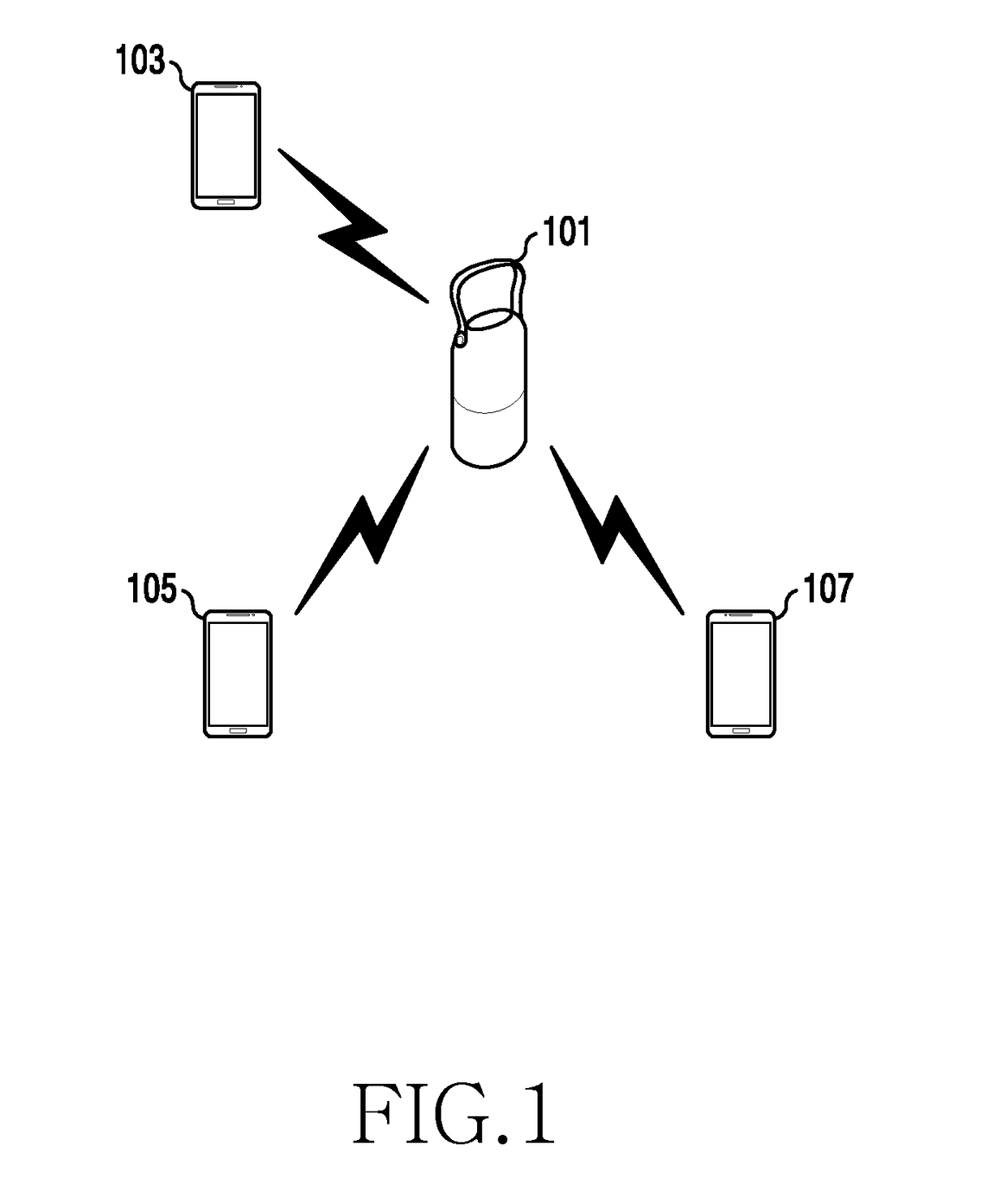
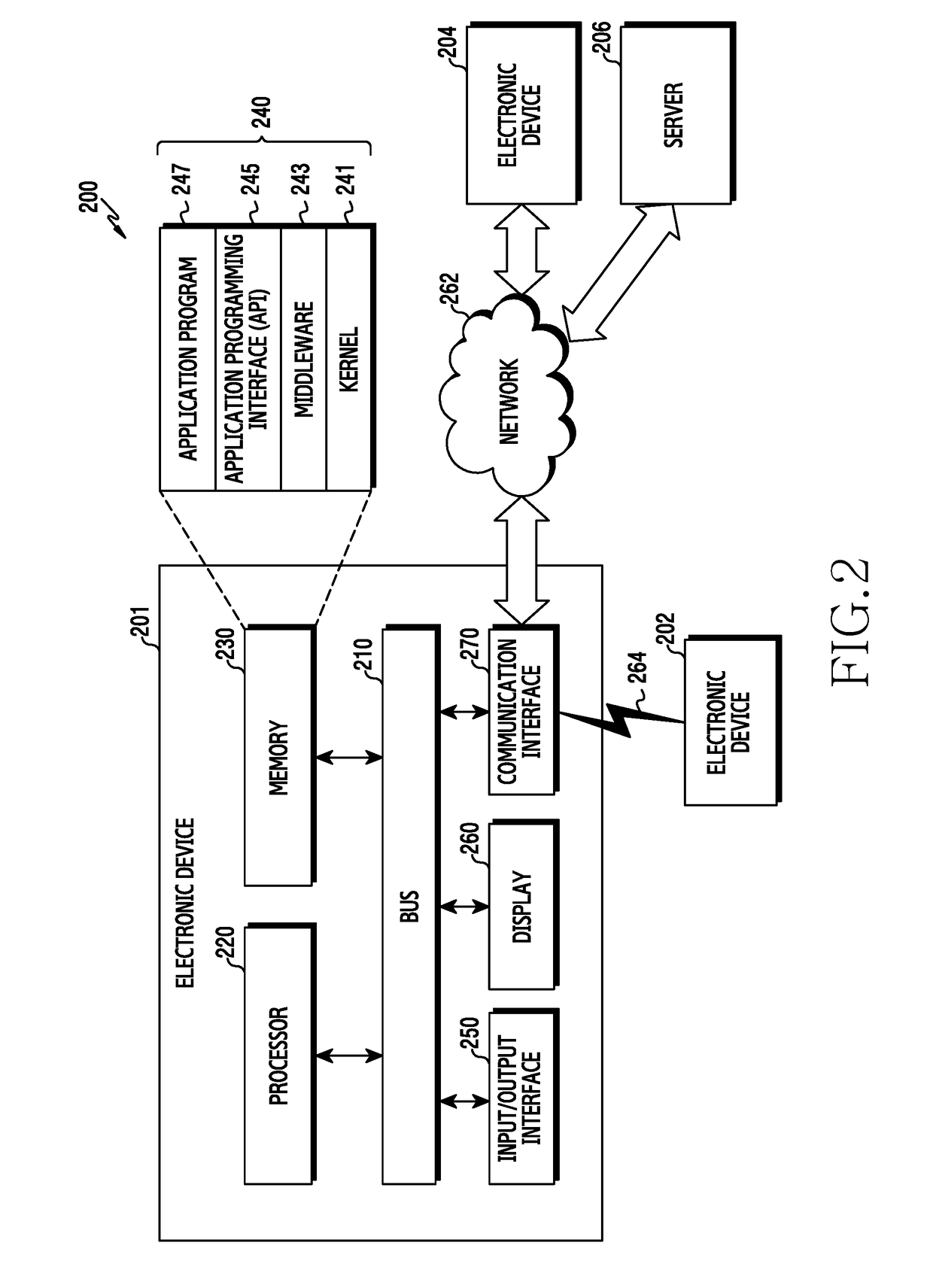
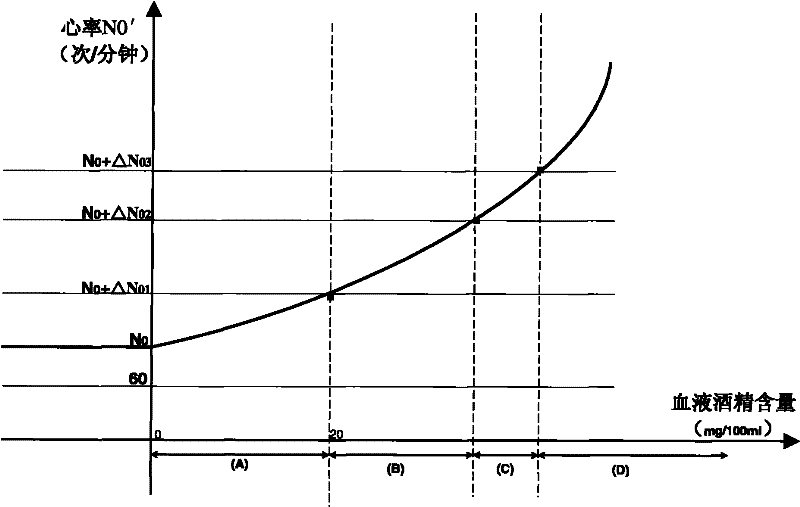
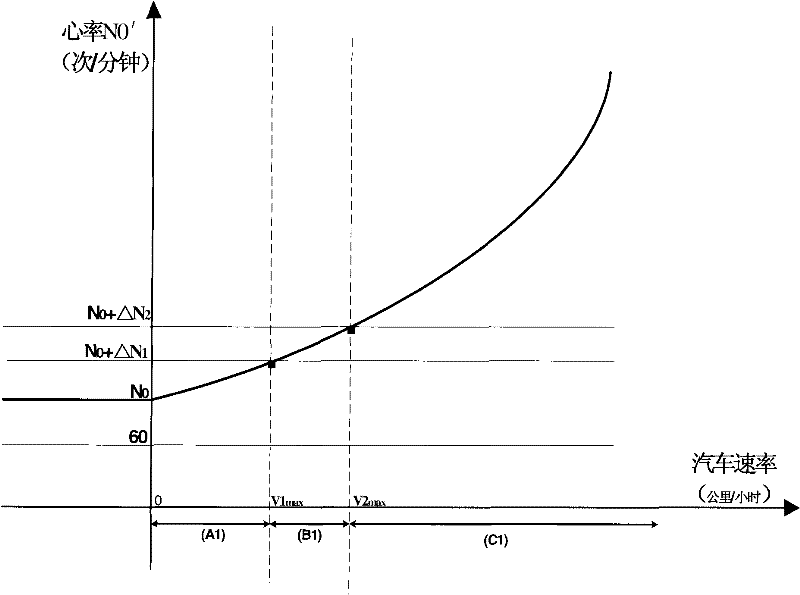
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
136results about "Alarms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
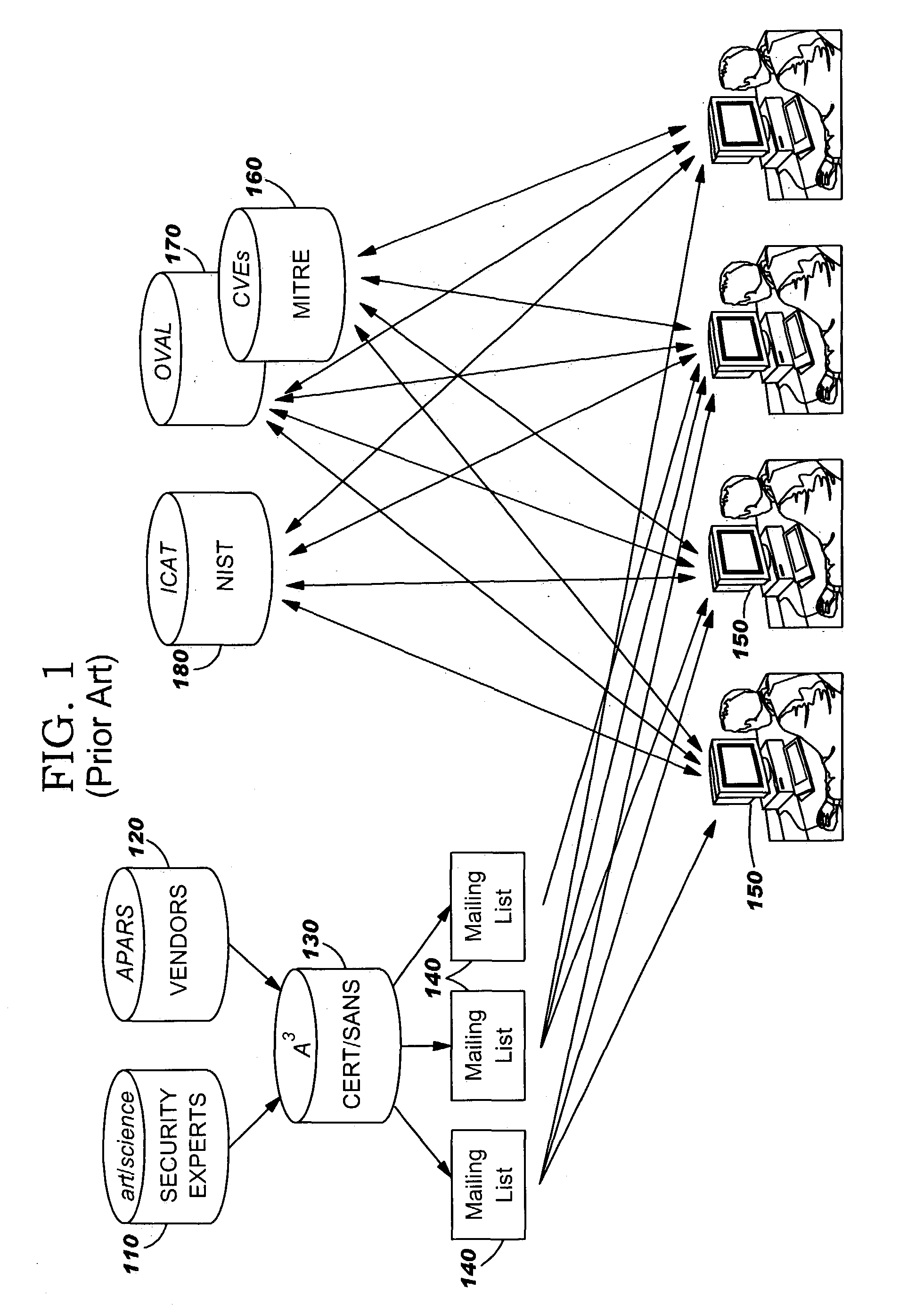
Methods for combating malicious software
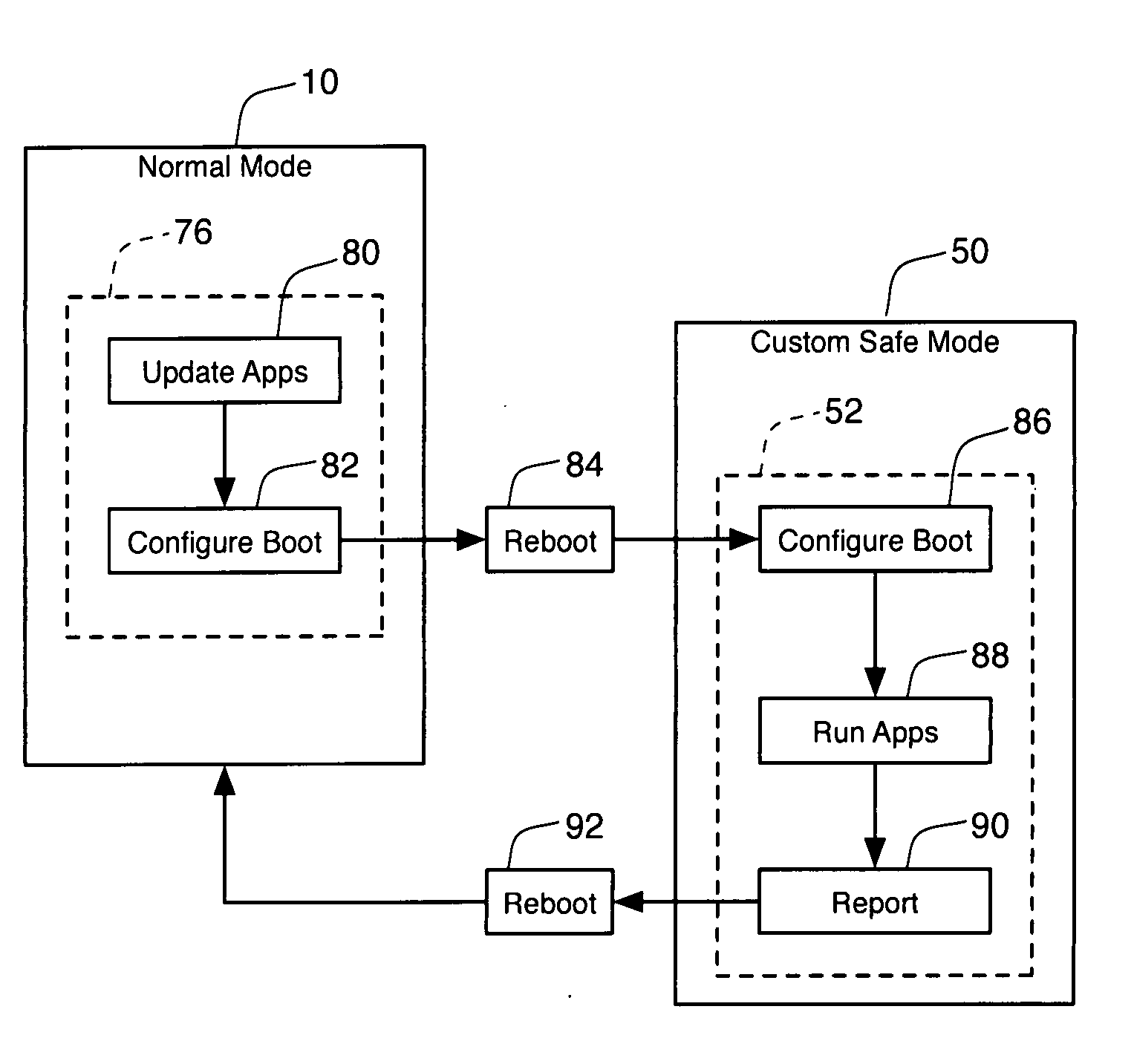
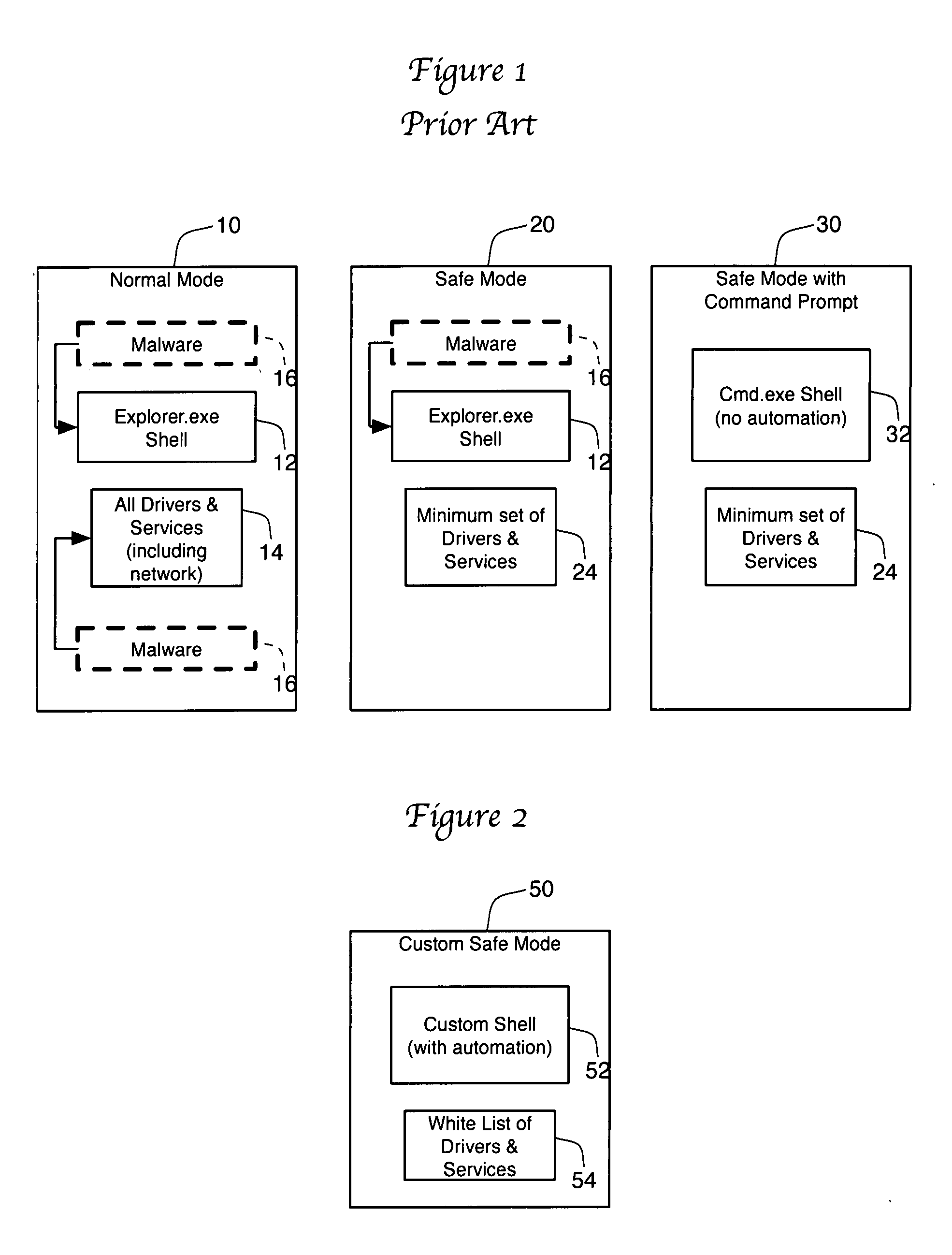
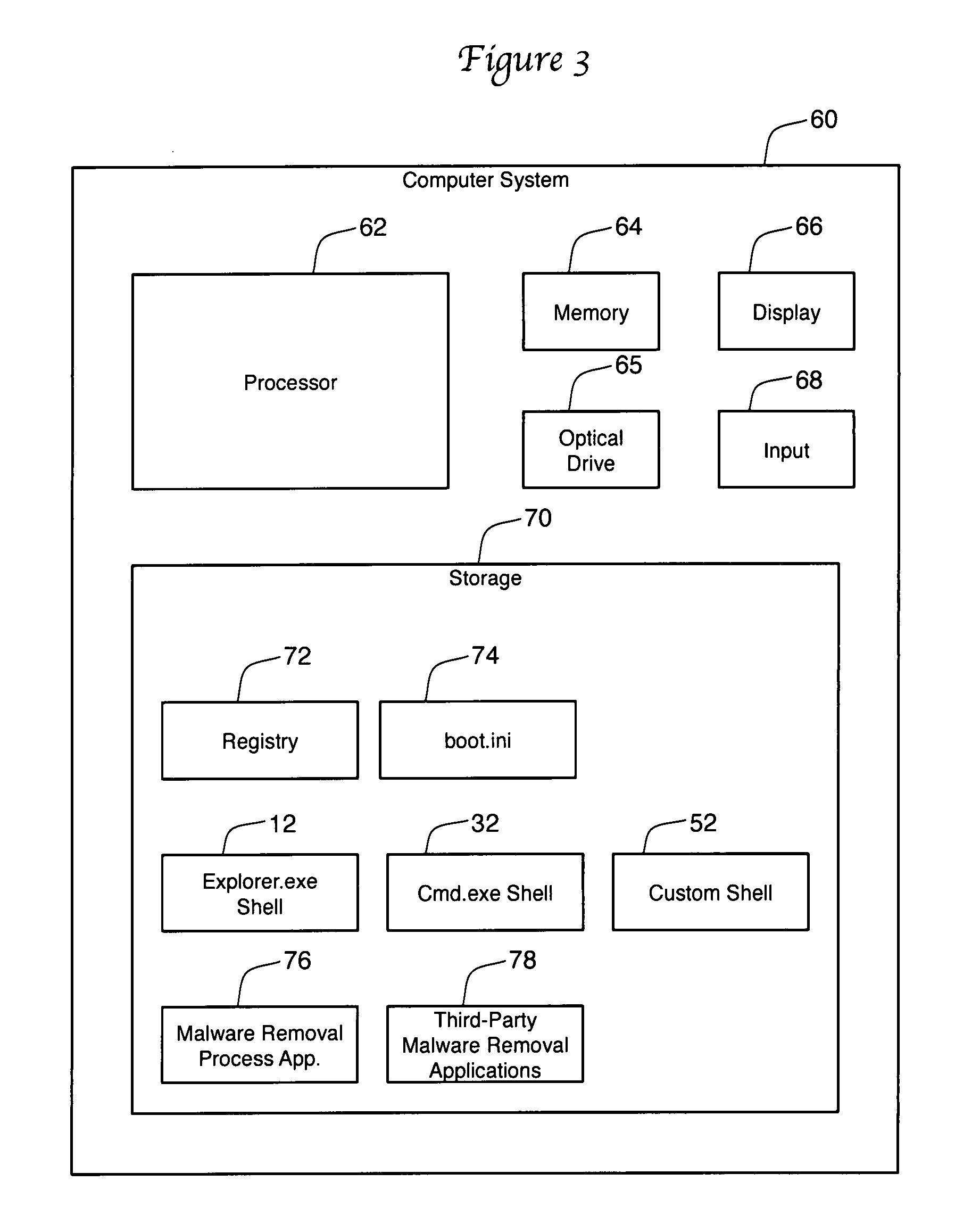
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
Method and Apparatus for Fingerprint Image Reconstruction
Owner:SYNAPTICS INC
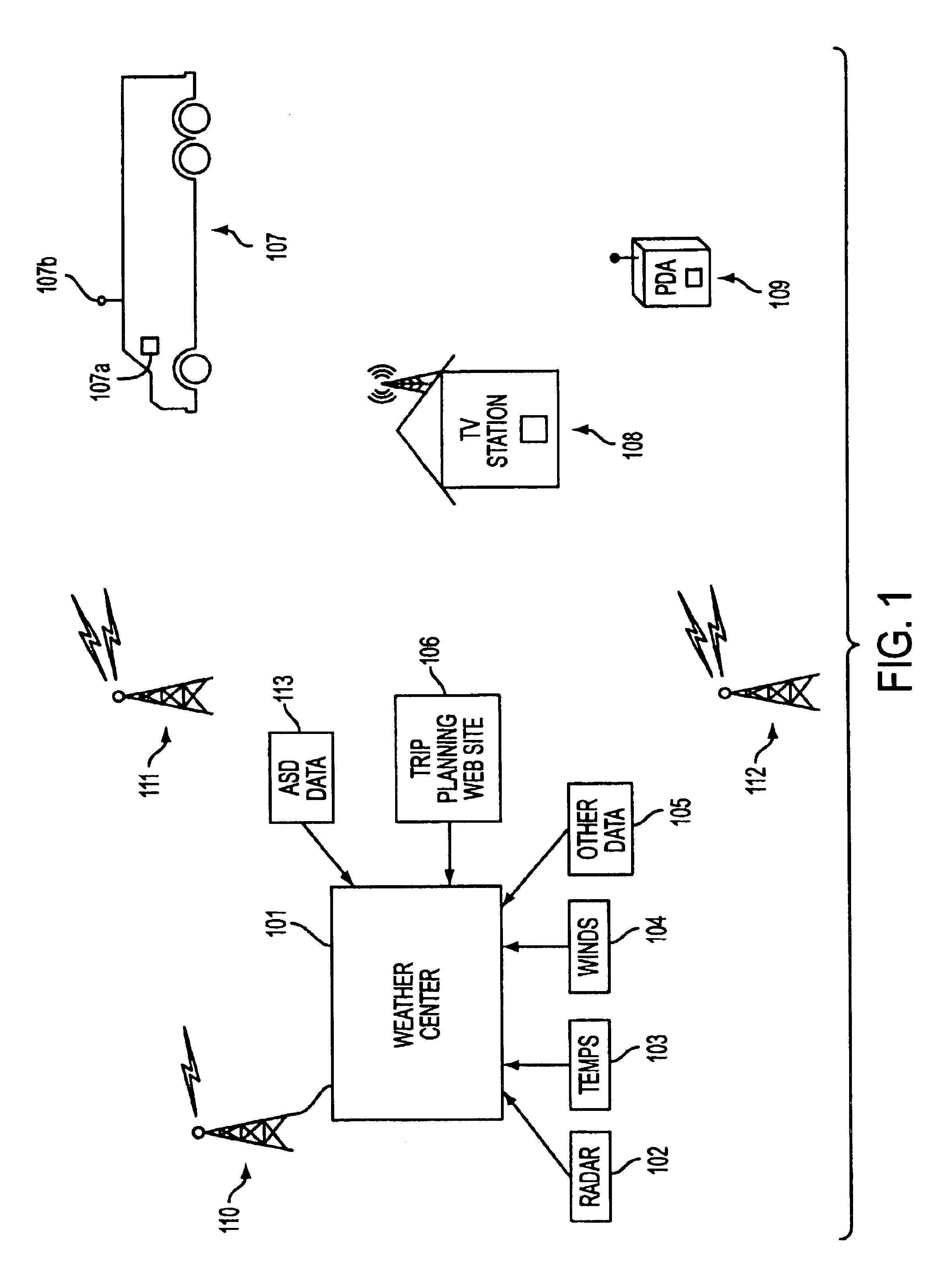
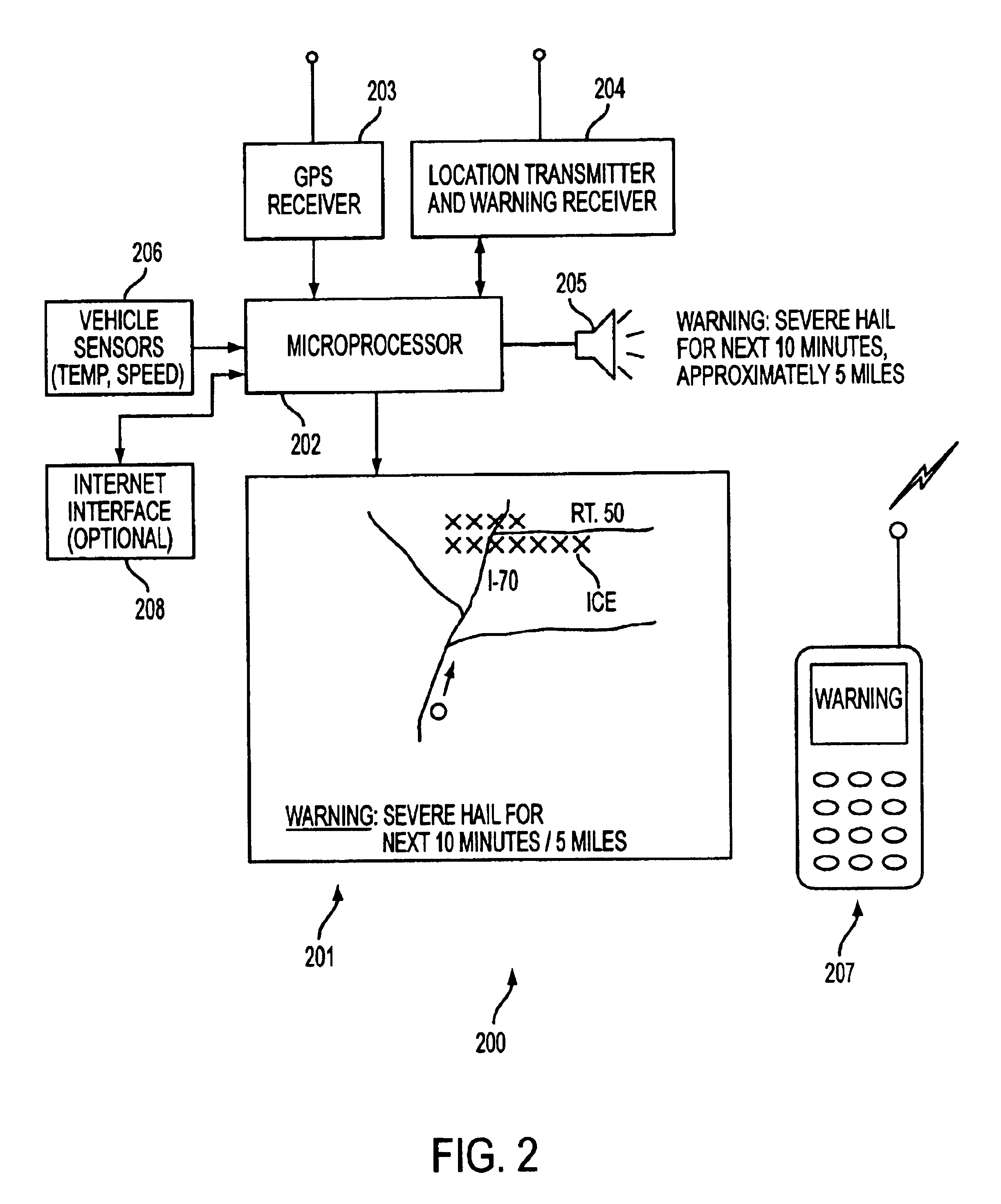
Rotating map and user-centric weather prediction
InactiveUS6845324B2Wide rangeDigital computer detailsAlarmsNumerical weather predictionAtmospheric sciences
Owner:USER CENTRIC IP
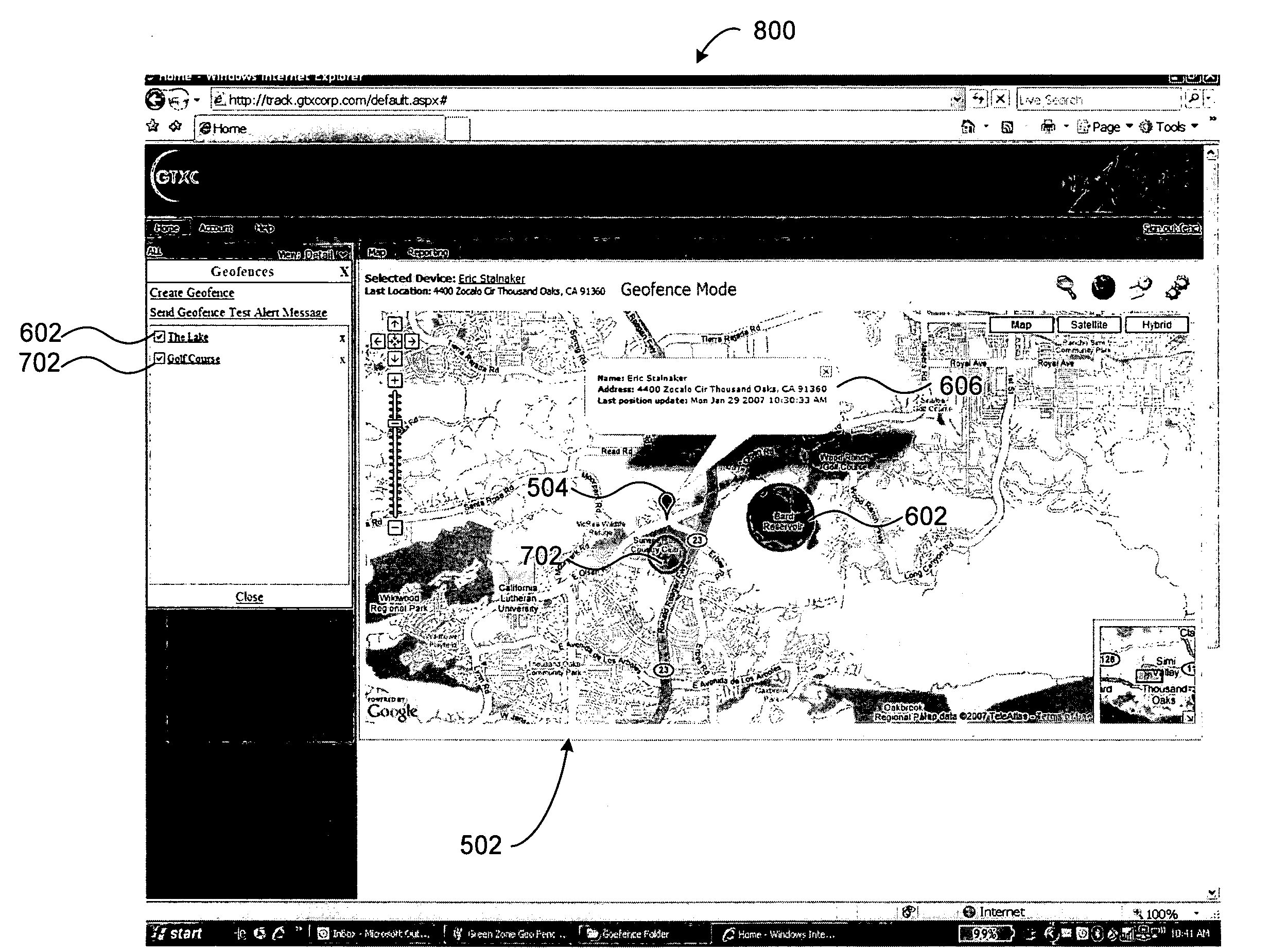
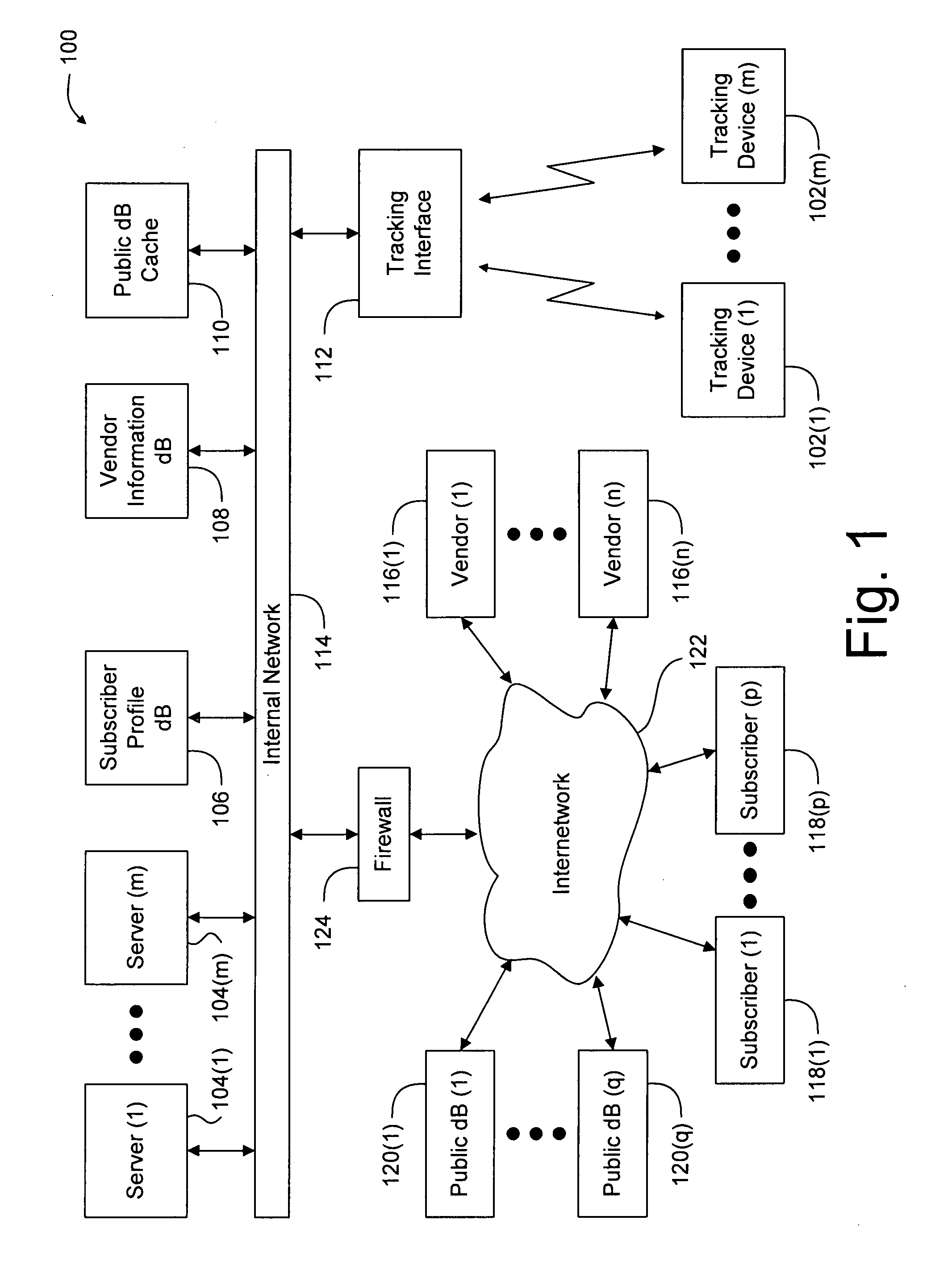
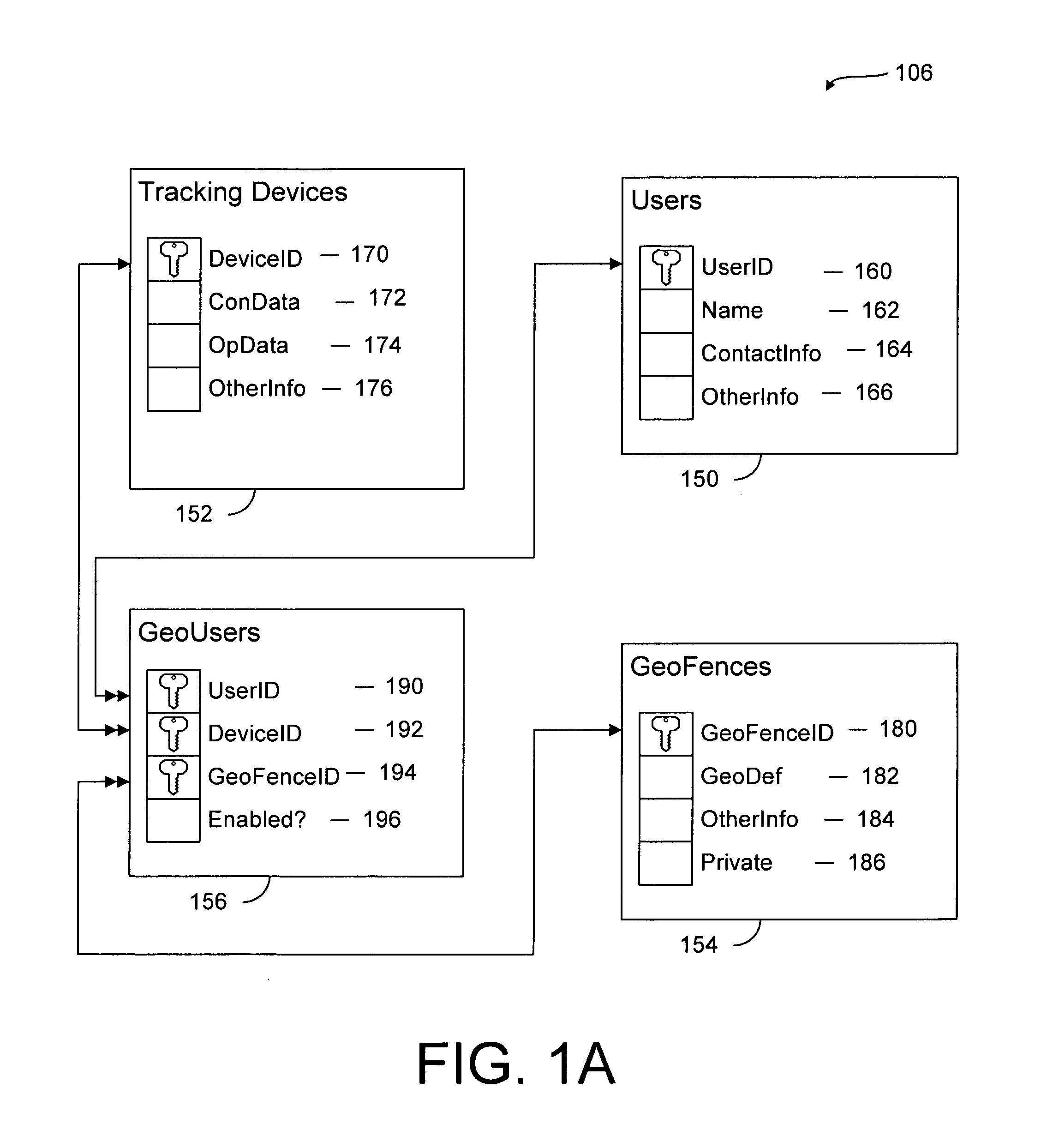
System and method for monitoring the location of a tracking device
InactiveUS20080186165A1Usage can be trackedRoad vehicles traffic controlAlarmsGraphical user interfaceLocation data
Owner:BERTAGNA PATRICK E +2
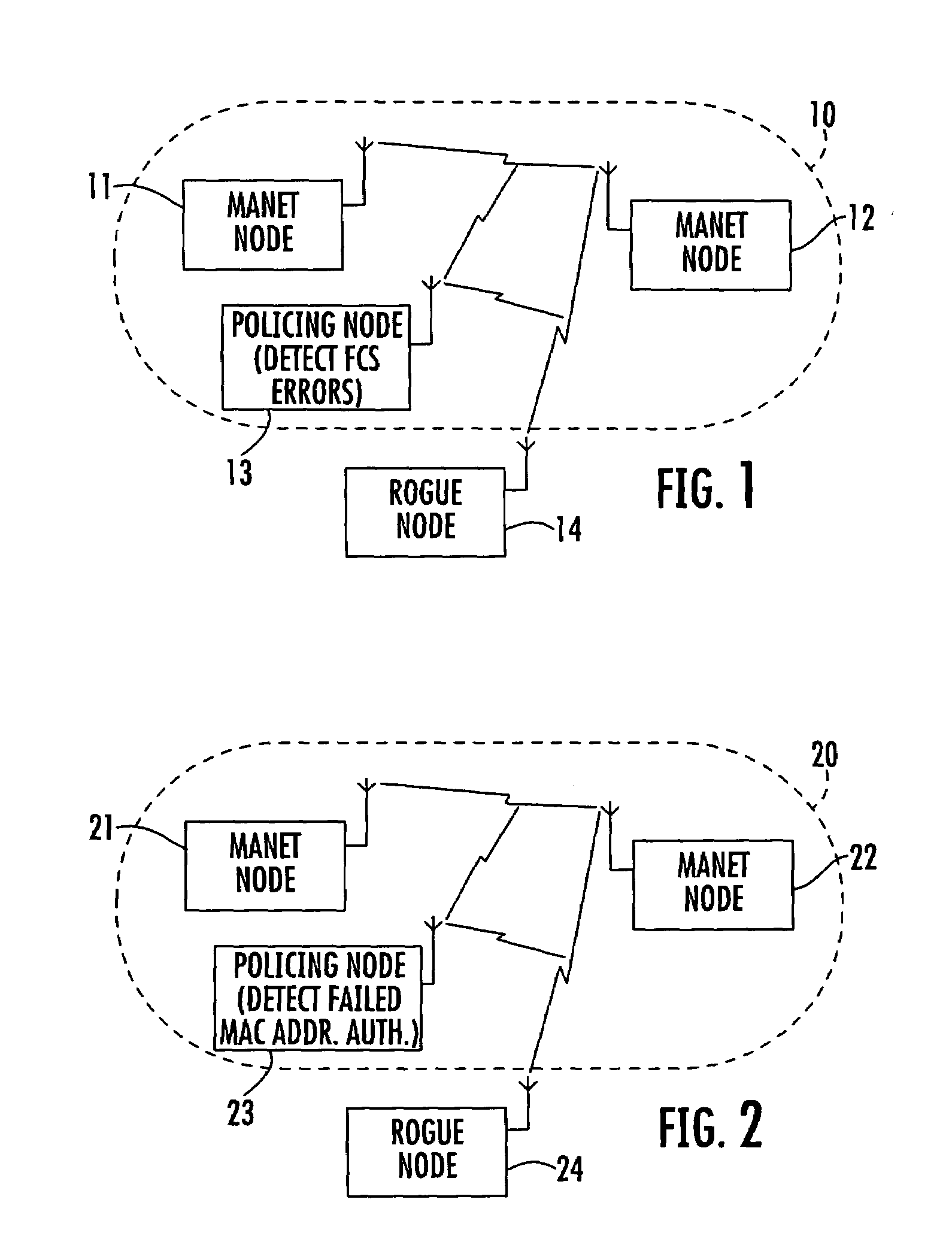
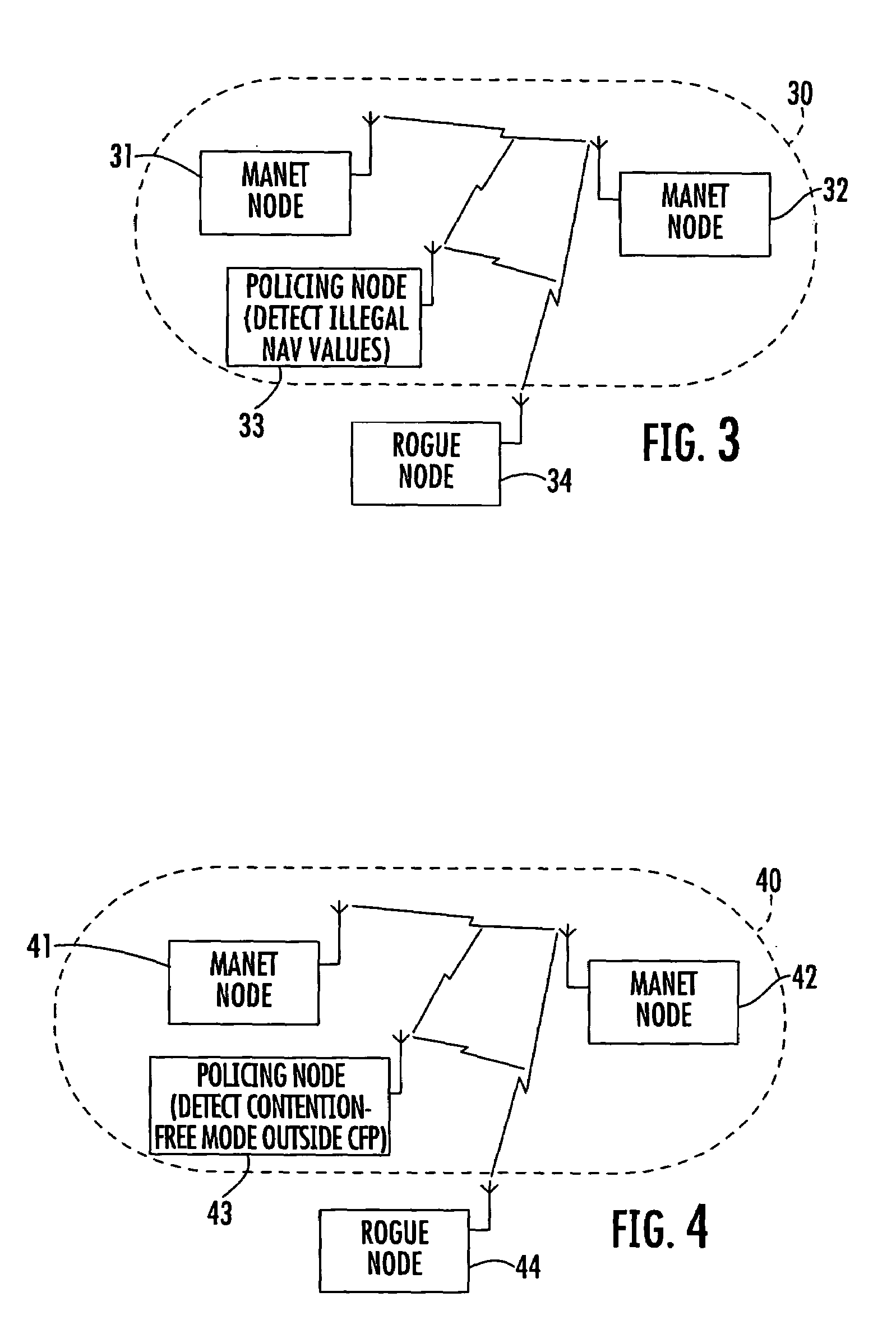
Mobile ad-hoc network with intrusion detection features and related methods
Owner:STINGRAY IP SOLUTIONS LLC
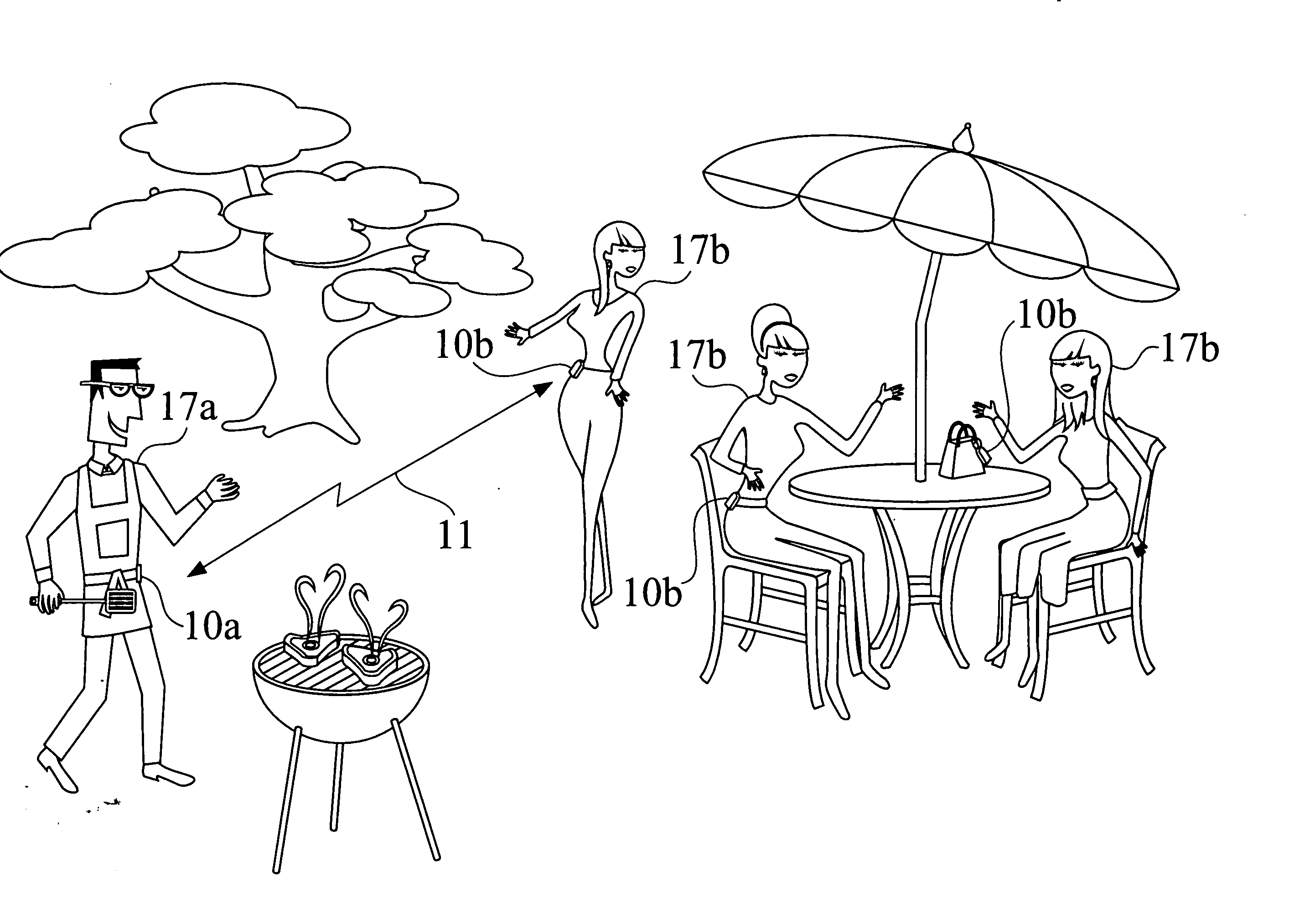
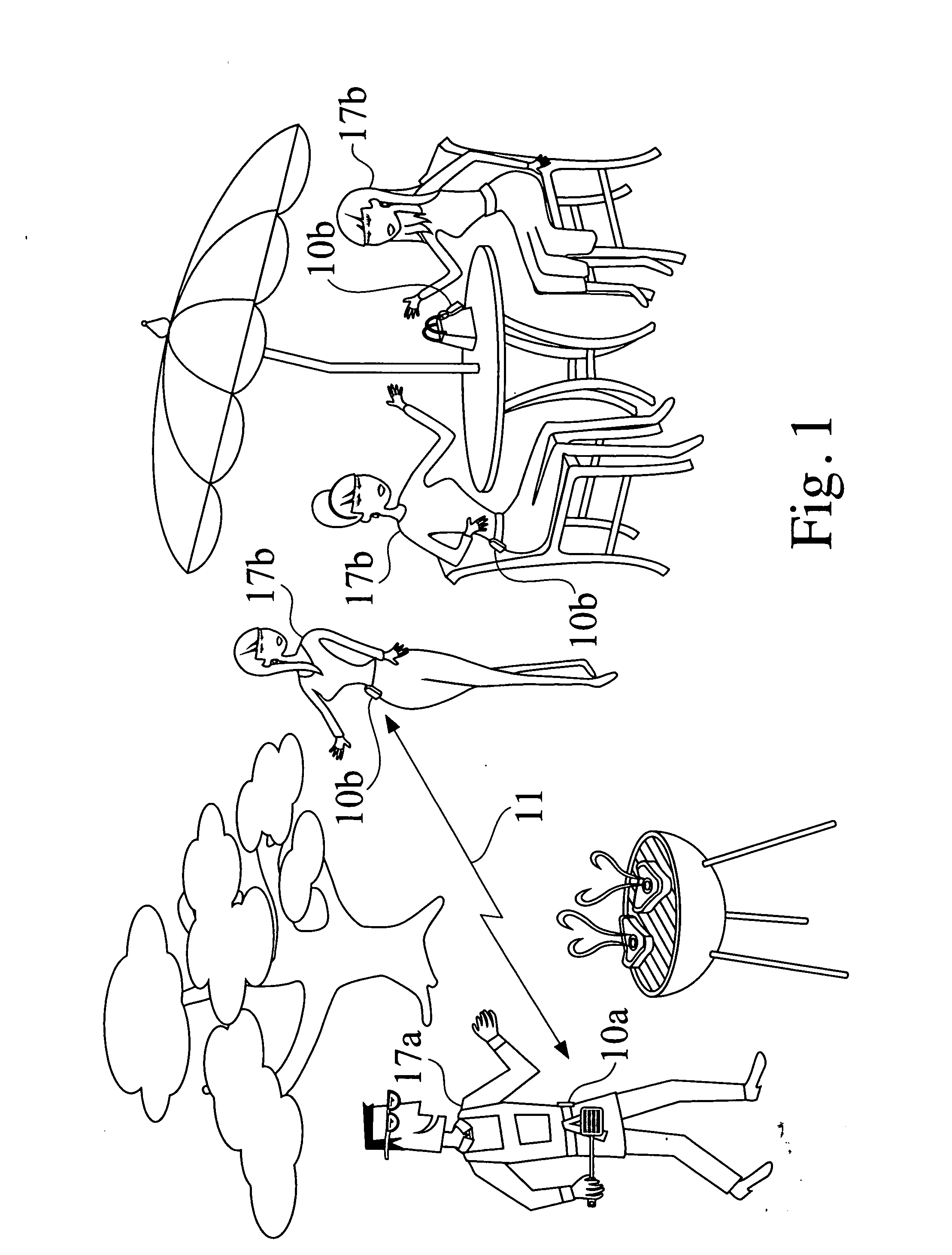
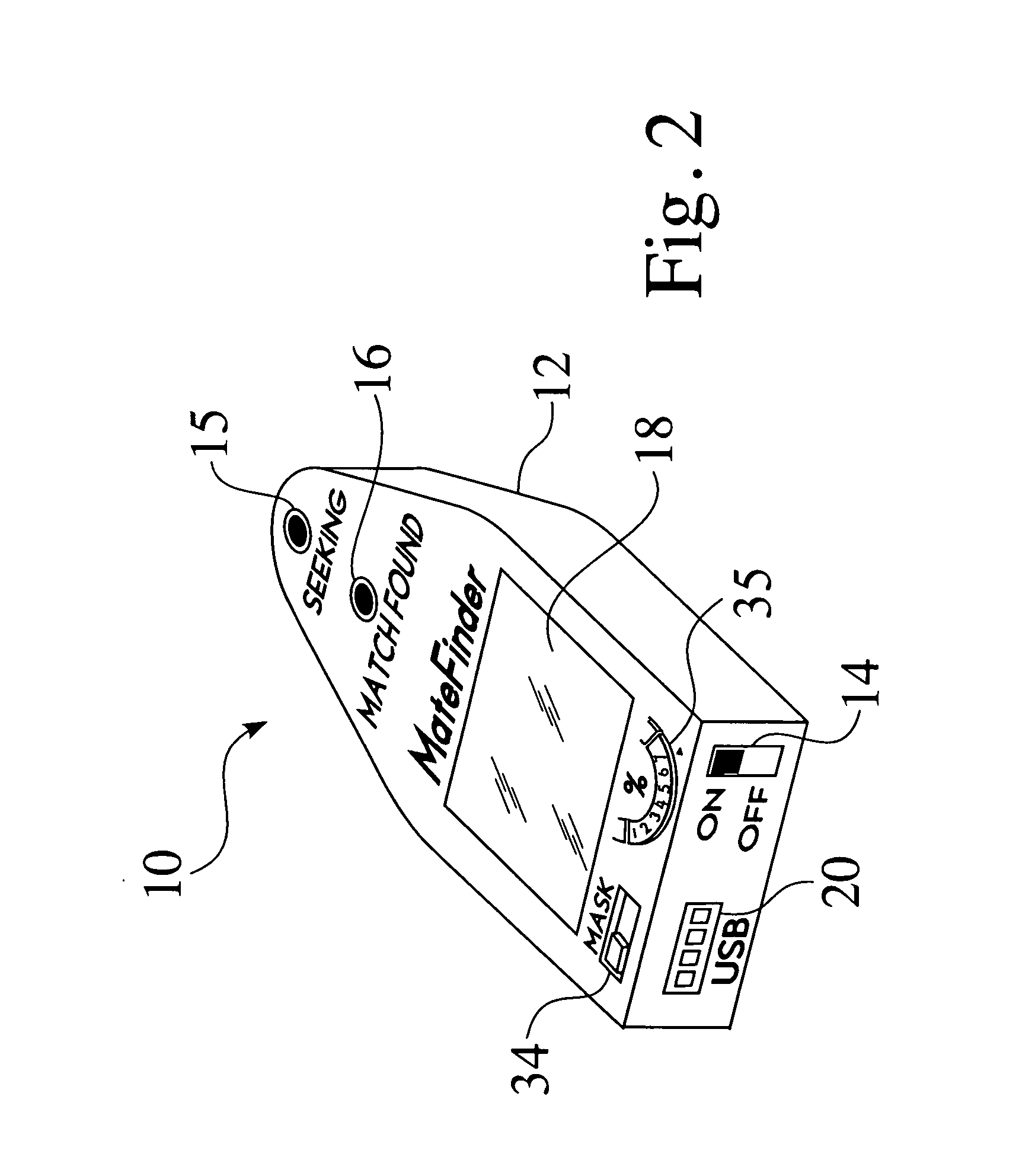
Matching system
InactiveUS20070069901A1Enhances sexual responsivityAlarmsDetergent perfumesHand heldElectronic equipment
Owner:TUCK EDWARD F
Method for providing notification and electronic device thereof
ActiveUS20180225933A1Improve performance deteriorationLoudspeaker transducer fixingBroadcast service distributionOutput deviceReal-time computing
Owner:SAMSUNG ELECTRONICS CO LTD
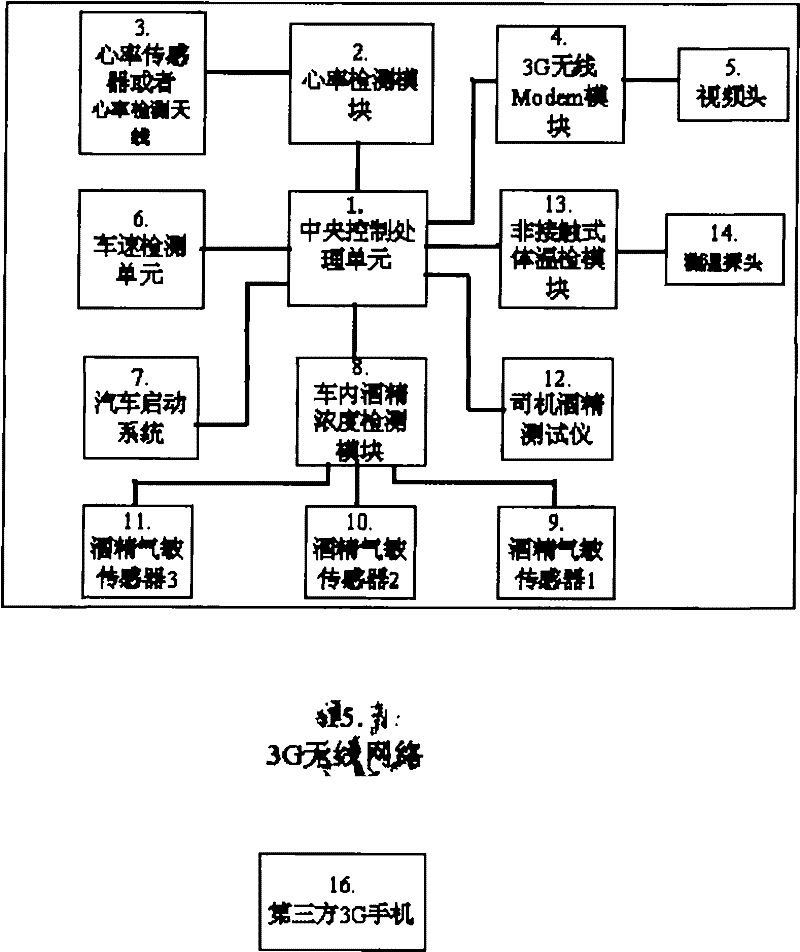
An anti-drunk driving and safe-health driving method
InactiveCN102163362AWays to Prevent Drunk DrivingGood for cardiovascular and cerebrovascular healthSensorsAlarmsThird partyDrunk driving
Owner:谢国华
Cargo theft prevention method and system
InactiveUS20050219037A1StampsKey distribution for secure communicationComputer hardwareCommunications system
Owner:HUANG TAO
Pre-warning method for vehicle
InactiveCN104575063AReduce riskImprove accuracyRegistering/indicating working of vehiclesRoad vehicles traffic controlDriver/operatorTotal risk
The invention discloses a pre-warning method for a vehicle. According to the method, the most appropriate pre-warning rule can be customized according to specific feature information of the vehicle, the pre-warning accuracy is high, and risks in the vehicle driving process are greatly reduced. The method is executed by a vehicle terminal and a background processing system mounted on the vehicle and comprises steps as follows: (1), indexes requiring attention are abstracted according to factors related to driving safety, and a corresponding weighted value is set for each index; (2), vehicle data are collected and comprise static data, vehicle driving dynamic data, space data and driver information; (3), a risk coefficient of each index is calculated according to the weighted value of each index and the corresponding vehicle data, the risk coefficients of all the indexes are accumulated, and a total risk coefficient is obtained; (4), whether the total risk coefficient is in a specified range is judged, if yes, the step (5) is executed, and otherwise, the step (2) is executed; (5), a pre-warning message is sent to the vehicle terminal.
Owner:BEIJING ZHONGJIAOXING ROAD INTERNET OF VEHICLES TECH CO LTD
Malware automated removal system and method
ActiveUS20090013409A1Automate operationImprove software performanceMemory loss protectionError detection/correctionComputerized systemMalware
Owner:BBY SOLUTIONS
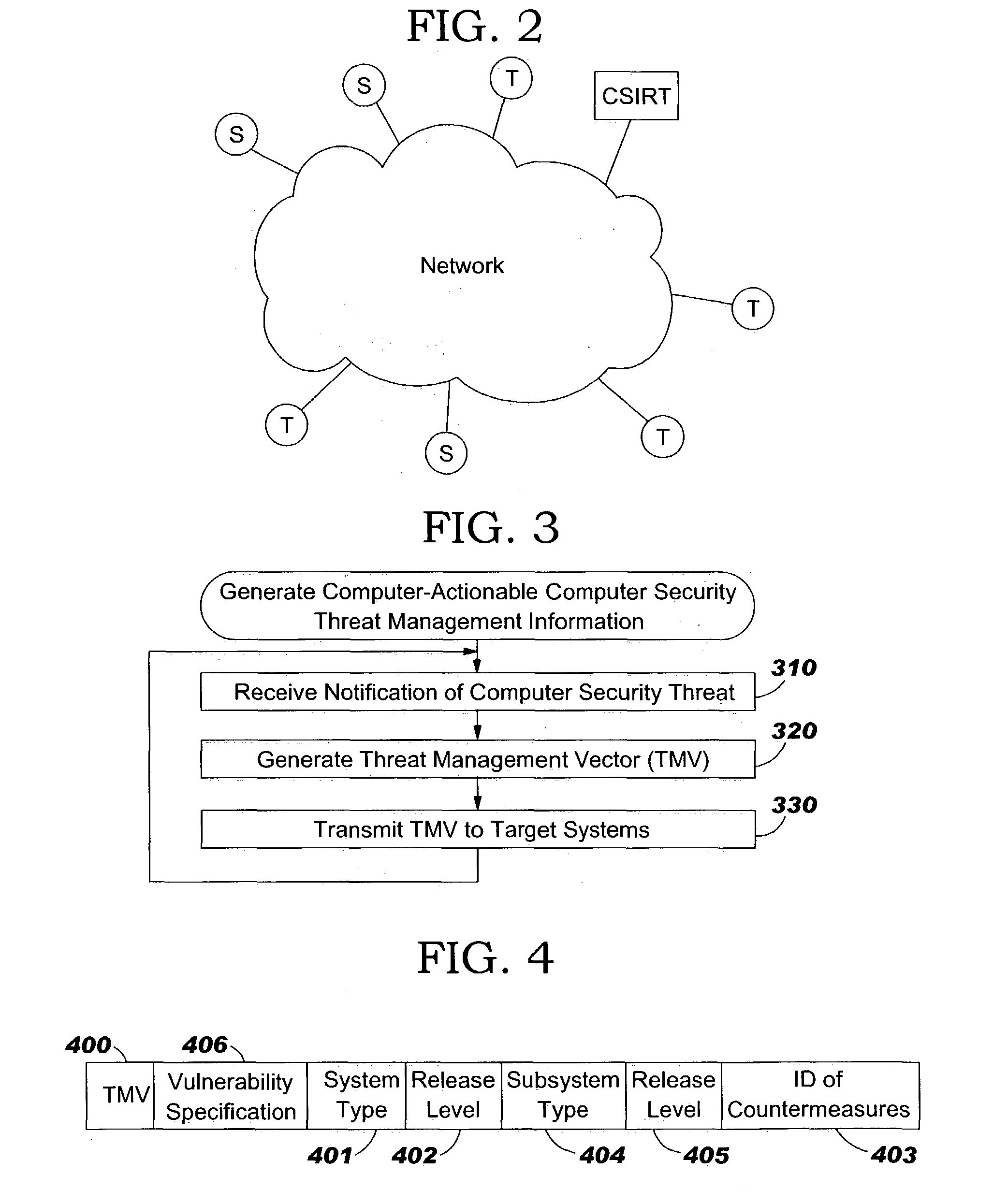
Systems, methods and computer program products for administration of computer security threat countermeasures to a computer system
InactiveUS20050039046A1Memory loss protectionDigital data processing detailsCountermeasureOperational system
Owner:TREND MICRO INC
Depth highlight, depth highlight range, and water level offset highlight display and systems
ActiveUS20110054785A1Good display functionWide flexibilityInstruments for road network navigationRoad vehicles traffic controlWater levelComputer science
Owner:JOHNSON OUTDOORS MARINE ELECTRONICS
Safe driving assisting system based on biological recognition technology
Owner:NANJING GENERAL ELECTRONICS
Automatic vehicle call-for-help method and system
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
In-cabinet thermal monitoring method and system
ActiveUS20100044567A1Avoid disadvantagesTelevision system detailsSwitchgear arrangementsThermal monitoringSwitchgear
Owner:ROCKWELL AUTOMATION TECH
Method of correlation of images in biometric applications
InactiveUS6961449B2Reduce background noiseElectric signal transmission systemsImage analysisPattern recognitionPalm print
Owner:UNIVERSITY OF MASSACHUSETTS LOWELL
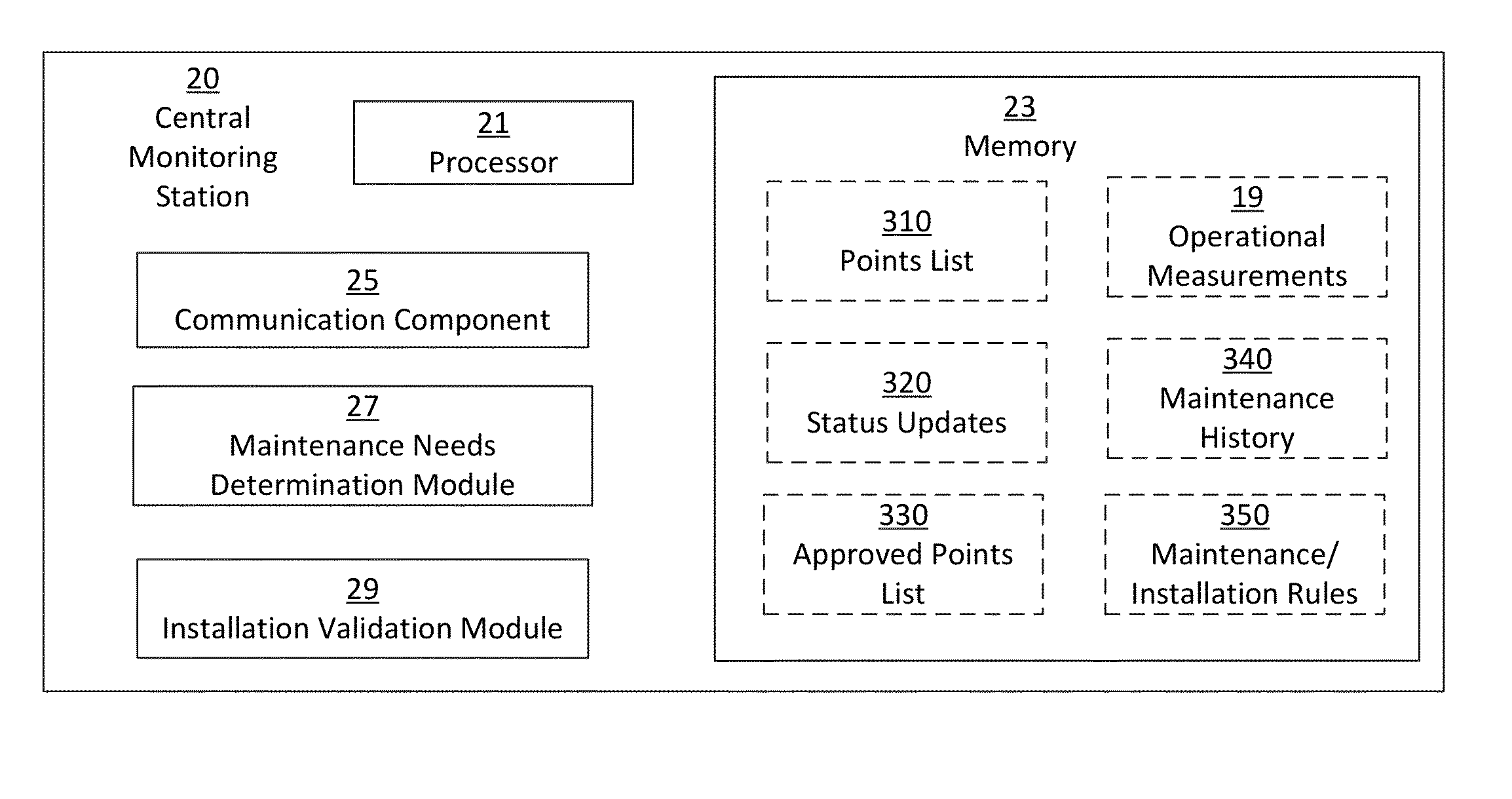
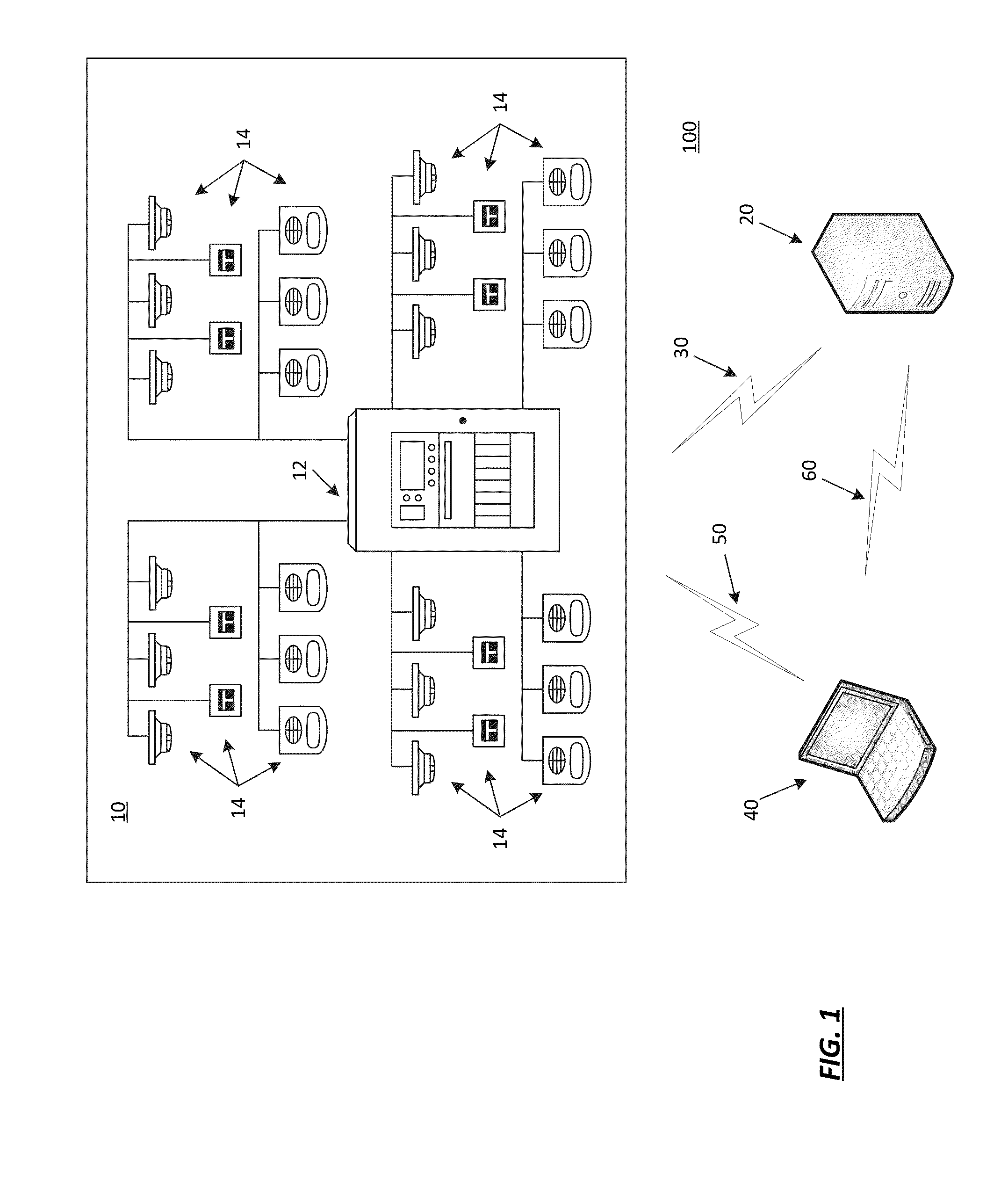
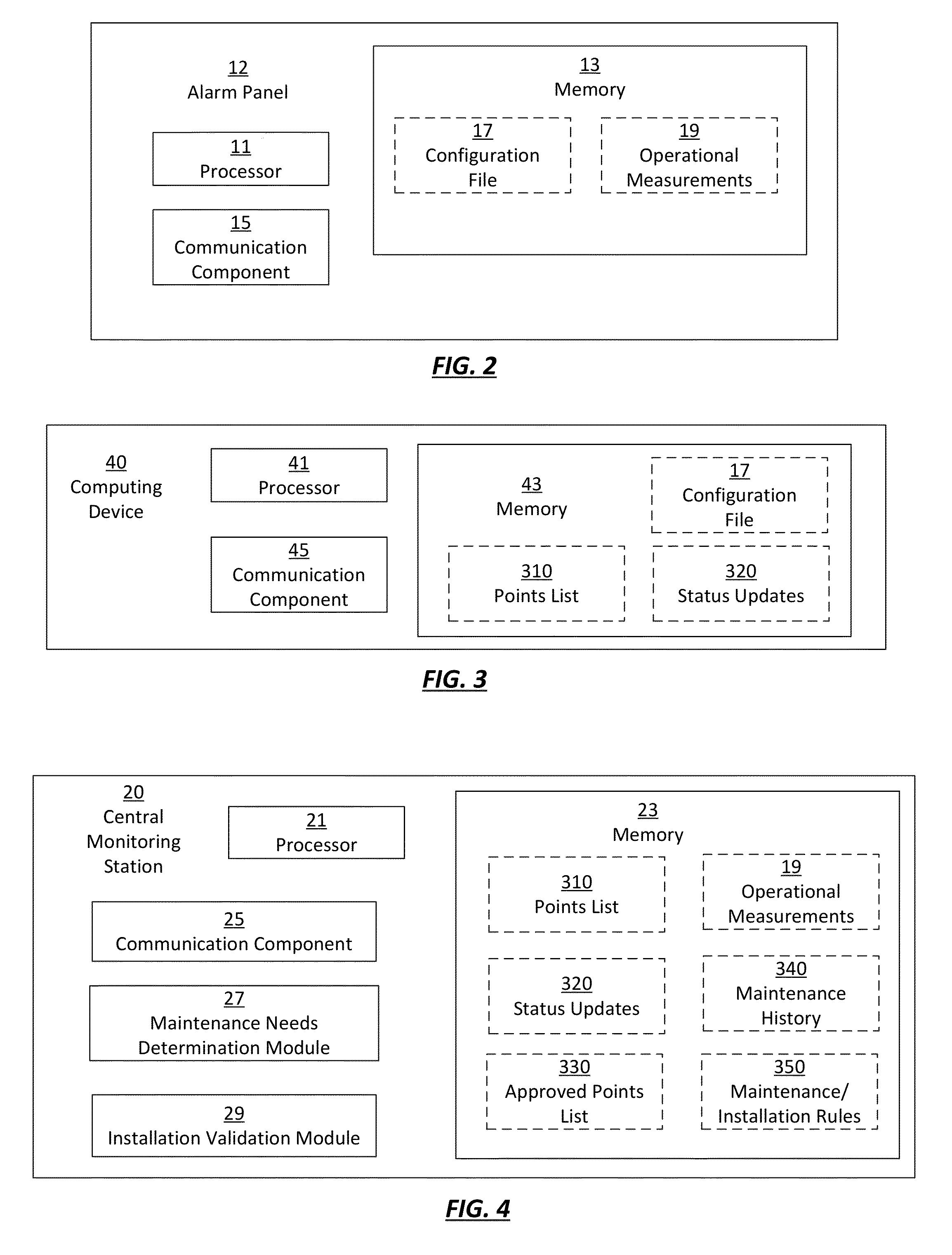
Method and apparatus for determining maintenance needs and validating the installation of an alarm system
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Eye guard with voice indication
InactiveUS20080082179A1Less interferenceIncrease power consumptionComputer controlElectric controllersElectricityDisplay device
An eye guard with voice indication is provided, and it includes an eye guard body, a filter, a display device and a voice output device. The display device is mounted inside the eye guard body to display a circumstance value or operating condition information. Furthermore, the voice output device is electrically connected with the display device and includes a main controller, a power supply, a sound output controller, a sensor circuit and a drive circuit. The sensor circuit has at least one sensor exposed on an external surface of the eye guard body and defined in a supposed centerline of the filter to detect the surrounding circumstance. Thus, the circumstance value and the operation condition information are noticed in the form of voice and vision simultaneously for the operators.
Owner:YANG YEA CHYI
Locks for wearable electronic bands
Provided is an electronic lock for wearable electronics, the electronic lock including: a button assembly; a spring assembly coupled to the button assembly, the spring assembly comprising: two bent arms configured to compress under a force applied to the button assembly; and an aperture configured to receive a stopping element when the locking mechanism is in a locked position; an actuator configured to electronically control movement of the stopping element in and out of the aperture; and a control circuit comprising: a tangible non-transitory machine readable media storing instructions that when executed by one or more processors of the control unit effectuate operations comprising: receiving a request to unlock the locking mechanism; sending a request for authentication; receiving authentication information; and controlling the actuator to move the stopping element from the locked position.
Owner:CEDAR LANE TECH INC
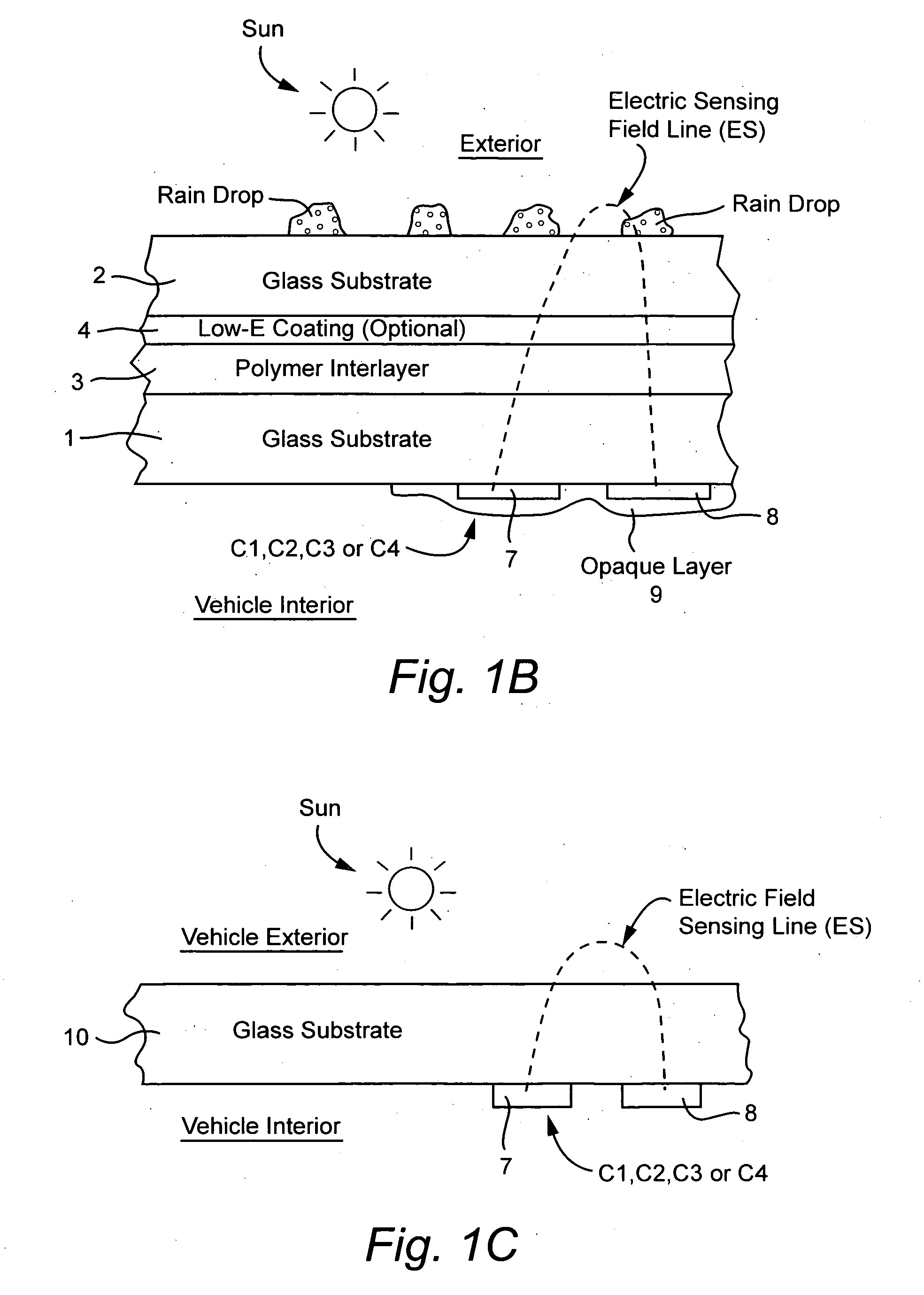
Rain sensor with sigma-delta modulation and/or footprinting comparison(s)
InactiveUS20070157721A1Hazard reductionReduce distractionsDC motor speed/torque controlEmergency protective circuit arrangementsCapacitanceEngineering
Owner:GUARDIAN GLASS LLC
Geological disaster early warning system
InactiveCN110264672APrediction is accurateIntelligent monitoringAlarmsEarly warning systemData management
Owner:GUANGZHOU URBAN PLANNING & DESIGN SURVEY RES INST +1
Device and method for monitoring and early warning of flood damages based on multi-resource integration
ActiveCN105894741AImprove accuracyExact approximation to the true solutionHuman health protectionAlarmsMulti resourceRadar
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Falling accident detecting system based on dual technologies
Owner:SHANGHAI JIAO TONG UNIV
System and Method for Detecting and Evicting Malicious Vehicles in a Vehicle Communications Network
ActiveUS20110214178A1Improve performanceReduce impactMemory loss protectionError detection/correctionMathematical modelSimulation
In a vehicle communication network, some vehicles may be used by attackers to send false information to other vehicles which may jeopardize the safety of other vehicles. Vehicles should be able to detect malicious communications activities and to mitigate the impact of malicious vehicles by evicting (eliminating) suspected malicious vehicles from the system. Evicting a vehicle is to ignore the messages sent from the vehicle for a specified time period. Voting and sacrifice principles are combined using a mathematical model based on the “Mafia Game”. The Mafia Game model focuses on the relative size of the group of attackers within a neighborhood necessary to dominate the entire network in the neighborhood (i.e., to eventually evict all the innocent vehicles).
Owner:PERSPECTA LABS INC
Credit card verification system and method
InactiveUS6912312B1Accurate comparisonElectric signal transmission systemsImage analysisCredit cardCommunication unit
The invention provides a credit card verification system, including a credit card company data storage and communication unit (4) for recording and storing data concerning authorized credit card holders, including an electronically reproducible image of each credit card holder, means (6) for introducing the image into the company data storage unit, and at least one remotely positioned credit card reader (10) and image display meants (12) communicating with the company data storage unit, for selectively retrieving data from the storage unit to be displayed on the image display means, to be viewed and approved by the person providing sales services. The invention also provides a method for verifying the identity of a credit card holder effecting a tansaction and a method enabling credit companies to monitor and verify credit card holder identity when a payment transaction is performed at a sales terminal.
Owner:CALLAHAN CELLULAR L L C
Anti-theft method based on compass short message function and anti-theft system based on compass short message function
ActiveCN103150874ARealize anti-theftAnti-theft in timeAnti-theft devicesAlarmsComputer terminalMobile Web
The invention provides an anti-theft method based on a compass short message function. The anti-theft method based on the compass short message function comprises the following steps: arranging an alarm information receiving address in advance; collecting gesture data of a target device in real time; judging whether a carrier is in a static state according to acceleration data, when the carrier is not in the static state, judging whether the acceleration data and replacement exceed preset values, when the acceleration data and the replacement exceed the preset values, judging that the target device is stolen, and retransmitting alarm information to the alarm information receiving address through a compass communication satellite or a mobile network. The invention further provides an anti-theft system based on the compass short message function. The anti-theft system based on the compass short message function comprises a compass receiving and transmission terminal, a gesture sensor and a controller. The controller is used for storing the preset alarm information receiving address, and judging whether the target device is stolen. The compass receiving and transmission terminal is used for retransmitting the alarm information through the compass communication satellite. The gesture sensor contains compass navigation location, and is used for collecting the gesture data of the target device. The anti-theft method based on the compass short message function and the anti-theft system based on the compass short message function are capable of timely carrying out effective alarms.
Owner:CHENGDUSCEON ELECTRONICS
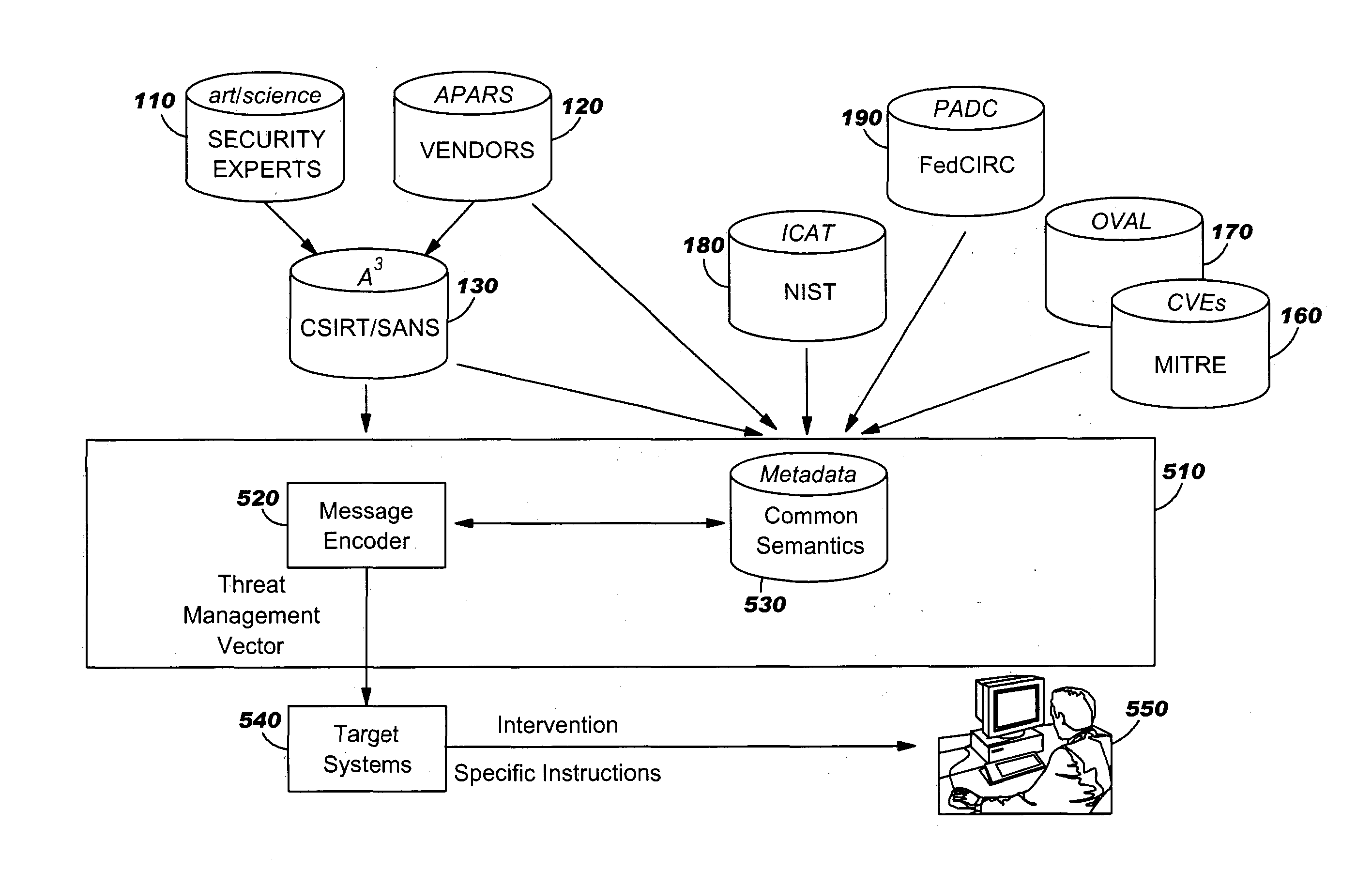
Alert transmission apparatus and method for policy-based intrusion detection and response
An alert transmission apparatus for a policy-based intrusion detection and response has a central policy server (CPS) and an intrusion detection and response system (IDRS). In the CPS, a policy management tool generates security policy information and then stores the generated security policy information in a policy repository. A COPS-IDR server sends the information to the IDRS and an IDMEF-XML-type alert transmission message to a high-level module. An IDMEF-XML message parsing and translation module stores a parsed and translated IDMEF-XML-type alert transmission message in an alert DB or provides the message to an alert viewer. In the IDRS, a COPS-IDR client generates the IDMEF-XML-type alert transmission message and provides the message to the CPS. An intrusion detection module detects an intrusion. An intrusion response module responds to the intrusion. An IDMEF-XML message building module generates an IDMEF-XML alert message and provides the message to the COPS-IDR client.
Owner:ELECTRONICS & TELECOMM RES INST
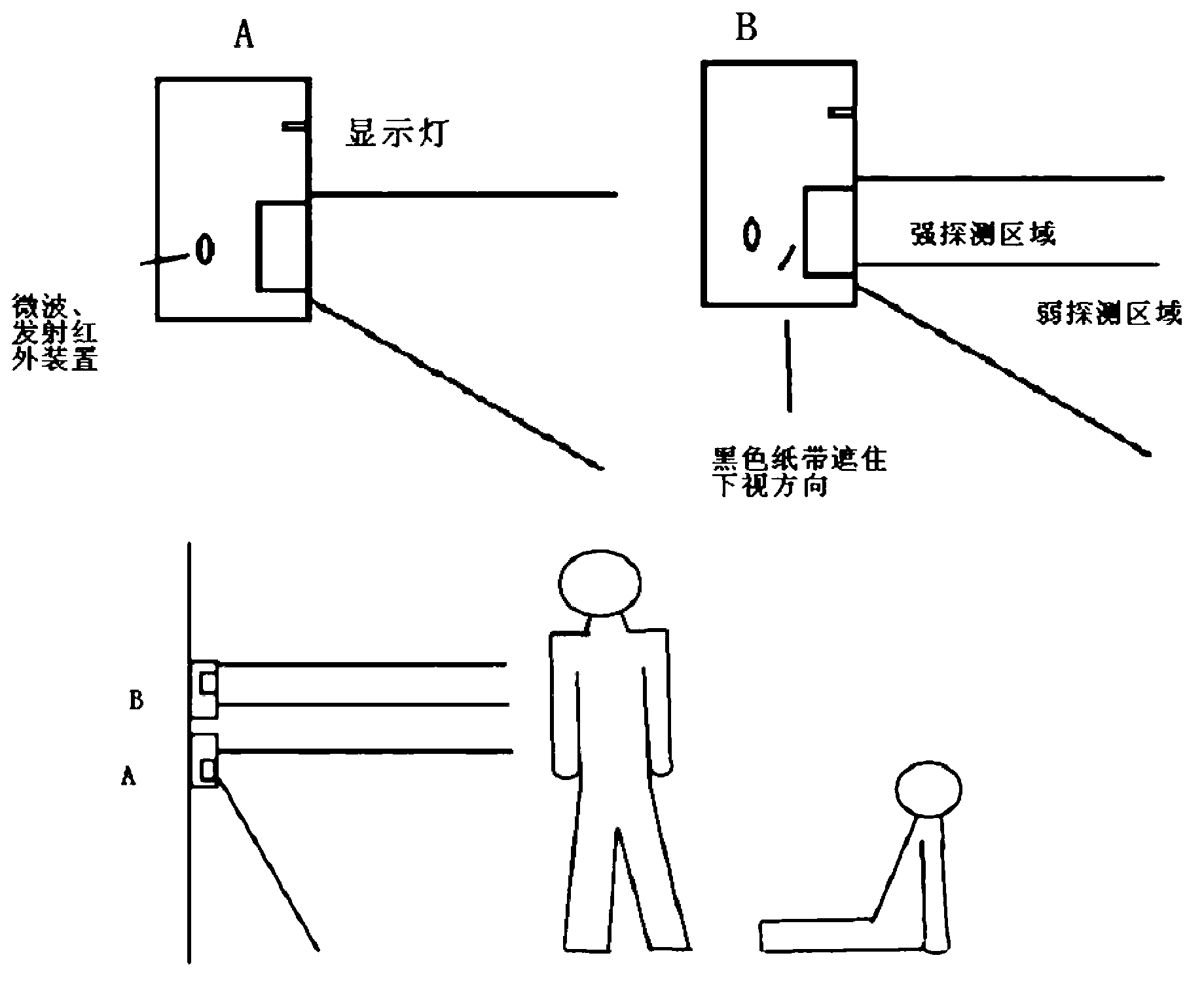
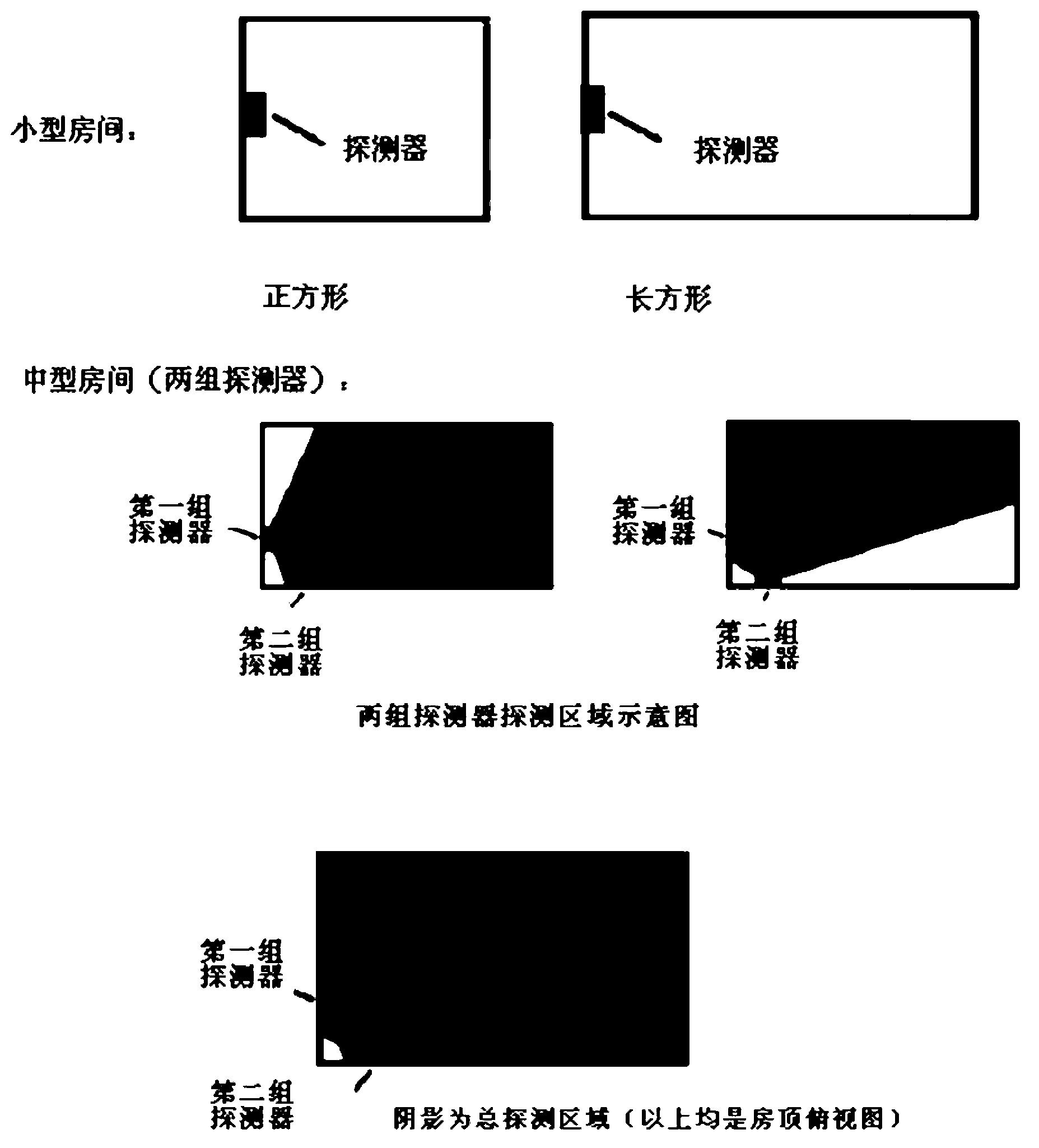
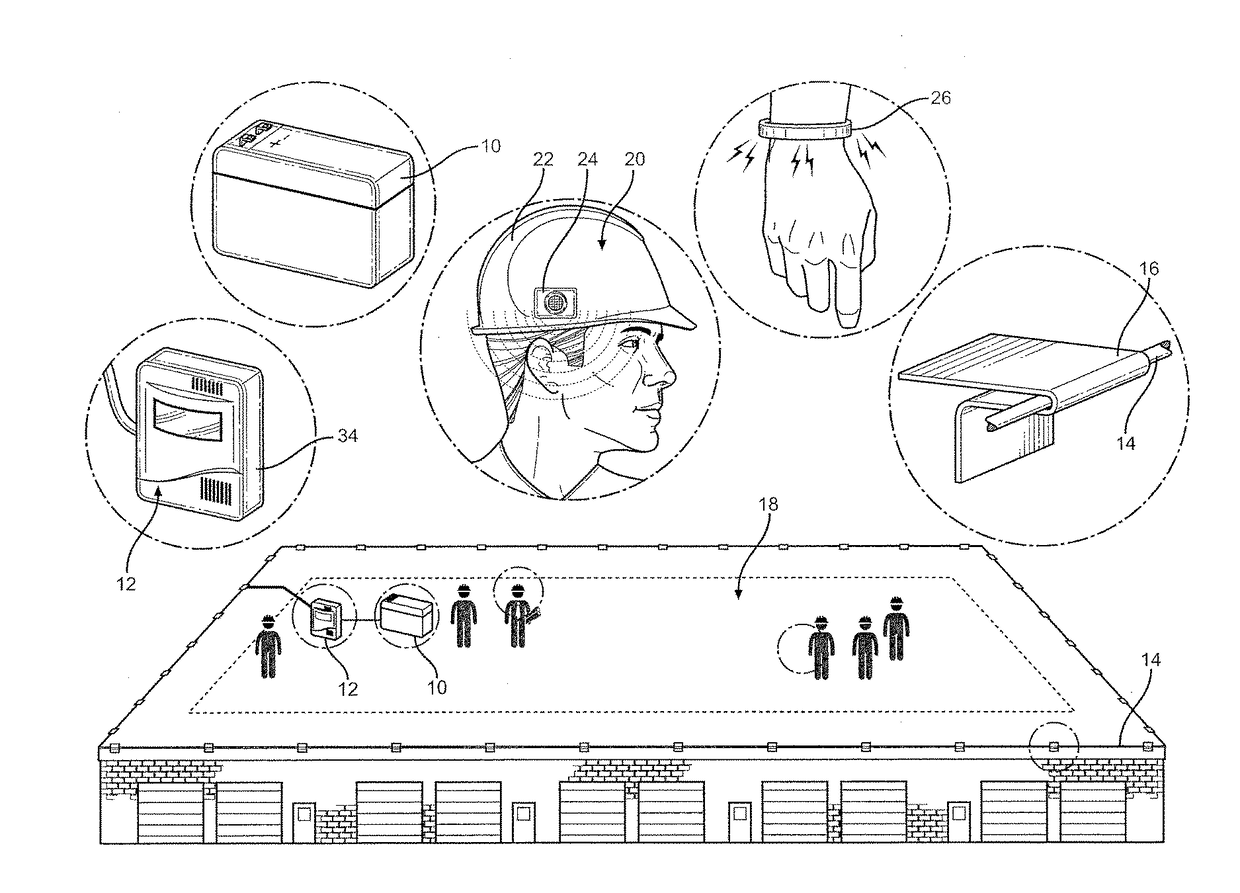
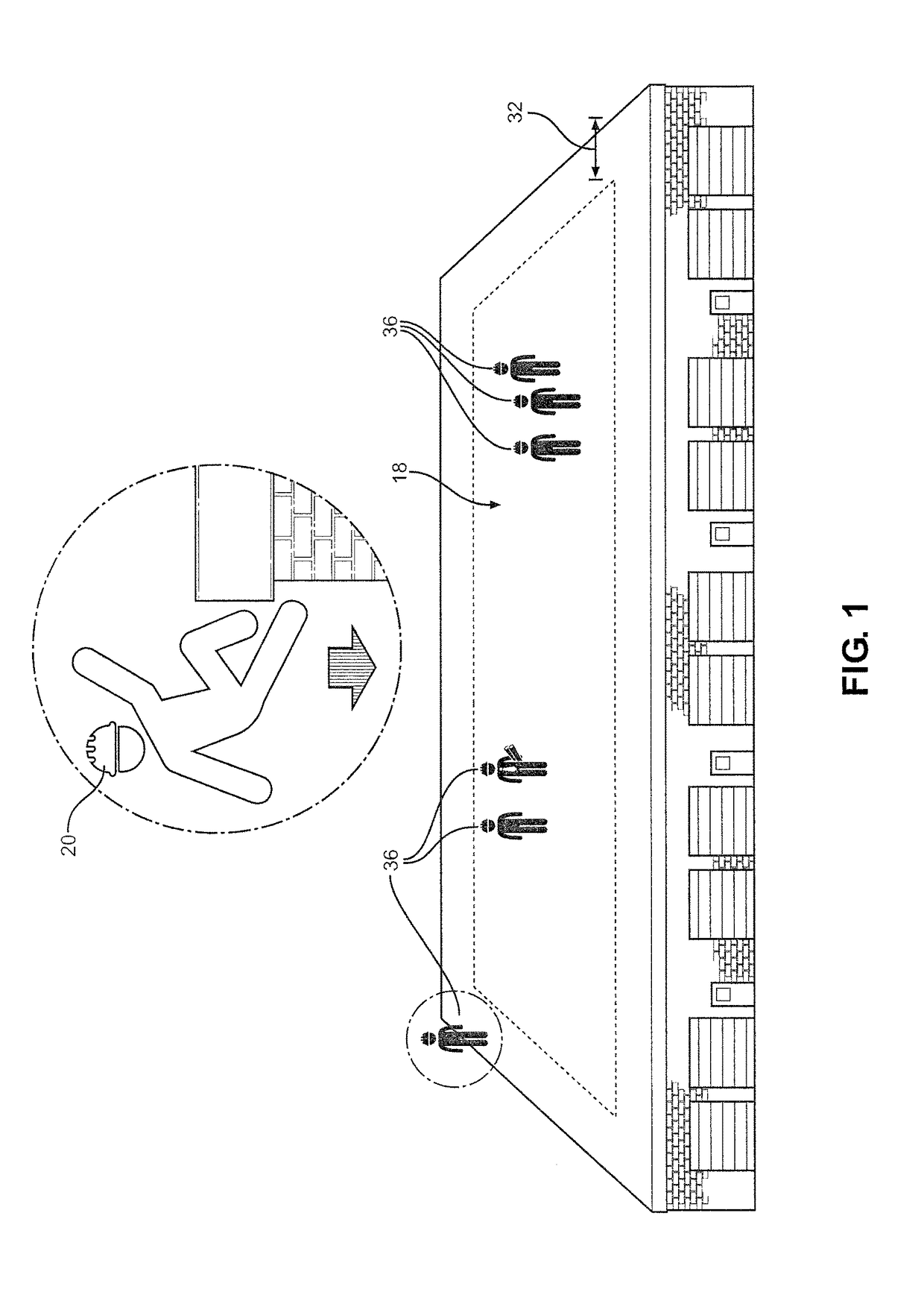
Fall protection for low slope roofers using radio waves
InactiveUS20170243457A1Easy to installLess interferenceSubstation equipmentAlarmsFall protectionPersonal protective equipment
Owner:MILBRAND JON
System and method for securing computers against computer viruses
In one embodiment, an antivirus mechanism (e.g., antivirus program) in a computer initiates shielding procedures in response to a triggering event indicative of a presence of a virus in the computer, the virus being of a type not recognized by the antivirus program. The shielding procedures advantageously protect important components of the computer while the antivirus program does not have the requisite antidote to directly deal with the virus.
Owner:TREND MICRO INC
Popular searches
User identity/authority verification Unauthorized memory use protection Analogue secracy/subscription systems Computer security arrangements Special data processing applications Input/output processes for data processing Programme control Simulator control Location information based service Hardware monitoring
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap