Security detection method, device and system based on iOS application
A security detection and safety technology, applied in decompilation/disassembly, program code conversion, instrumentation, etc., can solve problems such as incomplete detection, unautomated security detection, and damage to user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
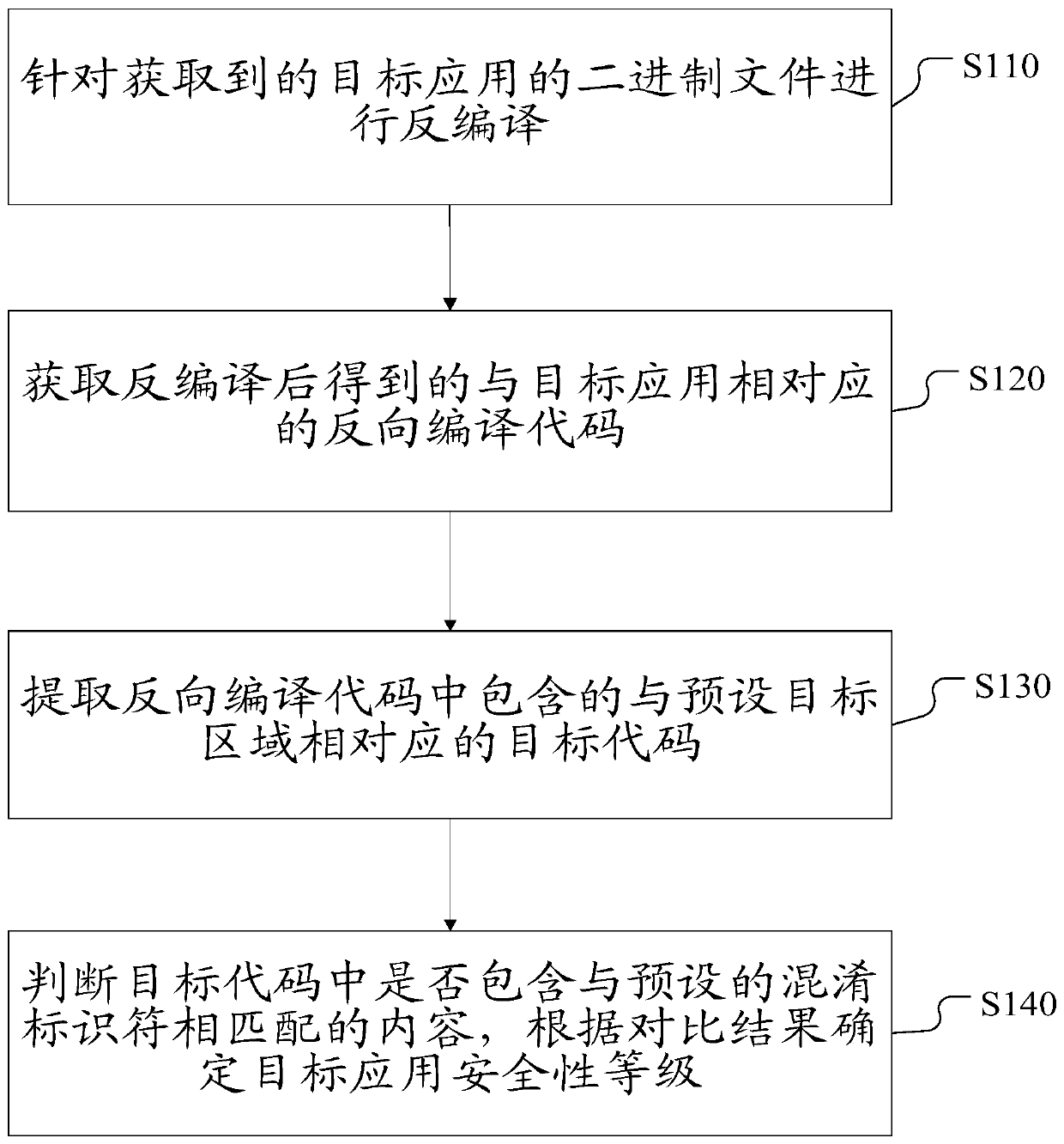
[0031] figure 1 A flow chart of a security detection method for an iOS application according to Embodiment 1 is shown. Such as figure 1 As shown, the method includes the following steps:
[0032] Step S110: Decompile the acquired binary file of the target application.
[0033] The execution subject of the present invention can be various, for example, it can be a security software client installed inside the mobile terminal where the target application is located, or a security testing terminal or a security testing terminal capable of communicating with the mobile terminal where the target application is located. server.
[0034] Wherein, the target application is an application to be detected, the application is an iOS application, and the binary file of the target application specifically includes: using a decompression tool to decompress the IPA package of the target application to obtain the binary file of the target application.
[0035] Specifically, in this step, a de
Embodiment 2
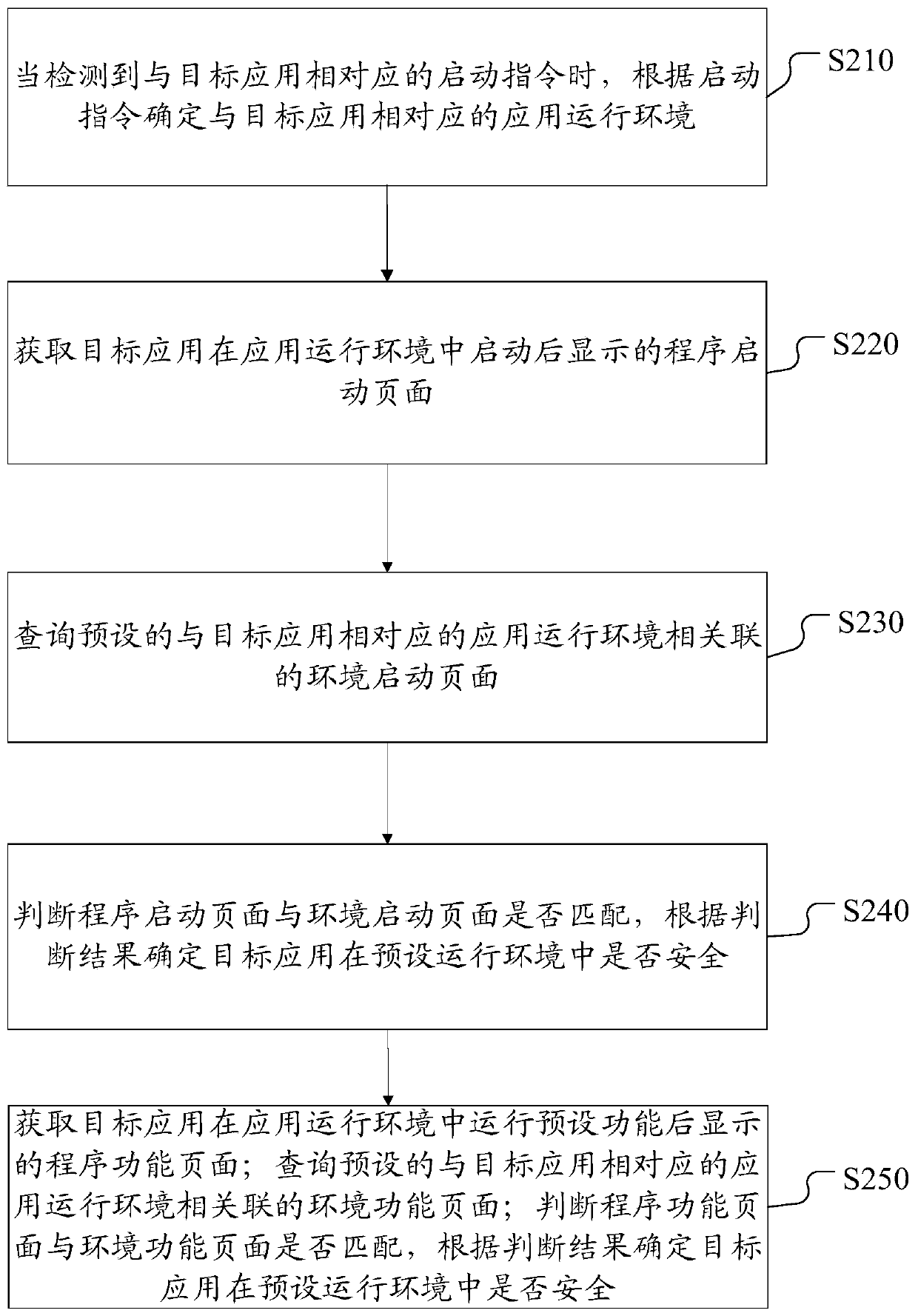
[0045] figure 2 A flow chart of a method for detecting security of a target application according to Embodiment 2 is shown.
[0046] In this embodiment, security detection is performed on the target application from the perspective of the running environment of the target application. Since iOS applications can run on various iOS systems and different iPhone devices, but the iOS system version of iOS applications and different iPhone device models are iteratively updated very quickly, it is necessary to ensure that iOS applications can run normally in various operating environments.
[0047] Such as figure 2 As shown, the method includes the following steps:
[0048] Step S210: When an activation instruction corresponding to the target application is detected, determine an application running environment corresponding to the target application according to the activation instruction.
[0049] The execution subject of the present invention can be various, for example, it can
Embodiment 3
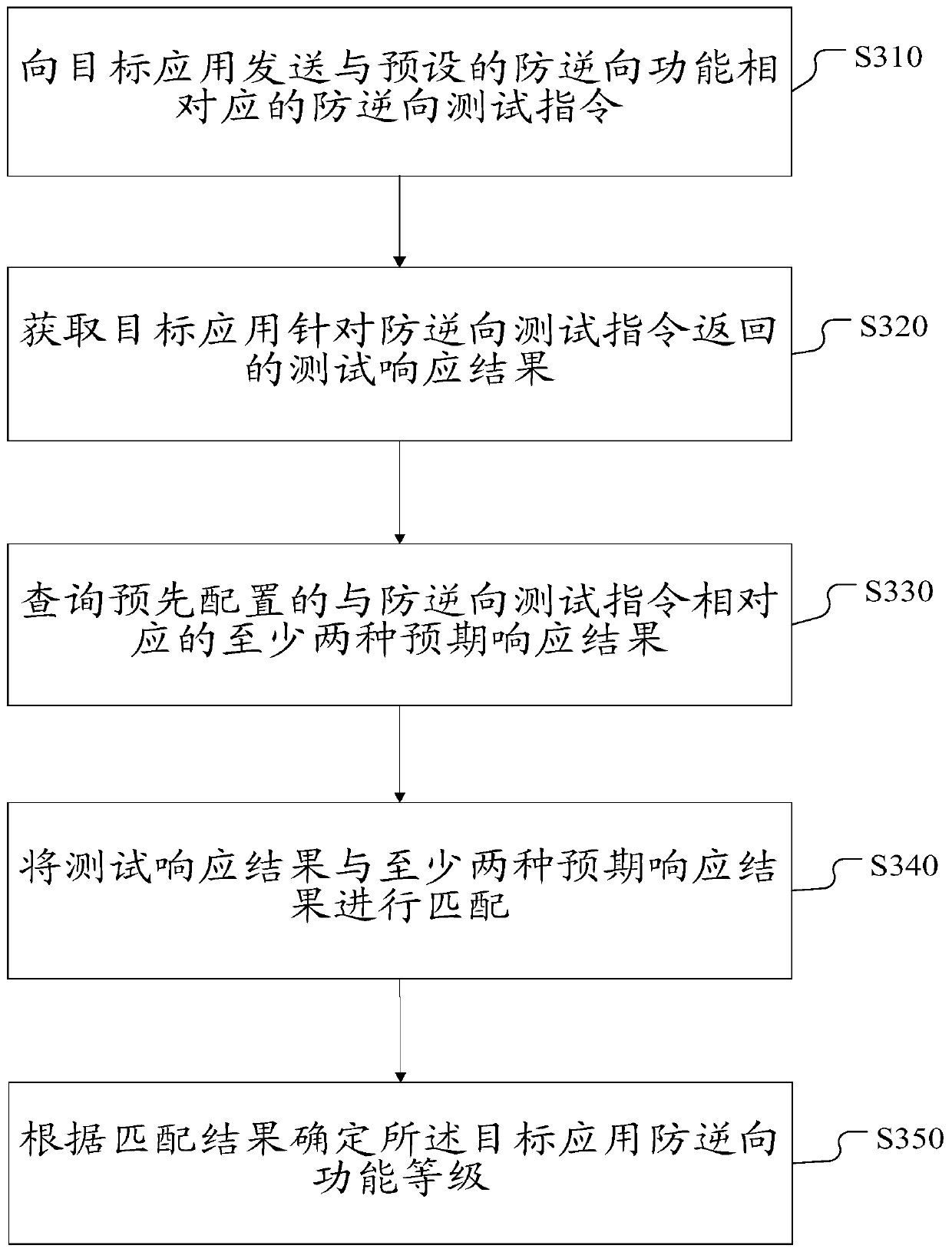
[0075] image 3 A flow chart of a method for detecting security of a target application according to Embodiment 3 is shown.
[0076] This embodiment performs security detection on the target application from the perspective of anti-reversal of the target application. At present, the phenomenon of debugging the source code of the application, intercepting the running process of the application, and injecting the dynamic library is serious. The anti-reverse function detection of the application can evaluate the strength of the anti-reverse function of the application, and find the defects of the anti-reverse function of the application early.
[0077] Such as image 3 As shown, the method includes the following steps:
[0078] Step S310: sending an anti-reverse test instruction corresponding to a preset anti-reverse function to the target application.
[0079] The execution subject of the present invention can be various, for example, it can be a security software client install
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap