SO file security reinforcement/calling method and system and reversible matrix generation server
A server and inverse matrix technology, applied in the direction of computer security devices, instruments, program/content distribution protection, etc., can solve problems such as source code security reinforcement of SO files, and achieve the effect of improving the difficulty of deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
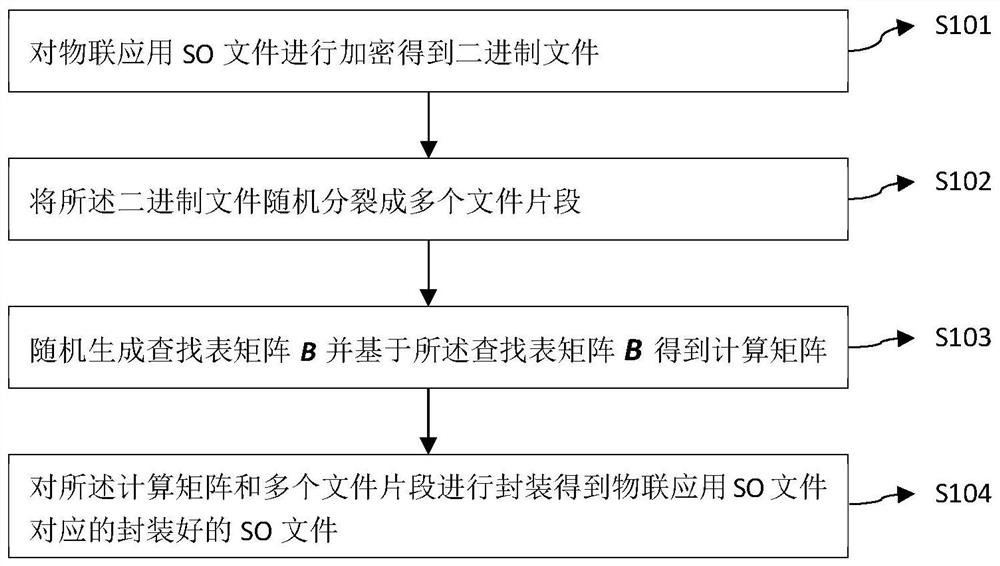
[0082] like figure 1 As shown, the present invention provides a SO file security hardening method, including: in the SO file security hardening system,
[0083] S101: Encrypt the SO file of the IoT application to obtain a binary file;
[0084] S102: Randomly split the binary file into multiple file segments;
[0085] S103: Randomly generate a lookup table matrix B and obtain a calculation matrix based on the lookup table matrix B;
[0086] S104: Encapsulate the calculation matrix and multiple file fragments to obtain an encapsulated SO file corresponding to the IoT application SO file.
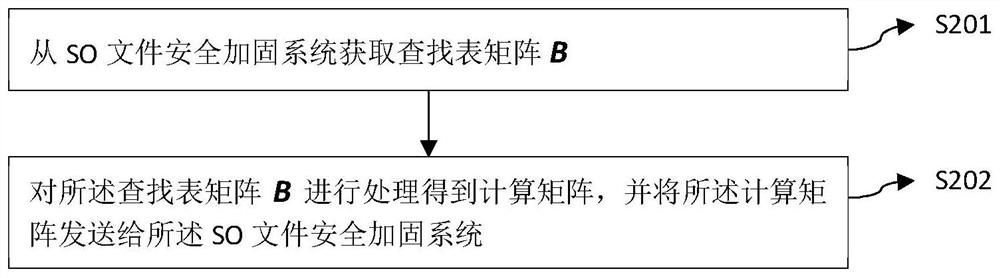
[0087] S103 in the present invention: randomly generate the lookup table matrix B and obtain the calculation matrix based on the lookup table matrix B, the randomly generated lookup table matrix B can be sent to the reversible matrix generation server, and the reversible matrix generation server performs the lookup table matrix B The calculation matrix is obtained through processing; when th
Embodiment 2
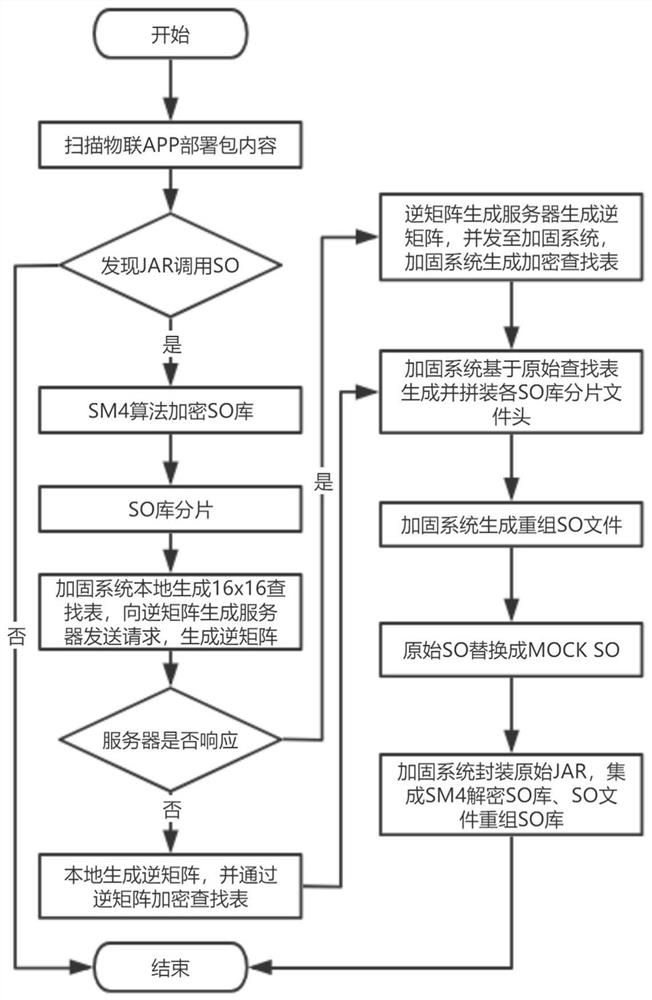
[0102] After the security hardening of the SO file, the SO file is encapsulated into a JAR package. Since the preprocessing process of the SO file needs to be performed before running the application JAR package, it is necessary to use a shell JAR file to integrate and serially reorganize the SO file, and SM4 to decrypt the SO file and the original JAR file. order of execution. The shell JAR file needs to meet:
[0103] 1. Replace with the same name as the original JAR file;
[0104] 2. The shell JAR uses the JNI mechanism to call the reorganized SO file first, then call SM4 to decrypt the SO file, and finally call the original JAR file;
[0105] 3. The driver shell JAR file must fully receive the input commands and parameters, and pass the commands and parameters to the original JAR file for execution.
[0106] Therefore the present invention also provides a calling method of SO file, such as Figure 11 As shown, when the IoT application calls the SO file during the execution
Embodiment 3
[0124] Based on the same inventive concept, the present invention also provides a calling system for SO files, including: shell files;
[0125] The shell file is used to: reorganize the pre-packaged SO file; then decrypt the reorganized SO file to obtain the IoT application SO file; execute operations on the IoT application SO file by calling the original JAR file;
[0126] Here, the SO file is encapsulated by using the SO file security hardening method provided by the present invention.
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap