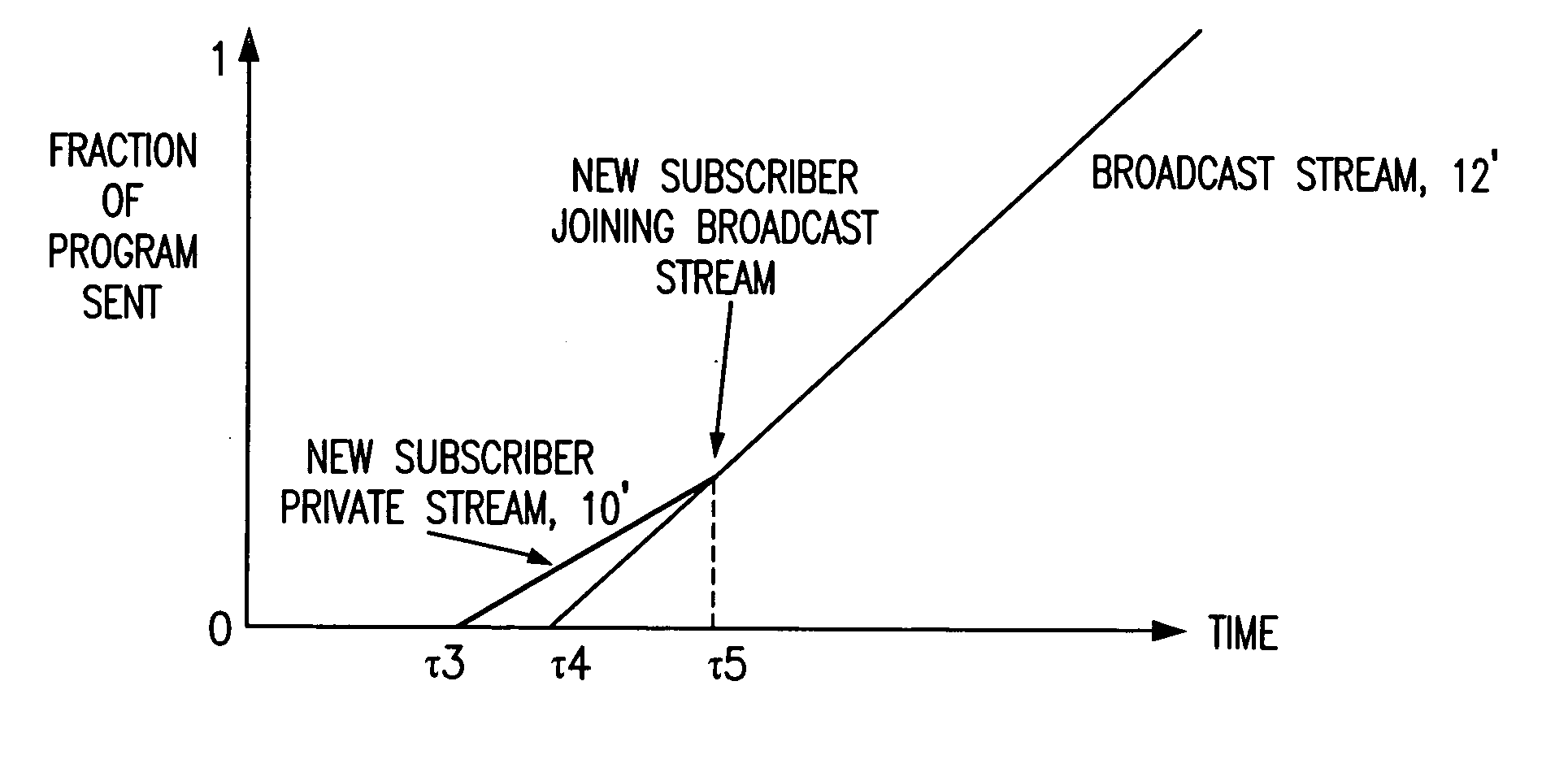
Switching to a broadcast data stream
InactiveUS20060075443A1Lower requirementAnalogue secracy/subscription systemsTwo-way working systemsData streamBroadcast data
Owner:LUCENT TECH INC
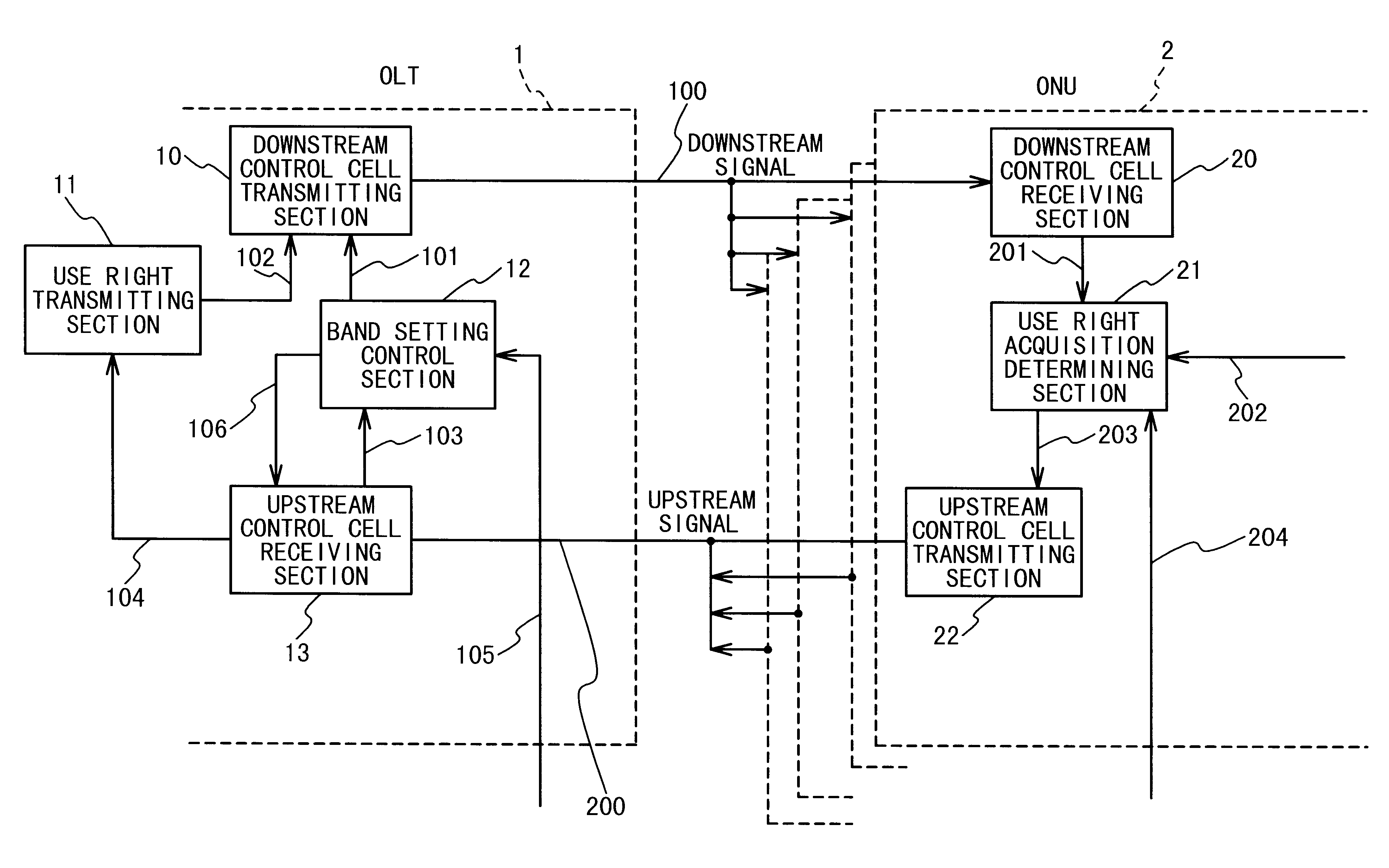
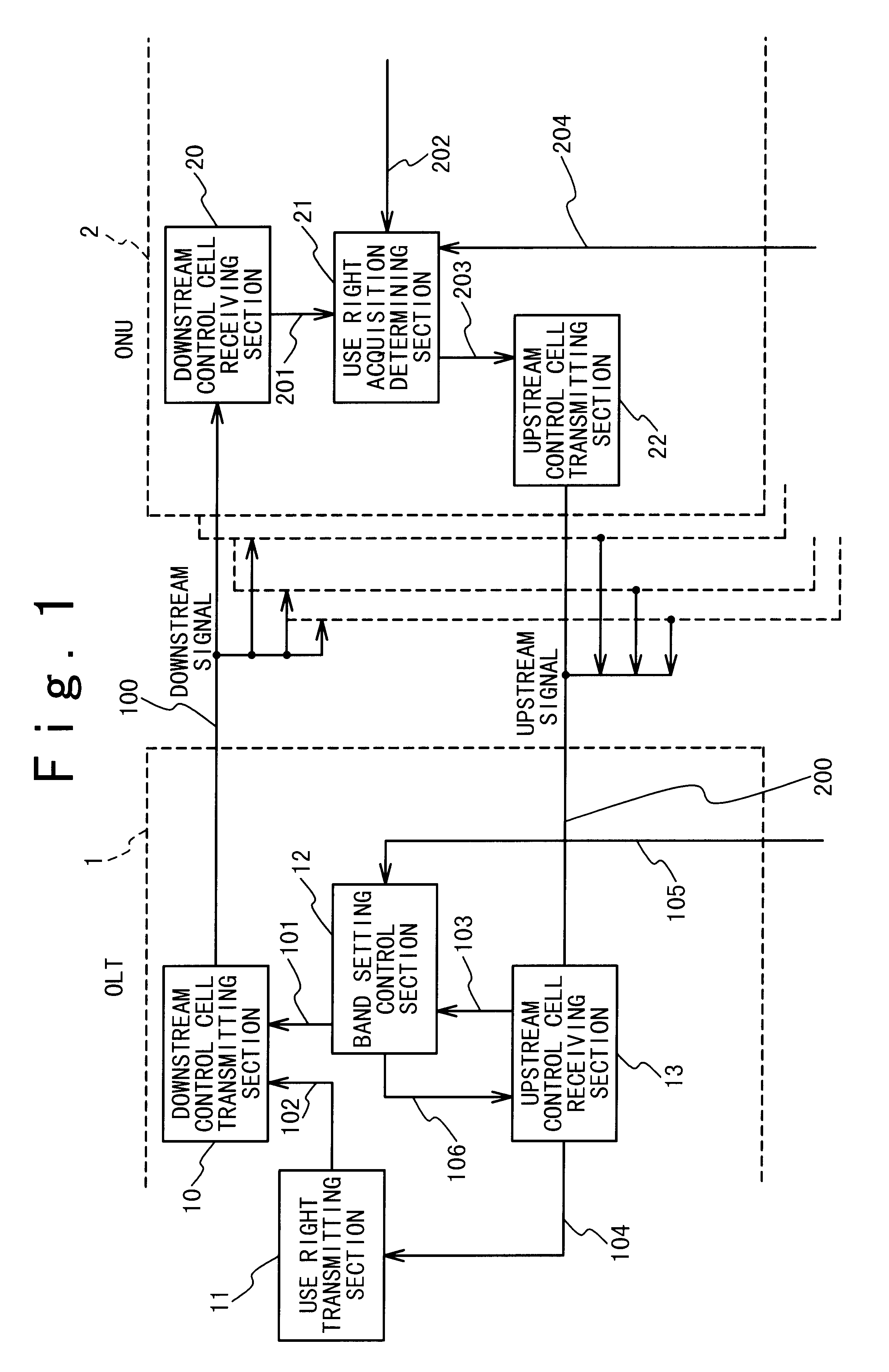
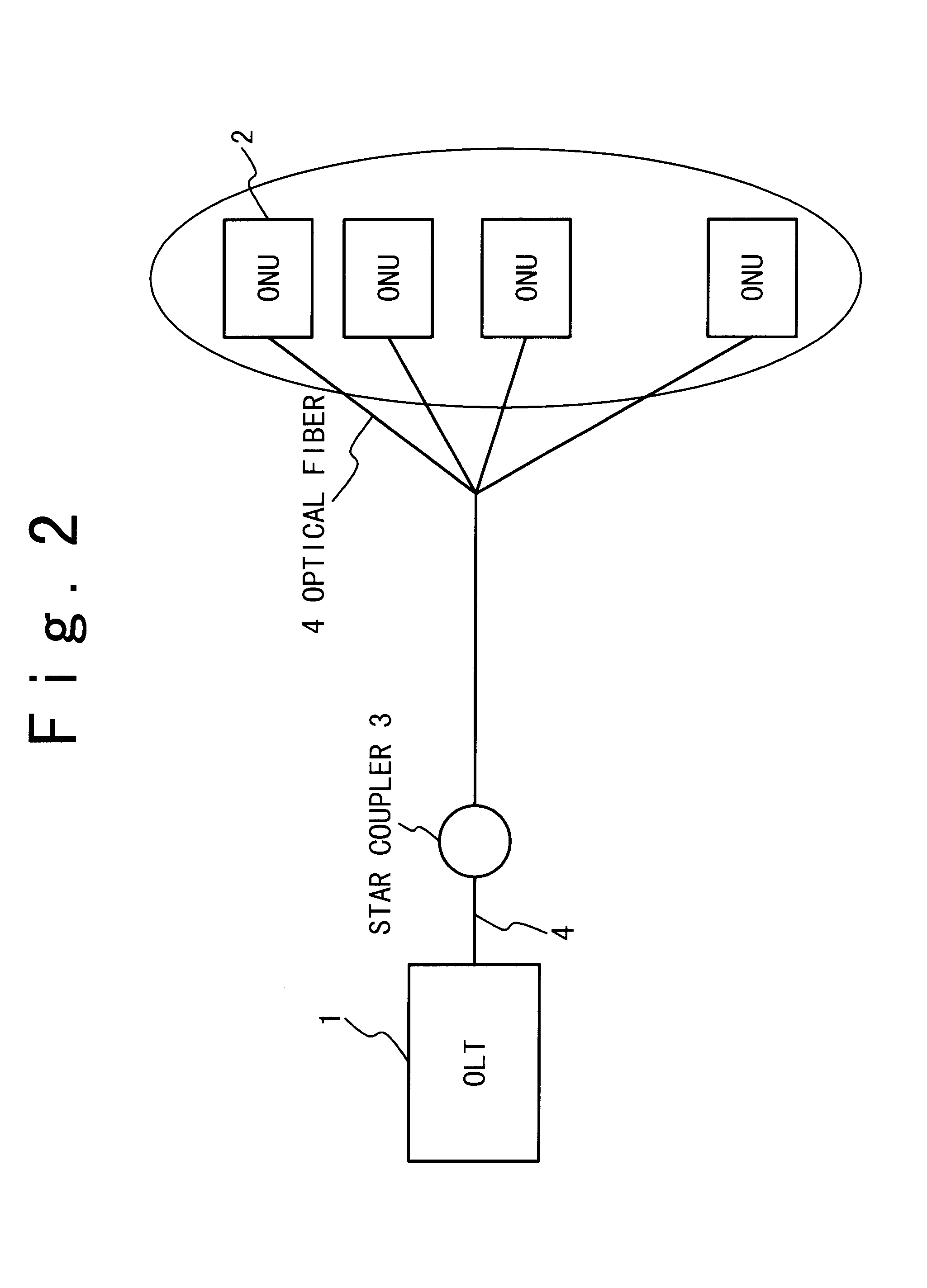
Unused band use right acquisition controlling method and passive optical network for the same
InactiveUS6850711B2Easy to useError preventionFrequency-division multiplex detailsControl cellOptical line termination
Owner:JUMIPER NETWORKS INC
Secure wireless communication
ActiveUS20090103728A1Unauthorised/fraudulent call preventionDigital data processing detailsHash-based message authentication codeCryptographic protocol
Owner:ALCATEL LUCENT SAS
System and method for controlling alternative access to video events associated with video broadcast services
ActiveUS20100115544A1Reduce disadvantagesEasy to identifyTelevision system detailsAnalogue secracy/subscription systemsBlack outBroadcast service
Owner:DISH TECH L L C
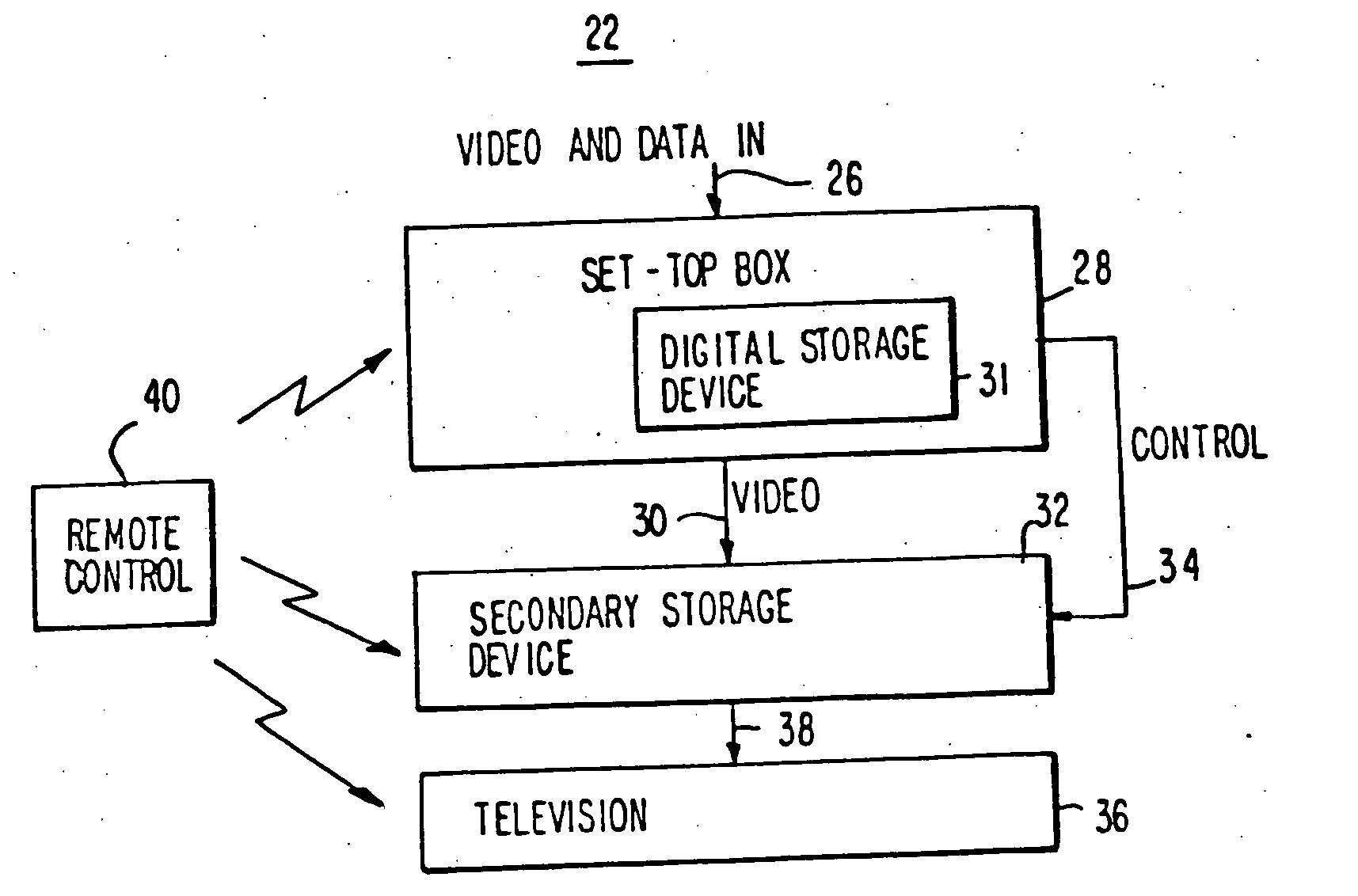
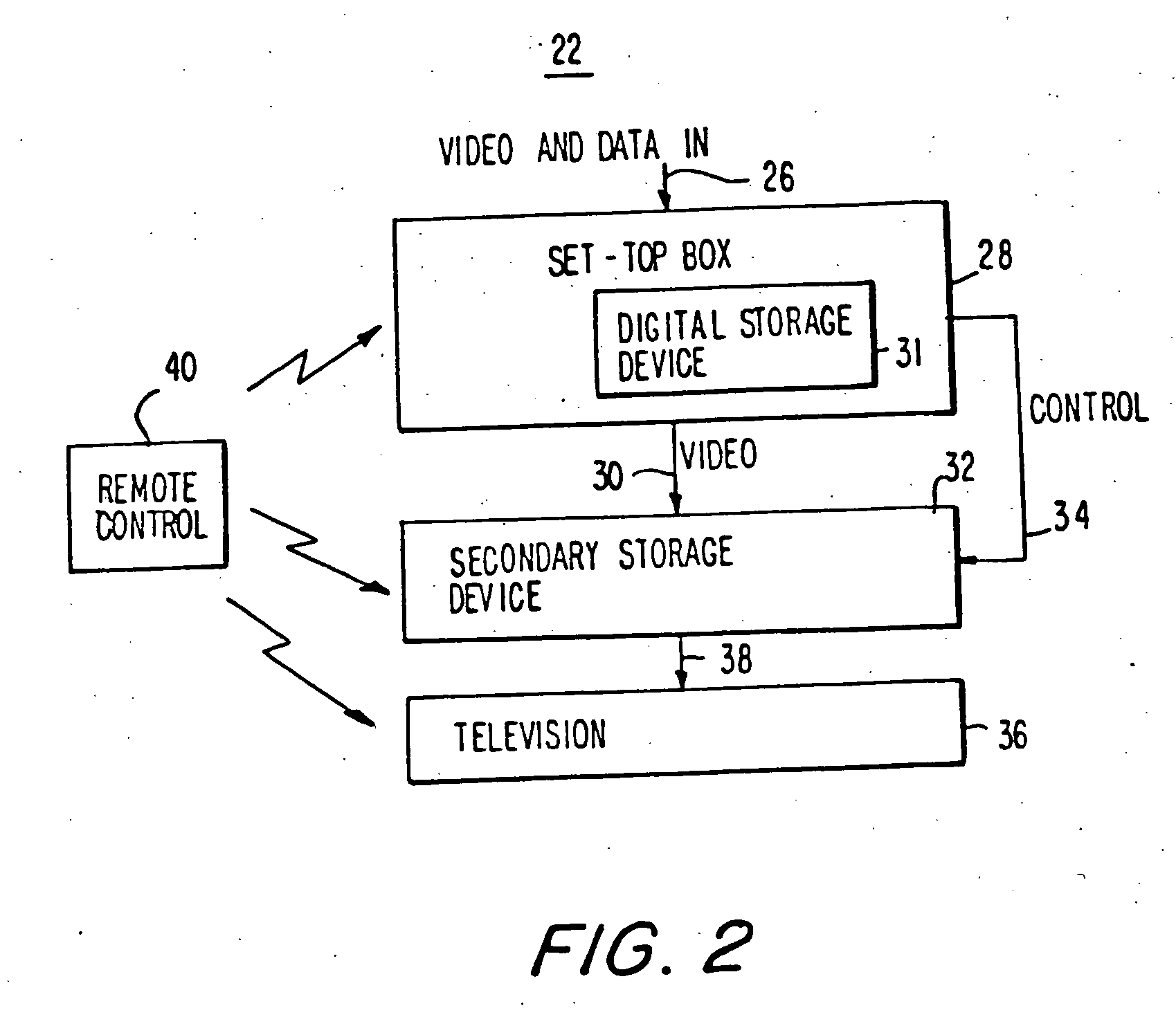
Electronic program guide with digital storage
InactiveUS20050278771A1Television system detailsAnalogue secracy/subscription systemsProgram segmentInteractive television
Owner:ROVI GUIDES INC
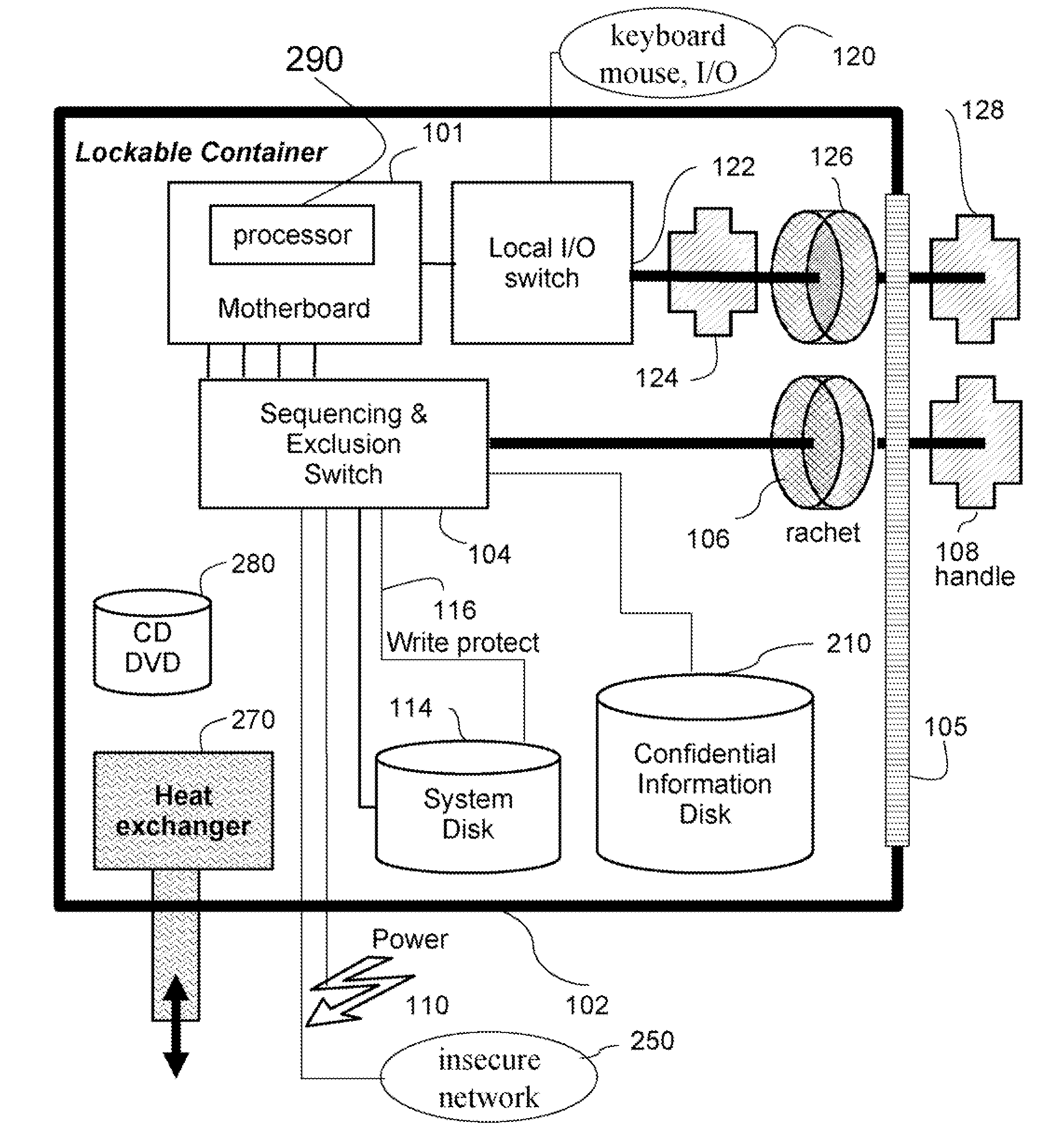
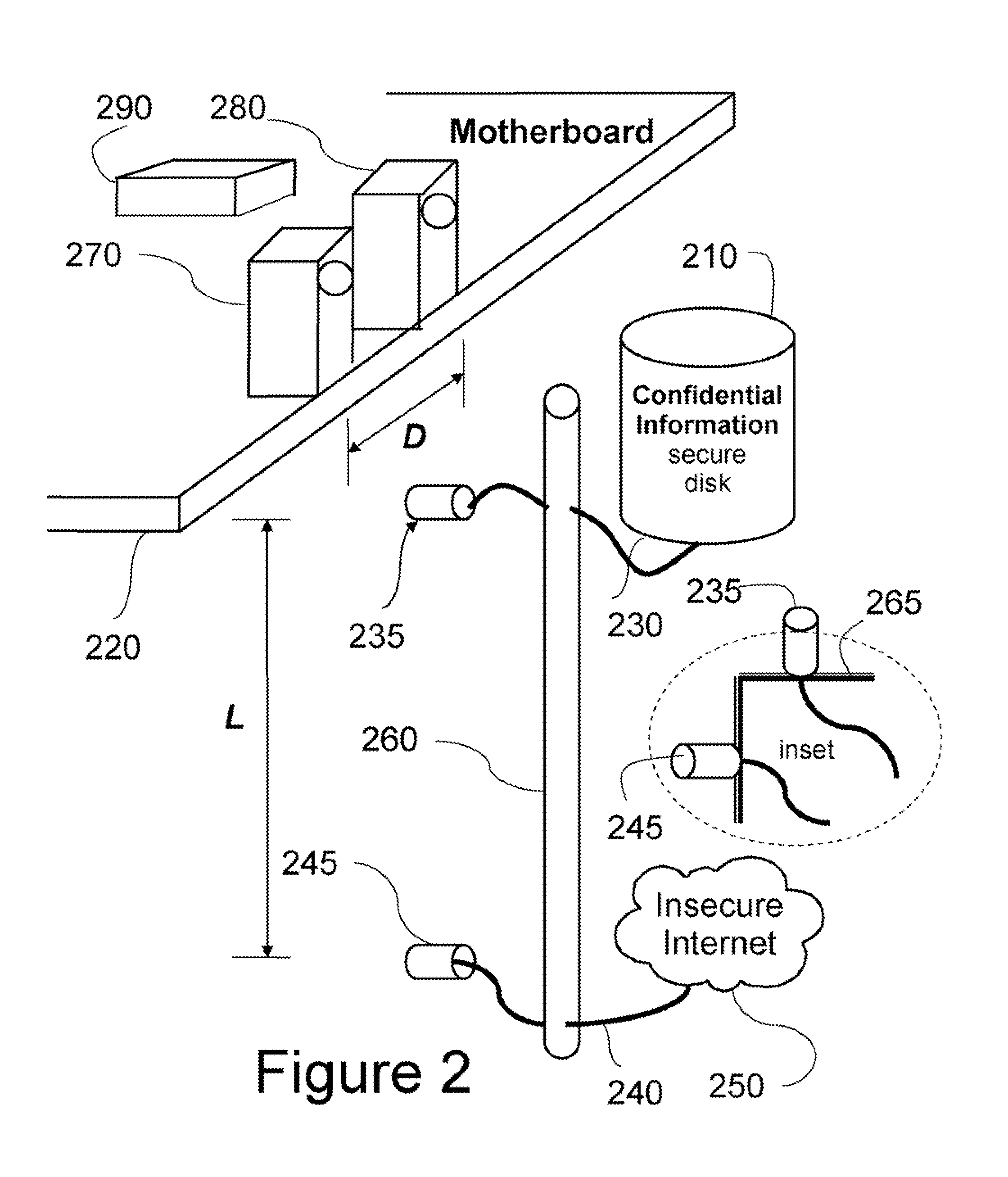
Secure Computer System and Method
InactiveUS20090165139A1Desired secure computing propertiesDigital data processing detailsAnalogue secracy/subscription systemsMagnetic disksInternet privacy
An apparatus is configured to perform secure processing of confidential information. The apparatus comprises a secure disk configured to store confidential information arranged inside a lockable container; a processor configured to process the confidential information arranged inside the lockable container; an insecure network arranged outside the lockable container; and means for connecting the processor only to the secure disk or alternatively to the insecure network at any one time, but not to both the secure disk and the insecure network at the same time.
Owner:MITSUBISHI ELECTRIC RES LAB INC
System and method for securing computers against computer viruses
In one embodiment, an antivirus mechanism (e.g., antivirus program) in a computer initiates shielding procedures in response to a triggering event indicative of a presence of a virus in the computer, the virus being of a type not recognized by the antivirus program. The shielding procedures advantageously protect important components of the computer while the antivirus program does not have the requisite antidote to directly deal with the virus.
Owner:TREND MICRO INC
Method for interactive digital cinema system
ActiveUS20120204203A1Improve playbackEasy selectionAnalogue secracy/subscription systemsBroadcast information monitoringDigital dataInteractive content
Owner:CINVOLVE
Determination of access checks in a mixed role based access control and discretionary access control environment
InactiveUS20080271139A1Digital data processing detailsUser identity/authority verificationDiscretionary access controlAuthorization
Owner:IBM CORP
Playing method of video/audio file and playing system using this method
InactiveCN101193264ATelevision system detailsAnalogue secracy/subscription systemsData recordingMultimedia
Owner:BENQ CORP
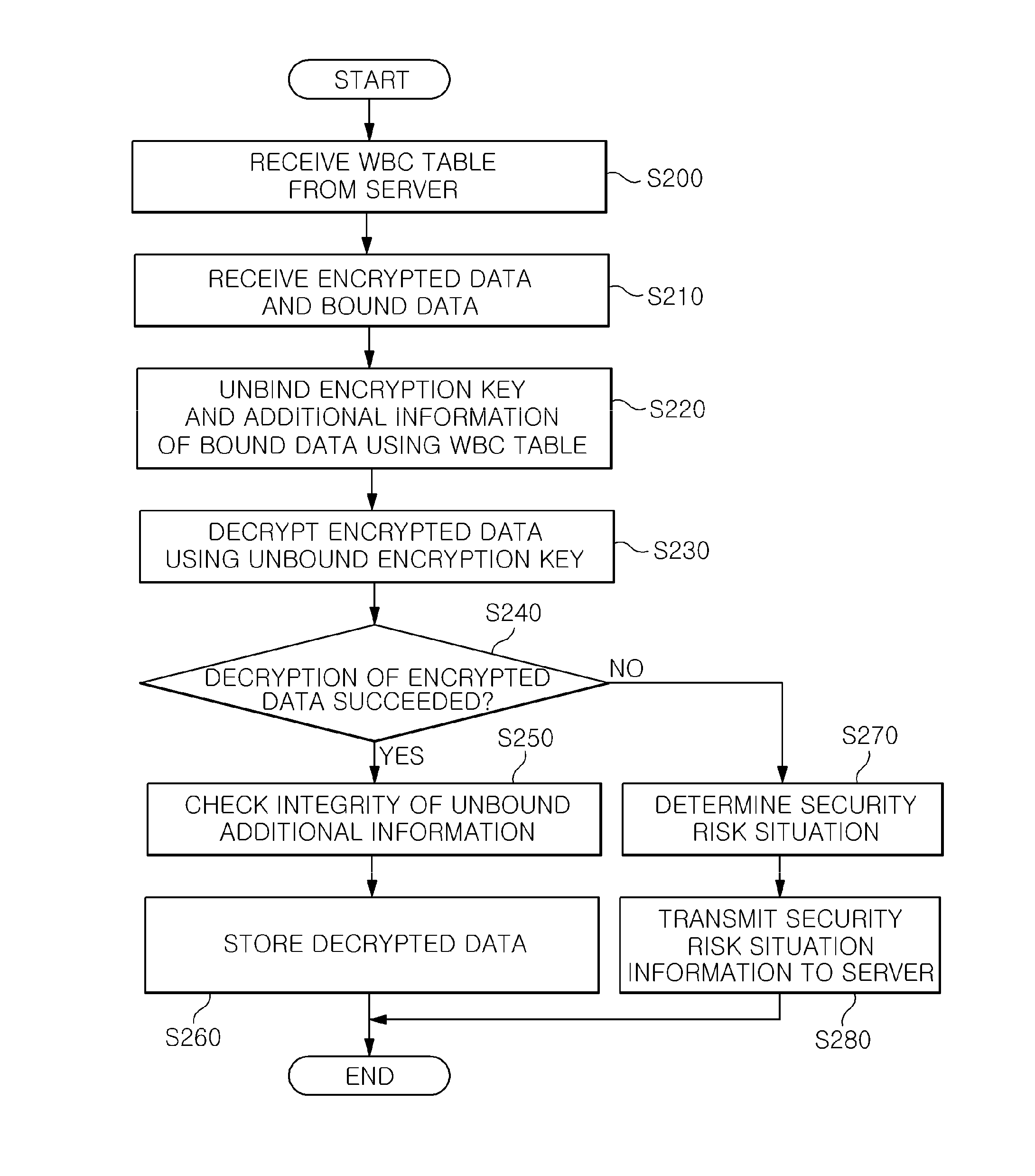
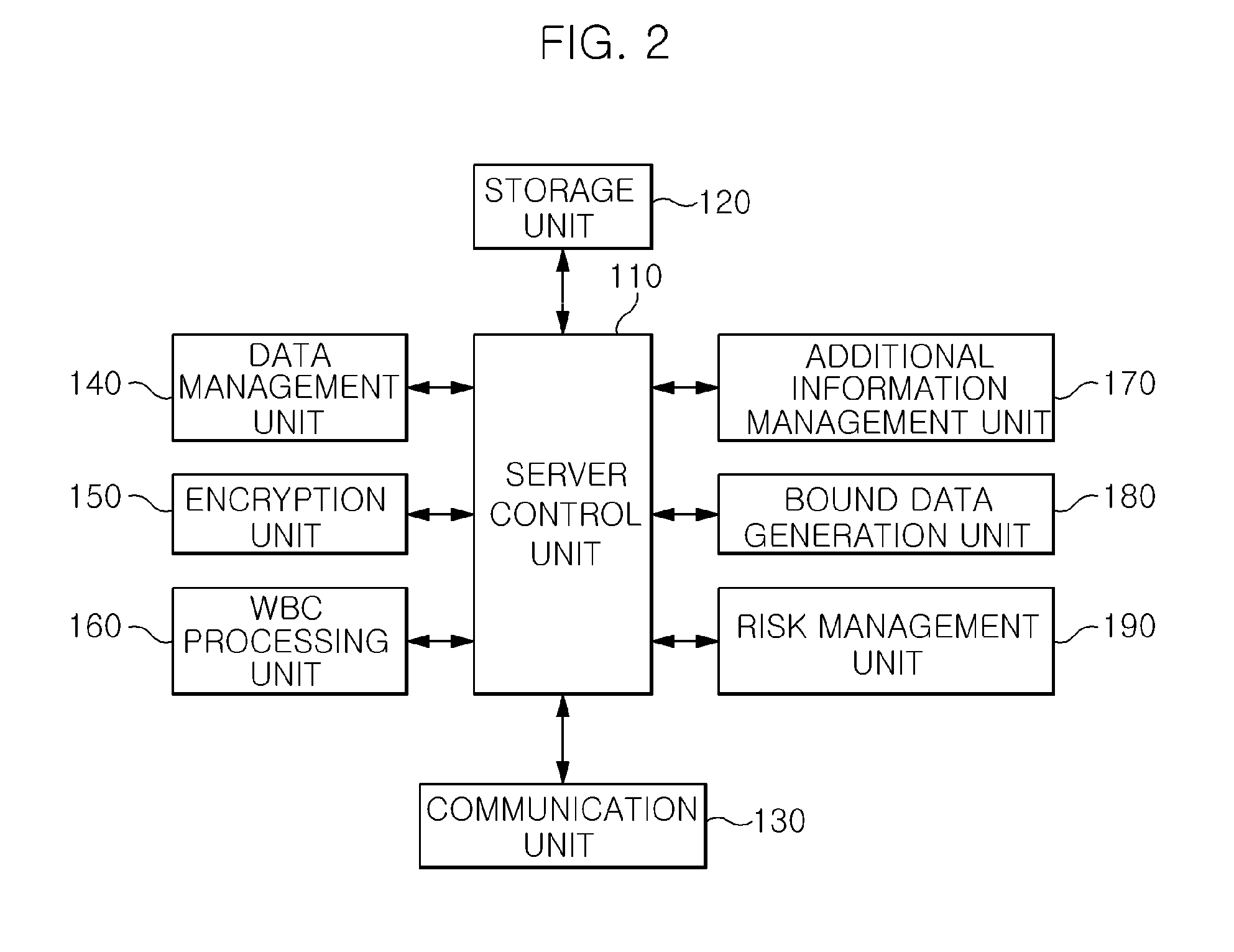
Content protection apparatus and method using binding of additional information to encryption key
InactiveUS20120099726A1Deciphering becomes impossibleKey distribution for secure communicationRandom number generatorsManagement unitProcessing element
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus and method for electronic mail filtering
ActiveUS7636947B2Digital data processing detailsAnalogue secracy/subscription systemsSecurity policyElectronic mail
Owner:FORCEPOINT LLC
Method and apparatus for providing network access privacy
InactiveUS20100031365A1Good suggestionImprove accuracyDigital data processing detailsAnalogue secracy/subscription systemsWeb accessAccess network
Owner:AT&T INTPROP I L P
Method, system and apparatus for video sharing
InactiveUS20080250466A1Reduce useless consumptionTelevision system detailsAnalogue secracy/subscription systemsApplication serverFile sharing
Owner:MASON LICENSING LLC
Context information management system and method
InactiveUS20070113249A1Television system detailsAnalogue secracy/subscription systemsEngineeringMobile service
A context information management system provides service mobility that allows user to maintain service even while moving the service environment. That is, when user service environment movement is sensed, user service provided in previous service environment is consecutively provided to the user in the new service environment using the service context information of user service provided in the previous service environment. In such a manner, the service user may continuously use a same service that used in the previous service environment although the user moves to other service environments without a service terminal.
Owner:ELECTRONICS & TELECOMM RES INST
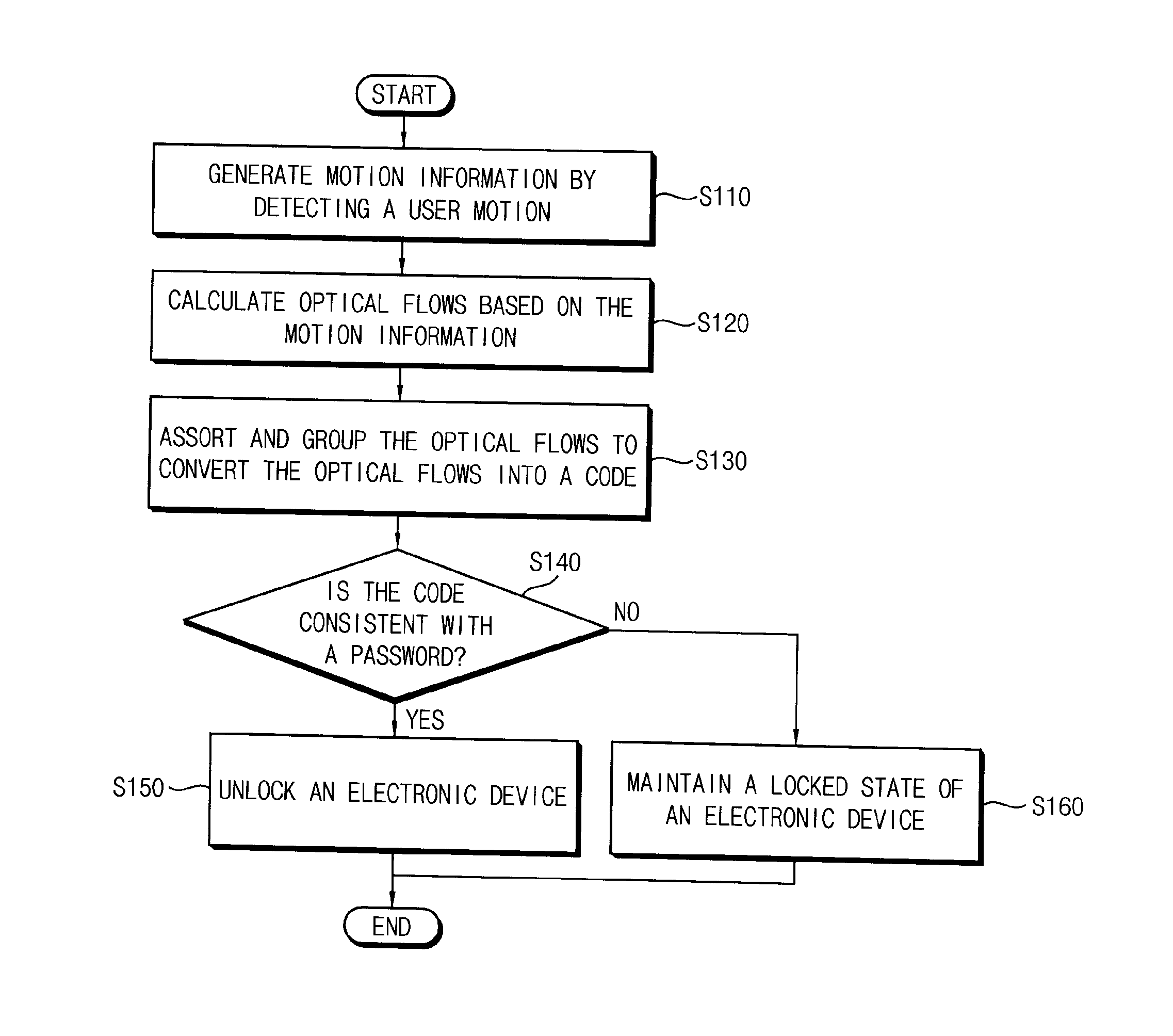
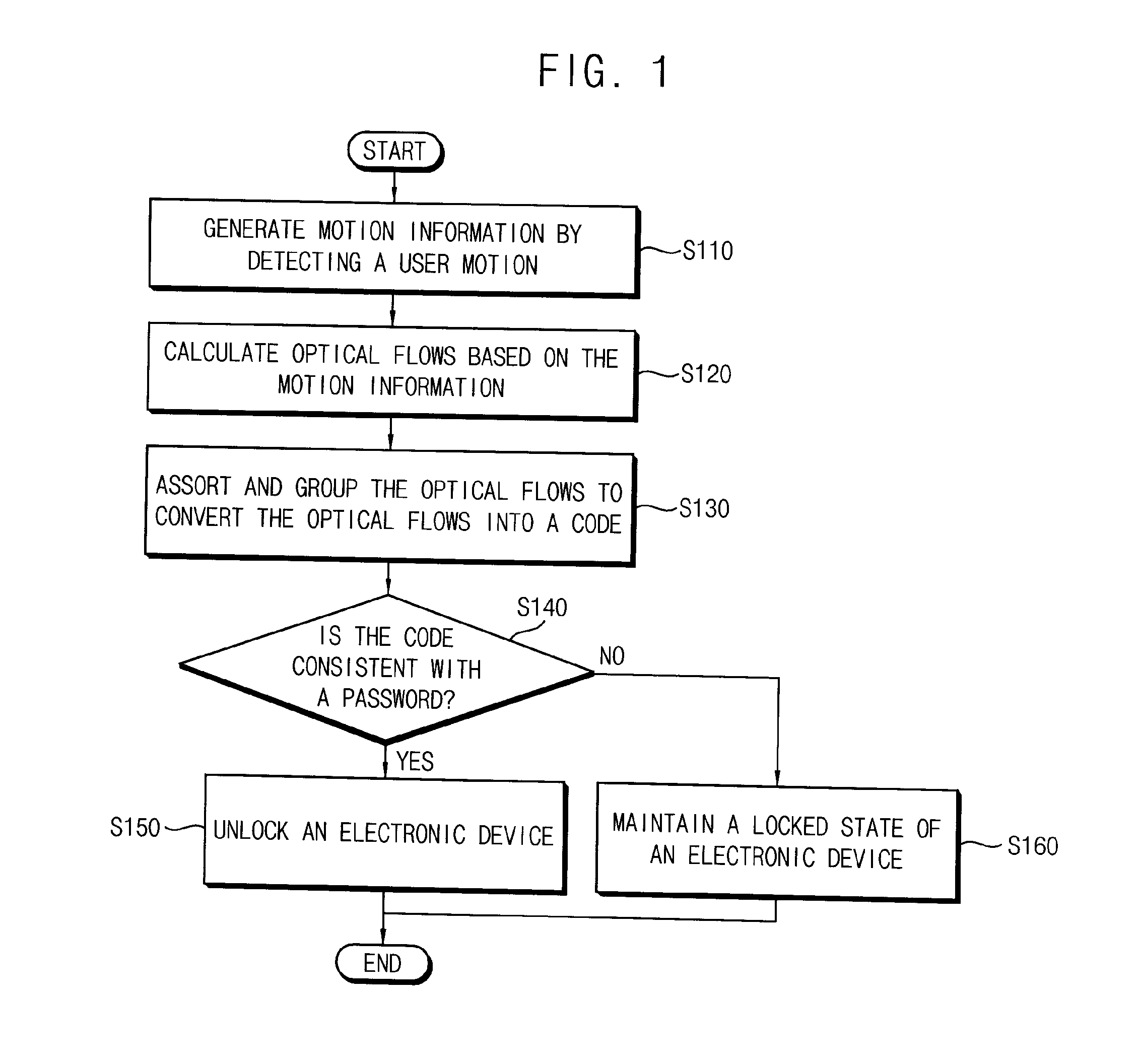
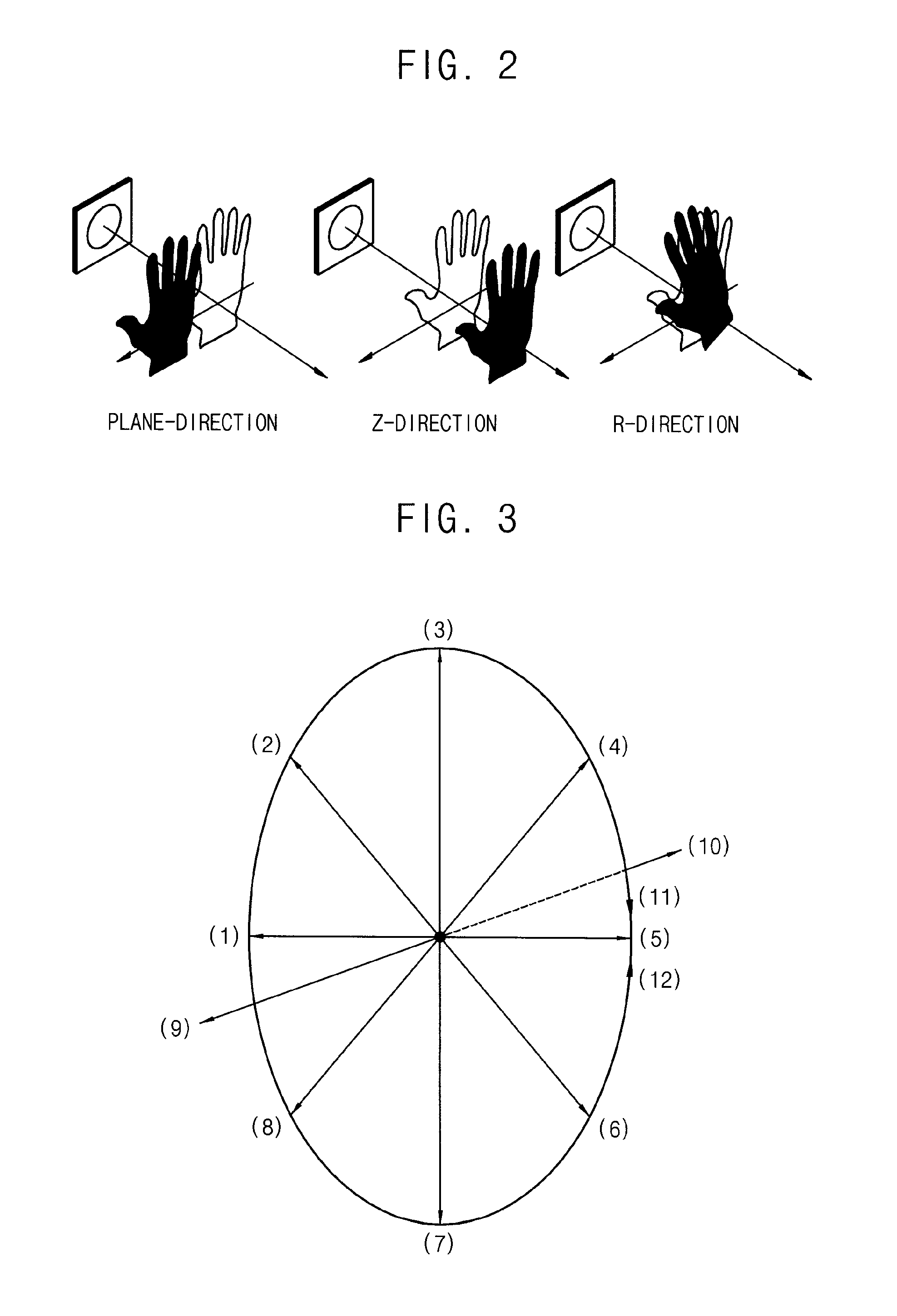
Method of unlocking an electronic device based on motion recognitions, motion recognition unlocking system, and electronic device including the same
InactiveUS20150248551A1Digital data processing detailsAnalogue secracy/subscription systemsPasswordSimulation
Owner:SAMSUNG ELECTRONICS CO LTD
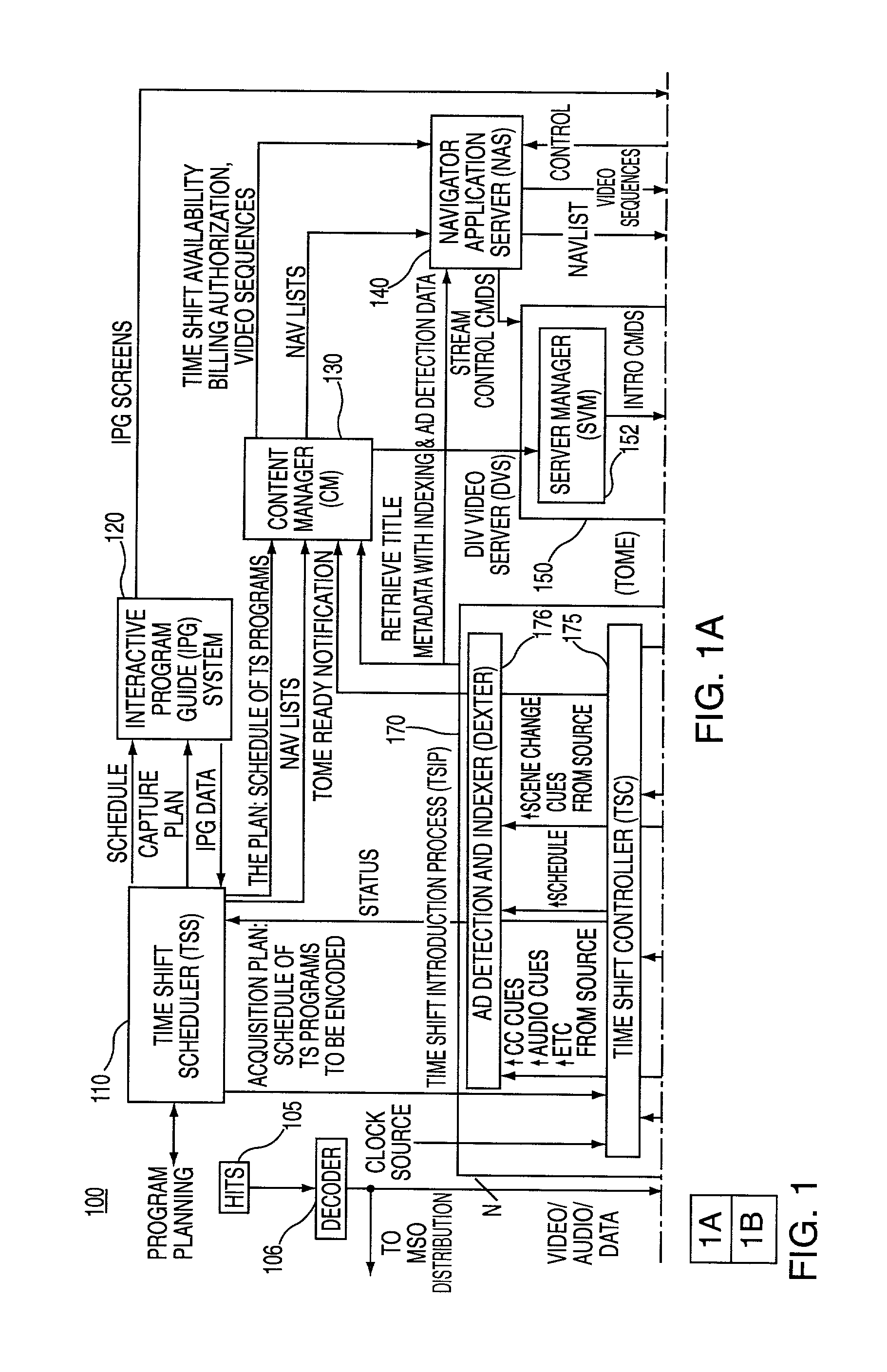
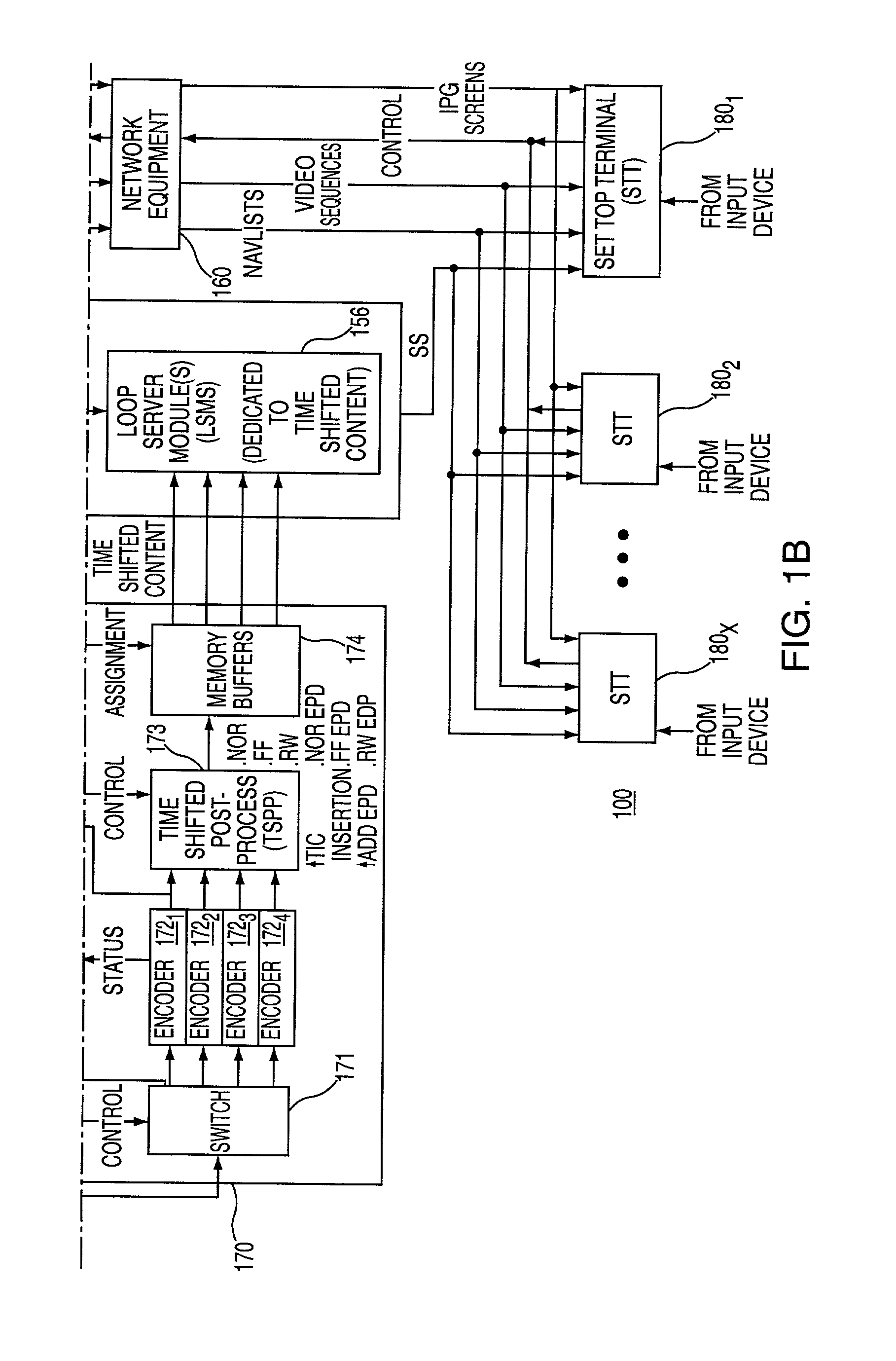
System and method for time shifting the delivery of video information
ActiveUS8352988B2Overcome disadvantagesTelevision system detailsRecording carrier detailsComputer hardwareTime shifting
Owner:COX COMMUNICATIONS
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap