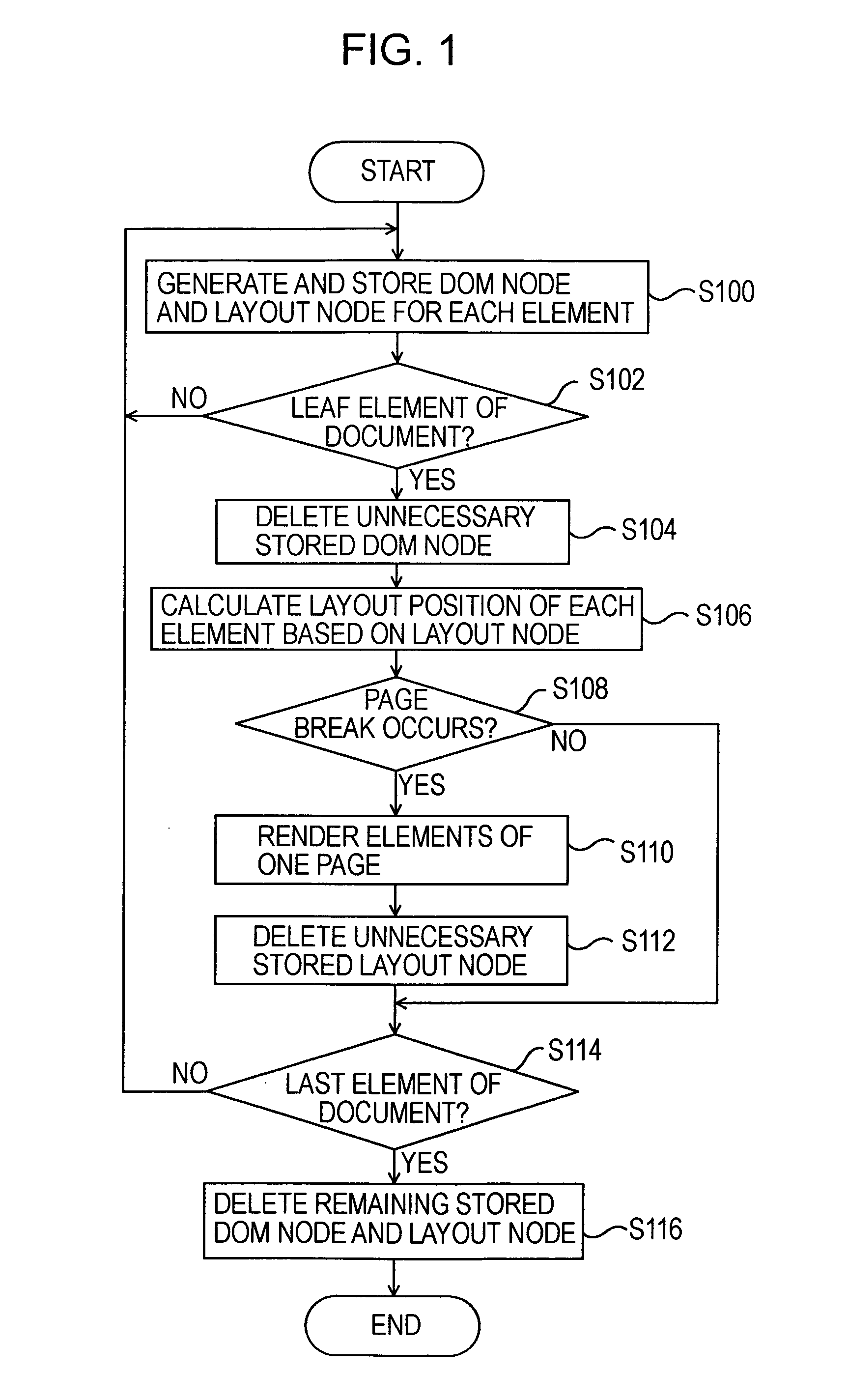
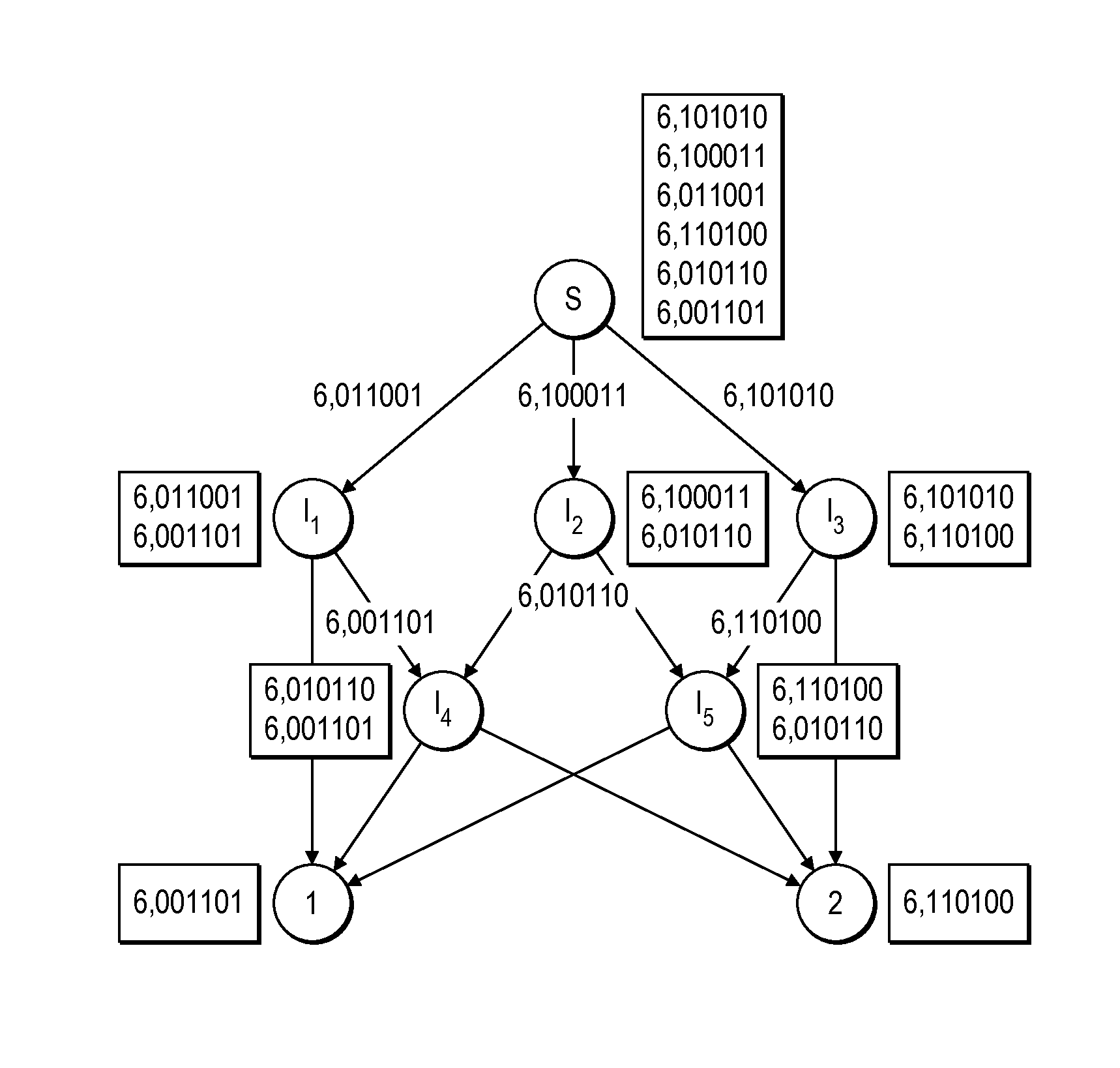
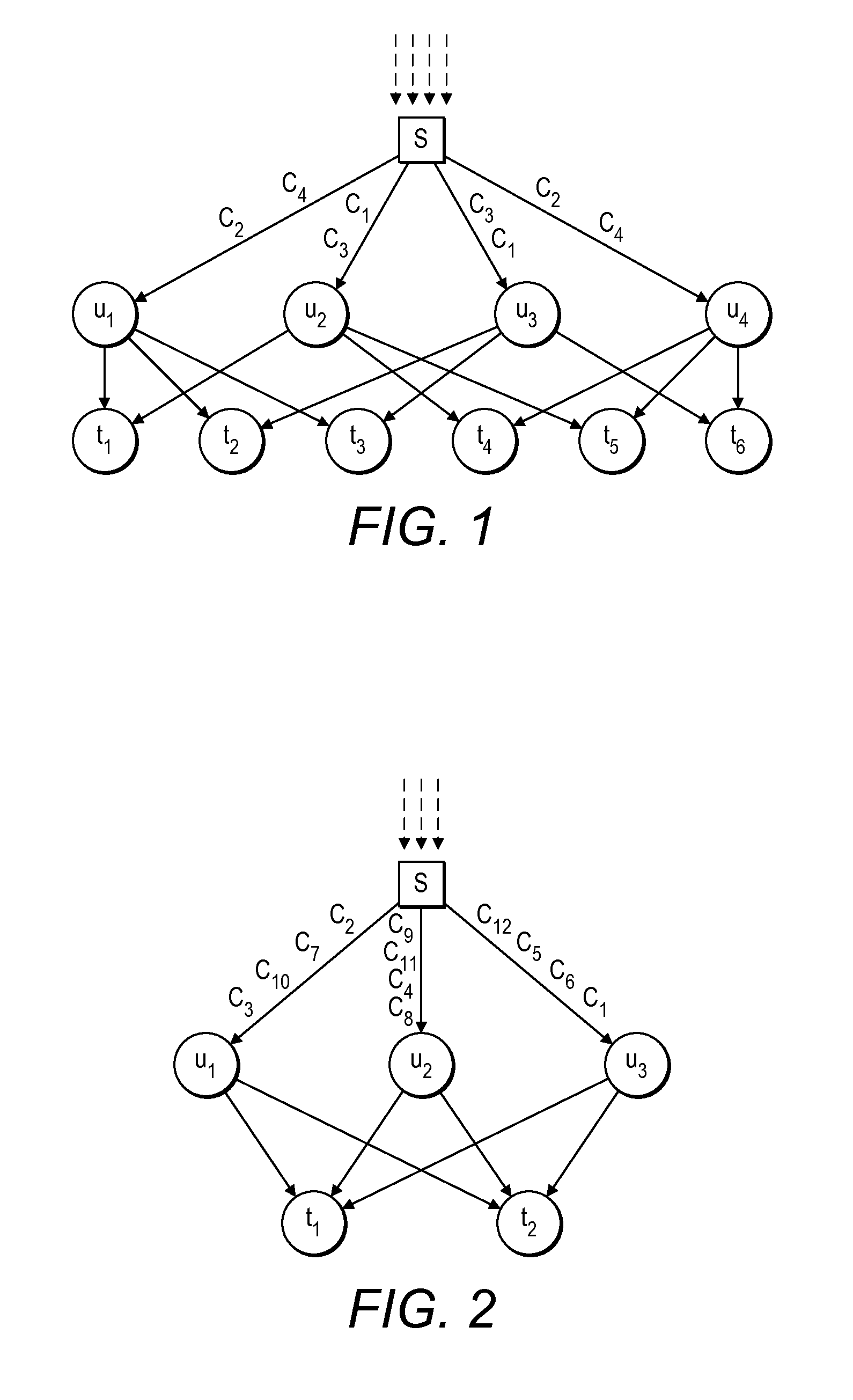
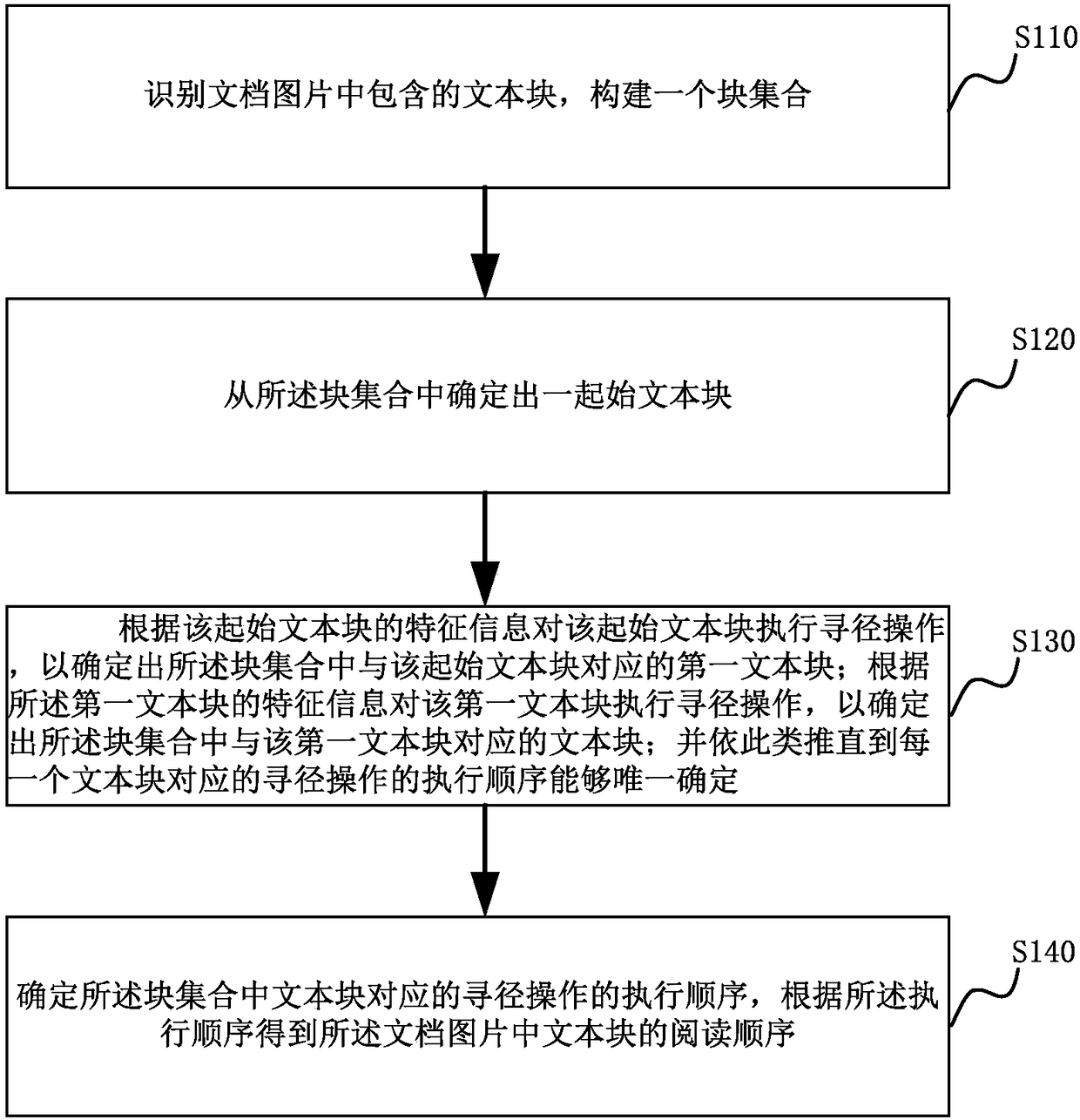
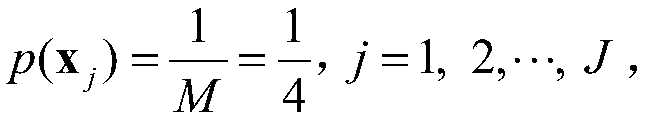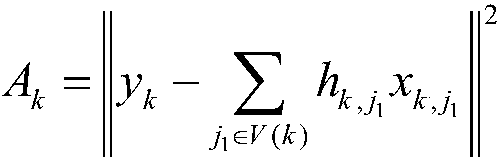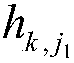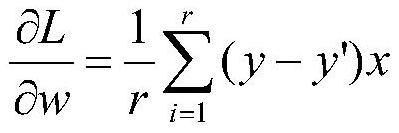Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
69 results about "Theoretical computer science" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Theoretical computer science (TCS) is a subset of general computer science and mathematics that focuses on more mathematical topics of computing and includes the theory of computation. It is difficult to circumscribe the theoretical areas precisely.
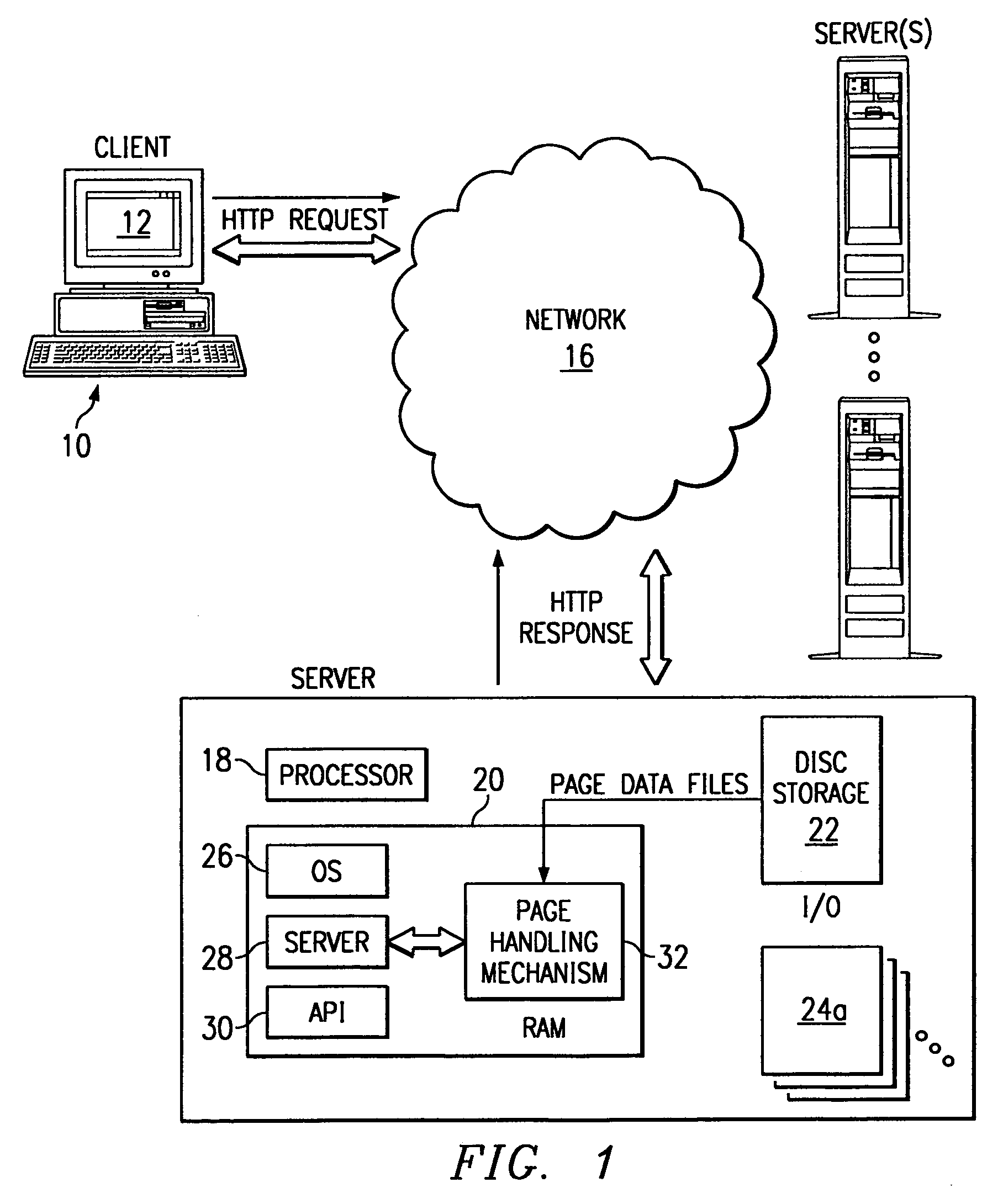
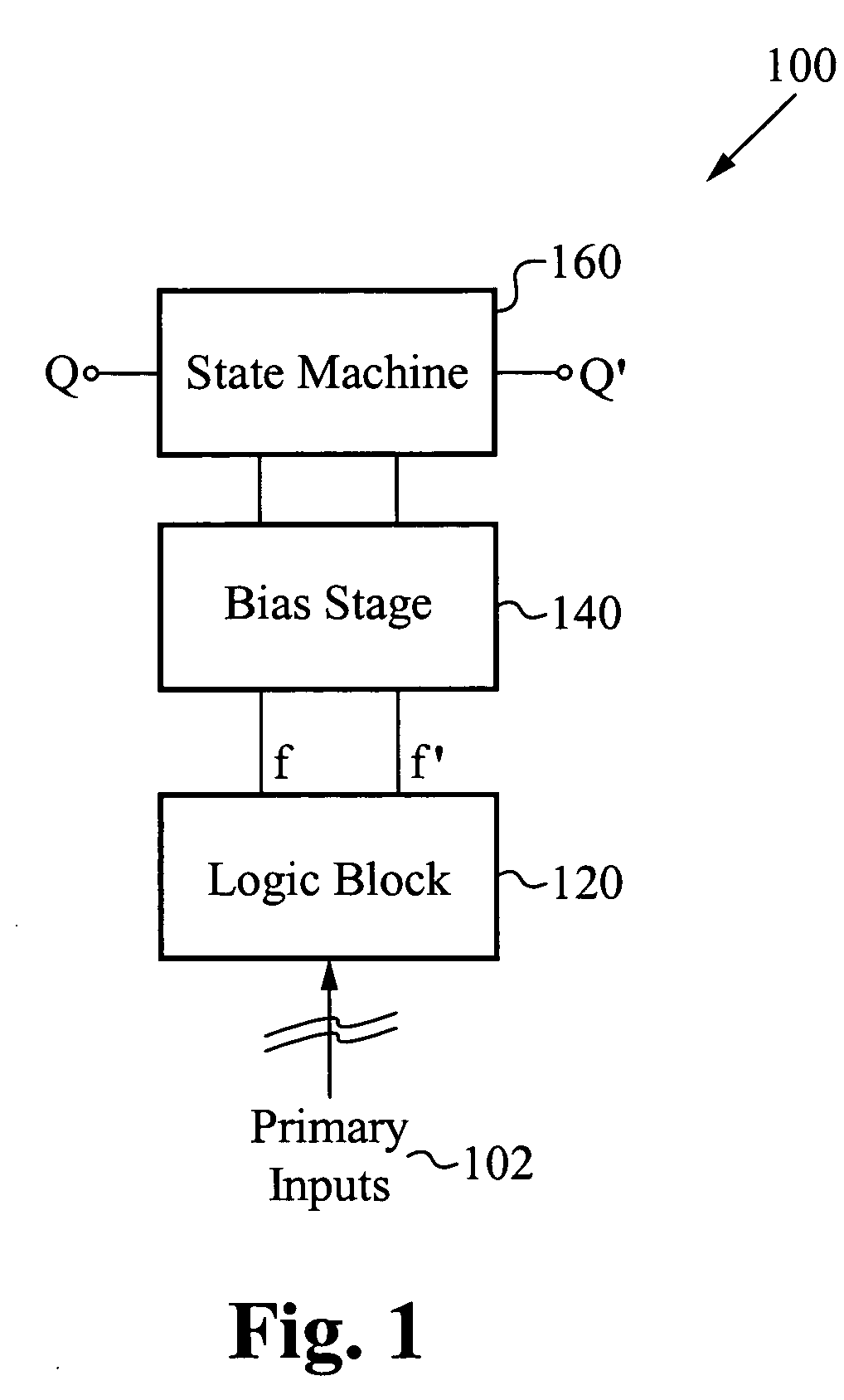
Systems and methods for searching of storage data with reduced bandwidth requirements
InactiveUS20060059207A1Amount of data can be transmittedReduce the amount requiredDigital data information retrievalError detection/correctionTheoretical computer scienceLinearity
Owner:IBM CORP
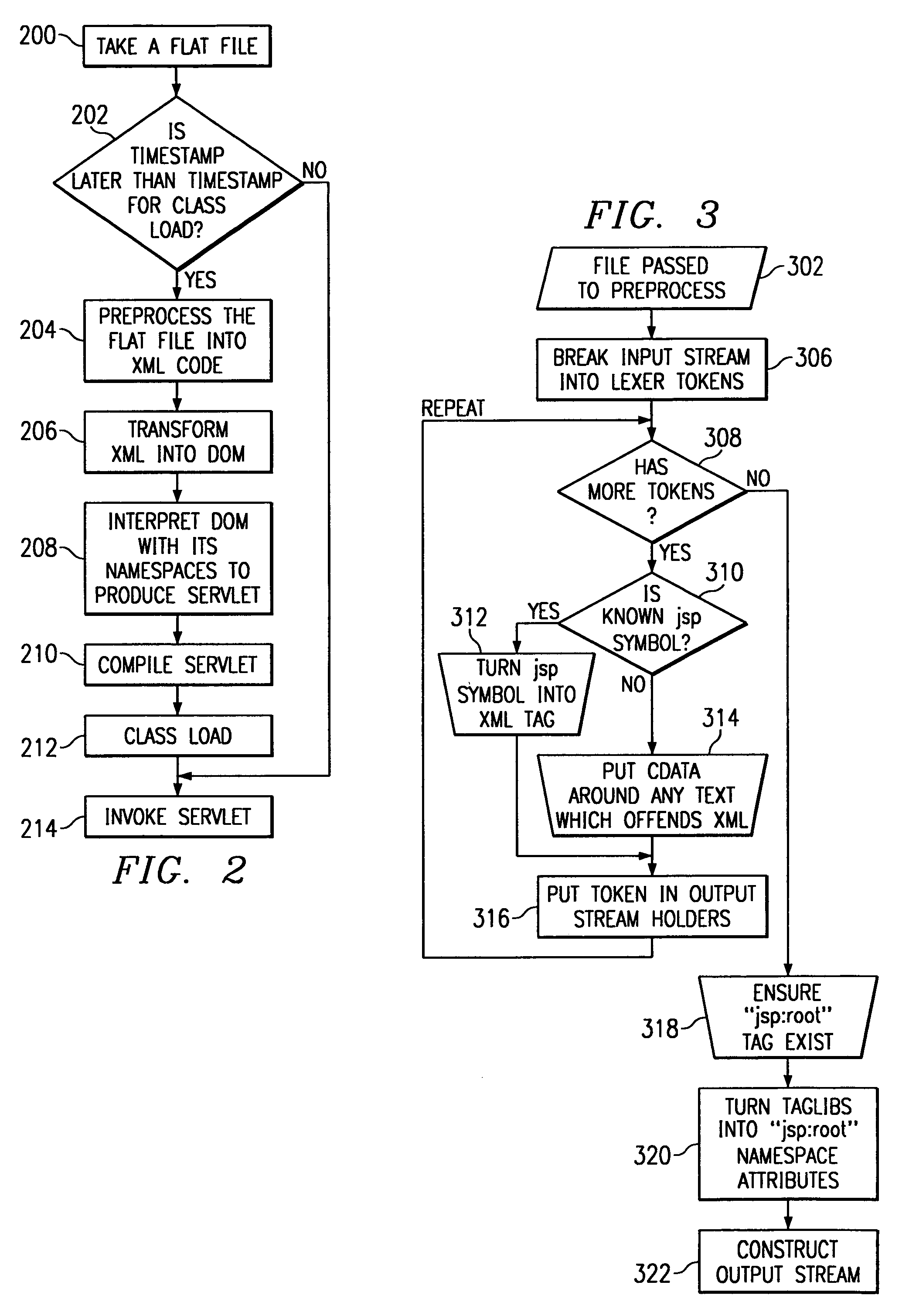
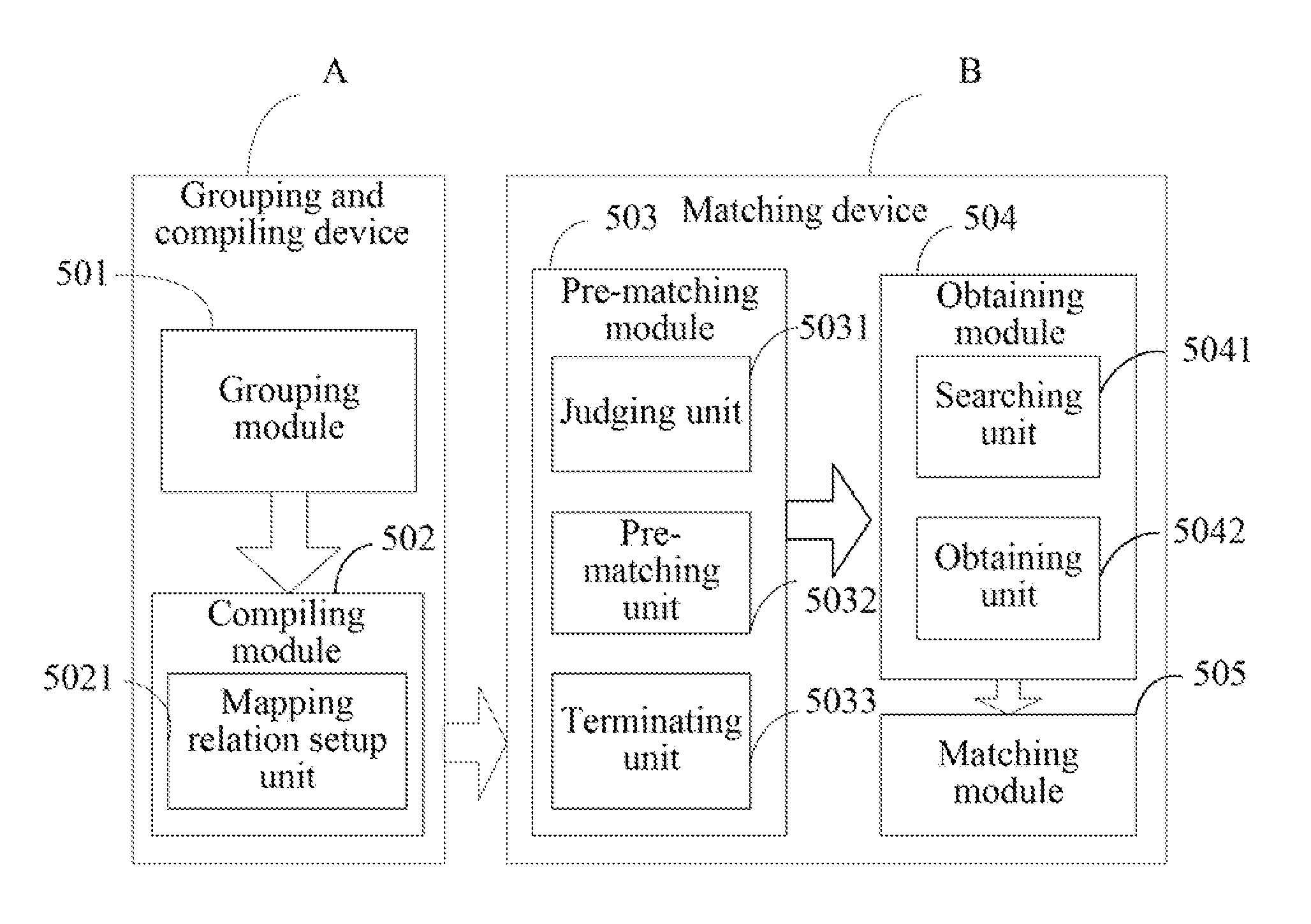
Method for processing a document object model (DOM) tree using a tagbean
InactiveUS6981211B1Easy to replaceDigital computer detailsSemi-structured data mapping/conversionComponent Object ModelTheoretical computer science
Owner:IBM CORP
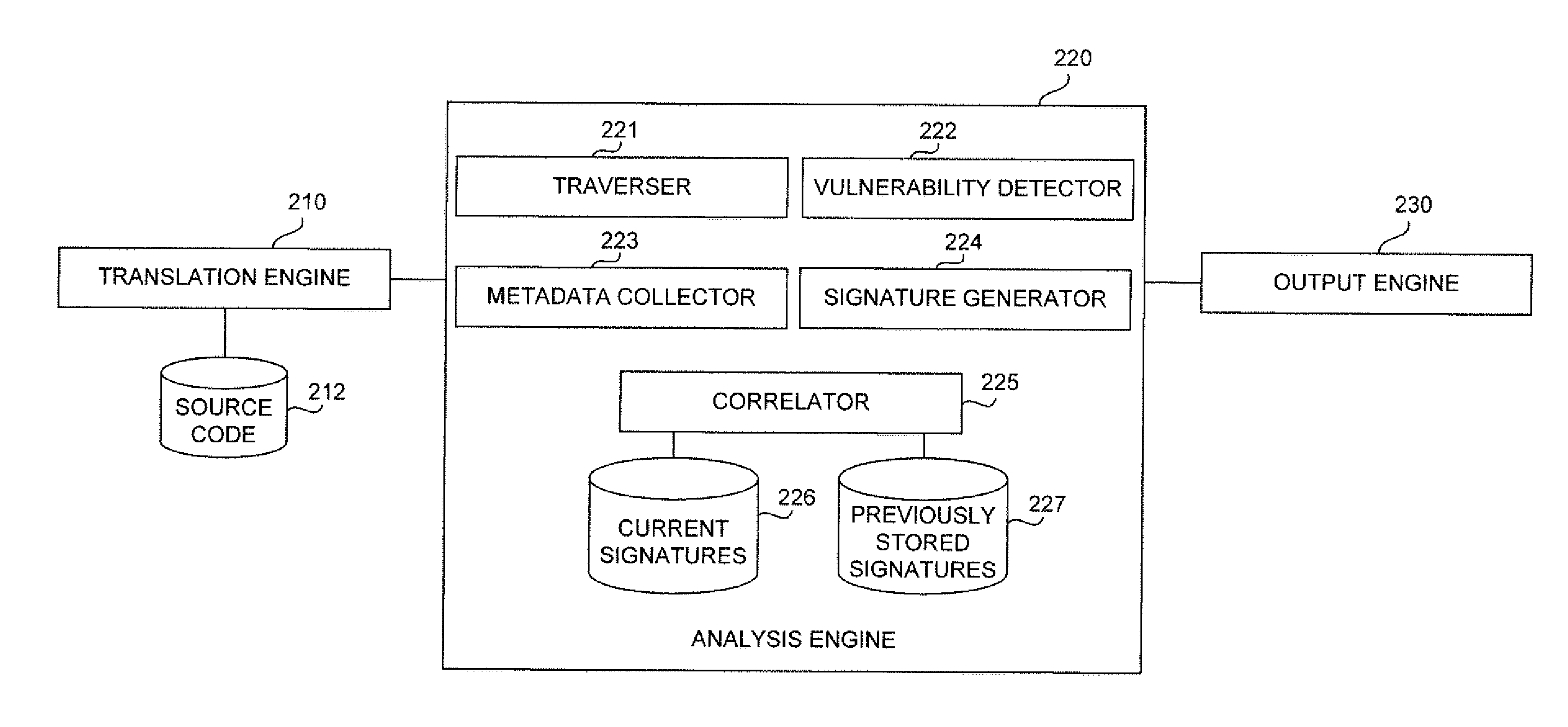
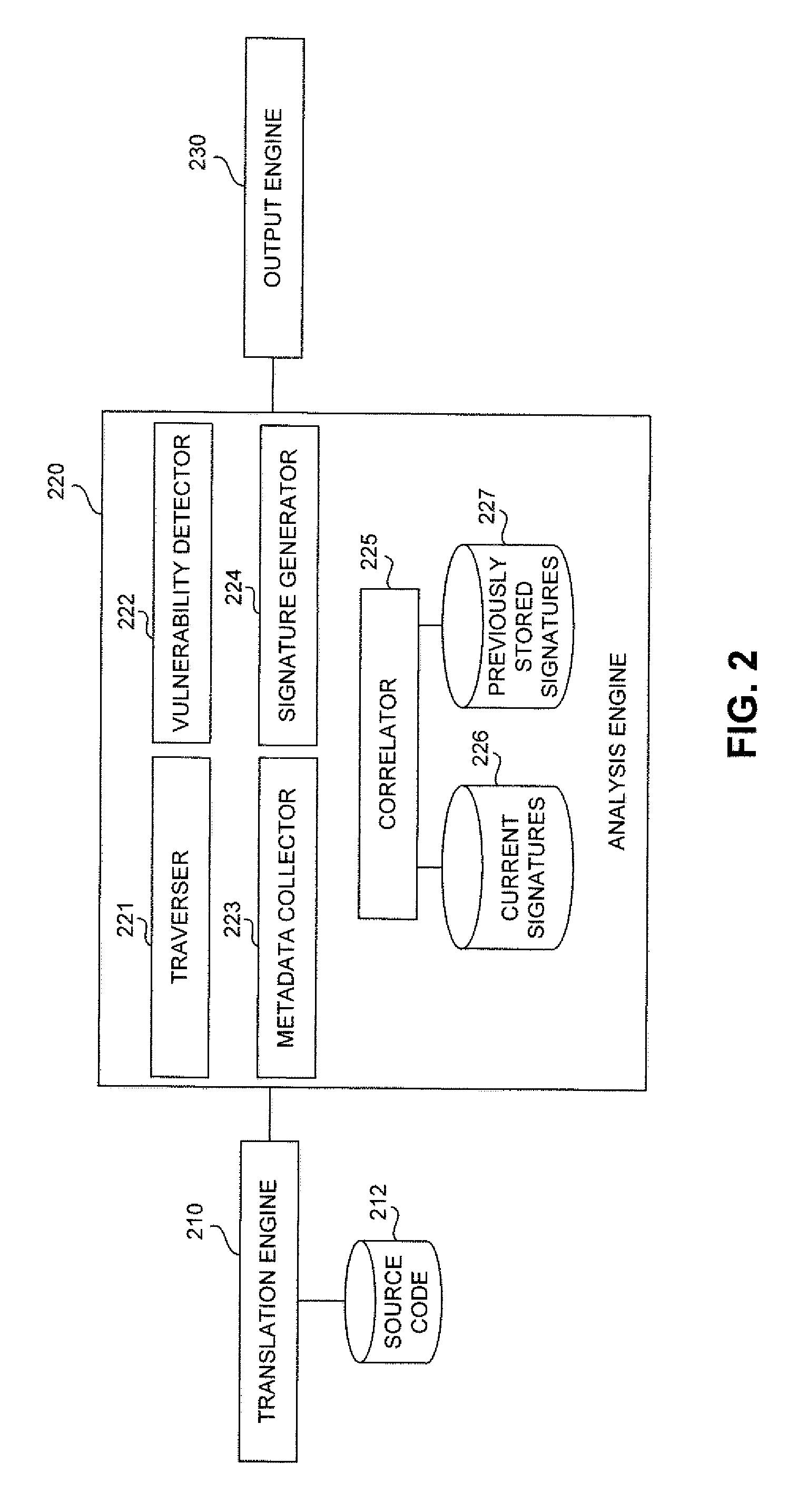
Techniques for correlating vulnerabilities across an evolving codebase
ActiveUS20140283081A1Memory loss protectionError detection/correctionCodebaseTheoretical computer science
Owner:SYNOPSYS INC
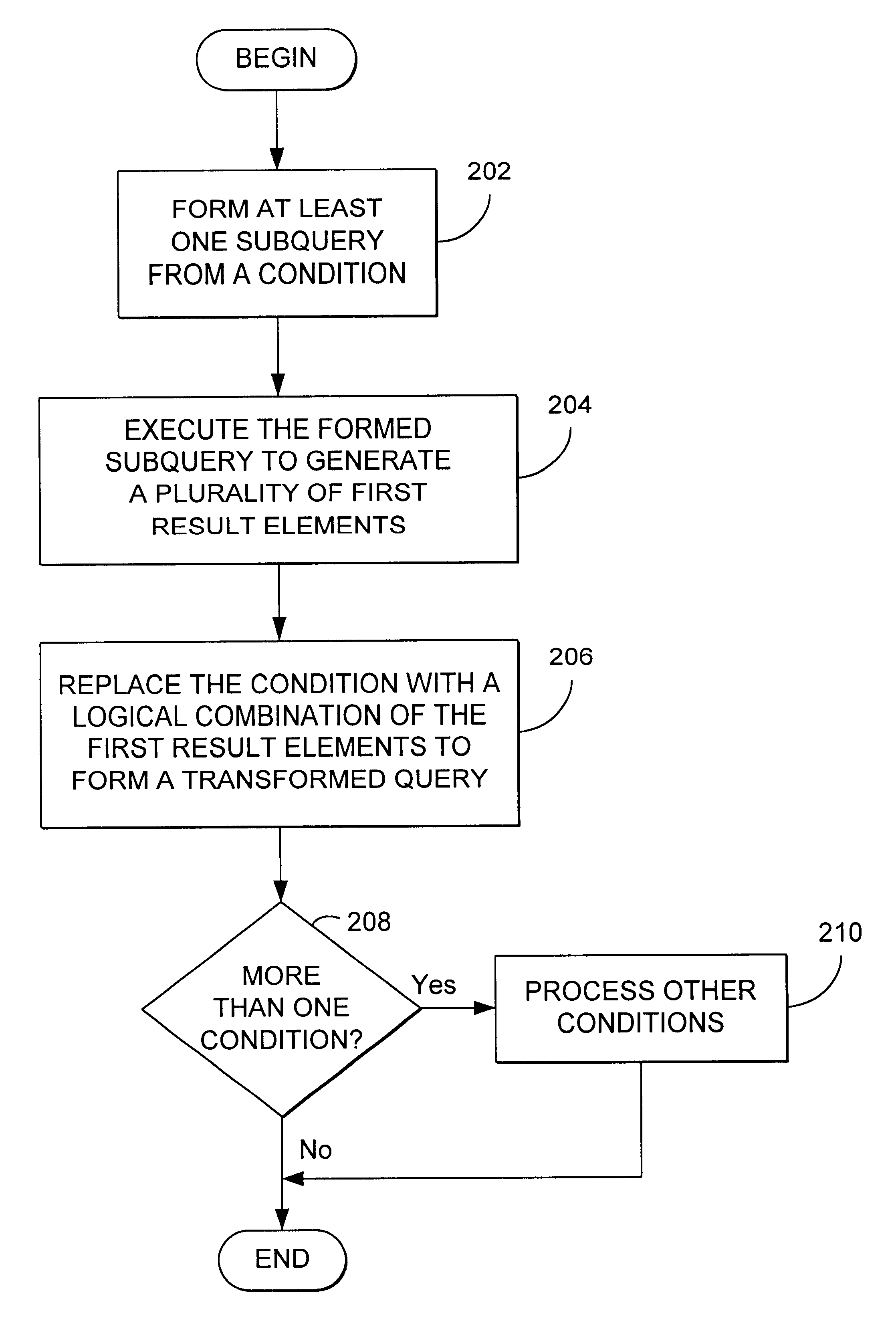
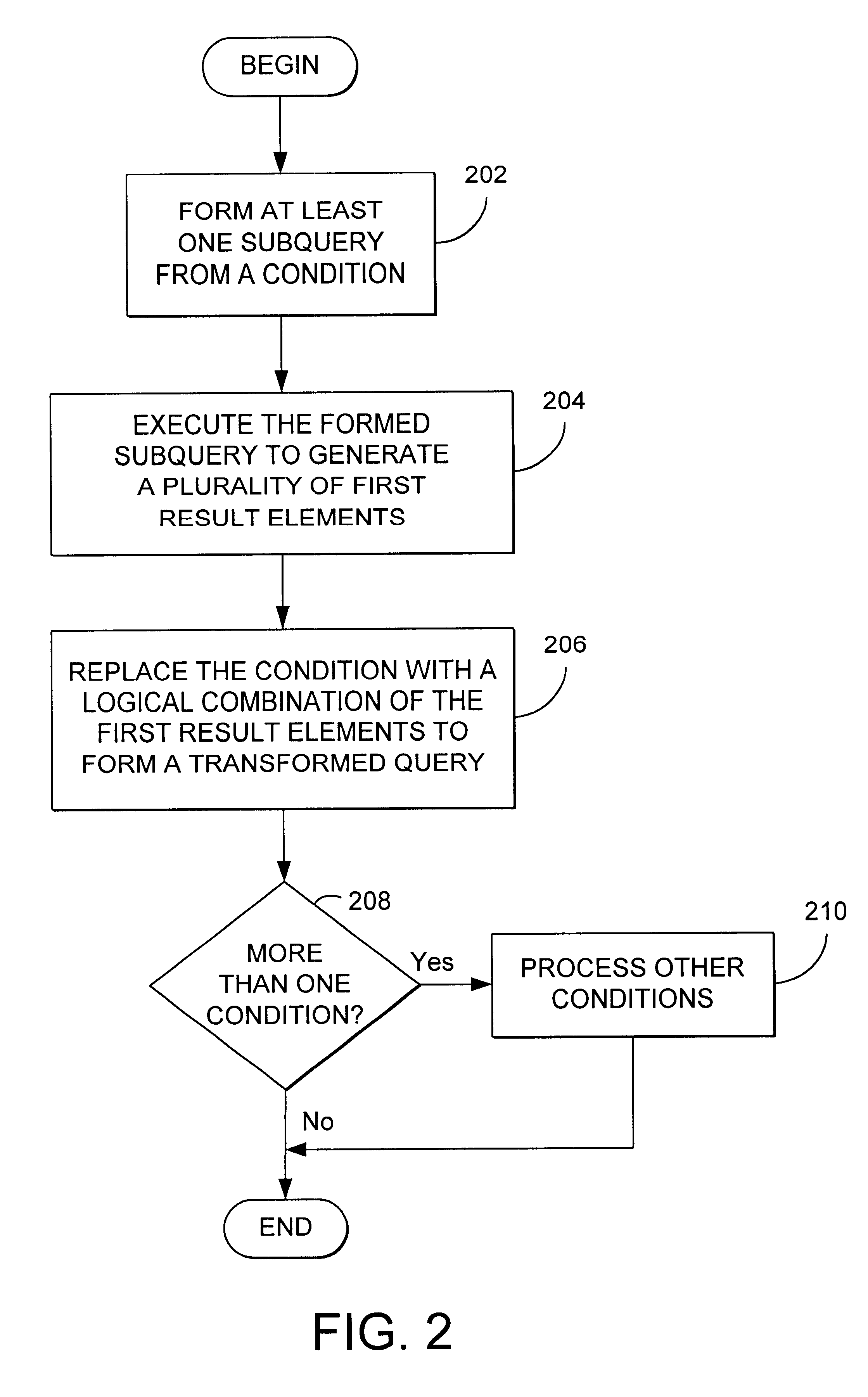
Method and apparatus for transforming queries
InactiveUS6345271B1Reduce needDigital data information retrievalData processing applicationsLogical combinationTheoretical computer science
Owner:IBM CORP
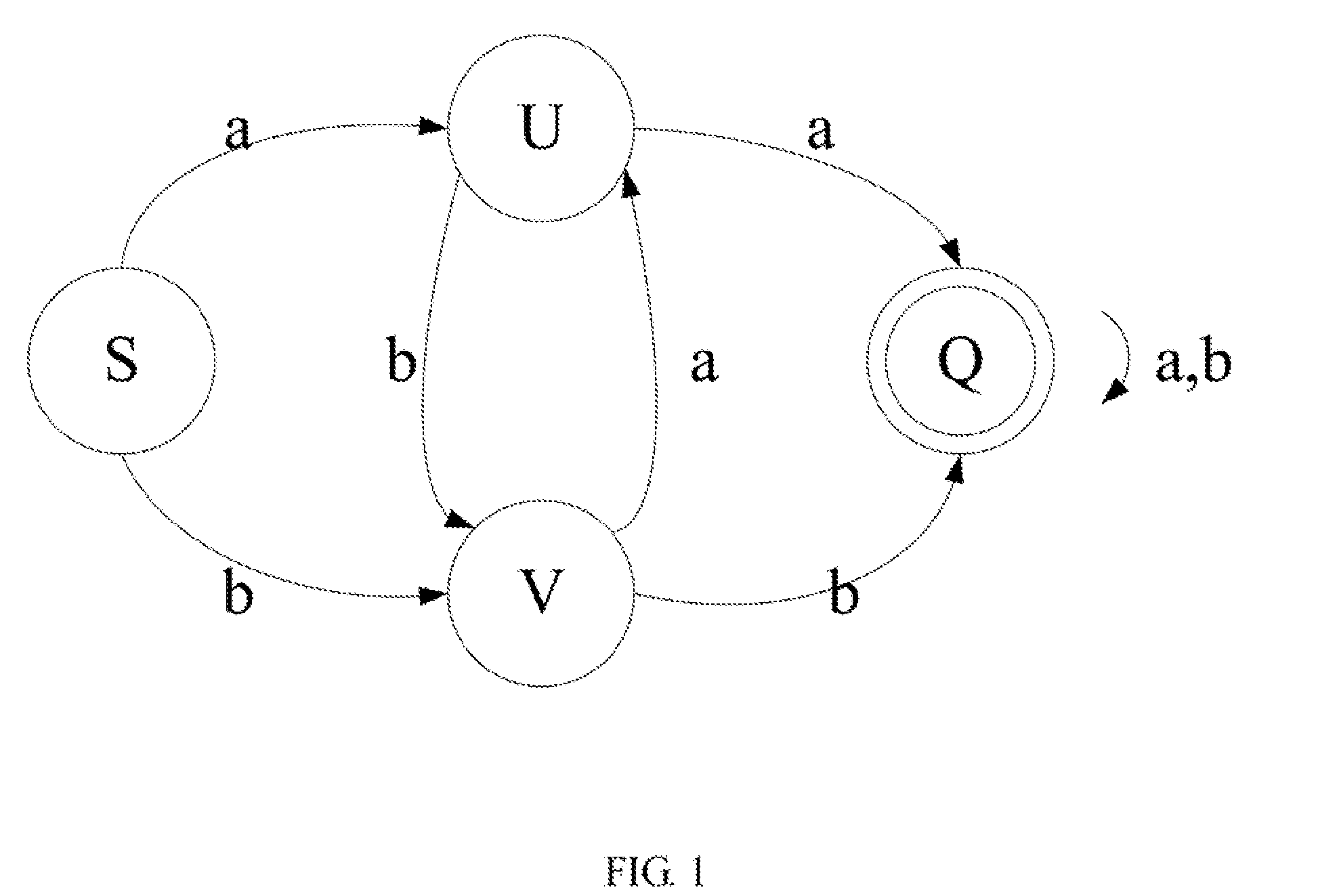
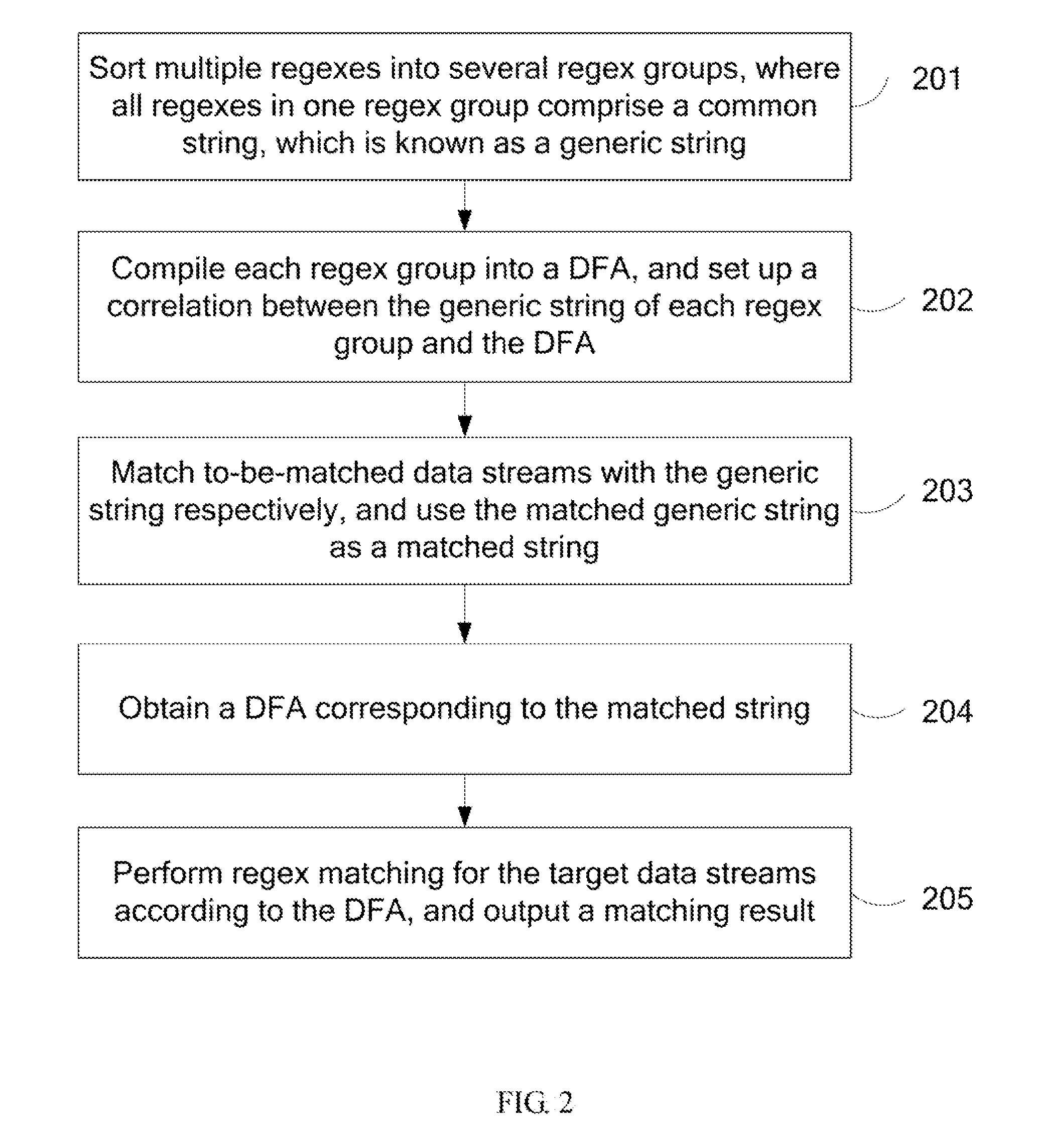
Regular expression matching method and system
ActiveUS20110295779A1Reduce dataReduce load on processDigital data information retrievalDigital computer detailsData streamTheoretical computer science
Owner:HUAWEI TECH CO LTD
Efficient Pipelined Binary Search
InactiveUS20130124491A1Digital data information retrievalDigital data processing detailsTheoretical computer scienceComparator
An apparatus and machine readable storage medium for performing a binary search of an ordered list containing 2N values, where N is an integer greater than one. The apparatus may include a pipeline having N stages numbered 1 to N in sequence. Stage M of the pipeline, where M is in integer from 1 to N, may include a memory storing 2M-1 values from the ordered list, a comparator to compare the key to a value read from the memory based on comparison results from previous stages in the pipeline, and a result storage register to store a comparison result from the comparator and the comparison results from the previous stages in the pipeline.
Owner:IXIA
Layout method
InactiveUS20070180364A1Easy to useNatural language data processingSpecial data processing applicationsTheoretical computer scienceDocument preparation
Owner:SEIKO EPSON CORP
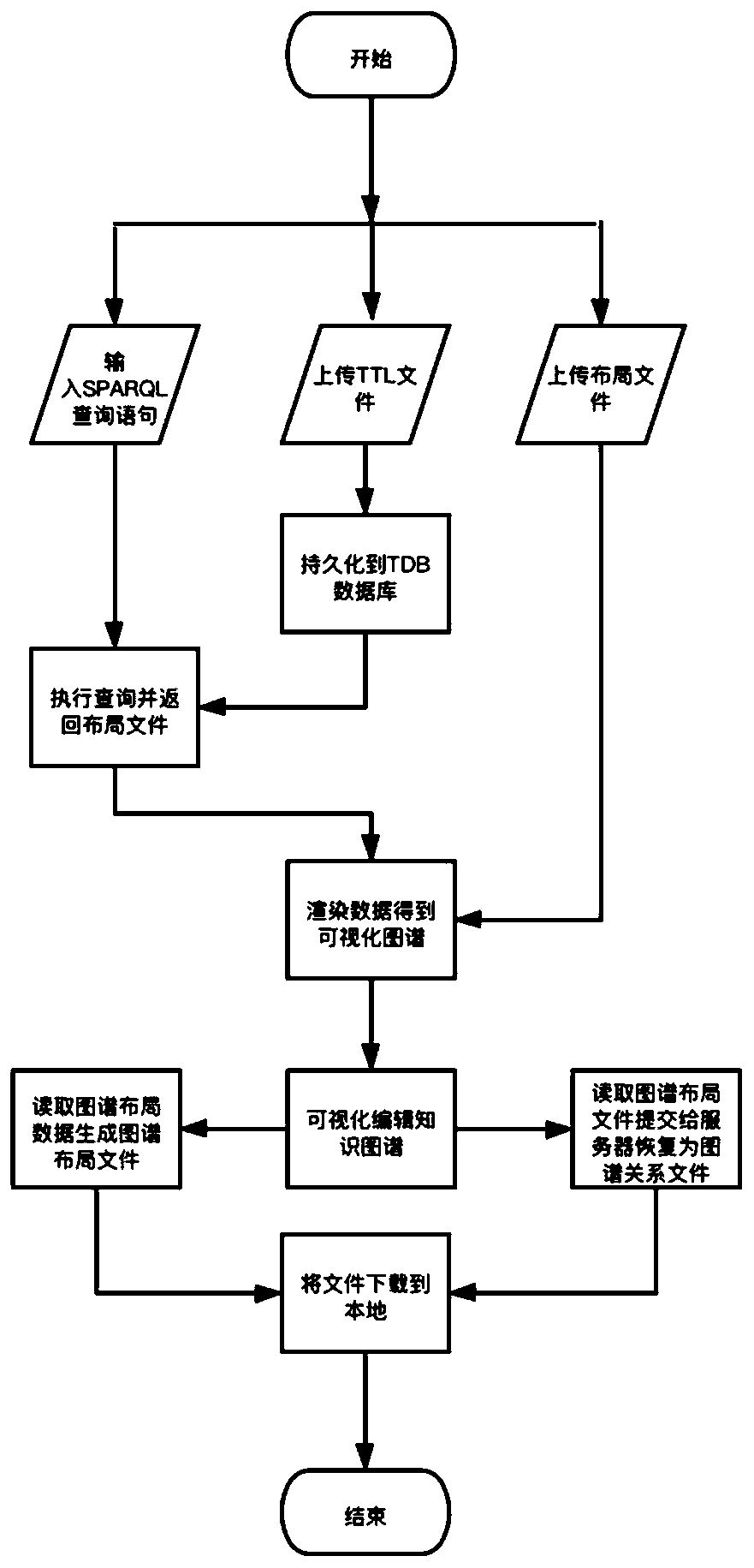
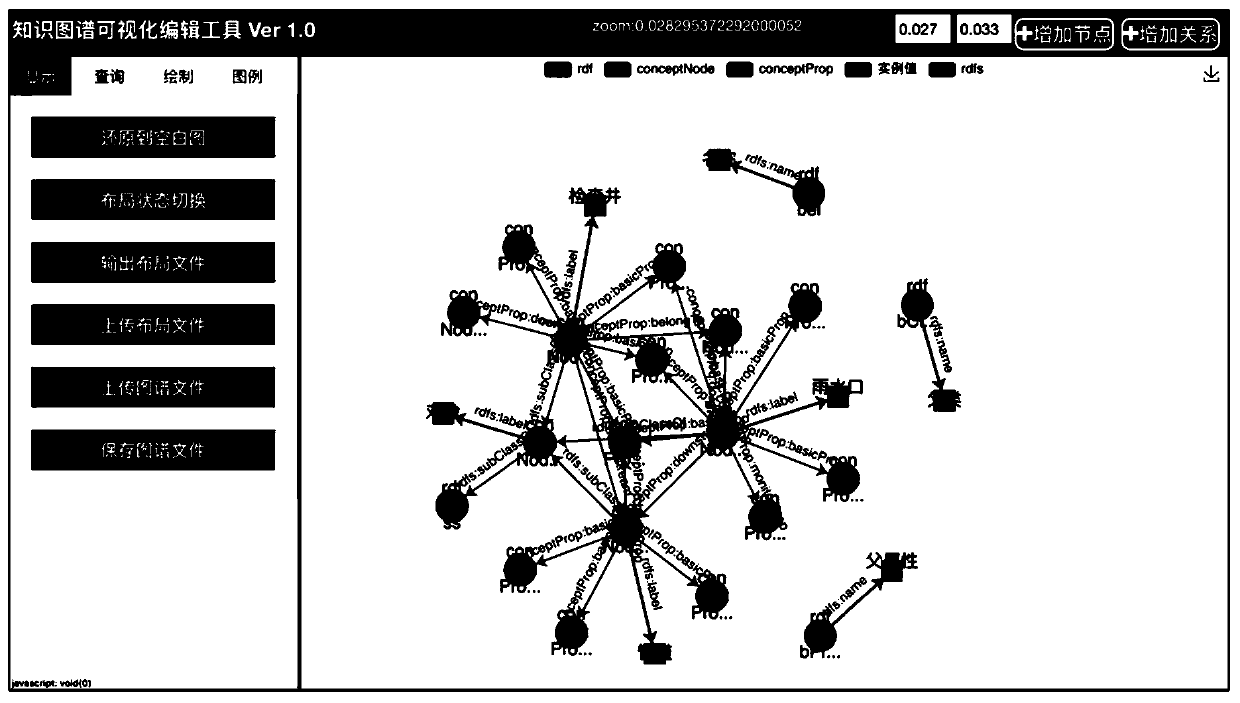
Knowledge graph visual editing and persistence implementation method and system architecture
PendingCN111339316AEasy to storePromote recoverySpecial data processing applicationsText database browsing/visualisationInteractive editingTheoretical computer science
Owner:HOHAI UNIV
Malicious software API call sequence detection method based on graph convolution
ActiveCN111259388AImprove bindingFlexible organizational structurePlatform integrity maintainanceNeural architecturesCall graphAlgorithm
Owner:SUN YAT SEN UNIV
Compile time linking via hashing technique
InactiveUS20060130020A1Simple processRapid techniqueLink editingProgram controlAddress resolutionMachine code
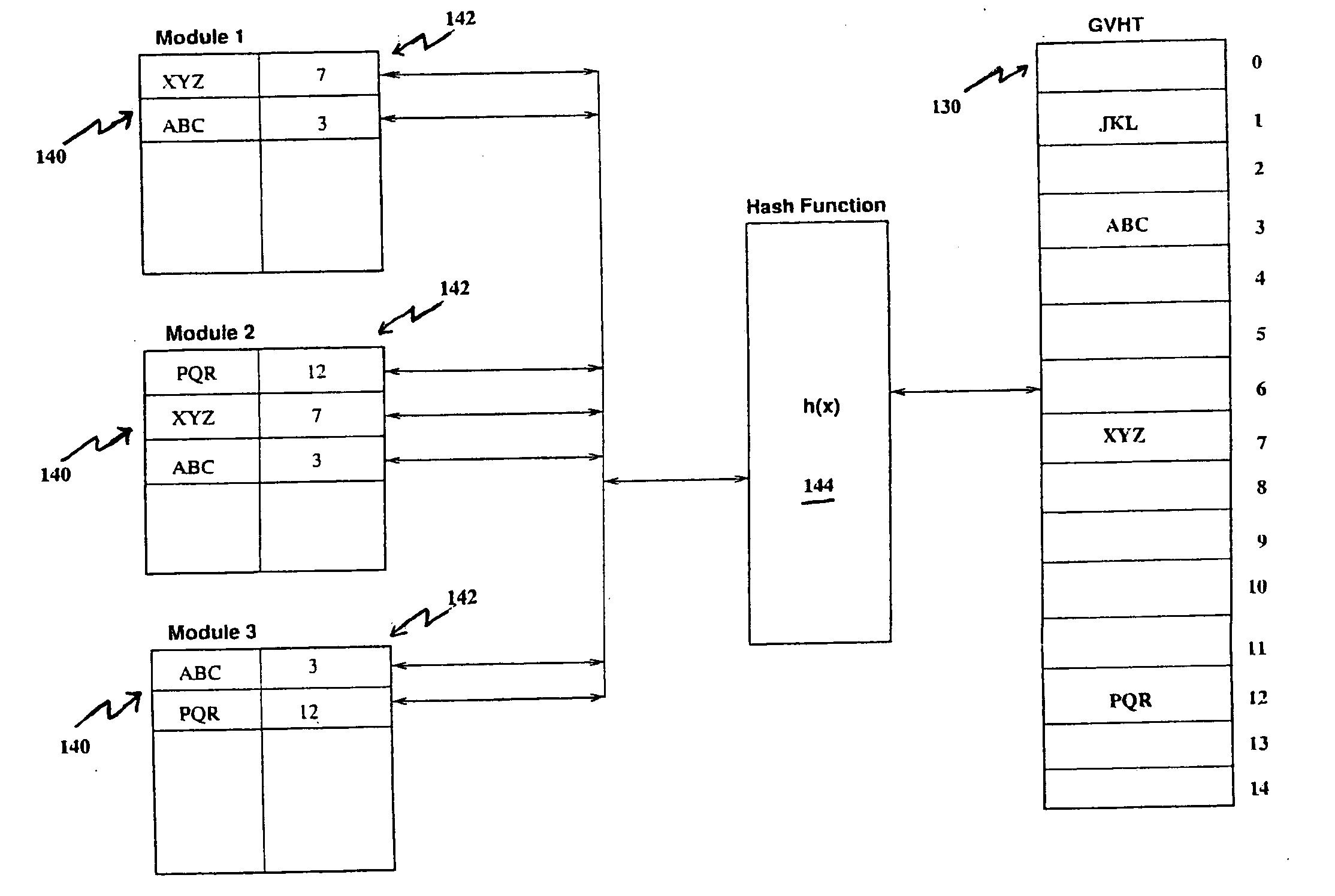
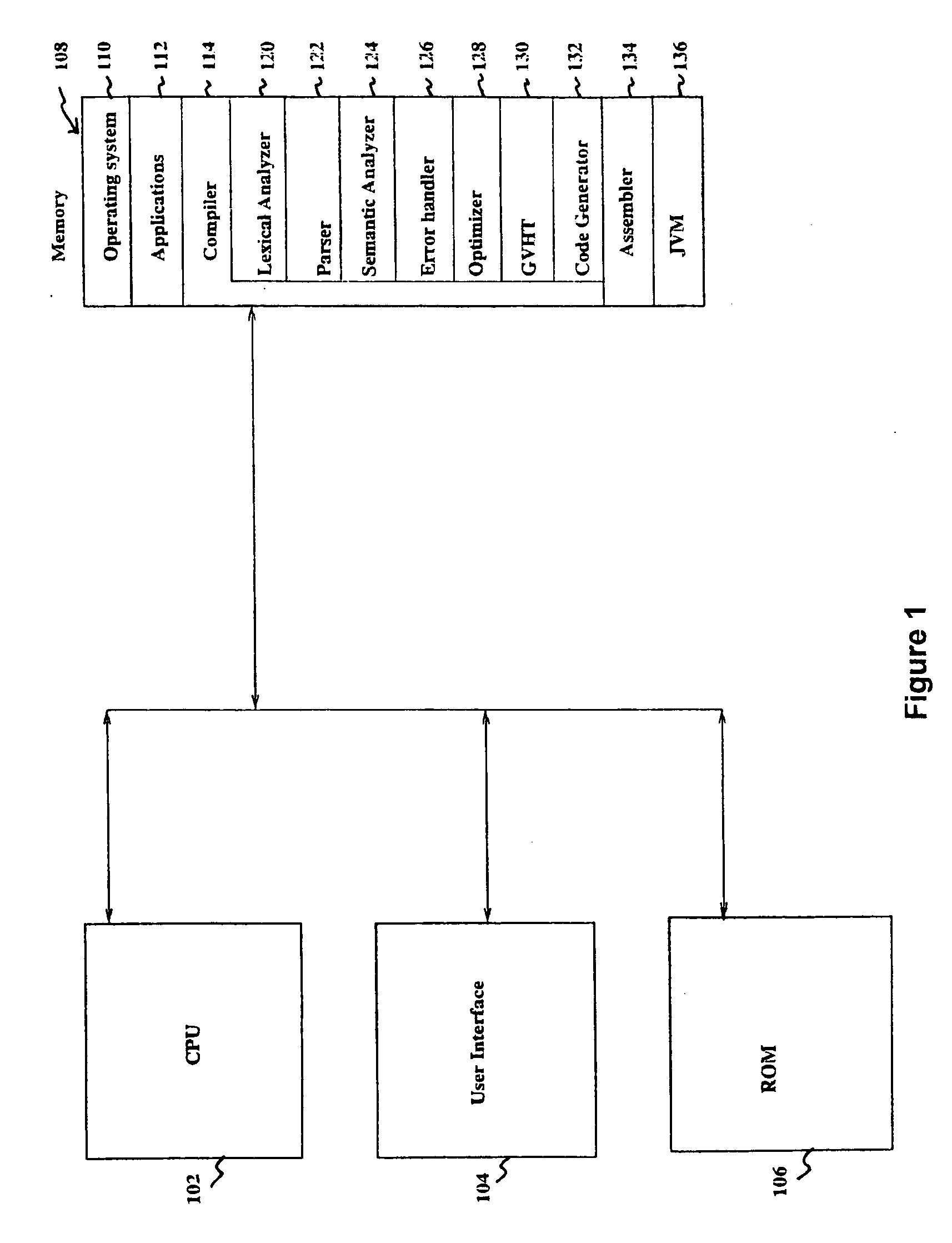
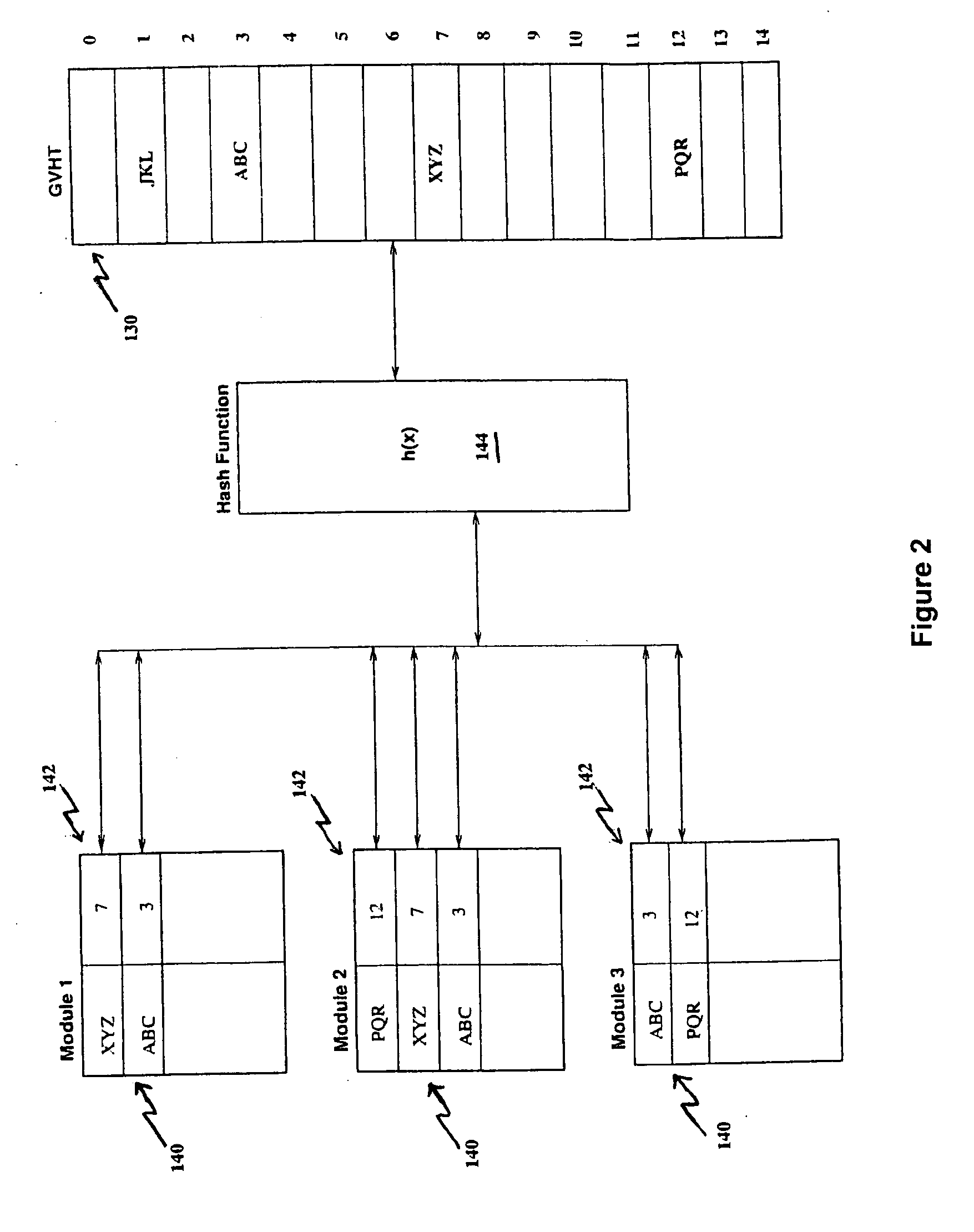
A linker is usually used, in post processing of compiling high-level languages such as C into machine executable language, to bind separately compiled object files and resolve the addresses (142) of global variables (140) declared in the separate files. The invention proposes linking during compile time by using a special purpose hash table called global variables hash table (130) shared among the separate files. This results in a collection of processed object files that are coherent in terms of their addresses (142) for global variables (140) that could be further assembled correctly into machine executable code. This method is useful for compiling separate high level language source files to generate executable machine code employing a technique of address resolution across separate modules.
Owner:AXIOMATIC SOLUTIONS
Method and Apparatus for Generation of a Sequence of Elements
InactiveUS20080208775A1Minimum delayThe process is fast and efficientElectronic editing digitised analogue information signalsDigital computer detailsTheoretical computer scienceAlgorithm
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Radiation tolerant combinational logic cell
InactiveUS20070109865A1Increase energy levelReduce sensitivityRead-only memoriesDigital storageCMOSData set
Owner:IDAHO UNIV OF +1
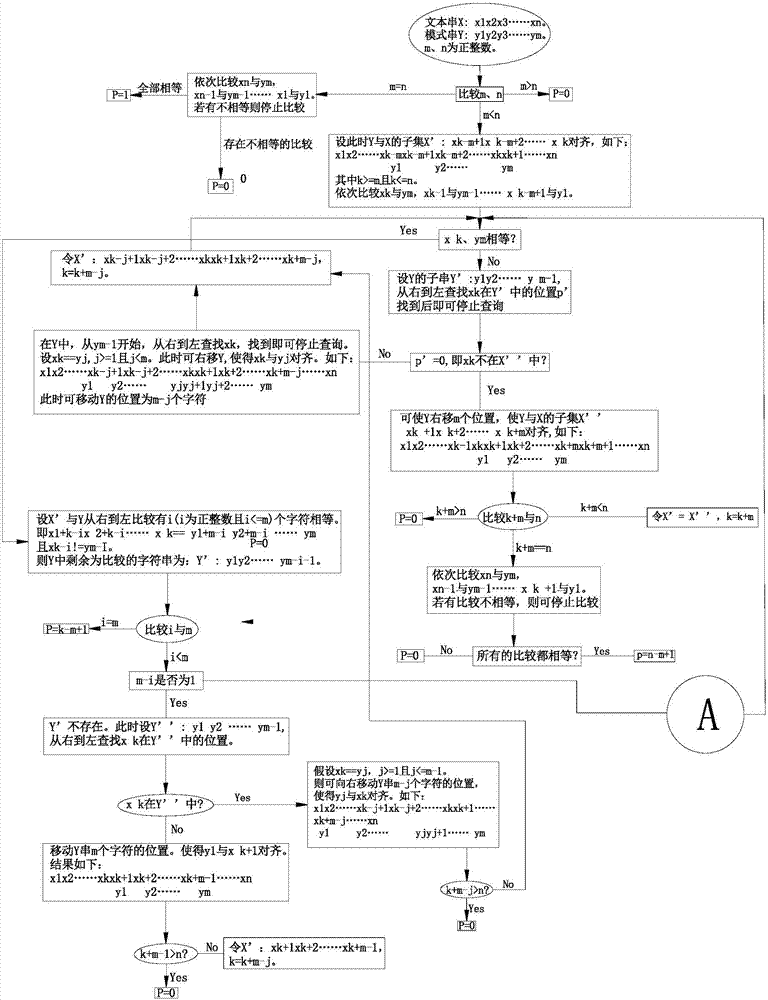
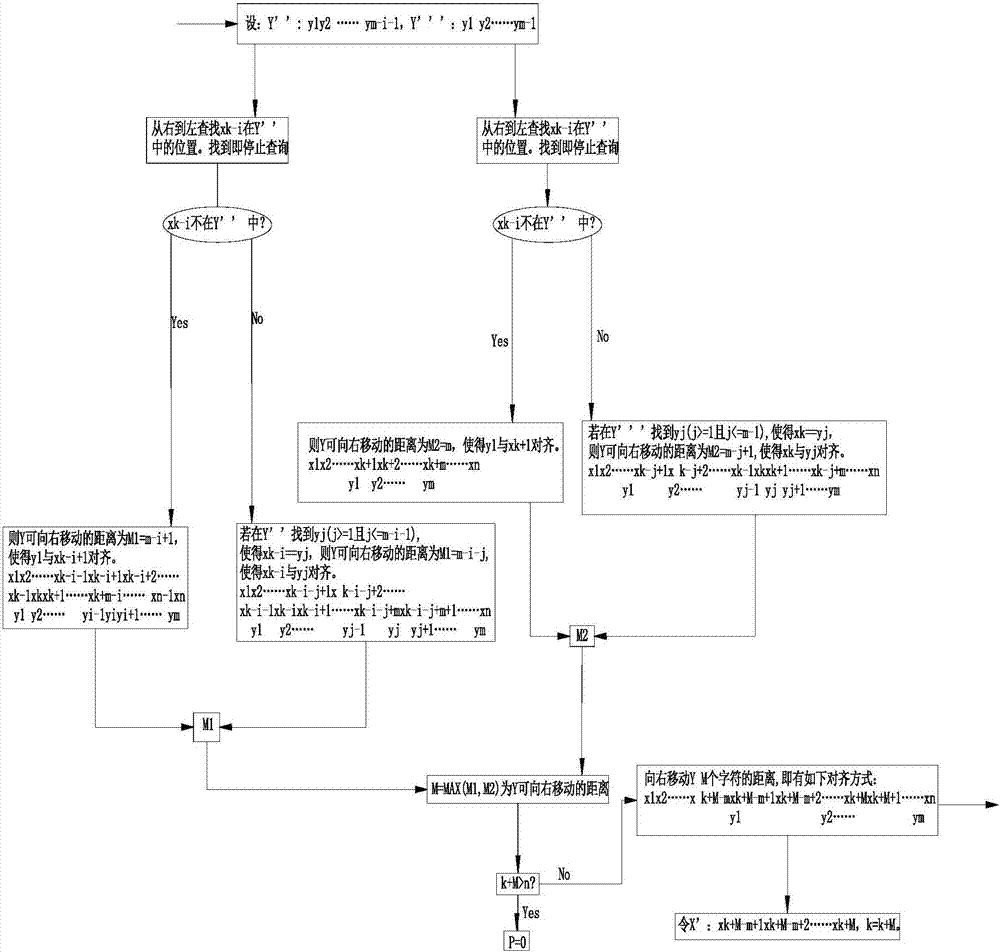
Method for matching character string patterns
ActiveCN107229759AText database queryingSpecial data processing applicationsTheoretical computer scienceAlgorithm
Owner:深圳市乐宜科技有限公司
A sparse code division multiple access signal detection method based on depth neural network
ActiveCN109039534APerformance advantageReduce computing pressureError preventionNeural architecturesAlgorithmCode division multiple access
Owner:SOUTHEAST UNIV
Network coding over gf(2)
InactiveUS20160373210A1Improve efficiencyImprove securityCode conversionCoding detailsComputer networkAlgorithm
Owner:MEMOSCALE AS
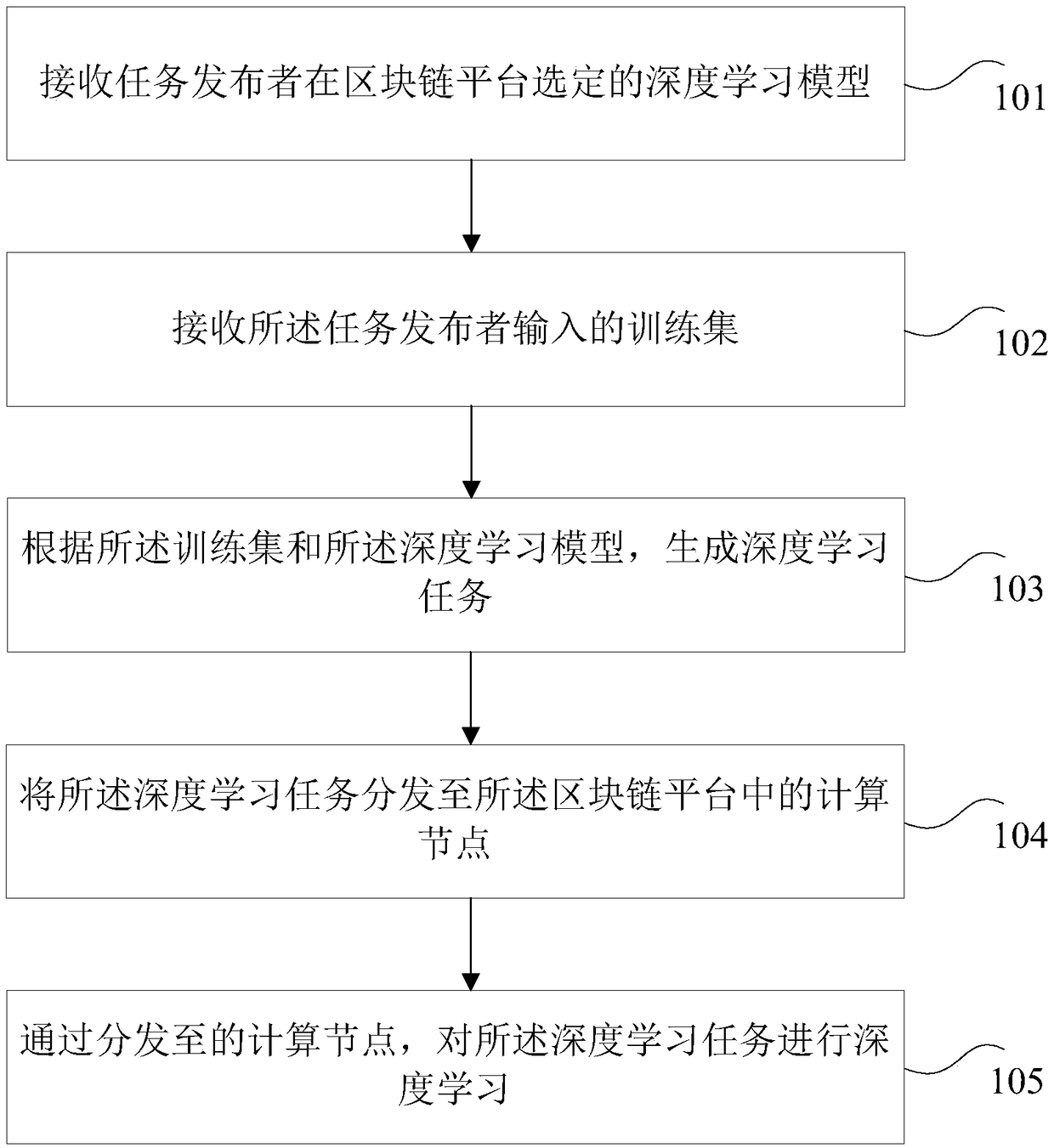
Depth learning method base on block chain platform, electronic device
PendingCN109409738ASolve the costSolve efficiency problemsResourcesTransmissionTheoretical computer scienceLearning methods
Owner:PING AN TECH (SHENZHEN) CO LTD
System and method for executing hybridized code on a dynamically configurable hardware environment
InactiveUS7032103B2Software engineeringGeneral purpose stored program computerMultiple contextTheoretical computer science
A system and method for executing previously created run time executables in a configurable processing element array is disclosed. In one embodiment, this system and method begins by identifying at least one subset of program code. The method may then generate at least one set of configuration memory contexts that replaces each of the at least one subsets of program code, the at least one set of configuration memory contexts emulating the at least one subset of program code. The method may then manipulate the at least one set of multiple context processing elements using the at least one set of configuration memory contexts. The method may then execute the plurality of threads of program code using the at least one set of multiple context processing elements.
Owner:QUALCOMM INC
Data formats and usage for massive point-to-point route calculation
InactiveUS7050904B2Instruments for road network navigationRoad vehicles traffic controlTheoretical computer scienceData format
The invention is directed to a method by which optimal paths are found between one or more start destinations and one or more end destinations. First destination and travel data is converted into a node and edge data format, wherein the nodes represent start points and the the edges have a weight related to a travel weight. These nodes and edges are subdivided into subsets. The paths between the start nodes and each of the end nodes are determined using the node and edge representations stored in the subsets. A selected union of subsets is determined that contains the start end end destinations. The optimal paths are determined by using the travel values associated with the edges connecting the nodes. The union of subsets, which may comprise less than the full amount of subsets, is loaded for the path determination. Or, when the path determination perceives that a relevant boundary has been reached in a path determination, that next subset in the union of subsets is loaded. The newly loaded subset is “joined” to the already loaded subsets, thus allowing the completion of the path determination.
Owner:GEOTAB
Method and device for data detection in communication system and computer storage medium
The embodiment of the invention provides a method and device for data detection in a communication system and a computer readable medium. The method described herein includes receiving, at a receivingdevice, a set of reference signal time domain symbols from a target transmitting device, the reference signal having a comb distribution with a spacing factor of N in the frequency domain, N being apositive integer not less than 2; for each reference signal time domain symbol in the set, dividing the reference signal time domain symbol into N parts with repeatability; obtaining channel estimation and estimation of a covariance matrix of interference and noise based on N parts of each reference signal time domain symbol in the set; applying an adjustment factor to the estimate of the covariance matrix to obtain a corrected covariance matrix, the adjustment factor being associated with a spacing factor N; and performing data detection based on the channel estimation and the corrected covariance matrix. By utilizing the embodiment of the invention, the performance of data detection can be improved.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD +1
Method and device for protecting derived symbol in so file
InactiveCN105447349AAchieve protectionImprove securityProgram/content distribution protectionAlgorithmTheoretical computer science
Owner:ZHUHAI DUOWAN INFORMATION TECH CO LTD
Multi keyword matching method for rapid content analysis
InactiveCN1508721AEasy to handleError detection/correctionUnauthorized memory use protectionAlgorithmTheoretical computer science
The invention is a kind of multi-keyword matching method of quick content analysis, which comprises following steps: 1) carries on pretreatment to the keywords; 2) creates the Huffman code of each character according to the occurrence frequency of each keyword, then codes each keyword into an integer; 3) creates a test table with all keywords; 4) scans the text; 5) uses the test table to carry on text content analysis. It can carry on dynamic adjustment according to the occurrence frequency of each word in keyword, thus enhances the matching speed of multi-keyword. The character lies in: it designs the multi-keyword matching algorithm based on Huffman code against large quantity of short keywords.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
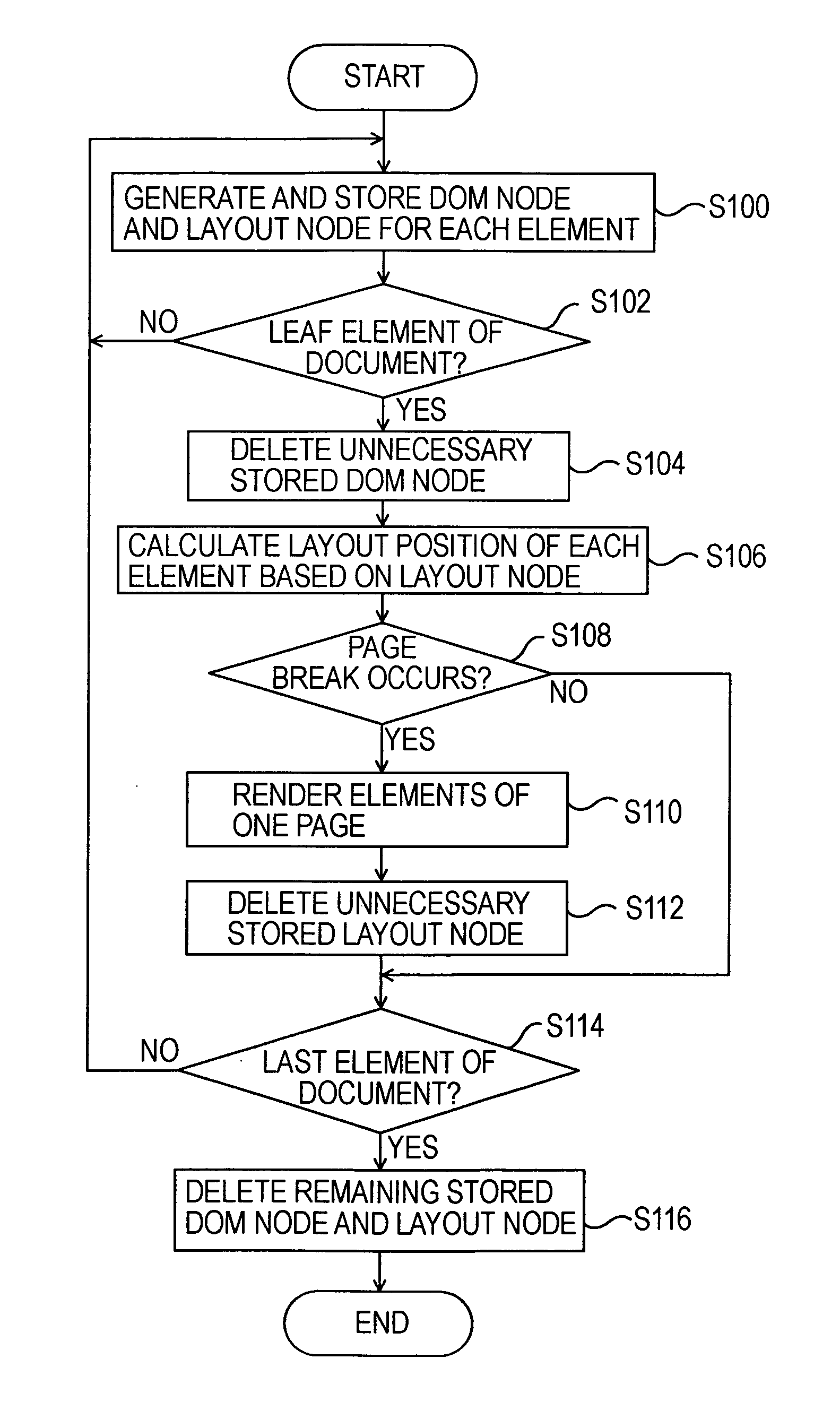
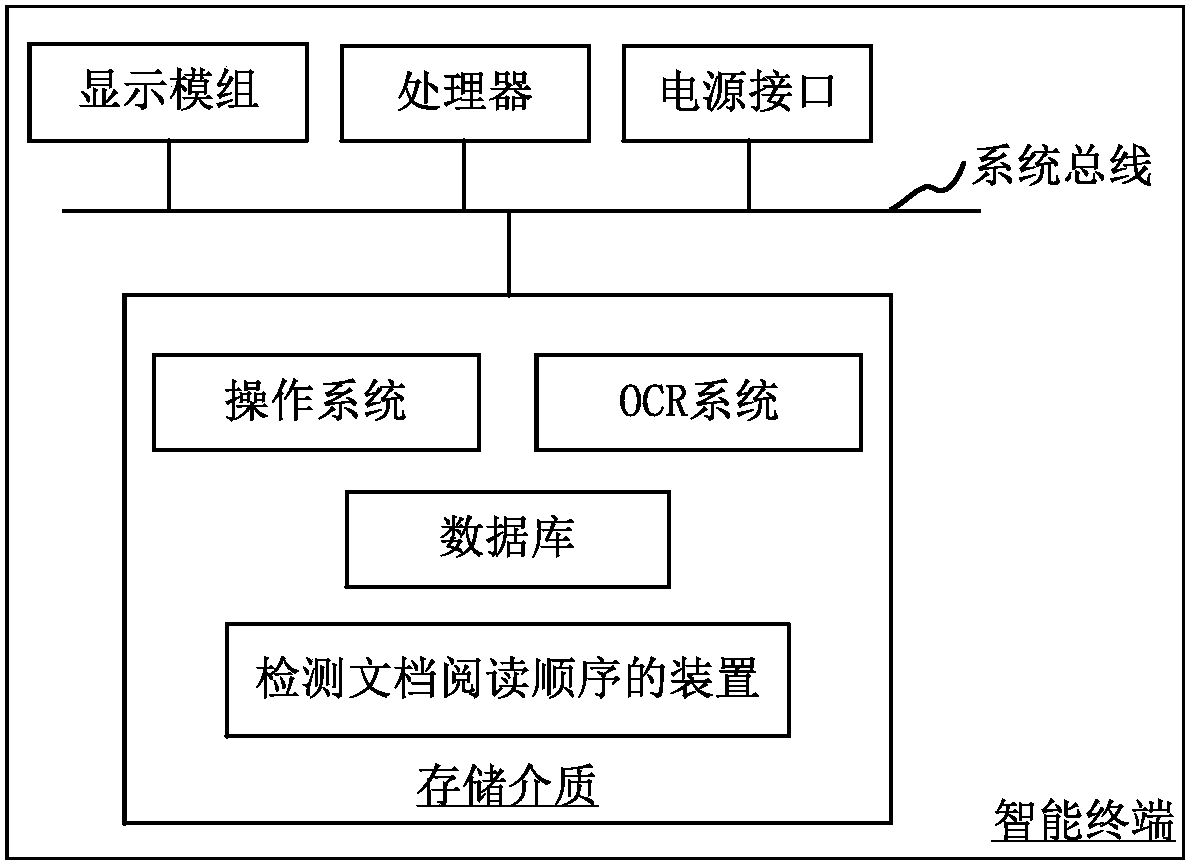
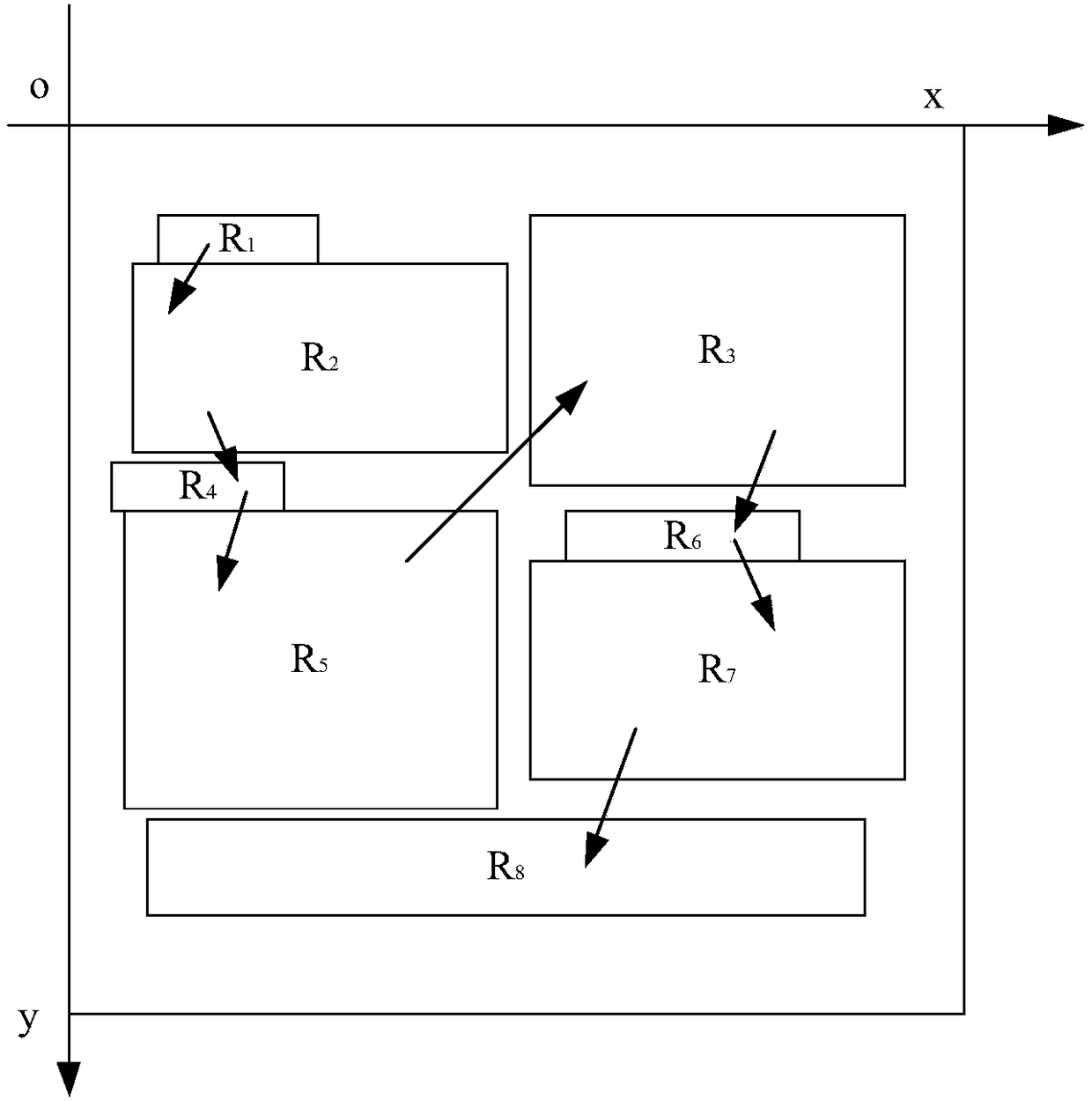
Method and apparatus for detecting reading order of document
Owner:TENCENT TECH (SHENZHEN) CO LTD
Program execution device and electronic apparatus
InactiveUS20080189507A1Short processing timeShort timeRuntime instruction translationMemory adressing/allocation/relocationTheoretical computer scienceLookup table
A program execution device includes: a lookup table storage section that stores a lookup table stipulating a plurality of relations between a plurality of input data and a plurality of output data that are results of operation conducted on the plurality of input data; a program storage section that stores a program including a command directing to obtain one of the output data that is a result of the operation conducted on one of the input data, which is defined by the one of the input data and the operation; and a program execution section having a first cycle of designating the one of the input data in the command to the lookup table in the lookup table storage section, and a second cycle of receiving the one of the output data corresponding to the one of the input data from the lookup table.
Owner:SEIKO EPSON CORP
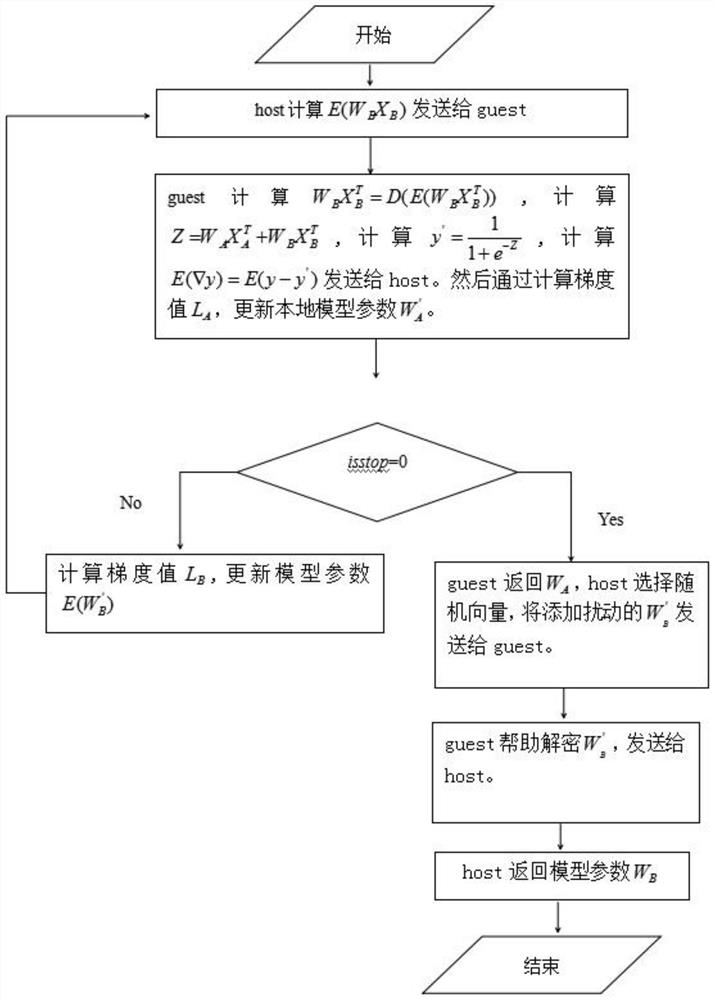
Security federated learning logistic regression algorithm
PendingCN112613618ATraining supportReduce complexityCharacter and pattern recognitionMachine learningAlgorithmTheoretical computer science
Owner:神谱科技(上海)有限公司
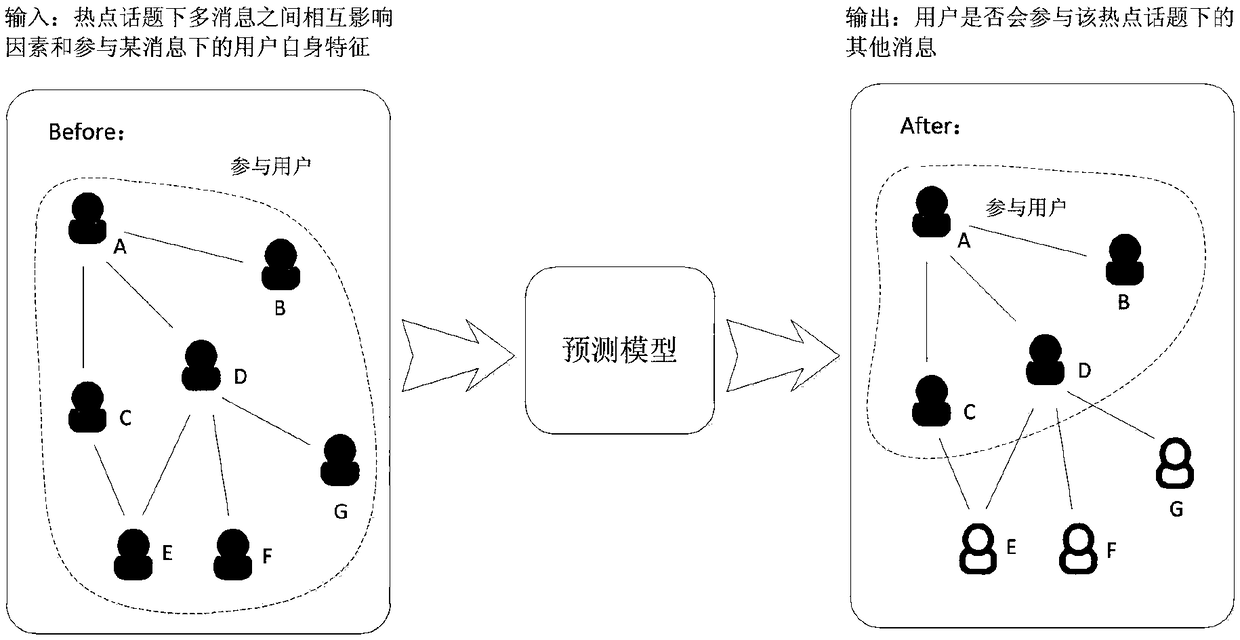
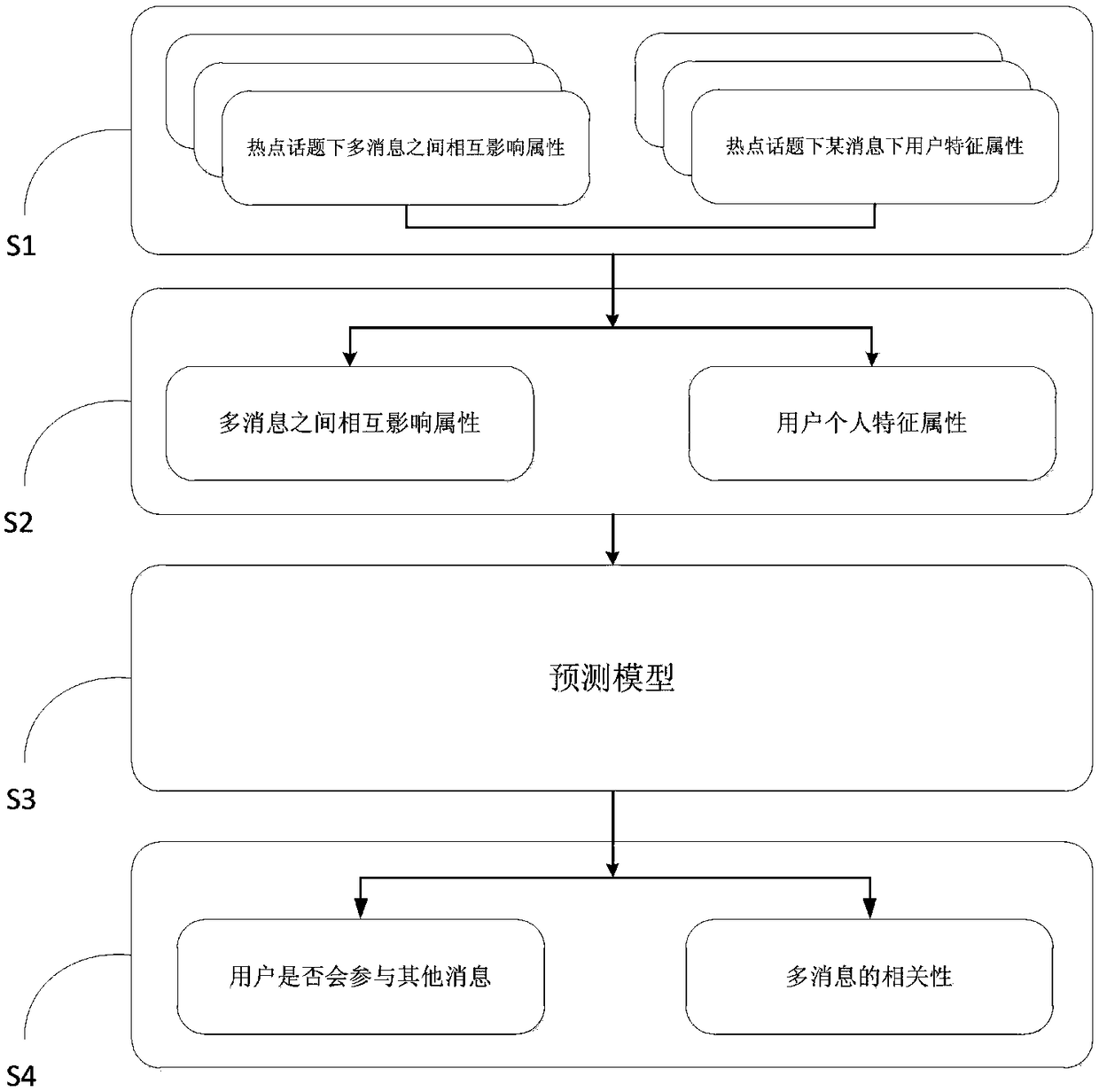
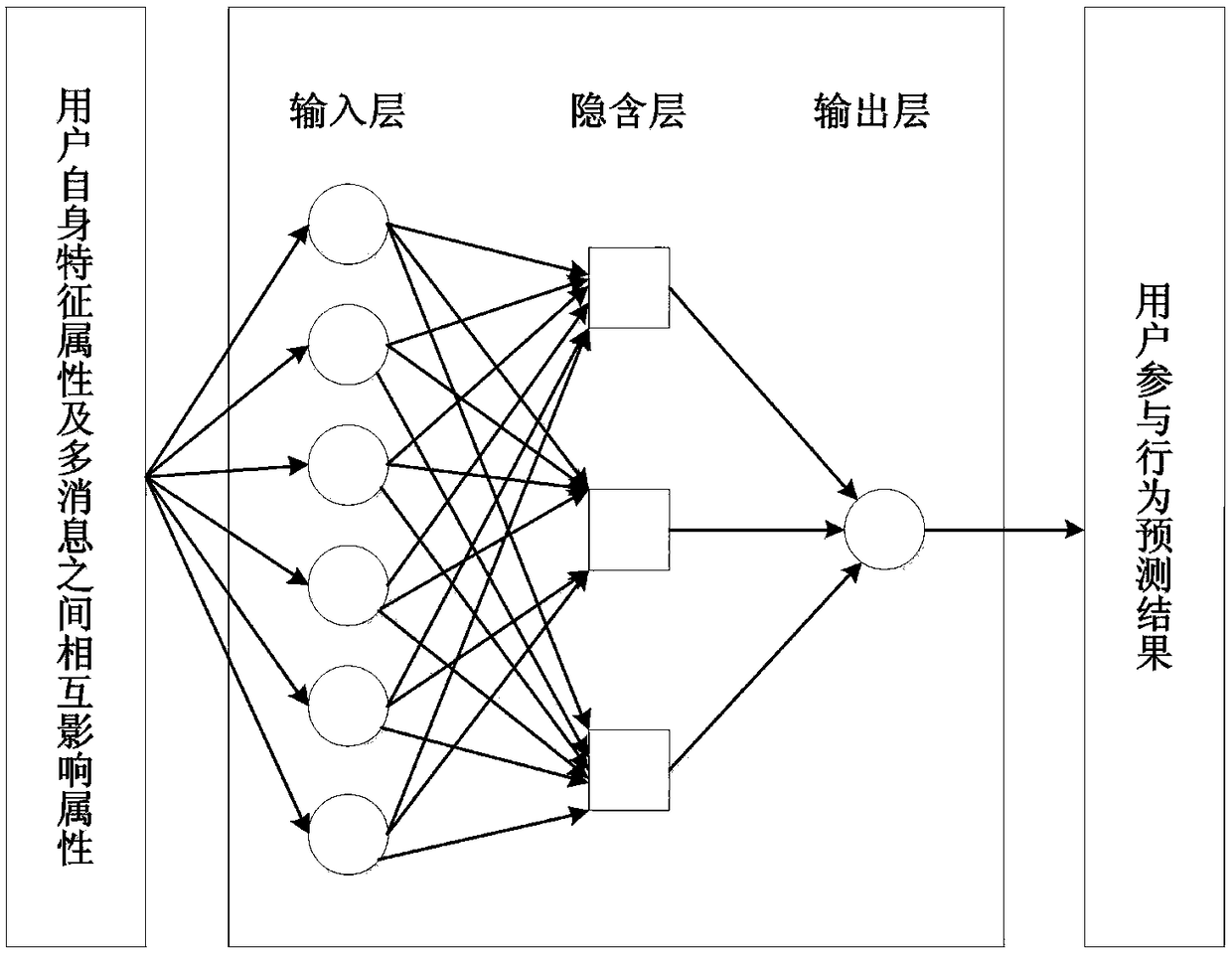
User behavior prediction system and method for multi-message interaction under hot topics
ActiveCN108229731AImprove forecast accuracyForecastingNeural learning methodsTheoretical computer scienceUser participation
Owner:CHONGQING UNIV OF POSTS & TELECOMM
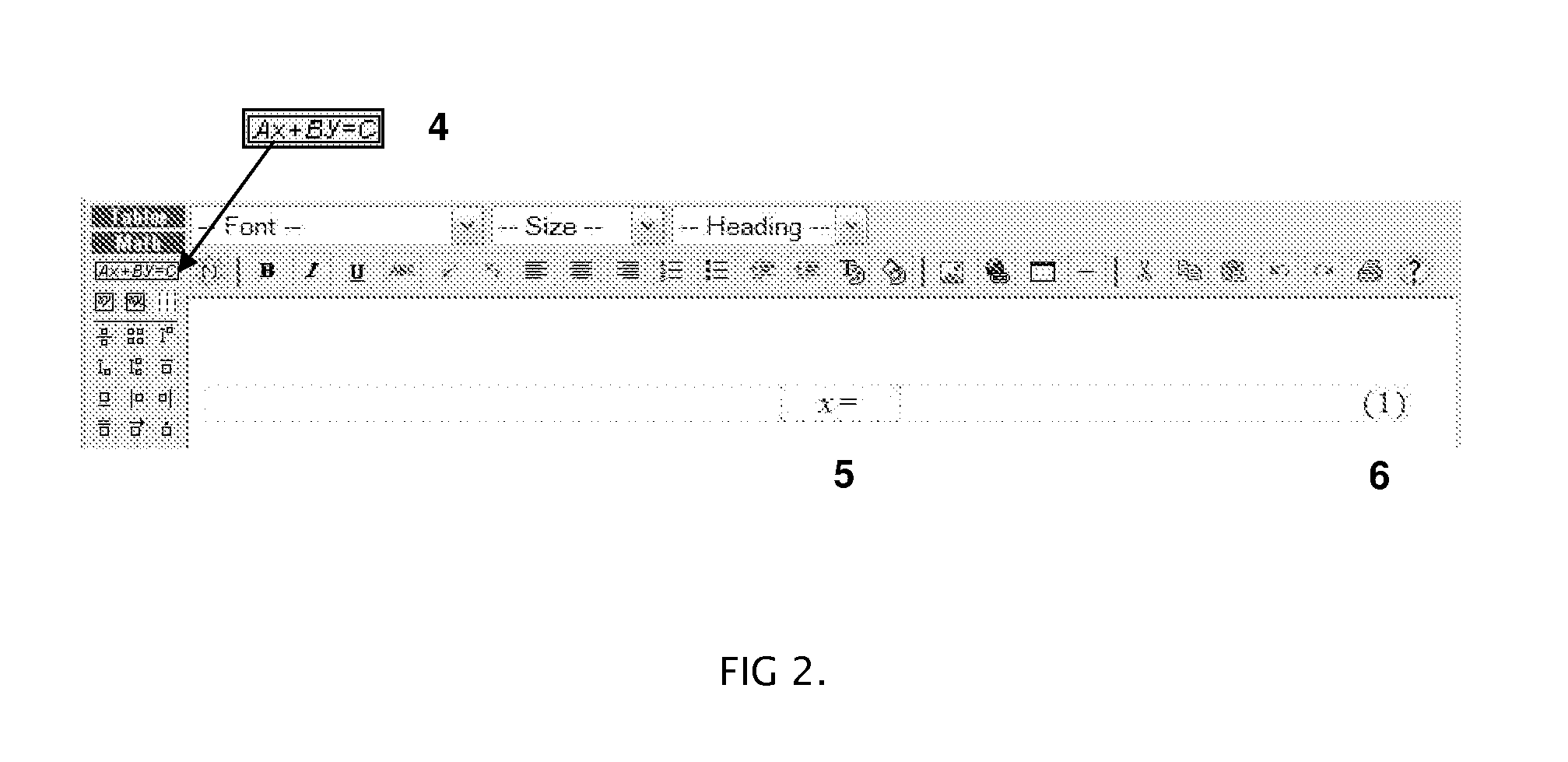
System and method for generating mathematical equations and symbolic scientific expressions in HTML and css
InactiveUS20080120355A1Input/output for user-computer interactionNatural language data processingGraphicsTheoretical computer science
Owner:ALABI KEHINDE
Median filtering implementation method for integrated circuit design
InactiveCN104811161AIncrease the median filter rateDigital technique networkTheoretical computer scienceIntegrated circuit
The invention discloses a median filtering implementation method for integrated circuit design. The median filtering implementation method for the integrated circuit design is implemented based on a memory and an FSM. The median filtering implementation method for the integrated circuit design comprises the step S1 of initialization and the step S2 of filtering output. The step S1 of initialization comprises the step that N data which are sorted by size are stored in the memory according to a data structure so as to establish a data table, wherein when the number of stored data is smaller than N, and new data come, polling is conducted from any one end of a stored sorted data table, the stored data and the new data are compared, the appropriate positions of the new data in the sorted data table are found out, the new data are inserted into the sorted data table, and the new data are inserted one by one until the number of the data is equal to N, and therefore initialization is completed. The step S2 of filtering output comprises the steps that the data table is reestablished in a deletion and insertion mode according to the time sequence on the basis of the established data table, and a median of the N data is outputted according to the reestablished data table. When the median filtering implementation method is applied, the hardware cost can be reduced, the median filtering rate can be increased to 700 KHz, the median filtering depth can be increased to 32, and therefore the comprehensive constraint conditions can be changed.
Owner:SHANGHAI PANCHIP MICROELECTRONICS CO LTD
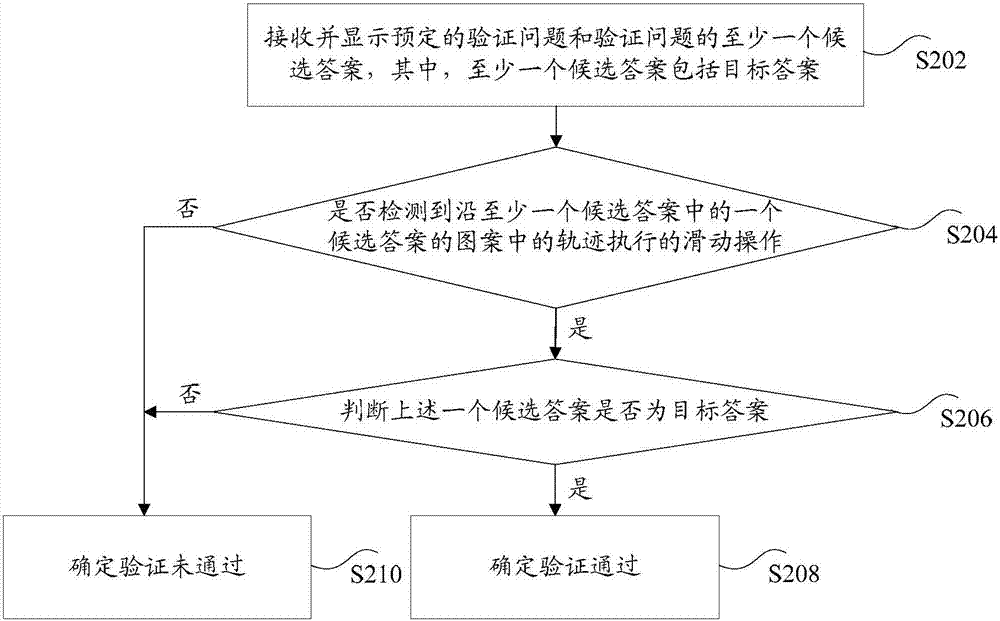
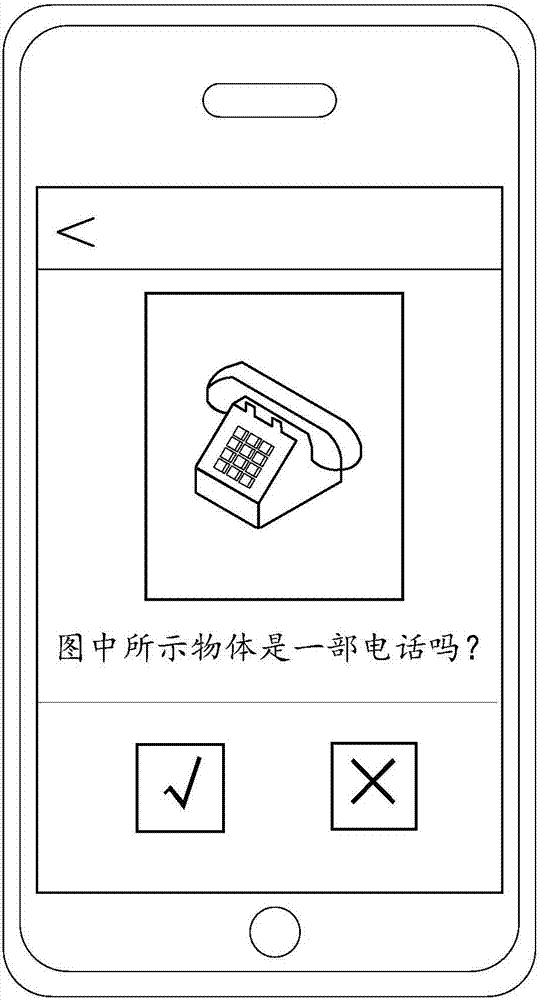
Information verification method and device
PendingCN107301337AImprove reliabilityImprove securityDigital data authenticationInput/output processes for data processingTheoretical computer scienceData mining
Owner:TENCENT TECH (SHENZHEN) CO LTD
Distributed computing unloading method and device based on deep reinforcement learning
PendingCN114449584AFast convergenceReduce complexityMathematical modelsResource allocationInterference ratioTheoretical computer science
The invention relates to a distributed computing unloading method and device based on deep reinforcement learning. The method comprises the steps that a calculation unloading framework is set, a communication model and a calculation model are established according to the calculation unloading framework, the communication model is used for calculating the signal-to-noise-interference ratio of terminal equipment, the calculation model is used for conducting local calculation and edge calculation on the terminal equipment, and the terminal equipment is calculated based on the calculation unloading framework, the communication model and the calculation model. And modeling a calculation unloading problem into a Markov decision process, and carrying out optimization iteration solution on the Markov decision process by utilizing a depth deterministic strategy gradient algorithm of the double-Critic network to obtain an unloading decision. Due to the fact that the depth deterministic strategy gradient algorithm of the double Critic networks is used for conducting optimization iteration solution, the double Critic networks are respectively fitted, the complexity of fitting of a single Critic network is reduced, the convergence speed of the Critic networks is improved, and the overall convergence speed of the model is greatly improved.
Owner:HUNAN UNIV
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap